Cracking Cryptocurrency Brainwallets
|
|
|
- Rafe Dean
- 6 years ago
- Views:
Transcription
1 Cracking Cryptocurrency Brainwallets Ryan Castellucci DRAFT SLIDES, WILL BE REVISED! FOR FINAL VERSION AFTER TALK
2 Disclaimer Stealing from people with weak passphrases isn t nice. Don t be an asshole.
3 What s a cryptocurrency? Bitcoin is the most widely known example. Electronic money which can operate without banks or governments Secured with cryptographic algorithms Transferred via a sort of electronic check Checks are made public to prevent bounces Control of key == Control of money
4 What s a brainwallet? A brainwallet is a cryptocurrency key that is created from a password (or passphrase) Some people believe that this will make their money harder to steal (or seize) Knowledge of password == Control of money Sending money to a brainwallet publishes a hash of it. What if the hash can be cracked?
5 It seemed like it might be interesting Came across a blog post about brainwallets The author made some and posted about it to see how long they d take to crack I figured writing a cracker would be a fun way to spend my commute for a few days But why try to crack three brainwallets when you can try to crack all of them?
6 My first brainwallet cracker Simple design, pass a file with pubkeyhashs, then pipe words/phrases on STDIN Written in C using OpenSSL s crypto ~10,000 passwords per second on my PC The slowest part, by far, is turning the private key into a public key. More on that later.
7 Taking it for a spin I start feeding it password cracking wordlists Find some tiny amounts of money Scrape wikiquote and a few other sites to build myself a phraselist Run the phraselist - it gets some hits after a few hours Pull balances, see one with 250BTC
8 Well, that is interesting. Now what? 250BTC was worth about $15k I wanted to fix this. I m friends with Dan Kaminsky. He s fixed some big things. After regaining my composure, I called him. As luck would have it, he was in town We meet up about an hour later to figure out how to do the right thing
9 A plan begins to form I felt it would be wrong to take and hope find the rightful owner I could send some spare change to it and then take it back You can even put short words in a Bitcoin address, so a subtle message is possible My girlfriend (now wife) piped up with yoink
10 That time I accidently stole 250 BTC After getting an appropriate address with vanitygen, I do some transactions
11 Oops. :-( What s that other address? why isn t it in the list of my addresses?...oh, right, that s my change address...and Bitcoin had its own opinions on what outputs should be spent Quick, before anyone notices!
12 Wait, what? Bitcoin transactions have inputs and outputs Old, unspent outputs are used as inputs on a new transaction, but they can only be spent in full You might need more than one, and you might need to make change for yourself If you want details, see
13
14 See, I put it back. It s fine. After fixing it, I did a few run a few cents through it transactions The owner did not take the hint :-( I ll just find them. The address was funded by 12DK76obundhnnbGKcaKEn3BcMNNH5SVU4 That address received a payout from DeepBit. DeepBit collects addresses.
15 Social engineering, Whitehat style I send Tycho the guy who runs DeepBit messages via BitcoinTalk, , and IRC Eventually I manage to talk to him on IRC I explain that one of his users has coins stored unsafely, but can t elaborate He wouldn t give out any user details He does agree to contact the user for me
16 Success. The guy s me, and I ask him to call me He does, and I establish that it was indeed his brainwallet He moves the coins and insists on sending me a small reward
17 Some history August 2011 Kaminsky demos Phidelius, an OpenSSL hack, mentions Bitcoin as a possible use January 2012 Casascius adds a brainwallet entry to the Bitcoin wiki April 2012 brainwallet.org comes online I couldn t really find anything pre-2012
18 How to make a brainwallet "correct horse battery staple" Passphrase v v v v v v v v SHA256 c4bbcb1fbec99d65bf59d85c8cb62ee2 Private key db963f0fe106f483d9afa73bd4e39a8a v v v v v v v v v v v v v v v v v v v privatetopublic (UNCOMPRESSED) (COMPRESSED) 04 78d430274f8c5ec e9f27f4 -> 03 78d430274f8c5ec e9f27f4 Public key c676a008bdf8638d07c0b6be9ab35c71 c676a008bdf8638d07c0b6be9ab35c71 a acd4dfe96b66e3f2ec801 3c8e072cd09b3834a19f81f659cc3455 SHA256 v v v v v v v v v v v v v v v v b e05a b06b05e0 7c7c6fae6b95780f7423ff9ccf0c552a 580fa00ba5f5e60499c5c7e7d9c7f50e 8a5a7f883bdb1ee6c22c05ce71c1f288 v v v v v v v v v v v v RIPEMD160 c4c5d791fcb4654a1ef5 79fbfc3f34e d7 Hash160 e03fe0ad3d9c598f da68f362380c606c (used for tx) v v v v v v v v v v v v Base58Check 1JwSSubhmg6iPtRjtyqhUYYH7bZg3Lfy1T 1C7zdTfnkzmr13HfA2vNm5SJYRK6nEKyq8 Address
19 What s wrong with that? It s an unsalted, un-iterated password hash that you publish to the world...and cracking them directly yields pseudonymous, easily laundered currency We ve known for years that passwords need to be run through a hardened hash People have very poor intuition of how strong their passphrases are
20 Better options Electrum-style 12 word seed, computer generated but memorable with some effort WarpWallet allows for a salt ( ) and uses key stretching, but weak passphrases still a problem BIP38 paper wallets - print it out and hide it under your mattress
21 Key strength Usually measured in bits Adding a bit doubles the strength Adding ten increases it a thousandfold Figuring out how many bits a password is equivalent to is very, very hard Microsoft s estimate was that the average user s password was equivalent to ~40 bits That seems absurdly high
22 Key stretching Make cracking hard by slowing it down scrypt, bcrypt, pbkdf2, sha512crypt, etc In practice, you can make it on the order of a million times slower Gain 20 bits +/- 4 bits in effective strength Need somewhere between 72 and 128 bits There s a significant shortfall here
23 Extreme key stretching (just an idea) Generate a short (16-24 bits) random salt Have the KDF chew on it for a few seconds Save the output (the shortcut) Use the shortcut as salt to a to second KDF Without the shortcut, you can spend a few hours brute forcing the salt A vetted scheme for this would be needed
24 Actually secure passwords Pick it randomly - easy, right? Random numbers are hard for humans to remember Password managers! What protects the password manager? Backups are hard Turtles all the way down
25 Cryptomnemonics Humans have a hard time memorizing a bunch of random numbers Turn the random numbers into something easier to memorize Diceware is a very old scheme that does this Open problem, actively researched I built - feedback? How easy can we make these things?
26 Introducing Brainflayer Does about 100,000 passphrases per second on my quad core i7 3.5GHz Using EC2 spot instances would cost about $700 to check a billion passphrases A mid-sized botnet with million nodes each trying 10,000 passphrases per second could check nearly (~ ) in a day
27 Introducing Brainflayer (cont d) At that speed a passphrase of four random common English words falls in about an hour Low level optimization and fancy math are not my thing, but there is plenty of room for improvement here even without GPGPU Has a lookup table generation mode Crack multiple cryptocurrencies at once
28 How Brainflayer works We need to go from passphrase to Hash160 and check if that Hash160 has been used I got about a 10x speed increase switching to libsecp256k1 to generate the public key Quickly checking if a Hash160 has ever received money can be done with a data structure called a bloom filter
29 Bloom filter? A space-efficient probabilistic data structure Consists of a large array of bits To add an item, hash that item n ways and set n corresponding bits To check if an item is present, hash that item n ways - if all n corresponding bits are set then it probably is.
30 Probably? The error rate can be made quite small Most of the time we re getting a no and we want that to be fast The probably can be fully verified later
31 Isn t running more hashes slow? Yes, even the non-cryptographic ones So we don t run more hashes Our items are already hashed Just slice and dice the bits, which is fast
32 Building a phraselist Song lyric sites, Wikiquotes, Wikipedia, Project Gutenberg, forums, reddit, etc. Needs normalization, then normalized lists can have rules applied to them
33 Example cracked brainwallets Zed's dead baby. Zed's dead. 22Jan1997 Am I invisible because you ignore me? antidis3stablishm3ntarianism youaremysunshinemyonlysunshine The Persistence Of Memory toby102 permit me to issue and control the money of a nation and i care not who makes its laws
34 Everyone loves demos. <INSERT DEMO HERE>
35 What s already happening? There appear to be at least four currently active brainwallet thieves, probably more Send funds to a particularly weak brainwallet and they ll be gone in seconds Lookup tables for large numbers of passwords have clearly been built Adaptive behaviour has been observed Cracking speeds unclear
36 Lookup tables? There is competition for weak brainwallets Must be fast, rainbow tables too slow Use your favorite key-value store Truncate the Hash160 (64 bits, save space) Store the passphrase or private key, whichever is shorter A $120 4TB disk will store 2 36 passphrases
37 Lookup tables? (cont d) Monitors for transactions Check addresses against key-value store LRU cache in front of key-value store On a hit, use the private key to make a new transaction taking the funds Do this faster than others trying to do the same I have not built any of this, but it exists
38 SUPER SECRET SECOND DEMO <INSERT DEMO HERE>
Chapter 13. Digital Cash. Information Security/System Security p. 570/626
 Chapter 13 Digital Cash Information Security/System Security p. 570/626 Introduction While cash is used in illegal activities such as bribing money laundering tax evasion it also protects privacy: not
Chapter 13 Digital Cash Information Security/System Security p. 570/626 Introduction While cash is used in illegal activities such as bribing money laundering tax evasion it also protects privacy: not
Hacking Deterministic Bitcoin Addresses. Michael McKinnon
 Hacking Deterministic Bitcoin Addresses Michael McKinnon - @bigmac This talk is ONLY about Bitcoin Bro, wanna buy some #sheepcoin? 2 I won t be outing Satoshi #whoissatoshi 3 I m not a Lawyer, This is
Hacking Deterministic Bitcoin Addresses Michael McKinnon - @bigmac This talk is ONLY about Bitcoin Bro, wanna buy some #sheepcoin? 2 I won t be outing Satoshi #whoissatoshi 3 I m not a Lawyer, This is
DER GOBBLE. Good Secure Crypto Wallet Practices. What is your wallet?
 DER GOBBLE Good Secure Crypto Wallet Practices When it comes to crypto currencies and securing your money, the absolute best 99% guaranteed security for your wallets is YOU. You are the one that will expose
DER GOBBLE Good Secure Crypto Wallet Practices When it comes to crypto currencies and securing your money, the absolute best 99% guaranteed security for your wallets is YOU. You are the one that will expose
CS 161 Computer Security
 Popa & Weaver Fall 2016 CS 161 Computer Security 10/4 Passwords 1 Passwords are widely used for authentication, especially on the web. What practices should be used to make passwords as secure as possible?
Popa & Weaver Fall 2016 CS 161 Computer Security 10/4 Passwords 1 Passwords are widely used for authentication, especially on the web. What practices should be used to make passwords as secure as possible?
Outline Key Management CS 239 Computer Security February 9, 2004
 Outline Key Management CS 239 Computer Security February 9, 2004 Properties of keys Key management Key servers Certificates Page 1 Page 2 Introduction Properties of Keys It doesn t matter how strong your
Outline Key Management CS 239 Computer Security February 9, 2004 Properties of keys Key management Key servers Certificates Page 1 Page 2 Introduction Properties of Keys It doesn t matter how strong your
P2P BitCoin: Technical details
 ELT-53206 Peer-to-Peer Networks P2P BitCoin: Technical details Mathieu Devos Tampere University of Technology Department of Electronics & Communications Engineering mathieu.devos@tut.fi TG406 2 Outline
ELT-53206 Peer-to-Peer Networks P2P BitCoin: Technical details Mathieu Devos Tampere University of Technology Department of Electronics & Communications Engineering mathieu.devos@tut.fi TG406 2 Outline
Bitcoin (Part I) Ken Calvert Keeping Current Seminar 22 January Keeping Current 1
 Bitcoin (Part I) Ken Calvert Keeping Current Seminar 22 January 2014 2014.01.22 Keeping Current 1 Questions What problem is Bitcoin solving? Where did it come from? How does the system work? What makes
Bitcoin (Part I) Ken Calvert Keeping Current Seminar 22 January 2014 2014.01.22 Keeping Current 1 Questions What problem is Bitcoin solving? Where did it come from? How does the system work? What makes
Bitcoin and Blockchain
 Bitcoin and Blockchain COS 418: Distributed Systems Lecture 18 Zhenyu Song [Credit: Selected content adapted from Michael Freedman. Slides refined by Chris Hodsdon and Theano Stavrinos] Why Bitcoin? All
Bitcoin and Blockchain COS 418: Distributed Systems Lecture 18 Zhenyu Song [Credit: Selected content adapted from Michael Freedman. Slides refined by Chris Hodsdon and Theano Stavrinos] Why Bitcoin? All
Smalltalk 3/30/15. The Mathematics of Bitcoin Brian Heinold
 Smalltalk 3/30/15 The Mathematics of Bitcoin Brian Heinold What is Bitcoin? Created by Satoshi Nakamoto in 2008 What is Bitcoin? Created by Satoshi Nakamoto in 2008 Digital currency (though not the first)
Smalltalk 3/30/15 The Mathematics of Bitcoin Brian Heinold What is Bitcoin? Created by Satoshi Nakamoto in 2008 What is Bitcoin? Created by Satoshi Nakamoto in 2008 Digital currency (though not the first)
SOLUTIONS GUIDE. I Don t Know What to or
 SOLUTIONS GUIDE I Don t Know What to Email or How to Write My Email, Can I Have Some Ideas? We often hear from new students that one of their biggest challenges creating content for email campaigns. Not
SOLUTIONS GUIDE I Don t Know What to Email or How to Write My Email, Can I Have Some Ideas? We often hear from new students that one of their biggest challenges creating content for email campaigns. Not
ENEE 457: E-Cash and Bitcoin
 ENEE 457: E-Cash and Bitcoin Charalampos (Babis) Papamanthou cpap@umd.edu Money today Any problems? Cash is cumbersome and can be forged Credit card transactions require centralized online bank are not
ENEE 457: E-Cash and Bitcoin Charalampos (Babis) Papamanthou cpap@umd.edu Money today Any problems? Cash is cumbersome and can be forged Credit card transactions require centralized online bank are not
Copyright 2017 by Kevin de Wit
 Copyright 2017 by Kevin de Wit All rights reserved. No part of this publication may be reproduced, distributed, or transmitted in any form or by any means, including photocopying, recording, or other electronic
Copyright 2017 by Kevin de Wit All rights reserved. No part of this publication may be reproduced, distributed, or transmitted in any form or by any means, including photocopying, recording, or other electronic
Outlook is easier to use than you might think; it also does a lot more than. Fundamental Features: How Did You Ever Do without Outlook?
 04 537598 Ch01.qxd 9/2/03 9:46 AM Page 11 Chapter 1 Fundamental Features: How Did You Ever Do without Outlook? In This Chapter Reading e-mail Answering e-mail Creating new e-mail Entering an appointment
04 537598 Ch01.qxd 9/2/03 9:46 AM Page 11 Chapter 1 Fundamental Features: How Did You Ever Do without Outlook? In This Chapter Reading e-mail Answering e-mail Creating new e-mail Entering an appointment
A Guide to Condor. Joe Antognini. October 25, Condor is on Our Network What is an Our Network?
 A Guide to Condor Joe Antognini October 25, 2013 1 Condor is on Our Network What is an Our Network? The computers in the OSU astronomy department are all networked together. In fact, they re networked
A Guide to Condor Joe Antognini October 25, 2013 1 Condor is on Our Network What is an Our Network? The computers in the OSU astronomy department are all networked together. In fact, they re networked
Clickbank Domination Presents. A case study by Devin Zander. A look into how absolutely easy internet marketing is. Money Mindset Page 1
 Presents A case study by Devin Zander A look into how absolutely easy internet marketing is. Money Mindset Page 1 Hey guys! Quick into I m Devin Zander and today I ve got something everybody loves! Me
Presents A case study by Devin Zander A look into how absolutely easy internet marketing is. Money Mindset Page 1 Hey guys! Quick into I m Devin Zander and today I ve got something everybody loves! Me
Cryptography for Software and Web Developers
 Cryptography for Software and Web Developers Part 4: randomness, hashing, tokens Hanno Böck 2014-05-28 1 / 13 Bad random numbers Random fails Example: Factoring RSA keys Good / bad randomness In security
Cryptography for Software and Web Developers Part 4: randomness, hashing, tokens Hanno Böck 2014-05-28 1 / 13 Bad random numbers Random fails Example: Factoring RSA keys Good / bad randomness In security
Ages Donʼt Fall for Fake: Activity 1 Don t bite that phishing hook! Goals for children. Letʼs talk
 Ages 11-14 Donʼt Fall for : Activity 1 Don t bite that phishing hook! Children play a game where they study various emails and texts and try to decide which messages are legit and which are phishing scams.
Ages 11-14 Donʼt Fall for : Activity 1 Don t bite that phishing hook! Children play a game where they study various emails and texts and try to decide which messages are legit and which are phishing scams.
Password cracking. IN Ethical Hacking. Bruvoll & Sørby. Department of Informatics 1 / 46
 Password cracking IN5290 - Ethical Hacking Bruvoll & Sørby Department of Informatics 2018 1 / 46 Agenda About passwords Cracking passwords 2 / 46 About passwords 3 / 46 Passwords as authentication Providing
Password cracking IN5290 - Ethical Hacking Bruvoll & Sørby Department of Informatics 2018 1 / 46 Agenda About passwords Cracking passwords 2 / 46 About passwords 3 / 46 Passwords as authentication Providing
EADS up. stop think connect
 EADS up stop think connect You text, you play games, you share photos and video. You update your status, you post comments, you probably spend some time in a virtual world. Being online connected through
EADS up stop think connect You text, you play games, you share photos and video. You update your status, you post comments, you probably spend some time in a virtual world. Being online connected through
Web Hosting. Important features to consider
 Web Hosting Important features to consider Amount of Storage When choosing your web hosting, one of your primary concerns will obviously be How much data can I store? For most small and medium web sites,
Web Hosting Important features to consider Amount of Storage When choosing your web hosting, one of your primary concerns will obviously be How much data can I store? For most small and medium web sites,
2016 All Rights Reserved
 2016 All Rights Reserved Table of Contents Chapter 1: The Truth About Safelists What is a Safelist Safelist myths busted Chapter 2: Getting Started What to look for before you join a Safelist Best Safelists
2016 All Rights Reserved Table of Contents Chapter 1: The Truth About Safelists What is a Safelist Safelist myths busted Chapter 2: Getting Started What to look for before you join a Safelist Best Safelists
Jan Møller Co-founder, CTO Chainalysis
 Jan Møller Co-founder, CTO Chainalysis How Does Bitcoin Actually Work? This talk is not about the poli:cal or economical impact of Bitcoin. This talk is not about how to buy, sell, spend, or secure your
Jan Møller Co-founder, CTO Chainalysis How Does Bitcoin Actually Work? This talk is not about the poli:cal or economical impact of Bitcoin. This talk is not about how to buy, sell, spend, or secure your
Effective Password Hashing
 Effective Password Hashing November 18th, 2015 Colin Keigher colin@keigher.ca ~ @afreak ~ https://afreak.ca ~ https://canary.pw Who am I? I am a Senior Security Analyst at a large Canadian company Actively
Effective Password Hashing November 18th, 2015 Colin Keigher colin@keigher.ca ~ @afreak ~ https://afreak.ca ~ https://canary.pw Who am I? I am a Senior Security Analyst at a large Canadian company Actively
Security Analysis of Bitcoin. Dibyojyoti Mukherjee Jaswant Katragadda Yashwant Gazula
 Security Analysis of Bitcoin Dibyojyoti Mukherjee Jaswant Katragadda Yashwant Gazula Security Analysis of Bitcoin Introduction How Bitcoin works? Similar peer-to-peer systems Vulnerabilities and solutions
Security Analysis of Bitcoin Dibyojyoti Mukherjee Jaswant Katragadda Yashwant Gazula Security Analysis of Bitcoin Introduction How Bitcoin works? Similar peer-to-peer systems Vulnerabilities and solutions
Who wants to be a millionaire? A class in creating your own cryptocurrency
 DEVNET-3626 Who wants to be a millionaire? A class in creating your own cryptocurrency Tom Davies, Sr. Manager, DevNet Sandbox Vallard Benincosa, Software Engineer Cisco Spark How Questions? Use Cisco
DEVNET-3626 Who wants to be a millionaire? A class in creating your own cryptocurrency Tom Davies, Sr. Manager, DevNet Sandbox Vallard Benincosa, Software Engineer Cisco Spark How Questions? Use Cisco
Introduction to Information Security Prof. V. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras
 Introduction to Information Security Prof. V. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 09 Now, we discuss about the insecurity of passwords.
Introduction to Information Security Prof. V. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 09 Now, we discuss about the insecurity of passwords.
Cryptographic Hash Functions. Secure Software Systems
 1 Cryptographic Hash Functions 2 Cryptographic Hash Functions Input: Message of arbitrary size Output: Digest (hashed output) of fixed size Loreum ipsum Hash Function 23sdfw83x8mjyacd6 (message of arbitrary
1 Cryptographic Hash Functions 2 Cryptographic Hash Functions Input: Message of arbitrary size Output: Digest (hashed output) of fixed size Loreum ipsum Hash Function 23sdfw83x8mjyacd6 (message of arbitrary
Releasing the Kracken: Building and Using a GPU Password Cracker
 Releasing the Kracken: Building and Using a GPU Password Cracker Jonathan Fallone About Me Jonathan Fallone Senior Pen Tester with Knowledge Consulting Group jonathan.fallone@knowledgecg.com @Shady_Wushu
Releasing the Kracken: Building and Using a GPU Password Cracker Jonathan Fallone About Me Jonathan Fallone Senior Pen Tester with Knowledge Consulting Group jonathan.fallone@knowledgecg.com @Shady_Wushu
Cold, Hard Cache KV? On the implementation and maintenance of caches. who is
 1 of 5 TE X T ONLY Cold, Hard Cache On the implementation and maintenance of caches who is KV? click for video Dear KV, Our latest project at work requires a large number of slightly different software
1 of 5 TE X T ONLY Cold, Hard Cache On the implementation and maintenance of caches who is KV? click for video Dear KV, Our latest project at work requires a large number of slightly different software
Crypto tricks: Proof of work, Hash chaining
 Crypto tricks: Proof of work, Hash chaining CS 161: Computer Security Prof. David Wagner April 13, 2016 A Tangent: How Can I Prove I Am Rich? Math Puzzle Proof of Work Problem. To prove to Bob I m not
Crypto tricks: Proof of work, Hash chaining CS 161: Computer Security Prof. David Wagner April 13, 2016 A Tangent: How Can I Prove I Am Rich? Math Puzzle Proof of Work Problem. To prove to Bob I m not
Once the file is downloaded we need to extract it. To do that, right click and select > Extract To.
 In this guide, we will show you how to setup Jaxx Blockchain Wallet for your desktop. If you re interested in how to setup your crypto wallet for your mobile, please download it here. To get started, visit
In this guide, we will show you how to setup Jaxx Blockchain Wallet for your desktop. If you re interested in how to setup your crypto wallet for your mobile, please download it here. To get started, visit
Computer Security. 14. Blockchain & Bitcoin. Paul Krzyzanowski. Rutgers University. Spring 2019
 Computer Security 14. Blockchain & Bitcoin Paul Krzyzanowski Rutgers University Spring 2019 April 15, 2019 CS 419 2019 Paul Krzyzanowski 1 Bitcoin & Blockchain Bitcoin cryptocurrency system Introduced
Computer Security 14. Blockchain & Bitcoin Paul Krzyzanowski Rutgers University Spring 2019 April 15, 2019 CS 419 2019 Paul Krzyzanowski 1 Bitcoin & Blockchain Bitcoin cryptocurrency system Introduced
BITCOIN PROTOCOL & CONSENSUS: A HIGH LEVEL OVERVIEW
 BITCOIN PROTOCOL & CONSENSUS: A HIGH LEVEL OVERVIEW Rustie Lin Wang Move the area1 over the image a little inside and then right click, replace image to change the background. (and delete this box while
BITCOIN PROTOCOL & CONSENSUS: A HIGH LEVEL OVERVIEW Rustie Lin Wang Move the area1 over the image a little inside and then right click, replace image to change the background. (and delete this box while
Ryan Parsons Chad Price Jia Reese Alex Vassallo
 Ryan Parsons - Paper Prototype, Writing Chad Price - Paper Prototype, Digital Mockup Jia Reese - Paper Prototype, Usability Testing Alex Vassallo - Usability Testing, Writing All we have to decide is what
Ryan Parsons - Paper Prototype, Writing Chad Price - Paper Prototype, Digital Mockup Jia Reese - Paper Prototype, Usability Testing Alex Vassallo - Usability Testing, Writing All we have to decide is what
9 R1 Get another piece of paper. We re going to have fun keeping track of (inaudible). Um How much time do you have? Are you getting tired?
 Page: 1 of 14 1 R1 And this is tell me what this is? 2 Stephanie x times y plus x times y or hm? 3 R1 What are you thinking? 4 Stephanie I don t know. 5 R1 Tell me what you re thinking. 6 Stephanie Well.
Page: 1 of 14 1 R1 And this is tell me what this is? 2 Stephanie x times y plus x times y or hm? 3 R1 What are you thinking? 4 Stephanie I don t know. 5 R1 Tell me what you re thinking. 6 Stephanie Well.
Lock Picking and Physical Security. Tyler Nighswander
 Lock Picking and Physical Security Tyler Nighswander Lock Picking and Physical Security Tyler Nighswander Introduction Who I am: PPP member (specializes in crypto and hardware interested in everything!)
Lock Picking and Physical Security Tyler Nighswander Lock Picking and Physical Security Tyler Nighswander Introduction Who I am: PPP member (specializes in crypto and hardware interested in everything!)
Backend IV: Authentication, Authorization and Sanitization. Tuesday, January 13, 15
 6.148 Backend IV: Authentication, Authorization and Sanitization The Internet is a scary place Security is a big deal! TODAY What is security? How will we try to break your site? Authentication,
6.148 Backend IV: Authentication, Authorization and Sanitization The Internet is a scary place Security is a big deal! TODAY What is security? How will we try to break your site? Authentication,
PYTHIA SERVICE BY VIRGIL SECURITY WHITE PAPER
 PYTHIA SERVICE WHITEPAPER BY VIRGIL SECURITY WHITE PAPER May 21, 2018 CONTENTS Introduction 2 How does Pythia solve these problems? 3 Are there any other solutions? 4 What is Pythia? 4 How does it work?
PYTHIA SERVICE WHITEPAPER BY VIRGIL SECURITY WHITE PAPER May 21, 2018 CONTENTS Introduction 2 How does Pythia solve these problems? 3 Are there any other solutions? 4 What is Pythia? 4 How does it work?
Unit 9 Tech savvy? Tech support. 1 I have no idea why... Lesson A. A Unscramble the questions. Do you know which battery I should buy?
 Unit 9 Tech savvy? Lesson A Tech support 1 I have no idea why... A Unscramble the questions. 1. which battery / Do you know / should / buy / I? Do you know which battery I should buy? 2. they / where /
Unit 9 Tech savvy? Lesson A Tech support 1 I have no idea why... A Unscramble the questions. 1. which battery / Do you know / should / buy / I? Do you know which battery I should buy? 2. they / where /
Text Input and Conditionals
 Text Input and Conditionals Text Input Many programs allow the user to enter information, like a username and password. Python makes taking input from the user seamless with a single line of code: input()
Text Input and Conditionals Text Input Many programs allow the user to enter information, like a username and password. Python makes taking input from the user seamless with a single line of code: input()
P2_L8 - Hashes Page 1
 P2_L8 - Hashes Page 1 Reference: Computer Security by Stallings and Brown, Chapter 21 In this lesson, we will first introduce the birthday paradox and apply it to decide the length of hash, in order to
P2_L8 - Hashes Page 1 Reference: Computer Security by Stallings and Brown, Chapter 21 In this lesson, we will first introduce the birthday paradox and apply it to decide the length of hash, in order to
CNIT 124: Advanced Ethical Hacking. Ch 9: Password Attacks
 CNIT 124: Advanced Ethical Hacking Ch 9: Password Attacks Topics Password Management Online Password Attacks Offline Password Attacks Dumping Passwords from RAM Password Management Password Alternatives
CNIT 124: Advanced Ethical Hacking Ch 9: Password Attacks Topics Password Management Online Password Attacks Offline Password Attacks Dumping Passwords from RAM Password Management Password Alternatives
The Website. Teaching Thoughts. Usability Report. By Jon Morris
 The Website Teaching Thoughts Usability Report By Jon Morris Original November 13 th, 2009 Modified on November 21 st 2009 Table of Contents 1. Introduction... 3 2. Executive Summary...3-4 3. Methodology...5-6
The Website Teaching Thoughts Usability Report By Jon Morris Original November 13 th, 2009 Modified on November 21 st 2009 Table of Contents 1. Introduction... 3 2. Executive Summary...3-4 3. Methodology...5-6
Activity Guide - Public Key Cryptography
 Unit 2 Lesson 19 Name(s) Period Date Activity Guide - Public Key Cryptography Introduction This activity is similar to the cups and beans encryption we did in a previous lesson. However, instead of using
Unit 2 Lesson 19 Name(s) Period Date Activity Guide - Public Key Cryptography Introduction This activity is similar to the cups and beans encryption we did in a previous lesson. However, instead of using
Yammer Product Manager Homework: LinkedІn Endorsements
 BACKGROUND: Location: Mountain View, CA Industry: Social Networking Users: 300 Million PART 1 In September 2012, LinkedIn introduced the endorsements feature, which gives its users the ability to give
BACKGROUND: Location: Mountain View, CA Industry: Social Networking Users: 300 Million PART 1 In September 2012, LinkedIn introduced the endorsements feature, which gives its users the ability to give
The LinkedIn Hack: Understanding Why It Was So Easy to Crack the Passwords
 The LinkedIn Hack: Understanding Why It Was So Easy to Crack the Passwords LinkedIn was breached in 2012 with a reported 6.5 million user accounts compromised. LinkedIn sent a request to known hacked users
The LinkedIn Hack: Understanding Why It Was So Easy to Crack the Passwords LinkedIn was breached in 2012 with a reported 6.5 million user accounts compromised. LinkedIn sent a request to known hacked users
Lesson 2. Introducing Apps. In this lesson, you ll unlock the true power of your computer by learning to use apps!
 Lesson 2 Introducing Apps In this lesson, you ll unlock the true power of your computer by learning to use apps! So What Is an App?...258 Did Someone Say Free?... 259 The Microsoft Solitaire Collection
Lesson 2 Introducing Apps In this lesson, you ll unlock the true power of your computer by learning to use apps! So What Is an App?...258 Did Someone Say Free?... 259 The Microsoft Solitaire Collection
Frontline Information Protection
 Frontline Information Protection a presentation to the Phoenix Chapter of ISACA by Hoyt L Kesterson II October 2014 OBSERVATION Most successful attacks spring from weakly-coded web pages or compromised
Frontline Information Protection a presentation to the Phoenix Chapter of ISACA by Hoyt L Kesterson II October 2014 OBSERVATION Most successful attacks spring from weakly-coded web pages or compromised
Where The Objects Roam
 CS61A, Spring 2006, Wei Tu (Based on Chung s Notes) 1 CS61A Week 8 Where The Objects Roam (v1.0) Paradigm Shift (or: The Rabbit Dug Another Hole) And here we are, already ready to jump into yet another
CS61A, Spring 2006, Wei Tu (Based on Chung s Notes) 1 CS61A Week 8 Where The Objects Roam (v1.0) Paradigm Shift (or: The Rabbit Dug Another Hole) And here we are, already ready to jump into yet another
Page Replacement. (and other virtual memory policies) Kevin Webb Swarthmore College March 27, 2018
 Page Replacement (and other virtual memory policies) Kevin Webb Swarthmore College March 27, 2018 Today s Goals Making virtual memory virtual : incorporating disk backing. Explore page replacement policies
Page Replacement (and other virtual memory policies) Kevin Webb Swarthmore College March 27, 2018 Today s Goals Making virtual memory virtual : incorporating disk backing. Explore page replacement policies
Fractions and their Equivalent Forms
 Fractions Fractions and their Equivalent Forms Little kids use the concept of a fraction long before we ever formalize their knowledge in school. Watching little kids share a candy bar or a bottle of soda
Fractions Fractions and their Equivalent Forms Little kids use the concept of a fraction long before we ever formalize their knowledge in school. Watching little kids share a candy bar or a bottle of soda
Introduction to Security and User Authentication
 Introduction to Security and User Authentication Brad Karp UCL Computer Science CS GZ03 / M030 14 th November 2016 Topics We ll Cover User login authentication (local and remote) Cryptographic primitives,
Introduction to Security and User Authentication Brad Karp UCL Computer Science CS GZ03 / M030 14 th November 2016 Topics We ll Cover User login authentication (local and remote) Cryptographic primitives,
MSI Sakib - Blogger, SEO Researcher and Internet Marketer
 About Author: MSI Sakib - Blogger, SEO Researcher and Internet Marketer Hi there, I am the Founder of Techmasi.com blog and CEO of Droid Digger (droiddigger.com) android app development team. I love to
About Author: MSI Sakib - Blogger, SEO Researcher and Internet Marketer Hi there, I am the Founder of Techmasi.com blog and CEO of Droid Digger (droiddigger.com) android app development team. I love to
FILED: NEW YORK COUNTY CLERK 07/31/ :17 AM INDEX NO /2018 NYSCEF DOC. NO. 53 RECEIVED NYSCEF: 07/31/2018
 SUPREME COURT OF THE STATE OF NEW YORK New York County LOUIS J DESY JR Plaintiff, - against- Index No.: 651541/2018 Filed: 03/30/2018 KEN WHITMAN AKA KEN WHITMAN JR AKA WHIT WHITMAN AKA d20 Entertainment
SUPREME COURT OF THE STATE OF NEW YORK New York County LOUIS J DESY JR Plaintiff, - against- Index No.: 651541/2018 Filed: 03/30/2018 KEN WHITMAN AKA KEN WHITMAN JR AKA WHIT WHITMAN AKA d20 Entertainment
Browsing the World Wide Web with Firefox
 Browsing the World Wide Web with Firefox B 660 / 1 Try this Popular and Featurepacked Free Alternative to Internet Explorer Internet Explorer 7 arrived with a bang a few months ago, but it hasn t brought
Browsing the World Wide Web with Firefox B 660 / 1 Try this Popular and Featurepacked Free Alternative to Internet Explorer Internet Explorer 7 arrived with a bang a few months ago, but it hasn t brought
Newcomer Finances Toolkit. Fraud. Worksheets
 Newcomer Finances Toolkit Fraud Worksheets Ottawa Community Loan Fund Fonds d emprunt Communautaire d Ottawa 22 O Meara St., Causeway Work Centre, Ottawa, ON K1Y 4N6 Tel: 613-594-3535 Fax: 613-594-8118
Newcomer Finances Toolkit Fraud Worksheets Ottawa Community Loan Fund Fonds d emprunt Communautaire d Ottawa 22 O Meara St., Causeway Work Centre, Ottawa, ON K1Y 4N6 Tel: 613-594-3535 Fax: 613-594-8118
Fractions and their Equivalent Forms
 Fractions Fractions and their Equivalent Forms Little kids use the concept of a fraction long before we ever formalize their knowledge in school. Watching little kids share a candy bar or a bottle of soda
Fractions Fractions and their Equivalent Forms Little kids use the concept of a fraction long before we ever formalize their knowledge in school. Watching little kids share a candy bar or a bottle of soda
Argon2 for password hashing and cryptocurrencies
 Argon2 for password hashing and cryptocurrencies Alex Biryukov, Daniel Dinu, Dmitry Khovratovich University of Luxembourg 2nd April 2016 Motivation Password-based authentication Keyless password authentication:
Argon2 for password hashing and cryptocurrencies Alex Biryukov, Daniel Dinu, Dmitry Khovratovich University of Luxembourg 2nd April 2016 Motivation Password-based authentication Keyless password authentication:
Easy Registration Renewal for GSCWM Parents/Guardians. Step-by-Step Instructions & Tips
 Easy Registration Renewal for GSCWM Parents/Guardians Step-by-Step Instructions & Tips Thank you, so much for choosing to spend this time with Girl Scouts. We would love to have you back for another year
Easy Registration Renewal for GSCWM Parents/Guardians Step-by-Step Instructions & Tips Thank you, so much for choosing to spend this time with Girl Scouts. We would love to have you back for another year
Introduction! 2. Why You NEED This Guide 2. Step One: Research! 3. What Are Your Customers Searching For? 3. Step Two: Title Tag!
 Table of Contents Introduction! 2 Why You NEED This Guide 2 Step One: Research! 3 What Are Your Customers Searching For? 3 Step Two: Title Tag! 4 The First Thing Google Sees 4 How Do I Change It 4 Step
Table of Contents Introduction! 2 Why You NEED This Guide 2 Step One: Research! 3 What Are Your Customers Searching For? 3 Step Two: Title Tag! 4 The First Thing Google Sees 4 How Do I Change It 4 Step
Bitcoin. CS6450: Distributed Systems Lecture 20 Ryan Stutsman
 Bitcoin CS6450: Distributed Systems Lecture 20 Ryan Stutsman Material taken/derived from Princeton COS-418 materials created by Michael Freedman and Kyle Jamieson at Princeton University. Licensed for
Bitcoin CS6450: Distributed Systems Lecture 20 Ryan Stutsman Material taken/derived from Princeton COS-418 materials created by Michael Freedman and Kyle Jamieson at Princeton University. Licensed for
Monitoring Tool Made to Measure for SharePoint Admins. By Stacy Simpkins
 Monitoring Tool Made to Measure for SharePoint Admins By Stacy Simpkins Contents About the Author... 3 Introduction... 4 Who s it for and what all can it do?... 4 SysKit Insights Features... 6 Drillable
Monitoring Tool Made to Measure for SharePoint Admins By Stacy Simpkins Contents About the Author... 3 Introduction... 4 Who s it for and what all can it do?... 4 SysKit Insights Features... 6 Drillable
What You Need to Know When Buying a New Computer JackaboutComputers.com
 If it s been a while since you bought your last computer, you could probably use a quick refresher on what you need to know to make a good purchase. Computers today are a much larger part of our life than
If it s been a while since you bought your last computer, you could probably use a quick refresher on what you need to know to make a good purchase. Computers today are a much larger part of our life than
Getting started with social media and comping
 Getting started with social media and comping Promotors are taking a leap further into the digital age, and we are finding that more and more competitions are migrating to Facebook and Twitter. If you
Getting started with social media and comping Promotors are taking a leap further into the digital age, and we are finding that more and more competitions are migrating to Facebook and Twitter. If you
A yahoo! groups chat group for the Sonata Association
 A yahoo! groups email chat group for the Sonata Association The Committee are trialling an email chat group to replace the web forum which has not received a lot of interest. The main difference in the
A yahoo! groups email chat group for the Sonata Association The Committee are trialling an email chat group to replace the web forum which has not received a lot of interest. The main difference in the
Bruce K.
 Bruce K. Marshall @PwdRsch bkmarshall@passwordresearch.com Frequently use common words or names Match predictable character patterns to comply with password policies Too short to resist password cracking
Bruce K. Marshall @PwdRsch bkmarshall@passwordresearch.com Frequently use common words or names Match predictable character patterns to comply with password policies Too short to resist password cracking
BACKUP, CLONE OR IMAGE? WHY YOU SHOULD BE INTERESTED
 BACKUP, CLONE OR IMAGE? WHY YOU SHOULD BE INTERESTED BACKUP For most people, this means making copies of important files. If the originals are lost, damaged or inaccessible, the copies can be used. Usually,
BACKUP, CLONE OR IMAGE? WHY YOU SHOULD BE INTERESTED BACKUP For most people, this means making copies of important files. If the originals are lost, damaged or inaccessible, the copies can be used. Usually,
Fractions and their Equivalent Forms
 Fractions Fractions and their Equivalent Forms Little kids use the concept of a fraction long before we ever formalize their knowledge in school. Watching little kids share a candy bar or a bottle of soda
Fractions Fractions and their Equivalent Forms Little kids use the concept of a fraction long before we ever formalize their knowledge in school. Watching little kids share a candy bar or a bottle of soda
Taskbar: Working with Several Windows at Once
 Taskbar: Working with Several Windows at Once Your Best Friend at the Bottom of the Screen How to Make the Most of Your Taskbar The taskbar is the wide bar that stretches across the bottom of your screen,
Taskbar: Working with Several Windows at Once Your Best Friend at the Bottom of the Screen How to Make the Most of Your Taskbar The taskbar is the wide bar that stretches across the bottom of your screen,
Hey there, I m (name) and today I m gonna talk to you about rate of change and slope.
 Rate and Change of Slope A1711 Activity Introduction Hey there, I m (name) and today I m gonna talk to you about rate of change and slope. Slope is the steepness of a line and is represented by the letter
Rate and Change of Slope A1711 Activity Introduction Hey there, I m (name) and today I m gonna talk to you about rate of change and slope. Slope is the steepness of a line and is represented by the letter
If you ve never used Quicken, begin here. This chapter tells you how to
 In This Chapter Installing and setting up Quicken Chapter 1 Setting Up Shop Setting up your bank (or other) accounts if you re a first-time user Providing a Quicken overview Solving setup problems If you
In This Chapter Installing and setting up Quicken Chapter 1 Setting Up Shop Setting up your bank (or other) accounts if you re a first-time user Providing a Quicken overview Solving setup problems If you
Content Curation Mistakes
 Table of Contents Table of Contents... 2 Introduction... 3 Mistake #1 Linking to Poor Quality Content... 4 Mistake #2 Using the Same Few Sources... 5 Mistake #3 Curating Only Blog Posts... 6 Mistake #4
Table of Contents Table of Contents... 2 Introduction... 3 Mistake #1 Linking to Poor Quality Content... 4 Mistake #2 Using the Same Few Sources... 5 Mistake #3 Curating Only Blog Posts... 6 Mistake #4
Passwords. CS 166: Introduction to Computer Systems Security. 3/1/18 Passwords J. Liebow-Feeser, B. Palazzi, R. Tamassia, CC BY-SA 2.
 Passwords CS 166: Introduction to Computer Systems Security 1 Source: https://shop.spectator.co.uk/wp-content/uploads/2015/03/open-sesame.jpg 2 Password Authentication 3 What Do These Passwords Have in
Passwords CS 166: Introduction to Computer Systems Security 1 Source: https://shop.spectator.co.uk/wp-content/uploads/2015/03/open-sesame.jpg 2 Password Authentication 3 What Do These Passwords Have in
I m kicking off this book with Outlook s Greatest Hits, the things you ll
 In This Chapter Chapter 1 The Outlook Features You Really Need to Know Reading and creating e-mail Sending files by e-mail Checking your calendar Entering appointments and contacts Managing tasks Keeping
In This Chapter Chapter 1 The Outlook Features You Really Need to Know Reading and creating e-mail Sending files by e-mail Checking your calendar Entering appointments and contacts Managing tasks Keeping
How to buy LIVE Token with Ethereum and Bitcoin step by step
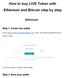 How to buy LIVE Token with Ethereum and Bitcoin step by step Ethereum Step 1. Create new wallet. Go to https://www.myetherwallet.com/, think of a strong password and enter it here: Click the button Create
How to buy LIVE Token with Ethereum and Bitcoin step by step Ethereum Step 1. Create new wallet. Go to https://www.myetherwallet.com/, think of a strong password and enter it here: Click the button Create
University of Duisburg-Essen Bismarckstr Duisburg Germany HOW BITCOIN WORKS. Matthäus Wander. June 29, 2011
 University of Duisburg-Essen Bismarckstr. 90 47057 Duisburg Germany HOW BITCOIN WORKS June 29, 2011 Overview Electronic currency system Decentralized No trusted third party involved Unstructured peer-to-peer
University of Duisburg-Essen Bismarckstr. 90 47057 Duisburg Germany HOW BITCOIN WORKS June 29, 2011 Overview Electronic currency system Decentralized No trusted third party involved Unstructured peer-to-peer
Token Sale. Participation guide
 Token Sale Participation guide 2 As the DataBroker DAO token sale is closing in, we want to inform our future participants on how to properly take part in our presale on 19th of March. At first glance,
Token Sale Participation guide 2 As the DataBroker DAO token sale is closing in, we want to inform our future participants on how to properly take part in our presale on 19th of March. At first glance,
DIRECTV Message Board
 DIRECTV Message Board DIRECTV Message Board is an exciting new product for commercial customers. It is being shown at DIRECTV Revolution 2012 for the first time, but the Solid Signal team were lucky enough
DIRECTV Message Board DIRECTV Message Board is an exciting new product for commercial customers. It is being shown at DIRECTV Revolution 2012 for the first time, but the Solid Signal team were lucky enough
Dashlane Security Whitepaper
 Dashlane Security Whitepaper November 2017 Contents 1. General Security Principles... 2 a. Protection of User Data in Dashlane... 2 b. Local access to User Data... 2 c. Local Data Usage after deciphering...
Dashlane Security Whitepaper November 2017 Contents 1. General Security Principles... 2 a. Protection of User Data in Dashlane... 2 b. Local access to User Data... 2 c. Local Data Usage after deciphering...
NEW COMPANY ~ NEW ERA ~ RENEWED COMMITMENT A DEALER PROGRAM DESIGNED FOR YOUR SUCCESS
 1811 Taylor Drive Gilbert, SC 29054 Office (803) 485-1544 Fax (866) 435-4111 Admin@FriendlySongs.com A division of KMConsolidated, LLC NEW COMPANY ~ NEW ERA ~ RENEWED COMMITMENT A DEALER PROGRAM DESIGNED
1811 Taylor Drive Gilbert, SC 29054 Office (803) 485-1544 Fax (866) 435-4111 Admin@FriendlySongs.com A division of KMConsolidated, LLC NEW COMPANY ~ NEW ERA ~ RENEWED COMMITMENT A DEALER PROGRAM DESIGNED
TOP DEVELOPERS MINDSET. All About the 5 Things You Don t Know.
 MINDSET TOP DEVELOPERS All About the 5 Things You Don t Know 1 INTRODUCTION Coding and programming are becoming more and more popular as technology advances and computer-based devices become more widespread.
MINDSET TOP DEVELOPERS All About the 5 Things You Don t Know 1 INTRODUCTION Coding and programming are becoming more and more popular as technology advances and computer-based devices become more widespread.
Midterm Exam. CS381-Cryptography. October 30, 2014
 Midterm Exam CS381-Cryptography October 30, 2014 Useful Items denotes exclusive-or, applied either to individual bits or to sequences of bits. The same operation in Python is denoted ˆ. 2 10 10 3 = 1000,
Midterm Exam CS381-Cryptography October 30, 2014 Useful Items denotes exclusive-or, applied either to individual bits or to sequences of bits. The same operation in Python is denoted ˆ. 2 10 10 3 = 1000,
Computational Complexity and Implications for Security DRAFT Notes on Infeasible Computation for MA/CS 109 Leo Reyzin with the help of Nick Benes
 Computational Complexity and Implications for Security DRAFT Notes on Infeasible Computation for MA/CS 109 Leo Reyzin with the help of Nick Benes The Study of Computational Complexity Let s summarize what
Computational Complexity and Implications for Security DRAFT Notes on Infeasible Computation for MA/CS 109 Leo Reyzin with the help of Nick Benes The Study of Computational Complexity Let s summarize what
XP: Backup Your Important Files for Safety
 XP: Backup Your Important Files for Safety X 380 / 1 Protect Your Personal Files Against Accidental Loss with XP s Backup Wizard Your computer contains a great many important files, but when it comes to
XP: Backup Your Important Files for Safety X 380 / 1 Protect Your Personal Files Against Accidental Loss with XP s Backup Wizard Your computer contains a great many important files, but when it comes to
Spam. Time: five years from now Place: England
 Spam Time: five years from now Place: England Oh no! said Joe Turner. When I go on the computer, all I get is spam email that nobody wants. It s all from people who are trying to sell you things. Email
Spam Time: five years from now Place: England Oh no! said Joe Turner. When I go on the computer, all I get is spam email that nobody wants. It s all from people who are trying to sell you things. Email
An Introduction to How PGP Works
 An Introduction to How PGP Works Revision: 0.01 Author: Kenneth Robert Ballou Date 2005-07-21 Document Change History Change Description/Reason Changed By Date Revision Initial Creation of Document Kenneth
An Introduction to How PGP Works Revision: 0.01 Author: Kenneth Robert Ballou Date 2005-07-21 Document Change History Change Description/Reason Changed By Date Revision Initial Creation of Document Kenneth
MyEtherWallet Step by Step Tutorial
 MyEtherWallet Step by Step Tutorial Step 1 1. Visit www.myetherwallet.com. The first thing you will see is Create New Wallet Create a strong password and fill it in the Enter a password field. You need
MyEtherWallet Step by Step Tutorial Step 1 1. Visit www.myetherwallet.com. The first thing you will see is Create New Wallet Create a strong password and fill it in the Enter a password field. You need
Bitcoin, Security for Cloud & Big Data
 Bitcoin, Security for Cloud & Big Data CS 161: Computer Security Prof. David Wagner April 18, 2013 Bitcoin Public, distributed, peer-to-peer, hash-chained audit log of all transactions ( block chain ).
Bitcoin, Security for Cloud & Big Data CS 161: Computer Security Prof. David Wagner April 18, 2013 Bitcoin Public, distributed, peer-to-peer, hash-chained audit log of all transactions ( block chain ).
ProgressTestA Unit 5. Vocabulary. Grammar
 ProgressTestA Unit Vocabulary 1 Completethesentenceswithappropriate words.thefirstlettersofthewordshavebeen given. a Can you believe it? She s getting married to a man she has met on a s networking site!
ProgressTestA Unit Vocabulary 1 Completethesentenceswithappropriate words.thefirstlettersofthewordshavebeen given. a Can you believe it? She s getting married to a man she has met on a s networking site!
Bitcoin, a decentralized and trustless protocol
 Bitcoin, a decentralized and trustless protocol Thomas Sibut-Pinote Inria Saclay February 12, 2015 Thomas Sibut-Pinote Bitcoin, a decentralized and trustless protocol 1 / 42 Introduction Questions 1 Introduction
Bitcoin, a decentralized and trustless protocol Thomas Sibut-Pinote Inria Saclay February 12, 2015 Thomas Sibut-Pinote Bitcoin, a decentralized and trustless protocol 1 / 42 Introduction Questions 1 Introduction
Dashlane Security White Paper July 2018
 Dashlane Security White Paper July 2018 Contents 1. General Security Principles... 2 a. Protection of User Data in Dashlane... 2 b. Local Access to User Data... 2 c. Local Data Usage After Deciphering...
Dashlane Security White Paper July 2018 Contents 1. General Security Principles... 2 a. Protection of User Data in Dashlane... 2 b. Local Access to User Data... 2 c. Local Data Usage After Deciphering...
CS103 Handout 50 Fall 2018 November 30, 2018 Problem Set 9
 CS103 Handout 50 Fall 2018 November 30, 2018 Problem Set 9 What problems are beyond our capacity to solve? Why are they so hard? And why is anything that we've discussed this quarter at all practically
CS103 Handout 50 Fall 2018 November 30, 2018 Problem Set 9 What problems are beyond our capacity to solve? Why are they so hard? And why is anything that we've discussed this quarter at all practically
 OpenSSL Hacks Anthony J. Stieber Abstract OpenSSL contains a command-line tool to do nearly everything possible within the OpenSSL library. Even better, it's probably already installed on your system.
OpenSSL Hacks Anthony J. Stieber Abstract OpenSSL contains a command-line tool to do nearly everything possible within the OpenSSL library. Even better, it's probably already installed on your system.
Lecture Nov. 21 st 2006 Dan Wendlandt ISP D ISP B ISP C ISP A. Bob. Alice. Denial-of-Service. Password Cracking. Traffic.
 15-441 Lecture Nov. 21 st 2006 Dan Wendlandt Worms & Viruses Phishing End-host impersonation Denial-of-Service Route Hijacks Traffic modification Spyware Trojan Horse Password Cracking IP Spoofing DNS
15-441 Lecture Nov. 21 st 2006 Dan Wendlandt Worms & Viruses Phishing End-host impersonation Denial-of-Service Route Hijacks Traffic modification Spyware Trojan Horse Password Cracking IP Spoofing DNS
Lecture 14 Passwords and Authentication
 Lecture 14 Passwords and Authentication Stephen Checkoway University of Illinois at Chicago CS 487 Fall 2017 Slides based on Bailey s ECE 422 Major Portions Courtesy Ryan Cunningham AUTHENTICATION Authentication
Lecture 14 Passwords and Authentication Stephen Checkoway University of Illinois at Chicago CS 487 Fall 2017 Slides based on Bailey s ECE 422 Major Portions Courtesy Ryan Cunningham AUTHENTICATION Authentication
WHITEPAPER 1.0 Boostx, Lead Developer BoxyCoin
 WHITEPAPER 1.0 Boostx, Lead Developer BoxyCoin Author Note: No Grant or Funding has been sought for the BoxyCoin Project. ABSTRACT Bitcoin and Litecoin are highly regarded as the first successful digital
WHITEPAPER 1.0 Boostx, Lead Developer BoxyCoin Author Note: No Grant or Funding has been sought for the BoxyCoin Project. ABSTRACT Bitcoin and Litecoin are highly regarded as the first successful digital
Click on a link below for additional information.
 Click on a link below for additional information. WHAT CAN I DO ON BARBIEGIRLS.COM?... 3 BARBIE GIRLS V.I.P. SOUNDS SUPER COOL. WHAT IS IT?... 3 HOW DO I BECOME A V.I.P. MEMBER? HOW MUCH DOES IT COST?...
Click on a link below for additional information. WHAT CAN I DO ON BARBIEGIRLS.COM?... 3 BARBIE GIRLS V.I.P. SOUNDS SUPER COOL. WHAT IS IT?... 3 HOW DO I BECOME A V.I.P. MEMBER? HOW MUCH DOES IT COST?...
Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi.
 Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture 18 Tries Today we are going to be talking about another data
Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture 18 Tries Today we are going to be talking about another data
Lecture 44 Blockchain Security I (Overview)
 Blockchains Architecture, Design and Use Cases Prof. Sandip Chakraborty Prof. Praveen Jayachandran Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 44 Blockchain
Blockchains Architecture, Design and Use Cases Prof. Sandip Chakraborty Prof. Praveen Jayachandran Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 44 Blockchain
Cryptography III Want to make a billion dollars? Just factor this one number!
 Cryptography III Want to make a billion dollars? Just factor this one number! 3082010a0282010100a3d56cf0bf8418d66f400be31c3f22036ca9f5cf01ef614de2eb9a1cd74a0c344b5a20d5f80df9a23c89 10c354821aa693432a61bd265ca70f309d56535a679d68d7ab89f9d32c47c1182e8a14203c050afd5f1831e5550e8700e008f2
Cryptography III Want to make a billion dollars? Just factor this one number! 3082010a0282010100a3d56cf0bf8418d66f400be31c3f22036ca9f5cf01ef614de2eb9a1cd74a0c344b5a20d5f80df9a23c89 10c354821aa693432a61bd265ca70f309d56535a679d68d7ab89f9d32c47c1182e8a14203c050afd5f1831e5550e8700e008f2
