Group-Based Management of Distributed File Caches
|
|
|
- Christiana Knight
- 5 years ago
- Views:
Transcription
1 Group-Based Management of Distributed File Caches Darrell D. E. Long Ahmed Amer Storage Systems Research Center Jack Baskin School of Engineering University of California, Santa Cruz Randal Burns Hopkins Storage Systems Laboratory Department of Computer Science Johns Hopkins University
2 Outline Motivation The Aggregating Cache Successor prediction and tracking Client Cache performance Filtering Effects Server-Side Caching Successor Entropy Visualizing Filtering Effect on Predictability Related Work Conclusions & Future Work
3 Motivation Improved client & server caching by grouping Reduced miss rates means fewer demand fetches Resilience to client-cache filtering effects Avoids pre-fetching drawbacks Incorrect prediction penalties can be limited based on storage system specifications All relationship and prediction maintenance is not time critical
4 The Aggregating Cache The aggregating cache is based on the retrieval of pre-built file groups Server-maintained groups are... based on file relationship modeling pre-constructed at the server This avoids timeliness issues of pre-fetching based on an associated set of likely successors for each file
5 The Aggregating Cache (cont d) Groups affect in-cache priority Upon receipt of a request for a file, associated group members are retrieved Files already in the cache need not be retrieved again Fewer fetches from the server occur Results in decreased latency Group sizes evaluated From 2 to 10 related files (report on groups of 5)
6 Aggregating Cache Data Client Single Request and Retrieval Relationship Metadata Server File Store Local File System Interface Cache Manager Single Request and Retrieval Limited Local Storage Single Request Group Retrieval Storage Server
7 Aggregating Cache (con td) Do the clients cooperate? Clients gather statistics and forward to the server, or Allow the server to simply observe More on this later
8 Successor Prediction File grouping relies on predictive per-file metadata Per-file metadata consists of successor predictions Successor predictors are simple, accurate and adjustable Noah Recent popularity
9 File Successor Prediction Given: Observations of the file access stream Knowledge of the current file access Limited per-object state maintainable as file metadata Successive file access events are predictable using very simple schemes File Successor (i+1) File (i) File Predictor (i+1)?
10 Static vs. Dynamic Prediction Static - First Successor The file that followed A the first time A was accessed is always predicted to follow A Dynamic - Last Successor The file that followed A the last time A was accessed is predicted to follow A
11 Static vs. Dynamic First and Last Successor Accuracy (%) workstation server First Last
12 Prediction with Noah Last-successor predicts better than firstsuccessor But transient successors cause double-faults for last successor! Noah Maintains a current prediction Changes current prediction to last successor if last successor was the same for S consecutive accesses S (stability) is a parameter, default = 2 File (i+1) File (i) File (i+1)? NOAH
13 Noah, Static and Dynamic Noah vs First and Last Successor Accuracy (%) workstation server First Last Noah
14 General and Specific Accuracy There is a difference between predictor accuracy over a workload accuracy per prediction General Accuracy Percentage of all events that are not predicted or not predicted correctly Specific Accuracy Percentage of all predictions offered that are not correct
15 Noah: Varying Stability Parameter Noah's Predictive Accuracy Percentage of File Accesses 100% 90% 80% 70% 60% 50% 40% 30% 20% 10% 0% Stability Not Predicted Predicted Wrong Predicted Correct
16 Recent Popularity (Best j of k ) File Access Sequence: S: A B C D B C D B D B D B C B C B C A B A B A B A B A: B: C: D: Per-File Successors B,B,B,B,B C,C,D,D,C,C,C,A,A,A D,D,B,B,A B,B,B,B Successor Counts B:5 A:3, C:5, D:2 A:1, B:2, D:2 B:4 Best (3 of 6) (B S) = A Best (4 of 6) (B S) = N/A Best (4 of 9) (B S) = C
17 Recent Popularity (Best j of k ) Varying J Parameter (K=10) Recent Popularity (K=10) Predictive Accuracy Percentage of File Accesses 100% 90% 80% 70% 60% 50% 40% 30% 20% 10% 0% J value Not Predicted Predicted Wrong Predicted Correct
18 Recent Popularity (Best j of k ) Varying J Parameter (K=20) Recent Popularity (K=20) Predictive Accuracy Percentage of File Accesses 100% 90% 80% 70% 60% 50% 40% 30% 20% 10% 0% J value Not Predicted Predicted Wrong Predicted Correct
19 Successor Prediction Static prediction schemes remain valid for extended periods and for very popular files Variation amongst file successors is very limited Noah and Recent Popularity are effective and adjustable successor predictors
20 File Grouping Given: Accurate file successor predictions Per-file successor metadata Knowledge of the current file access A group of n files can be constructed of those most likely to be accessed in the near future
21 File Relationship Graph File successor observations give us probability of a given file following another Fixed set of successors, P(Y X) [0,1,,S] Can construct a file relationship graph Nodes: Files Edges: succession probability A P(B A) P(C A) P(C B) C P(E C) P(H C) E H B P(D B) P(F B) D F
22 Constructing File Groups Given an access to file A, what n files constitute A s group G A n Best Successor algorithm G A {A} G A E A C 1 1 B 2 F 2 D G A G A {X}, for X with maximal P(X A) H Repeat until G A =n Example of n = 3
23 Constructing File Groups Given an access to file A, what n files constitute A s group G A n Best Successor algorithm G A {A} G A E A C 1 1 B 2 F 2 D G A G A {X}, for X with maximal P(X A) H Repeat until G A =n Example of n = 3
24 Constructing File Groups Given an access to file A, what n files constitute A s group G A n Best Successor algorithm G A {A} G A E A C 1 1 B 2 F 2 D G A G A {X}, for X with maximal P(X A) H Repeat until G A =n Example of n = 3
25 Constructing File Groups Given an access to file A, what n files constitute A s group G A n Best Successor algorithm G A {A} G A E A C 1 1 B 2 F 2 D G B G A G A {X}, for X with maximal P(X A) H G C Repeat until G A =n Example of n = 3
26 Server-Maintained Metadata: A Restricted Relationship Graph A simple graph of restricted degree, m Maximum number of vertices is equivalent to the number of unique files observed in the access stream, N Group size n N n m +1 Data Objects Related Data Objects m
27 Server-Maintained Metadata For each file A, we maintain a list of m successors S i and P(S i A) The feasibility of this strategy is dependent on limited variation in file successors For our workloads: Over periods of ~1 month, files average less than 10 unique successors Over periods of ~1 year, files average less than 20 unique successors
28 Successor variability Cummulative (%) of Files 100% 90% 80% 70% 60% 50% 40% 30% 20% 10% 0% Number of Unique Successors
29 Successor Window Hit Rates Accuracy 100% 90% 80% 70% 60% 50% 40% 30% 20% 10% 0% Successor Window Size optimal stability LRU LFU static
30 Relationship Graph: Example Simple Groupings Groups of size n n-1 most likely successors are grouped with each file G1 E A C 1 H 1 G3 B F 2 3 D G2 Example of n = 3
31 Aggregating Cache Miss Rates users workload Miss Rate (%) Cache Capacity (files) LRU G=2 G=5
32 Aggregating Cache Miss Rates server workload Miss Rate (%) Cache Capacity (files) LRU G=2 G=5
33 Client Cache Filtering Effects Filtered workload Result due to misses from an intervening (client) cache When client and server caches comparable sizes caching can be rendered ineffective for server-side caches Adding a cache is not necessarily a good thing! Server-side caching Filtered workloads observed when clients provide no access information beyond cache misses But filtered workloads turn out to be highly predictable!
34 Single-Stage Client Caching (original workload observed at the client) Data Client (Request Source) Original Requests Cache Final Requests Data Server (Request Sink)
35 Server-Side Caching (filtered workload observed at the server) Data Client (Request Source) Data Server (Request Sink) Original Requests Final Requests Client Cache (FILTER) Filtered Requests Server Cache (CACHE)
36 Aggregating Cache (used for server-side caching) Data Client (Request Source) Data Server (Request Sink) Single Retrieval Original Requests Group Retrieval Final Requests Client Cache (FILTER) Single Retrieval Filtered Requests Server Cache (CACHE)
37 Aggregating Cache Miss Rates (with client cache filtering) users workload (Filter Capacity = 100) Miss Rate (%) Cache Capacity (files) G=5 LRU LFU
38 Aggregating Cache Miss Rates (with client cache filtering) users workload (Cache Capacity = 300) Miss Rate (%) Filter Capacity (files) G=5 LRU LFU
39 Aggregating Cache Miss Rates (with client cache filtering) Berkley Instructional Workload (Cache Capacity = 300) Miss Rate (%) Filter Capacity (files) G=5 LRU LFU
40 Visualizing Caching Effects Why do aggregating caches still work? Intervening caches do not reduce access predictability How can we demonstrate this? Using a new visualization tool (developed in collaboration with the UCSC Viz group) we produce Cache-Frequency Plots These are based on successor entropy, a single context-based predictability measure
41 Successor Entropy Traditional Self-Information (Entropy) Higher values imply greater unpredictability Predictability of an independent sequence No context information Successor Entropy Entropy of individual successor sequences calculated for each file accessed Presented as a Predictability Histogram
42 Successor Entropy Traditional Self-Information (Entropy) weighted sum of independent loglikelihoods H Conditional entropy = P ( ) log( P( )) given knowledge that condition c is true c i si si H ( ) = P( c) log( P( c)) i s i s i
43 Successor Entropy Given observed accesses to m successors s i of file a, we define the successor entropy of file a as: H( a) = m i= 1 P( s i a) log( P( s i a))
44 Cache-Frequency Plots Predictability Histogram Cache Frequency Plot Z - Entropy X - Files Z - Entropy Y - Cache size X - Files X-axis Files, ordered by decreasing Z-value Y-axis Filtering cache sizes Z-axis Successor entropy Surface-Point Color File access frequency
45 Cache-Frequency Plots (cont d) Predictability histogram Demonstrates variation in file access predictability The Cache-Frequency Plots Effects of intervening cache sizes on predictability histograms Correlation between file popularity (access frequency) and successor predictability
46
47
48 Predictability Results File successor predictability varies as dramatically as file popularity High skew among file successor entropy Most have highly predictable successors Predictability independent of popularity Some of the most popular files have the most predictable successor behavior
49 Caching Effects Increasing the capacity of intervening caches reduces the skew of access frequencies, by reducing the number of very highfrequency and unpredictable files actually increases predictability, and reduces the variation among files
50
51
52 Related Work File Access Prediction Krishnan, Griffioen, Duchamp, and Kroeger Mobile File Hoarding Coda, and SEER Web Caching Bestavros, Duchamp, and Wolman
53 Conclusions Aggregating cache Most files see few unique successors Simple grouping can significantly reduce demand cache misses while providing implicit pre-fetching Can maintain reasonable hit rates in the presence of cache filtering effects
54 Conclusions (cont d) No pre-fetch timing issues Explicit pre-fetching may hurt performance, and demands timeliness Relationship tracking is an optional activity that can be safely delayed/ignored If you have a client cache and a server cache, you want to do this!
55 Ongoing and Future Work Examine alternate predictors Program-based predictors (Yeh et al.) Partial file transfer, block-level grouping Storage allocation & placement problems Mobile applications Multi-level caches
56 Further Information & Questions?
Identifying Stable File Access Patterns
 Identifying Stable File Access Patterns Purvi Shah Jehan-François Pâris 1 Ahmed Amer 2 Darrell D. E. Long 3 University of Houston University of Houston University of Pittsburgh U. C. Santa Cruz purvi@cs.uh.edu
Identifying Stable File Access Patterns Purvi Shah Jehan-François Pâris 1 Ahmed Amer 2 Darrell D. E. Long 3 University of Houston University of Houston University of Pittsburgh U. C. Santa Cruz purvi@cs.uh.edu
Aggregating Caches: A Mechanism for Implicit File Prefetching
 Aggregating Caches: A Mechanism for Implicit File Prefetching Ahmed Amer and Darrell D. E. Long Jack Baskin School of Engineering University of California, Santa Cruz 1156 High St., Santa Cruz 9564 a.amer@acm.org,
Aggregating Caches: A Mechanism for Implicit File Prefetching Ahmed Amer and Darrell D. E. Long Jack Baskin School of Engineering University of California, Santa Cruz 1156 High St., Santa Cruz 9564 a.amer@acm.org,
Group-Based Management of Distributed File Caches
 Group-Based Management of Distributed File Caches Ahmed Amer Darrell D. E. Long Randal C. Burns Department of Computer Science Department of Computer Science University of California, Santa Cruz Johns
Group-Based Management of Distributed File Caches Ahmed Amer Darrell D. E. Long Randal C. Burns Department of Computer Science Department of Computer Science University of California, Santa Cruz Johns
Using Multiple Predictors to Improve the Accuracy of File Access Predictions
 Using Multiple Predictors to Improve the Accuracy of File Access Predictions Gary A. S. Whittle Jehan-François Pâris 1 Ahmed Amer 2 Darrell D. E. Long 2 Randal Burns U. of Houston U. of Houston U. of Pittsburgh
Using Multiple Predictors to Improve the Accuracy of File Access Predictions Gary A. S. Whittle Jehan-François Pâris 1 Ahmed Amer 2 Darrell D. E. Long 2 Randal Burns U. of Houston U. of Houston U. of Pittsburgh
Using Multiple Predictors to Improve the Accuracy of File Access Predictions
 Using Multiple Predictors to Improve the Accuracy of File Access Predictions Gary A. S. Whittle Jehan-François Pâris 1 Ahmed Amer 2 Darrell D. E. Long 2 Randal Burns U. of Houston U. of Houston U. of Pittsburgh
Using Multiple Predictors to Improve the Accuracy of File Access Predictions Gary A. S. Whittle Jehan-François Pâris 1 Ahmed Amer 2 Darrell D. E. Long 2 Randal Burns U. of Houston U. of Houston U. of Pittsburgh
Dynamic Relationships and the Persistence of Pairings
 Dynamic Relationships and the Persistence of Pairings Ahmed Amer and Darrell D. E. Long' Jack Baskin School of Engineering University of California, Santa Cruz I156 High Street Santa Cruz, CA 95064 amer4,darrell@
Dynamic Relationships and the Persistence of Pairings Ahmed Amer and Darrell D. E. Long' Jack Baskin School of Engineering University of California, Santa Cruz I156 High Street Santa Cruz, CA 95064 amer4,darrell@
A Two-Expert Approach to File Access Prediction
 A Two-Expert Approach to File Access Prediction Wenjing Chen Christoph F. Eick Jehan-François Pâris 1 Department of Computer Science University of Houston Houston, TX 77204-3010 tigerchenwj@yahoo.com,
A Two-Expert Approach to File Access Prediction Wenjing Chen Christoph F. Eick Jehan-François Pâris 1 Department of Computer Science University of Houston Houston, TX 77204-3010 tigerchenwj@yahoo.com,
The Case for Efficient File Access Pattern Modeling
 The Case for Efficient File Access Pattern Modeling Thomas M. Kroeger and Darrell D. E. Long yz Jack Baskin School of Engineering University of California, Santa Cruz Abstract Most modern I/O systems treat
The Case for Efficient File Access Pattern Modeling Thomas M. Kroeger and Darrell D. E. Long yz Jack Baskin School of Engineering University of California, Santa Cruz Abstract Most modern I/O systems treat
Finding a needle in Haystack: Facebook's photo storage
 Finding a needle in Haystack: Facebook's photo storage The paper is written at facebook and describes a object storage system called Haystack. Since facebook processes a lot of photos (20 petabytes total,
Finding a needle in Haystack: Facebook's photo storage The paper is written at facebook and describes a object storage system called Haystack. Since facebook processes a lot of photos (20 petabytes total,
Review: Computer Organization
 Review: Computer Organization Cache Chansu Yu Caches: The Basic Idea A smaller set of storage locations storing a subset of information from a larger set. Typically, SRAM for DRAM main memory: Processor
Review: Computer Organization Cache Chansu Yu Caches: The Basic Idea A smaller set of storage locations storing a subset of information from a larger set. Typically, SRAM for DRAM main memory: Processor
Ceph: A Scalable, High-Performance Distributed File System PRESENTED BY, NITHIN NAGARAJ KASHYAP
 Ceph: A Scalable, High-Performance Distributed File System PRESENTED BY, NITHIN NAGARAJ KASHYAP Outline Introduction. System Overview. Distributed Object Storage. Problem Statements. What is Ceph? Unified
Ceph: A Scalable, High-Performance Distributed File System PRESENTED BY, NITHIN NAGARAJ KASHYAP Outline Introduction. System Overview. Distributed Object Storage. Problem Statements. What is Ceph? Unified
Locality of Reference
 Locality of Reference 1 In view of the previous discussion of secondary storage, it makes sense to design programs so that data is read from and written to disk in relatively large chunks but there is
Locality of Reference 1 In view of the previous discussion of secondary storage, it makes sense to design programs so that data is read from and written to disk in relatively large chunks but there is
Volley: Automated Data Placement for Geo-Distributed Cloud Services
 Volley: Automated Data Placement for Geo-Distributed Cloud Services Authors: Sharad Agarwal, John Dunagen, Navendu Jain, Stefan Saroiu, Alec Wolman, Harbinder Bogan 7th USENIX Symposium on Networked Systems
Volley: Automated Data Placement for Geo-Distributed Cloud Services Authors: Sharad Agarwal, John Dunagen, Navendu Jain, Stefan Saroiu, Alec Wolman, Harbinder Bogan 7th USENIX Symposium on Networked Systems
!! What is virtual memory and when is it useful? !! What is demand paging? !! When should pages in memory be replaced?
 Chapter 10: Virtual Memory Questions? CSCI [4 6] 730 Operating Systems Virtual Memory!! What is virtual memory and when is it useful?!! What is demand paging?!! When should pages in memory be replaced?!!
Chapter 10: Virtual Memory Questions? CSCI [4 6] 730 Operating Systems Virtual Memory!! What is virtual memory and when is it useful?!! What is demand paging?!! When should pages in memory be replaced?!!
Web Caching and Content Delivery
 Web Caching and Content Delivery Caching for a Better Web Performance is a major concern in the Web Proxy caching is the most widely used method to improve Web performance Duplicate requests to the same
Web Caching and Content Delivery Caching for a Better Web Performance is a major concern in the Web Proxy caching is the most widely used method to improve Web performance Duplicate requests to the same
Proceedings of the 2001 USENIX Annual Technical Conference
 USENIX Association Proceedings of the 21 USENIX Annual Technical Conference Boston, Massachusetts, USA June 25 3, 21 THE ADVANCED COMPUTING SYSTEMS ASSOCIATION 21 by The USENIX Association All Rights Reserved
USENIX Association Proceedings of the 21 USENIX Annual Technical Conference Boston, Massachusetts, USA June 25 3, 21 THE ADVANCED COMPUTING SYSTEMS ASSOCIATION 21 by The USENIX Association All Rights Reserved
On the Analysis of Caches with Pending Interest Tables
 On the Analysis of Caches with Pending Interest Tables Mostafa Dehghan 1, Bo Jiang 1 Ali Dabirmoghaddam 2, Don Towsley 1 1 University of Massachusetts Amherst 2 University of California Santa Cruz ICN,
On the Analysis of Caches with Pending Interest Tables Mostafa Dehghan 1, Bo Jiang 1 Ali Dabirmoghaddam 2, Don Towsley 1 1 University of Massachusetts Amherst 2 University of California Santa Cruz ICN,
CS 136: Advanced Architecture. Review of Caches
 1 / 30 CS 136: Advanced Architecture Review of Caches 2 / 30 Why Caches? Introduction Basic goal: Size of cheapest memory... At speed of most expensive Locality makes it work Temporal locality: If you
1 / 30 CS 136: Advanced Architecture Review of Caches 2 / 30 Why Caches? Introduction Basic goal: Size of cheapest memory... At speed of most expensive Locality makes it work Temporal locality: If you
SMD149 - Operating Systems - VM Management
 SMD149 - Operating Systems - VM Management Roland Parviainen November 17, 2005 1 / 35 Outline Overview Virtual memory management Fetch, placement and replacement strategies Placement strategies Paging,
SMD149 - Operating Systems - VM Management Roland Parviainen November 17, 2005 1 / 35 Outline Overview Virtual memory management Fetch, placement and replacement strategies Placement strategies Paging,
Copyright 2018, Oracle and/or its affiliates. All rights reserved.
 Beyond SQL Tuning: Insider's Guide to Maximizing SQL Performance Monday, Oct 22 10:30 a.m. - 11:15 a.m. Marriott Marquis (Golden Gate Level) - Golden Gate A Ashish Agrawal Group Product Manager Oracle
Beyond SQL Tuning: Insider's Guide to Maximizing SQL Performance Monday, Oct 22 10:30 a.m. - 11:15 a.m. Marriott Marquis (Golden Gate Level) - Golden Gate A Ashish Agrawal Group Product Manager Oracle
CMPSC 311- Introduction to Systems Programming Module: Caching
 CMPSC 311- Introduction to Systems Programming Module: Caching Professor Patrick McDaniel Fall 2016 Reminder: Memory Hierarchy L0: Registers CPU registers hold words retrieved from L1 cache Smaller, faster,
CMPSC 311- Introduction to Systems Programming Module: Caching Professor Patrick McDaniel Fall 2016 Reminder: Memory Hierarchy L0: Registers CPU registers hold words retrieved from L1 cache Smaller, faster,
Modeling and Caching of P2P Traffic
 School of Computing Science Simon Fraser University, Canada Modeling and Caching of P2P Traffic Mohamed Hefeeda Osama Saleh ICNP 06 15 November 2006 1 Motivations P2P traffic is a major fraction of Internet
School of Computing Science Simon Fraser University, Canada Modeling and Caching of P2P Traffic Mohamed Hefeeda Osama Saleh ICNP 06 15 November 2006 1 Motivations P2P traffic is a major fraction of Internet
1993. (BP-2) (BP-5, BP-10) (BP-6, BP-10) (BP-7, BP-10) YAGS (BP-10) EECC722
 Dynamic Branch Prediction Dynamic branch prediction schemes run-time behavior of branches to make predictions. Usually information about outcomes of previous occurrences of branches are used to predict
Dynamic Branch Prediction Dynamic branch prediction schemes run-time behavior of branches to make predictions. Usually information about outcomes of previous occurrences of branches are used to predict
Dual-Core Execution: Building A Highly Scalable Single-Thread Instruction Window
 Dual-Core Execution: Building A Highly Scalable Single-Thread Instruction Window Huiyang Zhou School of Computer Science University of Central Florida New Challenges in Billion-Transistor Processor Era
Dual-Core Execution: Building A Highly Scalable Single-Thread Instruction Window Huiyang Zhou School of Computer Science University of Central Florida New Challenges in Billion-Transistor Processor Era
Use-Based Register Caching with Decoupled Indexing
 Use-Based Register Caching with Decoupled Indexing J. Adam Butts and Guri Sohi University of Wisconsin Madison {butts,sohi}@cs.wisc.edu ISCA-31 München, Germany June 23, 2004 Motivation Need large register
Use-Based Register Caching with Decoupled Indexing J. Adam Butts and Guri Sohi University of Wisconsin Madison {butts,sohi}@cs.wisc.edu ISCA-31 München, Germany June 23, 2004 Motivation Need large register
CACHE MEMORIES ADVANCED COMPUTER ARCHITECTURES. Slides by: Pedro Tomás
 CACHE MEMORIES Slides by: Pedro Tomás Additional reading: Computer Architecture: A Quantitative Approach, 5th edition, Chapter 2 and Appendix B, John L. Hennessy and David A. Patterson, Morgan Kaufmann,
CACHE MEMORIES Slides by: Pedro Tomás Additional reading: Computer Architecture: A Quantitative Approach, 5th edition, Chapter 2 and Appendix B, John L. Hennessy and David A. Patterson, Morgan Kaufmann,
Memory Hierarchy Computing Systems & Performance MSc Informatics Eng. Memory Hierarchy (most slides are borrowed)
 Computing Systems & Performance Memory Hierarchy MSc Informatics Eng. 2011/12 A.J.Proença Memory Hierarchy (most slides are borrowed) AJProença, Computer Systems & Performance, MEI, UMinho, 2011/12 1 2
Computing Systems & Performance Memory Hierarchy MSc Informatics Eng. 2011/12 A.J.Proença Memory Hierarchy (most slides are borrowed) AJProença, Computer Systems & Performance, MEI, UMinho, 2011/12 1 2
Portland State University ECE 587/687. The Microarchitecture of Superscalar Processors
 Portland State University ECE 587/687 The Microarchitecture of Superscalar Processors Copyright by Alaa Alameldeen and Haitham Akkary 2011 Program Representation An application is written as a program,
Portland State University ECE 587/687 The Microarchitecture of Superscalar Processors Copyright by Alaa Alameldeen and Haitham Akkary 2011 Program Representation An application is written as a program,
Memory Hierarchy Computing Systems & Performance MSc Informatics Eng. Memory Hierarchy (most slides are borrowed)
 Computing Systems & Performance Memory Hierarchy MSc Informatics Eng. 2012/13 A.J.Proença Memory Hierarchy (most slides are borrowed) AJProença, Computer Systems & Performance, MEI, UMinho, 2012/13 1 2
Computing Systems & Performance Memory Hierarchy MSc Informatics Eng. 2012/13 A.J.Proença Memory Hierarchy (most slides are borrowed) AJProença, Computer Systems & Performance, MEI, UMinho, 2012/13 1 2
1. Creates the illusion of an address space much larger than the physical memory
 Virtual memory Main Memory Disk I P D L1 L2 M Goals Physical address space Virtual address space 1. Creates the illusion of an address space much larger than the physical memory 2. Make provisions for
Virtual memory Main Memory Disk I P D L1 L2 M Goals Physical address space Virtual address space 1. Creates the illusion of an address space much larger than the physical memory 2. Make provisions for
Lecture 2: Memory Systems
 Lecture 2: Memory Systems Basic components Memory hierarchy Cache memory Virtual Memory Zebo Peng, IDA, LiTH Many Different Technologies Zebo Peng, IDA, LiTH 2 Internal and External Memories CPU Date transfer
Lecture 2: Memory Systems Basic components Memory hierarchy Cache memory Virtual Memory Zebo Peng, IDA, LiTH Many Different Technologies Zebo Peng, IDA, LiTH 2 Internal and External Memories CPU Date transfer
Mismatch of CPU and MM Speeds
 Fö 3 Cache-Minne Introduction Cache design Replacement and write policy Zebo Peng, IDA, LiTH Mismatch of CPU and MM Speeds Cycle Time (nano second) 0 4 0 3 0 0 Main Memory CPU Speed Gap (ca. one order
Fö 3 Cache-Minne Introduction Cache design Replacement and write policy Zebo Peng, IDA, LiTH Mismatch of CPU and MM Speeds Cycle Time (nano second) 0 4 0 3 0 0 Main Memory CPU Speed Gap (ca. one order
Lecture 14: Cache & Virtual Memory
 CS 422/522 Design & Implementation of Operating Systems Lecture 14: Cache & Virtual Memory Zhong Shao Dept. of Computer Science Yale University Acknowledgement: some slides are taken from previous versions
CS 422/522 Design & Implementation of Operating Systems Lecture 14: Cache & Virtual Memory Zhong Shao Dept. of Computer Science Yale University Acknowledgement: some slides are taken from previous versions
Building JACK: Developing Metrics for Use in Multi-Objective Optimal Data Allocation Strategies
 Building JACK: Developing Metrics for Use in Multi-Objective Optimal Data Allocation Strategies Technical Report UCSC-SSRC-14-01 January 2014 Christina R. Strong Ahmed Amer Darrell D.E. Long crstrong@cs.ucsc.edu
Building JACK: Developing Metrics for Use in Multi-Objective Optimal Data Allocation Strategies Technical Report UCSC-SSRC-14-01 January 2014 Christina R. Strong Ahmed Amer Darrell D.E. Long crstrong@cs.ucsc.edu
CS252 Graduate Computer Architecture Midterm 1 Solutions
 CS252 Graduate Computer Architecture Midterm 1 Solutions Part A: Branch Prediction (22 Points) Consider a fetch pipeline based on the UltraSparc-III processor (as seen in Lecture 5). In this part, we evaluate
CS252 Graduate Computer Architecture Midterm 1 Solutions Part A: Branch Prediction (22 Points) Consider a fetch pipeline based on the UltraSparc-III processor (as seen in Lecture 5). In this part, we evaluate
EECS 470. Lecture 15. Prefetching. Fall 2018 Jon Beaumont. History Table. Correlating Prediction Table
 Lecture 15 History Table Correlating Prediction Table Prefetching Latest A0 A0,A1 A3 11 Fall 2018 Jon Beaumont A1 http://www.eecs.umich.edu/courses/eecs470 Prefetch A3 Slides developed in part by Profs.
Lecture 15 History Table Correlating Prediction Table Prefetching Latest A0 A0,A1 A3 11 Fall 2018 Jon Beaumont A1 http://www.eecs.umich.edu/courses/eecs470 Prefetch A3 Slides developed in part by Profs.
Accommodating Bursts in Distributed Stream Processing Systems
 Accommodating Bursts in Distributed Stream Processing Systems Distributed Real-time Systems Lab University of California, Riverside {drougas,vana}@cs.ucr.edu http://www.cs.ucr.edu/~{drougas,vana} Stream
Accommodating Bursts in Distributed Stream Processing Systems Distributed Real-time Systems Lab University of California, Riverside {drougas,vana}@cs.ucr.edu http://www.cs.ucr.edu/~{drougas,vana} Stream
Chapter 7 The Potential of Special-Purpose Hardware
 Chapter 7 The Potential of Special-Purpose Hardware The preceding chapters have described various implementation methods and performance data for TIGRE. This chapter uses those data points to propose architecture
Chapter 7 The Potential of Special-Purpose Hardware The preceding chapters have described various implementation methods and performance data for TIGRE. This chapter uses those data points to propose architecture
Agenda. EE 260: Introduction to Digital Design Memory. Naive Register File. Agenda. Memory Arrays: SRAM. Memory Arrays: Register File
 EE 260: Introduction to Digital Design Technology Yao Zheng Department of Electrical Engineering University of Hawaiʻi at Mānoa 2 Technology Naive Register File Write Read clk Decoder Read Write 3 4 Arrays:
EE 260: Introduction to Digital Design Technology Yao Zheng Department of Electrical Engineering University of Hawaiʻi at Mānoa 2 Technology Naive Register File Write Read clk Decoder Read Write 3 4 Arrays:
Memory Hierarchy. Jinkyu Jeong Computer Systems Laboratory Sungkyunkwan University
 Memory Hierarchy Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu EEE3050: Theory on Computer Architectures, Spring 2017, Jinkyu Jeong (jinkyu@skku.edu)
Memory Hierarchy Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu EEE3050: Theory on Computer Architectures, Spring 2017, Jinkyu Jeong (jinkyu@skku.edu)
Tutorial 11. Final Exam Review
 Tutorial 11 Final Exam Review Introduction Instruction Set Architecture: contract between programmer and designers (e.g.: IA-32, IA-64, X86-64) Computer organization: describe the functional units, cache
Tutorial 11 Final Exam Review Introduction Instruction Set Architecture: contract between programmer and designers (e.g.: IA-32, IA-64, X86-64) Computer organization: describe the functional units, cache
Branch Prediction & Speculative Execution. Branch Penalties in Modern Pipelines
 6.823, L15--1 Branch Prediction & Speculative Execution Asanovic Laboratory for Computer Science M.I.T. http://www.csg.lcs.mit.edu/6.823 6.823, L15--2 Branch Penalties in Modern Pipelines UltraSPARC-III
6.823, L15--1 Branch Prediction & Speculative Execution Asanovic Laboratory for Computer Science M.I.T. http://www.csg.lcs.mit.edu/6.823 6.823, L15--2 Branch Penalties in Modern Pipelines UltraSPARC-III
Demand fetching is commonly employed to bring the data
 Proceedings of 2nd Annual Conference on Theoretical and Applied Computer Science, November 2010, Stillwater, OK 14 Markov Prediction Scheme for Cache Prefetching Pranav Pathak, Mehedi Sarwar, Sohum Sohoni
Proceedings of 2nd Annual Conference on Theoretical and Applied Computer Science, November 2010, Stillwater, OK 14 Markov Prediction Scheme for Cache Prefetching Pranav Pathak, Mehedi Sarwar, Sohum Sohoni
Caches in Real-Time Systems. Instruction Cache vs. Data Cache
 Caches in Real-Time Systems [Xavier Vera, Bjorn Lisper, Jingling Xue, Data Caches in Multitasking Hard Real- Time Systems, RTSS 2003.] Schedulability Analysis WCET Simple Platforms WCMP (memory performance)
Caches in Real-Time Systems [Xavier Vera, Bjorn Lisper, Jingling Xue, Data Caches in Multitasking Hard Real- Time Systems, RTSS 2003.] Schedulability Analysis WCET Simple Platforms WCMP (memory performance)
Chapter 3 (CONT) Instructor: Josep Torrellas CS433. Copyright J. Torrellas 1999,2001,2002,2007,2013 1
 Chapter 3 (CONT) Instructor: Josep Torrellas CS433 Copyright J. Torrellas 1999,2001,2002,2007,2013 1 Dynamic Hardware Branch Prediction Control hazards are sources of losses, especially for processors
Chapter 3 (CONT) Instructor: Josep Torrellas CS433 Copyright J. Torrellas 1999,2001,2002,2007,2013 1 Dynamic Hardware Branch Prediction Control hazards are sources of losses, especially for processors
Elastic Queue: A Universal SSD Lifetime Extension Plug-in for Cache Replacement Algorithms
 Elastic Queue: A Universal SSD Lifetime Extension Plug-in for Cache Replacement Algorithms Yushi Liang, Yunpeng Chai, Ning Bao, Huanyu Chen, Yaohong Liu Key Laboratory of Data Engineering and Knowledge
Elastic Queue: A Universal SSD Lifetime Extension Plug-in for Cache Replacement Algorithms Yushi Liang, Yunpeng Chai, Ning Bao, Huanyu Chen, Yaohong Liu Key Laboratory of Data Engineering and Knowledge
high-speed-high-capacity memory
 Sanjay Rajopadhye Colorado State University n Transparently provide the illusion of a high-speed-high-capacity memory n Built out of caches: small memory devices that exploit the principle of locality
Sanjay Rajopadhye Colorado State University n Transparently provide the illusion of a high-speed-high-capacity memory n Built out of caches: small memory devices that exploit the principle of locality
Optimal Algorithm. Replace page that will not be used for longest period of time Used for measuring how well your algorithm performs
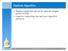 Optimal Algorithm Replace page that will not be used for longest period of time Used for measuring how well your algorithm performs page 1 Least Recently Used (LRU) Algorithm Reference string: 1, 2, 3,
Optimal Algorithm Replace page that will not be used for longest period of time Used for measuring how well your algorithm performs page 1 Least Recently Used (LRU) Algorithm Reference string: 1, 2, 3,
OASIS: Self-tuning Storage for Applications
 OASIS: Self-tuning Storage for Applications Kostas Magoutis, Prasenjit Sarkar, Gauri Shah 14 th NASA Goddard- 23 rd IEEE Mass Storage Systems Technologies, College Park, MD, May 17, 2006 Outline Motivation
OASIS: Self-tuning Storage for Applications Kostas Magoutis, Prasenjit Sarkar, Gauri Shah 14 th NASA Goddard- 23 rd IEEE Mass Storage Systems Technologies, College Park, MD, May 17, 2006 Outline Motivation
CS356: Discussion #9 Memory Hierarchy and Caches. Marco Paolieri Illustrations from CS:APP3e textbook
 CS356: Discussion #9 Memory Hierarchy and Caches Marco Paolieri (paolieri@usc.edu) Illustrations from CS:APP3e textbook The Memory Hierarchy So far... We modeled the memory system as an abstract array
CS356: Discussion #9 Memory Hierarchy and Caches Marco Paolieri (paolieri@usc.edu) Illustrations from CS:APP3e textbook The Memory Hierarchy So far... We modeled the memory system as an abstract array
CMPSC 311- Introduction to Systems Programming Module: Caching
 CMPSC 311- Introduction to Systems Programming Module: Caching Professor Patrick McDaniel Fall 2014 Lecture notes Get caching information form other lecture http://hssl.cs.jhu.edu/~randal/419/lectures/l8.5.caching.pdf
CMPSC 311- Introduction to Systems Programming Module: Caching Professor Patrick McDaniel Fall 2014 Lecture notes Get caching information form other lecture http://hssl.cs.jhu.edu/~randal/419/lectures/l8.5.caching.pdf
Advanced Computer Architecture
 ECE 563 Advanced Computer Architecture Fall 2009 Lecture 3: Memory Hierarchy Review: Caches 563 L03.1 Fall 2010 Since 1980, CPU has outpaced DRAM... Four-issue 2GHz superscalar accessing 100ns DRAM could
ECE 563 Advanced Computer Architecture Fall 2009 Lecture 3: Memory Hierarchy Review: Caches 563 L03.1 Fall 2010 Since 1980, CPU has outpaced DRAM... Four-issue 2GHz superscalar accessing 100ns DRAM could
LRC: Dependency-Aware Cache Management for Data Analytics Clusters. Yinghao Yu, Wei Wang, Jun Zhang, and Khaled B. Letaief IEEE INFOCOM 2017
 LRC: Dependency-Aware Cache Management for Data Analytics Clusters Yinghao Yu, Wei Wang, Jun Zhang, and Khaled B. Letaief IEEE INFOCOM 2017 Outline Cache Management for Data Analytics Clusters Inefficiency
LRC: Dependency-Aware Cache Management for Data Analytics Clusters Yinghao Yu, Wei Wang, Jun Zhang, and Khaled B. Letaief IEEE INFOCOM 2017 Outline Cache Management for Data Analytics Clusters Inefficiency
CS24: INTRODUCTION TO COMPUTING SYSTEMS. Spring 2017 Lecture 15
 CS24: INTRODUCTION TO COMPUTING SYSTEMS Spring 2017 Lecture 15 LAST TIME: CACHE ORGANIZATION Caches have several important parameters B = 2 b bytes to store the block in each cache line S = 2 s cache sets
CS24: INTRODUCTION TO COMPUTING SYSTEMS Spring 2017 Lecture 15 LAST TIME: CACHE ORGANIZATION Caches have several important parameters B = 2 b bytes to store the block in each cache line S = 2 s cache sets
CS370 Operating Systems
 CS370 Operating Systems Colorado State University Yashwant K Malaiya Fall 2016 Lecture 33 Virtual Memory Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 FAQ How does the virtual
CS370 Operating Systems Colorado State University Yashwant K Malaiya Fall 2016 Lecture 33 Virtual Memory Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 FAQ How does the virtual
Pipelined processors and Hazards
 Pipelined processors and Hazards Two options Processor HLL Compiler ALU LU Output Program Control unit 1. Either the control unit can be smart, i,e. it can delay instruction phases to avoid hazards. Processor
Pipelined processors and Hazards Two options Processor HLL Compiler ALU LU Output Program Control unit 1. Either the control unit can be smart, i,e. it can delay instruction phases to avoid hazards. Processor
Basic Page Replacement
 Basic Page Replacement 1. Find the location of the desired page on disk 2. Find a free frame: - If there is a free frame, use it - If there is no free frame, use a page replacement algorithm to select
Basic Page Replacement 1. Find the location of the desired page on disk 2. Find a free frame: - If there is a free frame, use it - If there is no free frame, use a page replacement algorithm to select
Caching and Demand-Paged Virtual Memory
 Caching and Demand-Paged Virtual Memory Definitions Cache Copy of data that is faster to access than the original Hit: if cache has copy Miss: if cache does not have copy Cache block Unit of cache storage
Caching and Demand-Paged Virtual Memory Definitions Cache Copy of data that is faster to access than the original Hit: if cache has copy Miss: if cache does not have copy Cache block Unit of cache storage
Chapter 8. Virtual Memory
 Operating System Chapter 8. Virtual Memory Lynn Choi School of Electrical Engineering Motivated by Memory Hierarchy Principles of Locality Speed vs. size vs. cost tradeoff Locality principle Spatial Locality:
Operating System Chapter 8. Virtual Memory Lynn Choi School of Electrical Engineering Motivated by Memory Hierarchy Principles of Locality Speed vs. size vs. cost tradeoff Locality principle Spatial Locality:
CACHE OPTIMIZATION. Mahdi Nazm Bojnordi. CS/ECE 6810: Computer Architecture. Assistant Professor School of Computing University of Utah
 CACHE OPTIMIZATION Mahdi Nazm Bojnordi Assistant Professor School of Computing University of Utah CS/ECE 6810: Computer Architecture Overview Announcement Homework 4 is due on Mar. 27 th This lecture Cache
CACHE OPTIMIZATION Mahdi Nazm Bojnordi Assistant Professor School of Computing University of Utah CS/ECE 6810: Computer Architecture Overview Announcement Homework 4 is due on Mar. 27 th This lecture Cache
Metrics for Security and Performance in Low-Latency Anonymity Systems
 Metrics for Security and Performance in Low-Latency Anonymity Systems Tor user Entry node Tor Network Middle node Exit node Bandwidth per node (kb/s) (log scale) 1e+01 1e+03 1e+05 Encrypted tunnel Web
Metrics for Security and Performance in Low-Latency Anonymity Systems Tor user Entry node Tor Network Middle node Exit node Bandwidth per node (kb/s) (log scale) 1e+01 1e+03 1e+05 Encrypted tunnel Web
QoS support for Intelligent Storage Devices
 QoS support for Intelligent Storage Devices Joel Wu Scott Brandt Department of Computer Science University of California Santa Cruz ISW 04 UC Santa Cruz Mixed-Workload Requirement General purpose systems
QoS support for Intelligent Storage Devices Joel Wu Scott Brandt Department of Computer Science University of California Santa Cruz ISW 04 UC Santa Cruz Mixed-Workload Requirement General purpose systems
CHAPTER 4 OPTIMIZATION OF WEB CACHING PERFORMANCE BY CLUSTERING-BASED PRE-FETCHING TECHNIQUE USING MODIFIED ART1 (MART1)
 71 CHAPTER 4 OPTIMIZATION OF WEB CACHING PERFORMANCE BY CLUSTERING-BASED PRE-FETCHING TECHNIQUE USING MODIFIED ART1 (MART1) 4.1 INTRODUCTION One of the prime research objectives of this thesis is to optimize
71 CHAPTER 4 OPTIMIZATION OF WEB CACHING PERFORMANCE BY CLUSTERING-BASED PRE-FETCHING TECHNIQUE USING MODIFIED ART1 (MART1) 4.1 INTRODUCTION One of the prime research objectives of this thesis is to optimize
Lecture 7 - Memory Hierarchy-II
 CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II John Wawrzynek Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~johnw
CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II John Wawrzynek Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~johnw
Memory hierarchy review. ECE 154B Dmitri Strukov
 Memory hierarchy review ECE 154B Dmitri Strukov Outline Cache motivation Cache basics Six basic optimizations Virtual memory Cache performance Opteron example Processor-DRAM gap in latency Q1. How to deal
Memory hierarchy review ECE 154B Dmitri Strukov Outline Cache motivation Cache basics Six basic optimizations Virtual memory Cache performance Opteron example Processor-DRAM gap in latency Q1. How to deal
CMSC Computer Architecture Lecture 12: Multi-Core. Prof. Yanjing Li University of Chicago
 CMSC 22200 Computer Architecture Lecture 12: Multi-Core Prof. Yanjing Li University of Chicago Administrative Stuff! Lab 4 " Due: 11:49pm, Saturday " Two late days with penalty! Exam I " Grades out on
CMSC 22200 Computer Architecture Lecture 12: Multi-Core Prof. Yanjing Li University of Chicago Administrative Stuff! Lab 4 " Due: 11:49pm, Saturday " Two late days with penalty! Exam I " Grades out on
Today CSCI Coda. Naming: Volumes. Coda GFS PAST. Instructor: Abhishek Chandra. Main Goals: Volume is a subtree in the naming space
 Today CSCI 5105 Coda GFS PAST Instructor: Abhishek Chandra 2 Coda Main Goals: Availability: Work in the presence of disconnection Scalability: Support large number of users Successor of Andrew File System
Today CSCI 5105 Coda GFS PAST Instructor: Abhishek Chandra 2 Coda Main Goals: Availability: Work in the presence of disconnection Scalability: Support large number of users Successor of Andrew File System
Two hours. Question ONE is COMPULSORY UNIVERSITY OF MANCHESTER SCHOOL OF COMPUTER SCIENCE. Date: Friday 25th January 2013 Time: 14:00-16:00
 Two hours Question ONE is COMPULSORY UNIVERSITY OF MANCHESTER SCHOOL OF COMPUTER SCIENCE Operating Systems Date: Friday 25th January 2013 Time: 14:00-16:00 Please answer Question ONE and any TWO other
Two hours Question ONE is COMPULSORY UNIVERSITY OF MANCHESTER SCHOOL OF COMPUTER SCIENCE Operating Systems Date: Friday 25th January 2013 Time: 14:00-16:00 Please answer Question ONE and any TWO other
Efficient Prefetching with Hybrid Schemes and Use of Program Feedback to Adjust Prefetcher Aggressiveness
 Journal of Instruction-Level Parallelism 13 (11) 1-14 Submitted 3/1; published 1/11 Efficient Prefetching with Hybrid Schemes and Use of Program Feedback to Adjust Prefetcher Aggressiveness Santhosh Verma
Journal of Instruction-Level Parallelism 13 (11) 1-14 Submitted 3/1; published 1/11 Efficient Prefetching with Hybrid Schemes and Use of Program Feedback to Adjust Prefetcher Aggressiveness Santhosh Verma
Page Replacement Algorithms
 Page Replacement Algorithms MIN, OPT (optimal) RANDOM evict random page FIFO (first-in, first-out) give every page equal residency LRU (least-recently used) MRU (most-recently used) 1 9.1 Silberschatz,
Page Replacement Algorithms MIN, OPT (optimal) RANDOM evict random page FIFO (first-in, first-out) give every page equal residency LRU (least-recently used) MRU (most-recently used) 1 9.1 Silberschatz,
Predicting Program Phases and Defending against Side-Channel Attacks using Hardware Performance Counters
 Predicting Program Phases and Defending against Side-Channel Attacks using Hardware Performance Counters Junaid Nomani and Jakub Szefer Computer Architecture and Security Laboratory Yale University junaid.nomani@yale.edu
Predicting Program Phases and Defending against Side-Channel Attacks using Hardware Performance Counters Junaid Nomani and Jakub Szefer Computer Architecture and Security Laboratory Yale University junaid.nomani@yale.edu
CFLRU:A A Replacement Algorithm for Flash Memory
 CFLRU:A A Replacement Algorithm for Flash Memory CASES'06, October 23 25, 2006, Seoul, Korea. Copyright 2006 ACM 1-59593-543-6/06/0010 Yen-Ting Liu Outline Introduction CFLRU Algorithm Simulation Implementation
CFLRU:A A Replacement Algorithm for Flash Memory CASES'06, October 23 25, 2006, Seoul, Korea. Copyright 2006 ACM 1-59593-543-6/06/0010 Yen-Ting Liu Outline Introduction CFLRU Algorithm Simulation Implementation
ECE 30 Introduction to Computer Engineering
 ECE 0 Introduction to Computer Engineering Study Problems, Set #9 Spring 01 1. Given the following series of address references given as word addresses:,,, 1, 1, 1,, 8, 19,,,,, 7,, and. Assuming a direct-mapped
ECE 0 Introduction to Computer Engineering Study Problems, Set #9 Spring 01 1. Given the following series of address references given as word addresses:,,, 1, 1, 1,, 8, 19,,,,, 7,, and. Assuming a direct-mapped
Analyzing Memory Access Patterns and Optimizing Through Spatial Memory Streaming. Ogün HEPER CmpE 511 Computer Architecture December 24th, 2009
 Analyzing Memory Access Patterns and Optimizing Through Spatial Memory Streaming Ogün HEPER CmpE 511 Computer Architecture December 24th, 2009 Agenda Introduction Memory Hierarchy Design CPU Speed vs.
Analyzing Memory Access Patterns and Optimizing Through Spatial Memory Streaming Ogün HEPER CmpE 511 Computer Architecture December 24th, 2009 Agenda Introduction Memory Hierarchy Design CPU Speed vs.
Tradeoff between coverage of a Markov prefetcher and memory bandwidth usage
 Tradeoff between coverage of a Markov prefetcher and memory bandwidth usage Elec525 Spring 2005 Raj Bandyopadhyay, Mandy Liu, Nico Peña Hypothesis Some modern processors use a prefetching unit at the front-end
Tradeoff between coverage of a Markov prefetcher and memory bandwidth usage Elec525 Spring 2005 Raj Bandyopadhyay, Mandy Liu, Nico Peña Hypothesis Some modern processors use a prefetching unit at the front-end
Best-Offset Hardware Prefetching
 Best-Offset Hardware Prefetching Pierre Michaud March 2016 2 BOP: yet another data prefetcher Contribution: offset prefetcher with new mechanism for setting the prefetch offset dynamically - Improvement
Best-Offset Hardware Prefetching Pierre Michaud March 2016 2 BOP: yet another data prefetcher Contribution: offset prefetcher with new mechanism for setting the prefetch offset dynamically - Improvement
Cache Performance and Memory Management: From Absolute Addresses to Demand Paging. Cache Performance
 6.823, L11--1 Cache Performance and Memory Management: From Absolute Addresses to Demand Paging Asanovic Laboratory for Computer Science M.I.T. http://www.csg.lcs.mit.edu/6.823 Cache Performance 6.823,
6.823, L11--1 Cache Performance and Memory Management: From Absolute Addresses to Demand Paging Asanovic Laboratory for Computer Science M.I.T. http://www.csg.lcs.mit.edu/6.823 Cache Performance 6.823,
Caches in Real-Time Systems. Instruction Cache vs. Data Cache
 Caches in Real-Time Systems [Xavier Vera, Bjorn Lisper, Jingling Xue, Data Caches in Multitasking Hard Real- Time Systems, RTSS 2003.] Schedulability Analysis WCET Simple Platforms WCMP (memory performance)
Caches in Real-Time Systems [Xavier Vera, Bjorn Lisper, Jingling Xue, Data Caches in Multitasking Hard Real- Time Systems, RTSS 2003.] Schedulability Analysis WCET Simple Platforms WCMP (memory performance)
Virtual Memory. Motivation:
 Virtual Memory Motivation:! Each process would like to see its own, full, address space! Clearly impossible to provide full physical memory for all processes! Processes may define a large address space
Virtual Memory Motivation:! Each process would like to see its own, full, address space! Clearly impossible to provide full physical memory for all processes! Processes may define a large address space
Advanced Caching Techniques
 Advanced Caching Approaches to improving memory system performance eliminate memory operations decrease the number of misses decrease the miss penalty decrease the cache/memory access times hide memory
Advanced Caching Approaches to improving memory system performance eliminate memory operations decrease the number of misses decrease the miss penalty decrease the cache/memory access times hide memory
CS433 Final Exam. Prof Josep Torrellas. December 12, Time: 2 hours
 CS433 Final Exam Prof Josep Torrellas December 12, 2006 Time: 2 hours Name: Instructions: 1. This is a closed-book, closed-notes examination. 2. The Exam has 6 Questions. Please budget your time. 3. Calculators
CS433 Final Exam Prof Josep Torrellas December 12, 2006 Time: 2 hours Name: Instructions: 1. This is a closed-book, closed-notes examination. 2. The Exam has 6 Questions. Please budget your time. 3. Calculators
A Scheme of Predictor Based Stream Buffers. Bill Hodges, Guoqiang Pan, Lixin Su
 A Scheme of Predictor Based Stream Buffers Bill Hodges, Guoqiang Pan, Lixin Su Outline Background and motivation Project hypothesis Our scheme of predictor-based stream buffer Predictors Predictor table
A Scheme of Predictor Based Stream Buffers Bill Hodges, Guoqiang Pan, Lixin Su Outline Background and motivation Project hypothesis Our scheme of predictor-based stream buffer Predictors Predictor table
SIC: Provably Timing-Predictable Strictly In-Order Pipelined Processor Core
 SIC: Provably Timing-Predictable Strictly In-Order Pipelined Processor Core Sebastian Hahn and Jan Reineke RTSS, Nashville December, 2018 saarland university computer science SIC: Provably Timing-Predictable
SIC: Provably Timing-Predictable Strictly In-Order Pipelined Processor Core Sebastian Hahn and Jan Reineke RTSS, Nashville December, 2018 saarland university computer science SIC: Provably Timing-Predictable
Computer Architecture and Engineering. CS152 Quiz #2. March 3rd, Professor Krste Asanovic. Name:
 Computer Architecture and Engineering CS152 Quiz #2 March 3rd, 2009 Professor Krste Asanovic Name: Notes: This is a closed book, closed notes exam. 80 Minutes 10 Pages Not all questions are of equal difficulty,
Computer Architecture and Engineering CS152 Quiz #2 March 3rd, 2009 Professor Krste Asanovic Name: Notes: This is a closed book, closed notes exam. 80 Minutes 10 Pages Not all questions are of equal difficulty,
Course Description: This course includes the basic concepts of operating system
 Operating Systems Course Title: Operating Systems Full Marks:60+ 20+20 Course No: CSC259 Pass Marks: 24+8+8 Nature of the Course: Theory + Lab Credit Hrs: 3 Course Description: This course includes the
Operating Systems Course Title: Operating Systems Full Marks:60+ 20+20 Course No: CSC259 Pass Marks: 24+8+8 Nature of the Course: Theory + Lab Credit Hrs: 3 Course Description: This course includes the
FairRide: Near-Optimal Fair Cache Sharing
 UC BERKELEY FairRide: Near-Optimal Fair Cache Sharing Qifan Pu, Haoyuan Li, Matei Zaharia, Ali Ghodsi, Ion Stoica 1 Caches are crucial 2 Caches are crucial 2 Caches are crucial 2 Caches are crucial 2 Cache
UC BERKELEY FairRide: Near-Optimal Fair Cache Sharing Qifan Pu, Haoyuan Li, Matei Zaharia, Ali Ghodsi, Ion Stoica 1 Caches are crucial 2 Caches are crucial 2 Caches are crucial 2 Caches are crucial 2 Cache
Computer Architecture Spring 2016
 omputer Architecture Spring 2016 Lecture 09: Prefetching Shuai Wang Department of omputer Science and Technology Nanjing University Prefetching(1/3) Fetch block ahead of demand Target compulsory, capacity,
omputer Architecture Spring 2016 Lecture 09: Prefetching Shuai Wang Department of omputer Science and Technology Nanjing University Prefetching(1/3) Fetch block ahead of demand Target compulsory, capacity,
A Flexible Model for Resource Management in Virtual Private Networks. Presenter: Huang, Rigao Kang, Yuefang
 A Flexible Model for Resource Management in Virtual Private Networks Presenter: Huang, Rigao Kang, Yuefang Overview Introduction of VPN Hose model Implementation scenarios Simulation experiments Simulation
A Flexible Model for Resource Management in Virtual Private Networks Presenter: Huang, Rigao Kang, Yuefang Overview Introduction of VPN Hose model Implementation scenarios Simulation experiments Simulation
A Fault-Tolerant Alternative to Lockstep Triple Modular Redundancy
 A Fault-Tolerant Alternative to Lockstep Triple Modular Redundancy Andrew L. Baldwin, BS 09, MS 12 W. Robert Daasch, Professor Integrated Circuits Design and Test Laboratory Problem Statement In a fault
A Fault-Tolerant Alternative to Lockstep Triple Modular Redundancy Andrew L. Baldwin, BS 09, MS 12 W. Robert Daasch, Professor Integrated Circuits Design and Test Laboratory Problem Statement In a fault
Adaptive Resync in vsan 6.7 First Published On: Last Updated On:
 First Published On: 04-26-2018 Last Updated On: 05-02-2018 1 Table of Contents 1. Overview 1.1.Executive Summary 1.2.vSAN's Approach to Data Placement and Management 1.3.Adaptive Resync 1.4.Results 1.5.Conclusion
First Published On: 04-26-2018 Last Updated On: 05-02-2018 1 Table of Contents 1. Overview 1.1.Executive Summary 1.2.vSAN's Approach to Data Placement and Management 1.3.Adaptive Resync 1.4.Results 1.5.Conclusion
Experiments With Expert Based Caching Policies
 Experiments With Expert Based Caching Policies Robert Abbott UCSC CMPS 242 Fall 2009 Abstract This project compares the performance of Window and Weighted Majority expert based caching algorithms under
Experiments With Expert Based Caching Policies Robert Abbott UCSC CMPS 242 Fall 2009 Abstract This project compares the performance of Window and Weighted Majority expert based caching algorithms under
Design Considerations for Using Flash Memory for Caching
 Design Considerations for Using Flash Memory for Caching Edi Shmueli, IBM XIV Storage Systems edi@il.ibm.com Santa Clara, CA August 2010 1 Solid-State Storage In a few decades solid-state storage will
Design Considerations for Using Flash Memory for Caching Edi Shmueli, IBM XIV Storage Systems edi@il.ibm.com Santa Clara, CA August 2010 1 Solid-State Storage In a few decades solid-state storage will
Reconfigurable and Self-optimizing Multicore Architectures. Presented by: Naveen Sundarraj
 Reconfigurable and Self-optimizing Multicore Architectures Presented by: Naveen Sundarraj 1 11/9/2012 OUTLINE Introduction Motivation Reconfiguration Performance evaluation Reconfiguration Self-optimization
Reconfigurable and Self-optimizing Multicore Architectures Presented by: Naveen Sundarraj 1 11/9/2012 OUTLINE Introduction Motivation Reconfiguration Performance evaluation Reconfiguration Self-optimization
Coordinated En-Route Web Caching
 This is the Pre-Published Version En-Route Web Caching Xueyan Tang & Samuel T. Chanson Department of Computer Science The Hong Kong University of Science and Technology Clear Water Bay, Hong Kong E-mail:
This is the Pre-Published Version En-Route Web Caching Xueyan Tang & Samuel T. Chanson Department of Computer Science The Hong Kong University of Science and Technology Clear Water Bay, Hong Kong E-mail:
IBM InfoSphere Streams v4.0 Performance Best Practices
 Henry May IBM InfoSphere Streams v4.0 Performance Best Practices Abstract Streams v4.0 introduces powerful high availability features. Leveraging these requires careful consideration of performance related
Henry May IBM InfoSphere Streams v4.0 Performance Best Practices Abstract Streams v4.0 introduces powerful high availability features. Leveraging these requires careful consideration of performance related
Automatic Generation of Behavioral Hard Disk Drive Access Time Models
 Automatic Generation of Behavioral Hard Disk Drive Access Time Models Adam Crume 1 Carlos Maltzahn 1 Lee Ward 2 Thomas Kroeger 2 Matthew Curry 2 Ron Oldfield 2 Patrick Widener 2 1 University of California,
Automatic Generation of Behavioral Hard Disk Drive Access Time Models Adam Crume 1 Carlos Maltzahn 1 Lee Ward 2 Thomas Kroeger 2 Matthew Curry 2 Ron Oldfield 2 Patrick Widener 2 1 University of California,
Considering Priority in Overlay Multicast Protocols under Heterogeneous Environments
 Considering Priority in Overlay Multicast Protocols under Heterogeneous Environments Michael Bishop and Sanjay Rao Purdue University Kunwadee Sripanidkulchai National Electronics and Computer Technology
Considering Priority in Overlay Multicast Protocols under Heterogeneous Environments Michael Bishop and Sanjay Rao Purdue University Kunwadee Sripanidkulchai National Electronics and Computer Technology
Advanced optimizations of cache performance ( 2.2)
 Advanced optimizations of cache performance ( 2.2) 30 1. Small and Simple Caches to reduce hit time Critical timing path: address tag memory, then compare tags, then select set Lower associativity Direct-mapped
Advanced optimizations of cache performance ( 2.2) 30 1. Small and Simple Caches to reduce hit time Critical timing path: address tag memory, then compare tags, then select set Lower associativity Direct-mapped
Multimedia Streaming. Mike Zink
 Multimedia Streaming Mike Zink Technical Challenges Servers (and proxy caches) storage continuous media streams, e.g.: 4000 movies * 90 minutes * 10 Mbps (DVD) = 27.0 TB 15 Mbps = 40.5 TB 36 Mbps (BluRay)=
Multimedia Streaming Mike Zink Technical Challenges Servers (and proxy caches) storage continuous media streams, e.g.: 4000 movies * 90 minutes * 10 Mbps (DVD) = 27.0 TB 15 Mbps = 40.5 TB 36 Mbps (BluRay)=
4.1 Introduction 4.3 Datapath 4.4 Control 4.5 Pipeline overview 4.6 Pipeline control * 4.7 Data hazard & forwarding * 4.
 Chapter 4: CPU 4.1 Introduction 4.3 Datapath 4.4 Control 4.5 Pipeline overview 4.6 Pipeline control * 4.7 Data hazard & forwarding * 4.8 Control hazard 4.14 Concluding Rem marks Hazards Situations that
Chapter 4: CPU 4.1 Introduction 4.3 Datapath 4.4 Control 4.5 Pipeline overview 4.6 Pipeline control * 4.7 Data hazard & forwarding * 4.8 Control hazard 4.14 Concluding Rem marks Hazards Situations that
