Cisco Firewall Basics
|
|
|
- Virgil Riley
- 6 years ago
- Views:
Transcription
1
2 Cisco Firewall Basics Mark Cairns, Consulting Systems Engineer BRKSEC-1020
3 Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this session in the Cisco Live Mobile App 2. Click Join the Discussion 3. Install Spark or go directly to the space 4. Enter messages/questions in the space Cisco Spark spaces will be available until July 3, cs.co/clus17/#brksec Cisco and/or its affiliates. All rights reserved. Cisco Public
4 BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 4
5 Mark Cairns Consulting Systems Engineer, GSSO, supporting US Commercial Based in Richmond, VA and cover accounts in Virginia and Washington DC 19 years experience with Cisco Security Solutions You can reach me at BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 5
6 Session Information Cisco Firewall Basics This is an introductory 1000 level session It is not meant for professionals with deep knowledge of firewalls and Cisco ASA This session is not for you if you want to deep dive into configurations for specific features / functionality References may be made to advanced functionality for context but we will stay at a fairly high level BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 6
7 Follow up Sessions Deeper dives on specific content Session ID Session Description Time BRKSEC-2058 A Deep Dive into using the Firepower Manager Wed 4:00-5:30 BRKSEC-3007 Advanced Cisco IOS Security Tuesday 1:30-3:30 BRKSEC-3300 Advanced IPS Deployment Thursday 8:30-10:00 BRKSEC-3690 Advanced Security Group Tags Monday 1:30-3:30 BRKSEC-2050 ASA Firepower NGFW typical deployment scenarios Monday 1:30-3:30, Tuesday 1:30-3:30 BRKSEC-2033 Best Security and deployment strategies SMB NGFW Tuesday 8:00-10:00 BRKSEC-2342 Branch Router Security Thursday 10:30-12:00 BRKSEC-2055 Cloud-Managed Security for Distributed Networks with Cisco Meraki MX Wednesday 4-5:30 BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 7
8 Follow up Sessions Deeper dives on specific content Session ID Session Description Time BRKSEC-2203 Deploying TrustSec Security Group Tagging Tuesday 4:00-5:30 BRKSEC-3455 Dissecting Firepower NGFW "Installation & Troubleshooting" Tuesday 1:30-3:30 BRKSEC-3035 Firepower Platform Deep Dive Wednesday 1:30-3:30 LTRSEC-1000 Firepower Threat Defense Deployment Hands-on Lab Wed 8:00-12:00, Thursday 8:00-12:00 BRKSEC-3032 NGFW Clustering Deep Dive Tuesday 8:00-10:00 BRKSEC-2020 NGFW Deployment in the Data Center and Network Edge Using Firepower Threat Defense Tuesday 8:00-10:00, Wed 1:30-3:30 BRKSEC-2064 NGFW and ASAv in Public Cloud (AWS and Azure) Thursday 1:00-2:30 BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 8
9 Agenda Introduction Firewalls in General Use Cases - Why Firewall Options - What Introduction to Firepower Advanced Use Case Examples Q&A Feel free to ask questions
10 Firewalls in General
11 Securing/Hardening for What Purpose or Need? Subversion Bots, Viruses, and Worms Spyware and Adware Disruption Denial of service attacks Advanced Persistent Threats (APTs) Penetration Attempt Zero-day Attacks Hacker Attacks Data Loss Data theft and/or interception Identity theft BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 11
12 Firewalls What are they? Primary filtering appliances/vms that work at both the network and application layers Provide a platform for the features/functionality needed for network security VPNs (remote-access and site to site) NGIPS Anti-Malware Protection Next-generation security should not abandon proven stateful inspection capabilities in favor of application and user ID awareness by itself Comprehensive network security solution needs include firewalls, next-generation firewalls (application inspection and filtering) and next generation intrusion prevention systems (context aware) The firewall often is the conduit from which other defense components combat the threats that face the network BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 12
13 Filtering on a Tuple? Packet The genesis of firewalls was initially a means to filter traffic based on the five tuple Source IP address the IP address of the initiator of the IP packet Destination IP Address the IP address of the destination of the IP packet Source Port UDP or TCP port used by initiator to establish communications with destination Destination Port UDP or TCP port used by destination to establish communications with source IP Protocol the specific IP protocol used in the communication BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 13
14 Filtering IP Protocols Packet ICMP (1) TCP (6) UDP (17) GRE (47) ESP (50) AH (51) EIGRP (88) OSPF (89) BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 14
15 Stateful Inspection Most routers and switches can filter based on the five tuple why a firewall then? Stateful firewalls track L3/L4 traffic as it leaves and returns to the network Connections are maintained in the connection table tracking five tuple and additional information such as sequence TCP outside: /80 ( /80) inside: /35478 ( /35478), flags UIO, idle 4m39s, uptime 6m16s, timeout 1h0m, bytes 3002 *Best Practice Limit outbound connections to known services and hosts such as SMTP servers only for port 25. Src IP Dest IP Src Port TCP/80 Dest Port TCP/35478 Packet Packet Src IP Dest IP Src Port TCP/35478 Dest Port TCP/80 BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 15
16 Network Address Translation Network address translation (NAT) is the mapping of IP addresses from a private network to a public network NAT gives network administrators and security administrators: Access to non-publically routable IPv4 space Cost savings because addresses are not cheap Allows for masquerading of internal network addresses IPv4 Address space is exhausted Src IP Dest IP Src Port TCP/35478 Dest Port TCP/80 Packet Src IP Dest IP Src Port TCP/35478 Dest Port TCP/80 BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 16
17 Use Cases
18 Use Case #1 Hospitality, Retail or other similar distributed deployment Remote sites 100+ Direct Internet Access (DIA) at remote sites Company has a Cloud First mandate 4 Network / Security Engineers ( jack of all trades, master of none ) Basic security needs for URL filtering, DNS security, IPS Need VPN connectivity to HQ BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 18
19 Cloud Networking Group BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 19
20 Meraki MX Options Reference Small branch Midsized branch MX64(W) MX65(W) MX84 MX100 ~50 users ~50 users ~200 users ~500 users ac wireless ac wireless & PoE+ Dedicated WAN uplinks Gigabit uplinks FW throughput: 250 Mbps FW throughput: 250 Mbps FW throughput: 500 Mbps FW throughput: 750 Mbps Large branch or campus Teleworker MX400 MX600 Z1 ~2,000 users ~10,000 users 1-5 users Modular interface Modular interface Dual-radio wireless FW throughput: 1 Gbps FW throughput: 1 Gbps FW throughput: 50 Mbps All devices support 3G/4G BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 20
21 Meraki MX Security Next Generation Firewall Application aware firewalling Intrusion Prevention (IPS) Based on Cisco Snort URL Content Filtering Geo-based security With over 80 categories and over 4 billion categorized URLs Allow or block traffic by country Malware Protection Automatic updates PCI compliance Cisco AMP and Threat Grid Software and security updates delivered from the cloud PCI 3.2 certified cloud management backend BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 21
22 Meraki MX Basics BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 22
23 Meraki MX Basics continued BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 23
24 Meraki MX Basics continued BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 24
25 Meraki Threat and Filtering BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 25
26 Meraki Threat and Filtering continued Cisco Umbrella BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 26
27 Use Case #2 Regional Services Company 8 sites on MPLS with ISR routers deployed Broadband Internet being added for DMVPN backup/redundancy (IWAN) Simple filter to protect the new Internet link HQ has a proxy for Internet BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 27
28 Securing the WAN Typical MPLS WAN Does not ensure privacy Best Practice Consider encryption across existing WAN BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 28
29 Internet based WAN Lower cost alternative to MPLS Dictates VPN for routing and privacy Balance complexity with features and functionality Typically no need for inbound access directly from Internet BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 29
30 Zone Based Firewall BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 30
31 Zone Based Firewall Support for: ISR, ASR, CSR NAT WAAS VRFs Redundancy VTIs for VPNs Deep Packet Inspection Trusted G0/1.101 G0/1.103 Note: For simple inside to outside configuration, remove all reference to DMZ interface. This DMZ configuration assumes a second security device to filter traffic or terminate VPN. DMZ All Traffic Permit G0/0 Internet TCP/UDP/ICMP Response OK BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 31
32 Configuring ZBF zone security Internet zone security Trusted zone security DMZ Create Zones interface LISP0 zone-member security DMZ! interface GigabitEthernet0/0 description Public Outside zone-member security Internet! interface GigabitEthernet0/1.101 description Inside zone-member security Trusted! interface GigabitEthernet0/1.103 description Public DMZ zone-member security DMZ Assign interfaces to security zones Note: For simple inside to outside configuration, remove all reference to DMZ interface. This DMZ configuration assumes a second security device to filter traffic or terminate VPN. BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 32
33 Configuring ZBF class-map type inspect match-any All_Protocols description - Match all outgoing protocols match protocol tcp match protocol udp match protocol icmp Note: For simple inside to outside configuration, remove all reference to DMZ interface. This DMZ configuration assumes a second security device to filter traffic or terminate VPN. Create Inspection Class policy-map type inspect trusted-to-internet class type inspect All_Protocols inspect class class-default drop policy-map type inspect DMZ class class-default pass Create Inspection Policy zone-pair security Trusted->Internet source Trusted destination Internet service-policy type inspect trusted-to-internet zone-pair security Internet->DMZ source Internet destination DMZ service-policy type inspect DMZ zone-pair security DMZ->Internet source DMZ destination Internet service-policy type inspect DMZ Create Zone Pairs and Associate Policy BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 33
34 Use Case #2 (Variant) Regional Services Company 8 sites on MPLS with ISR routers deployed Broadband Internet being added for DMVPN backup and DIA Simple Complete filter to protect the new Internet link Firepower Virtual VMware / KVM BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 34
35 Internet based WAN Lower cost alternative to MPLS Dictates VPN for routing and privacy Balance complexity with features and functionality Typically no need for inbound access directly from Internet Direct Internet Access (DIA) adds security risk BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 35
36 Use Case #3 Data Center upgrade Adding security to new design No L3 hop for security to reduce convergence time N+1 redundancy Multi 10 Gbps throughput BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 36
37 Data Center A/S or Clustering for Performance and Scale Firepower 9300 with SM-24, SM-36 or SM-44 Firepower 4110, 4120, 4140 or 4150 Firepower 2110, 2120, 2130*, 2140* *10 Gig Interfaces BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 37
38 Data Center Specifications Reference *Note 2100 models do not support clustering. Only 2130 and 2140 support 10 Gbps interfaces and optional network module. BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 38
39 Firepower 2100 Series FPR x 1G 12x 10G Port Firepower 2100 High Performance, Purpose Built Hardware for Cisco NGFW FPR x-1G 12x 10G Port Firepower 2100 Available in 4 Platforms FPR x 1G Port Firepower 2100 Higher Port Density in 1 Rack Unit FPR x 1G Port Firepower Gbps Support (2130 and 2140) BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 39
40 Data Center Clustering for Performance and Scale Handles asymmetric traffic associated with VPC/VSS N+1 redundancy Keeps DC design intact Scale to 16 firewalls BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 40
41 Data Center ACI Deployments APIC Agility and Visibility Simplicity Automation Scale and Performance Security Open BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 41
42 Use Case #4 Cloud expansion / Cloud First AWS and/or Azure Need to replicate security / inspection policy for cloud traffic Your Data Here BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 42
43 Cisco ASAv and Threat Defense Virtual Cisco ASA 9 Feature Set / Threat Defense 6 Cisco ASAv FTDv ASA 10 vnic interfaces and VLAN tagging Virtualization displaces multiple-context and clustering Parity with all other Cisco ASA platform features SDN (Cisco APIC) and traditional (Cisco ASDM and CSM) management tools Dynamic routing includes OSPF, EIGRP, and BGP REST API for programmed configuration and monitoring Cisco TrustSec PEP with SGT-based ACLs Failover Active/Standby HA model FTDv 4 vnic default 8 GB RAM, 4 vcpu VMware, KVM, Hyper V (ASA only), AWS, Azure (features can differ for cloud) BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 43
44 Cisco ASAv Platforms Cisco ASAv5 100 Mbps Cisco ASAv10 1 Gbps Cisco ASAv30 2 Gbps * Lab Edition license is built in with 100-Kbps throughput and 100 total connections allowed BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 44
45 Cisco ASAv Platforms Cisco ASAv50 10 Gbps Introduced with ASA release 9.8(1) Supported on KVM or ESXi Uses IXGBE-VF vnic Does not support Transparent mode (promiscuous restriction on IXGBE-VF) Not supported in Amazon Web Services, Microsoft Azure or Hyper-V BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 45
46 ASAv and/or NGFW Supported in both AWS and Azure *Note restrictions based on cloud deployment BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 46
47 Meraki Virtual MX for AWS (vmx100) Appears in the dashboard 500 Mbps VPN throughput Bring Your Own License (BYOL) BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 47
48 Use Case #5 Typical Internet Edge designs Outbound Internet (Web, , FTP, etc) Inbound traffic to DMZ and/or ecommerce VPN for Remote Access, L2L, business partners BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 48
49 Edge With DMZ Similar to a basic edge design with the addition of inbound traffic Traffic inbound from the DMZ to the trusted network may or may not pass the firewall. BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 49
50 Edge With DMZ - VPN Multiple path options for VPN with trusted and untrusted packets. VPN Concentrator may be connected outside the firewall Trusted traffic path usually depends on source. Employee or Vendor, B2B, etc. *Best Practices Remember that controlling access from a VPN to an internal resource is not a dead end! Jump box scenario. Hide your firewall with private IP space on the outside. BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 50
51 Tiered DMZs Typically seen in multi-tiered hosting for e-commerce Forces all traffic between tiers to pass firewall rules Can help mitigate risk and contain exploits and/or breaches within a DMZ BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 51
52 Bridge across your DMZs Sometimes referred to as clean and dirty DMZs VPN, Video, etc. Avoids hair-pinning *Best Practice Use destination NAT with a block of unused private IPs for outbound L2L VPN instead of routing individual remote IPs. BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 52
53 Split Firewalls Layer 3 hop between firewalls Avoids hair-pinning within a firewall Simplifies policy May still have an optional trusted connection BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 53
54 Quick Hardware Snapshot
55 Portfolio ASA 5506-X ASA 5508-X FPR 2110 FPR 2120 FPR 2130 FPR 2140 FPR 4110 FPR 4120 FPR 4140 FPR 4150 FPR SM-24 FPR SM-36 FPR SM-44 ASA 5516-X ASA 5585-X SSP60 EOS Aug 2017 ASA 5505 EOS Aug 2017 ASA 5515-X ASA 5512-X ASA 5555-X ASA 5545-X ASA 5525-X ASA 5585-X SSP40 ASA 5585-X SSP20 ASA 5585-X SSP10 SMB/SOHO Branch Internet Edge Data Center Service Provider BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 55
56 Latest Additions to the 5500 Portfolio 5506X with Firepower Services Reference Max 250 Mbps AVC throughput Max 125 Mbps AVC and NGIPS 90 Mbps AVC or IPS with 440 byte HTTP ASDM 7.3.x or CSM and Firepower Management Center Available in hardened and wireless configurations BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 56
57 Latest Additions to the 5500 Portfolio 5508X with FirePOWER Services Reference Max 450 Mbps AVC throughput Max 250 Mbps AVC and NGIPS 180 Mbps AVC or IPS with 440 byte HTTP ASDM 7.3.x or CSM, Firepower Management Center, On-box, CDO BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 57
58 Latest Additions to the 5500 Portfolio 5516X with FirePOWER Services Reference Max 850 Mbps AVC throughput Max 425 Mbps AVC and NGIPS 300 Mbps AVC or IPS with 440 byte HTTP ASDM 7.3.x or CSM, Firepower Management Center, On-box, CDO BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 58
59 Over, Through or Around The Wall
60 Things Change BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 60
61 If you knew you were going to be compromised, would you do security differently? BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 61
62 The package Chicken Pox Virus Tracking history Sender Receiver Reputation? Content (deep packet inspection) Vaccine BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 62
63 The Threat-Centric Firewall Proven Cisco ASA firewalling Industry leading NGIPS and AMP Cisco ASA with FirePOWER Services Integrating defense layers helps organizations get the best visibility Enable dynamic controls to automatically adapt Protect against advanced threats across the entire attack continuum BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 63
64 Indications of Compromise (IoCs) IPS Events Malware Backdoors Exploit Kits Web App Attacks CnC Connections Admin Privilege Escalations SI Events Connections to Known CnC IPs Malware Events Malware Detections Office/PDF/Java Compromises Malware Executions Dropper Infections BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 64
65 Application Visibility and Control BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 65
66 IPS with Snort BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 66
67 Host Profiles What OS? What Services? What Applications? What Vulnerabilities? BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 67
68 Impact Assessment Impact Flag Administrator Action Why Act immediately, vulnerable Investigate, potentially vulnerable Good to know, currently not vulnerable Good to know, unknown target Good to know, unknown network Event corresponds to vulnerability mapped to host Relevant port open or protocol in use, but no vuln mapped Relevant port not open or protocol not in use Monitored network, but unknown host Unmonitored network BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 68
69 Advanced Malware Analysis BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 69
70 Network File Trajectory Where Has It Been Seen? BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 70
71 SSL Inspection issues? - AMP for Endpoints BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 71
72 Firepower NGFW
73 Introducing Cisco Firepower NGFW Fully Integrated Threat Focused Unified Management FW / applications / IPS Cisco AMP network / endpoint Analysis and remediation Cisco security solutions Application-aware DDoS Networkwide visibility Industry-best threat protection Known and unknown threats Track / contain / recover Across attack continuum Manage, control, and investigate Automatically prioritize Automatically protect BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 73
74 Firepower 6.x on ASA Upgrade vs Re-Image Choose Firepower Services or Firepower Threat Defense Firepower Software on ASA Platforms Firepower Services 5.4 ASA 9.5.x Upgrade Re-Image Firepower Services 6.0 ASA 9.5.x* vs Firepower Threat Defense Firepower 9300 ASA or TD Firepower 4100 ASA or TD Firepower 2100 TD Only *Firepower Services 6.x compatible ASA Version Required BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 74
75 Firepower 6.x Virtual Upgrade vs Migrate Choose NGIPSv + ASAv or Firepower Threat Defense Firepower NGIPSv 5.4 ASAv Upgrade Migrate Upgrade Firepower NGIPSv 6.0 Firepower Threat Defense Virtual 6.0 ASAv BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 75
76 FXOS Chassis Operating System BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 76
77 FXOS Chassis Operating System - Continued BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 77
78 FXOS Chassis Operating System - Continued BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 78
79 Advanced Use Cases
80 SXP ASA Policy Enforcement with MDM WLC ASA 9 3 Policy on ASA by Security Group Web Server AP Security Group Query 8 Leverage security groups to authorize endpoints based on MDM compliance. 4 1 Create Security Groups on ISE 1 Compliant 2 Non-Compliant 6 ISE MDM Compliance check BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 80
81 TrustSec Demo
82 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 82
83 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 83
84 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 84
85 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 85
86 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 86
87 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 87
88 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 88
89 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 89
90 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 90
91 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 91
92 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 92
93 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 93
94 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 94
95 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 95
96 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 96
97 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 97
98 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 98
99 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 99
100 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 100
101 TrustSec (WLC, ISE, ASA, Firepower) Reference BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 101
102 Correlation
103 Custom Security Intelligence Correlate an action(s) with a remediation (in this case, create a custom security intelligence block list) In this example we are looking for blocking events based on geolocation and dropping the source IP into the custom security intelligence list. Monitor the events in Firepower Manager for a match against a rule. The remediation runs a perl script on the Firepower Manager, which leverages the remediation framework to parse event information. BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 103
104 Custom Security Intelligence BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 104
105 Custom Security Intelligence BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 105
106 Custom Security Intelligence BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 106
107 Custom Security Intelligence BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 107
108 Custom Security Intelligence BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 108
109 Custom Security Intelligence BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 109
110 Custom Security Intelligence BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 110
111 Custom Security Intelligence BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 111
112 Custom Security Intelligence BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 112
113 Custom Security Intelligence BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 113
114 Custom Security Intelligence BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 114
115 Reference Material
116 Support Tools BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 116
117 Security Threats and Notifications Current News Proactive Notifications BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 117
118 BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 118
119 SAFE Architecture BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 119
120 Complete Your Online Session Evaluation Give us your feedback to be entered into a Daily Survey Drawing. A daily winner will receive a $750 gift card. Complete your session surveys through the Cisco Live mobile app or on Don t forget: Cisco Live sessions will be available for viewing on demand after the event at Cisco and/or its affiliates. All rights reserved. Cisco Public
121 Continue Your Education Demos in the Cisco campus Walk-in Self-Paced Labs Lunch & Learn Meet the Engineer 1:1 meetings Related sessions BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 121
122 Thank you
123
124 Cybersecurity Cisco Education Offerings Course Description Cisco Certification Understanding Cisco Cybersecurity Fundamentals (SFUND) Implementing Cisco Cybersecurity Operations (SECOPS) The SECFND course provides understanding of cybersecurity s basic principles, foundational knowledge, and core skills needed to build a foundation for understanding more advanced cybersecurity material & skills. This course prepares candidates to begin a career within a Security Operations Center (SOC), working with Cybersecurity Analysts at the associate level. CCNA Cyber Ops CCNA Cyber Ops Securing Cisco Networks with Threat Detection and Analysis (SCYBER) Cisco Security Product Training Courses Designed for security analysts who work in a Security Operations Center, the course covers essential areas of security operations competency, including SIEM, Event monitoring, security event/alarm/traffic analysis (detection), and incident response Official deep-dive, hands-on product training on Cisco s latest security products, including NGFW, ASA, NGIPS, AMP, Identity Services Engine, and Web Security Appliances, and more. For more details, please visit: or Questions? Visit the Learning@Cisco Booth Cisco Cybersecurity Specialist BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 124
125 Cybersecurity Cisco Education Offerings Course Description Cisco Certification New! CCIE Security 5.0 Implementing Cisco Edge Network Security Solutions (SENSS) Implementing Cisco Threat Control Solutions (SITCS) v1.5 Implementing Cisco Secure Access Solutions (SISAS) Implementing Cisco Secure Mobility Solutions (SIMOS) Implementing Cisco Network Security (IINS 3.0) Configure Cisco perimeter edge security solutions utilizing Cisco Switches, Cisco Routers, and Cisco Adaptive Security Appliance (ASA) Firewalls Implement Cisco s Next Generation Firewall (NGFW), FirePOWER NGIPS (Next Generation IPS), Cisco AMP (Advanced Malware Protection), as well as Web Security, Security and Cloud Web Security Deploy Cisco s Identity Services Engine and 802.1X secure network access Protect data traversing a public or shared infrastructure such as the Internet by implementing and maintaining Cisco VPN solutions Focuses on the design, implementation, and monitoring of a comprehensive security policy, using Cisco IOS security features CCIE Security CCNP Security CCNA Security For more details, please visit: or Questions? Visit the Learning@Cisco Booth BRKSEC Cisco and/or its affiliates. All rights reserved. Cisco Public 125
Cisco Next Generation Firewall and IPS. Dragan Novakovic Security Consulting Systems Engineer
 Cisco Next Generation Firewall and IPS Dragan Novakovic Security Consulting Systems Engineer Cisco ASA with Firepower services Cisco TALOS - Collective Security Intelligence Enabled Clustering & High Availability
Cisco Next Generation Firewall and IPS Dragan Novakovic Security Consulting Systems Engineer Cisco ASA with Firepower services Cisco TALOS - Collective Security Intelligence Enabled Clustering & High Availability
Cloud-Managed Security for Distributed Networks with Cisco Meraki MX
 Cloud-Managed Security for Distributed Networks with Cisco Meraki MX Joe Aronow, Product Architect Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this
Cloud-Managed Security for Distributed Networks with Cisco Meraki MX Joe Aronow, Product Architect Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this
Resilient WAN and Security for Distributed Networks with Cisco Meraki MX
 Resilient WAN and Security for Distributed Networks with Cisco Meraki MX Daghan Altas, Director of Product Management BRKSEC-2900 Agenda Problem Cisco CNG Live network creation demo (45m) Product Brief
Resilient WAN and Security for Distributed Networks with Cisco Meraki MX Daghan Altas, Director of Product Management BRKSEC-2900 Agenda Problem Cisco CNG Live network creation demo (45m) Product Brief
Cisco Firepower Thread Defence. Claudiu Boar
 Cisco Firepower Thread Defence Claudiu Boar Security everywhere Stop threats at the edge Control who gets onto your network Find and contain problems fast Protect users wherever they work Simplify network
Cisco Firepower Thread Defence Claudiu Boar Security everywhere Stop threats at the edge Control who gets onto your network Find and contain problems fast Protect users wherever they work Simplify network
Cisco ASA with FirePOWER Services
 Cisco ASA with FirePOWER Services TDM Thomas Jankowsky Consulting Systems Engineer May 2015 Introduction Industry s First Threat-Focused Next-Generation Firewall (NGFW) Proven Cisco ASA firewalling Industry-leading
Cisco ASA with FirePOWER Services TDM Thomas Jankowsky Consulting Systems Engineer May 2015 Introduction Industry s First Threat-Focused Next-Generation Firewall (NGFW) Proven Cisco ASA firewalling Industry-leading
Implementing Cisco Edge Network Security Solutions ( )
 Implementing Cisco Edge Network Security Solutions (300-206) Exam Description: The Implementing Cisco Edge Network Security (SENSS) (300-206) exam tests the knowledge of a network security engineer to
Implementing Cisco Edge Network Security Solutions (300-206) Exam Description: The Implementing Cisco Edge Network Security (SENSS) (300-206) exam tests the knowledge of a network security engineer to
Cisco Firepower NGFW. Anticipate, block, and respond to threats
 Cisco Firepower NGFW Anticipate, block, and respond to threats You have a mandate to build and secure a network that supports ongoing innovation Mobile access Social collaboration Public / private hybrid
Cisco Firepower NGFW Anticipate, block, and respond to threats You have a mandate to build and secure a network that supports ongoing innovation Mobile access Social collaboration Public / private hybrid
The Internet of Everything is changing Everything
 The Internet of Everything is changing Everything Next Generation Security John Tzortzakakis Security Solutions Architect, Security Business Group November 2014 Threat Landscape evolution 60% of data is
The Internet of Everything is changing Everything Next Generation Security John Tzortzakakis Security Solutions Architect, Security Business Group November 2014 Threat Landscape evolution 60% of data is
NGFWv & ASAv in Public Cloud (AWS & Azure)
 & in Public Cloud (AWS & Azure) Anubhav Swami, CCIE# 21208 Technical Marketing Engineer Your Speaker Anubhav Swami answami@cisco.com Technical Marketing Engineer 5 years in Cisco TAC 2 years in ASA BU
& in Public Cloud (AWS & Azure) Anubhav Swami, CCIE# 21208 Technical Marketing Engineer Your Speaker Anubhav Swami answami@cisco.com Technical Marketing Engineer 5 years in Cisco TAC 2 years in ASA BU
Cisco ASA with FirePOWER services Eric Kostlan, Technical Marketing Engineer Security Technologies Group, Cisco Systems LABSEC-2339
 Cisco ASA with FirePOWER services Eric Kostlan, Technical Marketing Engineer Security Technologies Group, Cisco Systems LABSEC-2339 Agenda Introduction to Lab Exercises Platforms and Solutions ASA with
Cisco ASA with FirePOWER services Eric Kostlan, Technical Marketing Engineer Security Technologies Group, Cisco Systems LABSEC-2339 Agenda Introduction to Lab Exercises Platforms and Solutions ASA with
Evolution of Data Center Security Automated Security for Today s Dynamic Data Centers
 Evolution of Data Center Security Automated Security for Today s Dynamic Data Centers Speaker: Mun Hossain Director of Product Management - Security Business Group Cisco Twitter: @CiscoDCSecurity 2 Any
Evolution of Data Center Security Automated Security for Today s Dynamic Data Centers Speaker: Mun Hossain Director of Product Management - Security Business Group Cisco Twitter: @CiscoDCSecurity 2 Any
Cisco - ASA Lab Camp v9.0
 Cisco - ASA Lab Camp v9.0 Code: 0007 Lengt h: 5 days URL: View Online Based on our enhanced SASAC v1.0 and SASAA v1.2 courses, this exclusive, lab-based course, provides you with your own set of equipment
Cisco - ASA Lab Camp v9.0 Code: 0007 Lengt h: 5 days URL: View Online Based on our enhanced SASAC v1.0 and SASAA v1.2 courses, this exclusive, lab-based course, provides you with your own set of equipment
Cisco Firepower NGIPS Tuning and Best Practices
 Cisco Firepower NGIPS Tuning and Best Practices John Wise, Security Instructor High Touch Delivery, Cisco Learning Services CTHCRT-2000 Cisco Spark How Questions? Use Cisco Spark to communicate with the
Cisco Firepower NGIPS Tuning and Best Practices John Wise, Security Instructor High Touch Delivery, Cisco Learning Services CTHCRT-2000 Cisco Spark How Questions? Use Cisco Spark to communicate with the
Cisco Comstor
 Cisco Security @ Comstor 1 Agenda 1. Cisco Security Fundamentals Cyber Security? Cisco Security Solutions - Cisco NGFW - Cisco Umbrella Cisco Meraki, MR, MS, MV and MX Meraki Insight 2 1. Cisco Security
Cisco Security @ Comstor 1 Agenda 1. Cisco Security Fundamentals Cyber Security? Cisco Security Solutions - Cisco NGFW - Cisco Umbrella Cisco Meraki, MR, MS, MV and MX Meraki Insight 2 1. Cisco Security
Next generation branch with SD-WAN and NFV
 Next generation branch with SD-WAN and NFV Kiran Ghodgaonkar, Senior Manager, Enterprise Marketing Mani Ganeson, Senior Product Manager PSOCRS-2004 @ghodgaonkar Cisco Spark How Questions? Use Cisco Spark
Next generation branch with SD-WAN and NFV Kiran Ghodgaonkar, Senior Manager, Enterprise Marketing Mani Ganeson, Senior Product Manager PSOCRS-2004 @ghodgaonkar Cisco Spark How Questions? Use Cisco Spark
Data Center Security. Fuat KILIÇ Consulting Systems
 Data Center Security Fuat KILIÇ Consulting Systems Engineer @Security Data Center Evolution WHERE ARE YOU NOW? WHERE DO YOU WANT TO BE? Traditional Data Center Virtualized Data Center (VDC) Virtualized
Data Center Security Fuat KILIÇ Consulting Systems Engineer @Security Data Center Evolution WHERE ARE YOU NOW? WHERE DO YOU WANT TO BE? Traditional Data Center Virtualized Data Center (VDC) Virtualized
Deploying Intrusion Prevention Systems
 Deploying Intrusion Prevention Systems Gary Halleen Consulting Systems Engineer II Agenda Introductions Introduction to IPS Comparing Cisco IPS Solutions IPS Deployment Considerations Migration from IPS
Deploying Intrusion Prevention Systems Gary Halleen Consulting Systems Engineer II Agenda Introductions Introduction to IPS Comparing Cisco IPS Solutions IPS Deployment Considerations Migration from IPS
Threat Centric Network Security
 BRKSEC-2056 Threat Centric Network Security Ted Bedwell, Principal Engineer Network Threat Defence Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this
BRKSEC-2056 Threat Centric Network Security Ted Bedwell, Principal Engineer Network Threat Defence Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this
Design and Deployment of SourceFire NGIPS and NGFWL
 Design and Deployment of SourceFire NGIPS and NGFWL BRKSEC - 2024 Marcel Skjald Consulting Systems Engineer Enterprise / Security Architect Abstract Overview of Session This technical session covers the
Design and Deployment of SourceFire NGIPS and NGFWL BRKSEC - 2024 Marcel Skjald Consulting Systems Engineer Enterprise / Security Architect Abstract Overview of Session This technical session covers the
We re ready. Are you?
 We re ready. Are you? Deploying Scalable, Resilient WAN Architectures with Meraki MX and IWAN Joe Aronow - Product Specialist, Meraki MX Agenda Introduction: Cloud networking Meraki MX Security Appliances
We re ready. Are you? Deploying Scalable, Resilient WAN Architectures with Meraki MX and IWAN Joe Aronow - Product Specialist, Meraki MX Agenda Introduction: Cloud networking Meraki MX Security Appliances
Cisco ASA 5500-X NGFW
 Cisco ASA 5500-X NGFW Sieťová ochrana pre malé a stredné podniky pred modernými hrozbami Peter Mesjar CCIE 17428, Systémový Inžinier, Cisco What are we going to talk about Problem is THREATS How today
Cisco ASA 5500-X NGFW Sieťová ochrana pre malé a stredné podniky pred modernými hrozbami Peter Mesjar CCIE 17428, Systémový Inžinier, Cisco What are we going to talk about Problem is THREATS How today
Cisco Security. Advanced Malware Protection. Guillermo González Security Systems Engineer Octubre 2017
 Cisco Security Advanced Malware Protection Guillermo González Security Systems Engineer Octubre 2017 The New Security Model Attack Continuum Before During After Before Discover During Detect After Scope
Cisco Security Advanced Malware Protection Guillermo González Security Systems Engineer Octubre 2017 The New Security Model Attack Continuum Before During After Before Discover During Detect After Scope
Business Resiliency Through Superior Threat Defense
 Business Resiliency Through Superior Threat Defense Firepower 2100 Series/ Cisco Identity Services Engine Andre Lambertsen, Consulting Systems Engineer ala@cisco.com Cisco Firepower NGFW Fully Integrated
Business Resiliency Through Superior Threat Defense Firepower 2100 Series/ Cisco Identity Services Engine Andre Lambertsen, Consulting Systems Engineer ala@cisco.com Cisco Firepower NGFW Fully Integrated
Segmentation. Threat Defense. Visibility
 Segmentation Threat Defense Visibility Establish boundaries: network, compute, virtual Enforce policy by functions, devices, organizations, compliance Control and prevent unauthorized access to networks,
Segmentation Threat Defense Visibility Establish boundaries: network, compute, virtual Enforce policy by functions, devices, organizations, compliance Control and prevent unauthorized access to networks,
Agile Security Solutions
 Agile Security Solutions Piotr Linke Security Engineer CISSP CISA CRISC CISM Open Source SNORT 2 Consider these guys All were smart. All had security. All were seriously compromised. 3 The Industrialization
Agile Security Solutions Piotr Linke Security Engineer CISSP CISA CRISC CISM Open Source SNORT 2 Consider these guys All were smart. All had security. All were seriously compromised. 3 The Industrialization
Cisco Cloud Services Router 1000V with Cisco IOS XE Software Release 3.13
 Q&A Cisco Cloud Services Router 1000V with Cisco IOS XE Software Release 3.13 Q. What is the Cisco Cloud Services Router 1000V? A. The Cisco Cloud Services Router 1000V (CSR 1000V) is a router in virtual
Q&A Cisco Cloud Services Router 1000V with Cisco IOS XE Software Release 3.13 Q. What is the Cisco Cloud Services Router 1000V? A. The Cisco Cloud Services Router 1000V (CSR 1000V) is a router in virtual
Cisco Firepower NGFW. Anticipate, block, and respond to threats
 Cisco Firepower NGFW Anticipate, block, and respond to threats Digital Transformation on a Massive Scale 15B Devices Today Attack Surface 500B Devices In 2030 Threat Actors $19T Opportunity Next 10 Years
Cisco Firepower NGFW Anticipate, block, and respond to threats Digital Transformation on a Massive Scale 15B Devices Today Attack Surface 500B Devices In 2030 Threat Actors $19T Opportunity Next 10 Years
A Unified Threat Defense: The Need for Security Convergence
 A Unified Threat Defense: The Need for Security Convergence Udom Limmeechokchai, Senior system Engineer Cisco Systems November, 2005 1 Agenda Evolving Network Security Challenges META Group White Paper
A Unified Threat Defense: The Need for Security Convergence Udom Limmeechokchai, Senior system Engineer Cisco Systems November, 2005 1 Agenda Evolving Network Security Challenges META Group White Paper
Global vision. Local knowledge. Cisco Forum Kyiv Country Day Month Year
 Global vision. Local knowledge. Cisco Forum Kyiv Country Day Month Year Firepower Next Generation Firewall Subtitle goes here William Young Security Solutions Architect, Global Security Architecture Team
Global vision. Local knowledge. Cisco Forum Kyiv Country Day Month Year Firepower Next Generation Firewall Subtitle goes here William Young Security Solutions Architect, Global Security Architecture Team
AlgoSec: How to Secure and Automate Your Heterogeneous Cisco Environment
 BRKPAR-2488 AlgoSec: How to Secure and Automate Your Heterogeneous Cisco Environment Edy Almer How to Secure and Automate Your Heterogeneous Cisco Environment Yogesh Kaushik, Senior Director Cisco Doug
BRKPAR-2488 AlgoSec: How to Secure and Automate Your Heterogeneous Cisco Environment Edy Almer How to Secure and Automate Your Heterogeneous Cisco Environment Yogesh Kaushik, Senior Director Cisco Doug
Advanced CSR Lab with High Availability and Transit VPC
 Advanced CSR Lab with High Availability and Transit VPC Fan Yang, Cisco, Engineer, Technical Marketing Nikolai Pitaev, Cisco, Engineer, Technical Marketing LTRVIR-3004 Agenda Slides (30 Min.): CSR 1000V
Advanced CSR Lab with High Availability and Transit VPC Fan Yang, Cisco, Engineer, Technical Marketing Nikolai Pitaev, Cisco, Engineer, Technical Marketing LTRVIR-3004 Agenda Slides (30 Min.): CSR 1000V
Ciprian Stroe Senior Presales Consultant, CCIE# Cisco and/or its affiliates. All rights reserved.
 Ciprian Stroe Senior Presales Consultant, CCIE#45766 2015 Cisco and/or its affiliates. All rights reserved. Complete cloud-managed networking solution Wireless, switching, security, MDM Integrated hardware,
Ciprian Stroe Senior Presales Consultant, CCIE#45766 2015 Cisco and/or its affiliates. All rights reserved. Complete cloud-managed networking solution Wireless, switching, security, MDM Integrated hardware,
The IINS acronym to this exam will remain but the title will change slightly, removing IOS from the title, making the new title.
 I n t r o d u c t i o n The CCNA Security IINS exam topics have been refreshed from version 2.0 to version 3.0. This document will highlight exam topic changes between the current 640-554 IINS exam and
I n t r o d u c t i o n The CCNA Security IINS exam topics have been refreshed from version 2.0 to version 3.0. This document will highlight exam topic changes between the current 640-554 IINS exam and
Key Security Measures to Enable Next-Generation Data Center Transformation
 Key Security Measures to Enable Next-Generation Data Center Transformation Bill McGee Senior Manager, Security Solutions Cisco Systems, Inc. Agenda Data Center Security Challenges Secure DC Strategies
Key Security Measures to Enable Next-Generation Data Center Transformation Bill McGee Senior Manager, Security Solutions Cisco Systems, Inc. Agenda Data Center Security Challenges Secure DC Strategies
Cisco Cloud Architecture with Microsoft Cloud Platform Peter Lackey Technical Solutions Architect PSOSPG-1002
 Cisco Cloud Architecture with Microsoft Cloud Platform Peter Lackey Technical Solutions Architect PSOSPG-1002 Agenda Joint Cisco and Microsoft Integration Efforts Introduction to CCA-MCP What is a Pattern?
Cisco Cloud Architecture with Microsoft Cloud Platform Peter Lackey Technical Solutions Architect PSOSPG-1002 Agenda Joint Cisco and Microsoft Integration Efforts Introduction to CCA-MCP What is a Pattern?
Firepower Techupdate April Jesper Rathsach, Consulting Systems Engineer Cisco Security North April 2017
 Firepower 6.2.1 Techupdate April 2017 Jesper Rathsach, Consulting Systems Engineer Cisco Security North April 2017 Firepower 6.2.1 Nr. 1 most important!! Firepower 6.2.1 BUGFIXES!!!!! Alle kendte severity
Firepower 6.2.1 Techupdate April 2017 Jesper Rathsach, Consulting Systems Engineer Cisco Security North April 2017 Firepower 6.2.1 Nr. 1 most important!! Firepower 6.2.1 BUGFIXES!!!!! Alle kendte severity
The Internet of Everything is changing Everything
 The Internet of Everything is changing Everything Intelligent Threat Defense for the Enterprise Mobility Nikos Mourtzinos, CCIE #9763 Global Security Sales Organization Changing Business Models Any Device
The Internet of Everything is changing Everything Intelligent Threat Defense for the Enterprise Mobility Nikos Mourtzinos, CCIE #9763 Global Security Sales Organization Changing Business Models Any Device
Firewall nové generace na platformě SF, přístupové politiky, analýza souborů, FireAMP a trajektorie útoků
 Firewall nové generace na platformě SF, přístupové politiky, analýza souborů, FireAMP a trajektorie útoků Jiří Tesař, CSE Security, jitesar@cisco.com CCIE #14558, SFCE #124266 Mapping Technologies to the
Firewall nové generace na platformě SF, přístupové politiky, analýza souborů, FireAMP a trajektorie útoků Jiří Tesař, CSE Security, jitesar@cisco.com CCIE #14558, SFCE #124266 Mapping Technologies to the
JURUMANI MERAKI CLOUD MANAGED SECURITY & SD-WAN
 JURUMANI CLOUD MANAGED SECURITY & SD-WAN SECURITY BY DESIGN OVERVIEW Cisco Meraki MX Security Appliances are ideal for organizations considering a Unified Threat Managment (UTM) solution, for distributed
JURUMANI CLOUD MANAGED SECURITY & SD-WAN SECURITY BY DESIGN OVERVIEW Cisco Meraki MX Security Appliances are ideal for organizations considering a Unified Threat Managment (UTM) solution, for distributed
Cisco ASA with FirePOWER Services
 Data Sheet Cisco ASA with FirePOWER Meet the industry s first adaptive, threat-focused next-generation firewall (NGFW) designed for a new era of threat and advanced malware protection. Cisco ASA with FirePOWER
Data Sheet Cisco ASA with FirePOWER Meet the industry s first adaptive, threat-focused next-generation firewall (NGFW) designed for a new era of threat and advanced malware protection. Cisco ASA with FirePOWER
FirePower 2100 NGFW. Elodie Heurtevent Security BDM Commercial. 21 March 2017
 FirePower 2100 NGFW Elodie Heurtevent Security BDM Commercial 21 March 2017 Capture the NGFW Opportunity "Less than 40% of enterprise Internet connections today are secured using nextgeneration firewalls
FirePower 2100 NGFW Elodie Heurtevent Security BDM Commercial 21 March 2017 Capture the NGFW Opportunity "Less than 40% of enterprise Internet connections today are secured using nextgeneration firewalls
ASACAMP - ASA Lab Camp (5316)
 ASACAMP - ASA Lab Camp (5316) Price: $4,595 Cisco Course v1.0 Cisco Security Appliance Software v8.0 Based on our enhanced FIREWALL and VPN courses, this exclusive, lab-based course is designed to provide
ASACAMP - ASA Lab Camp (5316) Price: $4,595 Cisco Course v1.0 Cisco Security Appliance Software v8.0 Based on our enhanced FIREWALL and VPN courses, this exclusive, lab-based course is designed to provide
Aby se z toho bezpečnostní správci nezbláznili Cisco security integrace. Milan Habrcetl Cisco CyberSecurity Specialist Mikulov, 5. 9.
 Aby se z toho bezpečnostní správci nezbláznili aneb Cisco security integrace Aby se z toho bezpečnostní správci nezbláznili Cisco security integrace Milan Habrcetl Cisco CyberSecurity Specialist Mikulov,
Aby se z toho bezpečnostní správci nezbláznili aneb Cisco security integrace Aby se z toho bezpečnostní správci nezbláznili Cisco security integrace Milan Habrcetl Cisco CyberSecurity Specialist Mikulov,
Cisco ASA 5500 Series IPS Solution
 Cisco ASA 5500 Series IPS Product Overview As mobile devices and Web 2.0 applications proliferate, it becomes harder to secure corporate perimeters. Traditional firewall and intrusion prevention system
Cisco ASA 5500 Series IPS Product Overview As mobile devices and Web 2.0 applications proliferate, it becomes harder to secure corporate perimeters. Traditional firewall and intrusion prevention system
Cisco Security Exposed Through the Cyber Kill Chain
 Cisco Forschung & Lehre Forum für Mecklenburg Vorpommern Cisco Security Exposed Through the Cyber Kill Chain Rene Straube CSE, Cisco Advanced Threat Solutions January, 2017 The Cisco Security Model BEFORE
Cisco Forschung & Lehre Forum für Mecklenburg Vorpommern Cisco Security Exposed Through the Cyber Kill Chain Rene Straube CSE, Cisco Advanced Threat Solutions January, 2017 The Cisco Security Model BEFORE
Network Automation and Branch Agility The Network Helps Enable Digital Business. Rajinder Singh Product Sales Specialist June 2016
 Network Automation and Branch Agility The Network Helps Enable Digital Business Rajinder Singh Product Sales Specialist June 2016 Agenda WAN Market Drivers Cisco Intelligent WAN (IWAN) Cisco Intelligent
Network Automation and Branch Agility The Network Helps Enable Digital Business Rajinder Singh Product Sales Specialist June 2016 Agenda WAN Market Drivers Cisco Intelligent WAN (IWAN) Cisco Intelligent
SDN Security BRKSEC Alok Mittal Security Business Group, Cisco
 SDN Security Alok Mittal Security Business Group, Cisco Security at the Speed of the Network Automating and Accelerating Security Through SDN Countering threats is complex and difficult. Software Defined
SDN Security Alok Mittal Security Business Group, Cisco Security at the Speed of the Network Automating and Accelerating Security Through SDN Countering threats is complex and difficult. Software Defined
Cisco Cyber Range. Paul Qiu Senior Solutions Architect
 Cisco Cyber Range Paul Qiu Senior Solutions Architect Cyber Range Service A platform to experience the intelligent Cyber Security for the real world What I hear, I forget What I see, I remember What I
Cisco Cyber Range Paul Qiu Senior Solutions Architect Cyber Range Service A platform to experience the intelligent Cyber Security for the real world What I hear, I forget What I see, I remember What I
Introduction to the Cisco ASAv
 Hypervisor Support The Cisco Adaptive Security Virtual Appliance (ASAv) brings full firewall functionality to virtualized environments to secure data center traffic and multitenant environments. You can
Hypervisor Support The Cisco Adaptive Security Virtual Appliance (ASAv) brings full firewall functionality to virtualized environments to secure data center traffic and multitenant environments. You can
Borderless Networks. Tom Schepers, Director Systems Engineering
 Borderless Networks Tom Schepers, Director Systems Engineering Agenda Introducing Enterprise Network Architecture Unified Access Cloud Intelligent Network & Unified Services Enterprise Networks in Action
Borderless Networks Tom Schepers, Director Systems Engineering Agenda Introducing Enterprise Network Architecture Unified Access Cloud Intelligent Network & Unified Services Enterprise Networks in Action
Cloud Mobility: Meraki Wireless & EMM
 BRKEWN-2002 Cloud Mobility: Meraki Wireless & EMM Emily Sporl Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this session in the Cisco Live Mobile
BRKEWN-2002 Cloud Mobility: Meraki Wireless & EMM Emily Sporl Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this session in the Cisco Live Mobile
NETWORKING &SECURITY SOLUTIONSPORTFOLIO
 NETWORKING &SECURITY SOLUTIONSPORTFOLIO NETWORKING &SECURITY SOLUTIONSPORTFOLIO Acomprehensivesolutionsportfoliotohelpyougetyourbusiness securelyconnected.clickononeofoursolutionstoknowmore NETWORKING
NETWORKING &SECURITY SOLUTIONSPORTFOLIO NETWORKING &SECURITY SOLUTIONSPORTFOLIO Acomprehensivesolutionsportfoliotohelpyougetyourbusiness securelyconnected.clickononeofoursolutionstoknowmore NETWORKING
Cisco Cloud Security. How to Protect Business to Support Digital Transformation
 Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
Chapter 1: Content Security
 Chapter 1: Content Security Cisco Cloud Web Security (CWS) Cisco offers Cisco Cloud Web Security (CWS) to protect End Stations and Users devices from infection. Cisco Cloud Web Security (CWS) depends upon
Chapter 1: Content Security Cisco Cloud Web Security (CWS) Cisco offers Cisco Cloud Web Security (CWS) to protect End Stations and Users devices from infection. Cisco Cloud Web Security (CWS) depends upon
Stop Threats Before They Stop You
 Stop Threats Before They Stop You Gain visibility and control as you speed time to containment of infected endpoints Andrew Peters, Sr. Manager, Security Technology Group Agenda Situation System Parts
Stop Threats Before They Stop You Gain visibility and control as you speed time to containment of infected endpoints Andrew Peters, Sr. Manager, Security Technology Group Agenda Situation System Parts
Easy Setup Guide. Cisco ASA with Firepower Services. You can easily set up your ASA in this step-by-step guide.
 Cisco ASA with Firepower Services Easy Setup Guide You can easily set up your ASA in this step-by-step guide. Connecting PC to ASA Installing ASDM 3 Configuring ASA 4 Using Umbrella DNS Connecting PC to
Cisco ASA with Firepower Services Easy Setup Guide You can easily set up your ASA in this step-by-step guide. Connecting PC to ASA Installing ASDM 3 Configuring ASA 4 Using Umbrella DNS Connecting PC to
SAFE Architecture Guide. Places in the Network: Secure Campus
 SAFE Architecture Guide Places in the Network: Secure Campus January 2018 SAFE Architecture Guide Places in the Network: Secure Campus Contents January 2018 Contents 3 5 8 9 13 15 21 22 25 Overview Business
SAFE Architecture Guide Places in the Network: Secure Campus January 2018 SAFE Architecture Guide Places in the Network: Secure Campus Contents January 2018 Contents 3 5 8 9 13 15 21 22 25 Overview Business
IWAN APIC-EM Application Cisco Intelligent WAN
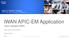 IWAN APIC-EM Application Cisco Intelligent WAN René og Per Cisco DK SE s Feb 23 th 2016 AVC MPLS Private Cloud 3G/4G-LTE Virtual Private Cloud Branch WAAS PfR Internet Public Cloud Control, Management,
IWAN APIC-EM Application Cisco Intelligent WAN René og Per Cisco DK SE s Feb 23 th 2016 AVC MPLS Private Cloud 3G/4G-LTE Virtual Private Cloud Branch WAAS PfR Internet Public Cloud Control, Management,
Cisco Meraki Cloud-Managed Networking. George Carlan
 Cisco Meraki Cloud-Managed Networking George Carlan Cisco Networking Portfolio Cisco Enterprise Portfolio Cisco Cloud Managed Prime ISE Cloud Management & Policy Systems Manager Systems Manager WLAN Controllers
Cisco Meraki Cloud-Managed Networking George Carlan Cisco Networking Portfolio Cisco Enterprise Portfolio Cisco Cloud Managed Prime ISE Cloud Management & Policy Systems Manager Systems Manager WLAN Controllers
SAFE Architecture Guide. Places in the Network: Secure Branch
 SAFE Architecture Guide Places in the Network: Secure Branch January 2018 SAFE Architecture Guide Places in the Network: Secure Branch Contents January 2018 Contents 3 5 8 9 13 17 22 23 26 Overview Business
SAFE Architecture Guide Places in the Network: Secure Branch January 2018 SAFE Architecture Guide Places in the Network: Secure Branch Contents January 2018 Contents 3 5 8 9 13 17 22 23 26 Overview Business
How to Predict, Detect & Stop threats at the Edge and Behind the Perimeter even in encrypted traffic without decryption
 How to Predict, Detect & Stop threats at the Edge and Behind the Perimeter even in encrypted traffic without decryption Nikos Mourtzinos, CCIE #9763 Cisco Cyber Security Sales Specialist April 2018 New
How to Predict, Detect & Stop threats at the Edge and Behind the Perimeter even in encrypted traffic without decryption Nikos Mourtzinos, CCIE #9763 Cisco Cyber Security Sales Specialist April 2018 New
Network Security: Firewall, VPN, IDS/IPS, SIEM
 Security: Firewall, VPN, IDS/IPS, SIEM Ahmet Burak Can Hacettepe University abc@hacettepe.edu.tr What is a Firewall? A firewall is hardware, software, or a combination of both that is used to prevent unauthorized
Security: Firewall, VPN, IDS/IPS, SIEM Ahmet Burak Can Hacettepe University abc@hacettepe.edu.tr What is a Firewall? A firewall is hardware, software, or a combination of both that is used to prevent unauthorized
Cisco Self Defending Network
 Cisco Self Defending Network Integrated Network Security George Chopin Security Business Development Manager, CISSP 2003, Cisco Systems, Inc. All rights reserved. 1 The Network as a Strategic Asset Corporate
Cisco Self Defending Network Integrated Network Security George Chopin Security Business Development Manager, CISSP 2003, Cisco Systems, Inc. All rights reserved. 1 The Network as a Strategic Asset Corporate
Cisco Exam Questions & Answers
 Cisco 648-385 Exam Questions & Answers Number: 648-385 Passing Score: 800 Time Limit: 120 min File Version: 34.4 http://www.gratisexam.com/ Cisco 648-385 Exam Questions & Answers Exam Name: CXFF - Cisco
Cisco 648-385 Exam Questions & Answers Number: 648-385 Passing Score: 800 Time Limit: 120 min File Version: 34.4 http://www.gratisexam.com/ Cisco 648-385 Exam Questions & Answers Exam Name: CXFF - Cisco
Defense-in-Depth Against Malicious Software. Speaker name Title Group Microsoft Corporation
 Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
Next Generation IPS and Advance Malware Protection. Mahmoud Rabi Consulting Systems Engineer - Security
 Next Generation IPS and Advance Malware Protection Mahmoud Rabi Consulting Systems Engineer - Security Threat Landscape and Attack Continuum Today s Real World: Threats are evolving and evading traditional
Next Generation IPS and Advance Malware Protection Mahmoud Rabi Consulting Systems Engineer - Security Threat Landscape and Attack Continuum Today s Real World: Threats are evolving and evading traditional
Fully Integrated, Threat-Focused Next-Generation Firewall
 Cisco Firepower NGFW Fully Integrated, Threat-Focused Next-Generation Firewall Fuat KILIÇ, fkilic@cisco.com, +905339284608 Security Consulting Systems Engineer, CCIE #21150 September 2016 Get ahead of
Cisco Firepower NGFW Fully Integrated, Threat-Focused Next-Generation Firewall Fuat KILIÇ, fkilic@cisco.com, +905339284608 Security Consulting Systems Engineer, CCIE #21150 September 2016 Get ahead of
Cisco TrustSec Software-Defined Segmentation Platform and Capability Matrix Release 6.3
 TrustSec Software-Defined Segmentation Platform and Capability Matrix Release 6.3 TrustSec uniquely builds upon your existing identity-aware infrastructure by enforcing segmentation and access control
TrustSec Software-Defined Segmentation Platform and Capability Matrix Release 6.3 TrustSec uniquely builds upon your existing identity-aware infrastructure by enforcing segmentation and access control
New Features for ASA Version 9.0(2)
 FIREWALL Features New Features for ASA Version 9.0(2) Cisco Adaptive Security Appliance (ASA) Software Release 9.0 is the latest release of the software that powers the Cisco ASA family. The same core
FIREWALL Features New Features for ASA Version 9.0(2) Cisco Adaptive Security Appliance (ASA) Software Release 9.0 is the latest release of the software that powers the Cisco ASA family. The same core
New methods to protect the network. Deeper visibility with Cisco NGFW Next Generation Firewall
 New methods to protect the network. Deeper visibility with Cisco NGFW Next Generation Firewall Claudiu Onisoru, Senior Network Specialist Cisco Connect - 15 May 2014 1 Agenda Frontal Communication: Who
New methods to protect the network. Deeper visibility with Cisco NGFW Next Generation Firewall Claudiu Onisoru, Senior Network Specialist Cisco Connect - 15 May 2014 1 Agenda Frontal Communication: Who
Appliance Comparison Chart
 Security Gateway Appliances 300 300 500 500 5400 5600 5800 5900 Branch Office Small Enterprise Mid-Size Enterprise Real-World Production Conditions Security 60 50 340 45 600 950 750 400 Firewall (Gbps)..
Security Gateway Appliances 300 300 500 500 5400 5600 5800 5900 Branch Office Small Enterprise Mid-Size Enterprise Real-World Production Conditions Security 60 50 340 45 600 950 750 400 Firewall (Gbps)..
Security Assessment Checklist
 Security Assessment Checklist Westcon Security Checklist - Instructions The first step to protecting your business includes a careful and complete assessment of your security posture. Our Security Assessment
Security Assessment Checklist Westcon Security Checklist - Instructions The first step to protecting your business includes a careful and complete assessment of your security posture. Our Security Assessment
Intelligent WAN (IWAN) Design and Deployment
 Intelligent WAN (IWAN) Design and Deployment Adam Groudan, Technical Solutions Architect David Prall, Communications Architect BRKCRS-2002 Cisco Spark How Questions? Use Cisco Spark to communicate with
Intelligent WAN (IWAN) Design and Deployment Adam Groudan, Technical Solutions Architect David Prall, Communications Architect BRKCRS-2002 Cisco Spark How Questions? Use Cisco Spark to communicate with
LTRDCN-2100 Cloud networking solutions with Cisco Cloud Services Router (CSR 1000V) on AWS and Azure
 LTRDCN-2100 Cloud networking solutions with Cisco Cloud Services Router (CSR 1000V) on AWS and Azure Fan Yang, Cisco, Engineer, Technical Marketing Raghavendra K S, Cisco, Engineer, Technical Marketing
LTRDCN-2100 Cloud networking solutions with Cisco Cloud Services Router (CSR 1000V) on AWS and Azure Fan Yang, Cisco, Engineer, Technical Marketing Raghavendra K S, Cisco, Engineer, Technical Marketing
ASA/PIX Security Appliance
 I N D E X A AAA, implementing, 27 28 access to ASA/PIX Security Appliance monitoring, 150 151 securing, 147 150 to websites, blocking, 153 155 access control, 30 access policies, creating for web and mail
I N D E X A AAA, implementing, 27 28 access to ASA/PIX Security Appliance monitoring, 150 151 securing, 147 150 to websites, blocking, 153 155 access control, 30 access policies, creating for web and mail
CyberP3i Course Module Series
 CyberP3i Course Module Series Spring 2017 Designer: Dr. Lixin Wang, Associate Professor Firewall Configuration Firewall Configuration Learning Objectives 1. Be familiar with firewalls and types of firewalls
CyberP3i Course Module Series Spring 2017 Designer: Dr. Lixin Wang, Associate Professor Firewall Configuration Firewall Configuration Learning Objectives 1. Be familiar with firewalls and types of firewalls
Future-ready security for small and mid-size enterprises
 First line of defense for your network Quick Heal Terminator (UTM) (Unified Threat Management Solution) Data Sheet Future-ready security for small and mid-size enterprises Quick Heal Terminator is a high-performance,
First line of defense for your network Quick Heal Terminator (UTM) (Unified Threat Management Solution) Data Sheet Future-ready security for small and mid-size enterprises Quick Heal Terminator is a high-performance,
Disclaimer CONFIDENTIAL 2
 Disclaimer This presentation may contain product features that are currently under development. This overview of new technology represents no commitment from VMware to deliver these features in any generally
Disclaimer This presentation may contain product features that are currently under development. This overview of new technology represents no commitment from VMware to deliver these features in any generally
MAKING THE CLOUD A SECURE EXTENSION OF YOUR DATACENTER
 MAKING THE CLOUD A SECURE EXTENSION OF YOUR DATACENTER Bret Hartman Cisco / Security & Government Group Session ID: SPO1-W25 Session Classification: General Interest 1 Mobility Cloud Threat Customer centric
MAKING THE CLOUD A SECURE EXTENSION OF YOUR DATACENTER Bret Hartman Cisco / Security & Government Group Session ID: SPO1-W25 Session Classification: General Interest 1 Mobility Cloud Threat Customer centric
Pluralsight CEU-Eligible Courses for CompTIA Network+ updated March 2018
 Pluralsight CEU-Eligible Courses for CompTIA Network+ updated March 2018 Access Control Lists (ACLs) for Cisco CCNA 200-125/100-105 Advanced Access Control with Cisco ISE for CCNP Security (300-208) SISAS
Pluralsight CEU-Eligible Courses for CompTIA Network+ updated March 2018 Access Control Lists (ACLs) for Cisco CCNA 200-125/100-105 Advanced Access Control with Cisco ISE for CCNP Security (300-208) SISAS
Cisco Cyber Range. Paul Qiu Senior Solutions Architect June 2016
 Cisco Cyber Range Paul Qiu Senior Solutions Architect June 2016 What I hear, I forget What I see, I remember What I do, I understand ~ Confucius Agenda Agenda Cyber Range Highlights Cyber Range Overview
Cisco Cyber Range Paul Qiu Senior Solutions Architect June 2016 What I hear, I forget What I see, I remember What I do, I understand ~ Confucius Agenda Agenda Cyber Range Highlights Cyber Range Overview
SONICWALL SECURITY HEALTH CHECK PSO 2017
 SONICWALL SECURITY HEALTH CHECK PSO 2017 Get help in fully utilizing your investment to protect your network Overview SonicWALL Security Health Check provides a customer with a comprehensive review of
SONICWALL SECURITY HEALTH CHECK PSO 2017 Get help in fully utilizing your investment to protect your network Overview SonicWALL Security Health Check provides a customer with a comprehensive review of
Cisco Advanced Malware Protection against WannaCry
 Cisco Advanced Malware Protection against WannaCry "A false sense of security is worse than a true sense of insecurity" Senad Aruc Consulting Systems Engineer Advanced Threats Group Nils Roald Advanced
Cisco Advanced Malware Protection against WannaCry "A false sense of security is worse than a true sense of insecurity" Senad Aruc Consulting Systems Engineer Advanced Threats Group Nils Roald Advanced
Sourcefire Solutions Overview Security for the Real World. SEE everything in your environment. LEARN by applying security intelligence to data
 SEE everything in your environment LEARN by applying security intelligence to data ADAPT defenses automatically ACT in real-time Sourcefire Solutions Overview Security for the Real World Change is constant.
SEE everything in your environment LEARN by applying security intelligence to data ADAPT defenses automatically ACT in real-time Sourcefire Solutions Overview Security for the Real World Change is constant.
Compare Security Analytics Solutions
 Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
Corrigendum 3. Tender Number: 10/ dated
 (A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
(A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
Stopping Advanced Persistent Threats In Cloud and DataCenters
 Stopping Advanced Persistent Threats In Cloud and DataCenters Frederik Van Roosendael PSE Belgium Luxembourg 10/9/2015 Copyright 2013 Trend Micro Inc. Agenda How Threats evolved Transforming Your Data
Stopping Advanced Persistent Threats In Cloud and DataCenters Frederik Van Roosendael PSE Belgium Luxembourg 10/9/2015 Copyright 2013 Trend Micro Inc. Agenda How Threats evolved Transforming Your Data
Cisco Network Admission Control (NAC) Solution
 Data Sheet Cisco Network Admission Control (NAC) Solution New: Updated to include the Cisco Secure Network Server (SNS) Cisco Network Admission Control (NAC) solutions allow you to authenticate wired,
Data Sheet Cisco Network Admission Control (NAC) Solution New: Updated to include the Cisco Secure Network Server (SNS) Cisco Network Admission Control (NAC) solutions allow you to authenticate wired,
Cisco Secure Access Control
 Cisco Secure Access Control Delivering Deeper Visibility, Centralized Control, and Superior Protection Martin Briand - Security Escalation VSE Global Virtual Engineering Oriol Madriles Soriano Security
Cisco Secure Access Control Delivering Deeper Visibility, Centralized Control, and Superior Protection Martin Briand - Security Escalation VSE Global Virtual Engineering Oriol Madriles Soriano Security
Service Provider Security Architecture
 Service Provider Security Architecture Andrew Turner Technical Marketing, Security Business Group April 12 th 2017 Digitization is disrupting the SP business The world has gone mobile Traffic growth, driven
Service Provider Security Architecture Andrew Turner Technical Marketing, Security Business Group April 12 th 2017 Digitization is disrupting the SP business The world has gone mobile Traffic growth, driven
Firefly Perimeter ( vsrx ) Technical information 12.1 X47 D10.2. Tuncay Seyran
 Firefly Perimeter ( vsrx ) Technical information 12.1 X47 D10.2 Tuncay Seyran Security in a virtualized environment: same security risks + more TRADITIONAL SECURITY RISKS IMPACTING VIRTUAL ENVIRONMENTS
Firefly Perimeter ( vsrx ) Technical information 12.1 X47 D10.2 Tuncay Seyran Security in a virtualized environment: same security risks + more TRADITIONAL SECURITY RISKS IMPACTING VIRTUAL ENVIRONMENTS
Inside Cisco IT: Secure, Simultaneous Access to Trusted and Untrusted Networks using C-Bridge
 Inside Cisco IT: Secure, Simultaneous Access to Trusted and Untrusted Networks using C-Bridge Tom Woodard Cisco InfoSec Architect BRKCOC-1900 This solution solves business challenges by securely allowing
Inside Cisco IT: Secure, Simultaneous Access to Trusted and Untrusted Networks using C-Bridge Tom Woodard Cisco InfoSec Architect BRKCOC-1900 This solution solves business challenges by securely allowing
Intelligent WAN Sumanth Kakaraparthi Principal Product Manager PSOCRS-2010
 Intelligent WAN Sumanth Kakaraparthi Principal Product Manager PSOCRS-2010 Agenda Challenges Architectures Cisco IWAN Proof Points Challenges Application landscape is changing Applications Are Moving to
Intelligent WAN Sumanth Kakaraparthi Principal Product Manager PSOCRS-2010 Agenda Challenges Architectures Cisco IWAN Proof Points Challenges Application landscape is changing Applications Are Moving to
APIC-EM / EasyQoS - End to End Orchestration of QoS in Enterprise Networks
 APIC-EM / EasyQoS - End to End Orchestration of QoS in Enterprise Networks Saurav Prasad Technical Marketing Engineer CTHNMS-1002 Cisco Spark How Questions? Use Cisco Spark to chat with the speaker after
APIC-EM / EasyQoS - End to End Orchestration of QoS in Enterprise Networks Saurav Prasad Technical Marketing Engineer CTHNMS-1002 Cisco Spark How Questions? Use Cisco Spark to chat with the speaker after
Zero Trust Security with Software-Defined Secure Networks
 Zero Trust Security with Software-Defined Secure Networks Srinivas Nimmagadda and Pradeep Nair Juniper Networks This statement of direction sets forth Juniper Networks current intention and is subject
Zero Trust Security with Software-Defined Secure Networks Srinivas Nimmagadda and Pradeep Nair Juniper Networks This statement of direction sets forth Juniper Networks current intention and is subject
Cisco TrustSec Software-Defined Segmentation Release 6.1 System Bulletin
 System Bulletin TrustSec Software-Defined Segmentation Release 6.1 System Bulletin Introduction Network segmentation is essential for protecting critical business assets. TrustSec Software Defined Segmentation
System Bulletin TrustSec Software-Defined Segmentation Release 6.1 System Bulletin Introduction Network segmentation is essential for protecting critical business assets. TrustSec Software Defined Segmentation
NGFW Requirements for SMBs and Distributed Enterprises
 White Paper NGFW Requirements for SMBs and Distributed Enterprises The Case for NGFWs for SMBs The need for threat-focused next-generation firewalls (NGFWs) that can effectively mitigate risks that traditional
White Paper NGFW Requirements for SMBs and Distributed Enterprises The Case for NGFWs for SMBs The need for threat-focused next-generation firewalls (NGFWs) that can effectively mitigate risks that traditional
McAfee Network Security Platform 9.2
 McAfee Network Security Platform 9.2 (9.2.7.22-9.2.7.20 Manager-Virtual IPS Release Notes) Contents About this release New features Enhancements Resolved issues Installation instructions Known issues Product
McAfee Network Security Platform 9.2 (9.2.7.22-9.2.7.20 Manager-Virtual IPS Release Notes) Contents About this release New features Enhancements Resolved issues Installation instructions Known issues Product
Cisco Systems Korea Cisco Systems, Inc. All rights reserved. 1
 10 (yonghkim@cisco.com) Cisco Systems Korea 2008 Cisco Systems, Inc. All rights reserved. 1 10G (UTM) 2008 Cisco Systems, Inc. All rights reserved. 2 10G 2008 Cisco Systems, Inc. All rights reserved. 3
10 (yonghkim@cisco.com) Cisco Systems Korea 2008 Cisco Systems, Inc. All rights reserved. 1 10G (UTM) 2008 Cisco Systems, Inc. All rights reserved. 2 10G 2008 Cisco Systems, Inc. All rights reserved. 3
A Deep Dive into the Firepower Manager
 A Deep Dive into the Firepower Manager William Young, Security Solutions Architect willyou@cisco.com @WilliamDYoung BRKSEC-2058 Just some Security Guy William Young Security Solutions Architect, Cisco
A Deep Dive into the Firepower Manager William Young, Security Solutions Architect willyou@cisco.com @WilliamDYoung BRKSEC-2058 Just some Security Guy William Young Security Solutions Architect, Cisco
