ASA 7.2(2): SSL VPN Client (SVC) for Public Internet VPN on a Stick Configuration Example
|
|
|
- Tamsin Baldwin
- 6 years ago
- Views:
Transcription
1 ASA 7.2(2): SSL VPN Client (SVC) for Public Internet VPN on a Stick Configuration Example Document ID: Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure Network Diagram ASA 7.2(2) Configurations Using ASDM 5.2(2) ASA 7.2(2) CLI Configuration Establish the SSL VPN Connection with SVC Verify Troubleshoot Related Information Introduction This document describes how to set up an Adaptive Security Appliance (ASA) to perform SSL VPN on a stick. This setup applies to a specific case in which the ASA does not allow split tunneling and users connect directly to the ASA before they are permitted to go to the Internet. Note: In ASA version 7.2.2, the intra interface keyword of the same security traffic permit configuration mode command allows all traffic to enter and exit the same interface (not just IPsec traffic). Prerequisites Requirements Ensure that you meet these requirements before you attempt this configuration: The hub ASA Security Appliance needs to run version Cisco SSL VPN Client (SVC) 1.x Note: Download the SSL VPN Client package (sslclient win*.pkg) from Cisco Software Download (registered customers only). Copy the SVC to the flash memory on the ASA. The SVC is to be downloaded to the remote user computers in order to establish the SSL VPN connection with the ASA. Refer to Installing the SVC Software section of the Cisco Security Appliance Command Line Configuration Guide, Version 7.2 for more information. Components Used The information in this document is based on these software and hardware versions:
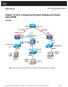
2 Cisco 5500 Series Adaptive Security Appliance (ASA) that runs software version 7.2(2) Cisco SSL VPN Client version for Windows PC that runs Windows 2000 Professional or Windows XP Cisco Adaptive Security Device Manager (ASDM) version 5.2(2) The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command. Conventions Refer to the Cisco Technical Tips Conventions for more information on document conventions. Background Information The SSL VPN Client (SVC) is a VPN tunneling technology that gives remote users the benefits of an IPSec VPN client without the need for network administrators to install and configure IPSec VPN clients on remote computers. The SVC uses the SSL encryption that is already present on the remote computer as well as the WebVPN login and authentication of the security appliance. To establish an SVC session, the remote user enters the IP address of a WebVPN interface of the security appliance in the browser, and the browser connects to that interface and displays the WebVPN login screen. If the user satisfies the login and authentication, and the security appliance identifies the user as requiring the SVC, the security appliance downloads the SVC to the remote computer. If the security appliance identifies the user as having the option to use the SVC, the security appliance downloads the SVC to the remote computer while presenting a link on the user screen to skip the SVC installation. After downloading, the SVC installs and configures itself, and then the SVC either remains or uninstalls itself (depending on the configuration) from the remote computer when the connection terminates. Configure In this section, you are presented with the information to configure the features described in this document. Note: Use the Command Lookup Tool (registered customers only) to obtain more information on the commands used in this section. Network Diagram This document uses this network setup:
3 Note: The IP addressing schemes used in this configuration are not legally routable on the Internet. They are RFC 1918 addresses which have been used in a lab environment. ASA 7.2(2) Configurations Using ASDM 5.2(2) This document assumes the basic configurations, such as interface configuration, are already made and working properly. Note: Refer to Allowing HTTPS Access for ASDM in order to allow the ASA to be configured by the ASDM. Note: WebVPN and ASDM cannot be enabled on the same ASA interface unless you change the port numbers. Refer to ASDM and WebVPN Enabled on the Same Interface of ASA for more information. Complete these steps in order to configure the SSL VPN on a stick in ASA: 1. Choose Configuration > Interfaces, and check the Enable traffic between two or more hosts connected to the same interface check box in order to allow SSL VPN traffic to enter and exit the same interface. 2. Click Apply.
4 Note: Here is the equivalent CLI configuration command: Cisco ASA 7.2(2) ciscoasa(config)#same security traffic permit intra interface 3. Choose Configuration > VPN > IP Address Management > IP Pools > Add in order to create an IP address pool named vpnpool. 4. Click Apply. Note: Here is the equivalent CLI configuration command:
5 Cisco ASA 7.2(2) ciscoasa(config)#ip local pool vpnpool Enable WebVPN: a. Choose Configuration > VPN > WebVPN > WebVPN Access, and select the outside interface. b. Click Enable. c. Check the Enable Tunnel Group Drop down List on WebVPN Login Page check box in order to allow users to choose their respective groups from the Login page. d. Click Apply. e. Choose Configuration > VPN > WebVPN > SSL VPN Client > Add in order to add the SSL VPN Client image from the flash memory of ASA.
6 f. Click OK. g. Click OK. h. Click SSL VPN Client check box.
7 Note: Here are the equivalent CLI configuration commands: Cisco ASA 7.2(2) ciscoasa(config)#webvpn ciscoasa(config webvpn)#enable outside ciscoasa(config webvpn)#svc image disk0:/sslclient win pkg 1 ciscoasa(config webvpn)#tunnel group list enable ciscoasa(config webvpn)#svc enable 6. Configure the group policy: a. Choose Configuration > VPN > General > Group Policy > Add (Internal Group Policy) in order to create an internal group policy named clientgroup. b. Click the General tab, and select the WebVPN check box in order to enable the WebVPN as tunneling protocol. c. Click the Client Configuration tab, and then click the General Client Parameters tab. d. Choose Tunnel All Networks from the Split Tunnel Policy drop down list in order to make all the packets travel from the remote PC through a secure tunnel.
8 e. Click the WebVPN > SSLVPN Client tab, and choose these options: a. For the Use SSL VPN Client option, uncheck the Inherit check box, and click the Optional radio button. This option allows the remote client to choose whether or not to download the SVC. The Always choice ensures that the SVC is downloaded to the remote workstation during each SSL VPN connection. b. For the Keep Installer on Client System option, uncheck the Inherit check box, and click the Yes radio button This option allows the SVC software to remain on the client machine. Therefore, the ASA is not required to download the SVC software to the client each time a connection is made. This option is a good choice for remote users who often access the corporate network. c. For the Renegotiation Interval option, uncheck the Inherit box, uncheck the Unlimited check box, and enter the number of minutes until rekey. Note: Security is enhanced by setting limits on the length of time a key is valid. d. For the Renegotiation Method option, uncheck the Inherit check box, and click the SSL radio button. Note: Renegotiation can use the present SSL tunnel or a new tunnel created specifically for renegotiation. Your SSL VPN Client attributes should be configured as shown in this image:
9 f. Click OK, and then click Apply. Note: Here are the equivalent CLI configuration commands: Cisco ASA 7.2(2) ciscoasa(config)#group policy clientgroup internal ciscoasa(config)#group policyclientgroup attributes ciscoasa(config group policy)#vpn tunnel protocol webvpn ciscoasa(config group policy)#split tunnel policy tunnelall ciscoasa(config group policy)#webvpn ciscoasa(config group webvpn)#svc required ciscoasa(config group webvpn)#svc keep installer installed
10 ciscoasa(config group webvpn)#svc rekey time 30 ciscoasa(config group webvpn)#svc rekey method ssl 7. Choose Configuration > VPN > General > Users > Add in order to create a new user account ssluser1. 8. Click OK, and then click Apply. Note: Here is the equivalent CLI command: Cisco ASA 7.2(2) ciscoasa(config)#username ssluser1 password asdmasa@ 9. Choose Configuration > Properties > AAA Setup > AAA Servers Groups > Edit. 10. Select the the default server group LOCAL, and click Edit. 11. In the Edit LOCAL Server Group dialog box, click the Enable Local User Lockout check box, and enter 16 in the Maximum Attempts text box. 12. Click OK.
11 Note: Here is the equivalent CLI command: Cisco ASA 7.2(2) ciscoasa(config)#aaa local authentication attempts max fail Configure the tunnel group: a. Choose Configuration > VPN > General > Tunnel Group > Add(WebVPN access) in order to create a new tunnel group named sslgroup. b. Click the General tab, and then click the Basic tab. c. Choose clientgroup from the Group Policy drop down list. d. Click the Client Address Assignment tab, and then click Add in order to assign the available address pool vpnpool.
12 e. Click the WebVPN tab, and then click the Group Aliases and URLs tab. f. Type the alias name in the parameter box, and click Add in order to add it to the list of group names on the Login page. g. Click OK, and then click Apply. Note: Here are the equivalent CLI configuration commands: Cisco ASA 7.2(2) ciscoasa(config)#tunnel group sslgroup type webvpn ciscoasa(config)#tunnel group sslgroup general attributes ciscoasa(config tunnel general)#address pool vpnpool ciscoasa(config tunnel general)#default group policy clientgroup ciscoasa(config tunnel general)#exit
13 ciscoasa(config)#tunnel group sslgroup webvpn attributes ciscoasa(config tunnel webvpn)#group alias sslgroup_users enable 14. Configure NAT: a. Choose Configuration > NAT > Add > Add Dynamic NAT Rule to allow the traffic that comes from the inside network to be translated with the use of the outside IP address b. Click OK. c. Choose Configuration > NAT > Add > Add Dynamic NAT Rule to allow the traffic that comes from the outside network to be translated with the use of the outside IP address
14 d. Click OK. e. Click Apply. Note: Here are the equivalent CLI configuration commands: Cisco ASA 7.2(2) ciscoasa(config)#global (outside) ciscoasa(config)#nat (inside) ciscoasa(config)#nat (outside) ASA 7.2(2) CLI Configuration Cisco ASA 7.2(2) ciscoasa#show running config : Saved : ASA Version 7.2(2)! hostname ciscoasa enable password 8Ry2YjIyt7RRXU24 encrypted names! interface Ethernet0/0 nameif inside
15 security level 100 ip address ! interface Ethernet0/1 nameif outside security level 0 ip address ! interface Ethernet0/2 shutdown no nameif no security level no ip address! interface Ethernet0/3 shutdown no nameif no security level no ip address! interface Management0/0 shutdown no nameif no security level no ip address! passwd 2KFQnbNIdI.2KYOU encrypted ftp mode passive same security traffic permit intra interface! Command that permits the SSL VPN traffic to enter! and exit the same interface. access list 100 extended permit icmp any any pager lines 24 mtu inside 1500 mtu outside 1500 ip local pool vpnpool ! The address pool for the SSL VPN Clients. no failover icmp unreachable rate limit 1 burst size 1 asdm image disk0:/asdm 522.bin no asdm history enable arp timeout global (outside) ! The global address for Internet access used by VPN Clients.! Note: Uses an RFC 1918 range for lab setup.! Apply an address from your public range provided by your ISP. nat (inside) ! The NAT statement to define what to encrypt! (the addresses from vpn pool).
16 nat (outside) access group 100 in interface outside route outside timeout xlate 3:00:00 timeout conn 1:00:00 half closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp pat 0:05:0 timeout sip 0:30:00 sip_media 0:02:00 sip invite 0:03:00 sip disconnect 0:02: timeout uauth 0:05:00 absolute group policy clientgroup internal! Create an internal group policy "clientgroup." group policy clientgroup attributes vpn tunnel protocol webvpn! Enable webvpn as tunneling protocol. split tunnel policy tunnelall! Encrypt all the traffic coming from the SSL VPN Clients. webvpn svc required! Activate the SVC under webvpn mode svc keep installer installed! When the security appliance and the SVC perform a rekey, they renegotiate! the crypto keys and initialization vectors, increasing the security of! the connection. svc rekey time 30 Command that specifies the number of minutes from the start of the! session until the rekey takes place, from 1 to (1 week). svc rekey method ssl! Command that specifies that SSL renegotiation takes place during SVC rekey. username ssluser1 password ZRhW85jZqEaVd5P. encrypted! Create an user account "ssluser1." aaa local authentication attempts max fail 16
17 ! Enable the AAA local authentication. http server enable http inside no snmp server location no snmp server contact snmp server enable traps snmp authentication linkup linkdown coldstart tunnel group sslgroup type webvpn! Create a tunnel group "sslgroup" with type as WebVPN. tunnel group sslgroup general attributes address pool vpnpool! Associate the address pool vpnpool created. default group policy clientgroup! Associate the group policy "clientgroup" created. tunnel group sslgroup webvpn attributes group alias sslgroup_users enable! Configure the group alias as sslgroup users. telnet timeout 5 ssh timeout 5 console timeout 0! class map inspection_default match default inspection traffic!! policy map type inspect dns preset_dns_map parameters message length maximum 512 policy map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect h323 h225 inspect h323 ras inspect netbios inspect rsh inspect rtsp inspect skinny inspect esmtp inspect sqlnet inspect sunrpc inspect tftp inspect sip inspect xdmcp! service policy global_policy global webvpn enable outside
18 ! Enable WebVPN on the outside interface. svc image disk0:/sslclient win pkg 1! Assign an order to the SVC image. svc enable! Enable the security appliance to download SVC images to remote computers. tunnel group list enable! Enable the display of the tunnel group list on the WebVPN Login page. prompt hostname context Cryptochecksum:d41d8cd98f00b204e ecf8427e : end ciscoasa# Establish the SSL VPN Connection with SVC Complete these steps in order to establish a SSL VPN connection with ASA. 1. Type in the Address field of your web browser the URL or IP address for the WebVPN interface of the ASA. For example: address of the ASA WebVPN interface>
19 2. Enter your user name and password, and then choose your respective group from the Group drop down list. Note: ActiveX software must be installed in your computer before you download the SSL VPN Client.
20 This dialog box appears as the connection is established: This message appears once the connection is established: 3. Once the connection is established, double click the yellow key icon that appears in the task bar of your computer. The Cisco Systems SSL VPN Client dialog box displays information about the SSL connection.
21
22 Verify Use this section in order to confirm that your configuration works properly. The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of show command output. show webvpn svcdisplays the SVC images stored in the ASA flash memory. ciscoasa#show webvpn svc 1. disk0:/sslclient win pkg 1 CISCO STC win2k ,1,4,179 Fri 01/18/ :19: SSL VPN Client(s) installed show vpn sessiondb svcdisplays the information about the current SSL connections. ciscoasa#show vpn sessiondb svc Session Type: SVC Username : ssluser1 Index : 1 Assigned IP : Public IP : Protocol : SVC Encryption : 3DES Hashing : SHA1 Bytes Tx : Bytes Rx : 5082 Client Type : Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) Client Ver : Cisco Systems SSL VPN Client 1, 1, 4, 179 Group Policy : clientgroup Tunnel Group : sslgroup Login Time : 12:38:47 UTC Mon Mar Duration : 0h:00m:53s Filter Name : show webvpn group aliasdisplays the configured alias for various groups. ciscoasa#show webvpn group alias Tunnel Group: sslgroup Group Alias: sslgroup_users enabled
23 In ASDM, choose Monitoring > VPN > VPN Statistics > Sessions in order to view information about the current WebVPN sessions in the ASA. Troubleshoot This section provides information you can use to troubleshoot your configuration. vpn sessiondb logoff name <username>allows you to log off the SSL VPN session for the specified user name. ciscoasa#vpn sessiondb logoff name ssluser1 Called vpn_remove_uauith: success! webvpn_svc_np_tear_down: no ACL NFO: Number of sessions with name "ssluser1" logged off : 1 Similarly, you can use the command vpn sessiondb logoff svc in order to terminate all the SVC sessions. Note: If the PC goes to standby or hibernate mode, then the SSL VPN connection can be terminated. webvpn_rx_data_cstp webvpn_rx_data_cstp: got message SVC message: t/s=5/16: Client PC is going into suspend mode (Sleep, Hibernate, etc) Called vpn_remove_uauth: success! webvpn_svc_np_tear_down: no ACL ciscoasa#show vpn sessiondb svc INFO: There are presently no active sessions Debug webvpn svc <1 255>Provides the real time WebVPN events in order to establish the session. Ciscoasa#debug webvpn svc 7 ATTR_CISCO_AV_PAIR: got SVC ACL: 1 webvpn_rx_data_tunnel_connect CSTP state = HEADER_PROCESSING http_parse_cstp_method()...input: 'CONNECT /CSCOSSLC/tunnel HTTP/1.1' webvpn_cstp_parse_request_field()...input: 'Host: ' Processing CSTP header line: 'Host: ' webvpn_cstp_parse_request_field()...input: 'User Agent: Cisco Systems SSL VPN Client 1, 1, 4, 179' Processing CSTP header line: 'User Agent: Cisco Systems SSL VPN Client 1, 1, 4, 179' Setting user agent to: 'Cisco Systems SSL VPN Client 1, 1, 4, 179' webvpn_cstp_parse_request_field()
24 ...input: 'X CSTP Version: 1' Processing CSTP header line: 'X CSTP Version: 1' Setting version to '1' webvpn_cstp_parse_request_field()...input: 'X CSTP Hostname: tacweb' Processing CSTP header line: 'X CSTP Hostname: tacweb' Setting hostname to: 'tacweb' webvpn_cstp_parse_request_field()...input: 'X CSTP Accept Encoding: deflate;q=1.0' Processing CSTP header line: 'X CSTP Accept Encoding: deflate;q=1.0' webvpn_cstp_parse_request_field()...input: 'Cookie: D5BC554D2' Processing CSTP header line: 'Cookie: CF236DB5E8BE70B1486D5BC554D2' Found WebVPN cookie: 486D5BC554D2' WebVPN Cookie: C554D2' Validating address: CSTP state = WAIT_FOR_ADDRESS webvpn_cstp_accept_address: / CSTP state = HAVE_ADDRESS No subnetmask... must calculate it SVC: NP setup webvpn_svc_np_setup SVC ACL Name: NULL SVC ACL ID: 1 SVC ACL ID: 1 vpn_put_uauth success! SVC: adding to sessmgmt SVC: Sending response CSTP state = CONNECTED In ASDM, choose Monitoring > Logging > Real time Log Viewer > View in order to view the real time events. These examples show session information between the SVC and Webserver in the Internet via ASA Related Information Cisco 5500 Series Adaptive Security Appliance Support Page PIX/ASA 7.x and VPN Client for Public Internet VPN on a Stick Configuration Example SSL VPN Client (SVC) on ASA with ASDM Configuration Example Technical Support & Documentation Cisco Systems
25 Contacts & Feedback Help Site Map Cisco Systems, Inc. All rights reserved. Terms & Conditions Privacy Statement Cookie Policy Trademarks of Cisco Systems, Inc. Updated: Oct 02, 2009 Document ID:
PIX/ASA 7.x ASDM: Restrict the Network Access of Remote Access VPN Users
 PIX/ASA 7.x ASDM: Restrict the Network Access of Remote Access VPN Users Document ID: 69308 Contents Introduction Prerequisites Requirements Components Used Related Products Network Diagram Conventions
PIX/ASA 7.x ASDM: Restrict the Network Access of Remote Access VPN Users Document ID: 69308 Contents Introduction Prerequisites Requirements Components Used Related Products Network Diagram Conventions
IPSec tunnel for ER75i routers application guide
 IPSec tunnel for ER75i routers application guide 1 Contents 1. Generally...3 2. IPSec limitation...3 3. Example of use IPSec tunnel Client side at ER75i...4 3.1. IPSec tunnel client side at ER75i...4 3.1.1.
IPSec tunnel for ER75i routers application guide 1 Contents 1. Generally...3 2. IPSec limitation...3 3. Example of use IPSec tunnel Client side at ER75i...4 3.1. IPSec tunnel client side at ER75i...4 3.1.1.
ASA/PIX: Remote VPN Server with Inbound NAT for VPN Client Traffic with CLI and ASDM Configuration Example
 ASA/PIX: Remote VPN Server with Inbound NAT for VPN Client Traffic with CLI and ASDM Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions
ASA/PIX: Remote VPN Server with Inbound NAT for VPN Client Traffic with CLI and ASDM Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions
Document ID: Contents. Introduction. Prerequisites. Requirements. Introduction. Prerequisites Requirements
 Products & Services ASA/PIX 7.x: Redundant or Backup ISP Links Configuration Example Document ID: 70559 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Background
Products & Services ASA/PIX 7.x: Redundant or Backup ISP Links Configuration Example Document ID: 70559 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Background
Configure the ASA for Dual Internal Networks
 Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
ASA Version 7.2(4)30! hostname vpn domain-name hollywood.com enable password BO5OGdtIUElAVJc7 encrypted passwd BO5OGdtIUElAVJc7 encrypted names name
 ASA Version 7.2(4)30 hostname vpn domain-name hollywood.com enable password BO5OGdtIUElAVJc7 encrypted passwd BO5OGdtIUElAVJc7 encrypted names name 172.30.232.128 XL description XL / idot name 172.28.28.0
ASA Version 7.2(4)30 hostname vpn domain-name hollywood.com enable password BO5OGdtIUElAVJc7 encrypted passwd BO5OGdtIUElAVJc7 encrypted names name 172.30.232.128 XL description XL / idot name 172.28.28.0
PIX/ASA: PPPoE Client Configuration Example
 PIX/ASA: PPPoE Client Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram CLI Configuration ASDM Configuration
PIX/ASA: PPPoE Client Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram CLI Configuration ASDM Configuration
PIX/ASA as a DHCP Server and Client Configuration Example
 PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
Table of Contents. Cisco IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example
 Table of Contents IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example...1 Document ID: 63881...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2
Table of Contents IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example...1 Document ID: 63881...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2
Downloaded from: justpaste.it/i2os
 : Saved : ASA Version 9.1(2) hostname ciscoasa enable password xxx encrypted names ip local pool poolvpn 192.168.20.10-192.168.20.30 mask 255.255.255.0 interface GigabitEthernet0/0 nameif inside security-level
: Saved : ASA Version 9.1(2) hostname ciscoasa enable password xxx encrypted names ip local pool poolvpn 192.168.20.10-192.168.20.30 mask 255.255.255.0 interface GigabitEthernet0/0 nameif inside security-level
: Saved : : Serial Number: JMX1813Z0GJ : Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz : Written by enable_15 at 09:21: UTC Thu Dec !
 : Saved : : Serial Number: JMX1813Z0GJ : Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz : Written by enable_15 at 09:21:59.078 UTC Thu Dec 17 2015 ASA Version 9.2(2)4 hostname ciscoasa enable password
: Saved : : Serial Number: JMX1813Z0GJ : Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz : Written by enable_15 at 09:21:59.078 UTC Thu Dec 17 2015 ASA Version 9.2(2)4 hostname ciscoasa enable password
VPN Between Sonicwall Products and Cisco Security Appliance Configuration Example
 VPN Between Sonicwall Products and Cisco Security Appliance Configuration Example Document ID: 66171 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure
VPN Between Sonicwall Products and Cisco Security Appliance Configuration Example Document ID: 66171 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure
Table of Contents. Cisco Enhanced Spoke to Client VPN Configuration Example for PIX Security Appliance Version 7.0
 Table of Contents Enhanced Spoke to Client VPN Configuration Example for PIX Security Appliance Version 7.0...1 Document ID: 64693...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1
Table of Contents Enhanced Spoke to Client VPN Configuration Example for PIX Security Appliance Version 7.0...1 Document ID: 64693...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1
Table of Contents. Cisco PIX/ASA 7.x Enhanced Spoke to Spoke VPN Configuration Example
 Table of Contents PIX/ASA 7.x Enhanced Spoke to Spoke VPN Configuration Example...1 Document ID: 64692...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...2 Configure...2
Table of Contents PIX/ASA 7.x Enhanced Spoke to Spoke VPN Configuration Example...1 Document ID: 64692...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...2 Configure...2
ASA with WebVPN and Single Sign-on using ASDM and NTLMv1 Configuration Example
 ASA with WebVPN and Single Sign-on using ASDM and NTLMv1 Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Configure Add an AAA Server for Windows Domain
ASA with WebVPN and Single Sign-on using ASDM and NTLMv1 Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Configure Add an AAA Server for Windows Domain
Configuring the PIX Firewall and VPN Clients Using PPTP, MPPE and IPSec
 Configuring the PIX Firewall and VPN Clients Using PPTP, MPPE and IPSec Document ID: 14095 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Configuring the PIX Firewall and VPN Clients Using PPTP, MPPE and IPSec Document ID: 14095 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
NAC Appliance (Cisco Clean Access) In Band Virtual Gateway for Remote Access VPN Configuration Example
 NAC Appliance (Cisco Clean Access) In Band Virtual Gateway for Remote Access VPN Configuration Example Document ID: 71573 Contents Introduction Prerequisites Requirements Components Used Network Diagram
NAC Appliance (Cisco Clean Access) In Band Virtual Gateway for Remote Access VPN Configuration Example Document ID: 71573 Contents Introduction Prerequisites Requirements Components Used Network Diagram
FWSM: Multiple Context Configuration Example
 FWSM: Multiple Context Configuration Example Document ID: 107524 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Context Configuration Files Unsupported
FWSM: Multiple Context Configuration Example Document ID: 107524 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Context Configuration Files Unsupported
SSL VPN Configuration of a Cisco ASA 8.0
 Published on Jisc community (https://community.jisc.ac.uk) Home > Advisory services > Multi-site Connectivity Advisory Service > Technical guides > Secure Virtual Private Networks > SSL VPN Configuration
Published on Jisc community (https://community.jisc.ac.uk) Home > Advisory services > Multi-site Connectivity Advisory Service > Technical guides > Secure Virtual Private Networks > SSL VPN Configuration
ASA/PIX 8.x: Radius Authorization (ACS 4.x) for VPN Access using Downloadable ACL with CLI and ASDM Configuration Example
 ASA/PIX 8.x: Radius Authorization (ACS 4.x) for VPN Access using Downloadable ACL with CLI and ASDM Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products
ASA/PIX 8.x: Radius Authorization (ACS 4.x) for VPN Access using Downloadable ACL with CLI and ASDM Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products
co Configuring PIX to Router Dynamic to Static IPSec with
 co Configuring PIX to Router Dynamic to Static IPSec with Table of Contents Configuring PIX to Router Dynamic to Static IPSec with NAT...1 Introduction...1 Configure...1 Components Used...1 Network Diagram...1
co Configuring PIX to Router Dynamic to Static IPSec with Table of Contents Configuring PIX to Router Dynamic to Static IPSec with NAT...1 Introduction...1 Configure...1 Components Used...1 Network Diagram...1
Permitting PPTP Connections Through the PIX/ASA
 Permitting PPTP Connections Through the PIX/ASA Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions PPTP with the Client Inside and the Server Outside Network
Permitting PPTP Connections Through the PIX/ASA Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions PPTP with the Client Inside and the Server Outside Network
Virtual Private Network Setup
 This chapter provides information about virtual private network setup. Virtual Private Network, page 1 Devices Supporting VPN, page 2 Set Up VPN Feature, page 2 Complete Cisco IOS Prerequisites, page 3
This chapter provides information about virtual private network setup. Virtual Private Network, page 1 Devices Supporting VPN, page 2 Set Up VPN Feature, page 2 Complete Cisco IOS Prerequisites, page 3
Virtual private network setup
 Virtual private network setup This chapter provides information about virtual private network setup. Virtual private network, page 1 Devices supporting VPN, page 2 Set up VPN feature, page 2 Complete IOS
Virtual private network setup This chapter provides information about virtual private network setup. Virtual private network, page 1 Devices supporting VPN, page 2 Set up VPN feature, page 2 Complete IOS
This document is intended to give guidance on how to read log entries from a Cisco PIX / ASA. The specific model in this case was a PIX 501.
 1.0 Overview This document is intended to give guidance on how to read log entries from a Cisco PIX / ASA. The specific model in this case was a PIX 501. 2.0 PIX Config The following is the PIX config
1.0 Overview This document is intended to give guidance on how to read log entries from a Cisco PIX / ASA. The specific model in this case was a PIX 501. 2.0 PIX Config The following is the PIX config
Physical Topology. Logical Topology
 Physical Topology Logical Topology Please, note that the configurations given below can certainly be clean-up and tuned. Some commands are still embedded for testing purposes. Note also that the text highlighted
Physical Topology Logical Topology Please, note that the configurations given below can certainly be clean-up and tuned. Some commands are still embedded for testing purposes. Note also that the text highlighted
Firewalling Avid ISIS in a Cisco environment
 Firewalling Avid ISIS in a Cisco environment Interoperability testing between Cisco ASA and ISIS results Francesca Martucci Consulting System Engineer for Security - Cisco David Shephard - Senior Network
Firewalling Avid ISIS in a Cisco environment Interoperability testing between Cisco ASA and ISIS results Francesca Martucci Consulting System Engineer for Security - Cisco David Shephard - Senior Network
PIX/ASA Active/Standby Failover Configuration Example
 PIX/ASA Active/Standby Failover Configuration Example Document ID: 77809 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Active/Standby Failover Active/Standby
PIX/ASA Active/Standby Failover Configuration Example Document ID: 77809 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Active/Standby Failover Active/Standby
How to Configure the Cisco VPN Client to PIX with AES
 How to Configure the Cisco VPN Client to PIX with AES Document ID: 42761 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configurations Network Diagram
How to Configure the Cisco VPN Client to PIX with AES Document ID: 42761 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configurations Network Diagram
PIX/ASA 7.x and Later : Easy VPN with Split Tunneling ASA 5500 as the Server and Cisco 871 as the Easy VPN Remote Configuration Example
 PIX/ASA 7.x and Later : Easy VPN with Split Tunneling ASA 5500 as the Server and Cisco 871 as the Easy VPN Remote Configuration Example Document ID: 68815 Contents Introduction Prerequisites Requirements
PIX/ASA 7.x and Later : Easy VPN with Split Tunneling ASA 5500 as the Server and Cisco 871 as the Easy VPN Remote Configuration Example Document ID: 68815 Contents Introduction Prerequisites Requirements
ASA/PIX 8.x: Block Certain Websites (URLs) Using Regular Expressions With MPF Configuration Example
 ASA/PIX 8.x: Block Certain Websites (URLs) Using Regular Expressions With MPF Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Background
ASA/PIX 8.x: Block Certain Websites (URLs) Using Regular Expressions With MPF Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Background
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM
 Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Lab Configure and Test Advanced Protocol Handling on the Cisco PIX Security Appliance
 Lab 9.4.10 Configure and Test Advanced Protocol Handling on the Cisco PIX Security Appliance Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Display the
Lab 9.4.10 Configure and Test Advanced Protocol Handling on the Cisco PIX Security Appliance Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Display the
Cisco Meraki EMM Integration with Cisco Identity Service Engine. Secure Access How -To Guides Series
 Cisco Meraki EMM Integration with Cisco Identity Service Engine Secure Access How -To Guides Series Author: Imran Bashir Date: March 2015 Table of Contents Mobile Device Management (MDM)... 3 Overview...
Cisco Meraki EMM Integration with Cisco Identity Service Engine Secure Access How -To Guides Series Author: Imran Bashir Date: March 2015 Table of Contents Mobile Device Management (MDM)... 3 Overview...
FTD: How to enable TCP State Bypass Configuration using FlexConfig Policy
 FTD: How to enable TCP State Bypass Configuration using FlexConfig Policy Contents Introduction Prerequisites Requirements Components Used Background Information Configuration Step 1. Configure an Extended
FTD: How to enable TCP State Bypass Configuration using FlexConfig Policy Contents Introduction Prerequisites Requirements Components Used Background Information Configuration Step 1. Configure an Extended
Configure AnyConnect Secure Mobility Client using One-Time Password (OTP) for Twofactor Authentication on an ASA
 Configure AnyConnect Secure Mobility Client using One-Time Password (OTP) for Twofactor Authentication on an ASA Contents Introduction Prerequisites Requirements Components Used Background Information
Configure AnyConnect Secure Mobility Client using One-Time Password (OTP) for Twofactor Authentication on an ASA Contents Introduction Prerequisites Requirements Components Used Background Information
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Contents. Introduction. Prerequisites. Requirements. Components Used
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram ASA ISE Step 1. Configure Network Device Step 2. Configure Posture conditions and policies Step 3. Configure Client
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram ASA ISE Step 1. Configure Network Device Step 2. Configure Posture conditions and policies Step 3. Configure Client
Chapter 9 Lab A: Configuring ASA Basic Settings and Firewall Using CLI
 A: Configuring ASA Basic Settings and Firewall Using CLI This lab has been updated for use on NETLAB+ Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2018
A: Configuring ASA Basic Settings and Firewall Using CLI This lab has been updated for use on NETLAB+ Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2018
Fundamentals of Network Security v1.1 Scope and Sequence
 Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Cisco Secure Desktop (CSD) on IOS Configuration Example using SDM
 Cisco Secure Desktop (CSD) on IOS Configuration Example using SDM Document ID: 70791 Contents Introduction Prerequisites Requirements Components Used Network Diagram Related Products Conventions Configure
Cisco Secure Desktop (CSD) on IOS Configuration Example using SDM Document ID: 70791 Contents Introduction Prerequisites Requirements Components Used Network Diagram Related Products Conventions Configure
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
upgrade-mp through xlate-bypass Commands
 CHAPTER 33 upgrade-mp To upgrade the maintenance partition software, use the upgrade-mp command. upgrade-mp {http[s]://[user:password@]server[:port]/pathname tftp[://server/pathname]} tftp http[s] server
CHAPTER 33 upgrade-mp To upgrade the maintenance partition software, use the upgrade-mp command. upgrade-mp {http[s]://[user:password@]server[:port]/pathname tftp[://server/pathname]} tftp http[s] server
Router Allows VPN Clients to Connect IPsec and Internet Using Split Tunneling Configuration Example
 Router Allows VPN Clients to Connect IPsec and Internet Using Split Tunneling Configuration Example Document ID: 91193 Contents Introduction Prerequisites Requirements Components Used Conventions Background
Router Allows VPN Clients to Connect IPsec and Internet Using Split Tunneling Configuration Example Document ID: 91193 Contents Introduction Prerequisites Requirements Components Used Conventions Background
Remote Access VPN. Remote Access VPN Overview. Licensing Requirements for Remote Access VPN
 Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a laptop or desktop computer connected to the Internet. This allows mobile workers
Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a laptop or desktop computer connected to the Internet. This allows mobile workers
Logging. About Logging. This chapter describes how to log system messages and use them for troubleshooting.
 This chapter describes how to log system messages and use them for troubleshooting. About, page 1 Guidelines for, page 7 Configure, page 8 Monitoring the Logs, page 26 History for, page 29 About System
This chapter describes how to log system messages and use them for troubleshooting. About, page 1 Guidelines for, page 7 Configure, page 8 Monitoring the Logs, page 26 History for, page 29 About System
Chapter 9 Lab A: Configuring ASA Basic Settings and Firewall Using CLI
 A: Configuring ASA Basic Settings and Firewall Using CLI Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2015 Cisco and/or its affiliates. All rights reserved.
A: Configuring ASA Basic Settings and Firewall Using CLI Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2015 Cisco and/or its affiliates. All rights reserved.
Secure ACS Database Replication Configuration Example
 Secure ACS Database Replication Configuration Example Document ID: 71320 Introduction Prerequisites Requirements Components Used Related Products Conventions Background Information Scenario I Scenario
Secure ACS Database Replication Configuration Example Document ID: 71320 Introduction Prerequisites Requirements Components Used Related Products Conventions Background Information Scenario I Scenario
Lab 8: Firewalls ASA Firewall Device
 Lab 8: Firewalls ASA Firewall Device 8.1 Details Aim: Rich Macfarlane 2015 The aim of this lab is to investigate a Cisco ASA Firewall Device, its default traffic flows, its stateful firewalling functionality,
Lab 8: Firewalls ASA Firewall Device 8.1 Details Aim: Rich Macfarlane 2015 The aim of this lab is to investigate a Cisco ASA Firewall Device, its default traffic flows, its stateful firewalling functionality,
Exam Name: Implementing Cisco Edge Network Security Solutions
 Vendor: Cisco Exam Code: 300-206 Exam Name: Implementing Cisco Edge Network Security Solutions Version: Demo QUESTION 1 The Cisco ASA must support dynamic routing and terminating VPN traffic. Which three
Vendor: Cisco Exam Code: 300-206 Exam Name: Implementing Cisco Edge Network Security Solutions Version: Demo QUESTION 1 The Cisco ASA must support dynamic routing and terminating VPN traffic. Which three
Configuration Examples
 CHAPTER 4 Before using this chapter, be sure that you have planned your site s security policy, as described in Chapter 1, Introduction, and configured the PIX Firewall, as described in Chapter 2, Configuring
CHAPTER 4 Before using this chapter, be sure that you have planned your site s security policy, as described in Chapter 1, Introduction, and configured the PIX Firewall, as described in Chapter 2, Configuring
Configuration Professional: Site to Site IPsec VPN Between Two IOS Routers Configuration Example
 Configuration Professional: Site to Site IPsec VPN Between Two IOS Routers Configuration Example Document ID: 113337 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration
Configuration Professional: Site to Site IPsec VPN Between Two IOS Routers Configuration Example Document ID: 113337 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration
Configuring Group Policies
 CHAPTER 2 This chapter describes how to configure VPN group policies using ASDM. This chapter includes the following sections. Overview of Group Policies, Tunnel Groups, and Users, page 2-1 Group Policies,
CHAPTER 2 This chapter describes how to configure VPN group policies using ASDM. This chapter includes the following sections. Overview of Group Policies, Tunnel Groups, and Users, page 2-1 Group Policies,
ASA/PIX: Configure Active/Standby Failover in Transparent Mode Contents
 ASA/PIX: Configure Active/Standby Failover in Transparent Mode Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Active/Standby Failover Active/Standby Failover
ASA/PIX: Configure Active/Standby Failover in Transparent Mode Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Active/Standby Failover Active/Standby Failover
VPN Client. VPN Client Overview. VPN Client Prerequisites. VPN Client Configuration Task Flow. Before You Begin
 Overview, page 1 Prerequisites, page 1 Configuration Task Flow, page 1 Overview The Cisco for Cisco Unified IP Phones creates a secure VPN connection for employees who telecommute. All settings of the
Overview, page 1 Prerequisites, page 1 Configuration Task Flow, page 1 Overview The Cisco for Cisco Unified IP Phones creates a secure VPN connection for employees who telecommute. All settings of the
PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands
 PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands Document ID: 63872 Introduction Prerequisites Requirements Components Used Related Products Conventions Network
PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands Document ID: 63872 Introduction Prerequisites Requirements Components Used Related Products Conventions Network
ASA Cluster for the Firepower 9300 Chassis
 Clustering lets you group multiple Firepower 9300 chassis ASAs together as a single logical device. The Firepower 9300 chassis series includes the Firepower 9300. A cluster provides all the convenience
Clustering lets you group multiple Firepower 9300 chassis ASAs together as a single logical device. The Firepower 9300 chassis series includes the Firepower 9300. A cluster provides all the convenience
Remote Access IPsec VPNs
 About, on page 1 Licensing Requirements for for 3.1, on page 3 Restrictions for IPsec VPN, on page 4 Configure, on page 4 Configuration Examples for, on page 11 Configuration Examples for Standards-Based
About, on page 1 Licensing Requirements for for 3.1, on page 3 Restrictions for IPsec VPN, on page 4 Configure, on page 4 Configuration Examples for, on page 11 Configuration Examples for Standards-Based
CISCO EXAM QUESTIONS & ANSWERS
 CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
ASA Cluster for the Firepower 9300 Chassis
 Clustering lets you group multiple Firepower 9300 chassis ASAs together as a single logical device. The Firepower 9300 chassis series includes the Firepower 9300. A cluster provides all the convenience
Clustering lets you group multiple Firepower 9300 chassis ASAs together as a single logical device. The Firepower 9300 chassis series includes the Firepower 9300. A cluster provides all the convenience
Cisco Secure PIX Firewall Advanced (CSPFA)
 9E0-571 9E0-571 Cisco Secure PIX Firewall Advanced (CSPFA) Version 3.0-1 - Important Note Please Read Carefully Study Tips This product will provide you questions and answers along with detailed explanations
9E0-571 9E0-571 Cisco Secure PIX Firewall Advanced (CSPFA) Version 3.0-1 - Important Note Please Read Carefully Study Tips This product will provide you questions and answers along with detailed explanations
Applying Application Layer Protocol Inspection
 CHAPTER 21 This chapter describes how to configure application layer protocol inspection. Inspection engines are required for services that embed IP addressing information in the user data packet or that
CHAPTER 21 This chapter describes how to configure application layer protocol inspection. Inspection engines are required for services that embed IP addressing information in the user data packet or that
Remote Access IPsec VPNs
 About, page 1 Licensing Requirements for for 3.1, page 2 Restrictions for IPsec VPN, page 3 Configure, page 3 Configuration Examples for, page 10 Configuration Examples for Standards-Based IPSec IKEv2
About, page 1 Licensing Requirements for for 3.1, page 2 Restrictions for IPsec VPN, page 3 Configure, page 3 Configuration Examples for, page 10 Configuration Examples for Standards-Based IPSec IKEv2
LAN to LAN IPsec Tunnel Between a Cisco VPN 3000 Concentrator and Router with AES Configuration Example
 LAN to LAN IPsec Tunnel Between a Cisco VPN 3000 Concentrator and Router with AES Configuration Example Document ID: 26402 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
LAN to LAN IPsec Tunnel Between a Cisco VPN 3000 Concentrator and Router with AES Configuration Example Document ID: 26402 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Configuring Management Access
 37 CHAPTER This chapter describes how to access the ASA for system management through Telnet, SSH, and HTTPS (using ASDM), how to authenticate and authorize users, how to create login banners, and how
37 CHAPTER This chapter describes how to access the ASA for system management through Telnet, SSH, and HTTPS (using ASDM), how to authenticate and authorize users, how to create login banners, and how
Three interface Router without NAT Cisco IOS Firewall Configuration
 Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Network Address Translation (NAT)
 The following topics explain and how to configure it. Why Use NAT?, page 1 NAT Basics, page 2 Guidelines for NAT, page 8 Configure NAT, page 12 Translating IPv6 Networks, page 40 Monitoring NAT, page 51
The following topics explain and how to configure it. Why Use NAT?, page 1 NAT Basics, page 2 Guidelines for NAT, page 8 Configure NAT, page 12 Translating IPv6 Networks, page 40 Monitoring NAT, page 51
This chapter covers the following exam topics for the Secure PIX Firewall Advanced Exam (CSPFA 9E0-511): 5. User interface 6. Configuring the PIX
 This chapter covers the following exam topics for the Secure PIX Firewall Advanced Exam (CSPFA 9E0-511): 5. User interface 6. Configuring the PIX Firewall 8. Time setting and NTP support 13. DHCP server
This chapter covers the following exam topics for the Secure PIX Firewall Advanced Exam (CSPFA 9E0-511): 5. User interface 6. Configuring the PIX Firewall 8. Time setting and NTP support 13. DHCP server
IOS Router : Easy VPN (EzVPN) in Network Extension Mode (NEM) with Split tunnelling Configuration Example
 IOS Router : Easy VPN (EzVPN) in Network Extension Mode (NEM) with Split tunnelling Configuration Example Document ID: 63098 Contents Introduction Prerequisites Requirements Components Used Conventions
IOS Router : Easy VPN (EzVPN) in Network Extension Mode (NEM) with Split tunnelling Configuration Example Document ID: 63098 Contents Introduction Prerequisites Requirements Components Used Conventions
Migrating to the Cisco ASA Services Module from the FWSM
 Migrating to the Cisco ASA Services Module from the FWSM Contents Information About the Migration, page 1 Migrating the FWSM Configuration to the ASA SM, page 2 Unsupported Runtime Commands, page 4 Configuration
Migrating to the Cisco ASA Services Module from the FWSM Contents Information About the Migration, page 1 Migrating the FWSM Configuration to the ASA SM, page 2 Unsupported Runtime Commands, page 4 Configuration
SSL VPN - IPv6 Support
 The feature implements support for IPv6 transport over IPv4 SSL VPN session between a client, such as Cisco AnyConnect Mobility Client, and SSL VPN. Finding Feature Information, on page 1 Prerequisites
The feature implements support for IPv6 transport over IPv4 SSL VPN session between a client, such as Cisco AnyConnect Mobility Client, and SSL VPN. Finding Feature Information, on page 1 Prerequisites
SSL VPN - IPv6 Support
 The feature implements support for IPv6 transport over IPv4 SSL VPN session between a client, such as Cisco AnyConnect Mobility Client, and SSL VPN. Finding Feature Information, page 1 Prerequisites for,
The feature implements support for IPv6 transport over IPv4 SSL VPN session between a client, such as Cisco AnyConnect Mobility Client, and SSL VPN. Finding Feature Information, page 1 Prerequisites for,
Setting General VPN Parameters
 CHAPTER 62 The adaptive security appliance implementation of virtual private networking includes useful features that do not fit neatly into categories. This chapter describes some of these features. It
CHAPTER 62 The adaptive security appliance implementation of virtual private networking includes useful features that do not fit neatly into categories. This chapter describes some of these features. It
Configuring AnyConnect VPN Client Connections
 CHAPTER 72 This section describes how to configure AnyConnect VPN Client Connections and covers the following topics: Information About AnyConnect VPN Client Connections, page 72-1 Licensing Requirements
CHAPTER 72 This section describes how to configure AnyConnect VPN Client Connections and covers the following topics: Information About AnyConnect VPN Client Connections, page 72-1 Licensing Requirements
VPN Connection through Zone based Firewall Router Configuration Example
 VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
Configuring AnyConnect VPN Client Connections
 CHAPTER 71 This chapter describes how to configure AnyConnect VPN Client Connections and includes the following topics: Information About AnyConnect VPN Client Connections, page 71-1 Licensing Requirements
CHAPTER 71 This chapter describes how to configure AnyConnect VPN Client Connections and includes the following topics: Information About AnyConnect VPN Client Connections, page 71-1 Licensing Requirements
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM
 Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
On completion of this chapter, you will be able to perform the following tasks: Describe the PIX Device Manager (PDM) and its capabilities.
 On completion of this chapter, you will be able to perform the following tasks: Describe the PIX Device Manager (PDM) and its capabilities. Describe PDM s browser and PIX Firewall requirements. Install
On completion of this chapter, you will be able to perform the following tasks: Describe the PIX Device Manager (PDM) and its capabilities. Describe PDM s browser and PIX Firewall requirements. Install
Platform Settings for Firepower Threat Defense
 Platform settings for devices configure a range of unrelated features whose values you might want to share among several devices. Even if you want different settings per device, you must create a shared
Platform settings for devices configure a range of unrelated features whose values you might want to share among several devices. Even if you want different settings per device, you must create a shared
Use NAT to Hide the Real IP Address of CTC to Establish a Session with ONS 15454
 Use NAT to Hide the Real IP Address of CTC to Establish a Session with ONS 15454 Document ID: 65122 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Topology
Use NAT to Hide the Real IP Address of CTC to Establish a Session with ONS 15454 Document ID: 65122 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Topology
VPN Configuration Guide. Cisco ASA 5500 Series
 VPN Configuration Guide Cisco ASA 5500 Series 2015 equinux AG and equinux USA, Inc. All rights reserved. Under copyright law, this configuration guide may not be copied, in whole or in part, without the
VPN Configuration Guide Cisco ASA 5500 Series 2015 equinux AG and equinux USA, Inc. All rights reserved. Under copyright law, this configuration guide may not be copied, in whole or in part, without the
Configuring PIX 5.1.x: TACACS+ and RADIUS
 Configuring PIX 5.1.x: TACACS+ and RADIUS Document ID: 4613 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Authentication vs. Authorization What the
Configuring PIX 5.1.x: TACACS+ and RADIUS Document ID: 4613 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Authentication vs. Authorization What the
Using NAT in Overlapping Networks
 Using NAT in Overlapping Networks Document ID: 13774 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Related Information
Using NAT in Overlapping Networks Document ID: 13774 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Related Information
gateway through hw-module module shutdown Commands
 CHAPTER 12 gateway through hw-module module shutdown Commands 12-1 gateway gateway To specify which group of call agents are managing a particular gateway, use the gateway command in MGCP map configuration
CHAPTER 12 gateway through hw-module module shutdown Commands 12-1 gateway gateway To specify which group of call agents are managing a particular gateway, use the gateway command in MGCP map configuration
Command Reference for Firepower Threat Defense 1
 t-z tail-logs, page 2 test aaa-server, page 4 traceroute, page 6 undebug, page 9 verify, page 11 vpn-sessiondb logoff, page 15 write net, page 16 write terminal, page 17 1 tail-logs t - z tail-logs To
t-z tail-logs, page 2 test aaa-server, page 4 traceroute, page 6 undebug, page 9 verify, page 11 vpn-sessiondb logoff, page 15 write net, page 16 write terminal, page 17 1 tail-logs t - z tail-logs To
Cisco CISCO Securing Networks with ASA Advanced. Practice Test. Version
 Cisco 642-515 CISCO 642-515 Securing Networks with ASA Advanced Practice Test Version 3.1 QUESTION NO: 1 Cisco 642-515: Practice Exam Which two statements correctly describe configuring active/active failover?
Cisco 642-515 CISCO 642-515 Securing Networks with ASA Advanced Practice Test Version 3.1 QUESTION NO: 1 Cisco 642-515: Practice Exam Which two statements correctly describe configuring active/active failover?
shun through sysopt radius ignore-secret Commands
 CHAPTER 30 shun through sysopt radius ignore-secret Commands 30-1 shun Chapter 30 shun To block connections from an attacking host, use the shun command in privileged EXEC mode. To disable a shun, use
CHAPTER 30 shun through sysopt radius ignore-secret Commands 30-1 shun Chapter 30 shun To block connections from an attacking host, use the shun command in privileged EXEC mode. To disable a shun, use
Multiple Context Mode
 This chapter describes how to configure multiple security contexts on the Cisco ASA. About Security Contexts, page 1 Licensing for, page 12 Prerequisites for, page 13 Guidelines for, page 14 Defaults for,
This chapter describes how to configure multiple security contexts on the Cisco ASA. About Security Contexts, page 1 Licensing for, page 12 Prerequisites for, page 13 Guidelines for, page 14 Defaults for,
Configuring the Cisco VPN 3000 Concentrator with MS RADIUS
 Configuring the Cisco VPN 3000 Concentrator with MS RADIUS Document ID: 20585 Contents Introduction Prerequisites Requirements Components Used Conventions Install and Configure the RADIUS Server on Windows
Configuring the Cisco VPN 3000 Concentrator with MS RADIUS Document ID: 20585 Contents Introduction Prerequisites Requirements Components Used Conventions Install and Configure the RADIUS Server on Windows
ASA Clientless SSL VPN (WebVPN) Troubleshooting Tech Note
 ASA Clientless SSL VPN (WebVPN) Troubleshooting Tech Note Document ID: 104298 Contents Introduction Prerequisites Requirements Components Used Conventions Troubleshooting ASA Version 7.1/7.2 Clientless
ASA Clientless SSL VPN (WebVPN) Troubleshooting Tech Note Document ID: 104298 Contents Introduction Prerequisites Requirements Components Used Conventions Troubleshooting ASA Version 7.1/7.2 Clientless
ASA Remote Access VPN IKE/SSL Password Expiry and Change for RADIUS, TACACS, and LDAP Configuration Example
 ASA Remote Access VPN IKE/SSL Password Expiry and Change for RADIUS, TACACS, and LDAP Configuration Example Document ID: 116757 Contributed by Michal Garcarz, Cisco TAC Engineer. Nov 25, 2013 Contents
ASA Remote Access VPN IKE/SSL Password Expiry and Change for RADIUS, TACACS, and LDAP Configuration Example Document ID: 116757 Contributed by Michal Garcarz, Cisco TAC Engineer. Nov 25, 2013 Contents
Remote Access VPN. Remote Access VPN Overview. Maximum Concurrent VPN Sessions By Device Model
 Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a computer or other supported ios or Android device connected to the Internet.
Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a computer or other supported ios or Android device connected to the Internet.
Getting Started. About the ASA for Firepower How the ASA Works with the Firepower 2100
 This chapter describes how to deploy the ASA on the Firepower 2100 in your network, and how to perform initial configuration. About the ASA for Firepower 2100, page 1 Connect the Interfaces, page 4 Power
This chapter describes how to deploy the ASA on the Firepower 2100 in your network, and how to perform initial configuration. About the ASA for Firepower 2100, page 1 Connect the Interfaces, page 4 Power
ASACAMP - ASA Lab Camp (5316)
 ASACAMP - ASA Lab Camp (5316) Price: $4,595 Cisco Course v1.0 Cisco Security Appliance Software v8.0 Based on our enhanced FIREWALL and VPN courses, this exclusive, lab-based course is designed to provide
ASACAMP - ASA Lab Camp (5316) Price: $4,595 Cisco Course v1.0 Cisco Security Appliance Software v8.0 Based on our enhanced FIREWALL and VPN courses, this exclusive, lab-based course is designed to provide
ASA/PIX: Allow Split Tunneling for VPN Clients on the ASA Configuration Example
 ASA/PIX: Allow Split Tunneling for VPN Clients on the ASA Configuration Example Contents Introduction Prerequisites Requirements Components Used Network Diagram Related Products Conventions Background
ASA/PIX: Allow Split Tunneling for VPN Clients on the ASA Configuration Example Contents Introduction Prerequisites Requirements Components Used Network Diagram Related Products Conventions Background
NAT Support for Multiple Pools Using Route Maps
 NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
This study aid describes the purpose of security contexts and explains how to enable, configure, and manage multiple contexts.
 Configuring Security Contexts Created by Bob Eckhoff This study aid describes the purpose of security contexts and explains how to enable, configure, and manage multiple contexts. Security Context Overview
Configuring Security Contexts Created by Bob Eckhoff This study aid describes the purpose of security contexts and explains how to enable, configure, and manage multiple contexts. Security Context Overview
Cisco PIX. Interoperability Guide
 Cisco PIX Interoperability Guide Copyright 2004, F/X Communications. All Rights Reserved. The use and copying of this product is subject to a license agreement. Any other use is strictly prohibited. No
Cisco PIX Interoperability Guide Copyright 2004, F/X Communications. All Rights Reserved. The use and copying of this product is subject to a license agreement. Any other use is strictly prohibited. No
Wireless LAN Controller and IPS Integration Guide
 Wireless LAN Controller and IPS Integration Guide Document ID: 71231 Contents Introduction Prerequisites Requirements Components Used Conventions Cisco IDS Overview Cisco IDS and WLC Integration Overview
Wireless LAN Controller and IPS Integration Guide Document ID: 71231 Contents Introduction Prerequisites Requirements Components Used Conventions Cisco IDS Overview Cisco IDS and WLC Integration Overview
