Anti-entropy works as follows: periodically, a server P randomly chooses a server Q and then the two exchange databases. Three modes of anti-entropy a
|
|
|
- Emma Lucas
- 5 years ago
- Views:
Transcription
1
2
3
4
5
6
7 Anti-entropy works as follows: periodically, a server P randomly chooses a server Q and then the two exchange databases. Three modes of anti-entropy are possible. In push mode, P pushes its database to Q, which adds to its database everything in P that it doesn t have. In the pull mode, the reverse is done. Push-pull mode works in both directions. This discussion comes from Epidemic Algorithms for Replicated Database Maintenance, by A. Demers, D. Greene, C. Hauser, W. Irish, J. Larson, S. Shenker, H. Sturgis, D. Swinehart, and D. Terry, Proceedings of the ACM SIGACT-SIGOPS 6 th Annual Symposium on Principles of Distributed Computing, August, 1987.
8
9 We look at the fundamentals of epidemic theory in order to analyze the basic performance of the anti-entropy algorithms. Assume that any server can infect any other server with equal probability. Also assume that k members are already infected and infections occur in rounds: at each round, each server randomly picks another server. For a simple epidemic, sites are either infective or susceptible and exchanges occur in rounds.
10
11 Note: for the last equation, the first parenthesized term is the probability of a site choosing to exchange with a site other than the one in question. The exponent is the expected number of infectious sites. Thus we have the probability of a site s being susceptible after the ith cycle times the probability that all the infectious sites chose to contact other sites. If we compare the performance of the pull and push approaches; we observe that (for a very large number of servers) the pull approach converges (i.e., infects the entire population) faster than push does. Push-pull performs similar to pull.
12
13 A form of non-simple epidemic is called rumor mongering.
14 The math is taken from epidemic theory. The final equation tells us how many are still susceptible when there are no more infectious nodes. Thus these will never get the updates.
15
16 Recall that we have no time stamps, so it cannot be determined if an update is new or old.
17
18 Papers on Bayou include: Session Guarantees for Weakly Consistent Replicated Data, Proceedings of the Third International Conference on Parallel and Distributed Information Systems, Managing Update Conflicts in Bayou, a Weakly Connected Replicated Storage System, Proceedings of the fifteenth ACM symposium on Operating systems principles, 1995 ( delivery.acm.org/ /230000/224070/p172-terry.pdf? key1=224070&key2= &coll=guide&dl=guide&cfi). Flexible Update Propagation for Weakly Consistent Replication, Proceedings of the sixteenth ACM symposium on Operating systems principles, 1997 ( / / / p p e t e r s e n. p d f? key1=266711&key2= &coll=guide&dl=guide&cfid= &cftoken= ).
19
20
21
22 There are many scenarios in which conventional version vector-based techniques fail to detect the conflicts correctly. In some applications, concurrent writes to the same object may not conflict as expected. Furthermore, concurrent writes to different objects may conflict. Bayou handles such cases by having the application define its own notion of conflict.
23 Conflict detection is accomplished by using dependency checks each write operation also supplies a dependency check that specifies a simple condition defined over the state of the database. The dependency check also defines what the application expects to see as a result when the condition gets evaluated. If indeed the expected result is observed then Bayou decides that there is no conflict, else it decides that there is a conflict. If there is a conflict, then a merge procedure (i.e., a conflict resolution procedure), also supplied by the application, is executed to resolve the conflict. The merge procedure produces a new alternate update that is acceptable by the application and that would not create a conflict with the current database state (i.e., an update for which the dependency check will produce the expected result).
24 The slide shows the basic format of a Bayou write.
25 The slide shows an example Bayou write, including the dependency check and the merge procedure.
26
27
28
29
30 Note that process here means a client who is connecting to multiple servers.
31
32
33
34
35
36 We sketch an approach to an implementation of the constraints. Our first few ideas aren t entirely practical, but will lead to an approach that is.
37 If a server can t be found that satisfies the restriction of the second bullet, then the application must be notified that read-your-writes cannot be maintained.
38
39
40
41
42
43
44
45
Anti-entropy works as follows: periodically, a server P randomly chooses a server Q and then the two exchange databases. Three modes of anti-entropy a
 Anti-entropy works as follows: periodically, a server P randomly chooses a server Q and then the two exchange databases. Three modes of anti-entropy are possible. In push mode, P pushes its database to
Anti-entropy works as follows: periodically, a server P randomly chooses a server Q and then the two exchange databases. Three modes of anti-entropy are possible. In push mode, P pushes its database to
Last Class: Web Caching. Today: More on Consistency
 Last Class: Web Caching Use web caching as an illustrative example Distribution protocols Invalidate versus updates Push versus Pull Cooperation between replicas Lecture 16, page 1 Today: More on Consistency
Last Class: Web Caching Use web caching as an illustrative example Distribution protocols Invalidate versus updates Push versus Pull Cooperation between replicas Lecture 16, page 1 Today: More on Consistency
Consistency and Replication. Why replicate?
 Consistency and Replication Today: Consistency models Data-centric consistency models Client-centric consistency models Lecture 15, page 1 Why replicate? Data replication versus compute replication Data
Consistency and Replication Today: Consistency models Data-centric consistency models Client-centric consistency models Lecture 15, page 1 Why replicate? Data replication versus compute replication Data
Cloud Computing: "network access to shared pool of configurable computing resources"
 Large-Scale Networks Gossip-based Protocols Consistency for Large-Scale Data Replication Uwe Roehm / Vincent Gramoli School of Information Technologies The University of Sydney Page 1 Cloud Computing:
Large-Scale Networks Gossip-based Protocols Consistency for Large-Scale Data Replication Uwe Roehm / Vincent Gramoli School of Information Technologies The University of Sydney Page 1 Cloud Computing:
A Middleware for Gossip Protocols
 A Middleware for Gossip Protocols Michael Chow Cornell University mcc59@cornell.edu Robbert van Renesse Cornell University rvr@cs.cornell.edu Gossip protocols are known to be highly robust in scenarios
A Middleware for Gossip Protocols Michael Chow Cornell University mcc59@cornell.edu Robbert van Renesse Cornell University rvr@cs.cornell.edu Gossip protocols are known to be highly robust in scenarios
Computing Parable. The Archery Teacher. Courtesy: S. Keshav, U. Waterloo. Computer Science. Lecture 16, page 1
 Computing Parable The Archery Teacher Courtesy: S. Keshav, U. Waterloo Lecture 16, page 1 Consistency and Replication Today: Consistency models Data-centric consistency models Client-centric consistency
Computing Parable The Archery Teacher Courtesy: S. Keshav, U. Waterloo Lecture 16, page 1 Consistency and Replication Today: Consistency models Data-centric consistency models Client-centric consistency
Managing Update Conflicts in Bayou. Lucy Youxuan Jiang, Hiwot Tadese Kassa
 Managing Update Conflicts in Bayou Lucy Youxuan Jiang, Hiwot Tadese Kassa Outline! Background + Motivation! Bayou Model Dependency checking for conflict detection Merge procedures for conflict resolution
Managing Update Conflicts in Bayou Lucy Youxuan Jiang, Hiwot Tadese Kassa Outline! Background + Motivation! Bayou Model Dependency checking for conflict detection Merge procedures for conflict resolution
Eventual Consistency. Eventual Consistency
 Eventual Consistency Many systems: one or few processes perform updates How frequently should these updates be made available to other read-only processes? Examples: DNS: single naming authority per domain
Eventual Consistency Many systems: one or few processes perform updates How frequently should these updates be made available to other read-only processes? Examples: DNS: single naming authority per domain
Gossip Protocols. Márk Jelasity. Hungarian Academy of Sciences and University of Szeged, Hungary
 Gossip Protocols Márk Jelasity Hungarian Academy of Sciences and University of Szeged, Hungary Introduction Gossip-like phenomena are commonplace human gossip epidemics (virus spreading, etc) computer
Gossip Protocols Márk Jelasity Hungarian Academy of Sciences and University of Szeged, Hungary Introduction Gossip-like phenomena are commonplace human gossip epidemics (virus spreading, etc) computer
Module 7 - Replication
 Module 7 - Replication Replication Why replicate? Reliability Avoid single points of failure Performance Scalability in numbers and geographic area Why not replicate? Replication transparency Consistency
Module 7 - Replication Replication Why replicate? Reliability Avoid single points of failure Performance Scalability in numbers and geographic area Why not replicate? Replication transparency Consistency
MUTE: A Peer-to-Peer Web-based Real-time Collaborative Editor
 MUTE: A Peer-to-Peer Web-based Real-time Collaborative Editor Matthieu Nicolas, Victorien Elvinger, Gérald Oster, Claudia-Lavinia Ignat, François Charoy To cite this version: Matthieu Nicolas, Victorien
MUTE: A Peer-to-Peer Web-based Real-time Collaborative Editor Matthieu Nicolas, Victorien Elvinger, Gérald Oster, Claudia-Lavinia Ignat, François Charoy To cite this version: Matthieu Nicolas, Victorien
Gossiping in Distributed Systems Foundations
 Gossiping in Distributed Systems Foundations Maarten van Steen 2 of 41 2 of 41 Introduction Observation: We continue to face hard scalability problems in distributed systems: Systems continue to grow in
Gossiping in Distributed Systems Foundations Maarten van Steen 2 of 41 2 of 41 Introduction Observation: We continue to face hard scalability problems in distributed systems: Systems continue to grow in
Excogitating File Replication and Consistency maintenance strategies intended for Providing High Performance at low Cost in Peer-to-Peer Networks
 Excogitating File Replication and Consistency maintenance strategies intended for Providing High Performance at low Cost in Peer-to-Peer Networks Bollimuntha Kishore Babu #1, Divya Vadlamudi #2, Movva
Excogitating File Replication and Consistency maintenance strategies intended for Providing High Performance at low Cost in Peer-to-Peer Networks Bollimuntha Kishore Babu #1, Divya Vadlamudi #2, Movva
Consistency and Replication (part b)
 Consistency and Replication (part b) EECS 591 Farnam Jahanian University of Michigan Tanenbaum Chapter 6.1-6.5 Eventual Consistency A very weak consistency model characterized by the lack of simultaneous
Consistency and Replication (part b) EECS 591 Farnam Jahanian University of Michigan Tanenbaum Chapter 6.1-6.5 Eventual Consistency A very weak consistency model characterized by the lack of simultaneous
G Bayou: A Weakly Connected Replicated Storage System. Robert Grimm New York University
 G22.3250-001 Bayou: A Weakly Connected Replicated Storage System Robert Grimm New York University Altogether Now: The Three Questions! What is the problem?! What is new or different?! What are the contributions
G22.3250-001 Bayou: A Weakly Connected Replicated Storage System Robert Grimm New York University Altogether Now: The Three Questions! What is the problem?! What is new or different?! What are the contributions
A Survey of Peer-to-Peer Systems
 A Survey of Peer-to-Peer Systems Kostas Stefanidis Department of Computer Science, University of Ioannina, Greece kstef@cs.uoi.gr Abstract Peer-to-Peer systems have become, in a short period of time, one
A Survey of Peer-to-Peer Systems Kostas Stefanidis Department of Computer Science, University of Ioannina, Greece kstef@cs.uoi.gr Abstract Peer-to-Peer systems have become, in a short period of time, one
CS 425 / ECE 428 Distributed Systems Fall 2015
 CS 425 / ECE 428 Distributed Systems Fall 2015 Indranil Gupta (Indy) Sep 24, 2015 Lecture 10: Gossiping All slides IG Multicast Fault-tolerance and Scalability Needs: 1. Reliability (Atomicity) 100% receipt
CS 425 / ECE 428 Distributed Systems Fall 2015 Indranil Gupta (Indy) Sep 24, 2015 Lecture 10: Gossiping All slides IG Multicast Fault-tolerance and Scalability Needs: 1. Reliability (Atomicity) 100% receipt
Multicast. Presented by Hakim Weatherspoon. Slides borrowed from Qi Huang 2009 and Tom Ternquist 2010
 Multicast Presented by Hakim Weatherspoon Slides borrowed from Qi Huang 2009 and Tom Ternquist 2010 Midterm report abstract, introduction, background, related work, and design section. These sections should
Multicast Presented by Hakim Weatherspoon Slides borrowed from Qi Huang 2009 and Tom Ternquist 2010 Midterm report abstract, introduction, background, related work, and design section. These sections should
The Case for Non-transparent Replication: Examples from Bayou
 The Case for Non-transparent Replication: Examples from Bayou Douglas B. Terry, Karin Petersen, Mike J. Spreitzer, and Marvin M. Theimer Computer Science Laboratory Xerox Palo Alto Research Center Palo
The Case for Non-transparent Replication: Examples from Bayou Douglas B. Terry, Karin Petersen, Mike J. Spreitzer, and Marvin M. Theimer Computer Science Laboratory Xerox Palo Alto Research Center Palo
Replication & Consistency Part II. CS403/534 Distributed Systems Erkay Savas Sabanci University
 Replication & Consistency Part II CS403/534 Distributed Systems Erkay Savas Sabanci University 1 Overview Implementation issues Replica Placement Update Propagation Epidemic Protocols Casually Consistent
Replication & Consistency Part II CS403/534 Distributed Systems Erkay Savas Sabanci University 1 Overview Implementation issues Replica Placement Update Propagation Epidemic Protocols Casually Consistent
Gossip Protocols. Márk Jelasity. Hungarian Academy of Sciences and University of Szeged, Hungary
 Gossip Protocols Márk Jelasity Hungarian Academy of Sciences and University of Szeged, Hungary Introduction Gossip-like phenomena are commonplace human gossip epidemics (virus spreading, etc) computer
Gossip Protocols Márk Jelasity Hungarian Academy of Sciences and University of Szeged, Hungary Introduction Gossip-like phenomena are commonplace human gossip epidemics (virus spreading, etc) computer
Towards a Solution to the Red Wedding Problem
 Towards a Solution to the Red Wedding Problem Christopher S. Meiklejohn Université catholique de Louvain Instituto Superior Técnico Heather Miller Northeastern University École Polytechnique Fédérale de
Towards a Solution to the Red Wedding Problem Christopher S. Meiklejohn Université catholique de Louvain Instituto Superior Técnico Heather Miller Northeastern University École Polytechnique Fédérale de
CS505: Distributed Systems
 Cristina Nita-Rotaru CS505: Distributed Systems Protocols. Slides prepared based on material by Prof. Ken Birman at Cornell University, available at http://www.cs.cornell.edu/ken/book/ Required reading
Cristina Nita-Rotaru CS505: Distributed Systems Protocols. Slides prepared based on material by Prof. Ken Birman at Cornell University, available at http://www.cs.cornell.edu/ken/book/ Required reading
Replica Placement. Replica Placement
 Replica Placement Model: We consider objects (and don t worry whether they contain just data or code, or both) Distinguish different processes: A process is capable of hosting a replica of an object or
Replica Placement Model: We consider objects (and don t worry whether they contain just data or code, or both) Distinguish different processes: A process is capable of hosting a replica of an object or
Decentralized Replication Mechanisms in Deno
 Decentralized Replication Mechanisms in Deno Peter J. Keleher keleher@cs.umd.edu Department of Computer Science University of Maryland College Park, Maryland 20742 We are currently finalizing the design
Decentralized Replication Mechanisms in Deno Peter J. Keleher keleher@cs.umd.edu Department of Computer Science University of Maryland College Park, Maryland 20742 We are currently finalizing the design
The Performance of Weak-consistency Replication Protocols
 The Performance of Weak-consistency Replication Protocols Richard A. Golding Darrell D. E. Long UCSC CRL 92 30 July 6, 1992 Concurrent Systems Laboratory Computer and Information Sciences University of
The Performance of Weak-consistency Replication Protocols Richard A. Golding Darrell D. E. Long UCSC CRL 92 30 July 6, 1992 Concurrent Systems Laboratory Computer and Information Sciences University of
Block lectures on Gossip-based protocols
 Block lectures on Gossip-based protocols Lecture 1: dissemination, randomness and aggregation Dr. Etienne Rivière University of Neuchâtel Etienne.Riviere@unine.ch Lectures funded by the EU commission as
Block lectures on Gossip-based protocols Lecture 1: dissemination, randomness and aggregation Dr. Etienne Rivière University of Neuchâtel Etienne.Riviere@unine.ch Lectures funded by the EU commission as
Simple, Fast and Deterministic Gossip and Rumor Spreading. Main paper by: B. Haeupler, MIT Talk by: Alessandro Dovis, ETH
 Simple, Fast and Deterministic Gossip and Rumor Spreading Main paper by: B. Haeupler, MIT Talk by: Alessandro Dovis, ETH Presentation Outline What is gossip? Applications Basic Algorithms Advanced Algorithms
Simple, Fast and Deterministic Gossip and Rumor Spreading Main paper by: B. Haeupler, MIT Talk by: Alessandro Dovis, ETH Presentation Outline What is gossip? Applications Basic Algorithms Advanced Algorithms
Network Working Group. E. Guttman Sun Microsystems April 2003
 Network Working Group Request for Comments: 3528 Category: Experimental W. Zhao H. Schulzrinne Columbia University E. Guttman Sun Microsystems April 2003 Status of this Memo Mesh-enhanced Service Location
Network Working Group Request for Comments: 3528 Category: Experimental W. Zhao H. Schulzrinne Columbia University E. Guttman Sun Microsystems April 2003 Status of this Memo Mesh-enhanced Service Location
An Approach to Massively Distributed Aggregate Computing on Peer-to-Peer Networks
 An Approach to Massively Distributed Aggregate Computing on Peer-to-Peer Networks Márk Jelasity University of Bologna, Italy, and RGAI, University of Szeged, Hungary jelasity@cs.vu.nl Wojtek Kowalczyk
An Approach to Massively Distributed Aggregate Computing on Peer-to-Peer Networks Márk Jelasity University of Bologna, Italy, and RGAI, University of Szeged, Hungary jelasity@cs.vu.nl Wojtek Kowalczyk
Asynchronous Replication and Bayou. Jeff Chase CPS 212, Fall 2000
 Asynchronous Replication and Bayou Jeff Chase CPS 212, Fall 2000 Asynchronous Replication Idea: build available/scalable information services with read-any-write-any replication and a weak consistency
Asynchronous Replication and Bayou Jeff Chase CPS 212, Fall 2000 Asynchronous Replication Idea: build available/scalable information services with read-any-write-any replication and a weak consistency
Reconciliation for Mobile Computing Environments with Portable Storage Devices
 Reconciliation for Mobile Computing Environments with Portable Storage Devices Marcos Bento 1, Nuno Preguiça 1, Carlos Baquero 2, and J. Legatheaux Martins 1 1 DI, FCT, Universidade Nova de Lisboa 2 DI,
Reconciliation for Mobile Computing Environments with Portable Storage Devices Marcos Bento 1, Nuno Preguiça 1, Carlos Baquero 2, and J. Legatheaux Martins 1 1 DI, FCT, Universidade Nova de Lisboa 2 DI,
Rumour spreading in the spatial preferential attachment model
 Rumour spreading in the spatial preferential attachment model Abbas Mehrabian University of British Columbia Banff, 2016 joint work with Jeannette Janssen The push&pull rumour spreading protocol [Demers,
Rumour spreading in the spatial preferential attachment model Abbas Mehrabian University of British Columbia Banff, 2016 joint work with Jeannette Janssen The push&pull rumour spreading protocol [Demers,
Consistency and Replication
 Consistency and Replication Introduction Data-centric consistency Client-centric consistency Distribution protocols Consistency protocols 1 Goal: Reliability Performance Problem: Consistency Replication
Consistency and Replication Introduction Data-centric consistency Client-centric consistency Distribution protocols Consistency protocols 1 Goal: Reliability Performance Problem: Consistency Replication
Design choices for weak-consistency group communication
 Design choices for weak-consistency group communication Richard A. Golding and Darrell D. E. Long UCSC TR 92 45 October 12, 1992 Concurrent Systems Laboratory Computer and Information Sciences University
Design choices for weak-consistency group communication Richard A. Golding and Darrell D. E. Long UCSC TR 92 45 October 12, 1992 Concurrent Systems Laboratory Computer and Information Sciences University
Designing and Implementing Asynchronous Collaborative Applications with Bayou
 Designing and Implementing Asynchronous Collaborative Applications with Bayou W. Keith Edwards, Elizabeth D. Mynatt, Karin Petersen, Mike J. Spreitzer, Douglas B. Terry, Marvin M. Theimer Xerox Palo Alto
Designing and Implementing Asynchronous Collaborative Applications with Bayou W. Keith Edwards, Elizabeth D. Mynatt, Karin Petersen, Mike J. Spreitzer, Douglas B. Terry, Marvin M. Theimer Xerox Palo Alto
Chapter 4: Distributed Systems: Replication and Consistency. Fall 2013 Jussi Kangasharju
 Chapter 4: Distributed Systems: Replication and Consistency Fall 2013 Jussi Kangasharju Chapter Outline n Replication n Consistency models n Distribution protocols n Consistency protocols 2 Data Replication
Chapter 4: Distributed Systems: Replication and Consistency Fall 2013 Jussi Kangasharju Chapter Outline n Replication n Consistency models n Distribution protocols n Consistency protocols 2 Data Replication
Important Lessons. Today's Lecture. Two Views of Distributed Systems
 Important Lessons Replication good for performance/ reliability Key challenge keeping replicas up-to-date Wide range of consistency models Will see more next lecture Range of correctness properties L-10
Important Lessons Replication good for performance/ reliability Key challenge keeping replicas up-to-date Wide range of consistency models Will see more next lecture Range of correctness properties L-10
Modeling replica divergence in a weak-consistency protocol for global-scale distributed data bases
 Modeling replica divergence in a weak-consistency protocol for global-scale distributed data bases Richard A. Golding y Vrije Universiteit, Amsterdam, The Netherlands Darrell D. E. Long z University of
Modeling replica divergence in a weak-consistency protocol for global-scale distributed data bases Richard A. Golding y Vrije Universiteit, Amsterdam, The Netherlands Darrell D. E. Long z University of
Course Syllabus. Comp 735 Distributed and Concurrent Algorithms. Spring 2017
 Course Syllabus Comp 735 Distributed and Concurrent Algorithms Spring 2017 Meeting Place: SN 115 Meeting Time: 11:00 12:15, TuTh Course Web Page: http://www.cs.unc.edu/ anderson/teach/comp735 Instructor:
Course Syllabus Comp 735 Distributed and Concurrent Algorithms Spring 2017 Meeting Place: SN 115 Meeting Time: 11:00 12:15, TuTh Course Web Page: http://www.cs.unc.edu/ anderson/teach/comp735 Instructor:
Consistency and Replication
 Topics to be covered Introduction Consistency and Replication Consistency Models Distribution Protocols Consistency Protocols 1 2 + Performance + Reliability Introduction Introduction Availability: proportion
Topics to be covered Introduction Consistency and Replication Consistency Models Distribution Protocols Consistency Protocols 1 2 + Performance + Reliability Introduction Introduction Availability: proportion
CS555: Distributed Systems [Fall 2017] Dept. Of Computer Science, Colorado State University
![CS555: Distributed Systems [Fall 2017] Dept. Of Computer Science, Colorado State University CS555: Distributed Systems [Fall 2017] Dept. Of Computer Science, Colorado State University](/thumbs/80/81272615.jpg) CS 555: DISTRIBUTED SYSTEMS [MESSAGING SYSTEMS] Shrideep Pallickara Computer Science Colorado State University Frequently asked questions from the previous class survey Distributed Servers Security risks
CS 555: DISTRIBUTED SYSTEMS [MESSAGING SYSTEMS] Shrideep Pallickara Computer Science Colorado State University Frequently asked questions from the previous class survey Distributed Servers Security risks
On the Benefits of Network Coding for Wireless Applications
 On the Benefits of Network Coding for Wireless Applications Christina Fragouli EPFL Lausanne, Switzerland Email: christina.fragouli@epfl.ch Jörg Widmer DoCoMo Euro-Labs Munich, Germany Email: widmer@docomolab-euro.com
On the Benefits of Network Coding for Wireless Applications Christina Fragouli EPFL Lausanne, Switzerland Email: christina.fragouli@epfl.ch Jörg Widmer DoCoMo Euro-Labs Munich, Germany Email: widmer@docomolab-euro.com
Consistency and Replication. Some slides are from Prof. Jalal Y. Kawash at Univ. of Calgary
 Consistency and Replication Some slides are from Prof. Jalal Y. Kawash at Univ. of Calgary Reasons for Replication Reliability/Availability : Mask failures Mask corrupted data Performance: Scalability
Consistency and Replication Some slides are from Prof. Jalal Y. Kawash at Univ. of Calgary Reasons for Replication Reliability/Availability : Mask failures Mask corrupted data Performance: Scalability
Symmetric Push-Sum Protocol for Decentralised Aggregation
 Symmetric Push-Sum Protocol for Decentralised Aggregation Francesco Blasa, Simone Cafiero, Giancarlo Fortino, Department of Electronics, Informatics and Systems University of Calabria, 87036 Rende (CS),
Symmetric Push-Sum Protocol for Decentralised Aggregation Francesco Blasa, Simone Cafiero, Giancarlo Fortino, Department of Electronics, Informatics and Systems University of Calabria, 87036 Rende (CS),
The push&pull protocol for rumour spreading
 The push&pull protocol for rumour spreading Abbas Mehrabian Simons Institute for Theory of Computing, UC Berkeley University of Waterloo 10 February 2017 Co-authors Huseyin Acan Omer Angel Petra Berenbrink
The push&pull protocol for rumour spreading Abbas Mehrabian Simons Institute for Theory of Computing, UC Berkeley University of Waterloo 10 February 2017 Co-authors Huseyin Acan Omer Angel Petra Berenbrink
Chapter 1 Operations With Numbers
 Chapter 1 Operations With Numbers Part I Negative Numbers You may already know what negative numbers are, but even if you don t, then you have probably seen them several times over the past few days. If
Chapter 1 Operations With Numbers Part I Negative Numbers You may already know what negative numbers are, but even if you don t, then you have probably seen them several times over the past few days. If
Epidemic-style Communication Primitives Exploiting Network Topology Information
 Epidemic-style Communication Primitives Exploiting Network Topology Information Mirco Musolesi and Cecilia Mascolo Department of Computer Science, University College London Gower Street, London, WC1E 6BT,
Epidemic-style Communication Primitives Exploiting Network Topology Information Mirco Musolesi and Cecilia Mascolo Department of Computer Science, University College London Gower Street, London, WC1E 6BT,
DS-Means: Distributed Data Stream Clustering
 DS-Means: Distributed Data Stream Clustering Alessio Guerrieri and Alberto Montresor University of Trento, Italy Abstract. This paper proposes DS-means, a novel algorithm for clustering distributed data
DS-Means: Distributed Data Stream Clustering Alessio Guerrieri and Alberto Montresor University of Trento, Italy Abstract. This paper proposes DS-means, a novel algorithm for clustering distributed data
Evaluation of Epidemic Routing Protocol in Delay Tolerant Networks
 Evaluation of Epidemic Routing Protocol in Delay Tolerant Networks D. Kiranmayi Department of CSE, Vignan s Institute Of IT, Visakhapatnam, India ABSTRACT:There are many routing protocols that which can
Evaluation of Epidemic Routing Protocol in Delay Tolerant Networks D. Kiranmayi Department of CSE, Vignan s Institute Of IT, Visakhapatnam, India ABSTRACT:There are many routing protocols that which can
Communication. Distributed Systems IT332
 Communication Distributed Systems IT332 2 Outline Fundamentals Layered network communication protocols Types of communication Remote Procedure Call Message Oriented Communication Multicast Communication
Communication Distributed Systems IT332 2 Outline Fundamentals Layered network communication protocols Types of communication Remote Procedure Call Message Oriented Communication Multicast Communication
An Analytical Model of Information Dissemination for a Gossip-based Protocol
 An Analytical Model of Information Dissemination for a Gossip-based Protocol Rena Bakhshi, Daniela Gavidia, Wan Fokkink, and Maarten van Steen Department of Computer Science, Vrije Universiteit Amsterdam,
An Analytical Model of Information Dissemination for a Gossip-based Protocol Rena Bakhshi, Daniela Gavidia, Wan Fokkink, and Maarten van Steen Department of Computer Science, Vrije Universiteit Amsterdam,
X X C 1. Recap. CSE 486/586 Distributed Systems Gossiping. Eager vs. Lazy Replication. Recall: Passive Replication. Fault-Tolerance and Scalability
 Recap Distributed Systems Gossiping Steve Ko Computer Sciences and Engineering University at Buffalo Consistency models Linearizability Sequential consistency Causal consistency Eventual consistency Depending
Recap Distributed Systems Gossiping Steve Ko Computer Sciences and Engineering University at Buffalo Consistency models Linearizability Sequential consistency Causal consistency Eventual consistency Depending
INF-5360 Presentation
 INF-5360 Presentation Optimistic Replication Ali Ahmad April 29, 2013 Structure of presentation Pessimistic and optimistic replication Elements of Optimistic replication Eventual consistency Scheduling
INF-5360 Presentation Optimistic Replication Ali Ahmad April 29, 2013 Structure of presentation Pessimistic and optimistic replication Elements of Optimistic replication Eventual consistency Scheduling
Distributed Systems: Consistency and Replication
 Distributed Systems: Consistency and Replication Alessandro Sivieri Dipartimento di Elettronica, Informazione e Bioingegneria Politecnico, Italy alessandro.sivieri@polimi.it http://corsi.dei.polimi.it/distsys
Distributed Systems: Consistency and Replication Alessandro Sivieri Dipartimento di Elettronica, Informazione e Bioingegneria Politecnico, Italy alessandro.sivieri@polimi.it http://corsi.dei.polimi.it/distsys
Intro to Github. Jessica Young
 Intro to Github Jessica Young jyoung22@nd.edu GitHub Basics 1. Installing GitHub and Git 2. Connecting Git and GitHub 3. Why use Git? Installing GitHub If you haven t already, create an account on GitHub
Intro to Github Jessica Young jyoung22@nd.edu GitHub Basics 1. Installing GitHub and Git 2. Connecting Git and GitHub 3. Why use Git? Installing GitHub If you haven t already, create an account on GitHub
Dr Markus Hagenbuchner CSCI319 SIM. Distributed Systems Chapter 4 - Communication
 Dr Markus Hagenbuchner markus@uow.edu.au CSCI319 SIM Distributed Systems Chapter 4 - Communication CSCI319 Chapter 4 Page: 1 Communication Lecture notes based on the textbook by Tannenbaum Study objectives:
Dr Markus Hagenbuchner markus@uow.edu.au CSCI319 SIM Distributed Systems Chapter 4 - Communication CSCI319 Chapter 4 Page: 1 Communication Lecture notes based on the textbook by Tannenbaum Study objectives:
1 Introduction In large distributed networks of computers, it is often the case that a subset of machines want to cooperate to perform a common task.
 Resource Discovery in Distributed Networks Mor Harchol-alter Tom Leighton y Daniel Lewin z MIT, Cambridge, MA 02139 h harchol,ftl,danli@theory.lcs.mit.edu Abstract In large distributed networks of computers,
Resource Discovery in Distributed Networks Mor Harchol-alter Tom Leighton y Daniel Lewin z MIT, Cambridge, MA 02139 h harchol,ftl,danli@theory.lcs.mit.edu Abstract In large distributed networks of computers,
Resource Discovery in Networks under Bandwidth Limitations
 Resource Discovery in Networks under Bandwidth Limitations Kishori M. Konwar Department of Computer Science and Engg University of Connecticut 371 Fairfield Rd., Unit 2155 Storrs, CT 06269, USA kishori@cse.uconn.edu
Resource Discovery in Networks under Bandwidth Limitations Kishori M. Konwar Department of Computer Science and Engg University of Connecticut 371 Fairfield Rd., Unit 2155 Storrs, CT 06269, USA kishori@cse.uconn.edu
Cloudy Weather for P2P
 Cloudy Weather for P2P with a Chance of Gossip Alberto Montresor Luca Abeni Best paper award in P2P'11 Presented by: amir@sics.se 1 Introduction 2 Cloud Computing vs. P2P Similarity: Providing the infinite
Cloudy Weather for P2P with a Chance of Gossip Alberto Montresor Luca Abeni Best paper award in P2P'11 Presented by: amir@sics.se 1 Introduction 2 Cloud Computing vs. P2P Similarity: Providing the infinite
Availability versus consistency. Eventual Consistency: Bayou. Eventual consistency. Bayou: A Weakly Connected Replicated Storage System
 Eventual Consistency: Bayou Availability versus consistency Totally-Ordered Multicast kept replicas consistent but had single points of failure Not available under failures COS 418: Distributed Systems
Eventual Consistency: Bayou Availability versus consistency Totally-Ordered Multicast kept replicas consistent but had single points of failure Not available under failures COS 418: Distributed Systems
Consistency in Distributed Systems
 Consistency in Distributed Systems Recall the fundamental DS properties DS may be large in scale and widely distributed 1. concurrent execution of components 2. independent failure modes 3. transmission
Consistency in Distributed Systems Recall the fundamental DS properties DS may be large in scale and widely distributed 1. concurrent execution of components 2. independent failure modes 3. transmission
Abstract Specifications for Weakly Consistent Data
 Abstract Specifications for Weakly Consistent Data Sebastian Burckhardt Microsoft Research Redmond, WA, USA Jonathan Protzenko Microsoft Research Redmond, WA, USA Abstract Weak consistency can improve
Abstract Specifications for Weakly Consistent Data Sebastian Burckhardt Microsoft Research Redmond, WA, USA Jonathan Protzenko Microsoft Research Redmond, WA, USA Abstract Weak consistency can improve
CS 138: Dynamo. CS 138 XXIV 1 Copyright 2017 Thomas W. Doeppner. All rights reserved.
 CS 138: Dynamo CS 138 XXIV 1 Copyright 2017 Thomas W. Doeppner. All rights reserved. Dynamo Highly available and scalable distributed data store Manages state of services that have high reliability and
CS 138: Dynamo CS 138 XXIV 1 Copyright 2017 Thomas W. Doeppner. All rights reserved. Dynamo Highly available and scalable distributed data store Manages state of services that have high reliability and
CSE 486/586 Distributed Systems
 CSE 486/586 Distributed Systems Gossiping Slides by Steve Ko Computer Sciences and Engineering University at Buffalo CSE 486/586 Revisiting Multicast Node with a piece of information to be communicated
CSE 486/586 Distributed Systems Gossiping Slides by Steve Ko Computer Sciences and Engineering University at Buffalo CSE 486/586 Revisiting Multicast Node with a piece of information to be communicated
Processing your Data in Enroll
 Processing your Data in Enroll Getting Started with Enroll: The Enroll Home Page The Enroll home page allows you to continue working on data that has been started but not completed, or start a new data
Processing your Data in Enroll Getting Started with Enroll: The Enroll Home Page The Enroll home page allows you to continue working on data that has been started but not completed, or start a new data
Parallelism. Master 1 International. Andrea G. B. Tettamanzi. Université de Nice Sophia Antipolis Département Informatique
 Parallelism Master 1 International Andrea G. B. Tettamanzi Université de Nice Sophia Antipolis Département Informatique andrea.tettamanzi@unice.fr Andrea G. B. Tettamanzi, 2014 1 Lecture 2 Communication
Parallelism Master 1 International Andrea G. B. Tettamanzi Université de Nice Sophia Antipolis Département Informatique andrea.tettamanzi@unice.fr Andrea G. B. Tettamanzi, 2014 1 Lecture 2 Communication
Understanding the Behavior of the Conflict-Rate Metric in Optimistic Peer Replication
 Understanding the Behavior of the Conflict-Rate Metric in Optimistic Peer Replication An-I A. Wang, Peter Reiher, and Rajive Bagrodia Computer Science Department University of California, Los Angeles {awang,
Understanding the Behavior of the Conflict-Rate Metric in Optimistic Peer Replication An-I A. Wang, Peter Reiher, and Rajive Bagrodia Computer Science Department University of California, Los Angeles {awang,
AGENT-BASED MODELING BOOTCAMP FOR HEALTH RESEARCHERS AUGUST 2012 A SIMPLE NETWORK-BASED INFECTION SPREAD AGENT-BASED MODEL
 Rating: Basic Prerequisites: Building a Minimalist Network-Based Model Framework Estimated Time Required: 1 hour This exercise rehearses basic steps that can be used to create a model of infection spread..
Rating: Basic Prerequisites: Building a Minimalist Network-Based Model Framework Estimated Time Required: 1 hour This exercise rehearses basic steps that can be used to create a model of infection spread..
Excel For Algebra. Conversion Notes: Excel 2007 vs Excel 2003
 Excel For Algebra Conversion Notes: Excel 2007 vs Excel 2003 If you re used to Excel 2003, you re likely to have some trouble switching over to Excel 2007. That s because Microsoft completely reworked
Excel For Algebra Conversion Notes: Excel 2007 vs Excel 2003 If you re used to Excel 2003, you re likely to have some trouble switching over to Excel 2007. That s because Microsoft completely reworked
Moderated by: Moheeb Rajab Background singers: Jay and Fabian
 Network Forensics and Next Generation Internet Attacks Moderated by: Moheeb Rajab Background singers: Jay and Fabian 1 Agenda Questions and Critique of Timezones paper Extensions Network Monitoring (recap)
Network Forensics and Next Generation Internet Attacks Moderated by: Moheeb Rajab Background singers: Jay and Fabian 1 Agenda Questions and Critique of Timezones paper Extensions Network Monitoring (recap)
Reducing Transaction Abort Rate of Epidemic Algorithm in Replicated Databases
 Reducing Transaction Abort Rate of Epidemic Algorithm in Replicated Databases Huaizhong Lin 1,*, Zengwei Zheng 1,2, and Chun Chen 1 1 College of Computer Science, Zhejiang University, 310027 Hangzhou,
Reducing Transaction Abort Rate of Epidemic Algorithm in Replicated Databases Huaizhong Lin 1,*, Zengwei Zheng 1,2, and Chun Chen 1 1 College of Computer Science, Zhejiang University, 310027 Hangzhou,
Data Consistency for P2P Collaborative Editing
 Data Consistency for P2P Collaborative Editing Gérald Oster Institute for Information Systems ETH Zurich osterg@inf.ethz.ch Pascal Urso, Pascal Molli, Abdessamad Imine Université Henri Poincaré, Nancy
Data Consistency for P2P Collaborative Editing Gérald Oster Institute for Information Systems ETH Zurich osterg@inf.ethz.ch Pascal Urso, Pascal Molli, Abdessamad Imine Université Henri Poincaré, Nancy
Math-2. Lesson 3-1. Equations of Lines
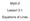 Math-2 Lesson 3-1 Equations of Lines How can an equation make a line? y = x + 1 x -4-3 -2-1 0 1 2 3 Fill in the rest of the table rule x + 1 f(x) -4 + 1-3 -3 + 1-2 -2 + 1-1 -1 + 1 0 0 + 1 1 1 + 1 2 2 +
Math-2 Lesson 3-1 Equations of Lines How can an equation make a line? y = x + 1 x -4-3 -2-1 0 1 2 3 Fill in the rest of the table rule x + 1 f(x) -4 + 1-3 -3 + 1-2 -2 + 1-1 -1 + 1 0 0 + 1 1 1 + 1 2 2 +
Example File Systems Using Replication CS 188 Distributed Systems February 10, 2015
 Example File Systems Using Replication CS 188 Distributed Systems February 10, 2015 Page 1 Example Replicated File Systems NFS Coda Ficus Page 2 NFS Originally NFS did not have any replication capability
Example File Systems Using Replication CS 188 Distributed Systems February 10, 2015 Page 1 Example Replicated File Systems NFS Coda Ficus Page 2 NFS Originally NFS did not have any replication capability
An Enhanced Binning Algorithm for Distributed Web Clusters
 1 An Enhanced Binning Algorithm for Distributed Web Clusters Hann-Jang Ho Granddon D. Yen Jack Lee Department of Information Management, WuFeng Institute of Technology SingLing Lee Feng-Wei Lien Department
1 An Enhanced Binning Algorithm for Distributed Web Clusters Hann-Jang Ho Granddon D. Yen Jack Lee Department of Information Management, WuFeng Institute of Technology SingLing Lee Feng-Wei Lien Department
On Collaborative Content Distribution using Multi-Message Gossip
 On Collaborative Content Distribution using Multi-Message Gossip Coby Fernandess Dahlia Malkhi Abstract We study epidemic schemes in the context of collaborative data delivery. In this context, multiple
On Collaborative Content Distribution using Multi-Message Gossip Coby Fernandess Dahlia Malkhi Abstract We study epidemic schemes in the context of collaborative data delivery. In this context, multiple
CSC D70: Compiler Optimization Register Allocation
 CSC D70: Compiler Optimization Register Allocation Prof. Gennady Pekhimenko University of Toronto Winter 2018 The content of this lecture is adapted from the lectures of Todd Mowry and Phillip Gibbons
CSC D70: Compiler Optimization Register Allocation Prof. Gennady Pekhimenko University of Toronto Winter 2018 The content of this lecture is adapted from the lectures of Todd Mowry and Phillip Gibbons
Middleware-Konzepte. Multicast. Dr. Gero Mühl
 Middleware-Konzepte Multicast Dr. Gero Mühl Kommunikations- und Betriebssysteme Fakultät für Elektrotechnik und Informatik Technische Universität Berlin Agenda > Introduction > IPv4 Multicast > Reliability
Middleware-Konzepte Multicast Dr. Gero Mühl Kommunikations- und Betriebssysteme Fakultät für Elektrotechnik und Informatik Technische Universität Berlin Agenda > Introduction > IPv4 Multicast > Reliability
Recap. CSE 486/586 Distributed Systems Case Study: Amazon Dynamo. Amazon Dynamo. Amazon Dynamo. Necessary Pieces? Overview of Key Design Techniques
 Recap CSE 486/586 Distributed Systems Case Study: Amazon Dynamo Steve Ko Computer Sciences and Engineering University at Buffalo CAP Theorem? Consistency, Availability, Partition Tolerance P then C? A?
Recap CSE 486/586 Distributed Systems Case Study: Amazon Dynamo Steve Ko Computer Sciences and Engineering University at Buffalo CAP Theorem? Consistency, Availability, Partition Tolerance P then C? A?
Replication and Consistency
 Replication and Consistency Today l Replication l Consistency models l Consistency protocols The value of replication For reliability and availability Avoid problems with disconnection, data corruption,
Replication and Consistency Today l Replication l Consistency models l Consistency protocols The value of replication For reliability and availability Avoid problems with disconnection, data corruption,
Efficient and Decentralized Computation of Approximate Global State
 Efficient and Decentralized Computation of Approximate Global State S. Keshav School of Computer Science, University of Waterloo Waterloo, ON, Canada, N2L 3G1 ABSTRACT The need for efficient computation
Efficient and Decentralized Computation of Approximate Global State S. Keshav School of Computer Science, University of Waterloo Waterloo, ON, Canada, N2L 3G1 ABSTRACT The need for efficient computation
Flexible Update Propagation for Weakly Consistent Replication
 Flexible Update Propagation for Weakly Consistent Replication Karin Petersen, Mike J. Spreitzer, Douglas B. Terry, Marvin M. Theimer and Alan J. Demers * Computer Science Laboratory Xerox Palo Alto Research
Flexible Update Propagation for Weakly Consistent Replication Karin Petersen, Mike J. Spreitzer, Douglas B. Terry, Marvin M. Theimer and Alan J. Demers * Computer Science Laboratory Xerox Palo Alto Research
Computing Frequent Elements Using Gossip
 Computing Frequent Elements Using Gossip Bibudh Lahiri and Srikanta Tirthapura Iowa State University, Ames, IA, 50011, USA {bibudh,snt}@iastate.edu Abstract. We present algorithms for identifying frequently
Computing Frequent Elements Using Gossip Bibudh Lahiri and Srikanta Tirthapura Iowa State University, Ames, IA, 50011, USA {bibudh,snt}@iastate.edu Abstract. We present algorithms for identifying frequently
Implementing Replication. Overview of Replication Managing Publications and Subscriptions Configuring Replication in Some Common Scenarios
 Implementing Replication Overview of Replication Managing Publications and Subscriptions Configuring Replication in Some Common Scenarios Lesson 1: Overview of Replication Distributing and Synchronizing
Implementing Replication Overview of Replication Managing Publications and Subscriptions Configuring Replication in Some Common Scenarios Lesson 1: Overview of Replication Distributing and Synchronizing
Improving Throughput and Node Proximity of P2P Live Video Streaming through Overlay Adaptation
 Ninth IEEE International Symposium on Multimedia 27 Improving Throughput and Node Proximity of P2P Live Video Streaming through Overlay Adaptation Bartosz Biskupski, Raymond Cunningham, and René Meier
Ninth IEEE International Symposium on Multimedia 27 Improving Throughput and Node Proximity of P2P Live Video Streaming through Overlay Adaptation Bartosz Biskupski, Raymond Cunningham, and René Meier
Scalable Information Dissemination for Pervasive Systems: Implementation and Evaluation
 Scalable Information Dissemination for Pervasive Systems: Implementation and Evaluation Graham Williamson, Graeme Stevenson, Steve Neely, Lorcan Coyle, Paddy Nixon Systems Research Group School of Computer
Scalable Information Dissemination for Pervasive Systems: Implementation and Evaluation Graham Williamson, Graeme Stevenson, Steve Neely, Lorcan Coyle, Paddy Nixon Systems Research Group School of Computer
Mining Distributed Frequent Itemsets Using a Gossip based Protocol
 Mining Distributed Frequent Itemsets Using a Gossip based Protocol Maryam Bagheri, Seyed-Hassan Mirian-Hosseinabadi, Hoda Mashayekhi, Jafar Habibi Department of Computer Engineering Sharif University of
Mining Distributed Frequent Itemsets Using a Gossip based Protocol Maryam Bagheri, Seyed-Hassan Mirian-Hosseinabadi, Hoda Mashayekhi, Jafar Habibi Department of Computer Engineering Sharif University of
6.1 Evaluate Roots and Rational Exponents
 VOCABULARY:. Evaluate Roots and Rational Exponents Radical: We know radicals as square roots. But really, radicals can be used to express any root: 0 8, 8, Index: The index tells us exactly what type of
VOCABULARY:. Evaluate Roots and Rational Exponents Radical: We know radicals as square roots. But really, radicals can be used to express any root: 0 8, 8, Index: The index tells us exactly what type of
Decisions, Decisions. Testing, testing C H A P T E R 7
 C H A P T E R 7 In the first few chapters, we saw some of the basic building blocks of a program. We can now make a program with input, processing, and output. We can even make our input and output a little
C H A P T E R 7 In the first few chapters, we saw some of the basic building blocks of a program. We can now make a program with input, processing, and output. We can even make our input and output a little
LINEAR PROGRAMMING: A GEOMETRIC APPROACH. Copyright Cengage Learning. All rights reserved.
 3 LINEAR PROGRAMMING: A GEOMETRIC APPROACH Copyright Cengage Learning. All rights reserved. 3.1 Graphing Systems of Linear Inequalities in Two Variables Copyright Cengage Learning. All rights reserved.
3 LINEAR PROGRAMMING: A GEOMETRIC APPROACH Copyright Cengage Learning. All rights reserved. 3.1 Graphing Systems of Linear Inequalities in Two Variables Copyright Cengage Learning. All rights reserved.
Scheduling of Multi-Stream Gossip Systems
 Scheduling of Multi-Stream Gossip Systems Nathanael Thompson, Ercan Ucan and Indranil Gupta Dept. of Computer Science, University of Illinois at Urbana-Champaign Email: {nathomps,eucan2,indy}@cs.uiuc.edu
Scheduling of Multi-Stream Gossip Systems Nathanael Thompson, Ercan Ucan and Indranil Gupta Dept. of Computer Science, University of Illinois at Urbana-Champaign Email: {nathomps,eucan2,indy}@cs.uiuc.edu
TECHNISCHE UNIVERSITEIT EINDHOVEN Faculteit Wiskunde en Informatica
 TECHNISCHE UNIVERSITEIT EINDHOVEN Faculteit Wiskunde en Informatica Examination Architecture of Distributed Systems (2IMN10 / 2II45), on Monday November 2, 2015, from 13.30 to 16.30 hours. Indicate on
TECHNISCHE UNIVERSITEIT EINDHOVEN Faculteit Wiskunde en Informatica Examination Architecture of Distributed Systems (2IMN10 / 2II45), on Monday November 2, 2015, from 13.30 to 16.30 hours. Indicate on
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 7, JULY
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 7, JULY 2008 2997 Fast Distributed Algorithms for Computing Separable Functions Damon Mosk-Aoyama and Devavrat Shah, Member, IEEE Abstract The problem
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 7, JULY 2008 2997 Fast Distributed Algorithms for Computing Separable Functions Damon Mosk-Aoyama and Devavrat Shah, Member, IEEE Abstract The problem
Project 2: How Parentheses and the Order of Operations Impose Structure on Expressions
 MAT 51 Wladis Project 2: How Parentheses and the Order of Operations Impose Structure on Expressions Parentheses show us how things should be grouped together. The sole purpose of parentheses in algebraic
MAT 51 Wladis Project 2: How Parentheses and the Order of Operations Impose Structure on Expressions Parentheses show us how things should be grouped together. The sole purpose of parentheses in algebraic
A Gossip-Style Failure Detection Service
 A Gossip-Style Failure Detection Service Robbert van Renesse, Yaron Minsky, and Mark Hayden Dept. of Computer Science, Cornell University 4118 Upson Hall, Ithaca, NY 14853 Abstract Failure Detection is
A Gossip-Style Failure Detection Service Robbert van Renesse, Yaron Minsky, and Mark Hayden Dept. of Computer Science, Cornell University 4118 Upson Hall, Ithaca, NY 14853 Abstract Failure Detection is
CS6450: Distributed Systems Lecture 13. Ryan Stutsman
 Eventual Consistency CS6450: Distributed Systems Lecture 13 Ryan Stutsman Material taken/derived from Princeton COS-418 materials created by Michael Freedman and Kyle Jamieson at Princeton University.
Eventual Consistency CS6450: Distributed Systems Lecture 13 Ryan Stutsman Material taken/derived from Princeton COS-418 materials created by Michael Freedman and Kyle Jamieson at Princeton University.
Chapter 7 Consistency And Replication
 DISTRIBUTED SYSTEMS Principles and Paradigms Second Edition ANDREW S. TANENBAUM MAARTEN VAN STEEN Chapter 7 Consistency And Replication Data-centric Consistency Models Figure 7-1. The general organization
DISTRIBUTED SYSTEMS Principles and Paradigms Second Edition ANDREW S. TANENBAUM MAARTEN VAN STEEN Chapter 7 Consistency And Replication Data-centric Consistency Models Figure 7-1. The general organization
Supporting Asynchronous Collaborative Editing in Mobile Computing Environments
 Supporting synchronous ollaborative Editing in Mobile omputing Environments Marcos ento, Nuno Preguiça ITI/DI, FT, Universidade Nova de Lisboa, Portugal Keywords: bstract: synchronous collaborative editing
Supporting synchronous ollaborative Editing in Mobile omputing Environments Marcos ento, Nuno Preguiça ITI/DI, FT, Universidade Nova de Lisboa, Portugal Keywords: bstract: synchronous collaborative editing
Lecture 5. Data Flow Analysis
 Lecture 5. Data Flow Analysis Wei Le 2014.10 Abstraction-based Analysis dataflow analysis: combines model checking s fix point engine with abstract interpretation of data values abstract interpretation:
Lecture 5. Data Flow Analysis Wei Le 2014.10 Abstraction-based Analysis dataflow analysis: combines model checking s fix point engine with abstract interpretation of data values abstract interpretation:
