A routing strategy and quorum based location update scheme for ad hoc wireless networks
|
|
|
- Brice Harrington
- 5 years ago
- Views:
Transcription
1 A routing strategy and quorum based location update scheme for ad hoc wireless networks Ivan Stojmenovic and Bosko Vukojevic Computer Science, SITE, University of Ottawa, Ottawa, Ontario K1N 6N5, Canada Abstract All previously proposed position based routing algorithms for wireless ad hoc networks were based on forwarding the actual message along multiple paths toward an area where destination is hopefully located. The significant communication overhead can be avoided if the routing strategy is changed. We propose that the source node issues several search 'tickets' (each ticket is a 'short' message containing sender's id and location, destination's best known location and time that location is reported, and constant amount of additional information) that will look for the exact position of destination node. When the first ticket arrives at the destination node D, D will report back to source with brief message containing its exact location, and possibly creating a route for the source. The source node then sends full data message ('long' message) toward exact location of destination. We then propose a quorum based location update scheme, in which nodes report their new positions to their neighbors whenever a link is broken or created. After certain number of such link changes, nodes forward their new position to all nodes located to the north and south of their current location with certain 'thickness' of reporting. The destination search then begins with two tickets being sent in the east and west direction, with certain 'thickness', looking for the most up to date information of destination's position. When the tickets reach each end of current 'row', the search is continued toward best reported destination position, with corrections along the path as better information becomes available closer to destination. One of tickets can be sent from the source directly toward destination, to take advantage of possibly correct information on destination location. We show through simulation that the proposed routing and location update schemes provide high success rates with reasonable communication overhead. 1. Introduction A broad variety of location dependent services will become feasible in the near future due to the use of the Global Position System (GPS), which provides location information (latitude, longitude and possibly height) and global timing to mobile users. GPS low power and small size cards will be deployed in each car and possibly in every user terminal. For instance, Differential GPS offers accuracy of a few meters [N]. Mobile ad hoc networks consist of wireless hosts that communicate with each other in the absence of a fixed infrastructure. Routes between two hosts in network may consist of hops through other hosts in the network. The task of finding and maintaining routes in the network is nontrivial since host mobility causes frequent unpredictable
2 topological changes. A number of protocols for achieving efficient routing have been recently proposed. They differ in the approach used for searching a new route and/or modifying a known route, when hosts move. The surveys of these protocols, that do not use geographic location in the routing decisions, are given in [BMJHJ, RS]. In this article we will discuss only GPS based approaches. Macker and Corson [MC] listed qualitative and quantitative independent metrics for judging the performance of routing protocols. Desirable qualitative properties include: distributed operation, loop-freedom (to avoid a worst case scenario of a small fraction of packets spinning around in the network), demand-based operation, and 'sleep' period operation (when some nodes become temporarily inactive). Some quantitative metrics that are appropriate for assessing the performance of any routing protocol include [MC]: end-to-end data delay, average number of data bits (or control bits) transmitted per data bits delivered. In this paper we use three quantitative metrics that are similar to these described in [BMJHJ] (each of them is an average value): - hop count (the number of edges, i.e. transmissions on the path from source to destination), - delivery rate (the ratio of numbers of messages received by destination and sent by senders), - flooding rate (the ratio of the number of message transmissions and the shortest possible hop count between two nodes). Each transmission in multiple routes is counted, and message can be sent to all neighbors with one transmission. Although 'algorithm' and 'protocol' have the same meaning in literature, we shall have a subtle difference in our discussions. The routing methods are described by algorithms which underline only major ideas of the corresponding detailed protocol. The actual protocol may always include additional techniques, most of them already being applied in other protocols, and details of communication between nodes. This paper will focus on routing algorithms, not protocols. Ad hoc networks are best modeled by minpower graphs constructed in the following way. Each node A has its transmission range t(a). Two nodes A and B in the network are neighbors (and thus joined by an edge) if the Euclidean distance between their coordinates in the network is less than the minimum between their transmission radii (i.e. d(a,b) < min {t(a), t(b)}) [BCSW]. If all transmission ranges are equal, the corresponding graph is known as the unit graph. These models provide acknowledgments for received messages. The minpower and unit graphs are valid models when there are no obstacles in the signal path (e.g. a building). Ad hoc networks with obstacles can be modeled by subgraphs of minpower or unit graphs. This paper deals primarily with unit graphs. Ad hoc networks consist of autonomous nodes that run their routines in asynchronous fashion. The communication algorithms between nodes are therefore all distributed. However, Estrin, Govindan, Heidemann, and Kumar [EGHK] defined the class of so called localized algorithms, as distributed algorithms where simple local node behavior achieves a desired global objective. Localized algorithms therefore resemble the class of greedy sequential algorithms. They argued that localized algorithms may be necessary for sensor and ad hoc network coordination, and described localized algorithms for clustering and object location. We propose a more formal definition of localized algorithms. In a localized algorithm, each node makes the decision to which neighbor(s) to forward the 2
3 message based solely on the location of itself, its neighboring nodes, and a constant amount of additional information. In addition, each node is allowed to perform local computation (since it is equipped with a small but powerful processor). The decision depends on the task performed and the algorithm followed, which is part of an incoming message. In case of routing, the additional information needed is the location of the destination. The sender uses the latest available location about the position of the destination and attaches it to the message. Intermediate nodes may use their more recent location information to replace the one that comes with the message (and also to update their own information otherwise). The other six problems may not need any additional information (other than the one that arrives as part of the message) to perform a localized algorithm. Note that the requirement for the location of a destination means that each node should update locations of all other nodes in the network, so that any routing that is initiated will have a reasonably good start. However, the path adjustments can be made as the message travels closer to the destination. Non-localized algorithms, on the other hand, typically require the knowledge of the locations of all nodes in the network, and also the information about the existence of every edge in the graph. All non-localized routing algorithms proposed in literature are variations of shortest weighted path algorithm (e.g. [CN, LL]). Although ad hoc network is fairly accurately modeled by unit graphs, nodes that are at distance less than R may have an obstacle between them blocking the communication, while two nodes at distance that exceeds R by a small amount may still be able to communicate between them (or a node may even choose whether to use that possible but power demanding link). Thus the use of non-localized algorithms requires the regular update of existing edges in addition to nodes location, which is a quadratic (in number of nodes) communication overhead requiring considerable bandwidth and battery power. Next, some nodes in the sensor or ad hoc network may be temporarily inactive, and non-localized algorithms need to know which of the nodes are active to make their best decisions. The activity information puts additional demand on the information update. For example, static nodes may need to broadcast such information to the whole network whenever they change their activity status while, at the same time, they have no need to update their location with the rest of the nodes. In order to preserve battery power over long periods of time, nodes may change their activity on a regular basis, or it may depend on the size of the job assigned to them. While the absence of a GPS receiver at nodes forces many problems (routing, for example) to be solved by only non-localized algorithms, their application, when GPS is available, may not be justified if efficient localized alternatives are available. The power savings obtained by applying a localized rather than non-localized algorithm outweighs even the additional power imposed to nodes for carrying and using GPS receiver. This paper deals solely with localized algorithms. This paper is organized as follows. Section 2 gives a review of localized routing algorithms and location update techniques in ad hoc networks. Section 3 proposes a new routing strategy, which separates the location update, destination search, path creation and data traffic phases in a routing process. Sections 4 and 5 propose new quorum based location update and destination search schemes. Section 6 deals with simulation and experimental results that confirm the efficiency of proposed methods. Future work is discussed in section 7. 3
4 4 2. Literature review Stojmenovic and Lin [SL] described and discussed basic localized routing algorithms. Source or any intermediate node S will select one of its neighbors A according to a criterion. In the DIR method, derived from [BCSW, KV, KSU], the best neighbor has the closest direction (that is, angle) toward the destination. That is, neighbor with minimum angular distance from the imaginary line joining the current node and the destination is selected. GEDIR method [SL] selects neighbor A that is closest to the destination D. In MFR method [TK], the best neighbor A will minimize the dot product DA. DS. Alternatively, one can maximize the dot product SD. SA. Each method stops forwarding the message at a node for which the best choice is to return the message back to previous node. GEDIR and MFR methods are loop-free, while DIR method may create loops, unless past traffic is memorized or a timestamp is enforced [SL]. The experiments in [SL, SSW, SL2] are carried on static networks. A routing algorithm that guarantees delivery in unit graphs is described in [BMSU]. Power aware routing is discussed in [SL2]. The concept of internal nodes is introduced in [WL] and significantly improves delivery rates and hop counts in routing algorithms [SSW]. Basagni, Chlamtac, Syrotiuk and Woodward [BCSW] described a distance routing effect algorithm for mobility (DREAM). The source or any intermediate node A calculates the direction of destination D and, based on the mobility information about D, chooses an angular range. The message m is forwarded to all neighbors whose direction belongs to the selected range. The range is determined by the tangents from A to the circle centered at D and with radius equal to a maximal possible movement of D since the last location update. The area containing the circle and two tangents is referred as the request zone in [KV]. DREAM algorithm [BCSW] incorporates the idea of triggering the sending of location updates by the moving nodes autonomously at a rate and hop distance that correspond to the node's mobility rate. Ko and Vaidya [KV] described, independently at the same conference, an almost identical algorithm, and a few modifications of it. In the location aided routing (LAR) algorithm [KV], the request zone is fixed from the source, and a node which is not in the request zone does not forward a route request to its neighbors. If the source has no neighbors within the request zone, the zone is expanded to include some. The size of the request zone depends on the average speed of the destination's movement and time elapsed since the last known location of the destination was recorded [BCSW, KV]. The definition of the request zone [BCSW, KV] was modified in [S1] in order to provide uniform framework with the corresponding notions in GEDIR and MFR methods. [S1] discusses the V-GEDIR, CH-MFR and R-DIR methods, in which m is forwarded to exactly those neighbors which may be best choices for a possible position of destination (using the appropriate criterion). The request zone in R-DIR method [S1] may include one or two neighbors that are outside of angular range, because they can have the closest direction for the tangents to the circle. In V-GEDIR method, these neighbors are determined by intersecting the Voronoi diagram of neighbors with the circle (or rectangle) of possible positions of destination, while the portion of the convex hull of neighboring nodes is analogously used in the CH-MFR method. Ko and Vaidya [KV] discussed various enhancements to their basic technique. The LAR scheme 1 [KV] proposes an alternative definition of the request zone, as the
5 smallest rectangle that includes current location of S and the expected zone of destination (a circular region). The request zone is thus increased, with increased chances of reaching destination but also with increased flooding. The modifications in [KV] include sending route requests before the message itself [JM]. Note that a route request may be considered as a routing of short messages. Nodes may update their location information with each exchange of messages between them. Messages may contain source location also to update location information at intermediate nodes. Recovery procedures based on partial or full flooding, to start flooding if the given algorithm fails to find the route within a timeout interval, are proposed by both papers [BCSW, KV]. Ko and Vaidya [KV] also proposed the LAR scheme 2. In this scheme, the source or each intermediate node A will forward the message to all nodes that are closer to the destination than A is (more precisely, at most δ farther from the destination than node A, to account for possible location error). The routing algorithms in [BCSW, KV] are fully distributed, and robust, since they provide multiple routes. They are also demand-based and adapt well to 'sleep' period operation. Simulation results presented in [BCSW] using a discrete event simulator show that the dynamic source routing protocol [JM] has a 25% to 250% larger end-to-end delay than the DREAM protocol. The average number of data bits transmitted per data bits delivered is consistently lower for both LAR schemes as compared to flooding [KV]. Therefore adding location information to the routing tables in all nodes resulted in significant improvement in the performance over the existing methods that do not use such information. Despite these advantages, the proposed methods [BCSW, KV] have some drawbacks. They have considerable flooding rates, and the directional methods are shown not to guaranty loop-free paths [SL]. In [CL], Camara and Loureiro used routing tables which are updated by mobile software agents modeled on ants. Ants are used to collect and disseminate information about nodes' location. Experiments in [CL] compared ants based method with LAR2 without memorizing past traffic and reported flooding ratio in LAR2 over thousand times higher than in ant based method. If past traffic is memorized, experiments in [SL] report 98% success rate for LAR2 (n=100 nodes with average degree k=7) with flooding rate (ratio of number of transmissions of a given method compared to a shortest path algorithm) of 5.3. This number assumes correct information about destination and forwarding full messages to it. This is in addition to flooding effect caused by the location update schemes in [KV, BCSW]. Amouris, Papavassiliou and Lu [APL] presented a position based multi-zone routing protocol for wide area mobile ad-hoc networks. Their algorithm is based on position updates within circles of increasing radii. Each node updates its location to all nodes located within circle of radii P, 2P, 4P, 8P, (each subsequent circle has twice larger radius than previous one). Whenever a given node A moves outside one of these circles of radius 2 t P for some t, node A broadcasts its location update to all nodes located inside of circle centered at current node position, and with radius 2 t+1 P. The routing toward destination then follows these circles of last updates. Source nodes send message toward the last reported position of destination (using the DIR method), which since the last report has moved within the circle of some radius. As routing message moves closer to destination, the information about position of destination becomes more precise, and nodes are able to send message toward center of circles with twice smaller radius than 5
6 previously, until the node is eventually reached. This method is very interesting and certainly competitive. We observe that the radius of larger circles may encompass almost all nodes of the network, and that the routing paths discovered by the algorithm do not have near optimal hop counts (which may be important in quality of service applications). However, if the path quality is important, one can apply our proposed routing scheme where destination may report back to source with a better path. The authors measured communication overhead for given fixed parameter setting (speed, direction, radius, number of nodes) with respect to increasing network size. No comparison of data traffic versus location update traffic is provided. Karumanchi, Muralidharan and Prakash [KMP] discussed information dissemination in partitionable mobile ad hoc networks. They study the problem of getting the location of some other node in the network and the surroundings of that node (e.g. firefighter) without the need to route any message to that node. Thus their performance evaluation is limited in measuring the accuracy of the obtained information (i.e. the distance between found and exact location of other node). They use a well known approach for information dissemination by replicating information at multiple nodes acting as repositories, and employing quorum based strategies to update and query information. In [KMP], n nodes are divided into n 1/2 groups with n 1/2 nodes in each in two ways (as explained below for any quorum based strategy) and preserve such quorums while nodes move. They also discussed the question when to update location, and argued that distance-based updates (based on absolute distance traveled since last update) and movement-based updates (based on the velocities of nodes) may have limited usefulness in ad-hoc networks (such location updates are used in [BCSW, KV]). For instance, nodes may move within a small circle, causing unnecessary location updates. Karumanchi, Muralidharan and Prakash [KMP] concluded experimentally that the best strategy is to update when a certain pre-specified number of links incident on a node have been established or broken since the last update. We decided to apply this strategy in our paper. Given a set S of n servers, a quorum system is a set of mutually disjoint subsets of S whose union is S. When one of servers require information from the other, it suffices to query one server from each quorum. It is possible to form quorums of size approximately n 1/2 [M]. For example, 25 servers can be organized into 5 rows and 5 columns. Each column serves as a quorum. Thus each node (i,j) (located in i-th row and j-th column) replicated its data to all servers (i',j) in its column. To extract the information from server (i,j), server (i', j') may inquire within its i'-th row, and the server (i',j) will provide requested information. Variations of this scheme are used in fixed networks, where the set of queried servers is bound to contain at least one server that belonged to the quorum that received the latest update. Hence, each query returns the latest value of the queried data. Such a query and update strategies has been previously employed for location management in cellular networks [KAS, PHS, PS]. Modifications of quorum based strategy for use in dynamic or partitionable servers has been considered in [ESC, H, KMP]. The main idea in these papers [ESC, H, KMP] is that each server (or node) selects one of quorums at random, to increase the chance of obtaining relatively up to date information in several 'columns'. 6
7 7 3. A routing strategy for ad hoc networks The problem of routing in mobile networks is apparently very difficult one, and so far no complete and satisfactory (in terms of almost guaranteed delivery without significant communication overhead) scheme was proposed. We propose to clearly divide the problem into several components, and study each of them separately. All the message traffic related to routing tasks is divided into four components as follows. 1) Location update messages are initiated by each node, which acts on its movement. Location updates are required by some other tasks as well (e.g. clustering, broadcasting, etc.). 2) Destination search messages, initiated by a source node, when it wants to route a message toward destination. This idea is similar to the dynamic source routing (e.g. [JM]) applied in ad hoc networks that do not use GPS in their routing decisions. However, it also differs significantly from these methods since they suggest full flooding as a means of searching, while we propose an intelligent search based on location of nodes. Also, we do not need to maintain any kind of routing tables, and believe that position information suffice to make intelligent decisions without them. 3) Path creation messages, initiated by destination upon receiving the first copy of a search message. The destination learns the location of sender from the search message and is able to find the best path accurately. Since the transmission speed is far greater than node movement speed, the path creation phase in a localized routing may, to a large extent, be considered as the operation performed on a static network. Thus routing algorithms for static networks (with known location of destination), such as those proposed in [KSU, SL, BMSU, SL2, SSW, TK], may be applied for the path creation phase. This assumption is justified since each node mountains the list of neighbors and learns the exact location of destination, which is the only information needed for making a routing decision at each node. 4) Data traffic messages, initiated by source upon receiving reply from destination containing its exact location, possibly together with the path toward destination (e.g. in a form of next hop routing information at intermediate nodes [PR]). Alternatively, the source may attempt to create another path, knowing destination location accurately, by applying any localized routing algorithm defined on static networks. In this routing scheme, we may also divide all messages into short and long ones. Short messages do not have the real information (to be forwarded to destination) as part of message (unless it is a very brief message, e.g. alarm), and therefore has much lesser number of bits than the message that contain the real information. Location update, destination search, and path creation messages are short messages. Location update messages are generated independently on routing request, as a preparation for successful destination search. Destination search and path creation messages are generated by routing requests. They are still a communication overhead. When the real message, containing data to be forwarded to destination, is long compared to first three kinds, this routing scheme is justified. Note that, with this general routing scheme, the routing problem is divided into two components that may be investigated separately, as follows.
8 8 Component 1: Location update and destination search schemes. Component 2: Routing to a destination whose position is known (includes path creation from destination to the source, and data traffic from source to destination). Satisfactory localized solutions for path creation and data traffic phases are already proposed in [BCSW, BMSU, KSU, KV, SL, SSW, SL2, S1]. Because of drawbacks of existing solutions for the location updates and destination search schemes, we shall concentrate on these two components in this paper. We shall propose new solutions for them in the next two sections. The main difference between our proposed location update and destination search strategies and previously proposed analogous solutions (including non-gps based route discoveries and route maintenance) is that full flooding was previously used as regular technique to construct the route, maintain the route or update the location in many cases. For example, when destination moves extensively but far way from the source, no solution other than full flooding was suggested. We propose to deal with such movement pattern by reducing full flooding to row and column paths of certain thickness. 4. Location update In this paper, we shall adopt the quorum based idea to enable efficient routing in mobile ad hoc networks. Clearly, nodes in ad hoc network do not stay in the same 'column', and the distributed information may easily disperse due to node movement. Moreover, it is not clear what the 'column' is, and how all the nodes in a column, once defined, will receive latest updates. Nevertheless, we believe that this idea is worth pursuing. The basic update procedure is performed by each moving node whenever it observes that, due to its movement, an existing edge will be broken (that is, the distance between two nodes becomes >R). The node will broadcast a message containing its new location information to all neighbors which are at distance tr. For t=1, the radius is same as the radius for transmitting data traffic. In this case, former neighboring node is assumed to have received new location information and will also record broken edge. However, nodes may adjust transmission power, and spend more energy for short messages. Lin and Liu [LL] discussed this difference and even proposed an extreme difference in radii for short and long messages. Nodes in [LL] are able to send their new location to all other nodes in network with a single broadcast (single-hop network for location updates). However, when sending exact data, the network is treated as multi-hop one. Note that the single-hop location update broadcast may fail to reach a number of nodes due to obstacles in the field. Next, those obstacles are not accounted for in the shortest weighted path QoS routing algorithm [CN]. Thus we believe that assuming single-hop network for location updates may not be justified, since it may require too much power from nodes to reach all other nodes (the transmission power is proportional to square, or higher degree, of the transmission radius). However, we still allow larger power for location updates, and may consider location update with radius tr, where t is network parameter. Spending larger power for update may be justified by better
9 destination search efficiency. Another possible solution is to keep transmission radius at R, but retransmit from each of neighbors few hops away. However, these retransmissions also require power (from neighboring nodes), and may cause broadcast storm problem [NTCS], and therefore its efficiency is doubtful. We thus assume a single broadcast at distance tr. Each node which is, at the moment of transmission, located inside that circle (of radius tr) is assumed to receive the new location accurately, without acknowledging the message. However, new neighbors will reply to node (using radius R), and other nodes within radius R will also learn updated position of that node. Each node A will send similar location updates (at radius tr, where t could be same or different parameter) when it discovers new neighbors, according to the last information they have about location of that new neighbor. That new neighbor B will acknowledge with exact location information, if indeed neighbor, and will use R as the transmission radius. If B is not within distance R but within tr, it will respond, by adjusting transmission radius to exact distance, and other nodes within that transmission radius also hear that transmission. If B is not within tr, it will not respond, and A will adjust location information for that node to new position, at distance (t+1)r, in direction of old position (keeping old timing information, though). The main location update method is to forward the new location information (and node's identifier) within a 'column' in the network, in the following way. Each node uses a counter to count the number of previously made changes in edge existence (the number of created or broken edges). When the counter reaches a fixed threshold value e, location information is forwarded along the 'column', and e is reset to 0. Node A uses radius pr, where p is network parameter ('thickness' of column). A initiates two routing messages, in the directions north and south. Each follows variation of the MFR algorithm [TK], with destination always to the north of current node, as follows. A first transmits update information over radius pr, and each node within distance pr receives the update. Only one of nodes, the most northern (and similarly the most southern) will retransmit, and is decided as follows. A sends separate message, with radius R, looking for such a node. The message is sent to the northernmost neighbor B of A, and retransmitted in the same fashion. If B has neighbors within pr of A, which are more north than B, B will send the message (also at radius R) to the northernmost among them. This search continues until a node B has no neighbor within pr which is more to the north than B. B will retransmit, with radius pr, and process continues until a node cannot find any neighbor to the north. Note that, for p=1, the method can be simplified easily to only one transmission. This process continues toward the northernmost and southernmost nodes. The initiator of location update sends the update in both directions, while other nodes follow only one of directions. Note that, for some reasons (e.g. in graphs of low density), the column may terminate without reaching nodes that are furthest north from A. Increased transmission radius (pr) is proposed to reduce the chances of such an event. Additional techniques (e.g. restrictions to the internal nodes [SSW, WL] may also be applied). Each node receiving new location information for A, by means of any of transmissions, will record it, together with date of update. Moreover, each node transmitting any kind of message will include its own location with the message, thus providing an update on its own position to its neighbor within the selected transmission radius. 9
10 10 5. Destination search The search for destination is performed in the following way. The source S broadcasts search request using radius sr, where s is another network parameter. If destination is within sr, it will reply, adjusting its transmission radius to exact distance to sender. The search messages always carry the location of sender (and time), and nodes receiving the information will update sender's location in their tables. If there is no reply, the search continues in east-west direction, in similar way as for the location update (that is, easternmost and westernmost neighbors will retransmit at same radius sr). The search message includes time of last available information, and other nodes are requested to provide more up to date information, if they have. This process goes as follows. Let A be the node that transmitted with radius sr. Each node C, AC < sr, which has no neighbor F such that FA < sr and AF > CF, will start response process within circle of radius sr. If node C has more up to date information about D than A, then it sends it to one of its neighbors that is closest to A (it sends both the time of information and location of D at that time). Other nodes C inside the circle (of radius sr) will wait certain time (proportional to their distance from the boundary of the circle) for reaction of its neighbors that are further from A. If C receives one or few such messages, it will choose the most up to date among them (including its own information), and forward it to its neighbor that is closest to A. If C receives no message, and has no better information, it remains silent. Eventually, node A may receive a better information about location of D. The best information is then forwarded in given direction (eastward or westward) to furthest possible neighbor, using radius R for transmission, and retransmitted similarly until a node is reached that has no neighbor in given direction but is still inside the circle. That neighbor repeats the process by transmitting with higher radius sr. When easternmost and westernmost nodes are reached, the search strategy changes. The message search is then oriented toward the destination, using latest available information for each search message. There are three searches initiated. The first one originates at sender node S, using the best information collected within circle of radius sr centered as S. This search does not need to wait for the result of searches in the east and west directions. The other two searches are initiated by easternmost and westernmost nodes in a given 'row'. Each of three search tasks follows a path toward destination, using GEDIR strategy [SL]. That is, at each step, the neighbor closest to destination is selected to forward the message. Since any of messages between two nodes can be heard by all nodes within radius R, if any of them has a better information about destination, it will react by using power 2R, so that receiver nodes will also hear it and possibly adjust the algorithm. GEDIR algorithm stops if the best neighbor for a node is the neighbor that actually sent the message. Such node, called concave node in [SL], will stop the search algorithm to avoid the creation of local loop. Before terminating the search, that node will make one last attempt to gain better information, and will broadcast destination search message using radius sr. If a better information is received, and new neighbor selected accordingly, the search may continue. Otherwise it terminates. Note that the location of source node is updated at each node that hears any of destination search or path creation messages.
11 11 S B W C R A5 A4 D3 A3 A2 D2 A1 D1 Figure 1 illustrates location update and destination search schemes, where we assume t=p=s=1. Destination node D moves (other nodes in Fig. 1 are assumed to be static) from positions D1 to D2 and finally to D3, and causes some edges to brake or to be created (indicated by arrows, with nodes A1, A2, A3 and A4). At position D3, it decides to send location update in its current 'column' by sending its position in the north direction (it does so in the south direction as well, but there is no neighbor in south direction in Fig. 1). The main update path is indicated in bold lines, and bold long dashed lined indicate some other nodes that hear the update message. Source node S initiates destination search in the east-west direction (in Fig. 1 it has only neighbors in west direction). The search path is indicated in bold line, and some other nodes that observe the search are connected by bold short dashed lines. The location update column and destination search row intersect in Fig. 1 in seven nodes. The easternmost and westernmost points in the row, and node S then turn the search toward learned position of D. In Fig. 1, point W learned the up to date information, and may find the destination by applying any localized routing algorithm for static nodes (in Fig. 1, GEDIR algorithm would produce path W-B-C-A3-D3). 6. Simulation Figure 1. Location update from D3 and destination search from S The parameters in the simulation as follows. The number n of nodes in the network is set to n=100. The average node degree k is set to k=7. The corresponding value for radius R is found as in [SL] (by sorting all possible edges and choosing R to provide exactly nk/2 edges). 20 random unit graphs generated. For each graph, n nodes select their x and y coordinates at random from the interval [0,100]. Graphs are not checked for connectivity, since node movement may disconnect each graph and reconnect it frequently. Thus initial connectivity does not secure connectivity during node movements. The parameters t, s, p for the link update, column update and destination searches are tested for values 1, 2, and 3 each, with all possible 27 variations. The rate e of column (or quorum) update received values e=3, 5, 10
12 12 The movement of nodes is similar to the one used in [CN, JM, MZ]. Each node generates a random number wait (rounded to nearest integer) in interval [0..maxwait]. The node does not move for wait seconds. This is called station time. When this time expires, node generates a random number travel in interval [0,maxtravel] (rounded to nearest integer), and generates a new position within the same square at random. Node then moves from old position to new position along the line segment joining them at equal speed for the duration of travel seconds. Upon arriving at new location, node again chooses waiting period etc. Mobility rate is given by formula mobrate = maxtravel/(maxtravel+maxwait). Parameter mobrate received values 10%, 20%, 30%, 50%, 100%, while maxtravel was set to 100 seconds. Routing rate routrate has an impact on the communication overheads and success rates. It is defined as the number of routing tasks initiated in each second. The tested values for routrate are 1, 5, 10, 20, We assume that the time needed for a location update or a destination search is expressed in miliseconds and that nodes do not move significantly during that time. In each second, the following events occur. 1) routrate routing tasks are performed, one after the other (sequentially). For each of them, source and destination nodes are chosen at random (they must be distinct). Each node has correct list of its neighbors, since the location update between neighboring nodes is regular and occurs whenever topology changes. Thus even if the actual distance is a bit over R (due to small inaccuracies in recorded mutual positions of nodes), we assume that neighboring nodes receive correctly the message. 2) All nodes move to a new position. 3) Each node that detects a broken or created link, based on the recorded position of its neighbors (neighbors may not be at that position), performs local or even quorum based location update. No routing tasks are issued in first 100 seconds. In the next 900 seconds, routrate routing tasks are issued in each second. The following performance measurements are taken in the experiment. Each value is an average over 20 graphs. 1) Success rate, equal to the percentage of successful destination search requests. 2) Numbers of transmissions with each of radii R, 2R, sr, pr, tr mentioned in the scheme, each divided by the number of routing tasks issued altogether, are reported separately. This is communication overhead. As in [APL], no link details (such as MAC protocol, link errors, frame retransmissions etc.) are modeled here. We assume that no collisions occur in any of simultaneous message transmissions, and all transmitted messages are correctly received (depending only on transmission radius). Thus each node is assumed to be an infinitebuffer, store-and-forward queuing station. Error free transmission in any direction, or in all directions simultaneously, is also assumed.
13 13 The obtained data will be included in the paper after the experiments are completed. The actual routing tasks, and even the reporting back from destination to source, are simulated separately. The same simulation is done in other papers [SL] using static nodes and several localized routing algorithms, but assuming that each graph is connected. The fact that nodes need only local information (position of neighbors) and precise information about destination, and the relative low speed of nodes compared to speed to transmissions, is equivalent to considering routing tasks with static nodes. Our obtained hop counts and success rates for GEDIR method are somewhat worse than reported data, but not significantly (because of possibly disconnected graphs). We did not report the obtained data since we believe that the problem of routing with precise information on destination location requires a separate investigation [SL]. 7. Future work This paper proposed location update and destination search algorithms. Once destination is found, an algorithm described in [BMSU] may be used for path creation and data traffic messages with guaranteed delivery. It is interesting to observe that this proposed scheme contains elements of all three basic routing algorithms: GEDIR, DIR and MFR. MFR algorithm is used for location update and first part of destination search, DIR algorithm is used in the FACE portion of GFG algorithm [BMSU] when GEDIR fails, and GEDIR is used otherwise. Our location update scheme works well even if nodes move together to a new area (e.g. group of vehicles or soldiers). The columns and rows defined in our location update scheme are relative, not absolute. The only problem could be if the movement is very synchronous (vehicles on a highway), keeping mutual distances but moving at high speed. This case is not dealt with in our experiments, but can be treated separately, by identifying such pattern of movement (this may involve the use of sensors with line of sight direction measurements [EGHK]), and reducing location update to a reasonable level. It is not difficult to incorporate such a change in the actual routing protocol. Unsuccessful searches for destination may be converted into full flooding at termination nodes, if guaranteed delivery is required. If this event occurs very rarely, it shall have no significant impact on communication overhead. In case of frequent failures, the quorum based strategy may need further improvements. It is easy to construct examples where our 'columns' for update and 'rows' for search do not intersect at all, even for static nodes. Our location update scheme may be improved by sending location update into both row and column containing node, and also by searching both row and column for location of destination. Further 'columns' and 'rows' definitions may also include lines at different angles (other than horizontal and vertical) if the nodes are aware of global network configuration and a different column and row directions are justified (e.g. at angles π/4). If global network configuration is not known, columns may be chosen in a random direction, perhaps adding orthogonal direction for location updates as well. The destination searches may also proceed in a random direction, and its orthogonal one, to assure a good intersection with recent location updates. A variation of MFR algorithm, where destination is changing so that it points in selected direction from current node, may be applied, to replace the notion of eat, west, north and south
14 14 directions. Thus, instead of merely comparing x or y coordinates and choosing minimum or maximum one, one can select the maximal dot product d. SA between fixed direction d and the vector joining current node S with candidate node A. The communication overhead may be reduced, with small impact on success rate, if the updates and searches using 'big' circles (radii pr and sr) are performed from first nodes outside previous 'big' circle, instead of last node located inside. The concept of internal nodes [SSW, WL] way be used to improve the performance of in destination search, location update and path creation phases. Six definitions of internal nodes are proposed in [SSW]. The simplest of them is defined as follows. A node is intermediate node if there exist two of its neighbors that are not directly connected [WL]. Thus intermediate node belongs to a shortest path between some pairs of nodes. Nodes which are not intermediate may stop forwarding the message, if it is sent to them in any of the phases (of course, such nodes may hear transmissions, but should not be selected as destination by any of the paths in any of the phases). The performance of any of the phase may be greatly improved by restricting the paths to internal nodes only. Longer and more successful path will be created that way. A variant of the method may choose to send location updates in a different way. Instead of counting the number of the number of link changes, node may act based on distance traveled since last location update, and act when this distance reaches tr, for some value of t (t=1, 2, 3, ). Thus we believe that quorum based idea for routing in ad hoc networks has the potential to be very efficient, in terms of small hop counts, almost guaranteed delivery, and small communication overhead. References [APL] K.N. Amouris, S. Papavassiliou, M. Li, A position based multi-zone routing protocol for wide area mobile ad-hoc networks, Proc. 49 th IEEE Vehicular Technology Conference, 1999, [BCSW] S. Basagni, I. Chlamtac, V.R. Syrotiuk, B.A. Woodward, A distance routing effect algorithm for mobility (DREAM), Proc. MOBICOM, 1998, [BMJHJ] J. Broch, D.A. Maltz, D.B. Johnson, Y.C. Hu, J. Jetcheva, A performance comparison of multi-hop wireless ad hoc network routing protocols, Proc. MOBICOM, 1998, [BMSU] P. Bose, P. Morin, I. Stojmenovic and J. Urrutia, Routing with guaranteed delivery in ad hoc wireless networks, 3 rd int. Workshop on Discrete Algorithms and Methods for Mobile Computing and Communications, Seattle, August 20, 1999, [CL] D. Camara and A.F. Loureiro, A novel routing algorithm for ad hoc networks, Proc. HICSS, Hawaii, January 2000, to appear. [CN] S. Chen and K. Nahrstedt, Distributed quality-of-service routing in ad hoc networks, IEEE J. Selected Areas in Communications, 17, 8, August 1999, [EGHK] D. Estrin, R. Govindan, J. Heidemann, S. Kumar, Next century challenges: Scalable coordination in sensor networks, Proc. MOBICOM, 1999, Seattle,
15 15 [ESC] A. El Abbadi, D. Skeen, F. Cristian, An efficient fault-tolerant algorithm for replicated data management, Proc. 5 th ACM SIGACT-SIGMOD Symp. Principles of Database Systems, , [H] M. Herlihy, Dynamic quorum adjustment for partitioned data, ACM Transactions on Database Systems, 12, 2, , June [JM] D. Johnson and D. Maltz, Dynamic source routing in ad hoc wireless networks, in Mobile Computing (T. Imielinski and H. Korth, eds), Norwell, MA: Kluwer, [KAS] G. Krishnamurthy, A. Azizoglu, A.K. Somani, Optimal location management algorithms for mobile networks, Proc. 4 th Annual ACM/IEEE Int. Conf. on Mobile Computing and Networking MOBICOM'98, , [KMP] G. Karumanchi, S. Muralidharan and R. Prakash, Information dissemination in partitionable mobile ad hoc networks, Proc. IEEE Symp. On Reliable Distributed Systems, Lausanne, Oct [KSU] E. Kranakis, H. Singh and J. Urrutia, Compass routing on geometric networks, Proc. 11 th Canadian Conf. on Computational Geometry, Vancouver, August, [KV] Y.B. Ko and N.H. Vaidya, Location-aided routing (LAR) in mobile ad hoc networks, Proc. MOBICOM, 1998, [LL] C. R. Lin and J.S. Liu, QoS routing in ad hoc wireless networks, IEEE J. Selected Areas in Communications, 17, 8, Aug. 1999, [M] M. Maekawa, A n 1/2 algorithm for mutual exclusion in decentralized systems, ACM Transactions on Computer Systems, , May [MC] J.P. Macker and M.S. Corson, Mobile ad hoc networking and the IETF, Mobile Computing and Communications Review, 2, 1, 1998, [MZ] A.B. McDonald and T.F. Znati, A mobility-based framework for adaptive clustering in wireless ad hoc networks, IEEE J. Selected Areas in Communications, 17, 8, August 1999, [N] NAVSTAR GPS operations, and Iowa State University GPS page, [NTCS] S.Y. Ni, Y.C. Tseng, Y.S. Chen, J.P. Sheu, The broadcast storm problem in a mobile ad hoc network, Proc. MOBICOM, Seattle, Aug. 1999, [PR] C. Perkins and E.M. Royer, Ad hoc on demand distance vector (AODV) routing, internet draft, August [PHS] R. Prakash, Z.J. Haas, M. Singhal, Load balanced location management for mobile systems using dynamic hashing and quorums, TR-UTDCS-05-97, The University of Texas at Dallas, October [PS] R. Prakash and M. Singhal, A dynamic approach to location management in mobile computing systems, Proc. 8 th Int. Conf. on Software Eng. & Knowledge Eng. SEKE'96, , Lake Tahoe, Nevada, June [RS] S. Ramanathan and M. Steenstrup, A survey of routing techniques for mobile communication networks, Mobile Networks and Applications, 1, 2, 1996, [SL] I. Stojmenovic and X. Lin, GEDIR: Loop-free location based routing in wireless networks, IASTED Int. Conf. on Parallel and Distributed Computing and Systems, Nov. 3-6, 1999, Boston, MA, USA, to appear. [SL2] I. Stojmenovic and Xu Lin, Power-aware routing in ad hoc wireless networks, SITE, University of Ottawa, TR-98-11, December 1998.
Internal node and shortcut based routing with guaranteed delivery in wireless networks
 Internal node and shortcut based routing with guaranteed delivery in wireless networks Susanta Datta 1, Ivan Stojmenovic 1,2 and Jie Wu 3 1 SITE, University of Ottawa, Ottawa, Ontario K1N 6N5, Canada ivan@site.uottawa.ca
Internal node and shortcut based routing with guaranteed delivery in wireless networks Susanta Datta 1, Ivan Stojmenovic 1,2 and Jie Wu 3 1 SITE, University of Ottawa, Ottawa, Ontario K1N 6N5, Canada ivan@site.uottawa.ca
Location-based localized alternate, disjoint and multi-path routing algorithms for wireless networks
 J. Parallel Distrib. Comput. 63 (2003) 22 32 Location-based localized alternate, disjoint and multi-path routing algorithms for wireless networks Xu Lin a and Ivan Stojmenovic b,c, * a Cognos Inc., 700-275
J. Parallel Distrib. Comput. 63 (2003) 22 32 Location-based localized alternate, disjoint and multi-path routing algorithms for wireless networks Xu Lin a and Ivan Stojmenovic b,c, * a Cognos Inc., 700-275
Evaluating the Performance of Mobile Agent-Based Message Communication among Mobile Hosts in Large Ad Hoc Wireless Network
 Evaluating the Performance of Mobile Agent-Based Communication among Mobile Hosts in Large Ad Hoc Wireless Network S. Bandyopadhyay Krishna Paul PricewaterhouseCoopers Limited Techna Digital Systems Sector
Evaluating the Performance of Mobile Agent-Based Communication among Mobile Hosts in Large Ad Hoc Wireless Network S. Bandyopadhyay Krishna Paul PricewaterhouseCoopers Limited Techna Digital Systems Sector
Broadcast algorithms for Active Safety Applications over Vehicular Ad-hoc Networks
 Broadcast algorithms for Active Safety Applications over Vehicular Ad-hoc Networks M.N. Mariyasagayam, M. Lenardi HITACHI Europe, "Le Thélème", 1503 Route des Dolines, 06560 Sophia Antipolis, France Phone:
Broadcast algorithms for Active Safety Applications over Vehicular Ad-hoc Networks M.N. Mariyasagayam, M. Lenardi HITACHI Europe, "Le Thélème", 1503 Route des Dolines, 06560 Sophia Antipolis, France Phone:
Data Communication. Guaranteed Delivery Based on Memorization
 Data Communication Guaranteed Delivery Based on Memorization Motivation Many greedy routing schemes perform well in dense networks Greedy routing has a small communication overhead Desirable to run Greedy
Data Communication Guaranteed Delivery Based on Memorization Motivation Many greedy routing schemes perform well in dense networks Greedy routing has a small communication overhead Desirable to run Greedy
Middle in Forwarding Movement (MFM): An efficient greedy forwarding approach in location aided routing for MANET
 Middle in Forwarding Movement (MFM): An efficient greedy forwarding approach in location aided routing for MANET 1 Prashant Dixit* Department of CSE FET, Manavrachna international institute of research
Middle in Forwarding Movement (MFM): An efficient greedy forwarding approach in location aided routing for MANET 1 Prashant Dixit* Department of CSE FET, Manavrachna international institute of research
AODV-PA: AODV with Path Accumulation
 -PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
-PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks
 A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks Stephen S. Yau, Wei Gao, and Dazhi Huang Dept. of Computer Science and Engineering Arizona State University Tempe,
A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks Stephen S. Yau, Wei Gao, and Dazhi Huang Dept. of Computer Science and Engineering Arizona State University Tempe,
Geographic Adaptive Fidelity and Geographic Energy Aware Routing in Ad Hoc Routing
 309 Geographic Adaptive Fidelity and Geographic Energy Aware Routing in Ad Hoc Routing Sinchan Roychowdhury Instrumentation Control Engineering Calcutta Institute of Engineering & Management Kolkata, India
309 Geographic Adaptive Fidelity and Geographic Energy Aware Routing in Ad Hoc Routing Sinchan Roychowdhury Instrumentation Control Engineering Calcutta Institute of Engineering & Management Kolkata, India
Zonal Rumor Routing for. Wireless Sensor Networks
 Tarun Banka Department of Electrical and Computer Engineering tarunb@engr.colostate.edu Zonal Rumor Routing for. Wireless Sensor Networks Gagan Tandon Department of Computer Science gagan@cs.colostate.edu
Tarun Banka Department of Electrical and Computer Engineering tarunb@engr.colostate.edu Zonal Rumor Routing for. Wireless Sensor Networks Gagan Tandon Department of Computer Science gagan@cs.colostate.edu
Probabilistic Mechanism to Avoid Broadcast Storm Problem in MANETS
 , pp.479-486 http://dx.doi.org/1.14257/astl.217.147.67 Probabilistic Mechanism to Avoid Broadcast Storm Problem in MANETS G Parimala 1, B Suvarna 2, N Rajeswari 3 and Venkatesulu Dondeti 4 VFSTR University,
, pp.479-486 http://dx.doi.org/1.14257/astl.217.147.67 Probabilistic Mechanism to Avoid Broadcast Storm Problem in MANETS G Parimala 1, B Suvarna 2, N Rajeswari 3 and Venkatesulu Dondeti 4 VFSTR University,
Performance of Ad-Hoc Network Routing Protocols in Different Network Sizes
 Performance of Ad-Hoc Network Routing Protocols in Different Network Sizes Sudheer Kumar 1, Akhilesh Yadav 2 Department of Computer Science and Engineering Kanpur Institute of Technology, Kanpur sudheerkr21@gmail.co
Performance of Ad-Hoc Network Routing Protocols in Different Network Sizes Sudheer Kumar 1, Akhilesh Yadav 2 Department of Computer Science and Engineering Kanpur Institute of Technology, Kanpur sudheerkr21@gmail.co
Efficient On-Demand Routing for Mobile Ad-Hoc Wireless Access Networks
 Efficient On-Demand Routing for Mobile Ad-Hoc Wireless Access Networks Joo-Han Song, Vincent Wong and Victor Leung Department of Electrical and Computer Engineering The University of British Columbia 56
Efficient On-Demand Routing for Mobile Ad-Hoc Wireless Access Networks Joo-Han Song, Vincent Wong and Victor Leung Department of Electrical and Computer Engineering The University of British Columbia 56
Impact of Node Velocity and Density on Probabilistic Flooding and its Effectiveness in MANET
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 12, December 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 12, December 2014,
Performance of New Broadcast Forwarding Criteria in MANET
 Performance of New Broadcast Forwarding Criteria in MANET Lijuan Zhu 1, Bu-Sung Lee 1, Boon-Chong Seet 2, Kai-Juan Wong 3, Genping Liu 1, Shell-Ying Huang 1, and Keok-Kee Lee 1 1 Centre for Multimedia
Performance of New Broadcast Forwarding Criteria in MANET Lijuan Zhu 1, Bu-Sung Lee 1, Boon-Chong Seet 2, Kai-Juan Wong 3, Genping Liu 1, Shell-Ying Huang 1, and Keok-Kee Lee 1 1 Centre for Multimedia
A Position-Based Connectionless Routing Algorithm for MANET and WiMAX under High Mobility and Various Node Densities
 Information Technology Journal 7 (3): 458-465, 08 ISSN 1812-5638 08 Asian Network for Scientific Information A Position-Based Connectionless Routing Algorithm for MANET and WiMAX under High Mobility and
Information Technology Journal 7 (3): 458-465, 08 ISSN 1812-5638 08 Asian Network for Scientific Information A Position-Based Connectionless Routing Algorithm for MANET and WiMAX under High Mobility and
A Simple Sink Mobility Support Algorithm for Routing Protocols in Wireless Sensor Networks
 A Simple Mobility Support Algorithm for Routing Protocols in Wireless Sensor Networks Chun-Su Park, You-Sun Kim, Kwang-Wook Lee, Seung-Kyun Kim, and Sung-Jea Ko Department of Electronics Engineering, Korea
A Simple Mobility Support Algorithm for Routing Protocols in Wireless Sensor Networks Chun-Su Park, You-Sun Kim, Kwang-Wook Lee, Seung-Kyun Kim, and Sung-Jea Ko Department of Electronics Engineering, Korea
A Proposed Routing Protocol for MANET
 International Journal of Engineering & Technology IJET-IJENS Vol: 11 No: 02 101 A Proposed Routing Protocol for MANET Mamoun Hussein Mamoun Faculty of Computer and Information Sciences Mansoura University,
International Journal of Engineering & Technology IJET-IJENS Vol: 11 No: 02 101 A Proposed Routing Protocol for MANET Mamoun Hussein Mamoun Faculty of Computer and Information Sciences Mansoura University,
BUSNet: Model and Usage of Regular Traffic Patterns in Mobile Ad Hoc Networks for Inter-Vehicular Communications
 BUSNet: Model and Usage of Regular Traffic Patterns in Mobile Ad Hoc Networks for Inter-Vehicular Communications Kai-Juan Wong, Bu-Sung Lee, Boon-Chong Seet, Genping Liu, Lijuan Zhu School of Computer
BUSNet: Model and Usage of Regular Traffic Patterns in Mobile Ad Hoc Networks for Inter-Vehicular Communications Kai-Juan Wong, Bu-Sung Lee, Boon-Chong Seet, Genping Liu, Lijuan Zhu School of Computer
Gateway Discovery Approaches Implementation and Performance Analysis in the Integrated Mobile Ad Hoc Network (MANET)-Internet Scenario
 Gateway Discovery Approaches Implementation and Performance Analysis in the Integrated Mobile Ad Hoc Network (MANET)-Internet Scenario K.Gautham 1, Nagajothi A 2 Student, Computer Science and Engineering,
Gateway Discovery Approaches Implementation and Performance Analysis in the Integrated Mobile Ad Hoc Network (MANET)-Internet Scenario K.Gautham 1, Nagajothi A 2 Student, Computer Science and Engineering,
Packet Routing using Optimal Flooding Protocol in Cluster based MANET
 IJSTE - International Journal of Science Technology & Engineering Volume 2 Issue 09 March 2016 ISSN (online): 2349-784X Packet Routing using Optimal Flooding Protocol in Cluster based MANET S.Bavani V.Aiswariya
IJSTE - International Journal of Science Technology & Engineering Volume 2 Issue 09 March 2016 ISSN (online): 2349-784X Packet Routing using Optimal Flooding Protocol in Cluster based MANET S.Bavani V.Aiswariya
Chapter 7 CONCLUSION
 97 Chapter 7 CONCLUSION 7.1. Introduction A Mobile Ad-hoc Network (MANET) could be considered as network of mobile nodes which communicate with each other without any fixed infrastructure. The nodes in
97 Chapter 7 CONCLUSION 7.1. Introduction A Mobile Ad-hoc Network (MANET) could be considered as network of mobile nodes which communicate with each other without any fixed infrastructure. The nodes in
An Approximation Algorithm for Connected Dominating Set in Ad Hoc Networks
 An Approximation Algorithm for Connected Dominating Set in Ad Hoc Networks Xiuzhen Cheng, Min Ding Department of Computer Science The George Washington University Washington, DC 20052, USA {cheng,minding}@gwu.edu
An Approximation Algorithm for Connected Dominating Set in Ad Hoc Networks Xiuzhen Cheng, Min Ding Department of Computer Science The George Washington University Washington, DC 20052, USA {cheng,minding}@gwu.edu
Performance Comparison of Scalable Location Services for Geographic Ad Hoc Routing
 Performance Comparison of Scalable Location Services for Geographic Ad Hoc Routing Saumitra M. Das, Himabindu Pucha and Y. Charlie Hu School of Electrical and Computer Engineering Purdue University West
Performance Comparison of Scalable Location Services for Geographic Ad Hoc Routing Saumitra M. Das, Himabindu Pucha and Y. Charlie Hu School of Electrical and Computer Engineering Purdue University West
A Graph-based Approach to Compute Multiple Paths in Mobile Ad Hoc Networks
 A Graph-based Approach to Compute Multiple Paths in Mobile Ad Hoc Networks Gunyoung Koh, Duyoung Oh 1 and Heekyoung Woo 2 1 School of Electrical Engineering and Computer Science Seoul National University,
A Graph-based Approach to Compute Multiple Paths in Mobile Ad Hoc Networks Gunyoung Koh, Duyoung Oh 1 and Heekyoung Woo 2 1 School of Electrical Engineering and Computer Science Seoul National University,
Performance evaluation of reactive and proactive routing protocol in IEEE ad hoc network
 Author manuscript, published in "ITCom 6 - next generation and sensor networks, Boston : United States (26)" DOI :.7/2.68625 Performance evaluation of reactive and proactive routing protocol in IEEE 82.
Author manuscript, published in "ITCom 6 - next generation and sensor networks, Boston : United States (26)" DOI :.7/2.68625 Performance evaluation of reactive and proactive routing protocol in IEEE 82.
Power-aware localized routing in wireless networks
 1 Power-aware localized routing in wireless networks Ivan Stojmenovic and Xu Lin Computer Science, SITE, University of Ottawa, Ottawa, Ontario K1N 6N5, Canada ivan@site.uottawa.ca Abstract Recently, a
1 Power-aware localized routing in wireless networks Ivan Stojmenovic and Xu Lin Computer Science, SITE, University of Ottawa, Ottawa, Ontario K1N 6N5, Canada ivan@site.uottawa.ca Abstract Recently, a
Improving Performance in Ad hoc Networks through Location based Multi Hop Forwarding
 Improving Performance in Ad hoc Networks through Location based Multi Hop Forwarding v.vallinayagi research scholar, manonmanium university tirunelveli-11 Dr.G.M.Nasira Assistant professor dept of computer
Improving Performance in Ad hoc Networks through Location based Multi Hop Forwarding v.vallinayagi research scholar, manonmanium university tirunelveli-11 Dr.G.M.Nasira Assistant professor dept of computer
Design and Implementation of a Simulator for Ad Hoc Network Routing Protocols
 Design and Implementation of a Simulator for Ad Hoc Network Routing Protocols Mudit, Sachin Chaudhary Abstract In consideration of adaptability to the environment and flexibility in protocol construction,
Design and Implementation of a Simulator for Ad Hoc Network Routing Protocols Mudit, Sachin Chaudhary Abstract In consideration of adaptability to the environment and flexibility in protocol construction,
Secure Protocol For Inter-Vehicle Communication Networks
 IVSS-005-APS-05 Secure Protocol For Inter-Vehicle Communication Networks Nader Mazen Rabadi and Syed Masud Mahmud Electrical and Computer Engineering Department, Wayne State University, Detroit, MI 480
IVSS-005-APS-05 Secure Protocol For Inter-Vehicle Communication Networks Nader Mazen Rabadi and Syed Masud Mahmud Electrical and Computer Engineering Department, Wayne State University, Detroit, MI 480
Figure 1: Ad-Hoc routing protocols.
 Performance Analysis of Routing Protocols for Wireless Ad-Hoc Networks Sukhchandan Lally and Ljiljana Trajković Simon Fraser University Vancouver, British Columbia Canada E-mail: {lally, ljilja}@sfu.ca
Performance Analysis of Routing Protocols for Wireless Ad-Hoc Networks Sukhchandan Lally and Ljiljana Trajković Simon Fraser University Vancouver, British Columbia Canada E-mail: {lally, ljilja}@sfu.ca
Scalable Position-Based Multicast for Mobile Ad-hoc Networks
 Scalable Position-Based Multicast for Mobile Ad-hoc Networks Matthias Transier, Holger Füßler, Jörg Widmer, Martin Mauve, and Wolfgang Effelsberg University of Mannheim, Institut für Informatik, 683 Mannheim,
Scalable Position-Based Multicast for Mobile Ad-hoc Networks Matthias Transier, Holger Füßler, Jörg Widmer, Martin Mauve, and Wolfgang Effelsberg University of Mannheim, Institut für Informatik, 683 Mannheim,
COMPARATIVE ANALYSIS AND STUDY OF DIFFERENT QOS PARAMETERS OF WIRELESS AD-HOC NETWORK
 COMPARATIVE ANALYSIS AND STUDY OF DIFFERENT QOS PARAMETERS OF WIRELESS AD-HOC NETWORK Nalin Gahlaut 1, Jaya sharma 2, Pankaj Kumar 3, Kaushal Kumar 4 1 Doctoral Candidate, Uttarakhand Technical University,
COMPARATIVE ANALYSIS AND STUDY OF DIFFERENT QOS PARAMETERS OF WIRELESS AD-HOC NETWORK Nalin Gahlaut 1, Jaya sharma 2, Pankaj Kumar 3, Kaushal Kumar 4 1 Doctoral Candidate, Uttarakhand Technical University,
Routing in Ad Hoc Wireless Networks PROF. MICHAEL TSAI / DR. KATE LIN 2014/05/14
 Routing in Ad Hoc Wireless Networks PROF. MICHAEL TSAI / DR. KATE LIN 2014/05/14 Routing Algorithms Link- State algorithm Each node maintains a view of the whole network topology Find the shortest path
Routing in Ad Hoc Wireless Networks PROF. MICHAEL TSAI / DR. KATE LIN 2014/05/14 Routing Algorithms Link- State algorithm Each node maintains a view of the whole network topology Find the shortest path
QoS Routing By Ad-Hoc on Demand Vector Routing Protocol for MANET
 2011 International Conference on Information and Network Technology IPCSIT vol.4 (2011) (2011) IACSIT Press, Singapore QoS Routing By Ad-Hoc on Demand Vector Routing Protocol for MANET Ashwini V. Biradar
2011 International Conference on Information and Network Technology IPCSIT vol.4 (2011) (2011) IACSIT Press, Singapore QoS Routing By Ad-Hoc on Demand Vector Routing Protocol for MANET Ashwini V. Biradar
Optimized Location Aided Routing Protocol using Greedy Forwarding Approach in MANET
 Volume-4, Issue-4, August-2014, ISSN No.: 2250-0758 International Journal of Engineering and Management Research Available at: www.ijemr.net Page Number: 110-116 Optimized Location Aided Routing Protocol
Volume-4, Issue-4, August-2014, ISSN No.: 2250-0758 International Journal of Engineering and Management Research Available at: www.ijemr.net Page Number: 110-116 Optimized Location Aided Routing Protocol
Efficient and Robust Geocasting Protocols for Sensor Networks
 Efficient and Robust Geocasting Protocols for Sensor Networks Karim Seada, Ahmed Helmy Electrical Engineering Department, University of Southern California {seada, helmy}@usc.edu Abstract- Geocasting is
Efficient and Robust Geocasting Protocols for Sensor Networks Karim Seada, Ahmed Helmy Electrical Engineering Department, University of Southern California {seada, helmy}@usc.edu Abstract- Geocasting is
A Routing Protocol for Utilizing Multiple Channels in Multi-Hop Wireless Networks with a Single Transceiver
 1 A Routing Protocol for Utilizing Multiple Channels in Multi-Hop Wireless Networks with a Single Transceiver Jungmin So Dept. of Computer Science, and Coordinated Science Laboratory University of Illinois
1 A Routing Protocol for Utilizing Multiple Channels in Multi-Hop Wireless Networks with a Single Transceiver Jungmin So Dept. of Computer Science, and Coordinated Science Laboratory University of Illinois
A SURVEY OF ROUTING PROTOCOLS IN MOBILE AD HOC NETWORKS
 Journal homepage: www.mjret.in ISSN:2348-6953 A SURVEY OF ROUTING PROTOCOLS IN MOBILE AD HOC NETWORKS Ms. Amruta Kodole 1, Prof. P. M. Agarkar 2 Computer Engineering Dr. D. Y. Patil School Of Engineering
Journal homepage: www.mjret.in ISSN:2348-6953 A SURVEY OF ROUTING PROTOCOLS IN MOBILE AD HOC NETWORKS Ms. Amruta Kodole 1, Prof. P. M. Agarkar 2 Computer Engineering Dr. D. Y. Patil School Of Engineering
Constructing Connected Dominating Sets with Bounded Diameters in Wireless Networks
 Constructing Connected Dominating Sets with Bounded Diameters in Wireless Networks Yingshu Li Department of Computer Science Georgia State University Atlanta, GA 30303 yli@cs.gsu.edu Donghyun Kim Feng
Constructing Connected Dominating Sets with Bounded Diameters in Wireless Networks Yingshu Li Department of Computer Science Georgia State University Atlanta, GA 30303 yli@cs.gsu.edu Donghyun Kim Feng
Rumor Routing Algorithm
 Aleksi.Ahtiainen@hut.fi T-79.194 Seminar on Theoretical Computer Science Feb 9 2005 Contents Introduction The Algorithm Research Results Future Work Criticism Conclusions Introduction is described in paper:
Aleksi.Ahtiainen@hut.fi T-79.194 Seminar on Theoretical Computer Science Feb 9 2005 Contents Introduction The Algorithm Research Results Future Work Criticism Conclusions Introduction is described in paper:
A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET
 ISSN: 2278 1323 All Rights Reserved 2016 IJARCET 296 A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET Dr. R. Shanmugavadivu 1, B. Chitra 2 1 Assistant Professor, Department of Computer
ISSN: 2278 1323 All Rights Reserved 2016 IJARCET 296 A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET Dr. R. Shanmugavadivu 1, B. Chitra 2 1 Assistant Professor, Department of Computer
Evaluation of Cartesian-based Routing Metrics for Wireless Sensor Networks
 Evaluation of Cartesian-based Routing Metrics for Wireless Sensor Networks Ayad Salhieh Department of Electrical and Computer Engineering Wayne State University Detroit, MI 48202 ai4874@wayne.edu Loren
Evaluation of Cartesian-based Routing Metrics for Wireless Sensor Networks Ayad Salhieh Department of Electrical and Computer Engineering Wayne State University Detroit, MI 48202 ai4874@wayne.edu Loren
Power-aware localized routing in wireless networks
 1 Power-aware localized routing in wireless networks Ivan Stojmenovic and Xu Lin Computer Science, SITE, University of Ottawa, Ottawa, Ontario K1N 6N5, Canada ivan@site.uottawa.ca Abstract We discuss routing
1 Power-aware localized routing in wireless networks Ivan Stojmenovic and Xu Lin Computer Science, SITE, University of Ottawa, Ottawa, Ontario K1N 6N5, Canada ivan@site.uottawa.ca Abstract We discuss routing
EZR: Enhanced Zone Based Routing In Manet
 EZR: Enhanced Zone Based Routing In Manet Bency Wilson 1, Geethu Bastian 2, Vinitha Ann Regi 3, Arun Soman 4 Department of Information Technology, Rajagiri School of Engineering and Technology, Rajagiri
EZR: Enhanced Zone Based Routing In Manet Bency Wilson 1, Geethu Bastian 2, Vinitha Ann Regi 3, Arun Soman 4 Department of Information Technology, Rajagiri School of Engineering and Technology, Rajagiri
Beaconless Position Based Routing with Guaranteed Delivery for Wireless Ad-Hoc and Sensor Networks
 Beaconless Position Based Routing with Guaranteed Delivery for Wireless Ad-Hoc and Sensor Networks Mohit Chawla 1, Nishith Goel 2, Kalai Kalaichelvan 3, Amiya Nayak 4, and Ivan Stojmenovic 4 1 IIT Guwahati,
Beaconless Position Based Routing with Guaranteed Delivery for Wireless Ad-Hoc and Sensor Networks Mohit Chawla 1, Nishith Goel 2, Kalai Kalaichelvan 3, Amiya Nayak 4, and Ivan Stojmenovic 4 1 IIT Guwahati,
Performance Comparison of Ad Hoc Routing Protocols over IEEE DCF and TDMA MAC Layer Protocols
 Performance Comparison of Ad Hoc Routing Protocols over IEEE 82.11 DCF and TDMA MAC Layer Protocols Govind. P. Gupta Computer Science Department R.K.G.I.T, Ghaziabad (India) er_gpgupta@yahoo.com A. K.
Performance Comparison of Ad Hoc Routing Protocols over IEEE 82.11 DCF and TDMA MAC Layer Protocols Govind. P. Gupta Computer Science Department R.K.G.I.T, Ghaziabad (India) er_gpgupta@yahoo.com A. K.
Exploiting the Synergy between Peer-to-Peer and Mobile Ad Hoc Networks
 Exploiting the Synergy between Peer-to-Peer and Mobile Ad Hoc Networks Y. Charlie Hu, Saumitra M. Das, and Himabindu Pucha Purdue University West Lafayette, IN 47907 {ychu, smdas, hpucha}@purdue.edu Abstract
Exploiting the Synergy between Peer-to-Peer and Mobile Ad Hoc Networks Y. Charlie Hu, Saumitra M. Das, and Himabindu Pucha Purdue University West Lafayette, IN 47907 {ychu, smdas, hpucha}@purdue.edu Abstract
A Study of Bellman-Ford, DSR and WRP Routing Protocols with Respect to Performance Parameters for Different Number of Nodes
 A Study of Bellman-Ford, DSR and WRP Routing Protocols with Respect to Performance Parameters for Different Number of Nodes Ruchi Khandelwal 1 & Akhilesh Kosta 2 Department of Computer Science and Engineering
A Study of Bellman-Ford, DSR and WRP Routing Protocols with Respect to Performance Parameters for Different Number of Nodes Ruchi Khandelwal 1 & Akhilesh Kosta 2 Department of Computer Science and Engineering
Cache Timeout Strategies for on-demand Routing in MANETs
 1 Cache Timeout Strategies for on-demand Routing in MANETs Sanlin Xu Kim Blackmore Haley Jones Department of Engineering, Australian National University, ACT 0200 {Sanlin.Xu, Kim.Blackmore, Haley.Jones}@anu.edu.au
1 Cache Timeout Strategies for on-demand Routing in MANETs Sanlin Xu Kim Blackmore Haley Jones Department of Engineering, Australian National University, ACT 0200 {Sanlin.Xu, Kim.Blackmore, Haley.Jones}@anu.edu.au
Multicasting in Ad-Hoc Networks: Comparing MAODV and ODMRP
 Multicasting in Ad-Hoc Networks: Comparing MAODV and ODMRP Thomas Kunz and Ed Cheng Carleton University tkunz@sce.carleton.ca Abstract. Multicasting can efficiently support a variety of applications that
Multicasting in Ad-Hoc Networks: Comparing MAODV and ODMRP Thomas Kunz and Ed Cheng Carleton University tkunz@sce.carleton.ca Abstract. Multicasting can efficiently support a variety of applications that
On Fault Tolerant Ad Hoc Network Design
 On Fault Tolerant Ad Hoc Network Design Wassim El-Hajj College of Information Technology UAE University United Arab Emirates welhajj@uaeu.ac.ae Hazem Hajj Faculty of Engineering and Architecture American
On Fault Tolerant Ad Hoc Network Design Wassim El-Hajj College of Information Technology UAE University United Arab Emirates welhajj@uaeu.ac.ae Hazem Hajj Faculty of Engineering and Architecture American
A Real-Time Directed Routing Protocol Based on Projection of Convex Holes on Underwater Acoustic Networks
 I.J. Wireless and Microwave Technologies, 01,, 65-73 Published Online April 01 in MECS (http://www.mecs-press.net) DOI: 10.5815/ijwmt.01.0.10 Available online at http://www.mecs-press.net/ijwmt A Real-Time
I.J. Wireless and Microwave Technologies, 01,, 65-73 Published Online April 01 in MECS (http://www.mecs-press.net) DOI: 10.5815/ijwmt.01.0.10 Available online at http://www.mecs-press.net/ijwmt A Real-Time
Efficient On-Demand Routing for Mobile Ad-Hoc Wireless Access Networks
 Efficient On-Demand Routing for Mobile Ad-Hoc Wireless Access Networks Joo-Han Song, Vincent W. S. Wong and Victor C. M. Leung Department of Electrical and Computer Engineering The University of British
Efficient On-Demand Routing for Mobile Ad-Hoc Wireless Access Networks Joo-Han Song, Vincent W. S. Wong and Victor C. M. Leung Department of Electrical and Computer Engineering The University of British
Poonam kori et al. / International Journal on Computer Science and Engineering (IJCSE)
 An Effect of Route Caching Scheme in DSR for Vehicular Adhoc Networks Poonam kori, Dr. Sanjeev Sharma School Of Information Technology, RGPV BHOPAL, INDIA E-mail: Poonam.kori@gmail.com Abstract - Routing
An Effect of Route Caching Scheme in DSR for Vehicular Adhoc Networks Poonam kori, Dr. Sanjeev Sharma School Of Information Technology, RGPV BHOPAL, INDIA E-mail: Poonam.kori@gmail.com Abstract - Routing
Survey on Location Based Routing Protocols in MANET
 Survey on Location Based Routing Protocols in MANET Vivek Nikam, Prof. G.T. Chavan Sinhgad College of engineering, University of Pune Abstract- Due to the infrastructure less and dynamic nature of mobile
Survey on Location Based Routing Protocols in MANET Vivek Nikam, Prof. G.T. Chavan Sinhgad College of engineering, University of Pune Abstract- Due to the infrastructure less and dynamic nature of mobile
Model and Algorithms for the Density, Coverage and Connectivity Control Problem in Flat WSNs
 Model and Algorithms for the Density, Coverage and Connectivity Control Problem in Flat WSNs Flávio V. C. Martins, cruzeiro@dcc.ufmg.br Frederico P. Quintão, fred@dcc.ufmg.br Fabíola G. Nakamura fgnaka@dcc.ufmg.br,fabiola@dcc.ufam.edu.br
Model and Algorithms for the Density, Coverage and Connectivity Control Problem in Flat WSNs Flávio V. C. Martins, cruzeiro@dcc.ufmg.br Frederico P. Quintão, fred@dcc.ufmg.br Fabíola G. Nakamura fgnaka@dcc.ufmg.br,fabiola@dcc.ufam.edu.br
Data gathering using mobile agents for reducing traffic in dense mobile wireless sensor networks
 Mobile Information Systems 9 (23) 295 34 295 DOI.3233/MIS-364 IOS Press Data gathering using mobile agents for reducing traffic in dense mobile wireless sensor networks Keisuke Goto, Yuya Sasaki, Takahiro
Mobile Information Systems 9 (23) 295 34 295 DOI.3233/MIS-364 IOS Press Data gathering using mobile agents for reducing traffic in dense mobile wireless sensor networks Keisuke Goto, Yuya Sasaki, Takahiro
IMPORTANCE OF RELAY NODE SET FRAMEWORK FOR MANET COMMUNICATION ENVIRONMENT
 IMPORTANCE OF RELAY NODE SET FRAMEWORK FOR MANET COMMUNICATION ENVIRONMENT Manoj Kumar Khinchi 1, Dr. Bharat Bhushan 2 1 Research Scholar of Department of computer science, Singhania University, Rajasthan,
IMPORTANCE OF RELAY NODE SET FRAMEWORK FOR MANET COMMUNICATION ENVIRONMENT Manoj Kumar Khinchi 1, Dr. Bharat Bhushan 2 1 Research Scholar of Department of computer science, Singhania University, Rajasthan,
Example of TORA operations. From last time, this was the DAG that was built. A was the source and X was the destination.
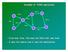 Example of TORA operations A Link 2 D Link 6 Y Link 1 Link 3 C Link 4 Link 8 B Link 5 E Link 7 X From last time, this was the DAG that was built. A was the source and X was the destination. Link 1 A B
Example of TORA operations A Link 2 D Link 6 Y Link 1 Link 3 C Link 4 Link 8 B Link 5 E Link 7 X From last time, this was the DAG that was built. A was the source and X was the destination. Link 1 A B
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols. Broch et al Presented by Brian Card
 A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols Broch et al Presented by Brian Card 1 Outline Introduction NS enhancements Protocols: DSDV TORA DRS AODV Evaluation Conclusions
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols Broch et al Presented by Brian Card 1 Outline Introduction NS enhancements Protocols: DSDV TORA DRS AODV Evaluation Conclusions
QoS Routing for Heterogeneous Mobile Ad Hoc Networks
 QoS Routing for Heterogeneous Mobile Ad Hoc Networks Mohammed Abdul Waheed 1, Dr. K Karibasappa 2 1 Research Scholar, Singhania University, Pacheri Bari Dist. Jhunjhunu, Rajasthan, India. Mohdabdul.waheed@mission10x.com,
QoS Routing for Heterogeneous Mobile Ad Hoc Networks Mohammed Abdul Waheed 1, Dr. K Karibasappa 2 1 Research Scholar, Singhania University, Pacheri Bari Dist. Jhunjhunu, Rajasthan, India. Mohdabdul.waheed@mission10x.com,
CSMA based Medium Access Control for Wireless Sensor Network
 CSMA based Medium Access Control for Wireless Sensor Network H. Hoang, Halmstad University Abstract Wireless sensor networks bring many challenges on implementation of Medium Access Control protocols because
CSMA based Medium Access Control for Wireless Sensor Network H. Hoang, Halmstad University Abstract Wireless sensor networks bring many challenges on implementation of Medium Access Control protocols because
Computation of Multiple Node Disjoint Paths
 Chapter 5 Computation of Multiple Node Disjoint Paths 5.1 Introduction In recent years, on demand routing protocols have attained more attention in mobile Ad Hoc networks as compared to other routing schemes
Chapter 5 Computation of Multiple Node Disjoint Paths 5.1 Introduction In recent years, on demand routing protocols have attained more attention in mobile Ad Hoc networks as compared to other routing schemes
Replica Distribution Scheme for Location-Dependent Data in Vehicular Ad Hoc Networks using a Small Number of Fixed Nodes
 Replica Distribution Scheme for Location-Dependent Data in Vehicular d Hoc Networks using a Small Number of Fixed Nodes Junichiro Okamoto and Susumu Ishihara Graduate School of Engineering, Shizuoka University,
Replica Distribution Scheme for Location-Dependent Data in Vehicular d Hoc Networks using a Small Number of Fixed Nodes Junichiro Okamoto and Susumu Ishihara Graduate School of Engineering, Shizuoka University,
Energy Aware and Anonymous Location Based Efficient Routing Protocol
 Energy Aware and Anonymous Location Based Efficient Routing Protocol N.Nivethitha 1, G.Balaji 2 1 PG student, 2 Asst.Professor Department of Electronics and Communication Engineering Angel College of Engineering
Energy Aware and Anonymous Location Based Efficient Routing Protocol N.Nivethitha 1, G.Balaji 2 1 PG student, 2 Asst.Professor Department of Electronics and Communication Engineering Angel College of Engineering
An efficient implementation of the greedy forwarding strategy
 An efficient implementation of the greedy forwarding strategy Hannes Stratil Embedded Computing Systems Group E182/2 Technische Universität Wien Treitlstraße 3 A-1040 Vienna Email: hannes@ecs.tuwien.ac.at
An efficient implementation of the greedy forwarding strategy Hannes Stratil Embedded Computing Systems Group E182/2 Technische Universität Wien Treitlstraße 3 A-1040 Vienna Email: hannes@ecs.tuwien.ac.at
Performance Comparison of MANETs Routing Protocols for Dense and Sparse Topology
 2012 International Conference on Information and Computer Networks (ICICN 2012) IPCSIT vol. 27 (2012) (2012) IACSIT Press, Singapore Performance Comparison of MANETs Routing Protocols for Dense and Sparse
2012 International Conference on Information and Computer Networks (ICICN 2012) IPCSIT vol. 27 (2012) (2012) IACSIT Press, Singapore Performance Comparison of MANETs Routing Protocols for Dense and Sparse
Compasses, Faces, and Butterflies: Route Discovery in Ad-Hoc Networks
 Evangelos Kranakis, School of Computer Science, Carleton University, Ottawa 1 Compasses, Faces, and Butterflies: Route Discovery in Ad-Hoc Networks By Evangelos Kranakis School of Computer Science Carleton
Evangelos Kranakis, School of Computer Science, Carleton University, Ottawa 1 Compasses, Faces, and Butterflies: Route Discovery in Ad-Hoc Networks By Evangelos Kranakis School of Computer Science Carleton
2. LITERATURE REVIEW. Performance Evaluation of Ad Hoc Networking Protocol with QoS (Quality of Service)
 2. LITERATURE REVIEW I have surveyed many of the papers for the current work carried out by most of the researchers. The abstract, methodology, parameters focused for performance evaluation of Ad-hoc routing
2. LITERATURE REVIEW I have surveyed many of the papers for the current work carried out by most of the researchers. The abstract, methodology, parameters focused for performance evaluation of Ad-hoc routing
Routing Protocols in Mobile Ad-Hoc Network
 International Journal of Computer Science & Management Studies, Vol. 12, Issue 02, April 2012 Protocols in Mobile Ad-Hoc Network Sachin Minocha M. Tech Student, Vaish College of Engineering, Rohtak, Haryana
International Journal of Computer Science & Management Studies, Vol. 12, Issue 02, April 2012 Protocols in Mobile Ad-Hoc Network Sachin Minocha M. Tech Student, Vaish College of Engineering, Rohtak, Haryana
Overhead Analysis of Reactive Shortest Single and Multi-path Routing Mechanism with Load Balance in MANET
 www.ijcsi.org https://doi.org/10.20943/01201605.102107 102 Overhead Analysis of Reactive Shortest Single and Multi-path Routing Mechanism with Load Balance in MANET K.MARIYAPPAN 1, Dr.M.KARNAN 2 1 Assistant
www.ijcsi.org https://doi.org/10.20943/01201605.102107 102 Overhead Analysis of Reactive Shortest Single and Multi-path Routing Mechanism with Load Balance in MANET K.MARIYAPPAN 1, Dr.M.KARNAN 2 1 Assistant
Mobile Advanced Networks. Position-based routing geometric, geographic, location-based. Navid Nikaein Mobile Communication Department
 Mobile Advanced Networks Position-based routing geometric, geographic, location-based Navid Nikaein Mobile Communication Department Navid Nikaein 2010 1 Reminder In topology-based routing, each node has
Mobile Advanced Networks Position-based routing geometric, geographic, location-based Navid Nikaein Mobile Communication Department Navid Nikaein 2010 1 Reminder In topology-based routing, each node has
A Congestion Controlled Multipath Routing Algorithm Based On Path Survivability Factor
 ABSTRACT A Congestion Controlled Multipath Routing Algorithm Based On Path Survivability Factor A.K. Daniel 1, Shishir Dwivedi 2, Tarun Verma 3, Pankaj Kumar Dubey 4 Department of Computer Science and
ABSTRACT A Congestion Controlled Multipath Routing Algorithm Based On Path Survivability Factor A.K. Daniel 1, Shishir Dwivedi 2, Tarun Verma 3, Pankaj Kumar Dubey 4 Department of Computer Science and
A Reliable Route Selection Algorithm Using Global Positioning Systems in Mobile Ad-hoc Networks
 A Reliable Route Selection Algorithm Using Global Positioning Systems in Mobile Ad-hoc Networks Won-Ik Kim Radio Performance Analysis Section Electronics & Telecommunications Research Institute 161 Kajong-dong,
A Reliable Route Selection Algorithm Using Global Positioning Systems in Mobile Ad-hoc Networks Won-Ik Kim Radio Performance Analysis Section Electronics & Telecommunications Research Institute 161 Kajong-dong,
Chapter 4 Routing in Wireless Sensor Networks
 Chapter 4 Routing in Wireless Sensor Networks Hannes Frey, Stefan Rührup, and Ivan Stojmenović Abstract Wireless sensor networks are formed by small sensor nodes communicating over wireless links without
Chapter 4 Routing in Wireless Sensor Networks Hannes Frey, Stefan Rührup, and Ivan Stojmenović Abstract Wireless sensor networks are formed by small sensor nodes communicating over wireless links without
Enhancing the Performance of Mobile Ad Hoc Networks with the Aid of Internet Gateways 1
 Enhancing the Performance of Mobile Ad Hoc Networks with the Aid of Internet Gateways 1 Shiv Mehra and Chansu Yu Department of Electrical and Computer Engineering Cleveland State University E-mail: {s.mehra,c.yu91}@csuohio.edu
Enhancing the Performance of Mobile Ad Hoc Networks with the Aid of Internet Gateways 1 Shiv Mehra and Chansu Yu Department of Electrical and Computer Engineering Cleveland State University E-mail: {s.mehra,c.yu91}@csuohio.edu
ROUTING IN MANETS USING ACO WITH MOBILITY ASSISTANCE
 ISSN : 0973-7391 Vol. 3, No. 1, January-June 2012, pp. 97-101 ROUTING IN MANETS USING ACO WITH MOBILITY ASSISTANCE Praveen Biradar 1, and Sowmya K.S 2 1,2 Dept. Of Computer Science and Engineering, Dayananda
ISSN : 0973-7391 Vol. 3, No. 1, January-June 2012, pp. 97-101 ROUTING IN MANETS USING ACO WITH MOBILITY ASSISTANCE Praveen Biradar 1, and Sowmya K.S 2 1,2 Dept. Of Computer Science and Engineering, Dayananda
Analysis of GPS and Zone Based Vehicular Routing on Urban City Roads
 Analysis of GPS and Zone Based Vehicular Routing on Urban City Roads Aye Zarchi Minn 1, May Zin Oo 2, Mazliza Othman 3 1,2 Department of Information Technology, Mandalay Technological University, Myanmar
Analysis of GPS and Zone Based Vehicular Routing on Urban City Roads Aye Zarchi Minn 1, May Zin Oo 2, Mazliza Othman 3 1,2 Department of Information Technology, Mandalay Technological University, Myanmar
A Comparative study of On-Demand Data Delivery with Tables Driven and On-Demand Protocols for Mobile Ad-Hoc Network
 A Comparative study of On-Demand Data Delivery with Tables Driven and On-Demand Protocols for Mobile Ad-Hoc Network Humayun Bakht Research Fellow, London School of Commerce, United Kingdom humayunbakht@yahoo.co.uk
A Comparative study of On-Demand Data Delivery with Tables Driven and On-Demand Protocols for Mobile Ad-Hoc Network Humayun Bakht Research Fellow, London School of Commerce, United Kingdom humayunbakht@yahoo.co.uk
AWERProcedia Information Technology & Computer Science
 AWERProcedia Information Technology & Computer Science Vol 03 (2013) 1424-1429 3 rd World Conference on Information Technology (WCIT-2012) Comparison of routing protocols in mobile ad-hoc wireless networks
AWERProcedia Information Technology & Computer Science Vol 03 (2013) 1424-1429 3 rd World Conference on Information Technology (WCIT-2012) Comparison of routing protocols in mobile ad-hoc wireless networks
DYNAMIC DATA ROUTING IN MANET USING POSITION BASED OPPORTUNISTIC ROUTING PROTOCOL
 INTERNATIONAL JOURNAL OF RESEARCH IN COMPUTER APPLICATIONS AND ROBOTICS ISSN 2320-7345 DYNAMIC DATA ROUTING IN MANET USING POSITION BASED OPPORTUNISTIC ROUTING PROTOCOL P. Kalaivani 1, G. Sathya 2, N.
INTERNATIONAL JOURNAL OF RESEARCH IN COMPUTER APPLICATIONS AND ROBOTICS ISSN 2320-7345 DYNAMIC DATA ROUTING IN MANET USING POSITION BASED OPPORTUNISTIC ROUTING PROTOCOL P. Kalaivani 1, G. Sathya 2, N.
Improved Performance of Mobile Adhoc Network through Efficient Broadcasting Technique
 Improved Performance of Mobile Adhoc Network through Efficient Broadcasting Technique Vijay J Parmar Department of Computer Engineering,Sarvajanic College of Engineering and Technology Surat, Gujrat (India),E-mail
Improved Performance of Mobile Adhoc Network through Efficient Broadcasting Technique Vijay J Parmar Department of Computer Engineering,Sarvajanic College of Engineering and Technology Surat, Gujrat (India),E-mail
Performance Evaluation of Routing Protocols for MAC Layer Models
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 10, Issue 4 (Mar. - Apr. 2013), PP 71-77 Performance Evaluation of Routing Protocols for MAC Layer Models Somya
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 10, Issue 4 (Mar. - Apr. 2013), PP 71-77 Performance Evaluation of Routing Protocols for MAC Layer Models Somya
ON THE PROBABILITY OF K-CONNECTIVITY IN WIRELESS AD HOC NETWORKS UNDER DIFFERENT MOBILITY MODELS
 ON THE PROBABILITY OF K-CONNECTIVITY IN WIRELESS AD HOC NETWORKS UNDER DIFFERENT MOBILITY MODELS Natarajan Meghanathan 1 and Sireesha Gorla 1, Jackson State University, 1400 Lynch St, Jackson, MS, USA
ON THE PROBABILITY OF K-CONNECTIVITY IN WIRELESS AD HOC NETWORKS UNDER DIFFERENT MOBILITY MODELS Natarajan Meghanathan 1 and Sireesha Gorla 1, Jackson State University, 1400 Lynch St, Jackson, MS, USA
Hybrid gateway advertisement scheme for connecting mobile ad hoc networks to the Internet
 * gateway advertisement scheme for connecting mobile ad hoc networks to the Internet Jeongkeun Lee (), Dongkyun Kim (2), J.J.Garcia-Luna-Aceves (3), Yanghee Choi (), Jihyuk Choi (4), Sangwoo Nam (4) ()
* gateway advertisement scheme for connecting mobile ad hoc networks to the Internet Jeongkeun Lee (), Dongkyun Kim (2), J.J.Garcia-Luna-Aceves (3), Yanghee Choi (), Jihyuk Choi (4), Sangwoo Nam (4) ()
Architecture of EHARP Routing Protocols in Ad Hoc Wireless Networks
 2009 International Conference on Intelligent Networking and Collaborative Systems Architecture of EHARP Routing Protocols in Ad Hoc Wireless Networks Saud Al otaibi Software Technology Research Laboratory
2009 International Conference on Intelligent Networking and Collaborative Systems Architecture of EHARP Routing Protocols in Ad Hoc Wireless Networks Saud Al otaibi Software Technology Research Laboratory
3. Evaluation of Selected Tree and Mesh based Routing Protocols
 33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
1 Multipath Node-Disjoint Routing with Backup List Based on the AODV Protocol
 1 Multipath Node-Disjoint Routing with Backup List Based on the AODV Protocol Vahid Zangeneh i and Shahriar Mohammadi ii * ABSTRACT In recent years, routing has been the most focused area in ad hoc networks
1 Multipath Node-Disjoint Routing with Backup List Based on the AODV Protocol Vahid Zangeneh i and Shahriar Mohammadi ii * ABSTRACT In recent years, routing has been the most focused area in ad hoc networks
Performance Analysis of Three Routing Protocols for Varying MANET Size
 Proceedings of the International MultiConference of Engineers and Computer Scientists 8 Vol II IMECS 8, 9- March, 8, Hong Kong Performance Analysis of Three Routing Protocols for Varying MANET Size N Vetrivelan,
Proceedings of the International MultiConference of Engineers and Computer Scientists 8 Vol II IMECS 8, 9- March, 8, Hong Kong Performance Analysis of Three Routing Protocols for Varying MANET Size N Vetrivelan,
Table of Contents. 1. Introduction. 2. Geographic Routing. 2.1 Routing Mechanisms. 2.2 Destination Location. 2.3 Location Inaccuracy. 3.
 Geographic Protocols in Sensor Networks Karim Seada, Ahmed Helmy Electrical Engineering Department, University of Southern California {seada, helmy}@usc.edu Table of Contents 1. Introduction 2. Geographic
Geographic Protocols in Sensor Networks Karim Seada, Ahmed Helmy Electrical Engineering Department, University of Southern California {seada, helmy}@usc.edu Table of Contents 1. Introduction 2. Geographic
Content. 1. Introduction. 2. The Ad-hoc On-Demand Distance Vector Algorithm. 3. Simulation and Results. 4. Future Work. 5.
 Rahem Abri Content 1. Introduction 2. The Ad-hoc On-Demand Distance Vector Algorithm Path Discovery Reverse Path Setup Forward Path Setup Route Table Management Path Management Local Connectivity Management
Rahem Abri Content 1. Introduction 2. The Ad-hoc On-Demand Distance Vector Algorithm Path Discovery Reverse Path Setup Forward Path Setup Route Table Management Path Management Local Connectivity Management
GATEWAY MULTIPOINT RELAYS AN MPR-BASED BROADCAST ALGORITHM FOR AD HOC NETWORKS. Ou Liang, Y. Ahmet Şekercioğlu, Nallasamy Mani
 GATEWAY MULTIPOINT RELAYS AN MPR-BASED BROADCAST ALGORITHM FOR AD HOC NETWORKS Ou Liang, Y. Ahmet Şekercioğlu, Nallasamy Mani Centre for Telecommunication and Information Engineering Monash University,
GATEWAY MULTIPOINT RELAYS AN MPR-BASED BROADCAST ALGORITHM FOR AD HOC NETWORKS Ou Liang, Y. Ahmet Şekercioğlu, Nallasamy Mani Centre for Telecommunication and Information Engineering Monash University,
BGR: Blind Geographic Routing for Sensor Networks
 BGR: Blind Geographic Routing for Sensor Networks Matthias Witt 1 and Volker Turau 1 1 Department of Telematics, Hamburg University of Technology, Hamburg, Germany {matthias.witt,turau}@tuhh.de Abstract
BGR: Blind Geographic Routing for Sensor Networks Matthias Witt 1 and Volker Turau 1 1 Department of Telematics, Hamburg University of Technology, Hamburg, Germany {matthias.witt,turau}@tuhh.de Abstract
SLALoM: A Scalable Location Management Scheme for Large Mobile Ad-hoc Networks
 SLALoM A Scalable Location Management Scheme for Large Mobile Ad-hoc Networks Christine T. Cheng *, Howard L. Lemberg, Sumesh J. Philip, Eric van den Berg and Tao Zhang * Institute for Math & its Applications,
SLALoM A Scalable Location Management Scheme for Large Mobile Ad-hoc Networks Christine T. Cheng *, Howard L. Lemberg, Sumesh J. Philip, Eric van den Berg and Tao Zhang * Institute for Math & its Applications,
Ad Hoc Routing Protocols and Issues
 Ad Hoc Routing Protocols and Issues Stefano Basagni ECE Dept Northeastern University Boston, Jan 2003 Ad hoc (AD-HAHK or AD-HOKE)-Adjective a) Concerned with a particular end or purpose, and b) formed
Ad Hoc Routing Protocols and Issues Stefano Basagni ECE Dept Northeastern University Boston, Jan 2003 Ad hoc (AD-HAHK or AD-HOKE)-Adjective a) Concerned with a particular end or purpose, and b) formed
Selfish Scheduler for Packet Scheduling Based on Packet Weighted Energy Drain Rate in Manets
 Journal of Computer Science, 9 (1): 37-42, 2013 ISSN 1549-3636 2013 Lakshmi and Radha, This open access article is distributed under a Creative Commons Attribution (CC-BY) 3.0 license doi:10.3844/jcssp.2013.37.42
Journal of Computer Science, 9 (1): 37-42, 2013 ISSN 1549-3636 2013 Lakshmi and Radha, This open access article is distributed under a Creative Commons Attribution (CC-BY) 3.0 license doi:10.3844/jcssp.2013.37.42
CS 229 Final Report: Location Based Adaptive Routing Protocol(LBAR) using Reinforcement Learning
 CS 229 Final Report: Location Based Adaptive Routing Protocol(LBAR) using Reinforcement Learning By: Eunjoon Cho and Kevin Wong Abstract In this paper we present an algorithm for a location based adaptive
CS 229 Final Report: Location Based Adaptive Routing Protocol(LBAR) using Reinforcement Learning By: Eunjoon Cho and Kevin Wong Abstract In this paper we present an algorithm for a location based adaptive
Factors Affecting the Performance of Ad Hoc Networks
 Factors Affecting the Performance of Ad Hoc Networks Dmitri D. Perkins, Herman D. Hughes, and Charles B. Owen Department of Computer Science and Engineering Michigan State University East Lansing, MI 88-6
Factors Affecting the Performance of Ad Hoc Networks Dmitri D. Perkins, Herman D. Hughes, and Charles B. Owen Department of Computer Science and Engineering Michigan State University East Lansing, MI 88-6
Location Services for Ad-Hoc Networks. Rich Goyette 11 Nov 05
 Location Services for Ad-Hoc Networks Rich Goyette 11 Nov 05 rgoyette@forces.gc.ca Outline Introduction Problem Characteristics of Location Services Solution Space Review Overview of Selected Approaches
Location Services for Ad-Hoc Networks Rich Goyette 11 Nov 05 rgoyette@forces.gc.ca Outline Introduction Problem Characteristics of Location Services Solution Space Review Overview of Selected Approaches
