May 2011 Intelligence Report
|
|
|
- Justina Casey
- 5 years ago
- Views:
Transcription
1 Symantec.cloud MessageLabs Intelligence May 2011 Intelligence Report For the First Time, Spammers Establish Their Own Fake URL-Shortening Services; Spam Rate Rises by 2.9% Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2011 to keep you informed regarding the ongoing fight against viruses, spam, spyware and other unwelcome content. Report highlights Spam 75.8% in May (an increase of 2.9 percentage points since April 2011) Viruses One in s in May contained malware (a decrease of 0.14 percentage points since April 2011) Phishing One in s comprised a phishing attack (a decrease of 0.06 percentage points since April 2011) Malicious web sites 3,170 web sites blocked per day (an increase of 30.4% since April 2011) 36.8% of all malicious domains blocked were new in May (an increase of 3.8 percentage points since April 2011) 24.6% of all web-based malware blocked was new in May (an increase of 2.1 percentage points since April 2011) For the First Time, Spammers establish their own fake URL-shortening services Report analysis Spammers establish their own fake URL-shortening services URL shortening services which allow long, unwieldy URLs, or links, to be converted into much shorter URLs have experienced growth in popularity with the advent of length-restricted micro-blogging services and social media status updates. Unfortunately, these services are very useful to spammers as they are simple, relatively anonymous and easy to automate by nature which makes them rife for abuse. In 2010, MessageLabs Intelligence published its security predictions 1 for 2011, which included the likelihood of more sophisticated attacks using URL-shortening services either by a criminal enterprise gaining control of a legitimate URL-shortening service or by one of these groups creating a service which appears legitimate, and operates in a legitimate manner, before being turned to malicious use. This month, MessageLabs Intelligence uncovered evidence of spammers establishing their own fake URL-shortening services for the first time. Shortened links created on these fake URL-shortening sites are not included directly in spam messages; instead, the spam s contain shortened URLs created on legitimate URL-shortening sites. Rather than leading directly to the spammer s final Web site, these links actually point to a shortened URL on the spammer s fake URL-shortening Web site, which in turn redirects to the spammer s final Web site. This process is shown in figure 5, below. MessageLabs Intelligence research has identified several similar fake URL-shortening Web sites associated with the same spammers, each behaving in the same way. All the sites use.ru (Russian) domain names, and many are hosted in Russia and Ukraine. To make things more interesting, the domains were registered several months before they were used, potentially as a means to evade detection by legitimate URL-shortening services since the age of the domain may be used as an indicator of legitimacy making it more difficult for the genuine shortening services to identify potential abuse. 1 Page 1 of 12
2 The MessageLabs Intelligence team has been monitoring how spammers abuse URL-shortening services for several years, and have observed spammers using a wide range of these services, often creating thousands of links in a very short period of time on a single site. Using the aforementioned method of establishing their own Web sites, spammers also often create elaborate "chains" where one short URL points to another URL from a different URL-shortening site. This is sometimes repeated more than ten times before arriving at the spammer's site. Figure 1, below, shows the trend over time of legitimate URL-shortening services being used in spam s. Following an increase at the end of 2010, the use has recently declined as spammers switched to spamming via social media, as reported in the April MessageLabs Intelligence report. However, in recent weeks, the practice appears to be returning to spam s, contributing to the recent rise in spam levels. Figure 1: Chart showing percentage of spam that contains a shortened URL over time Continual research and monitoring As part of its research, MessageLabs Intelligence tracks many URL-shortening sites, discovering new ones every day. During this process, we identified some particularly interesting new URL-shortening sites. These sites don't have public interfaces, are not found in search results and do not appear on any micro-blogging services. Therefore, they are unlikely to be private URL-shortening services created by some organizations (who prefer to use their own, rather than rely on external sites). Spammer-owned and operated sites? Many URL-shortening sites use common wordplays and abbreviations in their domain names, but these sites don't. They use a consistent pattern. There are no references to the sites in search engine results, and we have only seen them used in spam. This strongly suggests that these sites are actually run by spammers themselves. Even more suspiciously, the sites have another crucial difference to normal URL-shortening sites. The ID, which identifies the URL or link to which it redirects, is mostly ignored. After changing characters or the length of the ID, the URL still redirects to the same spam URL. Figure 2: Example of a legitimate shortened URL; the ID in the short URL uniquely identifies the target Web site Page 2 of 12
3 Site appearance The main pages of these URL-shortening sites are simply "holding" or "coming soon" pages, as shown in figure 3: Figure 3: Web site landing page for apparent spammer short URL domain As previously mentioned, there are no links to any page where a short URL can be created, and there are no details about the service. This page itself is generated by legitimate Web hosting "control panel" software. Despite this message, the site is being actively used as a URL-shortening service, redirecting visitors to spam Web sites. Putting it together Interestingly, these spammer URL-shortening sites are not used directly in spam messages. Instead, they are used as intermediate points or "stepping stones" between (usually) a link to a public URL-shortening service, and the spammer's site. A sample spam message contains a URL pointing to a normal, public URL-shortening service, as can be seen in figure 4, below. Page 3 of 12
4 Figure 4: Sample containing genuine shortened URL Anyone following this link is first taken to a public URL-shortening site, which redirects to the spammer's URLshortening service, and then finally on to the spammer's Web site, as shown in figure 5, below. Spam with link to public URL shortening site Public URL shortening site Spammer-run URL shortening site Spam site Figure 5: Process involved in redirecting users through spam s and URL-shortening services This particular spammer is promoting a rather strange mismatch of pirated software (including Symantec products), pharmaceutical products and hardcore adult content, as shown in the example in figure 6, below. Figure 6: Final Web site landing page involved in the redirection process These URL-shortening services don t work in the same way as legitimate ones; interestingly, any ID passed to the spammer s redirect service will redirect to the same spam Web site. This suggests that spammers are at this stage using this technique to dress-up their spam and give the appearance and functionality of a genuine URL-shortening service. The ability to use any seemingly genuine ID to redirect to the same Web site means that they don t have to go to the trouble of generating genuine IDs and with a low level of re-use, may help to better evade traditional anti-spam filters. With legitimate URL-shortening services attempting to tackle abuse more seriously, spammers seem to be experimenting with ways to establish their own services to better avoid disruption. We expect spammers to continue abusing URL-shortening services, particularly with the continual flow of new URLshortening services being created. Symantec MessageLabs AntiSpam.cloud customers benefit from our Page 4 of 12
5 proprietary technology to effectively block URL-shortening spam, while still allowing messages using URL-shortening for legitimate purposes. By Nick Johnston, Senior Software Engineer, Symantec Blog: Are You At Risk of a Targeted Attack? Lifting the Lid on Who Was Targeted in 2010 Targeted attacks are bespoke pieces of malware that are sent to addresses that appear to have been specifically selected by the attacker. In this way, they differ from the rest of malware that are sent in large numbers without apparent regard to the recipient. Approximately one in every 208 s contained malware in March 2011, rising to one in 168 in April; however, only one in every 5,000 (0.02%) of malware-containing s can be classified as targeted. Although these attacks are quite rare, MessageLabs Intelligence identified an increase of 60.4% in the average number of daily attacks between 2010 and Since April 2008, almost a third of all targeted attacks have been sent to the public sector (32.4%), followed by companies in the manufacturing sector (15.9%), financial companies (8.0%), IT Services (6.1%) and educational organizations (predominantly universities) (4.6%). Compared with 2009, the number of targeted attacks is increasing as is the number of companies attacked. Additionally there was a 17.4% increase in the number of attacked customers in 2010 over 2009 and a 31.4% increase in the number of distinct attacks. Moreover, there was a clear increase in the number of attacks directed against the most frequently targeted organizations; targeted attacks appear to be becoming more common, but also more highly targeted. Most of the recipients of targeted attacks could be identified from their Internet footprint. For example, 34% of recipients were senior managers and 24%of recipients were individuals with managerial responsibilities. Only 4% were of low seniority; many of these are personal assistants to senior managers. Interestingly, 19% of recipients are not identifiable through public Internet searches, yet the attackers know their identity possibly by way of successful attacks elsewhere. For more information, please visit the MessageLabs Intelligence blog at: Blog: Rise in ZIP File Attachments in Spam s Lead to Bredolab Malware On March 26, MessageLabs Intelligence tracked a large increase in the amount of data traffic hitting its spam traps, despite the overall volume of spam s continuing to decline in the wake of the recent Rustock botnet takedown. Further analysis revealed that the Cutwail botnet had begun sending more s than usual with ZIP file attachments, meaning the average size of each mail was much larger than normal. These mails are all variations on the same familiar subject, a package could not be delivered and the recipient would need to open the attachment to print out and take to their depot to collect it. Inside the ZIP file attachment is an executable file, which if run, will infect the users' machine. The malicious files are all variants of the Bredolab malware. Once on the system, the Bredolab family of malware allows the attacker to take control of the machine and download other software to it, including malware and fake, rogue security software. Most likely the infected machine would become part of a botnet and used to spread the infection to others. For more information, please visit the MessageLabs Intelligence blog at: Page 5 of 12
6 Global Trends & Content Analysis Symantec.cloud is focused on identifying, detecting and averting unwanted Internet threats such as viruses, spam, spyware and other inappropriate content. The intelligence collected from the billions of messages and millions of threats processed each day forms one of the most comprehensive and up-to-date knowledge bases of Internet threats in the world. Symantec MessageLabs AntiSpam.cloud: In May 2011, the global ratio of spam in traffic increased by 2.9 percentage points since April 2011 to 75.8% (1 in s) partly as a result of the increased level of activity around shortened URL redirects. However, it was also expected to rise again following the Rustock botnet takedown in March. Spam Rate 75.8% 80.1% 79.8% Russian 82.2% Federation 81.6% Hungary 81.0% Saudi Arabia Luxembourg China Automotive Marketing/Media Education Manufacturing Wholesale Last Month: 72.9% Six Month Avg.: 78.3% Top 5 Geographies Top 5 Verticals By Horizontal 78.2% 77.5% 77.4% 77.3% 80.2% 75.1% 74.9% 75.5% 75.3% % 76.1% % May 2011 As the overall spam level climbed in May 2011, Russia became the most spammed geography, with a spam rate of 82.2%. In the US, 76.4% of was spam and 75.3% in Canada. The spam level in the UK was 75.4%. In The Netherlands, spam accounted for 77.5% of traffic, 75.5% in Germany, 75.1% in Denmark and 73.9% in Australia. In Hong Kong, 75.2% of was blocked as spam and 74.0% in Singapore, compared with 72.3% in Japan. Spam accounted for 75.9% of traffic in South Africa and 74.8% in Brazil. In May, the Wholesale industry sector became the most spammed sector, with a spam rate of 80.2%. Spam levels for the Education sector reached 77.4% and 76.0% for the Chemical & Pharmaceutical sector; 75.4% for IT Services, 75.4% for Retail, 74.5% for Public Sector and 74.7% for Finance. Symantec MessageLabs AntiVirus.cloud: The global ratio of -borne viruses in traffic was one in s (0.450%) in May, a decrease of percentage points since April In May, 30.0% of -borne malware contained links to malicious Web sites, an increase of 16.9 percentage points since April A large number of s containing variants of Bredolab- related malware, accounted for 16.3% of all -borne malware, compared with 55.1% in the previous month. These variants were commonly attached as ZIP files, rather than hyperlinks, and as the volume of these attacks diminishes, the proportion of attacks using hyperlinks increased. Page 6 of 12
7 The UK had the highest ratio of malicious s in May, as one in s was blocked as malicious in May. A large number of variants of Bredolab malware continued to be observed in a number of countries during May, as highlighted in the table below. In the US, virus levels for -borne malware were 1 in and 1 in for Canada. In Germany virus activity reached 1 in 435.9, 1 in 1,197 in Denmark and in The Netherlands 1 in In Australia, 1 in s were malicious and 1 in in Hong Kong; for Japan it was 1 in 1,164, compared with 1 in in Singapore. In South Africa, 1 in s and 1 in s in Brazil contained malicious content. With 1 in s being blocked as malicious, the Public Sector remained the most targeted industry in May. Virus levels for the Chemical & Pharmaceutical sector were 1 in and 1 in for the IT Services sector; 1 in for Retail, 1 in for Education and 1 in for Finance. The table below shows the most frequently blocked -borne malware for May, many of which take advantage of malicious hyperlinks. Overall, 55.1% of -borne malware was associated with Bredolab, Sasfis, SpyEye and Zeus variants, a trend initially reported in the MessageLabs Intelligence Report for February Malware % Malware Gen:Variant.Bredo % Trojan.Bredolab!eml 5.15% W32/NewMalware!836b 4.64% W32/NewMalware! % W32/NewMalware-Generic-7ba5 2.38% HeurAuto-bb % W32/Generic-6bfd 2.30% Exploit/FakeAttach 1.60% W32/Packed.Generic-1d11-bd % Exploit/FakeAttach-844a 1.39% Page 7 of 12
8 Phishing Analysis: In May, phishing activity decreased by 0.06 percentage points since April 2011; one in s (0.349%) comprised some form of phishing attack. Phishing Rate 1 in in 80.2 South Africa 1 in 33.2 Public Sector 1 in in in United Kingdom 1 in Education 1 in in United Arab Emirates 1 in Finance 1 in in Canada 1 in Non-Profit 1 in in Brazil 1 in Business Support Svcs. 1 in Last Month: 1 in Six Month Avg.: 1 in Top 5 Geographies Top 5 Verticals By Horizontal 1 in May 2011 South Africa remained the most targeted geography for phishing s in May, with 1 in s identified as phishing attacks. South Africa suffers from a high level of phishing activity targeting many of its four major national banks, as well as other international financial institutions. In the UK, phishing accounted for 1 in s. Phishing levels for the US were 1 in 1,227 and 1 in for Canada. In Germany phishing levels were 1 in 1,540, 1 in 2662 in Denmark and 1 in in The Netherlands. In Australia, phishing activity accounted for 1 in 1,022 s and 1 in 2,235 in Hong Kong; for Japan it was 1 in 10,735 and 1 in 2,111 for Singapore. In Brazil, 1 in s were blocked as phishing attacks. The Public Sector remained the most targeted by phishing activity in May, with 1 in s comprising a phishing attack. Phishing levels for the Chemical & Pharmaceutical sector were 1 in and 1 in for the IT Services sector; 1 in for Retail, 1 in for Education and 1 in for Finance. Symantec MessageLabs Web Security.cloud: In May, MessageLabs Intelligence identified an average of 3,142 Web sites each day harboring malware and other potentially unwanted programs including spyware and adware; an increase of 30.4% since April This reflects the rate at which Web sites are being compromised or created for the purpose of spreading malicious content. Often this number is higher when Web-based malware is in circulation for a longer period of time to widen its potential spread and increase its longevity. As detection for Web-based malware increases, the number of new Web sites blocked decreases and the proportion of new malware begins to rise, but initially on fewer Web sites. Further analysis reveals that 36.8% of all malicious domains blocked were new in May; an increase of 3.8 percentage points compared with April Additionally, 24.6% of all Web-based malware blocked was new in May; an increase of 2.1 percentage points since the previous month. Symantec.cloud Web Security Services Activity: New Malware Sites per Day New sites with spyware New sites with web viruses Total 28/day 3,142/day 3,170/day May 2011 Page 8 of 12
9 The chart above shows the increase in the number of new spyware and adware Web sites blocked each day on average during May compared with the equivalent number of Web-based malware Web sites blocked each day. The most common trigger for policy-based filtering applied by Symantec MessageLabs Web Security.cloud for its business clients was for the Advertisements & Popups category, which accounted for 45.9% of blocked Web activity in May. The second most frequently blocked traffic was categorized as Social Networking, and accounted for 16.2% of URL-based filtering activity blocked, equivalent to one in every 6.2 Web sites blocked. Many organizations allow access to social networking Web sites, but facilitate access logging so that usage patterns can be tracked and in some cases implement policies to only permit access at certain times of the day and block access at all other times. This information is often used to address performance management issues, perhaps in the event of lost productivity due to social networking abuse. Activity related to Streaming Media policies resulted in 8.8% of URL-based filtering blocks in May. Streaming media is increasingly popular when there are major sporting events or high profile international news stories, which often result in an increased number of blocks, as businesses seek to preserve valuable bandwidth for other purposes. This rate is equivalent to one in every 11.3 Web sites blocked. Symantec Endpoint Protection.cloud: The endpoint is often the last line of defense and analysis. The threats found here can shed light on the wider nature of threats confronting businesses, especially from blended attacks. Attacks reaching the endpoint are likely to have already circumvented other layers of protection that may already be deployed, such as gateway filtering. The table below shows the malware most frequently blocked targeting endpoint devices for the last month. This includes data from endpoint devices protected by Symantec technology around the world, including data from clients which may not be using other layers of protection, such as Symantec MessageLabs Web Security.cloud or Symantec MessageLabs AntiVirus.cloud. Malware 2 % Malware W32.Ramnit!html 7.83% W32.Sality.AE 6.54% W32.Ramnit.B!inf 5.90% Trojan.Bamital 5.08% W32.Downadup.B 3.96% Trojan.FakeAV 2.82% Trojan.ADH % Trojan.ByteVerify 2.29% W32.SillyFDC 2.22% Trojan.ADH 2.14% Generic Detection* 19.7% 2 For further information on these threats, please visit: Page 9 of 12
10 The most frequently blocked malware for the last month was W32.Ramnit!html. This is a generic detection for.html files infected by W32.Ramnit 3, a worm that spreads through removable drives and by infecting executable files. The worm spreads by encrypting and then appending itself to files with.dll,.exe and.htm extensions. Variants of the Ramnit worm accounted for 14.0% of all malicious software blocked by endpoint protection technology in May. For much of 2010, W32.Sality.AE had been the most prevalent malicious threat blocked at the endpoint; however, for the first time in twelve months, it fell to second place in the chart. * Many new viruses and Trojans are based on earlier versions, where code has been copied or altered to create a new strain, or variant. Often these variants are created using toolkits and hundreds of thousands of variants can be created from the same piece of malware. This has become a popular tactic to evade signature-based detection, as each variant would traditionally need its own signature to be correctly identified and blocked. By deploying techniques, such as heuristic analysis and generic detection, it is possible to correctly identify and block several variants of the same malware families, as well as identify new forms of malicious code that seek to exploit certain vulnerabilities that can be identified generically. Approximately 19.7% of the most frequently blocked malware last month was identified and blocked using generic detection. 3 Page 10 of 12
11 Traffic Management Traffic Management continues to reduce the overall message volume through techniques operating at the protocol level. Unwanted senders are identified and connections to the mail server are slowed down using features embedded in the TCP protocol. Incoming volumes of known spam are significantly slowed, while ensuring legitimate is expedited. In May, MessageLabs services processed an average of 1.1 Billion SMTP connections per day, of which 34.8% were throttled back as a result of traffic management controls for traffic that was unequivocally malicious or unwanted. The remainder of these connections was subsequently processed by MessageLabs Connection Management controls and Skeptic. Connection Management Connection Management is particularly effective in stopping directory harvest, brute force and denial of service attacks, where unwanted senders send high volumes of messages to force spam into an organization or disrupt business communications and operations. Connection Management works at the SMTP level using techniques that verify legitimate connections to the mail server, using SMTP Validation techniques. It is able to identify unwanted originating from known spam and virus-sending sources, where the source can unequivocally be identified as an open proxy or a botnet, and rejects the connection accordingly. In May, an average of 35.4% of inbound messages was intercepted from botnets and other known malicious sources and rejected as a consequence. User Management User Management uses Registered User Address Validation techniques to reduce the overall volume of s for registered domains, by discarding connections for which the recipient addresses are identified as invalid or nonexistent. In May, an average of 8.1% of inbound messages was identified as invalid by User Management. Page 11 of 12
12 About MessageLabs Intelligence MessageLabs Intelligence is a respected source of data and analysis for messaging security issues, trends and statistics. MessageLabs Intelligence publishes a range of information on global security threats based on live data feeds from more than 15 data centers around the world scanning billions of messages and web pages each week. MessageLabs Team Skeptic comprises many world-renowned malware and spam experts, who have a global view of threats across multiple communication protocols drawn from the billions of web pages, and IM messages they monitor each day on behalf of 31,000 clients in more than 100 countries. More information is available at About Symantec Symantec is a global leader in providing security, storage and systems management solutions to help consumers and organizations secure and manage their information-driven world. Our software and services protect against more risks at more points, more completely and efficiently, enabling confidence wherever information is used or stored. More information is available at Copyright 2011 Symantec Corporation. All Rights Reserved. Symantec, the Symantec Logo, and the Checkmark Logo are trademarks or registered trademarks of Symantec Corporation or its affiliates in the US and other countries. Other names may be trademarks of their respective owners. NO WARRANTY. The information contained in this report is being delivered to you AS-IS, and Symantec Corporation makes no warranty as to its accuracy or use. Any use of the information contained herein is at the risk of the user. This report may include technical or other inaccuracies or typographical errors. Symantec reserves the right to make changes without prior notice. No part of this publication may be copied without the express written permission of Symantec Corporation, 350 Ellis Street, Mountain View, CA Page 12 of 12
Be certain. MessageLabs Intelligence: May 2006
 Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
MessageLabs Intelligence: October 2006 Do you want spam with that spam?
 Be certain MessageLabs Intelligence: October 2006 Do you want spam with that spam? Introduction Welcome to the October edition of the MessageLabs Intelligence monthly report. This report provides the latest
Be certain MessageLabs Intelligence: October 2006 Do you want spam with that spam? Introduction Welcome to the October edition of the MessageLabs Intelligence monthly report. This report provides the latest
MessageLabs Intelligence: August 2007 Storm botnet serves-up a diet of fast-flux spam
 Be certain MessageLabs Intelligence: August 2007 Storm botnet serves-up a diet of fast-flux spam Introduction Welcome to the August 2007 edition of the MessageLabs Intelligence monthly report. This report
Be certain MessageLabs Intelligence: August 2007 Storm botnet serves-up a diet of fast-flux spam Introduction Welcome to the August 2007 edition of the MessageLabs Intelligence monthly report. This report
Symantec Protection Suite Add-On for Hosted Security
 Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
SYMANTEC ENTERPRISE SECURITY. Symantec Internet Security Threat Report September 2005 Power and Energy Industry Data Sheet
 SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
Securing Your Business Against the Diversifying Targeted Attacks Leonard Sim
 Securing Your Business Against the Diversifying Targeted Attacks Leonard Sim Manager, Client & Partner Services, Asia 1 Agenda 2010 Threats Targeted Attacks Defense Against Targeted Attacks Questions 2
Securing Your Business Against the Diversifying Targeted Attacks Leonard Sim Manager, Client & Partner Services, Asia 1 Agenda 2010 Threats Targeted Attacks Defense Against Targeted Attacks Questions 2
Advanced Threat Defense Certification Testing Report. Symantec Corporation Symantec Advanced Threat Protection
 Advanced Threat Defense Certification Testing Report Symantec Advanced Threat Protection ICSA Labs Advanced Threat Defense December 8, 2015 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Advanced Threat Defense Certification Testing Report Symantec Advanced Threat Protection ICSA Labs Advanced Threat Defense December 8, 2015 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Top 10 Global Threat Rank by Source
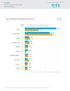 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Panda Security 2010 Page 1
 Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
How Enterprise Tackles Phishing. Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong
 How Enterprise Tackles Phishing Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong Hackers turning to easy marks - Social engineering Phishing was the #1 threat vector (> 50%) for Office
How Enterprise Tackles Phishing Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong Hackers turning to easy marks - Social engineering Phishing was the #1 threat vector (> 50%) for Office
Symantec Security.cloud
 Data Sheet: Messaging Security filters unwanted messages and protects mailboxes from targeted attacks. The service has selflearning capabilities and Symantec intelligence to deliver highly effective and
Data Sheet: Messaging Security filters unwanted messages and protects mailboxes from targeted attacks. The service has selflearning capabilities and Symantec intelligence to deliver highly effective and
Security Gap Analysis: Aggregrated Results
 Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
IC B01: Internet Security Threat Report: How to Stay Protected
 IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
Phishing Activity Trends Report August, 2006
 Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Internet Security Threat Report Volume XIII. Patrick Martin Senior Product Manager Symantec Security Response October, 2008
 Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
INSIDE. Symantec AntiVirus for Microsoft Internet Security and Acceleration (ISA) Server. Enhanced virus protection for Web and SMTP traffic
 Virus Protection & Content Filtering TECHNOLOGY BRIEF Symantec AntiVirus for Microsoft Internet Security and Acceleration (ISA) Server Enhanced virus protection for Web and SMTP traffic INSIDE The need
Virus Protection & Content Filtering TECHNOLOGY BRIEF Symantec AntiVirus for Microsoft Internet Security and Acceleration (ISA) Server Enhanced virus protection for Web and SMTP traffic INSIDE The need
Israel Internet Security Threat Profile
 Israel Internet Security Threat Profile Worldwide Ranking.%.%.%.%.%.%.%.%.%.%.% Overall Average Spam Zombies Malicious Code Phishing Hosts Bots Network Attacking Countries Copyright Symantec Corporation.
Israel Internet Security Threat Profile Worldwide Ranking.%.%.%.%.%.%.%.%.%.%.% Overall Average Spam Zombies Malicious Code Phishing Hosts Bots Network Attacking Countries Copyright Symantec Corporation.
Symantec Intelligence Quarterly: Best Practices and Methodologies October - December, 2009
 Symantec Intelligence Quarterly: Best Practices and Methodologies White Paper: Symantec Intelligence Quarterly Symantec Intelligence Quarterly: Best Practices and Methodologies Contents Symantec best
Symantec Intelligence Quarterly: Best Practices and Methodologies White Paper: Symantec Intelligence Quarterly Symantec Intelligence Quarterly: Best Practices and Methodologies Contents Symantec best
>MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE?
 >MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE? >CONTENTS >WHAT IS MESSAGING AND WEB SECURITY? >P1 >EMAIL THREATS >P1 >VIRUSES
>MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE? >CONTENTS >WHAT IS MESSAGING AND WEB SECURITY? >P1 >EMAIL THREATS >P1 >VIRUSES
Marshal s Defense-in-Depth Anti-Spam Engine
 Marshal s Defense-in-Depth Anti-Spam Engine January 2008 Contents Overview 2 Features 3 Summary 6 This whitepaper explores the underlying anti-spam and anti-phishing defense technology in Marshal s world
Marshal s Defense-in-Depth Anti-Spam Engine January 2008 Contents Overview 2 Features 3 Summary 6 This whitepaper explores the underlying anti-spam and anti-phishing defense technology in Marshal s world
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Office 365 Buyers Guide: Best Practices for Securing Office 365
 Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
Phishing Activity Trends Report October, 2004
 Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Botnets: major players in the shadows. Author Sébastien GOUTAL Chief Science Officer
 Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
The State of Spam. Paul Wood Senior Analyst, MessageLabs Intelligence Symantec Hosted Services
 The State of Spam Paul Wood Senior Analyst, MessageLabs Intelligence Symantec Hosted Services Agenda 1 Introduction 2 Malware & The Underground Shadow Economy 3 Spam Patterns & Trends 4 Technology & Botnets
The State of Spam Paul Wood Senior Analyst, MessageLabs Intelligence Symantec Hosted Services Agenda 1 Introduction 2 Malware & The Underground Shadow Economy 3 Spam Patterns & Trends 4 Technology & Botnets
Quick Heal Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac.
 Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
CloudSOC and Security.cloud for Microsoft Office 365
 Solution Brief CloudSOC and Email Security.cloud for Microsoft Office 365 DID YOU KNOW? Email is the #1 delivery mechanism for malware. 1 Over 40% of compliance related data in Office 365 is overexposed
Solution Brief CloudSOC and Email Security.cloud for Microsoft Office 365 DID YOU KNOW? Email is the #1 delivery mechanism for malware. 1 Over 40% of compliance related data in Office 365 is overexposed
Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection White Paper September 2017 www.cyren.com 1 White Paper September 2017 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
Fighting Spam, Phishing and Malware With Recurrent Pattern Detection White Paper September 2017 www.cyren.com 1 White Paper September 2017 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
KASPERSKY FRAUD PREVENTION FOR ENDPOINTS
 KASPERSKY FRAUD PREVENTION FOR ENDPOINTS www.kaspersky.com KASPERSKY FRAUD PREVENTION 1. Ways of Attacking Online Banking The prime motive behind cybercrime is making money and today s sophisticated criminal
KASPERSKY FRAUD PREVENTION FOR ENDPOINTS www.kaspersky.com KASPERSKY FRAUD PREVENTION 1. Ways of Attacking Online Banking The prime motive behind cybercrime is making money and today s sophisticated criminal
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
Prevent and Detect Malware with Symantec Advanced Threat Protection: Network
 WHITE PAPER: SYMANTEC ADVANCED THREAT PROTECTION........................................ Prevent and Detect Malware with Symantec Advanced Threat Protection: Network Who should read this paper This white
WHITE PAPER: SYMANTEC ADVANCED THREAT PROTECTION........................................ Prevent and Detect Malware with Symantec Advanced Threat Protection: Network Who should read this paper This white
3.5 SECURITY. How can you reduce the risk of getting a virus?
 3.5 SECURITY 3.5.4 MALWARE WHAT IS MALWARE? Malware, short for malicious software, is any software used to disrupt the computer s operation, gather sensitive information without your knowledge, or gain
3.5 SECURITY 3.5.4 MALWARE WHAT IS MALWARE? Malware, short for malicious software, is any software used to disrupt the computer s operation, gather sensitive information without your knowledge, or gain
JPCERT/CC Incident Handling Report [January 1, March 31, 2018]
![JPCERT/CC Incident Handling Report [January 1, March 31, 2018] JPCERT/CC Incident Handling Report [January 1, March 31, 2018]](/thumbs/89/100577955.jpg) JPCERT-IR-2018-01 Issued: 2018-04-12 JPCERT/CC Incident Handling Report [January 1, 2018 - March 31, 2018] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
JPCERT-IR-2018-01 Issued: 2018-04-12 JPCERT/CC Incident Handling Report [January 1, 2018 - March 31, 2018] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
Red Condor had. during. testing. Vx Technology high availability. AntiSpam,
 Lab Testing Summary Report July 21 Report 167 Product Category: Email Security Solution Vendors Tested: MessageLabs/Symantec MxLogic/McAfee SaaS Products Tested: - Cloudfilter; MessageLabs/Symantec Email
Lab Testing Summary Report July 21 Report 167 Product Category: Email Security Solution Vendors Tested: MessageLabs/Symantec MxLogic/McAfee SaaS Products Tested: - Cloudfilter; MessageLabs/Symantec Email
FAQ. Usually appear to be sent from official address
 FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY
 RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY RSA CYOTA PROJECT PROPOSAL RSA FRAUDACTION ANTI-PHISHING SERVICE V.1 2011 Overview This brief highlights the benefits
RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY RSA CYOTA PROJECT PROPOSAL RSA FRAUDACTION ANTI-PHISHING SERVICE V.1 2011 Overview This brief highlights the benefits
THE ACCENTURE CYBER DEFENSE SOLUTION
 THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
IPS with isensor sees, identifies and blocks more malicious traffic than other IPS solutions
 IPS Effectiveness IPS with isensor sees, identifies and blocks more malicious traffic than other IPS solutions An Intrusion Prevention System (IPS) is a critical layer of defense that helps you protect
IPS Effectiveness IPS with isensor sees, identifies and blocks more malicious traffic than other IPS solutions An Intrusion Prevention System (IPS) is a critical layer of defense that helps you protect
McAfee Labs Threat Report
 McAfee Labs Threat Report December 217 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threat Report, December 217 The McAfee Labs count of new malware in Q3 reached an all-time
McAfee Labs Threat Report December 217 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threat Report, December 217 The McAfee Labs count of new malware in Q3 reached an all-time
Phishing Activity Trends Report August, 2005
 Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Global DDoS Threat Landscape
 DDOS REPORT Global DDoS Threat Landscape OVERVIEW Overview The number of network layer attacks continued to fall in, the fourth consecutive quarterly drop since peaking in Q2 2016. After reaching a record
DDOS REPORT Global DDoS Threat Landscape OVERVIEW Overview The number of network layer attacks continued to fall in, the fourth consecutive quarterly drop since peaking in Q2 2016. After reaching a record
Easy Activation Effortless web-based administration that can be activated in as little as one business day - no integration or migration necessary.
 Security Solutions Our security suite protects against email spam, viruses, web-based threats and spyware while delivering disaster recovery, giving you peace of mind so you can focus on what matters most:
Security Solutions Our security suite protects against email spam, viruses, web-based threats and spyware while delivering disaster recovery, giving you peace of mind so you can focus on what matters most:
Symantec & Blue Coat Technical Update Webinar 29. Juni 2017
 Avantec Blue Coat/Symantec Webinar Jean Marc Edder Senior Systems Engineer The Global Leader in Cyber Network + + Cloud Global market leader in Endpoint, Email, Data Loss Prevention and Website, User Authentication
Avantec Blue Coat/Symantec Webinar Jean Marc Edder Senior Systems Engineer The Global Leader in Cyber Network + + Cloud Global market leader in Endpoint, Email, Data Loss Prevention and Website, User Authentication
Comparison of Firewall, Intrusion Prevention and Antivirus Technologies
 Comparison of Firewall, Intrusion Prevention and Antivirus Technologies (How each protects the network) Dr. Gaurav Kumar Jain Email: gaurav.rinkujain.jain@gmail.com Mr. Pradeep Sharma Mukul Verma Abstract
Comparison of Firewall, Intrusion Prevention and Antivirus Technologies (How each protects the network) Dr. Gaurav Kumar Jain Email: gaurav.rinkujain.jain@gmail.com Mr. Pradeep Sharma Mukul Verma Abstract
The State of Spam A Monthly Report August Generated by Symantec Messaging and Web Security
 The State of Spam A Monthly Report August 2007 Generated by Symantec Messaging and Web Security Monthly Spam Landscape While overall spam activity remained steady in July 2007, the tactics being used are
The State of Spam A Monthly Report August 2007 Generated by Symantec Messaging and Web Security Monthly Spam Landscape While overall spam activity remained steady in July 2007, the tactics being used are
CA Host-Based Intrusion Prevention System r8
 PRODUCT BRIEF: CA HOST-BASED INTRUSION PREVENTION SYSTEM CA Host-Based Intrusion Prevention System r8 CA HOST-BASED INTRUSION PREVENTION SYSTEM (CA HIPS) BLENDS A STAND-ALONE FIREWALL WITH INTRUSION DETECTION
PRODUCT BRIEF: CA HOST-BASED INTRUSION PREVENTION SYSTEM CA Host-Based Intrusion Prevention System r8 CA HOST-BASED INTRUSION PREVENTION SYSTEM (CA HIPS) BLENDS A STAND-ALONE FIREWALL WITH INTRUSION DETECTION
Extract of Summary and Key details of Symantec.cloud Health check Report
 SYMANTEC.CLOUD EXAMPLE HEALTH CHECK SUMMARY REPORT COMPUTER SECURITY TECHNOLOGY LTD. 8-9 Lovat lane, London, London. EC3R 8DW. Tel: 0207 621 9740. Email: info@cstl.com WWW.CSTL.COM Customer: - REDACTED
SYMANTEC.CLOUD EXAMPLE HEALTH CHECK SUMMARY REPORT COMPUTER SECURITY TECHNOLOGY LTD. 8-9 Lovat lane, London, London. EC3R 8DW. Tel: 0207 621 9740. Email: info@cstl.com WWW.CSTL.COM Customer: - REDACTED
Data Sheet: Endpoint Security Symantec Multi-tier Protection Trusted protection for endpoints and messaging environments
 Trusted protection for endpoints and messaging environments Overview creates a protected endpoint and messaging environment that is secure against today s complex data loss, malware, and spam threats controlling
Trusted protection for endpoints and messaging environments Overview creates a protected endpoint and messaging environment that is secure against today s complex data loss, malware, and spam threats controlling
Symantec Endpoint Protection 14
 Symantec Endpoint Protection Cloud Security Made Simple Symantec Endpoint Protection 14 Data Data Sheet: Sheet: Endpoint Endpoint Security Security Overview Last year, we saw 431 million new malware variants,
Symantec Endpoint Protection Cloud Security Made Simple Symantec Endpoint Protection 14 Data Data Sheet: Sheet: Endpoint Endpoint Security Security Overview Last year, we saw 431 million new malware variants,
Prevx 3.0 v Product Overview - Core Functionality. April, includes overviews of. MyPrevx, Prevx 3.0 Enterprise,
 Prevx 3.0 v3.0.1.65 Product Overview - Core Functionality April, 2009 includes overviews of MyPrevx, Prevx 3.0 Enterprise, and Prevx 3.0 Banking and Ecommerce editions Copyright Prevx Limited 2007,2008,2009
Prevx 3.0 v3.0.1.65 Product Overview - Core Functionality April, 2009 includes overviews of MyPrevx, Prevx 3.0 Enterprise, and Prevx 3.0 Banking and Ecommerce editions Copyright Prevx Limited 2007,2008,2009
Symantec Advanced Threat Protection: Endpoint
 Symantec Advanced Threat Protection: Endpoint Data Sheet: Advanced Threat Protection The Problem Virtually all of today's advanced persistent threats leverage endpoint systems in order to infiltrate their
Symantec Advanced Threat Protection: Endpoint Data Sheet: Advanced Threat Protection The Problem Virtually all of today's advanced persistent threats leverage endpoint systems in order to infiltrate their
Phishing Activity Trends Report March, 2005
 Phishing Activity Trends Report March, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report March, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
IBM Security Network Protection Solutions
 Systems IBM Security IBM Security Network Protection Solutions Pre-emptive protection to keep you Ahead of the Threat Tanmay Shah Product Lead Network Protection Appliances IBM Security Systems 1 IBM Security
Systems IBM Security IBM Security Network Protection Solutions Pre-emptive protection to keep you Ahead of the Threat Tanmay Shah Product Lead Network Protection Appliances IBM Security Systems 1 IBM Security
Advanced Threat Defense Certification Testing Report. Trend Micro Incorporated Trend Micro Deep Discovery Inspector
 Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]
![JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]](/thumbs/83/87837079.jpg) JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
Cisco Service Control Service Security: Outgoing Spam Mitigation Solution Guide, Release 4.1.x
 CISCO SERVICE CONTROL SOLUTION GUIDE Cisco Service Control Service Security: Outgoing Spam Mitigation Solution Guide, Release 4.1.x 1 Introduction and Scope 2 Functionality Overview 3 Mass-Mailing-Based
CISCO SERVICE CONTROL SOLUTION GUIDE Cisco Service Control Service Security: Outgoing Spam Mitigation Solution Guide, Release 4.1.x 1 Introduction and Scope 2 Functionality Overview 3 Mass-Mailing-Based
SYMANTEC INTELLIGENCE REPORT NOVEMBER 2015
 SYNTEC INTELLIGENCE REPORT NOVEBER 2015 2 November 2015 3 Summary 4 From the Security Response Blog 4 Terror-lert Spam Targets the iddle East, Canada to Spread alware 5 November in Numbers 6 Targeted ttacks
SYNTEC INTELLIGENCE REPORT NOVEBER 2015 2 November 2015 3 Summary 4 From the Security Response Blog 4 Terror-lert Spam Targets the iddle East, Canada to Spread alware 5 November in Numbers 6 Targeted ttacks
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 3 Protecting Systems
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 3 Protecting Systems Objectives Explain how to harden operating systems List ways to prevent attacks through a Web browser Define
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 3 Protecting Systems Objectives Explain how to harden operating systems List ways to prevent attacks through a Web browser Define
THE BUSINESS CASE FOR OUTSIDE-IN DATA CENTER SECURITY
 THE BUSINESS CASE FOR OUTSIDE-IN DATA CENTER SECURITY DATA CENTER WEB APPS NEED MORE THAN IP-BASED DEFENSES AND NEXT-GENERATION FIREWALLS table of contents.... 2.... 4.... 5 A TechTarget White Paper Does
THE BUSINESS CASE FOR OUTSIDE-IN DATA CENTER SECURITY DATA CENTER WEB APPS NEED MORE THAN IP-BASED DEFENSES AND NEXT-GENERATION FIREWALLS table of contents.... 2.... 4.... 5 A TechTarget White Paper Does
MX Control Console. Administrative User Manual
 MX Control Console Administrative User Manual This Software and Related Documentation are proprietary to MX Logic, Inc. Copyright 2003 MX Logic, Inc. The information contained in this document is subject
MX Control Console Administrative User Manual This Software and Related Documentation are proprietary to MX Logic, Inc. Copyright 2003 MX Logic, Inc. The information contained in this document is subject
Securing Office 365 with Symantec
 February, 2016 Solution Overview: Enterprise Security Adoption of Microsoft Office 365, Google Apps, and other cloud-based productivity solutions is growing. Microsoft in its Ignite 2015 session claimed
February, 2016 Solution Overview: Enterprise Security Adoption of Microsoft Office 365, Google Apps, and other cloud-based productivity solutions is growing. Microsoft in its Ignite 2015 session claimed
MESSAGING SECURITY GATEWAY. Solution overview
 MESSAGING SECURITY GATEWAY Solution overview April 2017 CONTENTS Executive Summary...3 The case for email protection and privacy... 3 Privacy in email communication... 3 LinkedIn Phishing Sample...4 Messaging
MESSAGING SECURITY GATEWAY Solution overview April 2017 CONTENTS Executive Summary...3 The case for email protection and privacy... 3 Privacy in email communication... 3 LinkedIn Phishing Sample...4 Messaging
Second International Barometer of Security in SMBs
 1 2 Contents 1. Introduction. 3 2. Methodology.... 5 3. Details of the companies surveyed 6 4. Companies with security systems 10 5. Companies without security systems. 15 6. Infections and Internet threats.
1 2 Contents 1. Introduction. 3 2. Methodology.... 5 3. Details of the companies surveyed 6 4. Companies with security systems 10 5. Companies without security systems. 15 6. Infections and Internet threats.
Kaspersky Security Network
 The Kaspersky Security Network (KSN) is a complex distributed infrastructure dedicated to intelligently processing cybersecurity-related data streams from millions of voluntary participants around the
The Kaspersky Security Network (KSN) is a complex distributed infrastructure dedicated to intelligently processing cybersecurity-related data streams from millions of voluntary participants around the
McAfee Firewall Enterprise: The only Firewall with the Intelligence to Continuously, Automatically Reduce the Risk and Threat Exposure of Your Network
 : The only Firewall with the Intelligence to Continuously, Automatically Reduce the Risk and Threat Exposure of Your Network Reputation filtering with TrustedSource and Geo-Location costeffectively minimizes
: The only Firewall with the Intelligence to Continuously, Automatically Reduce the Risk and Threat Exposure of Your Network Reputation filtering with TrustedSource and Geo-Location costeffectively minimizes
Spam Evolution Report: October 2009
 Spam Evolution Report: October 2009 Prepare by Kaspersky Lab,a leading manufacturer of secure content management solutions About Kaspersky Lab Kaspersky Lab delivers the world s most immediate protection
Spam Evolution Report: October 2009 Prepare by Kaspersky Lab,a leading manufacturer of secure content management solutions About Kaspersky Lab Kaspersky Lab delivers the world s most immediate protection
Perimeter Defenses T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN
 T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN Perimeter Defenses Enterprises need to take their security strategy beyond stacking up layers of perimeter defenses to building up predictive
T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN Perimeter Defenses Enterprises need to take their security strategy beyond stacking up layers of perimeter defenses to building up predictive
Cyber Security Guide for NHSmail
 Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
Data Communication. Chapter # 5: Networking Threats. By: William Stalling
 Data Communication Chapter # 5: By: Networking Threats William Stalling Risk of Network Intrusion Whether wired or wireless, computer networks are quickly becoming essential to everyday activities. Individuals
Data Communication Chapter # 5: By: Networking Threats William Stalling Risk of Network Intrusion Whether wired or wireless, computer networks are quickly becoming essential to everyday activities. Individuals
At a Glance: Symantec Security.cloud vs Microsoft O365 E3
 At a Glance: Symantec Email Security.cloud vs Microsoft O365 E3 Microsoft O365 E3 Security as a Feature Symantec Email Security.cloud Why This Is Important Spam Protection Third-party blacklists subscribed
At a Glance: Symantec Email Security.cloud vs Microsoft O365 E3 Microsoft O365 E3 Security as a Feature Symantec Email Security.cloud Why This Is Important Spam Protection Third-party blacklists subscribed
IBM Proventia Management SiteProtector Sample Reports
 IBM Proventia Management SiteProtector Page Contents IBM Proventia Management SiteProtector Reporting Functionality Sample Report Index 2-25 Reports 26 Available SiteProtector Reports IBM Proventia Management
IBM Proventia Management SiteProtector Page Contents IBM Proventia Management SiteProtector Reporting Functionality Sample Report Index 2-25 Reports 26 Available SiteProtector Reports IBM Proventia Management
Mitigating Outgoing Spam, DoS/DDoS Attacks and Other Security Threats
 Solution Brief Mitigating Outgoing Spam, DoS/DDoS Attacks and Other Security Threats 2006 Allot Communications Ltd. Allot Communications, NetEnforcer and the Allot logo are registered trademarks of Allot
Solution Brief Mitigating Outgoing Spam, DoS/DDoS Attacks and Other Security Threats 2006 Allot Communications Ltd. Allot Communications, NetEnforcer and the Allot logo are registered trademarks of Allot
The State of Spam A Monthly Report June Generated by Symantec Messaging and Web Security
 The State of Spam A Monthly Report June 2007 Generated by Symantec Messaging and Web Security Monthly Spam Landscape Spam activity in May 2007 was overall consistent with trends observed in previous months.
The State of Spam A Monthly Report June 2007 Generated by Symantec Messaging and Web Security Monthly Spam Landscape Spam activity in May 2007 was overall consistent with trends observed in previous months.
Spam Filtering Works Better With a Management Policy
 Select Q&A, M. Grey, A. Hallawell Research Note 22 September 2003 Spam Filtering Works Better With a Management Policy A deployment of spam-filtering technology that does not consider business issues will
Select Q&A, M. Grey, A. Hallawell Research Note 22 September 2003 Spam Filtering Works Better With a Management Policy A deployment of spam-filtering technology that does not consider business issues will
Phishing: When is the Enemy
 Phishing: When E-mail is the Enemy Phishing, once only a consumer worry, is creating headaches for e-mail administrators as businesses become the next target. CONTENTS Understanding the Enemy 2 Three Things
Phishing: When E-mail is the Enemy Phishing, once only a consumer worry, is creating headaches for e-mail administrators as businesses become the next target. CONTENTS Understanding the Enemy 2 Three Things
with Advanced Protection
 with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
Choosing the Right Solution for Strategic Deployment of Encryption
 Choosing the Right Solution for Strategic Deployment of Email Encryption White Paper: Enterprise Email Encryption Email Protection Buyer s Guide Choosing the Right Solution for Strategic Deployment of
Choosing the Right Solution for Strategic Deployment of Email Encryption White Paper: Enterprise Email Encryption Email Protection Buyer s Guide Choosing the Right Solution for Strategic Deployment of
Technical Brochure F-SECURE THREAT SHIELD
 Technical Brochure F-SECURE THREAT SHIELD F-SECURE THREATSHIELD F-Secure ThreatShield is a gateway-level security solution for protecting email and web traffic, with built-in network sandboxing technology.
Technical Brochure F-SECURE THREAT SHIELD F-SECURE THREATSHIELD F-Secure ThreatShield is a gateway-level security solution for protecting email and web traffic, with built-in network sandboxing technology.
Symantec Enterprise Solution Product Guide
 SOLUTION BRIEF: SYMANTEC ENTERPRISE SOLUTION PRODUCT GUIDE........................................ Symantec Enterprise Solution Product Guide Who should read this paper Businesses participating in the
SOLUTION BRIEF: SYMANTEC ENTERPRISE SOLUTION PRODUCT GUIDE........................................ Symantec Enterprise Solution Product Guide Who should read this paper Businesses participating in the
August 2009 Report #22
 August 2009 Report #22 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
August 2009 Report #22 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
Zimperium Global Threat Data
 Zimperium Global Threat Report Q2-2017 700 CVEs per Year for Mobile OS 500 300 100 07 08 09 10 11 12 13 14 15 16 17 Outdated ios Outdated ANDROID 1 of 4 Devices Introduces Unnecessary Risk 1 out of 50
Zimperium Global Threat Report Q2-2017 700 CVEs per Year for Mobile OS 500 300 100 07 08 09 10 11 12 13 14 15 16 17 Outdated ios Outdated ANDROID 1 of 4 Devices Introduces Unnecessary Risk 1 out of 50
Machine-Powered Learning for People-Centered Security
 White paper Machine-Powered Learning for People-Centered Security Protecting Email with the Proofpoint Stateful Composite Scoring Service www.proofpoint.com INTRODUCTION: OUTGUNNED AND OVERWHELMED Today
White paper Machine-Powered Learning for People-Centered Security Protecting Email with the Proofpoint Stateful Composite Scoring Service www.proofpoint.com INTRODUCTION: OUTGUNNED AND OVERWHELMED Today
REPORT. proofpoint.com
 REPORT proofpoint.com Email fraud, also known as business email compromise (BEC), is one of today s greatest cyber threats. These socially engineered attacks seek to exploit people rather than technology.
REPORT proofpoint.com Email fraud, also known as business email compromise (BEC), is one of today s greatest cyber threats. These socially engineered attacks seek to exploit people rather than technology.
Trustwave SEG Cloud BEC Fraud Detection Basics
 .trust Trustwave SEG Cloud BEC Fraud Detection Basics Table of Contents About This Document 1 1 Background 2 2 Configuring Trustwave SEG Cloud for BEC Fraud Detection 5 2.1 Enable the Block Business Email
.trust Trustwave SEG Cloud BEC Fraud Detection Basics Table of Contents About This Document 1 1 Background 2 2 Configuring Trustwave SEG Cloud for BEC Fraud Detection 5 2.1 Enable the Block Business Email
IBM Express Managed Security Services for Security. Anti-Virus Administrator s Guide. Version 5.31
 IBM Express Managed Security Services for Email Security Anti-Virus Administrator s Guide Version 5.31 Table of Contents 1. Service overview...3 1.1 Welcome... 3 1.2 Anti-Virus (AV) features... 3 1.3 How
IBM Express Managed Security Services for Email Security Anti-Virus Administrator s Guide Version 5.31 Table of Contents 1. Service overview...3 1.1 Welcome... 3 1.2 Anti-Virus (AV) features... 3 1.3 How
Symantec Endpoint Protection
 Overview provides unrivaled security across physical and virtual platforms and support for the latest operating systems-mac OS X 10.9 and Windows 8.1. Powered by Symantec Insight and by SONAR, a single,
Overview provides unrivaled security across physical and virtual platforms and support for the latest operating systems-mac OS X 10.9 and Windows 8.1. Powered by Symantec Insight and by SONAR, a single,
Deployment Guides. Help Documentation
 Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2019 SmarterTools Inc. Deployment Guides SmarterMail in Individual and Micro-business
Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2019 SmarterTools Inc. Deployment Guides SmarterMail in Individual and Micro-business
Phishing in the Age of SaaS
 Phishing in the Age of SaaS AN ESSENTIAL GUIDE FOR BUSINESSES AND USERS The Cloud Security Platform Q3 2017 intro Phishing attacks have become the primary hacking method used against organizations. In
Phishing in the Age of SaaS AN ESSENTIAL GUIDE FOR BUSINESSES AND USERS The Cloud Security Platform Q3 2017 intro Phishing attacks have become the primary hacking method used against organizations. In
Evaluating DMARC Effectiveness for the Financial Services Industry
 Evaluating DMARC Effectiveness for the Financial Services Industry by Robert Holmes General Manager, Email Fraud Protection Return Path Executive Summary Email spoofing steadily increases annually. DMARC
Evaluating DMARC Effectiveness for the Financial Services Industry by Robert Holmes General Manager, Email Fraud Protection Return Path Executive Summary Email spoofing steadily increases annually. DMARC
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
White Paper. Why IDS Can t Adequately Protect Your IoT Devices
 White Paper Why IDS Can t Adequately Protect Your IoT Devices Introduction As a key component in information technology security, Intrusion Detection Systems (IDS) monitor networks for suspicious activity
White Paper Why IDS Can t Adequately Protect Your IoT Devices Introduction As a key component in information technology security, Intrusion Detection Systems (IDS) monitor networks for suspicious activity
INSIDE. Overview of Intelligent Message Filter Integration. Symantec Enterprise Security
 Symantec Enterprise Security WHITE PAPER Overview of Intelligent Message Filter Integration by David Scott Sr. Product Manager Symantec Mail Security Symantec Corporation INSIDE Overview of the IMF Increasing
Symantec Enterprise Security WHITE PAPER Overview of Intelligent Message Filter Integration by David Scott Sr. Product Manager Symantec Mail Security Symantec Corporation INSIDE Overview of the IMF Increasing
Q WEB APPLICATION ATTACK STATISTICS
 WEB APPLICATION ATTACK STATISTICS CONTENTS Introduction...3 Results at a glance...4 Web application attacks: statistics...5 Attack types...5 Attack trends...8 Conclusions... 11 2 INTRODUCTION This report
WEB APPLICATION ATTACK STATISTICS CONTENTS Introduction...3 Results at a glance...4 Web application attacks: statistics...5 Attack types...5 Attack trends...8 Conclusions... 11 2 INTRODUCTION This report
Phishing Activity Trends Report January, 2005
 Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Real Security. In Real Time. White Paper. Preemptive Malware Protection through Outbreak Detection
 Real Security. In Real Time. White Paper Preemptive Malware Protection through Detection Table of Contents Executive Summary...2 Response Time to New s The Achilles Heel of the Anti-Virus Industry...3
Real Security. In Real Time. White Paper Preemptive Malware Protection through Detection Table of Contents Executive Summary...2 Response Time to New s The Achilles Heel of the Anti-Virus Industry...3
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS
 10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
Latest View on the Threat of Information Security and Risk Management Trends
 Latest View on the Threat of Information Security and Risk Management Trends Rob K Lamb, Vice-President, Worldwide Sales - Security, IBM Corporation lambr@us.ibm.com 2009 IBM Corporation Topics IBM security
Latest View on the Threat of Information Security and Risk Management Trends Rob K Lamb, Vice-President, Worldwide Sales - Security, IBM Corporation lambr@us.ibm.com 2009 IBM Corporation Topics IBM security
