Local Networks. Lecture 8 29-Apr-2016
|
|
|
- Meredith Watkins
- 5 years ago
- Views:
Transcription
1 Local Networks Lecture 8 29-Apr-2016
2 Roadmap of the Course So far Basic telecom concepts General study of LANs Local Networks Ethernet Token bus Token ring ATM LAN Wi-Fi Today LAN performance, Connecting LANs, LAN management
3 LAN Performance
4 LAN performance Theoretical, intricate issue Involves probability and queuing theories as well as stochastic processes We only define some basic notions here We analyze the performance of two (simplified) access methods CSMA/CD Token Ring
5 Parameters Maximum medium length: L medium Medium propagation speed: V Maximum propagation delay: D Capacity: C Average frame length in bits: L frame-bit Average frame transmission time: T frame Bit length of medium: L medium-bit Special ratio parameter: a
6 Maximum medium length L medium Measured in meters Maximum physical length a data frame can travel in a typical transmission Bus topology: bus length Ring topology: ring length Star topology: length between furthest stations
7 L medium illustration in bus
8 L medium illustration in ring
9 L medium illustration in star
10 Medium propagation speed V Propagation speed of the electromagnetic signal representing data in the medium Vacuum: 3*10 8 m/s Air: less than, but about the same Cable: approx. 2*10 8 m/s
11 Maximum propagation delay D Measured in seconds Time needed for the first bit of the frame to travel the maximum length of the medium D=L medium /V
12 Capacity C Measured in bps How many bits can be transmitted per second Also known as data rate LAN Traditional Ethernet Fast Ethernet Gigabit Ethernet Token Ring Wireless Ethernet Capacity 10 Mbps 100 Mbps 1 Gbps 4/16 Mbps 11/54/much more Mbps
13 Average frame length in bits L frame-bit and Average frame transmission time T frame L frame-bit : The average number of bits in a frame, including overhead bits T frame : The time in seconds needed to send the above average frame T frame = L frame-bit / C
14 Bit length of medium L medium-bit Maximum length of the medium in bits Number of bits the medium can hold L medium-bit = D*C = (L medium /V)*C = (C/V)*L medium
15 Special parameter a Ratio of D to T frame : a = D / T frame a = D / T frame = L medium-bit / L frame-bit a = how many frames fit on medium at the same time a proportional to C A network running at 100 Mbps has a bigger a than one running at 10 Mbps 3 cases: a>1, a=1, a<1
16 a>1
17 a=1
18 a<1
19 Efficiency μ of a LAN Defined as the ratio of The time used by a station to send data The time the medium is occupied, directly or indirectly, by this station (cannot be used by other stations) μ = time a station sends data / time medium is occupied for this purpose
20 Example 1 Bus topology, each station can transmit a fixedsize frame Other stations do no transmit until a frame has reached destination Worst case: furthest stations Time used by a station to send frame: T frame Occupied time on medium: T frame + D
21 Example 1, cont μ = T frame / (T frame + D) = 1/ (1+a) Hence When a increases, μ decreases When C increases, μ decreases
22 CSMA/CD efficiency Station sends frame but it s not guaranteed successful transmission due to possible collisions Main issue: how long, on average, it takes a station to send a frame without collision To simplify things, we assume Slotted Aloha No back-off waiting Time slot T s =2*D
23 Some computations Probability that a station finds a time slot with no collision, P success = n*p*(1-p) n-1 When p=1/n => P success = (1-1/n) n-1 (we assumed there are n stations and the probability that a station - for a given slot - has a frame to send is p) P success à 1/e when nà 1/e 0.36 => each station can get a slot to successfully send its frame at least 36% of time
24 Successful slot How many slots will pass, on average, before a station can get a successful slot? Denoted by N slots If a slot is successful with probability p => in average, it is the (1/p) th slot Hence, N slots = (1/P success ) -1 => N slots 1.71
25 Theoretical efficiency μ = time used by a station to send data / time the medium is occupied for this μ = T frame / (T frame + N slots *2*D) => μ = 1 / ( *a)
26 Actual efficiency Has been measured and shown to be less: μ = 1 / (1 + 5*a)
27 Token ring efficiency We assume n stations Each station has data to send When a station gets the token, it holds it and sends data After sending one frame the station releases token μ = time used by a station to send data / time the medium is occupied for this
28 Token ring efficiency 2 μ = T frame / (T frame + D + T token + D/n), i.e., we need the sum of the following T frame = time needed to transmit a frame D = time needed for the first bit of frame to come back T token = time needed to transmit a token The time for the token to reach next station n stations => the latter is D/n
29 Some assumptions Token very small (24 bits) => T token 0 In some token ring networks the sending station releases a token immediately after sending the frame Called early token release Implies the second term 0
30 Final token ring formula μ = T frame / (T frame + D/n), or μ = 1 / (1 + a/n)
31 CSMA/CD and Token ring Token ring has very high efficiency: 100% CSMA/CD has very low efficiency 30-40%
32 Connecting LANs
33 How can we put up a network? Connecting several devices Some possible problems LAN needs to cover bigger distance than media can handle efficiently Number of stations too big for efficient frame delivery (=> network needs to be subdivided) When connecting several networks, some other problems can occur
34 Devices that help
35 Internet An internet: an interconnection of individual network Not to be confused, of course, with Internet Routers and gateways Designed to overcome obstacles to interconnection, without disrupting the independent functioning of the network
36 OSI layers affected by the devices
37 Devices Repeaters: act only upon the electrical components of a signal Active only at the physical layer Bridges: utilize addressing protocols, can affect the flow control of a LAN Most active at data link layer Routers: provide links between separate LANs Most active at network layer Gateways: provide translation services between incompatible LANs or applications Active at all layers Each device also operates in layers below that in which it is most active
38 Repeaters
39 What is a repeater? Electronic device known also as regenerator Installed on a link Receives a signal before it becomes too weak/corrupted and It regenerates the original bit pattern It puts a refreshed copy back on the link Thus extends only the physical length of a network Does not change the functionality of the network in any way
40 Repeater illustration
41 Repeater is not an amplifier Amplifier Cannot discriminate noise from intended signal Amplifies equally whatever fed into it Repeater Does not amplify, buy regenerates the signal A weakened/corrupted signal is copied bit by bit, at original strength
42 Location of repeater Repeater must be placed so that A signal reaches it before any noise changes the meaning A little noise usually alters the precision of the signal s voltage, without destroying its identity The repeater can then read the signal well enough to determine intended voltages
43 Function of repeater
44 Bridges
45 A bridge and segments
46 What is a bridge? Device dividing a large network into smaller segments Also relays frames between two originally separate segments of one type They are repeaters with logic, filters They keep traffic for each segment separate A frame is relayed only to the side of segment containing intended recipient
47 Bridge example
48 Uses of a bridge They filter traffic => useful for Controlling congestion Isolating problem links They partition traffic => useful for security
49 How do bridges function? Do not modify the structure/contents of a frame => can be used only between segments using the same protocol When frame enters bridge Bridge regenerates signal Checks the destination address Forwards new copy only to corresponding segment (uses some tables for this)
50 Types of bridges Simple Most primitive and least expensive Links 2 segments only, has a table containing the addresses of all stations in each segment Addresses have to be entered and removed manually Installation and maintenance costs are time-consuming Multi-port Used to connect more than two LAN segments If N-port, then it connects N segments and thus has N tables Each table contains the physical addresses of stations reachable through corresponding port
51 3-port bridge
52 Transparent bridge Is a learning bridge Builds its tables on its own When first installed, tables are empty When receives a packet, it checks the source and, as it knows the segment from which the packet came, can associate the source address with that segment Eventually completes the table in this way When does not know the destination-segment correspondence it sends packet to all stations Important also as a self-updating mechanism Good for mobile computing
53 Loops in bridged LANs Bridges installed redundantly Two LAN segments may be connected by more than one bridge Loops can occur if bridges are transparent To avoid loops Spanning tree algorithms Source routing The packet source specifies the bridges (and segments) to be used
54 Bridges connecting different LANs Problems to solve Frame format Payload size Data rate Address bit order Other issues: acknowledgements, collisions, priorities that may be different in different LANs
55 Routers
56 What is a router? More sophisticated device (than a repeater or a bridge) Has access to NL addresses Has software enabling it to determine which of the possible paths between the NL addresses is the best for a particular transmission Router relays packets among multiple interconnected networks
57 Routers in an internet
58 Routers and routing Routers act as stations on a network Stations usually belong to one network Routers have addresses on several networks Routers have links to several networks Routing Simplest: get a packet from one connected network and pass it to another connected network If packet destination not on a network to which the router is member, then router can determine which of the connected networks is the next best relay for the packet
59 What does best mean for a router? Least-cost routing: based on efficiency (the cheapest (shortest) path is chosen) Each link assigned a value and the length of a route is the sum of all its component link values Fastest, cheapest, most reliable, most secure, etc Typically a combination of all these Named symbolic link length Smallest number of relays (hops) Hop-count routing Routes need updating only when a link becomes unavailable => link s value becomes
60 Hop-count algorithms Usually limit the routes of a single router to up to 15 hops Special (custom) algorithms for special requirementtransmissions (e.g., military) Some links given value 1, others higher values TCP/IP, OSI Use hop-count routing
61 Symbolic link length E.g., a full-duplex link The length in one direction may be different from the length in the other direction Physical distance is the same Traffic load or quality of cable may differ
62 Types of routing Non-adaptive Once a pathway to a destination is chosen, router sends all packets with that destination along the chosen route Topology or network condition not important Adaptive Router can select a new route for each packet (even packets in same transmission) Topology or network condition considered
63 Packet lifetime Usually number of hops allowed before a packet is considered lost and it s destroyed Used for eventually breaking loops (bouncing) With adaptive routing, a router may update its information before others and thus, loops may result The problem with bouncing is waste of resources
64 Gateways
65 What is a gateway? Protocol converter Usually operates in all 7 OSI layers Can accept a packet formatted for one protocol (e.g. AppleTalk) and convert it for another protocol (e.g. TCP/IP) before forwarding it Generally is software installed within a router
66 What does a gateway modify? In some cases only headers and trailers In some cases also data rate, size, format
67 Other devices Multi-protocol routers Brouters Switches Routing switches
68 Multi-protocol routers Traditional router requires same protocol at network layer for the networks it connects So that routing table uses one single addressing format Multi-protocol router: routes packets belonging to different protocols Sort of a gateway for network layer protocols
69 Traditional vs. multi-protocol routers
70 Brouters Bridge/router Single-protocol (SP) / multi-protocol (MP) router acting as both router and bridge If SP brouter gets a packet of the protocol it uses, it routes the packet; otherwise acts as bridge and passes packet using data link layer addresses If MP brouter gets a packet of one of the protocols it uses, it routes the packet; otherwise acts as bridge and passes packet using data link layer addresses
71 Brouters illustration
72 Switches Devices providing bridging functionality with greater efficiency May act as multi-port bridge to connect devices and segments in a LAN Have buffer for each link they are connected to Store received packet in buffer of receiving link Check address and CRC to find outgoing link If outgoing link is free, frame sent
73 Switch illustration
74 Switching strategies Store-and-forward Frame stored until whole packet arrived Cut-through Frame forwarded when destination is received
75 Routing switches Combining a switch (bridge) and a router Traditional router software Finds the NL address of next station and passes the information to DLL layer to find the output link Routing switches Use the NL destination address to find the output link Faster
76 LAN Management
77 Network management Monitoring, testing, configuring, trouble shooting network components to meet a series of requirements defined by an organization Smooth and efficient operation of the network Provides the predefined quality of service A network management system uses Hardware Software People
78 ISO definition
79 Configuration management (CM) Large networks usually have hundreds of entities physically/logically connected to each other Such entities have an initial configuration when the network is set up The configuration can change over time CM system must know at any time the status and relationships of each entity
80 CM division
81 Reconfiguration Can occur daily in a large network 3 types Hardware reconfiguration Software reconfiguration User-account reconfiguration
82 Hardware reconfiguration Covers all changes to hardware Desktops can be replaced Router may be moved Sub-networks may be added or removed This cannot be automated Is done manually, handled case by case Involves specially trained personnel
83 Software reconfiguration Covers all changes to the software New software may be installed on servers or clients Operating systems may need updating Most software reconfiguration can be automated
84 User-account reconfiguration Not only adding/deleting users on a system User privileges important As individual As member to a group Can be, to some extent, automated
85 Documentation The original network configuration as well as each subsequent change has to be recorded meticulously 3 types Hardware documentation Software documentation User-account documentation
86 Hardware documentation Involves 2 sets of documents Maps Specifications Maps Track each hardware piece and its network connection One general map showing the logical relationship between each 2 sub-networks Possibly another general map showing the physical location of each sub-network For each sub-network: one/more maps showing all pieces of equipment Written in some standard language
87 Hardware documentation 2 Specifications Each hardware piece needs to be documented There is a set of specifications for each hardware piece, connected to the network Information included: hardware type, serial number, vendor s details, time of purchase, warranty information
88 Software documentation All software must be documented Information included Software type Version The installation type License agreement
89 User-account documentation Most operating systems have a utility allowing the documentation of user accounts and their privileges The files containing the above information must be updated and secured Access privileges could be recorded in 2 documents One with all files and access types for each user Another with the list of users having particular access to some files
90 Fault management (FM) Large networks have hundreds/thousands of components Proper operation of the network depends on proper operation of each component Individually In relation to each other FM handles these issues Fault: abnormal condition in the system
91 FM illustration
92 Reactive FM Responsible for detecting, isolating, correcting and recording faults I.e., takes place after a fault occurred Handles short-term solutions to faults
93 Detecting faults Finding the exact location of a fault When a fault occurs The system either stops working properly The system creates excessive errors Example: damaged communication system
94 Isolating and Correcting faults Isolation Useful as it affects only some of the users After isolation, the users are notified and given estimated time of correction Correction Repairing or replacing the faulty component(s)
95 Recording faults Faults are documented Location, possible cause, action(s) taken for correction, cost, time it took for these steps Important because The problem may reoccur Frequency of some type of failure indicates major problem in the system Statistic helpful for performance management
96 Proactive FM Tries to prevent faults from occurring I.e., takes place before faults occur Not always successful Some types of failures may be prevented Replacing an aged component Reconfiguring some frequently faulty component Redundancy is a good strategy
97 Performance management (PM) Closely related to FM Monitors and control the network to ensure it runs as efficiently as possible Quantifies performance using measurable quantities Capacity Throughput Traffic Response time
98 PM criteria
99 Capacity and traffic Capacity Each network has limited capacity PM system ensures the network is not used above this capacity Traffic Can be measured internally and externally Internal: number of packets or bytes traveling inside the network External: exchange of packets or bytes outside the network
100 Throughput and response time Throughput Can be measured of an individual device (e.g., router) or of a part of a network PM system makes sure it is not reduced to unacceptable levels Response time (RT) Time it takes a user to get a service Capacity and traffic can influence RT PM system monitors the average RT and the peak-hour RT Increases in RT indicates network working above its capacity
101 Security management Responsible for controlling access to the network Based on predefined policy Encryption Allows user privacy in exchanging information Authentication Forces the users to identify themselves
102 Accounting management (AM) Controls the users access to the network resources through charges Charged entities for the services received form network Individual users Departments Divisions Projects
103 Accounting management 2 Charge does not have to mean money It may mean debiting the departments or divisions for budgeting purposes Uses of an AM system Prevents users from monopolizing resources Prevents users from using system inefficiently Allows for short/long term planning
104 SNMP Simple network management protocol Used together with TCP/IP protocol suite Provides fundamental operations for monitoring and maintaining a network Application-layer protocol Devices made by different manufacturers and installed on different networks can still be monitored Frees management tasks from physical features of managed devices and from network technology
105 SNMP concept
106 Managers and agents A few manager stations control a set of agents Manager: usually a host Control and monitors a set of agents Runs a SNMP client program Agent: usually a router or host Runs a SNMP server program Management achieved through simple interactions between the two entities
107 Managers and agents 2 Performance information is kept by the agent in a database SNMP management based on 3 ideas Manager checks the agent by requesting information reflecting agent s behavior Manager can force the agent to perform some tasks by resetting values in the database Agent contributes by warning manager of unusual situations
108 Management components
109 Other protocols contributing to Internet management Structure of management information (SMI) Management information base (MIB) SNMP uses SMI and MIB services All three use Abstract syntax notation 1 (ASN.1) Basic encoding rules (BER)
110 SMI functions 1. To name objects 2. To define the types of data to be stored in objects 3. To show how to encode data for transmission over network SMI is a guideline for SNMP, emphasizing 3 attributes for handling an object
111 SMI name SMI requires objects to have unique names Routers Variables in routers Values, etc Object identifier (OI) Used for naming objects globally Hierarchical identifier based on a tree structure
112 OI
113 Data type
114 Simple types Type Size Description Integer 4 bytes Cardinal number between 0 and String Variable 0 or more ASCII characters ObjectIdentifier Variable Object identifier represented in ASCII code IPAddress 4 bytes IP address made of four integers Counter 4 bytes Integer whose value can be incremented from 0 to ; when it reaches max value it wraps back to 0 Gauge 4 bytes Same as counter, but at max value it does not wrap; remains so until it s reset TimeTicks 4 bytes A counting value recording time in ms
115 Structured type sequence and sequence of sequence: combination of simple data types, not necessarily of the same type Analogous to record/struct in C sequence of : combination of simple or sequence data types, all of the same type Analogous to array in C
116 Conceptual data types
117 Encoding method Uses BER to encode data for transmission BER specifies each data piece is encoded in a triplet: (tag, length, value)
118 Tag 1-byte field defining type of data, has 3 subfields: class, format, number class: 2 bit-subfield, defines scope of data Universal: 00, application-wide: 01, context-specific: 10, private: 11 00: data types taken from ASN1 (integer, string, ObjectIdentifier, sequences) 01: data types added by SMI (the other simple 4 types) 10: types with meaning that may change from a protocol to another 11: vendor-specific
119 Tag 2 format: 1-bit subfield, indicates whether the data is simple (0) or structured (1) number: 5-bit subfield, further devides simple/structured data into subgroups
120 Some codes for data types Data type Class Format Number Tag hexa Integer String ObjectIdentifier sequence (of) IPAddress Counter Gauge TimeTicks
121 Length 1 or more bytes If 1 byte: first bit is 0, the rest define the length If more than 1 byte: first bit 1, next 7 bits define how many bytes needed for defining length
122 Some examples
123 MIB Each agent has its own MIB A collection of all objects that manager can manage Objects categorized under 8 different groups System, interface, address translation, ip, icmp, tcp, udp, egp Shown under mib object in the object identifier tree
124 Example: accessing MIB variables in udp group
125 For simple variables To get the instance (contents) we add as suffix a 0: udpindatagrams udpnoports udpinerrors udpoutdatagrams
126 For tables (sequence of) variables When we get to the instance, we need to define which instance At any moment, the table can have several values for the instances To access a certain instance (row) of the table, we need to add the index The indexes are not numeric, but based on one or more fields in the entries Not all tables are indexed the same way
127 udp variables and tables
128 Indexes for udp table
129 SNMP messages
130 Messages GetRequest Sent from manager to agent to retrieve the value of some variable GetNextRequest Same as above Retrieved value is the value of the object following the defined ObjectId in message Mostly used to get table entry values
131 Messages 2 GetNextRequest 2 If manager does not know the entry indexes, cannot access the values It can use this message to find out GetResponse From agent to manager, in response to above messages Contains the values of the variables requested by manager
132 Messages 3 SetRequest From manager to agent to set a value in a variable Trap From agent to manager to report an event Exp: if agent rebooted, reports to manager with time of rebooting
133 Message format
134 Message fields Version: version number -1 Community: defines the password If no password, string public is used Request ID: used to match a request to a response Sequence number used by manager in request message Repeated by agent in response
135 Message fields 2 Error status: integer used only in response messages to show an error occurred Has value 0 in request messages Error index: offset telling the manager which variable caused the error VarBindList: set of variables with corresponding values the manager wants to retrieve or set Null values in GetRequest and GetNextRequest In Trap message it shows the variables and values related to a specific message
136 Message fields 3 Enterprise: defines the ObjectId of the software that generates the Trap Agent address: IP address of agent that created the Trap Trap type: 1-bit field Specific code: if Trap value=6, this field set Time stamp: time elapsed since the event caused a trap
137 Error types Status Name Meaning 0 noerror No error 1 toobig Response too big to fit in one message 2 nosuchname Variable does not exist 3 badvalue The value to be stored is invalid 4 readonly The value cannot be modified 5 generr Other errors
138 Trap types Status Name Meaning 0 coldstart Agent has been booted 1 warmstart Agent has been rebooted 2 linkdown An interface has gone down 3 linkup An interface has come up 4 authenticationfailure Invalid community detected 5 egpneighborloss An EGP router has gone to down state 6 enterprisespecific Other messages
139 Encoding BER standard is used Messages defined using tags: class context sensitive (10), format is structured (1) and numbers 0 4: Data Class Format Number Tag in hexa GetRequest A0 GetNextRequest A1 GetResponse A2 SetRequest A3 Trap A4
140 Encoding SNMP using BER
COSC 301 Network Management
 COSC 301 Network Management Lecture 20: Management Tools and Protocols Zhiyi Huang Computer Science, University of Otago COSC301 Lecture 20: Management tools and protocols 1 What is Network Management?
COSC 301 Network Management Lecture 20: Management Tools and Protocols Zhiyi Huang Computer Science, University of Otago COSC301 Lecture 20: Management tools and protocols 1 What is Network Management?
TELE 301 Network Management
 TELE 301 Network Management Lecture 20: Management Tools and Protocols Haibo Zhang Computer Science, University of Otago TELE301 Lecture 20: Management tools and protocols 1 What is Network Management?
TELE 301 Network Management Lecture 20: Management Tools and Protocols Haibo Zhang Computer Science, University of Otago TELE301 Lecture 20: Management tools and protocols 1 What is Network Management?
CS Efficient Network Management. Class 5. Danny Raz
 CS236635 Efficient Network Management Class 5 Danny Raz 1 Minhalot Exercise 1 is due TODAY Exercise2 writing a paper review (list will be on the Web by the midterm) Mailing list - exists Mid Term exam:
CS236635 Efficient Network Management Class 5 Danny Raz 1 Minhalot Exercise 1 is due TODAY Exercise2 writing a paper review (list will be on the Web by the midterm) Mailing list - exists Mid Term exam:
Unit 2. Internet based Network Management
 Unit 2 Internet based Network Management Internet based Network Management In the Internet world Network management refers to management of networks, devices, and hosts Achieved through 'Simple Network
Unit 2 Internet based Network Management Internet based Network Management In the Internet world Network management refers to management of networks, devices, and hosts Achieved through 'Simple Network
7010INT Data Communications Lecture 7 The Network Layer
 Introduction 7010INT Data Communications Lecture 7 The Layer Internetworking & Devices Connecting LANs Routing Backbone networks Virtual LANs Addressing Application Presentation Session Data Link Physical
Introduction 7010INT Data Communications Lecture 7 The Layer Internetworking & Devices Connecting LANs Routing Backbone networks Virtual LANs Addressing Application Presentation Session Data Link Physical
Chapter 4 NETWORK HARDWARE
 Chapter 4 NETWORK HARDWARE 1 Network Devices As Organizations grow, so do their networks Growth in number of users Geographical Growth Network Devices : Are products used to expand or connect networks.
Chapter 4 NETWORK HARDWARE 1 Network Devices As Organizations grow, so do their networks Growth in number of users Geographical Growth Network Devices : Are products used to expand or connect networks.
Medium Access Protocols
 Medium Access Protocols Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division,Code Division, Frequency Division Random partitioning
Medium Access Protocols Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division,Code Division, Frequency Division Random partitioning
SNMP Basics BUPT/QMUL
 SNMP Basics BUPT/QMUL 2014-05-12 Agenda Brief introduction to Network Management Brief introduction to SNMP SNMP Network Management Framework RMON New trends of network management Summary 2 Brief Introduction
SNMP Basics BUPT/QMUL 2014-05-12 Agenda Brief introduction to Network Management Brief introduction to SNMP SNMP Network Management Framework RMON New trends of network management Summary 2 Brief Introduction
CH : 15 LOCAL AREA NETWORK OVERVIEW
 CH : 15 LOCAL AREA NETWORK OVERVIEW P. 447 LAN (Local Area Network) A LAN consists of a shared transmission medium and a set of hardware and software for interfacing devices to the medium and regulating
CH : 15 LOCAL AREA NETWORK OVERVIEW P. 447 LAN (Local Area Network) A LAN consists of a shared transmission medium and a set of hardware and software for interfacing devices to the medium and regulating
SNMP and Network Management
 SNMP and Network Management Nixu Ltd Contents Network Management MIB naming tree, MIB-II SNMP protocol SNMP traps SNMP versions 2 Network management When you have 100s of computers in a network or are
SNMP and Network Management Nixu Ltd Contents Network Management MIB naming tree, MIB-II SNMP protocol SNMP traps SNMP versions 2 Network management When you have 100s of computers in a network or are
Network Management. Raj Jain Raj Jain. Washington University in St. Louis
 Network Management Raj Jain Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@wustl.edu Audio/Video recordings of this lecture are available on-line at: http://www.cse.wustl.edu/~jain/cse473-09/
Network Management Raj Jain Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@wustl.edu Audio/Video recordings of this lecture are available on-line at: http://www.cse.wustl.edu/~jain/cse473-09/
Darshan Institute of Engineering & Technology for Diploma Studies
 1. Explain different network devices in detail. Or Explain NIC (Network Interface Card) in detail. Network interface cards are add on cards as hardware cards on the motherboard. This is additional hardware
1. Explain different network devices in detail. Or Explain NIC (Network Interface Card) in detail. Network interface cards are add on cards as hardware cards on the motherboard. This is additional hardware
Network Management: SNMP
 CHAPTER 28 Network Management: SNMP We can define network management as monitoring, testing, configuring, and troubleshooting network components to meet a set of requirements defined by an organization.
CHAPTER 28 Network Management: SNMP We can define network management as monitoring, testing, configuring, and troubleshooting network components to meet a set of requirements defined by an organization.
Chapter 2 - Part 1. The TCP/IP Protocol: The Language of the Internet
 Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
Chapter 23. Simple Network Management Protocol (SNMP)
 Chapter 23 Simple Network Management Protocol (SNMP) 1 The McGraw-Hill Companies, Inc., 2000 1 CONTENTS CONCEPT MANAGEMENT COMPONENTS SMI MIB SNMP MESSAGES UDP PORTS SECURITY 2 The McGraw-Hill Companies,
Chapter 23 Simple Network Management Protocol (SNMP) 1 The McGraw-Hill Companies, Inc., 2000 1 CONTENTS CONCEPT MANAGEMENT COMPONENTS SMI MIB SNMP MESSAGES UDP PORTS SECURITY 2 The McGraw-Hill Companies,
SNMP Basics BUPT/QMUL
 SNMP Basics BUPT/QMUL 2017-05-22 Agenda Brief introduction to Network Management Brief introduction to SNMP SNMP Network Management Framework RMON New trends of network management Summary 2 Brief Introduction
SNMP Basics BUPT/QMUL 2017-05-22 Agenda Brief introduction to Network Management Brief introduction to SNMP SNMP Network Management Framework RMON New trends of network management Summary 2 Brief Introduction
Network Management (NETW-1001)
 Network Management (NETW-1001) Dr. Mohamed Abdelwahab Saleh IET-Networks, GUC Spring 2017 TOC 1 SNMPv1 Messages 2 SNMP messages Two main purposes: Monitoring and configuration. SNMP version 1 defines five
Network Management (NETW-1001) Dr. Mohamed Abdelwahab Saleh IET-Networks, GUC Spring 2017 TOC 1 SNMPv1 Messages 2 SNMP messages Two main purposes: Monitoring and configuration. SNMP version 1 defines five
Connecting LANs, Backbone Networks, and Virtual LANs
 CHAPTER 15 Connecting LANs, Backbone Networks, and Virtual LANs LANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, or segments oflans, we
CHAPTER 15 Connecting LANs, Backbone Networks, and Virtual LANs LANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, or segments oflans, we
Data Link Layer. Our goals: understand principles behind data link layer services: instantiation and implementation of various link layer technologies
 Data Link Layer Our goals: understand principles behind data link layer services: link layer addressing instantiation and implementation of various link layer technologies 1 Outline Introduction and services
Data Link Layer Our goals: understand principles behind data link layer services: link layer addressing instantiation and implementation of various link layer technologies 1 Outline Introduction and services
SNMP and Network Management
 Contents SNMP and Network Management Network Management MIB naming tree, MIB-II SNMP protocol SNMP traps SNMP versions Nixu Ltd 2 Network management When you have 100s of computers in a network or are
Contents SNMP and Network Management Network Management MIB naming tree, MIB-II SNMP protocol SNMP traps SNMP versions Nixu Ltd 2 Network management When you have 100s of computers in a network or are
SNMP Simple Network Management Protocol
 SNMP Simple Network Management Protocol Simple Network Management Protocol SNMP is a framework that provides facilities for managing and monitoring network resources on the Internet. Components of SNMP:
SNMP Simple Network Management Protocol Simple Network Management Protocol SNMP is a framework that provides facilities for managing and monitoring network resources on the Internet. Components of SNMP:
More on LANS. LAN Wiring, Interface
 More on LANS Chapters 10-11 LAN Wiring, Interface Mostly covered this material already NIC = Network Interface Card Separate processor, buffers incoming/outgoing data CPU might not be able to keep up network
More on LANS Chapters 10-11 LAN Wiring, Interface Mostly covered this material already NIC = Network Interface Card Separate processor, buffers incoming/outgoing data CPU might not be able to keep up network
Outline. SNMP Simple Network Management Protocol. Before we start on SNMP. Simple Network Management Protocol
 Outline SNMP Simple Network Management Protocol Several slides are courtesy of the Addison Wesley companion web site for textbook by Liebeherr and El Zarki and others added by M. Veeraraghavan, Univ. of
Outline SNMP Simple Network Management Protocol Several slides are courtesy of the Addison Wesley companion web site for textbook by Liebeherr and El Zarki and others added by M. Veeraraghavan, Univ. of
Summary of MAC protocols
 Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division, Code Division, Frequency Division Random partitioning (dynamic) ALOHA, S-ALOHA,
Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division, Code Division, Frequency Division Random partitioning (dynamic) ALOHA, S-ALOHA,
Outline Network Management MIB naming tree, MIB-II SNMP protocol Network management in practice. Network Management. Jaakko Kotimäki.
 Outline MIB naming tree, MIB-II SNMP protocol Network management in practice 19.10.2010 Outline MIB naming tree, MIB-II SNMP protocol Network management in practice Outline Contents MIB naming tree, MIB-II
Outline MIB naming tree, MIB-II SNMP protocol Network management in practice 19.10.2010 Outline MIB naming tree, MIB-II SNMP protocol Network management in practice Outline Contents MIB naming tree, MIB-II
6.1.2 Repeaters. Figure Repeater connecting two LAN segments. Figure Operation of a repeater as a level-1 relay
 6.1.2 Repeaters A single Ethernet segment can have a maximum length of 500 meters with a maximum of 100 stations (in a cheapernet segment it is 185m). To extend the length of the network, a repeater may
6.1.2 Repeaters A single Ethernet segment can have a maximum length of 500 meters with a maximum of 100 stations (in a cheapernet segment it is 185m). To extend the length of the network, a repeater may
CCM 4300 Lecture 5 Computer Networks, Wireless and Mobile Communications. Dr Shahedur Rahman. Room: T115
 CCM 4300 Lecture 5 Computer Networks, Wireless and Mobile Communications Dr Shahedur Rahman s.rahman@mdx.ac.uk Room: T115 1 Recap of Last Session Described the physical layer Analogue and Digital signal
CCM 4300 Lecture 5 Computer Networks, Wireless and Mobile Communications Dr Shahedur Rahman s.rahman@mdx.ac.uk Room: T115 1 Recap of Last Session Described the physical layer Analogue and Digital signal
Introduction to Networking Devices
 Introduction to Networking Devices Objectives Explain the uses, advantages, and disadvantages of repeaters, hubs, wireless access points, bridges, switches, and routers Define the standards associated
Introduction to Networking Devices Objectives Explain the uses, advantages, and disadvantages of repeaters, hubs, wireless access points, bridges, switches, and routers Define the standards associated
Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs.
 Internetworking Multiple networks are a fact of life: Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs. Fault isolation,
Internetworking Multiple networks are a fact of life: Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs. Fault isolation,
Layer 2 functionality bridging and switching
 Layer 2 functionality bridging and switching BSAD 141 Dave Novak Sources: Network+ Guide to Networks, Dean 2013 Overview Layer 2 functionality Error detection Bridges Broadcast and collision domains How
Layer 2 functionality bridging and switching BSAD 141 Dave Novak Sources: Network+ Guide to Networks, Dean 2013 Overview Layer 2 functionality Error detection Bridges Broadcast and collision domains How
Chapter 28 Network Management: SNMP Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display.
 Chapter 28 Network Management: SNMP 28.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 28-1 NETWORK MANAGEMENT SYSTEM We can say that the functions performed
Chapter 28 Network Management: SNMP 28.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 28-1 NETWORK MANAGEMENT SYSTEM We can say that the functions performed
Network Management. Jaakko Kotimäki. Department of Computer Science Aalto University, School of Science and Technology. 16.
 Jaakko Kotimäki Department of Computer Science Aalto University, School of Science and Technology Outline Introduction SNMP architecture Management Information Base SNMP protocol Network management in
Jaakko Kotimäki Department of Computer Science Aalto University, School of Science and Technology Outline Introduction SNMP architecture Management Information Base SNMP protocol Network management in
Chapter 6: DataLink Layer - Ethernet Olivier Bonaventure (2010)
 Chapter 6: DataLink Layer - Ethernet Olivier Bonaventure (2010) 6.3.2. Ethernet Ethernet was designed in the 1970s at the Palo Alto Research Center [Metcalfe1976]. The first prototype [5] used a coaxial
Chapter 6: DataLink Layer - Ethernet Olivier Bonaventure (2010) 6.3.2. Ethernet Ethernet was designed in the 1970s at the Palo Alto Research Center [Metcalfe1976]. The first prototype [5] used a coaxial
2. LAN Topologies Gilbert Ndjatou Page 1
 2. LAN Topologies Two basic categories of network topologies exist, physical topologies and logical topologies. The physical topology of a network is the cabling layout used to link devices. This refers
2. LAN Topologies Two basic categories of network topologies exist, physical topologies and logical topologies. The physical topology of a network is the cabling layout used to link devices. This refers
Links Reading: Chapter 2. Goals of Todayʼs Lecture. Message, Segment, Packet, and Frame
 Links Reading: Chapter 2 CS 375: Computer Networks Thomas Bressoud 1 Goals of Todayʼs Lecture Link-layer services Encoding, framing, and error detection Error correction and flow control Sharing a shared
Links Reading: Chapter 2 CS 375: Computer Networks Thomas Bressoud 1 Goals of Todayʼs Lecture Link-layer services Encoding, framing, and error detection Error correction and flow control Sharing a shared
LAN Overview (part 2) Interconnecting LANs - Hubs
 LAN Overview (part 2) CSE 3213 Fall 2011 1 November 2011 Interconnecting LANs - Hubs active central element of star layout each station connected to hub by two UTP lines hub acts as a repeater limited
LAN Overview (part 2) CSE 3213 Fall 2011 1 November 2011 Interconnecting LANs - Hubs active central element of star layout each station connected to hub by two UTP lines hub acts as a repeater limited
TCOM 370 NOTES 99-1 NETWORKING AND COMMUNICATIONS
 TCOM 370 NOTES 99-1 NETWORKING AND COMMUNICATIONS Communication Networks Allow Exchange of Information between Users telephone network for voice communication interconnected computers and peripherals,
TCOM 370 NOTES 99-1 NETWORKING AND COMMUNICATIONS Communication Networks Allow Exchange of Information between Users telephone network for voice communication interconnected computers and peripherals,
Integrating Information Systems: Technology, Strategy, and Organizational Factors
 MASSACHUSETTS INSTITUTE OF TECHNOLOGY SLOAN SCHOOL OF MANAGEMENT 15.565 Integrating Information Systems: Technology, Strategy, and Organizational Factors 15.578 Global Information Systems: Communications
MASSACHUSETTS INSTITUTE OF TECHNOLOGY SLOAN SCHOOL OF MANAGEMENT 15.565 Integrating Information Systems: Technology, Strategy, and Organizational Factors 15.578 Global Information Systems: Communications
Network Management. Stuart Johnston 13 October 2011
 Network Management Stuart Johnston stuart.johnston@inmon.com 13 October 2011 Slides from: Computer Networking: A Top Down Approach, 4th edition. Jim Kurose, Keith Ross Addison-Wesley, July 2007 All material
Network Management Stuart Johnston stuart.johnston@inmon.com 13 October 2011 Slides from: Computer Networking: A Top Down Approach, 4th edition. Jim Kurose, Keith Ross Addison-Wesley, July 2007 All material
Links. CS125 - mylinks 1 1/22/14
 Links 1 Goals of Today s Lecture Link-layer services Encoding, framing, and error detection Error correction and flow control Sharing a shared media Channel partitioning Taking turns Random access Shared
Links 1 Goals of Today s Lecture Link-layer services Encoding, framing, and error detection Error correction and flow control Sharing a shared media Channel partitioning Taking turns Random access Shared
CCNA Exploration1 Chapter 7: OSI Data Link Layer
 CCNA Exploration1 Chapter 7: OSI Data Link Layer LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Explain the role of Data Link layer protocols in data transmission; Objectives Describe how the
CCNA Exploration1 Chapter 7: OSI Data Link Layer LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Explain the role of Data Link layer protocols in data transmission; Objectives Describe how the
King Fahd University of Petroleum & Minerals Electrical Engineering Department EE 400, Experiment # 2
 King Fahd University of Petroleum & Minerals Electrical Engineering Department EE 400, Experiment # 2 IP Addressing and Subnetting: Establishing Elementary Networks using Hubs, Switches and Routers. Objectives:
King Fahd University of Petroleum & Minerals Electrical Engineering Department EE 400, Experiment # 2 IP Addressing and Subnetting: Establishing Elementary Networks using Hubs, Switches and Routers. Objectives:
Local Area Network Overview
 Local Area Network Overview Chapter 15 CS420/520 Axel Krings Page 1 LAN Applications (1) Personal computer LANs Low cost Limited data rate Back end networks Interconnecting large systems (mainframes and
Local Area Network Overview Chapter 15 CS420/520 Axel Krings Page 1 LAN Applications (1) Personal computer LANs Low cost Limited data rate Back end networks Interconnecting large systems (mainframes and
Network Management System
 Network Management System NMS: Simple solution: Ping all elements routinely If machine down go and fix it Time stamps on ping packets indicate delay, congestion Becomes a problem with large and complex
Network Management System NMS: Simple solution: Ping all elements routinely If machine down go and fix it Time stamps on ping packets indicate delay, congestion Becomes a problem with large and complex
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca
 CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti Administrivia Homework I out later today, due next Thursday Today: Link Layer (cont.)
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti Administrivia Homework I out later today, due next Thursday Today: Link Layer (cont.)
Revision of Previous Lectures
 Lecture 15 Overview Last Lecture Local area networking This Lecture Wide area networking 1 Source: chapters 8.1-8.3, 17.1, 18.1, 18.2 Next Lecture Wide area networking 2 Source: Chapter 20 COSC244 Lecture
Lecture 15 Overview Last Lecture Local area networking This Lecture Wide area networking 1 Source: chapters 8.1-8.3, 17.1, 18.1, 18.2 Next Lecture Wide area networking 2 Source: Chapter 20 COSC244 Lecture
RMIT University. Data Communication and Net-Centric Computing COSC 1111/2061/1110. Lecture 8. Medium Access Control Methods & LAN
 RMIT University Data Communication and Net-Centric Computing COSC 1111/2061/1110 Medium Access Control Methods & LAN Technology Slide 1 Lecture Overview During this lecture, we will Look at several Multiple
RMIT University Data Communication and Net-Centric Computing COSC 1111/2061/1110 Medium Access Control Methods & LAN Technology Slide 1 Lecture Overview During this lecture, we will Look at several Multiple
Introduction to Open System Interconnection Reference Model
 Chapter 5 Introduction to OSI Reference Model 1 Chapter 5 Introduction to Open System Interconnection Reference Model Introduction The Open Systems Interconnection (OSI) model is a reference tool for understanding
Chapter 5 Introduction to OSI Reference Model 1 Chapter 5 Introduction to Open System Interconnection Reference Model Introduction The Open Systems Interconnection (OSI) model is a reference tool for understanding
Network Management. Stuart Johnston 08 November 2010
 Network Management Stuart Johnston stuart.johnston@inmon.com 08 November 2010 Slides from: Computer Networking: A Top Down Approach, 4th edition. Jim Kurose, Keith Ross Addison-Wesley, July 2007 All material
Network Management Stuart Johnston stuart.johnston@inmon.com 08 November 2010 Slides from: Computer Networking: A Top Down Approach, 4th edition. Jim Kurose, Keith Ross Addison-Wesley, July 2007 All material
HyperText Transfer Protocol. HTTP Commands. HTTP Responses
 Hyper Transfer Protocol HTTP - just a different file transfer protocol Simplified, standard client/server model just one connection for commands and data Data transferred is structured Similar to MIME
Hyper Transfer Protocol HTTP - just a different file transfer protocol Simplified, standard client/server model just one connection for commands and data Data transferred is structured Similar to MIME
Computer Networks Medium Access Control. Mostafa Salehi Fall 2008
 Computer Networks Medium Access Control Mostafa Salehi Fall 2008 2008 1 Outline Issues ALOHA Network Ethernet Token Ring Wireless 2 Main Issues Local Area Network (LAN) : Three or more machines are physically
Computer Networks Medium Access Control Mostafa Salehi Fall 2008 2008 1 Outline Issues ALOHA Network Ethernet Token Ring Wireless 2 Main Issues Local Area Network (LAN) : Three or more machines are physically
LAN Interconnection. different interconnecting devices, many approaches Vasile Dadarlat- Local Area Computer Networks
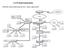 LAN Interconnection different interconnecting devices, many approaches 1 Need for ability to expand beyond single LAN; appears concept of Extended LAN, extending the number of attached stations and maximum
LAN Interconnection different interconnecting devices, many approaches 1 Need for ability to expand beyond single LAN; appears concept of Extended LAN, extending the number of attached stations and maximum
Layering in Networked computing. OSI Model TCP/IP Model Protocols at each layer
 Layering in Networked computing OSI Model TCP/IP Model Protocols at each layer Learning outcomes Understand the need of layering in Networked computing Understand the OSI model and the tcp/ip model Understand
Layering in Networked computing OSI Model TCP/IP Model Protocols at each layer Learning outcomes Understand the need of layering in Networked computing Understand the OSI model and the tcp/ip model Understand
Command Manual SNMP-RMON. Table of Contents
 Table of Contents Table of Contents... 1-1 1.1 SNMP Configuration Commands... 1-1 1.1.1 display snmp-agent... 1-1 1.1.2 display snmp-agent community... 1-2 1.1.3 display snmp-agent group... 1-3 1.1.4 display
Table of Contents Table of Contents... 1-1 1.1 SNMP Configuration Commands... 1-1 1.1.1 display snmp-agent... 1-1 1.1.2 display snmp-agent community... 1-2 1.1.3 display snmp-agent group... 1-3 1.1.4 display
Lecture 18: Network Management
 Lecture 18: Network Management Prof. Shervin Shirmohammadi SITE, University of Ottawa Prof. Shervin Shirmohammadi CEG 4183 18-1 Objective Manage a network by managing its components: routers, bridges,
Lecture 18: Network Management Prof. Shervin Shirmohammadi SITE, University of Ottawa Prof. Shervin Shirmohammadi CEG 4183 18-1 Objective Manage a network by managing its components: routers, bridges,
IT 4504 Section 4.0. Network Architectures. 2008, University of Colombo School of Computing 1
 IT 4504 Section 4.0 Network Architectures 2008, University of Colombo School of Computing 1 Section 4.1 Introduction to Computer Networks 2008, University of Colombo School of Computing 2 Introduction
IT 4504 Section 4.0 Network Architectures 2008, University of Colombo School of Computing 1 Section 4.1 Introduction to Computer Networks 2008, University of Colombo School of Computing 2 Introduction
Principles behind data link layer services
 Data link layer Goals: Principles behind data link layer services Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control: Done!
Data link layer Goals: Principles behind data link layer services Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control: Done!
===================================================================== Exercises =====================================================================
 ===================================================================== Exercises ===================================================================== 1 Chapter 1 1) Design and describe an application-level
===================================================================== Exercises ===================================================================== 1 Chapter 1 1) Design and describe an application-level
Network Infrastructure
 Network Infrastructure For building computer networks more complex than e.g. a short bus, some additional components are needed. They can be arranged hierarchically regarding their functionality: Repeater
Network Infrastructure For building computer networks more complex than e.g. a short bus, some additional components are needed. They can be arranged hierarchically regarding their functionality: Repeater
ET4254 Communications and Networking 1
 Topic 10:- Local Area Network Overview Aims:- LAN topologies and media LAN protocol architecture bridges, hubs, layer 2 & 3 switches 1 LAN Applications (1) personal computer LANs low cost limited data
Topic 10:- Local Area Network Overview Aims:- LAN topologies and media LAN protocol architecture bridges, hubs, layer 2 & 3 switches 1 LAN Applications (1) personal computer LANs low cost limited data
3.5 CONNECTING DEVICES
 3.5 CONNECTING DEVICES LANs or WANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs and WANs together we use connecting devices. Connecting devices
3.5 CONNECTING DEVICES LANs or WANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs and WANs together we use connecting devices. Connecting devices
Networks Hardware Components
 Lec. 5 Networks Hardware Components Dr. Eng. Samy Elmokadem Chapter 8 10/12/2017 1 internetworking devices used in backbone networks After studying this Chapter you should: Know which internetworking devices
Lec. 5 Networks Hardware Components Dr. Eng. Samy Elmokadem Chapter 8 10/12/2017 1 internetworking devices used in backbone networks After studying this Chapter you should: Know which internetworking devices
Guide to Networking Essentials, 6 th Edition. Chapter 7: Network Hardware in Depth
 Guide to Networking Essentials, 6 th Edition Chapter 7: Network Hardware in Depth Objectives Describe the advanced features and operation of network switches Describe routing table properties and discuss
Guide to Networking Essentials, 6 th Edition Chapter 7: Network Hardware in Depth Objectives Describe the advanced features and operation of network switches Describe routing table properties and discuss
OSI Model. Teran Subasinghe MBCS, Bsc.(Hons) in Computer Science - University of Greenwich, UK
 OSI Model Teran Subasinghe MBCS, Bsc.(Hons) in Computer Science - University of Greenwich, UK What is OSI Model? Open Systems Interconnection Reference Model Developed in 1984 by the International Standards
OSI Model Teran Subasinghe MBCS, Bsc.(Hons) in Computer Science - University of Greenwich, UK What is OSI Model? Open Systems Interconnection Reference Model Developed in 1984 by the International Standards
Chapter 15 Local Area Network Overview
 Chapter 15 Local Area Network Overview LAN Topologies Bus and Tree Bus: stations attach through tap to bus full duplex allows transmission and reception transmission propagates throughout medium heard
Chapter 15 Local Area Network Overview LAN Topologies Bus and Tree Bus: stations attach through tap to bus full duplex allows transmission and reception transmission propagates throughout medium heard
infrared Disadvantage: 1. cannot use for long-range communication or outside a building due to sun s rays.
 Chapter2: analog and digital signals can take one of two forms: 1. periodic 2. nonperiodic Periodic analog signals can be classified as: 1. simple 2. composite A sine wave is represented by three parameters:
Chapter2: analog and digital signals can take one of two forms: 1. periodic 2. nonperiodic Periodic analog signals can be classified as: 1. simple 2. composite A sine wave is represented by three parameters:
Reminder: Datalink Functions Computer Networking. Datalink Architectures
 Reminder: Datalink Functions 15-441 15 441 15-641 Computer Networking Lecture 5 Media Access Control Peter Steenkiste Fall 2015 www.cs.cmu.edu/~prs/15-441-f15 Framing: encapsulating a network layer datagram
Reminder: Datalink Functions 15-441 15 441 15-641 Computer Networking Lecture 5 Media Access Control Peter Steenkiste Fall 2015 www.cs.cmu.edu/~prs/15-441-f15 Framing: encapsulating a network layer datagram
High Level View. EE 122: Ethernet and Random Access protocols. Medium Access Protocols
 High Level View EE 122: Ethernet and 802.11 Ion Stoica September 18, 2002 Goal: share a communication medium among multiple hosts connected to it Problem: arbitrate between connected hosts Solution goals:
High Level View EE 122: Ethernet and 802.11 Ion Stoica September 18, 2002 Goal: share a communication medium among multiple hosts connected to it Problem: arbitrate between connected hosts Solution goals:
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca
 CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Janno< Administrivia Homework I out later today, due next Thursday, Sep 25th Today: Link Layer
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Janno< Administrivia Homework I out later today, due next Thursday, Sep 25th Today: Link Layer
A Brief Introduction to Internet Network Management. Geoff Huston
 A Brief Introduction to Internet Network Management Geoff Huston gih@telstra.net What are we talking about? Network Management Tasks fault management configuration management performance management security
A Brief Introduction to Internet Network Management Geoff Huston gih@telstra.net What are we talking about? Network Management Tasks fault management configuration management performance management security
EEC-484/584 Computer Networks
 EEC-484/584 Computer Networks Lecture 13 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline 2 Review of lecture 12 Routing Congestion
EEC-484/584 Computer Networks Lecture 13 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline 2 Review of lecture 12 Routing Congestion
Chapter 6: Network Communications and Protocols
 Learning Objectives Chapter 6: Network Communications and Protocols Understand the function and structure of packets in a network, and analyze and understand those packets Understand the function of protocols
Learning Objectives Chapter 6: Network Communications and Protocols Understand the function and structure of packets in a network, and analyze and understand those packets Understand the function of protocols
Principles behind data link layer services:
 Data link layer Goals: Principles behind data link layer services: Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control Example
Data link layer Goals: Principles behind data link layer services: Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control Example
Principles behind data link layer services:
 Data link layer Goals: Principles behind data link layer services: Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control Example
Data link layer Goals: Principles behind data link layer services: Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control Example
Link Layer and Ethernet
 Link Layer and Ethernet 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross traceroute Data Link Layer Multiple
Link Layer and Ethernet 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross traceroute Data Link Layer Multiple
The random access methods we study in this chapter have evolved from a very interesting protocol known as ALOHA, which used a very simple procedure
 Multiple Accesses When nodes or stations are connected and use a common link, called a multipoint or broadcast link, we need a multiple-access protocol to coordinate access to the link. The problem of
Multiple Accesses When nodes or stations are connected and use a common link, called a multipoint or broadcast link, we need a multiple-access protocol to coordinate access to the link. The problem of
Module 16: Distributed System Structures
 Chapter 16: Distributed System Structures Module 16: Distributed System Structures Motivation Types of Network-Based Operating Systems Network Structure Network Topology Communication Structure Communication
Chapter 16: Distributed System Structures Module 16: Distributed System Structures Motivation Types of Network-Based Operating Systems Network Structure Network Topology Communication Structure Communication
CS 43: Computer Networks Switches and LANs. Kevin Webb Swarthmore College December 5, 2017
 CS 43: Computer Networks Switches and LANs Kevin Webb Swarthmore College December 5, 2017 Ethernet Metcalfe s Ethernet sketch Dominant wired LAN technology: cheap $20 for NIC first widely used LAN technology
CS 43: Computer Networks Switches and LANs Kevin Webb Swarthmore College December 5, 2017 Ethernet Metcalfe s Ethernet sketch Dominant wired LAN technology: cheap $20 for NIC first widely used LAN technology
Switching and Forwarding Reading: Chapter 3 1/30/14 1
 Switching and Forwarding Reading: Chapter 3 1/30/14 1 Switching and Forwarding Next Problem: Enable communication between hosts that are not directly connected Fundamental Problem of the Internet or any
Switching and Forwarding Reading: Chapter 3 1/30/14 1 Switching and Forwarding Next Problem: Enable communication between hosts that are not directly connected Fundamental Problem of the Internet or any
CHAPTER 2 - NETWORK DEVICES
 CHAPTER 2 - NETWORK DEVICES TRUE/FALSE 1. Repeaters can reformat, resize, or otherwise manipulate the data packet. F PTS: 1 REF: 30 2. Because active hubs have multiple inbound and outbound connections,
CHAPTER 2 - NETWORK DEVICES TRUE/FALSE 1. Repeaters can reformat, resize, or otherwise manipulate the data packet. F PTS: 1 REF: 30 2. Because active hubs have multiple inbound and outbound connections,
ET4254 Communications and Networking 1
 Topic 9 Internet Protocols Aims:- basic protocol functions internetworking principles connectionless internetworking IP IPv6 IPSec 1 Protocol Functions have a small set of functions that form basis of
Topic 9 Internet Protocols Aims:- basic protocol functions internetworking principles connectionless internetworking IP IPv6 IPSec 1 Protocol Functions have a small set of functions that form basis of
Lecture 9: Bridging. CSE 123: Computer Networks Alex C. Snoeren
 Lecture 9: Bridging CSE 123: Computer Networks Alex C. Snoeren Lecture 9 Overview Finishing up media access Ethernet Contention-free methods (rings) Moving beyond one wire Link technologies have limits
Lecture 9: Bridging CSE 123: Computer Networks Alex C. Snoeren Lecture 9 Overview Finishing up media access Ethernet Contention-free methods (rings) Moving beyond one wire Link technologies have limits
Link Layer and Ethernet
 Link Layer and Ethernet 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross traceroute Data Link Layer Multiple
Link Layer and Ethernet 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross traceroute Data Link Layer Multiple
SNMP traps (simple network management protocol)
 SNMP traps (simple network management protocol) Nasser M. Abbasi Nov 25, 2000 page compiled on June 29, 2015 at 3:16am Contents 1 Processing on SNMP messages 2 2 Parsing an SNMP v1 UDP pkt 3 3 Program
SNMP traps (simple network management protocol) Nasser M. Abbasi Nov 25, 2000 page compiled on June 29, 2015 at 3:16am Contents 1 Processing on SNMP messages 2 2 Parsing an SNMP v1 UDP pkt 3 3 Program
3. (a) What is bridge? Explain the operation of a LAN bridge from to (b) Explain the operation of transparent bridge.
 Code No: RR320503 Set No. 1 III B.Tech II Semester Supplimentary Examinations, Aug/Sep 2007 COMPUTER NETWORKS ( Common to Computer Science & Engineering, Information Technology, Electronics & Control Engineering,
Code No: RR320503 Set No. 1 III B.Tech II Semester Supplimentary Examinations, Aug/Sep 2007 COMPUTER NETWORKS ( Common to Computer Science & Engineering, Information Technology, Electronics & Control Engineering,
Table of Contents 1 SNMP Configuration Commands RMON Configuration Commands 2-1
 Table of Contents 1 SNMP Configuration Commands 1-1 SNMP Configuration Commands 1-1 display snmp-agent 1-1 display snmp-agent community 1-1 display snmp-agent group 1-3 display snmp-agent mib-view 1-4
Table of Contents 1 SNMP Configuration Commands 1-1 SNMP Configuration Commands 1-1 display snmp-agent 1-1 display snmp-agent community 1-1 display snmp-agent group 1-3 display snmp-agent mib-view 1-4
Data & Computer Communication
 Basic Networking Concepts A network is a system of computers and other devices (such as printers and modems) that are connected in such a way that they can exchange data. A bridge is a device that connects
Basic Networking Concepts A network is a system of computers and other devices (such as printers and modems) that are connected in such a way that they can exchange data. A bridge is a device that connects
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca
 CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Janno< Administrivia Homework I out later today, due next ursday, Sep 27th Today: Link Layer
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Janno< Administrivia Homework I out later today, due next ursday, Sep 27th Today: Link Layer
Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin,
 Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin, ydlin@cs.nctu.edu.tw Chapter 1: Introduction 1. How does Internet scale to billions of hosts? (Describe what structure
Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin, ydlin@cs.nctu.edu.tw Chapter 1: Introduction 1. How does Internet scale to billions of hosts? (Describe what structure
SNMP. Simple Network Management Protocol
 SNMP Simple Network Management Protocol Network Management The network management is to Monitor the network Ensure the operations over the network are functional Assure the network works efficiently An
SNMP Simple Network Management Protocol Network Management The network management is to Monitor the network Ensure the operations over the network are functional Assure the network works efficiently An
airhaul Nexus sb3010
 u n w i r i n g o u r w o r l d TM airhaul Nexus sb3010 User Configuration Guide Version 1.3 Copyright smartbridges Pte Ltd. All Rights Reserved. About This Document This Software Configuration Guide is
u n w i r i n g o u r w o r l d TM airhaul Nexus sb3010 User Configuration Guide Version 1.3 Copyright smartbridges Pte Ltd. All Rights Reserved. About This Document This Software Configuration Guide is
CompSci 356: Computer Network Architectures. Lecture 7: Switching technologies Chapter 3.1. Xiaowei Yang
 CompSci 356: Computer Network Architectures Lecture 7: Switching technologies Chapter 3.1 Xiaowei Yang xwy@cs.duke.edu Types of switching Datagram Virtual circuit Source routing Today Bridges and LAN switches
CompSci 356: Computer Network Architectures Lecture 7: Switching technologies Chapter 3.1 Xiaowei Yang xwy@cs.duke.edu Types of switching Datagram Virtual circuit Source routing Today Bridges and LAN switches
Medium Access Control. CSCI370 Lecture 5 Michael Hutt New York Institute of Technology
 Medium Access Control CSCI370 Lecture 5 Michael Hutt New York Institute of Technology The Data Link Layer Logical Link Control (LLC) IEEE 802.2 Standard RFC 1042 Provides three service options Unreliable
Medium Access Control CSCI370 Lecture 5 Michael Hutt New York Institute of Technology The Data Link Layer Logical Link Control (LLC) IEEE 802.2 Standard RFC 1042 Provides three service options Unreliable
ECE 158A: Lecture 13. Fall 2015
 ECE 158A: Lecture 13 Fall 2015 Random Access and Ethernet! Random Access! Basic idea: Exploit statistical multiplexing Do not avoid collisions, just recover from them When a node has packet to send Transmit
ECE 158A: Lecture 13 Fall 2015 Random Access and Ethernet! Random Access! Basic idea: Exploit statistical multiplexing Do not avoid collisions, just recover from them When a node has packet to send Transmit
CS610- Computer Network Solved Subjective From Midterm Papers
 Solved Subjective From Midterm Papers May 08,2012 MC100401285 Moaaz.pk@gmail.com Mc100401285@gmail.com PSMD01 CS610- Computer Network Midterm Examination - Fall 2011 1. Where are destination and source
Solved Subjective From Midterm Papers May 08,2012 MC100401285 Moaaz.pk@gmail.com Mc100401285@gmail.com PSMD01 CS610- Computer Network Midterm Examination - Fall 2011 1. Where are destination and source
Goal and Outline. Computer Networking. What Do We Need? Today s Story Lecture 3: Packet Switched Networks Peter Steenkiste
 Goal and Outline 15-441 15-641 Computer Networking Lecture 3: Packet Switched Networks Peter Steenkiste Fall 2016 www.cs.cmu.edu/~prs/15 441 F16 Goal: gain a basic understanding of how you can build a
Goal and Outline 15-441 15-641 Computer Networking Lecture 3: Packet Switched Networks Peter Steenkiste Fall 2016 www.cs.cmu.edu/~prs/15 441 F16 Goal: gain a basic understanding of how you can build a
Computer Network : Lecture Notes Nepal Engineering College Compiled by: Junior Professor: Daya Ram Budhathoki Nepal Engineering college, Changunarayan
 Computer Network : Lecture Notes Nepal Engineering College Compiled by: Junior Professor: Daya Ram Budhathoki Nepal Engineering college, Changunarayan Chapter3: OSI Reference Model: Network Software: Network
Computer Network : Lecture Notes Nepal Engineering College Compiled by: Junior Professor: Daya Ram Budhathoki Nepal Engineering college, Changunarayan Chapter3: OSI Reference Model: Network Software: Network
Lecture 6 The Data Link Layer. Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it
 Lecture 6 The Data Link Layer Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it Link Layer: setting the context two physically connected devices: host-router, router-router, host-host,
Lecture 6 The Data Link Layer Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it Link Layer: setting the context two physically connected devices: host-router, router-router, host-host,
Lecture 5 The Data Link Layer. Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it
 Lecture 5 The Data Link Layer Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it Link Layer: setting the context two physically connected devices: host-router, router-router, host-host,
Lecture 5 The Data Link Layer Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it Link Layer: setting the context two physically connected devices: host-router, router-router, host-host,
ECE4110 Internetwork Programming. Introduction and Overview
 ECE4110 Internetwork Programming Introduction and Overview 1 EXAMPLE GENERAL NETWORK ALGORITHM Listen to wire Are signals detected Detect a preamble Yes Read Destination Address No data carrying or noise?
ECE4110 Internetwork Programming Introduction and Overview 1 EXAMPLE GENERAL NETWORK ALGORITHM Listen to wire Are signals detected Detect a preamble Yes Read Destination Address No data carrying or noise?
