Application Guide - Layer3 Systems Limited. FTP Poller. Application Guide. Version 3.4 January FTP Poller Applications
|
|
|
- Suzanna Craig
- 6 years ago
- Views:
Transcription
1 Application Guide Version 3.4 January 2016 Applications Application Guide - Copyright Layer3 Systems Limited 2016
2 Introduction The was created by Layer3 Systems to provide support for the movement of files between broadcasters. had long been the standard means of moving files between co-operating broadcasting companies. The provides an automated, extensible system that securely and reliably transfers files capable of running 24 hours per day 7 days per week. It can be provided as a fully managed service to minimise work load on your staff. / Automated The is designed to solve the problem of automatically transferring files, repeatedly, reliably and securely between systems and networks owned by independent companies. Centralised Operation Reduces staff workload Audit Trail Runs 24 hour everyday Simplifies file transfer Managed service (push) (pull) Expecting staff, no matter how diligent or expert they may be, to repeatedly transfer files quickly becomes unworkable. In a busy environment people may forget to carry out the work and may fail to keep proper logs of their activity. For a business environment where file transfer is part of the organisation s critical operation, highly reliable, automated, secure file transfer with a proper audit trail of activity is a crucial feature. Extensible Part of the design concept for the is to provide a means to interface with your existing systems. We achieve a good degree of extensibility by using pre-transfer and post-transfer hooks. This gives the ability to integrate the into your workflow so that it beomes an active part of your overall system, helping to automate and simplify operation. Pre-Transfer-Hook: Prior to a transfer starting some activity can be initiated Post-Transfer-Hook: After the file has been transferred some completion activity can be executed Transfer Applications Application Guide - Copyright Layer3 Systems Limited 2016 Page 1 of 7
3 Secure The enhances security by taking away from the ordinary user the need to access remote systems. Logins and passwords are centralised and remain under the control of IT staff. Thus login and password ID s need not be administered for the user, the user does not have yet more logins to manage and they are not vulnerable to having a login identity stolen. /S/S options for transfer. login details remains with IT. Reduces managing logins and accounts. (push/pull) Single point of control and management. Single point providing auditing and logging of all activity. Reduces () tools that allow data leakage The can work from within the users internal network or more securely from within a DMZ, depending on the degree of security required. If located within the users network, then a simple file share can be setup to give users access to folders where files may be dropped off for delivery or picked up once they have come in from remote hosts. If located within a DMZ the can be used to pass files back into the internal network onto a standard server where users may access a shared directory structure from their workstations. can be configured to use or the more secure variants S and S, these versions of the protocol further secure transfers by ensuring that file transfer is fully encrypted. Reliable The reliably moves files, generating an audit trail and detailed transfer logs. The system is designed to run continuously, checking regularly to see if there are any files to transfer. The system does not take breaks or go on holiday, so it can be relied upon to be there working all the time. It is implemented as a separate system, so it is not prone to upgrades from other software causing problems. It is inaccessible to the average user, so cannot get reconfigured accidentally. The is designed and implemented in house by our own experienced engineers that understand networks and file transfer. Cluster Designed and built specifically for file transfer Very robust extensively run mature software Secure operation from your network or DMZ Mon1 Single system or clustered options. Continuous operation 24x7x365 Mon2 (push/pull) Automated remote management centres It is "Transactional" in that it guarantees that a file will arrive intact or an error message will explain any fault. A great deal of the power of the software is that it can cope with the many complex faults that transferring files can throw up, providing clear diagnostics that save time and money in resolving problems. Our support and managed services allows us to monitor for problems and rapidly resolve them before they become a major concern. The system can be clustered so that there are multiple s running, if one system fails then the other system picks up seamlessly. This removes extended down time and allows repairs to take place reducing costly disruption. Our software has been running since 1995 in some highly demanding environments. Our highly resilient (High Availability) version runs on multiple hardware and provides continued operation in the face of hardware failure. Applications Application Guide - Copyright Layer3 Systems Limited 2016 Page 2 of 7
4 Managed One of the benefits of the way that the works is that the device can be supported as a fully managed service. Layer3 Systems Limited provides a complete one stop solution in design, integration and on going support that reduces the workload on your company minimises total cost of ownership. Our support service uses a state of the art multi data centre support system, allowing us to remotely and securely manage an. Fully managed design and support service One stop solution from design through operation Cluster Mon1 Mon2 (push/pull) Secure multi data centre support system Continuous 24x7 system monitoring and management Support for third party problem rectification We provide continuous 24 hour support and monitoring for your, often detecting problems on third party networks and resolving issues long before many IT departments are able to focus on a problem. Very often the biggest challenge in handling user driven is that any fault will always appear to be the local system or network. Users are not always able to determine if a fault is related to the Internet or a remote system and so invariably are forced to ask the IT department for help. The and our managed service take these problems away from your IT department, this saves your company time and money. Designed for the Internet The is designed to connect to servers that are part of your network, such as remote sites, or remote servers that belong to your clients, partners, or customers. Because it uses standard protocol it will work with any server anywhere on the Internet. The modular design of the allows us to support S and S. This enables mixed mode transfers where one leg of the transfer might use S and another leg could use S. It can be securely implemented over VPN s via the Internet. Giving a completely secure inter company site transfer capability. It is designed to reach out of your secure network and deliver or retrieve files, this model matches exactly what an ordinary user does when they use the Internet, so it should require no special changes to your firewall. Designed to Scale The does not have a graphical front end nor does it have a large per user license issue. Its written in a light weight language and designed to run as efficiently on a relatively small Linux based server/appliance as on a full cluster. It will handle the transfer of thousands of files per day and run continuously without human intervention for months. With the addition of an server built into the server, the system can become one of many identical nodes located at multiple sites or offices. This gives the ability to easily implement automatic file transfer between remote sites. Reliable and Robust Software The software was designed to run in a networked environment and was written in PERL, principally for use on a Unix or Linux based system. The combination of these elements give us a reliable system that will continue to operate reliably without intervention for months or sometimes years on end. Applications Application Guide - Copyright Layer3 Systems Limited 2016 Page 3 of 7
5 Operation The can provide the automated means to transfer files in a number of ways. From the internal file server via the local to a remote server (push). From a remote server to the local (pull) into the internal file server. Or from one remote server to another remote server (server to server). Whilst we describe transfers using the default protocol, each transfer may be implemented using S or S to further increase security through encryption. For the ultimate in non stop operation and High Availability, the can be implemented as a cluster. An can be configured to carry out a mixture of push, pull or server to server transfers as required. s work on file names, recognising files within a given directory that need to be transferred. Multiple pollers can operate at the same time on the same server, this can be used to implement a frequent service for small files and possibly a less frequent service for bigger files. / Diagnostics and an audit trail are produced per transfer - error and success messages can be ed out to designated groups. Local to Files are transferred from the local server to the destination server., S or S / In this scenario a user on a workstation drops a completed file onto a share directory on an internal server. The checks for the presence of a file at regular timed intervals, for example every 10 minutes. Once a file is detected the connects out from your network via the firewall or router and delivers the file onto a remote server. Applications Application Guide - Copyright Layer3 Systems Limited 2016 Page 4 of 7
6 to local Files are transferred from the remote source server to the local internal server., S or S / The connects to the remote server and checks for the presence of a file at regular timed intervals, for example every 10 minutes. Once a file is detected the gets the file and copies it onto a local share on the internal system, making it available for a user on a workstation. to Files are transferred from the source remote server to the destination remote server, S or S Files are picked up from the source server, held temporarily on the local server and then forwarded to the destination server. This provides a very simple way to mirror the contents of directories or to update multiple servers with latest copies of files. Applications Application Guide - Copyright Layer3 Systems Limited 2016 Page 5 of 7
7 Network Security The can be implemented within a network in a number of ways. This section considers the benefits of the two most common ways to implement inside a network; the Model and the DMZ Model. In its simplest ( Model) form it can be connected into the internal network like any other file server. This is fine for operation where you wish to transfer files out of the network to remote servers, and similarly picking up files from remote systems will work perfectly well. It would be secured from the outside by your firewall. However to increase security, and reduce attack from your internal network, it is worthwhile locating the into a DMZ. This then also makes it possible to give external access to the, allowing it to run an server so your customers can directly pick up files from you. (Ideally with an.) Model In this example the sits inside the user network. It uses the internal file server as a source and destination for files, it can then reach out to access and transfer files to and from remote sites. The initiates and controls all transfers, either pushing files out or pulling files in, external systems cannot access the. This is the same as how a normal user accesses the Internet from within your network, and is therefore just as secure - no service is exposed to the outside world and therefore no unauthorised access can take place. This can be inflexible though. If there are multiple co-operating sites and none have a DMZ then there would be no way for any site to safely access any other. This can be resolved by having a centralised Internet based server acting as a hub. File / DMZ Model In this example the sits in the DMZ. The can push or pull files onto or from remote servers in the usual way. The poller also accesses the internal file server inside the network as a place to pick up and drop off files locally. Users on the inside network simply access the local server to drop off or pick up files. This gives a high degree of flexibility with a reasonable amount of security. The firewall ensures that the in the DMZ can only access the service on the internal server. + File DMZ Applications / This model gives the added benefit that the can also act as an server. This makes it possible for other s on remote sites (or any other client) to access files available from this site. The provides the service of moving files between the internal network server and the public facing DMZ based /. This maintains good security but enhances flexibility and cooperative working with other companies. Application Guide - Copyright Layer3 Systems Limited 2016 Page 6 of 7
8 Enterprise Design The can be scaled to provide enterprise level solutions that can support world wide activity. The system can be relied upon to disseminate files as part of global workflow, enabling systems and colleagues around the world to focus on carrying out useful work instead of distributing files. The key to the systems flexibility is its simplicity, anywhere you have an accessible routed network an can deliver files. So it doesn t matter if you use a worldwide MPLS cloud, leased lines, or VPN over the Internet, the can move files between you sites with no extra specialised configuration on your networks or firewalls. Europe Headquarters Cluster DMZ America Headquarters Cluster DMZ Regional Offices 1 Regional Offices 2 Asia Headquarters DMZ Cluster The example shown draws on our experience of building global systems. In this case files originating in any one national headquarters would automatically be disseminated across to other national centres and down to regional offices. Reports originating in regional offices would be copied back up the tree to international headquarters. More Information If you would like more details of the or would like to discuss arranging a demonstration please contact us on: Layer3 Systems Limited 43 Pendle Road Streatham London SW16 6RT Applications Application Guide - Copyright Layer3 Systems Limited 2016 Page 7 of 7
Managed Services Rely on us to manage your business services
 Managed Services Rely on us to manage your business services Your business relies on a number of interconnected systems used by different departments from HR, Marketing, Sales and IT. Keeping all these
Managed Services Rely on us to manage your business services Your business relies on a number of interconnected systems used by different departments from HR, Marketing, Sales and IT. Keeping all these
MOBILE LIVE SHARE SMS FAX
 EMAIL messagehub email provides you with the edge in communications that will help to keep your business ahead of the game. Based on Microsoft Exchange Server 2003, messagehub is a totally reliable service
EMAIL messagehub email provides you with the edge in communications that will help to keep your business ahead of the game. Based on Microsoft Exchange Server 2003, messagehub is a totally reliable service
File Transfer and the GDPR
 General Data Protection Regulation Article 32 (2): In assessing the appropriate level of security account shall be taken in particular of the risks that are presented by processing, in particular from
General Data Protection Regulation Article 32 (2): In assessing the appropriate level of security account shall be taken in particular of the risks that are presented by processing, in particular from
NetPro. from Wireless Logic. Available on a per SIM license basis. No CAPEX. Retain your Airtime Contracts with your existing providers
 NetPro from Available on a per SIM license basis Real-time usage monitoring of Data SIMs Retain your Airtime Contracts with your existing providers No CAPEX Secure and resilient connectivity via VPN Be
NetPro from Available on a per SIM license basis Real-time usage monitoring of Data SIMs Retain your Airtime Contracts with your existing providers No CAPEX Secure and resilient connectivity via VPN Be
A practical guide to IT security
 Data protection A practical guide to IT security Ideal for the small business The Data Protection Act states that appropriate technical and organisational measures shall be taken against unauthorised or
Data protection A practical guide to IT security Ideal for the small business The Data Protection Act states that appropriate technical and organisational measures shall be taken against unauthorised or
Agent vs Agentless Log Collection
 Agent vs Agentless Log Collection Intersect Alliance International Pty Ltd. All rights reserved worldwide. Intersect Alliance Pty Ltd shall not be liable for errors contained herein or for direct, or indirect
Agent vs Agentless Log Collection Intersect Alliance International Pty Ltd. All rights reserved worldwide. Intersect Alliance Pty Ltd shall not be liable for errors contained herein or for direct, or indirect
SIP trunks with Microsoft Skype For Business
 Phone systems and services with Microsoft Skype For Business A cost effective alternative to ISDN that provides flexibility and continuity for your business Reliable voice services What is SIP? SIP trunking
Phone systems and services with Microsoft Skype For Business A cost effective alternative to ISDN that provides flexibility and continuity for your business Reliable voice services What is SIP? SIP trunking
Streamline IT with Secure Remote Connection and Password Management
 Streamline IT with Secure Remote Connection and Password Management Table of Contents Introduction Identifying IT pain points Selecting a secure remote connection and password management solution Turning
Streamline IT with Secure Remote Connection and Password Management Table of Contents Introduction Identifying IT pain points Selecting a secure remote connection and password management solution Turning
Developing a Network:
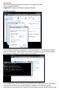 Developing a Network: This is setting up IP addresses in properties in Local Area Connection in the Network and Sharing Centre in Control Panel. I deselected all of the networks checkboxes accept the TCP/IP4
Developing a Network: This is setting up IP addresses in properties in Local Area Connection in the Network and Sharing Centre in Control Panel. I deselected all of the networks checkboxes accept the TCP/IP4
Automated Firewall Change Management Securing change management workflow to ensure continuous compliance and reduce risk
 Automated Firewall Change Management Securing change management workflow to ensure continuous compliance and reduce risk Skybox Security Whitepaper January 2015 Executive Summary Firewall management has
Automated Firewall Change Management Securing change management workflow to ensure continuous compliance and reduce risk Skybox Security Whitepaper January 2015 Executive Summary Firewall management has
Choose an internet connection to suit your business
 Choose an internet connection to suit your business With an ever increasing demand for bandwidth, your internet connection has never been so important to your business. Whether you re a small business
Choose an internet connection to suit your business With an ever increasing demand for bandwidth, your internet connection has never been so important to your business. Whether you re a small business
Bring more control and added efficiency to your scanning and print environment
 Bring more control and added efficiency to your scanning and print environment Incorporating into your processes will lead to real improvements in the control and efficiency of multifunctional devices.
Bring more control and added efficiency to your scanning and print environment Incorporating into your processes will lead to real improvements in the control and efficiency of multifunctional devices.
Real-time Communications Security and SDN
 Real-time Communications Security and SDN 2016 [Type here] Securing the new generation of communications applications, those delivering real-time services including voice, video and Instant Messaging,
Real-time Communications Security and SDN 2016 [Type here] Securing the new generation of communications applications, those delivering real-time services including voice, video and Instant Messaging,
Completing your AWS Cloud SECURING YOUR AMAZON WEB SERVICES ENVIRONMENT
 Completing your AWS Cloud SECURING YOUR AMAZON WEB SERVICES ENVIRONMENT Introduction Amazon Web Services (AWS) provides Infrastructure as a Service (IaaS) cloud offerings for organizations. Using AWS,
Completing your AWS Cloud SECURING YOUR AMAZON WEB SERVICES ENVIRONMENT Introduction Amazon Web Services (AWS) provides Infrastructure as a Service (IaaS) cloud offerings for organizations. Using AWS,
SIP TRUNKING THE COST EFFECTIVE AND FLEXIBLE ALTERNATIVE TO ISDN
 SIP TRUNKING THE COST EFFECTIVE AND FLEXIBLE ALTERNATIVE TO ISDN A cost-effective alternative to ISDN that provides flexibility and continuity Reliable voice services SIP trunking is the fastest-growing
SIP TRUNKING THE COST EFFECTIVE AND FLEXIBLE ALTERNATIVE TO ISDN A cost-effective alternative to ISDN that provides flexibility and continuity Reliable voice services SIP trunking is the fastest-growing
DEPLOYMENT WHITE PAPER.
 DEPLOYMENT WHITE PAPER www.seavusprojectviewer.com Deployment Options Seavus Project Viewer provides a wide variety of deployment options: Single User installation is a stand-alone, web downloadable configuration
DEPLOYMENT WHITE PAPER www.seavusprojectviewer.com Deployment Options Seavus Project Viewer provides a wide variety of deployment options: Single User installation is a stand-alone, web downloadable configuration
What Dropbox Can t Do For Your Business
 What Dropbox Can t Do For Your Business 33 Things to Consider When Choosing a Secure File Sharing and Collaboration Service for Your Business A Soonr White Paper Executive Summary The need for a well-rounded
What Dropbox Can t Do For Your Business 33 Things to Consider When Choosing a Secure File Sharing and Collaboration Service for Your Business A Soonr White Paper Executive Summary The need for a well-rounded
FILE REPLICATION AND COLLABORATION REQUIREMENT: THE ESSENTIALS
 101001010111011011010001010110111010101100101001010111011011010001010110111010101100101001010111011 101001010111011011010001010110111010101100101001010111011011010001010110111010101100101001010111011 101001010111011011010001010110111010101100101001010111011011010001010110111010101100101001010111011
101001010111011011010001010110111010101100101001010111011011010001010110111010101100101001010111011 101001010111011011010001010110111010101100101001010111011011010001010110111010101100101001010111011 101001010111011011010001010110111010101100101001010111011011010001010110111010101100101001010111011
Network Security Policy
 Network Security Policy Date: January 2016 Policy Title Network Security Policy Policy Number: POL 030 Version 3.0 Policy Sponsor Policy Owner Committee Director of Business Support Head of ICU / ICT Business
Network Security Policy Date: January 2016 Policy Title Network Security Policy Policy Number: POL 030 Version 3.0 Policy Sponsor Policy Owner Committee Director of Business Support Head of ICU / ICT Business
Transforming your network for the digital economy
 Transforming your network for the digital economy Ricky Chau, Vice President, Enterprise, CenturyLink Asia Pacific 15/11/2018 Services not available everywhere. 2 We re in an Era of Digital Transformation
Transforming your network for the digital economy Ricky Chau, Vice President, Enterprise, CenturyLink Asia Pacific 15/11/2018 Services not available everywhere. 2 We re in an Era of Digital Transformation
NFV and SDN what does it mean to enterprises?
 OPINION NFV and SDN what does it mean to enterprises? By Clive Hamilton, VP Network Services, NTT Europe Rethinking the enterprise network The typical enterprise network now comprises hundreds or even
OPINION NFV and SDN what does it mean to enterprises? By Clive Hamilton, VP Network Services, NTT Europe Rethinking the enterprise network The typical enterprise network now comprises hundreds or even
Secure Remote Access And Password Management
 +44(0)1425 270 333 email: sales@dtrack.com website: dtt.dtrack.com Secure Remote Access And Password Management Data Track Technolo gy Ltd 153 Somerford Road Christchurch Dorset BH23 3TY UK Contents The
+44(0)1425 270 333 email: sales@dtrack.com website: dtt.dtrack.com Secure Remote Access And Password Management Data Track Technolo gy Ltd 153 Somerford Road Christchurch Dorset BH23 3TY UK Contents The
ESSENTIAL, QUALITY IT SUPPORT FOR SMALL AND MEDIUM BUSINESSES
 ESSENTIAL, QUALITY IT SUPPORT FOR SMALL AND MEDIUM BUSINESSES YOUR OWN IT DEPARTMENT AT A FRACTION OF THE COST// Hand over the day-to-day management and responsibility of your IT so you can focus on what
ESSENTIAL, QUALITY IT SUPPORT FOR SMALL AND MEDIUM BUSINESSES YOUR OWN IT DEPARTMENT AT A FRACTION OF THE COST// Hand over the day-to-day management and responsibility of your IT so you can focus on what
Module 11 Technical Troubleshooting for Restaurant Managers
 Module 11 Technical Troubleshooting for Restaurant Managers Overview This module is about troubleshooting at an introductory level and to help you gain confidence and knowledge to problem-solve Pilot POS
Module 11 Technical Troubleshooting for Restaurant Managers Overview This module is about troubleshooting at an introductory level and to help you gain confidence and knowledge to problem-solve Pilot POS
Security-as-a-Service: The Future of Security Management
 Security-as-a-Service: The Future of Security Management EVERY SINGLE ATTACK THAT AN ORGANISATION EXPERIENCES IS EITHER ON AN ENDPOINT OR HEADING THERE 65% of CEOs say their risk management approach is
Security-as-a-Service: The Future of Security Management EVERY SINGLE ATTACK THAT AN ORGANISATION EXPERIENCES IS EITHER ON AN ENDPOINT OR HEADING THERE 65% of CEOs say their risk management approach is
SECURE DATA EXCHANGE
 POLICY-DRIVEN SOLUTIONS FOR SECURE DATA EXCHANGE Sending and receiving data is a fundamental part of daily business for nearly every organization. Companies need to share financial transaction details,
POLICY-DRIVEN SOLUTIONS FOR SECURE DATA EXCHANGE Sending and receiving data is a fundamental part of daily business for nearly every organization. Companies need to share financial transaction details,
Data Security at Smart Assessor
 Data Security at Smart Assessor Page 1 Contents Data Security...3 Hardware...3 Software...4 Data Backups...4 Personnel...5 Web Application Security...5 Encryption of web application traffic...5 User authentication...5
Data Security at Smart Assessor Page 1 Contents Data Security...3 Hardware...3 Software...4 Data Backups...4 Personnel...5 Web Application Security...5 Encryption of web application traffic...5 User authentication...5
A complete communications service for your business
 A complete communications service for your business Easily control your fixed and mobile telephony WHAT IS HORIZON? Horizon is a complete communications service for business that provides an extensive
A complete communications service for your business Easily control your fixed and mobile telephony WHAT IS HORIZON? Horizon is a complete communications service for business that provides an extensive
KERIO TECHNOLOGIES KERIO WINROUTE FIREWALL 6.3 REVIEWER S GUIDE
 KERIO TECHNOLOGIES KERIO WINROUTE FIREWALL 6.3 REVIEWER S GUIDE (4/20/07) WHO IS KERIO? Kerio Technologies provides Internet messaging and firewall software solutions for small to medium sized networks,
KERIO TECHNOLOGIES KERIO WINROUTE FIREWALL 6.3 REVIEWER S GUIDE (4/20/07) WHO IS KERIO? Kerio Technologies provides Internet messaging and firewall software solutions for small to medium sized networks,
X.25 Substitution. Maintaining X.25 services over a fully supported NGN/IP infrastructure. The Challenge. How it Works. Solution
 Substitution Maintaining services over a fully supported NGN/ infrastructure The Challenge Legacy services such as are still in use worldwide for a range of applications. Over the years, many customers
Substitution Maintaining services over a fully supported NGN/ infrastructure The Challenge Legacy services such as are still in use worldwide for a range of applications. Over the years, many customers
Remote Connection to Your Computers
 Remote Connection to Your Computers Page 1 Accessing files while you re on the go When you are at home or in the office, your ipad or iphone connects to your network wirelessly. And because it is part
Remote Connection to Your Computers Page 1 Accessing files while you re on the go When you are at home or in the office, your ipad or iphone connects to your network wirelessly. And because it is part
Guide. A small business guide to data storage and backup
 Guide A small business guide to data storage and backup 0345 600 3936 www.sfbcornwall.co.uk Contents Introduction... 3 Why is data storage and backup important?... 4 Benefits of cloud storage technology...
Guide A small business guide to data storage and backup 0345 600 3936 www.sfbcornwall.co.uk Contents Introduction... 3 Why is data storage and backup important?... 4 Benefits of cloud storage technology...
ServiceWorks ServiceWorks: Cloud Services from CDW
 ServiceWorks: Cloud Services from CDW 1 UK.CDW.COM 020.7791.6000 CDW: ServiceWorks ServiceWorks: Cloud Services from CDW Not cloud but real IT The economies the cloud represents are compelling: predictable
ServiceWorks: Cloud Services from CDW 1 UK.CDW.COM 020.7791.6000 CDW: ServiceWorks ServiceWorks: Cloud Services from CDW Not cloud but real IT The economies the cloud represents are compelling: predictable
Backup and Recovery. Backup and Recovery from Redstor. Making downtime a thing of the past Making downtime a thing of the past
 Backup and Recovery Backup and Recovery Backup from Redstor and Recovery from Redstor Making downtime a thing of the past Making downtime a thing of the past Reject risk Preventing data loss is a challenge
Backup and Recovery Backup and Recovery Backup from Redstor and Recovery from Redstor Making downtime a thing of the past Making downtime a thing of the past Reject risk Preventing data loss is a challenge
One platform for scanning, printing and copying management
 One platform for scanning, printing and copying management Bring more control and added efficiency to your scanning and print environment Incorporating into your processes will lead to real improvements
One platform for scanning, printing and copying management Bring more control and added efficiency to your scanning and print environment Incorporating into your processes will lead to real improvements
Data Aggregation for Asset Reconciliation
 INTRODUCTION This paper focuses on data consolidation for asset reconciliation within hedge funds and long only asset managers. The process requires aggregation of data from a number of external sources
INTRODUCTION This paper focuses on data consolidation for asset reconciliation within hedge funds and long only asset managers. The process requires aggregation of data from a number of external sources
Why Use Cisco Network Storage Systems for Your Business
 Why Use Cisco Network Storage Systems for Your Business Introduction This white paper highlights two new additions to the Cisco Small Business Network Storage System (NSS) line of products. The Cisco NSS2000
Why Use Cisco Network Storage Systems for Your Business Introduction This white paper highlights two new additions to the Cisco Small Business Network Storage System (NSS) line of products. The Cisco NSS2000
A Cloud WHERE PHYSICAL ARE TOGETHER AT LAST
 A Cloud WHERE PHYSICAL AND VIRTUAL STORAGE ARE TOGETHER AT LAST Not all Cloud solutions are the same so how do you know which one is right for your business now and in the future? NTT Communications ICT
A Cloud WHERE PHYSICAL AND VIRTUAL STORAGE ARE TOGETHER AT LAST Not all Cloud solutions are the same so how do you know which one is right for your business now and in the future? NTT Communications ICT
SAFECOM SECUREWEB - CUSTOM PRODUCT SPECIFICATION 1. INTRODUCTION 2. SERVICE DEFINITION. 2.1 Service Overview. 2.2 Standard Service Features APPENDIX 2
 APPENDIX 2 SAFECOM SECUREWEB - CUSTOM PRODUCT SPECIFICATION 1. INTRODUCTION This document contains product information for the Safecom SecureWeb Custom service. If you require more detailed technical information,
APPENDIX 2 SAFECOM SECUREWEB - CUSTOM PRODUCT SPECIFICATION 1. INTRODUCTION This document contains product information for the Safecom SecureWeb Custom service. If you require more detailed technical information,
SECURING YOUR BUSINESS INFRASTRUCTURE Today s Security Challenges & What You Can Do About Them
 BROTHER SECURITY WHITE PAPER NOVEMBER 2017 SECURING YOUR BUSINESS INFRASTRUCTURE Today s Security Challenges & What You Can Do About Them The last decade has seen many exciting advances in connectivity
BROTHER SECURITY WHITE PAPER NOVEMBER 2017 SECURING YOUR BUSINESS INFRASTRUCTURE Today s Security Challenges & What You Can Do About Them The last decade has seen many exciting advances in connectivity
7 Keys to Comparing Google Apps Premier Edition with Microsoft Exchange Server 2003/2007
 7 Keys to Comparing with Microsoft Exchange Server 2003/2007 Partner Guide Introduction is Google s Software as a Service (SaaS) solution for business messaging, collaboration, and security. It includes
7 Keys to Comparing with Microsoft Exchange Server 2003/2007 Partner Guide Introduction is Google s Software as a Service (SaaS) solution for business messaging, collaboration, and security. It includes
SpeechLive. Cloud dictation solution. Speak. Send. Done. You speak, we do the typing for you
 SpeechLive Cloud dictation solution Speak. Send. Done. You speak, we do the typing for you Overivew Your personal assistant in the cloud SpeechLive benefits Philips SpeechLive is the ultimate cloud dictation
SpeechLive Cloud dictation solution Speak. Send. Done. You speak, we do the typing for you Overivew Your personal assistant in the cloud SpeechLive benefits Philips SpeechLive is the ultimate cloud dictation
The Problem with Privileged Users
 Flash Point Paper Enforce Access Control The Problem with Privileged Users Four Steps to Reducing Breach Risk: What You Don t Know CAN Hurt You Today s users need easy anytime, anywhere access to information
Flash Point Paper Enforce Access Control The Problem with Privileged Users Four Steps to Reducing Breach Risk: What You Don t Know CAN Hurt You Today s users need easy anytime, anywhere access to information
MANAGING THE COMPLEXITY.
 AS A SERVICE MANAGING THE COMPLEXITY. HOW WILL YOU SIMPLIFY ESN MIGRATION? Control room IT solutions play a vital role in incident management. Technologies such as Integrated Communications Control Systems
AS A SERVICE MANAGING THE COMPLEXITY. HOW WILL YOU SIMPLIFY ESN MIGRATION? Control room IT solutions play a vital role in incident management. Technologies such as Integrated Communications Control Systems
ITSM SERVICES. Delivering Technology Solutions With Passion
 ITSM SERVICES Delivering Technology Solutions With Passion 02 CONTENTS OVERVIEW CLIENTS SOLUTIONS WHAT WE DO PROFESSIONAL SERVICES Overview IT Pillars is a dynamic company, which has served, over the past
ITSM SERVICES Delivering Technology Solutions With Passion 02 CONTENTS OVERVIEW CLIENTS SOLUTIONS WHAT WE DO PROFESSIONAL SERVICES Overview IT Pillars is a dynamic company, which has served, over the past
Security Awareness Training Courses
 Security Awareness Training Courses Trusted Advisor for All Your Information Security Needs ZERODAYLAB Security Awareness Training Courses 75% of large organisations were subject to a staff-related security
Security Awareness Training Courses Trusted Advisor for All Your Information Security Needs ZERODAYLAB Security Awareness Training Courses 75% of large organisations were subject to a staff-related security
ON SCHEDULE TERMS AND CONDITIONS (September 23rd 2018)
 By using On Schedule web application you are making an agreement with us, code fish, according to the current terms and conditions at the time of use. Upon the terms and conditions changing you will be
By using On Schedule web application you are making an agreement with us, code fish, according to the current terms and conditions at the time of use. Upon the terms and conditions changing you will be
Microsoft SQL Server on Stratus ftserver Systems
 W H I T E P A P E R Microsoft SQL Server on Stratus ftserver Systems Security, scalability and reliability at its best Uptime that approaches six nines Significant cost savings for your business Only from
W H I T E P A P E R Microsoft SQL Server on Stratus ftserver Systems Security, scalability and reliability at its best Uptime that approaches six nines Significant cost savings for your business Only from
Security Overview. Technical Whitepaper. Secure by design. End to end security. N-tier Application Architecture. Data encryption. User authentication
 Technical Whitepaper Security Overview As a team, we have a long history of developing and delivering HR software solutions to customers worldwide, including many of the world s most-demanding organisations.
Technical Whitepaper Security Overview As a team, we have a long history of developing and delivering HR software solutions to customers worldwide, including many of the world s most-demanding organisations.
Productivity starts with simplicity /This is Why we re making our MFPs easier to manage.
 Sharp Remote Device Manager SIMPLE, CENTRALISED MONITORING AND MANAGEMENT Productivity starts with simplicity /This is Why we re making our MFPs easier to manage. Optimise your device management We know
Sharp Remote Device Manager SIMPLE, CENTRALISED MONITORING AND MANAGEMENT Productivity starts with simplicity /This is Why we re making our MFPs easier to manage. Optimise your device management We know
A complete communications service for your business
 A complete communications service for your business Easily control your fixed and mobile telephony WHAT IS HORIZON? Horizon is a complete communications service for business that provides an extensive
A complete communications service for your business Easily control your fixed and mobile telephony WHAT IS HORIZON? Horizon is a complete communications service for business that provides an extensive
XenApp, XenDesktop and XenMobile Integration
 XA, XD and XM Integration XenApp, XenDesktop and XenMobile Integration for a Comprehensive Mobility and Digital Workspace Solution Citrix.com 1 Desktop and application virtualization have enhanced mobility
XA, XD and XM Integration XenApp, XenDesktop and XenMobile Integration for a Comprehensive Mobility and Digital Workspace Solution Citrix.com 1 Desktop and application virtualization have enhanced mobility
Buy don t Build. Use don t Manage.
 I N N O VAT E & O P E R AT E B E T T E R, FA S T E R RAPID Private Cloud Systems provide your business with a pre integrated, validated and tested private cloud delivered in 28 days, to any location, ready
I N N O VAT E & O P E R AT E B E T T E R, FA S T E R RAPID Private Cloud Systems provide your business with a pre integrated, validated and tested private cloud delivered in 28 days, to any location, ready
NEW DATA REGULATIONS: IS YOUR BUSINESS COMPLIANT?
 NEW DATA REGULATIONS: IS YOUR BUSINESS COMPLIANT? What the new data regulations mean for your business, and how Brennan IT and Microsoft 365 can help. THE REGULATIONS: WHAT YOU NEED TO KNOW Australia:
NEW DATA REGULATIONS: IS YOUR BUSINESS COMPLIANT? What the new data regulations mean for your business, and how Brennan IT and Microsoft 365 can help. THE REGULATIONS: WHAT YOU NEED TO KNOW Australia:
Integrating Password Management with Enterprise Single Sign-On
 Integrating Password Management with Enterprise Single Sign-On 2016 Hitachi ID Systems, Inc. All rights reserved. Contents 1 Introduction 1 2 Background: one problem, two solutions 2 2.1 The Problem.............................................
Integrating Password Management with Enterprise Single Sign-On 2016 Hitachi ID Systems, Inc. All rights reserved. Contents 1 Introduction 1 2 Background: one problem, two solutions 2 2.1 The Problem.............................................
FDS manual File Delivery Services SFTP and FTP file transfer
 FDS manual File Delivery Services SFTP and FTP file transfer Publisher Post CH Ltd Information Technology Webergutstrasse 12 CH-3030 Berne (Zollikofen) Contact Post CH Ltd Information Technology Webergutstrasse
FDS manual File Delivery Services SFTP and FTP file transfer Publisher Post CH Ltd Information Technology Webergutstrasse 12 CH-3030 Berne (Zollikofen) Contact Post CH Ltd Information Technology Webergutstrasse
Hosted Exchange 2013
 Our Cloud Services Hosted Exchange 2013 As a business professional you re under pressure to cut costs, streamline your business and become more productive and efficient, whilst making yourself more available
Our Cloud Services Hosted Exchange 2013 As a business professional you re under pressure to cut costs, streamline your business and become more productive and efficient, whilst making yourself more available
SnapCenter Software 4.0 Concepts Guide
 SnapCenter Software 4.0 Concepts Guide May 2018 215-12925_D0 doccomments@netapp.com Table of Contents 3 Contents Deciding whether to use the Concepts Guide... 7 SnapCenter overview... 8 SnapCenter architecture...
SnapCenter Software 4.0 Concepts Guide May 2018 215-12925_D0 doccomments@netapp.com Table of Contents 3 Contents Deciding whether to use the Concepts Guide... 7 SnapCenter overview... 8 SnapCenter architecture...
Installation Guide for Windows
 Installation Guide for Windows Advanced Research Computing V1.1 FINAL OPEN Document History This document relates to the BEAR DataShare service which is based on the product PowerFolder, version 11.5.625
Installation Guide for Windows Advanced Research Computing V1.1 FINAL OPEN Document History This document relates to the BEAR DataShare service which is based on the product PowerFolder, version 11.5.625
Choosing a Full Disk Encryption solution. A simple first step in preparing your business for GDPR
 Choosing a Full Disk Encryption solution A simple first step in preparing your business for GDPR beinformed Understand the impact Under GDPR, your organisation is required to protect data stored on devices,
Choosing a Full Disk Encryption solution A simple first step in preparing your business for GDPR beinformed Understand the impact Under GDPR, your organisation is required to protect data stored on devices,
TECHNOLOGY Introduction The Difference Protection at the End Points Security made Simple
 APPGATE TECHNOLOGY UNIFIED TECHNOLOGY Introduction The AppGate solution truly delivers holistic security and access control where other approaches fall short. It is designed to address the security and
APPGATE TECHNOLOGY UNIFIED TECHNOLOGY Introduction The AppGate solution truly delivers holistic security and access control where other approaches fall short. It is designed to address the security and
Custom Connect. All Area Networks. customer s guide to how it works version 1.0
 All Area Networks Custom Connect customer s guide to how it works version 1.0 The information in this technical user guide and the glossary of terms has been prepared in good faith and is correct at the
All Area Networks Custom Connect customer s guide to how it works version 1.0 The information in this technical user guide and the glossary of terms has been prepared in good faith and is correct at the
SIP Trunks. The cost-effective and flexible alternative to ISDN
 SIP Trunks The cost-effective and flexible alternative to ISDN A cost-effective alternative to ISDN that provides flexibility and continuity How does it work? SIP Trunks connect your to s network, enabling
SIP Trunks The cost-effective and flexible alternative to ISDN A cost-effective alternative to ISDN that provides flexibility and continuity How does it work? SIP Trunks connect your to s network, enabling
Securing Access to Network Devices
 Securing Access to Network s Data Track Technology October, 2003 A corporate information security strategy will not be effective unless IT administrative services are protected through processes that safeguard
Securing Access to Network s Data Track Technology October, 2003 A corporate information security strategy will not be effective unless IT administrative services are protected through processes that safeguard
Network Definition A network can be defined as two or more computers connected together in such a way that they can share resources.
 Networks, telecommunications and the Internet Network Definition A network can be defined as two or more computers connected together in such a way that they can share resources. The purpose of a network
Networks, telecommunications and the Internet Network Definition A network can be defined as two or more computers connected together in such a way that they can share resources. The purpose of a network
Bringing OpenStack to the Enterprise. An enterprise-class solution ensures you get the required performance, reliability, and security
 Bringing OpenStack to the Enterprise An enterprise-class solution ensures you get the required performance, reliability, and security INTRODUCTION Organizations today frequently need to quickly get systems
Bringing OpenStack to the Enterprise An enterprise-class solution ensures you get the required performance, reliability, and security INTRODUCTION Organizations today frequently need to quickly get systems
BIG DATA INDUSTRY PAPER
 BIG DATA INDUSTRY PAPER Encryption Key Management INFORMATION-RICH BIG DATA IS UNDER INCREASING THREAT OF THEFT AND BUSINESS DISRUPTION. AS THE NETWORKS AND TECHNOLOGIES THAT ENABLE BIG DATA COLLECTION,
BIG DATA INDUSTRY PAPER Encryption Key Management INFORMATION-RICH BIG DATA IS UNDER INCREASING THREAT OF THEFT AND BUSINESS DISRUPTION. AS THE NETWORKS AND TECHNOLOGIES THAT ENABLE BIG DATA COLLECTION,
NHSmail Migration Communications Plan Template
 NHSmail Migration Communications Plan Template June 2018 Version 2 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created
NHSmail Migration Communications Plan Template June 2018 Version 2 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created
Logicalis What we do
 Logicalis What we do Logicalis What we do Logicalis is an international IT solutions and managed services provider with a breadth of knowledge and expertise in Communications and Collaboration, Business
Logicalis What we do Logicalis What we do Logicalis is an international IT solutions and managed services provider with a breadth of knowledge and expertise in Communications and Collaboration, Business
CryptoEx: Applications for Encryption and Digital Signature
 CryptoEx: Applications for Encryption and Digital Signature CryptoEx Products: Overview CryptoEx Outlook CryptoEx Notes CryptoEx Volume CryptoEx Pocket CryptoEx File CryptoEx Office CryptoEx Business Server
CryptoEx: Applications for Encryption and Digital Signature CryptoEx Products: Overview CryptoEx Outlook CryptoEx Notes CryptoEx Volume CryptoEx Pocket CryptoEx File CryptoEx Office CryptoEx Business Server
UKEF UK Export Finance. Transformation with the Microsoft Cloud
 UKEF UK Export Finance Transformation with the Microsoft Cloud the customer overview Customer UKEF Website www.gov.uk/uk-export-finance Number of employees UKEF s fixed deadline had major financial implications,
UKEF UK Export Finance Transformation with the Microsoft Cloud the customer overview Customer UKEF Website www.gov.uk/uk-export-finance Number of employees UKEF s fixed deadline had major financial implications,
Disk Encryption Buyers Guide
 Briefing Paper Disk Encryption Buyers Guide Why not all solutions are the same and how to choose the one that s right for you.com CommercialSector Introduction We have written this guide to help you understand
Briefing Paper Disk Encryption Buyers Guide Why not all solutions are the same and how to choose the one that s right for you.com CommercialSector Introduction We have written this guide to help you understand
Oil/petrochemicals Case Study. 1 Oil/petrochemicals Case Study
 Oil/petrochemicals Case Study 1 Contents Introduction 03 Background 04 Selection 06 Solution 08 Benefits 11 2 Introduction Since April 2012 our client, a major company in the petrochemicals, speciality
Oil/petrochemicals Case Study 1 Contents Introduction 03 Background 04 Selection 06 Solution 08 Benefits 11 2 Introduction Since April 2012 our client, a major company in the petrochemicals, speciality
TynTec a VASCO Solution Partner Virtual Digipass / SMS Back-Up for Digipass March 2007
 TynTec a VASCO Solution Partner Virtual Digipass / SMS Back-Up for Digipass March 2007 1 TynTec Positioning For financial service providers who wish to eliminate the risk of delays and poor data security
TynTec a VASCO Solution Partner Virtual Digipass / SMS Back-Up for Digipass March 2007 1 TynTec Positioning For financial service providers who wish to eliminate the risk of delays and poor data security
Cyber Hygiene: Uncool but necessary. Automate Endpoint Patching to Mitigate Security Risks
 Cyber Hygiene: Uncool but necessary Automate Endpoint Patching to Mitigate Security Risks 1 Overview If you analyze any of the recent published attacks, two patterns emerge, 1. 80-90% of the attacks exploit
Cyber Hygiene: Uncool but necessary Automate Endpoint Patching to Mitigate Security Risks 1 Overview If you analyze any of the recent published attacks, two patterns emerge, 1. 80-90% of the attacks exploit
Frequently Asked Questions
 Frequently Asked Questions OpenText RightFax 10 May 2011 Introduction This document provides answers to commonly asked questions and additional links for more information about OpenText RightFax 10. In
Frequently Asked Questions OpenText RightFax 10 May 2011 Introduction This document provides answers to commonly asked questions and additional links for more information about OpenText RightFax 10. In
The Dropbox Problem: It s Worse than You Think
 The Dropbox Problem: It s Worse than You Think The Dropbox Problem: It s Worse than You Think Overview The unsanctioned use of consumer-oriented file sharing services in business is a growing issue. It
The Dropbox Problem: It s Worse than You Think The Dropbox Problem: It s Worse than You Think Overview The unsanctioned use of consumer-oriented file sharing services in business is a growing issue. It
GET CLOUD EMPOWERED. SEE HOW THE CLOUD CAN TRANSFORM YOUR BUSINESS.
 GET CLOUD EMPOWERED. SEE HOW THE CLOUD CAN TRANSFORM YOUR BUSINESS. Cloud computing is as much a paradigm shift in data center and IT management as it is a culmination of IT s capacity to drive business
GET CLOUD EMPOWERED. SEE HOW THE CLOUD CAN TRANSFORM YOUR BUSINESS. Cloud computing is as much a paradigm shift in data center and IT management as it is a culmination of IT s capacity to drive business
Smart Business Portal User Guide Version: 1.3
 Smart Business Portal User Guide Version: 1.3 Published on: 23 March 2012 ID 9030700 Table of Contents 1. Overview 3 1.1. Voice continuity services overview 3 1.1.1. Directed Recovery service 3 1.1.2.
Smart Business Portal User Guide Version: 1.3 Published on: 23 March 2012 ID 9030700 Table of Contents 1. Overview 3 1.1. Voice continuity services overview 3 1.1.1. Directed Recovery service 3 1.1.2.
SIP Trunks. The cost-effective and flexible alternative to ISDN
 SIP Trunks The cost-effective and flexible alternative to ISDN A cost-effective alternative to ISDN that provides flexibility and continuity How does it work? connect your to s network, enabling full PSTN
SIP Trunks The cost-effective and flexible alternative to ISDN A cost-effective alternative to ISDN that provides flexibility and continuity How does it work? connect your to s network, enabling full PSTN
Easyguard Carefree Mobile Computing
 Managebility connectivity Security Bringing innovation to business life Toshiba EasyGuard brings carefree mobile computing to your business life with unique features designed to address the mobility issues
Managebility connectivity Security Bringing innovation to business life Toshiba EasyGuard brings carefree mobile computing to your business life with unique features designed to address the mobility issues
NEN The Education Network
 NEN The Education Network School e-security Checklist This checklist sets out 20 e-security controls that, if implemented effectively, will help to ensure that school networks are kept secure and protected
NEN The Education Network School e-security Checklist This checklist sets out 20 e-security controls that, if implemented effectively, will help to ensure that school networks are kept secure and protected
Data Protection and GDPR
 Data Protection and GDPR At DPDgroup UK Ltd (DPD & DPD Local) we take data protection seriously and have updated all our relevant policies and documents to ensure we meet the requirements of GDPR. We have
Data Protection and GDPR At DPDgroup UK Ltd (DPD & DPD Local) we take data protection seriously and have updated all our relevant policies and documents to ensure we meet the requirements of GDPR. We have
UNCLASSIFIED. Mimecast UK Archiving Service Description
 UNCLASSIFIED 26/05/2016 v2.3 Mimecast UK Email Archiving Service Description Mimecast UK Email Archiving, provides businesses with a secure, scalable cloud-based message archive. It s designed to significantly
UNCLASSIFIED 26/05/2016 v2.3 Mimecast UK Email Archiving Service Description Mimecast UK Email Archiving, provides businesses with a secure, scalable cloud-based message archive. It s designed to significantly
NTT DATA Hokuriku Corporation in Hokuriku, Japan, a
 Case Study NTT DATA Hokuriku Corporation NTT DATA Hokuriku Corporation in Hokuriku, Japan, a system integration and networking system services company, selects an Allied Telesis network solution, providing
Case Study NTT DATA Hokuriku Corporation NTT DATA Hokuriku Corporation in Hokuriku, Japan, a system integration and networking system services company, selects an Allied Telesis network solution, providing
Basic rules for protecting remote maintenance accesses
 BSI publications on cyber security RECOMMENDATION: IT IN THE COMPANY Basic rules for protecting remote maintenance accesses The use of more and more complex hardware and software products makes it necessary
BSI publications on cyber security RECOMMENDATION: IT IN THE COMPANY Basic rules for protecting remote maintenance accesses The use of more and more complex hardware and software products makes it necessary
E-Security policy. Ormiston Academies Trust. James Miller OAT DPO. Approved by Exec, July Release date July Next release date July 2019
 Ormiston Academies Trust E-Security policy Date adopted: Autumn Term 2018 Next review date: Autumn Term 2019 Policy type Author Statutory James Miller OAT DPO Approved by Exec, July 2018 Release date July
Ormiston Academies Trust E-Security policy Date adopted: Autumn Term 2018 Next review date: Autumn Term 2019 Policy type Author Statutory James Miller OAT DPO Approved by Exec, July 2018 Release date July
Startup Notes for Standard CMD 2015.x Setup
 Startup Notes for Standard CMD 2015.x Setup The standard CMD program setup refers to the 2015 version of The Church Membership Directory software, which includes the two phone apps (one for staff use and
Startup Notes for Standard CMD 2015.x Setup The standard CMD program setup refers to the 2015 version of The Church Membership Directory software, which includes the two phone apps (one for staff use and
Connecting to Mimecast
 Page 1 of 5 0 KBID10577 Connecting to Mimecast Congratulations and welcome to Mimecast! Thank you for making the choice to move your email management to the cloud with the Mimecast Unified Email Management
Page 1 of 5 0 KBID10577 Connecting to Mimecast Congratulations and welcome to Mimecast! Thank you for making the choice to move your email management to the cloud with the Mimecast Unified Email Management
ON-LINE EXPERT SUPPORT THROUGH VPN ACCESS
 ON-LINE EXPERT SUPPORT THROUGH VPN ACCESS P. Fidry, V. Rakotomanana, C. Ausanneau Pierre.fidry@alcatel-lucent.fr Alcatel-Lucent, Centre de Villarceaux, 91620, Nozay, France Abstract: As a consequence of
ON-LINE EXPERT SUPPORT THROUGH VPN ACCESS P. Fidry, V. Rakotomanana, C. Ausanneau Pierre.fidry@alcatel-lucent.fr Alcatel-Lucent, Centre de Villarceaux, 91620, Nozay, France Abstract: As a consequence of
Resellers Guide Managing your Reseller Account
 Resellers Guide Managing your Reseller Account Read our Blog: http://blog.webfusion.co.uk/ View our support site: http://webfusion-support.co.uk/ Follow us on Twitter: http://twitter.com/webfusionuk Contents
Resellers Guide Managing your Reseller Account Read our Blog: http://blog.webfusion.co.uk/ View our support site: http://webfusion-support.co.uk/ Follow us on Twitter: http://twitter.com/webfusionuk Contents
GÉANT L3VPN Service Description. Multi-point, VPN services for NRENs
 GÉANT L3VPN Service Description Multi-point, VPN services for NRENs Issue Date: 1 November 2017 GÉANT L3VPN Overview The GÉANT L3VPN service offers the National Research and Education Networks (NRENs)
GÉANT L3VPN Service Description Multi-point, VPN services for NRENs Issue Date: 1 November 2017 GÉANT L3VPN Overview The GÉANT L3VPN service offers the National Research and Education Networks (NRENs)
ForeScout CounterACT. Continuous Monitoring and Mitigation. Real-time Visibility. Network Access Control. Endpoint Compliance.
 Real-time Visibility Network Access Control Endpoint Compliance Mobile Security ForeScout CounterACT Continuous Monitoring and Mitigation Rapid Threat Response Benefits Rethink IT Security Security Do
Real-time Visibility Network Access Control Endpoint Compliance Mobile Security ForeScout CounterACT Continuous Monitoring and Mitigation Rapid Threat Response Benefits Rethink IT Security Security Do
NotifyMDM Device Application User Guide Installation and Configuration for Android
 NotifyMDM Device Application User Guide Installation and Configuration for Android NotifyMDM for Android, Version 3.x NotifyMDM for Android 1 Table of Contents NotifyMDM for Android 3 Installation Instructions
NotifyMDM Device Application User Guide Installation and Configuration for Android NotifyMDM for Android, Version 3.x NotifyMDM for Android 1 Table of Contents NotifyMDM for Android 3 Installation Instructions
Hosted Acronis Backup Cloud. Keep your data safe with our cloud backup service, powered by Acronis
 Hosted Acronis Backup Cloud Keep your data safe with our cloud backup service, powered by Acronis Why choose Hosted Acronis Backup Cloud? Your most important business asset is data. After all, without
Hosted Acronis Backup Cloud Keep your data safe with our cloud backup service, powered by Acronis Why choose Hosted Acronis Backup Cloud? Your most important business asset is data. After all, without
Transform your network and your customer experience. Introducing SD-WAN Concierge
 Transform your network and your customer experience Introducing SD-WAN Concierge Optimize your application performance, lower your total cost of ownership and simplify your network management. 2X Bandwith
Transform your network and your customer experience Introducing SD-WAN Concierge Optimize your application performance, lower your total cost of ownership and simplify your network management. 2X Bandwith
INTEGRATED COMMUNICATIONS FOR YOUR BUSINESS: SIP TRUNK
 INTEGRATED COMMUNICATIONS FOR YOUR BUSINESS: SIP TRUNK cellular-solutions.co.uk A COST-EFFECTIVE ALTERNATIVE TO ISDN THAT PROVIDES FLEXIBILITY AND CONTINUITY Reliable voice services SIP trunking is the
INTEGRATED COMMUNICATIONS FOR YOUR BUSINESS: SIP TRUNK cellular-solutions.co.uk A COST-EFFECTIVE ALTERNATIVE TO ISDN THAT PROVIDES FLEXIBILITY AND CONTINUITY Reliable voice services SIP trunking is the
Data Sheet The PCI DSS
 Data Sheet The PCI DSS Protect profits by managing payment card risk IT Governance is uniquely qualified to provide Payment Card Industry (PCI) services. Our leadership in cyber security and technical
Data Sheet The PCI DSS Protect profits by managing payment card risk IT Governance is uniquely qualified to provide Payment Card Industry (PCI) services. Our leadership in cyber security and technical
Security Enhancements
 OVERVIEW Security Enhancements February 9, 2009 Abstract This paper provides an introduction to the security enhancements in Microsoft Windows 7. Built upon the security foundations of Windows Vista, Windows
OVERVIEW Security Enhancements February 9, 2009 Abstract This paper provides an introduction to the security enhancements in Microsoft Windows 7. Built upon the security foundations of Windows Vista, Windows
