OSPFv2 Cryptographic Authentication
|
|
|
- Jonas Lewis
- 6 years ago
- Views:
Transcription
1 To prevent unauthorized or invalid routing updates in your network, Open Shortest Path First version 2 (OSPFv2) protocol packets must be authenticated. There are two methods of authentication that are defined for OSPFv2: plain text authentication and cryptographic authentication. This module describes how to configure cryptographic authentication using the Hashed Message Authentication Code - Secure Hash Algorithm (HMAC-SHA). OSPFv2 specification (RFC 2328) allows only the Message-Digest 5 (MD5) algorithm for cryptographic authentication. However, RFC 5709 (OSPFv2 HMAC-SHA Cryptographic Authentication) allows OSPFv2 to use HMAC-SHA algorithms for cryptographic authentication. Finding Feature Information, page 1 Prerequisites for, page 1 Information About, page 2 How to Configure, page 3 Configuration Examples for, page 5 Additional References for, page 8 Feature Information for, page 9 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to An account on Cisco.com is not required. Prerequisites for Ensure that Open Shortest Path First version 2 (OSPFv2) is configured on your network. 1
2 Information About Information About Configuring The feature allows you to configure a key chain on the OSPF interface to authenticate OSPFv2 packets by using HMAC-SHA algorithms. You can use an existing key chain that is being used by another protocol, or you can create a key chain specifically for OSPFv2. A key chain is a list of keys. Each key consists of a key string, which is also called the password or passcode. A key-string is essential for a key to be operational. Each key is identified by a unique key ID. To authenticate the OSPFv2 packets, it is essential that the cryptographic authentication algorithm be configured with a key. OSPFv2 supports keys with key IDs ranging from 1 to 255. The combination of the cryptographic authentication algorithm and the key is known as a Security Association (SA). The authentication key on a key chain is valid for a specific time period called lifetime. An SA has the following configurable lifetimes: Accept lifetime Send lifetime While adding a new key, the Send lifetime is set to a time in the future so that the same key can be configured on all devices in the network before the new key becomes operational. Old keys are removed only after the new key is operational on all devices in the network. When packets are received, the key ID is used to fetch the data for that key. The packet is verified using the cryptographic authentication algorithm and the configured key ID. If the key ID is not found, the packet is dropped. Use the ip ospf authentication key-chain command to configure key chains for OSPFv2 cryptographic authentication. Note If OSPFv2 is configured to use a key chain, all MD5 keys that were previously configured using the ip ospf message-digest-key command are ignored. 2
3 How to Configure How to Configure Defining a Key Chain SUMMARY STEPS 1. enable 2. configure terminal 3. key chain name 4. key key-id 5. key-string name 6. cryptographic-algorithm name 7. send-lifetime start-time {infinite end-time duration seconds} 8. end DETAILED STEPS Step 1 Step 2 Command or Action enable Device> enable configure terminal Purpose Enables privileged EXEC mode. Enter your password if prompted. Enters global configuration mode. Step 3 Step 4 Device# configure terminal key chain name Device(config)# key chain sample1 key key-id Device(config-keychain)# key 1 Specifies the key chain name and enters key-chain configuration mode. Specifies the key identifier and enters key-chain key configuration mode. The range is from 1 to
4 Defining Authentication on an Interface Step 5 Command or Action key-string name Purpose Specifies the key string. Step 6 Step 7 Step 8 Device(config-keychain-key)# key-string string1 cryptographic-algorithm name Device(config-keychain-key)# cryptographic-algorithm hmac-sha-256 send-lifetime start-time {infinite end-time duration seconds} Device(config-keychain-key)# send-lifetime local 10:00:00 5 July 2013 infinite end Device(config-keychain-key)# end Configures the key with the specified cryptographic algorithm. Sets the time period during which an authentication key on a key chain is valid to be sent during key exchange with another device. Exits key-chain key configuration mode and returns to privileged EXEC mode. Defining Authentication on an Interface SUMMARY STEPS 1. enable 2. configure terminal 3. interface type number 4. ip ospf authentication key-chain name 5. end DETAILED STEPS Step 1 Command or Action enable Purpose Enables privileged EXEC mode. 4
5 Configuration Examples for Command or Action Purpose Enter your password if prompted. Step 2 Device> enable configure terminal Enters global configuration mode. Step 3 Step 4 Device# configure terminal interface type number Device(config)# interface gigabitethernet0/0/0 ip ospf authentication key-chain name Specifies an interface type and number and enters interface configuration mode. Specifies the key chain for an interface. Step 5 Device(config-if)# ip ospf authentication key-chain ospf1 end Device(config-if)# end Exits interface configuration mode and returns to privileged EXEC mode. Configuration Examples for OSPFv2 Cryptographic Authentication Defining a Key Chain The following example shows how to configure a key chain: Device> enable Device# configure terminal Device(config)# key chain sample1 Device(config-keychain)# key 1 Device(config-keychain-key)# key-string ThisIsASampleKey12345 Device(config-keychain-key)# cryptographic-algorithm hmac-sha-256 Device(config-keychain-key)# send-lifetime local 10:00:00 5 July 2013 infinite Device(config-keychain-key)# end 5
6 Verifying a Key Chain Verifying a Key Chain The following sample output from the show key chain command displays the key chain information: Device# show key chain Key-chain sample1 key 1 -- text "ThisIsASampleKey12345" accept lifetime (always valid) - (always valid) [valid now] send lifetime (10:00:00 PDT Jul ) - (infinite) The table below describes the significant fields in the output: Table 1: show ip ospf interface Field Descriptions Field key accept lifetime send lifetime Description Status of the configured key. The time interval within which the device accepts the key during key exchange with another device. The time interval within which the device sends the key during a key exchange with another device. Defining Authentication on an Interface The following example shows how to define authentication on Gigabit Ethernet interface 0/0/0: Device> enable Device# configure terminal Device(config)# interface GigabitEthernet0/0/0 Device (config-if)# ip ospf authentication key-chain sample1 Device (config-if)# end Verifying Authentication on an Interface The following sample output of the show ip ospf interface command displays the cryptographic key information: Device# show ip ospf interface GigabitEthernet0/0/0 GigabitEthernet0/0/0 is up, line protocol is up Internet Address /24, Area 1, Attached via Interface Enable Process ID 1, Router ID , Network Type BROADCAST, Cost: 10 Topology-MTID Cost Disabled Shutdown Topology Name 0 10 no no Base Enabled by interface config, including secondary ip addresses Transmit Delay is 1 sec, State DR, Priority 1 Designated Router (ID) , Interface address Backup Designated router (ID) , Interface address Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 oob-resync timeout 40 Hello due in 00:00:00 Supports Link-local Signaling (LLS) Cisco NSF helper support enabled IETF NSF helper support enabled 6
7 Verifying Authentication on an Interface Can be protected by per-prefix Loop-Free FastReroute Can be used for per-prefix Loop-Free FastReroute repair paths Index 1/1, flood queue length 0 Next 0x0(0)/0x0(0) Last flood scan length is 0, maximum is 1 Last flood scan time is 0 msec, maximum is 0 msec Neighbor Count is 1, Adjacent neighbor count is 1 Adjacent with neighbor (Backup Designated Router) Suppress hello for 0 neighbor(s) Cryptographic authentication enabled Sending SA: Key 25, Algorithm HMAC-SHA-256 key chain sample1 The table below describes the significant fields in the output: Table 2: show ip ospf interface Field Descriptions Field GigabitEthernet Internet Address Area Process ID Cost Topology-MTID Transmit Delay State Designated Router Backup Designated router Timer intervals configured Neighbor Count Cryptographic authentication Sending SA Description Status of the physical link and operational status of the protocol. Interface IP address, subnet mask, and area address. OSPF area. OSPF process ID. Administrative cost assigned to the interface. MTR topology Multitopology Identifier (MTID) is a number assigned so that the protocol can identify the topology associated with information that it sends to its peers. Transmit delay (in seconds), interface state, and router priority. Operational state of the interface. Designated router ID and respective interface IP address. Backup designated router ID and respective interface IP address. Configuration of timer intervals. Count of network neighbors and list of adjacent neighbors. Status of cryptographic authentication. Status of the sending SA (Security Association). Key, cryptographic algorithm, and key chain used. 7
8 Additional References for Additional References for Related Documents Related Topic Cisco IOS commands OSPF commands Document Title Cisco IOS Master Command List, All Releases Cisco IOS IP Routing: OSPF Command Reference Standards and RFCs Standard RFC 2328 RFC 5709 Title OSPF Version 2, April 1998 OSPFv2 HMAC-SHA Cryptographic Authentication, October 2009 Technical Assistance Description The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. Use these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies. Access to most tools on the Cisco Support and Documentation website requires a Cisco.com user ID and password. Link 8
9 Feature Information for Feature Information for Table 3: Feature Information for Feature Name OSPFv2 Cryptographic Authentication Releases 15.4(1)T Feature Information The OSPFv2 Cryptographic Authentication feature prevents unauthorized or invalid routing updates in your network by authenticating Open Shortest Path First version 2 (OSPFv2) protocol packets using HMAC-SHA algorithms. The following command was modified: ip ospf authentication. 9
10 Feature Information for 10
Area Command in Interface Mode for OSPFv2
 This document describes how to enable Open Shortest Path First version 2 (OSPFv2) on a per-interface basis to simplify the configuration of unnumbered interfaces. The ip ospf area command allows you to
This document describes how to enable Open Shortest Path First version 2 (OSPFv2) on a per-interface basis to simplify the configuration of unnumbered interfaces. The ip ospf area command allows you to
OSPFv3 Address Families
 The Open Shortest Path First version 3 (OSPFv3) address families feature enables both IPv4 and IPv6 unicast traffic to be supported. With this feature, users may have two processes per interface, but only
The Open Shortest Path First version 3 (OSPFv3) address families feature enables both IPv4 and IPv6 unicast traffic to be supported. With this feature, users may have two processes per interface, but only
OSPFv3 Address Families
 The Open Shortest Path First version 3 (OSPFv3) address families feature enables both IPv4 and IPv6 unicast traffic to be supported. With this feature, users may have two processes per interface, but only
The Open Shortest Path First version 3 (OSPFv3) address families feature enables both IPv4 and IPv6 unicast traffic to be supported. With this feature, users may have two processes per interface, but only
OSPF SNMP ifindex Value for Interface ID in Data Fields
 OSPF SNMP ifindex Value for Interface ID in Data Fields This feature allows you to configure the interface ID value Open Shortest Path First version 2 (OSPFv2) and Open Shortest Path First version 3 (OSPFv3)
OSPF SNMP ifindex Value for Interface ID in Data Fields This feature allows you to configure the interface ID value Open Shortest Path First version 2 (OSPFv2) and Open Shortest Path First version 3 (OSPFv3)
OSPFv3 Address Families
 The Open Shortest Path First version 3 (OSPFv3) address families feature enables both IPv4 and IPv6 unicast traffic to be supported. With this feature, users may have two processes per interface, but only
The Open Shortest Path First version 3 (OSPFv3) address families feature enables both IPv4 and IPv6 unicast traffic to be supported. With this feature, users may have two processes per interface, but only
Configuring NSF-OSPF
 This module describes how to configure Nonstop Forwarding (NSF) in Cisco software to minimize the duration for which a network is unavailable to its users after a switchover. The main objective of NSF
This module describes how to configure Nonstop Forwarding (NSF) in Cisco software to minimize the duration for which a network is unavailable to its users after a switchover. The main objective of NSF
The following questions are designed to test your understanding of this chapter s
 Review Questions The following questions are designed to test your understanding of this chapter s material. For more information on how to get additional questions, please see www.lammle.com/ccn a. You
Review Questions The following questions are designed to test your understanding of this chapter s material. For more information on how to get additional questions, please see www.lammle.com/ccn a. You
SNMP ifindex Value for Interface ID in OSPFv2 and OSPFv3 Data Fields
 SNMP ifindex Value for Interface ID in OSPFv2 and OSPFv3 Data Fields This document describes the configuration command that allows you to use either the current interface number or the SNMP MIB-II interface
SNMP ifindex Value for Interface ID in OSPFv2 and OSPFv3 Data Fields This document describes the configuration command that allows you to use either the current interface number or the SNMP MIB-II interface
HSRP MD5 Authentication
 Finding Feature Information, page 1 Information About, page 1 How to Configure, page 2 Configuration Examples for, page 8 Additional References, page 9 Feature Information for, page 10 Finding Feature
Finding Feature Information, page 1 Information About, page 1 How to Configure, page 2 Configuration Examples for, page 8 Additional References, page 9 Feature Information for, page 10 Finding Feature
Lab- Configuring Basic Single-Area OSPFv2
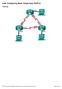 Lab- onfiguring Basic Single-Area OSPFv2 Topology G0/0 G0/0 2013 isco and/or its affiliates. All rights reserved. This document is isco Public. Page 1 of 29 Addressing Table Objectives Device Interface
Lab- onfiguring Basic Single-Area OSPFv2 Topology G0/0 G0/0 2013 isco and/or its affiliates. All rights reserved. This document is isco Public. Page 1 of 29 Addressing Table Objectives Device Interface
OSPF Limit on Number of Redistributed Routes
 Open Shortest Path First (OSPF) supports a user-defined maximum number of prefixes (routes) that are allowed to be redistributed into OSPF from other protocols or other OSPF processes. Such a limit could
Open Shortest Path First (OSPF) supports a user-defined maximum number of prefixes (routes) that are allowed to be redistributed into OSPF from other protocols or other OSPF processes. Such a limit could
VRRPv3 Protocol Support
 Virtual Router Redundancy Protocol (VRRP) enables a group of routers to form a single virtual router to provide redundancy. The LAN clients can then be configured with the virtual router as their default
Virtual Router Redundancy Protocol (VRRP) enables a group of routers to form a single virtual router to provide redundancy. The LAN clients can then be configured with the virtual router as their default
CCNA 3 (v v6.0) Chapter 10 Exam Answers % Full
 CCNA 3 (v5.0.3 + v6.0) Chapter 10 Exam Answers 2017 100% Full ccnav6.com /ccna-3-v5-0-3-v6-0-chapter-10-exam-answers-2017-100-full.html CCNA Exam Answers 2017 CCNA 3 (v5.0.3 + v6.0) Chapter 10 Exam Answers
CCNA 3 (v5.0.3 + v6.0) Chapter 10 Exam Answers 2017 100% Full ccnav6.com /ccna-3-v5-0-3-v6-0-chapter-10-exam-answers-2017-100-full.html CCNA Exam Answers 2017 CCNA 3 (v5.0.3 + v6.0) Chapter 10 Exam Answers
Configuring IP Summary Address for RIPv2
 Finding Feature Information, page 1 Information About IP Summary Address for RIPv2, page 1 How to Configure IP Summary Address for RIPv2, page 3 Configuring Examples for IP Summary Address for RIPv2, page
Finding Feature Information, page 1 Information About IP Summary Address for RIPv2, page 1 How to Configure IP Summary Address for RIPv2, page 3 Configuring Examples for IP Summary Address for RIPv2, page
Autoroute Announce and Forwarding Adjacencies For OSPFv3
 Autoroute Announce and Forwarding The Autoroute Announce and Forwarding Adjacencies for OSPFv3 feature advertises IPv6 routes over MPLS/TE IPv4 tunnels. This module describes how to configure the Autoroute
Autoroute Announce and Forwarding The Autoroute Announce and Forwarding Adjacencies for OSPFv3 feature advertises IPv6 routes over MPLS/TE IPv4 tunnels. This module describes how to configure the Autoroute
Autoroute Announce and Forwarding Adjacencies For OSPFv3
 Autoroute Announce and Forwarding The Autoroute Announce and Forwarding Adjacencies for OSPFv3 feature advertises IPv6 routes over MPLS/TE IPv4 tunnels. This module describes how to configure the Autoroute
Autoroute Announce and Forwarding The Autoroute Announce and Forwarding Adjacencies for OSPFv3 feature advertises IPv6 routes over MPLS/TE IPv4 tunnels. This module describes how to configure the Autoroute
DHCP Client. Finding Feature Information. Restrictions for the DHCP Client
 The Cisco Dynamic Host Configuration Protocol (DHCP) Client feature allows a Cisco device to act as a host requesting configuration parameters, such as an IP address, from a DHCP server. Finding Feature
The Cisco Dynamic Host Configuration Protocol (DHCP) Client feature allows a Cisco device to act as a host requesting configuration parameters, such as an IP address, from a DHCP server. Finding Feature
EIGRP Nonstop Forwarding
 EIGRP nonstop forwarding (NSF) capabilities are exchanged by EIGRP peers in hello packets. NSF works with the SSO feature in Cisco software to minimize the amount of time that a network is unavailable
EIGRP nonstop forwarding (NSF) capabilities are exchanged by EIGRP peers in hello packets. NSF works with the SSO feature in Cisco software to minimize the amount of time that a network is unavailable
EIGRP Route Tag Enhancements
 The feature enables you to specify and display route tags in dotted-decimal format, filter routes using the route tag value with wildcard mask, and set a default route tag for all internal Enhanced Interior
The feature enables you to specify and display route tags in dotted-decimal format, filter routes using the route tag value with wildcard mask, and set a default route tag for all internal Enhanced Interior
IGMP Proxy. Finding Feature Information. Prerequisites for IGMP Proxy
 This module describes how to configure IGMP proxy to enable a device to send an IGMP report to a specified destination IP address. Finding Feature Information, page 1 Prerequisites for, page 1 Information
This module describes how to configure IGMP proxy to enable a device to send an IGMP report to a specified destination IP address. Finding Feature Information, page 1 Prerequisites for, page 1 Information
Basic IP Routing. Finding Feature Information. Information About Basic IP Routing. Variable-Length Subnet Masks
 This module describes how to configure basic IP routing. The Internet Protocol (IP) is a network layer (Layer 3) protocol that contains addressing information and some control information that enables
This module describes how to configure basic IP routing. The Internet Protocol (IP) is a network layer (Layer 3) protocol that contains addressing information and some control information that enables
VLANs over IP Unnumbered SubInterfaces
 The VLANs over IP Unnumbered Subinterfaces feature allows IP unnumbered interface support to be configured on Ethernet VLAN subinterfaces. This feature also provides support for DHCP on VLAN subinterfaces.
The VLANs over IP Unnumbered Subinterfaces feature allows IP unnumbered interface support to be configured on Ethernet VLAN subinterfaces. This feature also provides support for DHCP on VLAN subinterfaces.
SSH Algorithms for Common Criteria Certification
 The feature provides the list and order of the algorithms that are allowed for Common Criteria Certification. This module describes how to configure the encryption, Message Authentication Code (MAC), and
The feature provides the list and order of the algorithms that are allowed for Common Criteria Certification. This module describes how to configure the encryption, Message Authentication Code (MAC), and
CCNA Semester 2 labs. Part 2 of 2 Labs for chapters 8 11
 CCNA Semester 2 labs Part 2 of 2 Labs for chapters 8 11 8.2.4.5 Lab - Configuring Basic Single-Area OSPFv2 8.3.3.6 Lab - Configuring Basic Single-Area OSPFv3 9.2.2.7 Lab - Configuring and Verifying Standard
CCNA Semester 2 labs Part 2 of 2 Labs for chapters 8 11 8.2.4.5 Lab - Configuring Basic Single-Area OSPFv2 8.3.3.6 Lab - Configuring Basic Single-Area OSPFv3 9.2.2.7 Lab - Configuring and Verifying Standard
Fine-Grain NBAR for Selective Applications
 By default NBAR operates in the fine-grain mode, offering NBAR's full application recognition capabilities. Used when per-packet reporting is required, fine-grain mode offers a troubleshooting advantage.
By default NBAR operates in the fine-grain mode, offering NBAR's full application recognition capabilities. Used when per-packet reporting is required, fine-grain mode offers a troubleshooting advantage.
IPv6 Routing: OSPFv3
 Open Shortest Path First version 3 (OSPFv3) is an IPv4 and IPv6 link-state routing protocol that supports IPv6 and IPv4 unicast address families (AFs). Finding Feature Information, page 1 Prerequisites
Open Shortest Path First version 3 (OSPFv3) is an IPv4 and IPv6 link-state routing protocol that supports IPv6 and IPv4 unicast address families (AFs). Finding Feature Information, page 1 Prerequisites
Basic IP Routing. Finding Feature Information. Information About Basic IP Routing. Variable-Length Subnet Masks
 This module describes how to configure basic IP routing. The Internet Protocol (IP) is a network layer (Layer 3) protocol that contains addressing information and some control information that enables
This module describes how to configure basic IP routing. The Internet Protocol (IP) is a network layer (Layer 3) protocol that contains addressing information and some control information that enables
Fine-Grain NBAR for Selective Applications
 By default NBAR operates in the fine-grain mode, offering NBAR's full application recognition capabilities. Used when per-packet reporting is required, fine-grain mode offers a troubleshooting advantage.
By default NBAR operates in the fine-grain mode, offering NBAR's full application recognition capabilities. Used when per-packet reporting is required, fine-grain mode offers a troubleshooting advantage.
Configuring Stateful Interchassis Redundancy
 The Stateful Interchassis Redundancy feature enables you to configure pairs of devices to act as backups for each other. This module describes conceptual information about and tasks for configuring stateful
The Stateful Interchassis Redundancy feature enables you to configure pairs of devices to act as backups for each other. This module describes conceptual information about and tasks for configuring stateful
Configuring OSPF. Finding Feature Information
 This module describes how to configure Open Shortest Path First (OSPF). OSPF is an Interior Gateway Protocol (IGP) developed by the OSPF working group of the Internet Engineering Task Force (IETF). OSPF
This module describes how to configure Open Shortest Path First (OSPF). OSPF is an Interior Gateway Protocol (IGP) developed by the OSPF working group of the Internet Engineering Task Force (IETF). OSPF
OSPF Stub Router Advertisement
 The feature allows you to bring a new router into a network without immediately routing traffic through the new router and allows you to gracefully shut down or reload a router without dropping packets
The feature allows you to bring a new router into a network without immediately routing traffic through the new router and allows you to gracefully shut down or reload a router without dropping packets
Configuring VRRP. Finding Feature Information. The Virtual Router Redundancy Protocol (VRRP) is an election protocol that dynamically assigns
 The Virtual Router Redundancy Protocol (VRRP) is an election protocol that dynamically assigns responsibility for one or more virtual routers to the VRRP routers on a LAN, allowing several routers on a
The Virtual Router Redundancy Protocol (VRRP) is an election protocol that dynamically assigns responsibility for one or more virtual routers to the VRRP routers on a LAN, allowing several routers on a
Configuring VRRP. Finding Feature Information. Contents
 Configuring VRRP First Published: May 2, 2005 Last Updated: July 30, 2010 The Virtual Router Redundancy Protocol (VRRP) is an election protocol that dynamically assigns responsibility for one or more virtual
Configuring VRRP First Published: May 2, 2005 Last Updated: July 30, 2010 The Virtual Router Redundancy Protocol (VRRP) is an election protocol that dynamically assigns responsibility for one or more virtual
Configuring Redundant Routing on the VPN 3000 Concentrator
 Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
OSPFv2 Local RIB. Finding Feature Information
 With the feature, each OSPF protocol instance has its own local Routing Information Base (RIB). The OSPF local RIB serves as the primary state for OSPF SPF route computation. The global RIB is not updated
With the feature, each OSPF protocol instance has its own local Routing Information Base (RIB). The OSPF local RIB serves as the primary state for OSPF SPF route computation. The global RIB is not updated
FPG Endpoint Agnostic Port Allocation
 When the Endpoint Agnostic Port Allocation feature is configured, an entry is added to the Symmetric Port Database. If the entry is already available, the port listed in the Symmetric Port Database is
When the Endpoint Agnostic Port Allocation feature is configured, an entry is added to the Symmetric Port Database. If the entry is already available, the port listed in the Symmetric Port Database is
IP Routing: RIP Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3650 Switches)
 IP Routing: RIP Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3650 Switches) First Published: November 15, 2012 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706
IP Routing: RIP Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3650 Switches) First Published: November 15, 2012 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706
Configuring Integrated IS-IS Protocol Shutdown Support Maintaining Configuration Parameters
 Configuring Integrated IS-IS Protocol Shutdown Support Maintaining Configuration Parameters The Integrated IS-IS Protocol Shutdown Support Maintaining Configuration Parameters feature allows you to disable
Configuring Integrated IS-IS Protocol Shutdown Support Maintaining Configuration Parameters The Integrated IS-IS Protocol Shutdown Support Maintaining Configuration Parameters feature allows you to disable
Configuring OSPF. Finding Feature Information
 This module describes how to configure Open Shortest Path First (OSPF). OSPF is an Interior Gateway Protocol (IGP) developed by the OSPF working group of the Internet Engineering Task Force (IETF). OSPF
This module describes how to configure Open Shortest Path First (OSPF). OSPF is an Interior Gateway Protocol (IGP) developed by the OSPF working group of the Internet Engineering Task Force (IETF). OSPF
Match-in-VRF Support for NAT
 The feature supports Network Address Translation (NAT) of packets that communicate between two hosts within the same VPN routing and forwarding (VRF) instance. In intra-vpn NAT, both the local and global
The feature supports Network Address Translation (NAT) of packets that communicate between two hosts within the same VPN routing and forwarding (VRF) instance. In intra-vpn NAT, both the local and global
DHCP Server Port-Based Address Allocation
 The feature provides port-based address allocation support on the Cisco IOS Dynamic Host Configuration Protocol (DHCP) server for the Ethernet platform. The DHCP server provides address assignment support
The feature provides port-based address allocation support on the Cisco IOS Dynamic Host Configuration Protocol (DHCP) server for the Ethernet platform. The DHCP server provides address assignment support
Add Path Support in EIGRP
 The feature enables hubs in a single Dynamic Multipoint VPN (DMVPN) domain to advertise multiple best paths to connected spokes when the Enhanced Interior Gateway Routing Protocol (EIGRP) is the routing
The feature enables hubs in a single Dynamic Multipoint VPN (DMVPN) domain to advertise multiple best paths to connected spokes when the Enhanced Interior Gateway Routing Protocol (EIGRP) is the routing
Configuring OSPF with CLI
 OSPF Configuring OSPF with CLI This section provides information to configure Open Shortest Path First (OSPF) using the command line interface. Topics in this section include: OSPF Configuration Guidelines
OSPF Configuring OSPF with CLI This section provides information to configure Open Shortest Path First (OSPF) using the command line interface. Topics in this section include: OSPF Configuration Guidelines
DHCPv6 Individual Address Assignment
 The Dynamic Host Configuration Protocol for IPv6 (DHCPv6) Individual Address Assignment feature manages nonduplicate address assignment in the correct prefix based on the network where the host is connected.
The Dynamic Host Configuration Protocol for IPv6 (DHCPv6) Individual Address Assignment feature manages nonduplicate address assignment in the correct prefix based on the network where the host is connected.
IS-IS Inbound Filtering
 The Intermediate System-to-Intermediate System (IS-IS) Inbound Filtering feature prevents unwanted IS-IS routes from being installed in a routing table. A user can deny or permit a route from being installed
The Intermediate System-to-Intermediate System (IS-IS) Inbound Filtering feature prevents unwanted IS-IS routes from being installed in a routing table. A user can deny or permit a route from being installed
Static NAT Mapping with HSRP
 This module contains procedures for configuring Network Address Translation (NAT) to support the increasing need for highly resilient IP networks. This network resiliency is required where application
This module contains procedures for configuring Network Address Translation (NAT) to support the increasing need for highly resilient IP networks. This network resiliency is required where application
IPsec Anti-Replay Window Expanding and Disabling
 IPsec Anti-Replay Window Expanding and Disabling Cisco IP security (IPsec) authentication provides anti-replay protection against an attacker duplicating encrypted packets by assigning a unique sequence
IPsec Anti-Replay Window Expanding and Disabling Cisco IP security (IPsec) authentication provides anti-replay protection against an attacker duplicating encrypted packets by assigning a unique sequence
IPv6 NEMO. Finding Feature Information. Restrictions for IPv6 NEMO
 The network mobility (NEMO) basic support protocol enables mobile IPv6 networks to attach to different points in the Internet. This protocol is an extension of Mobile IPv6 and allows session continuity
The network mobility (NEMO) basic support protocol enables mobile IPv6 networks to attach to different points in the Internet. This protocol is an extension of Mobile IPv6 and allows session continuity
BGP Graceful Shutdown
 The feature reduces or eliminates the loss of traffic along a link being shut down for maintenance. Routers always have a valid route available during the convergence process. This feature is used primarily
The feature reduces or eliminates the loss of traffic along a link being shut down for maintenance. Routers always have a valid route available during the convergence process. This feature is used primarily
OSPF with Multi Area Adjacency Configuration Example
 OSPF with Multi Area Adjacency Configuration Example Document ID: 118879 Contributed by Narra Naukwal, Cisco TAC Engineer. Mar 31, 2015 Contents Introduction Prerequisites Requirements Components Used
OSPF with Multi Area Adjacency Configuration Example Document ID: 118879 Contributed by Narra Naukwal, Cisco TAC Engineer. Mar 31, 2015 Contents Introduction Prerequisites Requirements Components Used
OSPF Incremental SPF
 The Open Shortest Path First (OSPF) protocol can be configured to use an incremental SPF algorithm for calculating the shortest path first routes. Incremental SPF is more efficient than the full SPF algorithm,
The Open Shortest Path First (OSPF) protocol can be configured to use an incremental SPF algorithm for calculating the shortest path first routes. Incremental SPF is more efficient than the full SPF algorithm,
scope scope {global vrf vrf-name} no scope {global vrf vrf-name} Syntax Description
 Multi-Toplogy Routing Commands scope scope To define the scope for a Border Gateway Protocol (BGP) routing session and to enter router scope configuration mode, use the scope command in router configuration
Multi-Toplogy Routing Commands scope scope To define the scope for a Border Gateway Protocol (BGP) routing session and to enter router scope configuration mode, use the scope command in router configuration
L2TP IPsec Support for NAT and PAT Windows Clients
 L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
ACL Syslog Correlation
 The Access Control List (ACL) Syslog Correlation feature appends a tag (either a user-defined cookie or a device-generated MD5 hash value) to access control entry (ACE) syslog entries. This tag uniquely
The Access Control List (ACL) Syslog Correlation feature appends a tag (either a user-defined cookie or a device-generated MD5 hash value) to access control entry (ACE) syslog entries. This tag uniquely
DHCP Relay Server ID Override and Link Selection Option 82 Suboptions
 DHCP Relay Server ID Override and Link Selection Option 82 Suboptions The DHCP Relay Server ID Override and Link Selection Option 82 Suboptions feature enables the relay agent to be part of all Dynamic
DHCP Relay Server ID Override and Link Selection Option 82 Suboptions The DHCP Relay Server ID Override and Link Selection Option 82 Suboptions feature enables the relay agent to be part of all Dynamic
Configuring OSPF TTL Security Check and OSPF Graceful Shutdown
 Configuring OSPF TTL Security Check and OSPF Graceful Shutdown This module describes configuration tasks to configure various options involving Open Shortest Path First (OSPF). This module contains tasks
Configuring OSPF TTL Security Check and OSPF Graceful Shutdown This module describes configuration tasks to configure various options involving Open Shortest Path First (OSPF). This module contains tasks
BGP Diverse Path Using a Diverse-Path Route Reflector
 BGP Diverse Path Using a Diverse-Path Route Reflector The feature allows Border Gateway Protocol (BGP) to distribute an alternative path other than the best path between BGP speakers when route reflectors
BGP Diverse Path Using a Diverse-Path Route Reflector The feature allows Border Gateway Protocol (BGP) to distribute an alternative path other than the best path between BGP speakers when route reflectors
Nested Class Map Support for Zone-Based Policy Firewall
 Nested Class Map Support for Zone-Based Policy Firewall The Nested Class Map Support for Zone-Based Policy Firewall feature provides the Cisco IOS XE firewall the functionality to configure multiple traffic
Nested Class Map Support for Zone-Based Policy Firewall The Nested Class Map Support for Zone-Based Policy Firewall feature provides the Cisco IOS XE firewall the functionality to configure multiple traffic
Using Flexible NetFlow Flow Sampling
 This document contains information about and instructions for configuring sampling to reduce the CPU overhead of analyzing traffic with Flexible NetFlow. NetFlow is a Cisco technology that provides statistics
This document contains information about and instructions for configuring sampling to reduce the CPU overhead of analyzing traffic with Flexible NetFlow. NetFlow is a Cisco technology that provides statistics
QoS Policy Propagation via BGP
 The feature allows you to classify packets by IP precedence based on the Border Gateway Protocol (BGP) community lists, BGP autonomous system paths, and access lists. After packets have been classified,
The feature allows you to classify packets by IP precedence based on the Border Gateway Protocol (BGP) community lists, BGP autonomous system paths, and access lists. After packets have been classified,
Using Flexible NetFlow Flow Sampling
 This document contains information about and instructions for configuring sampling to reduce the CPU overhead of analyzing traffic with Flexible NetFlow. NetFlow is a Cisco technology that provides statistics
This document contains information about and instructions for configuring sampling to reduce the CPU overhead of analyzing traffic with Flexible NetFlow. NetFlow is a Cisco technology that provides statistics
EIGRP Stub Routing. Finding Feature Information. Information About EIGRP Stub Routing. EIGRP Stub Routing
 The EIGRP stub routing feature improves network stability, reduces resource utilization, and simplifies the stub device configuration. Stub routing is commonly used in hub-and-spoke network topologies.
The EIGRP stub routing feature improves network stability, reduces resource utilization, and simplifies the stub device configuration. Stub routing is commonly used in hub-and-spoke network topologies.
RADIUS for Multiple UDP Ports
 RADIUS security servers are identified on the basis of their hostname or IP address, hostname and specific UDP port numbers, or IP address and specific UDP port numbers. The combination of the IP address
RADIUS security servers are identified on the basis of their hostname or IP address, hostname and specific UDP port numbers, or IP address and specific UDP port numbers. The combination of the IP address
BGP Route-Map Continue
 The feature introduces the continue clause to BGP route-map configuration. The continue clause allows for more programmable policy configuration and route filtering and introduces the capability to execute
The feature introduces the continue clause to BGP route-map configuration. The continue clause allows for more programmable policy configuration and route filtering and introduces the capability to execute
IPv6 Switching: Provider Edge Router over MPLS
 Multiprotocol Label Switching (MPLS) is deployed by many service providers in their IPv4 networks. Service providers want to introduce IPv6 services to their customers, but changes to their existing IPv4
Multiprotocol Label Switching (MPLS) is deployed by many service providers in their IPv4 networks. Service providers want to introduce IPv6 services to their customers, but changes to their existing IPv4
Lab - Configuring Basic Single-Area OSPFv2
 Lab - Configuring Basic Single-Area SPFv2 Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway G0/0 192.168.1.1 255.255.255.0 N/A R1 S0/0/0 (DCE) 192.168.12.1 255.255.255.252
Lab - Configuring Basic Single-Area SPFv2 Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway G0/0 192.168.1.1 255.255.255.0 N/A R1 S0/0/0 (DCE) 192.168.12.1 255.255.255.252
IPv6 Stateless Autoconfiguration
 The IPv6 stateless autoconfiguration feature can be used to manage link, subnet, and site addressing changes. Information About, page 1 How to Configure, page 2 Configuration Examples for, page 3 Additional
The IPv6 stateless autoconfiguration feature can be used to manage link, subnet, and site addressing changes. Information About, page 1 How to Configure, page 2 Configuration Examples for, page 3 Additional
BGP Policy Accounting
 Border Gateway Protocol (BGP) policy accounting measures and classifies IP traffic that is sent to, or received from, different peers. Policy accounting is enabled on an input interface, and counters based
Border Gateway Protocol (BGP) policy accounting measures and classifies IP traffic that is sent to, or received from, different peers. Policy accounting is enabled on an input interface, and counters based
Cisco Discovery Protocol Version 2
 Cisco Discovery Protocol (formerly known as CDP) is a Layer 2, media-independent, and network-independent protocol that runs on Cisco devices and enables networking applications to learn about directly
Cisco Discovery Protocol (formerly known as CDP) is a Layer 2, media-independent, and network-independent protocol that runs on Cisco devices and enables networking applications to learn about directly
NAT Routemaps Outside-to-Inside Support
 The feature enables you to configure a NAT routemap configuration that allows IP sessions to be initiated from outside the network to inside the network. This module explains how to configure the feature.
The feature enables you to configure a NAT routemap configuration that allows IP sessions to be initiated from outside the network to inside the network. This module explains how to configure the feature.
MPLS over GRE. Finding Feature Information. Prerequisites for MPLS VPN L3VPN over GRE
 The feature provides a mechanism for tunneling Multiprotocol Label Switching (MPLS) packets over a non-mpls network. This feature utilizes MPLS over generic routing encapsulation (MPLSoGRE) to encapsulate
The feature provides a mechanism for tunneling Multiprotocol Label Switching (MPLS) packets over a non-mpls network. This feature utilizes MPLS over generic routing encapsulation (MPLSoGRE) to encapsulate
AAA Dead-Server Detection
 The feature allows you to configure the criteria to be used to mark a RADIUS server as dead. If no criteria are explicitly configured, the criteria are computed dynamically on the basis of the number of
The feature allows you to configure the criteria to be used to mark a RADIUS server as dead. If no criteria are explicitly configured, the criteria are computed dynamically on the basis of the number of
An IPv6 unicast address is an identifier for a single interface, on a single node. A packet that is sent to a unicast
 An IPv6 unicast address is an identifier for a single interface, on a single node. A packet that is sent to a unicast address is delivered to the interface identified by that address. Finding Feature Information,
An IPv6 unicast address is an identifier for a single interface, on a single node. A packet that is sent to a unicast address is delivered to the interface identified by that address. Finding Feature Information,
Object Tracking: IPv6 Route Tracking
 The feature expands the Enhanced Object Tracking (EOT) functionality to allow the tracking of IPv6 routes. Finding Feature Information, page 1 Restrictions for, page 1 Information About, page 2 How to
The feature expands the Enhanced Object Tracking (EOT) functionality to allow the tracking of IPv6 routes. Finding Feature Information, page 1 Restrictions for, page 1 Information About, page 2 How to
PIM Allow RP. Finding Feature Information. Restrictions for PIM Allow RP
 This module describes how to configure the feature in IPv4 or IPv6 networks for inter-connecting Protocol Independent Multicast (PIM) Sparse Mode (SM) domains with different rendezvous points (RPs). enables
This module describes how to configure the feature in IPv4 or IPv6 networks for inter-connecting Protocol Independent Multicast (PIM) Sparse Mode (SM) domains with different rendezvous points (RPs). enables
IPv6 Routing: RIP for IPv6
 IPv6 Routing Information Protocol (RIP) functions the same and offers the same benefits as IPv4 RIP. RIP enhancements for IPv6, detailed in RFC 2080, include support for IPv6 addresses and prefixes and
IPv6 Routing Information Protocol (RIP) functions the same and offers the same benefits as IPv4 RIP. RIP enhancements for IPv6, detailed in RFC 2080, include support for IPv6 addresses and prefixes and
RMON Full. Finding Feature Information. Prerequisites for RMON Full
 Remote Network Monitoring (RMON) is a standard monitoring specification that enables various network monitors and console systems to exchange network-monitoring data. This module describes the features
Remote Network Monitoring (RMON) is a standard monitoring specification that enables various network monitors and console systems to exchange network-monitoring data. This module describes the features
NBAR2 HTTP-Based Visibility Dashboard
 The NBAR2 HTTP-based Visibility Dashboard provides a web interface displaying network traffic data and related information. The information is presented in an intuitive, interactive graphical format. Finding
The NBAR2 HTTP-based Visibility Dashboard provides a web interface displaying network traffic data and related information. The information is presented in an intuitive, interactive graphical format. Finding
BGP Dynamic Neighbors
 BGP dynamic neighbor support allows BGP peering to a group of remote neighbors that are defined by a range of IP addresses. Each range can be configured as a subnet IP address. BGP dynamic neighbors are
BGP dynamic neighbor support allows BGP peering to a group of remote neighbors that are defined by a range of IP addresses. Each range can be configured as a subnet IP address. BGP dynamic neighbors are
IPv6 Routing: IS-IS Support for IPv6
 This module describes how to configure Integrated Intermediate System-to-Intermediate System (IS-IS) for IPv6. IS-IS is an Interior Gateway Protocol (IGP) that advertises link-state information throughout
This module describes how to configure Integrated Intermediate System-to-Intermediate System (IS-IS) for IPv6. IS-IS is an Interior Gateway Protocol (IGP) that advertises link-state information throughout
Chapter 3 Lab 3-4, OSPF over Frame Relay
 Chapter 3 Lab 3-4, OSPF over Frame Relay Topology Objectives Background Configure OSPF over Frame Relay. Use non-broadcast and point-to-multipoint OSPF network types. Modify default OSPF timers. You are
Chapter 3 Lab 3-4, OSPF over Frame Relay Topology Objectives Background Configure OSPF over Frame Relay. Use non-broadcast and point-to-multipoint OSPF network types. Modify default OSPF timers. You are
IP Routing: OSPF Configuration Guide, Cisco IOS XE Release 3E
 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION
Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION
IPv6 Routing: IS-IS Support for IPv6
 This module describes how to configure Integrated Intermediate System-to-Intermediate System (IS-IS) for IPv6. IS-IS is an Interior Gateway Protocol (IGP) that advertises link-state information throughout
This module describes how to configure Integrated Intermediate System-to-Intermediate System (IS-IS) for IPv6. IS-IS is an Interior Gateway Protocol (IGP) that advertises link-state information throughout
DHCP Server Port-Based Address Allocation
 DHCP Server Port-Based Address Allocation Finding Feature Information DHCP Server Port-Based Address Allocation Last Updated: July 04, 2011 First Published: June 4, 2010 Last Updated: Sept 9, 2010 The
DHCP Server Port-Based Address Allocation Finding Feature Information DHCP Server Port-Based Address Allocation Last Updated: July 04, 2011 First Published: June 4, 2010 Last Updated: Sept 9, 2010 The
Configuring IKEv2 Load Balancer
 The IKEv2 Load Balancer feature provides support for enabling clusters of FlexVPN gateways and distributes incoming Internet Key Exchange Version 2 (IKEv2) connection requests among FlexVPN gateways. This
The IKEv2 Load Balancer feature provides support for enabling clusters of FlexVPN gateways and distributes incoming Internet Key Exchange Version 2 (IKEv2) connection requests among FlexVPN gateways. This
Sun RPC ALG Support for Firewalls and NAT
 The feature adds support for the Sun Microsystems remote-procedure call (RPC) application-level gateway (ALG) on the firewall and Network Address Translation (NAT). Sun RPC is an application layer protocol
The feature adds support for the Sun Microsystems remote-procedure call (RPC) application-level gateway (ALG) on the firewall and Network Address Translation (NAT). Sun RPC is an application layer protocol
Sun RPC ALG Support for Firewalls and NAT
 The feature adds support for the Sun Microsystems remote-procedure call (RPC) application-level gateway (ALG) on the firewall and Network Address Translation (NAT). Sun RPC is an application layer protocol
The feature adds support for the Sun Microsystems remote-procedure call (RPC) application-level gateway (ALG) on the firewall and Network Address Translation (NAT). Sun RPC is an application layer protocol
OSPF Support for Multi-VRF on CE Routers
 OSPF Support for Multi-VRF on CE Routers Finding Feature Information OSPF Support for Multi-VRF on CE Routers Last Updated: June 24, 2011 The OSPF Support for Multi-VRF on CE Routers feature provides the
OSPF Support for Multi-VRF on CE Routers Finding Feature Information OSPF Support for Multi-VRF on CE Routers Last Updated: June 24, 2011 The OSPF Support for Multi-VRF on CE Routers feature provides the
The ISG RADIUS Proxy Support for Mobile Users Hotspot Roaming and Accounting Start Filtering feature
 ISG RADIUS Proxy Support for Mobile Users Hotspot Roaming and Accounting Start Filtering The ISG RADIUS Proxy Support for Mobile Users Hotspot Roaming and Accounting Start Filtering feature allows the
ISG RADIUS Proxy Support for Mobile Users Hotspot Roaming and Accounting Start Filtering The ISG RADIUS Proxy Support for Mobile Users Hotspot Roaming and Accounting Start Filtering feature allows the
BGP NSF Awareness. Finding Feature Information
 Nonstop Forwarding (NSF) awareness allows a device to assist NSF-capable neighbors to continue forwarding packets during a Stateful Switchover (SSO) operation. The feature allows an NSF-aware device that
Nonstop Forwarding (NSF) awareness allows a device to assist NSF-capable neighbors to continue forwarding packets during a Stateful Switchover (SSO) operation. The feature allows an NSF-aware device that
AAA Server Groups. Finding Feature Information. Information About AAA Server Groups. AAA Server Groups
 Configuring a device to use authentication, authorization, and accounting (AAA) server groups provides a way to group existing server hosts. Grouping existing server hosts allows you to select a subset
Configuring a device to use authentication, authorization, and accounting (AAA) server groups provides a way to group existing server hosts. Grouping existing server hosts allows you to select a subset
IP Multicast Optimization: IGMP State Limit
 Finding Feature Information, page 1 Prerequisites for IGMP State Limit, page 1 Restrictions for IGMP State Limit, page 2 Information About IGMP State Limit, page 2 How to Configure IGMP State Limit, page
Finding Feature Information, page 1 Prerequisites for IGMP State Limit, page 1 Restrictions for IGMP State Limit, page 2 Information About IGMP State Limit, page 2 How to Configure IGMP State Limit, page
Configuration and Management of Networks
 onfiguration and Management of Networks SPF Virtual Links and Area Summarization The lab is built on the topology: bjectives Background! onfigure multi-area SPF on a r.! Verify multi-area behavior.! reate
onfiguration and Management of Networks SPF Virtual Links and Area Summarization The lab is built on the topology: bjectives Background! onfigure multi-area SPF on a r.! Verify multi-area behavior.! reate
EIGRP Dynamic Metric Calculations
 The features enables the Enhanced Interior Gateway Routing Protocol (EIGRP) to use dynamic raw radio-link characteristics (current and maximum bandwidth, latency, and resources) to compute a composite
The features enables the Enhanced Interior Gateway Routing Protocol (EIGRP) to use dynamic raw radio-link characteristics (current and maximum bandwidth, latency, and resources) to compute a composite
SSL Custom Application
 feature enables users to customize applications that run on any protocol over Secure Socket Layer (SSL), including HTTP over Secure Socket Layer (HTTPS), using the server name, if it exists in the Client
feature enables users to customize applications that run on any protocol over Secure Socket Layer (SSL), including HTTP over Secure Socket Layer (HTTPS), using the server name, if it exists in the Client
Configuring Routing Information Protocol
 Configuring Routing Information Protocol Last Updated: October 25, 2011 Routing Information Protocol (RIP) is a commonly used routing protocol in small to medium TCP/IP networks. It is a stable protocol
Configuring Routing Information Protocol Last Updated: October 25, 2011 Routing Information Protocol (RIP) is a commonly used routing protocol in small to medium TCP/IP networks. It is a stable protocol
GET VPN Resiliency. Finding Feature Information. Prerequisites for GET VPN Resiliency
 The feature improves the resiliency of Cisco Group Encrypted Transport (GET) VPN so that data traffic disruption is prevented or minimized when errors occur. Finding Feature Information, page 1 Prerequisites
The feature improves the resiliency of Cisco Group Encrypted Transport (GET) VPN so that data traffic disruption is prevented or minimized when errors occur. Finding Feature Information, page 1 Prerequisites
MPLS VPN Half-Duplex VRF
 The feature provides scalable hub-and-spoke connectivity for subscribers of an Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service. This feature addresses the limitations of hub-and-spoke
The feature provides scalable hub-and-spoke connectivity for subscribers of an Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service. This feature addresses the limitations of hub-and-spoke
SSL VPN - IPv6 Support
 The feature implements support for IPv6 transport over IPv4 SSL VPN session between a client, such as Cisco AnyConnect Mobility Client, and SSL VPN. Finding Feature Information, on page 1 Prerequisites
The feature implements support for IPv6 transport over IPv4 SSL VPN session between a client, such as Cisco AnyConnect Mobility Client, and SSL VPN. Finding Feature Information, on page 1 Prerequisites
NAT Box-to-Box High-Availability Support
 The feature enables network-wide protection by making an IP network more resilient to potential link and router failures at the Network Address Translation (NAT) border. NAT box-to-box high-availability
The feature enables network-wide protection by making an IP network more resilient to potential link and router failures at the Network Address Translation (NAT) border. NAT box-to-box high-availability
