2nd International Conference on Computers & Management (ICCM-2016) Dec 2016 Tentative Programme
|
|
|
- Hope Moore
- 6 years ago
- Views:
Transcription
1 2nd International Conference on Computers & Management (ICCM-2016) Dec 2016 Tentative Programme Day 1, Wednesday, 28 Dec 2016 IST 08:00 AM 09:00 AM 10:00 AM 10:30 AM 12:00 Noon Venue: V.C. Secretariat Registration Starts Opening Ceremony High Tea Keynote - 1 by Dr. Satish Sharma Keynote - 2 by Dr. Lalit Garg Venue: Department of Computer Science and Engineering 01:30 PM 02:30 PM Session-1 04:00 PM 04:15 PM Session-4 09:00 AM Session-7 10:30 AM 12:00 Noon 12:15 PM Session-10 01:30 PM 02:30 PM 04:00 PM 04:30 PM Lunch at Central Lobby Session-2 Tea Break Session-5 Day 2, Thursday, 29 Dec 2016 Session-8 Keynote -3 by Mr. Hirdesh Singhal (Skype) Tea Break Session-11 Lunch at Central Lobby Session-13 Closing Ceremony Refreshment at Central Lobby Session-3 Session-6 Session-9 Session-12
2 IST 08:00 AM Registration Starts 09:00-10:00 AM Opening Ceremony Detailed ICCM-2016 Conference Schedule Day 1, Wednesday, 28 Dec 2016 Venue: V.C. Secretariat 10:00-10:30 AM High Tea 10:30-12:00 Noon Keynote- 1 by Dr. Satish Sharma 12:00-01:30 PM Keynote- 2 by Dr. Lalit Garg Venue: Department of Computer Science and Engineering 01:30-02:30 PM Lunch at Central Lobby Track-1: User Authentication and Security 02:30-04:00 PM 28-Dec 2016 Session 1, Lecture Theatre Session Chair 121 Rifaqat Ali A Secure and Robust Three-factor Based Authentication Scheme using RSA Cryptosystem 122 Preeti Chandrakar Cryptanalysis and Security Enhancement of Three-Factor Remote User Authentication Scheme for Multi-Server Environment 21 Subhash Chandra Static Signature Verification Based on Texture Analysis using Support Vector Machine 5 Sudha Ellison Mathe Efficient Sequential Polynomial Basis Multiplier over GF(28) 11 Sohum Prabhudesai Enhanced Attribute Access Control Mechanism with Sensitive Attribute Protection Track-2: Software Engineering, Data Mining, Cloud Computing 02:30-04:00 PM Session 2, Lecture Theatre Session Chair Mr. Skype 117 Arodh Lal Karn News Sentiment Incorporation in Real-Time Trading: Alpha Testing the Event Trading Strategy in High Frequency Trading 77 Keith Vassallo Cross-Platform Development Frameworks: Review of contemporary technologies and methods for cross-platform application development 102 Pratiksha Gautam Correlation and Performance Estimation of Clone Detection Tools 59 Honey Jindal An Empirical analysis of Web Navigation Prediction Techniques Mr. Oral
3 58 Oshin Sharma Energy Efficient Virtual Machine Consolidation for Cloud Data Centers Using Analytic Hierarchy Process Track-3: Decision Support Systems, E-Commerce, E-Government 02:30-04:00 PM Session 3, Lecture Theatre Session Chair Mr. Oral 133 Supreet Kanwal Impact of Organizational Culture and Process-Structure on Marketing Intelligence: Perspective of IT Professionals 33 Satish Sharma Innovative Health Services for Seniors 110 G. Singh Fuzzy Decision Support System to enhance Productivity in Indian Coal Mining Industry 101 Vipul Gupta E-Marketing Strategy for an E-Business Analysing tools and media for the development of an E-Marketing strategy 50 Sonu Rajak Distance and Bearing Based Vehicle Trajectory Segmentation 04:00-04:15 PM Tea Break Track-4: Hardware Design, Communication Networks, Multimedia Technologies 12:15-01:30 PM Session 4, Lecture Theatre Session Chair Mr. Oral 42 Vandana Shukla A Novel Approach for Reversible Realization of N-bit Arithmetic Circuit for Low Power Loss ALU Applications 112 Amit Kumar Gupta Design and Performance Evaluation of Smart Job First Multilevel Feedback Queue (SJFMLFQ) Scheduling Algorithm with Dynamic Smart Time Quantum 71 Madan Mohan Agarwal Design of Fuzzy Controlled Routing Protocol to Save Energy in Ad Hoc Networks 15 Manali Chandani A Survey on Synchronization Approach in MAC Layer Protocols 125 Lalit Garg Dwell-Free Eye-Driven Typing: A review of literature Track-5: Engineering Management and Decision Support Systems 04:15-05:45 PM Session 5, Lecture Theatre Session Chair Mr. Skype 123 Lalit Garg Assessment in e-learning for Higher Education 88 Joseph Bonello Manufacturing Production Line Modelling and Classification of associated NP- Hard problems 114 Irappa Basappa Hunagund Plant Layout of Manufacturing Firm - A Case Study
4 12 Syed Ali Fathima S J Augmented Reality using Natural User Interface Based Physical Therapy Rehabilitation Framework with Mobile Decision Support System - A Global Solution for Remote Assistance 116 Gianpaolo Tomaselli A Review of Corporate Social Responsibility Application in the Healthcare Sector Track-6: Multimedia and Graphics Technologies 04:15-05:45 PM Session 6, Lecture Theatre Session Chair Oral 87 Sandeep Kumar Sharma OTCA Approach towards Blurred Image Feature Estimation and Enrichment 67 Neha Gopaliya Discrete Transform Based Image Fusion: A Review 64 Shiven Goyal, Poonam Sarda Image Fusion Based On Optimization Technique 108 Sugandha Agarwal Image Quality Improvement Using Shift Variant and Shift Invariant Based Wavelet Transform Methods- A Novel Approach 3 Sunita Kumari A review of RGB-D Sensor Calibration for Human Activity Recognition IST Day 2, Thursday, 29 Dec 2016 Track-7 Data Mining, Software Engineering and Business Intelligence 09:00-10:30 AM Session 7, Lecture Theatre Session Chair Mr. Oral 49 Megha Sharma Density- Based Clustering for Mixed Data 60 Nisha Comparison between Hierarchical and Graph Clustering method 137 Santosh Singh Evaluation of Neural Network Architectures for Lung Abnormality Classification 32 Satish Sharma Accumulative Software Development 19 Mehfooza. M Model on Quantifying Coastal data using Path Analysis to infer the Cause and Effect of the Pollutant Parameters 70 Supreet Kanwal The Role of Marketing Intelligence in Brand Positioning: Perspective of Marketing Professionals Track-8:Communication Networks, Data Mining, Decision Support Systems 09:00-10:30 AM Session 8, Lecture Theatre Session Chair Mr. Skype 55 Geetanjali Rathee Secure Modified Ad hoc On-demand Distance Vector (MAODV) routing protocol 02 Mamata Rath MAQ : A Mobile Agent Based Quality of Service Platform for Manets
5 90 Divya Agrawal Improving Classification Accuracy on Imbalanced Data by Ensembling Technique 84 Gianpaolo Tomaselli Healthcare Systems and Corporate Social Responsibility Communication: A Comparative Analysis between Malta and India 99 Dharmendra Sharma The determinants of Mobile Cloud Computing adoption by Financial Services Firms in Fiji Track-9 Cryptography and Information Security 09:00-10:30 AM Session 9, Lecture Theatre Session Chair Mr. Oral 98 Prerna Mohit Modification of Traditional RSA into Symmetric-RSA Cryptosystems 39 Sadanand Yadav A New Cryptographic Method for Image Encryption 4 Daya Sagar Gupta A Secure Cloud Storage using ECC-Based Homomorphic Encryption 25 Karan Singh Secure and Reliable Data Delivery Mechanism 26 Sugandha Agarwal Biometric Image Security Using Chaos Algorithm 10:30-12:00 Noon Keynote -3 by Mr. Hirdesh Singhal Lecture Theatre (Skype) 12:00-12:15 PM Tea Break Track-10: Hardware Design, Network Protocols, Cloud Computing 04:15-05:45 PM Session 10, Lecture Theatre Session Chair Mr. Oral 86 Vandana Shukla An Efficient Approach to Design a Low Power Loss Circuit for 2:4 Decoder with Reversible Logic 62 Manali Chandnani Node Synchronization Approach to Access CSMA/CA Channel 13 Vivek Jain Implement Multichannel Fractional Sample Rate Convertor using Genetic Algorithm 83 Priti Sharma Activity Scheduling Protocol for Energy Saving in Heterogeneous Wireless Sensor Networks 44 Jitendra Kumar Verma Resource Request Based Energy Efficient Heuristic for Server Offloading in Cloud Computing Environment Track-11: Cyber Security, Information Security 12:15-01:30 PM Session 11, Lecture Theatre Session Chair Mr. Skype 34 Regner Sabillon Cybersecurity Incident Handling and Incident Management 30 Hemraj Saini Mathematical Model for Cyber Attack in Computer Networking
6 89 Pratiksha Gautam A Novel Software Protection Approach for Code Obfuscation to Enhance Software Security 106 Sudhanshu Maurya Secuity and Privacy Aspects of Mobile Cloud Computing using Quantum Cryptography Track-12: 5th Generation Mobile Data Technologies 12:15-01:30 PM Session 12, Lecture Theatre Session Chair Mr. Oral 24 Karan Singh Review of Security Features in Mobile Android System 118 Anjali Mathur Utility of Social Networking Tools Among Indians-An Anaytical Study 14 Somayya Madakam 5G Mobile Communication Technology: We Had Never Seen Her Ever Before 74 Ruchi Verma Crisis Management Using Centrality Measurement in Social Networks 01:30-02:30 PM Lunch at Central Lobby Track-13: Communication Networks & Protocols,Cloud Computing 02:30-04:00 PM Session 13, Lecture Theatre Session Chair Mr. Skype 22 Geetanjali Rathee Secure Buffer-based Routing Protocol for WMN 92 Keith Vassallo Mobile Language Learning: Providing tools that allow the asynchronous, casual and sometimes gamified learning of languages on mobile devices 52 Akashdeep Bhardwaj Efficient Fault Tolerance on Cloud Environments 27 Oshin Sharma Performance Evaluation of VM Placement Using Classical Bin Packing and Genetic Algorithm for Cloud Environment 23 Geetanjali Rathee Behavior Detection Mechanism of the Node against Black Hole Attack in Hierarchical Mesh Networks 04:00-04:30 PM Closing Ceremony at Lecture Theatre 04:30-05:00 PM Refreshment
ACIT'2015. Conference Program. Under the Patronage of Her Excellency Mrs. Majd Shweikeh Minister of Telecommunications and Information Technology
 ACIT'2015 Conference Program Under the Patronage of Her Excellency Mrs. Majd Shweikeh Minister of Telecommunications and Information Technology Day 1 (Tuesday 15 December 2015) Registration Opening session
ACIT'2015 Conference Program Under the Patronage of Her Excellency Mrs. Majd Shweikeh Minister of Telecommunications and Information Technology Day 1 (Tuesday 15 December 2015) Registration Opening session
JAVA Projects. 1. Enforcing Multitenancy for Cloud Computing Environments (IEEE 2012).
 JAVA Projects I. IEEE based on CLOUD COMPUTING 1. Enforcing Multitenancy for Cloud Computing Environments 2. Practical Detection of Spammers and Content Promoters in Online Video Sharing Systems 3. An
JAVA Projects I. IEEE based on CLOUD COMPUTING 1. Enforcing Multitenancy for Cloud Computing Environments 2. Practical Detection of Spammers and Content Promoters in Online Video Sharing Systems 3. An
DOTNET Projects. DotNet Projects IEEE I. DOTNET based CLOUD COMPUTING. DOTNET based ARTIFICIAL INTELLIGENCE
 DOTNET Projects I. DOTNET based CLOUD COMPUTING 1. Enabling Cloud Storage Auditing with VerifiableOutsourcing of Key Updates (IEEE 2. Conjunctive Keyword Search with Designated Tester and Timing Enabled
DOTNET Projects I. DOTNET based CLOUD COMPUTING 1. Enabling Cloud Storage Auditing with VerifiableOutsourcing of Key Updates (IEEE 2. Conjunctive Keyword Search with Designated Tester and Timing Enabled
Payal Gulati. House No. 1H-36, NIT, Faridabad E xp e r i e nc e
 Payal Gulati House No. 1H-36, NIT, gulatipayal@yahoo.co.in Total Experience: 9.5 years E xp e r i e nc e Currently working as Assistant Professor (IT) in YMCA University of Science & Technology, since
Payal Gulati House No. 1H-36, NIT, gulatipayal@yahoo.co.in Total Experience: 9.5 years E xp e r i e nc e Currently working as Assistant Professor (IT) in YMCA University of Science & Technology, since
Name of the lecturer Doç. Dr. Selma Ayşe ÖZEL
 Y.L. CENG-541 Information Retrieval Systems MASTER Doç. Dr. Selma Ayşe ÖZEL Information retrieval strategies: vector space model, probabilistic retrieval, language models, inference networks, extended
Y.L. CENG-541 Information Retrieval Systems MASTER Doç. Dr. Selma Ayşe ÖZEL Information retrieval strategies: vector space model, probabilistic retrieval, language models, inference networks, extended
MASP Chapter on Safety and Security
 MASP Chapter on Safety and Security Daniel Watzenig Graz, Austria https://artemis.eu MASP Chapter on Safety & Security Daniel Watzenig daniel.watzenig@v2c2.at Francois Tuot francois.tuot@gemalto.com Antonio
MASP Chapter on Safety and Security Daniel Watzenig Graz, Austria https://artemis.eu MASP Chapter on Safety & Security Daniel Watzenig daniel.watzenig@v2c2.at Francois Tuot francois.tuot@gemalto.com Antonio
Proposal for Scrambled Method based on NTRU
 Proposal for Scrambled Method based on NTRU Ahmed Tariq Sadiq Computer Science Department University of Technology Baghdad, Iraq Najlaa Mohammad Hussein Computer Science Department Baghdad University Baghdad,
Proposal for Scrambled Method based on NTRU Ahmed Tariq Sadiq Computer Science Department University of Technology Baghdad, Iraq Najlaa Mohammad Hussein Computer Science Department Baghdad University Baghdad,
ALLOTMENT OF TOPICS FOR TERM PAPER WRITING
 Course: BCA ALLOTMENT OF TOPICS FOR TERM PAPER WRITING Appendix A Year: 2 nd Group: BCA-41 Semester: 4 th S. No. 1 2 3 4 5 6 7 8 9 10 11 University Roll No. 16065106001 16065106002 Name of Students Aayushi
Course: BCA ALLOTMENT OF TOPICS FOR TERM PAPER WRITING Appendix A Year: 2 nd Group: BCA-41 Semester: 4 th S. No. 1 2 3 4 5 6 7 8 9 10 11 University Roll No. 16065106001 16065106002 Name of Students Aayushi
SIR C R REDDY COLLEGE OF ENGINEERING
 SIR C R REDDY COLLEGE OF ENGINEERING DEPARTMENT OF INFORMATION TECHNOLOGY Course Outcomes II YEAR 1 st SEMESTER Subject: Data Structures (CSE 2.1.1) 1. Describe how arrays, records, linked structures,
SIR C R REDDY COLLEGE OF ENGINEERING DEPARTMENT OF INFORMATION TECHNOLOGY Course Outcomes II YEAR 1 st SEMESTER Subject: Data Structures (CSE 2.1.1) 1. Describe how arrays, records, linked structures,
LIGHTWEIGHT KEY MANAGEMENT SCHEME FOR HIERARCHICAL WIRELESS SENSOR NETWORKS
 LIGHTWEIGHT KEY MANAGEMENT SCHEME FOR HIERARCHICAL WIRELESS SENSOR NETWORKS Mohammed A. Al-taha 1 and Ra ad A. Muhajjar 2 1 Department of Computer Science, College of Science, Basrah University, Iraq 2
LIGHTWEIGHT KEY MANAGEMENT SCHEME FOR HIERARCHICAL WIRELESS SENSOR NETWORKS Mohammed A. Al-taha 1 and Ra ad A. Muhajjar 2 1 Department of Computer Science, College of Science, Basrah University, Iraq 2
International Journal of Computer Science Trends and Technology (IJCST) Volume 5 Issue 4, Jul Aug 2017
 RESEARCH ARTICLE OPEN ACCESS Optimizing Fully Homomorphic Encryption Algorithm using Greedy Approach in Cloud Computing Kirandeep Kaur [1], Jyotsna Sengupta [2] Department of Computer Science Punjabi University,
RESEARCH ARTICLE OPEN ACCESS Optimizing Fully Homomorphic Encryption Algorithm using Greedy Approach in Cloud Computing Kirandeep Kaur [1], Jyotsna Sengupta [2] Department of Computer Science Punjabi University,
Void main Technologies
 Sno Title Domain 1. A Cross Tenant Access Control (CTAC) Model for Cloud Computing: Formal Specification and Verification 2. A Lightweight Secure Data Sharing Scheme for Mobile Cloud Computing 3. A Modified
Sno Title Domain 1. A Cross Tenant Access Control (CTAC) Model for Cloud Computing: Formal Specification and Verification 2. A Lightweight Secure Data Sharing Scheme for Mobile Cloud Computing 3. A Modified
Academic Course Description
 BEC601 - COMPUTER COMMUNICATION AND NETWORKS Course (catalog) description Academic Course Description BHARATH UNIVERSITY Faculty of Engineering and Technology Department of Electronics and Communication
BEC601 - COMPUTER COMMUNICATION AND NETWORKS Course (catalog) description Academic Course Description BHARATH UNIVERSITY Faculty of Engineering and Technology Department of Electronics and Communication
International Journal of Scientific & Engineering Research, Volume 4, Issue 7, July-2013 ISSN
 1 Review: Boosting Classifiers For Intrusion Detection Richa Rawat, Anurag Jain ABSTRACT Network and host intrusion detection systems monitor malicious activities and the management station is a technique
1 Review: Boosting Classifiers For Intrusion Detection Richa Rawat, Anurag Jain ABSTRACT Network and host intrusion detection systems monitor malicious activities and the management station is a technique
AI: A UAE Perspective. Nawaf I. Almoosa Deputy Director - EBTIC March 7 th 2018
 AI: A UAE Perspective Nawaf I. Almoosa Deputy Director - EBTIC March 7 th 2018 2 EBTIC Overview 3 Our Model Research & Innovation Structure Partners and Target Sectors Sustainability Smart Air- Conditioning
AI: A UAE Perspective Nawaf I. Almoosa Deputy Director - EBTIC March 7 th 2018 2 EBTIC Overview 3 Our Model Research & Innovation Structure Partners and Target Sectors Sustainability Smart Air- Conditioning
Digital Humanities Digital Economics. Digital Arts. 05. One elective course from the courses offered at the university faculties
 Table 1. First study cycle 1 Year 1 semester 01. 10.9.AITMIR.1101.C е-democracy 02. 04.0.AITMIR.1102.C е-management 03. 08.9.AITMIR.1103.C е-ethics 04. One elective course from the following list 1. 08.0.AITMIR.1104.MaE
Table 1. First study cycle 1 Year 1 semester 01. 10.9.AITMIR.1101.C е-democracy 02. 04.0.AITMIR.1102.C е-management 03. 08.9.AITMIR.1103.C е-ethics 04. One elective course from the following list 1. 08.0.AITMIR.1104.MaE
Communication Networks & Cyber Security Workshop and Sixteenth GISFI Standardisation Series Meeting (GSSM),
 Series of GISFI s Five Years Anniversary First Series Event PROGRAMME Communication Networks & Cyber Security Workshop and Sixteenth GISFI Standardisation Series Meeting (GSSM), March 10-12, 2014 Organizing
Series of GISFI s Five Years Anniversary First Series Event PROGRAMME Communication Networks & Cyber Security Workshop and Sixteenth GISFI Standardisation Series Meeting (GSSM), March 10-12, 2014 Organizing
Saint Petersburg Electrotechnical University "LETI" (ETU "LETI") , Saint Petersburg, Russian FederationProfessoraPopova str.
 Saint Petersburg Electrotechnical University "LETI" (ETU "LETI") 197376, Saint Petersburg, Russian FederationProfessoraPopova str., 5 Master s program "Computer Science and Knowledge Discovery" Professor
Saint Petersburg Electrotechnical University "LETI" (ETU "LETI") 197376, Saint Petersburg, Russian FederationProfessoraPopova str., 5 Master s program "Computer Science and Knowledge Discovery" Professor
Indian Silicon Technologies 2013
 SI.No Topics IEEE YEAR 1. An RFID Based Solution for Real-Time Patient Surveillance and data Processing Bio- Metric System using FPGA 2. Real-time Binary Shape Matching System Based on FPGA 3. An Optimized
SI.No Topics IEEE YEAR 1. An RFID Based Solution for Real-Time Patient Surveillance and data Processing Bio- Metric System using FPGA 2. Real-time Binary Shape Matching System Based on FPGA 3. An Optimized
DOTNET PROJECTS. DOTNET Projects. I. IEEE based IOT IEEE BASED CLOUD COMPUTING
 DOTNET PROJECTS I. IEEE based IOT 1. A Fuzzy Model-based Integration Framework for Vision-based Intelligent Surveillance Systems 2. Learning communities in social networks and their relationship with the
DOTNET PROJECTS I. IEEE based IOT 1. A Fuzzy Model-based Integration Framework for Vision-based Intelligent Surveillance Systems 2. Learning communities in social networks and their relationship with the
DEPARTMENT OF COMPUTER SCIENCE
 Department of Computer Science 1 DEPARTMENT OF COMPUTER SCIENCE Office in Computer Science Building, Room 279 (970) 491-5792 cs.colostate.edu (http://www.cs.colostate.edu) Professor L. Darrell Whitley,
Department of Computer Science 1 DEPARTMENT OF COMPUTER SCIENCE Office in Computer Science Building, Room 279 (970) 491-5792 cs.colostate.edu (http://www.cs.colostate.edu) Professor L. Darrell Whitley,
ECE 646 Cryptography and Computer Network Security. Kris Gaj Research and teaching interests:
 646 Cryptography and Computer Network Security Course web page: web page Courses 646 Kris Gaj Research and teaching interests: cryptography network security computer arithmetic FPGA & ASIC design and testing
646 Cryptography and Computer Network Security Course web page: web page Courses 646 Kris Gaj Research and teaching interests: cryptography network security computer arithmetic FPGA & ASIC design and testing
IEEE 2013 JAVA PROJECTS Contact No: KNOWLEDGE AND DATA ENGINEERING
 IEEE 2013 JAVA PROJECTS www.chennaisunday.com Contact No: 9566137117 KNOWLEDGE AND DATA ENGINEERING (DATA MINING) 1. A Fast Clustering-Based Feature Subset Selection Algorithm for High Dimensional Data
IEEE 2013 JAVA PROJECTS www.chennaisunday.com Contact No: 9566137117 KNOWLEDGE AND DATA ENGINEERING (DATA MINING) 1. A Fast Clustering-Based Feature Subset Selection Algorithm for High Dimensional Data
Programme. Legal Instruments for the Internet Economy. Building Capacity and Implementing Regulation. Malta, 14 th to 19 th September, 2015
 A MALTA COMMONWEALTH THIRD COUNTRY TRAINING PROGRAMME Programme Legal Instruments for the Internet Economy Building Capacity and Implementing Regulation Malta, 14 th to 19 th September, 2015 www.diplomacy.edu/courses/legalinstruments2015
A MALTA COMMONWEALTH THIRD COUNTRY TRAINING PROGRAMME Programme Legal Instruments for the Internet Economy Building Capacity and Implementing Regulation Malta, 14 th to 19 th September, 2015 www.diplomacy.edu/courses/legalinstruments2015
Course Curriculum for Master Degree in Network Engineering and Security
 Course Curriculum for Master Degree in Network Engineering and Security The Master Degree in Network Engineering and Security is awarded by the Faculty of Graduate Studies at Jordan University of Science
Course Curriculum for Master Degree in Network Engineering and Security The Master Degree in Network Engineering and Security is awarded by the Faculty of Graduate Studies at Jordan University of Science
ONLINE BIOMETRIC VERIFICATION USING APACHE STORM ON PUBLIC CLOUD
 ONLINE BIOMETRIC VERIFICATION USING APACHE STORM ON PUBLIC CLOUD Prof. Shraddha More 1, Jigar Maniyar 2, Mrunmayee Vartak 3, Prasobh Nair 4, Chirag Raul 5 1,2,3,4,5 Department of Information Technology,
ONLINE BIOMETRIC VERIFICATION USING APACHE STORM ON PUBLIC CLOUD Prof. Shraddha More 1, Jigar Maniyar 2, Mrunmayee Vartak 3, Prasobh Nair 4, Chirag Raul 5 1,2,3,4,5 Department of Information Technology,
SRM UNIVERSITY FACULTY OF ENGINEERING AND TECHNOLOGY SCHOOL OF COMPUTING DEPARTMENT OF CSE COURSE PLAN
 Course Code : CS0331 Course Title : E Commerce Semester : V Course Time : July Dec 2009 SRM UNIVERSITY FACULTY OF ENGINEERING AND TECHNOLOGY SCHOOL OF COMPUTING DEPARTMENT OF CSE COURSE PLAN DAY Monday
Course Code : CS0331 Course Title : E Commerce Semester : V Course Time : July Dec 2009 SRM UNIVERSITY FACULTY OF ENGINEERING AND TECHNOLOGY SCHOOL OF COMPUTING DEPARTMENT OF CSE COURSE PLAN DAY Monday
The University of Jordan. Accreditation & Quality Assurance Center. Curriculum for Doctorate Degree
 Accreditation & Quality Assurance Center Curriculum for Doctorate Degree 1. Faculty King Abdullah II School for Information Technology 2. Department Computer Science الدكتوراة في علم الحاسوب (Arabic).3
Accreditation & Quality Assurance Center Curriculum for Doctorate Degree 1. Faculty King Abdullah II School for Information Technology 2. Department Computer Science الدكتوراة في علم الحاسوب (Arabic).3
INSTITUTE OF AERONAUTICAL ENGINEERING (Autonomous) Dundigal, Hyderabad
 INSTITUTE OF AERONAUTICAL ENGINEERING (Autonomous) Dundigal, yderabad - 500 043 COMPUTER SCIENCE AND ENGINEERING COURSE DESCRIPTION FORM Course Title Course Code Regulation Course Structure Course Coordinator
INSTITUTE OF AERONAUTICAL ENGINEERING (Autonomous) Dundigal, yderabad - 500 043 COMPUTER SCIENCE AND ENGINEERING COURSE DESCRIPTION FORM Course Title Course Code Regulation Course Structure Course Coordinator
What makes a hot topic hot? An NSF Perspective
 What makes a hot topic hot? An NSF Perspective August 2015 Jeremy Epstein Program Officer National Science Foundation SRI International NSF Mission Mission: promote the progress of science; to advance
What makes a hot topic hot? An NSF Perspective August 2015 Jeremy Epstein Program Officer National Science Foundation SRI International NSF Mission Mission: promote the progress of science; to advance
CompTIA Security+ Study Guide (SY0-501)
 CompTIA Security+ Study Guide (SY0-501) Syllabus Session 1 At the end of this session, students will understand what risk is and the basics of what it means to have security in an organization. This includes
CompTIA Security+ Study Guide (SY0-501) Syllabus Session 1 At the end of this session, students will understand what risk is and the basics of what it means to have security in an organization. This includes
A QUALITY SUPPORT FOR YOUR FINAL YEAR PROJECT DEVELOPMENT & RESEARCH WORK ANDROID TOPICS RESEARCH AND CONFERENCE ORIENTED TITLES
 A QUALITY SUPPORT FOR YOUR FINAL YEAR PROJECT DEVELOPMENT & RESEARCH WORK ANDROID TOPICS RESEARCH AND CONFERENCE ORIENTED TITLES We are experts in, CODING SUPPORT FOR FINAL YEAR PROJECT JOURNAL PREPARATION
A QUALITY SUPPORT FOR YOUR FINAL YEAR PROJECT DEVELOPMENT & RESEARCH WORK ANDROID TOPICS RESEARCH AND CONFERENCE ORIENTED TITLES We are experts in, CODING SUPPORT FOR FINAL YEAR PROJECT JOURNAL PREPARATION
HK ASTRI FinTech Initiative
 HK ASTRI FinTech Initiative October 2016 HK Financial Services Industry (FSI) FSI: one of HK s four pillar industries HK ranked third in the Global Financial Centres Index (GFCI) by London released in
HK ASTRI FinTech Initiative October 2016 HK Financial Services Industry (FSI) FSI: one of HK s four pillar industries HK ranked third in the Global Financial Centres Index (GFCI) by London released in
Name Qualification Designation Specialization Experience (in years) Dr. Shaily Jain PhD Faculty Networking, MP SoC
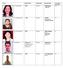 Name Qualification Designation Specialization Experience (in years) Dr. Shaily Jain PhD Networking, MP SoC 9.5 Dr. Sapna Saxena PhD Parallel Programming Network Security 14 Dr. Tanu Sharma PhD Biotechnology
Name Qualification Designation Specialization Experience (in years) Dr. Shaily Jain PhD Networking, MP SoC 9.5 Dr. Sapna Saxena PhD Parallel Programming Network Security 14 Dr. Tanu Sharma PhD Biotechnology
Kris Gaj Research and teaching interests: ECE 646 Cryptography and Computer Network Security. Course web page: Contact: ECE 646
 646 and Computer Network Security Course web page: web page Courses 646 Kris Gaj Research and teaching interests: cryptography network security computer arithmetic FPGA & ASIC design and testing Contact:
646 and Computer Network Security Course web page: web page Courses 646 Kris Gaj Research and teaching interests: cryptography network security computer arithmetic FPGA & ASIC design and testing Contact:
Fujitsu World Tour 2018
 Fujitsu World Tour 2018 May 30, 2018 #FujitsuWorldTour 1 Copyright 2018 FUJITSU Security and Privacy of Big Data A NIST Perspective Arnab Roy Fujitsu Laboratories of America Co-Chair, NIST Big Data WG:
Fujitsu World Tour 2018 May 30, 2018 #FujitsuWorldTour 1 Copyright 2018 FUJITSU Security and Privacy of Big Data A NIST Perspective Arnab Roy Fujitsu Laboratories of America Co-Chair, NIST Big Data WG:
Diversified Caesar Cipher for Impeccable Security
 Vol.11, No.3 (2017), pp.33-40 http://dx.doi.org/10.14257/ijsia.2017.11.2.04 Diversified Caesar Cipher for Impeccable Security 1 Priya Verma, 2 Gurjot Singh Gaba, 3 Rajan Miglani * 1,2,3 Discipline of Electronics
Vol.11, No.3 (2017), pp.33-40 http://dx.doi.org/10.14257/ijsia.2017.11.2.04 Diversified Caesar Cipher for Impeccable Security 1 Priya Verma, 2 Gurjot Singh Gaba, 3 Rajan Miglani * 1,2,3 Discipline of Electronics
CYBER FRAUD & DATA BREACHES 16 CPE s May 16-17, 2018
 CYBER FRAUD & DATA BREACHES 16 CPE s May 16-17, 2018 Cyber fraud attacks happen; they can t all be stopped. The higher order question must be how can we, as fraud examiners and assurance professionals,
CYBER FRAUD & DATA BREACHES 16 CPE s May 16-17, 2018 Cyber fraud attacks happen; they can t all be stopped. The higher order question must be how can we, as fraud examiners and assurance professionals,
COMPUTER SCIENCE INTERNET SCIENCE AND TECHOLOGY HUMAN MEDIA INTERACTION BUSINESS INFORMATION TECHNOLOGY
 COMPUTER SCIENCE INTERNET SCIENCE AND TECHOLOGY HUMAN MEDIA INTERACTION BUSINESS INFORMATION TECHNOLOGY UNIVERSITY OF DIGITAL REVOLUTION. Fourth industrial revolution is upon us and you can be part of
COMPUTER SCIENCE INTERNET SCIENCE AND TECHOLOGY HUMAN MEDIA INTERACTION BUSINESS INFORMATION TECHNOLOGY UNIVERSITY OF DIGITAL REVOLUTION. Fourth industrial revolution is upon us and you can be part of
ISSN: (Online) Volume 3, Issue 9, September 2015 International Journal of Advance Research in Computer Science and Management Studies
 ISSN: 2321-7782 (Online) Volume 3, Issue 9, September 2015 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online
ISSN: 2321-7782 (Online) Volume 3, Issue 9, September 2015 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online
Hybrid Key Encryption using Cryptography for Wireless Sensor Networks V-Algorithm
 ISSN : 0974 5572 International Science Press Volume 9 Number 40 2016 Hybrid Key Encryption using Cryptography for Wireless Sensor Networks V-Algorithm D. Anitha a S. Aruna a Mathew a K. Mathew a and Devilal
ISSN : 0974 5572 International Science Press Volume 9 Number 40 2016 Hybrid Key Encryption using Cryptography for Wireless Sensor Networks V-Algorithm D. Anitha a S. Aruna a Mathew a K. Mathew a and Devilal
2 nd Year. Module Basket of Courses Duration Credit Offered Status. 12 Weeks 4 NPTEL Programming in Java
 MAULANA ABUL KALAM AZAD UNIVERSITY OF TECHNOLOGY, WEST BENGAL List of Online Courses for 2nd Year, 3rd Year and 4th Year B.Tech Courses of IT and CSE for Additional Credit Earning 2 nd Year Module Basket
MAULANA ABUL KALAM AZAD UNIVERSITY OF TECHNOLOGY, WEST BENGAL List of Online Courses for 2nd Year, 3rd Year and 4th Year B.Tech Courses of IT and CSE for Additional Credit Earning 2 nd Year Module Basket
Leading the Digital Transformation from the Centre of Government
 37th Meeting of Senior Officials from Centres of Government Leading the Digital Transformation from the Centre of Government Dublin, Ireland, 8-9 November 2018 Agenda 2 GOV/PGC/MPM/A(2018)1/REV1 19.00
37th Meeting of Senior Officials from Centres of Government Leading the Digital Transformation from the Centre of Government Dublin, Ireland, 8-9 November 2018 Agenda 2 GOV/PGC/MPM/A(2018)1/REV1 19.00
IEEE Project Titles
 www.chennaisunday.com PH:9566137117 IEEE Project Titles -2018 S.No Project Title Year CLOUD COMPUTING 1 A Collaborative Key Management Protocol in Ciphertext Policy Attribute-Based Encryption for Cloud
www.chennaisunday.com PH:9566137117 IEEE Project Titles -2018 S.No Project Title Year CLOUD COMPUTING 1 A Collaborative Key Management Protocol in Ciphertext Policy Attribute-Based Encryption for Cloud
YMCA UNIVERSITY OF SCIENCE AND TECHNOLOGY, FARIDABAD
 YMCA UNIVERSITY OF SCIENCE AND TECHNOLOGY, FARIDABAD DEPARTMENT OF COMPUTER ENGINEERING List of Ph.D. Students Enrolled in the University for the year: - 2010-2011 S. No. Name of the student Title/ Topic
YMCA UNIVERSITY OF SCIENCE AND TECHNOLOGY, FARIDABAD DEPARTMENT OF COMPUTER ENGINEERING List of Ph.D. Students Enrolled in the University for the year: - 2010-2011 S. No. Name of the student Title/ Topic
Star: Sla-Aware Autonomic Management of Cloud Resources
 Star: Sla-Aware Autonomic Management of Cloud Resources Sakshi Patil 1, Meghana N Rathod 2, S. A Madival 3, Vivekanand M Bonal 4 1, 2 Fourth Sem M. Tech Appa Institute of Engineering and Technology Karnataka,
Star: Sla-Aware Autonomic Management of Cloud Resources Sakshi Patil 1, Meghana N Rathod 2, S. A Madival 3, Vivekanand M Bonal 4 1, 2 Fourth Sem M. Tech Appa Institute of Engineering and Technology Karnataka,
Void main Technologies
 SNO TITLE Domain 1. A Hybrid Approach for Detecting Automated Spammers in Twitter Data mining 2. A Key-Policy Attribute-Based Temporary Keyword Search scheme for Secure Storage 3. A Lightweight Secure
SNO TITLE Domain 1. A Hybrid Approach for Detecting Automated Spammers in Twitter Data mining 2. A Key-Policy Attribute-Based Temporary Keyword Search scheme for Secure Storage 3. A Lightweight Secure
M.B.Srinivas Chairman, IEEE Hyderabad Section General Co-Chair, TENCON 2008
 M.B.Srinivas Chairman, IEEE Hyderabad Section General Co-Chair, TENCON 2008 Conference Details To be Held in Hyderabad, located in South-Central India, about 800KM North of Bangalore Hyderabad is about
M.B.Srinivas Chairman, IEEE Hyderabad Section General Co-Chair, TENCON 2008 Conference Details To be Held in Hyderabad, located in South-Central India, about 800KM North of Bangalore Hyderabad is about
Security in ECE Systems
 Lecture 11 Information Security ECE 197SA Systems Appreciation Security in ECE Systems Information security Information can be very valuable Secure communication important to protect information Today
Lecture 11 Information Security ECE 197SA Systems Appreciation Security in ECE Systems Information security Information can be very valuable Secure communication important to protect information Today
Mobile Wireless Sensor Network enables convergence of ubiquitous sensor services
 1 2005 Nokia V1-Filename.ppt / yyyy-mm-dd / Initials Mobile Wireless Sensor Network enables convergence of ubiquitous sensor services Dr. Jian Ma, Principal Scientist Nokia Research Center, Beijing 2 2005
1 2005 Nokia V1-Filename.ppt / yyyy-mm-dd / Initials Mobile Wireless Sensor Network enables convergence of ubiquitous sensor services Dr. Jian Ma, Principal Scientist Nokia Research Center, Beijing 2 2005
Multiple Encryption using ECC and Its Time Complexity Analysis
 Volume 3, Issue 11, November-2016, pp. 568-572 ISSN (O): 2349-7084 International Journal of Computer Engineering In Research Trends Available online at: www.ijcert.org Multiple Encryption using ECC and
Volume 3, Issue 11, November-2016, pp. 568-572 ISSN (O): 2349-7084 International Journal of Computer Engineering In Research Trends Available online at: www.ijcert.org Multiple Encryption using ECC and
Innovation policy for Industry 4.0
 Innovation policy for Industry 4.0 Remarks from Giorgio Mosca Chair of Cybersecurity Steering Committee Confindustria Digitale Director Strategy & Technologies - Security & IS Division, Leonardo Agenda
Innovation policy for Industry 4.0 Remarks from Giorgio Mosca Chair of Cybersecurity Steering Committee Confindustria Digitale Director Strategy & Technologies - Security & IS Division, Leonardo Agenda
ECE 646 Cryptography and Computer Network Security. Course web page: Kris Gaj Research and teaching interests: Contact: ECE web page Courses ECE 646
 646 Cryptography and Computer Network Security Course web page: web page Courses 646 Kris Gaj Research and teaching interests: cryptography network security computer arithmetic FPGA & ASIC design and testing
646 Cryptography and Computer Network Security Course web page: web page Courses 646 Kris Gaj Research and teaching interests: cryptography network security computer arithmetic FPGA & ASIC design and testing
Analysis of Cryptography and Pseudorandom Numbers
 ISSN: 2454-2377 Volume 2, Issue 2, June 2016 Analysis of Cryptography and Pseudorandom Numbers Richa Agarwal Student, M. Tech., Computer Science, Invertis University, Bareilly, India Abstract: With the
ISSN: 2454-2377 Volume 2, Issue 2, June 2016 Analysis of Cryptography and Pseudorandom Numbers Richa Agarwal Student, M. Tech., Computer Science, Invertis University, Bareilly, India Abstract: With the
Security Standardization
 ISO-ITU ITU Cooperation on Security Standardization Dr. Walter Fumy Chairman ISO/IEC JTC 1/SC 27 Chief Scientist, Bundesdruckerei GmbH, Germany 7th ETSI Security Workshop - Sophia Antipolis, January 2012
ISO-ITU ITU Cooperation on Security Standardization Dr. Walter Fumy Chairman ISO/IEC JTC 1/SC 27 Chief Scientist, Bundesdruckerei GmbH, Germany 7th ETSI Security Workshop - Sophia Antipolis, January 2012
The NIST Cybersecurity Framework
 The NIST Cybersecurity Framework U.S. German Standards Panel 2018 April 10, 2018 Adam.Sedgewick@nist.gov National Institute of Standards and Technology About NIST Agency of U.S. Department of Commerce
The NIST Cybersecurity Framework U.S. German Standards Panel 2018 April 10, 2018 Adam.Sedgewick@nist.gov National Institute of Standards and Technology About NIST Agency of U.S. Department of Commerce
DISCLOSURE PROTECTION OF SENSITIVE ATTRIBUTES IN COLLABORATIVE DATA MINING V. Uma Rani *1, Dr. M. Sreenivasa Rao *2, V. Theresa Vinayasheela *3
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 3 Issue 5 May, 2014 Page No. 5594-5599 DISCLOSURE PROTECTION OF SENSITIVE ATTRIBUTES IN COLLABORATIVE DATA MINING
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 3 Issue 5 May, 2014 Page No. 5594-5599 DISCLOSURE PROTECTION OF SENSITIVE ATTRIBUTES IN COLLABORATIVE DATA MINING
The Road Ahead for Healthcare Sector: What to Expect in Cybersecurity Session CS6, February 19, 2017 Donna F. Dodson, Chief Cybersecurity Advisor,
 The Road Ahead for Healthcare Sector: What to Expect in Cybersecurity Session CS6, February 19, 2017 Donna F. Dodson, Chief Cybersecurity Advisor, National Institute of Standards and Technology 1 Speaker
The Road Ahead for Healthcare Sector: What to Expect in Cybersecurity Session CS6, February 19, 2017 Donna F. Dodson, Chief Cybersecurity Advisor, National Institute of Standards and Technology 1 Speaker
REV2019 Conference Schedule
 REV2019 Conference Schedule Date Time Workshop Title Resource 3-2-2019 9:30am to 11.00am 11.15-12.45pm 1.30pm to 3:00pm 3.15pm- 4.45pm Track 1A Track 1B An Open and Improved VISIR System Through PILAR
REV2019 Conference Schedule Date Time Workshop Title Resource 3-2-2019 9:30am to 11.00am 11.15-12.45pm 1.30pm to 3:00pm 3.15pm- 4.45pm Track 1A Track 1B An Open and Improved VISIR System Through PILAR
International Journal of Computer Engineering and Applications, Volume XI, Issue XII, Dec. 17, ISSN
 International Journal of Computer Engineering and Applications, Volume XI, Issue XII, Dec. 17, www.ijcea.com ISSN 2321-3469 DYNAMIC SELECTION OF ALGORITHM TO IMPROVE SECURITY Amit Jain 1 1 Computer Science
International Journal of Computer Engineering and Applications, Volume XI, Issue XII, Dec. 17, www.ijcea.com ISSN 2321-3469 DYNAMIC SELECTION OF ALGORITHM TO IMPROVE SECURITY Amit Jain 1 1 Computer Science
Academic Course Description
 BEC012 - CRYPTOGRAPHY AND NETWORK SECURITY Academic Course Description BHARATH UNIVERSITY Faculty of Engineering and Technology Department of Electronics and Communication Engineering BEC012 Cryptography
BEC012 - CRYPTOGRAPHY AND NETWORK SECURITY Academic Course Description BHARATH UNIVERSITY Faculty of Engineering and Technology Department of Electronics and Communication Engineering BEC012 Cryptography
New Horizons in Audit & Assurance
 IIA Hyderabad Chapter brings you a Seminar on New Horizons in Audit & Assurance 6 CPE Hours for IIA Members Date : 04 th January 2018 1 Schedule... SCHEDULE 09:00 AM to 09:30 AM Seminar Registration 09:30
IIA Hyderabad Chapter brings you a Seminar on New Horizons in Audit & Assurance 6 CPE Hours for IIA Members Date : 04 th January 2018 1 Schedule... SCHEDULE 09:00 AM to 09:30 AM Seminar Registration 09:30
An Overview of Smart Sustainable Cities and the Role of Information and Communication Technologies (ICTs)
 An Overview of Smart Sustainable Cities and the Role of Information and Communication Technologies (ICTs) Sekhar KONDEPUDI Ph.D. Vice Chair FG-SSC & Coordinator Working Group 1 ICT role and roadmap for
An Overview of Smart Sustainable Cities and the Role of Information and Communication Technologies (ICTs) Sekhar KONDEPUDI Ph.D. Vice Chair FG-SSC & Coordinator Working Group 1 ICT role and roadmap for
Kusum Lata, Sugandha Sharma
 International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2017 IJSRCSEIT Volume 2 Issue 4 ISSN : 2456-3307 A Survey on Cloud Computing and Mobile Cloud Computing
International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2017 IJSRCSEIT Volume 2 Issue 4 ISSN : 2456-3307 A Survey on Cloud Computing and Mobile Cloud Computing
ACKNOWLEDGEMENT. my PhD Supervisor Dr. Vidhyacharan Bhaskar, Professor, Department of
 iv ACKNOWLEDGEMENT It is my pleasant duty to thank a large number of people for the various forms of help, encouragement and support that they have provided during the time I have been working on this
iv ACKNOWLEDGEMENT It is my pleasant duty to thank a large number of people for the various forms of help, encouragement and support that they have provided during the time I have been working on this
Information Security: Principles and Practice Second Edition. Mark Stamp
 Information Security: Principles and Practice Second Edition Mark Stamp August 10, 2009 Contents Preface Second Edition Preface About The Author Acknowledgments xvii xix xxiii xxv 1 Introduction 1 1.1
Information Security: Principles and Practice Second Edition Mark Stamp August 10, 2009 Contents Preface Second Edition Preface About The Author Acknowledgments xvii xix xxiii xxv 1 Introduction 1 1.1
( It will be applied from Fall)
 İZMİR INSTITUTE OF TECHNOLOGY GRADUATE SCHOOL OF ENGINEERING AND SCIENCES DEPARTMENT OF COMPUTER ENGINEERING MASTER OF SCIENCE PROGRAM IN COMPUTER ENGINEERING Core Courses ECTS *CENG 590 Seminar (0-2)
İZMİR INSTITUTE OF TECHNOLOGY GRADUATE SCHOOL OF ENGINEERING AND SCIENCES DEPARTMENT OF COMPUTER ENGINEERING MASTER OF SCIENCE PROGRAM IN COMPUTER ENGINEERING Core Courses ECTS *CENG 590 Seminar (0-2)
Public Sector Cyber Security Series
 2018 Staying ahead of evolving threats Public Sector Cyber Security Series program Sydney 10 th September Melbourne 11 th September Canberra 12 th September Brisbane 19 th September Wellington 20 th September
2018 Staying ahead of evolving threats Public Sector Cyber Security Series program Sydney 10 th September Melbourne 11 th September Canberra 12 th September Brisbane 19 th September Wellington 20 th September
Programme Outcome COURSE OUTCOMES MCA
 Programme Outcome PO1: To provide trained human resource for the IT industry. COURSE OUTCOMES MCA MCA 101 : Object Oriented Programming CO1 The students develops a sound approach to problem solving using
Programme Outcome PO1: To provide trained human resource for the IT industry. COURSE OUTCOMES MCA MCA 101 : Object Oriented Programming CO1 The students develops a sound approach to problem solving using
Cyber Security 2018: Building Resilience Now and For the Future Mar 1 2, 2018 Ottawa
 Agenda and Speakers Cyber Security 2018: Building Resilience Now and For the Future Mar 1 2, 2018 Ottawa Thursday, March 01, 2018 7:30 am Registration and Continental Breakfast 8:00 am Opening Remarks
Agenda and Speakers Cyber Security 2018: Building Resilience Now and For the Future Mar 1 2, 2018 Ottawa Thursday, March 01, 2018 7:30 am Registration and Continental Breakfast 8:00 am Opening Remarks
Post-Quantum Cryptography A Collective Challenge
 Post-Quantum Cryptography A Collective Challenge Christophe Petit University of Oxford Mathematical Institute Christophe Petit -Oxford Crypto Day 1 Cryptography is very useful Cryptography is the science
Post-Quantum Cryptography A Collective Challenge Christophe Petit University of Oxford Mathematical Institute Christophe Petit -Oxford Crypto Day 1 Cryptography is very useful Cryptography is the science
IJENS-RPG [IJENS Researchers Promotion Group] ID: IJENS-1017-Joby
![IJENS-RPG [IJENS Researchers Promotion Group] ID: IJENS-1017-Joby IJENS-RPG [IJENS Researchers Promotion Group] ID: IJENS-1017-Joby](/thumbs/74/70155235.jpg) Dr. P.P.Joby Contact Address Professor & Dean, Department of Computer Science & Engineering, MBC College of Engineering and Technology, Kuttikanam, Peermade, Idukki Dt, Kerala-685531. Permanent Address
Dr. P.P.Joby Contact Address Professor & Dean, Department of Computer Science & Engineering, MBC College of Engineering and Technology, Kuttikanam, Peermade, Idukki Dt, Kerala-685531. Permanent Address
safely connecting to future smart hospital & healthcare
 Organizer Funding Organization Sponsors CYBER SECURITY ON MEDICAL AND HEALTHCARE SYSTEM safely connecting to future smart hospital & healthcare SYMPOSIUM CUM WORKSHOP Workshop: 30 November 2017 Symposium:
Organizer Funding Organization Sponsors CYBER SECURITY ON MEDICAL AND HEALTHCARE SYSTEM safely connecting to future smart hospital & healthcare SYMPOSIUM CUM WORKSHOP Workshop: 30 November 2017 Symposium:
Image Processing and Watermark
 IJCST Vo l. 7, Is s u e 1, Ja n - Ma r c h 2016 ISSN : 0976-8491 (Online) ISSN : 2229-4333 (Print) Image Processing and Watermark 1 Dr. Amit Verma, 2 Navdeep Kaur Gill 1,2 Dept. Computer Science and Engineering,
IJCST Vo l. 7, Is s u e 1, Ja n - Ma r c h 2016 ISSN : 0976-8491 (Online) ISSN : 2229-4333 (Print) Image Processing and Watermark 1 Dr. Amit Verma, 2 Navdeep Kaur Gill 1,2 Dept. Computer Science and Engineering,
Degree Branch / Specialization College University CSE SONA COLLEGE OF TECHNOLOGY : ASSISTANT PROFESSOR (SENIOR GRADE) ASSISTANT PROFESSOR
 FACULTY PROFILE Name Designation Email ID : NISHA SOMS : ASSISTANT PROFESSOR (SENIOR GRADE) : nishasoms.cse@srit.org Area of Specialization : Wireless Ad Hoc Networks, Mobile Computing Cryptography and
FACULTY PROFILE Name Designation Email ID : NISHA SOMS : ASSISTANT PROFESSOR (SENIOR GRADE) : nishasoms.cse@srit.org Area of Specialization : Wireless Ad Hoc Networks, Mobile Computing Cryptography and
Announcements. me your survey: See the Announcements page. Today. Reading. Take a break around 10:15am. Ack: Some figures are from Coulouris
 Announcements Email me your survey: See the Announcements page Today Conceptual overview of distributed systems System models Reading Today: Chapter 2 of Coulouris Next topic: client-side processing (HTML,
Announcements Email me your survey: See the Announcements page Today Conceptual overview of distributed systems System models Reading Today: Chapter 2 of Coulouris Next topic: client-side processing (HTML,
A Combined Encryption Compression Scheme Using Chaotic Maps
 BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 13, No 2 Sofia 2013 Print ISSN: 1311-9702; Online ISSN: 1314-4081 DOI: 10.2478/cait-2013-0016 A Combined Encryption Compression
BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 13, No 2 Sofia 2013 Print ISSN: 1311-9702; Online ISSN: 1314-4081 DOI: 10.2478/cait-2013-0016 A Combined Encryption Compression
1. INTRODUCTION 2. PROPOSED SYSTEM. Parashar Sangle, IJECS Volume 05 Issue 12 Dec., 2016 Page No Page 19489
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN: 2319-7242 Volume 5 Issue 12 Dec. 2016, Page No. 19489-19493 Data Security System in Cloud by Using Fog Computing and Data Mining
www.ijecs.in International Journal Of Engineering And Computer Science ISSN: 2319-7242 Volume 5 Issue 12 Dec. 2016, Page No. 19489-19493 Data Security System in Cloud by Using Fog Computing and Data Mining
OUR VISION To be a global leader of computing research in identified areas that will bring positive impact to the lives of citizens and society.
 Join the Innovation Qatar Computing Research Institute (QCRI) is a national research institute established in 2010 by Qatar Foundation for Education, Science and Community Development. As a primary constituent
Join the Innovation Qatar Computing Research Institute (QCRI) is a national research institute established in 2010 by Qatar Foundation for Education, Science and Community Development. As a primary constituent
National Institute of Standards and Technology
 National Institute of Standards and Technology April 2017 1 ITL Mission ITL promotes U.S. innovation and industrial competitiveness by advancing measurement science, standards, and related technology through
National Institute of Standards and Technology April 2017 1 ITL Mission ITL promotes U.S. innovation and industrial competitiveness by advancing measurement science, standards, and related technology through
Encryption Providing Perfect Secrecy COPYRIGHT 2001 NON-ELEPHANT ENCRYPTION SYSTEMS INC.
 Encryption Providing Perfect Secrecy Presented at Calgary Unix Users Group. November 27, 2001 by: Mario Forcinito, PEng, PhD With many thanks to Prof. Aiden Bruen from the Mathematics Department, University
Encryption Providing Perfect Secrecy Presented at Calgary Unix Users Group. November 27, 2001 by: Mario Forcinito, PEng, PhD With many thanks to Prof. Aiden Bruen from the Mathematics Department, University
Academic Course Description
 BET008 WIRELESS NETWORKS Academic Course Description Course (catalog) description BHARATH UNIVERSITY Faculty of Engineering and Technology Department of Electronics and Communication Engineering BET008
BET008 WIRELESS NETWORKS Academic Course Description Course (catalog) description BHARATH UNIVERSITY Faculty of Engineering and Technology Department of Electronics and Communication Engineering BET008
Key Findings from the Global State of Information Security Survey 2017 Indonesian Insights
 www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
Introduction to SPCOM Group (Signal Processing, Communication & IIT Kanpur. Abhishek Gupta, EE
 Introduction to SPCOM Group (Signal Processing, Communication & Networks) @ IIT Kanpur Abhishek Gupta, EE SPCOM Research Areas NET Comm. Networks Optical Networks Signal Proc. in Networks Network Localization
Introduction to SPCOM Group (Signal Processing, Communication & Networks) @ IIT Kanpur Abhishek Gupta, EE SPCOM Research Areas NET Comm. Networks Optical Networks Signal Proc. in Networks Network Localization
Aspects of Enhancing Security in Software Development Life Cycle
 Advances in Computational Sciences and Technology ISSN 0973-6107 Volume 10, Number 2 (2017) pp. 203-210 Research India Publications http://www.ripublication.com Aspects of Enhancing Security in Software
Advances in Computational Sciences and Technology ISSN 0973-6107 Volume 10, Number 2 (2017) pp. 203-210 Research India Publications http://www.ripublication.com Aspects of Enhancing Security in Software
Digital Communication Networks
 Digital Communication Networks MIT PROFESSIONAL INSTITUTE, 6.20s July 25-29, 2005 Professor Muriel Medard, MIT Professor, MIT Slide 1 Digital Communication Networks Introduction Slide 2 Course syllabus
Digital Communication Networks MIT PROFESSIONAL INSTITUTE, 6.20s July 25-29, 2005 Professor Muriel Medard, MIT Professor, MIT Slide 1 Digital Communication Networks Introduction Slide 2 Course syllabus
National Cybersecurity Challenges and NIST. Matthew Scholl Chief Computer Security Division
 National Cybersecurity Challenges and NIST Matthew Scholl Chief Computer Security Division National Archives The Importance of Standards Article I, Section 8: The Congress shall have the power to fix the
National Cybersecurity Challenges and NIST Matthew Scholl Chief Computer Security Division National Archives The Importance of Standards Article I, Section 8: The Congress shall have the power to fix the
Network Intrusion Detection System Using Fuzzy Logic Ppt
 Network Intrusion Detection System Using Fuzzy Logic Ppt Network intrusion detection, such as neural networks, appeared at a historic Although the approaches based on expert systems have high accuracy,
Network Intrusion Detection System Using Fuzzy Logic Ppt Network intrusion detection, such as neural networks, appeared at a historic Although the approaches based on expert systems have high accuracy,
Protection Against DDOS Using Secure Code Propagation In The VANETs
 Protection Against DDOS Using Secure Code Propagation In The VANETs Mandeep Kaur, Manish Mahajan Mandeepcheema6@gmail.com,cgccoe.hodcse@gmail.com ABSTRACT--VANETs are the vehicular networks used to connect
Protection Against DDOS Using Secure Code Propagation In The VANETs Mandeep Kaur, Manish Mahajan Mandeepcheema6@gmail.com,cgccoe.hodcse@gmail.com ABSTRACT--VANETs are the vehicular networks used to connect
Course Information
 Course Information 2018-2020 Master of Information Systems: Digital Business System Institutt for teknologi / Department of Technology Index Index... i 1 s... 1 1.1 Content... 1 1.2 Name... 1 1.3 Programme
Course Information 2018-2020 Master of Information Systems: Digital Business System Institutt for teknologi / Department of Technology Index Index... i 1 s... 1 1.1 Content... 1 1.2 Name... 1 1.3 Programme
COMP4109 : Applied Cryptography
 COMP4109 : Applied Cryptography Fall 2013 M. Jason Hinek Carleton University Applied Cryptography Day 2 information security cryptographic primitives unkeyed primitives NSA... one-way functions hash functions
COMP4109 : Applied Cryptography Fall 2013 M. Jason Hinek Carleton University Applied Cryptography Day 2 information security cryptographic primitives unkeyed primitives NSA... one-way functions hash functions
S. Indirakumari, A. Thilagavathy
 International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2017 IJSRCSEIT Volume 2 Issue 2 ISSN : 2456-3307 A Secure Verifiable Storage Deduplication Scheme
International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2017 IJSRCSEIT Volume 2 Issue 2 ISSN : 2456-3307 A Secure Verifiable Storage Deduplication Scheme
ANALYSIS OF AES ENCRYPTION WITH ECC
 ANALYSIS OF AES ENCRYPTION WITH ECC Samiksha Sharma Department of Computer Science & Engineering, DAV Institute of Engineering and Technology, Jalandhar, Punjab, India Vinay Chopra Department of Computer
ANALYSIS OF AES ENCRYPTION WITH ECC Samiksha Sharma Department of Computer Science & Engineering, DAV Institute of Engineering and Technology, Jalandhar, Punjab, India Vinay Chopra Department of Computer
School of Engineering and Technology. Department of Engineering
 1 2 School of Engineering and Technology Department of Engineering 3 Bachelor of Science in Communication Engineering The program focuses on the technical aspects of digital and analog communications,
1 2 School of Engineering and Technology Department of Engineering 3 Bachelor of Science in Communication Engineering The program focuses on the technical aspects of digital and analog communications,
Overview of Web Mining Techniques and its Application towards Web
 Overview of Web Mining Techniques and its Application towards Web *Prof.Pooja Mehta Abstract The World Wide Web (WWW) acts as an interactive and popular way to transfer information. Due to the enormous
Overview of Web Mining Techniques and its Application towards Web *Prof.Pooja Mehta Abstract The World Wide Web (WWW) acts as an interactive and popular way to transfer information. Due to the enormous
Cryptography Today. Ali El Kaafarani. Mathematical Institute Oxford University. 1 of 44
 Cryptography Today Ali El Kaafarani Mathematical Institute Oxford University 1 of 44 About the Course Regular classes with worksheets so you can work with some concrete examples (every Friday at 1pm).
Cryptography Today Ali El Kaafarani Mathematical Institute Oxford University 1 of 44 About the Course Regular classes with worksheets so you can work with some concrete examples (every Friday at 1pm).
Disquisition of a Novel Approach to Enhance Security in Data Mining
 Disquisition of a Novel Approach to Enhance Security in Data Mining Gurpreet Kaundal 1, Sheveta Vashisht 2 1 Student Lovely Professional University, Phagwara, Pin no. 144402 gurpreetkaundal03@gmail.com
Disquisition of a Novel Approach to Enhance Security in Data Mining Gurpreet Kaundal 1, Sheveta Vashisht 2 1 Student Lovely Professional University, Phagwara, Pin no. 144402 gurpreetkaundal03@gmail.com
Venue : Conference Hall, Second Floor YMCA Building Jai Singh Marg, Connaught Place, New Delhi
 Invitation for Continuing Professional Education Session On November 16, 2013 (Saturday) Venue : Conference Hall, Second Floor YMCA Building Jai Singh Marg, Connaught Place, New Delhi -110001 Time: 03:00
Invitation for Continuing Professional Education Session On November 16, 2013 (Saturday) Venue : Conference Hall, Second Floor YMCA Building Jai Singh Marg, Connaught Place, New Delhi -110001 Time: 03:00
ECE 646 Cryptography and Computer Network Security. Kris Gaj Research and teaching interests:
 646 Cryptography and Computer Network Security Course web page: Google Kris Gaj 646 Kris Gaj Research and teaching interests: cryptography network security computer arithmetic FPGA & ASIC design and testing
646 Cryptography and Computer Network Security Course web page: Google Kris Gaj 646 Kris Gaj Research and teaching interests: cryptography network security computer arithmetic FPGA & ASIC design and testing
International Journal of Computer Engineering and Applications,
 International Journal of Computer Engineering and Applications, Volume XII, Issue I, Jan. 18, www.ijcea.com ISSN 2321-3469 SECURING TEXT DATA BY HIDING IN AN IMAGE USING AES CRYPTOGRAPHY AND LSB STEGANOGRAPHY
International Journal of Computer Engineering and Applications, Volume XII, Issue I, Jan. 18, www.ijcea.com ISSN 2321-3469 SECURING TEXT DATA BY HIDING IN AN IMAGE USING AES CRYPTOGRAPHY AND LSB STEGANOGRAPHY
