MyFirewall (Pierre Burri)
|
|
|
- Eustace Page
- 6 years ago
- Views:
Transcription
1 MyFirewall ()!/bin/bash Copyright (c) MyFirewall is free for personal use only. Use this rewall at your own risks, I am NOT responsable if someone is able to break through it and corrupt your system. You have been warned! File Name : /etc/init.d/myfirewall Version : 1.2r09 Author :, can be reached at p.burri@linux-age.com This rewall is my own "soup" but inspired from the book "Das Firewall Buch" from Wolfgang Barth, "Linux Firewalls" second edition from Robert L. Ziegler, many articles and my rst rewall with ipchains. Licence : GNU GENERAL PUBLIC LICENCE (GPL) Date : 19-May-2001 Release : 05-Jun-2001 added forwarding for ICMP 09-Jun-2001 added possibility to administer the server from a remote host (ssh) 07-Jul-2001 ssh uses now only unprivileged ports 10-Jul-2001 removes module ipchains if necessary (SuSE 7.2) change grep to "inet addr" (SuSE 7.2) added transparent proxy 12-Jul-2001 use REDIRECT for transparent proxying "iptables -t nat -F" added when the rewall is stopped 02-Nov-2001 added tests for icmp_xxx because some kernel parameters have disappeared with SuSE Nov-2001 added second ethernet card for ADSL, added a few new local variables 24-Nov-2001 added a test if the script is run in a terminal 12-Dez-2001 added MSS (Max Segment Size) correction for ADSL in the FORWARD chain 20-Dez-2001 cleanup unnecessary test lines added many more comments, the new chains www_for, renamed logdropsyn in logdropopen, echo-request in INPUT but with burst-limit, doesn't log netbios packets anymore etc... 3-Jan-2002 service auth added in OUTPUT lter. TCP flags check added. New chains tcp_flags, spoofed_src_ip, spoofed_dst_ip, icpm_in & icmp_out added. log end of nat table. Replaced com_out and com_for with www_serv. 11-Apr changed the grep of the IP Addr because of english (addr) and german (Adr). - because of SuSE 8.0 added variables ifcong, netstat and iptables - added variable allow_smtp & allow_http for more flexibility and test purposes 15-Apr removed eth1 for DSL. with pppoe, only ppp0 is used and not eth1. - added variable allow_smtp_test 7-Jun xed ping problem. 8-Jun added possibility of a permanent ssh entry. - added variable forwarding for the possibility to disable forwarding/masquerading functions. - all lan can be disabled. 9-Jun xed bug with ssh remote entry. 89_MyFirewall.sdw - 1
2 20-Jun added variables allow_pop3 and allow_ftp for for pop3 server und ftp server. - for tests purposes added variables inside_c_lan & allow_cups_b. 16-Jul added Time Server entry and variable 16-Oct corrected a spelling mistake (int_inf1 -> int_if1) 17-Oct added echo-reply in icmp_out 28-Oct added protocols for VPN-Clients. 29-Oct added variable for switching logging on/off 13-Nov allow pop3s - "pop3 over ssl" (Port 995) 07-Dec allow imaps - "imap over ssl" (Port 993) 30-Mar allow a second ntp server - read variable from /root/.myfirewall.cong if le exists. 31-Mar remove lters on nat tables 5-Apr read variable from this le in any case and read afterward the variable from.myfirewall.cong - possibility to close some unprivilege ports if ftp is open (unpriv_ports_to_close) - added allow_webmin - dmz_server1 added for test purposes 16-Apr added the following variables: allow_ipsec, bypass_www_serv_input, nb_pings, bypass_www_serv_forward, allow_www_ip_as_src_for_lan, forward_ports_to_close, allow_hylafax, hylafax_ports - renamed unpriv_ports_to_close to input_ports_to_close 23-Apr added variable allow_only_rst_parameter and a warning message comes on the terminal. 25-Apr added variables udp_ports_to_not_log & tcp_ports_to_not_log - added variable forward_subnet_to_close 1-May added rules and variable for ntpd 26-May bug in the rules sequence in FORWARD xed. 27-May bug in forward_ports_to_close xed (www_if instead of $www_if). Usage : /etc/init.d/myfirewall cmd [ext-if] [dis ena IP-Address] 1. param: cmd = start or stop or restart or status. 2. param: ext-if = ppp0 for ADSL/Modem, ippp0 - ipppn for ISDN. 3. param: ssh-entry. If there is no 3. parameter or 3. parameter is "dis", ssh from outside is disabled (default). If 3. argument is "ena", ssh from outside is enabled. If 3. parameter is an IP-Address, only this IP-Address can enter through the rewall. Since version 1.2, MyFirewall reads its variables from this le and afterward from le /root/.myfirewall.cong if it exists. This means that the variables dened in.myfirewall.cong will overwrite the variable dened here!.myfirewall.cong should have a le access of 640 or 600. MyFirewall should be called by /etc/ppp/ip-up.local don't forget to make it execubale: chmod 755 /etc/ppp/ip-up.local ip-up.local should have the following lines:!/bin/bash /etc/init.d/myfirewall restart $1 It is probably a good idea, especially if you run a proxy like squid, to start as well a cache DNS Server (bind9 or bind8) beside the rewall. Don't forget to put the DNS Servers of your ISP (Provider) in the conguration le of /etc/named.conf A list of DNS Servers can be found on the following web page: (the following example is for DNS servers of T-Online): forwarders { ; ; }; 89_MyFirewall.sdw - 2
3 and congure carefully who can access your name server, eg.: allow-query { ; /24; }; ============================================================================== if [ $TERM = "linux" -o $TERM = "xterm" ] col_70="\015\033[80c\033[10d" green_on="\033[1;32m" red_on="\033[1;31m" color_off="\033[m\017" rc_=$col_70$green_on""$color_off rc_failed=$col_70$red_on"failed"$color_off else rc_="" rc_failed="failed" Variables with 3 stars *** have to be adapted! ======================================================= All or some of these variables will be overwritten if you have the personal conguration le /root/.myfirewall.cong!!! the following 3 variables have to be eventually adapded if "ifcong" or "netstat" or "iptables" are not in the same path on your linux distribution. These are set for SuSE Linux 8.0 For Debian and Red Hat: iptables=/sbin/iptables ifcong="/sbin/ifcong" netstat="/bin/netstat" iptables="/usr/sbin/iptables" Denition of local variables *** "ssh_rip" allow to control if a remote connection through ssh to this host is possible. The possible values are "dis" (disabled) or "ena" (enabled). The value of "ssh_rip" is overwritten, wenn an IP-Address is given as a third paramater at the start of the rewall. ssh_rip="dis" *** do you want to allow access to your web server (Apache) from outside? default = no allow_http="no" *** do you want to allow access to your mail server (Sendmail, Postx, Qmail) from outside? default = no allow_smtp="no" 89_MyFirewall.sdw - 3
4 the following variable is only for test purposes allow_smtp_test="no" *** do you want to allow access to your POP-3 server (qpopper) from outside? default = no allow_pop3="no" allow_pop3s="no" allow_imaps="no" *** do you want to allow access to your FTP server from outside? default = no allow_ftp="no" if allow_ftp=yes, all unprivilege ports will be open. input_ports_to_close allows to close all ports that we don't want to be suddenly open. input_ports_to_close can be a list of several ports. input_ports_to_close=" " input_ports_to_close="" similar to input_ports_to_close, it is possible to block some ports that are normally forwarded, undepedently of the variable allow_ftp. forward_ports_to_close="" Since this rewall is also used in certains schools, it might be desirable to stop some le sharing servers like edonkey, Gnutella, Napster, Morpheus etc. Some students otherwise would use almost the whole bandwidth for themselves... Both variables forward_ports_to_close & forward_subnet_to_close can be used for this Aimster: TCP 5025 Bearshare TCP 6346 DirectConnect: TCP edonkey: TCP UDP 4665 Gnutella: TCP 6346 Grokster: TCP 1214 Hotline: TCP KaZaA: TCP 1214 LimeWire: TCP Napster: TCP 6699 ToadNode: TCP 6346 WinMX: TCP 6699 UDP 6257 Xolox: TCP Audiogalaxy: / /24 IMesh: /24 Napigator: /24 Napster: /24 WinMX: / / forward_subnet_to_close="" do you want to allow access to your hylafax server or hylafax ftp server? allow_hylafax="no" The old port is 4557, the new one is 4559 hylafax_ports=" " hylafax_ports="4559" 89_MyFirewall.sdw - 4
5 do you want to allow access to your webmin interface? webmin should be setup with SSL! default = no allow_webmin=no webmin_port="10000" allow redirection to web, mail, ftp servers in a DMZ dmz_server1= dmz_server1_ports="80 21" is your rewall inside of a class C lan? MyFirewall is thought to protect a lan from the Internet. But, mainly for test purposes, it is possible to setup MyFirewall to protect a single host inside of a class C lan. If you set inside_c_lan=yes, probably def_ext_int will be = eth0, lan1 & lan2 will be disable and forwarding will be = no. Be sure you understand what you are doing before you change this variable! default = no inside_c_lan="no" do you want to allow CUPS broadcasts? this variable works only if inside_c_lan=yes and is mainly thought for tests purposes. default = no allow_cups_b="no" do you want to allow VPN-Clients? Prococol esp (50) and UDP port 500. default = no allow_vpn_clients="no" put here the IP-Address of your VPN-Servers vpn_server1="0/0" if do not have a second VPN-Server, just remove it. vpn_server2=0/0 do you allow full ipsec trafc? allow_ipsec="no" do you want to log dropped packets? the logles are in /var/log/messages and by SuSE also in /var/log/rewall. default for log_on = yes. default for log_nat_on = no log_on="yes" log_nat_on="no" some ports create a lot of entries in the log le. the two following variables allow to drop these port so there are not logged. udp_ports_to_not_log=" " tcp_ports_to_not_log="139" *** def_ext_int = default external interface (for the rewall's rst start) ippp0 - ipppn for ISDN, ppp0 for T-DSL/ADSL or Modems def_ext_int=ppp0 *** does this rewall run on a router? (this means that forwarding and masquarading is necessary) default = yes, otherwise set it to no. forwarding="yes" 89_MyFirewall.sdw - 5
6 *** the variable "adsl_router" is only necessary if you use this rewall on a router with a adsl/t-dsl connection. If you do not use this host as a adsl router, set "adsl_router" to no. adsl_router="yes" *** int_if1 (internal interface 1 is for the clients) int_if1="eth0" int_if2 (internal interface 2 can be for a DMZ) int_if2="eth2" rst ipsec interface ipsec_if0="ipsec0" *** IP address of this host where this rewall is running my_host=$($ifcong $int_if1 grep "inet [Aa]d" cut -d: -f 2 cut -d" " -f 1) *** lan 1 & 2 (local area network) are for your regular client-hosts, adapt it to your own needs if you do not have a lan at all, comment out () lan1 & lan2. lan1=" /24" *** if you do not have a second subnet, just remove "lan2" here or comment it out. "lan2" an be used for example as a DMZ. lan2=" /24" unprivileged ports unpriv_p="1024:" trace_p are the ports for "traceroute" trace_p="33434:33523" *** IP-Address for a transparent Proxy Server (Squid) remove "proxy" if you do not have a transparent Proxy Server proxy=$my_host Listening Port for the Proxy Server proxy_p="3128" Time Servers For a NTP-Server List see: ntp3.fau.de ntp_server1=" " ntps1-1.cs.tu-berlin.de ntp_server2=" " The ntp daemon (ntpd/xntpd) uses one of the unpriv sports The client program ntpdate uses sport ntp (123) allow_ntpd="no" allow to bypass rules of chain www_serv bypass_www_serv_output="no" bypass_www_serv_forward="no" as to be set in certain special cases e.g. ping to the own internet IP address allow_www_ip_as_src_for_lan="no" denes how many pings are allowed per minutes default is 5 per minutes nb_pings="5" 89_MyFirewall.sdw - 6
7 allows to disable the entrance of parameter $2 (external interface) and $3 (ssh remote access) on the command line. This is very usefull for servers that are administrated remotely, to avoid to block the own access over ssh. default value = no allow_only_rst_parameter="no" anything = The Internet any="0/0" list of illegal IP addresses class_a=" /8" class_b=" /12" class_c=" /16" class_d_multicast=" /4" class_e_reserved=" /5" loopback=" /8" broadcast_src=" " broadcast_dst=" " Takes variable denition from /root/.myfirewall.cong if [ -e /root/.myfirewall.cong ]. /root/.myfirewall.cong Determines all the interfaces if [ $1 = start ] Determines the ISDN or ADSL interface if [ $2 ] if [ $allow_only_rst_parameter = "no" ] www_if=$2 else if [ $TERM = "linux" -o $TERM = "xterm" ] echo -e $red_on"only rst parameter \ (start stop restart status) is allowed!"$color_off www_if=$def_ext_int else www_if=$def_ext_int Makes a list of all used interfaces all_if="$www_if $int_if1" if [ $int_if2 ] all_if="$www_if $int_if1 $int_if2" Determines the local IP on the external interface www_ip=$($ifcong $www_if grep "inet [Aa]d" cut -d: -f 2 cut -d" " -f 1) 89_MyFirewall.sdw - 7
8 determines if a remote connection with ssh for administration purposes is allowed. ssh_rip = ssh remote IP address if [ $3 ] if [ $allow_only_rst_parameter = "no" ] ssh_rip=$ START case "$1" in start) echo echo MyFirewall: Interface=$www_if Local-IP-Address=$www_ip Turning on dynamic kernel parameters echo 1 > /proc/sys/net/ipv4/tcp_syncookies echo 1 > /proc/sys/net/ipv4/icmp_echo_ignore_broadcasts echo 1 > /proc/sys/net/ipv4/icmp_ignore_bogus_error_responses the following parameters don't exist anymore with SuSE 7.3 le_exists="/proc/sys/net/ipv4/icmp_destunreach_rate" test -e $le_exists && echo 5 > $le_exists le_exists="/proc/sys/net/ipv4/icmp_echoreply_rate" test -e $le_exists && echo 5 > $le_exists le_exists="/proc/sys/net/ipv4/icmp_paramprob_rate" test -e $le_exists && echo 5 > $le_exists le_exists="/proc/sys/net/ipv4/icmp_timeexceed_rate" test -e $le_exists && echo 10 > $le_exists for f in $all_if; do if [ $allow_ipsec = "no" ] echo 1 > /proc/sys/net/ipv4/conf/$f/rp_lter else echo 0 > /proc/sys/net/ipv4/conf/$f/rp_lter echo 0 > /proc/sys/net/ipv4/conf/$f/accept_redirects echo 0 > /proc/sys/net/ipv4/conf/$f/accept_source_route echo 0 > /proc/sys/net/ipv4/conf/$f/bootp_relay echo 1 > /proc/sys/net/ipv4/conf/$f/log_martians Load the module ip_tables and remove ipchains if allready loaded modprobe -r ipchains modprobe ip_tables Set default policies echo "Setting up rewall rules..." $iptables -P INPUT DROP $iptables -P OUTPUT DROP $iptables -P FORWARD DROP Flushes all rules of all policies + nat table $iptables -F $iptables -t nat -F Create customized chains $iptables -N www_serv 89_MyFirewall.sdw - 8
9 $iptables -N com_check $iptables -N spoofed_src_ip $iptables -N spoofed_dst_ip $iptables -N icmp_in $iptables -N icmp_out $iptables -N tcp_flags $iptables -N logdropspoof $iptables -N logdropopen *** logdropspoof chain *** = log & drop spoofed packages if [ $log_on = "yes" ] $iptables -A logdropspoof -j LOG --log-prex "spoofed-ip " $iptables -A logdropspoof -j DROP *** logdropopen chain *** = log & drop new connections if [ $log_on = "yes" ] $iptables -A logdropopen -j LOG --log-prex "new-or-open " $iptables -A logdropopen -j DROP *** tcp_flags chain *** = check the validity of tcp flags 1st eld = which flags are checked 2nd eld = which flags are set $iptables -A tcp_flags -p tcp --tcp-flags ALL NONE -j DROP $iptables -A tcp_flags -p tcp --tcp-flags SYN,FIN SYN,FIN -j DROP $iptables -A tcp_flags -p tcp --tcp-flags SYN,RST SYN,RST -j DROP $iptables -A tcp_flags -p tcp --tcp-flags FIN,RST FIN,RST -j DROP $iptables -A tcp_flags -p tcp --tcp-flags ACK,FIN FIN -j DROP $iptables -A tcp_flags -p tcp --tcp-flags ACK,PSH PSH -j DROP $iptables -A tcp_flags -p tcp --tcp-flags ACK,URG URG -j DROP " *** icmp_in chain *** = accepts some icmp types if [ $log_on = "yes" ] $iptables -A icmp_in -p icmp --fragment -j LOG --log-prex "fragmented $iptables -A icmp_in -p icmp --fragment -j DROP $iptables -A icmp_in -p icmp --icmp-type echo-reply $iptables -A icmp_in -p icmp --icmp-type echo-request \ -m limit --limit $nb_pings/minute $iptables -A icmp_in -p icmp --icmp-type echo-request -j DROP $iptables -A icmp_in -p icmp --icmp-type destination-unreachable $iptables -A icmp_in -p icmp --icmp-type source-quench $iptables -A icmp_in -p icmp --icmp-type time-exceeded $iptables -A icmp_in -p icmp --icmp-type parameter-problem 89_MyFirewall.sdw - 9
10 *** spoofed_src_ip chain *** = list of invalid source IP addresses The following lines are taken from Refuse addresses dened as reserved by the IANA IANA = Internet Assigned Numbers Authority ( Note: this list includes the loopback, multicast, and reserved addresses. 0.*.*.*- Can't be blocked for DHCP users. $iptables -A spoofed_src_ip -s $class_a -j logdropspoof $iptables -A spoofed_src_ip -s $class_b -j logdropspoof if [ $inside_c_lan = "no" ] $iptables -A spoofed_src_ip -s $class_c -j logdropspoof $iptables -A spoofed_src_ip -s $class_d_multicast -j logdropspoof $iptables -A spoofed_src_ip -s $class_e_reserved -j logdropspoof $iptables -A spoofed_src_ip -s $loopback -j logdropspoof $iptables -A spoofed_src_ip -s /8 -j logdropspoof $iptables -A spoofed_src_ip -s /16 -j logdropspoof $iptables -A spoofed_src_ip -s /24 -j logdropspoof $iptables -A spoofed_src_ip -s $broadcast_src -j logdropspoof *** spoofed_dst_ip chain *** = list of invalid destination IP addresses $iptables -A spoofed_dst_ip -d $broadcast_dst -j logdropspoof $iptables -A spoofed_dst_ip -p! udp -d $class_d_multicast -j logdropspoof *** com_check chain *** = common check to INPUT & FORWARD chains Checks spoofed addresses, tcp flags and UDP open/listening ports. $iptables -A com_check -p tcp -j tcp_flags Spoong Protection: no packets comming in schould claim to be from lan 1 or 2 if [ $lan1 ] $iptables -A com_check -i $www_if -s $lan1 -j logdropspoof if [ $lan2 ] $iptables -A com_check -i $www_if -s $lan2 -j logdropspoof $iptables -A com_check -i $www_if -j spoofed_src_ip $iptables -A com_check -i $www_if -j spoofed_dst_ip reject all udp connections started from the Internet on listening port >= 1024, (for eg. NFS) but except port related to DNS for udp_p in $($netstat -nlpu grep -v named \ cut -d: -f2 cut -d" " -f1 \ sed -n '/[0-9].*/p'); do if [ $udp_p -ge 1024 ]; $iptables -A com_check -p udp -i $www_if --dport $udp_p -j logdropopen reject anything + log to X Window ports $iptables -A com_check -p tcp -i $www_if --dport 6000:6063 -j logdropopen reject + log anything to Open Window port $iptables -A com_check -p tcp -i $www_if --dport j logdropopen reject + log anything NFS & RPC port udp ports are already taken care above $iptables -A com_check -p tcp -i $www_if --dport j logdropopen 89_MyFirewall.sdw - 10
11 $iptables -A com_check -p tcp -i $www_if --dport 111 -j logdropopen *** INPUT chain *** ======================================================================= accept everything comming from loopback device $iptables -A INPUT -i lo if [ $allow_ipsec = "yes" ] $iptables -A INPUT -p udp --sport dport 500 $iptables -A INPUT -p 50 $iptables -A INPUT -p 51 accept everything comming from the lan 1 & 2 if [ $lan1 ] $iptables -A INPUT -i $int_if1 -s $lan1 if [ $lan2 ] $iptables -A INPUT -i $int_if2 -s $lan2 accepts some icmp_types if [ $allow_ipsec = "no" ] $iptables -A INPUT -i $www_if -p icmp -j icmp_in else $iptables -A INPUT -p icmp -j icmp_in checks TCP Flags and log and drop all possible known spoofed adresses $iptables -A INPUT -i $www_if -j com_check Admin entry:(ssh) only possible with a dened IP address or "ena" if [ $ssh_rip!= "dis" ] if [ $ssh_rip = "ena" ] -d $www_ip --dport ssh \ -m state --state NEW else $iptables -A INPUT -p tcp -i $www_if -s $ssh_rip --sport $unpriv_p \ -d $www_ip --dport ssh \ -m state --state NEW 89_MyFirewall.sdw - 11
12 Allow access to a mail server? if [ $allow_smtp = "yes" ] -d $www_ip --dport smtp \ -m state --state NEW Allow access to a POP-3 server? if [ $allow_pop3 = "yes" ] -d $www_ip --dport pop3 \ -m state --state NEW Allow access to a "POP-3 over SSL" server? if [ $allow_pop3s = "yes" ] -d $www_ip --dport pop3s \ -m state --state NEW Allow access to a "IMAP over SSL" server? if [ $allow_imaps = "yes" ] -d $www_ip --dport imaps \ -m state --state NEW Allow access to a FTP server? if [ $allow_ftp = "yes" ] -d $www_ip --dport ftp \ -m state --state NEW closes some ports that are suddenly open because of ftp for example 8081 is for tomcat if [ "$input_ports_to_close"!= "" ] for p in $input_ports_to_close do -d $www_ip --dport $p -j DROP -d $www_ip --dport $unpriv_p \ -m state --state NEW 89_MyFirewall.sdw - 12
13 Allow access to a Hylafax server? if [ $allow_hylafax = "yes" ] if [ "$hylafax_ports"!= "" ] for p in $hylafax_ports do -d $www_ip --dport $p Allow access to Webmin? if [ $allow_webmin = "yes" ] -d $www_ip --dport $webmin_port \ -m state --state NEW Inside c_lan? if [ $inside_c_lan = "yes" ] Allow CUP broadcasts? if [ $allow_cups_b = "yes" ] lan_b=$(echo $my_host cut -d. -f 1-3).255 $iptables -A INPUT -p udp -i $www_if --sport 631 \ -d $lan_b --dport 631 Allow access to web server? if [ $allow_http = "yes" ] -d $www_ip --dport http \ -m state --state NEW -d $www_ip --dport https \ -m state --state NEW accept replies only when the connection has been started by oneself $iptables -A INPUT -m state --state ESTABLISHED,RELATED doesn't log certain ports that ll up the log les if [ "$udp_ports_to_not_log"!= "" ] for p in $udp_ports_to_not_log do $iptables -A INPUT -p udp --dport $p -j DROP if [ "$tcp_ports_to_not_log"!= "" ] for p in $tcp_ports_to_not_log do $iptables -A INPUT -p tcp --dport $p -j DROP if [ $log_on = "yes" ] $iptables -A INPUT -m state --state NEW,INVALID \ -j LOG --log-prex "in-new " 89_MyFirewall.sdw - 13
14 log all surviving incomming packages if [ $log_on = "yes" ] $iptables -A INPUT -j LOG --log-prex "end-in " drops invalid new packages (SYN) $iptables -A INPUT -m state --state NEW,INVALID -j DROP *** icmp_out **** ======================================================================= accept some ICMP $iptables -A icmp_out -p icmp --icmp-type echo-reply $iptables -A icmp_out -p icmp --icmp-type echo-request $iptables -A icmp_out -p icmp --icmp-type destination-unreachable $iptables -A icmp_out -p icmp --icmp-type fragmentation-needed $iptables -A icmp_out -p icmp --icmp-type source-quench $iptables -A icmp_out -p icmp --icmp-type time-exceeded $iptables -A icmp_out -p icmp --icmp-type parameter-problem *** www_serv *** = output and forward to the Internet Services DNS $iptables -A www_serv -p tcp --sport $unpriv_p --dport domain $iptables -A www_serv -p udp --sport $unpriv_p --dport domain HTTP & HTTPS $iptables -A www_serv -p tcp --sport $unpriv_p --dport http $iptables -A www_serv -p tcp --sport $unpriv_p --dport https IMAP, IMAPS, POP3, POP3S & SMTP $iptables -A www_serv -p tcp --sport $unpriv_p --dport imap $iptables -A www_serv -p tcp --sport $unpriv_p --dport imaps $iptables -A www_serv -p tcp --sport $unpriv_p --dport pop3 $iptables -A www_serv -p tcp --sport $unpriv_p --dport pop3s $iptables -A www_serv -p tcp --sport $unpriv_p --dport smtp FTP (outgoing, control port) $iptables -A www_serv -p tcp --sport $unpriv_p --dport ftp FTP DATA (outgoing, passive data connection) $iptables -A www_serv -p tcp --sport $unpriv_p --dport $unpriv_p SSH $iptables -A www_serv -p tcp --sport $unpriv_p --dport ssh Traceroute $iptables -A www_serv -p udp --sport $unpriv_p --dport $trace_p Auth $iptables -A www_serv -p tcp --sport $unpriv_p --dport auth Time Servers (ntpdate uses sport ntp, xntpdd uses sport 1024:) $iptables -A www_serv -p udp --sport ntp -d $ntp_server1 --dport ntp \ if [ $ntp_server2 ] $iptables -A www_serv -p udp --sport ntp -d $ntp_server2 --dport ntp \ if [ $allow_ntpd = "yes" ] 89_MyFirewall.sdw - 14
15 $iptables -A www_serv -p udp --sport $unpriv_p -d $ntp_server1 \ --dport ntp if [ $ntp_server2 ] $iptables -A www_serv -p udp --sport $unpriv_p -d $ntp_server2 \ --dport ntp VPN - Virtual Private Network if [ $allow_vpn_clients = "yes" ] $iptables -A www_serv -p esp -d $vpn_server1 $iptables -A www_serv -p udp --sport 500 \ -d $vpn_server1 --dport 500 if [ $vpn_server2 ] $iptables -A www_serv -p esp -d $vpn_server2 $iptables -A www_serv -p udp --sport 500 \ -d $vpn_server2 --dport 500 *** OUTPUT chain *** ======================================================================= accept loopback, lan 1 & 2 $iptables -A OUTPUT -o lo if [ $allow_ipsec ] $iptables -A OUTPUT -p udp --sport dport 500 $iptables -A OUTPUT -p 50 $iptables -A OUTPUT -p 51 if [ $lan1 ] $iptables -A OUTPUT -o $int_if1 -s $my_host -d $lan1 if [ $allow_www_ip_as_src_for_lan = "yes" ] $iptables -A OUTPUT -o $int_if1 -s $www_ip -d $lan1 if [ $lan2 ] $iptables -A OUTPUT -o $int_if2 -s $my_host -d $lan2 if [ $allow_www_ip_as_src_for_lan = "yes" ] $iptables -A OUTPUT -o $int_if2 -s $www_ip -d $lan2 checks TCP flags integrity and allow some ICMP types $iptables -A OUTPUT -p tcp -j tcp_flags $iptables -A OUTPUT -p icmp -j icmp_out doesn't allow illegal destination IP addresses $iptables -A OUTPUT -j spoofed_dst_ip just for internal mail server tests if [ $allow_smtp_test = "yes" ] $iptables -A OUTPUT -p tcp -s $www_ip --sport smtp \ -d $any --dport $unpriv_p $iptables -A OUTPUT -p tcp -s $www_ip --sport smtp \ -d $any --dport smtp 89_MyFirewall.sdw - 15
16 outgoing established & related connections $iptables -A OUTPUT -o $www_if -m state --state ESTABLISHED,RELATED \ if [ $bypass_www_serv_output = "yes" ] $iptables -A OUTPUT -o $www_if -s $www_ip -m state --state NEW else $iptables -A OUTPUT -o $www_if -s $www_ip -m state --state NEW -j www_serv doesn't log certain ports that ll up the log les if [ "$udp_ports_to_not_log"!= "" ] for p in $udp_ports_to_not_log do $iptables -A OUTPUT -p udp --dport $p -j DROP if [ "$tcp_ports_to_not_log"!= "" ] for p in $tcp_ports_to_not_log do $iptables -A OUTPUT -p tcp --dport $p -j DROP log all surviving outgoing packages if [ $log_on = "yes" ] $iptables -A OUTPUT -j LOG --log-prex "end-out " drops all invalid new packages (SYN) $iptables -A OUTPUT -o $www_if -m state --state NEW,INVALID -j DROP 89_MyFirewall.sdw - 16
17 *** NAT / MASQUERADING *** ======================================================================= if [ $forwarding = "yes" ] transparent proxy for all clients if [ $proxy ] $iptables -t nat -A PREROUTING -i $int_if1 -p tcp \ --sport $unpriv_p -d! $proxy --dport http \ -j REDIRECT --to-port $proxy_p redirection of https to squid doesn't seem to work! $iptables -t nat -A PREROUTING -i $int_if1 -p tcp \ --sport $unpriv_p -d! $proxy --dport https \ -j REDIRECT --to-port $proxy_p IP Adress Redirection for Servers in a DMZ if [ $dmz_server1 ] for p in $dmz_server1_ports do $iptables -t nat -A PREROUTING -i $www_if -p tcp \ -d $www_ip --dport $p \ -j DNAT --to-destination $dmz_server1 if [ $lan1 ] $iptables -t nat -A POSTROUTING -o $www_if -s $lan1 -j MASQUERADE if [ $lan2 ] $iptables -t nat -A POSTROUTING -o $www_if -s $lan2 -j MASQUERADE if [ $log_nat_on = "yes" ] $iptables -t nat -A PREROUTING -j LOG --log-prex "end-nat-pre " $iptables -t nat -A POSTROUTING -j LOG --log-prex "end-nat-post " $iptables -t nat -A OUTPUT -j LOG --log-prex "end-nat-out " turn on IP Forwarding and dynamic address ======================================================================= echo 1 > /proc/sys/net/ipv4/ip_forward echo 1 > /proc/sys/net/ipv4/ip_dynaddr *** FORWARD chain *** ======================================================================= if [ $allow_ipsec ] if [ $lan1 ] $iptables -A FORWARD -i $int_if1 -o $ipsec_if0 $iptables -A FORWARD -i $ipsec_if0 -o $int_if1 if [ $lan2 ] $iptables -A FORWARD -i $int_if2 -o $ipsec_if0 $iptables -A FORWARD -i $ipsec_if0 -o $int_if2 correction of MSS (Max Segment Size) for ADSL clients 1452 Bytes + 40 Bytes (TCP Header) + 8 Bytes (PPPoE) = 1500 Bytes if [ $adsl_router = "yes" ] 89_MyFirewall.sdw - 17
18 $iptables -A FORWARD -p tcp --tcp-flags SYN,RST SYN \ -j TCPMSS --clamp-mss-to-pmtu $iptables -A FORWARD -i $www_if -o $int_if1 \ -m state --state ESTABLISHED,RELATED $iptables -A FORWARD -i $int_if1 -o $www_if \ -m state --state ESTABLISHED,RELATED if [ $int_if2 ] $iptables -A FORWARD -i $www_if -o $int_if2 \ -m state --state ESTABLISHED,RELATED $iptables -A FORWARD -i $int_if2 -o $www_if \ -m state --state ESTABLISHED,RELATED Allow SYN for Servers in a DMZ if [ $dmz_server1 ] for p in $dmz_server1_ports do $iptables -A FORWARD -i $www_if -p tcp \ -d $dmz_server1 --dport $p \ -m state --state NEW allow some ICMP types $iptables -A FORWARD -p icmp -j icmp_out checks TCP Flags and spoofed IPs $iptables -A FORWARD -i $www_if -j com_check closes some ports that are normally open through www_serv if [ "$forward_ports_to_close"!= "" ] for p in $forward_ports_to_close do if [ $lan1 ] $iptables -A FORWARD -p tcp -i $int_if1 -o $www_if \ -s $lan1 --dport $p -j DROP $iptables -A FORWARD -p udp -i $int_if1 -o $www_if \ -s $lan1 --dport $p -j DROP if [ $lan2 ] $iptables -A FORWARD -p tcp -i $int_if2 -o $www_if \ -s $lan2 --dport $p -j DROP $iptables -A FORWARD -p udp -i $int_if2 -o $www_if \ -s $lan2 --dport $p -j DROP closes some subnet that are normally open through www_serv if [ "$forward_subnet_to_close"!= "" ] for p in $forward_subnet_to_close do if [ $lan1 ] $iptables -A FORWARD -i $int_if1 -o $www_if \ -s $lan1 -d $p -j DROP if [ $lan2 ] 89_MyFirewall.sdw - 18
19 $iptables -A FORWARD -i $int_if2 -o $www_if \ -s $lan2 -d $p -j DROP if [ $lan1 ] if [ $bypass_www_serv_forward = "yes" ] $iptables -A FORWARD -i $int_if1 -s $lan1 -o $www_if \ -m state --state NEW else $iptables -A FORWARD -i $int_if1 -s $lan1 -o $www_if \ -m state --state NEW -j www_serv if [ $lan2 ] if [ $bypass_www_serv_forward = "yes" ] $iptables -A FORWARD -i $int_if2 -s $lan2 -o $www_if \ -m state --state NEW else $iptables -A FORWARD -i $int_if2 -s $lan2 -o $www_if \ -m state --state NEW -j www_serv catch all surviving rules for logging purpose if [ $log_on = "yes" ] $iptables -A FORWARD -i $www_if -o $int_if1 \ -m state --state NEW,INVALID \ -j LOG --log-prex "forw-drop " if [ $int_if2 ] $iptables -A FORWARD -i $www_if -o $int_if2 \ -m state --state NEW,INVALID \ -j LOG --log-prex "forw-drop " $iptables -A FORWARD -i $www_if -o $int_if1 \ -m state --state NEW,INVALID -j DROP if [ $int_if2 ] $iptables -A FORWARD -i $www_if -o $int_if2 \ -m state --state NEW,INVALID -j DROP if [ $log_on = "yes" ] $iptables -A FORWARD -j LOG --log-prex "end-forw " if [ $forwarding = "yes" ] else echo 0 > /proc/sys/net/ipv4/ip_forward echo 0 > /proc/sys/net/ipv4/ip_dynaddr echo -e "$rc_" ;; STOP stop) echo -n "shutting down rewall rules. " Turning off IP Forwarding 89_MyFirewall.sdw - 19
20 echo 0 > /proc/sys/net/ipv4/ip_forward Set default policies & clear all rules $iptables -P INPUT ACCEPT $iptables -P OUTPUT ACCEPT $iptables -P FORWARD DROP $iptables -t nat -P PREROUTING ACCEPT $iptables -t nat -P POSTROUTING ACCEPT $iptables -t nat -P OUTPUT ACCEPT flushing all rules of all policies $iptables -F $iptables -t nat -F Delete customized chains $iptables -X echo -e "$rc_" ;; restart) $0 stop && $0 start $2 $3 echo -e " $rc_failed" ;; status) $iptables -nvl echo " " echo "--- *** NAT-TABLE *** " echo " " $iptables -t nat -nvl ;; *) echo -n "Usage: $0 {start stop restart status}" echo -e "$rc_failed" exit 1 esac exit 0 89_MyFirewall.sdw - 20
Linux-Kurs, Samba-Server - Copyright 5. November 2002, Pierre Burri -Michel Bisson
 MyFirewall-(2 Interfaces)!/bin/bash Copyright (c) 2002 Pierre Burri MyFirewall is free for personal use only. Use this rewall at your own risks, I am NOT responsable if someone is able to break through
MyFirewall-(2 Interfaces)!/bin/bash Copyright (c) 2002 Pierre Burri MyFirewall is free for personal use only. Use this rewall at your own risks, I am NOT responsable if someone is able to break through
IP Packet. Deny-everything-by-default-policy
 IP Packet Deny-everything-by-default-policy IP Packet Accept-everything-by-default-policy iptables syntax iptables -I INPUT -i eth0 -p tcp -s 192.168.56.1 --sport 1024:65535 -d 192.168.56.2 --dport 22
IP Packet Deny-everything-by-default-policy IP Packet Accept-everything-by-default-policy iptables syntax iptables -I INPUT -i eth0 -p tcp -s 192.168.56.1 --sport 1024:65535 -d 192.168.56.2 --dport 22
Written by Muhammad Kamran Azeem Wednesday, 02 July :48 - Last Updated Saturday, 25 December :45
 Assalam-u-alaikum, I have been receiving many mails for few years now to provide with a firewall script. Lately I received one such mail and I decided to publish, what I replied him with. The names and
Assalam-u-alaikum, I have been receiving many mails for few years now to provide with a firewall script. Lately I received one such mail and I decided to publish, what I replied him with. The names and
Web Server ( ): FTP, SSH, HTTP, HTTPS, SMTP, POP3, IMAP, POP3S, IMAPS, MySQL (for some local services[qmail/vpopmail])
![Web Server ( ): FTP, SSH, HTTP, HTTPS, SMTP, POP3, IMAP, POP3S, IMAPS, MySQL (for some local services[qmail/vpopmail]) Web Server ( ): FTP, SSH, HTTP, HTTPS, SMTP, POP3, IMAP, POP3S, IMAPS, MySQL (for some local services[qmail/vpopmail])](/thumbs/72/66962801.jpg) The following firewall scripts will help you secure your web and db servers placed on the internet. The scenario is such that the MySQL db server is desired to receive db connections / traffic only from
The following firewall scripts will help you secure your web and db servers placed on the internet. The scenario is such that the MySQL db server is desired to receive db connections / traffic only from
Certification. Securing Networks
 Certification Securing Networks UNIT 9 Securing Networks 1 Objectives Explain packet filtering architecture Explain primary filtering command syntax Explain Network Address Translation Provide examples
Certification Securing Networks UNIT 9 Securing Networks 1 Objectives Explain packet filtering architecture Explain primary filtering command syntax Explain Network Address Translation Provide examples
Introduction to Firewalls using IPTables
 Introduction to Firewalls using IPTables The goal of this lab is to implement a firewall solution using IPTables, and to write and to customize new rules to achieve security. You will need to turn in your
Introduction to Firewalls using IPTables The goal of this lab is to implement a firewall solution using IPTables, and to write and to customize new rules to achieve security. You will need to turn in your
This material is based on work supported by the National Science Foundation under Grant No
 Source: http://en.wikipedia.org/wiki/file:firewall.png This material is based on work supported by the National Science Foundation under Grant No. 0802551 Any opinions, findings, and conclusions or recommendations
Source: http://en.wikipedia.org/wiki/file:firewall.png This material is based on work supported by the National Science Foundation under Grant No. 0802551 Any opinions, findings, and conclusions or recommendations
ECE 435 Network Engineering Lecture 23
 ECE 435 Network Engineering Lecture 23 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 30 November 2017 HW#11 will be posted Announcements Don t forget projects next week Presentation
ECE 435 Network Engineering Lecture 23 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 30 November 2017 HW#11 will be posted Announcements Don t forget projects next week Presentation
Layer 4: UDP, TCP, and others. based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers
 Layer 4: UDP, TCP, and others based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers Concepts application set transport set High-level, "Application Set" protocols deal only with how handled
Layer 4: UDP, TCP, and others based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers Concepts application set transport set High-level, "Application Set" protocols deal only with how handled
Firewalls, VPNs, and SSL Tunnels
 Chapter 20 Firewalls, VPNs, and SSL Tunnels IN THIS CHAPTER Using a packet-filtering firewall Using Squid as a firewall Using FreeS/Wan A FIREWALL IS A device that implements your security policy by shielding
Chapter 20 Firewalls, VPNs, and SSL Tunnels IN THIS CHAPTER Using a packet-filtering firewall Using Squid as a firewall Using FreeS/Wan A FIREWALL IS A device that implements your security policy by shielding
ECE 435 Network Engineering Lecture 23
 ECE 435 Network Engineering Lecture 23 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 4 December 2018 Announcements HW#9 graded Don t forget projects next week Presentation schedule
ECE 435 Network Engineering Lecture 23 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 4 December 2018 Announcements HW#9 graded Don t forget projects next week Presentation schedule
THE INTERNET PROTOCOL INTERFACES
 THE INTERNET PROTOCOL The Internet Protocol Stefan D. Bruda Winter 2018 A (connectionless) network protocol Designed for use in interconnected systems of packet-switched computer communication networks
THE INTERNET PROTOCOL The Internet Protocol Stefan D. Bruda Winter 2018 A (connectionless) network protocol Designed for use in interconnected systems of packet-switched computer communication networks
The Internet Protocol
 The Internet Protocol Stefan D. Bruda Winter 2018 THE INTERNET PROTOCOL A (connectionless) network layer protocol Designed for use in interconnected systems of packet-switched computer communication networks
The Internet Protocol Stefan D. Bruda Winter 2018 THE INTERNET PROTOCOL A (connectionless) network layer protocol Designed for use in interconnected systems of packet-switched computer communication networks
Masquerading Made Simple HOWTO
 Masquerading Made Simple HOWTO John Tapsell tapselj0@cs.man.ac.uk Thomas Spellman thomas@resonance.org Matthias Grimm DeadBull@gmx.net Revision History Revision 0.05 2001 09 07 Revised by: jpt Revision
Masquerading Made Simple HOWTO John Tapsell tapselj0@cs.man.ac.uk Thomas Spellman thomas@resonance.org Matthias Grimm DeadBull@gmx.net Revision History Revision 0.05 2001 09 07 Revised by: jpt Revision
TP5 Sécurité IPTABLE. * :sunrpc, localhost :domain,* :ssh, localhost :smtp, localhost:953,*: Tous sont des protocoles TCP
 TP5 Sécurité IPTABLE Routage classique Q1) Sur la machiine FIREWALL, les services actifs sont : Netstat -a * :sunrpc, localhost :domain,* :ssh, localhost :smtp, localhost:953,*:53856. Tous sont des protocoles
TP5 Sécurité IPTABLE Routage classique Q1) Sur la machiine FIREWALL, les services actifs sont : Netstat -a * :sunrpc, localhost :domain,* :ssh, localhost :smtp, localhost:953,*:53856. Tous sont des protocoles
How to use IP Tables
 How to use IP Tables ******************************************************************* *** IPTABLES TUTORIAL I. Definitions and similarities to ipchains II. Chain types and options III. Command line
How to use IP Tables ******************************************************************* *** IPTABLES TUTORIAL I. Definitions and similarities to ipchains II. Chain types and options III. Command line
THE INTERNET PROTOCOL/1
 THE INTERNET PROTOCOL a (connectionless) network layer protocol designed for use in interconnected systems of packet-switched computer communication networks (store-and-forward paradigm) provides for transmitting
THE INTERNET PROTOCOL a (connectionless) network layer protocol designed for use in interconnected systems of packet-switched computer communication networks (store-and-forward paradigm) provides for transmitting
Definition of firewall
 Internet Firewalls Definitions: firewall, policy, router, gateway, proxy NAT: Network Address Translation Source NAT, Destination NAT, Port forwarding NAT firewall compromise via UPnP/IGD Packet filtering
Internet Firewalls Definitions: firewall, policy, router, gateway, proxy NAT: Network Address Translation Source NAT, Destination NAT, Port forwarding NAT firewall compromise via UPnP/IGD Packet filtering
History Page. Barracuda NextGen Firewall F
 The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
10 A Security Primer. Copyright 2011 by The McGraw-Hill Companies CERTIFICATION OBJECTIVES. Q&A Self Test
 10 A Security Primer CERTIFICATION OBJECTIVES 10.01 The Layers of Linux Security 10.02 Firewalls and Network Address Translation 10.03 The Extended Internet Super-Server 10.04 TCP Wrappers 10.05 Pluggable
10 A Security Primer CERTIFICATION OBJECTIVES 10.01 The Layers of Linux Security 10.02 Firewalls and Network Address Translation 10.03 The Extended Internet Super-Server 10.04 TCP Wrappers 10.05 Pluggable
CS Computer and Network Security: Firewalls
 CS 5410 - Computer and Network Security: Firewalls Professor Patrick Traynor Fall 2017 Reminders Monday: Change of Plans Recording lecture - turn in your rules. Friday: Project Abstract The hardest paragraph
CS 5410 - Computer and Network Security: Firewalls Professor Patrick Traynor Fall 2017 Reminders Monday: Change of Plans Recording lecture - turn in your rules. Friday: Project Abstract The hardest paragraph
11 aid sheets., A non-programmable calculator.
 UNIVERSITY OF TORONTO MISSISSAUGA DECEMBER 2008 FINAL EXAMINATION CSC 347H5F Introduction to Information Security Arnold Rosenbloom Duration 3 hours Aids: Two double sided 8 1 2 11 aid sheets., A non-programmable
UNIVERSITY OF TORONTO MISSISSAUGA DECEMBER 2008 FINAL EXAMINATION CSC 347H5F Introduction to Information Security Arnold Rosenbloom Duration 3 hours Aids: Two double sided 8 1 2 11 aid sheets., A non-programmable
Basic Linux Desktop Security. Konrad Rosenbaum this presentation is protected by the GNU General Public License version 2 or any newer
 Basic Linux Desktop Security Konrad Rosenbaum this presentation is protected by the GNU General Public License version 2 or any newer Think Security: 5Q 1)What is the problem? 2)What is the proposed solution?
Basic Linux Desktop Security Konrad Rosenbaum this presentation is protected by the GNU General Public License version 2 or any newer Think Security: 5Q 1)What is the problem? 2)What is the proposed solution?
Linux System Administration, level 2
 Linux System Administration, level 2 IP Tables: the Linux firewall 2004 Ken Barber Some Rights Reserved This work is licensed under the Creative Commons Attribution-NonCommercial-ShareAlike License. To
Linux System Administration, level 2 IP Tables: the Linux firewall 2004 Ken Barber Some Rights Reserved This work is licensed under the Creative Commons Attribution-NonCommercial-ShareAlike License. To
Cisco PCP-PNR Port Usage Information
 Cisco PCP-PNR Port Usage Information Page 1 of 18 20-Sep-2013 Table of Contents 1 Introduction... 3 2 Prerequisites... 3 3 Glossary... 3 3.1 CISCO PCP Local Machine... 3 3.1.1 CISCO PCP Component... 4
Cisco PCP-PNR Port Usage Information Page 1 of 18 20-Sep-2013 Table of Contents 1 Introduction... 3 2 Prerequisites... 3 3 Glossary... 3 3.1 CISCO PCP Local Machine... 3 3.1.1 CISCO PCP Component... 4
firewall { all-ping enable broadcast-ping disable ipv6-receive-redirects disable ipv6-src-route disable ip-src-route disable log-martians enable name
 firewall { all-ping enable broadcast-ping disable ipv6-receive-redirects disable ipv6-src-route disable ip-src-route disable log-martians enable name WAN_IN { default-action drop description "WAN to internal"
firewall { all-ping enable broadcast-ping disable ipv6-receive-redirects disable ipv6-src-route disable ip-src-route disable log-martians enable name WAN_IN { default-action drop description "WAN to internal"
Kernel Korner A NATural Progression
 http://0elivery.acm.org.innopac.lib.ryerson.ca/10.1145/520000/513495... Kernel Korner A NATural Progression David continues his series on the Netfilter framework with a look at NAT and how to avoid common
http://0elivery.acm.org.innopac.lib.ryerson.ca/10.1145/520000/513495... Kernel Korner A NATural Progression David continues his series on the Netfilter framework with a look at NAT and how to avoid common
Netfilter. Fedora Core 5 setting up firewall for NIS and NFS labs. June 2006
 Netfilter Fedora Core 5 setting up firewall for NIS and NFS labs June 2006 Netfilter Features Address Translation S NAT, D NAT IP Accounting and Mangling IP Packet filtering (Firewall) Stateful packet
Netfilter Fedora Core 5 setting up firewall for NIS and NFS labs June 2006 Netfilter Features Address Translation S NAT, D NAT IP Accounting and Mangling IP Packet filtering (Firewall) Stateful packet
FireHOL Manual. Firewalling with FireHOL. FireHOL Team. Release pre3 Built 28 Oct 2013
 FireHOL Manual Firewalling with FireHOL FireHOL Team Release 2.0.0-pre3 Built 28 Oct 2013 FireHOL Manual Release 2.0.0-pre3 i Copyright 2012, 2013 Phil Whineray Copyright 2004, 2013
FireHOL Manual Firewalling with FireHOL FireHOL Team Release 2.0.0-pre3 Built 28 Oct 2013 FireHOL Manual Release 2.0.0-pre3 i Copyright 2012, 2013 Phil Whineray Copyright 2004, 2013
iptables and ip6tables An introduction to LINUX firewall
 7 19-22 November, 2017 Dhaka, Bangladesh iptables and ip6tables An introduction to LINUX firewall Imtiaz Rahman SBAC Bank Ltd AGENDA iptables and ip6tables Structure Policy (DROP/ACCEPT) Syntax Hands on
7 19-22 November, 2017 Dhaka, Bangladesh iptables and ip6tables An introduction to LINUX firewall Imtiaz Rahman SBAC Bank Ltd AGENDA iptables and ip6tables Structure Policy (DROP/ACCEPT) Syntax Hands on
Distributed Systems. 27. Firewalls and Virtual Private Networks Paul Krzyzanowski. Rutgers University. Fall 2013
 Distributed Systems 27. Firewalls and Virtual Private Networks Paul Krzyzanowski Rutgers University Fall 2013 November 25, 2013 2013 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive
Distributed Systems 27. Firewalls and Virtual Private Networks Paul Krzyzanowski Rutgers University Fall 2013 November 25, 2013 2013 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive
Assignment 3 Firewalls
 LEIC/MEIC - IST Alameda LEIC/MEIC IST Taguspark Network and Computer Security 2013/2014 Assignment 3 Firewalls Goal: Configure a firewall using iptables and fwbuilder. 1 Introduction This lab assignment
LEIC/MEIC - IST Alameda LEIC/MEIC IST Taguspark Network and Computer Security 2013/2014 Assignment 3 Firewalls Goal: Configure a firewall using iptables and fwbuilder. 1 Introduction This lab assignment
Firewalls. Firewall. means of protecting a local system or network of systems from network-based security threats creates a perimeter of defense
 FIREWALLS 3 Firewalls Firewall means of protecting a local system or network of systems from network-based security threats creates a perimeter of defense administered network public Internet firewall
FIREWALLS 3 Firewalls Firewall means of protecting a local system or network of systems from network-based security threats creates a perimeter of defense administered network public Internet firewall
Firewalls. IT443 Network Security Administration Slides courtesy of Bo Sheng
 Firewalls IT443 Network Security Administration Slides courtesy of Bo Sheng 1 Internet Security Mechanisms Prevent: Firewall, IPsec, SSL Detect: Intrusion Detection Survive/ Response: Recovery, Forensics
Firewalls IT443 Network Security Administration Slides courtesy of Bo Sheng 1 Internet Security Mechanisms Prevent: Firewall, IPsec, SSL Detect: Intrusion Detection Survive/ Response: Recovery, Forensics
Fundamentals of Computer Networking AE6382
 Computer networks are an integral part of the modern computing infrastructure The local network (LAN) is usually Ethernet LAN s are inter-connected with other LAN s in a hierarchical fashion eventually
Computer networks are an integral part of the modern computing infrastructure The local network (LAN) is usually Ethernet LAN s are inter-connected with other LAN s in a hierarchical fashion eventually
ICS 351: Networking Protocols
 ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
Firewalls N E T W O R K ( A N D D ATA ) S E C U R I T Y / P E D R O B R A N D Ã O M A N U E L E D U A R D O C O R R E I A
 Firewalls N E T W O R K ( A N D D ATA ) S E C U R I T Y 2 01 6 / 2 017 P E D R O B R A N D Ã O M A N U E L E D U A R D O C O R R E I A Slides are based on slides by Dr Lawrie Brown (UNSW@ADFA) for Computer
Firewalls N E T W O R K ( A N D D ATA ) S E C U R I T Y 2 01 6 / 2 017 P E D R O B R A N D Ã O M A N U E L E D U A R D O C O R R E I A Slides are based on slides by Dr Lawrie Brown (UNSW@ADFA) for Computer
Applied Networks & Security
 Applied Networks & Security TCP/IP Networks with Critical Analysis http://condor.depaul.edu/~jkristof/it263/ John Kristoff jtk@depaul.edu IT 263 Spring 2006/2007 John Kristoff - DePaul University 1 Critical
Applied Networks & Security TCP/IP Networks with Critical Analysis http://condor.depaul.edu/~jkristof/it263/ John Kristoff jtk@depaul.edu IT 263 Spring 2006/2007 John Kristoff - DePaul University 1 Critical
 This is Google's cache of http://www.rigacci.org/wiki/lib/exe/fetch.php/doc/appunti/linux/sa/iptables/conntrack.html. It is a snapshot of the page as it appeared on 24 Oct 2012 08:53:12 GMT. The current
This is Google's cache of http://www.rigacci.org/wiki/lib/exe/fetch.php/doc/appunti/linux/sa/iptables/conntrack.html. It is a snapshot of the page as it appeared on 24 Oct 2012 08:53:12 GMT. The current
Security and network design
 Security and network design Remco Hobo January 18, 2005 Nessus scan of own system Nessus is a program which can scan a computer for vunerabilities. It uses a unix server to scan from. The client, which
Security and network design Remco Hobo January 18, 2005 Nessus scan of own system Nessus is a program which can scan a computer for vunerabilities. It uses a unix server to scan from. The client, which
Hands-On Ethical Hacking and Network Defense
 Hands-On Ethical Hacking and Network Defense Chapter 2 TCP/IP Concepts Review Last modified 1-11-17 Objectives Describe the TCP/IP protocol stack Explain the basic concepts of IP addressing Explain the
Hands-On Ethical Hacking and Network Defense Chapter 2 TCP/IP Concepts Review Last modified 1-11-17 Objectives Describe the TCP/IP protocol stack Explain the basic concepts of IP addressing Explain the
Module: Firewalls. Professor Patrick McDaniel Fall CSE543 - Introduction to Computer and Network Security
 CSE543 - Introduction to Computer and Network Security Module: Firewalls Professor Patrick McDaniel Fall 2008 1 Midterm results!"#$%&'()*'+,)*-./('-!* +" *" )" (" '" &" %" $" #"!" #!!,*!"-./0" )+,)("-.,0"
CSE543 - Introduction to Computer and Network Security Module: Firewalls Professor Patrick McDaniel Fall 2008 1 Midterm results!"#$%&'()*'+,)*-./('-!* +" *" )" (" '" &" %" $" #"!" #!!,*!"-./0" )+,)("-.,0"
Stateless Firewall Implementation
 Stateless Firewall Implementation Network Security Lab, 2016 Group 16 B.Gamaliel K.Noellar O.Vincent H.Tewelde Outline : I. Enviroment Setup II. Today s Task III. Conclusion 2 Lab Objectives : After this
Stateless Firewall Implementation Network Security Lab, 2016 Group 16 B.Gamaliel K.Noellar O.Vincent H.Tewelde Outline : I. Enviroment Setup II. Today s Task III. Conclusion 2 Lab Objectives : After this
DFL-700 FAQ ? 6) The service I need to use is not listed in the group of pre-defined services. How do I create a custom
 DFL-700 FAQ Table of Contents Page 1) How do I do a factory reset 2 2) How do you backup the DFL-700 s configuration? 2 3) How do I block URLs using the Content Filtering function? 3 4) How do I limit
DFL-700 FAQ Table of Contents Page 1) How do I do a factory reset 2 2) How do you backup the DFL-700 s configuration? 2 3) How do I block URLs using the Content Filtering function? 3 4) How do I limit
The Administration Tab - Diagnostics
 The Administration Tab - Diagnostics The diagnostic tests (Ping and Traceroute) allow you to check the connections of your network components. Ping Test. The Ping test will check the status of a connection.
The Administration Tab - Diagnostics The diagnostic tests (Ping and Traceroute) allow you to check the connections of your network components. Ping Test. The Ping test will check the status of a connection.
TCP/IP Filtering. Main TCP/IP Filtering Dialog Box. Route Filters Button. Packet Filters Button CHAPTER
 CHAPTER 11 Main Dialog Box To access this dialog box (Figure 11-1), select Global/Filtering/ from the Device View. Figure 11-1 Main Configuration Dialog Box Route Filters Button This button brings up a
CHAPTER 11 Main Dialog Box To access this dialog box (Figure 11-1), select Global/Filtering/ from the Device View. Figure 11-1 Main Configuration Dialog Box Route Filters Button This button brings up a
FireHOL + FireQOS Reference
 FireHOL + FireQOS Reference FireHOL Team Release 2.0.0-pre7 Built 13 Apr 2014 FireHOL + FireQOS Reference Release 2.0.0-pre7 i Copyright 2012-2014 Phil Whineray Copyright 2004, 2013-2014
FireHOL + FireQOS Reference FireHOL Team Release 2.0.0-pre7 Built 13 Apr 2014 FireHOL + FireQOS Reference Release 2.0.0-pre7 i Copyright 2012-2014 Phil Whineray Copyright 2004, 2013-2014
Università Ca Foscari Venezia
 Firewalls Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Networks are complex (image from https://netcube.ru) 2 Example: traversal control Three subnetworks:
Firewalls Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Networks are complex (image from https://netcube.ru) 2 Example: traversal control Three subnetworks:
SE 4C03 Winter Final Examination Answer Key. Instructor: William M. Farmer
 SE 4C03 Winter 2003 Final Examination Answer Key Instructor: William M. Farmer (1) [2 pts.] Both the source and destination IP addresses are used to route IP datagrams. Is this statement true or false?
SE 4C03 Winter 2003 Final Examination Answer Key Instructor: William M. Farmer (1) [2 pts.] Both the source and destination IP addresses are used to route IP datagrams. Is this statement true or false?
Global Information Assurance Certification Paper
 Global Information Assurance Certification Paper Copyright SANS Institute Author Retains Full Rights This paper is taken from the GIAC directory of certified professionals. Reposting is not permited without
Global Information Assurance Certification Paper Copyright SANS Institute Author Retains Full Rights This paper is taken from the GIAC directory of certified professionals. Reposting is not permited without
ICS 451: Today's plan
 ICS 451: Today's plan ICMP ping traceroute ARP DHCP summary of IP processing ICMP Internet Control Message Protocol, 2 functions: error reporting (never sent in response to ICMP error packets) network
ICS 451: Today's plan ICMP ping traceroute ARP DHCP summary of IP processing ICMP Internet Control Message Protocol, 2 functions: error reporting (never sent in response to ICMP error packets) network
Linux. Sirindhorn International Institute of Technology Thammasat University. Linux. Firewalls with iptables. Concepts. Examples
 Linux Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 14 October 2013 Common/Reports/-introduction.tex, r715 1/14 Contents 2/14 Linux, netfilter and netfilter:
Linux Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 14 October 2013 Common/Reports/-introduction.tex, r715 1/14 Contents 2/14 Linux, netfilter and netfilter:
Advanced option settings on the command line. Set the interface and ports for the OpenVPN daemons
 Advanced option settings on the command line docs.openvpn.net/command-line/advanced-option-settings-on-the-command-line Set the interface and ports for the OpenVPN daemons In the Admin UI under Server
Advanced option settings on the command line docs.openvpn.net/command-line/advanced-option-settings-on-the-command-line Set the interface and ports for the OpenVPN daemons In the Admin UI under Server
Lecture 18: Packet Filtering Firewalls (Linux) Lecture Notes on Computer and Network Security. by Avi Kak
 Lecture 18: Packet Filtering Firewalls (Linux) Lecture Notes on Computer and Network Security by Avi Kak (kak@purdue.edu) March 20, 2017 11:49pm c 2017 Avinash Kak, Purdue University Goals: Packet-filtering
Lecture 18: Packet Filtering Firewalls (Linux) Lecture Notes on Computer and Network Security by Avi Kak (kak@purdue.edu) March 20, 2017 11:49pm c 2017 Avinash Kak, Purdue University Goals: Packet-filtering
Debian/GNU Linux Networking
 Debian/GNU Linux Networking Basics of the Networking Károly Erdei October 15, 2014 Károly Erdei Debian/GNU Linux Networking 1/41 Agenda 1 Networks 2 Ethernet 3 Internet Protocol 4 TCP 5 DHCP 6 Check Network
Debian/GNU Linux Networking Basics of the Networking Károly Erdei October 15, 2014 Károly Erdei Debian/GNU Linux Networking 1/41 Agenda 1 Networks 2 Ethernet 3 Internet Protocol 4 TCP 5 DHCP 6 Check Network
Network Security. Routing and Firewalls. Radboud University, The Netherlands. Spring 2018
 Network Security Routing and Firewalls Radboud University, The Netherlands Spring 2018 The coming weeks... Monday, May 21: Whit Monday, no lecture Monday, May 28: Security in Times of Surveillance https://www.win.tue.nl/eipsi/surveillance.html
Network Security Routing and Firewalls Radboud University, The Netherlands Spring 2018 The coming weeks... Monday, May 21: Whit Monday, no lecture Monday, May 28: Security in Times of Surveillance https://www.win.tue.nl/eipsi/surveillance.html
Packet Filtering and NAT
 Packet Filtering and NAT Alessandro Barenghi Dipartimento di Elettronica e Informazione Politecnico di Milano barenghi - at - elet.polimi.it May 14, 2014 Lesson contents Overview Netfilter/Iptables Structure
Packet Filtering and NAT Alessandro Barenghi Dipartimento di Elettronica e Informazione Politecnico di Milano barenghi - at - elet.polimi.it May 14, 2014 Lesson contents Overview Netfilter/Iptables Structure
Contents. Preventing Brute Force Attacks. The First Method: Basic Protection. Introduction. Prerequisites
 Contents 1 Preventing Brute Force Attacks 1.1 Introduction 1.2 Prerequisites 2 The First Method: Basic Protection 2.1 Implementing Basic Protection for SSH (outdated) 2.2 Protecting Telnet in Addition
Contents 1 Preventing Brute Force Attacks 1.1 Introduction 1.2 Prerequisites 2 The First Method: Basic Protection 2.1 Implementing Basic Protection for SSH (outdated) 2.2 Protecting Telnet in Addition
Network Configuration
 Network Configuration In order to access a network (whether a local area network or an Internet Service Provider), you need To have a network interface device for instance, an Ethernet card that physically
Network Configuration In order to access a network (whether a local area network or an Internet Service Provider), you need To have a network interface device for instance, an Ethernet card that physically
TCP /IP Fundamentals Mr. Cantu
 TCP /IP Fundamentals Mr. Cantu OSI Model and TCP/IP Model Comparison TCP / IP Protocols (Application Layer) The TCP/IP subprotocols listed in this layer are services that support a number of network functions:
TCP /IP Fundamentals Mr. Cantu OSI Model and TCP/IP Model Comparison TCP / IP Protocols (Application Layer) The TCP/IP subprotocols listed in this layer are services that support a number of network functions:
Network security Exercise 9 How to build a wall of fire Linux Netfilter
 Network security Exercise 9 How to build a wall of fire Linux Netfilter Tobias Limmer Computer Networks and Communication Systems Dept. of Computer Sciences, University of Erlangen-Nuremberg, Germany 2.2.
Network security Exercise 9 How to build a wall of fire Linux Netfilter Tobias Limmer Computer Networks and Communication Systems Dept. of Computer Sciences, University of Erlangen-Nuremberg, Germany 2.2.
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Linux 2.4 stateful firewall design
 Linux 2.4 stateful firewall design Presented by developerworks, your source for great tutorials Table of Contents If you're viewing this document online, you can click any of the topics below to link directly
Linux 2.4 stateful firewall design Presented by developerworks, your source for great tutorials Table of Contents If you're viewing this document online, you can click any of the topics below to link directly
NETWORK CONFIGURATION AND SERVICES. route add default gw /etc/init.d/apache restart
 NETWORK CONFIGURATION AND SERVICES route add default gw 192.168.0.1 /etc/init.d/apache restart NETWORK CONFIGURATION There are two main approaches to configuring a machine for network access: Static configuration
NETWORK CONFIGURATION AND SERVICES route add default gw 192.168.0.1 /etc/init.d/apache restart NETWORK CONFIGURATION There are two main approaches to configuring a machine for network access: Static configuration
Network Protocol Configuration Commands
 Network Protocol Configuration Commands Table of Contents Table of Contents Chapter 1 IP Addressing Configuration Commands...1 1.1 IP Addressing Configuration Commands...1 1.1.1 arp...1 1.1.2 arp timeout...2
Network Protocol Configuration Commands Table of Contents Table of Contents Chapter 1 IP Addressing Configuration Commands...1 1.1 IP Addressing Configuration Commands...1 1.1.1 arp...1 1.1.2 arp timeout...2
Outline. SC/CSE 3213 Winter Sebastian Magierowski York University. ICMP ARP DHCP NAT (not a control protocol) L9: Control Protocols
 SC/CSE 3213 Winter 2013 L9: Control Protocols Sebastian Magierowski York University 1 Outline ICMP ARP DHCP NAT (not a control protocol) 2 1 Control Protocols IP is used to transfer data Network layer
SC/CSE 3213 Winter 2013 L9: Control Protocols Sebastian Magierowski York University 1 Outline ICMP ARP DHCP NAT (not a control protocol) 2 1 Control Protocols IP is used to transfer data Network layer
Implementing Firewall Technologies
 Implementing Firewall Technologies Network firewalls separate protected from non-protected areas preventing unauthorized users from accessing protected network resources. Technologies used: ACLs Standard,
Implementing Firewall Technologies Network firewalls separate protected from non-protected areas preventing unauthorized users from accessing protected network resources. Technologies used: ACLs Standard,
IPv6 NAT. Open Source Days 9th-10th March 2013 Copenhagen, Denmark. Patrick McHardy
 IPv6 NAT Open Source Days 9th-10th March 2013 Copenhagen, Denmark Patrick McHardy Netfilter and IPv6 NAT historically http://lists.netfilter.org/pipermail/netfilter/2005-march/059463.html
IPv6 NAT Open Source Days 9th-10th March 2013 Copenhagen, Denmark Patrick McHardy Netfilter and IPv6 NAT historically http://lists.netfilter.org/pipermail/netfilter/2005-march/059463.html
Command Manual Network Protocol. Table of Contents
 Table of Contents Table of Contents Chapter 1 IP Address Configuration Commands... 1-1 1.1 IP Address Configuration Commands... 1-1 1.1.1 display ip host... 1-1 1.1.2 display ip interface... 1-1 1.1.3
Table of Contents Table of Contents Chapter 1 IP Address Configuration Commands... 1-1 1.1 IP Address Configuration Commands... 1-1 1.1.1 display ip host... 1-1 1.1.2 display ip interface... 1-1 1.1.3
Some of the slides borrowed from the book Computer Security: A Hands on Approach by Wenliang Du. Firewalls. Chester Rebeiro IIT Madras
 Some of the slides borrowed from the book Computer Security: A Hands on Approach by Wenliang Du Firewalls Chester Rebeiro IIT Madras Firewall Block unauthorized traffic flowing from one network to another
Some of the slides borrowed from the book Computer Security: A Hands on Approach by Wenliang Du Firewalls Chester Rebeiro IIT Madras Firewall Block unauthorized traffic flowing from one network to another
Computer Security Spring Firewalls. Aggelos Kiayias University of Connecticut
 Computer Security Spring 2008 Firewalls Aggelos Kiayias University of Connecticut Idea: Monitor inbound/ outbound traffic at a communication point Firewall firewall Internet LAN A firewall can run on any
Computer Security Spring 2008 Firewalls Aggelos Kiayias University of Connecticut Idea: Monitor inbound/ outbound traffic at a communication point Firewall firewall Internet LAN A firewall can run on any
CHAPTER 7 ADVANCED ADMINISTRATION PC
 ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
HP High-End Firewalls
 HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2650 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2650 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
Why Build My Own Router?
 Why Build My Own Router? With most ISPs, you only get a single uplink jack, but you probably have more than just the one computer. Most people solve this by purchasing a all-in-one router from one of the
Why Build My Own Router? With most ISPs, you only get a single uplink jack, but you probably have more than just the one computer. Most people solve this by purchasing a all-in-one router from one of the
Packet Header Formats
 A P P E N D I X C Packet Header Formats S nort rules use the protocol type field to distinguish among different protocols. Different header parts in packets are used to determine the type of protocol used
A P P E N D I X C Packet Header Formats S nort rules use the protocol type field to distinguish among different protocols. Different header parts in packets are used to determine the type of protocol used
Network Security: Firewalls. Tuomas Aura T Network security Aalto University, Nov-Dec 2013
 Network Security: Firewalls Tuomas Aura T-110.5241 Network security Aalto University, Nov-Dec 2013 2 Firewalls: Stateless packet filter Firewall Perimeter defence: Divide the world into the good/safe inside
Network Security: Firewalls Tuomas Aura T-110.5241 Network security Aalto University, Nov-Dec 2013 2 Firewalls: Stateless packet filter Firewall Perimeter defence: Divide the world into the good/safe inside
SLE in Virtual Private Networks
 EN-4000 Reference Manual Document 9 SLE in Virtual Private Networks T his document discusses implementation of Encore Networks Selective Layer Encryption (SLE, patented), a proprietary method of enhancing
EN-4000 Reference Manual Document 9 SLE in Virtual Private Networks T his document discusses implementation of Encore Networks Selective Layer Encryption (SLE, patented), a proprietary method of enhancing
20-CS Cyber Defense Overview Fall, Network Basics
 20-CS-5155 6055 Cyber Defense Overview Fall, 2017 Network Basics Who Are The Attackers? Hackers: do it for fun or to alert a sysadmin Criminals: do it for monetary gain Malicious insiders: ignores perimeter
20-CS-5155 6055 Cyber Defense Overview Fall, 2017 Network Basics Who Are The Attackers? Hackers: do it for fun or to alert a sysadmin Criminals: do it for monetary gain Malicious insiders: ignores perimeter
LevelOne FBR User s Manual. 1W, 4L 10/100 Mbps ADSL Router. Ver
 LevelOne FBR-1416 1W, 4L 10/100 Mbps ADSL Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 FBR-1416 Features... 1 Package Contents... 3 Physical Details... 3 CHAPTER 2
LevelOne FBR-1416 1W, 4L 10/100 Mbps ADSL Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 FBR-1416 Features... 1 Package Contents... 3 Physical Details... 3 CHAPTER 2
Firewalls. Content. Location of firewalls Design of firewalls. Definitions. Forwarding. Gateways, routers, firewalls.
 Firewalls INFO 404 - Lecture 10 31/03/2009 nfoukia@infoscience.otago.ac.nz Credit: Cameron Kerr : ckerr@cs.otago.ac.nz Definitions Content Gateways, routers, firewalls Location of firewalls Design of firewalls
Firewalls INFO 404 - Lecture 10 31/03/2009 nfoukia@infoscience.otago.ac.nz Credit: Cameron Kerr : ckerr@cs.otago.ac.nz Definitions Content Gateways, routers, firewalls Location of firewalls Design of firewalls
Dual-stack Firewalling with husk
 Dual-stack Firewalling with husk Phil Smith linux.conf.au Perth 2014 1 Phil Smith SysAdmin from Melbourne Personal Care Manufacturer Implemented complete Dual-stack Previous role in managed security 4WD'ing
Dual-stack Firewalling with husk Phil Smith linux.conf.au Perth 2014 1 Phil Smith SysAdmin from Melbourne Personal Care Manufacturer Implemented complete Dual-stack Previous role in managed security 4WD'ing
A Technique for improving the scheduling of network communicating processes in MOSIX
 A Technique for improving the scheduling of network communicating processes in MOSIX Rengakrishnan Subramanian Masters Report, Final Defense Guidance by Prof. Dan Andresen Agenda MOSIX Network communicating
A Technique for improving the scheduling of network communicating processes in MOSIX Rengakrishnan Subramanian Masters Report, Final Defense Guidance by Prof. Dan Andresen Agenda MOSIX Network communicating
Table of Contents. Cisco Blocking Peer to Peer File Sharing Programs with the PIX Firewall
 Table of Contents Blocking Peer to Peer File Sharing Programs with the PIX Firewall...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...2 PIX Configuration...2 Blubster/Piolet
Table of Contents Blocking Peer to Peer File Sharing Programs with the PIX Firewall...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...2 PIX Configuration...2 Blubster/Piolet
Distributed Systems. 29. Firewalls. Paul Krzyzanowski. Rutgers University. Fall 2015
 Distributed Systems 29. Firewalls Paul Krzyzanowski Rutgers University Fall 2015 2013-2015 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive data & systems not accessible Integrity:
Distributed Systems 29. Firewalls Paul Krzyzanowski Rutgers University Fall 2015 2013-2015 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive data & systems not accessible Integrity:
Firewall. Laboratory for the class Computer system security (02KRQ) Politecnico di Torino AA 2018/19 Prof. Antonio Lioy
 Firewall Laboratory for the class Computer system security (02KRQ) Politecnico di Torino AA 2018/19 Prof. Antonio Lioy prepared by: Cataldo Basile (cataldo.basile@polito.it) v. 3.1 (06/12/2018) Purpose
Firewall Laboratory for the class Computer system security (02KRQ) Politecnico di Torino AA 2018/19 Prof. Antonio Lioy prepared by: Cataldo Basile (cataldo.basile@polito.it) v. 3.1 (06/12/2018) Purpose
Firewalls. Firewall types. Packet filter. Proxy server. linux, iptables-based Windows XP s built-in router device built-ins single TCP conversation
 Firewalls Firewall types Packet filter linux, iptables-based Windows XP s built-in router device built-ins single TCP conversation Proxy server specialized server program on internal machine client talks
Firewalls Firewall types Packet filter linux, iptables-based Windows XP s built-in router device built-ins single TCP conversation Proxy server specialized server program on internal machine client talks
Guide to Networking Essentials, 6 th Edition. Chapter 5: Network Protocols
 Guide to Networking Essentials, 6 th Edition Chapter 5: Network Protocols Objectives Describe the purpose of a network protocol, the layers in the TCP/IP architecture, and the protocols in each TCP/IP
Guide to Networking Essentials, 6 th Edition Chapter 5: Network Protocols Objectives Describe the purpose of a network protocol, the layers in the TCP/IP architecture, and the protocols in each TCP/IP
Inexpensive Firewalls
 Inexpensive Firewalls Simon Cooper Lisa 1999 11 November 1999 http://reality.sgi.com/sc/papers/lisa-1999.pdf - or - http://www.sfik.com/papers/lisa-1999.pdf 1 of 37 A Firewall? 2 of 37 What
Inexpensive Firewalls Simon Cooper Lisa 1999 11 November 1999 http://reality.sgi.com/sc/papers/lisa-1999.pdf - or - http://www.sfik.com/papers/lisa-1999.pdf 1 of 37 A Firewall? 2 of 37 What
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Configuring the EN-2000 s VPN Firewall
 EN-2000 Reference Manual Document 10 Configuring the EN-2000 s VPN Firewall T his document discusses implementation of firewall rules to support IPsec VPN transmissions in the EN-2000. It presents procedures
EN-2000 Reference Manual Document 10 Configuring the EN-2000 s VPN Firewall T his document discusses implementation of firewall rules to support IPsec VPN transmissions in the EN-2000. It presents procedures
IP - The Internet Protocol. Based on the slides of Dr. Jorg Liebeherr, University of Virginia
 IP - The Internet Protocol Based on the slides of Dr. Jorg Liebeherr, University of Virginia Orientation IP (Internet Protocol) is a Network Layer Protocol. IP: The waist of the hourglass IP is the waist
IP - The Internet Protocol Based on the slides of Dr. Jorg Liebeherr, University of Virginia Orientation IP (Internet Protocol) is a Network Layer Protocol. IP: The waist of the hourglass IP is the waist
Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning
 Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning Last revised 10-4-17 KonBoot Get into any account without the password Works on Windows and Linux No longer free Link Ch 5r From the
Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning Last revised 10-4-17 KonBoot Get into any account without the password Works on Windows and Linux No longer free Link Ch 5r From the
Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning
 Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning Last revised 1-11-17 KonBoot Get into any account without the password Works on Windows and Linux No longer free Link Ch 5r From the
Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning Last revised 1-11-17 KonBoot Get into any account without the password Works on Windows and Linux No longer free Link Ch 5r From the
Internet Layers. Physical Layer. Application. Application. Transport. Transport. Network. Network. Network. Network. Link. Link. Link.
 Internet Layers Application Application Transport Transport Network Network Network Network Link Link Link Link Ethernet Fiber Optics Physical Layer Wi-Fi ARP requests and responses IP: 192.168.1.1 MAC:
Internet Layers Application Application Transport Transport Network Network Network Network Link Link Link Link Ethernet Fiber Optics Physical Layer Wi-Fi ARP requests and responses IP: 192.168.1.1 MAC:
Dual WAN VPN Firewall VPN 3000 User s Guide. Version 1.0 Date : 1 July 2005 Please check for the latest version
 Dual WAN VPN Firewall VPN 3000 User s Guide Version 1.0 Date : 1 July 2005 Please check www.basewall.com for the latest version Basewall 2005 TABLE OF CONTENTS 1: INTRODUCTION... 4 Internet Features...
Dual WAN VPN Firewall VPN 3000 User s Guide Version 1.0 Date : 1 July 2005 Please check www.basewall.com for the latest version Basewall 2005 TABLE OF CONTENTS 1: INTRODUCTION... 4 Internet Features...
UNIVERSITY OF BOLTON SCHOOL OF CREATIVE TECHNOLOGIES COMPUTER AND NETWORK SECURITY SEMESTER TWO EXAMINATIONS 2016/2017 NETWORK SECURITY
 [CRT03] UNIVERSITY OF BOLTON SCHOOL OF CREATIVE TECHNOLOGIES COMPUTER AND NETWORK SECURITY SEMESTER TWO EXAMINATIONS 2016/2017 NETWORK SECURITY MODULE NO: CPU6004 Date: Tuesday 16 th May 2017 Time: 14:00-16:00
[CRT03] UNIVERSITY OF BOLTON SCHOOL OF CREATIVE TECHNOLOGIES COMPUTER AND NETWORK SECURITY SEMESTER TWO EXAMINATIONS 2016/2017 NETWORK SECURITY MODULE NO: CPU6004 Date: Tuesday 16 th May 2017 Time: 14:00-16:00
Communication Networks ( ) / Fall 2013 The Blavatnik School of Computer Science, Tel-Aviv University. Allon Wagner
 Communication Networks (0368-3030) / Fall 2013 The Blavatnik School of Computer Science, Tel-Aviv University Allon Wagner Kurose & Ross, Chapter 4 (5 th ed.) Many slides adapted from: J. Kurose & K. Ross
Communication Networks (0368-3030) / Fall 2013 The Blavatnik School of Computer Science, Tel-Aviv University Allon Wagner Kurose & Ross, Chapter 4 (5 th ed.) Many slides adapted from: J. Kurose & K. Ross
LKR Port Broadband Router. User's Manual. Revision C
 LKR-604 4-Port Broadband Router User's Manual Revision C 1 Contents 1 Introduction... 4 1.1 Features... 4 1.2 Package Contents... 4 1.3 Finding Your Way Around... 5 1.3.1 Front Panel... 5 1.3.2 Rear Panel
LKR-604 4-Port Broadband Router User's Manual Revision C 1 Contents 1 Introduction... 4 1.1 Features... 4 1.2 Package Contents... 4 1.3 Finding Your Way Around... 5 1.3.1 Front Panel... 5 1.3.2 Rear Panel
OmniPeek Report: 21/01/ :17:00. Start: 21/01/ :16:06, Duration: 00:00:33. Total Bytes: , Total Packets: 5274
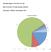 OmniPeek Report: 21/01/2015 14:17:00 Start: 21/01/2015 14:16:06, Duration: 00:00:33 Total Bytes: 1307284, Total Packets: 5274 Summary Statistics: Reported 21/01/2015 14:17:00 Name Bytes Packets Pct of
OmniPeek Report: 21/01/2015 14:17:00 Start: 21/01/2015 14:16:06, Duration: 00:00:33 Total Bytes: 1307284, Total Packets: 5274 Summary Statistics: Reported 21/01/2015 14:17:00 Name Bytes Packets Pct of
Assignment - 1 Chap. 1 Wired LAN s
 Assignment - 1 Chap. 1 Wired LAN s 1. (1 Mark) 1. Draw the frame format of Ethernet. 2. What is unicast, multicast and broadcast address? 3. State the purpose of CRC field. 2. (5 Marks) 1. Explain how
Assignment - 1 Chap. 1 Wired LAN s 1. (1 Mark) 1. Draw the frame format of Ethernet. 2. What is unicast, multicast and broadcast address? 3. State the purpose of CRC field. 2. (5 Marks) 1. Explain how
