Practical Techniques for Eliminating Storage of Deleted Data
|
|
|
- Bryan Reed
- 5 years ago
- Views:
Transcription
1 Practical Techniques for Eliminating Storage of Deleted Data David Boutcher and Abhishek Chandra Department of Computer Science University of Minnesota Minneapolis, MN boutcher, Abstract The layered design of modern file systems hides the liveness of data from the underlying storage systems. In this paper, we define a generic purge operation that can be used by a file system to pass liveness information to the storage system with minimal changes in the layer interfaces. We present three approaches for implementing such a purge operation: direct call, zero pages, and flagged writes. We demonstrate the feasibility of these techniques through a reference implementation in User-mode Linux to dynamically manage a copy-onwrite (COW) data store. Performance results obtained from this reference implementation show that these techniques can achieve significant storage savings with a reasonable execution time overhead. Our results demonstrate that passing liveness information across the file system-block layer interface with minimal changes is not only feasible but practical. 1 Introduction Modern storage systems are implemented in a layered architecture, where the storage subsystem is separated from the file system, with a narrow interface between them. This interface typically supports only simple operations such as read block and write block at the block layer, and no additional information is provided about the type of data being written. While such a layered approach is desirable for modular design and maintenance of storage systems, the narrow interface between the file system and the block layer also prevents useful performance optimizations [8]. In particular, the block layer has no awareness of the liveness [18] of data: whether a given block contains data associated with a file currently existing in the file system. Such lack of liveness information at the block level prevents the storage system from discarding blocks deleted by the file system, often leading to issues with utilization [13], security [1, 12], backing up unnecessary data [14], inefficient caching [2, 15], and migration overheads [4]. To quote [1]: The implementations and interfaces of today s operating systems, programming languages, libraries and other software components generally overlook data lifetime issues. Fundamentally this is another example of the end-to-end system design issue described by Saltzer et. al. [17] Traditional fixed-sized media, such as hard drives, often do not distinguish between live and dead data blocks. However, more intelligent storage subsystems can make use of this information in several ways: A storage subsystem with an intelligent cache hierarchy can ensure that only live, and therefore useful, blocks occupy space in the cache, thus leading to better cache utilization [2, 15]. A Storage Area Network (SAN) that dynamically allocates data blocks as data is written by clients, can free dead data blocks, thus preserving storage as well as network and I/O bandwidth, which might be wasted on useless data otherwise [13]. A copy-on-write (COW) storage driver, as described later in Section 3, can ensure that only live data occupies space in the COW copy of the data, thus ensuring small-size COW files. One potential use of smaller COW files can be to substantially reduce the storage requirements for multiple virtual machines sharing identical file systems, and also to reduce their migration overheads [4]. Even on traditional fixed-sized media, awareness of the liveness of blocks can be used to store rotationally optimal replicas of data in blocks that are otherwise not in use [24]. From security perspective, removing deleted blocks can be useful for physically purging the data of deleted files to prevent it from being retrieved later [12]. Some techniques have been proposed for passing liveness information to the block layer [18, 15, 5]. 1
2 These techniques have typically involved either significant changes to the block layer interface used in the industry, or are very specific to the structure of the data, such as the file systems, stored on the block device. These limitations have made these techniques impractical for wide-spread adoption into existing storage system interfaces. The goal of this paper is to investigate practical techniques for passing liveness data that overcome some of the limitations of the existing techniques, and show their utility in a real implementation. In this paper, we define a generic purge operation that can be used by a file system to pass liveness information to the storage system with minimal changes in the layer interface. This operation is designed to be backcompatible, so that file systems and block devices that do not support this operation can continue to function as expected. To instantiate this purge operation in a real system, we investigate three practical techniques: direct call, zero blocks, and flagged writes. provides an explicit call that a file system can make to the block layer to indicate that a block is dead. Zero blocks allows a dead block to be indicated by writing zeros to it. Finally, flagged writes use a special flag to indicate a block s liveness status. We demonstrate the feasibility of these techniques through a reference implementation of a dynamically resizable copy-on-write (COW) data store in User-mode Linux (UML) [7]. Performance results obtained from this reference implementation show that we can recover virtually all the blocks occupied by deleted data (95% to 99.7% across our benchmarks) as compared to recovery of no blocks in the default implementation. Further, these techniques showed reasonable execution time overhead ranging from 2% to 26% across the different benchmarks. These results demonstrate that it is not only feasible but also practical to implement techniques for passing liveness information in a storage system. While we focus on using liveness information in support of more efficient storage of file systems, the same techniques could be used by any interface to the block device. Many database systems, for example, interact directly with storage devices at the block layer [15]. These same techniques can be applied to such database systems, to indicate to the storage layer when a record or blob has been deleted. The rest of the paper is organized as follows. We present the purge operation and the various techniques for its instantiation in Section 2. The reference implementation of a dynamically re-sizable COW storage system is described in Section 3, followed by its experimental evaluation in Section 4. We present related work in Section 5, and conclude in Section 6. 2 Passing Liveness Information The narrow, and fairly standard, interface between the file system layer and the block layer simplifies development of both new file systems and new storage devices. For example, the ext2 [3] file system runs identically on IDE, SCSI, and loop-back file systems. Similarly, new file systems, with semantics such as journaling [23], or log-based file systems [16] have been developed without requiring changes to underlying block devices. Any change to pass liveness data between the file system and the block layer should be made in a way that minimizes changes to the interface. In addition, to support backward compatibility, such a change should not require that all storage devices or file systems be modified. Thus, to be practical, any mechanism designed to pass liveness information between the file system and the block layer must satisfy the following key requirements: 1. The changes to the file system-block layer interface must be minimal. 2. Normal I/O operations such as reads and writes must remain unchanged. For instance, writing a block of data and subsequently reading it must give the same data. 3. Block devices must continue to support any file systems that do not provide liveness information, and file systems must function correctly on block devices that do not support the purge operation. 2.1 Purge Operation To meet the above requirements, we define a purge operation to be provided by the file system. We define the semantics of the purge operation as follows: 1. The purge operation identifies blocks whose data is no longer alive. 2. Purging a block of data results in subsequent reads from that block returning zeros. 3. Purging a block of data does not affect subsequent writes to the block. 4. Purging a block does not impact any read/write operations on other blocks in the storage system. By defining the purge operation in this manner, we meet the practicality requirements as follows. First of all, the purge operation is only a single operation added to the file system-storage system interface. As we will describe below, this purge operation can be instantiated in different ways to minimize the breakdown in the transparency of the file system and storage system layers. Thus, it 2
3 requires minimal changes to the interface. Second, the purge operation maintains the expected semantics of all reads and writes. In particular, any reads and writes to the purged block are in essence same as reading or writing to an unused block, while reads and writes to all other blocks remain unaffected. Third, the purge operation is provided mainly as a hint to the storage system, which does not require it for the management of data blocks. If a file system does not provide the purge operation, it will continue to function as before, with the storage system working without the liveness information. Similarly, if the block layer does not support the purge operation, the file system will function correctly. 2.2 Techniques to Implement Purge Operation We examine three techniques to instantiate the purge operation as defined above. All these techniques are designed to implement the purge semantics as described above. Direct Call The block device driver provides a direct call interface that the file system layer can use to identify dead blocks. This is the most straightforward way to implement the purge operation, however it bypasses many layers of the operating system. Zero blocks The file system zeros dead blocks. The block layer detects blocks that consist only of zeroes and treats them as dead. A special case of this technique is to use zero pages for zeroing dead blocks. Many operating system implementations have one or more pages explicitly set to zero. By issuing write operations through the block layer referencing the zero page, the block device can identify dead pages without requiring that every byte of the block be set to zero. Flagged Writes Flags are typically provided on I/O operations through the block layer. Additional flags, indicating dead data, can be defined, so that the file system can set these flags for a dead block to indicate it should be purged. We now describe each of these techniques in more detail, presenting the implementation issues, as well as the pros and cons associated with each of them. 2.3 Direct Call Perhaps the simplest technique for passing additional information between the layers is the addition of a new function call to the list of calls exported by the block layer. In the Linux kernel 1 all block devices export the following structure: struct block_device_operations { int (*open)(...) int (*release)(...) int (*ioctl)(...) long (*unlocked_ioctl)(...) long (*compat_ioctl)(...) int (*direct_access)(...) int (*media_changed)(...) int (*revalidate_disk)(...) struct module *owner; }; This structure provides a set of primitive functions (open, release, ioctl, etc.) supported by the block level. The simplest method of declaring a block dead is to implement an additional function, such as int (*purge_sectors)(struct block_device *, sector_t sector, unsignedlong *length) that can be used by the file system. The function takes a pointer to a the structure describing block devices, a starting sector, and the number of sectors to mark as dead. To support compatibility with block devices that may not implement the new function, the file system can check whether the function pointer is valid before calling it. The behavior for block devices not implementing the function will be the same as their default behavior. if (fops->purge_sectors) fops->purge_sectors(bdev, sector, num_sector); Advantages and Disadvantages The primary advantage of the direct call approach is its simplicity. By adding a single, architected call to the block device operations structure, the file system can inform the block layer of deleted blocks. The disadvantages of this approach are the layering and ordering violations it introduces. In the current Linux system, for example, the file system does not deal directly with the block layer. Rather there is a page cache in between. The file system deals with pages, and the page cache takes care of asynchronously scheduling I/O to the physical devices. The file system marks a page as dirty, and relies on the page cache to queue and schedule the write operations to move the page to disk. Even in the case of synchronous I/O, the file system relies on the page cache to manage I/O operations. By introducing a direct call from the file system 1 All references to the Linux kernel in this paper will be made to the kernel. 3
4 Figure 1: Direct Call ordering example to the block layer, an architecturally difficult layer violation is introduced. Additionally, since I/O is queued up between the file system and the block layer, the file system does not know, at the time the block is purged, what other I/O operations may or may not have completed. The situation is made worse by the fact that the purge operation, which may result in block device I/O operations, should not be a synchronous operation. In the case of cache management with an intelligent adapter, the purge operation may require an I/O operation to the adapter. In the COW device implementation described in section 3, a purge operation may result in multiple data I/O operations as data is moved around in the COW file. The file system should not stop dead while a longrunning synchronous operation is performed. This requires that any I/O resulting from the purge operation be enqueued, presumably in a queue internal to the block device. The block device must then ensure that the integrity of the file system data is maintained while processing two asynchronous queues of operations (i.e. not incorrectly purging data.) If a write is followed by a purge, there is no data corruption issue if the operations are re-ordered, and the only consequence is that dead data will be written to the media. Figure 1 shows such a situation, where the curved solid line shows I/O queued typically, and the dashed line shows the direct call bypassing any I/O queueing. This does not introduce correctness issues, but may be problematic if, for example, the goal of liveness detection is purging data for security reasons. There is a much greater problem if the purge is incorrectly scheduled after the write, since valuable data may be lost or if a purge operation is incorrectly scheduled ahead of a read operation, since the read will not correctly return data. It is unclear what file system semantics would result in a such operations being concurrently scheduled. Further, some I/O operations are treated as barrier operations to enforce certain I/O ordering. A direct call from the file system to the block layer ignores scheduling constraints placed by barrier operations in flight. In our reference implementation of direct call (described in Section 4), the call to the block layer results in purge operations being inserted at the tail of the queue of scheduled I/O operations (i.e. operations already scheduled at the block layer by the page cache.) The purge operation will occur prior to any subsequent write operations. This ensures that while the purge may skip ahead of a write operation (write:purge gets re-scheduled as purge:write), the inverse well never occur. Our implementation currently ignores the issue of barrier operations. Barrier operations in a file system are typically required to ensure that the data on the storage device is always consistent, especially in the case of a system failure during a sequence of operations [9][6]. Ignoring barrier operations allowed for a simpler implementation that enabled the benchmarking described in section 4, however it could result in inconsistent on-disk data if a system failure occurs. One such scenario involves the deletion of a file, where the file system first updates its meta-data to indicated that the file is deleted and the blocks are freed, then issues the direct-call purge operation to remove the blocks. If the purge operation occurs before the meta-data gets written to disk, a window exists where the data blocks have been purged from the storage device before the file system meta-data is updated to indicate that the file is deleted. In the reference implementation this would result in a file that contains all zero blocks. This scenario highlights the risks involved in bypassing operating system layers to implement a new function Using IOCTL for the Direct Call An alternative to adding the function pointer to the block device operation structure would be to implement the call as an ioctl call. There are some further advantages and disadvantages to this approach. An advantage is that the ioctl can be used from user programs, allowing increased management of the block device from administrative programs. One example of this is formatting a file system using a user program such as the Linux mke2fs program. Such programs, when initializing a block device, could inform the block layer of all the dead blocks (in the simple case, performing a purge starting at the beginning of the disk and extending to the end before initializing file system meta-data structures.) A disadvantage to the ioctl approach is the lack of architecture to the interface. The ioctl function is difficult to validate at compile time, and the data passed through in an invalidated form. There are very few ioctl() calls made from one part of the Linux kernel to another for 4
5 these reasons. 2.4 Zero Blocks A brute force method for indicating dead data is to always write blocks of zero to any area of the file system that does not contain live data. Existing file system implementations already use this technique, primarily to ensure that deleted data is not recoverable. 2 The block layer then examines blocks of data written, and if they are zero, treats them as dead data. It is critically important that any read to a block that has previously been written with zeros subsequently return an identical block. This can be problematic if a block of zeros is used to indicate that the storage layer can purge, and not store, the block of data. Subsequent read operations must return zeros even if the contents of the block are not physically stored Advantages and Disadvantages The advantage of the zero block approach is that it requires no changes to the file system-block layer interface, and block devices that do not treat zero blocks specially will be semantically identical to devices that treat zero blocks as purged. A further advantage of the zero block approach is that it can be used in any component of the I/O infrastructure. For example, if data is being stored on a storage area network (SAN), the device drivers on the host system need not perform the zero block detection or be aware of the purgability of data. The data can be passed all the way across the SAN fabric to the SAN controller, which could perform the zero detection. The main disadvantage with this technique is that the file system must physically write zero to each byte of a dead block, and the storage layer must physically examine each byte in the block to see if it is zero. This is a serious performance penalty, particularly if the data must all be loaded into the processor s cache. In the case of a write containing non-zero data, it is likely such a test will detect non-zero data early in the block. In the case of zero data, however, the block layer must examine the full block before concluding that it is purgable Using Zero Page Mapping A more elegant alternative to the zero block approach is to take advantage of the fact that many operating systems maintain one or more pages whose contents are always zero. These pages are used in any case that a zeroinitialized block of memory is required (such as the BSS 2 As an example, see the zero-free patch to the Linux kernel at segment of a program.) Such pages are often COW memory pages, that will be mapped to a unique writable page on the first write operation. When the file system wishes to delete a block in a file, it can re-map the page in the page cache to the zero page and issue the appropriate write. The block layer then detects write operations whose data is coming from the address range of the zero page and recognizes those as zero data as in the zero block case. Even in the case that the zero block detection occurs on some remote device this approach may have some performance advantages, since the system need not write zeros to every byte of the blocks to be purged. 2.5 Flagged Writes Perhaps the architecturally cleanest approach to passing liveness data between the file system and the block layer is to introduce a new flag that accompanies the I/O request indicating that the I/O is purging data. There are a number of flags already in the Linux kernel, such as REQ FASTFAIL, that indicates an I/O should not be retried, and REQ HARDBARRIER that indicates other I/O operations should not be re-scheduled around this one. Similarly, to indicate a purge operation, a new flag, REQ PURGE can be defined and set by the file system, and recognized by the block layer. It is important to note that since the file system deals with page through the page cache, the purge flag is set on all pages to be purged. Those pages then migrate out to disk through normal I/O mechanisms and are purged from, rather than written to, the media when they reach the block layer with the flag set Advantages and Disadvantages The main disadvantage of a new I/O flag is that it is a more invasive change than those previously described. The flag (in the case of Linux) must be defined in three different kernel structures: The buffer head struct The bio struct The request struct The buffer head structure is the primary link to the page cache updated by the file system. The page cache then creates bios, which in turn are grouped into requests. A flag indicating purgable data must be set by the file system in the buffer head, and that information in turn passed along through the other layers. An additional concern is the way I/O operations are merged. Multiple bio operations are merged into a single request. Purge 5
6 and non-purge I/O operations should not be merged together lest the purge bit be applied to an incorrect I/O or dropped from a purge I/O. Finally, since the pages are flagged as purgable, they must be scheduled to be written out by the block layer, resulting in additional I/O operations. The main advantage of the flagged write approach is that it is architecturally clean. The purged I/O operations are scheduled along with other I/O operations, and respect ordering with operations such as barriers. If the purging operations are performed in storage components such as a SAN, the flag must be added to the interface to the SAN controller (e.g. to the fiber protocol) in order to be effective. Cow File Backing File 2.6 Comparison of the Techniques There is one significant difference in the approach of the three techniques. The direct call technique provides a very efficient interface to the block layer, at the expense of violating architected layering. The interface provides a starting sector and range to be purged, and that call is the only new invocation of the block layer in support of purging data. The zero block and flagged I/O techniques, on the other hand, require that all pages associated with the purged data be marked in the page cache. The zero block technique marks them by filling the pages with zeros whereas the flagged I/O technique marks them by setting a flag on the page. Both the zero block and flagged I/O techniques cause significantly more I/O operations to occur between the page cache and the block layer, since all those marked pages must then be scheduled to be written out by the block layer. 3 Implementing a Liveness-Aware Copy-On-Write Storage Subsystem To explore the above described purge techniques in a practical environment, we implemented a dynamically resizable Copy-On-Write (COW) storage system that uses each of these techniques to pass liveness information to the block layer. We first give a background of COW storage, followed by a description of our implementation. 3.1 Background Copy-On-Write Copy-On-Write (COW) is a lazy optimization mechanism for data storage that maximizes shared copies of data for as long as possible. Multiple users of a piece of data all reference the same copy of the data, with a private copy being created only when a user attempts to modify Figure 2: COW storage the data. This mechanism is typically implemented transparently to users of the data. Copy-on-write is used for disk storage to reduce the storage required when multiple similar copies of a file system are created. Two common examples of this are multiple similar virtual machines executing within a single physical machine [21], and snapshot copies of file system state. In both of these cases, the original disk storage remains unaltered. Any updates by the file system are made to separate, smaller, disk storage that contains only the altered blocks. In the rest if this paper, we refer to the original, immutable, storage as the backing data, and the storage containing only the changed regions of the data as the COW data. Figure 2 illustrates a COW storage system. The figure shows the allocated regions of COW file in gray. The COW file only allocates storage for the blocks of the the backing file that have been written to, while the unmodified blocks are read from the backing file. One fundamental attribute of existing COW storage is that it is grow only. In other words, the COW data increases in size as blocks are written to the storage, but it never decreases in size. The prototypical example would be copying a 1GB file to a file system backed by COW storage, and then deleting the file. 1GB of blocks would be written to the COW file, but would not be freed when the file is deleted Sparse File COW Implementations Sparse files are used to reduce storage requirements by formalizing the assumption that files are initially filled with zeros, and therefore data blocks need only be allocated when new, non-zero data is written to regions of the file. In a Posix file system, for example, a sparse file is created by opening the file, seeking to some, potentially 6
7 large, offset in the file, and writing data at that offset. The size of the file, as recorded by the file system, will be the byte last written. Data blocks are not allocated on the media, however, for all the intermediate data. A read to any region of the file not previously written to, will return zero. 3 The use of sparse files makes for a very elegant implementation of COW data store. A sparse COW data file is created, with the same size as the original backing data. Assuming that the file is created by writing single zero byte at an offset equal to the size of the backing file, the COW file nominally occupies a single byte of storage. 4 In addition, a bitmap is maintained indicating which blocks of the COW store have been written to. Initially the bitmap is all zero. There is one bit for each region of the backing data. In many implementations, a region is considered to be a standard 512 byte sector, though other region sizes can be used. There is, therefore, overhead of 1 bit for each 512 bytes of the backing data store. This works out to an overhead of.24%, which is very acceptable for most applications. As writes are made to the COW data store, the writes are made to the COW sparse file, at the same offset as the original file. Writes to the sparse file cause those regions to be allocated, however regions not written to remain sparse. The bitmap is updated whenever a new region of the file is written to. When read operations are performed, the COW data store examines the bitmap to determine if the read should be made from the COW sparse file, or the original backing file. Since the bitmap of used blocks is an integral part of the data store, it is often stored at the beginning of the COW file, and the offsets of I/O operations done to the COW file are adjusted to account for the size of the bitmap at the beginning of the file. Limitations of Sparse File COW Storage The most significant limitation to sparse file COW implementations is that sparse files do not have an interface for making a region of the file sparse again once it has been written to. In other words, once a region has been written to, and storage allocated for that region, even writing zeros back to that region will not deallocate the space. The allocated size of sparse files can only grow. 5 This limitation on deallocating storage is significant 3 Interestingly, the Windows NTFS file system allows the default value returned for sparse regions to be set to a value other than zero. 4 In practice, the COW file will likely consume one block in the file system, depending on how the file system deals with writes of less than a block size. That is file system dependent. 5 Peter Braam (braam@clusterfilesystem.com) created a prototype syscall in Linux, named sys punch to punch holes in a file. In other words, return regions of a file to a sparse state. This syscall was never accepted into Linux. for COW implementations that allow for data to be marked deleted, and therefore no longer requiring space in the COW store. Techniques do exist for shrinking sparse COW files. The existing techniques, however, are limited by the inability to add holes back into the sparse file. They rely, therefore, on first writing zero blocks to any non-allocated blocks in the file system, and then copying the COW file to a new file, skipping over any zero regions. Moreover, this resizing operation can only be performed when the COW file is not in use, preventing the use of these techniques in an online manner. 3.2 Dynamically Resizable COW Store A dynamically resizable COW store supports growing as data is written to the store as well as shrinking as data is deleted from the store. The dynamic COW file adjusts its size while the file is in use. Implementing a dynamic COW file requires interfaces from the file system to determine the liveness of data, and is thus a very suitable implementation for testing the techniques described in the previous section. The management of storage in a resizable COW file is a significant issue by itself. As data is purged from the COW file, generally from the middle of the file, the remaining data needs to be re-arranged to reduce the size of the file. Techniques for this kind of storage management exist in other computer science disciplines [11], and are very similar to the management of a database file where records are added and deleted arbitrarily from the file. As the focus of our implementation was to explore the liveness issue, rather than data management, we employed a simple technique to manage storage in the file. As a data block is purged from the COW file, the data at the end of the file is immediately moved to the purged area, reducing the size of the COW file. This technique has the advantage of simplicity, but it can lead to inefficiencies. If a large amount of data is being deleted from a COW file, for example, it is likely that the moved data will be deleted very shortly. More efficient mechanisms, involving lazy deletion, for example, would likely improve the performance of the system Resizable COW Data Structures Our implementation of resizable COW file uses an indirect map that maps any changed blocks in the backing data file to blocks at some arbitrary location in the COW file. This indirect map is used in conjunction with a bitmap of allocated COW blocks that keeps track of which blocks have been changed from the backing file. The indirect map allows changed blocks in the backing data to be stored at any location in the COW data. Additionally, blocks in the COW data can be moved as long 7
8 Figure 4: Purging a block Figure 3: Indirect Mapping Data-structure as the indirect map is updated. This feature is required to shrink the COW file as blocks are deleted, since shrinking the COW file may require rearranging the remaining blocks. Figure 3 shows the indirect mapping of storage regions in the COW file. The indirect map is only looked up if the bitmap indicates that a COW block exists. This in turn allows for the recording of purged blocks, whose contents should be returned as zero. Any block with a value of one in the bitmap, but a value of zero in the indirect map is considered a purged block and will return zeros on subsequent read operations. When an I/O operation is performed, the block number of the I/O is first used as an index into the bitmap, and then used as an index into the indirect mapping entry array. If the indirect map entry is non-zero, the indirect map indicates the block number in the COW file that contains the current copy of the block of data. Write operations to a block that does not currently have a copy in the COW data require the allocation of new space in the COW file. New allocations are always made at the end of the COW file, and the block where the data was written is stored in the indirect map. Read operations either are directed to the backing file, if the bitmap entry is zero, or to the COW file, if both the bitmap and the indirect map entries are non-zero. If the bitmap entry is non-zero but the indirect map entry is zero, it indicates a purged block and the read returns zeros. The memory overhead of this COW store is significantly larger than the bitmap used in the sparse file implementation described in section Assuming that the indirect map stores the offset in the COW file in blocks, or sectors, the overhead is dependent on the size of the block. The size of the index directly affects the maximum file size supported by the COW implementation. For a sector size of 512 bytes, a 32 bit index will support file sizes up to 2TB. The overhead of that implementation is 4 bytes for each 512 bytes of data, or.8%. Using this implementation, the memory overhead is constant regardless of how much data is written to the COW store. More complex and dynamic allocation schemes, such as a tree, a hash table, or a multi-level index are also possible. These schemes could have the advantage of growing the overhead associated with the COW store proportionally to the amount of data written to it. The current implementation of dynamic COW files always keeps a copy of the indirect map in memory. A more scalable approach would cache portions of the indirect map in memory without requiring that the whole map be resident Purging Blocks from the COW File When a block is purged from the COW file, the COW file should shrink. In order to implement that semantic, the last block in the COW file is moved to the purged block, and the appropriate indirect maps updated. The indirect map for the purged block is set to zero, and the indirect map for the moved block is changed from the last block in the file to the deleted block. This ensures that the COW file is always packed. The ordering of these operations is very important to preserve ensure the correctness of the data in the event of a failure during the operation. Figure 4 shows the mapping of storage regions in gray. The ordering must be: 1. file system calls purge 2. write to purged indirect map entry 3. Copy data block from end of file to the purged block 4. Update the moved block s indirect entry 8
9 5. Truncate the file There are advantages and disadvantages to keeping the COW file packed. One advantage is that no utilization bits need be kept and managed. All blocks in the COW file are always used. A disadvantage, though, is that purge operations are expensive and synchronous. When a block is purged, a block must be read and written, and the indirect map must be updated. 4 Experimental Evaluation 4.1 Implementation and Experimental Setup We have implemented a reference implementation of our dynamically resizable COW storage system in User Mode Linux (UML) [7], UML is a virtual machine implementation of Linux that allows a version of Linux to run as an application on top of an underlying Linux system. We chose UML for our implementation for two reasons. Firstly, it has an existing grow-only COW implementation against which the resizable COW implementation can be compared. Secondly, it provides a simple environment for developing and testing new Linux kernel code. A 5MB file system was created and an ext2 [3] file system created on it. The Linux system running the benchmarks had the zerofree patch applied, allowing the ext2 file system to write zeros to deleted blocks for the zero detection algorithms. The system on which the benchmarks were run was an AMD Athlon(tm) XP 26+ with 1GB of memory. A Linux kernel was used for both the host system as well as the UML kernel. We used the following benchmarks to analyze the performance of our dynamic COW implementation: Linux build: This benchmark performed a make and clean of Linux source code. This benchmark was chosen since building the kernel involves the creation of a large number of files with a significant amount of data, and performing the make clean operation causes all the files to be deleted again. dbench: dbench [22] is an I/O benchmark that simulates the I/O load produced by the netbench benchmark, without the network component. It creates, populates, and deletes files. bonnie: bonnie [1] is a Linux I/O benchmark that performs a number of I/O tests, including reading/writing data and creating/deleting files. We implemented three versions of the dynamically resizable COW system, using each of the three purge techniques described in Section 2 (namely, direct call, zero File Size (1K blocks) File Size (1K blocks) start COW File Sizes run1 run2 run3 run4 run5 run6 run7 run8 run9 run1 after "make" and after "make clean" Figure 5: Linux build COW file sizes start run1 run2 run3 run4 run5 run6 run7 run8 run9 run1 COW File Sizes dbench during/after Figure 6: dbench COW file sizes. page, and flagged writes) to pass liveness information from the file system to the COW layer. We ran our benchmarks on these three versions and compared the results to those obtained on the default implementation. 4.2 Storage Savings The main reason for implementing a resizable COW store is to minimize the amount of storage used. Here, we present results in the storage savings achieved by the various purge techniques in the resizable COW implementation. Figure 5 shows the size of the COW file (in KB) for the Linux build benchmark. The figure shows the size of the COW file at two points in each run: the size of the COW file after the compile, and the size of the COW file after a make clean command to delete the resulting binaries. The top line in the graph correspond to the default, while the other curves corresponds to the three resizable COW implementations (these curves are so close that they are indistinguishable). It is clear from 9
10 File Size (1K blocks) COW File Sizes dbench during/after Zero Detect Purge - dbench zero files Figure 7: Behavior of zero page purge implementation with the default dbench benchmark. File Size (1K blocks) start run1 run2 run3 run4 run5 run6 run7 run8 run9 run1 COW File Sizes after bonnie benchmark Figure 8: bonnie COW file sizes. this graph that the resizable COW implementation provides significant storage benefits. In the existing COW implementation, the storage occupied by the COW file continues to grow, even after the make clean operation deletes the binaries produced by the kernel compile. The resizable COW implementation, by comparison, grows and shrinks on demand. After 1 cycles of compile and clean, the resizable file is only 5% the size of the UML COW implementation (4MB compared to 87MB). Figure 6 shows a similar graph for the dbench benchmark, with snapshots taken 2 seconds into each benchmark run, and at the end of each run. Once again, we can see that resizable COW implementations are able to reclaim the storage for all the deleted data, and by the end of each run, the COW file is at its minimal size. We noticed an interesting aspect of dbench during our experiments. By default, the dbench benchmark writes only zeros to all its data files. Using this default behavior with the zero page detection approach results in the COW file never growing at all as illustrated in Figure 7: the barely visible line at the bottom of the graph is the size of the COW file using zero page detection. We in fact modified the dbench benchmark slightly to store one non-zero byte in each 512 byte block to produce the results shown in Figure 6. Finally, the COW file size for the bonnie runs is shown in Figure 8. The figure shows only the size of the COW file at the end of each benchmark run. We did not measure the file size during the runs, because bonnie executes a number of phases (a block I/O phase, a file seek phase, a file creation phase, etc.), making it difficult to determine a fixed point during the benchmark where files are created/deleted. However, as can be seen from the figure, the size of the COW file remains minimal (it is the barely visible curve very close to the x-axis), with a saving of 99.7% over the default after 1 runs of the benchmark. These results demonstrate that purging deleted data based on liveness information passed from the file system has significant savings in terms of storage. 4.3 Performance Next we look at the performance of the various purge techniques, and the overheads involved in resizing the COW file using these techniques. Figure 9(a) shows timing comparisons for building the kernel and subsequently deleting the binaries. As can be seen from the figure, the overall compilation and clean time of the resizable COW implementations was comparable to the implementation. The wall-clock time to build the kernel was increased by only 1% in the worst case (the flagged purge approach) and was statistically identical for the other approaches. The overall time for the make/clean cycle is dominated by the compilation, which is primarily a CPU-intensive operation. Since the file deletion is much more I/O-intensive, we show the performance for cleaning the binaries separately in Figure 9(b). As shown in the figure, the time to delete the binaries (make clean) was increased by 46% in the worst case (flagged purge), while the aggregate of both make and clean operations is increased by only 2% (6 minutes, 26 seconds compared to 6 minutes 19 seconds.) This level of overhead seems reasonable given the storage savings achieved. As mentioned above, the kernel compilation has a significant CPU component to its performance in addition to I/O. The dbench benchmark was used to analyze the overhead of the resizable COW implementation in a much more I/O intensive environment. Figure 1(a) shows the average throughput achieved over 1 runs of dbench. As can be seen from the figure, the performance of direct call purge is statistically identical to that of, while those of zero-detect purge and flagged purge are 41% and 39% less respectively. Figure 1(b) explains why the zero-detect purge may 1
11 4 Make and Clean Elapsed Times 1 Clean Elapsed Times seconds seconds Make time Clean time Time with 95% confidence (a) Make performance (b) Clean performance Figure 9: Performance of Linux build benchmark. 7 dbench throughput 7 dbench throughput MB/sec 4 3 MB/sec with zero Throughput with 95% confidence Throughput with 95% confidence (a) dbench (b) dbench with zero on delete Figure 1: dbench throughput. be doing so poorly. The figure shows the impact of writing zeros to all deleted blocks. It compares the dbench throughput of with a version implementing zero writes to deleted blocks (without purging and resizing), and the zero-detect purge implementation. As can be seen from the figure, the performance of the with zero writes is comparable to that of the zero-detect purge, indicating that most of the overhead is occurring due to the writing of zeros to the deleted blocks. The degradation in the performance of flagged purges is because of the extra I/O operations it generates. We hypothesize that there is also a degradation due to the fact that it prevents coalescing of non-flagged operations with flagged operations, as explained in Section 2.5. Thus several extra operations are performed which would not have been done if they could have been coalesced. Figure 11(a) shows the elapsed time to complete the bonnie benchmark, which is a multi-stage I/O-intensive benchmark measuring a number of I/O functions such as sequential and random reading/writing, creating/deleting files, seeking, etc. Note that while on the dbench throughput graph, higher is better, in the bonnie elapsed time graph, lower is better. As seen from Figure 11(a), the elapsed time for direct call purge is again comparable to that for, while those of zero-detect purge and flagged purge are 26% and 8% higher respectively. Figure 11(b) shows the impact of writing zero blocks on deletion, and, we can see that, as with dbench, the addition of writing zeros to all deleted blocks adds most of 11
12 9 Bonnie Elapsed Times 9 Bonnie Elapsed Times seconds 5 4 seconds with zero Bonnie elapsed time with 95% confidence Bonnie elapsed time with 95% confidence (a) Bonnie (b) Bonnie with zero on delete Figure 11: Bonnie elapsed time 3 Bonnie Random Creates 8 Bonnie Random Deletes per sec per sec Bonnie data with 95% confidence Bonnie data with 95% confidence (a) Creates (b) Deletes Figure 12: Comparison of the purge techniques for file creations and deletions. the overhead. The differences between the three approaches are highlighted by Figures12(a) and 12(b), which show the number of creates and deletes respectively that bonnie performed per second. Note that using the direct call purge approach has very good performance on creates, but much worse performance on deletes, as might be expected since on a file deletion a direct and immediate call is made to the block layer. This adds overhead of resizing the COW file at the time of the delete operation itself. The flagged purge approach, on the other hand, shows much better performance on deletes, but poor performance on creates. This is because when a file is deleted, the relevant pages are just flagged for purging, but the purge operation itself does not occur until the marked pages naturally migrate to disk. The poor performance on creates can be attributed to the additional I/O operations already in the queue. The two measurements focused most closely on the cost of the delete operation itself are the make clean times, shown in Figure 9(b) and the bonnie delete measurements, shown in Figure 12(b). Those two measurements agree that the direct call approach has the worst performance, and the flagged purge approach has the best performance. On more mixed workloads, however, such as overall dbench throughput or the bonnie overall elapsed time, the ordering is reversed with direct call providing the best performance. We hypothesize that this is because the flagged I/O approach affects the overall I/O scheduling and merging of other I/O operations, whereas 12
13 the direct call approach restricts its impact to the delete operations themselves. Finally, it is difficult to separate the overhead of writing zeros to deleted buffers from the other overhead of resizing COW files. However, Figures 1(b) and 11(b) indicate that writing zeros to blocks has a significant impact on the performance of the zero block detection technique. This overhead can perhaps be reduced by using mechanisms such as zero page mapping, as described in Section Overall, we see that the purge operations have acceptable performance particularly given the amount of storage savings. Moreover, each of these purge operations may be suited for a different environment based on what I/O operations are expected to dominate the workload in that environment. 5 Related Work [19] also addresses the narrow interface between the file system and the block layer and advocates creating semantically-smart disk systems that can understand the file systems above them to make more intelligent storage decisions. They state that changing the interface to storage is fraught with peril, requiring broad industry consensus, and massive upheaval in existing infrastructure. While the approach described in our paper addresses only the liveness of data blocks, we believe we have demonstrated that it is practical to make minimal interface changes in support of new and more intelligent storage behaviors. [18] presents techniques to determine the liveness of data blocks, classified as explicit and implicit. Their explicit detection approach is similar to our direct call interface, without necessarily addressing the scheduling difficulties associated with calling the block layer from the file system. The implicit detection technique relies on the block layer making inferences about the liveness of data without any direct interaction with the file system. While the implicit detection approach is the least nonintrusive, there are a number of limitations to it. The first is that the storage layer must be modified to understand the semantics of each file system. Further, if file system enhancements or fixes are made that subtly alter the semantics, a corresponding change must be made to the storage layer. Another disadvantage is that not all file systems provide sufficient semantics to fully understand the liveness of data. Moreover, since file system structures may be cached in memory, it is not always possible to define provably correct semantics for understanding block liveness. For these reasons, we did not explore the implicit detection approach in this paper, as our focus was on a practical and general approach that can be applied across different file systems and block layers. [5] proposed a completely new interface between file systems and storage devices that provides a much richer set of functions, including a delete operation. While being more versatile, this approach is also much more invasive than the one described in our paper. [15] describes an interesting approach for providing write hints to the storage devices servicing an on-line transaction processing (OLTP) workload. Since their approach focuses on database transactions, their hints indicate whether a given write is synchronous, asynchronous replacement, or asynchronous recoverability. There appears to be some synergy with the approach described in this paper, since in dealing with second level cache management, the deletion (purge) of an OLTP record would appear to be of interest to a cache management system. Interestingly, Strunk et. al. [2] argue that in some cases it is desirable to be able to recognize and preserve deleted data. They refer to this as information survival. Both the flagged I/O and direct call techniques described in this paper lend themselves to this requirement. The zero block approach is less applicable, though a block layer that detects when data is being overwritten by a block of zeros could also trigger the preservation of the previous contents of the block. 6 Concluding Remarks We have demonstrated the practicality of making minimal changes to the file system-block level interface to inform storage devices of the liveness of data blocks. We defined a purge operation to pass this liveness information, and presented three techniques to instantiate this operation: direct call, zero blocks and flagged writes, with each technique having some advantages and disadvantages. We evaluated these techniques in a reference implementation of a dynamically resizable copy-on-write storage system. Our results demonstrate that these techniques provide significant storage savings over existing COW implementations, while incurring acceptable performance overhead. In the future, we plan to investigate other environments, such as Xen virtual machines, where these techniques could provide value, for instance, for live VM migration. We will also continue to explore more efficient liveness passing mechanisms, such as the zero page approach describe earlier. Scalable data management within resizable COW files is also an area that deserves more attention. References [1] Tim Bray. bonnie. bonnie/. [2] N. Burnett, J. Bent, A. Arpaci-Dusseau, and R. Arpaci-Dusseau. Exploiting Gray-Box Knowledge of Buffer-Cache Management. 13
Practical Techniques for Purging Deleted Data Using Liveness Information
 Practical Techniques for Purging Deleted Data Using Liveness Information David Boutcher Department of Computer Science University of Minnesota Minneapolis, MN 55455 boutcher@cs.umn.edu ABSTRACT The layered
Practical Techniques for Purging Deleted Data Using Liveness Information David Boutcher Department of Computer Science University of Minnesota Minneapolis, MN 55455 boutcher@cs.umn.edu ABSTRACT The layered
Operating Systems. Operating Systems Professor Sina Meraji U of T
 Operating Systems Operating Systems Professor Sina Meraji U of T How are file systems implemented? File system implementation Files and directories live on secondary storage Anything outside of primary
Operating Systems Operating Systems Professor Sina Meraji U of T How are file systems implemented? File system implementation Files and directories live on secondary storage Anything outside of primary
Chapter 9 Memory Management
 Contents 1. Introduction 2. Computer-System Structures 3. Operating-System Structures 4. Processes 5. Threads 6. CPU Scheduling 7. Process Synchronization 8. Deadlocks 9. Memory Management 10. Virtual
Contents 1. Introduction 2. Computer-System Structures 3. Operating-System Structures 4. Processes 5. Threads 6. CPU Scheduling 7. Process Synchronization 8. Deadlocks 9. Memory Management 10. Virtual
Operating Systems. File Systems. Thomas Ropars.
 1 Operating Systems File Systems Thomas Ropars thomas.ropars@univ-grenoble-alpes.fr 2017 2 References The content of these lectures is inspired by: The lecture notes of Prof. David Mazières. Operating
1 Operating Systems File Systems Thomas Ropars thomas.ropars@univ-grenoble-alpes.fr 2017 2 References The content of these lectures is inspired by: The lecture notes of Prof. David Mazières. Operating
CLOUD-SCALE FILE SYSTEMS
 Data Management in the Cloud CLOUD-SCALE FILE SYSTEMS 92 Google File System (GFS) Designing a file system for the Cloud design assumptions design choices Architecture GFS Master GFS Chunkservers GFS Clients
Data Management in the Cloud CLOUD-SCALE FILE SYSTEMS 92 Google File System (GFS) Designing a file system for the Cloud design assumptions design choices Architecture GFS Master GFS Chunkservers GFS Clients
FILE SYSTEMS, PART 2. CS124 Operating Systems Fall , Lecture 24
 FILE SYSTEMS, PART 2 CS124 Operating Systems Fall 2017-2018, Lecture 24 2 Last Time: File Systems Introduced the concept of file systems Explored several ways of managing the contents of files Contiguous
FILE SYSTEMS, PART 2 CS124 Operating Systems Fall 2017-2018, Lecture 24 2 Last Time: File Systems Introduced the concept of file systems Explored several ways of managing the contents of files Contiguous
Chapter 4 File Systems. Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved
 Chapter 4 File Systems File Systems The best way to store information: Store all information in virtual memory address space Use ordinary memory read/write to access information Not feasible: no enough
Chapter 4 File Systems File Systems The best way to store information: Store all information in virtual memory address space Use ordinary memory read/write to access information Not feasible: no enough
File system internals Tanenbaum, Chapter 4. COMP3231 Operating Systems
 File system internals Tanenbaum, Chapter 4 COMP3231 Operating Systems Summary of the FS abstraction User's view Hierarchical structure Arbitrarily-sized files Symbolic file names Contiguous address space
File system internals Tanenbaum, Chapter 4 COMP3231 Operating Systems Summary of the FS abstraction User's view Hierarchical structure Arbitrarily-sized files Symbolic file names Contiguous address space
UNIT III MEMORY MANAGEMENT
 UNIT III MEMORY MANAGEMENT TOPICS TO BE COVERED 3.1 Memory management 3.2 Contiguous allocation i Partitioned memory allocation ii Fixed & variable partitioning iii Swapping iv Relocation v Protection
UNIT III MEMORY MANAGEMENT TOPICS TO BE COVERED 3.1 Memory management 3.2 Contiguous allocation i Partitioned memory allocation ii Fixed & variable partitioning iii Swapping iv Relocation v Protection
The Google File System
 The Google File System Sanjay Ghemawat, Howard Gobioff and Shun Tak Leung Google* Shivesh Kumar Sharma fl4164@wayne.edu Fall 2015 004395771 Overview Google file system is a scalable distributed file system
The Google File System Sanjay Ghemawat, Howard Gobioff and Shun Tak Leung Google* Shivesh Kumar Sharma fl4164@wayne.edu Fall 2015 004395771 Overview Google file system is a scalable distributed file system
File Systems. Chapter 11, 13 OSPP
 File Systems Chapter 11, 13 OSPP What is a File? What is a Directory? Goals of File System Performance Controlled Sharing Convenience: naming Reliability File System Workload File sizes Are most files
File Systems Chapter 11, 13 OSPP What is a File? What is a Directory? Goals of File System Performance Controlled Sharing Convenience: naming Reliability File System Workload File sizes Are most files
6. Results. This section describes the performance that was achieved using the RAMA file system.
 6. Results This section describes the performance that was achieved using the RAMA file system. The resulting numbers represent actual file data bytes transferred to/from server disks per second, excluding
6. Results This section describes the performance that was achieved using the RAMA file system. The resulting numbers represent actual file data bytes transferred to/from server disks per second, excluding
COMPUTER SCIENCE 4500 OPERATING SYSTEMS
 Last update: 3/28/2017 COMPUTER SCIENCE 4500 OPERATING SYSTEMS 2017 Stanley Wileman Module 9: Memory Management Part 1 In This Module 2! Memory management functions! Types of memory and typical uses! Simple
Last update: 3/28/2017 COMPUTER SCIENCE 4500 OPERATING SYSTEMS 2017 Stanley Wileman Module 9: Memory Management Part 1 In This Module 2! Memory management functions! Types of memory and typical uses! Simple
File system internals Tanenbaum, Chapter 4. COMP3231 Operating Systems
 File system internals Tanenbaum, Chapter 4 COMP3231 Operating Systems Architecture of the OS storage stack Application File system: Hides physical location of data on the disk Exposes: directory hierarchy,
File system internals Tanenbaum, Chapter 4 COMP3231 Operating Systems Architecture of the OS storage stack Application File system: Hides physical location of data on the disk Exposes: directory hierarchy,
What is a file system
 COSC 6397 Big Data Analytics Distributed File Systems Edgar Gabriel Spring 2017 What is a file system A clearly defined method that the OS uses to store, catalog and retrieve files Manage the bits that
COSC 6397 Big Data Analytics Distributed File Systems Edgar Gabriel Spring 2017 What is a file system A clearly defined method that the OS uses to store, catalog and retrieve files Manage the bits that
FILE SYSTEMS. CS124 Operating Systems Winter , Lecture 23
 FILE SYSTEMS CS124 Operating Systems Winter 2015-2016, Lecture 23 2 Persistent Storage All programs require some form of persistent storage that lasts beyond the lifetime of an individual process Most
FILE SYSTEMS CS124 Operating Systems Winter 2015-2016, Lecture 23 2 Persistent Storage All programs require some form of persistent storage that lasts beyond the lifetime of an individual process Most
CS Operating Systems
 CS 4500 - Operating Systems Module 9: Memory Management - Part 1 Stanley Wileman Department of Computer Science University of Nebraska at Omaha Omaha, NE 68182-0500, USA June 9, 2017 In This Module...
CS 4500 - Operating Systems Module 9: Memory Management - Part 1 Stanley Wileman Department of Computer Science University of Nebraska at Omaha Omaha, NE 68182-0500, USA June 9, 2017 In This Module...
CS Operating Systems
 CS 4500 - Operating Systems Module 9: Memory Management - Part 1 Stanley Wileman Department of Computer Science University of Nebraska at Omaha Omaha, NE 68182-0500, USA June 9, 2017 In This Module...
CS 4500 - Operating Systems Module 9: Memory Management - Part 1 Stanley Wileman Department of Computer Science University of Nebraska at Omaha Omaha, NE 68182-0500, USA June 9, 2017 In This Module...
Chapter 8 Virtual Memory
 Operating Systems: Internals and Design Principles Chapter 8 Virtual Memory Seventh Edition William Stallings Operating Systems: Internals and Design Principles You re gonna need a bigger boat. Steven
Operating Systems: Internals and Design Principles Chapter 8 Virtual Memory Seventh Edition William Stallings Operating Systems: Internals and Design Principles You re gonna need a bigger boat. Steven
Linux SMR Support Status
 Linux SMR Support Status Damien Le Moal Vault Linux Storage and Filesystems Conference - 2017 March 23rd, 2017 Outline Standards and Kernel Support Status Kernel Details - What was needed Block stack File
Linux SMR Support Status Damien Le Moal Vault Linux Storage and Filesystems Conference - 2017 March 23rd, 2017 Outline Standards and Kernel Support Status Kernel Details - What was needed Block stack File
Chapter 8: Virtual Memory. Operating System Concepts
 Chapter 8: Virtual Memory Silberschatz, Galvin and Gagne 2009 Chapter 8: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating
Chapter 8: Virtual Memory Silberschatz, Galvin and Gagne 2009 Chapter 8: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating
Improving I/O Bandwidth With Cray DVS Client-Side Caching
 Improving I/O Bandwidth With Cray DVS Client-Side Caching Bryce Hicks Cray Inc. Bloomington, MN USA bryceh@cray.com Abstract Cray s Data Virtualization Service, DVS, is an I/O forwarder providing access
Improving I/O Bandwidth With Cray DVS Client-Side Caching Bryce Hicks Cray Inc. Bloomington, MN USA bryceh@cray.com Abstract Cray s Data Virtualization Service, DVS, is an I/O forwarder providing access
CS5460: Operating Systems Lecture 20: File System Reliability
 CS5460: Operating Systems Lecture 20: File System Reliability File System Optimizations Modern Historic Technique Disk buffer cache Aggregated disk I/O Prefetching Disk head scheduling Disk interleaving
CS5460: Operating Systems Lecture 20: File System Reliability File System Optimizations Modern Historic Technique Disk buffer cache Aggregated disk I/O Prefetching Disk head scheduling Disk interleaving
RAID SEMINAR REPORT /09/2004 Asha.P.M NO: 612 S7 ECE
 RAID SEMINAR REPORT 2004 Submitted on: Submitted by: 24/09/2004 Asha.P.M NO: 612 S7 ECE CONTENTS 1. Introduction 1 2. The array and RAID controller concept 2 2.1. Mirroring 3 2.2. Parity 5 2.3. Error correcting
RAID SEMINAR REPORT 2004 Submitted on: Submitted by: 24/09/2004 Asha.P.M NO: 612 S7 ECE CONTENTS 1. Introduction 1 2. The array and RAID controller concept 2 2.1. Mirroring 3 2.2. Parity 5 2.3. Error correcting
Virtual to physical address translation
 Virtual to physical address translation Virtual memory with paging Page table per process Page table entry includes present bit frame number modify bit flags for protection and sharing. Page tables can
Virtual to physical address translation Virtual memory with paging Page table per process Page table entry includes present bit frame number modify bit flags for protection and sharing. Page tables can
CA485 Ray Walshe Google File System
 Google File System Overview Google File System is scalable, distributed file system on inexpensive commodity hardware that provides: Fault Tolerance File system runs on hundreds or thousands of storage
Google File System Overview Google File System is scalable, distributed file system on inexpensive commodity hardware that provides: Fault Tolerance File system runs on hundreds or thousands of storage
Topics. File Buffer Cache for Performance. What to Cache? COS 318: Operating Systems. File Performance and Reliability
 Topics COS 318: Operating Systems File Performance and Reliability File buffer cache Disk failure and recovery tools Consistent updates Transactions and logging 2 File Buffer Cache for Performance What
Topics COS 318: Operating Systems File Performance and Reliability File buffer cache Disk failure and recovery tools Consistent updates Transactions and logging 2 File Buffer Cache for Performance What
Crash Consistency: FSCK and Journaling. Dongkun Shin, SKKU
 Crash Consistency: FSCK and Journaling 1 Crash-consistency problem File system data structures must persist stored on HDD/SSD despite power loss or system crash Crash-consistency problem The system may
Crash Consistency: FSCK and Journaling 1 Crash-consistency problem File system data structures must persist stored on HDD/SSD despite power loss or system crash Crash-consistency problem The system may
Virtual Memory. Reading. Sections 5.4, 5.5, 5.6, 5.8, 5.10 (2) Lecture notes from MKP and S. Yalamanchili
 Virtual Memory Lecture notes from MKP and S. Yalamanchili Sections 5.4, 5.5, 5.6, 5.8, 5.10 Reading (2) 1 The Memory Hierarchy ALU registers Cache Memory Memory Memory Managed by the compiler Memory Managed
Virtual Memory Lecture notes from MKP and S. Yalamanchili Sections 5.4, 5.5, 5.6, 5.8, 5.10 Reading (2) 1 The Memory Hierarchy ALU registers Cache Memory Memory Memory Managed by the compiler Memory Managed
Chapter 11: Implementing File Systems
 Silberschatz 1 Chapter 11: Implementing File Systems Thursday, November 08, 2007 9:55 PM File system = a system stores files on secondary storage. A disk may have more than one file system. Disk are divided
Silberschatz 1 Chapter 11: Implementing File Systems Thursday, November 08, 2007 9:55 PM File system = a system stores files on secondary storage. A disk may have more than one file system. Disk are divided
OPERATING SYSTEM. Chapter 9: Virtual Memory
 OPERATING SYSTEM Chapter 9: Virtual Memory Chapter 9: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating Kernel Memory
OPERATING SYSTEM Chapter 9: Virtual Memory Chapter 9: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating Kernel Memory
Accelerated Library Framework for Hybrid-x86
 Software Development Kit for Multicore Acceleration Version 3.0 Accelerated Library Framework for Hybrid-x86 Programmer s Guide and API Reference Version 1.0 DRAFT SC33-8406-00 Software Development Kit
Software Development Kit for Multicore Acceleration Version 3.0 Accelerated Library Framework for Hybrid-x86 Programmer s Guide and API Reference Version 1.0 DRAFT SC33-8406-00 Software Development Kit
Chapter 11: File System Implementation. Objectives
 Chapter 11: File System Implementation Objectives To describe the details of implementing local file systems and directory structures To describe the implementation of remote file systems To discuss block
Chapter 11: File System Implementation Objectives To describe the details of implementing local file systems and directory structures To describe the implementation of remote file systems To discuss block
CHAPTER 11: IMPLEMENTING FILE SYSTEMS (COMPACT) By I-Chen Lin Textbook: Operating System Concepts 9th Ed.
 CHAPTER 11: IMPLEMENTING FILE SYSTEMS (COMPACT) By I-Chen Lin Textbook: Operating System Concepts 9th Ed. File-System Structure File structure Logical storage unit Collection of related information File
CHAPTER 11: IMPLEMENTING FILE SYSTEMS (COMPACT) By I-Chen Lin Textbook: Operating System Concepts 9th Ed. File-System Structure File structure Logical storage unit Collection of related information File
CS252 S05. Main memory management. Memory hardware. The scale of things. Memory hardware (cont.) Bottleneck
 Main memory management CMSC 411 Computer Systems Architecture Lecture 16 Memory Hierarchy 3 (Main Memory & Memory) Questions: How big should main memory be? How to handle reads and writes? How to find
Main memory management CMSC 411 Computer Systems Architecture Lecture 16 Memory Hierarchy 3 (Main Memory & Memory) Questions: How big should main memory be? How to handle reads and writes? How to find
Shared snapshots. 1 Abstract. 2 Introduction. Mikulas Patocka Red Hat Czech, s.r.o. Purkynova , Brno Czech Republic
 Shared snapshots Mikulas Patocka Red Hat Czech, s.r.o. Purkynova 99 612 45, Brno Czech Republic mpatocka@redhat.com 1 Abstract Shared snapshots enable the administrator to take many snapshots of the same
Shared snapshots Mikulas Patocka Red Hat Czech, s.r.o. Purkynova 99 612 45, Brno Czech Republic mpatocka@redhat.com 1 Abstract Shared snapshots enable the administrator to take many snapshots of the same
Ref: Chap 12. Secondary Storage and I/O Systems. Applied Operating System Concepts 12.1
 Ref: Chap 12 Secondary Storage and I/O Systems Applied Operating System Concepts 12.1 Part 1 - Secondary Storage Secondary storage typically: is anything that is outside of primary memory does not permit
Ref: Chap 12 Secondary Storage and I/O Systems Applied Operating System Concepts 12.1 Part 1 - Secondary Storage Secondary storage typically: is anything that is outside of primary memory does not permit
File Systems: Consistency Issues
 File Systems: Consistency Issues File systems maintain many data structures Free list/bit vector Directories File headers and inode structures res Data blocks File Systems: Consistency Issues All data
File Systems: Consistency Issues File systems maintain many data structures Free list/bit vector Directories File headers and inode structures res Data blocks File Systems: Consistency Issues All data
Disk Scheduling COMPSCI 386
 Disk Scheduling COMPSCI 386 Topics Disk Structure (9.1 9.2) Disk Scheduling (9.4) Allocation Methods (11.4) Free Space Management (11.5) Hard Disk Platter diameter ranges from 1.8 to 3.5 inches. Both sides
Disk Scheduling COMPSCI 386 Topics Disk Structure (9.1 9.2) Disk Scheduling (9.4) Allocation Methods (11.4) Free Space Management (11.5) Hard Disk Platter diameter ranges from 1.8 to 3.5 inches. Both sides
Chapter 8 & Chapter 9 Main Memory & Virtual Memory
 Chapter 8 & Chapter 9 Main Memory & Virtual Memory 1. Various ways of organizing memory hardware. 2. Memory-management techniques: 1. Paging 2. Segmentation. Introduction Memory consists of a large array
Chapter 8 & Chapter 9 Main Memory & Virtual Memory 1. Various ways of organizing memory hardware. 2. Memory-management techniques: 1. Paging 2. Segmentation. Introduction Memory consists of a large array
CS 111. Operating Systems Peter Reiher
 Operating System Principles: File Systems Operating Systems Peter Reiher Page 1 Outline File systems: Why do we need them? Why are they challenging? Basic elements of file system design Designing file
Operating System Principles: File Systems Operating Systems Peter Reiher Page 1 Outline File systems: Why do we need them? Why are they challenging? Basic elements of file system design Designing file
CS370 Operating Systems
 CS370 Operating Systems Colorado State University Yashwant K Malaiya Fall 2017 Lecture 21 Main Memory Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 FAQ Why not increase page size
CS370 Operating Systems Colorado State University Yashwant K Malaiya Fall 2017 Lecture 21 Main Memory Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 FAQ Why not increase page size
Heap Management. Heap Allocation
 Heap Management Heap Allocation A very flexible storage allocation mechanism is heap allocation. Any number of data objects can be allocated and freed in a memory pool, called a heap. Heap allocation is
Heap Management Heap Allocation A very flexible storage allocation mechanism is heap allocation. Any number of data objects can be allocated and freed in a memory pool, called a heap. Heap allocation is
IMPROVING THE PERFORMANCE, INTEGRITY, AND MANAGEABILITY OF PHYSICAL STORAGE IN DB2 DATABASES
 IMPROVING THE PERFORMANCE, INTEGRITY, AND MANAGEABILITY OF PHYSICAL STORAGE IN DB2 DATABASES Ram Narayanan August 22, 2003 VERITAS ARCHITECT NETWORK TABLE OF CONTENTS The Database Administrator s Challenge
IMPROVING THE PERFORMANCE, INTEGRITY, AND MANAGEABILITY OF PHYSICAL STORAGE IN DB2 DATABASES Ram Narayanan August 22, 2003 VERITAS ARCHITECT NETWORK TABLE OF CONTENTS The Database Administrator s Challenge
The Google File System
 October 13, 2010 Based on: S. Ghemawat, H. Gobioff, and S.-T. Leung: The Google file system, in Proceedings ACM SOSP 2003, Lake George, NY, USA, October 2003. 1 Assumptions Interface Architecture Single
October 13, 2010 Based on: S. Ghemawat, H. Gobioff, and S.-T. Leung: The Google file system, in Proceedings ACM SOSP 2003, Lake George, NY, USA, October 2003. 1 Assumptions Interface Architecture Single
Name: Instructions. Problem 1 : Short answer. [48 points] CMU / Storage Systems 23 Feb 2011 Spring 2012 Exam 1
![Name: Instructions. Problem 1 : Short answer. [48 points] CMU / Storage Systems 23 Feb 2011 Spring 2012 Exam 1 Name: Instructions. Problem 1 : Short answer. [48 points] CMU / Storage Systems 23 Feb 2011 Spring 2012 Exam 1](/thumbs/95/126247775.jpg) CMU 18-746/15-746 Storage Systems 23 Feb 2011 Spring 2012 Exam 1 Instructions Name: There are three (3) questions on the exam. You may find questions that could have several answers and require an explanation
CMU 18-746/15-746 Storage Systems 23 Feb 2011 Spring 2012 Exam 1 Instructions Name: There are three (3) questions on the exam. You may find questions that could have several answers and require an explanation
CS24: INTRODUCTION TO COMPUTING SYSTEMS. Spring 2015 Lecture 25
 CS24: INTRODUCTION TO COMPUTING SYSTEMS Spring 2015 Lecture 25 LAST TIME: PROCESS MEMORY LAYOUT! Explored how Linux uses IA32! All processes have a similar layout Each process has its own page table structure
CS24: INTRODUCTION TO COMPUTING SYSTEMS Spring 2015 Lecture 25 LAST TIME: PROCESS MEMORY LAYOUT! Explored how Linux uses IA32! All processes have a similar layout Each process has its own page table structure
Chapter 8 Virtual Memory
 Chapter 8 Virtual Memory Contents Hardware and control structures Operating system software Unix and Solaris memory management Linux memory management Windows 2000 memory management Characteristics of
Chapter 8 Virtual Memory Contents Hardware and control structures Operating system software Unix and Solaris memory management Linux memory management Windows 2000 memory management Characteristics of
Filesystem. Disclaimer: some slides are adopted from book authors slides with permission 1
 Filesystem Disclaimer: some slides are adopted from book authors slides with permission 1 Storage Subsystem in Linux OS Inode cache User Applications System call Interface Virtual File System (VFS) Filesystem
Filesystem Disclaimer: some slides are adopted from book authors slides with permission 1 Storage Subsystem in Linux OS Inode cache User Applications System call Interface Virtual File System (VFS) Filesystem
Deallocation Mechanisms. User-controlled Deallocation. Automatic Garbage Collection
 Deallocation Mechanisms User-controlled Deallocation Allocating heap space is fairly easy. But how do we deallocate heap memory no longer in use? Sometimes we may never need to deallocate! If heaps objects
Deallocation Mechanisms User-controlled Deallocation Allocating heap space is fairly easy. But how do we deallocate heap memory no longer in use? Sometimes we may never need to deallocate! If heaps objects
I, J A[I][J] / /4 8000/ I, J A(J, I) Chapter 5 Solutions S-3.
![I, J A[I][J] / /4 8000/ I, J A(J, I) Chapter 5 Solutions S-3. I, J A[I][J] / /4 8000/ I, J A(J, I) Chapter 5 Solutions S-3.](/thumbs/81/83055456.jpg) 5 Solutions Chapter 5 Solutions S-3 5.1 5.1.1 4 5.1.2 I, J 5.1.3 A[I][J] 5.1.4 3596 8 800/4 2 8 8/4 8000/4 5.1.5 I, J 5.1.6 A(J, I) 5.2 5.2.1 Word Address Binary Address Tag Index Hit/Miss 5.2.2 3 0000
5 Solutions Chapter 5 Solutions S-3 5.1 5.1.1 4 5.1.2 I, J 5.1.3 A[I][J] 5.1.4 3596 8 800/4 2 8 8/4 8000/4 5.1.5 I, J 5.1.6 A(J, I) 5.2 5.2.1 Word Address Binary Address Tag Index Hit/Miss 5.2.2 3 0000
Operating Systems. Lecture File system implementation. Master of Computer Science PUF - Hồ Chí Minh 2016/2017
 Operating Systems Lecture 7.2 - File system implementation Adrien Krähenbühl Master of Computer Science PUF - Hồ Chí Minh 2016/2017 Design FAT or indexed allocation? UFS, FFS & Ext2 Journaling with Ext3
Operating Systems Lecture 7.2 - File system implementation Adrien Krähenbühl Master of Computer Science PUF - Hồ Chí Minh 2016/2017 Design FAT or indexed allocation? UFS, FFS & Ext2 Journaling with Ext3
Discriminating Hierarchical Storage (DHIS)
 Discriminating Hierarchical Storage (DHIS) Chaitanya Yalamanchili, Kiron Vijayasankar, Erez Zadok Stony Brook University Gopalan Sivathanu Google Inc. http://www.fsl.cs.sunysb.edu/ Discriminating Hierarchical
Discriminating Hierarchical Storage (DHIS) Chaitanya Yalamanchili, Kiron Vijayasankar, Erez Zadok Stony Brook University Gopalan Sivathanu Google Inc. http://www.fsl.cs.sunysb.edu/ Discriminating Hierarchical
Utilizing Linux Kernel Components in K42 K42 Team modified October 2001
 K42 Team modified October 2001 This paper discusses how K42 uses Linux-kernel components to support a wide range of hardware, a full-featured TCP/IP stack and Linux file-systems. An examination of the
K42 Team modified October 2001 This paper discusses how K42 uses Linux-kernel components to support a wide range of hardware, a full-featured TCP/IP stack and Linux file-systems. An examination of the
Modification and Evaluation of Linux I/O Schedulers
 Modification and Evaluation of Linux I/O Schedulers 1 Asad Naweed, Joe Di Natale, and Sarah J Andrabi University of North Carolina at Chapel Hill Abstract In this paper we present three different Linux
Modification and Evaluation of Linux I/O Schedulers 1 Asad Naweed, Joe Di Natale, and Sarah J Andrabi University of North Carolina at Chapel Hill Abstract In this paper we present three different Linux
Che-Wei Chang Department of Computer Science and Information Engineering, Chang Gung University
 Che-Wei Chang chewei@mail.cgu.edu.tw Department of Computer Science and Information Engineering, Chang Gung University l Chapter 10: File System l Chapter 11: Implementing File-Systems l Chapter 12: Mass-Storage
Che-Wei Chang chewei@mail.cgu.edu.tw Department of Computer Science and Information Engineering, Chang Gung University l Chapter 10: File System l Chapter 11: Implementing File-Systems l Chapter 12: Mass-Storage
Ricardo Rocha. Department of Computer Science Faculty of Sciences University of Porto
 Ricardo Rocha Department of Computer Science Faculty of Sciences University of Porto Slides based on the book Operating System Concepts, 9th Edition, Abraham Silberschatz, Peter B. Galvin and Greg Gagne,
Ricardo Rocha Department of Computer Science Faculty of Sciences University of Porto Slides based on the book Operating System Concepts, 9th Edition, Abraham Silberschatz, Peter B. Galvin and Greg Gagne,
OPERATING SYSTEM. Chapter 12: File System Implementation
 OPERATING SYSTEM Chapter 12: File System Implementation Chapter 12: File System Implementation File-System Structure File-System Implementation Directory Implementation Allocation Methods Free-Space Management
OPERATING SYSTEM Chapter 12: File System Implementation Chapter 12: File System Implementation File-System Structure File-System Implementation Directory Implementation Allocation Methods Free-Space Management
File Systems: Fundamentals
 File Systems: Fundamentals 1 Files! What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks)! File attributes Ø Name, type, location, size, protection, creator,
File Systems: Fundamentals 1 Files! What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks)! File attributes Ø Name, type, location, size, protection, creator,
A GPFS Primer October 2005
 A Primer October 2005 Overview This paper describes (General Parallel File System) Version 2, Release 3 for AIX 5L and Linux. It provides an overview of key concepts which should be understood by those
A Primer October 2005 Overview This paper describes (General Parallel File System) Version 2, Release 3 for AIX 5L and Linux. It provides an overview of key concepts which should be understood by those
CIS Operating Systems File Systems. Professor Qiang Zeng Fall 2017
 CIS 5512 - Operating Systems File Systems Professor Qiang Zeng Fall 2017 Previous class I/O subsystem: hardware aspect Terms: controller, bus, port Addressing: port-mapped IO and memory-mapped IO I/O subsystem:
CIS 5512 - Operating Systems File Systems Professor Qiang Zeng Fall 2017 Previous class I/O subsystem: hardware aspect Terms: controller, bus, port Addressing: port-mapped IO and memory-mapped IO I/O subsystem:
GFS: The Google File System
 GFS: The Google File System Brad Karp UCL Computer Science CS GZ03 / M030 24 th October 2014 Motivating Application: Google Crawl the whole web Store it all on one big disk Process users searches on one
GFS: The Google File System Brad Karp UCL Computer Science CS GZ03 / M030 24 th October 2014 Motivating Application: Google Crawl the whole web Store it all on one big disk Process users searches on one
Flash Drive Emulation
 Flash Drive Emulation Eric Aderhold & Blayne Field aderhold@cs.wisc.edu & bfield@cs.wisc.edu Computer Sciences Department University of Wisconsin, Madison Abstract Flash drives are becoming increasingly
Flash Drive Emulation Eric Aderhold & Blayne Field aderhold@cs.wisc.edu & bfield@cs.wisc.edu Computer Sciences Department University of Wisconsin, Madison Abstract Flash drives are becoming increasingly
Chapter 9: Virtual Memory
 Chapter 9: Virtual Memory Silberschatz, Galvin and Gagne 2013 Chapter 9: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating
Chapter 9: Virtual Memory Silberschatz, Galvin and Gagne 2013 Chapter 9: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating
CIS Operating Systems File Systems. Professor Qiang Zeng Spring 2018
 CIS 3207 - Operating Systems File Systems Professor Qiang Zeng Spring 2018 Previous class I/O subsystem: hardware aspect Terms: controller, bus, port Addressing: port-mapped IO and memory-mapped IO I/O
CIS 3207 - Operating Systems File Systems Professor Qiang Zeng Spring 2018 Previous class I/O subsystem: hardware aspect Terms: controller, bus, port Addressing: port-mapped IO and memory-mapped IO I/O
File Systems: Fundamentals
 1 Files Fundamental Ontology of File Systems File Systems: Fundamentals What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks) File attributes Ø Name, type,
1 Files Fundamental Ontology of File Systems File Systems: Fundamentals What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks) File attributes Ø Name, type,
Addresses in the source program are generally symbolic. A compiler will typically bind these symbolic addresses to re-locatable addresses.
 1 Memory Management Address Binding The normal procedures is to select one of the processes in the input queue and to load that process into memory. As the process executed, it accesses instructions and
1 Memory Management Address Binding The normal procedures is to select one of the processes in the input queue and to load that process into memory. As the process executed, it accesses instructions and
Chapter 11: Implementing File Systems
 Chapter 11: Implementing File Systems Operating System Concepts 99h Edition DM510-14 Chapter 11: Implementing File Systems File-System Structure File-System Implementation Directory Implementation Allocation
Chapter 11: Implementing File Systems Operating System Concepts 99h Edition DM510-14 Chapter 11: Implementing File Systems File-System Structure File-System Implementation Directory Implementation Allocation
Chapter 8: Virtual Memory. Operating System Concepts Essentials 2 nd Edition
 Chapter 8: Virtual Memory Silberschatz, Galvin and Gagne 2013 Chapter 8: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating
Chapter 8: Virtual Memory Silberschatz, Galvin and Gagne 2013 Chapter 8: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating
Foster B-Trees. Lucas Lersch. M. Sc. Caetano Sauer Advisor
 Foster B-Trees Lucas Lersch M. Sc. Caetano Sauer Advisor 14.07.2014 Motivation Foster B-Trees Blink-Trees: multicore concurrency Write-Optimized B-Trees: flash memory large-writes wear leveling defragmentation
Foster B-Trees Lucas Lersch M. Sc. Caetano Sauer Advisor 14.07.2014 Motivation Foster B-Trees Blink-Trees: multicore concurrency Write-Optimized B-Trees: flash memory large-writes wear leveling defragmentation
Chapter 11: Implementing File-Systems
 Chapter 11: Implementing File-Systems Chapter 11 File-System Implementation 11.1 File-System Structure 11.2 File-System Implementation 11.3 Directory Implementation 11.4 Allocation Methods 11.5 Free-Space
Chapter 11: Implementing File-Systems Chapter 11 File-System Implementation 11.1 File-System Structure 11.2 File-System Implementation 11.3 Directory Implementation 11.4 Allocation Methods 11.5 Free-Space
Multi-version Data recovery for Cluster Identifier Forensics Filesystem with Identifier Integrity
 Multi-version Data recovery for Cluster Identifier Forensics Filesystem with Identifier Integrity Mohammed Alhussein, Duminda Wijesekera Department of Computer Science George Mason University Fairfax,
Multi-version Data recovery for Cluster Identifier Forensics Filesystem with Identifier Integrity Mohammed Alhussein, Duminda Wijesekera Department of Computer Science George Mason University Fairfax,
Chapter 13: I/O Systems
 Chapter 13: I/O Systems Chapter 13: I/O Systems I/O Hardware Application I/O Interface Kernel I/O Subsystem Transforming I/O Requests to Hardware Operations Streams Performance 13.2 Silberschatz, Galvin
Chapter 13: I/O Systems Chapter 13: I/O Systems I/O Hardware Application I/O Interface Kernel I/O Subsystem Transforming I/O Requests to Hardware Operations Streams Performance 13.2 Silberschatz, Galvin
An Efficient Snapshot Technique for Ext3 File System in Linux 2.6
 An Efficient Snapshot Technique for Ext3 File System in Linux 2.6 Seungjun Shim*, Woojoong Lee and Chanik Park Department of CSE/GSIT* Pohang University of Science and Technology, Kyungbuk, Republic of
An Efficient Snapshot Technique for Ext3 File System in Linux 2.6 Seungjun Shim*, Woojoong Lee and Chanik Park Department of CSE/GSIT* Pohang University of Science and Technology, Kyungbuk, Republic of
COMPUTER ARCHITECTURE. Virtualization and Memory Hierarchy
 COMPUTER ARCHITECTURE Virtualization and Memory Hierarchy 2 Contents Virtual memory. Policies and strategies. Page tables. Virtual machines. Requirements of virtual machines and ISA support. Virtual machines:
COMPUTER ARCHITECTURE Virtualization and Memory Hierarchy 2 Contents Virtual memory. Policies and strategies. Page tables. Virtual machines. Requirements of virtual machines and ISA support. Virtual machines:
Chapter 12: File System Implementation
 Chapter 12: File System Implementation Chapter 12: File System Implementation File-System Structure File-System Implementation Directory Implementation Allocation Methods Free-Space Management Efficiency
Chapter 12: File System Implementation Chapter 12: File System Implementation File-System Structure File-System Implementation Directory Implementation Allocation Methods Free-Space Management Efficiency
<Insert Picture Here> Filesystem Features and Performance
 Filesystem Features and Performance Chris Mason Filesystems XFS Well established and stable Highly scalable under many workloads Can be slower in metadata intensive workloads Often
Filesystem Features and Performance Chris Mason Filesystems XFS Well established and stable Highly scalable under many workloads Can be slower in metadata intensive workloads Often
Memory Management Topics. CS 537 Lecture 11 Memory. Virtualizing Resources
 Memory Management Topics CS 537 Lecture Memory Michael Swift Goals of memory management convenient abstraction for programming isolation between processes allocate scarce memory resources between competing
Memory Management Topics CS 537 Lecture Memory Michael Swift Goals of memory management convenient abstraction for programming isolation between processes allocate scarce memory resources between competing
FILE SYSTEMS, PART 2. CS124 Operating Systems Winter , Lecture 24
 FILE SYSTEMS, PART 2 CS124 Operating Systems Winter 2015-2016, Lecture 24 2 Files and Processes The OS maintains a buffer of storage blocks in memory Storage devices are often much slower than the CPU;
FILE SYSTEMS, PART 2 CS124 Operating Systems Winter 2015-2016, Lecture 24 2 Files and Processes The OS maintains a buffer of storage blocks in memory Storage devices are often much slower than the CPU;
Clustering and Reclustering HEP Data in Object Databases
 Clustering and Reclustering HEP Data in Object Databases Koen Holtman CERN EP division CH - Geneva 3, Switzerland We formulate principles for the clustering of data, applicable to both sequential HEP applications
Clustering and Reclustering HEP Data in Object Databases Koen Holtman CERN EP division CH - Geneva 3, Switzerland We formulate principles for the clustering of data, applicable to both sequential HEP applications
Chapter 1: Distributed Information Systems
 Chapter 1: Distributed Information Systems Contents - Chapter 1 Design of an information system Layers and tiers Bottom up design Top down design Architecture of an information system One tier Two tier
Chapter 1: Distributed Information Systems Contents - Chapter 1 Design of an information system Layers and tiers Bottom up design Top down design Architecture of an information system One tier Two tier
Virtualization and memory hierarchy
 Virtualization and memory hierarchy Computer Architecture J. Daniel García Sánchez (coordinator) David Expósito Singh Francisco Javier García Blas ARCOS Group Computer Science and Engineering Department
Virtualization and memory hierarchy Computer Architecture J. Daniel García Sánchez (coordinator) David Expósito Singh Francisco Javier García Blas ARCOS Group Computer Science and Engineering Department
GFS: The Google File System. Dr. Yingwu Zhu
 GFS: The Google File System Dr. Yingwu Zhu Motivating Application: Google Crawl the whole web Store it all on one big disk Process users searches on one big CPU More storage, CPU required than one PC can
GFS: The Google File System Dr. Yingwu Zhu Motivating Application: Google Crawl the whole web Store it all on one big disk Process users searches on one big CPU More storage, CPU required than one PC can
File Systems. CS170 Fall 2018
 File Systems CS170 Fall 2018 Table of Content File interface review File-System Structure File-System Implementation Directory Implementation Allocation Methods of Disk Space Free-Space Management Contiguous
File Systems CS170 Fall 2018 Table of Content File interface review File-System Structure File-System Implementation Directory Implementation Allocation Methods of Disk Space Free-Space Management Contiguous
Future File System: An Evaluation
 Future System: An Evaluation Brian Gaffey and Daniel J. Messer, Cray Research, Inc., Eagan, Minnesota, USA ABSTRACT: Cray Research s file system, NC1, is based on an early System V technology. Cray has
Future System: An Evaluation Brian Gaffey and Daniel J. Messer, Cray Research, Inc., Eagan, Minnesota, USA ABSTRACT: Cray Research s file system, NC1, is based on an early System V technology. Cray has
Main Points. File layout Directory layout
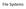 File Systems Main Points File layout Directory layout File System Design Constraints For small files: Small blocks for storage efficiency Files used together should be stored together For large files:
File Systems Main Points File layout Directory layout File System Design Constraints For small files: Small blocks for storage efficiency Files used together should be stored together For large files:
Operating System Concepts Ch. 11: File System Implementation
 Operating System Concepts Ch. 11: File System Implementation Silberschatz, Galvin & Gagne Introduction When thinking about file system implementation in Operating Systems, it is important to realize the
Operating System Concepts Ch. 11: File System Implementation Silberschatz, Galvin & Gagne Introduction When thinking about file system implementation in Operating Systems, it is important to realize the
File System Implementation. Jin-Soo Kim Computer Systems Laboratory Sungkyunkwan University
 File System Implementation Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Implementing a File System On-disk structures How does file system represent
File System Implementation Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Implementing a File System On-disk structures How does file system represent
The Google File System
 The Google File System Sanjay Ghemawat, Howard Gobioff, and Shun-Tak Leung SOSP 2003 presented by Kun Suo Outline GFS Background, Concepts and Key words Example of GFS Operations Some optimizations in
The Google File System Sanjay Ghemawat, Howard Gobioff, and Shun-Tak Leung SOSP 2003 presented by Kun Suo Outline GFS Background, Concepts and Key words Example of GFS Operations Some optimizations in
COMP 530: Operating Systems File Systems: Fundamentals
 File Systems: Fundamentals Don Porter Portions courtesy Emmett Witchel 1 Files What is a file? A named collection of related information recorded on secondary storage (e.g., disks) File attributes Name,
File Systems: Fundamentals Don Porter Portions courtesy Emmett Witchel 1 Files What is a file? A named collection of related information recorded on secondary storage (e.g., disks) File attributes Name,
Operating Systems. Designed and Presented by Dr. Ayman Elshenawy Elsefy
 Operating Systems Designed and Presented by Dr. Ayman Elshenawy Elsefy Dept. of Systems & Computer Eng.. AL-AZHAR University Website : eaymanelshenawy.wordpress.com Email : eaymanelshenawy@yahoo.com Reference
Operating Systems Designed and Presented by Dr. Ayman Elshenawy Elsefy Dept. of Systems & Computer Eng.. AL-AZHAR University Website : eaymanelshenawy.wordpress.com Email : eaymanelshenawy@yahoo.com Reference
The Btrfs Filesystem. Chris Mason
 The Btrfs Filesystem Chris Mason The Btrfs Filesystem Jointly developed by a number of companies Oracle, Redhat, Fujitsu, Intel, SUSE, many others All data and metadata is written via copy-on-write CRCs
The Btrfs Filesystem Chris Mason The Btrfs Filesystem Jointly developed by a number of companies Oracle, Redhat, Fujitsu, Intel, SUSE, many others All data and metadata is written via copy-on-write CRCs
Ext3/4 file systems. Don Porter CSE 506
 Ext3/4 file systems Don Porter CSE 506 Logical Diagram Binary Formats Memory Allocators System Calls Threads User Today s Lecture Kernel RCU File System Networking Sync Memory Management Device Drivers
Ext3/4 file systems Don Porter CSE 506 Logical Diagram Binary Formats Memory Allocators System Calls Threads User Today s Lecture Kernel RCU File System Networking Sync Memory Management Device Drivers
CS3350B Computer Architecture
 CS335B Computer Architecture Winter 25 Lecture 32: Exploiting Memory Hierarchy: How? Marc Moreno Maza wwwcsduwoca/courses/cs335b [Adapted from lectures on Computer Organization and Design, Patterson &
CS335B Computer Architecture Winter 25 Lecture 32: Exploiting Memory Hierarchy: How? Marc Moreno Maza wwwcsduwoca/courses/cs335b [Adapted from lectures on Computer Organization and Design, Patterson &
CS307: Operating Systems
 CS307: Operating Systems Chentao Wu 吴晨涛 Associate Professor Dept. of Computer Science and Engineering Shanghai Jiao Tong University SEIEE Building 3-513 wuct@cs.sjtu.edu.cn Download Lectures ftp://public.sjtu.edu.cn
CS307: Operating Systems Chentao Wu 吴晨涛 Associate Professor Dept. of Computer Science and Engineering Shanghai Jiao Tong University SEIEE Building 3-513 wuct@cs.sjtu.edu.cn Download Lectures ftp://public.sjtu.edu.cn
PROJECT 6: PINTOS FILE SYSTEM. CS124 Operating Systems Winter , Lecture 25
 PROJECT 6: PINTOS FILE SYSTEM CS124 Operating Systems Winter 2015-2016, Lecture 25 2 Project 6: Pintos File System Last project is to improve the Pintos file system Note: Please ask before using late tokens
PROJECT 6: PINTOS FILE SYSTEM CS124 Operating Systems Winter 2015-2016, Lecture 25 2 Project 6: Pintos File System Last project is to improve the Pintos file system Note: Please ask before using late tokens
FFS: The Fast File System -and- The Magical World of SSDs
 FFS: The Fast File System -and- The Magical World of SSDs The Original, Not-Fast Unix Filesystem Disk Superblock Inodes Data Directory Name i-number Inode Metadata Direct ptr......... Indirect ptr 2-indirect
FFS: The Fast File System -and- The Magical World of SSDs The Original, Not-Fast Unix Filesystem Disk Superblock Inodes Data Directory Name i-number Inode Metadata Direct ptr......... Indirect ptr 2-indirect
The Google File System
 The Google File System Sanjay Ghemawat, Howard Gobioff, and Shun-Tak Leung December 2003 ACM symposium on Operating systems principles Publisher: ACM Nov. 26, 2008 OUTLINE INTRODUCTION DESIGN OVERVIEW
The Google File System Sanjay Ghemawat, Howard Gobioff, and Shun-Tak Leung December 2003 ACM symposium on Operating systems principles Publisher: ACM Nov. 26, 2008 OUTLINE INTRODUCTION DESIGN OVERVIEW
CSCI 8530 Advanced Operating Systems. Part 8 High-level Memory Management
 CSCI 8530 Advanced Operating Systems Part 8 High-level Memory Management Updated 9/27/2016 Location of High-level Memory Management in the Hierarchy Our Approach to Memory Management (Review) Divide memory
CSCI 8530 Advanced Operating Systems Part 8 High-level Memory Management Updated 9/27/2016 Location of High-level Memory Management in the Hierarchy Our Approach to Memory Management (Review) Divide memory
Introduction to OS. File Management. MOS Ch. 4. Mahmoud El-Gayyar. Mahmoud El-Gayyar / Introduction to OS 1
 Introduction to OS File Management MOS Ch. 4 Mahmoud El-Gayyar elgayyar@ci.suez.edu.eg Mahmoud El-Gayyar / Introduction to OS 1 File Management Objectives Provide I/O support for a variety of storage device
Introduction to OS File Management MOS Ch. 4 Mahmoud El-Gayyar elgayyar@ci.suez.edu.eg Mahmoud El-Gayyar / Introduction to OS 1 File Management Objectives Provide I/O support for a variety of storage device
