How does Internet (Big-I) routing work? The Internet is broken up into Autonomous Systems (AS) An AS is an administrative boundary. Each ISP has 1 or
|
|
|
- Harold Day
- 6 years ago
- Views:
Transcription
1 Internet Routing Robustness Improving ftp://engr.ans.net/pub/slides/ndss/feb-1999/ Curtis Villamizar How does Internet routing work? How noticeable are routing related outages? Why have routing attacks not occurred? What measures are being taken today? Approaches to improve external routing robustness.
2 How does Internet (Big-I) routing work? The Internet is broken up into Autonomous Systems (AS) An AS is an administrative boundary. Each ISP has 1 or { AS. Major ISPs have 10s of AS. more Within an AS an Interior Gateway Protocol (IGP) is used. OSPF and IS-IS are used exclusively. No major ISP uses { or EIGRP in their backbones. RIP-2 Routers within an AS are under common administration. { External routes (inter-as routes) are carried by BGP-4 IBGP is used within an AS to carry external routes. { EBGP is used to exchange routes among adjacent peers. { Inter-AS routing (EBGP) reects routing policy that is { by business relationships. determined
3 Some characteristics of Internet Routing Physical topology is relatively static. Logical topology (AS boundaries and adjacencies) is relatively static. 3. Routing is highly dynamic. 4. There are just under 4,000 AS numbers in use. 5. The global routing table has about 60,000 routes. Typical days see peaks on the order of thousands of announcements 6. in a fteen minute measurement interval. Last week (for example) saw a peak interval over 6,000 and 7. adjacent intervals in the 2,000-4,000 range. numerous These characteristics must be considered when examining 8. properties of proposals. scaling
4 of Internet route selection Characteristics Routing protocols implicitly prefer more specic routes unless conguration per route dictates otherwise. explicit Regardless of all other path attributes, if a more specic is accepted, trac will be directed toward that route. route If an erroneous route covers critical hosts such as DNS servers 3. WWW servers, a denial of service can occur. or Many providers accept all routes from peers, with minimal 4. but lower BGP LOCAL PREF (which does not ltering a more specic route from overriding a less specic). override A least one major provider does not lter route announcements 5. from its customers. Misconguration by a customer can cause widespread denial 6. service for a specic prex if there are no sanity lters. of Router software error or radical misconguration can cause 7. outage for a wide range of prexes. an
5 noticeable are routing related outages? How Outages can be widespread and can get wide press coverage. For example consider the incident on April 25, glitch cuts Net access" By Nick Wingeld, Sta, \Router News.com CNET \Net The Oops Heard 'Round the World" by Michael Outage: Wired Stutz, Other articles on are listed on the IPMA \Death of the Internet" page. this More than a year earlier a similar incident occurred. The seems to average one every few years. Internet Smaller incidents are occurring much more frequently.
6 Why have routing attacks not occurred? In a routing based outage false routing information is injected the global routing data. Since many sites log routing into activity malicious action would be too easily traced. The impact of a routing based attack would be limited to a of service. denial A routing attack in progress can be contained with the 3. of a route lter and completely neutralized if the installation lter is at or near the source. The combination of little eect (short term denial of service 4. and high risk (too easily traced) is probably what is only) preventing any malicious activity.
7 What measures are being taken today? IGP protocols use peer to peer authentication, usually based MD5, but sometimes based on simple password. Snooping on exchanges is dicult. IGP IBGP typically uses at least MD5 authentication within IBGP TCP/MD5 is also used, specically to address a itself. BGP denial of service (RFC2385). potential Often no authentication is used over EBGP though some 3. TCP/MD5 between peers. These are usually switched use and EBGP uses a TTL of Using TCP/MD5 is interfaces better practice. a The amount of sanity checking on external route announcements 4. ranges from close to none to only accepting specic prexes from specic peers.
8 Approaches to improve external routing robustness. Information Storage DNS - zone transfer on request, expire and refresh timers. IRR - current: centralized database with full mirrors; toward: distributed with exchange of deltas moving Authorization Model DNS - simple delegation hierarchy, authorization per DNS based on signature of zone le zone IRR - hierarchies on AS, IP address, and routes relying on AS and IP address, authorization per object based both hierarchy of maintainer objects on Verifying Route Announcements Sanity lters applied to EBGP peers Signatures on route origination only Signatures at each BGP exchange 3.
9 Possible Approaches Current Proposals DNS distribution with origin signatures DNS distribution with full AS path signatures IRR distribution with BGP lters on peers 3. Worth Considering IRR distribution with per ISP selection of lters, origin signatures, or full AS path signatures
10 Distributed Routing Registry Repositories do not need to trust each other. Repositories agree to common authorization rules and use authentication methods. common For any given object there is exactly one repository in which object can be created and modied unless delegated. the An object and any beneath it in the hierarchy may be to another repository. delegated Transactions are ooded and each repository can recheck the and authorization of incoming transactions. authentication Repositories and mirrors will have a complete copy of the set repositories through processing the deltas to the database. of A small number of ooding adjacencies are needed. Scales according to the rate of change of the database. For details, consult RPS WG internet-drafts.
11 the authorization check requires objects from other repositories, If then the sequence numbers of the local copies of those Transaction submitter 3 - seqnos needed for auth submit object 2 - authorization check 4 - redistribute Primary repository identified by RPSL source sequence number Transaction submitter sequence numbers of other databases repository Initial Object Submission and Redistribution databases is required for mirrors to recheck the authorization.
12 Transaction submitter 1 Primary repository identified by RPSL source 1 - submit object 2 3 return to submitter sign transaction 2 - authorization check 3 - seqnos needed for auth 4 - redistribute 4 sequence number Transaction submitter sequence numbers of other databases submitter and repository Alternate Initial Object Submission the submitter is protected against the possibility of the Note: replaying a submission later. This method is not in repository the cuurent draft.
13 sequence number Transaction submitter sequence numbers of other databases 1 Mirror repository sequence number Transaction submitter sequence numbers of other databases Further Transaction Redistribution repository 1 - redistributed transaction 2 - recheck the authorization against full DB at the time of transaction using seqnos 3 - auth pass/fail 4 - optionally sign then redistribute repository optional signature of mirror the authorization check was repeated, the mirror may optionally If add a signature before passing the transaction any further.
14 sequence number Transaction submitter sequence numbers of other databases repository 1 - redistributed transaction 2 - recheck the authorization against full DB at the time of transaction using seqnos Redistribution to Lightweight Mirrors 1 Mirror repository sequence number Transaction submitter sequence numbers of other databases repository Lightweight Mirror (router?) 3 - auth pass/fail optional signature 4 - sign and redistribute of mirror 5 - just check mirror signature 6 - apply change with no authorization check 5 6 lightweight mirror must trust the mirror from which it gets The feed. This is a safe assumption if the two are under the same a (the mirror providing the feed is a host owned by administration same ISP who owns the routers). The lightweight mirror the simply checks the signature to insure data integrity.
15 Transaction submitter 1 Primary repository identified by 5 6 RPSL source 4 Optional Commit and Conrm Mirror Repository 1 - submit object 2 3 return to submitter Mirror sign transaction Repository 2 - authorization check 3 - seqnos needed for auth 4 - redistribute 5 - mirror confirms 6 - repository confirms In the event of a disk crash, the repository has already successfully ooded the transaction before sending the conrm back to the submitter. If a mirror is under the same administration, the repository can recover from disk and roll forward the transactions from the mirror before resuming operation.
16 Signatures on Route Origination Only The BGP route originator signs the BGP route. Determine public key for an IP prex. When receiving a route the public key for the prex is 3. and the signature is veried. determined
17 Full AS Path Signature The BGP route originator signs the BGP route. At each exchange of a BGP route a signature is added the advertising router indicating what AS the route was by advertised to. When receiving a route the public key for the prex and the 3. key for each AS must be determined and the signature public veried for the originator and each AS in the AS Path.
18 Filtering Routes from EBGP Peers AS numbers and IP addresses are assigned hierarchically. Intention to announce a route can be registered with autho- from both the AS and the IP address holder. rization AS registrations may include AS adjacencies and policy. All registry changes must follow a set of authorization rules include authentication requirements (with public keys which authorization species cryptographic authentication) where Complete registry mirrors can (and should) repeat authoriza- and authentication checks. tion Filters may be constructed from registry information. The type of lter used by ISPs may vary.
19 of Filters with Registry Based Approach Types As a minimum measure, an ISP can lter their direct announcements using a (relatively small) list of customers based on registered routes. This prevents becoming prexes source of a denial of service. the As a protection to direct customers, lters may be added deny more specic routes for any customer routes. which lter list can become quite lengthy. These If registration of routes reaches a critical mass, the announcements 3. of routing peers can be limited to specic prexes with assigned according to stated policies along the preferences These lters can also become quite lengthy. path. Filters may assign preferences to specic AS paths if adjacencies 4. and policy of the complete path is documented in the database. This form of ltering is not yet in use.
20 and Cons of Origin Signature Pros Advantages: Prevents most or all accidental attacks seen today. Disadvantages: Replay attacks and accidental replay Scaling wrt number of routes and announcements. One signature verications per route received. { Deployment: None. {
21 and Cons of Full Path Signature Pros Advantages: Origination and path is authenticated. Disadvantages: Scaling wrt number of routes and announcements. Two or more signature verications per route received. { Route aggregation removes signatures of originator of more specics or increases BGP overhead dramatically. Deployment: None in Internet. Elsewhere? {
22 Pros and Cons of Registry and Sanity Filters Advantages: No signature checks per route when a route is received. Frequency of cryptographic authentication check is logical change (database update). Changes to registry topology are infrequent (on the order of a few hundred information day) and rarely needs to be reected in real time. per 3. BGP ltering is implemented in currently shipping routers. Disadvantages: Origin and path is sanity checked but not authenticated. Filters are expensive in terms of router resources, though expensive than signature verication. less
23 Deployment of Registry and Sanity Filters There are 5 closely cooperating major registries (ANS, CW, RADB, RIPE) referred to as the IRR. CANET, There are many private ISP registries and a number of wishing to join the IRR. registries Common policy description dened by RFC2280. Distributed registry and common authorization and au- model is specied (IETF drafts) and being thentication Source will be freely distributed. implemented. Numerous providers use the IRR or a private registry to router lters based on their own routing policy. congure Critical mass has not been reached. Route objects are about populated. Adjacencies and tools necessary to base 90% local policy on policies of entire routed path are not available.
24 Common Limitations Partial origin deployment yields routes with no originating or origination of unregistered routes. signature Partial transit deployment or cooperation yields incomplete chain or AS with no stated policy. signature Security compromise along the transit path results in denial 3. service in either case. A complete signature chain in this of provides no assurance of trac delivery and therefore case security advantage. limited
25 Among Proposals, Which is Better? This may be a question of applicability. Full AS path signatures may be preferable for smaller { security networks who prefer signatures though higher security advantage is oered. limited Sanity lters may be more applicable for the global { where scaling is critical. Internet Both types of information, AS adjacency and policy, and keys, can be held in the routing registry. public
26 Summary Signatures on BGP AS Path oers security advantage over In the ltering model there is often no assurance ltering. the downstream AS is ltering and lters are not that applied against the full AS path. A complete commonly chain provides a clear positive indication. signature Either originator only signature or ltering oer a substantial in routing robustness over doing nothing. improvement Filters oer scalability over the signature techniques that is 3. in very large deployments such as the global Internet. critical It may be that the two/three types of solution are applicable 4. dierent situations. in All of the information needed for either approach can be 5. using the routing registries with the addition of distributed optional public key per AS and route. an
27 References ftp://engr.ans.net/pub/slides/ndss/feb RFC-2280 (RPSL) draft-ietf-rps-rpsl-v2-0txt draft-ietf-rps-auth-0txt draft-ietf-rps-dist-0txt draft-ietf-rps-dbsec-pgp-authent-00.txt
Securing BGP. Geoff Huston November 2007
 Securing BGP Geoff Huston November 2007 Agenda An Introduction to BGP BGP Security Questions Current Work Research Questions An Introduction to BGP Background to Internet Routing The routing architecture
Securing BGP Geoff Huston November 2007 Agenda An Introduction to BGP BGP Security Questions Current Work Research Questions An Introduction to BGP Background to Internet Routing The routing architecture
CS 43: Computer Networks. 24: Internet Routing November 19, 2018
 CS 43: Computer Networks 24: Internet Routing November 19, 2018 Last Class Link State + Fast convergence (reacts to events quickly) + Small window of inconsistency Distance Vector + + Distributed (small
CS 43: Computer Networks 24: Internet Routing November 19, 2018 Last Class Link State + Fast convergence (reacts to events quickly) + Small window of inconsistency Distance Vector + + Distributed (small
Introduction. Keith Barker, CCIE #6783. YouTube - Keith6783.
 Understanding, Implementing and troubleshooting BGP 01 Introduction http:// Instructor Introduction Keith Barker, CCIE #6783 CCIE Routing and Switching 2001 CCIE Security 2003 kbarker@ine.com YouTube -
Understanding, Implementing and troubleshooting BGP 01 Introduction http:// Instructor Introduction Keith Barker, CCIE #6783 CCIE Routing and Switching 2001 CCIE Security 2003 kbarker@ine.com YouTube -
Life After IPv4 Depletion
 1 Life After IPv4 Depletion Jon Worley Analyst Securing Core Internet Functions Resource Certification, RPKI Mark Kosters Chief Technology Officer 2 Core Internet Functions: Routing & DNS The Internet
1 Life After IPv4 Depletion Jon Worley Analyst Securing Core Internet Functions Resource Certification, RPKI Mark Kosters Chief Technology Officer 2 Core Internet Functions: Routing & DNS The Internet
An Operational Perspective on BGP Security. Geoff Huston February 2005
 An Operational Perspective on BGP Security Geoff Huston February 2005 Disclaimer This is not a description of the approach taken by any particular service provider in securing their network. It is intended
An Operational Perspective on BGP Security Geoff Huston February 2005 Disclaimer This is not a description of the approach taken by any particular service provider in securing their network. It is intended
Routing Basics. ISP Workshops. Last updated 10 th December 2015
 Routing Basics ISP Workshops Last updated 10 th December 2015 1 Routing Concepts p IPv4 & IPv6 p Routing p Forwarding p Some definitions p Policy options p Routing Protocols 2 IPv4 p Internet still uses
Routing Basics ISP Workshops Last updated 10 th December 2015 1 Routing Concepts p IPv4 & IPv6 p Routing p Forwarding p Some definitions p Policy options p Routing Protocols 2 IPv4 p Internet still uses
A PKI For IDR Public Key Infrastructure and Number Resource Certification
 A PKI For IDR Public Key Infrastructure and Number Resource Certification AUSCERT 2006 Geoff Huston Research Scientist APNIC If You wanted to be Bad on the Internet And you wanted to: Hijack a site Inspect
A PKI For IDR Public Key Infrastructure and Number Resource Certification AUSCERT 2006 Geoff Huston Research Scientist APNIC If You wanted to be Bad on the Internet And you wanted to: Hijack a site Inspect
Introduction to BGP ISP/IXP Workshops
 Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol Routing Protocol used to exchange routing information between networks exterior gateway protocol RFC1771 work in progress to update draft-ietf-idr-bgp4-18.txt
Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol Routing Protocol used to exchange routing information between networks exterior gateway protocol RFC1771 work in progress to update draft-ietf-idr-bgp4-18.txt
CS 43: Computer Networks Internet Routing. Kevin Webb Swarthmore College November 16, 2017
 CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 16, 2017 1 Hierarchical routing Our routing study thus far - idealization all routers identical network flat not true in
CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 16, 2017 1 Hierarchical routing Our routing study thus far - idealization all routers identical network flat not true in
Routing Basics ISP/IXP Workshops
 Routing Basics ISP/IXP Workshops 1 Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 2 IPv4 Internet uses IPv4 addresses are 32 bits long range from 1.0.0.0 to
Routing Basics ISP/IXP Workshops 1 Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 2 IPv4 Internet uses IPv4 addresses are 32 bits long range from 1.0.0.0 to
Using MSDP to Interconnect Multiple PIM-SM Domains
 Using MSDP to Interconnect Multiple PIM-SM Domains This module describes the tasks associated with using Multicast Source Discovery Protocol (MSDP) to interconnect multiple Protocol Independent Multicast
Using MSDP to Interconnect Multiple PIM-SM Domains This module describes the tasks associated with using Multicast Source Discovery Protocol (MSDP) to interconnect multiple Protocol Independent Multicast
Routing Basics ISP/IXP Workshops
 Routing Basics ISP/IXP Workshops 1 Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 2 IPv4 Internet uses IPv4 addresses are 32 bits long range from 1.0.0.0 to
Routing Basics ISP/IXP Workshops 1 Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 2 IPv4 Internet uses IPv4 addresses are 32 bits long range from 1.0.0.0 to
Routing Concepts. IPv4 Routing Forwarding Some definitions Policy options Routing Protocols
 Routing Basics 1 Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 2 IPv4 Internet uses IPv4 Addresses are 32 bits long Range from 1.0.0.0 to 223.255.255.255 0.0.0.0
Routing Basics 1 Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 2 IPv4 Internet uses IPv4 Addresses are 32 bits long Range from 1.0.0.0 to 223.255.255.255 0.0.0.0
Security in inter-domain routing
 DD2491 p2 2011 Security in inter-domain routing Olof Hagsand KTH CSC 1 Literature Practical BGP pages Chapter 9 See reading instructions Beware of BGP Attacks (Nordström, Dovrolis) Examples of attacks
DD2491 p2 2011 Security in inter-domain routing Olof Hagsand KTH CSC 1 Literature Practical BGP pages Chapter 9 See reading instructions Beware of BGP Attacks (Nordström, Dovrolis) Examples of attacks
RPKI and Routing Security
 Presentation September 2015 Yerevan Regional Meeting Routing Security 2 Routing Registry route objects RPKI (Resource Public Key Infrastructure) ROAs (Route Origin Authorisation) What is the Purpose of
Presentation September 2015 Yerevan Regional Meeting Routing Security 2 Routing Registry route objects RPKI (Resource Public Key Infrastructure) ROAs (Route Origin Authorisation) What is the Purpose of
Configuring MSDP. Overview. How MSDP operates. MSDP peers
 Contents Configuring MSDP 1 Overview 1 How MSDP operates 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 7 Configuring basic MSDP functions 7 Configuration prerequisites
Contents Configuring MSDP 1 Overview 1 How MSDP operates 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 7 Configuring basic MSDP functions 7 Configuration prerequisites
Routing Basics. ISP Workshops
 Routing Basics ISP Workshops These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/) Last updated 26
Routing Basics ISP Workshops These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/) Last updated 26
Routing Basics. Routing Concepts. IPv4. IPv4 address format. A day in a life of a router. What does a router do? IPv4 Routing
 Routing Concepts IPv4 Routing Routing Basics ISP/IXP Workshops Forwarding Some definitions Policy options Routing Protocols 1 2 IPv4 IPv4 address format Internet uses IPv4 addresses are 32 bits long range
Routing Concepts IPv4 Routing Routing Basics ISP/IXP Workshops Forwarding Some definitions Policy options Routing Protocols 1 2 IPv4 IPv4 address format Internet uses IPv4 addresses are 32 bits long range
Securing Core Internet Functions Resource Certification, RPKI. Mark Kosters ARIN CTO
 Securing Core Internet Functions Resource Certification, RPKI Mark Kosters ARIN CTO Core Internet Functions: Routing & DNS The Internet relies on two critical resources DNS: Translates domain names to
Securing Core Internet Functions Resource Certification, RPKI Mark Kosters ARIN CTO Core Internet Functions: Routing & DNS The Internet relies on two critical resources DNS: Translates domain names to
Problem Statement and Considerations for ROA Mergence. 96 SIDR meeting
 Problem Statement and Considerations for ROA Mergence draft-yan-sidr-roa-mergence-00 @IETF 96 SIDR meeting fuyu@cnnic.cn Background RFC 6482 1/19 ROA mergence What is the ROA mergence? is a common case
Problem Statement and Considerations for ROA Mergence draft-yan-sidr-roa-mergence-00 @IETF 96 SIDR meeting fuyu@cnnic.cn Background RFC 6482 1/19 ROA mergence What is the ROA mergence? is a common case
Multihoming. Copy Rights
 Multihoming or provider independent addressing (possible usage) János Mohácsi NIIF/HUNGARNET Copy Rights This slide set is the ownership of the 6DISS project via its partners The Powerpoint version of
Multihoming or provider independent addressing (possible usage) János Mohácsi NIIF/HUNGARNET Copy Rights This slide set is the ownership of the 6DISS project via its partners The Powerpoint version of
CS519: Computer Networks. Lecture 4, Part 5: Mar 1, 2004 Internet Routing:
 : Computer Networks Lecture 4, Part 5: Mar 1, 2004 Internet Routing: AS s, igp, and BGP As we said earlier, the Internet is composed of Autonomous Systems (ASs) Where each AS is a set of routers, links,
: Computer Networks Lecture 4, Part 5: Mar 1, 2004 Internet Routing: AS s, igp, and BGP As we said earlier, the Internet is composed of Autonomous Systems (ASs) Where each AS is a set of routers, links,
Inter-Domain Routing: BGP
 Inter-Domain Routing: BGP Brad Karp UCL Computer Science (drawn mostly from lecture notes by Hari Balakrishnan and Nick Feamster, MIT) CS 3035/GZ01 4 th December 2014 Outline Context: Inter-Domain Routing
Inter-Domain Routing: BGP Brad Karp UCL Computer Science (drawn mostly from lecture notes by Hari Balakrishnan and Nick Feamster, MIT) CS 3035/GZ01 4 th December 2014 Outline Context: Inter-Domain Routing
IETF RFCs Supported by Cisco NX-OS Unicast Features Release 6.x
 IETF Supported by Cisco NX-OS Unicast Features Release 6.x BGP, page 1 First-Hop Redundancy Protocols, page 2 IP Services, page 3 IPv6, page 3 IS-IS, page 4 OSPF, page 5 RIP, page 5 BGP RFC 1997 BGP Communities
IETF Supported by Cisco NX-OS Unicast Features Release 6.x BGP, page 1 First-Hop Redundancy Protocols, page 2 IP Services, page 3 IPv6, page 3 IS-IS, page 4 OSPF, page 5 RIP, page 5 BGP RFC 1997 BGP Communities
Introduction to BGP. ISP/IXP Workshops
 Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol A Routing Protocol used to exchange routing information between different networks Exterior gateway protocol Described in RFC4271 RFC4276
Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol A Routing Protocol used to exchange routing information between different networks Exterior gateway protocol Described in RFC4271 RFC4276
Network Security - ISA 656 Routing Security
 Network Security - ISA 656 Angelos Stavrou December 4, 2007 What is? What is Routing Security? History of Routing Security Why So Little Work? How is it Different? The Enemy s Goal? Bad guys play games
Network Security - ISA 656 Angelos Stavrou December 4, 2007 What is? What is Routing Security? History of Routing Security Why So Little Work? How is it Different? The Enemy s Goal? Bad guys play games
Unit 3: Dynamic Routing
 Unit 3: Dynamic Routing Basic Routing The term routing refers to taking a packet from one device and sending it through the network to another device on a different network. Routers don t really care about
Unit 3: Dynamic Routing Basic Routing The term routing refers to taking a packet from one device and sending it through the network to another device on a different network. Routers don t really care about
Routing Protocols. Technology Description BGP CHAPTER
 CHAPTER 11 This chapter describes the level of support that Cisco ANA provides for routing protocols, as follows: Technology Description, page 11-1 Information Model Objects (IMOs), page 11-3 Vendor-Specific
CHAPTER 11 This chapter describes the level of support that Cisco ANA provides for routing protocols, as follows: Technology Description, page 11-1 Information Model Objects (IMOs), page 11-3 Vendor-Specific
IPv6 Module 16 An IPv6 Internet Exchange Point
 IPv6 Module 16 An IPv6 Internet Exchange Point Objective: To investigate methods for connecting to an Internet Exchange Point. Prerequisites: Modules 12, 14 and 15, and the Exchange Points Presentation
IPv6 Module 16 An IPv6 Internet Exchange Point Objective: To investigate methods for connecting to an Internet Exchange Point. Prerequisites: Modules 12, 14 and 15, and the Exchange Points Presentation
Configuring MSDP. MSDP overview. How MSDP works. MSDP peers
 Contents Configuring MSDP 1 MSDP overview 1 How MSDP works 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 6 Configuring basic MSDP functions 7 Configuration prerequisites
Contents Configuring MSDP 1 MSDP overview 1 How MSDP works 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 6 Configuring basic MSDP functions 7 Configuration prerequisites
debug ip ospf database external default-metric subnet area 0 stub distribute-list in Serial0/1
 Which statement about stateless autoconfiguration is true? A host can autoconfigure itself by appending its MAC address to the local link prefix (64 bits). 2 Autoconfiguration allows devices to connect
Which statement about stateless autoconfiguration is true? A host can autoconfigure itself by appending its MAC address to the local link prefix (64 bits). 2 Autoconfiguration allows devices to connect
BGP for Internet Service Providers
 BGP for Internet Service Providers Philip Smith Seoul KIOW 2002 1 BGP current status RFC1771 is quite old, and no longer reflects current operational practice nor vendor implementations
BGP for Internet Service Providers Philip Smith Seoul KIOW 2002 1 BGP current status RFC1771 is quite old, and no longer reflects current operational practice nor vendor implementations
Border Gateway Protocol
 39 CHAPTER Chapter Goals Understand the purpose of the. Explain BGP attributes and their use in route selection. Examine the BGP route selection process. Introduction The (BGP) is an interautonomous system
39 CHAPTER Chapter Goals Understand the purpose of the. Explain BGP attributes and their use in route selection. Examine the BGP route selection process. Introduction The (BGP) is an interautonomous system
Table of Contents 1 MSDP Configuration 1-1
 Table of Contents 1 MSDP Configuration 1-1 MSDP Overview 1-1 Introduction to MSDP 1-1 How MSDP Works 1-2 Protocols and Standards 1-7 MSDP Configuration Task List 1-7 Configuring Basic Functions of MSDP
Table of Contents 1 MSDP Configuration 1-1 MSDP Overview 1-1 Introduction to MSDP 1-1 How MSDP Works 1-2 Protocols and Standards 1-7 MSDP Configuration Task List 1-7 Configuring Basic Functions of MSDP
Network Security - ISA 656 Routing Security
 What is? Network Security - ISA 656 Angelos Stavrou What is Routing Security? History of Routing Security Why So Little Work? How is it Different? Bad guys play games with routing protocols. Traffic is
What is? Network Security - ISA 656 Angelos Stavrou What is Routing Security? History of Routing Security Why So Little Work? How is it Different? Bad guys play games with routing protocols. Traffic is
Routing Between Autonomous Systems (Example: BGP4) RFC 1771
 CS 4/55231 Internet Engineering Kent State University Dept. of Computer Science LECT-7B Routing Between Autonomous Systems (Example: BGP4) RFC 1771 52 53 BGP4 Overview Example of Operations BGP4 is a path
CS 4/55231 Internet Engineering Kent State University Dept. of Computer Science LECT-7B Routing Between Autonomous Systems (Example: BGP4) RFC 1771 52 53 BGP4 Overview Example of Operations BGP4 is a path
Chapter 16 OSPF Version 3 Commands
 Chapter 16 OSPF Version 3 Commands NOTE: The OSPF version 3 configuration level is present only on HP devices that support IPv6. area Assigns OSPF version 3 areas. You can assign an IPv4 address or a number
Chapter 16 OSPF Version 3 Commands NOTE: The OSPF version 3 configuration level is present only on HP devices that support IPv6. area Assigns OSPF version 3 areas. You can assign an IPv4 address or a number
Routing Basics. Campus Network Design & Operations Workshop
 Routing Basics Campus Network Design & Operations Workshop These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/)
Routing Basics Campus Network Design & Operations Workshop These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/)
Unicast Routing. TCP/IP class
 Unicast Routing TCP/IP class Routing Protocols intro RIP and son of RIP OSPF BGP odd bodkins NAT TCP/IP Internetworking Protocols 2 divide routing world into 3 parts topology IETF ISO/OSI same link or
Unicast Routing TCP/IP class Routing Protocols intro RIP and son of RIP OSPF BGP odd bodkins NAT TCP/IP Internetworking Protocols 2 divide routing world into 3 parts topology IETF ISO/OSI same link or
Inter-Domain Routing: BGP
 Inter-Domain Routing: BGP Richard T. B. Ma School of Computing National University of Singapore CS 3103: Compute Networks and Protocols Inter-Domain Routing Internet is a network of networks Hierarchy
Inter-Domain Routing: BGP Richard T. B. Ma School of Computing National University of Singapore CS 3103: Compute Networks and Protocols Inter-Domain Routing Internet is a network of networks Hierarchy
Configuring BGP. Cisco s BGP Implementation
 Configuring BGP This chapter describes how to configure Border Gateway Protocol (BGP). For a complete description of the BGP commands in this chapter, refer to the BGP s chapter of the Network Protocols
Configuring BGP This chapter describes how to configure Border Gateway Protocol (BGP). For a complete description of the BGP commands in this chapter, refer to the BGP s chapter of the Network Protocols
Internet Interconnection Structure
 Internet Interconnection Structure Basic Concepts (1) Internet Service Provider (ISP) Provider who connects an end user customer with the Internet in one or few geographic regions. National & Regional
Internet Interconnection Structure Basic Concepts (1) Internet Service Provider (ISP) Provider who connects an end user customer with the Internet in one or few geographic regions. National & Regional
Module 10 An IPv6 Internet Exchange Point
 ISP/IXP Networking Workshop Lab Module 10 An IPv6 Internet Exchange Point Objective: To investigate methods for connecting to an Internet Exchange Point. Prerequisites: Modules 1 to 4, and the Exchange
ISP/IXP Networking Workshop Lab Module 10 An IPv6 Internet Exchange Point Objective: To investigate methods for connecting to an Internet Exchange Point. Prerequisites: Modules 1 to 4, and the Exchange
Keying & Authentication for Routing Protocols (KARP) draft-lebovitz-kmart-roadmap-03
 Keying & Authentication for Routing Protocols (KARP) KARP BoF IETF76, Hiroshima, Tue, 09 Nov, 2009 Gregory M. Lebovitz, Juniper gregory.ietf@gmail.com Intellectual Property When starting a presentation
Keying & Authentication for Routing Protocols (KARP) KARP BoF IETF76, Hiroshima, Tue, 09 Nov, 2009 Gregory M. Lebovitz, Juniper gregory.ietf@gmail.com Intellectual Property When starting a presentation
Introducción al RPKI (Resource Public Key Infrastructure)
 Introducción al RPKI (Resource Public Key Infrastructure) Roque Gagliano rogaglia@cisco.com 4 Septiembre 2013 Quito, Equator 2011 Cisco and/or its affiliates. All rights reserved. 1 Review of problem to
Introducción al RPKI (Resource Public Key Infrastructure) Roque Gagliano rogaglia@cisco.com 4 Septiembre 2013 Quito, Equator 2011 Cisco and/or its affiliates. All rights reserved. 1 Review of problem to
Internet Resource Certification and Inter- Domain Routing Security! Eric Osterweil!
 Internet Resource Certification and Inter- Domain Routing Security! Eric Osterweil! Who is allowed to do what?! BGP (the Internet s inter-domain routing protocol) runs by rumor Participants assert reachability
Internet Resource Certification and Inter- Domain Routing Security! Eric Osterweil! Who is allowed to do what?! BGP (the Internet s inter-domain routing protocol) runs by rumor Participants assert reachability
CCNA 3 (v v6.0) Chapter 5 Exam Answers % Full
 CCNA 3 (v5.0.3 + v6.0) Chapter 5 Exam Answers 2017 100% Full ccnav6.com /ccna-3-v5-0-3-v6-0-chapter-5-exam-answers-2017-100-full.html CCNA Exam Answers 2017 CCNA 3 (v5.0.3 + v6.0) Chapter 5 Exam Answers
CCNA 3 (v5.0.3 + v6.0) Chapter 5 Exam Answers 2017 100% Full ccnav6.com /ccna-3-v5-0-3-v6-0-chapter-5-exam-answers-2017-100-full.html CCNA Exam Answers 2017 CCNA 3 (v5.0.3 + v6.0) Chapter 5 Exam Answers
c2001, Dr.Y.N.Singh, EED, IITK 2 Border Gateway Protocol - 4 BGP-4 (RFC intended to be used for routing between Autonomou
 c2001, Dr.Y.N.Singh, EED, IITK 1 Layer Routing - V Network Gateway Protocol -4 Border Yatindra Nath Singh ynsingh@ieee.org Dept. Of Electrical Engineering IIT Kanpur-208016 22 August 2001 c2001, Dr.Y.N.Singh,
c2001, Dr.Y.N.Singh, EED, IITK 1 Layer Routing - V Network Gateway Protocol -4 Border Yatindra Nath Singh ynsingh@ieee.org Dept. Of Electrical Engineering IIT Kanpur-208016 22 August 2001 c2001, Dr.Y.N.Singh,
Securing BGP: The current state of RPKI. Geoff Huston Chief Scientist, APNIC
 Securing BGP: The current state of RPKI Geoff Huston Chief Scientist, APNIC Incidents What happens when I announce your addresses in BGP? All the traffic that used to go to you will now come to me I can
Securing BGP: The current state of RPKI Geoff Huston Chief Scientist, APNIC Incidents What happens when I announce your addresses in BGP? All the traffic that used to go to you will now come to me I can
Chapter 13 Configuring BGP4
 Chapter 13 Configuring BGP4 This chapter provides details on how to configure Border Gateway Protocol version 4 (BGP4) on HP products using the CLI and the Web management interface. BGP4 is supported on
Chapter 13 Configuring BGP4 This chapter provides details on how to configure Border Gateway Protocol version 4 (BGP4) on HP products using the CLI and the Web management interface. BGP4 is supported on
Migrating from OSPF to IS-IS
 Migrating from OSPF to IS-IS Philip Smith philip@nsrc.org SAFNOG 2 7 th -8 th April 2015 Mbabane Last updated 27 March 2014 1 Presentation slides p Available at: n http://bgp4all.com/ftp/seminars/safnog2-
Migrating from OSPF to IS-IS Philip Smith philip@nsrc.org SAFNOG 2 7 th -8 th April 2015 Mbabane Last updated 27 March 2014 1 Presentation slides p Available at: n http://bgp4all.com/ftp/seminars/safnog2-
APNIC Training. Internet Routing Registry (IRR)
 APNIC Training Internet Routing Registry (IRR) Objectives To provide an introduction to the APNIC Routing Registry Explain concepts of the global RR Outline the benefits of the APNIC Routing Registry Discuss
APNIC Training Internet Routing Registry (IRR) Objectives To provide an introduction to the APNIC Routing Registry Explain concepts of the global RR Outline the benefits of the APNIC Routing Registry Discuss
Chapter 15 OSPF Commands
 Chapter 15 OSPF Commands NOTE: This chapter contains information about OSPF version 2 commands only. For information about OSPF version 3 commands, see OSPF Version 3 Commands on page 16-1. area Assigns
Chapter 15 OSPF Commands NOTE: This chapter contains information about OSPF version 2 commands only. For information about OSPF version 3 commands, see OSPF Version 3 Commands on page 16-1. area Assigns
BGP Commands. Network Protocols Command Reference, Part 1 P1R-355
 BGP Commands Use the commands in this chapter to configure and monitor Border Gateway Protocol (BGP). For BGP configuration information and examples, refer to the Configuring BGP chapter of the Network
BGP Commands Use the commands in this chapter to configure and monitor Border Gateway Protocol (BGP). For BGP configuration information and examples, refer to the Configuring BGP chapter of the Network
Chapter 17 BGP4 Commands
 Chapter 17 BGP4 Commands NOTE: This chapter describes commands in the BGP configuration level, which is present on HP devices that support IPv4 only. For information about BGP commands and configuration
Chapter 17 BGP4 Commands NOTE: This chapter describes commands in the BGP configuration level, which is present on HP devices that support IPv4 only. For information about BGP commands and configuration
Overview of the Resource PKI (RPKI) Dr. Stephen Kent VP & Chief Scientist BBN Technologies
 Overview of the Resource PKI (RPKI) Dr. Stephen Kent VP & Chief Scientist BBN Technologies Presentation Outline The BGP security problem RPKI overiew Address & AS number allocation system Certificates
Overview of the Resource PKI (RPKI) Dr. Stephen Kent VP & Chief Scientist BBN Technologies Presentation Outline The BGP security problem RPKI overiew Address & AS number allocation system Certificates
Networking 101 ISP/IXP Workshops
 Networking 101 ISP/IXP Workshops 1 Network Topology and Definitions Definitions and icons Network topologies PoP topologies Interconnections and IXPs IP Addressing Gluing it all together 2 Topologies and
Networking 101 ISP/IXP Workshops 1 Network Topology and Definitions Definitions and icons Network topologies PoP topologies Interconnections and IXPs IP Addressing Gluing it all together 2 Topologies and
RPKI. Resource Pubic Key Infrastructure
 RPKI Resource Pubic Key Infrastructure Purpose of RPKI RPKI replaces IRR or lives side by side? Side by side: different advantages Security, almost real time, simple interface: RPKI Purpose of RPKI Is
RPKI Resource Pubic Key Infrastructure Purpose of RPKI RPKI replaces IRR or lives side by side? Side by side: different advantages Security, almost real time, simple interface: RPKI Purpose of RPKI Is
CS 457 Networking and the Internet. The Global Internet (Then) The Global Internet (And Now) 10/4/16. Fall 2016
 CS 457 Networking and the Internet Fall 2016 The Global Internet (Then) The tree structure of the Internet in 1990 The Global Internet (And Now) A simple multi-provider Internet 1 The Global Internet Some
CS 457 Networking and the Internet Fall 2016 The Global Internet (Then) The tree structure of the Internet in 1990 The Global Internet (And Now) A simple multi-provider Internet 1 The Global Internet Some
Table of Contents 1 MSDP Configuration 1-1
 Table of Contents 1 MSDP Configuration 1-1 MSDP Overview 1-1 Introduction to MSDP 1-1 How MSDP Works 1-2 Multi-Instance MSDP 1-7 Protocols and Standards 1-7 MSDP Configuration Task List 1-7 Configuring
Table of Contents 1 MSDP Configuration 1-1 MSDP Overview 1-1 Introduction to MSDP 1-1 How MSDP Works 1-2 Multi-Instance MSDP 1-7 Protocols and Standards 1-7 MSDP Configuration Task List 1-7 Configuring
Problem. BGP is a rumour mill.
 Problem BGP is a rumour mill. We want to give it a bit more authorita We think we have a model AusNOG-03 2009 IP ADDRESS AND ASN CERTIFICATION TO IMPROVE ROUTING SECURITY George Michaelson APNIC R&D ggm@apnic.net
Problem BGP is a rumour mill. We want to give it a bit more authorita We think we have a model AusNOG-03 2009 IP ADDRESS AND ASN CERTIFICATION TO IMPROVE ROUTING SECURITY George Michaelson APNIC R&D ggm@apnic.net
BGP in the Internet Best Current Practices
 BGP in the Internet Best Current Practices 1 Recommended IOS Releases Which IOS?? 2 Which IOS? IOS is a feature rich and highly complex router control system ISPs should choose the IOS variant which is
BGP in the Internet Best Current Practices 1 Recommended IOS Releases Which IOS?? 2 Which IOS? IOS is a feature rich and highly complex router control system ISPs should choose the IOS variant which is
Connecting to a Service Provider Using External BGP
 Connecting to a Service Provider Using External BGP First Published: May 2, 2005 Last Updated: August 21, 2007 This module describes configuration tasks that will enable your Border Gateway Protocol (BGP)
Connecting to a Service Provider Using External BGP First Published: May 2, 2005 Last Updated: August 21, 2007 This module describes configuration tasks that will enable your Border Gateway Protocol (BGP)
LARGE SCALE IP ROUTING
 Building ISP Networks Xantaro Page 1 / 18 TABLE OF CONTENTS 1. LAB ACCESS 4 1.1 Accessing the Jumphost... 4 1.2 Access to your routers... 4 1.3 Local Network Topology... 5 1.4 Global Network Topology...
Building ISP Networks Xantaro Page 1 / 18 TABLE OF CONTENTS 1. LAB ACCESS 4 1.1 Accessing the Jumphost... 4 1.2 Access to your routers... 4 1.3 Local Network Topology... 5 1.4 Global Network Topology...
Ravi Chandra cisco Systems Cisco Systems Confidential
 BGP4 1 Ravi Chandra cisco Systems 0799_04F7_c2 Cisco Systems Confidential 2 Border Gateway Protocol (BGP) Introduction to BGP BGP Peer Relationship BGP Attributes Applying Policy with BGP Putting it all
BGP4 1 Ravi Chandra cisco Systems 0799_04F7_c2 Cisco Systems Confidential 2 Border Gateway Protocol (BGP) Introduction to BGP BGP Peer Relationship BGP Attributes Applying Policy with BGP Putting it all
Network Security: Routing security. Aapo Kalliola T Network security Aalto University, Nov-Dec 2012
 Network Security: Routing security Aapo Kalliola T-110.5241 Network security Aalto University, Nov-Dec 2012 Outline 1. Structure of internet 2. Routing basics 3. Security issues 4. Attack 5. Solutions
Network Security: Routing security Aapo Kalliola T-110.5241 Network security Aalto University, Nov-Dec 2012 Outline 1. Structure of internet 2. Routing basics 3. Security issues 4. Attack 5. Solutions
Contents. Configuring MSDP 1
 Contents Configuring MSDP 1 Overview 1 How MSDP works 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 7 Configuring basic MSDP features 7 Configuration prerequisites 7
Contents Configuring MSDP 1 Overview 1 How MSDP works 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 7 Configuring basic MSDP features 7 Configuration prerequisites 7
Resource Public Key Infrastructure (RPKI) Nurul Islam Roman, APNIC
 Resource Public Key Infrastructure (RPKI) Nurul Islam Roman, APNIC Target Audience Knowledge of Internet Routing(specially BGP) Fair idea on Routing Policy No need to know Cryptography Basic knowledge
Resource Public Key Infrastructure (RPKI) Nurul Islam Roman, APNIC Target Audience Knowledge of Internet Routing(specially BGP) Fair idea on Routing Policy No need to know Cryptography Basic knowledge
CSCD 433/533 Network Programming Fall Lecture 14 Global Address Space Autonomous Systems, BGP Protocol Routing
 CSCD 433/533 Network Programming Fall 2012 Lecture 14 Global Address Space Autonomous Systems, BGP Protocol Routing 1 Topics Interdomain Routing BGP Interdomain Routing Benefits vs. Link State Routing
CSCD 433/533 Network Programming Fall 2012 Lecture 14 Global Address Space Autonomous Systems, BGP Protocol Routing 1 Topics Interdomain Routing BGP Interdomain Routing Benefits vs. Link State Routing
Open Shortest Path Firts -2 OSPF-2 (RFC As mentioned before, there are two basic routing algorithms. rst one, distance ve
 Layer Routing - IV Network OSPF-2 Yatindra Nath Singh ynsingh@ieee.org Dept. Of Electrical Engineering IIT Kanpur-208016 22 August 2001 1 Open Shortest Path Firts -2 OSPF-2 (RFC 2328 - http://www.ietf.org/)
Layer Routing - IV Network OSPF-2 Yatindra Nath Singh ynsingh@ieee.org Dept. Of Electrical Engineering IIT Kanpur-208016 22 August 2001 1 Open Shortest Path Firts -2 OSPF-2 (RFC 2328 - http://www.ietf.org/)
Interdomain routing CSCI 466: Networks Keith Vertanen Fall 2011
 Interdomain routing CSCI 466: Networks Keith Vertanen Fall 2011 Overview Business relationships between ASes Interdomain routing using BGP Advertisements Routing policy Integration with intradomain routing
Interdomain routing CSCI 466: Networks Keith Vertanen Fall 2011 Overview Business relationships between ASes Interdomain routing using BGP Advertisements Routing policy Integration with intradomain routing
CSCI-1680 Network Layer: Inter-domain Routing Rodrigo Fonseca
 CSCI-1680 Network Layer: Inter-domain Routing Rodrigo Fonseca Based partly on lecture notes by Rob Sherwood, David Mazières, Phil Levis, John Janno? Administrivia Midterm moved up from 3/17 to 3/15 IP
CSCI-1680 Network Layer: Inter-domain Routing Rodrigo Fonseca Based partly on lecture notes by Rob Sherwood, David Mazières, Phil Levis, John Janno? Administrivia Midterm moved up from 3/17 to 3/15 IP
Migrating from OSPF to IS-IS
 Migrating from OSPF to IS-IS ISP Workshops Last updated 25 th August 2015 1 Introduction p With the advent of IPv6 and dual stack networks, more ISPs expressing interest to migrate to IS-IS n Migration
Migrating from OSPF to IS-IS ISP Workshops Last updated 25 th August 2015 1 Introduction p With the advent of IPv6 and dual stack networks, more ISPs expressing interest to migrate to IS-IS n Migration
CS 43: Computer Networks Internet Routing. Kevin Webb Swarthmore College November 14, 2013
 CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 14, 2013 1 Reading Quiz Hierarchical routing Our routing study thus far - idealization all routers identical network flat
CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 14, 2013 1 Reading Quiz Hierarchical routing Our routing study thus far - idealization all routers identical network flat
Module 16 An Internet Exchange Point
 ISP Workshop Lab Module 16 An Internet Exchange Point Objective: To investigate methods for connecting to an Internet Exchange Point. Prerequisites: Modules 12 and 13, and the Exchange Points Presentation
ISP Workshop Lab Module 16 An Internet Exchange Point Objective: To investigate methods for connecting to an Internet Exchange Point. Prerequisites: Modules 12 and 13, and the Exchange Points Presentation
Routing, Routing Algorithms & Protocols
 Routing, Routing Algorithms & Protocols Computer Networks Lecture 6 http://goo.gl/pze5o8 Circuit-Switched and Packet-Switched WANs 2 Circuit-Switched Networks Older (evolved from telephone networks), a
Routing, Routing Algorithms & Protocols Computer Networks Lecture 6 http://goo.gl/pze5o8 Circuit-Switched and Packet-Switched WANs 2 Circuit-Switched Networks Older (evolved from telephone networks), a
Configuring Redundant Routing on the VPN 3000 Concentrator
 Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
BGP Diverse Path Using a Diverse-Path Route Reflector
 BGP Diverse Path Using a Diverse-Path Route Reflector The feature allows Border Gateway Protocol (BGP) to distribute an alternative path other than the best path between BGP speakers when route reflectors
BGP Diverse Path Using a Diverse-Path Route Reflector The feature allows Border Gateway Protocol (BGP) to distribute an alternative path other than the best path between BGP speakers when route reflectors
Module: Routing Security. Professor Patrick McDaniel Spring CMPSC443 - Introduction to Computer and Network Security
 CMPSC443 - Introduction to Computer and Network Security Module: Routing Security Professor Patrick McDaniel Spring 2009 1 Routing 101 Network routing exists to provide hosts desirable paths from the source
CMPSC443 - Introduction to Computer and Network Security Module: Routing Security Professor Patrick McDaniel Spring 2009 1 Routing 101 Network routing exists to provide hosts desirable paths from the source
OSPF Protocol Overview on page 187. OSPF Standards on page 188. OSPF Area Terminology on page 188. OSPF Routing Algorithm on page 190
 Chapter 17 OSPF Protocol Overview The Open Shortest Path First (OSPF) protocol is an interior gateway protocol (IGP) that routes packets within a single autonomous system (AS). OSPF uses link-state information
Chapter 17 OSPF Protocol Overview The Open Shortest Path First (OSPF) protocol is an interior gateway protocol (IGP) that routes packets within a single autonomous system (AS). OSPF uses link-state information
Topology for: EIGRP, BGP, Redistribution
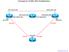 Topology for: EIGRP, BGP, Redistribution e1/0 10.0.12.1/24 10.0.12.2/24 e1/0 R1 s2/0 10.0.0.1/24 10.0.13.3/24 e0/0 10.0.23.2/24 e0/0 e0/0 10.0.13.1/24 R3 e1/0 10.0.23.3/24 R2 S2/0 10.0.0.2/24 PVC 104 PVC
Topology for: EIGRP, BGP, Redistribution e1/0 10.0.12.1/24 10.0.12.2/24 e1/0 R1 s2/0 10.0.0.1/24 10.0.13.3/24 e0/0 10.0.23.2/24 e0/0 e0/0 10.0.13.1/24 R3 e1/0 10.0.23.3/24 R2 S2/0 10.0.0.2/24 PVC 104 PVC
RIP Version 2. The Classless Brother
 RIP Version 2 The Classless Brother (C) Herbert Haas 2005/03/11 1 Why RIPv2 Need for subnet information and VLSM Need for Next Hop addresses for each route entry Need for external route tags Need for multicast
RIP Version 2 The Classless Brother (C) Herbert Haas 2005/03/11 1 Why RIPv2 Need for subnet information and VLSM Need for Next Hop addresses for each route entry Need for external route tags Need for multicast
Small additions by Dr. Enis Karaarslan, Purdue - Aaron Jarvis (Network Engineer)
 Routing Basics 1 Small additions by Dr. Enis Karaarslan, 2014 Purdue - Aaron Jarvis (Network Engineer) Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 3 IPv4
Routing Basics 1 Small additions by Dr. Enis Karaarslan, 2014 Purdue - Aaron Jarvis (Network Engineer) Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 3 IPv4
Inter-Domain Routing: BGP
 Inter-Domain Routing: BGP Stefano Vissicchio UCL Computer Science CS 3035/GZ01 Agenda We study how to route over the Internet 1. Context The Internet, a network of networks Relationships between ASes 2.
Inter-Domain Routing: BGP Stefano Vissicchio UCL Computer Science CS 3035/GZ01 Agenda We study how to route over the Internet 1. Context The Internet, a network of networks Relationships between ASes 2.
Service Advertisement Framework Configuration Guide, Cisco IOS Release 12.2SX
 Service Advertisement Framework Configuration Guide, Cisco IOS Release 12.2SX Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000
Service Advertisement Framework Configuration Guide, Cisco IOS Release 12.2SX Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000
J. A. Drew Hamilton, Jr., Ph.D. Director, Information Assurance Laboratory and Associate Professor Computer Science & Software Engineering
 Auburn Information Assurance Laboratory J. A. Drew Hamilton, Jr., Ph.D. Director, Information Assurance Laboratory and Associate Professor Computer Science & Software Engineering 107 Dunstan Hall Auburn
Auburn Information Assurance Laboratory J. A. Drew Hamilton, Jr., Ph.D. Director, Information Assurance Laboratory and Associate Professor Computer Science & Software Engineering 107 Dunstan Hall Auburn
Internet Routing : Fundamentals of Computer Networks Bill Nace
 Internet Routing 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Looking Ahead Lab #2 just due Quiz #2
Internet Routing 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Looking Ahead Lab #2 just due Quiz #2
Routing & Protocols 1
 Routing & Protocols 1 Paul Traina cisco Engineering 2 Today's Talk Terminology Routing Static Routes Interior Gateway Protocols Exterior Gateway Protocols Building an ISP network 3 Terminology network
Routing & Protocols 1 Paul Traina cisco Engineering 2 Today's Talk Terminology Routing Static Routes Interior Gateway Protocols Exterior Gateway Protocols Building an ISP network 3 Terminology network
Configuring basic MBGP
 Contents Configuring MBGP 1 MBGP overview 1 Protocols and standards 1 MBGP configuration task list 1 Configuring basic MBGP 2 Controlling route advertisement and reception 2 Configuration prerequisites
Contents Configuring MBGP 1 MBGP overview 1 Protocols and standards 1 MBGP configuration task list 1 Configuring basic MBGP 2 Controlling route advertisement and reception 2 Configuration prerequisites
Resource Public Key Infrastructure
 Resource Public Key Infrastructure A pilot for the Internet2 Community to secure the global route table Andrew Gallo The Basics The Internet is a self organizing network of networks. How do you find your
Resource Public Key Infrastructure A pilot for the Internet2 Community to secure the global route table Andrew Gallo The Basics The Internet is a self organizing network of networks. How do you find your
BGP can also be used for carrying routing information for IPv6 prefix over IPv6 networks.
 This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Border Gateway Protocol (). About, page 1 Guidelines for, page
This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Border Gateway Protocol (). About, page 1 Guidelines for, page
Network Layer: Routing
 Network Layer: Routing The Problem A B R 1 R 2 R 4 R 3 Goal: for each destination, compute next hop 1 Lecture 9 2 Basic Assumptions Trivial solution: Flooding Dynamic environment: links and routers unreliable:
Network Layer: Routing The Problem A B R 1 R 2 R 4 R 3 Goal: for each destination, compute next hop 1 Lecture 9 2 Basic Assumptions Trivial solution: Flooding Dynamic environment: links and routers unreliable:
Introduction to BGP. ISP Workshops. Last updated 30 October 2013
 Introduction to BGP ISP Workshops Last updated 30 October 2013 1 Border Gateway Protocol p A Routing Protocol used to exchange routing information between different networks n Exterior gateway protocol
Introduction to BGP ISP Workshops Last updated 30 October 2013 1 Border Gateway Protocol p A Routing Protocol used to exchange routing information between different networks n Exterior gateway protocol
Internet-Draft Intended status: Standards Track July 4, 2014 Expires: January 5, 2015
 Network Working Group M. Lepinski, Ed. Internet-Draft BBN Intended status: Standards Track July 4, 2014 Expires: January 5, 2015 Abstract BGPSEC Protocol Specification draft-ietf-sidr-bgpsec-protocol-09
Network Working Group M. Lepinski, Ed. Internet-Draft BBN Intended status: Standards Track July 4, 2014 Expires: January 5, 2015 Abstract BGPSEC Protocol Specification draft-ietf-sidr-bgpsec-protocol-09
Chapter 8 Configuring OSPF
 Chapter 8 Configuring OSPF This chapter describes how to configure OSPF on HP routing switches using the CLI and Web management interface. To display OSPF configuration information and statistics, see
Chapter 8 Configuring OSPF This chapter describes how to configure OSPF on HP routing switches using the CLI and Web management interface. To display OSPF configuration information and statistics, see
Table of Contents 1 MBGP Configuration 1-1
 Table of Contents 1 MBGP Configuration 1-1 MBGP Over 1-1 Protocols and Standards 1-2 MBGP Configuration Task List 1-2 Configuring MBGP Basic Functions 1-2 Prerequisites 1-2 Configuration Procedure 1-3
Table of Contents 1 MBGP Configuration 1-1 MBGP Over 1-1 Protocols and Standards 1-2 MBGP Configuration Task List 1-2 Configuring MBGP Basic Functions 1-2 Prerequisites 1-2 Configuration Procedure 1-3
Routing Overview for Firepower Threat Defense
 Path Determination This chapter describes underlying concepts of how routing behaves within the Cisco Firepower Threat Defense, and the routing protocols that are supported. Routing is the act of moving
Path Determination This chapter describes underlying concepts of how routing behaves within the Cisco Firepower Threat Defense, and the routing protocols that are supported. Routing is the act of moving
ICS 351: Today's plan. OSPF BGP Routing in general routing protocol comparison encapsulation network dynamics
 ICS 351: Today's plan OSPF BGP Routing in general routing protocol comparison encapsulation network dynamics OSPF OSPF generally used within a single Autonomous System (AS), i.e. within an organization
ICS 351: Today's plan OSPF BGP Routing in general routing protocol comparison encapsulation network dynamics OSPF OSPF generally used within a single Autonomous System (AS), i.e. within an organization
University of Belgrade - School of Electrical Engineering Department of Telecommunications
 University of Belgrade - School of Electrical Engineering Department of Telecommunications 1 BGP-4 Theory and Practice Berislav Todorović beri@etf.bg.ac.yu Nenad Krajnović krajko@etf.bg.ac.yu 2 Routers
University of Belgrade - School of Electrical Engineering Department of Telecommunications 1 BGP-4 Theory and Practice Berislav Todorović beri@etf.bg.ac.yu Nenad Krajnović krajko@etf.bg.ac.yu 2 Routers
Steven M. Bellovin AT&T Labs Research Florham Park, NJ 07932
 Steven M. Bellovin! " $#"##%& '( ) * 973-360-8656 AT&T Labs Research Florham Park, NJ 07932 Steven M. Bellovin June 13, 2003 1 What is? Bad guys play games with routing protocols. Traffic is diverted.
Steven M. Bellovin! " $#"##%& '( ) * 973-360-8656 AT&T Labs Research Florham Park, NJ 07932 Steven M. Bellovin June 13, 2003 1 What is? Bad guys play games with routing protocols. Traffic is diverted.
