SYMANTEC INTELLIGENCE REPORT NOVEMBER 2015
|
|
|
- Basil Thomas
- 5 years ago
- Views:
Transcription
1 SYNTEC INTELLIGENCE REPORT NOVEBER 2015
2 2 November Summary 4 From the Security Response Blog 4 Terror-lert Spam Targets the iddle East, Canada to Spread alware 5 November in Numbers 6 Targeted ttacks & Phishing 6 Top 10 Industries Targeted in Spear-Phishing ttacks 6 Spear-Phishing ttacks by Size of Targeted Organization 7 Phishing Rate 7 Proportion of Traffic Identified as Phishing by Industry Sector 8 Proportion of Traffic Identified as Phishing by Organization Size 9 Vulnerabilities 9 Total Number of Vulnerabilities 10 alware 10 New alware Variants 10 Top 10 alware 11 Top 10 ac OSX alware Blocked on OSX Endpoints 12 Proportion of Traffic in Which alware Was Detected 12 Percent of alware as URL vs. ttachment by onth 13 Proportion of Traffic Identified as alicious by Industry Sector 13 Proportion of Traffic Identified as alicious by Industry Sector 13 Proportion of Traffic Identified as alicious by Organization Size Welcome to the November edition of the Symantec Intelligence report. Symantec Intelligence aims to provide the latest analysis of cyber security threats, trends, and insights concerning malware, spam, and other potentially harmful business risks. Symantec has established the most comprehensive source of Internet threat data in the world through the Symantec Global Intelligence Network, which is made up of more than 57.6 million attack sensors and records thousands of events per second. This network monitors threat activity in over 157 countries and territories through a combination of Symantec products and services such as Symantec DeepSight Intelligence, Symantec anaged Security Services, Norton consumer products, and other third-party data sources. 14 obile & Social edia 14 ndroid obile alware Families by onth 14 New ndroid Variants per Family by onth 15 Social edia 16 Spam 16 Overall Spam Rate 16 Proportion of Traffic Identified as Spam by Industry Sector 17 Proportion of Traffic Identified as Spam by Organization Size 18 bout Symantec 18 ore Information
3 3 November 2015 Summary The proportion of traffic containing malware was up in November, where one in 140 s contained malware. Public dministration was the most targeted sector in November, with one in every s containing malware. Organizations with employees were most likely to be targeted by malicious in the month of November, where one in s was malicious. In one campaign in particular, attackers attempted to prey upon user s fears of terror attacks in light of recent international news. While the attachments were presented as security tips to help the recipients protect themselves, one of the files contained a malicious payload that included a remote access Trojan. (See this month s Security Response blog for more details.) Interestingly, there were 19.4 million new pieces of malware created in November. This rate has steadily declined in the second half of 2015, from a high of 57.6 million seen in une. While such a decline could point to a reduction in malicious activity, it could also mean that attackers are having a higher success rate in compromising computers, thus not needing to produce as much malware to achieve their goals. The overall spam rate in November was also up at 54.1 percent, an increase of 0.6 percentage points from October. t 57 percent, the ining sector again had the highest spam rate during November. In terms of targeted attacks in general, the Finance, Insurance, & Real Estate sector was the most targeted sector during November, comprising 41 percent of all targeted attacks. Large enterprises were the target of 49.9 percent of these spear-phishing attacks. Ben Nahorney, Cyber Security Threat nalyst symantec_intelligence@symantec.com ethodology The comprises monthly analysis based on the latest data available from the Symantec Global Intelligence Network. s new information is continually being discovered, some metrics published in the report may be subject to change. Subsequent reports will be updated to reflect the latest information in order to ensure the most accurate reporting and analysis of the threat landscape.
4 4 November 2015 From the Security Response Blog Terror-lert Spam Targets the iddle East, Canada to Spread alware Cybercriminals spoof law enforcement officials in Dubai, Bahrain, Turkey, and Canada to send terror-alert spear-phishing s containing Backdoor.Sockrat. By Symantec Security Response Last month, Symantec observed malicious s spoofing the address of one United rab Emirates (UE) law enforcement agency, particularly the Dubai Police Force. These spear-phishing s, which read like a warning from the Dubai Police, bank on users fear of terror attacks to trick them into executing the malicious attachments. The attachments are disguised as valuable security tips that could help recipients to protect themselves, as well as their companies and their families, from potential terror attacks that may occur in their business location. To add more credibility to the s, the crooks impersonate the incumbent Dubai Police lieutenant general, who is also the head of general security for the emirate of Dubai, by signing the with his name. The s come with two attachments, one of which is a PDF file that is not actually malicious but acts as a decoy file. The malware resides in the other attachment, an archive, as a.jar file. Further analysis of the malware confirms that the cybercriminals behind this campaign are using a multiplatform remote access Trojan (RT) called socket (detected as Backdoor.Sockrat). This RT is a new product from the creators of the lienspy RT, which has been discontinued earlier this year. Targets beyond the UE While the group behind this campaign mainly targeted UE-based companies and employees, we have also seen similar spear-phishing runs targeting three other countries: Bahrain, Turkey and, more recently, Canada. Like in the Dubai campaign, the cybercriminals are also using incumbent law enforcement officials names in these countries to lend credibility to their fake terror alerts, which also purport to provide protective measures supposedly outlined in attached files. The group is expanding their reach and we may see new models targeting additional countries. Interestingly enough, despite not being entirely written in the countries respective official languages, the s are pretty crafty. ll officials used in the cybercriminals scheme are currently in office. The subject in most cases reflects the name of an employee who works for the targeted company. ll these details show that the crooks did some research before sending these phishing s. If they do not have any employee information, then they would other targets in the company that could provide them an entry point, such as customer service representatives or IT department personnel. t the time of writing, we can confirm that this campaign is aimed at various big companies in the iddle East and Canada. While the campaign does not target a specific type of industry, we have observed such s sent to the following sectors: energy, defense contractor, finance, government, marketing, and IT. With recent events such as those witnessed in Paris and Beirut, terrorist attacks have become a threat across the world, and terror groups have been known to make their presence felt online too. We may yet see more of these kinds of social engineering tactics preying on real-world fears. bout the Security Response blog In the we republish a blog that highlights key data or an event that stood out during the month. Our security researchers around the world frequently publish new blogs during the month on topics such as malware, security risks, vulnerabilities, and spam. For the latest security news and information, visit:
5 5 November 2015 NOVEBER IN NUBERS
6 6 November 2015 Targeted ttacks & Phishing Finance, Insurance & Real Estate Transportation, Communications, Electric, Gas & Sanitary Services Services - Non Traditional Services - Professional Wholesale Energy/Utilities anufacturing Retail ining Nonclassifiable Establishments Top 10 Industries Targeted in Spear-Phishing ttacks November 4% 3% 4% 4% 4% N 4% 5% 3% 1% 2% 1% 1% 2% 12% 10% 11% 18% October 41% Top 10 Industries Targeted in Spear-Phishing ttacks Company Size November October % 19.7% % 5.2% 69% The Finance, Insurance, & Real Estate sector was the most targeted sector during November, comprising 41 percent of all targeted attacks. Large enterprises were the target of 49.9 percent of spear-phishing attacks in November. Similarly, 24.9 percent of attacks were directed at small businesses with less than 250 employees % 2.6% % 3.7% % 0.9% % 67.9% Spear-Phishing ttacks by Size of Targeted Organization Spear-Phishing ttacks by Size of Targeted Organization
7 7 November 2015 D 2015 F S O N The overall phishing rate has decreased slightly this month, where one in 2,278 s was a phishing attempt IN ,517 1,004 1,465 2,057 1,865 1,628 1,905 1, ,666 2,448 2,174 2,278 Phishing Rate Inverse Graph: Smaller Number = Greater Risk Phishing Rate Industry November October griculture, Forestry, & Fishing 1 in 1, in 1,082.9 Nonclassifiable Establishments 1 in 1, in 1,036.9 griculture, Forestry, & Fishing topped the list of industries with the highest proportion of phishing attempts during the month of November. Public dministration 1 in 1, in 1,397.0 Services - Professional 1 in 1, in 2,011.3 ining 1 in 2, in 1,957.6 Finance, Insurance, & Real Estate 1 in 2, in 2,262.6 Services - Non Traditional 1 in 2, in 2,466.1 Wholesale 1 in 2, in 2,431.5 Construction 1 in 2, in 2,486.5 Transportation, Communications, Electric, Gas, & Sanitary Services 1 in 3, in 3,016.4 Proportion of Traffic Identified as Phishing by Industry Sector.cloud Proportion of Traffic Identified as Phishing by Industry Sector
8 8 November 2015 Company Size November October in 2, in 2,015.2 Companies with employees were the most targeted organization size in November for phishing attempts in 1, in 1, in 2, in 2, in 2, in 2, in 1, in 1, in 2, in 2,421.4 Proportion of Traffic Identified as Phishing by Organization Size.cloud Proportion of Traffic Identified as Phishing by Organization Size
9 9 November 2015 Vulnerabilities The number of vulnerabilities disclosed decreased in November, from 441 in October to 346 reported during this month D 2015 F S O N Total Number of Vulnerabilities Total Number of Vulnerabilities
10 10 November 2015 alware ILLIONS There were 19.4 million new pieces of malware created in November. This rate has steadily declined in the second half of 2015, from a high of 57.6 million seen in une D New alware Variants 2015 F S O N New alware Variants Rank alware Name November Percentage alware Name 1 W32.Ramnit!html 7.6% W32.Ramnit!html 7.0% October Percentage W32.Ramnit!html and W32. lmanahe.b!inf continue to be the most commonly seen malware detections in November. 2 W32.lmanahe.B!inf 6.0% W32.lmanahe.B!inf 5.8% 3 W32.Sality.E 5.5% W32.Sality.E 5.7% 4 W32.Ramnit.B 4.0% W32.Downadup.B 4.0% 5 W32.Downadup.B 3.6% W32.Ramnit.B 4.0% 6 W97.Downloader 3.1% W32.Ramnit.B!inf 2.8% 7 W32.Ramnit.B!inf 3.0% W32.Virut.CF 1.7% 8 W32.Virut.CF 1.7% W97.Downloader 1.6% 9 W32.Chir.B@mm(html) 1.7% W32.SillyFDC.BDP!lnk 1.4% 10 Trojan.Swifi 1.3% W32.Chir.B@mm(html) 1.4% Top 10 alware Top 10 alware
11 11 November 2015 Rank alware Name November Percentage alware Name October Percentage OSX.CnetDownloader was the most commonly seen OS X threat on OS X endpoints in November. 1 OSX.CnetDownloader 82.6% OSX.Sudoprint 42.0% 2 OSX.Sudoprint 4.5% OSX.RSPlug. 9.9% 3 OSX.RSPlug. 1.9% OSX.Klog. 6.1% 4 OSX.Klog. 1.7% OSX.CnetDownloader 5.8% 5 OSX.Sabpab 1.4% OSX.Wirelurker 5.5% 6 OSX.Keylogger 1.4% OSX.Flashback.K 5.4% 7 OSX.Okaz 0.9% OSX.Luaddit 3.9% 8 OSX.Wirelurker 0.9% OSX.Keylogger 3.6% 9 OSX.Luaddit 0.8% OSX.Exploit.Launchd 3.0% 10 OSX.Remoteaccess 0.7% OSX.Okaz 2.4% Top 10 ac OS X alware Blocked on OS X Endpoints Top 10 ac OSX alware Blocked on OSX Endpoints
12 12 November D 2015 F S O N The proportion of traffic containing malware increased this month, where one in 140 s contained malware IN Inverse Graph: Smaller Number = Greater Risk Proportion of Traffic in Which alware Was Detected Proportion of Traffic in Which alware Was Detected 25% 20 The percentage of malware that contains a URL remained low this month, hovering around two percent D F S 2 2 O N Percent of alware as URL vs. ttachment by onth Percent of alware as URL vs. ttachment by onth
13 13 November 2015 Industry November October Public dministration 1 in in Services - Professional 1 in in Public dministration was the most targeted sector in November for malware, where one in every s contained malware. griculture, Forestry, & Fishing 1 in in Wholesale 1 in in Construction 1 in in Services - Non Traditional 1 in in Finance, Insurance, & Real Estate 1 in in ining 1 in in Transportation, Communications, Electric, Gas, & Sanitary Services 1 in in Nonclassifiable Establishments 1 in in Proportion of Traffic Identified as alicious by Industry Sector.cloud Proportion of Traffic Identified as alicious by Industry Sector Company Size November October in in in in Organizations with employees were most likely to be targeted by malicious in the month of November, where one in s was malicious in in in in in in in in Proportion of Traffic Identified as alicious by Organization Size.cloud Proportion of Traffic Identified as alicious by Organization Size
14 14 November 2015 obile & Social edia 9 8 In November there was one new mobile malware family discovered D F S 1 1 O N ndroid obile alware Families by onth ndroid obile alware Families by onth There was an average of 46 ndroid malware variants per family in the month of in November D 2015 F S O N New ndroid Variants per Family by onth New ndroid Variants per Family by onth
15 15 November % Last 12 onths In the last twelve months, 77 percent of social media threats required end users to propagate them Fake offerings comprised 16 percent of social media threats anual Sharing Fake Offering 5 Likejacking 2 Fake pps.02 Comment acking anual Sharing These rely on victims to actually do the work of sharing the scam by presenting them with intriguing videos, fake offers or messages that they share with their friends. Fake Offering These scams invite social network users to join a fake event or group with incentives such as free gift cards. oining often requires the user to share credentials with the attacker or send a text to a premium rate number. Likejacking Using fake Like buttons, attackers trick users into clicking website buttons that install malware and may post updates on a user s newsfeed, spreading the attack. Fake pps Users are invited to subscribe to an application that appears to be integrated for use with a social network, but is not as described and may be used to steal credentials or harvest other personal data. Comment acking This attack is similar to the "Like" jacking where the attacker tricks the user into submitting a comment about a link or site, which will then be posted to his/her wall. Social edia Social edia
16 16 November 2015 Spam % 53.5% 52.2% +.6% pts +1.3% pts -.5% pts The overall spam rate in November was 54.1 percent, up 0.6 percentage points from October. November October September Overall Spam Rate Overall Spam Rate Industry November October ining 57.0% 57.8% anufacturing 55.5% 55.4% t 57 percent, the ining sector again had the highest spam rate during November. The anufacturing sector came in second with 55.5 percent. Services - Non Traditional 55.2% 52.7% Construction 55.0% 54.0% griculture, Forestry & Fishing 54.7% 53.9% Public dministration 54.7% 52.7% Services - Professional 54.2% 53.9% Retail 54.1% 54.2% Nonclassifiable Establishments 53.6% 53.6% Wholesale 53.4% 53.2% Proportion of Traffic Identified as Spam by Industry Sector.cloud Proportion of Traffic Identified as Spam by Industry Sector
17 17 November 2015 Company Size November October % 53.4% % 54.4% While most organization sizes had around a 54 percent spam rate, organizations with employees had the highest rate at 54.9 percent % 53.8% % 53.2% % 53.7% % 53.3% Proportion of Traffic Identified as Spam by Organization Size.cloud Proportion of Traffic Identified as Spam by Organization Size
18 18 November 2015 bout Symantec Symantec Corporation (NSDQ: SYC) is the global leader in cybersecurity. Operating one of the world s largest cyber intelligence networks, we see more threats, and protect more customers from the next generation of attacks. We help companies, governments and individuals secure their most important data wherever it lives. ore Information Symantec Worldwide: ISTR and Symantec Intelligence Resources: Symantec Security Response: Norton Threat Explorer:
19 Symantec Corporation World Headquarters 350 Ellis Street ountain View, C US +1 (650) (800) For specific country offices and contact numbers, please visit our website. For product information in the U.S., call toll-free 1 (800) Copyright 2015 Symantec Corporation. ll rights reserved. Symantec, the Symantec Logo, and the Checkmark Logo are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners 04/15 21,
SYMANTEC INTELLIGENCE REPORT NOVEMBER 2014
 SYNTEC INTELLIGENCE REPORT NOVEBER p. 2 Symantec Intelligence Report :: NOVEBER CONTENTS 3 Summary 4 TRGETE TTCKS + T BRECHES 5 Targeted ttacks 5 ttachments Used in Spear-Phishing Emails 5 Spear-Phishing
SYNTEC INTELLIGENCE REPORT NOVEBER p. 2 Symantec Intelligence Report :: NOVEBER CONTENTS 3 Summary 4 TRGETE TTCKS + T BRECHES 5 Targeted ttacks 5 ttachments Used in Spear-Phishing Emails 5 Spear-Phishing
Top 10 Global Threat Rank by Source
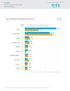 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
IC B01: Internet Security Threat Report: How to Stay Protected
 IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
Advanced Threat Defense Certification Testing Report. Symantec Corporation Symantec Advanced Threat Protection
 Advanced Threat Defense Certification Testing Report Symantec Advanced Threat Protection ICSA Labs Advanced Threat Defense December 8, 2015 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Advanced Threat Defense Certification Testing Report Symantec Advanced Threat Protection ICSA Labs Advanced Threat Defense December 8, 2015 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Phishing Activity Trends Report August, 2005
 Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report August, 2006
 Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Phishing Activity Trends Report October, 2004
 Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
REPORT. proofpoint.com
 REPORT proofpoint.com Email fraud, also known as business email compromise (BEC), is one of today s greatest cyber threats. These socially engineered attacks seek to exploit people rather than technology.
REPORT proofpoint.com Email fraud, also known as business email compromise (BEC), is one of today s greatest cyber threats. These socially engineered attacks seek to exploit people rather than technology.
Evolution of Spear Phishing. White Paper
 Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
Security & Phishing
 Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
The Credential Phishing Handbook. Why It Still Works and 4 Steps to Prevent It
 The Credential Phishing Handbook Why It Still Works and 4 Steps to Prevent It Introduction Phishing is more than 20 years old, but still represents more than 90% of targeted attacks. The reason is simple:
The Credential Phishing Handbook Why It Still Works and 4 Steps to Prevent It Introduction Phishing is more than 20 years old, but still represents more than 90% of targeted attacks. The reason is simple:
Office 365 Buyers Guide: Best Practices for Securing Office 365
 Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
SYMANTEC ENTERPRISE SECURITY. Symantec Internet Security Threat Report September 2005 Power and Energy Industry Data Sheet
 SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
CloudSOC and Security.cloud for Microsoft Office 365
 Solution Brief CloudSOC and Email Security.cloud for Microsoft Office 365 DID YOU KNOW? Email is the #1 delivery mechanism for malware. 1 Over 40% of compliance related data in Office 365 is overexposed
Solution Brief CloudSOC and Email Security.cloud for Microsoft Office 365 DID YOU KNOW? Email is the #1 delivery mechanism for malware. 1 Over 40% of compliance related data in Office 365 is overexposed
Symantec Advanced Threat Protection: Endpoint
 Symantec Advanced Threat Protection: Endpoint Data Sheet: Advanced Threat Protection The Problem Virtually all of today's advanced persistent threats leverage endpoint systems in order to infiltrate their
Symantec Advanced Threat Protection: Endpoint Data Sheet: Advanced Threat Protection The Problem Virtually all of today's advanced persistent threats leverage endpoint systems in order to infiltrate their
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Panda Security 2010 Page 1
 Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
Phishing Activity Trends Report January, 2005
 Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Discussion. Pete Scheidt Lead Information Security Analyst California ISO
 Phishing Discussion Pete Scheidt Lead Information Security Analyst California ISO 2 Phish What is Phishing Types of Phish 3 Phish What is Phishing Attackers (Phishers) would email (cast their nets) far
Phishing Discussion Pete Scheidt Lead Information Security Analyst California ISO 2 Phish What is Phishing Types of Phish 3 Phish What is Phishing Attackers (Phishers) would email (cast their nets) far
Symantec Secure One Services Program Brief
 Symantec Secure One Services Program Brief Align with the industry leader Differentiate your business Increase support services revenue July 2017 Table of Contents Secure One Services Program Overview
Symantec Secure One Services Program Brief Align with the industry leader Differentiate your business Increase support services revenue July 2017 Table of Contents Secure One Services Program Overview
Prevent and Detect Malware with Symantec Advanced Threat Protection: Network
 WHITE PAPER: SYMANTEC ADVANCED THREAT PROTECTION........................................ Prevent and Detect Malware with Symantec Advanced Threat Protection: Network Who should read this paper This white
WHITE PAPER: SYMANTEC ADVANCED THREAT PROTECTION........................................ Prevent and Detect Malware with Symantec Advanced Threat Protection: Network Who should read this paper This white
Symantec Security.cloud
 Data Sheet: Messaging Security filters unwanted messages and protects mailboxes from targeted attacks. The service has selflearning capabilities and Symantec intelligence to deliver highly effective and
Data Sheet: Messaging Security filters unwanted messages and protects mailboxes from targeted attacks. The service has selflearning capabilities and Symantec intelligence to deliver highly effective and
Security and Compliance for Office 365
 Security and Compliance for Office 365 [Proofpoint has] given us our time back to focus on the really evil stuff. CISO, Global 500 Manufacturer Like millions of businesses around the world, you may be
Security and Compliance for Office 365 [Proofpoint has] given us our time back to focus on the really evil stuff. CISO, Global 500 Manufacturer Like millions of businesses around the world, you may be
Symantec Security Monitoring Services
 24x7 real-time security monitoring and protection Protect corporate assets from malicious global threat activity before it impacts your network. Partnering with Symantec skilled and experienced analysts
24x7 real-time security monitoring and protection Protect corporate assets from malicious global threat activity before it impacts your network. Partnering with Symantec skilled and experienced analysts
Product Roadmap Symantec Endpoint Protection Suzanne Konvicka & Paul Murgatroyd
 Product Roadmap Symantec Endpoint Protection Suzanne Konvicka & Paul Murgatroyd Symantec Endpoint Protection Product Roadmap 1 Safe Harbor Disclaimer Any information regarding pre-release Symantec offerings,
Product Roadmap Symantec Endpoint Protection Suzanne Konvicka & Paul Murgatroyd Symantec Endpoint Protection Product Roadmap 1 Safe Harbor Disclaimer Any information regarding pre-release Symantec offerings,
Internet Security Threat Report Volume XIII. Patrick Martin Senior Product Manager Symantec Security Response October, 2008
 Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
How Enterprise Tackles Phishing. Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong
 How Enterprise Tackles Phishing Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong Hackers turning to easy marks - Social engineering Phishing was the #1 threat vector (> 50%) for Office
How Enterprise Tackles Phishing Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong Hackers turning to easy marks - Social engineering Phishing was the #1 threat vector (> 50%) for Office
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
Phishing Activity Trends Report March, 2005
 Phishing Activity Trends Report March, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report March, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Automated Context and Incident Response
 Technical Brief Automated Context and Incident Response www.proofpoint.com Incident response requires situational awareness of the target, his or her environment, and the attacker. However, security alerts
Technical Brief Automated Context and Incident Response www.proofpoint.com Incident response requires situational awareness of the target, his or her environment, and the attacker. However, security alerts
2018 Edition. Security and Compliance for Office 365
 2018 Edition Security and Compliance for Office 365 [Proofpoint has] given us our time back to focus on the really evil stuff. CISO, Global 500 Manufacturer Like millions of businesses around the world,
2018 Edition Security and Compliance for Office 365 [Proofpoint has] given us our time back to focus on the really evil stuff. CISO, Global 500 Manufacturer Like millions of businesses around the world,
FAQ. Usually appear to be sent from official address
 FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
May 2011 Intelligence Report
 Symantec.cloud MessageLabs Intelligence May 2011 Intelligence Report For the First Time, Spammers Establish Their Own Fake URL-Shortening Services; Spam Rate Rises by 2.9% Welcome to the May edition of
Symantec.cloud MessageLabs Intelligence May 2011 Intelligence Report For the First Time, Spammers Establish Their Own Fake URL-Shortening Services; Spam Rate Rises by 2.9% Welcome to the May edition of
Israel Internet Security Threat Profile
 Israel Internet Security Threat Profile Worldwide Ranking.%.%.%.%.%.%.%.%.%.%.% Overall Average Spam Zombies Malicious Code Phishing Hosts Bots Network Attacking Countries Copyright Symantec Corporation.
Israel Internet Security Threat Profile Worldwide Ranking.%.%.%.%.%.%.%.%.%.%.% Overall Average Spam Zombies Malicious Code Phishing Hosts Bots Network Attacking Countries Copyright Symantec Corporation.
New Zealand National Cyber Security Centre Incident Summary
 New Zealand National Cyber Security Centre 2013 Incident Summary National Cyber Security Centre 2013 Incident Summary Foreword The incidents summarised in this report reinforce that cyber security is truly
New Zealand National Cyber Security Centre 2013 Incident Summary National Cyber Security Centre 2013 Incident Summary Foreword The incidents summarised in this report reinforce that cyber security is truly
Machine-Powered Learning for People-Centered Security
 White paper Machine-Powered Learning for People-Centered Security Protecting Email with the Proofpoint Stateful Composite Scoring Service www.proofpoint.com INTRODUCTION: OUTGUNNED AND OVERWHELMED Today
White paper Machine-Powered Learning for People-Centered Security Protecting Email with the Proofpoint Stateful Composite Scoring Service www.proofpoint.com INTRODUCTION: OUTGUNNED AND OVERWHELMED Today
Delivering Integrated Cyber Defense for the Cloud Generation Darren Thomson
 Delivering Integrated Cyber Defense for the Generation Darren Thomson Vice President & CTO, EMEA Region Symantec In 2009 there were 2,361,414 new piece of malware created. In 2015 that number was 430,555,582
Delivering Integrated Cyber Defense for the Generation Darren Thomson Vice President & CTO, EMEA Region Symantec In 2009 there were 2,361,414 new piece of malware created. In 2015 that number was 430,555,582
Train employees to avoid inadvertent cyber security breaches
 Train employees to avoid inadvertent cyber security breaches TRAIN EMPLOYEES TO AVOID INADVERTENT CYBER SECURITY BREACHES PAGE 2 How much do you know about cyber security? Small business owners often lack
Train employees to avoid inadvertent cyber security breaches TRAIN EMPLOYEES TO AVOID INADVERTENT CYBER SECURITY BREACHES PAGE 2 How much do you know about cyber security? Small business owners often lack
Symantec Protection Suite Add-On for Hosted Security
 Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
Measuring Cyber Risk Understanding the Right Data Sources. Sponsored By:
 Measuring Cyber Risk Understanding the Right Data Sources Sponsored By: Measuring Cyber Risk Understanding the Right Data Sources Visit www.advisenltd.com at the end of this webinar to download: Copy of
Measuring Cyber Risk Understanding the Right Data Sources Sponsored By: Measuring Cyber Risk Understanding the Right Data Sources Visit www.advisenltd.com at the end of this webinar to download: Copy of
Advanced Threat Defense Certification Testing Report. Trend Micro Incorporated Trend Micro Deep Discovery Inspector
 Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
The Cost of Phishing. Understanding the True Cost Dynamics Behind Phishing Attacks A CYVEILLANCE WHITE PAPER MAY 2015
 The Cost of Phishing Understanding the True Cost Dynamics Behind Phishing Attacks A CYVEILLANCE WHITE PAPER MAY 2015 Executive Summary.... 3 The Costs... 4 How To Estimate the Cost of an Attack.... 5 Table
The Cost of Phishing Understanding the True Cost Dynamics Behind Phishing Attacks A CYVEILLANCE WHITE PAPER MAY 2015 Executive Summary.... 3 The Costs... 4 How To Estimate the Cost of an Attack.... 5 Table
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS
 10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
Security Gap Analysis: Aggregrated Results
 Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
Phishing Activity Trends Report November, 2004
 Phishing Activity Trends Report November, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report November, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Proofpoint, Inc.
 1 2018 Proofpoint, Inc. Juan Carlos Cabrera Country Manager Caribbean & Central America AMENAZAS EN EL 2018 SABES QUIEN ESTA UTILIZANDO TU DOMINIO? 2 2017 Proofpoint, Inc. Juan Carlos Cabrera Country Manager
1 2018 Proofpoint, Inc. Juan Carlos Cabrera Country Manager Caribbean & Central America AMENAZAS EN EL 2018 SABES QUIEN ESTA UTILIZANDO TU DOMINIO? 2 2017 Proofpoint, Inc. Juan Carlos Cabrera Country Manager
REPORT. Year In Review. proofpoint.com
 REPORT Year In Review proofpoint.com Email fraud, also known as business email compromise (BEC), is one of today s greatest cyber threats. These socially engineered attacks seek to exploit people rather
REPORT Year In Review proofpoint.com Email fraud, also known as business email compromise (BEC), is one of today s greatest cyber threats. These socially engineered attacks seek to exploit people rather
9 Steps to Protect Against Ransomware
 9 Steps to Protect Against Ransomware IT Support Analyst Task Overview Security Manager Security Dashboard Self Service log Secur Devices With Vulnerabilities Critical Important/High Moderate/Medium 40
9 Steps to Protect Against Ransomware IT Support Analyst Task Overview Security Manager Security Dashboard Self Service log Secur Devices With Vulnerabilities Critical Important/High Moderate/Medium 40
Data Sheet: Endpoint Security Symantec Multi-tier Protection Trusted protection for endpoints and messaging environments
 Trusted protection for endpoints and messaging environments Overview creates a protected endpoint and messaging environment that is secure against today s complex data loss, malware, and spam threats controlling
Trusted protection for endpoints and messaging environments Overview creates a protected endpoint and messaging environment that is secure against today s complex data loss, malware, and spam threats controlling
Symantec Intelligence Quarterly: Best Practices and Methodologies October - December, 2009
 Symantec Intelligence Quarterly: Best Practices and Methodologies White Paper: Symantec Intelligence Quarterly Symantec Intelligence Quarterly: Best Practices and Methodologies Contents Symantec best
Symantec Intelligence Quarterly: Best Practices and Methodologies White Paper: Symantec Intelligence Quarterly Symantec Intelligence Quarterly: Best Practices and Methodologies Contents Symantec best
Cybersecurity 2016 Survey Summary Report of Survey Results
 Introduction In 2016, the International City/County Management Association (ICMA), in partnership with the University of Maryland, Baltimore County (UMBC), conducted a survey to better understand local
Introduction In 2016, the International City/County Management Association (ICMA), in partnership with the University of Maryland, Baltimore County (UMBC), conducted a survey to better understand local
RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY
 RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY RSA CYOTA PROJECT PROPOSAL RSA FRAUDACTION ANTI-PHISHING SERVICE V.1 2011 Overview This brief highlights the benefits
RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY RSA CYOTA PROJECT PROPOSAL RSA FRAUDACTION ANTI-PHISHING SERVICE V.1 2011 Overview This brief highlights the benefits
with Advanced Protection
 with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
PEOPLE CENTRIC SECURITY THE NEW
 PEOPLE CENTRIC SECURITY THE NEW PARADIGM IN CYBERSECURITY David Karlsson SE Nordics March 2018 1 2018 Proofpoint, Inc. Proofpoint at a Glance LEADING CUSTOMERS DEEP SECURITY DNA UNIQUE VISIBILITY PARTNERS
PEOPLE CENTRIC SECURITY THE NEW PARADIGM IN CYBERSECURITY David Karlsson SE Nordics March 2018 1 2018 Proofpoint, Inc. Proofpoint at a Glance LEADING CUSTOMERS DEEP SECURITY DNA UNIQUE VISIBILITY PARTNERS
Holiday Season Cyberattacks on Pace to Increase by Nearly 60%
 Holiday Season Cyberattacks on Pace to Increase by Nearly 60% NOVEMBER 2018 1 Tis the season for cyberattacks. According to the Carbon Black Threat Analysis Unit (TAU), organizations should expect to see
Holiday Season Cyberattacks on Pace to Increase by Nearly 60% NOVEMBER 2018 1 Tis the season for cyberattacks. According to the Carbon Black Threat Analysis Unit (TAU), organizations should expect to see
SYMANTEC SECURITY UPDATE JUNE 2005
 SYMANTEC SECURITY UPDATE JUNE 005 Symantec Security Update - June 005 Worldwide and APAC Monthly report examining recent high severity vulnerabilities, cyber attacks, malicious code and spam activity.
SYMANTEC SECURITY UPDATE JUNE 005 Symantec Security Update - June 005 Worldwide and APAC Monthly report examining recent high severity vulnerabilities, cyber attacks, malicious code and spam activity.
The State of Spam A Monthly Report June Generated by Symantec Messaging and Web Security
 The State of Spam A Monthly Report June 2007 Generated by Symantec Messaging and Web Security Monthly Spam Landscape Spam activity in May 2007 was overall consistent with trends observed in previous months.
The State of Spam A Monthly Report June 2007 Generated by Symantec Messaging and Web Security Monthly Spam Landscape Spam activity in May 2007 was overall consistent with trends observed in previous months.
IBM Security Systems IBM X-Force 2012 Annual Trend and Risk Report
 IBM Security Systems IBM X-Force 2012 Annual Trend and Risk Report Leslie Horacek X-Force Threat Response Manager horacek@be.ibm.com April 2013 1 X-Force is the foundation for advanced security and threat
IBM Security Systems IBM X-Force 2012 Annual Trend and Risk Report Leslie Horacek X-Force Threat Response Manager horacek@be.ibm.com April 2013 1 X-Force is the foundation for advanced security and threat
Managed Enterprise Phishing Protection. Comprehensive protection delivered 24/7 by anti-phishing experts
 Managed Enterprise Phishing Protection Comprehensive protection delivered 24/7 by anti-phishing experts MANAGED ENTERPRISE PHISHING PROTECTION 24/7 expert protection against phishing attacks that get past
Managed Enterprise Phishing Protection Comprehensive protection delivered 24/7 by anti-phishing experts MANAGED ENTERPRISE PHISHING PROTECTION 24/7 expert protection against phishing attacks that get past
Securing Office 365 with Symantec
 February, 2016 Solution Overview: Enterprise Security Adoption of Microsoft Office 365, Google Apps, and other cloud-based productivity solutions is growing. Microsoft in its Ignite 2015 session claimed
February, 2016 Solution Overview: Enterprise Security Adoption of Microsoft Office 365, Google Apps, and other cloud-based productivity solutions is growing. Microsoft in its Ignite 2015 session claimed
2017 Annual Meeting of Members and Board of Directors Meeting
 2017 Annual Meeting of Members and Board of Directors Meeting Dan Domagala; "Cybersecurity: An 8-Point Checklist for Protecting Your Assets" Join this interactive discussion about cybersecurity trends,
2017 Annual Meeting of Members and Board of Directors Meeting Dan Domagala; "Cybersecurity: An 8-Point Checklist for Protecting Your Assets" Join this interactive discussion about cybersecurity trends,
DMARC ADOPTION AMONG
 DMARC ADOPTION AMONG US and UK Nonprofit Organizations Q2 2018 Featuring Matthew Vernhout (CIPP/C) Director of Privacy, 250ok TABLE OF CONTENTS Introduction... 03 Research Overview... 04 US and UK Nonprofit
DMARC ADOPTION AMONG US and UK Nonprofit Organizations Q2 2018 Featuring Matthew Vernhout (CIPP/C) Director of Privacy, 250ok TABLE OF CONTENTS Introduction... 03 Research Overview... 04 US and UK Nonprofit
KnowBe4 is the world s largest integrated platform for awareness training combined with simulated phishing attacks.
 KnowBe4 is the world s largest integrated platform for awareness training combined with simulated phishing attacks. About Us The world s most popular integrated Security Awareness Training and Simulated
KnowBe4 is the world s largest integrated platform for awareness training combined with simulated phishing attacks. About Us The world s most popular integrated Security Awareness Training and Simulated
Wayward Wi-Fi. How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk
 Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
Small Business Is Big Business in Cybercrime A TrendLabs Primer
 Small Business Is Big Business in Cybercrime A TrendLabs Primer Things Every Small Business Should Know About Web Threats and Cybercrime For cybercriminals, no business is too small to exploit. Albeit
Small Business Is Big Business in Cybercrime A TrendLabs Primer Things Every Small Business Should Know About Web Threats and Cybercrime For cybercriminals, no business is too small to exploit. Albeit
Who We Are! Natalie Timpone
 Who We Are! Natalie Timpone Manager of Security Business Management Office Enterprise Security Awareness Manager Carmelo Walsh Security, Risk, and Compliance Security Awareness Subject Matter Expert Who
Who We Are! Natalie Timpone Manager of Security Business Management Office Enterprise Security Awareness Manager Carmelo Walsh Security, Risk, and Compliance Security Awareness Subject Matter Expert Who
QUARTERLY TRENDS AND ANALYSIS REPORT
 September 1, 2007 Volume 2, Issue 3 QUARTERLY TRENDS AND ANALYSIS REPORT www.us-cert.gov Introduction This report summarizes and provides analysis of incident reports submitted to US-CERT during the U.S.
September 1, 2007 Volume 2, Issue 3 QUARTERLY TRENDS AND ANALYSIS REPORT www.us-cert.gov Introduction This report summarizes and provides analysis of incident reports submitted to US-CERT during the U.S.
Supercharge Your SIEM: How Domain Intelligence Enhances Situational Awareness
 Supercharge Your SIEM: How Domain Intelligence Enhances Situational Awareness Introduction Drowning in data but starving for information. It s a sentiment that resonates with most security analysts. For
Supercharge Your SIEM: How Domain Intelligence Enhances Situational Awareness Introduction Drowning in data but starving for information. It s a sentiment that resonates with most security analysts. For
Teradata and Protegrity High-Value Protection for High-Value Data
 Teradata and Protegrity High-Value Protection for High-Value Data 12.16 EB7178 DATA SECURITY Table of Contents 2 Data Centric Security: Providing High-Value Protection for High-Value Data 3 Visibility:
Teradata and Protegrity High-Value Protection for High-Value Data 12.16 EB7178 DATA SECURITY Table of Contents 2 Data Centric Security: Providing High-Value Protection for High-Value Data 3 Visibility:
NOT PROTECTIVELY MARKED PHISHING. July 2016
 - PHISHING July 2016 1 Introduction: The purpose of this document is to provide an analysis of the most prevalent trends and characteristics of phishing campaigns in the UK in July 2016. The analysis is
- PHISHING July 2016 1 Introduction: The purpose of this document is to provide an analysis of the most prevalent trends and characteristics of phishing campaigns in the UK in July 2016. The analysis is
Symantec Endpoint Protection
 Overview provides unrivaled security across physical and virtual platforms and support for the latest operating systems-mac OS X 10.9 and Windows 8.1. Powered by Symantec Insight and by SONAR, a single,
Overview provides unrivaled security across physical and virtual platforms and support for the latest operating systems-mac OS X 10.9 and Windows 8.1. Powered by Symantec Insight and by SONAR, a single,
Administration of Symantec Cyber Security Services (July 2015) Sample Exam
 Administration of Symantec Cyber Security Services (July 2015) Sample Exam Contents SAMPLE QUESTIONS... 1 ANSWERS... 6 Sample Questions 1. Which DeepSight Intelligence Datafeed can be used to create a
Administration of Symantec Cyber Security Services (July 2015) Sample Exam Contents SAMPLE QUESTIONS... 1 ANSWERS... 6 Sample Questions 1. Which DeepSight Intelligence Datafeed can be used to create a
Symantec Endpoint Protection 14
 Symantec Endpoint Protection Cloud Security Made Simple Symantec Endpoint Protection 14 Data Data Sheet: Sheet: Endpoint Endpoint Security Security Overview Last year, we saw 431 million new malware variants,
Symantec Endpoint Protection Cloud Security Made Simple Symantec Endpoint Protection 14 Data Data Sheet: Sheet: Endpoint Endpoint Security Security Overview Last year, we saw 431 million new malware variants,
Webroot Phishing Threat Trends
 December 2016 Webroot Phishing Threat Trends An update to the 2016 Threat Brief Introduction Who would ever fall for that? That s what many people think when they see a phishing attempt, since less advanced
December 2016 Webroot Phishing Threat Trends An update to the 2016 Threat Brief Introduction Who would ever fall for that? That s what many people think when they see a phishing attempt, since less advanced
State of the Phish 2016
 State of the Phish 2016 1 Introduction & Overview In October 2015, Wombat Security acquired ThreatSim, bringing together two of the leading simulated phishing attack tools. ThreatSim has historically prepared
State of the Phish 2016 1 Introduction & Overview In October 2015, Wombat Security acquired ThreatSim, bringing together two of the leading simulated phishing attack tools. ThreatSim has historically prepared
CE Advanced Network Security Phishing I
 CE 817 - Advanced Network Security Phishing I Lecture 15 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
CE 817 - Advanced Network Security Phishing I Lecture 15 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
WHITEPAPER. Protecting Against Account Takeover Based Attacks
 WHITEPAPER Protecting Against Account Takeover Based Email Attacks Executive Summary The onslaught of targeted email attacks such as business email compromise, spear phishing, and ransomware continues
WHITEPAPER Protecting Against Account Takeover Based Email Attacks Executive Summary The onslaught of targeted email attacks such as business email compromise, spear phishing, and ransomware continues
falanx Cyber Falanx Phishing: Measure your resilience
 falanx Cyber Falanx Email Phishing: Measure your resilience Contents What is Email Phishing? 3 Why should I carry out an Email Phishing exercise? 4 PhishEd Managed regular phishing 5 Single assessments
falanx Cyber Falanx Email Phishing: Measure your resilience Contents What is Email Phishing? 3 Why should I carry out an Email Phishing exercise? 4 PhishEd Managed regular phishing 5 Single assessments
Comodo Internet Security Essentials Software Version 1.3
 Comodo Internet Security Essentials Software Version 1.3 User Guide Guide Version 1.3.010518 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Table of Contents Comodo Internet
Comodo Internet Security Essentials Software Version 1.3 User Guide Guide Version 1.3.010518 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Table of Contents Comodo Internet
Be certain. MessageLabs Intelligence: May 2006
 Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco
 What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
FTA 2017 SEATTLE. Cybersecurity and the State Tax Threat Environment. Copyright FireEye, Inc. All rights reserved.
 FTA 2017 SEATTLE Cybersecurity and the State Tax Threat Environment 1 Agenda Cybersecurity Trends By the Numbers Attack Trends Defensive Trends State and Local Intelligence What Can You Do? 2 2016: Who
FTA 2017 SEATTLE Cybersecurity and the State Tax Threat Environment 1 Agenda Cybersecurity Trends By the Numbers Attack Trends Defensive Trends State and Local Intelligence What Can You Do? 2 2016: Who
ISACA GEEK WEEK SECURITY MANAGEMENT TO ENTERPRISE RISK MANAGEMENT USING THE ISO FRAMEWORK AUGUST 19, 2015
 ISACA GEEK WEEK SECURITY MANAGEMENT TO ENTERPRISE RISK MANAGEMENT USING THE ISO 27001 FRAMEWORK AUGUST 19, 2015 Agenda Coalfire Overview Threat Landscape What is ISO Why ISO ISO Cycle Q&A 2 Presenters
ISACA GEEK WEEK SECURITY MANAGEMENT TO ENTERPRISE RISK MANAGEMENT USING THE ISO 27001 FRAMEWORK AUGUST 19, 2015 Agenda Coalfire Overview Threat Landscape What is ISO Why ISO ISO Cycle Q&A 2 Presenters
The Cyber War on Small Business
 The Cyber War on Small Business Dillon Behr Executive Lines Broker Risk Placement Services, Inc. Meet Our Speaker Dillon Behr Executive Lines Broker Risk Placement Services, Inc. Previously worked as Cyber
The Cyber War on Small Business Dillon Behr Executive Lines Broker Risk Placement Services, Inc. Meet Our Speaker Dillon Behr Executive Lines Broker Risk Placement Services, Inc. Previously worked as Cyber
Segment Your Network for Stronger Security
 Segment Your Network for Stronger Security Protecting Critical Assets with Cisco Security 2017 Cisco and/or its affiliates. All rights reserved. 2017 Cisco and/or its affiliates. All rights reserved. The
Segment Your Network for Stronger Security Protecting Critical Assets with Cisco Security 2017 Cisco and/or its affiliates. All rights reserved. 2017 Cisco and/or its affiliates. All rights reserved. The
MOBILE THREAT LANDSCAPE. February 2018
 MOBILE THREAT LANDSCAPE February 2018 WHERE DO MOBILE THREATS COME FROM? In 2017, mobile applications have been a target of choice for hackers to access and steal data, with 86% of mobile threats coming
MOBILE THREAT LANDSCAPE February 2018 WHERE DO MOBILE THREATS COME FROM? In 2017, mobile applications have been a target of choice for hackers to access and steal data, with 86% of mobile threats coming
Symantec Client Security. Integrated protection for network and remote clients.
 Symantec Client Security Integrated protection for network and remote clients. Complex Internet threats require comprehensive security. Today's complex threats require comprehensive security solutions
Symantec Client Security Integrated protection for network and remote clients. Complex Internet threats require comprehensive security. Today's complex threats require comprehensive security solutions
IRONSCALES Federation Combines Human Intelligence with Machine Learning to Discover & Stop Spear-Phishing Attacks
 IRONSCALES Federation Combines Human Intelligence with Machine Learning to Discover & Stop Spear-Phishing Attacks Phishing attacks have evolved in sophistication and frequency since they first originated
IRONSCALES Federation Combines Human Intelligence with Machine Learning to Discover & Stop Spear-Phishing Attacks Phishing attacks have evolved in sophistication and frequency since they first originated
IT & DATA SECURITY BREACH PREVENTION
 IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
CRITICAL INFRASTRUCTURE AND CYBER THREAT CRITICAL INFRASTRUCTURE AND CYBER THREAT
 CRITICAL INFRASTRUCTURE SAFER CITIES. THRIVING COMMUNITIES. Critical Infrastructure sectors have become prime targets for cyber criminals due to their vitality to a nation s security and stability. 16
CRITICAL INFRASTRUCTURE SAFER CITIES. THRIVING COMMUNITIES. Critical Infrastructure sectors have become prime targets for cyber criminals due to their vitality to a nation s security and stability. 16
Phishing Read Behind The Lines
 Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
Symantec Endpoint Protection Mobile - Admin Guide v3.2.1 May 2018
 Symantec Endpoint Protection Mobile - Admin Guide v3.2.1 May 2018 Symantec Endpoint Protection Mobile - Admin Guide Documentation version: 3.0 This document was last updated on: August 21, 2017 Legal Notice
Symantec Endpoint Protection Mobile - Admin Guide v3.2.1 May 2018 Symantec Endpoint Protection Mobile - Admin Guide Documentation version: 3.0 This document was last updated on: August 21, 2017 Legal Notice
CLOUD REPORT LITTLE CHANGE IN GDPR-READINESS LEVELS WITH MAY 2018 DEADLINE LOOMING. 24.6% of cloud services rated high on GDPR-readiness
 SEPTEMBER 2017 CLOUD REPORT LITTLE CHANGE IN GDPR-READINESS LEVELS WITH MAY 2018 DEADLINE LOOMING 24.6% of cloud services rated high on GDPR-readiness REPORT HIGHLIGHTS 24.6 percent of cloud services are
SEPTEMBER 2017 CLOUD REPORT LITTLE CHANGE IN GDPR-READINESS LEVELS WITH MAY 2018 DEADLINE LOOMING 24.6% of cloud services rated high on GDPR-readiness REPORT HIGHLIGHTS 24.6 percent of cloud services are
WORKSHOP CYBER SECURITY AND CYBERCRIME POLICIES FOR AFRICAN DIPLOMATS. Okechukwu Emmanuel Ibe
 WORKSHOP CYBER SECURITY AND CYBERCRIME POLICIES FOR AFRICAN DIPLOMATS Okechukwu Emmanuel Ibe INTRODUCTION The Intelligence and Security Committee (ISC) is a Unit in the Office of the Chairperson of the
WORKSHOP CYBER SECURITY AND CYBERCRIME POLICIES FOR AFRICAN DIPLOMATS Okechukwu Emmanuel Ibe INTRODUCTION The Intelligence and Security Committee (ISC) is a Unit in the Office of the Chairperson of the
Predators are lurking in the Dark Web - is your network vulnerable?
 Predators are lurking in the Dark Web - is your network vulnerable? Venkatesh Sadayappan (Venky) Security Portfolio Marketing Leader IBM Security - Central & Eastern Europe Venky.iss@cz.ibm.com @IBMSecurityCEE
Predators are lurking in the Dark Web - is your network vulnerable? Venkatesh Sadayappan (Venky) Security Portfolio Marketing Leader IBM Security - Central & Eastern Europe Venky.iss@cz.ibm.com @IBMSecurityCEE
Cyber Security Guide for NHSmail
 Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
U.S. State of Cybercrime
 EXCLUSIVE RESEARCH FROM EXECUTIVE SUMMARY 2017 U.S. State of Cybercrime IDG Communications, Inc. 2017 U.S. State of Cybercrime TODAY S CYBERCRIMES ARE BECOMING MORE TARGETED AND BUILT FOR MAXIMUM IMPACT,
EXCLUSIVE RESEARCH FROM EXECUTIVE SUMMARY 2017 U.S. State of Cybercrime IDG Communications, Inc. 2017 U.S. State of Cybercrime TODAY S CYBERCRIMES ARE BECOMING MORE TARGETED AND BUILT FOR MAXIMUM IMPACT,
Phishing. What do phishing s do?
 Phishing We have become all too familiar with phishing emails but if that s the case, why do we as a community still fall victim? In this newsletter our goal is to provide you with some basic information
Phishing We have become all too familiar with phishing emails but if that s the case, why do we as a community still fall victim? In this newsletter our goal is to provide you with some basic information
