SHED: Spam Ham Dataset
|
|
|
- Doris Baker
- 5 years ago
- Views:
Transcription
1 Volume: 5 Issue: SHED: Spam Ham Dataset Upasana Sharma Student Central University of Punjab Bathinda, Punjab upasana.upasana@gmail.com Surinder Singh Khurana Assistant Professor Central University of Punjab Bathinda, Punjab surinder.seeeker@gmail.com Abstract Automatic filtering of spam s becomes essential feature for a good service provider. To gain direct or indirect benefits organizations/individuals are sending a lot of spam s. Such kind s activities are not only distracting the user but also consume lot of resources including processing power, memory and network bandwidth. The security issues are also associated with these unwanted s as these s may contain malicious content and/or links. Content based spam filtering is one of the effective approaches used for filtering. However, its efficiency depends upon the training set. The most of the existing datasets were collected and prepared a long back and the spammers have been changing the content to evade the filters trained based on these datasets. In this paper, we introduce Spam Ham dataset (SHED): a dataset consisting spam and ham . We evaluated the performance of filtering techniques trained by previous datasets and filtering techniques trained by SHED. It was observed that the filtering techniques trained by SHED outperformed the technique trained by other dataset. Furthermore, we also classified the spam into various categories. Key-Spam , Non-spam s, WEKA, feature selection,, Parameters ***** I. INTRODUCTION Spam also known as junk or unsolicited bulk (UBE) is a subset of electronic spam involving nearly identical messages sent to numerous recipients by [1]. The messages may contain disguised links that appear to be for familiar websites but in fact lead to phishing web sites or sites that are hosting malware[2]. Spam may also include malware as scripts or other executable file attachments. Spammers collect addresses from chat rooms, websites, customer lists, newsgroups, and viruses which harvest users' address books, and are sold to other spammers. Ham is a term opposed to spam messages. Ham is then all "good" legitimate messages, that is to say, all messages solicited by the recipient through an opt-in process[3]. II. LITERATURE REVIEW There are large amounts of researches had been done by researchers to defend against spam. To enable the researchers various datasets were also prepared. SpamAssassin is a public mail corpus[4]. This is a selection of mail messages, suitable for use in testing spam filtering systems. TREC s Spam [5] track uses a standard testing framework that presents a set of chronologically ordered messages a spam filter for classification. In the filtering task, the messages are presented one at time to the filter, which yields a binary judgment (spam or ham). Four different forms of user feedback are modeled: with immediate feedback, delayed feedback, partial feedback and full delayed feedback. Ling- Spam[] is a mixture of spam messages, and legitimate messages sent via the Linguist list, a moderated and spam-free mailing list about the science and profession of linguistics. The corpus consists of 2893 messages:2412 legitimate messages, obtained by randomly downloading digests from the list s archives, 481 spam messages, received by Ion Androutsopoulos, one of the authors of the corpus. Ling-Spam has the disadvantage that its legitimate messages are more topic-specific than the legitimate messages most users receive. Hence, the performance of a learning-based anti-spam filter on Ling-Spam may be an over-optimistic estimate of the performance that can be achieved on the incoming messages of a real user, where topic-specific terminology may be less dominant among legitimate messages. Enron corpus[7] is another dataset. Authors analyzed its suitability with respect to folder prediction, and provide the baseline results of a state-of-the-art classifier (Support Vector Machines) under various conditions, including the cases of using individual sections (From, To, Subject and body) alone as the input to the classifier, and using all the sections in combination with regression weights. A large set of messages, the Enron corpus, was made public during the legal investigation concerning the Enron corporation. Table 1: List of Spam Datasets Corpus Name Number of Messages Spa Ha m m Year of Creat ion Reference/Used SpamAssassin [M endez et al, 2] Enron-Spam IJRITCC June 217, [Koprinska et al, 27] LingSpam [Sakkis et al, 1512] PU [Attar et al, 211] Spambase [Sakkis et al, 1512] Trec [Androutsopoulos et al, 2a] 178
2 Volume: 5 Issue: III. RESEARCH METHODOLOGY dataset into spam and ham categories. We divided Methodology used to carry out the work is divided the corpora into proportions of ham (legitimate) and spam into five phases: messages[9]. The experiment is performed with the 135 most frequent in spam and 154 most frequent 1) Phase-1:Creation of various address in ham . To compare the efficiency of the In phase 1, 8 addresses are created to collect various dataset we also classified the dataset with list of 55 spam as well as non spam s in it. All the s are specified in Spambase dataset and with list having most created on gmail.com. Fictitious addresses have been frequent 55 prepares from the dataset. assigned to these ids. Table 3: List of top 135 spam 2) Phase-2: Circulation of Address In the next step we populate these addresses on the Internet to make them publically available. The aim of this activity is derived from the methodology followed by spammers to collect and prepare list. We mentioned these ids on various blog and registered these ids on various sites such as sites belong to Online Gambling. We have a strong opinion that such kind of sites are not only providing activities like gambling but also using the user data like addresses for other purposes. These purposes may include advertising and/or sending malicious or social engineering s. addresses and websites on which these s are registered/circulated are mentioned in table 2. Table 2: Various websites where addresses are registered. 1 Online Lottery 2 online rummy websites 3 online gambling 4 online jobs 5 freelancer work online viagara 7 weight loss 8 online ipad 9 loan websites 1 Jeevansathi 11 online pizza 12 online viruses 3) Phase-3: Feature Extraction In this phase various features of the s has been extracted and stored in excel sheet. These features are Subject, body, recipient id, sender id, date, time and message id.. Features of 2 s have been obtained in this activity. 4) Phase-4: Calculation of attributes Further we calculated the values of attributes used by existing spam detection techniques. 1. Subject Length 2. Body Length 3. Frequently Appearing Word List for Spam as well as Ham s 4. Word Frequency for Spam as well as Ham s. B. Phase 5: Classification Further using above dataset we evaluated the performance of the dataset by using various (, Naïve bayes,, )[8] to classify Get most Even Much Subject Out order Work marketing Next One Per First Cost Income More Take Easy Save Only Name Way home Service People Internet Credit message Month Money Call Offer Full Sent Business addresses Web sales Apply Over Receive See Few special Know Million place Amount Make program Search Pay Earn Time Now Company products Limited Just Need Software show Click Like Very Number hours Advertisement Free Please Best great Detail information address Product good Here New Site Right available Price Send Own Give check Important Mail Use Help Less Loan List Find Start Buy Tax future PM ID version Science Case Enron Trade Excel Users Daily Field FEE content ever High Read Mobile Dear follow Article Try Weekly Such Daily account Health Based directly Rights Parts Receiving Other Reply Basis Table 4: List of top 154 non- spam Market Junior Universit-y Commissio-n Microsoft sure Manager Corporat-ion Holder Sep Letter Details Staff Trainee Mar Computer Project Naukri General National 217 Unsubscri be Mountain Deputy Life Last Applicatio n Graduate Degree Reading Date Image View.Net Office 21 Research United Advt Here PST Subscribed Technician Create Technology Assistant India Powered Development Core Updated Engineer Options ASP.NET DATES Votes Medical States Public Singh AM Google Torronto State IMPORTANT Various Bank Form Horoscope Ghansham Invites Senior Build Multiple Facebook Officer Code News Forwarded Police Ago Institute Client Wipeout August Yesterday Technical Data Blogs Open Entry Official Details Executive Tips Stop Group Pradesh Ontario Operator wrote Library Continue SQL Gmail Results Android Code Video Charting Scale Selection Bathinda Delhi Sarkari API District Board Chief Horoscope IJRITCC June 217, 179
3 Volume: 5 Issue: Table Performance in 1-fold cross validation with new 55 attributes HTML Centre Stenographe r Preparation Framework Division Affairs Punjab App Clerk Singles mailbox Ferrand Laboratory Professor C# Bengal Canada Inspector Government Drive Court Newsletter Applicants Note Unattende Managem Corresponde d ent nce Tasking Swapout Examinatio n Insurance Angular Apprentices Classifiers Accuracy Time Taken to build model ( sec ) Precision Recall Furthermore, various feature selection approaches: Greedy Stepwise, Ranker Search, Best First and Genetic Search have been applied to find the reduce in the list so that the detection time can be reduced. IV. RESULTS AND DISCISSION As per the methodology we collected the spam and ham s. Total 2 s were collected. These includes 449 spam and 1512 ham s. By manual analysis these spam s have been categorized into 14 categories. These categories and number of s we covered in each category are mentioned in table 5.Important point of note here is about Article publication spam category. In this category 348 out of 449 spam s fall, which may be indicating about commercialization of our education system. Table 5: Categorization of spam s Types of spam No. of spam s Social media spam 298 Lucky winner spam 245 Dream job spam 41 Weight loss spam 335 Male enhancement spam 33 Debt Reduction spam 239 Credential spam 327 Loan spam 331 Tax spam 29 Discount offer spam 451 Article publication spam 348 Software related spam 297 Product sale spam 34 money stealing spam 3 Total Performance analysis of 2 s (spam as well as nonspam)with 55 new attributes with chisquare evaluator and ranker attribute selection at 1 fold cross validation. From figure 1, correctly classified instances or accuracy obtained for Random Forest is 99.18% and time taken to build model is seconds. Table shows performance analysis of 2 s (spam as well as non-spam) with 55 new attributes with chisquare evaluator and ranker attribute selection at 1 fold cross validation. Table, shows the values for accuracy, time, precision and recall rate that are used for the comparison of four algorithms. It evaluates that random forest gives the best result among all the four algorithms. It gives highest accuracy and runs efficiently on large databases, whereas Bayes Net gives the second highest accuracy with least time to build the models. Table 7 Performance in 1-fold cross validation with old 55 attributes Time Taken to Classifiers Accuracy Precision Recall build model ( sec ) Table 7 shows performance analysis of 2 s (spam as well as non-spam) with 55 old attributes with chisquare evaluator and ranker attribute selection at 1 fold cross validation. IJRITCC June 217, 18
4 Volume: 5 Issue: Accuracy of new Accuracy of old Fig1 Accuracy of different Time taken of new Time taken of old Time taken for new Time taken for old fig 2 Time taken to build models of different Fig 3 Precision and recall rate of different Fig 4.4 shows performance analysis of 2 s (spam as well as non-spam) with 55 new attributes and old attributes with chisquare evaluator and ranker attribute selection at percentage split (:34).). From fig 4, correctly classified instances or accuracy obtained is 98.8% and in fig 5 time taken to build model is seconds Precision for Precision for new 55 old 55 Accuracy of new Recall for new 55 Accuracy of old Fig 4 Accuracy of different Recall for old 55 RandomFores Naïve Bayes Bayesn t Random Forest fig 5 Time taken to build models of different V. CONCLUSION AND FUTURE WORK In this work we prepared a dataset called SHED: Spam Ham Dataset. For the purpose various s ids were created and circulated to public web domain so that the same can be collected by spammers. Around s were collected to prepare the data set. Further we extracted various features from the s. These features include: subject, body, sender s address, and receiver s address, header, etc. Further we also calculated word frequencies. We prepared a list of frequently occurring in both spam and non spam s. To evaluate the spam filtering process we use four classification approaches:,, and. These approaches were trained with SHED and spambase dataset(already existing). During the evaluation it was observed that the accuracy of all the is comparatively high while trained with SHED, as compared to the accuracy while trained with spambase. This is due to the change of different used by spammers. The efficient among these is Random forest which classified the s with 99.18% accuracy. From the study, it can be concluded that spam cannot be completely stopped but it can be filtered with high accuracy. In future, several other algorithms other than the incorporated ones can be used to filter s. Furthermore, work can be carried out to filter image based spam s. IJRITCC June 217, VI. REFERENCES [1] P. Ozarkar and M. Patwardhan, Efficient Spam Classification by Appropriate Feature Selection, Glob. J. Comput. Sci. Technol. Softw. Data Eng., vol. 13, no. 5, 213. [2] S. Martin, B. Nelson, and A. D. Joseph, Analyzing Behaviorial Features for Classification, Micro, vol. 3, pp , 24. [3] S. Teli and S. Biradar, Effective Spam Detection Method for , Int. Conf. Adv. Eng. Technol., vol. 214, pp. 8 72, 214. [4] A. A. Blaheta, Project 3 : Spamassassin, no. November, pp. 2 7, 214. [5] G. Cormack and T. Lynam, TREC 27 Spam Track Overview, Sixt. Text Retr. Conf. (TREC 27), no. Trec, pp. 1 9, 27. [] G. Costa, M. Errecalde, U. Nacional, D. S. Luis, and S. Luis, Learning to detect spam messages. [7] B. Klimt and Y. Yang, The Enron Corpus: A New Dataset 181
5 Volume: 5 Issue: for Classification Research, pp , 24. [8] S. Sharma and A. Arora, Adaptive Approach for Spam Detection, Int. J. Comput. Sci. Issues, vol. 1, no. 4, pp. 23 2, 213. [9] R. Sharma and G. Kaur, Spam Detection Techniques : A Review, vol. 4, no. 5, pp , 215. [1] Rathi and Megha and Pareek, Vikas, Spam mail detection through data mining-a comparative performance analysis, Int. J. Comput. Sci.,213 [11] Trivedi, shrawan kumar and Dey,Shubhamoy, A combining approach for detecting spams Proceedings IEEE,24. IJRITCC June 217, 182
International Journal of Computer Engineering and Applications, Volume XI, Issue VIII, August 17, ISSN
 International Journal of Computer Engineering and Applications, Volume XI, Issue VIII, August 17, www.ijcea.com ISSN 2321-3469 SPAM E-MAIL DETECTION USING CLASSIFIERS AND ADABOOST TECHNIQUE Nilam Badgujar
International Journal of Computer Engineering and Applications, Volume XI, Issue VIII, August 17, www.ijcea.com ISSN 2321-3469 SPAM E-MAIL DETECTION USING CLASSIFIERS AND ADABOOST TECHNIQUE Nilam Badgujar
An electronic mailing list is a way to distribute information to many Internet users using . It is a list of names and addresses, similar to a
 1 An electronic mailing list is a way to distribute information to many Internet users using email. It is a list of names and addresses, similar to a traditional mailing list and works using a reflector,
1 An electronic mailing list is a way to distribute information to many Internet users using email. It is a list of names and addresses, similar to a traditional mailing list and works using a reflector,
Countering Spam Using Classification Techniques. Steve Webb Data Mining Guest Lecture February 21, 2008
 Countering Spam Using Classification Techniques Steve Webb webb@cc.gatech.edu Data Mining Guest Lecture February 21, 2008 Overview Introduction Countering Email Spam Problem Description Classification
Countering Spam Using Classification Techniques Steve Webb webb@cc.gatech.edu Data Mining Guest Lecture February 21, 2008 Overview Introduction Countering Email Spam Problem Description Classification
Chapter-8. Conclusion and Future Scope
 Chapter-8 Conclusion and Future Scope This thesis has addressed the problem of Spam E-mails. In this work a Framework has been proposed. The proposed framework consists of the three pillars which are Legislative
Chapter-8 Conclusion and Future Scope This thesis has addressed the problem of Spam E-mails. In this work a Framework has been proposed. The proposed framework consists of the three pillars which are Legislative
Project Report. Prepared for: Dr. Liwen Shih Prepared by: Joseph Hayes. April 17, 2008 Course Number: CSCI
 University of Houston Clear Lake School of Science & Computer Engineering Project Report Prepared for: Dr. Liwen Shih Prepared by: Joseph Hayes April 17, 2008 Course Number: CSCI 5634.01 University of
University of Houston Clear Lake School of Science & Computer Engineering Project Report Prepared for: Dr. Liwen Shih Prepared by: Joseph Hayes April 17, 2008 Course Number: CSCI 5634.01 University of
A Comparison of Text-Categorization Methods applied to N-Gram Frequency Statistics
 A Comparison of Text-Categorization Methods applied to N-Gram Frequency Statistics Helmut Berger and Dieter Merkl 2 Faculty of Information Technology, University of Technology, Sydney, NSW, Australia hberger@it.uts.edu.au
A Comparison of Text-Categorization Methods applied to N-Gram Frequency Statistics Helmut Berger and Dieter Merkl 2 Faculty of Information Technology, University of Technology, Sydney, NSW, Australia hberger@it.uts.edu.au
DIRECT TESTIMONY AFFIDAVIT OF ED FALK. ED FALK, being first duly sworn, and deposes and says as follows:
 STATE OF NORTH DAKOTA IN DISTRICT COURT COUNTY OF CASS EAST CENTRAL JUDICIAL DISTRICT John Doe, vs. Ed Falk, Plaintiff, Civil No. 09-05-C-543 Hon. Frank Racek Defendant. DIRECT TESTIMONY AFFIDAVIT OF ED
STATE OF NORTH DAKOTA IN DISTRICT COURT COUNTY OF CASS EAST CENTRAL JUDICIAL DISTRICT John Doe, vs. Ed Falk, Plaintiff, Civil No. 09-05-C-543 Hon. Frank Racek Defendant. DIRECT TESTIMONY AFFIDAVIT OF ED
Computer aided mail filtering using SVM
 Computer aided mail filtering using SVM Lin Liao, Jochen Jaeger Department of Computer Science & Engineering University of Washington, Seattle Introduction What is SPAM? Electronic version of junk mail,
Computer aided mail filtering using SVM Lin Liao, Jochen Jaeger Department of Computer Science & Engineering University of Washington, Seattle Introduction What is SPAM? Electronic version of junk mail,
Collaborative Filtering. Doug Herbers Master s Oral Defense June 28, 2005
 Collaborative E-Mail Filtering Doug Herbers Master s Oral Defense June 28, 2005 Background Spamming the use of any electronic communications medium to send unsolicited messages in bulk E-Mail is the most
Collaborative E-Mail Filtering Doug Herbers Master s Oral Defense June 28, 2005 Background Spamming the use of any electronic communications medium to send unsolicited messages in bulk E-Mail is the most
AN INTRODUCTION TO QUICKBOOKS ONLINE. Getting Started Guide
 AN INTRODUCTION TO QUICKBOOKS ONLINE Getting Started Guide Copyright Copyright 2014 Intuit Ltd. All rights reserved. Intuit Canada Trademarks 2014 Intuit Inc. All rights reserved. Intuit the Intuit logo,
AN INTRODUCTION TO QUICKBOOKS ONLINE Getting Started Guide Copyright Copyright 2014 Intuit Ltd. All rights reserved. Intuit Canada Trademarks 2014 Intuit Inc. All rights reserved. Intuit the Intuit logo,
Introduction to
 Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting
GFI product comparison: GFI MailEssentials vs. McAfee Security for Servers
 GFI product comparison: GFI MailEssentials vs. McAfee Security for Email Servers Features GFI MailEssentials McAfee Integrates with Microsoft Exchange Server 2003/2007/2010/2013 Scans incoming and outgoing
GFI product comparison: GFI MailEssentials vs. McAfee Security for Email Servers Features GFI MailEssentials McAfee Integrates with Microsoft Exchange Server 2003/2007/2010/2013 Scans incoming and outgoing
SCSUG 2017 Classifying and Predicting Spam Messages using Text Mining in SAS Enterprise Miner
 SCSUG 2017 Classifying and Predicting Spam Messages using Text Mining in SAS Enterprise Miner Mounika Kondamudi, Oklahoma State University, Mentored by Balamurugan Mohan, H&R Block Abstract In this technologically
SCSUG 2017 Classifying and Predicting Spam Messages using Text Mining in SAS Enterprise Miner Mounika Kondamudi, Oklahoma State University, Mentored by Balamurugan Mohan, H&R Block Abstract In this technologically
ProofPoint Protection Perimeter Security Daily Digest and Configuration Guide. Faculty/Staff Guide
 ProofPoint Email Protection Email Perimeter Security Daily Digest and Configuration Guide Faculty/Staff Guide Contents Introduction and ProofPoint Overview... 2 Daily Email Digest... 3 ProofPoint Portal
ProofPoint Email Protection Email Perimeter Security Daily Digest and Configuration Guide Faculty/Staff Guide Contents Introduction and ProofPoint Overview... 2 Daily Email Digest... 3 ProofPoint Portal
South Central Power Stop Scams
 Don t get tricked. People around the country have been receiving emails and phone calls from scammers. South Central Power wants to help you keep your money and prevent scams. Review the helpful tips below.
Don t get tricked. People around the country have been receiving emails and phone calls from scammers. South Central Power wants to help you keep your money and prevent scams. Review the helpful tips below.
Cyber Security Guide for NHSmail
 Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
Analysis of Naïve Bayes Algorithm for Spam Filtering across Multiple Datasets
 IOP Conference Series: Materials Science and Engineering PAPER OPEN ACCESS Analysis of Naïve Bayes Algorithm for Email Spam Filtering across Multiple Datasets To cite this article: Nurul Fitriah Rusland
IOP Conference Series: Materials Science and Engineering PAPER OPEN ACCESS Analysis of Naïve Bayes Algorithm for Email Spam Filtering across Multiple Datasets To cite this article: Nurul Fitriah Rusland
AN EFFECTIVE SPAM FILTERING FOR DYNAMIC MAIL MANAGEMENT SYSTEM
 ISSN: 2229-6956(ONLINE) DOI: 1.21917/ijsc.212.5 ICTACT JOURNAL ON SOFT COMPUTING, APRIL 212, VOLUME: 2, ISSUE: 3 AN EFFECTIVE SPAM FILTERING FOR DYNAMIC MAIL MANAGEMENT SYSTEM S. Arun Mozhi Selvi 1 and
ISSN: 2229-6956(ONLINE) DOI: 1.21917/ijsc.212.5 ICTACT JOURNAL ON SOFT COMPUTING, APRIL 212, VOLUME: 2, ISSUE: 3 AN EFFECTIVE SPAM FILTERING FOR DYNAMIC MAIL MANAGEMENT SYSTEM S. Arun Mozhi Selvi 1 and
Acceptable Use Policy
 Acceptable Use Policy. August 2016 1. Overview Kalamazoo College provides and maintains information technology resources to support its academic programs and administrative operations. This Acceptable
Acceptable Use Policy. August 2016 1. Overview Kalamazoo College provides and maintains information technology resources to support its academic programs and administrative operations. This Acceptable
Spam Detection ECE 539 Fall 2013 Ethan Grefe. For Public Use
 Email Detection ECE 539 Fall 2013 Ethan Grefe For Public Use Introduction email is sent out in large quantities every day. This results in email inboxes being filled with unwanted and inappropriate messages.
Email Detection ECE 539 Fall 2013 Ethan Grefe For Public Use Introduction email is sent out in large quantities every day. This results in email inboxes being filled with unwanted and inappropriate messages.
Contents. Management. Client. Choosing One 1/20/17
 Contents Email Management CSCU9B2 Email clients choosing and using Email message header and content Emailing to lists of people In and out message management Mime attachments and HTML email SMTP, HTTP,
Contents Email Management CSCU9B2 Email clients choosing and using Email message header and content Emailing to lists of people In and out message management Mime attachments and HTML email SMTP, HTTP,
An Empirical Performance Comparison of Machine Learning Methods for Spam Categorization
 An Empirical Performance Comparison of Machine Learning Methods for Spam E-mail Categorization Chih-Chin Lai a Ming-Chi Tsai b a Dept. of Computer Science and Information Engineering National University
An Empirical Performance Comparison of Machine Learning Methods for Spam E-mail Categorization Chih-Chin Lai a Ming-Chi Tsai b a Dept. of Computer Science and Information Engineering National University
Online Communication. Chat Rooms Instant Messaging Blogging Social Media
 Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media { Advantages: { Reduces cost of postage Fast and convenient Need an email address to sign up for other online accounts. Eliminates
Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media { Advantages: { Reduces cost of postage Fast and convenient Need an email address to sign up for other online accounts. Eliminates
How I use Outlook: Rev 04/17/08
 How I use Outlook: Rev 04/17/08 Intro: Did I hear someone whine about email messages? Too many, too much spam, can t find them, cant track them can t keep them organized? I feel your pain but excuse me,
How I use Outlook: Rev 04/17/08 Intro: Did I hear someone whine about email messages? Too many, too much spam, can t find them, cant track them can t keep them organized? I feel your pain but excuse me,
Summer 2010 Research Project. Spam Filtering by Text Classification. Manoj Reddy Advisor: Dr. Behrang Mohit
 Summer 2010 Research Project Spam Filtering by Text Classification Manoj Reddy Advisor: Dr. Behrang Mohit NLP Field of Computer Science and Linguistics concerned with interactions between computers and
Summer 2010 Research Project Spam Filtering by Text Classification Manoj Reddy Advisor: Dr. Behrang Mohit NLP Field of Computer Science and Linguistics concerned with interactions between computers and
GFI product comparison: GFI MailEssentials vs. Barracuda Spam Firewall
 GFI product comparison: GFI MailEssentials vs. Barracuda Spam Firewall Features GFI MailEssentials Barracuda Spam Firewall Integrates with Microsoft Exchange Server 2007/2010/2013 Scans incoming and outgoing
GFI product comparison: GFI MailEssentials vs. Barracuda Spam Firewall Features GFI MailEssentials Barracuda Spam Firewall Integrates with Microsoft Exchange Server 2007/2010/2013 Scans incoming and outgoing
Canadian Anti-Spam Legislation (CASL)
 Canadian Anti-Spam Legislation (CASL) FREQUENTLY ASKED QUESTIONS The purpose of this document is to assist and guide U of R employees regarding their obligations under the Canadian Anti-Spam Legislation
Canadian Anti-Spam Legislation (CASL) FREQUENTLY ASKED QUESTIONS The purpose of this document is to assist and guide U of R employees regarding their obligations under the Canadian Anti-Spam Legislation
Get Twitter Followers in an Easy Way Step by Step Guide
 Get Twitter Followers in an Easy Way Step by Step Guide See how I made $2300 in 3 Days using Twitter Traffic All in one guide for getting traffic via Twitter 1 Get Twitter Followers in an easy way Step
Get Twitter Followers in an Easy Way Step by Step Guide See how I made $2300 in 3 Days using Twitter Traffic All in one guide for getting traffic via Twitter 1 Get Twitter Followers in an easy way Step
Online Communication. Chat Rooms Instant Messaging Blogging Social Media
 Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media Advantages: Reduces cost of postage Fast and convenient Eliminates phone charges Disadvantages: May be difficult to understand
Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media Advantages: Reduces cost of postage Fast and convenient Eliminates phone charges Disadvantages: May be difficult to understand
, Rules & Regulations
 Email, Rules & Regulations Social Media and Digital Communication Social Pro = #SocPro Steve Lee, APR 1 A Simple Contract Permission-based email marketing Be clear what you want to send Information, promotional
Email, Rules & Regulations Social Media and Digital Communication Social Pro = #SocPro Steve Lee, APR 1 A Simple Contract Permission-based email marketing Be clear what you want to send Information, promotional
A Performance Evaluation of Lfun Algorithm on the Detection of Drifted Spam Tweets
 A Performance Evaluation of Lfun Algorithm on the Detection of Drifted Spam Tweets Varsha Palandulkar 1, Siddhesh Bhujbal 2, Aayesha Momin 3, Vandana Kirane 4, Raj Naybal 5 Professor, AISSMS Polytechnic
A Performance Evaluation of Lfun Algorithm on the Detection of Drifted Spam Tweets Varsha Palandulkar 1, Siddhesh Bhujbal 2, Aayesha Momin 3, Vandana Kirane 4, Raj Naybal 5 Professor, AISSMS Polytechnic
Quick recap on ing Security Recap on where to find things on Belvidere website & a look at the Belvidere Facebook page
 Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Text Classification for Spam Using Naïve Bayesian Classifier
 Text Classification for E-mail Spam Using Naïve Bayesian Classifier Priyanka Sao 1, Shilpi Chaubey 2, Sonali Katailiha 3 1,2,3 Assistant ProfessorCSE Dept, Columbia Institute of Engg&Tech, Columbia Institute
Text Classification for E-mail Spam Using Naïve Bayesian Classifier Priyanka Sao 1, Shilpi Chaubey 2, Sonali Katailiha 3 1,2,3 Assistant ProfessorCSE Dept, Columbia Institute of Engg&Tech, Columbia Institute
SPAM UNDERSTANDING & AVOIDING
 SPAM UNDERSTANDING & AVOIDING Modified: March 8, 2016 SPAM UNDERSTANDING & AVOIDING... 5 What is Spam?... 6 How to avoid Spam... 6 How to view message headers... 8 Checking and emptying Junk E-mail...
SPAM UNDERSTANDING & AVOIDING Modified: March 8, 2016 SPAM UNDERSTANDING & AVOIDING... 5 What is Spam?... 6 How to avoid Spam... 6 How to view message headers... 8 Checking and emptying Junk E-mail...
An Efficient Spam Classification System Using Ensemble Machine Learning Algorithm
 An Efficient Spam Classification System Using Ensemble Machine Learning Algorithm A.Lakshmanarao 1, K.Chandra Sekhar 2, Y.Swathi 3 Associate Professor 1, Assistant Professor 2, Assistant Professor 3 1,2,3
An Efficient Spam Classification System Using Ensemble Machine Learning Algorithm A.Lakshmanarao 1, K.Chandra Sekhar 2, Y.Swathi 3 Associate Professor 1, Assistant Professor 2, Assistant Professor 3 1,2,3
Lesson 25 Communication Services
 Communication Services Computer Literacy BASICS: A Comprehensive Guide to IC 3, 3 rd Edition 1 Objectives Identify types of electronic communication. Describe users of electronic communication. Identify
Communication Services Computer Literacy BASICS: A Comprehensive Guide to IC 3, 3 rd Edition 1 Objectives Identify types of electronic communication. Describe users of electronic communication. Identify
Collaborative Spam Mail Filtering Model Design
 I.J. Education and Management Engineering, 2013, 2, 66-71 Published Online February 2013 in MECS (http://www.mecs-press.net) DOI: 10.5815/ijeme.2013.02.11 Available online at http://www.mecs-press.net/ijeme
I.J. Education and Management Engineering, 2013, 2, 66-71 Published Online February 2013 in MECS (http://www.mecs-press.net) DOI: 10.5815/ijeme.2013.02.11 Available online at http://www.mecs-press.net/ijeme
Botnets: major players in the shadows. Author Sébastien GOUTAL Chief Science Officer
 Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
2. Design Methodology
 Content-aware Email Multiclass Classification Categorize Emails According to Senders Liwei Wang, Li Du s Abstract People nowadays are overwhelmed by tons of coming emails everyday at work or in their daily
Content-aware Email Multiclass Classification Categorize Emails According to Senders Liwei Wang, Li Du s Abstract People nowadays are overwhelmed by tons of coming emails everyday at work or in their daily
A Reputation-based Collaborative Approach for Spam Filtering
 Available online at www.sciencedirect.com ScienceDirect AASRI Procedia 5 (2013 ) 220 227 2013 AASRI Conference on Parallel and Distributed Computing Systems A Reputation-based Collaborative Approach for
Available online at www.sciencedirect.com ScienceDirect AASRI Procedia 5 (2013 ) 220 227 2013 AASRI Conference on Parallel and Distributed Computing Systems A Reputation-based Collaborative Approach for
KEY FUNCTIONS. Dynamic content. Conditional s. A/B/X testing. Creation. testing. Video s. Spam. testing. Advanced personalisation
 KEY FUNCTIONS Dynamic content Conditional emails Messages sent as part of one campaign will automatically adjust their looks to particular addressees preferences. Depending on the values of the characteristics
KEY FUNCTIONS Dynamic content Conditional emails Messages sent as part of one campaign will automatically adjust their looks to particular addressees preferences. Depending on the values of the characteristics
NOT PROTECTIVELY MARKED PHISHING. July 2016
 - PHISHING July 2016 1 Introduction: The purpose of this document is to provide an analysis of the most prevalent trends and characteristics of phishing campaigns in the UK in July 2016. The analysis is
- PHISHING July 2016 1 Introduction: The purpose of this document is to provide an analysis of the most prevalent trends and characteristics of phishing campaigns in the UK in July 2016. The analysis is
Computer networks 2013
 Chapter 4 EXERCISE 1 1 Describe what is meant by each of the following: a Router b Bridge c Proxy server Answers: see the Glossary. 2 Many small businesses have computer networks. a List three advantages
Chapter 4 EXERCISE 1 1 Describe what is meant by each of the following: a Router b Bridge c Proxy server Answers: see the Glossary. 2 Many small businesses have computer networks. a List three advantages
Decision Science Letters
 Decision Science Letters 3 (2014) 439 444 Contents lists available at GrowingScience Decision Science Letters homepage: www.growingscience.com/dsl Identifying spam e-mail messages using an intelligence
Decision Science Letters 3 (2014) 439 444 Contents lists available at GrowingScience Decision Science Letters homepage: www.growingscience.com/dsl Identifying spam e-mail messages using an intelligence
Canada s Anti-Spam Legislation (CASL) What it means for Advisors. Distributor Learning & Development
 Canada s Anti-Spam Legislation (CASL) What it means for Advisors Distributor Learning & Development Learning objectives By the end of this session, you will be able to: Describe CASL and how it impacts
Canada s Anti-Spam Legislation (CASL) What it means for Advisors Distributor Learning & Development Learning objectives By the end of this session, you will be able to: Describe CASL and how it impacts
Panda Security. Protection. User s Manual. Protection. Version PM & Business Development Team
 Panda Security Email Protection Email Protection PM & Business Development Team User s Manual Version 4.3.2-2 1 Table of Contents Table of Contents... 2 1. Introduction to Email Protection... 3 2. Email
Panda Security Email Protection Email Protection PM & Business Development Team User s Manual Version 4.3.2-2 1 Table of Contents Table of Contents... 2 1. Introduction to Email Protection... 3 2. Email
IJTC.ORG. A Review on Various Classification Techniques in Spamming. Gurwinder Kaur 1, Rupinder Kaur Gurm 2. Sahib, Punjab, India,
 A Review on Various Classification Techniques in Email Spamming Gurwinder Kaur 1, Rupinder Kaur Gurm 2 1 Research Scholar, Department of CSE, RIMT-IET, Mandi Gobindgarh, Fatehgarh Sahib, Punjab, India,
A Review on Various Classification Techniques in Email Spamming Gurwinder Kaur 1, Rupinder Kaur Gurm 2 1 Research Scholar, Department of CSE, RIMT-IET, Mandi Gobindgarh, Fatehgarh Sahib, Punjab, India,
A study of Video Response Spam Detection on YouTube
 A study of Video Response Spam Detection on YouTube Suman 1 and Vipin Arora 2 1 Research Scholar, Department of CSE, BITS, Bhiwani, Haryana (India) 2 Asst. Prof., Department of CSE, BITS, Bhiwani, Haryana
A study of Video Response Spam Detection on YouTube Suman 1 and Vipin Arora 2 1 Research Scholar, Department of CSE, BITS, Bhiwani, Haryana (India) 2 Asst. Prof., Department of CSE, BITS, Bhiwani, Haryana
Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection White Paper September 2017 www.cyren.com 1 White Paper September 2017 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
Fighting Spam, Phishing and Malware With Recurrent Pattern Detection White Paper September 2017 www.cyren.com 1 White Paper September 2017 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
GFI product comparison: GFI MailEssentials vs. Trend Micro ScanMail Suite for Microsoft Exchange
 GFI product comparison: GFI MailEssentials vs. Trend Micro ScanMail Suite for Microsoft Exchange Features GFI MailEssentials Trend Micro ScanMail Suite for Microsoft Exchange Integrates with Microsoft
GFI product comparison: GFI MailEssentials vs. Trend Micro ScanMail Suite for Microsoft Exchange Features GFI MailEssentials Trend Micro ScanMail Suite for Microsoft Exchange Integrates with Microsoft
Ethical Hacking and. Version 6. Spamming
 Ethical Hacking and Countermeasures Version 6 Module XL Spamming News Source: http://www.nzherald.co.nz/ Module Objective This module will familiarize you with: Spamming Techniques used by Spammers How
Ethical Hacking and Countermeasures Version 6 Module XL Spamming News Source: http://www.nzherald.co.nz/ Module Objective This module will familiarize you with: Spamming Techniques used by Spammers How
WITH INTEGRITY
 EMAIL WITH INTEGRITY Reaching for inboxes in a world of spam a white paper by: www.oprius.com Table of Contents... Introduction 1 Defining Spam 2 How Spam Affects Your Earnings 3 Double Opt-In Versus Single
EMAIL WITH INTEGRITY Reaching for inboxes in a world of spam a white paper by: www.oprius.com Table of Contents... Introduction 1 Defining Spam 2 How Spam Affects Your Earnings 3 Double Opt-In Versus Single
Comodo Antispam Gateway Software Version 2.12
 Comodo Antispam Gateway Software Version 2.12 User Guide Guide Version 2.12.112017 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Antispam Gateway...3
Comodo Antispam Gateway Software Version 2.12 User Guide Guide Version 2.12.112017 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Antispam Gateway...3
Comodo Comodo Dome Antispam MSP Software Version 2.12
 Comodo Comodo Dome Antispam MSP Software Version 2.12 User Guide Guide Version 2.12.111517 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Dome
Comodo Comodo Dome Antispam MSP Software Version 2.12 User Guide Guide Version 2.12.111517 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Dome
2 User Guide. Contents
 E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
Image Spam. Introduction. Project description:
 Image Spam Introduction Image spam is a kind of E-mail spam where the message text of the spam is presented as a picture in an image file. Since most modern graphical E-mail client software will render
Image Spam Introduction Image spam is a kind of E-mail spam where the message text of the spam is presented as a picture in an image file. Since most modern graphical E-mail client software will render
Binarytech Digital Education Karta Allahabad ( Notes)
 Email Email is a service which allows us to send the message in electronic mode over the internet. It offers an efficient, inexpensive and real time mean of distributing information among people. E-Mail
Email Email is a service which allows us to send the message in electronic mode over the internet. It offers an efficient, inexpensive and real time mean of distributing information among people. E-Mail
November 2009 Report #35
 November 2009 Report #35 In October 2009, spam volumes made up 87 percent of all email messages. The most notable highlight this month is the growth of spam originating from APJ (23 percent) and South
November 2009 Report #35 In October 2009, spam volumes made up 87 percent of all email messages. The most notable highlight this month is the growth of spam originating from APJ (23 percent) and South
Jacksonville State University Acceptable Use Policy 1. Overview 2. Purpose 3. Scope
 Jacksonville State University Acceptable Use Policy 1. Overview Information Technology s (IT) intentions for publishing an Acceptable Use Policy are not to impose restrictions that are contrary to Jacksonville
Jacksonville State University Acceptable Use Policy 1. Overview Information Technology s (IT) intentions for publishing an Acceptable Use Policy are not to impose restrictions that are contrary to Jacksonville
DONE FOR YOU SAMPLE INTERNET ACCEPTABLE USE POLICY
 DONE FOR YOU SAMPLE INTERNET ACCEPTABLE USE POLICY Published By: Fusion Factor Corporation 2647 Gateway Road Ste 105-303 Carlsbad, CA 92009 USA 1.0 Overview Fusion Factor s intentions for publishing an
DONE FOR YOU SAMPLE INTERNET ACCEPTABLE USE POLICY Published By: Fusion Factor Corporation 2647 Gateway Road Ste 105-303 Carlsbad, CA 92009 USA 1.0 Overview Fusion Factor s intentions for publishing an
Classifying and Predicting Spam Messages Using Text Mining in SAS Enterprise Miner Session ID: 2650
 Classifying and Predicting Spam Messages Using Text Mining in SAS Enterprise Miner Session ID: 2650 Mounika Kondamudi, Oklahoma State University Mentored by Balamurugan Mohan, H&R Block SAS and all other
Classifying and Predicting Spam Messages Using Text Mining in SAS Enterprise Miner Session ID: 2650 Mounika Kondamudi, Oklahoma State University Mentored by Balamurugan Mohan, H&R Block SAS and all other
Library. Summary Report
 Library Summary Report 217-218 Prepared by: Library Staff December 218 Table of Contents Introduction..1 New Books.2 Print Circulation.3 Interlibrary Loan 4 Information Literacy 5 Reference Statistics.6
Library Summary Report 217-218 Prepared by: Library Staff December 218 Table of Contents Introduction..1 New Books.2 Print Circulation.3 Interlibrary Loan 4 Information Literacy 5 Reference Statistics.6
IT User accounts. IT resources for McGill students. McGill ID ( a 9 digit number) Minerva PIN - (yymmdd) First time login to Minerva
 IT resources for McGill students IT User accounts First time login to Minerva McGill ID - 260123456 ( a 9 digit number) Minerva PIN - (yymmdd) Will be prompted to change the initial Minerva PIN 1 IT User
IT resources for McGill students IT User accounts First time login to Minerva McGill ID - 260123456 ( a 9 digit number) Minerva PIN - (yymmdd) Will be prompted to change the initial Minerva PIN 1 IT User
MARKETING VOL. 1
 EMAIL MARKETING VOL. 1 TITLE: Email Promoting: What You Need To Do Author: Iris Carter-Collins Table Of Contents 1 Email Promoting: What You Need To Do 4 Building Your Business Through Successful Marketing
EMAIL MARKETING VOL. 1 TITLE: Email Promoting: What You Need To Do Author: Iris Carter-Collins Table Of Contents 1 Email Promoting: What You Need To Do 4 Building Your Business Through Successful Marketing
News English.com Ready-to-use ESL / EFL Lessons
 www.breaking News English.com Ready-to-use ESL / EFL Lessons 1,000 IDEAS & ACTIVITIES FOR LANGUAGE TEACHERS The Breaking News English.com Resource Book http://www.breakingnewsenglish.com/book.html Top
www.breaking News English.com Ready-to-use ESL / EFL Lessons 1,000 IDEAS & ACTIVITIES FOR LANGUAGE TEACHERS The Breaking News English.com Resource Book http://www.breakingnewsenglish.com/book.html Top
CS294-1 Final Project. Algorithms Comparison
 CS294-1 Final Project Algorithms Comparison Deep Learning Neural Network AdaBoost Random Forest Prepared By: Shuang Bi (24094630) Wenchang Zhang (24094623) 2013-05-15 1 INTRODUCTION In this project, we
CS294-1 Final Project Algorithms Comparison Deep Learning Neural Network AdaBoost Random Forest Prepared By: Shuang Bi (24094630) Wenchang Zhang (24094623) 2013-05-15 1 INTRODUCTION In this project, we
Interim Report Technical Support for Integrated Library Systems Comparison of Open Source and Proprietary Software
 Interim Report Technical Support for Integrated Library Systems Comparison of Open Source and Proprietary Software Vandana Singh Assistant Professor, School of Information Science, University of Tennessee,
Interim Report Technical Support for Integrated Library Systems Comparison of Open Source and Proprietary Software Vandana Singh Assistant Professor, School of Information Science, University of Tennessee,
GFI product comparison: GFI MailEssentials vs Symantec Mail Security for Microsoft Exchange 7.5
 GFI product comparison: GFI MailEssentials vs Symantec Mail Security for Microsoft Exchange 7.5 Features GFI MailEssentials Symantec Mail Security for Microsoft Exchange 7.5 Integrates with Microsoft Exchange
GFI product comparison: GFI MailEssentials vs Symantec Mail Security for Microsoft Exchange 7.5 Features GFI MailEssentials Symantec Mail Security for Microsoft Exchange 7.5 Integrates with Microsoft Exchange
Comparative analysis of classifiers for header based s classification using supervised learning
 Comparative analysis of classifiers for header based emails classification using supervised learning Priti Kulkarni 1, Dr. Haridas Acharya 2 1Assistant Professor, Symbiosis Institute of Computer Studies
Comparative analysis of classifiers for header based emails classification using supervised learning Priti Kulkarni 1, Dr. Haridas Acharya 2 1Assistant Professor, Symbiosis Institute of Computer Studies
Collaborative Filtering
 Collaborative E-Mail Filtering by Doug Herbers B.S. Computer Engineering, University of Kansas, 2002 Submitted to the Department of Electrical Engineering and Computer Science and the Faculty of the Graduate
Collaborative E-Mail Filtering by Doug Herbers B.S. Computer Engineering, University of Kansas, 2002 Submitted to the Department of Electrical Engineering and Computer Science and the Faculty of the Graduate
ATTACHMENTS, INSERTS, AND LINKS...
 Conventions used in this document: Keyboard keys that must be pressed will be shown as Enter or Ctrl. Objects to be clicked on with the mouse will be shown as Icon or. Cross Reference Links will be shown
Conventions used in this document: Keyboard keys that must be pressed will be shown as Enter or Ctrl. Objects to be clicked on with the mouse will be shown as Icon or. Cross Reference Links will be shown
Spam Classification Documentation
 Spam Classification Documentation What is SPAM? Unsolicited, unwanted email that was sent indiscriminately, directly or indirectly, by a sender having no current relationship with the recipient. Objective:
Spam Classification Documentation What is SPAM? Unsolicited, unwanted email that was sent indiscriminately, directly or indirectly, by a sender having no current relationship with the recipient. Objective:
A quick guide to... Permission: Single or Double Opt-in?
 A quick guide to... Permission: Single or Double Opt-in? In this guide... Learn how to improve campaign results by sending new contacts a confirmation email to verify their intention to join. Table of
A quick guide to... Permission: Single or Double Opt-in? In this guide... Learn how to improve campaign results by sending new contacts a confirmation email to verify their intention to join. Table of
August 2009 Report #32
 August 2009 Report #32 While overall spam volumes averaged 89 percent of all email messages in July 2009, spam volumes continue to fluctuate. During July 2009, image spam continued to have an impact reaching
August 2009 Report #32 While overall spam volumes averaged 89 percent of all email messages in July 2009, spam volumes continue to fluctuate. During July 2009, image spam continued to have an impact reaching
Self-tuning ongoing terminology extraction retrained on terminology validation decisions
 Self-tuning ongoing terminology extraction retrained on terminology validation decisions Alfredo Maldonado and David Lewis ADAPT Centre, School of Computer Science and Statistics, Trinity College Dublin
Self-tuning ongoing terminology extraction retrained on terminology validation decisions Alfredo Maldonado and David Lewis ADAPT Centre, School of Computer Science and Statistics, Trinity College Dublin
Marketing 101. Mellissa Lee
 Email Marketing 101 Mellissa Lee Introduction to GetResponse video Building a List An average email list degrades about 23% every year. Tip #1 Search Engine Optimization (SEO) One of the most effective
Email Marketing 101 Mellissa Lee Introduction to GetResponse video Building a List An average email list degrades about 23% every year. Tip #1 Search Engine Optimization (SEO) One of the most effective
June 2009 Report #30
 June 2009 Report #30 The McColo shutdown is all but a distant memory with spam levels in May 2009 at approximately 90 percent of all email consistent with the levels observed one year ago in May 2008.
June 2009 Report #30 The McColo shutdown is all but a distant memory with spam levels in May 2009 at approximately 90 percent of all email consistent with the levels observed one year ago in May 2008.
Comodo Antispam Gateway Software Version 2.11
 Comodo Antispam Gateway Software Version 2.11 User Guide Guide Version 2.11.041917 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Antispam Gateway...3
Comodo Antispam Gateway Software Version 2.11 User Guide Guide Version 2.11.041917 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Antispam Gateway...3
Naïve Bayes Classifiers. Jonathan Lee and Varun Mahadevan
 Naïve Bayes Classifiers Jonathan Lee and Varun Mahadevan Programming Project: Spam Filter Due: Thursday, November 10, 11:59pm Implement the Naive Bayes classifier for classifying emails as either spam
Naïve Bayes Classifiers Jonathan Lee and Varun Mahadevan Programming Project: Spam Filter Due: Thursday, November 10, 11:59pm Implement the Naive Bayes classifier for classifying emails as either spam
SMS Price List (W.E.F. 1 st April 2018) A. Transactional SMS # Particulars & Description SMS Qty. Total Price (In Rs.) TAX
 SMS Price List (W.E.F. 1 st April 2018) A. Transactional SMS # Particulars & Description SMS Qty. Total Price (In Rs.) TAX 1 Transactional SMS (With Sender ID) 5,00,000 52,000.00 2 Transactional SMS (With
SMS Price List (W.E.F. 1 st April 2018) A. Transactional SMS # Particulars & Description SMS Qty. Total Price (In Rs.) TAX 1 Transactional SMS (With Sender ID) 5,00,000 52,000.00 2 Transactional SMS (With
Guidelines for Account Management and Effective Usage
 Guidelines for E-mail Account Management and Effective E-mail Usage June 2018 Version 1.1 Ministry of Electronics and Information Technology Government of India New Delhi 110003 Page 1 of 13 Table of Contents
Guidelines for E-mail Account Management and Effective E-mail Usage June 2018 Version 1.1 Ministry of Electronics and Information Technology Government of India New Delhi 110003 Page 1 of 13 Table of Contents
A Kosher Source of Ham
 A Kosher Source of Ham Nathan Friess John Aycock Department of Computer Science University of Calgary Canada Building A Ham Corpus Hard To Publish Samples Copyright Issues Privacy Issues Some Goals Realistic
A Kosher Source of Ham Nathan Friess John Aycock Department of Computer Science University of Calgary Canada Building A Ham Corpus Hard To Publish Samples Copyright Issues Privacy Issues Some Goals Realistic
An Ensembled Classifier for Spam Classification in Hadoop Environment
 Appl. Math. Inf. Sci. 11, No. 4, 1123-1128 (2017) 1123 Applied Mathematics & Information Sciences An International Journal http://dx.doi.org/10.18576/amis/110419 An Ensembled Classifier for Email Spam
Appl. Math. Inf. Sci. 11, No. 4, 1123-1128 (2017) 1123 Applied Mathematics & Information Sciences An International Journal http://dx.doi.org/10.18576/amis/110419 An Ensembled Classifier for Email Spam
Cleveland State University General Policy for University Information and Technology Resources
 Cleveland State University General Policy for University Information and Technology Resources 08/13/2007 1 Introduction As an institution of higher learning, Cleveland State University both uses information
Cleveland State University General Policy for University Information and Technology Resources 08/13/2007 1 Introduction As an institution of higher learning, Cleveland State University both uses information
An approach for Malicious Spam Detection In with comparison of different classifiers
 An approach for Malicious Spam Detection In Email with comparison of different classifiers Umesh Kumar Sah 1,Narendra Parmar 2 1M.Tech Scholar, 2 Assistant Professor, 1,2 Sri Satya Sai College of Engineering,
An approach for Malicious Spam Detection In Email with comparison of different classifiers Umesh Kumar Sah 1,Narendra Parmar 2 1M.Tech Scholar, 2 Assistant Professor, 1,2 Sri Satya Sai College of Engineering,
Best Customer Services among the E-Commerce Websites A Predictive Analysis
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN: 2319-7242 Volume 5 Issues 6 June 2016, Page No. 17088-17095 Best Customer Services among the E-Commerce Websites A Predictive
www.ijecs.in International Journal Of Engineering And Computer Science ISSN: 2319-7242 Volume 5 Issues 6 June 2016, Page No. 17088-17095 Best Customer Services among the E-Commerce Websites A Predictive
Product Guide Revision A. McAfee Customer Submission Tool 2.4.0
 Product Guide Revision A McAfee Customer Submission Tool 2.4.0 COPYRIGHT Copyright 2016 McAfee, Inc., 2821 Mission College Boulevard, Santa Clara, CA 95054, 1.888.847.8766, www.intelsecurity.com TRADEMARK
Product Guide Revision A McAfee Customer Submission Tool 2.4.0 COPYRIGHT Copyright 2016 McAfee, Inc., 2821 Mission College Boulevard, Santa Clara, CA 95054, 1.888.847.8766, www.intelsecurity.com TRADEMARK
Introduction This paper will discuss the best practices for stopping the maximum amount of SPAM arriving in a user's inbox. It will outline simple
 Table of Contents Introduction...2 Overview...3 Common techniques to identify SPAM...4 Greylisting...5 Dictionary Attack...5 Catchalls...5 From address...5 HELO / EHLO...6 SPF records...6 Detecting SPAM...6
Table of Contents Introduction...2 Overview...3 Common techniques to identify SPAM...4 Greylisting...5 Dictionary Attack...5 Catchalls...5 From address...5 HELO / EHLO...6 SPF records...6 Detecting SPAM...6
In this project, I examined methods to classify a corpus of s by their content in order to suggest text blocks for semi-automatic replies.
 December 13, 2006 IS256: Applied Natural Language Processing Final Project Email classification for semi-automated reply generation HANNES HESSE mail 2056 Emerson Street Berkeley, CA 94703 phone 1 (510)
December 13, 2006 IS256: Applied Natural Language Processing Final Project Email classification for semi-automated reply generation HANNES HESSE mail 2056 Emerson Street Berkeley, CA 94703 phone 1 (510)
An Experimental Evaluation of Spam Filter Performance and Robustness Against Attack
 An Experimental Evaluation of Spam Filter Performance and Robustness Against Attack Steve Webb, Subramanyam Chitti, and Calton Pu {webb, chittis, calton}@cc.gatech.edu College of Computing Georgia Institute
An Experimental Evaluation of Spam Filter Performance and Robustness Against Attack Steve Webb, Subramanyam Chitti, and Calton Pu {webb, chittis, calton}@cc.gatech.edu College of Computing Georgia Institute
Content Based Spam Filtering
 2016 International Conference on Collaboration Technologies and Systems Content Based Spam E-mail Filtering 2nd Author Pingchuan Liu and Teng-Sheng Moh Department of Computer Science San Jose State University
2016 International Conference on Collaboration Technologies and Systems Content Based Spam E-mail Filtering 2nd Author Pingchuan Liu and Teng-Sheng Moh Department of Computer Science San Jose State University
Online Scams. Ready to get started? Click on the green button to continue.
 Online Scams Hi, I m Kate. We re here to learn how to protect ourselves from online scams. We ll follow along with Kevin to learn what types of scams are out there, how to recognize the warning signs,
Online Scams Hi, I m Kate. We re here to learn how to protect ourselves from online scams. We ll follow along with Kevin to learn what types of scams are out there, how to recognize the warning signs,
Karami, A., Zhou, B. (2015). Online Review Spam Detection by New Linguistic Features. In iconference 2015 Proceedings.
 Online Review Spam Detection by New Linguistic Features Amir Karam, University of Maryland Baltimore County Bin Zhou, University of Maryland Baltimore County Karami, A., Zhou, B. (2015). Online Review
Online Review Spam Detection by New Linguistic Features Amir Karam, University of Maryland Baltimore County Bin Zhou, University of Maryland Baltimore County Karami, A., Zhou, B. (2015). Online Review
Franzes Francisco Manila IBM Domino Server Crash and Messaging
 Franzes Francisco Manila IBM Domino Server Crash and Messaging Topics to be discussed What is SPAM / email Spoofing? How to identify one? Anti-SPAM / Anti-email spoofing basic techniques Domino configurations
Franzes Francisco Manila IBM Domino Server Crash and Messaging Topics to be discussed What is SPAM / email Spoofing? How to identify one? Anti-SPAM / Anti-email spoofing basic techniques Domino configurations
TABLE OF CONTENTS CHAPTER 1: INTRODUCTION TO THE INTERNET & WEB BROWSERS 1
 TABLE OF CONTENTS CHAPTER 1: INTRODUCTION TO THE INTERNET & WEB BROWSERS 1 WHAT IS THE INTERNET 1 WEB BROWSERS 1 Title Bar 2 Address Bar 3 Menu Bar 3 Saving Web Pages 4 Downloading Web Pages 5 Printing
TABLE OF CONTENTS CHAPTER 1: INTRODUCTION TO THE INTERNET & WEB BROWSERS 1 WHAT IS THE INTERNET 1 WEB BROWSERS 1 Title Bar 2 Address Bar 3 Menu Bar 3 Saving Web Pages 4 Downloading Web Pages 5 Printing
You can purchase directly through our online store.
 atmail cloud FAQ Last updated 31 October 2017 QUESTION SALES How do I contact atmail Sales? What does an atmail cloud licence include? Please complete the Contact Us form on our site to contact our sales
atmail cloud FAQ Last updated 31 October 2017 QUESTION SALES How do I contact atmail Sales? What does an atmail cloud licence include? Please complete the Contact Us form on our site to contact our sales
Use and Abuse of Anti-Spam White/Black Lists
 Page 1 of 5 Use and Abuse of Anti-Spam White/Black Lists September 26, 2006 White and Black lists are standard spam filters. Their typically simple interface, provide a way to quickly identify emails as
Page 1 of 5 Use and Abuse of Anti-Spam White/Black Lists September 26, 2006 White and Black lists are standard spam filters. Their typically simple interface, provide a way to quickly identify emails as
Find Your Perfect Plan
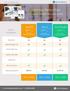 http://www.cpa Call Us: 800.896.4500 Site Solutions.com/_responsive/images/hero/search-engine-optimization-feature.png Find Your Perfect Plan No setup fee. No hidden fees. Cancel anytime. Service Comparison
http://www.cpa Call Us: 800.896.4500 Site Solutions.com/_responsive/images/hero/search-engine-optimization-feature.png Find Your Perfect Plan No setup fee. No hidden fees. Cancel anytime. Service Comparison
Cooper Press. Q Media Kit. JavaScript Weekly Ruby Weekly HTML5 Weekly Node Weekly StatusCode Dart Weekly Postgres Weekly
 Q2 2014 Media Kit JavaScript Weekly Ruby Weekly HTML5 Weekly Node Weekly StatusCode Dart Weekly Postgres Weekly This revision: January 23, 2014 Note: Please contact us if any information you require is
Q2 2014 Media Kit JavaScript Weekly Ruby Weekly HTML5 Weekly Node Weekly StatusCode Dart Weekly Postgres Weekly This revision: January 23, 2014 Note: Please contact us if any information you require is
Canadian Anti-Spam Legislation (CASL) FREQUENTLY ASKED QUESTIONS
 Canadian Anti-Spam Legislation (CASL) FREQUENTLY ASKED QUESTIONS 1. General Questions 1.1 What is the Canadian Anti-Spam Legislation? The primary purpose of the Canadian Anti-Spam Legislation (called CASL;
Canadian Anti-Spam Legislation (CASL) FREQUENTLY ASKED QUESTIONS 1. General Questions 1.1 What is the Canadian Anti-Spam Legislation? The primary purpose of the Canadian Anti-Spam Legislation (called CASL;
