I never signed up for this!
|
|
|
- Lucy McCoy
- 5 years ago
- Views:
Transcription
1 I never signed up for this! Privacy implications of tracking Steven senglehardt.com I m now at... Joint work with: Jeffrey Han and Arvind Narayanan
2
3
4 Many s are completely unreadable without remote content!
5 Remote content enabled What are the privacy implications?
6
7 s are tracked far beyond send tracking
8 Your device contacts 24 companies 20 can track you (if supported) 10 receive an MD5 hash of your address Sets a Cookie Receives MD5( address) & Sets a Cookie American List Counsel (alcmpn.com) LiveIntent (liadm.com) Oracle (nexac.com) Acxiom (rlcdn.com, pippio.com, acxiom-online.com) Criteo (criteo.com) Conversant Media (dotomi.com) V12 Data (v12group.com) VideoAmp (videoamp.com) <Unknown> (alocdn.com) OpenX (openx.net) comscore (scorecardresearch.com, voicefive.com) Oracle (bluekai.com) Google (doubleclick.net) Realtime Targeting Aps (mojn.com) Receives MD5( addr.) Criteo ( retargeting.com) Neustar (agkn.com) MediaMath (mathtag.com) TapAd (tapad.com) IPONWEB (bidswitch.net) AOL (advertising.com) Centro (sitescout.com) The Trade Desk (adsrvr.org) Adobe (demdex.net) Receives Bare Request LiveIntent (licasd.com) Google (2mdn.net) Akamai (akamai.net)
9 A user s address is the perfect identifier! PII-based tracking It s unique UUID = { It rarely changes It s the same across devices Consumers freely provide it to stores There s a lot of associated data MD5(bob@example.com), SHA1(bob@example.com), SHA256(bob@example.com) }
10 Why hashed addresses? User privacy! LiveIntent Privacy Policy Source: To de-identify this information, either we or our business partners [hash it]. Criteo Privacy Policy Source: we use a double hashing method... to ensure the non-reversibility of your information. A hash of your corresponds to a series of characters that does not permit your identification.
11 Maybe hashing isn t so effective at protecting users... More on this: ses/
12 Methods
13 Challenge: Measurements require the automated submission of PII to sites Mailing list sign-ups Login Forms
14 Measuring tracking at scale 1. Crawled 15,700 sites 2. Signed up for mailing lists 3. Received 13,000 s from ~900 sites 4. Measured tracking with OpenWPM
15 Web - Javascript Tracking Tracking
16 Our Findings
17 Many of the top web trackers are in s 85% of s embed third parties (with an average of 5 per )
18 29% of s ( from 19% of senders) leak the address to third parties
19 A sample leak: 12 redirects in a single image tag
20 Trackers can correlate and web tracking
21 Ongoing research: trackers also harvest addresses from the web
22 Is identity-based marketing the future? The top collectors all sell identity-based marketing. Allowing advertisers to reach individuals on any device and connect with individual purchase data and other offline data.
23 Defenses
24
25 Tracking defenses are incomplete Block cookies Prevents PII leaks from being connected to tracking cookies Doesn t prevent linkage of PII to IP address / passive fingerprint Proxy image requests Prevents linkage of PII to cookies, IP, and fingerprint Doesn t prevent targeted advertising / data collection Block images Prevents tracking, but many s are unreadable
26 Ad blockers help, but don t fully protect users Nearly half of the recipients of leaked addresses are blocked (from 99 to 51) The number of senders leaking addresses drops from 19% to 7% Filtering requests with EasyList + EasyPrivacy...they also aren t available on all platforms
27 Our proposal: Filtering at the service provider level <html> <p>hello there!</p> <img src= example.com/mailinglist.png > <img src= tracker.com/pixel.gif > <p>buy our products</p> </html> Performs almost as well as client-side filtering; misses redirects
28 Our proposal: Filtering at the service provider level Server-side filtering using blocklists <html> <p>hello there!</p> <img src= example.com/mailinglist.png > <img src= tracker.com/pixel.gif > <p>buy our products</p> </html> <html> <p>hello there!</p> <img src= example.com/mailinglist.png > <p>buy our products</p> </html> Performs almost as well as client-side filtering; misses redirects
29 Takeaways
30 Takeaways 1. The line between tracking/marketing and web tracking is blurry 2. We need better tracking defenses. a. Is measurement + filtering the only path forward? 3. A budding industry is building around tracking with hashed identifiers a. Hard to block and control. Is policy the only solution? Data + Code: Paper: This research was funded by NSF grant CNS , by a research grant from Mozilla, and by an Amazon AWS Cloud Credits for Research grant.
Characterizing the Use of Browser- Based Blocking Extensions To Prevent Online Tracking
 Characterizing the Use of Browser- Based Blocking Extensions To Prevent Online Arunesh Mathur @aruneshmathur with Jessica Vitak, Arvind Narayanan, and Marshini Chetty Online The New York Times The Telegraph
Characterizing the Use of Browser- Based Blocking Extensions To Prevent Online Arunesh Mathur @aruneshmathur with Jessica Vitak, Arvind Narayanan, and Marshini Chetty Online The New York Times The Telegraph
How Tracking Companies Circumvented Ad Blockers Using WebSockets
 How Tracking Companies Circumvented Ad Blockers Using WebSockets Muhammad Ahmad Bashir, Sajjad Arshad, Engin Kirda, William Robertson, Christo Wilson Northeastern University Online Tracking 2 Online Tracking
How Tracking Companies Circumvented Ad Blockers Using WebSockets Muhammad Ahmad Bashir, Sajjad Arshad, Engin Kirda, William Robertson, Christo Wilson Northeastern University Online Tracking 2 Online Tracking
Detailed User Activity 1
 Detailed User Activity 1 REDACTED Google Services OCSP Protocol Google Analytics image2.pubmatic.com/adserver/pug Google Ads DNS Protocol Web Browsing Google Search MSN-web REDACTED 507,678 346,945 284,521
Detailed User Activity 1 REDACTED Google Services OCSP Protocol Google Analytics image2.pubmatic.com/adserver/pug Google Ads DNS Protocol Web Browsing Google Search MSN-web REDACTED 507,678 346,945 284,521
Definition. Quantifying Anonymity. Anonymous Communication. How can we calculate how anonymous we are? Who you are from the communicating party
 Definition Anonymous Communication Hiding identities of parties involved in communications from each other, or from third-parties Who you are from the communicating party Who you are talking to from everyone
Definition Anonymous Communication Hiding identities of parties involved in communications from each other, or from third-parties Who you are from the communicating party Who you are talking to from everyone
Anonymous communications: Crowds and Tor
 Anonymous communications: Crowds and Tor Basic concepts What do we want to hide? sender anonymity attacker cannot determine who the sender of a particular message is receiver anonymity attacker cannot
Anonymous communications: Crowds and Tor Basic concepts What do we want to hide? sender anonymity attacker cannot determine who the sender of a particular message is receiver anonymity attacker cannot
How Tracking Companies Circumvented Ad Blockers Using WebSockets
 How Tracking Companies Circumvented Ad Blockers Using WebSockets Muhammad Ahmad Bashir, Sajjad Arshad, Engin Kirda, William Robertson, Christo Wilson Northeastern University Online Tracking 2 Online Tracking
How Tracking Companies Circumvented Ad Blockers Using WebSockets Muhammad Ahmad Bashir, Sajjad Arshad, Engin Kirda, William Robertson, Christo Wilson Northeastern University Online Tracking 2 Online Tracking
Detailed User Activity 1
 Detailed User Activity 1 REDACTED OCSP Protocol ctldl.windowsupdate.com Google Services msftncsi.com Google Ads MSN-web Google Analytics Google Search RSS BBC News 819 416 321 289 267 189 189 167 154 135
Detailed User Activity 1 REDACTED OCSP Protocol ctldl.windowsupdate.com Google Services msftncsi.com Google Ads MSN-web Google Analytics Google Search RSS BBC News 819 416 321 289 267 189 189 167 154 135
Doing it for FREE Online
 Here s to the crazy ones. The rebels. The troublemakers. The ones who see things differently. While some may see them as the crazy ones, we see genius. Because the people who are crazy enough to think
Here s to the crazy ones. The rebels. The troublemakers. The ones who see things differently. While some may see them as the crazy ones, we see genius. Because the people who are crazy enough to think
Tracking the Trackers: Analysing the global tracking landscape with GhostRank
 Tracking the Trackers: Analysing the global tracking landscape with GhostRank Sam Macbeth Cliqz GmbH, https://cliqz.com July 2017 1 Introduction In April 2016 we published our innovative
Tracking the Trackers: Analysing the global tracking landscape with GhostRank Sam Macbeth Cliqz GmbH, https://cliqz.com July 2017 1 Introduction In April 2016 we published our innovative
Tenable.io User Guide. Last Revised: November 03, 2017
 Tenable.io User Guide Last Revised: November 03, 2017 Table of Contents Tenable.io User Guide 1 Getting Started with Tenable.io 10 Tenable.io Workflow 12 System Requirements 15 Scanners and Agents 16 Link
Tenable.io User Guide Last Revised: November 03, 2017 Table of Contents Tenable.io User Guide 1 Getting Started with Tenable.io 10 Tenable.io Workflow 12 System Requirements 15 Scanners and Agents 16 Link
Do-It-Yourself Guide for Advertisers
 Do-It-Yourself Guide for Advertisers Foreword Affinity's Advertiser DIY Guide is intended to provide Advertisers with helpful insights on how to best run their ad campaigns on the Affinity Ad Platform.
Do-It-Yourself Guide for Advertisers Foreword Affinity's Advertiser DIY Guide is intended to provide Advertisers with helpful insights on how to best run their ad campaigns on the Affinity Ad Platform.
Beyond Blind Defense: Gaining Insights from Proactive App Sec
 Beyond Blind Defense: Gaining Insights from Proactive App Sec Speaker Rami Essaid CEO Distil Networks Blind Defense Means Trusting Half Your Web Traffic 46% of Web Traffic is Bots Source: Distil Networks
Beyond Blind Defense: Gaining Insights from Proactive App Sec Speaker Rami Essaid CEO Distil Networks Blind Defense Means Trusting Half Your Web Traffic 46% of Web Traffic is Bots Source: Distil Networks
Privacy Policy
 http://simplewishesnorth.com/ Privacy Policy This privacy policy has been compiled to better serve those who are concerned with how their Personally identi able information (PII) is being used online.
http://simplewishesnorth.com/ Privacy Policy This privacy policy has been compiled to better serve those who are concerned with how their Personally identi able information (PII) is being used online.
How to make Secure Easier to use
 How to make Secure Email Easier to use Simson L. Garfinkel (MIT) Jeffrey I. Schiller (MIT) Erik Nordlander (MIT) David Margrave (Amazon) Robert C. Miller (MIT) http://www.simson.net/smime-survey.html/
How to make Secure Email Easier to use Simson L. Garfinkel (MIT) Jeffrey I. Schiller (MIT) Erik Nordlander (MIT) David Margrave (Amazon) Robert C. Miller (MIT) http://www.simson.net/smime-survey.html/
Digital Marketing, Privacy, and New Technologies. Jules Polonetsky, CEO Future of Privacy Forum
 Digital Marketing, Privacy, and New Technologies Jules Polonetsky, CEO Future of Privacy Forum 9.26.17 Future of Privacy Forum The Members 140+ Companies 25+ Leading Academics 10+ Advocates The Mission
Digital Marketing, Privacy, and New Technologies Jules Polonetsky, CEO Future of Privacy Forum 9.26.17 Future of Privacy Forum The Members 140+ Companies 25+ Leading Academics 10+ Advocates The Mission
Appendix: List of possible compliance measures. Note:
 Ref. Ares(2014)3113072-23/09/2014 Appendix: List of possible compliance measures Note: In order to guide Google in the implementation of the legal requirements regarding data protection, the Article 29
Ref. Ares(2014)3113072-23/09/2014 Appendix: List of possible compliance measures Note: In order to guide Google in the implementation of the legal requirements regarding data protection, the Article 29
How to use Fusioncoin Wallet
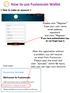 How to use Fusioncoin Wallet < How to make an account > Please click Register Type your user name, email address, password and click Register If you have authentication key, do not forget type it. (Email
How to use Fusioncoin Wallet < How to make an account > Please click Register Type your user name, email address, password and click Register If you have authentication key, do not forget type it. (Email
Is Browsing Safe? Web Browser Security. Subverting the Browser. Browser Security Model. XSS / Script Injection. 1. XSS / Script Injection
 Is Browsing Safe? Web Browser Security Charlie Reis Guest Lecture - CSE 490K - 5/24/2007 Send Spam Search Results Change Address? Install Malware Web Mail Movie Rentals 2 Browser Security Model Pages are
Is Browsing Safe? Web Browser Security Charlie Reis Guest Lecture - CSE 490K - 5/24/2007 Send Spam Search Results Change Address? Install Malware Web Mail Movie Rentals 2 Browser Security Model Pages are
Parks Industries LLC Privacy Policy
 Parks Industries LLC Privacy Policy We collect the following types of information about you: Information you provide us directly: We ask for certain information such as your username, real name, birthdate,
Parks Industries LLC Privacy Policy We collect the following types of information about you: Information you provide us directly: We ask for certain information such as your username, real name, birthdate,
What is Privacy? Steven M. Bellovin February 12,
 What is Privacy? Steven M. Bellovin February 12, 2018 1 What is Privacy? Warren and Brandeis (1890): the right to be let alone (They were trying to find a legal rationale to protect privacy under then-existing
What is Privacy? Steven M. Bellovin February 12, 2018 1 What is Privacy? Warren and Brandeis (1890): the right to be let alone (They were trying to find a legal rationale to protect privacy under then-existing
Frequently Asked Questions for PRO Users
 (HTTPS://WWW.FLOSPORTS.TV/)! Frequently Asked Questions for PRO Users What are my PRO subscription options? YEARLY: With a yearly subscription, you gain access to premium content on the site you joined
(HTTPS://WWW.FLOSPORTS.TV/)! Frequently Asked Questions for PRO Users What are my PRO subscription options? YEARLY: With a yearly subscription, you gain access to premium content on the site you joined
Data Collection Document version
 Data Collection Document version 5.3 2017 Contents 1 Options for data collection 1.1 Tag Integration 1.2 Standard pixel 1.3 Accelerated Mobile Pages AMP 1.4 Mobile SDKs 1.5 Server-to-Server 2 Advanced
Data Collection Document version 5.3 2017 Contents 1 Options for data collection 1.1 Tag Integration 1.2 Standard pixel 1.3 Accelerated Mobile Pages AMP 1.4 Mobile SDKs 1.5 Server-to-Server 2 Advanced
Jake Egginton Management Ltd ( Privacy Policy
 Jake Egginton Management Ltd (www.wearejem.com) Privacy Policy This privacy policy has been compiled to better serve those who are concerned with how their 'Personally Identifiable Information' (PII) is
Jake Egginton Management Ltd (www.wearejem.com) Privacy Policy This privacy policy has been compiled to better serve those who are concerned with how their 'Personally Identifiable Information' (PII) is
Recommended Browser Settings for Self Service Applications Revised: 10/10/2013 vmc
 Recommended Browser Settings for Self Service Applications Revised: 10/10/2013 vmc This document describes the steps to configure the common web browsers for use with the City of Boise s webbased applications.
Recommended Browser Settings for Self Service Applications Revised: 10/10/2013 vmc This document describes the steps to configure the common web browsers for use with the City of Boise s webbased applications.
User Directories. Overview, Pros and Cons
 User Directories Overview, Pros and Cons Overview Secure ISMS can operate with one or more of the following user directories. Secure ISMS Users (ISMS) Internal users local to the Secure ISMS application
User Directories Overview, Pros and Cons Overview Secure ISMS can operate with one or more of the following user directories. Secure ISMS Users (ISMS) Internal users local to the Secure ISMS application
Privacy Policy
 www.hotcoldrental.com Privacy Policy This privacy policy has been compiled to better serve those who are concerned with how their 'Personally Identifiable Information' (PII) is being used online. PII,
www.hotcoldrental.com Privacy Policy This privacy policy has been compiled to better serve those who are concerned with how their 'Personally Identifiable Information' (PII) is being used online. PII,
Measurement and evaluation: Web analytics and data mining. MGMT 230 Week 10
 Measurement and evaluation: Web analytics and data mining MGMT 230 Week 10 After today s class you will be able to: Explain the types of information routinely gathered by web servers Understand how analytics
Measurement and evaluation: Web analytics and data mining MGMT 230 Week 10 After today s class you will be able to: Explain the types of information routinely gathered by web servers Understand how analytics
Content Security Policy
 About Tim Content Security Policy New Tools for Fighting XSS Pentester > 10 years Web Applications Network Security Products Exploit Research Founded Blindspot Security in 2014 Pentesting Developer Training
About Tim Content Security Policy New Tools for Fighting XSS Pentester > 10 years Web Applications Network Security Products Exploit Research Founded Blindspot Security in 2014 Pentesting Developer Training
How to use Fusioncoin Wallet
 How to use Fusioncoin Wallet < How to make an account > Please click Register Type your user name, email address, password and click Register If you have authentication key, do not forget type it. (Email
How to use Fusioncoin Wallet < How to make an account > Please click Register Type your user name, email address, password and click Register If you have authentication key, do not forget type it. (Email
Odyssey Entertainment Marketing, LLC Privacy Policy
 Odyssey Entertainment Marketing, LLC Privacy Policy We collect the following types of information about you: Information you provide us directly: We ask for certain information such as your username, real
Odyssey Entertainment Marketing, LLC Privacy Policy We collect the following types of information about you: Information you provide us directly: We ask for certain information such as your username, real
HCA Tech Note 500. HCA Cloud Account (as of 29-May-2017) Do I need a Cloud Account?
 HCA Cloud Account (as of 29-May-2017) Running on a computer in your home, HCA controls devices and executes schedules and programs. And at one time that is all there was. Everything resided in the home.
HCA Cloud Account (as of 29-May-2017) Running on a computer in your home, HCA controls devices and executes schedules and programs. And at one time that is all there was. Everything resided in the home.
Privacy. CS Computer Security Profs. Vern Paxson & David Wagner
 Privacy CS 161 - Computer Security Profs. Vern Paxson & David Wagner TAs: John Bethencourt, Erika Chin, Matthew Finifter, Cynthia Sturton, Joel Weinberger http://inst.eecs.berkeley.edu/~cs161/ March 31,
Privacy CS 161 - Computer Security Profs. Vern Paxson & David Wagner TAs: John Bethencourt, Erika Chin, Matthew Finifter, Cynthia Sturton, Joel Weinberger http://inst.eecs.berkeley.edu/~cs161/ March 31,
emetrics Study Llew Mason, Zijian Zheng, Ron Kohavi, Brian Frasca Blue Martini Software {lmason, zijian, ronnyk,
 emetrics Study Llew Mason, Zijian Zheng, Ron Kohavi, Brian Frasca Blue Martini Software {lmason, zijian, ronnyk, brianf}@bluemartini.com December 5 th 2001 2001 Blue Martini Software 1. Introduction Managers
emetrics Study Llew Mason, Zijian Zheng, Ron Kohavi, Brian Frasca Blue Martini Software {lmason, zijian, ronnyk, brianf}@bluemartini.com December 5 th 2001 2001 Blue Martini Software 1. Introduction Managers
milestoned LLP Privacy Policy p. 1 Privacy Policy
 milestoned LLP Privacy Policy p. 1 Privacy Policy milestoned LLP Privacy Policy p. 2 www.milestoned.co.uk Privacy Policy This privacy policy has been compiled to better serve those who are concerned with
milestoned LLP Privacy Policy p. 1 Privacy Policy milestoned LLP Privacy Policy p. 2 www.milestoned.co.uk Privacy Policy This privacy policy has been compiled to better serve those who are concerned with
Tolbert Family SPADE Foundation Privacy Policy
 Tolbert Family SPADE Foundation Privacy Policy We collect the following types of information about you: Information you provide us directly: We ask for certain information such as your username, real name,
Tolbert Family SPADE Foundation Privacy Policy We collect the following types of information about you: Information you provide us directly: We ask for certain information such as your username, real name,
Privacy Policy of ManualsLib App
 Privacy Policy of ManualsLib App This Application collects some Personal Data from its Users. POLICY SUMMARY Personal Data collected for the following purposes and using the following services: Access
Privacy Policy of ManualsLib App This Application collects some Personal Data from its Users. POLICY SUMMARY Personal Data collected for the following purposes and using the following services: Access
The Invisible Trail: Third- Party Tracking on the Web
 The Invisible Trail: Third- Party Tracking on the Web Franziska Roesner Assistant Professor Computer Science & Engineering University of Washington The Invisible Trail: Third- Party Tracking on the Web
The Invisible Trail: Third- Party Tracking on the Web Franziska Roesner Assistant Professor Computer Science & Engineering University of Washington The Invisible Trail: Third- Party Tracking on the Web
Onion Routing. Varun Pandey Dept. of Computer Science, Virginia Tech. CS 6204, Spring
 Onion Routing Varun Pandey Dept. of Computer Science, Virginia Tech 1 What is Onion Routing? a distributed overlay network to anonymize TCP based routing Circuit based (clients choose the circuit) Each
Onion Routing Varun Pandey Dept. of Computer Science, Virginia Tech 1 What is Onion Routing? a distributed overlay network to anonymize TCP based routing Circuit based (clients choose the circuit) Each
How Facebook knows exactly what turns you on
 How Facebook knows exactly what turns you on We have developed our anti tracking system to combat a culture of user data collection which, we believe, has gone too far. These systems operate hidden from
How Facebook knows exactly what turns you on We have developed our anti tracking system to combat a culture of user data collection which, we believe, has gone too far. These systems operate hidden from
GRANDSTREAM PRIVACY STATEMENT
 GRANDSTREAM PRIVACY STATEMENT This Privacy Statement governs how Grandstream Networks, Inc. and its affiliates ( Grandstream, us, our or we ) may collect, use, and disclose information that we obtain through
GRANDSTREAM PRIVACY STATEMENT This Privacy Statement governs how Grandstream Networks, Inc. and its affiliates ( Grandstream, us, our or we ) may collect, use, and disclose information that we obtain through
PRIVACY NOTICE INFORMATION COLLECTED
 PRIVACY NOTICE Iberian Property is responsible for the sites available at the domain iberian.property, as well as for its subdomains (collectively named websites ). Iberian Property takes the privacy and
PRIVACY NOTICE Iberian Property is responsible for the sites available at the domain iberian.property, as well as for its subdomains (collectively named websites ). Iberian Property takes the privacy and
CS 142 Winter Session Management. Dan Boneh
 CS 142 Winter 2009 Session Management Dan Boneh Sessions A sequence of requests and responses from one browser to one (or more) sites Session can be long (Gmail - two weeks) or short without session mgmt:
CS 142 Winter 2009 Session Management Dan Boneh Sessions A sequence of requests and responses from one browser to one (or more) sites Session can be long (Gmail - two weeks) or short without session mgmt:
Guide to Marketing
 Guide to Email Marketing Why Email Marketing? Isn t Email Dead? Email is not dead. In fact, it s very much alive. More and more businesses are using email as an effective form of communication, and more
Guide to Email Marketing Why Email Marketing? Isn t Email Dead? Email is not dead. In fact, it s very much alive. More and more businesses are using email as an effective form of communication, and more
WorldNow Producer. Requirements Set-up
 WorldNow Producer Requirements Set-up Table of Contents Introduction... 3 1. System Requirements... 3 2. Set-up Producer URL as a 'Trusted Site' (Internet Explorer only)... 4 3. Enable JavaScript in your
WorldNow Producer Requirements Set-up Table of Contents Introduction... 3 1. System Requirements... 3 2. Set-up Producer URL as a 'Trusted Site' (Internet Explorer only)... 4 3. Enable JavaScript in your
Robust Defenses for Cross-Site Request Forgery Review
 Robust Defenses for Cross-Site Request Forgery Review Network Security Instructor:Dr. Shishir Nagaraja Submitted By: Jyoti Leeka October 16, 2011 1 Introduction to the topic and the reason for the topic
Robust Defenses for Cross-Site Request Forgery Review Network Security Instructor:Dr. Shishir Nagaraja Submitted By: Jyoti Leeka October 16, 2011 1 Introduction to the topic and the reason for the topic
Flash Ads. Tracking Clicks with Flash Clicks using the ClickTAG
 How-to Guide to Displaying and Tracking Rich-Media/Flash Ads Image advertising varies from standard GIF, JPG, PNG to more interactive ad technologies such as Flash, or rich-media (HTML Ads). Ad Peeps can
How-to Guide to Displaying and Tracking Rich-Media/Flash Ads Image advertising varies from standard GIF, JPG, PNG to more interactive ad technologies such as Flash, or rich-media (HTML Ads). Ad Peeps can
Does Windows 10 Have Privacy Issues? February 11, Joel Ewing
 Does Windows 10 Have Privacy Issues? February 11, 2019 Joel Ewing Joel C. Ewing, Feb 2019 Permission for non-profit distribution and derivative works granted to The Bella Vista Computer Club Windows 10
Does Windows 10 Have Privacy Issues? February 11, 2019 Joel Ewing Joel C. Ewing, Feb 2019 Permission for non-profit distribution and derivative works granted to The Bella Vista Computer Club Windows 10
CUSTOMER PORTAL. Custom HTML splashpage Guide
 CUSTOMER PORTAL Custom HTML splashpage Guide 1 CUSTOM HTML Custom HTML splash page templates are intended for users who have a good knowledge of HTML, CSS and JavaScript and want to create a splash page
CUSTOMER PORTAL Custom HTML splashpage Guide 1 CUSTOM HTML Custom HTML splash page templates are intended for users who have a good knowledge of HTML, CSS and JavaScript and want to create a splash page
PRIVACY POLICY Let us summarize this for you...
 PRIVACY POLICY Let us summarize this for you... We promise to never sell your personal information. This site collects usage information to provide a better web experience for our users. If you purchase
PRIVACY POLICY Let us summarize this for you... We promise to never sell your personal information. This site collects usage information to provide a better web experience for our users. If you purchase
Web Security. Thierry Sans
 Web Security Thierry Sans 1991 Sir Tim Berners-Lee Web Portals 2014 Customer Resources Managemen Accounting and Billing E-Health E-Learning Collaboration Content Management Social Networks Publishing Web
Web Security Thierry Sans 1991 Sir Tim Berners-Lee Web Portals 2014 Customer Resources Managemen Accounting and Billing E-Health E-Learning Collaboration Content Management Social Networks Publishing Web
Browser Guide for PeopleSoft
 Browser Guide for PeopleSoft Business Process Guide For Academic Support Specialists (Advisors) TABLE OF CONTENTS PURPOSE...2 INTERNET EXPLORER 7...3 GENERAL TAB...4 SECURITY TAB...6 PRIVACY TAB...10 CONTENT
Browser Guide for PeopleSoft Business Process Guide For Academic Support Specialists (Advisors) TABLE OF CONTENTS PURPOSE...2 INTERNET EXPLORER 7...3 GENERAL TAB...4 SECURITY TAB...6 PRIVACY TAB...10 CONTENT
When do I collect information? I collect information from you when you subscribe to a newsletter, fill out a form or enter information on my site.
 Privacy Policy This privacy policy has been compiled to better serve those who are concerned with how their Personally identifiable information (PII) is being used online. PII, as used in US privacy law
Privacy Policy This privacy policy has been compiled to better serve those who are concerned with how their Personally identifiable information (PII) is being used online. PII, as used in US privacy law
Apps, Trackers, Privacy, and Regulators A Global Study of the Mobile Tracking Ecosystem
 Apps, Trackers, Privacy, and Regulators A Global Study of the Mobile Tracking Ecosystem Abbas Razaghpanah, Rishab Nithyanand, Narseo Vallina-Rodriguez, Srikanth Sundaresan, Mark Allman, Christian Kreibich,
Apps, Trackers, Privacy, and Regulators A Global Study of the Mobile Tracking Ecosystem Abbas Razaghpanah, Rishab Nithyanand, Narseo Vallina-Rodriguez, Srikanth Sundaresan, Mark Allman, Christian Kreibich,
Recipient USER GUIDE
 Recipient USER GUIDE General Information What is smartmail? smartmail is smartview s proprietary email encryption system used to protect your personal and transaction related information. What is smartportal?
Recipient USER GUIDE General Information What is smartmail? smartmail is smartview s proprietary email encryption system used to protect your personal and transaction related information. What is smartportal?
Network Security (PhD Section)
 CSE508 Network Security (PhD Section) 4/30/2015 Online Privacy and Anonymity Michalis Polychronakis Stony Brook University 1 Privacy The right of an entity (normally a person), acting in its own behalf,
CSE508 Network Security (PhD Section) 4/30/2015 Online Privacy and Anonymity Michalis Polychronakis Stony Brook University 1 Privacy The right of an entity (normally a person), acting in its own behalf,
Computer Networks. HTTP and more. Jianping Pan Spring /20/17 CSC361 1
 Computer Networks HTTP and more Jianping Pan Spring 2017 1/20/17 CSC361 1 First things first W1 due next Monday (Jan 23) submit a single PDF file through connex Noah posted a docx for for questions on
Computer Networks HTTP and more Jianping Pan Spring 2017 1/20/17 CSC361 1 First things first W1 due next Monday (Jan 23) submit a single PDF file through connex Noah posted a docx for for questions on
Security and Privacy. SWE 432, Fall 2016 Design and Implementation of Software for the Web
 Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
Overture Advertiser Workbook. Chapter 4: Tracking Your Results
 Overture Advertiser Workbook Chapter 4: Tracking Your Results Tracking Your Results TRACKING YOUR RESULTS Tracking the performance of your keywords enables you to effectively analyze your results, adjust
Overture Advertiser Workbook Chapter 4: Tracking Your Results Tracking Your Results TRACKING YOUR RESULTS Tracking the performance of your keywords enables you to effectively analyze your results, adjust
Connect-2-Everything SAML SSO (client documentation)
 Connect-2-Everything SAML SSO (client documentation) Table of Contents Summary Overview Refined tags Summary The Connect-2-Everything landing page by Refined Data allows Adobe Connect account holders to
Connect-2-Everything SAML SSO (client documentation) Table of Contents Summary Overview Refined tags Summary The Connect-2-Everything landing page by Refined Data allows Adobe Connect account holders to
1. INFORMATION WE COLLECT AND THE REASON FOR THE COLLECTION 2. HOW WE USE COOKIES AND OTHER TRACKING TECHNOLOGY TO COLLECT INFORMATION 3
 Privacy Policy Last updated on February 18, 2017. Friends at Your Metro Animal Shelter ( FAYMAS, we, our, or us ) understands that privacy is important to our online visitors to our website and online
Privacy Policy Last updated on February 18, 2017. Friends at Your Metro Animal Shelter ( FAYMAS, we, our, or us ) understands that privacy is important to our online visitors to our website and online
Dot-Tech LLC DBA Fallout-Hosting Privacy Policy
 Dot-Tech LLC DBA Fallout-Hosting Privacy Policy This privacy policy has been compiled to better serve those who are concerned with how their 'Personally Identifiable Information' (PII) is being used online.
Dot-Tech LLC DBA Fallout-Hosting Privacy Policy This privacy policy has been compiled to better serve those who are concerned with how their 'Personally Identifiable Information' (PII) is being used online.
SECTION 1 WHAT DO WE DO W ITH YOUR INFORMATION?
 Hasslefreerepartnership.com is serious about protecting your online privacy. This Privacy Statement explains our views and practices concerning privacy, and how they may pertain to you as a user of our
Hasslefreerepartnership.com is serious about protecting your online privacy. This Privacy Statement explains our views and practices concerning privacy, and how they may pertain to you as a user of our
Privacy Policy White Paper
 Published April 2014 401 Edgewater Place, Suite 600 Wakefield, MA 01880 Phone: +1 (781) 876-8933 +1 (800) 349-1070 Fax: (781) 224-1239 www.digitalanalyticsassociation.org License This work is licensed
Published April 2014 401 Edgewater Place, Suite 600 Wakefield, MA 01880 Phone: +1 (781) 876-8933 +1 (800) 349-1070 Fax: (781) 224-1239 www.digitalanalyticsassociation.org License This work is licensed
Variations in Tracking In Relation To Geographic Location
 Variations in Tracking In Relation To Geographic Location Nathaniel Fruchter Hsin Miao Scott Stevenson Rebecca Balebako W2SP 2015 The short version An empirical, automated method of measuring web tracking
Variations in Tracking In Relation To Geographic Location Nathaniel Fruchter Hsin Miao Scott Stevenson Rebecca Balebako W2SP 2015 The short version An empirical, automated method of measuring web tracking
CS Paul Krzyzanowski
 Computer Security 17. Tor & Anonymous Connectivity Anonymous Connectivity Paul Krzyzanowski Rutgers University Spring 2018 1 2 Anonymity on the Internet Often considered bad Only criminals need to hide
Computer Security 17. Tor & Anonymous Connectivity Anonymous Connectivity Paul Krzyzanowski Rutgers University Spring 2018 1 2 Anonymity on the Internet Often considered bad Only criminals need to hide
Project 2: Web Security
 EECS 388 September 30, 2016 Intro to Computer Security Project 2: Web Security Project 2: Web Security This project is due on Thursday, October 13 at 6 p.m. and counts for 8% of your course grade. Late
EECS 388 September 30, 2016 Intro to Computer Security Project 2: Web Security Project 2: Web Security This project is due on Thursday, October 13 at 6 p.m. and counts for 8% of your course grade. Late
Assignment 6: Web Security
 COS 432 November 20, 2017 Information Security Assignment 6: Web Security Assignment 6: Web Security This project is due on Monday, December 4 at 11:59 p.m.. Late submissions will be penalized by 10% per
COS 432 November 20, 2017 Information Security Assignment 6: Web Security Assignment 6: Web Security This project is due on Monday, December 4 at 11:59 p.m.. Late submissions will be penalized by 10% per
ECONOMIC DISCLOSURE STATEMENT AND AFFIDAVIT (EDS) The web link for the Online EDS is https://webapps.cityofchicago.org/edsweb
 CITY OF CHICAGO Department of Procurement Services Jamie L. Rhee, Chief Procurement Officer 121 North LaSalle Street, Room 403 Chicago, Illinois 60602-1284 ECONOMIC DISCLOSURE STATEMENT AND AFFIDAVIT (EDS)
CITY OF CHICAGO Department of Procurement Services Jamie L. Rhee, Chief Procurement Officer 121 North LaSalle Street, Room 403 Chicago, Illinois 60602-1284 ECONOMIC DISCLOSURE STATEMENT AND AFFIDAVIT (EDS)
Omron Healthcare Online Privacy Policy Updated December 2017
 Omron Healthcare Online Privacy Policy Updated December 2017 1. Introduction 1.1 Purpose. The purpose of this Privacy Policy is to describe how Omron Healthcare, Inc. (collectively, Omron ) collects, uses
Omron Healthcare Online Privacy Policy Updated December 2017 1. Introduction 1.1 Purpose. The purpose of this Privacy Policy is to describe how Omron Healthcare, Inc. (collectively, Omron ) collects, uses
Adobe Experience Cloud Adobe Analytics and GDPR
 Adobe Experience Cloud Adobe Analytics and GDPR Contents Adobe Analytics and GDPR...3 Frequently Asked Questions...5 Adobe Analytics GDPR Workflow...9 View/Manage Report Suite's Data Governance Settings...10
Adobe Experience Cloud Adobe Analytics and GDPR Contents Adobe Analytics and GDPR...3 Frequently Asked Questions...5 Adobe Analytics GDPR Workflow...9 View/Manage Report Suite's Data Governance Settings...10
What Is Voice SEO and Why Should My Site Be Optimized For Voice Search?
 What Is Voice SEO and Why Should My Site Be Optimized For Voice Search? Voice search is a speech recognition technology that allows users to search by saying terms aloud rather than typing them into a
What Is Voice SEO and Why Should My Site Be Optimized For Voice Search? Voice search is a speech recognition technology that allows users to search by saying terms aloud rather than typing them into a
If you re a Facebook marketer, you re likely always looking for ways to
 Chapter 1: Custom Apps for Fan Page Timelines In This Chapter Using apps for Facebook marketing Extending the Facebook experience Discovering iframes, Application Pages, and Canvas Pages Finding out what
Chapter 1: Custom Apps for Fan Page Timelines In This Chapter Using apps for Facebook marketing Extending the Facebook experience Discovering iframes, Application Pages, and Canvas Pages Finding out what
3. WWW and HTTP. Fig.3.1 Architecture of WWW
 3. WWW and HTTP The World Wide Web (WWW) is a repository of information linked together from points all over the world. The WWW has a unique combination of flexibility, portability, and user-friendly features
3. WWW and HTTP The World Wide Web (WWW) is a repository of information linked together from points all over the world. The WWW has a unique combination of flexibility, portability, and user-friendly features
1. If you are a new user, register for the platform at truaudience.tru-signal.com.
 QUICK START GUIDE REGISTER 1. If you are a new user, register for the platform at truaudience.tru-signal.com. 2. Click sign up and complete the registration form. 3. Once you complete the form, you will
QUICK START GUIDE REGISTER 1. If you are a new user, register for the platform at truaudience.tru-signal.com. 2. Click sign up and complete the registration form. 3. Once you complete the form, you will
Compliance of Panda Products with General Data Protection Regulation (GDPR) Panda Security
 Panda Security Compliance of Panda Products with General Data Protection Regulation (GDPR) 1 Contents 1.1. SCOPE OF THIS DOCUMENT... 3 1.2. GENERAL DATA PROTECTION REGULATION: OBJECTIVES... 3 1.3. STORED
Panda Security Compliance of Panda Products with General Data Protection Regulation (GDPR) 1 Contents 1.1. SCOPE OF THIS DOCUMENT... 3 1.2. GENERAL DATA PROTECTION REGULATION: OBJECTIVES... 3 1.3. STORED
Back-end architecture
 Back-end architecture Tiberiu Vilcu Prepared for EECS 411 Sugih Jamin 2 January 2018 https://education.github.com/pack 1 2 Outline HTTP 1. HTTP and useful web tools 2. Designing APIs 3. Back-end services
Back-end architecture Tiberiu Vilcu Prepared for EECS 411 Sugih Jamin 2 January 2018 https://education.github.com/pack 1 2 Outline HTTP 1. HTTP and useful web tools 2. Designing APIs 3. Back-end services
This privacy policy has been compiled to better serve those who are concerned with
 This privacy policy has been compiled to better serve those who are concerned with how their Personally identifiable information (PII) is being used online. PII, as used in US privacy law and information
This privacy policy has been compiled to better serve those who are concerned with how their Personally identifiable information (PII) is being used online. PII, as used in US privacy law and information
Privacy Policy for Scholaric.com
 Privacy Policy for Scholaric.com SCOPE Positive Slope LLC (Positive Slope), the publisher of Scholaric.com respects your privacy. This Privacy Statement applies to personal data collected by Positive Slope
Privacy Policy for Scholaric.com SCOPE Positive Slope LLC (Positive Slope), the publisher of Scholaric.com respects your privacy. This Privacy Statement applies to personal data collected by Positive Slope
Blackboard Student Guide
 Blackboard Student Guide Blackboard is an Internet application used by many instructors to put their courses online. Typically, your instructor will let you know on the first day of class if he or she
Blackboard Student Guide Blackboard is an Internet application used by many instructors to put their courses online. Typically, your instructor will let you know on the first day of class if he or she
Learning Center Computer and Security Settings
 Learning Center Computer and Security Settings Learning Center Computer Settings Please Note: To allow your computer to communicate most effectively with the Learning Center, and update your training record
Learning Center Computer and Security Settings Learning Center Computer Settings Please Note: To allow your computer to communicate most effectively with the Learning Center, and update your training record
INGI1341: Project 2 Analysis of a website
 INGI3141:PROJECT 2 1 INGI1341: Project 2 Analysis of a website Sergio Alejandro Chávez Cárdenas Abstract The details of a remote website sopitas.com are analysed and its responses over the Internet are
INGI3141:PROJECT 2 1 INGI1341: Project 2 Analysis of a website Sergio Alejandro Chávez Cárdenas Abstract The details of a remote website sopitas.com are analysed and its responses over the Internet are
DEVELOPEO.COM PRIVACY POLICY
 DEVELOPEO.COM PRIVACY POLICY Please check and read Developeo.com Privacy Policy to get a clear grasp of how Developeo protects, uses, collects or handles your information in accordance with the website.
DEVELOPEO.COM PRIVACY POLICY Please check and read Developeo.com Privacy Policy to get a clear grasp of how Developeo protects, uses, collects or handles your information in accordance with the website.
Internet+ Mobile Developer Starter Guide. Version 1.0
 Internet+ Mobile Developer Starter Guide Version 1.0 1 Table of contents Table of contents... 2 What is it... 3 Overview... 3 Buyers Advantages... 3 Merchants Advantages... 3 How does it work?... 4 Overview...
Internet+ Mobile Developer Starter Guide Version 1.0 1 Table of contents Table of contents... 2 What is it... 3 Overview... 3 Buyers Advantages... 3 Merchants Advantages... 3 How does it work?... 4 Overview...
PhishEye: Live Monitoring of Sandboxed Phishing Kits. Xiao Han Nizar Kheir Davide Balzarotti
 PhishEye: Live Monitoring of Sandboxed Phishing Kits Xiao Han Nizar Kheir Davide Balzarotti Summary Motivation Sandboxed phishing kits Implementation Results [APWG Phishing Activity Trends Report 2 nd
PhishEye: Live Monitoring of Sandboxed Phishing Kits Xiao Han Nizar Kheir Davide Balzarotti Summary Motivation Sandboxed phishing kits Implementation Results [APWG Phishing Activity Trends Report 2 nd
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 3 Protecting Systems
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 3 Protecting Systems Objectives Explain how to harden operating systems List ways to prevent attacks through a Web browser Define
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 3 Protecting Systems Objectives Explain how to harden operating systems List ways to prevent attacks through a Web browser Define
WHY CSRF WORKS. Implicit authentication by Web browsers
 WHY CSRF WORKS To explain the root causes of, and solutions to CSRF attacks, I need to share with you the two broad types of authentication mechanisms used by Web applications: 1. Implicit authentication
WHY CSRF WORKS To explain the root causes of, and solutions to CSRF attacks, I need to share with you the two broad types of authentication mechanisms used by Web applications: 1. Implicit authentication
Privacy Policy. What Information Is Collected? Internet Traffic Data
 Privacy Policy Purple Tree Photography, doing business as Purple Tree Photography ( Purple Tree Photography, we or us ) is sensitive to concerns that personal information collected from its customers (
Privacy Policy Purple Tree Photography, doing business as Purple Tree Photography ( Purple Tree Photography, we or us ) is sensitive to concerns that personal information collected from its customers (
Per Scholas does not require you to register or provide information to us in order to view our Site. Per
 This Privacy Policy is designed to explain our online information practices in connection with the Per Scholas web site (the Site ). Per Scholas is committed to protecting the privacy of its online visitors
This Privacy Policy is designed to explain our online information practices in connection with the Per Scholas web site (the Site ). Per Scholas is committed to protecting the privacy of its online visitors
THE FUTURE OF PERSONALIZATION IS VISUAL WHITE PAPER
 WHITE PAPER The Future of Personalization is Visual 1 It s hard to believe that ecommerce has been around for more than two decades, and juggernaut sites like Amazon and ebay were first launched in the
WHITE PAPER The Future of Personalization is Visual 1 It s hard to believe that ecommerce has been around for more than two decades, and juggernaut sites like Amazon and ebay were first launched in the
Amazon WorkMail. User Guide Version 1.0
 Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2018 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2018 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
Getting Started with Amazon Web Services
 Getting Started with Amazon Web Services Version 3.3 September 24, 2013 Contacting Leostream Leostream Corporation 411 Waverley Oaks Rd. Suite 316 Waltham, MA 02452 USA http://www.leostream.com Telephone:
Getting Started with Amazon Web Services Version 3.3 September 24, 2013 Contacting Leostream Leostream Corporation 411 Waverley Oaks Rd. Suite 316 Waltham, MA 02452 USA http://www.leostream.com Telephone:
Quick Online Shop Documentation
 Quick Online Shop Documentation In the following tutorial, you will get a complete step by step guide of using Quick Online Shop WordPress theme for building an amazon affiliate store site. All steps have
Quick Online Shop Documentation In the following tutorial, you will get a complete step by step guide of using Quick Online Shop WordPress theme for building an amazon affiliate store site. All steps have
, Rules & Regulations
 Email, Rules & Regulations Social Media and Digital Communication Social Pro = #SocPro Steve Lee, APR 1 A Simple Contract Permission-based email marketing Be clear what you want to send Information, promotional
Email, Rules & Regulations Social Media and Digital Communication Social Pro = #SocPro Steve Lee, APR 1 A Simple Contract Permission-based email marketing Be clear what you want to send Information, promotional
Let your customers login to your store after pre-approval
 Customer Approve & Disapprove Let your customers login to your store after pre-approval Extension Specification Document Version: 2.0.0 Magento 2 Extension URL: https://www.extensionhut.com/customer-approve-disapprove-for-magento-2.html
Customer Approve & Disapprove Let your customers login to your store after pre-approval Extension Specification Document Version: 2.0.0 Magento 2 Extension URL: https://www.extensionhut.com/customer-approve-disapprove-for-magento-2.html
Privacy Policy- ADDO Worldwide LLC LAST UPDATED: September 9, 2014
 Privacy Policy- ADDO Worldwide LLC LAST UPDATED: September 9, 2014 1. Introduction Chick-fil-A Leader Academy is owned and operated by ADDO Worldwide, LLC ( ADDO Worldwide, LLC, we, us, our ). We at ADDO
Privacy Policy- ADDO Worldwide LLC LAST UPDATED: September 9, 2014 1. Introduction Chick-fil-A Leader Academy is owned and operated by ADDO Worldwide, LLC ( ADDO Worldwide, LLC, we, us, our ). We at ADDO
Full and detailed technical cookies disclosure
 Digital Control Room Limited Apex Plaza, Forbury Road, Reading, RG1 1AX United Kingdom t: +44 20 7129 8113 www.digitalcontorlroom.com Full and detailed technical cookies disclosure Website audited: Audit
Digital Control Room Limited Apex Plaza, Forbury Road, Reading, RG1 1AX United Kingdom t: +44 20 7129 8113 www.digitalcontorlroom.com Full and detailed technical cookies disclosure Website audited: Audit
To review material modifications and their effective dates scroll to the bottom of the page.
 PRIVACY POLICY Effective Date: October 1, 2016 To review material modifications and their effective dates scroll to the bottom of the page. Cobra Trading, Inc. ("Cobra") owns and operates this cobratrading.com
PRIVACY POLICY Effective Date: October 1, 2016 To review material modifications and their effective dates scroll to the bottom of the page. Cobra Trading, Inc. ("Cobra") owns and operates this cobratrading.com
Frequently Asked Questions Exhibitor Online Platform. Simply pick the subject (below) that covers your query and topic to access the FAQs:
 Exhibitor Online Platform Simply pick the subject (below) that covers your query and topic to access the FAQs: 1. What is Exhibitor Online Platform (EOP)?...2 2. System requirements...3 2.1. What are the
Exhibitor Online Platform Simply pick the subject (below) that covers your query and topic to access the FAQs: 1. What is Exhibitor Online Platform (EOP)?...2 2. System requirements...3 2.1. What are the
Liferay Security Features Overview. How Liferay Approaches Security
 Liferay Security Features Overview How Liferay Approaches Security Table of Contents Executive Summary.......................................... 1 Transport Security............................................
Liferay Security Features Overview How Liferay Approaches Security Table of Contents Executive Summary.......................................... 1 Transport Security............................................
Layer by Layer: Protecting from Attack in Office 365
 Layer by Layer: Protecting Email from Attack in Office 365 Office 365 is the world s most popular office productivity suite, with user numbers expected to surpass 100 million in 2017. With the vast amount
Layer by Layer: Protecting Email from Attack in Office 365 Office 365 is the world s most popular office productivity suite, with user numbers expected to surpass 100 million in 2017. With the vast amount
