OPTIMUM DETECTION WITHOUT COMPROMISE. DRA_0291_Scanna_CapBro_AW.indd 1 21/02/ :16
|
|
|
- Joanna Carpenter
- 6 years ago
- Views:
Transcription
1 OPTIMUM DETECTION WITHOUT COMPROMISE DRA_0291_Scanna_CapBro_AW.indd 1 21/02/ :16
2 WITHOUT COMPROMI E DRA_0291_Scanna_CapBro_AW.indd 2 21/02/ :16
3 Scanna - leading manufacturers of portable X-ray and postal security equipment Scanna designs and manufactures portable X-ray and mail screening equipment for the Defence, Security, Commercial and Industrial sectors. Based in the UK, with operations in the USA and Middle East, and a worldwide network of representatives, we provide critical on-site support to our customers globally. Our products are frequently used in life-threatening situations, so our ethos of without compromise underpins everything we do - from design and manufacture, through to installation and support. Every component of every device is engineered to ensure optimum detection performance and outstanding quality. In today s increasingly unstable geopolitical landscape, organisations must recognise and cope with diverse threats from multiple sources, so Scanna s product range continually evolves to keep pace with the changing threat matrix. Our equipment is utilised in diverse environments, from high-risk conflict zones to normal commercial and industrial settings, and in applications as varied as Bomb Disposal, Prison Cell Search, TSCM and Mail Room Protection. Our threat screening and detection equipment is developed by a team of specialists who combine leading-edge technical capabilities with vast experience in the field. The result is a range of world-leading X-ray and scanning equipment that is rugged, robust and simple to use in even the most extreme conditions. Our client list spans more than 100 countries and includes UK MoD, US DoD and many other NATO forces and Federal Agencies, plus a wide range of Governmental and Bluechip Commercial Organisations. Around the world, Scanna threat screening systems help protect military bases, government and embassy buildings, critical infrastructure and private-sector infrastructure and personnel. Scanna - protecting people and infrastructure worldwide, without compromise. 2 DRA_0291_Scanna_CapBro_AW.indd 3 21/02/ :16
4 DEEP IN IGHT DRA_0291_Scanna_CapBro_AW.indd 4 21/02/ :16
5 Defence Scanna has a long track-record of providing high-performance detection equipment to the Defence sector, so we have a deep insight into the challenges our customers face. Our products combine leading-edge, field-proven technologies with simple-to-use functionality, enabling operators to make intelligent decisions in the most challenging of circumstances. Our portable X-ray devices deliver industry-leading image quality - an indispensable asset when inspecting IEDs or carrying out baggage searches. Scanna products can be deployed in a range of scenarios, including Explosive Ordnance Disposal, Forensic Search, Weapons Intelligence, Base and Building Security, Demilitarisation, Ammunition Inspection and Technical Surveillance Counter Measures. Engineered to perform under the most demanding conditions in diverse and extreme environments, Scanna s portable detection systems offer best-in-class solutions for the protection of personnel and critical infrastructure. WITHOUT COMPROMISE. 4 DRA_0291_Scanna_CapBro_AW.indd 5 21/02/ :16
6 VER ATILE SOLUTIONS DRA_0291_Scanna_CapBro_AW.indd 6 21/02/ :16
7 Security Scanna responds quickly to its customers changing needs, creating high-performance screening and detection products that enhance the security of buildings and public events and facilitate mobile deployment across the law enforcement and transport sectors. Our detection equipment can be utilised in vehicle checks at border crossings, in the search of prison cells, the investigation of suspicious and unattended luggage and packages at transport hubs, and to reinforce security screening at sporting, commercial and cultural events. Our postal screening equipment includes both electronic and X-ray based technologies, Compliant with recognised international standards, it is compact, robust and very easy to operate. Scanna s client list includes multinational corporations and a great many governmental bodies, including Border Security Agencies and Counter Narcotics Teams. Our customers put great faith not only in our products, but also in our comprehensive support services that train their staff and help keep their security systems fully operational 24/7. WITHOUT COMPROMISE. 6 DRA_0291_Scanna_CapBro_AW.indd 7 21/02/ :16
8 DIVER E APPLICATIONS DRA_0291_Scanna_CapBro_AW.indd 8 21/02/ :16
9 Industrial Scanna X-ray and postal screening equipment has a diverse range of applications in the industrial and commercial sectors, and we have a wealth of experience devising cost-effective technical solutions that deliver optimal X-ray imaging performance and fast on screen acquisition time. Typical applications include the inspection of illegally manufactured or counterfeit goods, X-ray inspection for reverse engineering, and lifecycle quality control of manufactured goods such as ammunition. Practical application also extends to testing the integrity of body armour, armour plates and other military equipment and materials, ensuring compliance with recognised protection standards and defined customer expectations. Our product range includes lightweight mobile X-ray scanners that are portable, easy to set up, and suitable for laboratory integration or for providing a robust scanning solution in hard-to-reach areas. WITHOUT COMPROMISE. 8 DRA_0291_Scanna_CapBro_AW.indd 9 21/02/ :16
10 Worldwide Support Scanna designs and manufactures highperformance equipment of unsurpassed quality. Yet we recognise that this goes only part way to meeting our customers requirements. That s why we provide comprehensive training and support, on hand wherever and whenever our customers need it. From delivery, installation and training, through to servicing and maintenance by international Field Service Teams, our technical support ensures maximum equipment life and optimal ongoing performance. Our clients are able to draw on the knowledge and know-how of our professional staff, which includes leading technical experts and former military personnel with a wealth of experience at the sharp end of the industry. This capability enables Scanna to offer consultancy and advice on a broad range of security and defence issues, from selecting the most appropriate equipment, to designing bespoke solutions to meet specific challenges. WITHOUT COMPROMISE. HIGHLY RE PONSIVE DRA_0291_Scanna_CapBro_AW.indd 10 21/02/ :16
11 10 DRA_0291_Scanna_CapBro_AW.indd 11 21/02/ :16
12 SCANNA MSC Ltd 223 Regent Street, London W1B 2EB Telephone: +44(0) Fax: +44(0) Designed by DRA_0291_Scanna_CapBro_AW.indd 12 21/02/ :16
WITHOUT COMPROMISE. Cutting edge screening and detection solutions.
 WITHOUT COMPROMISE Cutting edge screening and detection solutions. www.scanna-msc.com WITHOUT COMPROMISE Cutting edge screening and detection solutions. www.scanna-msc.com Digital CCD Portable X-ray System
WITHOUT COMPROMISE Cutting edge screening and detection solutions. www.scanna-msc.com WITHOUT COMPROMISE Cutting edge screening and detection solutions. www.scanna-msc.com Digital CCD Portable X-ray System
An Introduction To Security Planning
 An Introduction To Security Planning A strategic planning consultancy designed to enhance the management and operational delivery of protective security services within any business and organisation 1
An Introduction To Security Planning A strategic planning consultancy designed to enhance the management and operational delivery of protective security services within any business and organisation 1
Defence services. Independent systems and technology advice that delivers real value. Systems and Engineering Technology
 Defence services Independent systems and technology advice that delivers real value Systems and Engineering Technology Frazer-Nash Consultancy Working in the UK and internationally, Frazer-Nash is making
Defence services Independent systems and technology advice that delivers real value Systems and Engineering Technology Frazer-Nash Consultancy Working in the UK and internationally, Frazer-Nash is making
Max Security Solutions
 Max Security Solutions Max Security Solutions Proactive Risk Management What we do Max Security provides comprehensive security and risk management solutions for the business sector, private clients and
Max Security Solutions Max Security Solutions Proactive Risk Management What we do Max Security provides comprehensive security and risk management solutions for the business sector, private clients and
CYBER RESILIENCE & INCIDENT RESPONSE
 CYBER RESILIENCE & INCIDENT RESPONSE www.nccgroup.trust Introduction The threat landscape has changed dramatically over the last decade. Once the biggest threats came from opportunist attacks and preventable
CYBER RESILIENCE & INCIDENT RESPONSE www.nccgroup.trust Introduction The threat landscape has changed dramatically over the last decade. Once the biggest threats came from opportunist attacks and preventable
Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services
 Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
COUNTERING IMPROVISED EXPLOSIVE DEVICES
 COUNTERING IMPROVISED EXPLOSIVE DEVICES FEBRUARY 26, 2013 COUNTERING IMPROVISED EXPLOSIVE DEVICES Strengthening U.S. Policy Improvised explosive devices (IEDs) remain one of the most accessible weapons
COUNTERING IMPROVISED EXPLOSIVE DEVICES FEBRUARY 26, 2013 COUNTERING IMPROVISED EXPLOSIVE DEVICES Strengthening U.S. Policy Improvised explosive devices (IEDs) remain one of the most accessible weapons
Salamanca Risk Management. Global Security and Risk Management Solutions. www. salamancarm. com
 Salamanca Risk Global Security and Risk Solutions www. salamancarm. com Salamanca Risk Global Security and Risk Solutions Salamanca Risk provides security risk management services to our clients in order
Salamanca Risk Global Security and Risk Solutions www. salamancarm. com Salamanca Risk Global Security and Risk Solutions Salamanca Risk provides security risk management services to our clients in order
keeping executives safe
 keeping executives safe Neil Austin and Lawrence Dando, two career surveillance specialists, established Mint Executive in 2015, having worked on and managed some of the most complex Police operations
keeping executives safe Neil Austin and Lawrence Dando, two career surveillance specialists, established Mint Executive in 2015, having worked on and managed some of the most complex Police operations
Security by Default: Enabling Transformation Through Cyber Resilience
 Security by Default: Enabling Transformation Through Cyber Resilience FIVE Steps TO Better Security Hygiene Solution Guide Introduction Government is undergoing a transformation. The global economic condition,
Security by Default: Enabling Transformation Through Cyber Resilience FIVE Steps TO Better Security Hygiene Solution Guide Introduction Government is undergoing a transformation. The global economic condition,
How AlienVault ICS SIEM Supports Compliance with CFATS
 How AlienVault ICS SIEM Supports Compliance with CFATS (Chemical Facility Anti-Terrorism Standards) The U.S. Department of Homeland Security has released an interim rule that imposes comprehensive federal
How AlienVault ICS SIEM Supports Compliance with CFATS (Chemical Facility Anti-Terrorism Standards) The U.S. Department of Homeland Security has released an interim rule that imposes comprehensive federal
GDPR: Get Prepared! A Checklist for Implementing a Security and Event Management Tool. Contact. Ashley House, Ashley Road London N17 9LZ
 GDPR: Get Prepared! A Checklist for Implementing a Security and Event Management Tool Contact Ashley House, Ashley Road London N17 9LZ 0333 234 4288 info@networkiq.co.uk The General Data Privacy Regulation
GDPR: Get Prepared! A Checklist for Implementing a Security and Event Management Tool Contact Ashley House, Ashley Road London N17 9LZ 0333 234 4288 info@networkiq.co.uk The General Data Privacy Regulation
Simplifying Information Sharing Across Security Boundaries. Deep-Secure Overview 12 th November 2013, Prague. Presentation to.
 Simplifying Information Sharing Across Security Boundaries Presentation to Deep-Secure Overview 12 th November 2013, Prague 10 October 2011 1 What we do Deep-Secure offer solutions that help organisations
Simplifying Information Sharing Across Security Boundaries Presentation to Deep-Secure Overview 12 th November 2013, Prague 10 October 2011 1 What we do Deep-Secure offer solutions that help organisations
T-SURE VIGILANCE CYBER SECURITY OPERATIONS CENTRE
 www.thalesgroup.com/uk SECURE COMMUNICATIONS AND INFORMATION SYSTEMS T-SURE VIGILANCE CYBER SECURITY OPERATIONS CENTRE An enterprise-level bespoke security service for the detection and response to cyber
www.thalesgroup.com/uk SECURE COMMUNICATIONS AND INFORMATION SYSTEMS T-SURE VIGILANCE CYBER SECURITY OPERATIONS CENTRE An enterprise-level bespoke security service for the detection and response to cyber
COUNTER-TERRORISM. Future-oriented policing projects
 COUNTER-TERRORISM Future-oriented policing projects In keeping with its consistent support of international organisations to strengthen the global community, the United Arab Emirates through the Interpol
COUNTER-TERRORISM Future-oriented policing projects In keeping with its consistent support of international organisations to strengthen the global community, the United Arab Emirates through the Interpol
AVIATION. The leading provider of integrated security solutions in the field of aviation fjcsecurity.com/fjcaviation
 AVIATION The leading provider of integrated security solutions in the field of aviation. 718-244-1400 fjcsecurity.com/fjcaviation 718-244-1400 fjcsecurity.com/fjcaviation HARDWORKING, RELIABLE EXPERTS
AVIATION The leading provider of integrated security solutions in the field of aviation. 718-244-1400 fjcsecurity.com/fjcaviation 718-244-1400 fjcsecurity.com/fjcaviation HARDWORKING, RELIABLE EXPERTS
SYMANTEC: SECURITY ADVISORY SERVICES. Symantec Security Advisory Services The World Leader in Information Security
 SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
Welcome to a world where technology flows through the heart of your business environment. Welcome to CDC
 Welcome to a world where technology flows through the heart of your business environment Welcome to CDC Overview 4 Urban Campus 5 Intelligent Campus Management Solution 6 Key Features 7 Integra Management
Welcome to a world where technology flows through the heart of your business environment Welcome to CDC Overview 4 Urban Campus 5 Intelligent Campus Management Solution 6 Key Features 7 Integra Management
AUSTRALIAN DESIGNED & MANUFACTURED SMALL-ARMS SYSTEMS SOLUTIONS FOR MILITARY, LAW ENFORCEMENT & GOVERNMENT
 AUSTRALIAN DESIGNED & MANUFACTURED SMALL-ARMS SYSTEMS SOLUTIONS FOR MILITARY, LAW ENFORCEMENT & GOVERNMENT AUSTRALIAN MADE, INTERNATIONAL REACH: FORCE ORDNANCE DESIGNS, MANUFACTURES AND INTEGRATES HIGH-PRECISION,
AUSTRALIAN DESIGNED & MANUFACTURED SMALL-ARMS SYSTEMS SOLUTIONS FOR MILITARY, LAW ENFORCEMENT & GOVERNMENT AUSTRALIAN MADE, INTERNATIONAL REACH: FORCE ORDNANCE DESIGNS, MANUFACTURES AND INTEGRATES HIGH-PRECISION,
Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services
 Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
Strategic threat advisory services
 Strategic threat advisory services Preparing you to be secure Physical security threats most often come without warning. Today, every growing organisation needs to be ready to combat such risks to stay
Strategic threat advisory services Preparing you to be secure Physical security threats most often come without warning. Today, every growing organisation needs to be ready to combat such risks to stay
50 years Committed to Service with Integrity
 www.adcock.co.uk 2 50 years Committed to Service with Integrity Welcome to Adcock, the UK s most successful independent climate control company Our achievements were recognised at the prestigious RAC Cooling
www.adcock.co.uk 2 50 years Committed to Service with Integrity Welcome to Adcock, the UK s most successful independent climate control company Our achievements were recognised at the prestigious RAC Cooling
Transforming the utilities industry. How our insight and infrastructure can help you thrive in a changing world
 Transforming the utilities industry How our insight and infrastructure can help you thrive in a changing world The utilities industry is changing You need to be leaner, greener and smarter. And we re here
Transforming the utilities industry How our insight and infrastructure can help you thrive in a changing world The utilities industry is changing You need to be leaner, greener and smarter. And we re here
Security is one of the biggest concerns today. Ever since the advent of the 21 st century, the world has been facing several challenges regarding the
 Security is one of the biggest concerns today. Ever since the advent of the 21 st century, the world has been facing several challenges regarding the security of people, economy, and infrastructure. One
Security is one of the biggest concerns today. Ever since the advent of the 21 st century, the world has been facing several challenges regarding the security of people, economy, and infrastructure. One
More than 85% of our work is either repeat business or referrals from satisfied customers, a statistic that we are very proud of.
 Corporate Brochure More than 85% of our work is either repeat business or referrals from satisfied customers, a statistic that we are very proud of. Adcock Refrigeration and Air Conditioning Corporate
Corporate Brochure More than 85% of our work is either repeat business or referrals from satisfied customers, a statistic that we are very proud of. Adcock Refrigeration and Air Conditioning Corporate
ITIL : Professional Education Training. Innovative solutions for modern businesses.
 ITIL : 2011 Professional Education Training Innovative solutions for modern businesses www.syzygal.com The ITIL Service Lifecycle ITIL (IT INFRASTRUCTURE LIBRARY) is a best practice framework for IT Service
ITIL : 2011 Professional Education Training Innovative solutions for modern businesses www.syzygal.com The ITIL Service Lifecycle ITIL (IT INFRASTRUCTURE LIBRARY) is a best practice framework for IT Service
Deloitte Discovery Caribbean & Bermuda Countries Guide
 Deloitte Discovery Caribbean & Bermuda Countries Guide Deloitte Discovery Caribbean & Bermuda Countries Guide Caribbean & Bermuda Countries Our Region Deloitte CBC primarily serves businesses located or
Deloitte Discovery Caribbean & Bermuda Countries Guide Deloitte Discovery Caribbean & Bermuda Countries Guide Caribbean & Bermuda Countries Our Region Deloitte CBC primarily serves businesses located or
From Terminals to Teleports to All the Tools in Between. Aerospace Broadcast Government Infrastructure. datapath.com
 From Terminals to Teleports to All the Tools in Between Aerospace Broadcast Government Infrastructure datapath.com High Definition Communications in Even the Most Remote Locations For operations in remote,
From Terminals to Teleports to All the Tools in Between Aerospace Broadcast Government Infrastructure datapath.com High Definition Communications in Even the Most Remote Locations For operations in remote,
CRISIS RESPONSE COMMITTED GLOBAL EXPERTISE
 CRISIS RESPONSE COMMITTED GLOBAL EXPERTISE Since 1990 we have been committed to helping clients understand the threats to their people, information, property and reputation. Our global team provides you
CRISIS RESPONSE COMMITTED GLOBAL EXPERTISE Since 1990 we have been committed to helping clients understand the threats to their people, information, property and reputation. Our global team provides you
Pictured is HMS Argyll with an idyllic scene of English countryside behind her.
 Pictured is HMS Argyll with an idyllic scene of English countryside behind her. Department for International Trade Defence & Security Organisation Helping UK Companies to export www.gov.uk/dit-dso Our
Pictured is HMS Argyll with an idyllic scene of English countryside behind her. Department for International Trade Defence & Security Organisation Helping UK Companies to export www.gov.uk/dit-dso Our
Jane s Defence Industry & Markets Intelligence Centre. Develop Advantage. Mitigate Risk. Capture Opportunity.
 Jane s Defence Industry & Markets Intelligence Centre Develop Advantage. Mitigate Risk. Capture Opportunity. OVERVIEW A challenging marketplace The global A&D industry is facing an increasingly volatile,
Jane s Defence Industry & Markets Intelligence Centre Develop Advantage. Mitigate Risk. Capture Opportunity. OVERVIEW A challenging marketplace The global A&D industry is facing an increasingly volatile,
Integrated C4isr and Cyber Solutions
 Integrated C4isr and Cyber Solutions When Performance Matters L3 Communication Systems-East provides solutions in the C4ISR and cyber markets that support mission-critical operations worldwide. With a
Integrated C4isr and Cyber Solutions When Performance Matters L3 Communication Systems-East provides solutions in the C4ISR and cyber markets that support mission-critical operations worldwide. With a
GREEN DEFENCE FRAMEWORK
 GREEN DEFENCE FRAMEWORK Approved by the North Atlantic Council in February 2014 GREEN DEFENCE FRAMEWORK OVERVIEW 1. Green Defence could, at this stage, be defined as a multifaceted endeavour cutting across
GREEN DEFENCE FRAMEWORK Approved by the North Atlantic Council in February 2014 GREEN DEFENCE FRAMEWORK OVERVIEW 1. Green Defence could, at this stage, be defined as a multifaceted endeavour cutting across
General Data Protection Regulation: Knowing your data. Title. Prepared by: Paul Barks, Managing Consultant
 General Data Protection Regulation: Knowing your data Title Prepared by: Paul Barks, Managing Consultant Table of Contents 1. Introduction... 3 2. The challenge... 4 3. Data mapping... 7 4. Conclusion...
General Data Protection Regulation: Knowing your data Title Prepared by: Paul Barks, Managing Consultant Table of Contents 1. Introduction... 3 2. The challenge... 4 3. Data mapping... 7 4. Conclusion...
Transguard Group. Security Services
 Transguard Group Security Services Transguard Security Services Transguard s Integrated Solutions provide a single system model to meet all your security needs. We work in partnership with commercial and
Transguard Group Security Services Transguard Security Services Transguard s Integrated Solutions provide a single system model to meet all your security needs. We work in partnership with commercial and
Detect Fraud & Financial Crime
 IBM i2 Intelligence Analysis Detect Fraud & Financial Crime Acquire Discover Action! Urs Christen Security Sales Government urs.christen@ch.ibm.com 1 IBM Security 2014 IBM Corporation Build an integrated
IBM i2 Intelligence Analysis Detect Fraud & Financial Crime Acquire Discover Action! Urs Christen Security Sales Government urs.christen@ch.ibm.com 1 IBM Security 2014 IBM Corporation Build an integrated
RSA Solution Brief. Managing Risk Within Advanced Security Operations. RSA Solution Brief
 RSA Solution Brief Managing Risk Within Advanced Security Operations RSA Solution Brief How do you advance your security operations function? Increasingly sophisticated security threats and the growing
RSA Solution Brief Managing Risk Within Advanced Security Operations RSA Solution Brief How do you advance your security operations function? Increasingly sophisticated security threats and the growing
Defence and Security
 Defence and Security 13 HVM Perimeter Security Deployed at Westminster 2 Our Story TSP Projects is an innovative solutions driven company which prides itself on engineering projects and products, tailored
Defence and Security 13 HVM Perimeter Security Deployed at Westminster 2 Our Story TSP Projects is an innovative solutions driven company which prides itself on engineering projects and products, tailored
locuz.com SOC Services
 locuz.com SOC Services 1 Locuz IT Security Lifecycle services combine people, processes and technologies to provide secure access to business applications, over any network and from any device. Our security
locuz.com SOC Services 1 Locuz IT Security Lifecycle services combine people, processes and technologies to provide secure access to business applications, over any network and from any device. Our security
Today s cyber threat landscape is evolving at a rate that is extremely aggressive,
 Preparing for a Bad Day The importance of public-private partnerships in keeping our institutions safe and secure Thomas J. Harrington Today s cyber threat landscape is evolving at a rate that is extremely
Preparing for a Bad Day The importance of public-private partnerships in keeping our institutions safe and secure Thomas J. Harrington Today s cyber threat landscape is evolving at a rate that is extremely
Military Forensics COLLECT, EXPLOIT, AND REACT IN THE FIELD
 Military Forensics COLLECT, EXPLOIT, AND REACT IN THE FIELD Military Forensics : COLLECT, EXPLOIT, AND REACT IN THE FIELD 2 Collect, Exploit, and React in the Field Timely access to battlefield intelligence
Military Forensics COLLECT, EXPLOIT, AND REACT IN THE FIELD Military Forensics : COLLECT, EXPLOIT, AND REACT IN THE FIELD 2 Collect, Exploit, and React in the Field Timely access to battlefield intelligence
Security Director - VisionFund International
 Security Director - VisionFund International Location: [Europe & the Middle East] [United Kingdom] Category: Security Job Type: Open-ended, Full-time *Preferred location: United Kingdom/Eastern Time Zone
Security Director - VisionFund International Location: [Europe & the Middle East] [United Kingdom] Category: Security Job Type: Open-ended, Full-time *Preferred location: United Kingdom/Eastern Time Zone
Boundary Security. Innovative Planning Solutions. Analysis Planning Design. criterra Technology
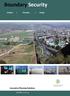 Boundary Security Analysis Planning Design Innovative Planning Solutions criterra Technology Setting the new standard DEFENSOFT - A Global Leader in Boundary Security Planning Threats, illegal immigration
Boundary Security Analysis Planning Design Innovative Planning Solutions criterra Technology Setting the new standard DEFENSOFT - A Global Leader in Boundary Security Planning Threats, illegal immigration
Defence and Security. At a Glance
 Defence and Security At a Glance Welcome to Cranfield University One of the world s largest providers of postgraduate education in defence and security technology and management, working on classified
Defence and Security At a Glance Welcome to Cranfield University One of the world s largest providers of postgraduate education in defence and security technology and management, working on classified
Cyber Security Technologies
 1 / Cyber Security Technologies International Seminar on Cyber Security: An Action to Establish the National Cyber Security Center Lisbon, 12 th September 2013 23 / Key highlights - Thales Group Thales
1 / Cyber Security Technologies International Seminar on Cyber Security: An Action to Establish the National Cyber Security Center Lisbon, 12 th September 2013 23 / Key highlights - Thales Group Thales
Mission Statement & Company Overview
 STP_SOLUTIONS_Services_Brochure 13/09/2011 14:22 Page 1 SPECIALISTS IN PROVIDING NATIONWIDE WORKSPACE SOLUTIONS OFFICE REFURBISHMENT DATA CENTRES / DISASTER RECOVERY SITES ELECTRICAL & MECHANICAL INSTALLATIONS
STP_SOLUTIONS_Services_Brochure 13/09/2011 14:22 Page 1 SPECIALISTS IN PROVIDING NATIONWIDE WORKSPACE SOLUTIONS OFFICE REFURBISHMENT DATA CENTRES / DISASTER RECOVERY SITES ELECTRICAL & MECHANICAL INSTALLATIONS
ISO/IEC Information technology Security techniques Code of practice for information security controls
 INTERNATIONAL STANDARD ISO/IEC 27002 Second edition 2013-10-01 Information technology Security techniques Code of practice for information security controls Technologies de l information Techniques de
INTERNATIONAL STANDARD ISO/IEC 27002 Second edition 2013-10-01 Information technology Security techniques Code of practice for information security controls Technologies de l information Techniques de
Compliance with ISPS and The Maritime Transportation Security Act of 2002
 Mr. Melchor Becena Security Administrator Port Everglades SecurePort Conference Miami, Florida 25-27 27 February, 2004 Compliance with ISPS and The Maritime Transportation Security Act of 2002 Overview
Mr. Melchor Becena Security Administrator Port Everglades SecurePort Conference Miami, Florida 25-27 27 February, 2004 Compliance with ISPS and The Maritime Transportation Security Act of 2002 Overview
McAfee Complete Endpoint Threat Protection Advanced threat protection for sophisticated attacks
 McAfee Complete Endpoint Threat Protection Advanced threat protection for sophisticated attacks Key Advantages Stay ahead of zero-day threats, ransomware, and greyware with machine learning and dynamic
McAfee Complete Endpoint Threat Protection Advanced threat protection for sophisticated attacks Key Advantages Stay ahead of zero-day threats, ransomware, and greyware with machine learning and dynamic
The Office of Infrastructure Protection
 The Office of Infrastructure Protection National Protection and Programs Directorate Department of Homeland Security Native American Risk Management Conference 20 July, 2018 Bridging the Gap: Delivering
The Office of Infrastructure Protection National Protection and Programs Directorate Department of Homeland Security Native American Risk Management Conference 20 July, 2018 Bridging the Gap: Delivering
Vulnerability Assessments and Penetration Testing
 CYBERSECURITY Vulnerability Assessments and Penetration Testing A guide to understanding vulnerability assessments and penetration tests. OVERVIEW When organizations begin developing a strategy to analyze
CYBERSECURITY Vulnerability Assessments and Penetration Testing A guide to understanding vulnerability assessments and penetration tests. OVERVIEW When organizations begin developing a strategy to analyze
CYBER SECURITY TRAINING
 CYBER Security skills for the digital age. Cyber Crime has never been more predominant. The number of breaches is exponentially rising year on year leading to an ever increasing Cyber Security threat.
CYBER Security skills for the digital age. Cyber Crime has never been more predominant. The number of breaches is exponentially rising year on year leading to an ever increasing Cyber Security threat.
Cybersmart Buildings: Securing Your Investments in Connectivity and Automation
 Cybersmart Buildings: Securing Your Investments in Connectivity and Automation Jason Rosselot, CISSP, Director Product Cyber Security, Johnson Controls AIA Quality Assurance The Building Commissioning
Cybersmart Buildings: Securing Your Investments in Connectivity and Automation Jason Rosselot, CISSP, Director Product Cyber Security, Johnson Controls AIA Quality Assurance The Building Commissioning
World s Most Secure Government IT Solution
 SOLUTION BRIEF World s Most Secure Government IT Solution Secure and control highly-classified data access with Teradici PCoIP Solutions Government organizations worldwide depend on PCoIP remote desktops
SOLUTION BRIEF World s Most Secure Government IT Solution Secure and control highly-classified data access with Teradici PCoIP Solutions Government organizations worldwide depend on PCoIP remote desktops
MONITORING OBLIGATIONS. FULFiL CSP REQUIREMENTS FOR COMMUNICATIONS MONITORING.
 MONITORING OBLIGATIONS. FULFiL CSP REQUIREMENTS FOR COMMUNICATIONS MONITORING. DataBridge Flexible communications monitoring Meeting your obligations flexibly As terrorists and organized criminals take
MONITORING OBLIGATIONS. FULFiL CSP REQUIREMENTS FOR COMMUNICATIONS MONITORING. DataBridge Flexible communications monitoring Meeting your obligations flexibly As terrorists and organized criminals take
TSA/FTA Security and Emergency Management Action Items for Transit Agencies
 TSA/FTA Security and Emergency Management Action Items for Transit Agencies AACTION ITEM LIST Management and Accountability 1. Establish Written System Security Programs and Emergency Management Plans:
TSA/FTA Security and Emergency Management Action Items for Transit Agencies AACTION ITEM LIST Management and Accountability 1. Establish Written System Security Programs and Emergency Management Plans:
Presentation to the ITU on the Q-CERT Incident Management Team. Ian M Dowdeswell Incident Manager, Q-CERT
 Presentation to the ITU on the Q-CERT Incident Management Team Ian M Dowdeswell Incident Manager, Q-CERT 2 Q-CERT Mission The Mission of Q-CERT is to be a world-class center of excellence providing expert
Presentation to the ITU on the Q-CERT Incident Management Team Ian M Dowdeswell Incident Manager, Q-CERT 2 Q-CERT Mission The Mission of Q-CERT is to be a world-class center of excellence providing expert
BPF GLOBAL SECURITY DETECT DEFEND DETER. Company Profile
 BPF GLOBAL SECURITY Company Profile BPF GLOBAL SECURITY Guarding, patrolling and protecting Australia wide BPF Global Security is a specialist Security and Facilities Management company providing professional
BPF GLOBAL SECURITY Company Profile BPF GLOBAL SECURITY Guarding, patrolling and protecting Australia wide BPF Global Security is a specialist Security and Facilities Management company providing professional
Defence, Safety and Security
 Defence, Safety and Security 2 The mission of TNO TNO connects people and knowledge to create innovations that boost the sustainable competitive strength of industry and well-being of society. 3 TNO facts
Defence, Safety and Security 2 The mission of TNO TNO connects people and knowledge to create innovations that boost the sustainable competitive strength of industry and well-being of society. 3 TNO facts
Security and Fleet Manager
 Security and Fleet Manager Location: [Europe & the Middle East] [Jordan] Town/City: Amman Category: Security Job Type: Open-ended, Full-time Position Title: Security and Fleet Manager PURPOSE OF POSITION:
Security and Fleet Manager Location: [Europe & the Middle East] [Jordan] Town/City: Amman Category: Security Job Type: Open-ended, Full-time Position Title: Security and Fleet Manager PURPOSE OF POSITION:
The Case for National CSIRTs
 The Case for National CSIRTs ENOG 12 Yerevan 3-4 Oct 2016 What is a CERT (CSIRT)? A Computer Security Incident Response Team (CSIRT) is a service organization that is responsible for receiving, reviewing,
The Case for National CSIRTs ENOG 12 Yerevan 3-4 Oct 2016 What is a CERT (CSIRT)? A Computer Security Incident Response Team (CSIRT) is a service organization that is responsible for receiving, reviewing,
ACTIVE SHOOTER RESPONSE CAPABILITY STATEMENT. Dynamiq - Active Shooter Response
 ACTIVE SHOOTER RESPONSE CAPABILITY STATEMENT ACTIVE SHOOTER RESPONSE Responding to armed assault acts of terrorism and active shooter incidents Acts of terrorism and shootings in public places have become
ACTIVE SHOOTER RESPONSE CAPABILITY STATEMENT ACTIVE SHOOTER RESPONSE Responding to armed assault acts of terrorism and active shooter incidents Acts of terrorism and shootings in public places have become
National Policy and Guiding Principles
 National Policy and Guiding Principles National Policy, Principles, and Organization This section describes the national policy that shapes the National Strategy to Secure Cyberspace and the basic framework
National Policy and Guiding Principles National Policy, Principles, and Organization This section describes the national policy that shapes the National Strategy to Secure Cyberspace and the basic framework
CRITICAL INFRASTRUCTURE PROTECTION
 CRITICAL INFRASTRUCTURE PROTECTION Cosmos Business Systems COSMOS BUSINESS SYSTEMS SA established in Greek & Cypriot market for more than 25 years dealing in all IT related projects in both Governmental
CRITICAL INFRASTRUCTURE PROTECTION Cosmos Business Systems COSMOS BUSINESS SYSTEMS SA established in Greek & Cypriot market for more than 25 years dealing in all IT related projects in both Governmental
EMERGENCY/DISASTER RESPONSE TEAM
 EMERGENCY/DISASTER RESPONSE TEAM For More Information Contact Us Toll-Free at: 1(888) 610-7769 at: (305) 670-6544 Security Alliance LLC. 8323 NW 12th Street, Suite# 218 Miami, Florida 33126 info@securityalliancegroup.com
EMERGENCY/DISASTER RESPONSE TEAM For More Information Contact Us Toll-Free at: 1(888) 610-7769 at: (305) 670-6544 Security Alliance LLC. 8323 NW 12th Street, Suite# 218 Miami, Florida 33126 info@securityalliancegroup.com
CYBER INCIDENT REPORTING GUIDANCE. Industry Reporting Arrangements for Incident Response
 CYBER INCIDENT REPORTING GUIDANCE Industry Reporting Arrangements for Incident Response DfT Cyber Security Team CYBER@DFT.GSI.GOV.UK Introduction The Department for Transport (DfT) has produced this cyber
CYBER INCIDENT REPORTING GUIDANCE Industry Reporting Arrangements for Incident Response DfT Cyber Security Team CYBER@DFT.GSI.GOV.UK Introduction The Department for Transport (DfT) has produced this cyber
THE CYBER SECURITY PLAYBOOKECTOR SHOULD KNOW BEFPRE, DURING & AFTER WHAT EVERY DIRECTOR SHOULD KNOW BEFORE, DURING AND AFTER AN ATTACK
 THE CYBER SECURITY PLAYBOOKECTOR SHOULD KNOW BEFPRE, DURING & AFTER WHAT EVERY DIRECTOR SHOULD KNOW BEFORE, DURING AND AFTER AN ATTACK 03 Introduction 04 Step 1: Preparing for a breach CONTENTS 08 Step
THE CYBER SECURITY PLAYBOOKECTOR SHOULD KNOW BEFPRE, DURING & AFTER WHAT EVERY DIRECTOR SHOULD KNOW BEFORE, DURING AND AFTER AN ATTACK 03 Introduction 04 Step 1: Preparing for a breach CONTENTS 08 Step
1925 Dubilier in London Founded by William Dubilier. Design and manufacture of capacitors for radar, radio & tv, & EMC filters
 MPE Heritage 1925 Dubilier in London Founded by William Dubilier. Design and manufacture of capacitors for radar, radio & tv, & EMC filters 1947 Dubilier relocated to Knowsley, Liverpool 1980 Manufacturing
MPE Heritage 1925 Dubilier in London Founded by William Dubilier. Design and manufacture of capacitors for radar, radio & tv, & EMC filters 1947 Dubilier relocated to Knowsley, Liverpool 1980 Manufacturing
SRM Service Guide. Smart Security. Smart Compliance. Service Guide
 SRM Service Guide Smart Security. Smart Compliance. Service Guide Copyright Security Risk Management Limited Smart Security. Smart Compliance. Introduction Security Risk Management s (SRM) specialists
SRM Service Guide Smart Security. Smart Compliance. Service Guide Copyright Security Risk Management Limited Smart Security. Smart Compliance. Introduction Security Risk Management s (SRM) specialists
Securing Your Digital Transformation
 Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
New Zealand Government IBM Infrastructure as a Service
 New Zealand Government IBM Infrastructure as a Service A world class agile cloud infrastructure designed to provide quick access to a security-rich, enterprise-class virtual server environment. 2 New Zealand
New Zealand Government IBM Infrastructure as a Service A world class agile cloud infrastructure designed to provide quick access to a security-rich, enterprise-class virtual server environment. 2 New Zealand
If you were under cyber attack would you ever know?
 If you were under cyber attack would you ever know? EY and Los Alamos National Laboratory introduce a shift in cybersecurity strategy and bring behavioral analytics inside Asking behavioral questions inside
If you were under cyber attack would you ever know? EY and Los Alamos National Laboratory introduce a shift in cybersecurity strategy and bring behavioral analytics inside Asking behavioral questions inside
PROVIDING INVESTIGATIVE SOLUTIONS
 PROVIDING INVESTIGATIVE SOLUTIONS Experienced Professionals Northeast Intelligence Group, Inc. (NEIG) has been helping clients meet challenges for more than twenty years. By providing meaningful and timely
PROVIDING INVESTIGATIVE SOLUTIONS Experienced Professionals Northeast Intelligence Group, Inc. (NEIG) has been helping clients meet challenges for more than twenty years. By providing meaningful and timely
TSP Technical Solutions in Partnership
 TSP Technical Solutions in Partnership Discovering our customers needs and delivering the correct solutions: on budget, on time, first time. w: tspprojects.co.uk t: +44(0)1904 454600 Offices in Birmingham,
TSP Technical Solutions in Partnership Discovering our customers needs and delivering the correct solutions: on budget, on time, first time. w: tspprojects.co.uk t: +44(0)1904 454600 Offices in Birmingham,
IT-CNP, Inc. Capability Statement
 Securing America s Infrastructure Security Compliant IT Operations Hosting Cyber Security Information FISMA Cloud Management Hosting Security Compliant IT Logistics Hosting 1 IT-CNP, Inc. is a Government
Securing America s Infrastructure Security Compliant IT Operations Hosting Cyber Security Information FISMA Cloud Management Hosting Security Compliant IT Logistics Hosting 1 IT-CNP, Inc. is a Government
Enterprise SM VOLUME 1, SECTION 5.4: ANTI-VIRUS MANAGEMENT SERVICE
 VOLUME 1, SECTION 5.4: ANTI-VIRUS MANAGEMENT SERVICE 5.4 ANTI-VIRUS MANAGEMENT SERVICE [C.2.10.4, M.2.1.3] The Level 3 Team s (AVMS) will meet or exceed the Government s requirements for AVMS, as defined
VOLUME 1, SECTION 5.4: ANTI-VIRUS MANAGEMENT SERVICE 5.4 ANTI-VIRUS MANAGEMENT SERVICE [C.2.10.4, M.2.1.3] The Level 3 Team s (AVMS) will meet or exceed the Government s requirements for AVMS, as defined
Cisco Smart+Connected Communities
 Brochure Cisco Smart+Connected Communities Helping Cities on Their Digital Journey Cities worldwide are becoming digital or are evaluating strategies for doing so in order to make use of the unprecedented
Brochure Cisco Smart+Connected Communities Helping Cities on Their Digital Journey Cities worldwide are becoming digital or are evaluating strategies for doing so in order to make use of the unprecedented
BT Compute. BT Private Compute. Dedicated cloud infrastructure hosting your IT. BT Compute
 BT Compute BT Private Compute Dedicated cloud infrastructure hosting your IT BT Compute IT needs to help organisations be more agile, flexible and efficient, whilst reducing complexity and cost. However,
BT Compute BT Private Compute Dedicated cloud infrastructure hosting your IT BT Compute IT needs to help organisations be more agile, flexible and efficient, whilst reducing complexity and cost. However,
Better Operational Agility. For more flexible, resilient and secure communications. Vodafone Power to you
 Better Operational Agility For more flexible, resilient and secure communications Vodafone Power to you 02 We gained the best value for our money from Vodafone. We reduced management time despite increasing
Better Operational Agility For more flexible, resilient and secure communications Vodafone Power to you 02 We gained the best value for our money from Vodafone. We reduced management time despite increasing
Introduction. When it comes to GDPR compliance, is OK for now enough? Minds made for protecting financial services
 When it comes to GDPR compliance, is OK for now enough? EY CertifyPoint s GDPR certification process will help you achieve and demonstrate compliance. Minds made for protecting financial services Introduction
When it comes to GDPR compliance, is OK for now enough? EY CertifyPoint s GDPR certification process will help you achieve and demonstrate compliance. Minds made for protecting financial services Introduction
Get Armoured Against Endpoint Attacks. Singtel Business. Managed Defense Endpoint Services Threat Detection and Response (ETDR)
 Singtel Business Product Factsheet Brochure Managed Defense Endpoint Services Threat Detection and Response (ETDR) Get Armoured Against Endpoint Attacks. Singtel Managed Endpoint Threat Detection and Response
Singtel Business Product Factsheet Brochure Managed Defense Endpoint Services Threat Detection and Response (ETDR) Get Armoured Against Endpoint Attacks. Singtel Managed Endpoint Threat Detection and Response
Battery Technology. Advancing technology, leading the power revolution
 Battery Technology Advancing technology, leading the power revolution QinetiQ Battery Technology Services Battery technology is advancing rapidly, and new challenges constantly arise. Through its technology
Battery Technology Advancing technology, leading the power revolution QinetiQ Battery Technology Services Battery technology is advancing rapidly, and new challenges constantly arise. Through its technology
CYBER CAMPUS KPMG BUSINESS SCHOOL THE CYBER SCHOOL FOR THE REAL WORLD. The Business School for the Real World
 CYBER CAMPUS THE CYBER SCHOOL FOR THE REAL WORLD. KPMG BUSINESS SCHOOL The Business School for the Real World In the real world, cyber security applies to all: large firms and small companies, tech experts,
CYBER CAMPUS THE CYBER SCHOOL FOR THE REAL WORLD. KPMG BUSINESS SCHOOL The Business School for the Real World In the real world, cyber security applies to all: large firms and small companies, tech experts,
how to manage risks in those rare cases where existing mitigation mechanisms are insufficient or impractical.
 Contents Introduction... 2 Purpose of this paper... 2 Critical Infrastructure Security and Resilience... 3 The National Security Environment... 5 A Proactive and Collaborative Approach... 7 Critical Infrastructure
Contents Introduction... 2 Purpose of this paper... 2 Critical Infrastructure Security and Resilience... 3 The National Security Environment... 5 A Proactive and Collaborative Approach... 7 Critical Infrastructure
OMNIS TRACKING TECHNOLOGY TAMED PUTTING CUSTOMS IN CONTROL OF CARGO
 OMNIS TRACKING TECHNOLOGY TAMED PUTTING CUSTOMS IN CONTROL OF CARGO 2 OUR NEW VISION FOR BETTER, FASTER CARGO CONTROL Cross-border trade is vital for a nation s well-being. However, as trade volumes grow
OMNIS TRACKING TECHNOLOGY TAMED PUTTING CUSTOMS IN CONTROL OF CARGO 2 OUR NEW VISION FOR BETTER, FASTER CARGO CONTROL Cross-border trade is vital for a nation s well-being. However, as trade volumes grow
National Cyber Security Operations Center (N-CSOC) Stakeholders' Conference
 National Cyber Security Operations Center (N-CSOC) Stakeholders' Conference Benefits to the Stakeholders A Collaborative and Win-Win Strategy Lal Dias Chief Executive Officer Sri Lanka CERT CC Cyber attacks
National Cyber Security Operations Center (N-CSOC) Stakeholders' Conference Benefits to the Stakeholders A Collaborative and Win-Win Strategy Lal Dias Chief Executive Officer Sri Lanka CERT CC Cyber attacks
IT Governance ISO/IEC 27001:2013 ISMS Implementation. Service description. Protect Comply Thrive
 IT Governance ISO/IEC 27001:2013 ISMS Implementation Service description Protect Comply Thrive 100% guaranteed ISO 27001 certification with the global experts With the IT Governance ISO 27001 Implementation
IT Governance ISO/IEC 27001:2013 ISMS Implementation Service description Protect Comply Thrive 100% guaranteed ISO 27001 certification with the global experts With the IT Governance ISO 27001 Implementation
Data ownership within governance: getting it right
 Data ownership within governance: getting it right Control your data An Experian white paper Data Ownership within Governance : Getting it right - 1 Table of contents 1. Introduction 03 2. Why is data
Data ownership within governance: getting it right Control your data An Experian white paper Data Ownership within Governance : Getting it right - 1 Table of contents 1. Introduction 03 2. Why is data
to Enhance Your Cyber Security Needs
 Our Service to Enhance Your Cyber Security Needs Since the business critical systems by its nature are ON all of the time and the increasingly connected world makes you open your organization to everything
Our Service to Enhance Your Cyber Security Needs Since the business critical systems by its nature are ON all of the time and the increasingly connected world makes you open your organization to everything
TRUE SECURITY-AS-A-SERVICE
 TRUE SECURITY-AS-A-SERVICE To effectively defend against today s cybercriminals, organizations must look at ways to expand their ability to secure and maintain compliance across their evolving IT infrastructure.
TRUE SECURITY-AS-A-SERVICE To effectively defend against today s cybercriminals, organizations must look at ways to expand their ability to secure and maintain compliance across their evolving IT infrastructure.
Security Awareness Training Courses
 Security Awareness Training Courses Trusted Advisor for All Your Information Security Needs ZERODAYLAB Security Awareness Training Courses 75% of large organisations were subject to a staff-related security
Security Awareness Training Courses Trusted Advisor for All Your Information Security Needs ZERODAYLAB Security Awareness Training Courses 75% of large organisations were subject to a staff-related security
Internet Scanner 7.0 Service Pack 2 Frequently Asked Questions
 Frequently Asked Questions Internet Scanner 7.0 Service Pack 2 Frequently Asked Questions April 2005 6303 Barfield Road Atlanta, GA 30328 Tel: 404.236.2600 Fax: 404.236.2626 Internet Security Systems (ISS)
Frequently Asked Questions Internet Scanner 7.0 Service Pack 2 Frequently Asked Questions April 2005 6303 Barfield Road Atlanta, GA 30328 Tel: 404.236.2600 Fax: 404.236.2626 Internet Security Systems (ISS)
M&A Cyber Security Due Diligence
 M&A Cyber Security Due Diligence Prepared by: Robert Horton, Ollie Whitehouse & Sherief Hammad Contents Page 1 Introduction 3 2 Technical due diligence goals 3 3 Enabling the business through cyber security
M&A Cyber Security Due Diligence Prepared by: Robert Horton, Ollie Whitehouse & Sherief Hammad Contents Page 1 Introduction 3 2 Technical due diligence goals 3 3 Enabling the business through cyber security
IBM Global Technology Services Provide around-the-clock expertise and protect against Internet threats.
 IBM Global Technology Services Provide around-the-clock expertise and protect against Internet threats. Enhancing cost to serve and pricing maturity Keeping up with quickly evolving ` Internet threats
IBM Global Technology Services Provide around-the-clock expertise and protect against Internet threats. Enhancing cost to serve and pricing maturity Keeping up with quickly evolving ` Internet threats
Electronic warfare, information and cyber
 Electronic warfare, information and cyber 2018-2019 Symposia Symposia at Shrivenham provides a forum to Government agencies, military and civilian, industry and research establishments for the exploration
Electronic warfare, information and cyber 2018-2019 Symposia Symposia at Shrivenham provides a forum to Government agencies, military and civilian, industry and research establishments for the exploration
Defence Science and Technology Laboratory
 Defence Science and Technology Laboratory Alex Kanaouris MEng (CompSci) Michael Jones MSc (Physics) Earl Merson MEng (Elec. Eng.) Dstl Electronics Department Who are Dstl? Integral part of MOD Research
Defence Science and Technology Laboratory Alex Kanaouris MEng (CompSci) Michael Jones MSc (Physics) Earl Merson MEng (Elec. Eng.) Dstl Electronics Department Who are Dstl? Integral part of MOD Research
ICT support for Primary Schools. Helping primary schools to apply a successful ICT strategy for teaching and digital learning.
 ICT support for Primary Schools. Helping primary schools to apply a successful ICT strategy for teaching and digital learning. Professional ICT support for primary schools. Our ICT is the technology partner
ICT support for Primary Schools. Helping primary schools to apply a successful ICT strategy for teaching and digital learning. Professional ICT support for primary schools. Our ICT is the technology partner
Innovation and Excellence in Engineering and Support. Solutions.
 Innovation and Excellence in Engineering and Support Marshall Aerospace and Defence Group Airport House The Airport Cambridge CB5 8RX UK T +44 (0) 1223 373737 marshalladg.com Contains public sector information
Innovation and Excellence in Engineering and Support Marshall Aerospace and Defence Group Airport House The Airport Cambridge CB5 8RX UK T +44 (0) 1223 373737 marshalladg.com Contains public sector information
SECURITY, SAFETY AND SOVEREIGNTY FOR THE INDO-ASIA-PACIFIC
 SECURITY, SAFETY AND SOVEREIGNTY FOR THE INDO-ASIA-PACIFIC CivSec 2018 CIVIL SECURITY CONGRESS AND EXPOSITION 1-3 MAY 2018 MELBOURNE AUSTRALIA MELBOURNE CONVENTION AND EXHIBITION CENTRE www.civsec.com.au
SECURITY, SAFETY AND SOVEREIGNTY FOR THE INDO-ASIA-PACIFIC CivSec 2018 CIVIL SECURITY CONGRESS AND EXPOSITION 1-3 MAY 2018 MELBOURNE AUSTRALIA MELBOURNE CONVENTION AND EXHIBITION CENTRE www.civsec.com.au
Contact Centre Qualifications Reference Guide for Centres
 Contact Centre Qualifications Reference Guide for Centres www.cityandguilds.com March 2008 Version 1.2 City & Guilds is the UK s leading provider of vocational qualifications, offering over 500 awards
Contact Centre Qualifications Reference Guide for Centres www.cityandguilds.com March 2008 Version 1.2 City & Guilds is the UK s leading provider of vocational qualifications, offering over 500 awards
