FWSM: Multiple Context Configuration Example
|
|
|
- Phyllis Russell
- 6 years ago
- Views:
Transcription
1 FWSM: Multiple Context Configuration Example Document ID: Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Context Configuration Files Unsupported Features Management Access to Security Contexts Configure Network Diagram Enabling or Disabling Multiple Context Mode Configure a Security Context FWSM: System Execution Space Configuration Change Between Contexts and the System Execution Space FWSM ContextA Configuration FWSM ContextB Configuration Save Configuration Changes in Multiple Context Mode Verify Troubleshoot Restore Single Context Mode Reload a Security Context Rename the Context Delete Context Related Information Introduction This document describes the steps used to configure multiple context in Firewall Service Module (FWSM). You can partition a single FWSM into multiple virtual devices, known as security contexts. Each context has its own security policy, interfaces, and administrators. Multiple contexts are similar to multiple standalone devices. Many features are supported in multiple context mode, which includes routing tables, firewall features, and management. Some features are not supported, which includes dynamic routing protocols. You can use multiple security contexts in these situations: You are a service provider and want to sell security services to many customers. When you enable multiple security contexts on the FWSM, you can implement a cost effective, space saving solution that keeps all customer traffic separate and secure, and also eases configuration. You are a large enterprise or a college campus and want to keep departments completely separate. You are an enterprise that wants to provide distinct security policies to different departments. You have any network that requires more than one firewall. Refer to PIX/ASA 7.x and Above: Multiple Context Configuration Example for more information on how to describe the steps used to configure multiple context in security appliances.
2 Prerequisites Requirements There are no specific requirements for this document. Components Used The information in this document is based on the Firewall Service Module (FWSM) that runs software version 3.2(5). The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command. Conventions Refer to the Cisco Technical Tips Conventions for more information on document conventions. Background Information Context Configuration Files Context Configurations The FWSM includes a configuration for each context that identifies the security policy, interfaces, and almost all the options you can configure on a standalone device. You can store context configurations on the internal Flash memory or the external Flash memory card, or you can download them from a TFTP, FTP, or HTTP(S) server. System Configuration The system administrator adds and manages contexts with the configuration of each context configuration location, allocated interfaces, and other context operating parameters in the system configuration, which, like a single mode configuration, is the startup configuration. The system configuration identifies basic settings for the FWSM. The system configuration does not include any network interfaces or network settings for itself; rather, when the system needs to access network resources, such as downloading the contexts from the server, it uses one of the contexts that is designated as the admin context. The system configuration does include a specialized failover interface for failover traffic only. Admin Context Configuration The admin context is just like any other context, except that when you log in to the admin context, then you have system administrator rights and can access the system and all other contexts. The admin context is not restricted in any way, and can be used as a regular context. But, because logging into the admin context grants you administrator privileges over all contexts, you can possibly need to restrict access to the admin context to appropriate users. The admin context must reside on Flash memory, and not remotely. If your system is already in multiple context mode, or if you convert from single mode, the admin context is created automatically as a file on the internal Flash memory called admin.cfg. This context is named admin. If you do not want to use admin.cfg as the admin context, you can change the admin context.
3 Unsupported Features Multiple context mode does not support these features: Dynamic routing protocols Security contexts support only static routes. You cannot enable OSPF or RIP in multiple context mode. Multicast Management Access to Security Contexts The FWSM provides system administrator access in multiple context mode as well as access for individual context administrators. These sections describe logging in as a system administrator or as a a context administrator: System Administrator Access You can access the FWSM as a system administrator in two ways: Session to the FWSM from the switch. From the switch, you access the system execution space. Access the admin context using Telnet, SSH, or ASDM. Refer to Configuring Management Access for more information on how to enable Telnet, SSH, and SDM access. As the system administrator, you can access all contexts. When you change to a context from admin or the system, your username changes to the default enable_15" username. If you configured command authorization in that context, you need to either configure authorization privileges for the enable_15 user, or you can log in as a different name for which you provide sufficient privileges in the command authorization configuration for the context. Enter the login command in order to log in with a username. For example, you log in to the admin context with the username admin. The admin context does not have any command authorization configuration, but all other contexts include command authorization. For convenience, each context configuration includes a user admin with maximum privileges. When you change from the admin context to context A, your username is altered, so you must log in again as admin when you enter the login command. When you change to context B, you must again enter the login command to log in as admin. The system execution space does not support any AAA commands, but you can configure its own enable password, as well as usernames in the local database, in order to provide individual logins. Context Administrator Access You can access a context with Telnet, SSH, or ASDM. If you log in to a non admin context, you can only access the configuration for that context. You can provide individual logins to the context. Configure In this section, you are presented with the information to configure the features described in this document.
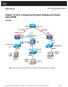
4 Note: Use the Command Lookup Tool (registered customers only) in order to obtain more information on the commands used in this section. Network Diagram This document uses this network setup: Enabling or Disabling Multiple Context Mode Your FWSM might already be configured for multiple security contexts depending on how you ordered it from Cisco. If you are upgrading, however, you might need to convert from single mode to multiple mode by following the procedures in this section. ASDM does not support changing modes, so you need to change modes using the CLI. Backing Up the Single Mode Configuration When you convert from single mode to multiple mode, the FWSM converts the running configuration into two files. The original startup configuration is not saved, so if it differs from the running configuration, you should back it up before proceeding. Enabling Multiple Context Mode The context mode (single or multiple) is not stored in the configuration file, even though it does endure reboots. If you need to copy your configuration to another device, set the mode on the new device to match with the mode command. When you convert from single mode to multiple mode, the FWSM converts the running configuration into two files:.
5 1. A new startup configuration that comprises the system configuration 2. An admin.cfg that comprises of the admin context in the root directory of the internal Flash memory The original running configuration is saved as old_running.cfg (in the root directory of the internal Flash memory). The original startup configuration is not saved. The FWSM automatically adds an entry for the admin context to the system configuration with the name "admin." Enter this command in order to enable multiple mode: hostname(config)#mode multiple You are prompted to reboot the FWSM. FWSM(config)#mode multiple WARNING: This command will change the behavior of the device WARNING: This command will initiate a Reboot Proceed with change mode? [confirm] Convert the system configuration? [confirm] The old running configuration file will be written to flash The admin context configuration will be written to flash The new running configuration file was written to flash Security context mode: multiple *** *** SHUTDOWN NOW *** *** Message to all terminals: *** *** change mode Rebooting... Booting system, please wait... * * Output suppressed * * INFO: Admin context is required to get the interfaces *** Output from config line 20, "arp timeout 14400" Creating context 'admin'... Done. (1) *** Output from config line 23, "admin context admin" Cryptochecksum (changed): a219baf3 037b31b ab9790a *** Output from config line 25, " config url flash:/admi..." Cryptochecksum (changed): d4f0451b e1 bbccf404 86be061c Type help or '?' for a list of available commands. FWSM> After reboot, this is the default configuration of the FWSM: FWSM Default Configuration
6 FWSM#show running config : Saved : FWSM Version 3.2(5)5 <system> resource acl partition 12 hostname FWSM domain name default.domain.invalid enable password 8Ry2YjIyt7RRXU24 encrypted interface Vlan501 interface Vlan502 passwd 2KFQnbNIdI.2KYOU encrypted class default limit resource IPSec 5 limit resource Mac addresses limit resource ASDM 5 limit resource SSH 5 limit resource Telnet 5 limit resource All 0 ftp mode passive gdb enable pager lines 24 no failover no asdm history enable arp timeout console timeout 0 admin context admin context admin allocate interface Vlan501 allocate interface Vlan502 config url disk:/admin.cfg admin context is created by default once you enable multiple mode prompt hostname context Cryptochecksum:d62411d2a15f1da35c76fe071b61dcdb : end FWSM# Configure a Security Context The security context definition in the system configuration identifies the context name, configuration file URL, interfaces that a context can use, and other context parameters. Note: If you do not have an admin context, for example, if you clear the configuration, you must first specify the admin context name when you enter this command:. hostname(config)#admin context <name> Note: Although this context name does not exist yet in your configuration, you can subsequently enter the context name command in order to match the specified name to continue the admin context configuration.
7 In order to add or change a context in the system configuration, complete these steps: 1. In order to add or modify a context, enter this command in the system execution space: hostname(config)#context <name> The name is a string up to 32 characters long. This name is case sensitive, so you can have two contexts named "customera" and "CustomerA," for example. You can use letters, digits, or hyphens, but you cannot start or end the name with a hyphen. "System" or "Null" (in upper or lower case letters) are reserved names, and cannot be used. 2. (Optional) In order to add a description for this context, enter this command: hostname(config ctx)#description text 3. In order to specify the interfaces you can use in the context, enter this command: hostname(config ctx)#allocate interface vlannumber[ vlannumber] [map_name[ map_name] [invisible visible]] You can enter this command multiple times in order to specify different ranges. If you remove an allocation with the no form of this command, then any context commands that include this interface are removed from the running configuration. Enter a VLAN number or a range of VLANs, typically from 2 to 1000 and from 1025 to See the switch documentation for supported VLANs. Use the show vlan command in order to see a list of VLANs assigned to the FWSM. You can allocate a VLAN that is not yet assigned to the FWSM, but you need to assign them from the switch if you want them to pass traffic. When you allocate an interface, the FWSM automatically adds the interface command for each VLAN in the system configuration. 4. Enter this command in order to identify the URL from which the system downloads the context configuration: hostname(config ctx)#config url url When you add a context URL, the system immediately loads the context so that it is running, if the configuration is available. Note: Enter the allocate interface command(s) before you enter the config url command. The FWSM must assign interfaces to the context before it loads the context configuration; the context configuration can possibly include commands that refer to interfaces, for example, interface, nat, global and so forth. If you enter the config url command first, the FWSM loads the context configuration immediately. If the context contains any commands that refer to interfaces, those commands fail. In this scenario, complete the steps in the table in order to configure the multiple context. There are two customers, Customer A and Customer B. Create three multiple contexts (virtually three FWSMs ) in a single FWSM module such as Context A for Customer A, Context B for Customer B, and Admin Context to administrate the FWSM contexts. Note: Create VLANs 300, 301, 400, 401, 500 and 501 in the Catalyst 6500 Series Switch before you use it in the FWSM.
8 Create the contexts in the system execution space and allocate the respective VLAN's to the each created context and configure the URL path for every context as shown. FWSM Multiple Context Configuration Steps FWSM(config)#context admin FWSM(config ctx)#allocate interface VLAN500 FWSM(config ctx)#allocate interface VLAN501 FWSM(config ctx)#config url disk:/admin.cfg Allocate VLAN 500 and 501 to admin context FWSM(config)#context contexta Customer A Context as Context A FWSM(config ctx)#allocate interface VLAN300 FWSM(config ctx)#allocate interface VLAN301 Allocate VLAN 300 and 301 to admin context FWSM(config ctx)#config url disk:/contexta.cfg WARNING: Could not fetch the URL disk:/contexta.cfg INFO: Creating context with default config To identify the URL from which the system downloads the context configuration. FWSM(config ctx)#context contextb Creating context 'contextb'... Done. (3) Customer B Context as Context B FWSM(config ctx)#allocate interface VLAN400 FWSM(config ctx)#allocate interface VLAN401 Allocate VLAN 400 and 401 to admin context FWSM(config ctx)#config url disk:/contextb.cfg WARNING: Could not fetch the URL disk:/contextb.cfg INFO: Creating context with default config FWSM(config ctx)#exit FWSM: System Execution Space Configuration FWSM System Execution Space Configuration FWSM(config)#show running config : Saved : FWSM Version 3.2(5)5 <system>
9 resource acl partition 12 hostname FWSM domain name default.domain.invalid enable password 8Ry2YjIyt7RRXU24 encrypted interface Vlan300 interface Vlan301 interface Vlan400 interface Vlan401 interface Vlan501 interface Vlan502 passwd 2KFQnbNIdI.2KYOU encrypted class default limit resource IPSec 5 limit resource Mac addresses limit resource ASDM 5 limit resource SSH 5 limit resource Telnet 5 limit resource All 0 ftp mode passive gdb enable pager lines 24 no failover no asdm history enable arp timeout console timeout 0 admin context admin context admin allocate interface Vlan501 allocate interface Vlan502 config url disk:/admin.cfg context contexta allocate interface Vlan300 allocate interface Vlan301 config url disk:/contexta.cfg context contextb allocate interface Vlan400 allocate interface Vlan401 config url disk:/contextb.cfg prompt hostname context Cryptochecksum:d62411d2a15f1da35c76fe071b61dcdb : end FWSM# Change Between Contexts and the System Execution Space If you log in to the system execution space (or the admin context using Telnet or SSH), you can change between contexts and perform configuration and monitoring tasks within each context. The running configuration that you edit in a configuration mode, or that is affected by the copy or write commands,
10 depends on your location. When you are in the system execution space, the running configuration consists only of the system configuration; when you are in a context, the running configuration consists only of that context. For example, you cannot view all running configurations (system plus all contexts) if you enter the show running config command. Only the current configuration displays. You can, however, save all context running configurations from the system execution space if you use the write memory all command. In order to change between the system execution space and a context, or between contexts, see these commands: In order to change to a context, enter this command: hostname#changeto context <context name> The prompt changes to this: hostname/name# In order to change to the system execution space, enter this command hostname/admin#changeto system The prompt changes to this: hostname# FWSM ContextA Configuration In order to configure the contexta, change to the contexta and follow the procedure: From the system execution space, enter the changeto context contexta command in order to configure the contexta configuration. FWSM(config)#changeto context contexta FWSM/context1(config)# FWSM ContextA Default Configuration FWSM/contextA(config)#show running config Default configuration of the context1 : Saved : FWSM Version 3.2(5)5 <context> hostname contexta enable password 8Ry2YjIyt7RRXU24 encrypted names interface Vlan300 no nameif no security level no ip address interface Vlan301 no nameif
11 no security level no ip address passwd 2KFQnbNIdI.2KYOU encrypted gdb enable pager lines 24 mtu inside 1500 mtu outside 1500 no asdm history enable arp timeout timeout xlate 3:00:00 timeout conn 1:00:00 half closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 1:00:00 h225 1:00:00 mgcp 0:05:00 timeout mgcp pat 0:05:00 sip 0:30:00 sip_media 0:02:00 timeout sip invite 0:03:00 sip disconnect 0:02:00 timeout uauth 0:05:00 absolute no snmp server location no snmp server contact telnet timeout 5 ssh timeout 5 class map inspection_default match default inspection traffic policy map global_policy class inspection_default inspect dns maximum length 512 inspect ftp inspect h323 h225 inspect h323 ras inspect netbios inspect rsh inspect skinny inspect smtp inspect sqlnet inspect sunrpc inspect tftp inspect sip inspect xdmcp service policy global_policy global Cryptochecksum: : end FWSM/contextA# no nameif no security level no ip address passwd 2KFQnbNIdI.2KYOU encrypted gdb enable pager lines 24 no asdm history enable arp timeout timeout xlate 3:00:00 timeout conn 1:00:00 half closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 1:00:00 h225 1:00:00 mgcp 0:05:00 timeout mgcp pat 0:05:00 sip 0:30:00 sip_media 0:02:00 timeout sip invite 0:03:00 sip disconnect 0:02:00 timeout uauth 0:05:00 absolute no snmp server location no snmp server contact telnet timeout 5 ssh timeout 5 class map inspection_default
12 match default inspection traffic policy map global_policy class inspection_default inspect dns maximum length 512 inspect ftp inspect h323 h225 inspect h323 ras inspect netbios inspect rsh inspect skinny inspect smtp inspect sqlnet inspect sunrpc inspect tftp inspect sip inspect xdmcp service policy global_policy global Cryptochecksum: : end Customer A Configuration for Internet connectivity. FWSM Configuration of ContextA FWSM/contextA(config)#interface vlan300 FWSM/contextA(config if)#nameif inside WARNING: VLAN *300* is not configured. INFO: Security level for "inside" set to 100 by default. Access Rules Download Complete: Memory Utilization: 1% FWSM/contextA(config if)#ip address FWSM/contextA(config if)#no shut FWSM/contextA(config if)#interface vlan 301 FWSM/contextA(config if)#nameif outside INFO: Security level for "outside" set to 0 by default. Access Rules Download Complete: Memory Utilization: 1% FWSM/contextA(config if)#ip add FWSM/contextA(config if)#no shut FWSM/contextA(config)#access list outbound permit ip any any FWSM/contextA(config)#nat (inside) 1 access list outbound FWSM/contextA(config)#global (outside) 1 interface INFO: outside interface address added to PAT pool FWSM/contextA(config)#route outside context FWSM/contextA(config)#exit FWSM ContextA Configuration FWSM/contextA#show running config : Saved : FWSM Version 3.2(5)5 <context> hostname contexta enable password 8Ry2YjIyt7RRXU24 encrypted names interface Vlan300 nameif inside security level 100 ip address
13 interface Vlan301 nameif outside security level 0 ip address passwd 2KFQnbNIdI.2KYOU encrypted access list outbound extended permit ip any any gdb enable pager lines 24 mtu inside 1500 mtu outside 1500 no asdm history enable arp timeout global (outside) 1 interface nat (inside) 1 access list outbound route outside Output Suppressed class map inspection_default match default inspection traffic policy map global_policy class inspection_default inspect dns maximum length 512 inspect ftp inspect h323 h225 inspect h323 ras inspect netbios inspect rsh inspect skinny inspect smtp inspect sqlnet inspect sunrpc inspect tftp inspect sip inspect xdmcp service policy global_policy global Cryptochecksum: : end FWSM/contextA# FWSM ContextB Configuration Customer B Configuration for Internet connectivity. In order to configure the contextb, change to contextb from contexta: From the system execution space, enter the changeto context contextb command in orderto configure the contextb configuration. FWSM/contextA(config)#changeto context contextb FWSM/contextB(config)# FWSM ContextB Configuration
14 FWSM/contextB(config)#show running config : Saved : FWSM Version 3.2(5)5 <context> hostname contextb enable password 8Ry2YjIyt7RRXU24 encrypted names interface Vlan400 nameif inside security level 100 ip address interface Vlan401 nameif outside security level 0 ip address passwd 2KFQnbNIdI.2KYOU encrypted access list outbound extended permit ip any any gdb enable pager lines 24 mtu inside 1500 mtu outside 1500 no asdm history enable arp timeout global (outside) 1 interface nat (inside) 1 access list outbound route outside Output Suppressed class map inspection_default match default inspection traffic policy map global_policy class inspection_default inspect dns maximum length 512 inspect ftp inspect h323 h225 inspect h323 ras inspect netbios inspect rsh inspect skinny inspect smtp inspect sqlnet inspect sunrpc inspect tftp inspect sip inspect xdmcp service policy global_policy global Cryptochecksum: : end FWSM/contextB(config)# Similarly configure the admin context to administrate the FWSM and its contexts from the inside and outside interface.
15 Save Configuration Changes in Multiple Context Mode You can save each context (and system) configuration separately, or you can save all context configurations at the same time. This section includes these topics: Save Each Context and System Separately In order to save the system or context configuration, enter this command within the system or context: hostname#write memory Note: The copy running config startup config command is equivalent to the write memory command. For multiple context mode, context startup configurations can reside on external servers. In this case, the security appliance saves the configuration back to the server that you identified in the context URL, except for an HTTP or HTTPS URL, which does not let you save the configuration to the server. Save All Context Configurations at the Same Time In order to save all context configurations at the same time, as well as the system configuration, enter this command in the system execution space: hostname#write memory all [/noconfirm] If you do not enter the /noconfirm keyword, you see this prompt: Verify Are you sure [Y/N]: Use this section to confirm that your configuration works properly. The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of show command output. show contextdisplays the various contexts. FWSM(config)#show context Context Name Class Interfaces Mode URL *admin default Vlan501,Vlan502 Routed disk:/admin.cfg contexta default Vlan300,Vlan301 Routed disk:/contexta.cfg contextb default Vlan400,Vlan401 Routed disk:/contextb.cfg Total active Security Contexts: 3 show modeverify that the FWSM is configured as a single or multiple mode. Troubleshoot FWSM(config)#show mode Security context mode: multiple The flash mode is the SAME as the running mode.
16 Restore Single Context Mode If you convert from multiple mode to single mode, it is possible to first copy a full startup configuration (if available) to the FWSM; the system configuration inherited from multiple mode is not a completely functional configuration for a single mode device. Because the system configuration does not have any network interfaces as part of its configuration, you must access the security appliance from the console to perform the copy. In order to copy the old running configuration to the startup configuration and to change the mode to single modecomplete these steps in the system execution space: 1. In order to copy the backup version of your original running configuration to the current startup configuration, enter this command in the system execution space: hostname(config)#copy flash:old_running.cfg startup config 2. In order to set the mode to single mode, enter this command in the system execution space: FWSM reboots. hostname(config)#mode single Reload a Security Context You can reload the context in two ways: 1. Clear the running configuration and then import the startup configuration. This action clears most attributes associated with the context, such as connections and NAT tables. 2. Remove the context from the system configuration. This action clears additional attributes, such as memory allocation, which can be useful for troubleshooting. But, in order to add the context back to the system requires you to respecify the URL and interfaces. This section includes these topics: Reloading by Clearin g the Configuration Reloading by Removing and Reading the Context Rename the Context In multiple context mode, to rename a context without changing the configuration is not supported. You can save the configuration as a firewall configuration, but you need to copy the entire configuration to a new context name and delete the old context configuration. Delete Context Use this command in order to delete the Context. From the system space issue, issue this command: no context conta Also make sure to remove the corresponding config file for the context.
17 dir disk: delete disk:/conta.cfg Related Information FWSM Basic Configuration Example PIX/ASA 7.x and Above: Multiple Context Configuration Example Technical Support & Documentation Cisco Systems Contacts & Feedback Help Site Map Cisco Systems, Inc. All rights reserved. Terms & Conditions Privacy Statement Cookie Policy Trademarks of Cisco Systems, Inc. Updated: Jul 04, 2008 Document ID:
PIX/ASA as a DHCP Server and Client Configuration Example
 PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
PIX/ASA 7.x ASDM: Restrict the Network Access of Remote Access VPN Users
 PIX/ASA 7.x ASDM: Restrict the Network Access of Remote Access VPN Users Document ID: 69308 Contents Introduction Prerequisites Requirements Components Used Related Products Network Diagram Conventions
PIX/ASA 7.x ASDM: Restrict the Network Access of Remote Access VPN Users Document ID: 69308 Contents Introduction Prerequisites Requirements Components Used Related Products Network Diagram Conventions
Table of Contents. Cisco PIX/ASA 7.x Enhanced Spoke to Spoke VPN Configuration Example
 Table of Contents PIX/ASA 7.x Enhanced Spoke to Spoke VPN Configuration Example...1 Document ID: 64692...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...2 Configure...2
Table of Contents PIX/ASA 7.x Enhanced Spoke to Spoke VPN Configuration Example...1 Document ID: 64692...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...2 Configure...2
Table of Contents. Cisco IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example
 Table of Contents IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example...1 Document ID: 63881...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2
Table of Contents IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example...1 Document ID: 63881...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2
ASA/PIX: Remote VPN Server with Inbound NAT for VPN Client Traffic with CLI and ASDM Configuration Example
 ASA/PIX: Remote VPN Server with Inbound NAT for VPN Client Traffic with CLI and ASDM Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions
ASA/PIX: Remote VPN Server with Inbound NAT for VPN Client Traffic with CLI and ASDM Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions
VPN Between Sonicwall Products and Cisco Security Appliance Configuration Example
 VPN Between Sonicwall Products and Cisco Security Appliance Configuration Example Document ID: 66171 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure
VPN Between Sonicwall Products and Cisco Security Appliance Configuration Example Document ID: 66171 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure
: Saved : : Serial Number: JMX1813Z0GJ : Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz : Written by enable_15 at 09:21: UTC Thu Dec !
 : Saved : : Serial Number: JMX1813Z0GJ : Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz : Written by enable_15 at 09:21:59.078 UTC Thu Dec 17 2015 ASA Version 9.2(2)4 hostname ciscoasa enable password
: Saved : : Serial Number: JMX1813Z0GJ : Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz : Written by enable_15 at 09:21:59.078 UTC Thu Dec 17 2015 ASA Version 9.2(2)4 hostname ciscoasa enable password
Document ID: Contents. Introduction. Prerequisites. Requirements. Introduction. Prerequisites Requirements
 Products & Services ASA/PIX 7.x: Redundant or Backup ISP Links Configuration Example Document ID: 70559 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Background
Products & Services ASA/PIX 7.x: Redundant or Backup ISP Links Configuration Example Document ID: 70559 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Background
Configure the ASA for Dual Internal Networks
 Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
PIX/ASA: PPPoE Client Configuration Example
 PIX/ASA: PPPoE Client Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram CLI Configuration ASDM Configuration
PIX/ASA: PPPoE Client Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram CLI Configuration ASDM Configuration
Table of Contents. Cisco Enhanced Spoke to Client VPN Configuration Example for PIX Security Appliance Version 7.0
 Table of Contents Enhanced Spoke to Client VPN Configuration Example for PIX Security Appliance Version 7.0...1 Document ID: 64693...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1
Table of Contents Enhanced Spoke to Client VPN Configuration Example for PIX Security Appliance Version 7.0...1 Document ID: 64693...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1
NAC Appliance (Cisco Clean Access) In Band Virtual Gateway for Remote Access VPN Configuration Example
 NAC Appliance (Cisco Clean Access) In Band Virtual Gateway for Remote Access VPN Configuration Example Document ID: 71573 Contents Introduction Prerequisites Requirements Components Used Network Diagram
NAC Appliance (Cisco Clean Access) In Band Virtual Gateway for Remote Access VPN Configuration Example Document ID: 71573 Contents Introduction Prerequisites Requirements Components Used Network Diagram
This study aid describes the purpose of security contexts and explains how to enable, configure, and manage multiple contexts.
 Configuring Security Contexts Created by Bob Eckhoff This study aid describes the purpose of security contexts and explains how to enable, configure, and manage multiple contexts. Security Context Overview
Configuring Security Contexts Created by Bob Eckhoff This study aid describes the purpose of security contexts and explains how to enable, configure, and manage multiple contexts. Security Context Overview
Configuring the PIX Firewall and VPN Clients Using PPTP, MPPE and IPSec
 Configuring the PIX Firewall and VPN Clients Using PPTP, MPPE and IPSec Document ID: 14095 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Configuring the PIX Firewall and VPN Clients Using PPTP, MPPE and IPSec Document ID: 14095 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
co Configuring PIX to Router Dynamic to Static IPSec with
 co Configuring PIX to Router Dynamic to Static IPSec with Table of Contents Configuring PIX to Router Dynamic to Static IPSec with NAT...1 Introduction...1 Configure...1 Components Used...1 Network Diagram...1
co Configuring PIX to Router Dynamic to Static IPSec with Table of Contents Configuring PIX to Router Dynamic to Static IPSec with NAT...1 Introduction...1 Configure...1 Components Used...1 Network Diagram...1
PIX/ASA Active/Standby Failover Configuration Example
 PIX/ASA Active/Standby Failover Configuration Example Document ID: 77809 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Active/Standby Failover Active/Standby
PIX/ASA Active/Standby Failover Configuration Example Document ID: 77809 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Active/Standby Failover Active/Standby
ASA with WebVPN and Single Sign-on using ASDM and NTLMv1 Configuration Example
 ASA with WebVPN and Single Sign-on using ASDM and NTLMv1 Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Configure Add an AAA Server for Windows Domain
ASA with WebVPN and Single Sign-on using ASDM and NTLMv1 Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Configure Add an AAA Server for Windows Domain
ASA 7.2(2): SSL VPN Client (SVC) for Public Internet VPN on a Stick Configuration Example
 ASA 7.2(2): SSL VPN Client (SVC) for Public Internet VPN on a Stick Configuration Example Document ID: 100894 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information
ASA 7.2(2): SSL VPN Client (SVC) for Public Internet VPN on a Stick Configuration Example Document ID: 100894 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information
IPSec tunnel for ER75i routers application guide
 IPSec tunnel for ER75i routers application guide 1 Contents 1. Generally...3 2. IPSec limitation...3 3. Example of use IPSec tunnel Client side at ER75i...4 3.1. IPSec tunnel client side at ER75i...4 3.1.1.
IPSec tunnel for ER75i routers application guide 1 Contents 1. Generally...3 2. IPSec limitation...3 3. Example of use IPSec tunnel Client side at ER75i...4 3.1. IPSec tunnel client side at ER75i...4 3.1.1.
Downloaded from: justpaste.it/i2os
 : Saved : ASA Version 9.1(2) hostname ciscoasa enable password xxx encrypted names ip local pool poolvpn 192.168.20.10-192.168.20.30 mask 255.255.255.0 interface GigabitEthernet0/0 nameif inside security-level
: Saved : ASA Version 9.1(2) hostname ciscoasa enable password xxx encrypted names ip local pool poolvpn 192.168.20.10-192.168.20.30 mask 255.255.255.0 interface GigabitEthernet0/0 nameif inside security-level
Multiple Context Mode
 This chapter describes how to configure multiple security contexts on the Cisco ASA. About Security Contexts About Security Contexts, on page 1 Licensing for, on page 10 Prerequisites for, on page 12 Guidelines
This chapter describes how to configure multiple security contexts on the Cisco ASA. About Security Contexts About Security Contexts, on page 1 Licensing for, on page 10 Prerequisites for, on page 12 Guidelines
Permitting PPTP Connections Through the PIX/ASA
 Permitting PPTP Connections Through the PIX/ASA Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions PPTP with the Client Inside and the Server Outside Network
Permitting PPTP Connections Through the PIX/ASA Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions PPTP with the Client Inside and the Server Outside Network
ASA Version 7.2(4)30! hostname vpn domain-name hollywood.com enable password BO5OGdtIUElAVJc7 encrypted passwd BO5OGdtIUElAVJc7 encrypted names name
 ASA Version 7.2(4)30 hostname vpn domain-name hollywood.com enable password BO5OGdtIUElAVJc7 encrypted passwd BO5OGdtIUElAVJc7 encrypted names name 172.30.232.128 XL description XL / idot name 172.28.28.0
ASA Version 7.2(4)30 hostname vpn domain-name hollywood.com enable password BO5OGdtIUElAVJc7 encrypted passwd BO5OGdtIUElAVJc7 encrypted names name 172.30.232.128 XL description XL / idot name 172.28.28.0
Physical Topology. Logical Topology
 Physical Topology Logical Topology Please, note that the configurations given below can certainly be clean-up and tuned. Some commands are still embedded for testing purposes. Note also that the text highlighted
Physical Topology Logical Topology Please, note that the configurations given below can certainly be clean-up and tuned. Some commands are still embedded for testing purposes. Note also that the text highlighted
Lab Configure and Test Advanced Protocol Handling on the Cisco PIX Security Appliance
 Lab 9.4.10 Configure and Test Advanced Protocol Handling on the Cisco PIX Security Appliance Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Display the
Lab 9.4.10 Configure and Test Advanced Protocol Handling on the Cisco PIX Security Appliance Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Display the
Multiple Context Mode
 This chapter describes how to configure multiple security contexts on the Cisco ASA. About Security Contexts, page 1 Licensing for, page 13 Prerequisites for, page 14 Guidelines for, page 14 Defaults for,
This chapter describes how to configure multiple security contexts on the Cisco ASA. About Security Contexts, page 1 Licensing for, page 13 Prerequisites for, page 14 Guidelines for, page 14 Defaults for,
Multiple Context Mode
 This chapter describes how to configure multiple security contexts on the Cisco ASA. About Security Contexts, page 1 Licensing for, page 12 Prerequisites for, page 13 Guidelines for, page 14 Defaults for,
This chapter describes how to configure multiple security contexts on the Cisco ASA. About Security Contexts, page 1 Licensing for, page 12 Prerequisites for, page 13 Guidelines for, page 14 Defaults for,
ASA/PIX 8.x: Radius Authorization (ACS 4.x) for VPN Access using Downloadable ACL with CLI and ASDM Configuration Example
 ASA/PIX 8.x: Radius Authorization (ACS 4.x) for VPN Access using Downloadable ACL with CLI and ASDM Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products
ASA/PIX 8.x: Radius Authorization (ACS 4.x) for VPN Access using Downloadable ACL with CLI and ASDM Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products
This document is intended to give guidance on how to read log entries from a Cisco PIX / ASA. The specific model in this case was a PIX 501.
 1.0 Overview This document is intended to give guidance on how to read log entries from a Cisco PIX / ASA. The specific model in this case was a PIX 501. 2.0 PIX Config The following is the PIX config
1.0 Overview This document is intended to give guidance on how to read log entries from a Cisco PIX / ASA. The specific model in this case was a PIX 501. 2.0 PIX Config The following is the PIX config
Firewalling Avid ISIS in a Cisco environment
 Firewalling Avid ISIS in a Cisco environment Interoperability testing between Cisco ASA and ISIS results Francesca Martucci Consulting System Engineer for Security - Cisco David Shephard - Senior Network
Firewalling Avid ISIS in a Cisco environment Interoperability testing between Cisco ASA and ISIS results Francesca Martucci Consulting System Engineer for Security - Cisco David Shephard - Senior Network
Catalyst 6500 FWSM Replacement of Failover Unit after a Hardware Failure
 Catalyst 6500 FWSM Replacement of Failover Unit after a Hardware Failure Document ID: 65604 Contents Introduction Prerequisites Requirements Components Used Conventions Overview Upgrade the FWSM Code Enable
Catalyst 6500 FWSM Replacement of Failover Unit after a Hardware Failure Document ID: 65604 Contents Introduction Prerequisites Requirements Components Used Conventions Overview Upgrade the FWSM Code Enable
SSL VPN Configuration of a Cisco ASA 8.0
 Published on Jisc community (https://community.jisc.ac.uk) Home > Advisory services > Multi-site Connectivity Advisory Service > Technical guides > Secure Virtual Private Networks > SSL VPN Configuration
Published on Jisc community (https://community.jisc.ac.uk) Home > Advisory services > Multi-site Connectivity Advisory Service > Technical guides > Secure Virtual Private Networks > SSL VPN Configuration
Virtual Private Network Setup
 This chapter provides information about virtual private network setup. Virtual Private Network, page 1 Devices Supporting VPN, page 2 Set Up VPN Feature, page 2 Complete Cisco IOS Prerequisites, page 3
This chapter provides information about virtual private network setup. Virtual Private Network, page 1 Devices Supporting VPN, page 2 Set Up VPN Feature, page 2 Complete Cisco IOS Prerequisites, page 3
Applying Application Layer Protocol Inspection
 CHAPTER 21 This chapter describes how to configure application layer protocol inspection. Inspection engines are required for services that embed IP addressing information in the user data packet or that
CHAPTER 21 This chapter describes how to configure application layer protocol inspection. Inspection engines are required for services that embed IP addressing information in the user data packet or that
Getting Started. Getting Started with Your Platform Model. Factory Default Configurations CHAPTER
 CHAPTER 2 This chapter describes how to access the command-line interface, configure the firewall mode, and work with the configuration. This chapter includes the following sections: with Your Platform
CHAPTER 2 This chapter describes how to access the command-line interface, configure the firewall mode, and work with the configuration. This chapter includes the following sections: with Your Platform
Virtual private network setup
 Virtual private network setup This chapter provides information about virtual private network setup. Virtual private network, page 1 Devices supporting VPN, page 2 Set up VPN feature, page 2 Complete IOS
Virtual private network setup This chapter provides information about virtual private network setup. Virtual private network, page 1 Devices supporting VPN, page 2 Set up VPN feature, page 2 Complete IOS
Sample Configurations
 APPENDIXA This appendix illustrates and describes a number of common ways to implement the ASA, and includes the following sections: Example 1: Multiple Mode Firewall With Outside Access, page A-1 Example
APPENDIXA This appendix illustrates and describes a number of common ways to implement the ASA, and includes the following sections: Example 1: Multiple Mode Firewall With Outside Access, page A-1 Example
Chapter 9 Lab A: Configuring ASA Basic Settings and Firewall Using CLI
 A: Configuring ASA Basic Settings and Firewall Using CLI Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2015 Cisco and/or its affiliates. All rights reserved.
A: Configuring ASA Basic Settings and Firewall Using CLI Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2015 Cisco and/or its affiliates. All rights reserved.
Migrating to the Cisco ASA Services Module from the FWSM
 Migrating to the Cisco ASA Services Module from the FWSM Contents Information About the Migration, page 1 Migrating the FWSM Configuration to the ASA SM, page 2 Unsupported Runtime Commands, page 4 Configuration
Migrating to the Cisco ASA Services Module from the FWSM Contents Information About the Migration, page 1 Migrating the FWSM Configuration to the ASA SM, page 2 Unsupported Runtime Commands, page 4 Configuration
Chapter 9 Lab A: Configuring ASA Basic Settings and Firewall Using CLI
 A: Configuring ASA Basic Settings and Firewall Using CLI This lab has been updated for use on NETLAB+ Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2018
A: Configuring ASA Basic Settings and Firewall Using CLI This lab has been updated for use on NETLAB+ Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2018
ASA/PIX: Configure Active/Standby Failover in Transparent Mode Contents
 ASA/PIX: Configure Active/Standby Failover in Transparent Mode Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Active/Standby Failover Active/Standby Failover
ASA/PIX: Configure Active/Standby Failover in Transparent Mode Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Active/Standby Failover Active/Standby Failover
Fundamentals of Network Security v1.1 Scope and Sequence
 Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM
 Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
FTD: How to enable TCP State Bypass Configuration using FlexConfig Policy
 FTD: How to enable TCP State Bypass Configuration using FlexConfig Policy Contents Introduction Prerequisites Requirements Components Used Background Information Configuration Step 1. Configure an Extended
FTD: How to enable TCP State Bypass Configuration using FlexConfig Policy Contents Introduction Prerequisites Requirements Components Used Background Information Configuration Step 1. Configure an Extended
upgrade-mp through xlate-bypass Commands
 CHAPTER 33 upgrade-mp To upgrade the maintenance partition software, use the upgrade-mp command. upgrade-mp {http[s]://[user:password@]server[:port]/pathname tftp[://server/pathname]} tftp http[s] server
CHAPTER 33 upgrade-mp To upgrade the maintenance partition software, use the upgrade-mp command. upgrade-mp {http[s]://[user:password@]server[:port]/pathname tftp[://server/pathname]} tftp http[s] server
PIX Security Appliance Contexts, Failover, and Management
 CHAPTER 8 PIX Security Appliance Contexts, Failover, and Management Upon completion of this chapter, you should be able to answer the following questions: How do I configure a Pix Security Appliance to
CHAPTER 8 PIX Security Appliance Contexts, Failover, and Management Upon completion of this chapter, you should be able to answer the following questions: How do I configure a Pix Security Appliance to
How to Configure the Cisco VPN Client to PIX with AES
 How to Configure the Cisco VPN Client to PIX with AES Document ID: 42761 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configurations Network Diagram
How to Configure the Cisco VPN Client to PIX with AES Document ID: 42761 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configurations Network Diagram
Troubleshooting. Testing Your Configuration CHAPTER
 82 CHAPTER This chapter describes how to troubleshoot the ASA and includes the following sections: Testing Your Configuration, page 82-1 Reloading the ASA, page 82-8 Performing Password Recovery, page
82 CHAPTER This chapter describes how to troubleshoot the ASA and includes the following sections: Testing Your Configuration, page 82-1 Reloading the ASA, page 82-8 Performing Password Recovery, page
ASA Cluster for the Firepower 9300 Chassis
 Clustering lets you group multiple Firepower 9300 chassis ASAs together as a single logical device. The Firepower 9300 chassis series includes the Firepower 9300. A cluster provides all the convenience
Clustering lets you group multiple Firepower 9300 chassis ASAs together as a single logical device. The Firepower 9300 chassis series includes the Firepower 9300. A cluster provides all the convenience
ASA/PIX 8.x: Block Certain Websites (URLs) Using Regular Expressions With MPF Configuration Example
 ASA/PIX 8.x: Block Certain Websites (URLs) Using Regular Expressions With MPF Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Background
ASA/PIX 8.x: Block Certain Websites (URLs) Using Regular Expressions With MPF Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Background
Secure ACS Database Replication Configuration Example
 Secure ACS Database Replication Configuration Example Document ID: 71320 Introduction Prerequisites Requirements Components Used Related Products Conventions Background Information Scenario I Scenario
Secure ACS Database Replication Configuration Example Document ID: 71320 Introduction Prerequisites Requirements Components Used Related Products Conventions Background Information Scenario I Scenario
Lab 8: Firewalls ASA Firewall Device
 Lab 8: Firewalls ASA Firewall Device 8.1 Details Aim: Rich Macfarlane 2015 The aim of this lab is to investigate a Cisco ASA Firewall Device, its default traffic flows, its stateful firewalling functionality,
Lab 8: Firewalls ASA Firewall Device 8.1 Details Aim: Rich Macfarlane 2015 The aim of this lab is to investigate a Cisco ASA Firewall Device, its default traffic flows, its stateful firewalling functionality,
Configuration Examples
 CHAPTER 4 Before using this chapter, be sure that you have planned your site s security policy, as described in Chapter 1, Introduction, and configured the PIX Firewall, as described in Chapter 2, Configuring
CHAPTER 4 Before using this chapter, be sure that you have planned your site s security policy, as described in Chapter 1, Introduction, and configured the PIX Firewall, as described in Chapter 2, Configuring
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
This chapter covers the following exam topics for the Secure PIX Firewall Advanced Exam (CSPFA 9E0-511): 5. User interface 6. Configuring the PIX
 This chapter covers the following exam topics for the Secure PIX Firewall Advanced Exam (CSPFA 9E0-511): 5. User interface 6. Configuring the PIX Firewall 8. Time setting and NTP support 13. DHCP server
This chapter covers the following exam topics for the Secure PIX Firewall Advanced Exam (CSPFA 9E0-511): 5. User interface 6. Configuring the PIX Firewall 8. Time setting and NTP support 13. DHCP server
ASA Cluster for the Firepower 9300 Chassis
 Clustering lets you group multiple Firepower 9300 chassis ASAs together as a single logical device. The Firepower 9300 chassis series includes the Firepower 9300. A cluster provides all the convenience
Clustering lets you group multiple Firepower 9300 chassis ASAs together as a single logical device. The Firepower 9300 chassis series includes the Firepower 9300. A cluster provides all the convenience
Getting Started. Access the Console for the Command-Line Interface. Access the Appliance Console
 This chapter describes how to get started with your Cisco ASA. Access the Console for the Command-Line Interface, on page 1 Configure ASDM Access, on page 9 Start ASDM, on page 15 Factory Default Configurations,
This chapter describes how to get started with your Cisco ASA. Access the Console for the Command-Line Interface, on page 1 Configure ASDM Access, on page 9 Start ASDM, on page 15 Factory Default Configurations,
CISCO EXAM QUESTIONS & ANSWERS
 CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
Managing Services Modules
 CHAPTER 58 This chapter describes how to manage the following module types: Security Services Cards (SSCs) Security Services Modules (SSMs) Security Services Processors (SSPs) Modules run advanced security
CHAPTER 58 This chapter describes how to manage the following module types: Security Services Cards (SSCs) Security Services Modules (SSMs) Security Services Processors (SSPs) Modules run advanced security
PIX/ASA 7.x and Later : Easy VPN with Split Tunneling ASA 5500 as the Server and Cisco 871 as the Easy VPN Remote Configuration Example
 PIX/ASA 7.x and Later : Easy VPN with Split Tunneling ASA 5500 as the Server and Cisco 871 as the Easy VPN Remote Configuration Example Document ID: 68815 Contents Introduction Prerequisites Requirements
PIX/ASA 7.x and Later : Easy VPN with Split Tunneling ASA 5500 as the Server and Cisco 871 as the Easy VPN Remote Configuration Example Document ID: 68815 Contents Introduction Prerequisites Requirements
Troubleshooting the Security Appliance
 CHAPTER 43 This chapter describes how to troubleshoot the security appliance, and includes the following sections: Testing Your Configuration, page 43-1 Reloading the Security Appliance, page 43-6 Performing
CHAPTER 43 This chapter describes how to troubleshoot the security appliance, and includes the following sections: Testing Your Configuration, page 43-1 Reloading the Security Appliance, page 43-6 Performing
HPE Security ArcSight Connectors
 HPE Security ArcSight Connectors SmartConnector for IP Flow (NetFlow/J-Flow) Configuration Guide October 17, 2017 SmartConnector for IP Flow (NetFlow/J-Flow) October 17, 2017 Copyright 2004 2017 Hewlett
HPE Security ArcSight Connectors SmartConnector for IP Flow (NetFlow/J-Flow) Configuration Guide October 17, 2017 SmartConnector for IP Flow (NetFlow/J-Flow) October 17, 2017 Copyright 2004 2017 Hewlett
Exam Name: Implementing Cisco Edge Network Security Solutions
 Vendor: Cisco Exam Code: 300-206 Exam Name: Implementing Cisco Edge Network Security Solutions Version: Demo QUESTION 1 The Cisco ASA must support dynamic routing and terminating VPN traffic. Which three
Vendor: Cisco Exam Code: 300-206 Exam Name: Implementing Cisco Edge Network Security Solutions Version: Demo QUESTION 1 The Cisco ASA must support dynamic routing and terminating VPN traffic. Which three
Configuring Management Access
 37 CHAPTER This chapter describes how to access the ASA for system management through Telnet, SSH, and HTTPS (using ASDM), how to authenticate and authorize users, how to create login banners, and how
37 CHAPTER This chapter describes how to access the ASA for system management through Telnet, SSH, and HTTPS (using ASDM), how to authenticate and authorize users, how to create login banners, and how
Configuring the AIP SSM
 CHAPTER 18 The number of concurrent CLI sessions is limited based on the platform. IDS 4215 and NM CIDS are limited to three concurrent CLI sessions. All other platforms allow ten concurrent sessions.
CHAPTER 18 The number of concurrent CLI sessions is limited based on the platform. IDS 4215 and NM CIDS are limited to three concurrent CLI sessions. All other platforms allow ten concurrent sessions.
Sample Configurations
 APPENDIXB This appendix illustrates and describes a number of common ways to implement the security appliance, and includes the following topics: Example 1: Multiple Mode Firewall With Outside Access,
APPENDIXB This appendix illustrates and describes a number of common ways to implement the security appliance, and includes the following topics: Example 1: Multiple Mode Firewall With Outside Access,
Overview of the Cisco NCS Command-Line Interface
 CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
Firepower Threat Defense Cluster for the Firepower 4100/9300
 Firepower Threat Defense Cluster for the Firepower 4100/9300 Clustering lets you group multiple Firepower Threat Defense units together as a single logical device. Clustering is only supported for the
Firepower Threat Defense Cluster for the Firepower 4100/9300 Clustering lets you group multiple Firepower Threat Defense units together as a single logical device. Clustering is only supported for the
Cisco Meraki EMM Integration with Cisco Identity Service Engine. Secure Access How -To Guides Series
 Cisco Meraki EMM Integration with Cisco Identity Service Engine Secure Access How -To Guides Series Author: Imran Bashir Date: March 2015 Table of Contents Mobile Device Management (MDM)... 3 Overview...
Cisco Meraki EMM Integration with Cisco Identity Service Engine Secure Access How -To Guides Series Author: Imran Bashir Date: March 2015 Table of Contents Mobile Device Management (MDM)... 3 Overview...
Use NAT to Hide the Real IP Address of CTC to Establish a Session with ONS 15454
 Use NAT to Hide the Real IP Address of CTC to Establish a Session with ONS 15454 Document ID: 65122 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Topology
Use NAT to Hide the Real IP Address of CTC to Establish a Session with ONS 15454 Document ID: 65122 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Topology
Three interface Router without NAT Cisco IOS Firewall Configuration
 Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Password Recovery Procedure for the PIX
 Password Recovery Procedure for the PIX Document ID: 8529 Introduction Prerequisites Requirements Components Used Conventions Step by Step Procedure PIX With a Floppy Drive PIX Without a Floppy Drive Sample
Password Recovery Procedure for the PIX Document ID: 8529 Introduction Prerequisites Requirements Components Used Conventions Step by Step Procedure PIX With a Floppy Drive PIX Without a Floppy Drive Sample
through ftp-map Commands
 CHAPTER 12 12-1 email Chapter 12 email To include the indicated email address in the Subject Alternative Name extension of the certificate during enrollment, use the email command in crypto ca trustpoint
CHAPTER 12 12-1 email Chapter 12 email To include the indicated email address in the Subject Alternative Name extension of the certificate during enrollment, use the email command in crypto ca trustpoint
GSS Administration and Troubleshooting
 CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands
 PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands Document ID: 63872 Introduction Prerequisites Requirements Components Used Related Products Conventions Network
PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands Document ID: 63872 Introduction Prerequisites Requirements Components Used Related Products Conventions Network
Configuring the Hostname, Domain Name, Passwords, and Other Basic Settings
 CHAPTER 5 Configuring the Hostname, Domain Name, Passwords, and Other Basic Settings This chapter describes how to configure basic settings on your ASA 1000V that are typically required for a functioning
CHAPTER 5 Configuring the Hostname, Domain Name, Passwords, and Other Basic Settings This chapter describes how to configure basic settings on your ASA 1000V that are typically required for a functioning
VPN Connection through Zone based Firewall Router Configuration Example
 VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
ASA Cluster for the Firepower 4100/9300 Chassis
 Clustering lets you group multiple Firepower 4100/9300 chassis ASAs together as a single logical device. The Firepower 4100/9300 chassis series includes the Firepower 9300 and Firepower 4100 series. A
Clustering lets you group multiple Firepower 4100/9300 chassis ASAs together as a single logical device. The Firepower 4100/9300 chassis series includes the Firepower 9300 and Firepower 4100 series. A
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem
 How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM
 Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
This section describes the clustering architecture and how it works. Management access to each ASA for configuration and monitoring.
 Clustering lets you group multiple ASAs together as a single logical device. A cluster provides all the convenience of a single device (management, integration into a network) while achieving the increased
Clustering lets you group multiple ASAs together as a single logical device. A cluster provides all the convenience of a single device (management, integration into a network) while achieving the increased
ASA 7.x/PIX 6.x and Above: Open/Block the Ports Configuration Example
 ASA 7.x/PIX 6.x and Above: Open/Block the Ports Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram Blocking the
ASA 7.x/PIX 6.x and Above: Open/Block the Ports Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram Blocking the
Installing or Upgrading ANM Virtual Appliance
 CHAPTER 2 This chapter describes how to deploy Cisco ANM Virtual Appliance 4.3 (new installation) and how to upgrade from ANM software version 4.1 or 4.2 to software version 4.3. This chapter includes
CHAPTER 2 This chapter describes how to deploy Cisco ANM Virtual Appliance 4.3 (new installation) and how to upgrade from ANM software version 4.1 or 4.2 to software version 4.3. This chapter includes
ASA Cluster for the Firepower 4100/9300 Chassis
 Clustering lets you group multiple Firepower 4100/9300 chassis ASAs together as a single logical device. The Firepower 4100/9300 chassis series includes the Firepower 9300 and Firepower 4100 series. A
Clustering lets you group multiple Firepower 4100/9300 chassis ASAs together as a single logical device. The Firepower 4100/9300 chassis series includes the Firepower 9300 and Firepower 4100 series. A
Context Based Access Control (CBAC): Introduction and Configuration
 Context Based Access Control (CBAC): Introduction and Configuration Document ID: 13814 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information What Traffic Do
Context Based Access Control (CBAC): Introduction and Configuration Document ID: 13814 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information What Traffic Do
PIX, TACACS+, and RADIUS Sample Configurations: 4.4.x
 PIX, TACACS+, and RADIUS Sample Configurations: 4.4.x Document ID: 13819 Contents Introduction Prerequisites Requirements Components Used Conventions Authentication vs. Authorization What the User Sees
PIX, TACACS+, and RADIUS Sample Configurations: 4.4.x Document ID: 13819 Contents Introduction Prerequisites Requirements Components Used Conventions Authentication vs. Authorization What the User Sees
Integration of Customer Instance with Shared Management
 Integration of Customer Instance with Shared Management Unified CCDM Integration, page 1 Cisco UCDM Integration, page 21 ASA Integration, page 24 Perimeta SBC Integration, page 34 Cisco Prime Collaboration
Integration of Customer Instance with Shared Management Unified CCDM Integration, page 1 Cisco UCDM Integration, page 21 ASA Integration, page 24 Perimeta SBC Integration, page 34 Cisco Prime Collaboration
Overview. ACE Appliance Device Manager Overview CHAPTER
 1 CHAPTER This section contains the following: ACE Appliance Device Manager, page 1-1 Logging Into ACE Appliance Device Manager, page 1-3 Changing Your Account Password, page 1-4 ACE Appliance Device Manager
1 CHAPTER This section contains the following: ACE Appliance Device Manager, page 1-1 Logging Into ACE Appliance Device Manager, page 1-3 Changing Your Account Password, page 1-4 ACE Appliance Device Manager
Some features are not supported when using clustering. See Unsupported Features with Clustering, on page 11.
 Clustering lets you group multiple ASAs together as a single logical device. A cluster provides all the convenience of a single device (management, integration into a network) while achieving the increased
Clustering lets you group multiple ASAs together as a single logical device. A cluster provides all the convenience of a single device (management, integration into a network) while achieving the increased
PIX/ASA 7.x to 7.x Upgrade a Software Image using ASDM or CLI Configuration Example
 PIX/ASA 7.x to 7.x Upgrade a Software Image using ASDM or CLI Configuration Example Document ID: 69984 Introduction Prerequisites Requirements Components Used Related Products Conventions Upgrade a Software
PIX/ASA 7.x to 7.x Upgrade a Software Image using ASDM or CLI Configuration Example Document ID: 69984 Introduction Prerequisites Requirements Components Used Related Products Conventions Upgrade a Software
Cisco CISCO Securing Networks with ASA Advanced. Practice Test. Version
 Cisco 642-515 CISCO 642-515 Securing Networks with ASA Advanced Practice Test Version 3.1 QUESTION NO: 1 Cisco 642-515: Practice Exam Which two statements correctly describe configuring active/active failover?
Cisco 642-515 CISCO 642-515 Securing Networks with ASA Advanced Practice Test Version 3.1 QUESTION NO: 1 Cisco 642-515: Practice Exam Which two statements correctly describe configuring active/active failover?
On completion of this chapter, you will be able to perform the following tasks: Describe the PIX Device Manager (PDM) and its capabilities.
 On completion of this chapter, you will be able to perform the following tasks: Describe the PIX Device Manager (PDM) and its capabilities. Describe PDM s browser and PIX Firewall requirements. Install
On completion of this chapter, you will be able to perform the following tasks: Describe the PIX Device Manager (PDM) and its capabilities. Describe PDM s browser and PIX Firewall requirements. Install
Configuring Logging. Information About Logging CHAPTER
 74 CHAPTER This chapter describes how to configure and manage logs for the ASA, and includes the following sections: Information About Logging, page 74-1 Licensing Requirements for Logging, page 74-5 Prerequisites
74 CHAPTER This chapter describes how to configure and manage logs for the ASA, and includes the following sections: Information About Logging, page 74-1 Licensing Requirements for Logging, page 74-5 Prerequisites
Release Notes for Cisco ASDM Version 5.2(5)
 May 2010 This document contains release information for Cisco ASDM Version 5.2(5) on the Cisco ASA 5500. It includes the following sections: New Features, page 1 System Requirements, page 1 Upgrading ASDM,
May 2010 This document contains release information for Cisco ASDM Version 5.2(5) on the Cisco ASA 5500. It includes the following sections: New Features, page 1 System Requirements, page 1 Upgrading ASDM,
UniNets CCNA Security LAB MANUAL UNiNets CCNA Cisco Certified Network Associate Security LAB MANUAL UniNets CCNA LAB MANUAL
 UNiNets CCNA Cisco Certified Network Associate Security LAB MANUAL Contents: UniNets CCNA Security LAB MANUAL Section 1 Securing Layer 2 Lab 1-1 Configuring Native VLAN on a Trunk Links Lab 1-2 Disabling
UNiNets CCNA Cisco Certified Network Associate Security LAB MANUAL Contents: UniNets CCNA Security LAB MANUAL Section 1 Securing Layer 2 Lab 1-1 Configuring Native VLAN on a Trunk Links Lab 1-2 Disabling
ASA Cluster for the Firepower 4100/9300 Chassis
 Clustering lets you group multiple Firepower 4100/9300 chassis ASAs together as a single logical device. The Firepower 4100/9300 chassis series includes the Firepower 9300 and Firepower 4100 series. A
Clustering lets you group multiple Firepower 4100/9300 chassis ASAs together as a single logical device. The Firepower 4100/9300 chassis series includes the Firepower 9300 and Firepower 4100 series. A
Cisco ASDM Release Notes Version 6.1(x)F
 July 2009 This document contains release information for the following Cisco ASDM Versions: 6.1(5)F 6.1(4)F 6.1(3)F 6.1(2)F 6.1(1)F ASDM 6.1(x)F runs with Cisco 6500 series and Cisco 7600 series Firewall
July 2009 This document contains release information for the following Cisco ASDM Versions: 6.1(5)F 6.1(4)F 6.1(3)F 6.1(2)F 6.1(1)F ASDM 6.1(x)F runs with Cisco 6500 series and Cisco 7600 series Firewall
gateway through hw-module module shutdown Commands
 CHAPTER 12 gateway through hw-module module shutdown Commands 12-1 gateway gateway To specify which group of call agents are managing a particular gateway, use the gateway command in MGCP map configuration
CHAPTER 12 gateway through hw-module module shutdown Commands 12-1 gateway gateway To specify which group of call agents are managing a particular gateway, use the gateway command in MGCP map configuration
