61A Lecture 31. November 14th 2011
|
|
|
- Wilfred Harrison
- 6 years ago
- Views:
Transcription
1 61A Lecture 31 November 14th 2011
2 Parallel and Distributed Computing Coordinating groups of computers
3 So far functions data structures objects abstraction interpretation evaluation 3
4 So far functions data structures objects One program One machine abstraction One computer interpretation evaluation 4
5 Parallel and Distributed Computing Distributed Computing Groups of computers communicating and exchanging data with a shared goal. Communication networks Data storage Large scale computing Parallel Computing One computer with many processes collaborating to execute the same program faster. Speeding up computation 5
6 Lecture plan Today Distributed computing Wednesday Parallel computing: problems Friday Parallel computing: solutions 6
7 Distributed Computer Systems Interconnected groups of independent computers that collaborate to get work done. 7
8 Characteristics of distributed systems 1. Independent computers 2. (Often) In different locations 3. Connected by a network 4. Communicate by passing messages to each other 5. A shared computational goal. 8
9 Examples of distributed systems Information sharing & communication Telephone networks, cellular networks The world wide web Skype, IM, Xbox/PlayStation and other online multiplayer systems Large scale computation Cloud computing - Amazon and Microsoft MapReduce - later in this course 9
10 Topics in Distributed Systems Architectures Client-server Peer-to-peer Message passing Design principles Modularity Interfaces 10
11 Architecture Computers in a distributed system can have different roles depending on the goal of the system. The network of computers can be structured in different ways. Client-server Peer-to-peer 11
12 Client-Server Architecture request Good for dispensing a service request 2 roles request Clients: make requests from server response request server response request Server: listens for requests and responds to them. request Many s request Only 1 server. request 12
13 Example: world wide web The New York Times request response 13
14 Example: world wide web Server s job Listen for requests Calculate front page ads personalized content Send web page back to correct browser Client s job Send correct request to server based on user input Display received web page fonts & colors images interactivity Send further requests 14
15 Division of labor Server One source Many consumers Provide information or service Use service, or make it usable to humans Client 15
16 Single point of failure request request request Server is a single point of failure. response request server response request System stops working if server goes down. If goes down, only that is affected. request request request 16
17 Disadvantage: performance degrades under load The more s that want to use a server, the worse the server performs Connection speed becomes slow -- limited bandwidth Server becomes slow to respond -- limited processing power Cannot shrink and grow with changing demand 17
18 Peer to peer architecture Division of labor among all computers All computers send and receive data All computer contribute resources Disk space Memory Processing power Applications Data storage Communication Large-scale computation 18
19 The importance of an organized network structure B A 19
20 The importance of an organized network structure B A The shortest path for A to send a message to B. 20
21 The importance of an organized network structure B A roundabout path A Inefficient. 21
22 The importance of an organized network structure B Everyone sends A s message to their neighbors, until B is reached. A Huge load on network. Inefficient use of resources 22
23 Supernodes: keep track of network structure Computers with a special function No longer pure peer-topeer Knows locations of other supernodes Knows which computers are under it Keeps track of newcomers and computers that leave 23
24 Example: Skype B Peers: all computers running skype Not a pure peer-to-peer network Supernodes coordinate users and manage sign-ins and sign-outs. A 24
25 Disadvantages Complex network structure Inefficiency in communication Can take up a lot of traffic trying to route messages. Advantages No single point of failure Can grow and shrink with demand 25
26 Messages A B Used to coordinate behavior Send or receive data Request that a function be executed Signal that a particular event has occurred 26
27 Message Structure A B SENDER RECIPIENT... CONTENT... 27
28 Message Structure A B SENDER So recipient knows where to send response RECIPIENT... CONTENT... So message can be routed properly. Data, remote procedure call, signal, encoded video, text, etc. 28
29 Within a program A (string,...,...) B Sender and recipient implicit Dispatch procedure Data sent using underlying data structures.???? A B Over a network, there are no underlying data structures! 29
30 Message protocol A B A set of rules for encoding and decoding messages. All computers in the system must obey the protocol when sending and receiving messages. Example The first 3 bytes are the sender The next 3 bytes are the recipient After that is the content, which is video, encoded according to... etc. etc. 30
31 Example: messages on the world wide web 31
32 Example: messages on the world wide web Protocol name Server Requested page Your IP address en.wikipedia.org GET wiki/uc_berkeley HTTP
33 Modularity The components of a system should be black boxes with respect to each other. The black boxes are required to hold up interfaces. Dispatch procedures General Systems Interface = List of messages that can be taken in Responses that should be given to each message Interface = List of inputs that can be taken in Outputs that should be given in response to inputs. 33
34 Advantages of modularity Easy to understand => Easy to change and expand If something goes wrong, only defective component needs to be replaced Easy to debug Compare real outputs to the supposed interface Defective component is the one that doesn t hold up the interface any longer. 34
Chapter 4: Distributed and Parallel Computing
 Chapter 4: Distributed and Parallel Computing Contents 4.1 Introduction 1 4.2 Distributed Computing 1 4.2.1 Client/Server Systems........................................ 1 4.2.2 Peer-to-peer Systems........................................
Chapter 4: Distributed and Parallel Computing Contents 4.1 Introduction 1 4.2 Distributed Computing 1 4.2.1 Client/Server Systems........................................ 1 4.2.2 Peer-to-peer Systems........................................
CS61A Lecture 28 Distributed Computing. Jom Magrotker UC Berkeley EECS August 6, 2012
 CS61A Lecture 28 Distributed Computing Jom Magrotker UC Berkeley EECS August 6, 2012 COMPUTER SCIENCE IN THE NEWS http://www.newscientist.com/blogs/onepercent/2012/07/ai predicts when youre about t.html
CS61A Lecture 28 Distributed Computing Jom Magrotker UC Berkeley EECS August 6, 2012 COMPUTER SCIENCE IN THE NEWS http://www.newscientist.com/blogs/onepercent/2012/07/ai predicts when youre about t.html
ITEC 350: Introduction To Computer Networking Midterm Exam #2 Key. Fall 2008
 ITEC 350: Introduction To Computer Networking Midterm Exam #2 Key Closed book and closed notes. Fall 2008 No electronic devices allowed, e.g., calculator, laptop, PDA. Show your work. No work, no credit.
ITEC 350: Introduction To Computer Networking Midterm Exam #2 Key Closed book and closed notes. Fall 2008 No electronic devices allowed, e.g., calculator, laptop, PDA. Show your work. No work, no credit.
Network Applications Principles of Network Applications
 Network Applications Principles of Network Applications A Network application is an application running on one host and provides communication to another application running on a different host. At the
Network Applications Principles of Network Applications A Network application is an application running on one host and provides communication to another application running on a different host. At the
Good day. Today we will be talking about Local Internetworking What is Internetworking? Internetworking is the connection of different networks.
 Computer Networks Prof: Sujoy Ghosh Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture - 21 Local Internetworking Good day. Today we will be talking about
Computer Networks Prof: Sujoy Ghosh Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture - 21 Local Internetworking Good day. Today we will be talking about
November 2017 WebRTC for Live Media and Broadcast Second screen and CDN traffic optimization. Author: Jesús Oliva Founder & Media Lead Architect
 November 2017 WebRTC for Live Media and Broadcast Second screen and CDN traffic optimization Author: Jesús Oliva Founder & Media Lead Architect Introduction It is not a surprise if we say browsers are
November 2017 WebRTC for Live Media and Broadcast Second screen and CDN traffic optimization Author: Jesús Oliva Founder & Media Lead Architect Introduction It is not a surprise if we say browsers are
Today s class. Operating System Machine Level. Informationsteknologi. Friday, November 16, 2007 Computer Architecture I - Class 12 1
 Today s class Operating System Machine Level Friday, November 16, 2007 Computer Architecture I - Class 12 1 Operating System Machine Friday, November 16, 2007 Computer Architecture I - Class 12 2 Paging
Today s class Operating System Machine Level Friday, November 16, 2007 Computer Architecture I - Class 12 1 Operating System Machine Friday, November 16, 2007 Computer Architecture I - Class 12 2 Paging
Introductions. Computer Networking Lecture 01. January 16, HKU SPACE Community College. HKU SPACE CC CN Lecture 01 1/36
 Introductions Computer Networking Lecture 01 HKU SPACE Community College January 16, 2012 HKU SPACE CC CN Lecture 01 1/36 Outline What is a Computer Network? Basic Requirements of Building a Computer Network
Introductions Computer Networking Lecture 01 HKU SPACE Community College January 16, 2012 HKU SPACE CC CN Lecture 01 1/36 Outline What is a Computer Network? Basic Requirements of Building a Computer Network
Memory: Overview. CS439: Principles of Computer Systems February 26, 2018
 Memory: Overview CS439: Principles of Computer Systems February 26, 2018 Where We Are In the Course Just finished: Processes & Threads CPU Scheduling Synchronization Next: Memory Management Virtual Memory
Memory: Overview CS439: Principles of Computer Systems February 26, 2018 Where We Are In the Course Just finished: Processes & Threads CPU Scheduling Synchronization Next: Memory Management Virtual Memory
Part I: Hardware and communication
 Part I: Hardware and communication The following are a list of definitions for most things in the first section of the syllabus for CG1(Computing Theory). To test yourself on these items, you should attempt
Part I: Hardware and communication The following are a list of definitions for most things in the first section of the syllabus for CG1(Computing Theory). To test yourself on these items, you should attempt
Lecture 1: January 22
 CMPSCI 677 Distributed and Operating Systems Spring 2018 Lecture 1: January 22 Lecturer: Prashant Shenoy Scribe: Bin Wang 1.1 Introduction to the course The lecture started by outlining the administrative
CMPSCI 677 Distributed and Operating Systems Spring 2018 Lecture 1: January 22 Lecturer: Prashant Shenoy Scribe: Bin Wang 1.1 Introduction to the course The lecture started by outlining the administrative
AT&T SD-WAN Network Based service quick start guide
 AT&T SD-WAN Network Based service quick start guide After you order your AT&T SD-WAN Network Based service, you can: Create administrator accounts Log in to the SD-WAN orchestrator Configure business policy
AT&T SD-WAN Network Based service quick start guide After you order your AT&T SD-WAN Network Based service, you can: Create administrator accounts Log in to the SD-WAN orchestrator Configure business policy
Linked lists. Prof. Noah Snavely CS1114
 Linked lists Prof. Noah Snavely CS1114 http://cs1114.cs.cornell.edu Administrivia Assignment 2, Part 2 due tomorrow Please don t wait until the last minute to finish (the last two problems are challenging)
Linked lists Prof. Noah Snavely CS1114 http://cs1114.cs.cornell.edu Administrivia Assignment 2, Part 2 due tomorrow Please don t wait until the last minute to finish (the last two problems are challenging)
Web Mechanisms. Draft: 2/23/13 6:54 PM 2013 Christopher Vickery
 Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
CS 162 Operating Systems and Systems Programming Professor: Anthony D. Joseph Spring Lecture 20: Networks and Distributed Systems
 S 162 Operating Systems and Systems Programming Professor: Anthony D. Joseph Spring 2003 Lecture 20: Networks and Distributed Systems 20.0 Main Points Motivation for distributed vs. centralized systems
S 162 Operating Systems and Systems Programming Professor: Anthony D. Joseph Spring 2003 Lecture 20: Networks and Distributed Systems 20.0 Main Points Motivation for distributed vs. centralized systems
CS 162 Operating Systems and Systems Programming Professor: Anthony D. Joseph Spring Lecture 19: Networks and Distributed Systems
 S 162 Operating Systems and Systems Programming Professor: Anthony D. Joseph Spring 2004 Lecture 19: Networks and Distributed Systems 19.0 Main Points Motivation for distributed vs. centralized systems
S 162 Operating Systems and Systems Programming Professor: Anthony D. Joseph Spring 2004 Lecture 19: Networks and Distributed Systems 19.0 Main Points Motivation for distributed vs. centralized systems
Unit A - Connecting to the Network
 Unit A - Connecting to the Network 1 What is a network? The ability to connect people and equipment no matter where they are in the world. telephone computers television How does your body work as a network?
Unit A - Connecting to the Network 1 What is a network? The ability to connect people and equipment no matter where they are in the world. telephone computers television How does your body work as a network?
Department of Industrial Engineering. Sharif University of Technology. Contents: The role of managers in Information Technology (IT)
 Department of Industrial Engineering Sharif University of Technology Session# 14 Contents: The role of managers in Information Technology (IT) Organizational Issues Information Technology Operational and
Department of Industrial Engineering Sharif University of Technology Session# 14 Contents: The role of managers in Information Technology (IT) Organizational Issues Information Technology Operational and
SaaS Providers. ThousandEyes for. Summary
 USE CASE ThousandEyes for SaaS Providers Summary With Software-as-a-Service (SaaS) applications rapidly replacing onpremise solutions, the onus of ensuring a great user experience for these applications
USE CASE ThousandEyes for SaaS Providers Summary With Software-as-a-Service (SaaS) applications rapidly replacing onpremise solutions, the onus of ensuring a great user experience for these applications
Computer Systems C S Cynthia Lee Today s materials adapted from Kevin Webb at Swarthmore College
 Computer Systems C S 0 7 Cynthia Lee Today s materials adapted from Kevin Webb at Swarthmore College 2 Today s Topics TODAY S LECTURE: Caching ANNOUNCEMENTS: Assign6 & Assign7 due Friday! 6 & 7 NO late
Computer Systems C S 0 7 Cynthia Lee Today s materials adapted from Kevin Webb at Swarthmore College 2 Today s Topics TODAY S LECTURE: Caching ANNOUNCEMENTS: Assign6 & Assign7 due Friday! 6 & 7 NO late
Definition. Quantifying Anonymity. Anonymous Communication. How can we calculate how anonymous we are? Who you are from the communicating party
 Definition Anonymous Communication Hiding identities of parties involved in communications from each other, or from third-parties Who you are from the communicating party Who you are talking to from everyone
Definition Anonymous Communication Hiding identities of parties involved in communications from each other, or from third-parties Who you are from the communicating party Who you are talking to from everyone
Component Function Example
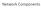 Network Components Component Names Component Function Example Application, or app, user Uses the network Skype, itunes, Amazon Host, or end-system, edge device, node, source, sink Router, or switch, node,
Network Components Component Names Component Function Example Application, or app, user Uses the network Skype, itunes, Amazon Host, or end-system, edge device, node, source, sink Router, or switch, node,
ECE 650 Systems Programming & Engineering. Spring 2018
 ECE 650 Systems Programming & Engineering Spring 2018 Networking Introduction Tyler Bletsch Duke University Slides are adapted from Brian Rogers (Duke) Computer Networking A background of important areas
ECE 650 Systems Programming & Engineering Spring 2018 Networking Introduction Tyler Bletsch Duke University Slides are adapted from Brian Rogers (Duke) Computer Networking A background of important areas
Lecture 1: January 23
 CMPSCI 677 Distributed and Operating Systems Spring 2019 Lecture 1: January 23 Lecturer: Prashant Shenoy Scribe: Jonathan Westin (2019), Bin Wang (2018) 1.1 Introduction to the course The lecture started
CMPSCI 677 Distributed and Operating Systems Spring 2019 Lecture 1: January 23 Lecturer: Prashant Shenoy Scribe: Jonathan Westin (2019), Bin Wang (2018) 1.1 Introduction to the course The lecture started
CSCI Computer Networks
 CSCI-1680 - Computer Networks Chen Avin (avin) Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti, Peterson & Davie, Rodrigo Fonseca Administrivia Sign and hand in Collaboration
CSCI-1680 - Computer Networks Chen Avin (avin) Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti, Peterson & Davie, Rodrigo Fonseca Administrivia Sign and hand in Collaboration
OSI Transport Layer. Network Fundamentals Chapter 4. Version Cisco Systems, Inc. All rights reserved. Cisco Public 1
 OSI Transport Layer Network Fundamentals Chapter 4 Version 4.0 1 Transport Layer Role and Services Transport layer is responsible for overall end-to-end transfer of application data 2 Transport Layer Role
OSI Transport Layer Network Fundamentals Chapter 4 Version 4.0 1 Transport Layer Role and Services Transport layer is responsible for overall end-to-end transfer of application data 2 Transport Layer Role
Describe the two most important ways in which subspaces of F D arise. (These ways were given as the motivation for looking at subspaces.
 Quiz Describe the two most important ways in which subspaces of F D arise. (These ways were given as the motivation for looking at subspaces.) What are the two subspaces associated with a matrix? Describe
Quiz Describe the two most important ways in which subspaces of F D arise. (These ways were given as the motivation for looking at subspaces.) What are the two subspaces associated with a matrix? Describe
From last time to this time
 /7/6 CS/MA 9 Fall 26 Wayne Snyder Department Boston University Today and Wednesday: Error-detecting and error-correcting codes Wednesday & Friday: Cryptography From last time to this time Compression takes
/7/6 CS/MA 9 Fall 26 Wayne Snyder Department Boston University Today and Wednesday: Error-detecting and error-correcting codes Wednesday & Friday: Cryptography From last time to this time Compression takes
Internet Protocol Stack! Principles of Network Applications! Some Network Apps" (and Their Protocols)! Application-Layer Protocols! Our goals:!
 Internet Protocol Stack! Principles of Network Applications! application: supporting network applications!! HTTP,, FTP, etc.! transport: endhost-endhost data transfer!! TCP, UDP! network: routing of datagrams
Internet Protocol Stack! Principles of Network Applications! application: supporting network applications!! HTTP,, FTP, etc.! transport: endhost-endhost data transfer!! TCP, UDP! network: routing of datagrams
Media-Ready Network Transcript
 Media-Ready Network Transcript Hello and welcome to this Cisco on Cisco Seminar. I m Bob Scarbrough, Cisco IT manager on the Cisco on Cisco team. With me today are Sheila Jordan, Vice President of the
Media-Ready Network Transcript Hello and welcome to this Cisco on Cisco Seminar. I m Bob Scarbrough, Cisco IT manager on the Cisco on Cisco team. With me today are Sheila Jordan, Vice President of the
NET ID. CS519, Prelim (March 17, 2004) NAME: You have 50 minutes to complete the test. 1/17
 CS519, Prelim (March 17, 2004) NAME: You have 50 minutes to complete the test. 1/17 Q1. 2 points Write your NET ID at the top of every page of this test. Q2. X points Name 3 advantages of a circuit network
CS519, Prelim (March 17, 2004) NAME: You have 50 minutes to complete the test. 1/17 Q1. 2 points Write your NET ID at the top of every page of this test. Q2. X points Name 3 advantages of a circuit network
Computer networks 2013
 Chapter 4 EXERCISE 1 1 Describe what is meant by each of the following: a Router b Bridge c Proxy server Answers: see the Glossary. 2 Many small businesses have computer networks. a List three advantages
Chapter 4 EXERCISE 1 1 Describe what is meant by each of the following: a Router b Bridge c Proxy server Answers: see the Glossary. 2 Many small businesses have computer networks. a List three advantages
Scalable overlay Networks
 overlay Networks Dr. Samu Varjonen 1 Lectures MO 15.01. C122 Introduction. Exercises. Motivation. TH 18.01. DK117 Unstructured networks I MO 22.01. C122 Unstructured networks II TH 25.01. DK117 Bittorrent
overlay Networks Dr. Samu Varjonen 1 Lectures MO 15.01. C122 Introduction. Exercises. Motivation. TH 18.01. DK117 Unstructured networks I MO 22.01. C122 Unstructured networks II TH 25.01. DK117 Bittorrent
Parts of a Network. app. router. link. host. Computer Networks 2
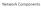 Network Components Parts of a Network app host router link Computer Networks 2 Parts of a Network app host router link Computer Networks 3 Component Names Component Function Example Application, or app,
Network Components Parts of a Network app host router link Computer Networks 2 Parts of a Network app host router link Computer Networks 3 Component Names Component Function Example Application, or app,
CSC 2405: Computer Systems II
 CSC 2405: Computer Systems II Dr. Mirela Damian http://www.csc.villanova.edu/~mdamian/csc2405/ Spring 2016 Course Goals: Look under the hood Help you learn what happens under the hood of computer systems
CSC 2405: Computer Systems II Dr. Mirela Damian http://www.csc.villanova.edu/~mdamian/csc2405/ Spring 2016 Course Goals: Look under the hood Help you learn what happens under the hood of computer systems
CLIENT SERVER ARCHITECTURE:
 CLIENT SERVER ARCHITECTURE: Client-Server architecture is an architectural deployment style that describe the separation of functionality into layers with each segment being a tier that can be located
CLIENT SERVER ARCHITECTURE: Client-Server architecture is an architectural deployment style that describe the separation of functionality into layers with each segment being a tier that can be located
The Internet and World Wide Web. Chapter4
 The Internet and World Wide Web Chapter4 ITBIS105 IS-IT-UOB 2016 The Internet What is the Internet? Worldwide collection of millions of computers networks that connects ITBIS105 IS-IT-UOB 2016 2 History
The Internet and World Wide Web Chapter4 ITBIS105 IS-IT-UOB 2016 The Internet What is the Internet? Worldwide collection of millions of computers networks that connects ITBIS105 IS-IT-UOB 2016 2 History
Lecture 16: Interdomain Routing. CSE 123: Computer Networks Stefan Savage
 Lecture 16: Interdomain Routing CSE 123: Computer Networks Stefan Savage Overview Autonomous Systems Each network on the Internet has its own goals Path-vector Routing Allows scalable, informed route selection
Lecture 16: Interdomain Routing CSE 123: Computer Networks Stefan Savage Overview Autonomous Systems Each network on the Internet has its own goals Path-vector Routing Allows scalable, informed route selection
ICS 451: Today's plan. Network Layer Protocols: virtual circuits Static Routing Distance-Vector Routing
 ICS 451: Today's plan Network Layer Protocols: virtual circuits Static Routing Distance-Vector Routing Virtual Circuits: Motivation Implementing the routing table in hardware can be expensive to make it
ICS 451: Today's plan Network Layer Protocols: virtual circuits Static Routing Distance-Vector Routing Virtual Circuits: Motivation Implementing the routing table in hardware can be expensive to make it
Lecture 2: Links and Signaling
 Lecture 2: Links and Signaling CSE 123: Computer Networks Alex C. Snoeren DISCUSSION @7pm Tomorrow Our Problem Communications is complicated Modulation and encoding bits Splitting sequences of bits into
Lecture 2: Links and Signaling CSE 123: Computer Networks Alex C. Snoeren DISCUSSION @7pm Tomorrow Our Problem Communications is complicated Modulation and encoding bits Splitting sequences of bits into
ThousandEyes for. Application Delivery White Paper
 ThousandEyes for Application Delivery White Paper White Paper Summary The rise of mobile applications, the shift from on-premises to Software-as-a-Service (SaaS), and the reliance on third-party services
ThousandEyes for Application Delivery White Paper White Paper Summary The rise of mobile applications, the shift from on-premises to Software-as-a-Service (SaaS), and the reliance on third-party services
Traceroute. Communication Networks. Decipher a Packet Route. Exercises week 1 and 2 Introduction. Prof. Laurent Vanbever Networked Systems Group
 Prof. Laurent Vanbever Networked Systems Group Communication Networks Exercises week 1 and 2 Introduction Traceroute Decipher a Packet Route The traceroute (or tracert on Windows) command a is a useful
Prof. Laurent Vanbever Networked Systems Group Communication Networks Exercises week 1 and 2 Introduction Traceroute Decipher a Packet Route The traceroute (or tracert on Windows) command a is a useful
Ossification of the Internet
 Ossification of the Internet The Internet evolved as an experimental packet-switched network Today, many aspects appear to be set in stone - Witness difficulty in getting IP multicast deployed - Major
Ossification of the Internet The Internet evolved as an experimental packet-switched network Today, many aspects appear to be set in stone - Witness difficulty in getting IP multicast deployed - Major
Announcements. me your survey: See the Announcements page. Today. Reading. Take a break around 10:15am. Ack: Some figures are from Coulouris
 Announcements Email me your survey: See the Announcements page Today Conceptual overview of distributed systems System models Reading Today: Chapter 2 of Coulouris Next topic: client-side processing (HTML,
Announcements Email me your survey: See the Announcements page Today Conceptual overview of distributed systems System models Reading Today: Chapter 2 of Coulouris Next topic: client-side processing (HTML,
CSE 123A Computer Networks
 CSE 123A Computer Networks Winter 2005 Lecture 14 Congestion Control Some images courtesy David Wetherall Animations by Nick McKeown and Guido Appenzeller The bad news and the good news The bad news: new
CSE 123A Computer Networks Winter 2005 Lecture 14 Congestion Control Some images courtesy David Wetherall Animations by Nick McKeown and Guido Appenzeller The bad news and the good news The bad news: new
Last Class: Clock Synchronization. Today: More Canonical Problems
 Last Class: Clock Synchronization Logical clocks Vector clocks Global state Lecture 11, page 1 Today: More Canonical Problems Distributed snapshot and termination detection Election algorithms Bully algorithm
Last Class: Clock Synchronization Logical clocks Vector clocks Global state Lecture 11, page 1 Today: More Canonical Problems Distributed snapshot and termination detection Election algorithms Bully algorithm
Fundamentals of Communications Networks
 Fundamentals of Communications Networks Yaakov (J) Stein Fundamentals of Communications Networks 1 Digital Communications Services and Networks Fundamentals of Communications Networks 2 Father of the telephone
Fundamentals of Communications Networks Yaakov (J) Stein Fundamentals of Communications Networks 1 Digital Communications Services and Networks Fundamentals of Communications Networks 2 Father of the telephone
Basic Computer Hardware
 CSC 2405: Computer Systems II Spring 2014 (TR 8:30-9:45 in G86) Mirela Damian http://www.csc.villanova.edu/~mdamian/csc2405/ Basic Computer Hardware CPU Control Data BUS Memory (RAM) I/O Device 1 Basic
CSC 2405: Computer Systems II Spring 2014 (TR 8:30-9:45 in G86) Mirela Damian http://www.csc.villanova.edu/~mdamian/csc2405/ Basic Computer Hardware CPU Control Data BUS Memory (RAM) I/O Device 1 Basic
Lecture 2: January 24
 CMPSCI 677 Operating Systems Spring 2017 Lecture 2: January 24 Lecturer: Prashant Shenoy Scribe: Phuthipong Bovornkeeratiroj 2.1 Lecture 2 Distributed systems fall into one of the architectures teaching
CMPSCI 677 Operating Systems Spring 2017 Lecture 2: January 24 Lecturer: Prashant Shenoy Scribe: Phuthipong Bovornkeeratiroj 2.1 Lecture 2 Distributed systems fall into one of the architectures teaching
Memory - Paging. Copyright : University of Illinois CS 241 Staff 1
 Memory - Paging Copyright : University of Illinois CS 241 Staff 1 Physical Frame Allocation How do we allocate physical memory across multiple processes? What if Process A needs to evict a page from Process
Memory - Paging Copyright : University of Illinois CS 241 Staff 1 Physical Frame Allocation How do we allocate physical memory across multiple processes? What if Process A needs to evict a page from Process
Part I Overview Chapter 1: Introduction
 Part I Overview Chapter 1: Introduction Fall 2010 1 What is an Operating System? A computer system can be roughly divided into the hardware, the operating system, the application i programs, and dthe users.
Part I Overview Chapter 1: Introduction Fall 2010 1 What is an Operating System? A computer system can be roughly divided into the hardware, the operating system, the application i programs, and dthe users.
Skype for Business for Android
 Skype for Business for Android November 2015 Topics in this guide include: Joining meetings Updating availability status Managing contacts Having conversations Customizing your settings For more information
Skype for Business for Android November 2015 Topics in this guide include: Joining meetings Updating availability status Managing contacts Having conversations Customizing your settings For more information
IP Security Protocol Working Group (IPSEC) draft-ietf-ipsec-nat-t-ike-03.txt. B. Swander Microsoft V. Volpe Cisco Systems 24 June 2002
 IP Security Protocol Working Group (IPSEC) INTERNET-DRAFT draft-ietf-ipsec-nat-t-ike-03.txt Expires: 24 December 2002 T. Kivinen SSH Communications Security A. Huttunen F- Secure Corporation B. Swander
IP Security Protocol Working Group (IPSEC) INTERNET-DRAFT draft-ietf-ipsec-nat-t-ike-03.txt Expires: 24 December 2002 T. Kivinen SSH Communications Security A. Huttunen F- Secure Corporation B. Swander
Lecture 14: Multimedia Communications
 Lecture 14: Multimedia Communications Prof. Shervin Shirmohammadi SITE, University of Ottawa Fall 2005 CEG 4183 14-1 Multimedia Characteristics Bandwidth Media has natural bitrate, not very flexible. Packet
Lecture 14: Multimedia Communications Prof. Shervin Shirmohammadi SITE, University of Ottawa Fall 2005 CEG 4183 14-1 Multimedia Characteristics Bandwidth Media has natural bitrate, not very flexible. Packet
Chapter 1 : Introduction to Computer Networks
 Topic List: A. Need to Share Resources B. Layering Concept and Example C. TCP/IP and OSI Layering Models D. Connection Oriented vs. Connectionless Transfer E. Top-Down and Bottom Up Approaches to study
Topic List: A. Need to Share Resources B. Layering Concept and Example C. TCP/IP and OSI Layering Models D. Connection Oriented vs. Connectionless Transfer E. Top-Down and Bottom Up Approaches to study
CS 640: Introduction to Computer Networks
 CS 640: Introduction to Computer Networks Midterm I 10/19/2006 Allotted time: 11:00AM to 12:30 PM (90 minutes) Name: Answers in bold italic font UW -ID Number: 1. There are 6 questions in this mid-term.
CS 640: Introduction to Computer Networks Midterm I 10/19/2006 Allotted time: 11:00AM to 12:30 PM (90 minutes) Name: Answers in bold italic font UW -ID Number: 1. There are 6 questions in this mid-term.
Large- Scale Sor,ng: Breaking World Records. Mike Conley CSE 124 Guest Lecture 12 March 2015
 Large- Scale Sor,ng: Breaking World Records Mike Conley CSE 124 Guest Lecture 12 March 2015 Sor,ng Given an array of items, put them in order 5 2 8 0 2 5 4 9 0 1 0 0 0 0 0 0 1 2 2 4 5 5 8 9 Many algorithms
Large- Scale Sor,ng: Breaking World Records Mike Conley CSE 124 Guest Lecture 12 March 2015 Sor,ng Given an array of items, put them in order 5 2 8 0 2 5 4 9 0 1 0 0 0 0 0 0 1 2 2 4 5 5 8 9 Many algorithms
Programming Assignment 3: Transmission Control Protocol
 CS 640 Introduction to Computer Networks Spring 2005 http://www.cs.wisc.edu/ suman/courses/640/s05 Programming Assignment 3: Transmission Control Protocol Assigned: March 28,2005 Due: April 15, 2005, 11:59pm
CS 640 Introduction to Computer Networks Spring 2005 http://www.cs.wisc.edu/ suman/courses/640/s05 Programming Assignment 3: Transmission Control Protocol Assigned: March 28,2005 Due: April 15, 2005, 11:59pm
Midterm Exam #2 December 4, 2013 CS162 Operating Systems
 University of California, Berkeley College of Engineering Computer Science Division EECS Fall 2013 Anthony D. Joseph and John Canny Midterm Exam #2 December 4, 2013 CS162 Operating Systems Your Name: SID
University of California, Berkeley College of Engineering Computer Science Division EECS Fall 2013 Anthony D. Joseph and John Canny Midterm Exam #2 December 4, 2013 CS162 Operating Systems Your Name: SID
UseNet and Gossip Protocol
 CPSC 426/526 UseNet and Gossip Protocol Ennan Zhai Computer Science Department Yale University Recall: Lec-1 Understanding: - Distributed systems vs. decentralized systems - Why we need both? red P2P network
CPSC 426/526 UseNet and Gossip Protocol Ennan Zhai Computer Science Department Yale University Recall: Lec-1 Understanding: - Distributed systems vs. decentralized systems - Why we need both? red P2P network
CS61C Machine Structures Lecture 37 Networks. No Machine is an Island!
 CS61C Machine Structures Lecture 37 Networks April 24, 2006 John Wawrzynek Page 1 No Machine is an Island! Computer Processor (active) Control ( brain ) Datapath ( brawn ) Memory (passive) (where programs,
CS61C Machine Structures Lecture 37 Networks April 24, 2006 John Wawrzynek Page 1 No Machine is an Island! Computer Processor (active) Control ( brain ) Datapath ( brawn ) Memory (passive) (where programs,
CS 307: Software Engineering. Lecture 10: Software Design and Architecture
 CS 307: Software Engineering Lecture 10: Software Design and Architecture Prof. Jeff Turkstra 2017 Dr. Jeffrey A. Turkstra 1 Announcements Discuss your product backlog in person or via email by Today Office
CS 307: Software Engineering Lecture 10: Software Design and Architecture Prof. Jeff Turkstra 2017 Dr. Jeffrey A. Turkstra 1 Announcements Discuss your product backlog in person or via email by Today Office
Introduction to the Internet
 Introduction to the Internet CCST9015 8 th Sep, 2010 Dr. Hayden Kwok-Hay So Department of Electrical and Electronic Engineering 2 Internet in 2003 3 Internet Basics The Internet is a network that connects
Introduction to the Internet CCST9015 8 th Sep, 2010 Dr. Hayden Kwok-Hay So Department of Electrical and Electronic Engineering 2 Internet in 2003 3 Internet Basics The Internet is a network that connects
Architecture as Interface
 Architecture as Interface André DeHon Friday, June 21, 2002 Previously How do we build efficient, programmable machines How we mix Computational complexity W/ physical landscape
Architecture as Interface André DeHon Friday, June 21, 2002 Previously How do we build efficient, programmable machines How we mix Computational complexity W/ physical landscape
CS 43: Computer Networks The Link Layer. Kevin Webb Swarthmore College November 28, 2017
 CS 43: Computer Networks The Link Layer Kevin Webb Swarthmore College November 28, 2017 TCP/IP Protocol Stack host host HTTP Application Layer HTTP TCP Transport Layer TCP router router IP IP Network Layer
CS 43: Computer Networks The Link Layer Kevin Webb Swarthmore College November 28, 2017 TCP/IP Protocol Stack host host HTTP Application Layer HTTP TCP Transport Layer TCP router router IP IP Network Layer
Lecture 10: Protocol Design
 Lecture 10: Protocol Design Prof. Shervin Shirmohammadi SITE, University of Ottawa Fall 2005 CEG 4183 10-1 Introduction TCP and UDP are generic protocols: They fulfill the needs of a wide range of applications
Lecture 10: Protocol Design Prof. Shervin Shirmohammadi SITE, University of Ottawa Fall 2005 CEG 4183 10-1 Introduction TCP and UDP are generic protocols: They fulfill the needs of a wide range of applications
Communication Networks. Prof. Laurent Vanbever. Exercises week 1 and 2 Introduction. a https://linux.die.net/man/8/traceroute
 Communication Networks Prof. Laurent Vanbever Exercises week 1 and 2 Introduction Traceroute Decipher a Packet Route The traceroute (or tracert on Windows) command a is a useful tool to observe the route
Communication Networks Prof. Laurent Vanbever Exercises week 1 and 2 Introduction Traceroute Decipher a Packet Route The traceroute (or tracert on Windows) command a is a useful tool to observe the route
This is a sample chapter of WebRTC: APIs and RTCWEB Protocols of the HTML5 Real-Time Web by Alan B. Johnston and Daniel C. Burnett.
 This is a sample chapter of WebRTC: APIs and RTCWEB Protocols of the HTML5 Real-Time Web by Alan B. Johnston and Daniel C. Burnett. For more information or to buy the paperback or ebook editions, visit
This is a sample chapter of WebRTC: APIs and RTCWEB Protocols of the HTML5 Real-Time Web by Alan B. Johnston and Daniel C. Burnett. For more information or to buy the paperback or ebook editions, visit
An Introduction to Python (TEJ3M & TEJ4M)
 An Introduction to Python (TEJ3M & TEJ4M) What is a Programming Language? A high-level language is a programming language that enables a programmer to write programs that are more or less independent of
An Introduction to Python (TEJ3M & TEJ4M) What is a Programming Language? A high-level language is a programming language that enables a programmer to write programs that are more or less independent of
Exercises for the Lectures on Communication Networks
 Exercises for the Lectures on Prof. Jochen Seitz & Dipl.-Ing. Karsten Renhak Department of University of Technology Ilmenau October 5, 010 [Jochen.Seitz Karsten.Renhak]@tu-ilmenau.de Contents 1 Communication
Exercises for the Lectures on Prof. Jochen Seitz & Dipl.-Ing. Karsten Renhak Department of University of Technology Ilmenau October 5, 010 [Jochen.Seitz Karsten.Renhak]@tu-ilmenau.de Contents 1 Communication
key h(key) Hash Indexing Friday, April 09, 2004 Disadvantages of Sequential File Organization Must use an index and/or binary search to locate data
 Lectures Desktop (C) Page 1 Hash Indexing Friday, April 09, 004 11:33 AM Disadvantages of Sequential File Organization Must use an index and/or binary search to locate data File organization based on hashing
Lectures Desktop (C) Page 1 Hash Indexing Friday, April 09, 004 11:33 AM Disadvantages of Sequential File Organization Must use an index and/or binary search to locate data File organization based on hashing
Conges'on. Last Week: Discovery and Rou'ng. Today: Conges'on Control. Distributed Resource Sharing. Conges'on Collapse. Conges'on
 Last Week: Discovery and Rou'ng Provides end-to-end connectivity, but not necessarily good performance Conges'on logical link name Michael Freedman COS 461: Computer Networks Lectures: MW 10-10:50am in
Last Week: Discovery and Rou'ng Provides end-to-end connectivity, but not necessarily good performance Conges'on logical link name Michael Freedman COS 461: Computer Networks Lectures: MW 10-10:50am in
Lecture 3: Modulation & Layering"
 Lecture 3: Modulation & Layering" CSE 123: Computer Networks Alex C. Snoeren HW 1 out Today, due 10/09! Lecture 3 Overview" Encoding schemes Shannon s Law and Nyquist Limit Clock recovery Manchester, NRZ,
Lecture 3: Modulation & Layering" CSE 123: Computer Networks Alex C. Snoeren HW 1 out Today, due 10/09! Lecture 3 Overview" Encoding schemes Shannon s Law and Nyquist Limit Clock recovery Manchester, NRZ,
Computer Engineering II Exercise Sheet Chapter 2
 Distributed Computing FS 019 Prof. R. Wattenhofer Computer Engineering II Exercise Sheet Chapter We categorize questions into four different categories: Quiz Short questions which we will solve rather
Distributed Computing FS 019 Prof. R. Wattenhofer Computer Engineering II Exercise Sheet Chapter We categorize questions into four different categories: Quiz Short questions which we will solve rather
Ananta: Cloud Scale Load Balancing. Nitish Paradkar, Zaina Hamid. EECS 589 Paper Review
 Ananta: Cloud Scale Load Balancing Nitish Paradkar, Zaina Hamid EECS 589 Paper Review 1 Full Reference Patel, P. et al., " Ananta: Cloud Scale Load Balancing," Proc. of ACM SIGCOMM '13, 43(4):207-218,
Ananta: Cloud Scale Load Balancing Nitish Paradkar, Zaina Hamid EECS 589 Paper Review 1 Full Reference Patel, P. et al., " Ananta: Cloud Scale Load Balancing," Proc. of ACM SIGCOMM '13, 43(4):207-218,
Virtualizing Memory: Paging. Announcements
 CS 537 Introduction to Operating Systems UNIVERSITY of WISCONSIN-MADISON Computer Sciences Department Andrea C. Arpaci-Dusseau Remzi H. Arpaci-Dusseau Virtualizing Memory: Paging Questions answered in
CS 537 Introduction to Operating Systems UNIVERSITY of WISCONSIN-MADISON Computer Sciences Department Andrea C. Arpaci-Dusseau Remzi H. Arpaci-Dusseau Virtualizing Memory: Paging Questions answered in
EECS 122, Lecture 19. Reliable Delivery. An Example. Improving over Stop & Wait. Picture of Go-back-n/Sliding Window. Send Window Maintenance
 EECS 122, Lecture 19 Today s Topics: More on Reliable Delivery Round-Trip Timing Flow Control Intro to Congestion Control Kevin Fall, kfall@cs cs.berkeley.eduedu Reliable Delivery Stop and Wait simple
EECS 122, Lecture 19 Today s Topics: More on Reliable Delivery Round-Trip Timing Flow Control Intro to Congestion Control Kevin Fall, kfall@cs cs.berkeley.eduedu Reliable Delivery Stop and Wait simple
416 Distributed Systems. Networks review; Day 1 of 2 Jan 5 + 8, 2018
 416 Distributed Systems Networks review; Day 1 of 2 Jan 5 + 8, 2018 1 Distributed Systems vs. Networks Low level (c/go) Run forever Support others Adversarial environment Distributed & concurrent Resources
416 Distributed Systems Networks review; Day 1 of 2 Jan 5 + 8, 2018 1 Distributed Systems vs. Networks Low level (c/go) Run forever Support others Adversarial environment Distributed & concurrent Resources
CS/MA 109 Fall Wayne Snyder Computer Science Department Boston University
 CS/MA 9 Fall 25 Wayne Snyder Department Boston University Today (Friday the 3 th!): Error-detecting and error-correcting codes. Next week: Cryptography From last time to this time Compression takes advantage
CS/MA 9 Fall 25 Wayne Snyder Department Boston University Today (Friday the 3 th!): Error-detecting and error-correcting codes. Next week: Cryptography From last time to this time Compression takes advantage
CS455: Introduction to Distributed Systems [Spring 2018] Dept. Of Computer Science, Colorado State University
![CS455: Introduction to Distributed Systems [Spring 2018] Dept. Of Computer Science, Colorado State University CS455: Introduction to Distributed Systems [Spring 2018] Dept. Of Computer Science, Colorado State University](/thumbs/77/76273701.jpg) CS 455: INTRODUCTION TO DISTRIBUTED SYSTEMS [NETWORKING] Shrideep Pallickara Computer Science Colorado State University Frequently asked questions from the previous class survey Why not spawn processes
CS 455: INTRODUCTION TO DISTRIBUTED SYSTEMS [NETWORKING] Shrideep Pallickara Computer Science Colorado State University Frequently asked questions from the previous class survey Why not spawn processes
Lecture 16: Border Gateway Protocol
 Lecture 16: Border Gateway Protocol CSE 123: Computer Networks Alex C. Snoeren Some figures courtesy Mike Freedman Lecture 16 Overview Border Gateway Protocol (BGP) The canonical path vector protocol How
Lecture 16: Border Gateway Protocol CSE 123: Computer Networks Alex C. Snoeren Some figures courtesy Mike Freedman Lecture 16 Overview Border Gateway Protocol (BGP) The canonical path vector protocol How
ML from Large Datasets
 10-605 ML from Large Datasets 1 Announcements HW1b is going out today You should now be on autolab have a an account on stoat a locally-administered Hadoop cluster shortly receive a coupon for Amazon Web
10-605 ML from Large Datasets 1 Announcements HW1b is going out today You should now be on autolab have a an account on stoat a locally-administered Hadoop cluster shortly receive a coupon for Amazon Web
I-MINDS USER MANUAL. Download and Install I-MINDS
 I-MINDS USER MANUAL Download and Install I-MINDS Running I-MINDS Download the I-MINDS Student Agent from http://cse.unl.edu/~knobel/i-minds Unzip the downloaded file in your local drive (Your Z: drive
I-MINDS USER MANUAL Download and Install I-MINDS Running I-MINDS Download the I-MINDS Student Agent from http://cse.unl.edu/~knobel/i-minds Unzip the downloaded file in your local drive (Your Z: drive
CSC 4900 Computer Networks: End-to-End Design
 CSC 4900 Computer Networks: End-to-End Design Professor Henry Carter Fall 2017 Villanova University Department of Computing Sciences Review In the last two lectures, we discussed the fundamentals of networking
CSC 4900 Computer Networks: End-to-End Design Professor Henry Carter Fall 2017 Villanova University Department of Computing Sciences Review In the last two lectures, we discussed the fundamentals of networking
Lecture 15 Networking Fundamentals. Today s Plan
 Lecture 15 Networking Fundamentals Slides attributed to Neil Spring Today s Plan Talk about networking in general Layers, Routing Specifically about IP and TCP Service model, what TCP provides Work our
Lecture 15 Networking Fundamentals Slides attributed to Neil Spring Today s Plan Talk about networking in general Layers, Routing Specifically about IP and TCP Service model, what TCP provides Work our
ECE232: Hardware Organization and Design
 ECE232: Hardware Organization and Design Lecture 23: Associative Caches Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Overview Last time: Direct mapped cache Pretty simple to
ECE232: Hardware Organization and Design Lecture 23: Associative Caches Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Overview Last time: Direct mapped cache Pretty simple to
Paging algorithms. CS 241 February 10, Copyright : University of Illinois CS 241 Staff 1
 Paging algorithms CS 241 February 10, 2012 Copyright : University of Illinois CS 241 Staff 1 Announcements MP2 due Tuesday Fabulous Prizes Wednesday! 2 Paging On heavily-loaded systems, memory can fill
Paging algorithms CS 241 February 10, 2012 Copyright : University of Illinois CS 241 Staff 1 Announcements MP2 due Tuesday Fabulous Prizes Wednesday! 2 Paging On heavily-loaded systems, memory can fill
Architectural Principles
 Architectural Principles Brighten Godfrey CS 538 January 29 2018 slides 2010-2017 by Brighten Godfrey unless otherwise noted Cerf and Kahn: TCP/IP Clark: TCP / IP design philosophy Goals of the architecture
Architectural Principles Brighten Godfrey CS 538 January 29 2018 slides 2010-2017 by Brighten Godfrey unless otherwise noted Cerf and Kahn: TCP/IP Clark: TCP / IP design philosophy Goals of the architecture
Peer-To-Peer Network!
 Computer Networks! Introduction. I've been asked to create a PowerPoint on two different kinds of computer networks to be able to discuss the strengths and weaknesses of both. In this PowerPoint I will
Computer Networks! Introduction. I've been asked to create a PowerPoint on two different kinds of computer networks to be able to discuss the strengths and weaknesses of both. In this PowerPoint I will
CS419: Computer Networks. Lecture 10, Part 3: Apr 13, 2005 Transport: TCP performance
 : Computer Networks Lecture 10, Part 3: Apr 13, 2005 Transport: TCP performance TCP performance We ve seen how TCP the protocol works But there are a lot of tricks required to make it work well Indeed,
: Computer Networks Lecture 10, Part 3: Apr 13, 2005 Transport: TCP performance TCP performance We ve seen how TCP the protocol works But there are a lot of tricks required to make it work well Indeed,
PRACTICE QUESTIONS FOR FINAL EXAMINATION Spring 2005
 PRACTICE QUESTIONS FOR 15.561 FINAL EXAMINATION Spring 2005 CLARIFICATION: This is not a practice final but a collection of questions similar to those likely to be on the final. COMPUTER FUNDAMENTALS PRACTICE
PRACTICE QUESTIONS FOR 15.561 FINAL EXAMINATION Spring 2005 CLARIFICATION: This is not a practice final but a collection of questions similar to those likely to be on the final. COMPUTER FUNDAMENTALS PRACTICE
Edge Datacenter Placement BY ABHISHEK GUPTA FRIDAY GROUP MEETING JUNE 10, 2016
 Edge Datacenter Placement BY ABHISHEK GUPTA FRIDAY GROUP MEETING JUNE 10, 2016 Why the need for a Edge Datacenter? For cloud services, performance at the user end is very important. In recent years, the
Edge Datacenter Placement BY ABHISHEK GUPTA FRIDAY GROUP MEETING JUNE 10, 2016 Why the need for a Edge Datacenter? For cloud services, performance at the user end is very important. In recent years, the
CS 640 Introduction to Computer Networks Spring 2009
 CS 640 Introduction to Computer Networks Spring 2009 http://pages.cs.wisc.edu/~suman/courses/wiki/doku.php?id=640-spring2009 Programming Assignment 3: Transmission Control Protocol Assigned: March 26,
CS 640 Introduction to Computer Networks Spring 2009 http://pages.cs.wisc.edu/~suman/courses/wiki/doku.php?id=640-spring2009 Programming Assignment 3: Transmission Control Protocol Assigned: March 26,
Switching Networks (Fall 2010) EE 586 Communication and. August 27, Lecture 2. (modified by Cheung for EE586; based on K&R original) 1-1
 EE 586 Communication and Switching Networks (Fall 2010) Lecture 2 August 27, 2010 (modified by Cheung for EE586; based on K&R original) 1-1 Announcements Read Chapter 1 First homework is due 9/3 In Blackboard
EE 586 Communication and Switching Networks (Fall 2010) Lecture 2 August 27, 2010 (modified by Cheung for EE586; based on K&R original) 1-1 Announcements Read Chapter 1 First homework is due 9/3 In Blackboard
Lecture 1 Introduction (Chapter 1 of Textbook)
 Bilkent University Department of Computer Engineering CS342 Operating Systems Lecture 1 Introduction (Chapter 1 of Textbook) Dr. İbrahim Körpeoğlu http://www.cs.bilkent.edu.tr/~korpe 1 References The slides
Bilkent University Department of Computer Engineering CS342 Operating Systems Lecture 1 Introduction (Chapter 1 of Textbook) Dr. İbrahim Körpeoğlu http://www.cs.bilkent.edu.tr/~korpe 1 References The slides
Introduction to Information Science and Technology 2017 Networking I. Sören Schwertfeger 师泽仁
 I Sören Schwertfeger 师泽仁 Outline Internet History of the Internet Internet Structure Internet Protocols Network layer details 1. Physical Layer 2. Data Link Layer 3. Network Layer Internet: Huge network
I Sören Schwertfeger 师泽仁 Outline Internet History of the Internet Internet Structure Internet Protocols Network layer details 1. Physical Layer 2. Data Link Layer 3. Network Layer Internet: Huge network
Carnegie Mellon Computer Science Department Spring 2015 Midterm Exam
 Carnegie Mellon Computer Science Department. 15-744 Spring 2015 Midterm Exam Name: Andrew ID: INSTRUCTIONS: There are 7 pages (numbered at the bottom). Make sure you have all of them. Please write your
Carnegie Mellon Computer Science Department. 15-744 Spring 2015 Midterm Exam Name: Andrew ID: INSTRUCTIONS: There are 7 pages (numbered at the bottom). Make sure you have all of them. Please write your
Inter-AS routing. Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley
 Inter-AS routing Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley Some materials copyright 1996-2012 J.F Kurose and K.W. Ross, All Rights Reserved Chapter 4:
Inter-AS routing Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley Some materials copyright 1996-2012 J.F Kurose and K.W. Ross, All Rights Reserved Chapter 4:
Architectural Styles II
 Architectural Styles II Software Architecture VO/KU (707.023/707.024) Denis Helic, Roman Kern KMI, TU Graz Nov 21, 2012 Denis Helic, Roman Kern (KMI, TU Graz) Architectural Styles II Nov 21, 2012 1 / 66
Architectural Styles II Software Architecture VO/KU (707.023/707.024) Denis Helic, Roman Kern KMI, TU Graz Nov 21, 2012 Denis Helic, Roman Kern (KMI, TU Graz) Architectural Styles II Nov 21, 2012 1 / 66
Wi-Fi 6 What s It All About?
 WHITE PAPER Wi-Fi 6 What s It All About? By Cees Links, GM of Qorvo Wireless Connectivity Business Unit Formerly Founder & CEO of GreenPeak Technologies Is Wi-Fi Running Out of Steam? Despite that nobody
WHITE PAPER Wi-Fi 6 What s It All About? By Cees Links, GM of Qorvo Wireless Connectivity Business Unit Formerly Founder & CEO of GreenPeak Technologies Is Wi-Fi Running Out of Steam? Despite that nobody
