An Algorithm for an Intermittently Atomic Data Service Based on Group Communication
|
|
|
- Clyde Melton
- 5 years ago
- Views:
Transcription
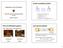
1 An Algorithm for an Intermittently Atomic Data Service Based on Group Communication Roger Khazan and Nancy Lynch I. INTRODUCTION Group communication provides a convenient mechanism for building applications that maintain a replicated state of some sort [1]. Such applications typically implement certain consistency properties regarding how different application clients perceive the replicated state. One of the well-understood and often preferred consistency properties is strong-consistency or atomicity [2], [3, Ch. 13], which creates a perception of the replicated state as being non-replicated. However, in large-scale wide-area settings, providing atomicity may result in prohibitive levels of overhead and sometimes, during network partitions, in blocking the applications until partitions repair. Thus, weaker consistency properties may be more appropriate in such settings. A key question is which weaker consistency properties are still coherent and acceptable to the application clients. In this paper, we propose one way to weaken the atomicity property and illustrate the resulting property, intermittent atomicity, with a simple application. We call this application intermittently-atomic data service (IADS); the application implements a variant of a data service that allows a dynamic group of clients to access and modify a replicated data object. The IADS application is prototypical of some collaborative computing applications, such as a shared white-board application (e.g., [4], [5]). Roughly speaking, intermittent atomicity guarantees that, while the underlying network component is stable, clients perceive the data object as atomic. 1 During periods of instability, the clients perceptions of the object may diverge from the atomic one. The non-atomic semantics may persist until after the underlying component becomes stable again. When stability is regained, the atomic semantics is restored within some finite amount MIT Lincoln Laboratory. 244 Wood St., Lexington, MA 02420, USA. This work was partially sponsored by the Department of the Air Force under the Air Force Contract F C Opinions, interpretations, conclusions, and recommendations are not necessarily endorsed by the US Government. MIT Laboratory for Computer Science. 200 Technology Square, Cambridge, MA 02139, USA. 1 Atomic objects are also known as linearizable [6], stronglyconsistent, non-replicated, and one-copy equivalent. of time: The clients comprising the stable component are informed about the current membership of the client group and the new state of the data object. The new state is computed as an application-specified merge of the states of the members object replicas. From that point on while stability lasts, the clients again perceive the object as an atomic one. A formal definition of intermittent atomicity is presented in [7, Ch. 10] (where intermittent atomicity is called interim atomicity). The IADS application can be conveniently built using standard group communication mechanisms. We demonstrate this by presenting a simple algorithm, IADS, that operates atop a group communication service, GCS, which we assume satisfies the formal design specification of [8], [7]. The algorithm follows the active replication/state-machine approach [9], [10] and utilizes the state-transfer protocol of Amir, et al. [11]. The Virtual Synchrony semantics provided by GCS allows the application to sometimes avoid state-transfer when views change and also to reduce the number of state messages exchanged during a state-transfer protocol. The set of group members that transitions together from v to v is known as the transitional set T of v and v [1]. The Virtually Synchronous Delivery property guarantees that every server in T receives the same set of messages while in view v, before receiving view v and set T from GCS. Thus, if the object replicas of T were mutually consistent upon entering normal mode in view v, they remain mutually consistent when view v is delivered. This leads to two observations: First, it is enough for only one member of T to communicate the state of its replica during state-transfer protocol. Second, state-transfer is unnecessary in situations when the entire membership of the new view v has transitioned together from view v (i.e., v.set = T). II. APPLICATION DESCRIPTION The Obj Data Type: The IADS application manages deterministic data objects whose serial behavior is specified by some data type, Obj. The Obj data type defines possible states of the objects and operators on the objects; it is defined similarly to the variable type of [3]. Formally, the Obj type consists of: a) a set S of
2 object states; b) a distinguished initial state s 0 S; c) a set R of values; and d) a set O of operations, each of the type S (S R). Furthermore, we assume an application-defined function merge: SetOf(Proc S) S. This function is used during state-transfer to compute a new, common, state of the object based on, possibly different, states of the participating object replicas. We assume that the merge function has the identity property, i.e., merge({ p 1, x, p 2, x,..., p k, x }) = x. For simplicity we assume that the application manages a single data object and all the operations requested by clients pertain to this object. The algorithm for the intermittently-atomic data service follows the standard active replication (statemachine) approach [9], [10] and utilizes the state-transfer protocol of Amir et al. [11]. The algorithm is composed of a collection of application end-points, which run the same algorithm. The application end-points operate as clients of the GCS system as members of the same process group. Figure 2 shows interaction of an application end-point with its client and with the underlying GCS end-point. Client request refresh Client p request refresh Client q request refresh The IADS Application Client r request refresh send IADS End point deliver block block_ok view Fig. 1. Interaction of the application with its clients. GCS End Point Application Interface: The interface between the IADS application and its clients consists of the typical request, and actions: The application receives client p s request to process operation o O via input action request p (o), and it eventually responds to the operation via p (o, r), where r R is the return value resulting from applying operation o to the underlying data object. In addition to the request/reply actions, the interface with client p includes special refresh p (set, x) actions, where set SetOf(Proc) and x S. The application uses these actions to refresh the client s perception of its collaboration group (set) and the state of the underlying data object (x). For simplicity, we do not include the join and leave actions as part of the interface. Such actions can be processed by the group communication service as requests to join or leave a specified application group. Application Semantics: Chapter 10 of [7] contains a formal specification of IADS. Among the specified properties, there are some basic ones that are not specific to intermittent atomicity; these include properties such as correspondence between requests and s, and processing of requests submitted by a given client in gap-free FIFO order. The properties that are specific to intermittent atomicity are Stabilization and Interim Atomicity. The Stabilization property is a liveness property that requires IADS to eventually stabilize after a set of clients becomes stable. The Interim Atomicity property is a combination of safety and liveness; it requires IADS to behave as an atomic data service in situations when IADS is stable. III. GCS-BASED ALGORITHM Fig. 2. Application design architecture: An application end-point interacts with its client and the underlying GCS end-point. normal view state transfer completed view state transfer Fig. 3. Application modes of operation: view-labeled transitions leading to normal mode correspond to circumstances when an application end-point avoids state-transfer by relying on the GCS semantics. Every application end-point maintains a replica of the data object. The object replicas are modified during normal mode of operation when clients requests are processed, and as a result of state-transfer when a new state of the object is computed from the merge of the object replicas of different application end-points. Figure 3 depicts a state-transition diagram that governs transitions between normal and state-transfer modes. Initially, the mode is normal. An application end-point may switch from normal to state-transfer when it receives a new view from GCS; in some situations, discussed below, the application end-point is able to rely on the guarantees provided by GCS to avoid state-transfer and remain in normal mode. When an application endpoint completes state-transfer, it switches back to normal mode. If GCS delivers a new view before the application end-point completes state-transfer, the application endpoint typically remains in state-transfer mode, but in some situations, discussed below, it may again rely on the guarantees provided by GCS to immediately switch to normal mode.
3 Figure 4 contains an I/O automaton, IADS p, modeling the application end-point at process p (see [3] for the definition of I/O automata). The application end-point maintains a replica, obj, of the data object. Requests submitted by the client are placed into a queue, inp, and later multicast using GCS to the application endpoints comprising the current view. GCS delivers these requests within the same view and in FIFO order. The application end-points append the requests delivered by GCS into a queue, ops[q], according to the sender q. The requests stored in the ops queues are processed during normal mode, according to a total order on all requests communicated in a given view; as we explain below, the algorithm establishes this total order by tagging requests with logical timestamps [9] (see also [10] and [3, page 607]). 2 Processing of requests is done by an internal action do and as a result of receiving a view input from GCS. When an application end-point processes an operation request, it applies the operation to its object replica. If the operation request that is being processed was submitted by the application end-point s own client, the application end-point places the operation and the resulting return value into an output queue, out, to be later reported to the client. Consider application end-points belonging to some stable view. Assume that, at the times when the application end-points start processing requests in the view, the states of their object replicas are the same. In order for their object replicas to stay mutually consistent, the object replicas should undergo the same modifications in the same order at different application end-points; that is, different application end-points should apply the same sequences of operations to their object replicas. Total order through logical time: The IADS algorithm establishes a total ordering on all requests communicated through GCS in a given view using logical timestamps, as in [9] and [3, Sec ]. We chose this well-known, symmetric approach for the sake of concreteness and simplicity. Many different algorithms for implementing totally ordered multicast exist and can be used here, including those that focus on scalability and efficiency in WANs (see [12]). Application end-point p maintains an integer lt[p] which corresponds to p s logical time within the current view; the initial value of lt[p] is 0 and it is reset to 0 when p receives view inputs. When p starts processing a request by multicasting it to other application endpoints, p increments lt[p] and tags the request with the timestamp. Also, whenever p receives a request tagged 2 Note that we implement total ordering within the application algorithm to make it easier to visualize how the algorithm works. In general, however, total ordering would be implemented as a separate layer, above GCS and below the application. with a timestamp ts from some application end-point q, p updates its logical time to max(lt[p], ts) + 1. The total order on messages communicated within the same view is defined as their ordering by the timestamp, application end-point identifier pair. That is, o p totally precedes o q if and only if ((ts p < ts q ) ((ts p = ts q ) (p < q)), where o p is an operation sent by p and tagged with timestamp ts p, and o q is an operation sent by q in the same view as o p and tagged with timestamp ts q. Note that this total order is consistent with both FIFO and causal orderings of requests and s. Normal mode: In normal mode, application end-point p processes the operations in its ops queues according to the total order defined above. Internal action do p (q, o) models processing of an operation o submitted by client at q. Operation o is processed if (a) operation o totally precedes all other operations currently in the ops queues; and (b) p knows that the logical times of all other application end-points in the view exceed the timestamp associated with o. Condition (b) guarantees that p has received all the operations that precede o, and thus, o is the next one in the totally ordered sequence of operations sent in the current view; see [3, Sec ]. The algorithm implements condition (b) by keeping track of the known logical time of every application end-point q in the current view. The application end-point updates lt[q] whenever it receives operation requests sent by q. In addition to communicating the values of their logical times through operations, application end-points also let others know of their logical times by periodically sending special heartbeat messages, lt msg, ts. While the current view remains stable, the application end-points process the same sequences of operations, and thus, remain mutually consistent. When an application end-point receives a new view from GCS, the application end-point processes all of the operations in its ops queues according to the total order, even though condition (b) may not hold for these messages. The sequence of operations processed at this point may diverge from the global sequence because the application end-point may have received only a subset of all of the operations sent in the current view; for example, it may be missing some of the operations sent by disconnected application end-points. However, what is guaranteed by GCS is that members of the transitional set of the new view receive the same set of messages, and hence process the same sequence, if they receive the new view. Thus, after processing the operations in their ops queues, the members of the transitional set have the same states of their object replicas.
4 AUTOMATON IADS p Type: AppMsg = (O Int) Int (SetOf(Proc) S) // operations, heartbeats, and state-transfer OutType = (O R) (SetOf(Proc) S) // operation replies and refresh information Signature: Input: request p (o), O o gcs.deliver p (q, m), Proc q, m AppMsg gcs.view p (v, T), View v, SetOf(Proc) T gcs.block p () Internal: do p (q, o), Proc q, O o Output: p (o, r), O o, R r refresh p (s, x), SetOf(Proc) s, S x gcs.send p (m), m AppMsg gcs.block ok p () State: S obj, initially s 0 QueueOf(O) inp, initially empty QueueOf(OutType) out, initially empty ( q Proc) Int lt[q], initially 0 ( q Proc) QueueOf(O Int) ops[q], initially empty block status {unblocked, requested, blocked}, initially unblocked Transitions: INPUT request p (o) eff: append o to inp OUTPUT gcs.send p ( op msg, o, ts ) pre: block status blocked o = First(inp) ts = lt[p] + 1 eff: remove o from inp lt[p] lt[p]+1 append o, ts to ops[p] INPUT gcs.deliver p (q, op msg, o, ts ) eff: if (q p) then lt[q] ts lt[p] max(lt[p], ts) + 1 append o, ts to ops[q] INTERNAL do p (q, o) pre: mode = normal q = min{t myview.set : First(ops[t]).ts = = (min{first(ops[r]).ts : r myview.set})} ( t myview.set) lt[t] > First(ops[q]).ts o, ts = First(ops[q]) let x and r be s.t. x, r = o(obj) eff: remove o, ts from ops[q] obj x if(p = q) then append o, r to out OUTPUT p (o, r) pre: o, r is first on out eff: remove o, r from out OUTPUT refresh p (set, x) pre: set, x is first on out eff: remove set, x from out OUTPUT gcs.send p ( lt msg, ts ) pre: block status blocked ts = lt[p] INPUT gcs.deliver p (q, lt msg, ts ) eff: if (q p) then lt[q] ts lt[p] max(lt[p], ts) + 1 Fig. 4. View myview, initially v p Bool mode {normal, st} Bool send state, initially false SetOf(Proc) SS, initially {p} SetOf(Proc S) StatesV, initially empty SetOf(Proc) States Await, initially {} INPUT gcs.block p () eff: block status requested OUTPUT gcs.block ok p () pre: block status = requested eff: block status blocked INPUT gcs.view p (v, T) eff: // process all operations in the ops queue while ( q) such that (q = min{t myview.set : First(ops[t]).ts = = (min{first(ops[r]).ts : r myview.set})}) remove first element o, ts from ops[q] obj, r o(obj) if(p = q) then append o, r to out end ( t myview.set) lt[t] 0 myview v block status unblocked // state transfer decision: (mode = normal? SS T : SS SS T) if(v.set = SS) then // normal mode append v.set, obj to out mode normal else // state-transfer State Await v.set; StatesV empty send state (p = min(ss)) mode st state transfer OUTPUT gcs.send p ( st msg, set, x ) pre: block status = unblocked send state = true set, x = SS, obj eff: send state false INPUT gcs.deliver p (q, st msg, set, x ) eff: ( t set) add t, x to StatesV States Await States Await - set if (States Await = {}) then obj merge(statesv) append myview.set, obj to out mode normal Application end-point IADSp of an Interim-Atomic Data Service.
5 After the operations are processed, application endpoint p decides whether or not to enter the state-transfer protocol. Variable SS is used for keeping track of the set of application end-points whose object replicas are synchronized with p; according to [11], SS is computed as the intersection of all the transitional sets delivered since normal mode. If SS is the same as the membership of a new view v, then everyone in the new view is already synchronized and p does not need to participate in a state-transfer protocol for view v; it may resume its normal mode of operation. Otherwise, p enters the state-transfer protocol (see below). The following two paragraphs explain why computing SS as the intersection of all the transitional sets delivered since normal mode makes sense. Consider an application end-point p that receives gcs.view p (v, T) while in view v, and assume that p s mode is normal prior to receiving the new view. If the membership v.set of the new view is the same as transitional set T, then all of the members of v enter the new view directly from v (provided they do enter v). The Virtual Synchrony semantics guarantees that these members have received the same sets of messages while in view v, and hence have applied the same operations in the same order to their object replicas. Since the states of the object replicas of the members of T were the same when they began normal mode in view v, their object replicas are the same after receiving view v from GCS. As an alternative, consider a situation in which the application end-point p receives gcs.view p (v, T) while already engaged in state-transfer in view v. Even though all the application end-points may be transitioning together from v to v, it may be the case that these application end-points had inconsistent object replicas prior to entering view v. Since the state-transfer protocol was interrupted, they did not have a chance to synchronize their object replicas. Thus, it is not sufficient to simply consider transitional set T. The intersection of the current SS set and T yields the set of application endpoints that a) were synchronized when they switched from normal mode to state-transfer, and b) have been synchronized since then. State-transfer protocol: The state-transfer protocol involves each end-point collecting the states of the object replicas of the members of the new view, and then computing a new state for its replica as a merge of the collected states. After the object replica is updated with the result of the merge, the refresh information is placed on the out queue. The refresh information contains the new membership set and the new state of the object. The GCS semantics allows us to reduce the number of messages and the amount of information communicated during the protocol: Only one end-point among the members of SS needs to send the state of its object replica to others. This is because our algorithm maintains a property that after receiving a view, all members of SS have their object replicas in the same state. The optimization is important because state-transfer messages are typically costly due to their large size. The state-transfer protocol in Figure 4 follows the algorithm of [11]. Boolean variable send state controls whether end-point p is the one that has to send its object replica s state on behalf of the end-points in set SS. Set StatesV is used for collecting object replicas states of the view members, and set States Await is used for keeping track of the list of end-points from whom p has not yet received a state-transfer message. Note that end-points keep multicasting their clients operations to one another in the new view, in parallel with the state-transfer protocol. The only part of the algorithm that is blocked during state-transfer is the actual processing of the operations. When state-transfer completes, the end-point may be able to process a whole bunch of operations collected in the ops queues right away, by executing a sequence of do actions. If the state-transfer protocol is interrupted by a delivery of a new view, the end-point, as before, processes all of the operations in its ops queues according to the total order, and then decides whether to re-start a statetransfer protocol or to switch back to normal mode. IV. CONCLUSIONS A proof of the algorithm s correctness and two theoretical performance analysis results are presented in [7, Ch. 10]. One of the performance results deals with how quickly the IADS algorithm processes requests and delivers s to its clients. The algorithm is able to process a given request as soon as it determines the request s position in the totally-ordered sequence of all the requests communicated in the current view and as soon as it receives and processes all the preceding requests. This time depends on the specific algorithm used for totally ordering requests. In general, the performance of state-of-the-art total order algorithms, in situations when the underlying network is well-behaved, is close to a single message latency. To put this result in a larger context, an alternative approach to using Group Communication for building replicated data services is to use Consensus (e.g., [13], [10]). In this approach, during normal mode of operation, the servers hosting object replicas run Consensus to agree on the order in which to process clients requests. For the data services that provide weaker consistency semantics, such as the IADS application, using Consensus is an overkill. Optimized solutions based on Consensus require two round-trip messages: the original message to
6 the leader, a query message from the leader to the endpoints and back, and then the decision message from the leader to the end-points [13]. In contrast, the IADS algorithm is able to process requests in the time it takes to totally-order them, which in the case of a leader-based scheme requires only one round-trip time to the leader. In addition, unlike Consensus, Group Communication provides convenient mechanisms to support partitionable semantics and dynamic sets of clients. The second performance result in [7] expresses how quickly IADS reconfigures and delivers refresh inputs when instabilities occur. Roughly speaking, the performance theorem proved in [7] states that, when used in conjunction with a WAN-oriented group communication service described in [8], [7], every application end-point delivers the final refresh event within about two latencies one detection latency and one message latency away from the time the final group event occurs, provided the application end-point is able to rely on Virtual Synchrony to avoid participating in a state-transfer protocol. Otherwise, if state-transfer is necessary, the final refresh event occurs within about three latencies one detection latency and two message latencies away from the time the final group event occurs. Acknowledgments: We thank Idit Keidar for her helpful comments on the algorithm and this paper. REFERENCES [1] G. V. Chockler and I. Keidar and R. Vitenberg, Group Communication Specifications: A Comprehensive Study, ACM Computing Surveys, vol. 33, no. 4, pp. 1 43, December [2] L. Lamport, On interprocess communication, Parts I and II, Distributed Computing, vol. 1, no. 2, pp , [3] N. A. Lynch, Distributed Algorithms, Morgan Kaufmann Publishers, [4] S. McCanne, A Distributed Whiteboard for Network Conferencing, UC Berkeley CS Dept., May 1992, Available from ftp://ftp.ee.lbl.gov/conferencing/wb. [5] G. Shamir, Shared Whiteboard: A Java Application in the Transis Environment, Lab project, High Availability lab, The Hebrew University of Jerusalem, Jerusalem, Israel, October 1996, Available from: [6] Maurice P. Herlihy and Jeannette M. Wing, Linearizability: A correctness condition for concurrent objects, ACM Transactions on Programming Languages and Systems, vol. 12, no. 3, pp , July [7] Roger Khazan, A One-Round Algorithm for Virtually Synchronous Group Communication in Wide Area Networks, Ph.D. thesis, MIT Dept. of Electrical Eng. and Computer Science, May [8] Idit Keidar and Roger Khazan, A virtually synchronous group multicast algorithm for WANs: Formal approach, SIAM Journal on Computing, vol. 32, no. 1, pp , November 2002, Previous version in ICDCS 2000, pp [9] Lamport, L., Time, clocks, and the ordering of events in a distributed system, Communications of the ACM, vol. 21, no. 7, pp , July 78. [10] Schneider, F. B., Implementing fault tolerant services using the state machine approach: A tutorial, ACM Computing Surveys, vol. 22, no. 4, pp , December [11] Y. Amir and G. V. Chockler and D. Dolev and R. Vitenberg, Efficient state transfer in partitionable environments, in 2nd European Research Seminar on Advances in Distributed Systems (ERSADS 97), pp., , Full version: TR CS98-12, Institute of Computer Science, The Hebrew University, Jerusalem, Israel. [12] Xavier Défago and André Schiper and Péter Urbán, Totally ordered broadcast and multicast algorithms: A comprehensive survey, Tech. Rep.DSC/2000/036, Swiss Federal Institute of Technology, Lausanne, Switzerland, September [13] B. Lampson, How to build a highly available system using consensus, in Distributed Algorithms, LNCS 1151, 1996.
A Framework for Highly Available Services Based on Group Communication
 A Framework for Highly Available Services Based on Group Communication Alan Fekete fekete@cs.usyd.edu.au http://www.cs.usyd.edu.au/ fekete Department of Computer Science F09 University of Sydney 2006,
A Framework for Highly Available Services Based on Group Communication Alan Fekete fekete@cs.usyd.edu.au http://www.cs.usyd.edu.au/ fekete Department of Computer Science F09 University of Sydney 2006,
A Correctness Proof for a Practical Byzantine-Fault-Tolerant Replication Algorithm
 Appears as Technical Memo MIT/LCS/TM-590, MIT Laboratory for Computer Science, June 1999 A Correctness Proof for a Practical Byzantine-Fault-Tolerant Replication Algorithm Miguel Castro and Barbara Liskov
Appears as Technical Memo MIT/LCS/TM-590, MIT Laboratory for Computer Science, June 1999 A Correctness Proof for a Practical Byzantine-Fault-Tolerant Replication Algorithm Miguel Castro and Barbara Liskov
A Virtually Synchronous Group Multicast Algorithm for WANs: Formal Approach
 A Virtually Synchronous Group Multicast Algorithm for WANs: Formal Approach Idit Keidar Roger Khazan Massachusetts Institute of Technology Lab for Computer Science 545 Technology Square, Cambridge, MA
A Virtually Synchronous Group Multicast Algorithm for WANs: Formal Approach Idit Keidar Roger Khazan Massachusetts Institute of Technology Lab for Computer Science 545 Technology Square, Cambridge, MA
Fork Sequential Consistency is Blocking
 Fork Sequential Consistency is Blocking Christian Cachin Idit Keidar Alexander Shraer Novembe4, 008 Abstract We consider an untrusted server storing shared data on behalf of clients. We show that no storage
Fork Sequential Consistency is Blocking Christian Cachin Idit Keidar Alexander Shraer Novembe4, 008 Abstract We consider an untrusted server storing shared data on behalf of clients. We show that no storage
Fork Sequential Consistency is Blocking
 Fork Sequential Consistency is Blocking Christian Cachin Idit Keidar Alexander Shraer May 14, 2008 Abstract We consider an untrusted server storing shared data on behalf of clients. We show that no storage
Fork Sequential Consistency is Blocking Christian Cachin Idit Keidar Alexander Shraer May 14, 2008 Abstract We consider an untrusted server storing shared data on behalf of clients. We show that no storage
A Mechanism for Sequential Consistency in a Distributed Objects System
 A Mechanism for Sequential Consistency in a Distributed Objects System Cristian Ţăpuş, Aleksey Nogin, Jason Hickey, and Jerome White California Institute of Technology Computer Science Department MC 256-80,
A Mechanism for Sequential Consistency in a Distributed Objects System Cristian Ţăpuş, Aleksey Nogin, Jason Hickey, and Jerome White California Institute of Technology Computer Science Department MC 256-80,
at the September 2000 LIBRARIES A uthor... Department of Electrical Engineering and Computer Science August 31, 2000
 I Virtual Synchrony Semantics: A Client - Server Implementation by Igor Tarashchanskiy Submitted to the Department of Electrical Engineering and Computer Science in partial fulfillment of the requirements
I Virtual Synchrony Semantics: A Client - Server Implementation by Igor Tarashchanskiy Submitted to the Department of Electrical Engineering and Computer Science in partial fulfillment of the requirements
Replication in Distributed Systems
 Replication in Distributed Systems Replication Basics Multiple copies of data kept in different nodes A set of replicas holding copies of a data Nodes can be physically very close or distributed all over
Replication in Distributed Systems Replication Basics Multiple copies of data kept in different nodes A set of replicas holding copies of a data Nodes can be physically very close or distributed all over
Distributed systems. Lecture 6: distributed transactions, elections, consensus and replication. Malte Schwarzkopf
 Distributed systems Lecture 6: distributed transactions, elections, consensus and replication Malte Schwarzkopf Last time Saw how we can build ordered multicast Messages between processes in a group Need
Distributed systems Lecture 6: distributed transactions, elections, consensus and replication Malte Schwarzkopf Last time Saw how we can build ordered multicast Messages between processes in a group Need
Multimedia Multicast Transport Service for Groupware
 Multimedia Multicast Transport Service for Groupware Chockler, Gregory V., Huleihel, Nabil, Keidar, Idit, and Dolev, Danny, The Hebrew University of Jerusalem, Jerusalem, Israel 1.0 Abstract Reliability
Multimedia Multicast Transport Service for Groupware Chockler, Gregory V., Huleihel, Nabil, Keidar, Idit, and Dolev, Danny, The Hebrew University of Jerusalem, Jerusalem, Israel 1.0 Abstract Reliability
Asynchronous Reconfiguration for Paxos State Machines
 Asynchronous Reconfiguration for Paxos State Machines Leander Jehl and Hein Meling Department of Electrical Engineering and Computer Science University of Stavanger, Norway Abstract. This paper addresses
Asynchronous Reconfiguration for Paxos State Machines Leander Jehl and Hein Meling Department of Electrical Engineering and Computer Science University of Stavanger, Norway Abstract. This paper addresses
Coordination and Agreement
 Coordination and Agreement Nicola Dragoni Embedded Systems Engineering DTU Informatics 1. Introduction 2. Distributed Mutual Exclusion 3. Elections 4. Multicast Communication 5. Consensus and related problems
Coordination and Agreement Nicola Dragoni Embedded Systems Engineering DTU Informatics 1. Introduction 2. Distributed Mutual Exclusion 3. Elections 4. Multicast Communication 5. Consensus and related problems
Brewer's Conjecture and the Feasibility of Consistent, Available, Partition-Tolerant Web Services
 PODC 2004 The PODC Steering Committee is pleased to announce that PODC 2004 will be held in St. John's, Newfoundland. This will be the thirteenth PODC to be held in Canada but the first to be held there
PODC 2004 The PODC Steering Committee is pleased to announce that PODC 2004 will be held in St. John's, Newfoundland. This will be the thirteenth PODC to be held in Canada but the first to be held there
Connection-Oriented Reliable FIFO Multicast Service
 A Client-Server Approach to Virtually Synchronous Group Multicast: Specications, Algorithms, and Proofs Idit Keidar Roger Khazan MIT Lab for Computer Science Email: fidish, rogerg@theory.lcs.mit.edu URL:
A Client-Server Approach to Virtually Synchronous Group Multicast: Specications, Algorithms, and Proofs Idit Keidar Roger Khazan MIT Lab for Computer Science Email: fidish, rogerg@theory.lcs.mit.edu URL:
Important Lessons. A Distributed Algorithm (2) Today's Lecture - Replication
 Important Lessons Lamport & vector clocks both give a logical timestamps Total ordering vs. causal ordering Other issues in coordinating node activities Exclusive access to resources/data Choosing a single
Important Lessons Lamport & vector clocks both give a logical timestamps Total ordering vs. causal ordering Other issues in coordinating node activities Exclusive access to resources/data Choosing a single
Replication and Consistency
 Replication and Consistency Today l Replication l Consistency models l Consistency protocols The value of replication For reliability and availability Avoid problems with disconnection, data corruption,
Replication and Consistency Today l Replication l Consistency models l Consistency protocols The value of replication For reliability and availability Avoid problems with disconnection, data corruption,
Linearizability CMPT 401. Sequential Consistency. Passive Replication
 Linearizability CMPT 401 Thursday, March 31, 2005 The execution of a replicated service (potentially with multiple requests interleaved over multiple servers) is said to be linearizable if: The interleaved
Linearizability CMPT 401 Thursday, March 31, 2005 The execution of a replicated service (potentially with multiple requests interleaved over multiple servers) is said to be linearizable if: The interleaved
Semi-Passive Replication in the Presence of Byzantine Faults
 Semi-Passive Replication in the Presence of Byzantine Faults HariGovind V. Ramasamy Adnan Agbaria William H. Sanders University of Illinois at Urbana-Champaign 1308 W. Main Street, Urbana IL 61801, USA
Semi-Passive Replication in the Presence of Byzantine Faults HariGovind V. Ramasamy Adnan Agbaria William H. Sanders University of Illinois at Urbana-Champaign 1308 W. Main Street, Urbana IL 61801, USA
Intuitive distributed algorithms. with F#
 Intuitive distributed algorithms with F# Natallia Dzenisenka Alena Hall @nata_dzen @lenadroid A tour of a variety of intuitivedistributed algorithms used in practical distributed systems. and how to prototype
Intuitive distributed algorithms with F# Natallia Dzenisenka Alena Hall @nata_dzen @lenadroid A tour of a variety of intuitivedistributed algorithms used in practical distributed systems. and how to prototype
Specifying and Proving Broadcast Properties with TLA
 Specifying and Proving Broadcast Properties with TLA William Hipschman Department of Computer Science The University of North Carolina at Chapel Hill Abstract Although group communication is vitally important
Specifying and Proving Broadcast Properties with TLA William Hipschman Department of Computer Science The University of North Carolina at Chapel Hill Abstract Although group communication is vitally important
Clock Synchronization. Synchronization. Clock Synchronization Algorithms. Physical Clock Synchronization. Tanenbaum Chapter 6 plus additional papers
 Clock Synchronization Synchronization Tanenbaum Chapter 6 plus additional papers Fig 6-1. In a distributed system, each machine has its own clock. When this is the case, an event that occurred after another
Clock Synchronization Synchronization Tanenbaum Chapter 6 plus additional papers Fig 6-1. In a distributed system, each machine has its own clock. When this is the case, an event that occurred after another
Wait-Free Regular Storage from Byzantine Components
 Wait-Free Regular Storage from Byzantine Components Ittai Abraham Gregory Chockler Idit Keidar Dahlia Malkhi July 26, 2006 Abstract We consider the problem of implementing a wait-free regular register
Wait-Free Regular Storage from Byzantine Components Ittai Abraham Gregory Chockler Idit Keidar Dahlia Malkhi July 26, 2006 Abstract We consider the problem of implementing a wait-free regular register
Coordination 1. To do. Mutual exclusion Election algorithms Next time: Global state. q q q
 Coordination 1 To do q q q Mutual exclusion Election algorithms Next time: Global state Coordination and agreement in US Congress 1798-2015 Process coordination How can processes coordinate their action?
Coordination 1 To do q q q Mutual exclusion Election algorithms Next time: Global state Coordination and agreement in US Congress 1798-2015 Process coordination How can processes coordinate their action?
Using Optimistic Atomic Broadcast in Transaction Processing Systems
 Using Optimistic Atomic Broadcast in Transaction Processing Systems Bettina Kemme Fernando Pedone Gustavo Alonso André Schiper Matthias Wiesmann School of Computer Science McGill University Montreal, Canada,
Using Optimistic Atomic Broadcast in Transaction Processing Systems Bettina Kemme Fernando Pedone Gustavo Alonso André Schiper Matthias Wiesmann School of Computer Science McGill University Montreal, Canada,
On the interconnection of message passing systems
 Information Processing Letters 105 (2008) 249 254 www.elsevier.com/locate/ipl On the interconnection of message passing systems A. Álvarez a,s.arévalo b, V. Cholvi c,, A. Fernández b,e.jiménez a a Polytechnic
Information Processing Letters 105 (2008) 249 254 www.elsevier.com/locate/ipl On the interconnection of message passing systems A. Álvarez a,s.arévalo b, V. Cholvi c,, A. Fernández b,e.jiménez a a Polytechnic
CS6450: Distributed Systems Lecture 11. Ryan Stutsman
 Strong Consistency CS6450: Distributed Systems Lecture 11 Ryan Stutsman Material taken/derived from Princeton COS-418 materials created by Michael Freedman and Kyle Jamieson at Princeton University. Licensed
Strong Consistency CS6450: Distributed Systems Lecture 11 Ryan Stutsman Material taken/derived from Princeton COS-418 materials created by Michael Freedman and Kyle Jamieson at Princeton University. Licensed
SIMULATING I/O AUTOMATA. TRACE PROPERTIES
 SIMULATING I/O AUTOMATA. TRACE PROPERTIES Cristian Gavrilă and Ioan Jurca fcristig,ionelg@cs.utt.ro University Politehnica of Timişoara Computer Science Department Abstract I/O automaton is a mathematical
SIMULATING I/O AUTOMATA. TRACE PROPERTIES Cristian Gavrilă and Ioan Jurca fcristig,ionelg@cs.utt.ro University Politehnica of Timişoara Computer Science Department Abstract I/O automaton is a mathematical
Active leave behavior of members in a fault-tolerant group
 260 Science in China Ser. F Information Sciences 2004 Vol.47 No.2 260 272 Active leave behavior of members in a fault-tolerant group WANG Yun Department of Computer Science and Engineering, Southeast University,
260 Science in China Ser. F Information Sciences 2004 Vol.47 No.2 260 272 Active leave behavior of members in a fault-tolerant group WANG Yun Department of Computer Science and Engineering, Southeast University,
Basic vs. Reliable Multicast
 Basic vs. Reliable Multicast Basic multicast does not consider process crashes. Reliable multicast does. So far, we considered the basic versions of ordered multicasts. What about the reliable versions?
Basic vs. Reliable Multicast Basic multicast does not consider process crashes. Reliable multicast does. So far, we considered the basic versions of ordered multicasts. What about the reliable versions?
SCALABLE CONSISTENCY AND TRANSACTION MODELS
 Data Management in the Cloud SCALABLE CONSISTENCY AND TRANSACTION MODELS 69 Brewer s Conjecture Three properties that are desirable and expected from realworld shared-data systems C: data consistency A:
Data Management in the Cloud SCALABLE CONSISTENCY AND TRANSACTION MODELS 69 Brewer s Conjecture Three properties that are desirable and expected from realworld shared-data systems C: data consistency A:
Research Report. (Im)Possibilities of Predicate Detection in Crash-Affected Systems. RZ 3361 (# 93407) 20/08/2001 Computer Science 27 pages
 RZ 3361 (# 93407) 20/08/2001 Computer Science 27 pages Research Report (Im)Possibilities of Predicate Detection in Crash-Affected Systems Felix C. Gärtner and Stefan Pleisch Department of Computer Science
RZ 3361 (# 93407) 20/08/2001 Computer Science 27 pages Research Report (Im)Possibilities of Predicate Detection in Crash-Affected Systems Felix C. Gärtner and Stefan Pleisch Department of Computer Science
殷亚凤. Synchronization. Distributed Systems [6]
![殷亚凤. Synchronization. Distributed Systems [6] 殷亚凤. Synchronization. Distributed Systems [6]](/thumbs/88/117193765.jpg) Synchronization Distributed Systems [6] 殷亚凤 Email: yafeng@nju.edu.cn Homepage: http://cs.nju.edu.cn/yafeng/ Room 301, Building of Computer Science and Technology Review Protocols Remote Procedure Call
Synchronization Distributed Systems [6] 殷亚凤 Email: yafeng@nju.edu.cn Homepage: http://cs.nju.edu.cn/yafeng/ Room 301, Building of Computer Science and Technology Review Protocols Remote Procedure Call
Distributed Algorithms Reliable Broadcast
 Distributed Algorithms Reliable Broadcast Alberto Montresor University of Trento, Italy 2016/04/26 This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. Contents
Distributed Algorithms Reliable Broadcast Alberto Montresor University of Trento, Italy 2016/04/26 This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. Contents
Coordination 2. Today. How can processes agree on an action or a value? l Group communication l Basic, reliable and l ordered multicast
 Coordination 2 Today l Group communication l Basic, reliable and l ordered multicast How can processes agree on an action or a value? Modes of communication Unicast 1ç è 1 Point to point Anycast 1è
Coordination 2 Today l Group communication l Basic, reliable and l ordered multicast How can processes agree on an action or a value? Modes of communication Unicast 1ç è 1 Point to point Anycast 1è
Failure Tolerance. Distributed Systems Santa Clara University
 Failure Tolerance Distributed Systems Santa Clara University Distributed Checkpointing Distributed Checkpointing Capture the global state of a distributed system Chandy and Lamport: Distributed snapshot
Failure Tolerance Distributed Systems Santa Clara University Distributed Checkpointing Distributed Checkpointing Capture the global state of a distributed system Chandy and Lamport: Distributed snapshot
Consensus a classic problem. Consensus, impossibility results and Paxos. Distributed Consensus. Asynchronous networks.
 Consensus, impossibility results and Paxos Ken Birman Consensus a classic problem Consensus abstraction underlies many distributed systems and protocols N processes They start execution with inputs {0,1}
Consensus, impossibility results and Paxos Ken Birman Consensus a classic problem Consensus abstraction underlies many distributed systems and protocols N processes They start execution with inputs {0,1}
Distributed Consensus: Making Impossible Possible
 Distributed Consensus: Making Impossible Possible Heidi Howard PhD Student @ University of Cambridge heidi.howard@cl.cam.ac.uk @heidiann360 hh360.user.srcf.net Sometimes inconsistency is not an option
Distributed Consensus: Making Impossible Possible Heidi Howard PhD Student @ University of Cambridge heidi.howard@cl.cam.ac.uk @heidiann360 hh360.user.srcf.net Sometimes inconsistency is not an option
Last time. Distributed systems Lecture 6: Elections, distributed transactions, and replication. DrRobert N. M. Watson
 Distributed systems Lecture 6: Elections, distributed transactions, and replication DrRobert N. M. Watson 1 Last time Saw how we can build ordered multicast Messages between processes in a group Need to
Distributed systems Lecture 6: Elections, distributed transactions, and replication DrRobert N. M. Watson 1 Last time Saw how we can build ordered multicast Messages between processes in a group Need to
Strong Consistency & CAP Theorem
 Strong Consistency & CAP Theorem CS 240: Computing Systems and Concurrency Lecture 15 Marco Canini Credits: Michael Freedman and Kyle Jamieson developed much of the original material. Consistency models
Strong Consistency & CAP Theorem CS 240: Computing Systems and Concurrency Lecture 15 Marco Canini Credits: Michael Freedman and Kyle Jamieson developed much of the original material. Consistency models
Byzantine Consensus in Directed Graphs
 Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
Generating Fast Indulgent Algorithms
 Generating Fast Indulgent Algorithms Dan Alistarh 1, Seth Gilbert 2, Rachid Guerraoui 1, and Corentin Travers 3 1 EPFL, Switzerland 2 National University of Singapore 3 Université de Bordeaux 1, France
Generating Fast Indulgent Algorithms Dan Alistarh 1, Seth Gilbert 2, Rachid Guerraoui 1, and Corentin Travers 3 1 EPFL, Switzerland 2 National University of Singapore 3 Université de Bordeaux 1, France
CS6450: Distributed Systems Lecture 15. Ryan Stutsman
 Strong Consistency CS6450: Distributed Systems Lecture 15 Ryan Stutsman Material taken/derived from Princeton COS-418 materials created by Michael Freedman and Kyle Jamieson at Princeton University. Licensed
Strong Consistency CS6450: Distributed Systems Lecture 15 Ryan Stutsman Material taken/derived from Princeton COS-418 materials created by Michael Freedman and Kyle Jamieson at Princeton University. Licensed
Implementing Shared Registers in Asynchronous Message-Passing Systems, 1995; Attiya, Bar-Noy, Dolev
 Implementing Shared Registers in Asynchronous Message-Passing Systems, 1995; Attiya, Bar-Noy, Dolev Eric Ruppert, York University, www.cse.yorku.ca/ ruppert INDEX TERMS: distributed computing, shared memory,
Implementing Shared Registers in Asynchronous Message-Passing Systems, 1995; Attiya, Bar-Noy, Dolev Eric Ruppert, York University, www.cse.yorku.ca/ ruppert INDEX TERMS: distributed computing, shared memory,
Failures, Elections, and Raft
 Failures, Elections, and Raft CS 8 XI Copyright 06 Thomas W. Doeppner, Rodrigo Fonseca. All rights reserved. Distributed Banking SFO add interest based on current balance PVD deposit $000 CS 8 XI Copyright
Failures, Elections, and Raft CS 8 XI Copyright 06 Thomas W. Doeppner, Rodrigo Fonseca. All rights reserved. Distributed Banking SFO add interest based on current balance PVD deposit $000 CS 8 XI Copyright
BYZANTINE AGREEMENT CH / $ IEEE. by H. R. Strong and D. Dolev. IBM Research Laboratory, K55/281 San Jose, CA 95193
 BYZANTINE AGREEMENT by H. R. Strong and D. Dolev IBM Research Laboratory, K55/281 San Jose, CA 95193 ABSTRACT Byzantine Agreement is a paradigm for problems of reliable consistency and synchronization
BYZANTINE AGREEMENT by H. R. Strong and D. Dolev IBM Research Laboratory, K55/281 San Jose, CA 95193 ABSTRACT Byzantine Agreement is a paradigm for problems of reliable consistency and synchronization
Multi-writer Regular Registers in Dynamic Distributed Systems with Byzantine Failures
 Multi-writer Regular Registers in Dynamic Distributed Systems with Byzantine Failures Silvia Bonomi, Amir Soltani Nezhad Università degli Studi di Roma La Sapienza, Via Ariosto 25, 00185 Roma, Italy bonomi@dis.uniroma1.it
Multi-writer Regular Registers in Dynamic Distributed Systems with Byzantine Failures Silvia Bonomi, Amir Soltani Nezhad Università degli Studi di Roma La Sapienza, Via Ariosto 25, 00185 Roma, Italy bonomi@dis.uniroma1.it
Consensus, impossibility results and Paxos. Ken Birman
 Consensus, impossibility results and Paxos Ken Birman Consensus a classic problem Consensus abstraction underlies many distributed systems and protocols N processes They start execution with inputs {0,1}
Consensus, impossibility results and Paxos Ken Birman Consensus a classic problem Consensus abstraction underlies many distributed systems and protocols N processes They start execution with inputs {0,1}
6.852: Distributed Algorithms Fall, Class 21
 6.852: Distributed Algorithms Fall, 2009 Class 21 Today s plan Wait-free synchronization. The wait-free consensus hierarchy Universality of consensus Reading: [Herlihy, Wait-free synchronization] (Another
6.852: Distributed Algorithms Fall, 2009 Class 21 Today s plan Wait-free synchronization. The wait-free consensus hierarchy Universality of consensus Reading: [Herlihy, Wait-free synchronization] (Another
2017 Paul Krzyzanowski 1
 Question 1 What problem can arise with a system that exhibits fail-restart behavior? Distributed Systems 06. Exam 1 Review Stale state: the system has an outdated view of the world when it starts up. Not:
Question 1 What problem can arise with a system that exhibits fail-restart behavior? Distributed Systems 06. Exam 1 Review Stale state: the system has an outdated view of the world when it starts up. Not:
CS /15/16. Paul Krzyzanowski 1. Question 1. Distributed Systems 2016 Exam 2 Review. Question 3. Question 2. Question 5.
 Question 1 What makes a message unstable? How does an unstable message become stable? Distributed Systems 2016 Exam 2 Review Paul Krzyzanowski Rutgers University Fall 2016 In virtual sychrony, a message
Question 1 What makes a message unstable? How does an unstable message become stable? Distributed Systems 2016 Exam 2 Review Paul Krzyzanowski Rutgers University Fall 2016 In virtual sychrony, a message
EECS 498 Introduction to Distributed Systems
 EECS 498 Introduction to Distributed Systems Fall 2017 Harsha V. Madhyastha Replicated State Machines Logical clocks Primary/ Backup Paxos? 0 1 (N-1)/2 No. of tolerable failures October 11, 2017 EECS 498
EECS 498 Introduction to Distributed Systems Fall 2017 Harsha V. Madhyastha Replicated State Machines Logical clocks Primary/ Backup Paxos? 0 1 (N-1)/2 No. of tolerable failures October 11, 2017 EECS 498
Time Synchronization and Logical Clocks
 Time Synchronization and Logical Clocks CS 240: Computing Systems and Concurrency Lecture 5 Mootaz Elnozahy Today 1. The need for time synchronization 2. Wall clock time synchronization 3. Logical Time
Time Synchronization and Logical Clocks CS 240: Computing Systems and Concurrency Lecture 5 Mootaz Elnozahy Today 1. The need for time synchronization 2. Wall clock time synchronization 3. Logical Time
DISTRIBUTED COMPUTER SYSTEMS
 DISTRIBUTED COMPUTER SYSTEMS CONSISTENCY AND REPLICATION CONSISTENCY MODELS Dr. Jack Lange Computer Science Department University of Pittsburgh Fall 2015 Consistency Models Background Replication Motivation
DISTRIBUTED COMPUTER SYSTEMS CONSISTENCY AND REPLICATION CONSISTENCY MODELS Dr. Jack Lange Computer Science Department University of Pittsburgh Fall 2015 Consistency Models Background Replication Motivation
Availability versus consistency. Eventual Consistency: Bayou. Eventual consistency. Bayou: A Weakly Connected Replicated Storage System
 Eventual Consistency: Bayou Availability versus consistency Totally-Ordered Multicast kept replicas consistent but had single points of failure Not available under failures COS 418: Distributed Systems
Eventual Consistency: Bayou Availability versus consistency Totally-Ordered Multicast kept replicas consistent but had single points of failure Not available under failures COS 418: Distributed Systems
A Fast Group Communication Mechanism for Large Scale Distributed Objects 1
 A Fast Group Communication Mechanism for Large Scale Distributed Objects 1 Hojjat Jafarpour and Nasser Yazdani Department of Electrical and Computer Engineering University of Tehran Tehran, Iran hjafarpour@ece.ut.ac.ir,
A Fast Group Communication Mechanism for Large Scale Distributed Objects 1 Hojjat Jafarpour and Nasser Yazdani Department of Electrical and Computer Engineering University of Tehran Tehran, Iran hjafarpour@ece.ut.ac.ir,
Implementation of Clocks and Sensors
 Implementation of Clocks and Sensors Term Paper EE 382N Distributed Systems Dr. Garg November 30, 2000 Submitted by: Yousuf Ahmed Chandresh Jain Onur Mutlu Global Predicate Detection in Distributed Systems
Implementation of Clocks and Sensors Term Paper EE 382N Distributed Systems Dr. Garg November 30, 2000 Submitted by: Yousuf Ahmed Chandresh Jain Onur Mutlu Global Predicate Detection in Distributed Systems
Replication. Consistency models. Replica placement Distribution protocols
 Replication Motivation Consistency models Data/Client-centric consistency models Replica placement Distribution protocols Invalidate versus updates Push versus Pull Cooperation between replicas Client-centric
Replication Motivation Consistency models Data/Client-centric consistency models Replica placement Distribution protocols Invalidate versus updates Push versus Pull Cooperation between replicas Client-centric
Distributed Systems. 05. Clock Synchronization. Paul Krzyzanowski. Rutgers University. Fall 2017
 Distributed Systems 05. Clock Synchronization Paul Krzyzanowski Rutgers University Fall 2017 2014-2017 Paul Krzyzanowski 1 Synchronization Synchronization covers interactions among distributed processes
Distributed Systems 05. Clock Synchronization Paul Krzyzanowski Rutgers University Fall 2017 2014-2017 Paul Krzyzanowski 1 Synchronization Synchronization covers interactions among distributed processes
Recall: Primary-Backup. State machine replication. Extend PB for high availability. Consensus 2. Mechanism: Replicate and separate servers
 Replicated s, RAFT COS 8: Distributed Systems Lecture 8 Recall: Primary-Backup Mechanism: Replicate and separate servers Goal #: Provide a highly reliable service Goal #: Servers should behave just like
Replicated s, RAFT COS 8: Distributed Systems Lecture 8 Recall: Primary-Backup Mechanism: Replicate and separate servers Goal #: Provide a highly reliable service Goal #: Servers should behave just like
From Total Order to Database Replication
 From Total Order to Database Replication Yair Amir and Ciprian Tutu Department of Computer Science Johns Hopkins University Baltimore, MD 21218, USA {yairamir, ciprian}@cnds.jhu.edu Technical Report CNDS-2001-6
From Total Order to Database Replication Yair Amir and Ciprian Tutu Department of Computer Science Johns Hopkins University Baltimore, MD 21218, USA {yairamir, ciprian}@cnds.jhu.edu Technical Report CNDS-2001-6
Selecting a Primary Partition in Partitionable Asynchronous Distributed Systems
 Selecting a Primary Partition in Partitionable Asynchronous Distributed Systems Alberto Bartoli Dip. Ingegneria dell Informazione University of Pisa, Italy E-mail: alberto@iet.unipi.it Özalp Babaoglu Dept.
Selecting a Primary Partition in Partitionable Asynchronous Distributed Systems Alberto Bartoli Dip. Ingegneria dell Informazione University of Pisa, Italy E-mail: alberto@iet.unipi.it Özalp Babaoglu Dept.
Distributed Algorithms 6.046J, Spring, 2015 Part 2. Nancy Lynch
 Distributed Algorithms 6.046J, Spring, 2015 Part 2 Nancy Lynch 1 This Week Synchronous distributed algorithms: Leader Election Maximal Independent Set Breadth-First Spanning Trees Shortest Paths Trees
Distributed Algorithms 6.046J, Spring, 2015 Part 2 Nancy Lynch 1 This Week Synchronous distributed algorithms: Leader Election Maximal Independent Set Breadth-First Spanning Trees Shortest Paths Trees
Distributed Systems. Pre-Exam 1 Review. Paul Krzyzanowski. Rutgers University. Fall 2015
 Distributed Systems Pre-Exam 1 Review Paul Krzyzanowski Rutgers University Fall 2015 October 2, 2015 CS 417 - Paul Krzyzanowski 1 Selected Questions From Past Exams October 2, 2015 CS 417 - Paul Krzyzanowski
Distributed Systems Pre-Exam 1 Review Paul Krzyzanowski Rutgers University Fall 2015 October 2, 2015 CS 417 - Paul Krzyzanowski 1 Selected Questions From Past Exams October 2, 2015 CS 417 - Paul Krzyzanowski
Introduction to Distributed Systems Seif Haridi
 Introduction to Distributed Systems Seif Haridi haridi@kth.se What is a distributed system? A set of nodes, connected by a network, which appear to its users as a single coherent system p1 p2. pn send
Introduction to Distributed Systems Seif Haridi haridi@kth.se What is a distributed system? A set of nodes, connected by a network, which appear to its users as a single coherent system p1 p2. pn send
Replicated State Machines for Collision-Prone Wireless Networks
 Replicated State Machines for Collision-Prone Wireless Networks Gregory Chockler Seth Gilbert MIT Computer Science and Artificial Intelligence Lab Cambridge, MA 02139 {grishac,sethg}@theory.csail.mit.edu
Replicated State Machines for Collision-Prone Wireless Networks Gregory Chockler Seth Gilbert MIT Computer Science and Artificial Intelligence Lab Cambridge, MA 02139 {grishac,sethg}@theory.csail.mit.edu
Two phase commit protocol. Two phase commit protocol. Recall: Linearizability (Strong Consistency) Consensus
 Recall: Linearizability (Strong Consistency) Consensus COS 518: Advanced Computer Systems Lecture 4 Provide behavior of a single copy of object: Read should urn the most recent write Subsequent reads should
Recall: Linearizability (Strong Consistency) Consensus COS 518: Advanced Computer Systems Lecture 4 Provide behavior of a single copy of object: Read should urn the most recent write Subsequent reads should
Practical Byzantine Fault Tolerance
 Practical Byzantine Fault Tolerance Robert Grimm New York University (Partially based on notes by Eric Brewer and David Mazières) The Three Questions What is the problem? What is new or different? What
Practical Byzantine Fault Tolerance Robert Grimm New York University (Partially based on notes by Eric Brewer and David Mazières) The Three Questions What is the problem? What is new or different? What
Deadlock Managing Process in P2P System
 Deadlock Managing Process in P2P System Akshaya A.Bhosale Department of Information Technology Gharda Institute Of Technology,Lavel, Chiplun,Maharashtra, India Ashwini B.Shinde Department of Information
Deadlock Managing Process in P2P System Akshaya A.Bhosale Department of Information Technology Gharda Institute Of Technology,Lavel, Chiplun,Maharashtra, India Ashwini B.Shinde Department of Information
1. INTRODUCTION Totally Ordered Broadcast is a powerful service for the design of fault tolerant applications, e.g., consistent cache, distributed sha
 Chapter 3 TOTALLY ORDERED BROADCAST IN THE FACE OF NETWORK PARTITIONS Exploiting Group Communication for Replication in Partitionable Networks 1 Idit Keidar Laboratory for Computer Science Massachusetts
Chapter 3 TOTALLY ORDERED BROADCAST IN THE FACE OF NETWORK PARTITIONS Exploiting Group Communication for Replication in Partitionable Networks 1 Idit Keidar Laboratory for Computer Science Massachusetts
Time Synchronization and Logical Clocks
 Time Synchronization and Logical Clocks CS 240: Computing Systems and Concurrency Lecture 5 Marco Canini Credits: Michael Freedman and Kyle Jamieson developed much of the original material. Today 1. The
Time Synchronization and Logical Clocks CS 240: Computing Systems and Concurrency Lecture 5 Marco Canini Credits: Michael Freedman and Kyle Jamieson developed much of the original material. Today 1. The
Paxos and Raft (Lecture 21, cs262a) Ion Stoica, UC Berkeley November 7, 2016
 Paxos and Raft (Lecture 21, cs262a) Ion Stoica, UC Berkeley November 7, 2016 Bezos mandate for service-oriented-architecture (~2002) 1. All teams will henceforth expose their data and functionality through
Paxos and Raft (Lecture 21, cs262a) Ion Stoica, UC Berkeley November 7, 2016 Bezos mandate for service-oriented-architecture (~2002) 1. All teams will henceforth expose their data and functionality through
Distributed Systems Exam 1 Review. Paul Krzyzanowski. Rutgers University. Fall 2016
 Distributed Systems 2016 Exam 1 Review Paul Krzyzanowski Rutgers University Fall 2016 Question 1 Why does it not make sense to use TCP (Transmission Control Protocol) for the Network Time Protocol (NTP)?
Distributed Systems 2016 Exam 1 Review Paul Krzyzanowski Rutgers University Fall 2016 Question 1 Why does it not make sense to use TCP (Transmission Control Protocol) for the Network Time Protocol (NTP)?
Distributed Systems 8L for Part IB
 Distributed Systems 8L for Part IB Handout 3 Dr. Steven Hand 1 Distributed Mutual Exclusion In first part of course, saw need to coordinate concurrent processes / threads In particular considered how to
Distributed Systems 8L for Part IB Handout 3 Dr. Steven Hand 1 Distributed Mutual Exclusion In first part of course, saw need to coordinate concurrent processes / threads In particular considered how to
TAPIR. By Irene Zhang, Naveen Sharma, Adriana Szekeres, Arvind Krishnamurthy, and Dan Ports Presented by Todd Charlton
 TAPIR By Irene Zhang, Naveen Sharma, Adriana Szekeres, Arvind Krishnamurthy, and Dan Ports Presented by Todd Charlton Outline Problem Space Inconsistent Replication TAPIR Evaluation Conclusion Problem
TAPIR By Irene Zhang, Naveen Sharma, Adriana Szekeres, Arvind Krishnamurthy, and Dan Ports Presented by Todd Charlton Outline Problem Space Inconsistent Replication TAPIR Evaluation Conclusion Problem
Event Ordering. Greg Bilodeau CS 5204 November 3, 2009
 Greg Bilodeau CS 5204 November 3, 2009 Fault Tolerance How do we prepare for rollback and recovery in a distributed system? How do we ensure the proper processing order of communications between distributed
Greg Bilodeau CS 5204 November 3, 2009 Fault Tolerance How do we prepare for rollback and recovery in a distributed system? How do we ensure the proper processing order of communications between distributed
Time and distributed systems. Just use time stamps? Correct consistency model? Replication and Consistency
 Correct consistency model? Replication and Consistency B COS 58: dvanced Computer Systems Lecture 3 Let s say and B send an op. ll readers see B? ll readers see B? Michael Freedman Some see B and others
Correct consistency model? Replication and Consistency B COS 58: dvanced Computer Systems Lecture 3 Let s say and B send an op. ll readers see B? ll readers see B? Michael Freedman Some see B and others
Programming with Object Groups in PHOENIX
 Programming with Object Groups in PHOENIX Pascal Felber Rachid Guerraoui Département d Informatique Ecole Polytechnique Fédérale de Lausanne CH-1015 Lausanne, Switzerland felber@lse.epfl.ch rachid@lse.epfl.ch
Programming with Object Groups in PHOENIX Pascal Felber Rachid Guerraoui Département d Informatique Ecole Polytechnique Fédérale de Lausanne CH-1015 Lausanne, Switzerland felber@lse.epfl.ch rachid@lse.epfl.ch
Accepted Manuscript. On the Interconnection of Message Passing Systems. A. Álvarez, S. Arévalo, V. Cholvi, A. Fernández, E.
 Accepted Manuscript On the Interconnection of Message Passing Systems A. Álvarez, S. Arévalo, V. Cholvi, A. Fernández, E. Jiménez PII: S0020-0190(07)00270-0 DOI: 10.1016/j.ipl.2007.09.006 Reference: IPL
Accepted Manuscript On the Interconnection of Message Passing Systems A. Álvarez, S. Arévalo, V. Cholvi, A. Fernández, E. Jiménez PII: S0020-0190(07)00270-0 DOI: 10.1016/j.ipl.2007.09.006 Reference: IPL
Practical Byzantine Fault Tolerance Using Fewer than 3f+1 Active Replicas
 Proceedings of the 17th International Conference on Parallel and Distributed Computing Systems San Francisco, California, pp 241-247, September 24 Practical Byzantine Fault Tolerance Using Fewer than 3f+1
Proceedings of the 17th International Conference on Parallel and Distributed Computing Systems San Francisco, California, pp 241-247, September 24 Practical Byzantine Fault Tolerance Using Fewer than 3f+1
Time. COS 418: Distributed Systems Lecture 3. Wyatt Lloyd
 Time COS 418: Distributed Systems Lecture 3 Wyatt Lloyd Today 1. The need for time synchronization 2. Wall clock time synchronization 3. Logical Time: Lamport Clocks 2 A distributed edit-compile workflow
Time COS 418: Distributed Systems Lecture 3 Wyatt Lloyd Today 1. The need for time synchronization 2. Wall clock time synchronization 3. Logical Time: Lamport Clocks 2 A distributed edit-compile workflow
Concurrent Objects and Linearizability
 Chapter 3 Concurrent Objects and Linearizability 3.1 Specifying Objects An object in languages such as Java and C++ is a container for data. Each object provides a set of methods that are the only way
Chapter 3 Concurrent Objects and Linearizability 3.1 Specifying Objects An object in languages such as Java and C++ is a container for data. Each object provides a set of methods that are the only way
CSE 5306 Distributed Systems
 CSE 5306 Distributed Systems Fault Tolerance Jia Rao http://ranger.uta.edu/~jrao/ 1 Failure in Distributed Systems Partial failure Happens when one component of a distributed system fails Often leaves
CSE 5306 Distributed Systems Fault Tolerance Jia Rao http://ranger.uta.edu/~jrao/ 1 Failure in Distributed Systems Partial failure Happens when one component of a distributed system fails Often leaves
Coordination and Agreement
 Coordination and Agreement 12.1 Introduction 12.2 Distributed Mutual Exclusion 12.4 Multicast Communication 12.3 Elections 12.5 Consensus and Related Problems AIM: Coordination and/or Agreement Collection
Coordination and Agreement 12.1 Introduction 12.2 Distributed Mutual Exclusion 12.4 Multicast Communication 12.3 Elections 12.5 Consensus and Related Problems AIM: Coordination and/or Agreement Collection
Erasure Coding in Object Stores: Challenges and Opportunities
 Erasure Coding in Object Stores: Challenges and Opportunities Lewis Tseng Boston College July 2018, PODC Acknowledgements Nancy Lynch Muriel Medard Kishori Konwar Prakash Narayana Moorthy Viveck R. Cadambe
Erasure Coding in Object Stores: Challenges and Opportunities Lewis Tseng Boston College July 2018, PODC Acknowledgements Nancy Lynch Muriel Medard Kishori Konwar Prakash Narayana Moorthy Viveck R. Cadambe
Reliable Distributed System Approaches
 Reliable Distributed System Approaches Manuel Graber Seminar of Distributed Computing WS 03/04 The Papers The Process Group Approach to Reliable Distributed Computing K. Birman; Communications of the ACM,
Reliable Distributed System Approaches Manuel Graber Seminar of Distributed Computing WS 03/04 The Papers The Process Group Approach to Reliable Distributed Computing K. Birman; Communications of the ACM,
Synchronization. Chapter 5
 Synchronization Chapter 5 Clock Synchronization In a centralized system time is unambiguous. (each computer has its own clock) In a distributed system achieving agreement on time is not trivial. (it is
Synchronization Chapter 5 Clock Synchronization In a centralized system time is unambiguous. (each computer has its own clock) In a distributed system achieving agreement on time is not trivial. (it is
Trek: Testable Replicated Key-Value Store
 Trek: Testable Replicated Key-Value Store Yen-Ting Liu, Wen-Chien Chen Stanford University Abstract This paper describes the implementation of Trek, a testable, replicated key-value store with ZooKeeper-like
Trek: Testable Replicated Key-Value Store Yen-Ting Liu, Wen-Chien Chen Stanford University Abstract This paper describes the implementation of Trek, a testable, replicated key-value store with ZooKeeper-like
Distributed Systems. Day 9: Replication [Part 1]
![Distributed Systems. Day 9: Replication [Part 1] Distributed Systems. Day 9: Replication [Part 1]](/thumbs/94/121965696.jpg) Distributed Systems Day 9: Replication [Part 1] Hash table k 0 v 0 k 1 v 1 k 2 v 2 k 3 v 3 ll Facebook Data Does your client know about all of F s servers? Security issues? Performance issues? How do clients
Distributed Systems Day 9: Replication [Part 1] Hash table k 0 v 0 k 1 v 1 k 2 v 2 k 3 v 3 ll Facebook Data Does your client know about all of F s servers? Security issues? Performance issues? How do clients
Tradeoffs in Byzantine-Fault-Tolerant State-Machine-Replication Protocol Design
 Tradeoffs in Byzantine-Fault-Tolerant State-Machine-Replication Protocol Design Michael G. Merideth March 2008 CMU-ISR-08-110 School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213
Tradeoffs in Byzantine-Fault-Tolerant State-Machine-Replication Protocol Design Michael G. Merideth March 2008 CMU-ISR-08-110 School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213
Distributed Systems. 09. State Machine Replication & Virtual Synchrony. Paul Krzyzanowski. Rutgers University. Fall Paul Krzyzanowski
 Distributed Systems 09. State Machine Replication & Virtual Synchrony Paul Krzyzanowski Rutgers University Fall 2016 1 State machine replication 2 State machine replication We want high scalability and
Distributed Systems 09. State Machine Replication & Virtual Synchrony Paul Krzyzanowski Rutgers University Fall 2016 1 State machine replication 2 State machine replication We want high scalability and
GFS Overview. Design goals/priorities Design for big-data workloads Huge files, mostly appends, concurrency, huge bandwidth Design for failures
 GFS Overview Design goals/priorities Design for big-data workloads Huge files, mostly appends, concurrency, huge bandwidth Design for failures Interface: non-posix New op: record appends (atomicity matters,
GFS Overview Design goals/priorities Design for big-data workloads Huge files, mostly appends, concurrency, huge bandwidth Design for failures Interface: non-posix New op: record appends (atomicity matters,
To do. Consensus and related problems. q Failure. q Raft
 Consensus and related problems To do q Failure q Consensus and related problems q Raft Consensus We have seen protocols tailored for individual types of consensus/agreements Which process can enter the
Consensus and related problems To do q Failure q Consensus and related problems q Raft Consensus We have seen protocols tailored for individual types of consensus/agreements Which process can enter the
CSE 5306 Distributed Systems. Fault Tolerance
 CSE 5306 Distributed Systems Fault Tolerance 1 Failure in Distributed Systems Partial failure happens when one component of a distributed system fails often leaves other components unaffected A failure
CSE 5306 Distributed Systems Fault Tolerance 1 Failure in Distributed Systems Partial failure happens when one component of a distributed system fails often leaves other components unaffected A failure
Distributed Systems (5DV147)
 Distributed Systems (5DV147) Replication and consistency Fall 2013 1 Replication 2 What is replication? Introduction Make different copies of data ensuring that all copies are identical Immutable data
Distributed Systems (5DV147) Replication and consistency Fall 2013 1 Replication 2 What is replication? Introduction Make different copies of data ensuring that all copies are identical Immutable data
Today: Fault Tolerance
 Today: Fault Tolerance Agreement in presence of faults Two army problem Byzantine generals problem Reliable communication Distributed commit Two phase commit Three phase commit Paxos Failure recovery Checkpointing
Today: Fault Tolerance Agreement in presence of faults Two army problem Byzantine generals problem Reliable communication Distributed commit Two phase commit Three phase commit Paxos Failure recovery Checkpointing
Reconfigurable Distributed Storage for Dynamic Networks
 Reconfigurable Distributed Storage for Dynamic Networks Gregory Chockler 1,2, Seth Gilbert 1, Vincent Gramoli 3,4, Peter M Musial 3, and Alexander A Shvartsman 1,3 1 CSAIL, Massachusetts Institute of Technology,
Reconfigurable Distributed Storage for Dynamic Networks Gregory Chockler 1,2, Seth Gilbert 1, Vincent Gramoli 3,4, Peter M Musial 3, and Alexander A Shvartsman 1,3 1 CSAIL, Massachusetts Institute of Technology,
Distributed Systems. Characteristics of Distributed Systems. Lecture Notes 1 Basic Concepts. Operating Systems. Anand Tripathi
 1 Lecture Notes 1 Basic Concepts Anand Tripathi CSci 8980 Operating Systems Anand Tripathi CSci 8980 1 Distributed Systems A set of computers (hosts or nodes) connected through a communication network.
1 Lecture Notes 1 Basic Concepts Anand Tripathi CSci 8980 Operating Systems Anand Tripathi CSci 8980 1 Distributed Systems A set of computers (hosts or nodes) connected through a communication network.
Distributed Systems. Characteristics of Distributed Systems. Characteristics of Distributed Systems. Goals in Distributed System Designs
 1 Anand Tripathi CSci 8980 Operating Systems Lecture Notes 1 Basic Concepts Distributed Systems A set of computers (hosts or nodes) connected through a communication network. Nodes may have different speeds
1 Anand Tripathi CSci 8980 Operating Systems Lecture Notes 1 Basic Concepts Distributed Systems A set of computers (hosts or nodes) connected through a communication network. Nodes may have different speeds
Consensus on Transaction Commit
 Consensus on Transaction Commit Jim Gray and Leslie Lamport Microsoft Research 1 January 2004 revised 19 April 2004, 8 September 2005, 5 July 2017 MSR-TR-2003-96 This paper appeared in ACM Transactions
Consensus on Transaction Commit Jim Gray and Leslie Lamport Microsoft Research 1 January 2004 revised 19 April 2004, 8 September 2005, 5 July 2017 MSR-TR-2003-96 This paper appeared in ACM Transactions
Two-Phase Atomic Commitment Protocol in Asynchronous Distributed Systems with Crash Failure
 Two-Phase Atomic Commitment Protocol in Asynchronous Distributed Systems with Crash Failure Yong-Hwan Cho, Sung-Hoon Park and Seon-Hyong Lee School of Electrical and Computer Engineering, Chungbuk National
Two-Phase Atomic Commitment Protocol in Asynchronous Distributed Systems with Crash Failure Yong-Hwan Cho, Sung-Hoon Park and Seon-Hyong Lee School of Electrical and Computer Engineering, Chungbuk National
