STATE OF NORTH CAROLINA
|
|
|
- Gyles Baldwin
- 6 years ago
- Views:
Transcription
1 STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS OF THE NORTH CAROLINA COMMUNITY COLLEGE SYSTEM RALEIGH, NORTH CAROLINA JUNE 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR
2 AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS OF THE NORTH CAROLINA COMMUNITY COLLEGE SYSTEMS RALEIGH, NORTH CAROLINA JUNE 2004
3 STATE OF NORTH CAROLINA Office of the State Auditor Ralph Campbell, Jr. State Auditor 2 S. Salisbury Street Mail Service Center Raleigh, NC Telephone: (919) Fax: (919) Internet AUDITOR S TRANSMITTAL The Honorable Michael F. Easley, Governor Members of the North Carolina General Assembly The Board of Directors of the North Carolina Community College System Mr. Martin Lancaster, President Ladies and Gentlemen: We have completed our information systems (IS) audit of the North Carolina Community College System (NCCCS), which is comprised of the North Carolina Community College Systems Office (Systems Office), 58 Community Colleges, and the NC Center for Applied Textile Technology (Center). The audit was conducted in accordance with Government Auditing Standards and Information Systems Audit Standards. This report represents a summary of the general results of our audits. A separate audit report containing the conditions found and recommended corrective action was provided to each individual entity at the conclusion of our fieldwork. The primary objective of this audit was to evaluate IS general controls at the North Carolina Community College Systems Office, 58 Community Colleges, and the Center. The scope of our IS general controls audit included reviewing for general security policies and evaluating the following: access to student and financial information, security of the networks and critical operating system, Systems Development Life Cycle (SDLC) methodology used to implement critical applications, maintenance of the operating system, physical security over the computer center, and disaster recovery planning. We reviewed controls in the following six areas: general security, access controls, system development, systems software, physical security, and disaster recovery. Other IS general control topics were reviewed as considered necessary. In early April 2003, the Office of the State Auditor began the review of all the entities within NCCCS. We visited each entity to gather audit information, performed onsite test work, and attempted to penetrate the security of the critical operating system and the networks. These audits were conducted during the period from April 4, 2003 through April 30, The audits were conducted under the authority granted by North Carolina General Statute (c)(18) which states: The Auditor shall, after consultation and in coordination with the State Chief Information Officer, assess, confirm, and report on the security practices of information technology systems. If an agency has adopted standards pursuant to
4 AUDITOR S TRANSMITTAL (CONCLUDED) General Statutes (d)(1) or (2), the audit shall be in accordance with those standards. The Auditor s assessment of information security practices shall include an assessment of network vulnerability. The Auditor may conduct network penetration or any similar procedure, as the Auditor may deem necessary. The Auditor may investigate reported information technology security breaches, cyber attacks, and cyber fraud in State Government. The Auditor shall issue public reports on the general results of the reviews undertaken pursuant to this subdivision, but may provide agencies with detailed reports of the security issues identified pursuant to this subdivision which shall not be disclosed as provided in General Statute (c). This report contains an executive summary that highlights the areas where the North Carolina Community College System has performed satisfactorily and where improvements should be made. We wish to express our appreciation to the staff of all the entities comprising the North Carolina Community College System for the courtesy, cooperation, and assistance provided to us during this audit. North Carolina General Statutes require the State Auditor to make audit reports available to the public. Copies of audit reports issued by the Office of the State Auditor may be obtained through one of the options listed in the back of this report. Respectfully submitted, Ralph Campbell, Jr. State Auditor
5 TABLE OF CONTENTS PAGE EXECUTIVE SUMMARY... 1 AUDIT OBJECTIVES, SCOPE, AND METHODOLOGY... 3 BACKGROUND INFORMATION... 5 AUDIT RESULTS AND AUDITEE RESPONSES... 7 DISTRIBUTION OF AUDIT REPORT..23
6 EXECUTIVE SUMMARY We conducted an information system (IS) audit of the North Carolina Community College System (NCCCS), which is comprised of the North Carolina Community College Systems Office (Systems Office), 58 Community Colleges, and the NC Center for Applied Textile Technology (Center) from April 4, 2003 through April 30, The primary objective of this audit was to evaluate the IS general controls in place during that period. We did not review the applications on the operating systems under review. Our audit focused on the following six areas of general controls: general security, access controls, systems development, systems software, physical security, and disaster recovery. We also performed scans for known vulnerabilities to determine if unauthorized access to sensitive student and financial information could be gained, and if so, we determined if this information could be read, modified, or even destroyed. Our audit identified general controls within NCCCS that were well defined and effective, as well as, controls that posed extreme security risks. We used a risk approach to define the level of risk associated with a general controls area under review. We classified each area s relative risk level using the following definitions. High Risk: Defined as a weakness that could cause grave consequences if not addressed and remedied immediately. This type of weakness is evident within the most sensitive portions of the critical operating systems and network. The security posture of the entity offers little protection from various security threats. This weakness could cause the data residing on the critical operating system to be modified or even destroyed by an unauthorized user or circumstance. Medium Risk: Defined as a weakness that should be addressed within the near future. This weakness could cause the data residing on the critical operating system to be read by an unauthorized user, however no modification or destruction of data can occur if not remedied. Low Risk: Defined as a weakness that should be fixed; however, it is unlikely that this weakness alone would allow the critical operating system or networks to be exploited. Based on the tests performed and severity of the control weaknesses identified, we found that the overall combined risk level for NCCCS is HIGH. We found that the general controls are not effective for protecting the operating systems for the majority of the entities within NCCCS. Based on our objective, we report the following conclusions. General security involves the establishment of a reasonable security program that addresses the general security of information resources. We found that the Systems Office, 57 of 58 Community Colleges, and the Center had not adopted formal information technology (IT) standards, policies, and procedures for many critical IT areas. However, we did find one community college that had adopted its own standards for information technology. This College s polices and procedures were considered adequate to promote good information technology security. Although almost all NCCCS entities failed to meet the standard controls 1
7 EXECUTIVE SUMMARY (CONTINUED) for general security, we consider the risk level for this area to be LOW. However, the absence of good general security policies and management contribute to weaknesses in other control areas. Access Control involves the implementation of controls to restrict access to computer resources to only those users who have an authorized need to use or know critical information. The access control environment consists of access control software, operating system and network configurations, and the implementation of information security policies and procedures. We reviewed the access controls to the networks and sensitive student and financial information residing on the critical operating systems for the Systems Office, 58 Community Colleges, and the Center. We found several access control weaknesses for all entities under review. Due to the sensitive nature of the conditions found, we have conveyed the details of these findings to management in a separate letter pursuant to the provision of North Carolina General Statute (c)(18). We consider the risk level for this area is HIGH because access controls are not working and are not effective for the majority of the entities within NCCCS. Systems development includes the creation of new application systems or significant changes to existing systems. Good system development controls suggest the use of a formal Systems Development Life Cycle (SDLC) Methodology to implement new application systems or modify existing systems. The Systems Office has the primary responsibility to select financial and student application systems and modify existing systems. The Systems Office is the only entity within NCCCS that is responsible for this area. The decisions made by the Systems Office in this area can have a significant impact on how well the other entities within NCCCS operate their critical systems. We found that the Systems Office had adopted a SDLC that included formal policies and procedures to implement the new critical application into the production environment of all the entities within NCCCS. However, the Systems Office did not include in their SDLC any security requirements or security specifications for the critical operating system, which host the critical applications. We evaluated the risk level for this area as HIGH because failing to specify security requirements for the critical operating system causes all of the entities within NCCCS to operate the new critical applications on operating systems that may not be secure. Systems software is the collection of programs that drive the computer. The selection of systems software should be properly approved and the software should be maintained by the computer center. We found a significant weakness in systems software maintenance controls. We found that procedures used to notify the entities within NCCCS of enhancements or changes to the critical operating system were ineffective. However, we found three colleges that had adopted their own procedures for systems software maintenance and their procedures were effective. We consider the risk level for this area is HIGH because system software controls were not maintained at current release levels for the majority of the entities within NCCCS. 2
8 EXECUTIVE SUMMARY (CONCLUDED) Physical security primarily involves the inspection of a computer center for the controls that should reasonably secure the operations of the computer center from foreseeable and preventable threats from fire, water, electrical problems, and vandalism. We found 10 community colleges computer centers are not secure from foreseeable and preventable security and environmental threats. Improvements in physical security should be made for the ten colleges identified with physical control weaknesses, however the risk level for this area is LOW because physical security controls are working and are effective for the majority of the entities within NCCCS. Disaster Recovery involves the creation of a plan to enable the recovery from an extended business interruption due to the destruction of the computer center or other assets. A complete disaster recovery plan that is tested periodically is necessary to ensure prompt resumption of computer systems. Fifteen community colleges did not have a formal written disaster recovery plan. Thirty-seven community colleges, the Systems Office, and the Center had disaster recovery plans, however, the plans were inadequate. The remaining six colleges disaster recovery plans were adequate. In addition, the community colleges are relying on the Systems Office as an alternate disaster recovery site; however, the Systems Office only has enough space on their back-up server to handle a few community colleges at a time. Furthermore, the server has not been tested for remote processing capabilities. We consider the risk level for this area is HIGH because disaster recovery controls may not be adequate or effective for the majority of the entities within NCCCS. This report represents a summary of the general results of our audits. A separate audit report containing the conditions found and recommended corrective actions was provided to each individual entity at the conclusion of our fieldwork. A copy of a specific entity s report can be obtained from the Office of the State Auditor website Auditor s Note: The findings in this report address the operating systems on which applications are installed and the surrounding information technology environment. The findings in this report are not associated with nor can these findings be resolved with the implementation of the Colleague student and financial application. General controls surrounding the operating system have a direct impact on the applications it hosts, therefore, NCCCS needs to ensure that they develop corrective actions apart from the installation of the new application to resolve these findings. 3
9 [ This Page Left Blank Intentionally ] 4
10 AUDIT OBJECTIVES, SCOPE, AND METHODOLOGY OBJECTIVES Under the North Carolina General Statutes Chapter , the State Auditor is responsible for examining and evaluating the adequacy of operating and administrative procedures and practices, systems of accounting, and other elements of State agencies. This IS audit was designed to ascertain the effectiveness of general controls at the North Carolina Community College Systems Office, the 58 community colleges and the NC Center for Applied Textile Technology. SCOPE General controls govern the operation and management of computer processing activities. The scope of our IS general controls audit was to review general security issues, access controls, systems development, systems software, physical security, and disaster recovery which directly affect the entities within the NCCCS computing operations. Other IS general control topics were reviewed as considered necessary. METHODOLOGY We audited policies and procedures, used questionnaires to interview key administrators and other personnel, developed a program to generate information from the critical operating systems to examine system configurations, toured the computer facility, tested on-line system controls, reviewed appropriate technical literature, reviewed computer-generated reports, and used security evaluation software in our audit of controls. We performed the following tasks. PHASE 1 Information Gathering In Phase 1, we sent questionnaires to all the entities within the NCCCS. We asked them to provide specific information regarding their critical operating systems, their security policies and procedures, their access and network infrastructure, and their disaster recovery plans. This information was reviewed to determine whether security policies and procedures exist and whether those polices and procedures covered standard areas. We determined whether the maintenance of the critical applications and operating system was current to prevent unauthorized access by individuals using known vulnerabilities. We reviewed the disaster recovery plans to ensure that recovery of critical systems was possible in the event of a disaster. PHASE 2 Onsite Review We then visited each entity to perform tests that could not be performed offsite to confirm suspected weaknesses. We viewed the computer operations of all the entities within the NCCCS. During this examination, we identified conditions that could allow physical security breaches into the computer centers and evaluated environmental concerns of the computing center. 5
11 AUDIT OBJECTIVES, SCOPE, AND METHODOLOGY (CONCLUDED) PHASE 3 Review of Audit Scripts In Phase 3, we internally developed a program to review the server configurations of the operating systems and the configuration of critical and sensitive files. We ran this program on each critical system of the community college to determine if the server and files were configured to restrict unauthorized access to critical student and financial information. PHASE 4 Vulnerability assessment In Phase 4, we tested for known vulnerabilities, specific to the critical operating system under review, and also tested to see if unauthorized access could be obtained into the critical operating systems. We accomplished this task by using services that come standard with all computers. The overall goal of this phase was to determine if vulnerabilities exist that would allow user level access to the critical operating systems via the internet or internally. We conducted our audit in accordance with the standards applicable to performance audits contained in Government Auditing Standards issued by the Comptroller General of the United States and Information Systems Audit Standards issued by the Information Systems Audit and Control Association. 1 1 In 1992 the State created the Information Resource Management Commission to provide statewide coordination of information technology resources planning. The IRMC provides state enterprise IT leadership including increased emphasis and oversight for strategic information technology planning and management; policy development; technical architecture; and project certification. Pursuant to North Carolina General Statute numerous state officials serve on the IRMC including four members of the Council of State who are appointed by the Governor. The State Auditor has been appointed a member of the IRMC and elected as chair of the IRMC by its members. 6
12 BACKGROUND INFORMATION The North Carolina Community College System (NCCCS) is comprised of the North Carolina Community College Systems Office, which is located in Raleigh, North Carolina, 58 community colleges located across North Carolina, and the NC Center for Applied Textile Technology. The mission of the North Carolina Community College System is to open the door to high-quality, accessible educational opportunities that minimize barriers to postsecondary education, maximize student success, and improve the lives and well being of individuals within North Carolina. The entities within NCCCS share responsibility for information technology. Each entity has a division that is responsible for information technology for their respective entity. The mission of the information technology divisions is to ensure that information technology is utilized and delivered to the students, faculty, and staff to aid them in accomplishing the overall mission of the North Carolina Community College System. 7
13 [ This Page Left Blank Intentionally ] 8
14 AUDIT RESULTS AND AUDITEE RESPONSES The following audit results reflect the areas where the North Carolina Community College Systems Office (Systems Office), the 58 community colleges, and the NC Center for Applied Textile Technology (Center) has performed satisfactorily and where recommendations have been made for improvement. A number of conditions were found within the entities that could be strengthened to improve security and general controls in the areas under review. Each area under review was classified according to its relative risk using the following definitions. High Risk: Defined as a weakness that could cause grave consequences if not addressed and remedied immediately. This type of weakness is evident within the most sensitive portions of the critical operating systems and network. The security posture of the entity offers little protection from various security threats. This weakness could cause the data residing on the critical operating system to be modified or even destroyed by an unauthorized user or circumstance. Medium Risk: Defined as a weakness that should be addressed within the near future. This weakness could cause the data residing on the critical operating system to be read by an unauthorized user, however no modification or destruction of data can occur if not remedied. Low Risk: Defined as a weakness that should be fixed; however, it is unlikely that this weakness alone would allow the critical operating system or networks to be exploited. OVERALL RISK- HIGH RISK The overall risk level of the North Carolina Community College System was HIGH based on the control weaknesses identified at the Systems Office, the 58 community colleges and the Center, and the level of risk classified for each area under review. The following is a graphical classification of risk and a depiction of the weaknesses found for each area under review. Maximum combined number of findings is 70. The majority of colleges received at least 15 or more findings with the majority of those findings occurring in a high-risk area. 9
15 AUDIT RESULTS AND AUDITEE RESPONSES (CONTINUED) Overall Findings Combined Maximum Number of Findings is 70 NCCCS Wilson Tech Wilkes Western Piedmont Wayne Wake Tech Vance-Granville Tri-County Surry Stanly Southwestern Southeastern South Piedmont Sandhills Sampson Rowan-Cabarrus Rockingham Robeson Roanoke-Chowan Richmond Randolph Pitt Piedmont Pamlico NC Center Applied Tech Nash Montgomery Mitchell McDowell Tech Mayland Martin Lenoir Johnston James Sprunt Isothermal Haywood Halifax Guilford Gaston Forsyth Tech Fayetteville Tech Edgecombe Durham Tech Davidson Craven College of Albemarle Coastal Carolina Cleveland Central Piedmont Central Carolina Catawba Valley Carteret Cape Fear Caldwell Brunswick Blue Ridge Bladen Beaufort County Ashe-Bun Tech Alamance General Security Disaster Recovery Network Infrastructure Access Controls Systems Software Physical Security Systems Development # of Findings
16 AUDIT RESULTS AND AUDITEE RESPONSES (CONTINUED) GENERAL SECURITY ISSUES- LOW RISK General security issues involve the maintenance of a sound security management structure. A sound security management structure should include a method of classifying and establishing ownership of resources, proper segregation of duties, a security organization and resources, policies regarding access to the computer systems and a security education program. The Systems Office, 57 community colleges, and the Center have not adopted formal information technology (IT) standards to help them address all critical areas of their IT security environment. One College did have acceptable policies and procedures. Two community colleges did not have any IT polices, while 55 colleges and the Center had IT policies, however, the policies lacked one or more of the following critical policies and procedures. Organizational-wide security policies; User security policies; Group assignment and re-assignment polices; New accounts and termination policies; Monitoring of the critical operating systems and servers; How to respond to security threats and incidents; How users should securely use the networks; Baseline configuration for securing the critical operating system; and Risk assessment. Although, the majority of the entities within NCCCS received a finding in this area, we believe the overall risk level for this area is LOW because the nature of the weaknesses found in this area alone would not allow the critical operating system or networks to be exploited 11
17 AUDIT RESULTS AND AUDITEE RESPONSES (CONTINUED) General Security Maximum Number of Findings in this area is 5. Wilson Tech Wilkes Western Piedmont Wayne Wake Tech Vance-Granville Tri-County Surry Stanly Southwestern Southeastern South Piedmont Sandhills Sampson Rowan-Cabarrus Rockingham Robeson Roanoke-Chowan Richmond Randolph Pitt Piedmont Mayland NC Center Applied Tech Nash Montgomery Mitchell McDowell Tech Martin Lenoir Johnston James Sprunt Isothermal Haywood Halifax Forsyth Tech Fayetteville Tech Edgecombe Durham Tech Davidson Craven College of Albemarle Coastal Carolina Cleveland Central Piedmont Central Carolina Catawba Valley Carteret Cape Fear Brunswick Caldwell Blue Ridge Bladen Beaufort County Alamance NCCCS Pamlico Guilford Gaston Ashe-Bun Tech # of Findings
18 AUDIT RESULTS AND AUDITEE RESPONSES (CONTINUED) ACCESS CONTROLS- HIGH RISK Access Control involves the implementation of controls to restrict access to computer resources to only those users who have an authorized need to use or know critical information. The access control environment consists of access control software and operating system and network configurations, and the implementation of information security policies and procedures. An individual or a group with responsibility for security administration should develop information security policies, perform account administration functions and establish procedures to monitor and report any security violations. We reviewed the access controls for the NCCCS critical operating systems. We found several significant weaknesses in access controls. At the time of our testing, the majority of the entities within NCCCS had significant weaknesses in this area. Therefore, we believe the overall risk level for this area is HIGH. Subsequently, these security enhancements have been acted upon. 13
19 AUDIT RESULTS AND AUDITEE RESPONSES (CONTINUED) Access and Network Controls Maximum Number of Findings in this area is 60. NCCCS Wilson Tech Wilkes Western Piedmont Wayne Wake Tech Vance-Granville Tri-County Surry Stanly Southwestern Southeastern South Piedmont Sandhills Sampson Rowan-Cabarrus Rockingham Robeson Roanoke-Chowan Richmond Randolph Pitt Piedmont Pamlico NC Center Applied Tech Nash Montgomery Mitchell McDowell Tech Mayland Martin Lenoir Johnston James Sprunt Isothermal Haywood Halifax Guilford Forsyth Tech Gaston Fayetteville Tech Edgecombe Durham Tech Davidson Craven College of Albemarle Coastal Carolina Cleveland Central Piedmont Central Carolina Catawba Valley Carteret Cape Fear Caldwell Brunswick Blue Ridge Bladen Beaufort County Ashe-Bun Tech Alamance Access Controls Network Infrastructure # of Findings
20 AUDIT RESULTS AND AUDITEE RESPONSES (CONTINUED) SYSTEMS DEVELOPMENT- HIGH RISK Systems development includes the creation of new application systems or significant changes to existing systems. Systems development projects can be expensive and affect the operations of the agency in significant ways. Consequently, the agency should have a strategic or master plan for systems development. Each development project should be managed using project management techniques and should adhere to a clearly defined systems development methodology. When a project is completed, the finished product should include comprehensive documentation so that the users, operators, and programmers each have the information they need to do their jobs. The Systems Office has been delegated the authority of selecting new application systems or modify existing systems, which process the financial and student data for all of the entities within NCCCS. The Systems Office is the only entity within NCCCS that is responsible for this area. We reviewed the phases of the Systems Development Life Cycle for Systems Office and found that no security requirements were defined for the critical operating system under review. This weakness has a significant impact on how well the other entities within NCCCS operate their critical systems. Therefore, the overall risk level for this area is HIGH. SYSTEMS SOFTWARE- HIGH RISK Systems software is the collection of programs that the computer center uses to run the computer and support the application systems. This software includes the operating system, utility programs, compilers, database management systems and other programs. The systems programmers have responsibility for the installation and testing of upgrades to the system software when received. At the time of our testing, the majority of the entities within NCCCS had significant weaknesses in this area. However, we found three colleges who had adopted their own procedures for systems software maintenance and their procedures were effective. Therefore, we believe the overall risk level for this area is HIGH. 15
21 AUDIT RESULTS AND AUDITEE RESPONSES (CONTINUED) System Software Maximum Number of Finding in this area is 1. Wilson Tech Wilkes Western Piedmont Wayne Vance-Granville Tri-County Surry Stanly Southwestern Southeastern South Piedmont Sandhills Sampson Rowan-Cabarrus Rockingham Robeson Richmond Randolph Pitt Piedmont Pamlico NC Center Applied Tech Nash Montgomery Mitchell McDowell Tech Mayland Lenoir Johnston James Sprunt Isothermal Haywood Halifax Guildford Gaston Forsyth Tech Fayetteville Tech Edgecombe Durham Tech Davidson Craven College of Albemarle Coastal Carolina Cleveland Central Piedmont Central Carolina Catawba Valley Carteret Cape Fear Caldwell Brunswick Blue Ridge Bladen Beaufort County Ashe-Bun Tech Alamance NCCCS Wake Tech Roanoke-Chowan Martin 16
22 AUDIT RESULTS AND AUDITEE RESPONSES (CONTINUED) PHYSICAL SECURITY- LOW RISK Controls over physical security are designed to protect a computer center from service interruptions resulting from fire, water, electrical problems, vandalism, and other causes. Ten community colleges did not have computer centers that were secure from foreseeable and preventable security and environmental threats. At the time of our testing, the ten community colleges had a HIGH risk level in this area. Physical Security Controls are ineffective for only those community colleges. Of these 10 community colleges, we found the following types of physical security weaknesses. The offsite storage area and the computer area are not restricted to authorized personnel. As a result, the physical security over the community college s back-up tapes and computing resources is weakened and could allow unauthorized tampering of the data stored on the back-up tapes and unauthorized access to computer hardware. The System Administrator leaves the door unlocked to the computer room. Because the critical operating system, which host the financial and student information, resides in this computer room, unauthorized personnel could directly access the main console and modify, delete, and corrupt data, or interrupt the community college s computer processing capabilities. The computer room is not equipped with smoke detectors, automated fire suppression system, or hand-pulled fire alarms. Therefore, the community college is not protected from an environmental hazard, such as, fire. The computer room has water leaks in the ceiling that can drip onto servers below, thus the critical server is not protected from water damage. Water is an environmental hazard to computer servers and can cause a computer to malfunction. Since the critical server resides in the computer room, this server is subject to water damage, which would cause the community college to lose computer-processing capabilities. The computer room is not protected from electrical hazards. Therefore, the community college is susceptible to electrical fluctuations or power outages. Electrical fluctuations and power outages can cause data on a computer server to become non-useable. Electrical fluctuations and power outages are another environmental hazard that could cause the community college to lose computerprocessing capabilities. The Systems Office, the other 48 community colleges, and the Center s computer centers appear secure from foreseeable and preventable security and environmental threats. We found no significant weaknesses in physical security for these entities. Therefore, the overall risk level for this area is LOW. 17
23 AUDIT RESULTS AND AUDITEE RESPONSES (CONTINUED) Physical Security Maximum Number of Findings is 1. Wilkes Vance-Granville Surry Sandhills Piedmont Nash Montgomery Edgecombe Blue Ridge Alamance Wilson Tech Western Piedmont Wayne Wake Tech Tri-County Stanly Southwestern Southeastern South Piedmont Sampson Rowan-Cabarrus Rockingham Robeson Roanoke-Chowan Richmond Randolph Pitt Pamlico NC Center Applied Tech Mitchell McDowell Tech Mayland Martin Lenoir Johnston James Sprunt Isothermal Haywood Halifax Guildford Gaston Forsyth Tech Fayetteville Tech Durham Tech Davidson Craven College of Albemarle Coastal Carolina Cleveland Central Piedmont Central Carolina Catawba Valley Carteret Cape Fear Caldwell Brunswick Bladen Beaufort County Ashe-Bun Tech NCCCS 18
24 AUDIT RESULTS AND AUDITEE RESPONSES (CONTINUED) DISASTER RECOVERY- HIGH RISK Disasters such as fire and flood can destroy a computer service center and leave its users without computer processing support. Without computer processing, many college services would grind to a halt. To reduce this risk, computer service centers develop disaster recovery plans. Disaster recovery procedures should be tested periodically to ensure the recoverability of the data center. Our audit identified fifteen community colleges that did not have disaster recovery plans. The Systems Office, thirty-seven community colleges, and the Center have disaster recovery plans (DRP); however, the disaster recovery plans are incomplete and have not been tested. We found six community colleges that had no significant weakness in their disaster recovery plan. For the entities that had plans we looked for the following critical components: Executive management's signature of approval of the plan; Statement of the assumptions, such as the maximum time without computing, underlying the plan; Identification of critical applications in each user department and the priority in which these applications will be restored if resources are limited; Identification of key personnel and their assignments during the restoration of processing; Alternate user department procedures to manage their workloads until processing resumes; An inventory of equipment, special stock and arrangements to acquire replacement equipment; and A procedure to update the plan when there are major changes to the environment or at least annually. The disaster recovery plans are not tested annually. Because the majority of the entities within NCCCS did not have adequate plans, we believe the overall risk level for this area is HIGH. 19
25 AUDIT RESULTS AND AUDITEE RESPONSES (CONCLUDED) Disaster Recovery Maximum Number of Findings is 2. Wilkes Tri-County Sampson Rockingham Robeson Richmond NC Center Applied Tech Nash Montgomery Mitchell McDowell Tech Mayland Martin Lenoir Johnston James Sprunt Isothermal Haywood Halifax Guilford Gaston Forsyth Tech Fayetteville Tech Edgecombe Durham Tech Davidson Craven College of Albemarle Coastal Carolina Cleveland Central Piedmont Central Carolina Catawba Valley Carteret Cape Fear Caldwell Blue Ridge Alamance Wilson Tech Western Piedmont Wayne Wake Tech Vance-Granville Surry Stanly Southwestern South Piedmont Rowan-Cabarrus Roanoke-Chowan Randolph Piedmont Bladen Beaufort County NCCCS Southeastern Sandhills Pitt Pamlico Brunswick Ashe-Bun Tech 20
26 21
27 [ This Page Left Blank Intentionally ] 22
28 DISTRIBUTION OF AUDIT REPORT In accordance with General Statutes and (c)(14), copies of this report have been distributed to the public officials listed below. Additional copies are provided to other legislators, state officials, the press, and the general public upon request. EXECUTIVE BRANCH The Honorable Michael F. Easley The Honorable Beverly M. Perdue The Honorable Richard H. Moore The Honorable Roy A. Cooper, III Mr. David T. McCoy Mr. Robert L. Powell Mr. Martin Lancaster Governor of North Carolina Lieutenant Governor of North Carolina State Treasurer Attorney General State Budget Officer State Controller President, North Carolina Community College System President Pro Tempore Senator Marc Basnight, Co-Chair Senator Charles W. Albertson Senator Patrick J. Ballantine Senator Daniel G. Clodfelter Senator Walter H. Dalton Senator Charlie S. Dannelly Senator James Forrester Senator Linda Garrou Senator Wilbur P. Gulley Senator Fletcher L. Hartsell, Jr. Senator David W. Hoyle Senator Ellie Kinnaird Senator Jeanne H. Lucas Senator Stephen M. Metcalf Senator Anthony E. Rand Senator Eric M. Reeves Senator Robert A. Rucho Senator R. C. Soles, Jr. Senator Scott Thomas LEGISLATIVE BRANCH Appointees to the Joint Legislative Commission on Governmental Operations Speaker of the House Representative James B. Black, Co-Chair Representative Richard T. Morgan, Co-Chair Representative Martha B. Alexander Representative Rex L. Baker Representative Bobby H. Barbee, Sr. Representative Harold J. Brubaker Representative Debbie A. Clary Representative E. Nelson Cole Representative James W. Crawford, Jr. Representative William T. Culpepper, III Representative W. Pete Cunningham Representative W. Robert Grady Representative Joe Hackney Representative Julia C. Howard Representative Joe L. Kiser Representative Edd Nye Representative William C. Owens, Jr. Representative Wilma M. Sherrill Representative Thomas E. Wright Other Legislative Officials Mr. James D. Johnson Director, Fiscal Research Division Other Officials Chairman and Members of the Information Resource Management Commission 23
29 ORDERING INFORMATION Copies of this report may be obtained by contacting the: Office of the State Auditor State of North Carolina 2 South Salisbury Street Mail Service Center Raleigh, North Carolina Internet: Telephone: 919/ Facsimile: 919/
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT BRUNSWICK COMMUNITY COLLEGE SUPPLY, NORTH CAROLINA JUNE 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR AUDIT
STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT BRUNSWICK COMMUNITY COLLEGE SUPPLY, NORTH CAROLINA JUNE 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR AUDIT
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT ROANOKE-CHOWAN COMMUNITY COLLEGE AHOSKIE, NORTH CAROLINA JUNE 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR
STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT ROANOKE-CHOWAN COMMUNITY COLLEGE AHOSKIE, NORTH CAROLINA JUNE 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT DURHAM TECHNICAL COMMUNITY COLLEGE DURHAM, NORTH CAROLINA JUNE 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR
STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT DURHAM TECHNICAL COMMUNITY COLLEGE DURHAM, NORTH CAROLINA JUNE 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT BLUE RIDGE COMMUNITY COLLEGE FLAT ROCK, NORTH CAROLINA JUNE 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR
STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT BLUE RIDGE COMMUNITY COLLEGE FLAT ROCK, NORTH CAROLINA JUNE 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT HALIFAX COMMUNITY COLLEGE WELDON, NORTH CAROLINA JUNE 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR AUDIT
STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT HALIFAX COMMUNITY COLLEGE WELDON, NORTH CAROLINA JUNE 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR AUDIT
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT MONTGOMERY COMMUNITY COLLEGE TROY, NORTH CAROLINA JUNE 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR AUDIT
STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT MONTGOMERY COMMUNITY COLLEGE TROY, NORTH CAROLINA JUNE 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR AUDIT
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEMS GENERAL CONTROLS ADMINISTRATIVE OFFICE OF THE COURTS MAY 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR AUDIT OF THE INFORMATION
STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEMS GENERAL CONTROLS ADMINISTRATIVE OFFICE OF THE COURTS MAY 2004 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL, JR. STATE AUDITOR AUDIT OF THE INFORMATION
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEMS GENERAL CONTROLS NC A&T STATE UNIVERSITY GREENSBORO, NORTH CAROLINA APRIL 2005 OFFICE OF THE STATE AUDITOR LESLIE W. MERRITT, JR., CPA, CFP STATE
STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEMS GENERAL CONTROLS NC A&T STATE UNIVERSITY GREENSBORO, NORTH CAROLINA APRIL 2005 OFFICE OF THE STATE AUDITOR LESLIE W. MERRITT, JR., CPA, CFP STATE
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEMS GENERAL CONTROLS ELIZABETH CITY STATE UNIVERSITY JULY 2006 OFFICE OF THE STATE AUDITOR LESLIE MERRITT, JR., CPA, CFP STATE AUDITOR AUDIT OF THE
STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEMS GENERAL CONTROLS ELIZABETH CITY STATE UNIVERSITY JULY 2006 OFFICE OF THE STATE AUDITOR LESLIE MERRITT, JR., CPA, CFP STATE AUDITOR AUDIT OF THE
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEMS GENERAL CONTROLS CARTERET COMMUNITY COLLEGE OCTOBER 2007 OFFICE OF THE STATE AUDITOR LESLIE MERRITT, JR., CPA, CFP STATE AUDITOR AUDIT OF THE INFORMATION
STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEMS GENERAL CONTROLS CARTERET COMMUNITY COLLEGE OCTOBER 2007 OFFICE OF THE STATE AUDITOR LESLIE MERRITT, JR., CPA, CFP STATE AUDITOR AUDIT OF THE INFORMATION
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEMS GENERAL CONTROLS FAYETTEVILLE STATE UNIVERSITY MAY 2007 OFFICE OF THE STATE AUDITOR LESLIE MERRITT, JR., CPA, CFP STATE AUDITOR AUDIT OF THE INFORMATION
STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEMS GENERAL CONTROLS FAYETTEVILLE STATE UNIVERSITY MAY 2007 OFFICE OF THE STATE AUDITOR LESLIE MERRITT, JR., CPA, CFP STATE AUDITOR AUDIT OF THE INFORMATION
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT THE UNIVERSITY OF NORTH CAROLINA AT CHARLOTTE CHARLOTTE, NORTH CAROLINA FEBRUARY 2002 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL,
STATE OF NORTH CAROLINA AUDIT OF THE INFORMATION SYSTEM GENERAL CONTROLS AT THE UNIVERSITY OF NORTH CAROLINA AT CHARLOTTE CHARLOTTE, NORTH CAROLINA FEBRUARY 2002 OFFICE OF THE STATE AUDITOR RALPH CAMPBELL,
College and Career Readiness. Basic Skills PLUS Career Pathways by College and NC Career Cluster 1
 and Career Readiness Basic Skills PLUS Career Pathways by and NC Career Cluster 1 (October 2016) Basic Skills PLUS is a program that provides workforce preparation activities and workforce training for
and Career Readiness Basic Skills PLUS Career Pathways by and NC Career Cluster 1 (October 2016) Basic Skills PLUS is a program that provides workforce preparation activities and workforce training for
College and Career Readiness. Basic Skills PLUS Career Pathways by College and NC Career Cluster 1
 and Career Readiness Basic Skills PLUS Career Pathways by and NC Career Cluster 1 (November 2016) Basic Skills PLUS is a program that provides workforce preparation activities and workforce training for
and Career Readiness Basic Skills PLUS Career Pathways by and NC Career Cluster 1 (November 2016) Basic Skills PLUS is a program that provides workforce preparation activities and workforce training for
STATE OF NORTH CAROLINA OFFICE OF THE STATE AUDITOR BETH A. WOOD, CPA FAYETTEVILLE STATE UNIVERSITY
 STATE OF NORTH CAROLINA OFFICE OF THE STATE AUDITOR BETH A. WOOD, CPA FAYETTEVILLE STATE UNIVERSITY INFORMATION TECHNOLOGY GENERAL CONTROLS INFORMATION SYSTEMS AUDIT JANUARY 2016 EXECUTIVE SUMMARY PURPOSE
STATE OF NORTH CAROLINA OFFICE OF THE STATE AUDITOR BETH A. WOOD, CPA FAYETTEVILLE STATE UNIVERSITY INFORMATION TECHNOLOGY GENERAL CONTROLS INFORMATION SYSTEMS AUDIT JANUARY 2016 EXECUTIVE SUMMARY PURPOSE
UNIVERSITY OF NORTH CAROLINA CHARLOTTE
 STATE OF NORTH CAROLINA OFFICE OF THE STATE AUDITOR BETH A. WOOD, CPA UNIVERSITY OF NORTH CAROLINA CHARLOTTE INFORMATION TECHNOLOGY GENERAL CONTROLS INFORMATION SYSTEMS AUDIT JULY 2017 EXECUTIVE SUMMARY
STATE OF NORTH CAROLINA OFFICE OF THE STATE AUDITOR BETH A. WOOD, CPA UNIVERSITY OF NORTH CAROLINA CHARLOTTE INFORMATION TECHNOLOGY GENERAL CONTROLS INFORMATION SYSTEMS AUDIT JULY 2017 EXECUTIVE SUMMARY
Market Reform Policy Issues Geographic Analysis
 Market Reform Policy Issues Geographic Analysis March 8, 2013 Relevant Laws and Regulations Geographic Rating Areas The final rules set minimum requirements for geographic rating areas, while still permitting
Market Reform Policy Issues Geographic Analysis March 8, 2013 Relevant Laws and Regulations Geographic Rating Areas The final rules set minimum requirements for geographic rating areas, while still permitting
UNIVERSITY OF NORTH CAROLINA CHAPEL HILL
 abd STATE OF NORTH CAROLINA OFFICE OF THE STATE AUDITOR BETH A. WOOD, CPA UNIVERSITY OF NORTH CAROLINA CHAPEL HILL INFORMATION TECHNOLOGY GENERAL CONTROLS INFORMATION SYSTEMS AUDIT NOVEMBER 2017 EXECUTIVE
abd STATE OF NORTH CAROLINA OFFICE OF THE STATE AUDITOR BETH A. WOOD, CPA UNIVERSITY OF NORTH CAROLINA CHAPEL HILL INFORMATION TECHNOLOGY GENERAL CONTROLS INFORMATION SYSTEMS AUDIT NOVEMBER 2017 EXECUTIVE
Review of the Feasibility Plan for Coordinating Operations of the North Carolina Research and Education Network and the State Network Infrastructure
 Review of the Feasibility Plan for Coordinating Operations of the North Carolina Research and Education Network and the State Network Infrastructure Final Report to the Joint Legislative Program Evaluation
Review of the Feasibility Plan for Coordinating Operations of the North Carolina Research and Education Network and the State Network Infrastructure Final Report to the Joint Legislative Program Evaluation
Statewide. North Carolina CISM Team Contacts
 Statewide HIGHWAY PATROL MEMBER ASSISTANCE TEAM COUNTY: WAKE Statewide All 100- NCDPS. Out of state upon request CONTACT: A. Aaron Back OFFICE PHONE: 919-733-4030 CELL PHONE: 919-306-7497 EMAIL: Anthony.back@ncdps.gov
Statewide HIGHWAY PATROL MEMBER ASSISTANCE TEAM COUNTY: WAKE Statewide All 100- NCDPS. Out of state upon request CONTACT: A. Aaron Back OFFICE PHONE: 919-733-4030 CELL PHONE: 919-306-7497 EMAIL: Anthony.back@ncdps.gov
Presentation to the Joint Legislative Oversight Committees on HHS and IT December 13, Presenter: Anthony Vellucci, NC FAST Program Director
 Presentation to the Joint Legislative Oversight Committees on HHS and IT December 13, 2011 Presenter: Anthony Vellucci, NC FAST Program Director Introduction The NC FAST Program will deliver tools that
Presentation to the Joint Legislative Oversight Committees on HHS and IT December 13, 2011 Presenter: Anthony Vellucci, NC FAST Program Director Introduction The NC FAST Program will deliver tools that
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA UNIVERSITY OF NORTH CAROLINA SCHOOL OF THE ARTS INFORMATION TECHNOLOGY GENERAL CONTROLS MARCH 2011 PERFORMANCE AUDIT OFFICE OF THE STATE AUDITOR BETH A. WOOD, CPA STATE AUDITOR
STATE OF NORTH CAROLINA UNIVERSITY OF NORTH CAROLINA SCHOOL OF THE ARTS INFORMATION TECHNOLOGY GENERAL CONTROLS MARCH 2011 PERFORMANCE AUDIT OFFICE OF THE STATE AUDITOR BETH A. WOOD, CPA STATE AUDITOR
SCO Availability - Cotton 2015 RY Raleigh, NC RO. page 1 of 6
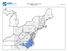 page 1 of 6 page 2 of 6 Anson Beaufort Bertie Bladen Brunswick Cabarrus Camden Carteret Chatham Chowan Cleveland Columbus Craven Cumberland Currituck SCO-RP No Type Specified I, NI 1,182.0 0.15 19.27%
page 1 of 6 page 2 of 6 Anson Beaufort Bertie Bladen Brunswick Cabarrus Camden Carteret Chatham Chowan Cleveland Columbus Craven Cumberland Currituck SCO-RP No Type Specified I, NI 1,182.0 0.15 19.27%
Information Technology General Control Review
 Information Technology General Control Review David L. Shissler, Senior IT Auditor, CPA, CISA, CISSP Office of Internal Audit and Risk Assessment September 15, 2016 Background Presenter Senior IT Auditor
Information Technology General Control Review David L. Shissler, Senior IT Auditor, CPA, CISA, CISSP Office of Internal Audit and Risk Assessment September 15, 2016 Background Presenter Senior IT Auditor
NORTH CAROLINA LEAD CONTACTS
 NORTH CAROLINA LEAD CONTACTS NC CHILDHOOD LEAD POISONING PREVENTION PROGRAM (CLPPP) DAVID BROWN, SURVEILLANCE COORDINATOR 919/218-5460 Department of Health and Human Services FAX: 919/807-4015 email: w.david.brown@dhhs.nc.gov
NORTH CAROLINA LEAD CONTACTS NC CHILDHOOD LEAD POISONING PREVENTION PROGRAM (CLPPP) DAVID BROWN, SURVEILLANCE COORDINATOR 919/218-5460 Department of Health and Human Services FAX: 919/807-4015 email: w.david.brown@dhhs.nc.gov
STATE OF NORTH CAROLINA
 STATE OF NORTH CAROLINA AUDIT OF APPLICATION CONTROLS EMPLOYMENT SECURITY COMMISSION DECEMBER 2008 OFFICE OF THE STATE AUDITOR LESLIE W. MERRITT, JR., CPA, CFP STATE AUDITOR AUDIT OF APPLICATION CONTROLS
STATE OF NORTH CAROLINA AUDIT OF APPLICATION CONTROLS EMPLOYMENT SECURITY COMMISSION DECEMBER 2008 OFFICE OF THE STATE AUDITOR LESLIE W. MERRITT, JR., CPA, CFP STATE AUDITOR AUDIT OF APPLICATION CONTROLS
TARGET2-SECURITIES INFORMATION SECURITY REQUIREMENTS
 Target2-Securities Project Team TARGET2-SECURITIES INFORMATION SECURITY REQUIREMENTS Reference: T2S-07-0270 Date: 09 October 2007 Version: 0.1 Status: Draft Target2-Securities - User s TABLE OF CONTENTS
Target2-Securities Project Team TARGET2-SECURITIES INFORMATION SECURITY REQUIREMENTS Reference: T2S-07-0270 Date: 09 October 2007 Version: 0.1 Status: Draft Target2-Securities - User s TABLE OF CONTENTS
Statewide Information Technology Contingency Planning
 New Jersey State Legislature Office of Legislative Services Office of the State Auditor Statewide Information Technology Contingency Planning March 9, 2015 to June 10, 2016 Stephen M. Eells State Auditor
New Jersey State Legislature Office of Legislative Services Office of the State Auditor Statewide Information Technology Contingency Planning March 9, 2015 to June 10, 2016 Stephen M. Eells State Auditor
Postal Inspection Service Mail Covers Program
 Postal Inspection Service Mail Covers Program May 28, 2014 AUDIT REPORT Report Number HIGHLIGHTS BACKGROUND: In fiscal year 2013, the U.S. Postal Inspection Service processed about 49,000 mail covers.
Postal Inspection Service Mail Covers Program May 28, 2014 AUDIT REPORT Report Number HIGHLIGHTS BACKGROUND: In fiscal year 2013, the U.S. Postal Inspection Service processed about 49,000 mail covers.
2017 LEGISLATIVE recommendations cyber security
 2017 LEGISLATIVE recommendations cyber security Cyber security risk is a policy-level issue to be handled at the elected and appointed official level, not just administratively at an agency or within information
2017 LEGISLATIVE recommendations cyber security Cyber security risk is a policy-level issue to be handled at the elected and appointed official level, not just administratively at an agency or within information
Golden LEAF Rural Broadband Initiative and the Future of MCNC/NCREN
 Golden LEAF Rural Broadband Initiative and the Future of MCNC/NCREN Joe Freddoso NCPLDA MCNC Operates NCREN A high speed optical backbone for Community Anchor Institutions (K12, Community Colleges, Universities,
Golden LEAF Rural Broadband Initiative and the Future of MCNC/NCREN Joe Freddoso NCPLDA MCNC Operates NCREN A high speed optical backbone for Community Anchor Institutions (K12, Community Colleges, Universities,
FOLLOW-UP REPORT Industrial Control Systems Audit
 FOLLOW-UP REPORT Industrial Control Systems Audit February 2017 Office of the Auditor Audit Services Division City and County of Denver Timothy M. O Brien, CPA The Auditor of the City and County of Denver
FOLLOW-UP REPORT Industrial Control Systems Audit February 2017 Office of the Auditor Audit Services Division City and County of Denver Timothy M. O Brien, CPA The Auditor of the City and County of Denver
Standard for Security of Information Technology Resources
 MARSHALL UNIVERSITY INFORMATION TECHNOLOGY COUNCIL Standard ITP-44 Standard for Security of Information Technology Resources 1 General Information: Marshall University expects all individuals using information
MARSHALL UNIVERSITY INFORMATION TECHNOLOGY COUNCIL Standard ITP-44 Standard for Security of Information Technology Resources 1 General Information: Marshall University expects all individuals using information
REPORT 2015/010 INTERNAL AUDIT DIVISION
 INTERNAL AUDIT DIVISION REPORT 2015/010 Audit of information and communications technology strategic planning, governance and management in the Investment Management Division of the United Nations Joint
INTERNAL AUDIT DIVISION REPORT 2015/010 Audit of information and communications technology strategic planning, governance and management in the Investment Management Division of the United Nations Joint
Office of MN.IT Services Data Centers
 Office of MN.IT Services Data Centers Information Technology Controls and Compliance Audit As of November 2016 March 2, 2017 REPORT 17-06 Financial Audit Division Office of the Legislative Auditor State
Office of MN.IT Services Data Centers Information Technology Controls and Compliance Audit As of November 2016 March 2, 2017 REPORT 17-06 Financial Audit Division Office of the Legislative Auditor State
Subject: University Information Technology Resource Security Policy: OUTDATED
 Policy 1-18 Rev. 2 Date: September 7, 2006 Back to Index Subject: University Information Technology Resource Security Policy: I. PURPOSE II. University Information Technology Resources are at risk from
Policy 1-18 Rev. 2 Date: September 7, 2006 Back to Index Subject: University Information Technology Resource Security Policy: I. PURPOSE II. University Information Technology Resources are at risk from
Judiciary Judicial Information Systems
 Audit Report Judiciary Judicial Information Systems February 2005 OFFICE OF LEGISLATIVE AUDITS DEPARTMENT OF LEGISLATIVE SERVICES MARYLAND GENERAL ASSEMBLY This report and any related follow-up correspondence
Audit Report Judiciary Judicial Information Systems February 2005 OFFICE OF LEGISLATIVE AUDITS DEPARTMENT OF LEGISLATIVE SERVICES MARYLAND GENERAL ASSEMBLY This report and any related follow-up correspondence
REPORT Bill Bradbury, Secretary of State Cathy Pollino, Director, Audits Division
 Secretary of State Report No. 2003-20 June 3, 2003 AUDIT Department of Administrative Services Information Resources Management Division Follow Up REPORT Bill Bradbury, Secretary of State Cathy Pollino,
Secretary of State Report No. 2003-20 June 3, 2003 AUDIT Department of Administrative Services Information Resources Management Division Follow Up REPORT Bill Bradbury, Secretary of State Cathy Pollino,
REVIEW OF MANAGEMENT AND OVERSIGHT OF THE INTEGRATED BUSINESS MANAGEMENT SYSTEM (IBMS) January 16, 2009
 APPENDIX 1 REVIEW OF MANAGEMENT AND OVERSIGHT OF THE INTEGRATED BUSINESS MANAGEMENT SYSTEM (IBMS) January 16, 2009 Auditor General s Office Jeffrey Griffiths, C.A., C.F.E. Auditor General City of Toronto
APPENDIX 1 REVIEW OF MANAGEMENT AND OVERSIGHT OF THE INTEGRATED BUSINESS MANAGEMENT SYSTEM (IBMS) January 16, 2009 Auditor General s Office Jeffrey Griffiths, C.A., C.F.E. Auditor General City of Toronto
NORTH CAROLINA NC MRITE. Nominating Category: Enterprise IT Management Initiatives
 NORTH CAROLINA MANAGING RISK IN THE INFORMATION TECHNOLOGY ENTERPRISE NC MRITE Nominating Category: Nominator: Ann V. Garrett Chief Security and Risk Officer State of North Carolina Office of Information
NORTH CAROLINA MANAGING RISK IN THE INFORMATION TECHNOLOGY ENTERPRISE NC MRITE Nominating Category: Nominator: Ann V. Garrett Chief Security and Risk Officer State of North Carolina Office of Information
General Information Technology Controls Follow-up Review
 Office of Internal Audit General Information Technology Controls Follow-up Review May 19, 2015 Internal Audit Team Shannon B. Henry Chief Audit Executive Stacy Sneed Audit Manager Rod Isom Auditor Winston-Salem
Office of Internal Audit General Information Technology Controls Follow-up Review May 19, 2015 Internal Audit Team Shannon B. Henry Chief Audit Executive Stacy Sneed Audit Manager Rod Isom Auditor Winston-Salem
AUDIT UNITED NATIONS VOLUNTEERS PROGRAMME INFORMATION AND COMMUNICATION TECHNOLOGY. Report No Issue Date: 8 January 2014
 UNITED NATIONS DEVELOPMENT PROGRAMME AUDIT OF UNITED NATIONS VOLUNTEERS PROGRAMME INFORMATION AND COMMUNICATION TECHNOLOGY Report No. 1173 Issue Date: 8 January 2014 Table of Contents Executive Summary
UNITED NATIONS DEVELOPMENT PROGRAMME AUDIT OF UNITED NATIONS VOLUNTEERS PROGRAMME INFORMATION AND COMMUNICATION TECHNOLOGY Report No. 1173 Issue Date: 8 January 2014 Table of Contents Executive Summary
Department of Management Services REQUEST FOR INFORMATION
 RESPONSE TO Department of Management Services REQUEST FOR INFORMATION Cyber-Security Assessment, Remediation, and Identity Protection, Monitoring, and Restoration Services September 3, 2015 250 South President
RESPONSE TO Department of Management Services REQUEST FOR INFORMATION Cyber-Security Assessment, Remediation, and Identity Protection, Monitoring, and Restoration Services September 3, 2015 250 South President
STAFF REPORT. January 26, Audit Committee. Information Security Framework. Purpose:
 STAFF REPORT January 26, 2001 To: From: Subject: Audit Committee City Auditor Information Security Framework Purpose: To review the adequacy of the Information Security Framework governing the security
STAFF REPORT January 26, 2001 To: From: Subject: Audit Committee City Auditor Information Security Framework Purpose: To review the adequacy of the Information Security Framework governing the security
"Charting the Course... Certified Information Systems Auditor (CISA) Course Summary
 Course Summary Description In this course, you will perform evaluations of organizational policies, procedures, and processes to ensure that an organization's information systems align with overall business
Course Summary Description In this course, you will perform evaluations of organizational policies, procedures, and processes to ensure that an organization's information systems align with overall business
North Carolina Department of State Treasurer
 North Carolina Department of State Treasurer RICHARD H. MOORE TREASURER State and Local Government Finance Division and the Local Government Commission August 11, 2005 JANICE BURKE DEPUTY TREASURER Memorandum
North Carolina Department of State Treasurer RICHARD H. MOORE TREASURER State and Local Government Finance Division and the Local Government Commission August 11, 2005 JANICE BURKE DEPUTY TREASURER Memorandum
Position Description IT Auditor
 Position Title IT Auditor Position Number Portfolio Performance and IT Audit Location Victoria Supervisor s Title IT Audit Director Travel Required Yes FOR OAG HR USE ONLY: Approved Classification or Leadership
Position Title IT Auditor Position Number Portfolio Performance and IT Audit Location Victoria Supervisor s Title IT Audit Director Travel Required Yes FOR OAG HR USE ONLY: Approved Classification or Leadership
Information Technology Audit
 O L A OFFICE OF THE LEGISLATIVE AUDITOR STATE OF MINNESOTA FINANCIAL AUDIT DIVISION REPORT Minnesota State Retirement System Information Technology Audit June 23, 2009 Report 09-23 FINANCIAL AUDIT DIVISION
O L A OFFICE OF THE LEGISLATIVE AUDITOR STATE OF MINNESOTA FINANCIAL AUDIT DIVISION REPORT Minnesota State Retirement System Information Technology Audit June 23, 2009 Report 09-23 FINANCIAL AUDIT DIVISION
State of Rhode Island Department of Administration Division of Information Technol
 Division of Information Technol 1. Background Physical and environmental security controls protect information system facilities from physical and environmental threats. Physical access to facilities and
Division of Information Technol 1. Background Physical and environmental security controls protect information system facilities from physical and environmental threats. Physical access to facilities and
Chapter 18 SaskPower Managing the Risk of Cyber Incidents 1.0 MAIN POINTS
 Chapter 18 SaskPower Managing the Risk of Cyber Incidents 1.0 MAIN POINTS The Saskatchewan Power Corporation (SaskPower) is the principal supplier of power in Saskatchewan with its mission to deliver power
Chapter 18 SaskPower Managing the Risk of Cyber Incidents 1.0 MAIN POINTS The Saskatchewan Power Corporation (SaskPower) is the principal supplier of power in Saskatchewan with its mission to deliver power
DATA CENTER OPERATIONS CALIFORNIA STATE UNIVERSITY, DOMINGUEZ HILLS. Audit Report June 15, 2012
 DATA CENTER OPERATIONS CALIFORNIA STATE UNIVERSITY, DOMINGUEZ HILLS Audit Report 12-31 June 15, 2012 Henry Mendoza, Chair William Hauck Steven M. Glazer Glen O. Toney Members, Committee on Audit University
DATA CENTER OPERATIONS CALIFORNIA STATE UNIVERSITY, DOMINGUEZ HILLS Audit Report 12-31 June 15, 2012 Henry Mendoza, Chair William Hauck Steven M. Glazer Glen O. Toney Members, Committee on Audit University
Information Technology Disaster Recovery Planning Audit Redacted Public Report
 1200, Scotia Place, Tower 1 10060 Jasper Avenue Edmonton, Alberta T5J 3R8 edmonton.ca/auditor Information Technology Disaster Recovery Planning Audit Redacted Public Report June 12, 2018 City of Edmonton
1200, Scotia Place, Tower 1 10060 Jasper Avenue Edmonton, Alberta T5J 3R8 edmonton.ca/auditor Information Technology Disaster Recovery Planning Audit Redacted Public Report June 12, 2018 City of Edmonton
ASSEMBLY, No STATE OF NEW JERSEY. 217th LEGISLATURE INTRODUCED FEBRUARY 4, 2016
 ASSEMBLY, No. STATE OF NEW JERSEY th LEGISLATURE INTRODUCED FEBRUARY, 0 Sponsored by: Assemblywoman VALERIE VAINIERI HUTTLE District (Bergen) Assemblyman DANIEL R. BENSON District (Mercer and Middlesex)
ASSEMBLY, No. STATE OF NEW JERSEY th LEGISLATURE INTRODUCED FEBRUARY, 0 Sponsored by: Assemblywoman VALERIE VAINIERI HUTTLE District (Bergen) Assemblyman DANIEL R. BENSON District (Mercer and Middlesex)
REPORT 2015/149 INTERNAL AUDIT DIVISION
 INTERNAL AUDIT DIVISION REPORT 2015/149 Audit of the information and communications technology operations in the Investment Management Division of the United Nations Joint Staff Pension Fund Overall results
INTERNAL AUDIT DIVISION REPORT 2015/149 Audit of the information and communications technology operations in the Investment Management Division of the United Nations Joint Staff Pension Fund Overall results
Subject: Audit Report 16-50, IT Disaster Recovery, California State University, Fresno
 Larry Mandel Vice Chancellor and Chief Audit Officer Office of Audit and Advisory Services 401 Golden Shore, 4th Floor Long Beach, CA 90802-4210 562-951-4430 562-951-4955 (Fax) lmandel@calstate.edu February
Larry Mandel Vice Chancellor and Chief Audit Officer Office of Audit and Advisory Services 401 Golden Shore, 4th Floor Long Beach, CA 90802-4210 562-951-4430 562-951-4955 (Fax) lmandel@calstate.edu February
1997 Minna Laws Chap. February 1, The Honorable Jesse Ventura Governor 130 State Capitol Building
 This document is made available electronically by the Minnesota Legislative Reference Library as part of an ongoing digital archiving project. http://www.leg.state.mn.us/lrl/lrl.asp Department of Administration
This document is made available electronically by the Minnesota Legislative Reference Library as part of an ongoing digital archiving project. http://www.leg.state.mn.us/lrl/lrl.asp Department of Administration
DISASTER PREPAREDNESS IN THE COUNTY: IMPROVEMENTS NEEDED
 2006-2007 SANTA CLARA COUNTY CIVIL GRAND JURY REPORT Summary DISASTER PREPAREDNESS IN THE COUNTY: IMPROVEMENTS NEEDED Disaster events that have occurred in Santa Clara County (County) have heightened interest
2006-2007 SANTA CLARA COUNTY CIVIL GRAND JURY REPORT Summary DISASTER PREPAREDNESS IN THE COUNTY: IMPROVEMENTS NEEDED Disaster events that have occurred in Santa Clara County (County) have heightened interest
Apex Information Security Policy
 Apex Information Security Policy Table of Contents Sr.No Contents Page No 1. Objective 4 2. Policy 4 3. Scope 4 4. Approval Authority 5 5. Purpose 5 6. General Guidelines 7 7. Sub policies exist for 8
Apex Information Security Policy Table of Contents Sr.No Contents Page No 1. Objective 4 2. Policy 4 3. Scope 4 4. Approval Authority 5 5. Purpose 5 6. General Guidelines 7 7. Sub policies exist for 8
The University of British Columbia Board of Governors
 The University of British Columbia Board of Governors Policy No.: 118 Approval Date: February 15, 2016 Responsible Executive: University Counsel Title: Safety and Security Cameras Background and Purposes:
The University of British Columbia Board of Governors Policy No.: 118 Approval Date: February 15, 2016 Responsible Executive: University Counsel Title: Safety and Security Cameras Background and Purposes:
NEN The Education Network
 NEN The Education Network School e-security Checklist This checklist sets out 20 e-security controls that, if implemented effectively, will help to ensure that school networks are kept secure and protected
NEN The Education Network School e-security Checklist This checklist sets out 20 e-security controls that, if implemented effectively, will help to ensure that school networks are kept secure and protected
Title of Nomination: Security Policies and Standards Project/System Manager: Donna Crutcher Title: State Security Manager Agency: Department:
 Title of Nomination: Security Policies and Standards Project/System Manager: Donna Crutcher Title: State Security Manager Agency: Department: Information Technology Address: 505 East King Street, Room
Title of Nomination: Security Policies and Standards Project/System Manager: Donna Crutcher Title: State Security Manager Agency: Department: Information Technology Address: 505 East King Street, Room
AUDIT REPORT. Network Assessment Audit Audit Opinion: Needs Improvement. Date: December 15, Report Number: 2014-IT-03
 AUDIT REPORT Network Assessment Audit Audit Opinion: Needs Improvement Date: December 15, 2014 Report Number: 2014-IT-03 Table of Contents: Page Executive Summary Background 1 Audit Objectives and Scope
AUDIT REPORT Network Assessment Audit Audit Opinion: Needs Improvement Date: December 15, 2014 Report Number: 2014-IT-03 Table of Contents: Page Executive Summary Background 1 Audit Objectives and Scope
Number: USF System Emergency Management Responsible Office: Administrative Services
 POLICY USF System USF USFSP USFSM Number: 6-010 Title: USF System Emergency Management Responsible Office: Administrative Services Date of Origin: 2-7-12 Date Last Amended: 8-24-16 (technical) Date Last
POLICY USF System USF USFSP USFSM Number: 6-010 Title: USF System Emergency Management Responsible Office: Administrative Services Date of Origin: 2-7-12 Date Last Amended: 8-24-16 (technical) Date Last
Information Security Incident Response Plan
 Information Security Incident Response Plan Purpose It is the objective of the university to maintain secure systems and data. In order to comply with federal, state, and local law and contractual obligations,
Information Security Incident Response Plan Purpose It is the objective of the university to maintain secure systems and data. In order to comply with federal, state, and local law and contractual obligations,
Virginia State University Policies Manual. Title: Information Security Program Policy: 6110
 Purpose Virginia State University (VSU) uses information to perform the business services and functions necessary to fulfill its mission. VSU information is contained in many different mediums including
Purpose Virginia State University (VSU) uses information to perform the business services and functions necessary to fulfill its mission. VSU information is contained in many different mediums including
manner. IOPA conducts its reviews in conformance with Government Auditing Standards issued by the Comptroller General of the United States.
 PCAOB Public Company Accounting Oversight Board 1666 K Street, N.W. Washington, DC 20006 Telephone: (202) 207-9100 Facsimile: (202) 862-8430 www.pcaobus.org The Honorable Christopher Cox Chairman Securities
PCAOB Public Company Accounting Oversight Board 1666 K Street, N.W. Washington, DC 20006 Telephone: (202) 207-9100 Facsimile: (202) 862-8430 www.pcaobus.org The Honorable Christopher Cox Chairman Securities
Computer Security Incident Response Plan. Date of Approval: 23-FEB-2014
 Computer Security Incident Response Plan Name of Approver: Mary Ann Blair Date of Approval: 23-FEB-2014 Date of Review: 31-MAY-2016 Effective Date: 23-FEB-2014 Name of Reviewer: John Lerchey Table of Contents
Computer Security Incident Response Plan Name of Approver: Mary Ann Blair Date of Approval: 23-FEB-2014 Date of Review: 31-MAY-2016 Effective Date: 23-FEB-2014 Name of Reviewer: John Lerchey Table of Contents
Texas A&M University: Learning Management System General & Application Controls Review
 Overall Conclusion Overall, the controls established over the primary learning management system at Texas A&M University, Blackboard Learn (ecampus), are effective in providing reasonable assurance that
Overall Conclusion Overall, the controls established over the primary learning management system at Texas A&M University, Blackboard Learn (ecampus), are effective in providing reasonable assurance that
Privacy Breach Policy
 1. PURPOSE 1.1 The purpose of this policy is to guide NB-IRDT employees and approved users on how to proceed in the event of a privacy breach, and to demonstrate to stakeholders that a systematic procedure
1. PURPOSE 1.1 The purpose of this policy is to guide NB-IRDT employees and approved users on how to proceed in the event of a privacy breach, and to demonstrate to stakeholders that a systematic procedure
Identity Theft Prevention Program. Effective beginning August 1, 2009
 Identity Theft Prevention Program Effective beginning August 1, 2009 I. PROGRAM ADOPTION Christian Brothers University developed this Identity Theft Prevention Program pursuant to the Federal Trade Commission's
Identity Theft Prevention Program Effective beginning August 1, 2009 I. PROGRAM ADOPTION Christian Brothers University developed this Identity Theft Prevention Program pursuant to the Federal Trade Commission's
TEL2813/IS2820 Security Management
 TEL2813/IS2820 Security Management Security Management Models And Practices Lecture 6 Jan 27, 2005 Introduction To create or maintain a secure environment 1. Design working security plan 2. Implement management
TEL2813/IS2820 Security Management Security Management Models And Practices Lecture 6 Jan 27, 2005 Introduction To create or maintain a secure environment 1. Design working security plan 2. Implement management
79th OREGON LEGISLATIVE ASSEMBLY Regular Session. Senate Bill 90
 th OREGON LEGISLATIVE ASSEMBLY-- Regular Session Senate Bill 0 Printed pursuant to Senate Interim Rule. by order of the President of the Senate in conformance with presession filing rules, indicating neither
th OREGON LEGISLATIVE ASSEMBLY-- Regular Session Senate Bill 0 Printed pursuant to Senate Interim Rule. by order of the President of the Senate in conformance with presession filing rules, indicating neither
Criminal Case Information System for Public Defenders [Section 18B.10 of S. L , as amended by Section 18A.2 of S.L.
 Criminal Case Information System for Public Defenders [Section 18B.10 of S. L. 2013-360, as amended by Section 18A.2 of S.L. 2014-100] Technology Services Division July 1, 2015 Introduction Section 18B.10
Criminal Case Information System for Public Defenders [Section 18B.10 of S. L. 2013-360, as amended by Section 18A.2 of S.L. 2014-100] Technology Services Division July 1, 2015 Introduction Section 18B.10
Any observations not included in this report were discussed with your staff at the informal exit conference and may be subject to follow-up.
 Larry Mandel Vice Chancellor and Chief Audit Officer Audit and Advisory Services 401 Golden Shore, 4th Floor Long Beach, CA 90802-4210 562-951-4430 562-951-4955 (Fax) lmandel@calstate.edu June 5, 2018
Larry Mandel Vice Chancellor and Chief Audit Officer Audit and Advisory Services 401 Golden Shore, 4th Floor Long Beach, CA 90802-4210 562-951-4430 562-951-4955 (Fax) lmandel@calstate.edu June 5, 2018
INFORMATION TECHNOLOGY DATA MANAGEMENT PROCEDURES AND GOVERNANCE STRUCTURE BALL STATE UNIVERSITY OFFICE OF INFORMATION SECURITY SERVICES
 INFORMATION TECHNOLOGY DATA MANAGEMENT PROCEDURES AND GOVERNANCE STRUCTURE BALL STATE UNIVERSITY OFFICE OF INFORMATION SECURITY SERVICES 1. INTRODUCTION If you are responsible for maintaining or using
INFORMATION TECHNOLOGY DATA MANAGEMENT PROCEDURES AND GOVERNANCE STRUCTURE BALL STATE UNIVERSITY OFFICE OF INFORMATION SECURITY SERVICES 1. INTRODUCTION If you are responsible for maintaining or using
DATA CENTER OPERATIONS CALIFORNIA STATE UNIVERSITY, LONG BEACH. Audit Report July 24, 2012
 DATA CENTER OPERATIONS CALIFORNIA STATE UNIVERSITY, LONG BEACH Audit Report 12-32 July 24, 2012 Henry Mendoza, Chair Steven M. Glazer William Hauck Glen O. Toney Members, Committee on Audit University
DATA CENTER OPERATIONS CALIFORNIA STATE UNIVERSITY, LONG BEACH Audit Report 12-32 July 24, 2012 Henry Mendoza, Chair Steven M. Glazer William Hauck Glen O. Toney Members, Committee on Audit University
Subject: Audit Report 18-84, IT Disaster Recovery, California State University, Sacramento
 Larry Mandel Vice Chancellor and Chief Audit Officer Audit and Advisory Services 401 Golden Shore, 4th Floor Long Beach, CA 90802-4210 562-951-4430 562-951-4955 (Fax) lmandel@calstate.edu October 23, 2018
Larry Mandel Vice Chancellor and Chief Audit Officer Audit and Advisory Services 401 Golden Shore, 4th Floor Long Beach, CA 90802-4210 562-951-4430 562-951-4955 (Fax) lmandel@calstate.edu October 23, 2018
SECURITY & PRIVACY DOCUMENTATION
 Okta s Commitment to Security & Privacy SECURITY & PRIVACY DOCUMENTATION (last updated September 15, 2017) Okta is committed to achieving and preserving the trust of our customers, by providing a comprehensive
Okta s Commitment to Security & Privacy SECURITY & PRIVACY DOCUMENTATION (last updated September 15, 2017) Okta is committed to achieving and preserving the trust of our customers, by providing a comprehensive
Prevention of Identity Theft in Student Financial Transactions AP 5800
 Reference: Fair and Accurate Credit Transactions Act (Pub. L. 108-159) The Board recognizes that some activities of the Shasta-Tehama-Trinity Joint Community College District, "District," are subject to
Reference: Fair and Accurate Credit Transactions Act (Pub. L. 108-159) The Board recognizes that some activities of the Shasta-Tehama-Trinity Joint Community College District, "District," are subject to
UTAH VALLEY UNIVERSITY Policies and Procedures
 Page 1 of 5 POLICY TITLE Section Subsection Responsible Office Private Sensitive Information Facilities, Operations, and Information Technology Information Technology Office of the Vice President of Information
Page 1 of 5 POLICY TITLE Section Subsection Responsible Office Private Sensitive Information Facilities, Operations, and Information Technology Information Technology Office of the Vice President of Information
Trust Services Principles and Criteria
 Trust Services Principles and Criteria Security Principle and Criteria The security principle refers to the protection of the system from unauthorized access, both logical and physical. Limiting access
Trust Services Principles and Criteria Security Principle and Criteria The security principle refers to the protection of the system from unauthorized access, both logical and physical. Limiting access
Standard CIP Cyber Security Critical Cyber Asset Identification
 Standard CIP 002 1 Cyber Security Critical Cyber Asset Identification Standard Development Roadmap This section is maintained by the drafting team during the development of the standard and will be removed
Standard CIP 002 1 Cyber Security Critical Cyber Asset Identification Standard Development Roadmap This section is maintained by the drafting team during the development of the standard and will be removed
New York Department of Financial Services Cybersecurity Regulation Compliance and Certification Deadlines
 New York Department of Financial Services Cybersecurity Regulation Compliance and Certification Deadlines New York Department of Financial Services ( DFS ) Regulation 23 NYCRR 500 requires that entities
New York Department of Financial Services Cybersecurity Regulation Compliance and Certification Deadlines New York Department of Financial Services ( DFS ) Regulation 23 NYCRR 500 requires that entities
SALARY $ $72.54 Hourly $3, $5, Biweekly $8, $12, Monthly $103, $150, Annually
 SALARY $49.72 - $72.54 Hourly $3,977.88 - $5,803.27 Biweekly $8,618.75 - $12,573.75 Monthly $103,425.00 - $150,885.00 Annually ISSUE DATE: 03/21/18 THE POSITION DIRECTOR OF CYBER SECURITY OPEN TO THE PUBLIC
SALARY $49.72 - $72.54 Hourly $3,977.88 - $5,803.27 Biweekly $8,618.75 - $12,573.75 Monthly $103,425.00 - $150,885.00 Annually ISSUE DATE: 03/21/18 THE POSITION DIRECTOR OF CYBER SECURITY OPEN TO THE PUBLIC
[Utility Name] Identity Theft Prevention Program
![[Utility Name] Identity Theft Prevention Program [Utility Name] Identity Theft Prevention Program](/thumbs/77/75712648.jpg) [Utility Name] Identity Theft Prevention Program Effective beginning, 2008 Minnesota Municipal Utilities Association Sample Red Flag policy I. PROGRAM ADOPTION The [Utility Name] ("Utility") developed
[Utility Name] Identity Theft Prevention Program Effective beginning, 2008 Minnesota Municipal Utilities Association Sample Red Flag policy I. PROGRAM ADOPTION The [Utility Name] ("Utility") developed
Standard CIP Cyber Security Critical Cyber Asset Identification
 Standard CIP 002 1 Cyber Security Critical Cyber Asset Identification Standard Development Roadmap This section is maintained by the drafting team during the development of the standard and will be removed
Standard CIP 002 1 Cyber Security Critical Cyber Asset Identification Standard Development Roadmap This section is maintained by the drafting team during the development of the standard and will be removed
Reviewed by ADM(RS) in accordance with the Access to Information Act. Information UNCLASSIFIED.
 Assistant Deputy Minister (Review Services) Reviewed by in accordance with the Access to Information Act. Information UNCLASSIFIED. Security Audits: Management Action Plan Follow-up December 2015 1850-3-003
Assistant Deputy Minister (Review Services) Reviewed by in accordance with the Access to Information Act. Information UNCLASSIFIED. Security Audits: Management Action Plan Follow-up December 2015 1850-3-003
Cybersecurity & Privacy Enhancements
 Business, Industry and Government Cybersecurity & Privacy Enhancements John Lainhart, Director, Grant Thornton The National Institute of Standards and Technology (NIST) is in the process of updating their
Business, Industry and Government Cybersecurity & Privacy Enhancements John Lainhart, Director, Grant Thornton The National Institute of Standards and Technology (NIST) is in the process of updating their
Office of Internal Audit
 Office of Internal Audit March 16, 2017 Dr. Kirk Calhoun, President UT Health Northeast 11937 U. S. Hwy 271 Tyler, TX 75708 Dr. Calhoun: We have completed the Security Control Standards as part of our
Office of Internal Audit March 16, 2017 Dr. Kirk Calhoun, President UT Health Northeast 11937 U. S. Hwy 271 Tyler, TX 75708 Dr. Calhoun: We have completed the Security Control Standards as part of our
The CISO is the owner of the vulnerability management process. This person designs the process and ensures is implemented as designed.
 University of Alabama at Birmingham VULNERABILITY MANAGEMENT RULE May 19, 2017 Related Policies, Procedures, and Resources Data Protection and Security Policy Data Classification Rule 1.0 Introduction
University of Alabama at Birmingham VULNERABILITY MANAGEMENT RULE May 19, 2017 Related Policies, Procedures, and Resources Data Protection and Security Policy Data Classification Rule 1.0 Introduction
Any observations not included in this report were discussed with your staff at the informal exit conference and may be subject to follow-up.
 Larry Mandel Vice Chancellor and Chief Audit Officer Audit and Advisory Services 401 Golden Shore, 4th Floor Long Beach, CA 90802-4210 562-951-4430 562-951-4955 (Fax) lmandel@calstate.edu October 10, 2018
Larry Mandel Vice Chancellor and Chief Audit Officer Audit and Advisory Services 401 Golden Shore, 4th Floor Long Beach, CA 90802-4210 562-951-4430 562-951-4955 (Fax) lmandel@calstate.edu October 10, 2018
NEW YORK CYBERSECURITY REGULATION COMPLIANCE GUIDE
 COMPLIANCE ADVISOR NEW YORK CYBERSECURITY REGULATION COMPLIANCE GUIDE A PUBLICATION BY THE EXCESS LINE ASSOCIATION OF NEW YORK One Exchange Plaza 55 Broadway 29th Floor New York, New York 10006-3728 Telephone:
COMPLIANCE ADVISOR NEW YORK CYBERSECURITY REGULATION COMPLIANCE GUIDE A PUBLICATION BY THE EXCESS LINE ASSOCIATION OF NEW YORK One Exchange Plaza 55 Broadway 29th Floor New York, New York 10006-3728 Telephone:
University of Pittsburgh Security Assessment Questionnaire (v1.7)
 Technology Help Desk 412 624-HELP [4357] technology.pitt.edu University of Pittsburgh Security Assessment Questionnaire (v1.7) Directions and Instructions for completing this assessment The answers provided
Technology Help Desk 412 624-HELP [4357] technology.pitt.edu University of Pittsburgh Security Assessment Questionnaire (v1.7) Directions and Instructions for completing this assessment The answers provided
Cyber Security Program
 Cyber Security Program Cyber Security Program Goals and Objectives Goals Provide comprehensive Security Education and Awareness to the University community Build trust with the University community by
Cyber Security Program Cyber Security Program Goals and Objectives Goals Provide comprehensive Security Education and Awareness to the University community Build trust with the University community by
IT Audit Process Prof. Liang Yao Week Six IT Audit Planning
 Week Six IT Audit Planning IT Audit Planning Process Institute of Internal Audit Standards - Section 2010: Planning The chief audit executive must establish a risk-based plan to determine the priorities
Week Six IT Audit Planning IT Audit Planning Process Institute of Internal Audit Standards - Section 2010: Planning The chief audit executive must establish a risk-based plan to determine the priorities
Corporate Security & Emergency Management Summary of Submitted 2015 Budget From Rates
 Corporate Security & Emergency Management Summary of Submitted 2015 From Rates Service Expense 2014 2015 Revised Non Tax Revenue Net Tax Supported Expense Draft Non Tax Revenue Net Tax Supported Increase
Corporate Security & Emergency Management Summary of Submitted 2015 From Rates Service Expense 2014 2015 Revised Non Tax Revenue Net Tax Supported Expense Draft Non Tax Revenue Net Tax Supported Increase
Page 1 of 15. Applicability. Compatibility EACMS PACS. Version 5. Version 3 PCA EAP. ERC NO ERC Low Impact BES. ERC Medium Impact BES
 002 5 R1. Each Responsible Entity shall implement a process that considers each of the following assets for purposes of parts 1.1 through 1.3: i. Control Centers and backup Control Centers; ii. Transmission
002 5 R1. Each Responsible Entity shall implement a process that considers each of the following assets for purposes of parts 1.1 through 1.3: i. Control Centers and backup Control Centers; ii. Transmission
Information Security Incident Response Plan
 Information Security Incident Response Plan Purpose It is the objective of the university to maintain secure systems and data. In order to comply with federal, state, and local law and contractual obligations,
Information Security Incident Response Plan Purpose It is the objective of the university to maintain secure systems and data. In order to comply with federal, state, and local law and contractual obligations,
IT SECURITY OFFICER. Department: Information Technology. Pay Range: Professional 18
 Pierce County Classification Description IT SECURITY OFFICER Department: Information Technology Job Class #: 634900 Pay Range: Professional 18 FLSA: Exempt Represented: No Classification descriptions are
Pierce County Classification Description IT SECURITY OFFICER Department: Information Technology Job Class #: 634900 Pay Range: Professional 18 FLSA: Exempt Represented: No Classification descriptions are
Policies & Regulations
 Policies & Regulations Email Policy Number Effective Revised Review Responsible Division/Department: Administration and Finance / Office of the CIO/ Information Technology Services (ITS) New Policy Major
Policies & Regulations Email Policy Number Effective Revised Review Responsible Division/Department: Administration and Finance / Office of the CIO/ Information Technology Services (ITS) New Policy Major
