System Up and Running. We are now going to shut down the system. Load Average: How Busy the System Is. System Halt (1)
|
|
|
- Joanna Pope
- 5 years ago
- Views:
Transcription
1 7. Booting Booting 401 System Up and Running We are now going to shut down the system 7. Booting Booting 402 Load Average: How Busy the System Is System Halt (1) the command shutdown halts the system this command is reserved to the super user halt with shutdown -h (-p power off) reboot with shutdown -r shutdown requires a time (when to shutdown) shutdown notifies all users via the wall command Examples: shutdown -h 11:15 shutdown -r +20 shutdown -c (Linux: cancel running shutdown)
2 7. Booting Kernel 405 System Halt, Respect Your Users 8. Kernel not immediately not throwing out users not, if load > 0 make sure: no users, no processes, advance notice 7. Booting Kernel 406 System Halt (2) Installing a New Kernel kills all processes first per TERM signal then per KILL signal writes all buffered data to disk (sync) Usually not necessary, except you want install security patches faster boot-up less memory usage support for extra hardware components
3 9. System Logging System Logging System Logging Nuclear World: INES scale Level 7: Major accident Chernobyl, 26 April 1986 Fukushima, 11 March 2011 Level 6: Serious accident Kyshtym, Mayak, Soviet Union, 29 September 1957 Level 5: Accident with wider consequences Harrisburg, Pennsylvania, 28 March 1979 Goi^ania, Brazil, 13 September 1987 Level 4: Accident with local consequences Tokaimura, Japan, 1999 Level 3: Serious incident Level 2: Incident Cattenom, 18. Januar 2012 Level 1: Anomaly Level 0: Deviation 9. System Logging System Logging 410 Nuclear World Example Auditing International Atomic Energy Agency (IAEA) Chernobyl, Fukushima etc Priorities: how important is the message Facility: which subsystem Configuration: where should the message be delivered the log file is the newspaper Auditing = the ability to tell when who did what to what Example: on Monday, June 1st, 2014, user video-wizard did overflow the /home filesystem Resource: system wide log file (extension: network wide log file)
4 9. System Logging System Logging 413 How to Write to the System Log (1) System Messages: Facility which subsystem causes the message open(), fopen()? No! (Do not even think about it.) Assume two processes writing simultaneously. Serialization needed! Assume you want to store the logs somewhere else. Configurability needed!. Kernel Mail System System Daemons Printer System Keywords: auth, authpriv, console, cron, daemon, ftp, kern, lpr, mail, mark, news, ntp, security, syslog, user, uucp, local0 through local7 9. System Logging System Logging 414 How to Write to the System Log (2) System Messages: Priority how important is the message Solution: a special process, called syslogd (syslog daemon) serializes write requests can be configured in various ways may be reached over a network is supported by the C library (syslog(3)) value constant name description 0 LOG_EMERG emergency system is unusable 1 LOG_ALERT alert action must be taken immediately 2 LOG_CRIT critical critical conditions (probably hardware) 3 LOG_ERR error error conditions 4 LOG_WARN warning warning conditions 5 LOG_NOTICE notice normal but significant condition 6 LOG_INFO info informational message 7 LOG_DEBUG debug debug-level message Keywords: emerg, alert, crit, err, warning, notice, info, debug
5 10. Network Network Network 3. Routing adding a default gateway example route add default gw (Linux) example route add default (BSD) 4. DNS add entry nameserver in /etc/resolv.conf add entry search in /etc/resolv.conf use DNS diagnosis tools dig and host do not use nslookup 10. Network Network 418 Network Configuration DNS Records subtle differences between UNIX systems 1. Network Interface Card (NIC) must be recognized by the kernel kernel configuration is then available under a name like fxp0, em0, vr0,... depends on driver (BSD) eth0, eth1,... (Linux) 2. IP address (broadcast, netmask) must be configured via ifconfig example (Linux/Solaris/BSD) ifconfig eth netmask \ broadcast there are different types of addresses A records: request host, reply IP $ dig +short isl-s-01.htw-saarland.de MX records: request mail-domain, reply mail server (with prio) $ dig +short htw-saarland.de MX 80 m-relay2.rz.uni-saarland.de. 90 m-relay3.rz.uni-saarland.de. 20 m-relay.htw-saarland.de. 80 m-relay.rz.uni-saarland.de. SOA records: request domain, reply administrative parameters
6 10. Network Network 421 $ dig +short htw-saarland.de SOA ns.rz.uni-saarland.de. Margit\.Meyer.htw-saarland.de.... NS records: request domain, reply name-server $ dig +short htw-saarland.de NS ns.rz.uni-saarland.de. ns1.htw-saarland.de. ns.htw-saarland.de. ws-ber1.win-ip.dfn.de. PTR records: reverse DNS lookup $ dig +short in-addr.arpa ptr isl-c-01.htw-saarland.de. CNAME records: alias names $ dig +short cname www-portal.htw-saarland.de. $ for x in dig +short. NS sort ; do echo $x" " dig +short $x ; done a.root-servers.net b.root-servers.net c.root-servers.net d.root-servers.net e.root-servers.net f.root-servers.net g.root-servers.net h.root-servers.net i.root-servers.net j.root-servers.net k.root-servers.net l.root-servers.net m.root-servers.net Network Network 422 Root Servers $ dig +short. NS sort a.root-servers.net. b.root-servers.net. c.root-servers.net. d.root-servers.net. e.root-servers.net. f.root-servers.net. g.root-servers.net. h.root-servers.net. i.root-servers.net. j.root-servers.net. k.root-servers.net. l.root-servers.net. m.root-servers.net.
7 10. Network Network 425 Login via Network Login via Network telnet : a virtual terminal, first form of remote login rlogin : simplified remote login ssh : encrypted, authenticated remote login 10. Network Network 426 Problems of rlogin/telnet the network connection is unauthenticated is the target host genuine? is the connecting host genuine? unencrypted everybody sniffing on the wire (for example promiscious mode NIC) can read passwords, transmitted data,...
8 10. Network Network 429 Public Key Cryptography (1) Public Key Cryptography (3) solves both problems every user U has a public key P U a secret (private) key S U Example: To send a message m to Alice, Bob must compute m = E(P Alice,m) Alice decrypts m by computing D(S Alice,m ) There are three algorithms which are more or less used in PKC: RSA (based on factoring, 1978) DSA (based on discrete logs in Galois fields, 1985) ECDSA (based on discrete logs on elliptic curves, 1989) World records for breaking these schemes: factoring 728 bits (220 decimal digits) in 2016 (Inria, FR) factoring 768 bits special number in 2010 (Uni Bonn) factoring 663 bits (200 decimal digits) in 2005 (Uni Bonn) discrete log in GF(p), p with 768 bits in June, 2016 (U Leipzig) discrete log in GF(p), p with 596 bits in 2014 (Loria, FR) DL on EC over GF(p), p with 113 bits in Network Network 430 Public Key Cryptography (2) Recommended key sizes for these schemes RSA 2048 bits DSA 2048 bits ECDSA 160 bits The encryption function E() and the decryption function D() are public. it must be impossible to compute S U from P U
9 10. Network Firewalling 433 Client side: ssh Server side: sshd Properties authenticated ssh Implementation: OpenSSH and others connecting host must prove its identity (public key) accepting host must prove its identity (public key) user must prove his identity (public key, password) encrypted connection (especially no plain text passwords) Public Key authentication: $ ssh isl-l-01 Enter passphrase for key /home/dweber/.ssh/id_dsa : Last login: Mon Jul 16 15:46: from stl-s-studwork.htw-saarland.de FreeBSD 9.0-STABLE (ISL-S-01) #0: Wed Jun 13 01:32:10 CEST 2012 ipfw: the FreeBSD Way of Firewalling enable firewalling in /etc/rc.conf firewall_enable="yes" firewall_type="client" add rules to /etc/rc.firewall for the chosen firewall type open no rules client no servers on this machine simple basic server configuration (DNS, HTTP, NTP) closed all IP services disabled, except loopback 12. Firewalling Firewalling Firewalling Keep the bad guys out, and let the good guys in. Firewalls have rules to refuse IP packets, and accept them. First match logic: iptables, ipfw rule after rule until a rule (positively or negatively) matches Last match logic: pf, ipfilter rule after rule the last rule that matches determines target firewalling is part of TCP/IP code, therefore part of kernel Good Luck while Defending Against Hackers superhighway.html
Configuring System Message Logging
 CHAPTER 14 This chapter describes how to configure system message logging on the Cisco MDS 9020 Fabric Switch. It includes the following sections: About System Message Logging, page 14-1 System Message
CHAPTER 14 This chapter describes how to configure system message logging on the Cisco MDS 9020 Fabric Switch. It includes the following sections: About System Message Logging, page 14-1 System Message
Networking Applications
 Networking Dr. Ayman A. Abdel-Hamid College of Computing and Information Technology Arab Academy for Science & Technology and Maritime Transport 1 Outline Introduction Name Space concepts Domain Name Space
Networking Dr. Ayman A. Abdel-Hamid College of Computing and Information Technology Arab Academy for Science & Technology and Maritime Transport 1 Outline Introduction Name Space concepts Domain Name Space
Testing IPv6 address records in the DNS root
 Testing IPv6 address records in the DNS root February 2007 Geoff Huston Chief Scientist APNIC Priming a DNS name server 1. Take the provided root hints file 2. Generate a DNS query for resource records
Testing IPv6 address records in the DNS root February 2007 Geoff Huston Chief Scientist APNIC Priming a DNS name server 1. Take the provided root hints file 2. Generate a DNS query for resource records
Lecture 4: Basic Internet Operations
 Lecture 4: Basic Internet Operations Prof. Shervin Shirmohammadi SITE, University of Ottawa Prof. Shervin Shirmohammadi CEG 4395 4-1 LAN View A LAN 2 B Hub 2 Gateway to Internet Hub 1 Z (Gateway) LAN 1
Lecture 4: Basic Internet Operations Prof. Shervin Shirmohammadi SITE, University of Ottawa Prof. Shervin Shirmohammadi CEG 4395 4-1 LAN View A LAN 2 B Hub 2 Gateway to Internet Hub 1 Z (Gateway) LAN 1
DNS. David Malone. 19th October 2004
 DNS David Malone 19th October 2004 1 Names vs. Addresses Computers like addresses eg. 134.226.81.11. People prefer names salmon.maths.tcd.ie. Need a way to translate. walton.maths.tcd.ie close to salmon.maths.tcd.ie.
DNS David Malone 19th October 2004 1 Names vs. Addresses Computers like addresses eg. 134.226.81.11. People prefer names salmon.maths.tcd.ie. Need a way to translate. walton.maths.tcd.ie close to salmon.maths.tcd.ie.
Configuring System Message Logging
 58 CHAPTER This chapter describes how to configure system message logging on the Catalyst 4500 series switch. This chapter consists of these sections: About System Message Logging, page 58-1, page 58-2
58 CHAPTER This chapter describes how to configure system message logging on the Catalyst 4500 series switch. This chapter consists of these sections: About System Message Logging, page 58-1, page 58-2
IPv6 Support in the DNS. Athanassios Liakopoulos 6DEPLOY IPv6 Training, Skopje, June 2011
 IPv6 Support in the DNS Athanassios Liakopoulos (aliako@grnet.gr) 6DEPLOY IPv6 Training, Skopje, June 2011 Copy Rights This slide set is the ownership of the 6DEPLOY project via its partners The Powerpoint
IPv6 Support in the DNS Athanassios Liakopoulos (aliako@grnet.gr) 6DEPLOY IPv6 Training, Skopje, June 2011 Copy Rights This slide set is the ownership of the 6DEPLOY project via its partners The Powerpoint
External Alerting with Alert Responses
 The following topics describe how to send external event alerts from the Firepower Management Center using alert responses: Firepower Management Center Alert Responses, page 1 Creating an SNMP Alert Response,
The following topics describe how to send external event alerts from the Firepower Management Center using alert responses: Firepower Management Center Alert Responses, page 1 Creating an SNMP Alert Response,
Configuring System Message Logging
 CHAPTER 3 This chapter describes how to configure system message logging on Cisco MDS 9000 Family switches. It includes the following sections: About System Message Logging, page 3-1 System Message Logging
CHAPTER 3 This chapter describes how to configure system message logging on Cisco MDS 9000 Family switches. It includes the following sections: About System Message Logging, page 3-1 System Message Logging
The Domain Name System
 The Domain Name System History of DNS Before DNS ARPAnet HOSTS.txt contains all the hosts information Maintained by SRI s Network Information Center In SRI-NIC host Problems: Not scalable! Traffic and
The Domain Name System History of DNS Before DNS ARPAnet HOSTS.txt contains all the hosts information Maintained by SRI s Network Information Center In SRI-NIC host Problems: Not scalable! Traffic and
Configuring System Message Logging
 CHAPTER 3 This chapter describes how to configure system message logging on Cisco DCNM-SAN. It includes the following sections: Information About System Message Logging, page 3-1 Guidelines and Limitations,
CHAPTER 3 This chapter describes how to configure system message logging on Cisco DCNM-SAN. It includes the following sections: Information About System Message Logging, page 3-1 Guidelines and Limitations,
Preparation Test AAAA and EDNS0 support Share Your Results Results Reported Testing Period
 Testing Recursive Name Servers for IPv6 and EDNS0 Support SAC 017 15 March 2007 Preparation Test AAAA and EDNS0 support Share Your Results Results Reported Testing Period Background The DNS Root Server
Testing Recursive Name Servers for IPv6 and EDNS0 Support SAC 017 15 March 2007 Preparation Test AAAA and EDNS0 support Share Your Results Results Reported Testing Period Background The DNS Root Server
CounterACT Syslog Plugin
 Version 3.2.0 Table of Contents About the Syslog Plugin... 3 Multiple Destination Syslog Server Support... 3 Receiving Event Messages... 3 Sending Syslog Messages... 4 Sending CounterACT Event Messages...
Version 3.2.0 Table of Contents About the Syslog Plugin... 3 Multiple Destination Syslog Server Support... 3 Receiving Event Messages... 3 Sending Syslog Messages... 4 Sending CounterACT Event Messages...
Configuring System Message Logging
 CHAPTER 31 This chapter describes how to configure system message logging on the Catalyst 3560 switch. Note For complete syntax and usage information for the commands used in this chapter, see the Cisco
CHAPTER 31 This chapter describes how to configure system message logging on the Catalyst 3560 switch. Note For complete syntax and usage information for the commands used in this chapter, see the Cisco
Forescout. Configuration Guide. Version 3.5
 Forescout Version 3.5 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 3.5 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
External Alerting for Intrusion Events
 The following topics describe how to configure external alerting for intrusion events: About, page 1 Configuring SNMP Alerting for Intrusion Events, page 2 Configuring Syslog Alerting for Intrusion Events,
The following topics describe how to configure external alerting for intrusion events: About, page 1 Configuring SNMP Alerting for Intrusion Events, page 2 Configuring Syslog Alerting for Intrusion Events,
MSE System and Appliance Hardening Guidelines
 MSE System and Appliance Hardening Guidelines This appendix describes the hardening of MSE, which requires some services and processes to be exposed to function properly. This is referred to as MSE Appliance
MSE System and Appliance Hardening Guidelines This appendix describes the hardening of MSE, which requires some services and processes to be exposed to function properly. This is referred to as MSE Appliance
Using Debug Commands
 Using Debug Commands This chapter explains how you use debug commands to diagnose and resolve internetworking problems. Specifically, it covers the following topics: Entering debug commands Using the debug?
Using Debug Commands This chapter explains how you use debug commands to diagnose and resolve internetworking problems. Specifically, it covers the following topics: Entering debug commands Using the debug?
Services, logging, accounting Todd Kelley CST8177 Todd Kelley 1
 Services, logging, accounting Todd Kelley kelleyt@algonquincollege.com CST8177 Todd Kelley 1 services syslog logger command line utility psacct lastcomm ac, last, lastlog 2 chkconfig vs service (review)
Services, logging, accounting Todd Kelley kelleyt@algonquincollege.com CST8177 Todd Kelley 1 services syslog logger command line utility psacct lastcomm ac, last, lastlog 2 chkconfig vs service (review)
INSTITUT NATIONAL DES TELECOMMUNICATIONS. MSc Computer and Communication Networks MSc Information Technology Final Examination
 INSTITUT NATIONAL DES TELECOMMUNICATIONS Course: Computer Networking (CCN112) Duration: 2 hours MSc Computer and Communication Networks MSc Information Technology Final Examination Date: 13 February 2007
INSTITUT NATIONAL DES TELECOMMUNICATIONS Course: Computer Networking (CCN112) Duration: 2 hours MSc Computer and Communication Networks MSc Information Technology Final Examination Date: 13 February 2007
The Domain Name System
 The Domain Name System History of DNS Before DNS ARPAnet HOSTS.txt contains all the hosts information Maintained by SRI s Network Information Center In SRI-NIC host Problems: Not scalable! Traffic and
The Domain Name System History of DNS Before DNS ARPAnet HOSTS.txt contains all the hosts information Maintained by SRI s Network Information Center In SRI-NIC host Problems: Not scalable! Traffic and
K-Root Nameserver Operations
 K-Root Nameserver Operations Andrei Robachevsky Chief Technical Officer andrei@ripe.net 1 Outline Root Server System What is a root server? Where is the root? Anycast Routing The basics Advantages of using
K-Root Nameserver Operations Andrei Robachevsky Chief Technical Officer andrei@ripe.net 1 Outline Root Server System What is a root server? Where is the root? Anycast Routing The basics Advantages of using
Network System Services
 Network System Services Computer Networks Lecture 11 http://goo.gl/pze5o8 Syslog Syslog Aggregates logged messages from multiple network devices on the common logging server Easier event lookup and evaluation
Network System Services Computer Networks Lecture 11 http://goo.gl/pze5o8 Syslog Syslog Aggregates logged messages from multiple network devices on the common logging server Easier event lookup and evaluation
Troubleshooting and Fault Management Commands
 Troubleshooting and Fault Management Commands Cisco IOS Release 12.2 This chapter describes the commands used to troubleshoot a routing device. To troubleshoot, you need to discover, isolate, and resolve
Troubleshooting and Fault Management Commands Cisco IOS Release 12.2 This chapter describes the commands used to troubleshoot a routing device. To troubleshoot, you need to discover, isolate, and resolve
CS615 - Aspects of System Administration
 CS615 - Aspects of System Administration Slide 1 CS615 - Aspects of System Administration DNS; HTTP Department of Computer Science Stevens Institute of Technology Jan Schaumann jschauma@stevens-tech.edu
CS615 - Aspects of System Administration Slide 1 CS615 - Aspects of System Administration DNS; HTTP Department of Computer Science Stevens Institute of Technology Jan Schaumann jschauma@stevens-tech.edu
System Management Commands
 C H A P T E R 5 System Management Commands This chapter describes the commands used to manage the router system and its performance on the network. In general, system or network management falls into the
C H A P T E R 5 System Management Commands This chapter describes the commands used to manage the router system and its performance on the network. In general, system or network management falls into the
Basic Configuration Commands
 Basic Configuration Commands - I - Table of Contents Table of Contents Basic Configuration Commands... I Table of Contents... I Chapter 1 System Management Commands...1 1.1 Configuring File Management
Basic Configuration Commands - I - Table of Contents Table of Contents Basic Configuration Commands... I Table of Contents... I Chapter 1 System Management Commands...1 1.1 Configuring File Management
NETWORK CONFIGURATION AND SERVICES. route add default gw /etc/init.d/apache restart
 NETWORK CONFIGURATION AND SERVICES route add default gw 192.168.0.1 /etc/init.d/apache restart NETWORK CONFIGURATION There are two main approaches to configuring a machine for network access: Static configuration
NETWORK CONFIGURATION AND SERVICES route add default gw 192.168.0.1 /etc/init.d/apache restart NETWORK CONFIGURATION There are two main approaches to configuring a machine for network access: Static configuration
K-Root Name Server Operations
 K-Root Name Server Operations Andrei Robachevsky andrei@ripe.net 1 Outline Root Server System brief update Architecture Current locations Anycast deployment K.root-servers.net Server Major milestones Current
K-Root Name Server Operations Andrei Robachevsky andrei@ripe.net 1 Outline Root Server System brief update Architecture Current locations Anycast deployment K.root-servers.net Server Major milestones Current
Configuring the Cisco NAM 2220 Appliance
 CHAPTER 5 This section describes how to configure the Cisco NAM 2220 appliance to establish network connectivity, configure IP parameters, and how to perform other required administrative tasks using the
CHAPTER 5 This section describes how to configure the Cisco NAM 2220 appliance to establish network connectivity, configure IP parameters, and how to perform other required administrative tasks using the
Root DNS Anycast in South Asia
 Root DNS Anycast in South Asia Anurag Bhatia, Network Researcher JANOG 38 What are root DNS servers? Authoritative DNS servers for top level dot (like com. / net. etc) Knows authoritative DNS server of
Root DNS Anycast in South Asia Anurag Bhatia, Network Researcher JANOG 38 What are root DNS servers? Authoritative DNS servers for top level dot (like com. / net. etc) Knows authoritative DNS server of
Configuring the JUNOS Software the First Time on a Router with a Single Routing Engine
 Configuring the JUNOS Software the First Time on a Router with a Single Routing Engine When you turn on a router the first time, the JUNOS Software automatically boots and starts. You must enter basic
Configuring the JUNOS Software the First Time on a Router with a Single Routing Engine When you turn on a router the first time, the JUNOS Software automatically boots and starts. You must enter basic
CS615 - Aspects of System Administration
 CS615 - Aspects of System Administration Slide 1 CS615 - Aspects of System Administration DNS; HTTP Department of Computer Science Stevens Institute of Technology Jan Schaumann jschauma@stevens-tech.edu
CS615 - Aspects of System Administration Slide 1 CS615 - Aspects of System Administration DNS; HTTP Department of Computer Science Stevens Institute of Technology Jan Schaumann jschauma@stevens-tech.edu
Content and Purpose of This Guide... 1 User Management... 2
 Contents Introduction--1 Content and Purpose of This Guide........................... 1 User Management........................................ 2 Security--3 Security Features.........................................
Contents Introduction--1 Content and Purpose of This Guide........................... 1 User Management........................................ 2 Security--3 Security Features.........................................
If you prefer to use your own SSH client, configure NG Admin with the path to the executable:
 Each Barracuda NG Firewall system is routinely equipped with an SSH daemon listening on TCP port 22 on all administrative IP addresses (the primary box IP address and all other IP addresses that administrative
Each Barracuda NG Firewall system is routinely equipped with an SSH daemon listening on TCP port 22 on all administrative IP addresses (the primary box IP address and all other IP addresses that administrative
The net and it s Ecosystem
 The net and it s Ecosystem ICANN manages TLDs IANA manages assigned numbers TLD Owners Sell domain DNS names resolves names DNS Providers Resell domain names Regional Registries assign addresses CDN caches/
The net and it s Ecosystem ICANN manages TLDs IANA manages assigned numbers TLD Owners Sell domain DNS names resolves names DNS Providers Resell domain names Regional Registries assign addresses CDN caches/
Configuring System Message Logging
 This chapter describes how to configure system message logging on Cisco NX-OS devices. This chapter contains the following sections: About System Message Logging, page 1 Licensing Requirements for System
This chapter describes how to configure system message logging on Cisco NX-OS devices. This chapter contains the following sections: About System Message Logging, page 1 Licensing Requirements for System
Interested in learning more? Global Information Assurance Certification Paper. Copyright SANS Institute Author Retains Full Rights
 Global Information Assurance Certification Paper Copyright SANS Institute Author Retains Full Rights This paper is taken from the GIAC directory of certified professionals. Reposting is not permited without
Global Information Assurance Certification Paper Copyright SANS Institute Author Retains Full Rights This paper is taken from the GIAC directory of certified professionals. Reposting is not permited without
IPCop Installation and Management. By: Kritsada Pinato (Bugfly)
 IPCop Installation and Management By: Kritsada Pinato (Bugfly) Introduction to IPCop What is IPCop? IPCop is a firewall; first, last and always. IPCop is a specialized Linux Distribution; complete, configured,
IPCop Installation and Management By: Kritsada Pinato (Bugfly) Introduction to IPCop What is IPCop? IPCop is a firewall; first, last and always. IPCop is a specialized Linux Distribution; complete, configured,
Table of Contents 1 Information Center 1-1
 Table of Contents 1 Information Center 1-1 Information Center Overview 1-1 Introduction to Information Center 1-1 System Information Format 1-4 Information Center Configuration 1-6 Introduction to the
Table of Contents 1 Information Center 1-1 Information Center Overview 1-1 Introduction to Information Center 1-1 System Information Format 1-4 Information Center Configuration 1-6 Introduction to the
Linux Network Administration
 Secure Remote Connections with OpenSSH Objective At the conclusion of this module, the student will be able to: Configure the ssh daemon start, stop, and restart sshd 17 January 2005 NETW 111 - SSH 2 SSH
Secure Remote Connections with OpenSSH Objective At the conclusion of this module, the student will be able to: Configure the ssh daemon start, stop, and restart sshd 17 January 2005 NETW 111 - SSH 2 SSH
Advanced Networking. Domain Name System
 Advanced Networking Domain Name System Purpose of DNS servers Human being has many identifications: 1) Our name can be used for identification Problem: Two differenet people may have same name. 2) Mobile
Advanced Networking Domain Name System Purpose of DNS servers Human being has many identifications: 1) Our name can be used for identification Problem: Two differenet people may have same name. 2) Mobile
Advanced Networking. Domain Name System. Purpose of DNS servers. Purpose of DNS servers. Purpose of DNS servers
 Purpose of DNS servers Advanced Networking Domain Name System Human being has many identifications: 1) Our name can be used for identification Problem: Two differenet people may have same name. 2) Mobile
Purpose of DNS servers Advanced Networking Domain Name System Human being has many identifications: 1) Our name can be used for identification Problem: Two differenet people may have same name. 2) Mobile
Linux Network Administration
 Linux Network Administration Objective Describe the organization of the namespace Define the top-level subdomains of the Describe the process of converting IP addresses into names Define the concept of
Linux Network Administration Objective Describe the organization of the namespace Define the top-level subdomains of the Describe the process of converting IP addresses into names Define the concept of
Configuring System Message Logging
 This chapter contains the following sections: Information About System Message Logging, page 1 Licensing Requirements for System Message Logging, page 2 Guidelines and Limitations for System Message Logging,
This chapter contains the following sections: Information About System Message Logging, page 1 Licensing Requirements for System Message Logging, page 2 Guidelines and Limitations for System Message Logging,
CIT 470: Advanced Network and System Administration. Topics. System Logs. Logging
 CIT 470: Advanced Network and System Administration Logging CIT 470: Advanced Network and System Administration Slide #1 1. System logs 2. Logging policies 3. Finding logs 4. Syslog 5. Syslog servers 6.
CIT 470: Advanced Network and System Administration Logging CIT 470: Advanced Network and System Administration Slide #1 1. System logs 2. Logging policies 3. Finding logs 4. Syslog 5. Syslog servers 6.
RHCE BOOT CAMP. System Administration
 RHCE BOOT CAMP System Administration X WINDOWS X Windows was developed in the 1980 s to provide an intelligent GUI system for UNIX. It is an extremely simple client/server model, that is exceptionally
RHCE BOOT CAMP System Administration X WINDOWS X Windows was developed in the 1980 s to provide an intelligent GUI system for UNIX. It is an extremely simple client/server model, that is exceptionally
Viewing Log Files. Understanding GSS Logging Levels CHAPTER
 CHAPTER 8 This chapter describes how to store and view logged information about your GSS devices. Each GSS device contains a number of log files that retain records of specified GSS-related activities
CHAPTER 8 This chapter describes how to store and view logged information about your GSS devices. Each GSS device contains a number of log files that retain records of specified GSS-related activities
syslog: The UNIX System Logger
 1. Introduction 2150 John Fenwick Development Engineer Enterprise Systems Division Hewlett-Packard Company Cupertino, California USA fenwick@cup.hp.com Tel. 408-447-4976 syslog is a powerful and easily
1. Introduction 2150 John Fenwick Development Engineer Enterprise Systems Division Hewlett-Packard Company Cupertino, California USA fenwick@cup.hp.com Tel. 408-447-4976 syslog is a powerful and easily
CSE 265: System & Network Administration
 CSE 265: System & Network Administration DNS The Domain Name System History of DNS What does DNS do? The DNS namespace BIND software How DNS works DNS database Testing and debugging (tools) DNS History
CSE 265: System & Network Administration DNS The Domain Name System History of DNS What does DNS do? The DNS namespace BIND software How DNS works DNS database Testing and debugging (tools) DNS History
"Charting the Course... RHCE Rapid Track Course. Course Summary
 Course Summary Description This course is carefully designed to match the topics found in the Red Hat RH299 exam prep course but also features the added benefit of an entire extra day of comprehensive
Course Summary Description This course is carefully designed to match the topics found in the Red Hat RH299 exam prep course but also features the added benefit of an entire extra day of comprehensive
Table of Contents 1 V3 & V4 Appliance Quick Start V4 Appliance Reference...3
 Table of Contents 1 V & V4 Appliance Quick Start...1 1.1 Quick Start...1 1.2 Accessing Appliance Menus...1 1. Updating Appliance...1 1.4 Webmin...1 1.5 Setting Hostname IP Address...2 1.6 Starting and
Table of Contents 1 V & V4 Appliance Quick Start...1 1.1 Quick Start...1 1.2 Accessing Appliance Menus...1 1. Updating Appliance...1 1.4 Webmin...1 1.5 Setting Hostname IP Address...2 1.6 Starting and
Configuring System Message Logging
 This chapter contains the following sections: Information About System Message Logging, page 1 System Message Logging Facilities, page 2 Guidelines and Limitations for System Message Logging, page 6 Default
This chapter contains the following sections: Information About System Message Logging, page 1 System Message Logging Facilities, page 2 Guidelines and Limitations for System Message Logging, page 6 Default
Computer Center, CS, NCTU. Outline. Installation Basic Configuration
 BIND Part 1 pschiu Outline Installation Basic Configuration 2 Installing ISC BIND Step # pkg install bind911 or # cd /usr/ports/dns/bind911 # make install clean or # yum install bind.x86_64 # yum install
BIND Part 1 pschiu Outline Installation Basic Configuration 2 Installing ISC BIND Step # pkg install bind911 or # cd /usr/ports/dns/bind911 # make install clean or # yum install bind.x86_64 # yum install
The Balabit s Privileged Session Management 5 F5 Azure Reference Guide
 The Balabit s Privileged Session Management 5 F5 Azure Reference Guide March 12, 2018 Abstract Administrator Guide for Balabit s Privileged Session Management (PSM) Copyright 1996-2018 Balabit, a One Identity
The Balabit s Privileged Session Management 5 F5 Azure Reference Guide March 12, 2018 Abstract Administrator Guide for Balabit s Privileged Session Management (PSM) Copyright 1996-2018 Balabit, a One Identity
Overview of the Cisco NCS Command-Line Interface
 CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
Utilities. Introduction. Working with SCE Platform Files. Working with Directories CHAPTER
 CHAPTER 4 Revised: September 27, 2012, Introduction This chapter describes the following utilities: Working with SCE Platform Files, page 4-1 The User Log, page 4-5 Managing Syslog, page 4-8 Flow Capture,
CHAPTER 4 Revised: September 27, 2012, Introduction This chapter describes the following utilities: Working with SCE Platform Files, page 4-1 The User Log, page 4-5 Managing Syslog, page 4-8 Flow Capture,
Lab 2: Creating Secure Architectures
 Lab 2: Creating Secure Architectures A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For this you will
Lab 2: Creating Secure Architectures A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For this you will
Introduction to Network. Topics
 Introduction to Network Security Chapter 7 Transport Layer Protocols 1 TCP Layer Topics Responsible for reliable end-to-end transfer of application data. TCP vulnerabilities UDP UDP vulnerabilities DNS
Introduction to Network Security Chapter 7 Transport Layer Protocols 1 TCP Layer Topics Responsible for reliable end-to-end transfer of application data. TCP vulnerabilities UDP UDP vulnerabilities DNS
Lab 1: Creating Secure Architectures (Revision)
 Lab 1: Creating Secure Architectures (Revision) A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For
Lab 1: Creating Secure Architectures (Revision) A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For
Reliable Delivery and Filtering for Syslog
 Reliable Delivery and Filtering for Syslog First Published: November 17, 2006 Last Updated: September 10, 2007 The Reliable Delivery and Filtering for Syslog feature allows a device to be customized for
Reliable Delivery and Filtering for Syslog First Published: November 17, 2006 Last Updated: September 10, 2007 The Reliable Delivery and Filtering for Syslog feature allows a device to be customized for
DNS Session 2: DNS cache operation and DNS debugging. Joe Abley AfNOG 2006 workshop
 DNS Session 2: DNS cache operation and DNS debugging Joe Abley AfNOG 2006 workshop How caching NS works (1) If we've dealt with this query before recently, answer is already in the cache easy! Resolver
DNS Session 2: DNS cache operation and DNS debugging Joe Abley AfNOG 2006 workshop How caching NS works (1) If we've dealt with this query before recently, answer is already in the cache easy! Resolver
Goal of this session
 DNS refresher Overview Goal of this session What is DNS? How is DNS built and how does it work? How does a query work? Record types Caching and Authoritative Delegation: domains vs zones Finding the error:
DNS refresher Overview Goal of this session What is DNS? How is DNS built and how does it work? How does a query work? Record types Caching and Authoritative Delegation: domains vs zones Finding the error:
Defending Yourself Against The Wily Wireless Hacker
 Defending Yourself Against The Wily Wireless Hacker Brian S. Walden NYCWireless Presentation October 27, 2004 http://wifidefense.cuzuco.com/ What You Expect Common Hacker Techniques Direct Break-In Man-In-The-Middle
Defending Yourself Against The Wily Wireless Hacker Brian S. Walden NYCWireless Presentation October 27, 2004 http://wifidefense.cuzuco.com/ What You Expect Common Hacker Techniques Direct Break-In Man-In-The-Middle
Domain Name System (DNS)
 Domain Name System (DNS) Computer Networks Lecture 9 http://goo.gl/pze5o8 Domain Name System Naming service used in the Internet Accomplishes mapping of logical ("domain") names to IP addresses (and other
Domain Name System (DNS) Computer Networks Lecture 9 http://goo.gl/pze5o8 Domain Name System Naming service used in the Internet Accomplishes mapping of logical ("domain") names to IP addresses (and other
CS 716: Introduction to communication networks. Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay
 CS 716: Introduction to communication networks - 16 th class; 28 th Sept 2011 Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay What is IP address An identifier for a computer or device on a TCP/IP
CS 716: Introduction to communication networks - 16 th class; 28 th Sept 2011 Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay What is IP address An identifier for a computer or device on a TCP/IP
Using Debug Commands on Cisco IOS XR Software
 Using Debug Commands on Cisco IOS XR Software This document describes how to use the Cisco IOS XR software debug commands to monitor system operations and troubleshoot errors. Contents Listing Available
Using Debug Commands on Cisco IOS XR Software This document describes how to use the Cisco IOS XR software debug commands to monitor system operations and troubleshoot errors. Contents Listing Available
CompSci 356: Computer Network Architectures. Lecture 20: Domain Name System (DNS) and Content distribution networks Chapter 9.3.1
 CompSci 356: Computer Network Architectures Lecture 20: Domain Name System (DNS) and Content distribution networks Chapter 9.3.1 Xiaowei Yang xwy@cs.duke.edu Overview Domain Name System Content Distribution
CompSci 356: Computer Network Architectures Lecture 20: Domain Name System (DNS) and Content distribution networks Chapter 9.3.1 Xiaowei Yang xwy@cs.duke.edu Overview Domain Name System Content Distribution
WASABI SYSTEMS INC. Wasabi Storage Builder for NAS Quick Start Guide
 WASABI SYSTEMS INC. Wasabi Storage Builder for NAS Quick Start Guide Release v1.1 December 2006 How to Contact Wasabi Wasabi Systems Inc. 500 E. Main Street, Suite 1520 Norfolk, VA 23510 USA EMAIL: info@wasabisystems.com
WASABI SYSTEMS INC. Wasabi Storage Builder for NAS Quick Start Guide Release v1.1 December 2006 How to Contact Wasabi Wasabi Systems Inc. 500 E. Main Street, Suite 1520 Norfolk, VA 23510 USA EMAIL: info@wasabisystems.com
DNS and BIND Rock Eagle Computing Conference October 27, 2000 CL 10/25/00
 DNS and BIND 2000 Rock Eagle Computing Conference October 27, 2000 CL 10/25/00 1 The ARPANET ARPA: Advanced Research Projects Agency Part of the Department of Defense Funds defense-related projects In
DNS and BIND 2000 Rock Eagle Computing Conference October 27, 2000 CL 10/25/00 1 The ARPANET ARPA: Advanced Research Projects Agency Part of the Department of Defense Funds defense-related projects In
Cryptography Application : SSH. Cyber Security & Network Security March, 2017 Dhaka, Bangladesh
 Cryptography Application : SSH Cyber Security & Network Security 20-22 March, 2017 Dhaka, Bangladesh Issue Date: [31-12-2015] Revision: [v.1] What is Safely Authentication I am Assured of Which Host I
Cryptography Application : SSH Cyber Security & Network Security 20-22 March, 2017 Dhaka, Bangladesh Issue Date: [31-12-2015] Revision: [v.1] What is Safely Authentication I am Assured of Which Host I
Appliance Guide. Version 1.0
 Appliance Guide Version 1.0 Contents Contents 1 Revision history 2 Getting Started 3 Getting to Know the R7-3000/5000/5000x 5 Getting to Know the R7-1000 6 Setting Up the Appliance 7 Logging in to the
Appliance Guide Version 1.0 Contents Contents 1 Revision history 2 Getting Started 3 Getting to Know the R7-3000/5000/5000x 5 Getting to Know the R7-1000 6 Setting Up the Appliance 7 Logging in to the
Networks Lab Pod Diagram
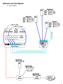 (Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
(Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
Introduction to UNIX/LINUX Security. Hu Weiwei
 Introduction to UNIX/LINUX Security Hu Weiwei Operation System Security The Security Problems in Operation Systems become more and more important The Security techniques improved rapidly The number of
Introduction to UNIX/LINUX Security Hu Weiwei Operation System Security The Security Problems in Operation Systems become more and more important The Security techniques improved rapidly The number of
CCNA Exploration Network Fundamentals. Chapter 03 Application Functionality and Protocols
 CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
Network Configuration Example
 Network Configuration Example Adding a New Routing Device to Your Network Modified: 2017-01-17 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All
Network Configuration Example Adding a New Routing Device to Your Network Modified: 2017-01-17 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All
SysadminSG RHCSA Study Guide
 SysadminSG RHCSA Study Guide This is the RHCSA Study Guide for the System Administration Study Group. The study guide is intended to be printed by those who wish to study common tasks performed by many
SysadminSG RHCSA Study Guide This is the RHCSA Study Guide for the System Administration Study Group. The study guide is intended to be printed by those who wish to study common tasks performed by many
Cisco Unified Operating System Administration Web Interface for Cisco Emergency Responder
 Cisco Unified Operating System Administration Web Interface for Cisco Emergency Responder These topics describe the Cisco Unified Operating System (OS) Administration web interface for Cisco Emergency
Cisco Unified Operating System Administration Web Interface for Cisco Emergency Responder These topics describe the Cisco Unified Operating System (OS) Administration web interface for Cisco Emergency
Cisco Unified Operating System Administration Web Interface
 Cisco Unified Operating System Administration Web Interface ServerGroup, page 1 Hardware, page 2 Network Configuration, page 3 Software Packages, page 4 System, page 5 IP Preferences, page 6 Ethernet Configuration,
Cisco Unified Operating System Administration Web Interface ServerGroup, page 1 Hardware, page 2 Network Configuration, page 3 Software Packages, page 4 System, page 5 IP Preferences, page 6 Ethernet Configuration,
f.root-servers.net ISOC cctld Workshop Nairobi, Kenya, 2005
 f.root-servers.net ISOC cctld Workshop Nairobi, Kenya, 2005 The Basics DNS The Domain Name System is a huge database of resource records globally distributed, loosely coherent, scaleable, reliable, dynamic
f.root-servers.net ISOC cctld Workshop Nairobi, Kenya, 2005 The Basics DNS The Domain Name System is a huge database of resource records globally distributed, loosely coherent, scaleable, reliable, dynamic
SEEM4540 Open Systems for E-Commerce Lecture 03 Internet Security
 SEEM4540 Open Systems for E-Commerce Lecture 03 Internet Security Consider 2. Based on DNS, identified the IP address of www.cuhk.edu.hk is 137.189.11.73. 1. Go to http://www.cuhk.edu.hk 3. Forward the
SEEM4540 Open Systems for E-Commerce Lecture 03 Internet Security Consider 2. Based on DNS, identified the IP address of www.cuhk.edu.hk is 137.189.11.73. 1. Go to http://www.cuhk.edu.hk 3. Forward the
Agha Mohammad Haidari General ICT Manager in Ministry of Communication & IT Cell#
 Install a DNS server in Windows Server 2008 IT administrators who have little or no experience with Domain Name System (DNS), can learn to install, configure and troubleshoot a Windows Server 2008 DNS
Install a DNS server in Windows Server 2008 IT administrators who have little or no experience with Domain Name System (DNS), can learn to install, configure and troubleshoot a Windows Server 2008 DNS
After you install WatchGuard XCS v10.2, make sure you install any additional software updates available for this release.
 WatchGuard XCS v10.2 Release Notes WatchGuard XCS Build 250118 Release Date February 12, 2018 Release Notes Revision Date June 5, 2018 After you install WatchGuard XCS v10.2, make sure you install any
WatchGuard XCS v10.2 Release Notes WatchGuard XCS Build 250118 Release Date February 12, 2018 Release Notes Revision Date June 5, 2018 After you install WatchGuard XCS v10.2, make sure you install any
Protocol Classification
 DNS and DHCP TCP/IP Suite Suite of protocols (not just TCP and IP) Main protocols TCP and UDP at the Transport Layer, and IP at the Network Layer Other protocols ICMP, ARP, Telnet, Ftp, HTTP, SMTP, SNMP
DNS and DHCP TCP/IP Suite Suite of protocols (not just TCP and IP) Main protocols TCP and UDP at the Transport Layer, and IP at the Network Layer Other protocols ICMP, ARP, Telnet, Ftp, HTTP, SMTP, SNMP
DNS Session 2: DNS cache operation and DNS debugging. How caching NS works (1) What if the answer is not in the cache? How caching NS works (2)
 D Session 2: D cache operation and D debugging How caching works (1) If we've dealt with this query before recently, answer is already in the cache - easy! Joe Abley AfNOG 2006 workshop Resolver Query
D Session 2: D cache operation and D debugging How caching works (1) If we've dealt with this query before recently, answer is already in the cache - easy! Joe Abley AfNOG 2006 workshop Resolver Query
Advanced Linux System Administra3on
 Advanced Linux System Administra3on Subject 9. Logging Pablo Abad Fidalgo José Ángel Herrero Velasco Departamento de Ingeniería Informá2ca y Electrónica Este tema se publica bajo Licencia: Crea2ve Commons
Advanced Linux System Administra3on Subject 9. Logging Pablo Abad Fidalgo José Ángel Herrero Velasco Departamento de Ingeniería Informá2ca y Electrónica Este tema se publica bajo Licencia: Crea2ve Commons
Network security session 9-2 Router Security. Network II
 Network security session 9-2 Router Security Network II Router security First line of defense of the network Compromise of a router can lead to many issues: Denial of network services Degrading of network
Network security session 9-2 Router Security Network II Router security First line of defense of the network Compromise of a router can lead to many issues: Denial of network services Degrading of network
BIND-USERS and Other Debugging Experiences. Mark Andrews Internet Systems Consortium
 BIND-USERS and Other Debugging Experiences Mark Andrews Internet Systems Consortium Mark_Andrews@isc.org http://isc.org BIND-USERS and Other Debugging Experiences We will look at some typical debugging
BIND-USERS and Other Debugging Experiences Mark Andrews Internet Systems Consortium Mark_Andrews@isc.org http://isc.org BIND-USERS and Other Debugging Experiences We will look at some typical debugging
G54ADM Sample Exam Questions and Answers
 G54ADM Sample Exam Questions and Answers Question 1 Compulsory Question (34 marks) (a) i. Explain the purpose of the UNIX password file. (2 marks) ii. Why doesn t the password file contain passwords? (2
G54ADM Sample Exam Questions and Answers Question 1 Compulsory Question (34 marks) (a) i. Explain the purpose of the UNIX password file. (2 marks) ii. Why doesn t the password file contain passwords? (2
Deploying Cisco UCS Central
 This chapter includes the following sections: Obtaining the Cisco UCS Central Software from Cisco, page 1 Using the Cisco UCS Central OVA File, page 2 Using the Cisco UCS Central ISO File, page 4 Logging
This chapter includes the following sections: Obtaining the Cisco UCS Central Software from Cisco, page 1 Using the Cisco UCS Central OVA File, page 2 Using the Cisco UCS Central ISO File, page 4 Logging
Linux for UNIX Administrators
 A fast paced 5-day course that is a combination of "Enterprise Linux Systems Administration", and "Enterprise Linux Networking Services. Particular focus is given to translating Solaris and HP-UX skills
A fast paced 5-day course that is a combination of "Enterprise Linux Systems Administration", and "Enterprise Linux Networking Services. Particular focus is given to translating Solaris and HP-UX skills
Course Outline: Linux Professional Institute-LPI 202. Learning Method: Instructor-led Classroom Learning. Duration: 5.00 Day(s)/ 40 hrs.
 Course Outline: Linux Professional Institute-LPI 202 Learning Method: Instructor-led Classroom Learning Duration: 5.00 Day(s)/ 40 hrs Overview: The LPI certification is a vendor-neutral Linux credential
Course Outline: Linux Professional Institute-LPI 202 Learning Method: Instructor-led Classroom Learning Duration: 5.00 Day(s)/ 40 hrs Overview: The LPI certification is a vendor-neutral Linux credential
I/A 50 Series and X- Terminals with Dynamic IP Addresses Using DNS and DHCP
 I/A 50 Series and X- Terminals with Dynamic IP Addresses R. de Groot (Rob.de.Groot@IPS.Invensys.com) R. Deen (Ron.Deen@IPS.Invensys.com) Revision 1.5 March 15, 2005 This document is Copyright 2003-2005
I/A 50 Series and X- Terminals with Dynamic IP Addresses R. de Groot (Rob.de.Groot@IPS.Invensys.com) R. Deen (Ron.Deen@IPS.Invensys.com) Revision 1.5 March 15, 2005 This document is Copyright 2003-2005
CompTIA Exam LX0-102 Linux Part 2 Version: 10.0 [ Total Questions: 177 ]
![CompTIA Exam LX0-102 Linux Part 2 Version: 10.0 [ Total Questions: 177 ] CompTIA Exam LX0-102 Linux Part 2 Version: 10.0 [ Total Questions: 177 ]](/thumbs/88/115613672.jpg) s@lm@n CompTIA Exam LX0-102 Linux Part 2 Version: 10.0 [ Total Questions: 177 ] CompTIA LX0-102 : Practice Test Topic break down Topic No. of Questions Topic 1: Volume A 60 Topic 2: Volume B 59 Topic 3:
s@lm@n CompTIA Exam LX0-102 Linux Part 2 Version: 10.0 [ Total Questions: 177 ] CompTIA LX0-102 : Practice Test Topic break down Topic No. of Questions Topic 1: Volume A 60 Topic 2: Volume B 59 Topic 3:
Alarm and System Message Overview
 CHAPTER 1 The Cisco ACNS Alarms and Error Messages Guide lists and describes the error messages for the Application and Content Networking System (ACNS). The system software sends these error messages
CHAPTER 1 The Cisco ACNS Alarms and Error Messages Guide lists and describes the error messages for the Application and Content Networking System (ACNS). The system software sends these error messages
Firewall Builder User s Guide
 Firewall Builder User s Guide Firewall Builder User s Guide $Revision: 1.24 $ $Date: 2003/11/04 06:46:19 $ Edition Copyright 2003 by NetCitadel LLC The information in this manual is subject to change without
Firewall Builder User s Guide Firewall Builder User s Guide $Revision: 1.24 $ $Date: 2003/11/04 06:46:19 $ Edition Copyright 2003 by NetCitadel LLC The information in this manual is subject to change without
Protogate Freeway Ports, Protocols, and Services (PPS)
 Protogate Freeway Ports, Protocols, and Services (PPS) DC 900-2022C Protogate, Inc. 12225 World Trade Drive Suite R San Diego, CA 92128 USA Web: www.protogate.com Email: sales@protogate.com Voice: (858)
Protogate Freeway Ports, Protocols, and Services (PPS) DC 900-2022C Protogate, Inc. 12225 World Trade Drive Suite R San Diego, CA 92128 USA Web: www.protogate.com Email: sales@protogate.com Voice: (858)
XPress-I/O Device Server Command Reference
 XPress-I/O Device Server Command Reference Part Number 900-464 Revision B July 2007 Copyright & Trademark Contacts 2006, 2007, Lantronix. All rights reserved. No part of the contents of this book may be
XPress-I/O Device Server Command Reference Part Number 900-464 Revision B July 2007 Copyright & Trademark Contacts 2006, 2007, Lantronix. All rights reserved. No part of the contents of this book may be
Domain Name System (DNS) Session 2: Resolver Operation and debugging. Joe Abley AfNOG Workshop, AIS 2017, Nairobi
 Domain Name System (DNS) Session 2: Resolver Operation and debugging Joe Abley AfNOG Workshop, AIS 2017, Nairobi DNS Resolver Operation How Resolvers Work (1)! If we've dealt with this query before recently,
Domain Name System (DNS) Session 2: Resolver Operation and debugging Joe Abley AfNOG Workshop, AIS 2017, Nairobi DNS Resolver Operation How Resolvers Work (1)! If we've dealt with this query before recently,
Cryptography Application : SSH. 7 Sept 2017, Taichung, Taiwan
 Cryptography Application : SSH 7 Sept 2017, Taichung, Taiwan What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows Who I Am The Traffic is Encrypted
Cryptography Application : SSH 7 Sept 2017, Taichung, Taiwan What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows Who I Am The Traffic is Encrypted
