Accurate Real-time Identification of IP Hijacking. Presented by Jacky Mak
|
|
|
- Felicity Elizabeth Martin
- 6 years ago
- Views:
Transcription
1 Accurate Real-time Identification of IP Hijacking Presented by Jacky Mak
2 Outline Problem and Objectives Interdomain Routing and BGP Basics Attack Model of IP Hijacking Real-time Detection Techniques Implementation Evaluation Conclusion and Critique
3 The Problem What is IP hijacking? Stealing IP addresses belonging to other networks to: Conduct malicious activities such as spamming and DoS attacks Disrupt the reachability of legitimate hosts in the stolen addresses Also known as BGP (Border Gateway Protocol) hijacking or fraudulent origin attacks
4 The Problem IP hijacking is not difficult! The current BGP protocol (RFC 4271) [1] implements little authentication and assumes a significant level of trust between peering ASes IP hijacking may occur if an autonomous system (AS) advertises a prefix that it is not authorized to use either on purpose or by accident
5 The Problem Public incidents: Feb 2008: Pakistan's attempt to block YouTube access within their country takes down YouTube entirely [2] Jan 2006: Con-Edison hijacks big chunk of the Internet [3] Dec 2004: TTNet in Turkey pretends to be the entire Internet [4] Apr 1997: The misbehaving AS7007 brings down the whole Internet [5]
6 The Problem Network providers could preclude customers from announcing routes for prefixes that they do not own. However: Providers do not always know which address blocks their customers own Route filtering is impossible along peering edges because the information about the peers customers are often not available As long as there is one provider that does not enforce filtering, IP hijacking can still occur
7 The Objectives We want a solution to detect IP hijacking with these properties: Timeliness detect suspicious routing updates as soon as they occur Accuracy minimize both false positives and false negatives Scalability does not require too much resources to monitor a large number of routing updates in real time Practicability can be incrementally deployed without modifying infrastructure nor requiring support from networks
8 Interdomain Routing and BGP Basics Autonomous System (AS) A set of routers that has a single routing policy, and that run under a single technical administration Viewed as a single entity from the outside world Each public AS has a unique number (ASN) assigned by IANA. See RFC 1930 ASNs were 16-bit until early 2007; 32-bit ASN is described in RFC 4893 Routing information is exchanged between ASes via an exterior gateway protocol such as BGP
9 Interdomain Routing and BGP Basics Autonomous System (AS) Stub AS an AS that is connected to only one other AS Multihomed AS an AS that is connectioned to more than one AS Transit AS an AS that provides connections through itself to separate networks. ISPs are always transit ASes. Peering voluntary interconnection of ASes for the purpose of exchanging traffic without each party paying the other
10 Interdomain Routing and BGP Basics Autonomous System (AS) Tier-1 ISPs backbones Tier-2 ISPs Tier-3 ISPs
11 Interdomain Routing and BGP Basics BGP Allows a subnet to advertise its existence to the rest of the Internet and how to get there ASes exchange routing information over TCP connections over port 179 ASes determine good routes to subnets based on the reachability information and on AS policies
12 Interdomain Routing and BGP Basics BGP Uses path vector routing instead of link-state routing (OSPF) or distance-vector routing (RIP)
13 Interdomain Routing and BGP Basics The global routing table has over 200,000 entries as of later 2006
14 Attack Model of IP Hijacking Type-1: Hijack a prefix Type-2: Hijack a prefix and its AS Type-3: Hijack a subnet of a prefix Type-4: Hijack a subnet of a prefix and its AS Type-5: Hijack along a legitimate path
15 1: Hijack a Prefix The attacker announces the ownership of IP indexes that belong to some victim ASes Multiple Origin AS (MOAS) conflicts in routing table the same prefix appears to have originated from both the original owner s AS and the hijacker s AS
16 1: Hijack a Prefix
17 1: Hijack a Prefix
18 2: Hijack a Prefix and its AS The attacker announces a route to a prefix with an AS path that traverses its own AS to reach the victim There is no MOAS conflict, but the route is still invalid The attacker can easily intercept, modify, and insert traffic
19 2: Hijack a Prefix and its AS Fake AS edge or routing policy violation
20 3: Hijack a Subnet of a Prefix Similar to type 1, except the attacker only announces a subnet of an existing prefix There is no directly observable MOAS without examining its supernet prefix submoas
21 3: Hijack a Subnet of a Prefix
22 3: Hijack a Subnet of a Prefix
23 4: Hijack a Subnet of a Prefix and its AS The attacker announces a path to reach the victim AS and a subnet of this AS s prefix Most difficult to detect because it introduces neither MOAS nor submoas
24 4: Hijack a Subnet of a Prefix and its AS
25 5: Hijack along a Legitimate Path Instead of forwarding the traffic to the expected next-hop network, the attacker intercepts traffic and originates traffic using the address block of the downstream network Merely violate the rule of forwarding traffic based on its advertised route Can be identified by traceroute easily
26 Real-time Detection Techniques Fingerprinting-based consistency checks Type 1: Detection of prefix hijacking Type 2: Detection of prefix and AS hijacking Type 3: Detection of prefix subnet hijacking Type 4: Detection of prefix subnet and AS hijacking
27 Fingerprinting-based Consistency Checks (FP Checks) When IP hijacking occurs, a given IP address in the hijacked prefix may be used by different end hosts We can check the consistency of destination hosts by verifying whether their properties match Two types of fingerprints: host-based and network based
28 Fingerprinting-based Consistency Checks (FP Checks) Host OS properties Nmap [6] Starting Nmap 4.03 ( ) at :29 HKT Insufficient responses for TCP sequencing (0), OS detection may be less accurate Interesting ports on fortress.cse.cuhk.edu.hk ( ): (The 1668 ports scanned but not shown below are in state: closed) PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2 137/tcp filtered netbios-ns 138/tcp filtered netbios-dgm 139/tcp filtered netbios-ssn 443/tcp open ssl/http Apache httpd /tcp filtered pptp Device type: general purpose Running: Sun Solaris 10 OS details: SunOS 5.10 (sparc) Nmap finished: 1 IP address (1 host up) scanned in seconds Difficulties: probe duration, load-balanced hosts, firewall,
29 Fingerprinting-based Consistency Checks (FP Checks) IP Identifier probing
30 Fingerprinting-based Consistency Checks (FP Checks) IP Identifier probing IP ID should be unique for each IP datagram with the same source-destination to facilitate IP fragment reassembly A common implementation is global IP ID, i.e., incrementing IP ID by 1 for every packet sent, regardless of the destination IP Difficulties: some systems use random IP ID or reset it to be 0; some systems set IP ID to unique across every connection or peer; not applicable if DF (Don t Fragment) flag is set
31 Fingerprinting-based Consistency Checks (FP Checks) IP Identifier probing hping [7] hping2-rc3]# hping -c 5 HPING (eth ): NO FLAGS are set, 40 headers + 0 data bytes len=46 ip= ttl=250 DF id=6153 sport=0 flags=ra seq=0 win=0 rtt=1.9 ms len=46 ip= ttl=250 DF id=6154 sport=0 flags=ra seq=1 win=0 rtt=1.7 ms len=46 ip= ttl=250 DF id=6155 sport=0 flags=ra seq=2 win=0 rtt=1.7 ms len=46 ip= ttl=250 DF id=6156 sport=0 flags=ra seq=3 win=0 rtt=2.0 ms len=46 ip= ttl=250 DF id=6157 sport=0 flags=ra seq=4 win=0 rtt=1.8 ms hping statistic packets tramitted, 5 packets received, 0% packet loss round-trip min/avg/max = 1.7/1.8/2.0 ms [root@labsupport hping2-rc3]# hping -c 5 HPING (eth ): NO FLAGS are set, 40 headers + 0 data bytes len=46 ip= ttl=252 DF id=6158 sport=0 flags=ra seq=0 win=0 rtt=20.0 ms len=46 ip= ttl=252 DF id=6159 sport=0 flags=ra seq=1 win=0 rtt= ms len=46 ip= ttl=252 DF id=6160 sport=0 flags=ra seq=2 win=0 rtt=639.0 ms len=46 ip= ttl=252 DF id=6161 sport=0 flags=ra seq=3 win=0 rtt=58.2 ms len=46 ip= ttl=252 DF id=6162 sport=0 flags=ra seq=4 win=0 rtt=673.7 ms hping statistic packets tramitted, 5 packets received, 0% packet loss round-trip min/avg/max = 20.0/573.0/ ms
32 Fingerprinting-based Consistency Checks (FP Checks) TCP timestamp probing The TCP timestamp option specified by RFC 1323 [8] used for measuring round-trip times, but it can also be used to estimate the uptime of the target host TCP timestamp is set based on the internal clock of the machine s TCP network stack which is reset upon system reboot This virtual clock runs at a certain frequency ranging from 1Hz to 10kHz Knowing the frequency and the TCP timestamp, the system uptime can be inferred
33 Fingerprinting-based Consistency Checks (FP Checks) ICMP timestamp probing The ICMP timestamp reply contains the system time of the target host reported in millisecond [9] Since many hosts are not synchronized with NTP, we can expect two different hosts likely to have noticeable differences in their clock and hence in their ICMP timestamp replies Difficulties: many hosts do not reply to ICMP timestamp requests
34 Detection of Prefix Hijacking 1. For each prefix involved in MOAS conflicts, find all paths reaching the prefix 2. Build an AS path tree, rooted at the prefix 3. Find a live host if possible in the prefix serving as the probing target 4. Select probe locations so that packets traverse different AS paths and reach conflicting origin ASes 5. Perform FP checks 6. Analyze obtained fingerprints to check for mismatches implying potential IP hijack attacks
35 Detection of Prefix Hijacking Challenge: how to select probe locations such that probe traffic goes into different origin ASes? Use the current best AS paths from publicly available BGP data to guide the selection Probe locations should be as close to the original ASes as possible Difficulties: Incomplete routing data to predict AS-level paths Limited probe locations
36 Detection of Prefix and AS Hijacking Edge popularity constraint: Suspicious if the AS edge has never been observed in other route announcements or there are few prefixes using routes traversing this edge Geographic constraint: BGP peering sessions between two ASes almost always occur between routers colocated, but a fake AS edge can connect two geographically distant networks Relationship constraint: Use inferred AS relationship to identify obvious violations of routing policies within the AS paths
37 Detection of Prefix Subnet Hijacking Customer-provider check: Providers will not intentionally hijack customer s routes due to lack of economic incentives Customers are incapable of hijacking provider s routes because traffic needs to first traverse the provider s network, and providers can easily detect such routing announcements Unlike peer to peer relationships, customer provider relationships can be viewed as transitive No AS path can traverse a customer-provider edge after a provider-customer or peer-peer edge No path can go through more than one peer-peer edge
38 Detection of Prefix Subnet Hijacking Customer-provider check (continued): Edges appearing before the tier-1 AS in the AS path are all customer-provider edges ( up edges) and edges appearing after the tier-1 AS must be all providercustomer edges ( down edges) Legitimate AS paths must be valley-free Given the prevalence of AS paths containing tier-1 ISPs, this check reduces false positives of submoas cases with very low false positives Low overhead and suitable for real-time monitoring Does not deal with conflicts involving two provider ASes who do not have a customer-provider relationship, so we need to resort to fingerprinting for the remaining cases
39 Detection of Prefix Subnet Hijacking Reflect scan: Make use of predictable IP ID increment IP packet and IGP routing within victim AS which is unaffected by polluted BGP updates Use IP spoofing to solicit traffic inside the victim AS The target host will respond differently depending on whether the submoas is caused by hijacking Difficulties: Need to identify a relatively idle host in the hijacked prefix There is no ingress filtering for spoofed packets
40 Reflect Scan when Hijacking Occurs
41 Reflect Scan without Hijacking
42 Detection of Prefix Subnet and AS Hijacking Continuously monitor new prefixes that are subnets of existing prefixes in the routing table Apply similar checks for type-2 attacks: edge popularity constraints, geographic constraints, and relationship constraints (EGR constraints) Apply reflect scan probing to deal with the remaining cases that violates the previous checks We can still achieve real-time monitoring given that the space of suspicious cases for this attack type only include new prefixes not present in the current routing tables
43 Summary of Detection Techniques
44 Implementation System Architecture: Monitor module: processes BGP updates in real time to identify potential IP hijacking Probing module: takes input from the Monitor module and selects corresponding probing techniques. It chooses the appropriate probing locations and launches probing to the target prefix Detection module: analyzes and compares the probe results to identify real hijacking incidents
45 Implementation System architecture:
46 Implementation Classification of hijack types:
47 Implementation BGP data set: University of Oregon RouteViews Server [10] peering with 57 BGP routers in 46 different ASes: Larger coverage but 2-hour lag Used to evaluate the prototype system s scalability and efficiency in processing large number of BGP updates University of Michigan s route monitor peering with 7 BGP routers in 7 distinct ASes including academic and commercial networks: Smaller coverage but real time updates Used to study timely responses to anomalous updates
48 Implementation Probe location selection: Planetlab [11] testbed is used as the probing places for both type-1 and type-2 atackes 642 machines in 179 different ASes including 3 tier-1 ISPs Able to find probing locations for 89% MOAS cases and 75% type-2 attack cases Reflect scans can be conducted anywhere as long as IP spoofing is not blocked
49 Implementation Live IP addresses for probing: Collected by combining locally collected DNS and Web server logs Used reverse DNS to look up authoritative DNS servers and mail servers of various domains Used light-weight ping sweeps for a very limited address range if unable to find a live host from the list 1,165,845 unique IP addresses collected: allowing to find 70.3% target hosts for all prefixes in MOAS conflicts, 55.2% for type-2 attacks, 71.0% for submoas conflicts, and 90.1% for type-4 attacks
50 Implementation Geographic information of prefixes: Used the NetGeo [12] database to map IP addresses and AS numbers to geographic locations NetGeo returned detailed longitude and latitude values for 98.4% of 198,146 prefixes queried
51 Evaluation System Performance Update rate: Maximum: 12 updates/second Minimum: < 1 update/second Average: 2.45 updates/second A workstation machine can easily handle such update rates for many BGP feeds
52 Evaluation System Performance Anomaly rate:
53 Evaluation System Performance Probing time: In general, probing takes less than 10 minutes Average time is less than 3 minutes for Nmap and 4 minutes for reflect scan
54 Evaluation System Performance Memory usage: The prototype system is implemented using both Perl and C and runs on a desktop computer with P4 3.2GHz CPU and 1.5GB memory For RouteViews data, it uses 66% of total memory For real-time BGP data, it uses less than 7% of total memory
55 Evaluation Feasibility of probing techniques: IP ID probing: for each OS, we can always select appropriate probing technique to ensure the IP ID reply is globally sequential TCP/ICMP timestamp probing: both ICMP and TCP timestamp are supported by all of them except Windows XP and Cisco routers. Some routers also disable ICMP timestamp replies.
56 Evaluation Feasibility of probing techniques:
57 Evaluation Effectiveness of customer-provider checking: Using a tier-1 ISP list obtained based on [13], on average 84.4% of all AS paths in RouteViews data contains at least one tier-1 AS, and this increases to than 96% for the locally collected BGP data. Therefore the proposed customer-provider heuristic is fairly effective at eliminating valid submoas conflicts, also demonstrated in Table II.
58 Evaluation Monitoring results: Obtained from over 111 hours of real-time monitoring across 8 days. The rate is averaged over all 7 feeds monitored:
59 Evaluation Suspicious MOAS conflicts:
60 Evaluation Suspicious type-2 attacks:
61 Evaluation Suspicious type-2 attacks:
62 Evaluation Suspicious submoas attacks: Prefix /24 is announced by AS15390 at 21:27 April 25th, 2006, which has a submoas conflict with prefix /16 owned by AS8517:
63 Conclusion A framework for accurate, real-time IP hijacking detection Based on the insight that a real hijacking attack will result in conflicting data-plane fingerprints describing the hijacked network Significantly reduce false positives without sacrificing efficiency Can be incrementally deployed without modifying any infrastructure nor requiring support from networks
64 Further Works and Critique FP efficiency and difficulties caused by firewalls and load balancing Limited by the availability of suitable probing locations Continuous monitoring? Performance-triggered probing? How to notify the victim?
65 References [1] RFC 4271 Border Gateway Protocol 4 (BGP-4) [2] Pakistan hijacks YouTube [3] Con-Ed Steals the 'Net [4] TTNet in Turkey hijacks the Internet [5] Murphy's Law Strikes Again: AS [6] Nmap [7] hping
66 References [8] RFC 1323 TCP Extensions for High Performance [9] RFC 792 Internet Control Message Protocol [10] University of Oregon Route Views Archive Project [11] PlanetLab [12] NetGeo The Internet Geographic Database [13] Subramanian et al. Characterizing the Internet hierarchy from multiple vantage points. In Proc. IEEE INFOCOM, 2002.
Accurate Real-time Identification of IP Hijacking
 Accurate Real-time Identification of IP Hijacking 1 Xin Hu Z. Morley Mao University of Michigan huxin@umich.edu zmao@umich.edu Abstract In this paper, we present novel and practical techniques to accurately
Accurate Real-time Identification of IP Hijacking 1 Xin Hu Z. Morley Mao University of Michigan huxin@umich.edu zmao@umich.edu Abstract In this paper, we present novel and practical techniques to accurately
Interdomain routing CSCI 466: Networks Keith Vertanen Fall 2011
 Interdomain routing CSCI 466: Networks Keith Vertanen Fall 2011 Overview Business relationships between ASes Interdomain routing using BGP Advertisements Routing policy Integration with intradomain routing
Interdomain routing CSCI 466: Networks Keith Vertanen Fall 2011 Overview Business relationships between ASes Interdomain routing using BGP Advertisements Routing policy Integration with intradomain routing
Network Forensics Prefix Hijacking Theory Prefix Hijacking Forensics Concluding Remarks. Network Forensics:
 Network Forensics: Network OS Fingerprinting Prefix Hijacking Analysis Scott Hand September 30 th, 2011 Outline 1 Network Forensics Introduction OS Fingerprinting 2 Prefix Hijacking Theory BGP Background
Network Forensics: Network OS Fingerprinting Prefix Hijacking Analysis Scott Hand September 30 th, 2011 Outline 1 Network Forensics Introduction OS Fingerprinting 2 Prefix Hijacking Theory BGP Background
Inter-domain Routing. Outline. Border Gateway Protocol
 Inter-domain Routing Outline Border Gateway Protocol Internet Structure Original idea CS 640 2 Internet Structure Today CS 640 3 Route Propagation in the Internet Autonomous System (AS) corresponds to
Inter-domain Routing Outline Border Gateway Protocol Internet Structure Original idea CS 640 2 Internet Structure Today CS 640 3 Route Propagation in the Internet Autonomous System (AS) corresponds to
Internet Control Message Protocol (ICMP)
 Internet Control Message Protocol (ICMP) 1 Overview The IP (Internet Protocol) relies on several other protocols to perform necessary control and routing functions: Control functions (ICMP) Multicast signaling
Internet Control Message Protocol (ICMP) 1 Overview The IP (Internet Protocol) relies on several other protocols to perform necessary control and routing functions: Control functions (ICMP) Multicast signaling
network security cs642 computer security adam everspaugh
 network security cs642 computer security adam everspaugh ace@cs.wisc.edu today Reminder: HW3 due in one week: April 18, 2016 CIDR addressing Border Gateway Protocol Network reconnaissance via nmap Idle
network security cs642 computer security adam everspaugh ace@cs.wisc.edu today Reminder: HW3 due in one week: April 18, 2016 CIDR addressing Border Gateway Protocol Network reconnaissance via nmap Idle
Lecture 19: Network Layer Routing in the Internet
 Lecture 19: Network Layer Routing in the Internet COMP 332, Spring 2018 Victoria Manfredi Acknowledgements: materials adapted from Computer Networking: A Top Down Approach 7 th edition: 1996-2016, J.F
Lecture 19: Network Layer Routing in the Internet COMP 332, Spring 2018 Victoria Manfredi Acknowledgements: materials adapted from Computer Networking: A Top Down Approach 7 th edition: 1996-2016, J.F
BGP Anomaly Detection. Bahaa Al-Musawi PhD candidate Supervisors: Dr. Philip Branch and Prof. Grenville Armitage.
 BGP Anomaly Detection Bahaa Al-Musawi PhD candidate Supervisors: Dr. Philip Branch and Prof. Grenville Armitage balmusawi@swin.edu.au Centre for Advanced Internet Architectures (CAIA) Swinburne University
BGP Anomaly Detection Bahaa Al-Musawi PhD candidate Supervisors: Dr. Philip Branch and Prof. Grenville Armitage balmusawi@swin.edu.au Centre for Advanced Internet Architectures (CAIA) Swinburne University
Lecture 6. Internet Security: How the Internet works and some basic vulnerabilities. Thursday 19/11/2015
 Lecture 6 Internet Security: How the Internet works and some basic vulnerabilities Thursday 19/11/2015 Agenda Internet Infrastructure: Review Basic Security Problems Security Issues in Routing Internet
Lecture 6 Internet Security: How the Internet works and some basic vulnerabilities Thursday 19/11/2015 Agenda Internet Infrastructure: Review Basic Security Problems Security Issues in Routing Internet
CS 43: Computer Networks. 24: Internet Routing November 19, 2018
 CS 43: Computer Networks 24: Internet Routing November 19, 2018 Last Class Link State + Fast convergence (reacts to events quickly) + Small window of inconsistency Distance Vector + + Distributed (small
CS 43: Computer Networks 24: Internet Routing November 19, 2018 Last Class Link State + Fast convergence (reacts to events quickly) + Small window of inconsistency Distance Vector + + Distributed (small
The Impact of Router Outages on the AS-Level Internet
 The Impact of Router Outages on the AS-Level Internet Matthew Luckie* - University of Waikato Robert Beverly - Naval Postgraduate School *work started while at CAIDA, UC San Diego SIGCOMM 2017, August
The Impact of Router Outages on the AS-Level Internet Matthew Luckie* - University of Waikato Robert Beverly - Naval Postgraduate School *work started while at CAIDA, UC San Diego SIGCOMM 2017, August
Network Security: Routing security. Aapo Kalliola T Network security Aalto University, Nov-Dec 2012
 Network Security: Routing security Aapo Kalliola T-110.5241 Network security Aalto University, Nov-Dec 2012 Outline 1. Structure of internet 2. Routing basics 3. Security issues 4. Attack 5. Solutions
Network Security: Routing security Aapo Kalliola T-110.5241 Network security Aalto University, Nov-Dec 2012 Outline 1. Structure of internet 2. Routing basics 3. Security issues 4. Attack 5. Solutions
Computer Networks ICS 651. IP Routing RIP OSPF BGP MPLS Internet Control Message Protocol IP Path MTU Discovery
 Computer Networks ICS 651 IP Routing RIP OSPF BGP MPLS Internet Control Message Protocol IP Path MTU Discovery Routing Information Protocol DV modified with split horizon and poisoned reverse distance
Computer Networks ICS 651 IP Routing RIP OSPF BGP MPLS Internet Control Message Protocol IP Path MTU Discovery Routing Information Protocol DV modified with split horizon and poisoned reverse distance
Introduction. Keith Barker, CCIE #6783. YouTube - Keith6783.
 Understanding, Implementing and troubleshooting BGP 01 Introduction http:// Instructor Introduction Keith Barker, CCIE #6783 CCIE Routing and Switching 2001 CCIE Security 2003 kbarker@ine.com YouTube -
Understanding, Implementing and troubleshooting BGP 01 Introduction http:// Instructor Introduction Keith Barker, CCIE #6783 CCIE Routing and Switching 2001 CCIE Security 2003 kbarker@ine.com YouTube -
CS 43: Computer Networks Internet Routing. Kevin Webb Swarthmore College November 16, 2017
 CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 16, 2017 1 Hierarchical routing Our routing study thus far - idealization all routers identical network flat not true in
CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 16, 2017 1 Hierarchical routing Our routing study thus far - idealization all routers identical network flat not true in
Internet Infrastructure
 Internet Infrastructure Internet Infrastructure Local and inter-domain routing TCP/IP for routing and messaging BGP for routing announcements Domain Name System Find IP address from symbolic name (www.cc.gatech.edu)
Internet Infrastructure Internet Infrastructure Local and inter-domain routing TCP/IP for routing and messaging BGP for routing announcements Domain Name System Find IP address from symbolic name (www.cc.gatech.edu)
Inter-Domain Routing: BGP
 Inter-Domain Routing: BGP Richard T. B. Ma School of Computing National University of Singapore CS 3103: Compute Networks and Protocols Inter-Domain Routing Internet is a network of networks Hierarchy
Inter-Domain Routing: BGP Richard T. B. Ma School of Computing National University of Singapore CS 3103: Compute Networks and Protocols Inter-Domain Routing Internet is a network of networks Hierarchy
CSC 4900 Computer Networks: Routing Protocols
 CSC 4900 Computer Networks: Routing Protocols Professor Henry Carter Fall 2017 Last Time Link State (LS) versus Distance Vector (DV) algorithms: What are some of the differences? What is an AS? Why do
CSC 4900 Computer Networks: Routing Protocols Professor Henry Carter Fall 2017 Last Time Link State (LS) versus Distance Vector (DV) algorithms: What are some of the differences? What is an AS? Why do
Initial motivation: 32-bit address space soon to be completely allocated. Additional motivation:
 IPv6 Initial motivation: 32-bit address space soon to be completely allocated. Additional motivation: header format helps speed processing/forwarding header changes to facilitate QoS IPv6 datagram format:
IPv6 Initial motivation: 32-bit address space soon to be completely allocated. Additional motivation: header format helps speed processing/forwarding header changes to facilitate QoS IPv6 datagram format:
Security in inter-domain routing
 DD2491 p2 2011 Security in inter-domain routing Olof Hagsand KTH CSC 1 Literature Practical BGP pages Chapter 9 See reading instructions Beware of BGP Attacks (Nordström, Dovrolis) Examples of attacks
DD2491 p2 2011 Security in inter-domain routing Olof Hagsand KTH CSC 1 Literature Practical BGP pages Chapter 9 See reading instructions Beware of BGP Attacks (Nordström, Dovrolis) Examples of attacks
Detecting routing anomalies using RIPE Atlas
 Detecting routing anomalies using RIPE Atlas Todor Yakimov Graduate School of Informatics University of Amsterdam Wednesday, February 5, 2014 Todor Yakimov (UvA) Detecting routing anomalies using RIPE
Detecting routing anomalies using RIPE Atlas Todor Yakimov Graduate School of Informatics University of Amsterdam Wednesday, February 5, 2014 Todor Yakimov (UvA) Detecting routing anomalies using RIPE
Achieving scale: Large scale active measurements from PlanetLab
 Achieving scale: Large scale active measurements from PlanetLab Marc-Olivier Buob, Jordan Augé (UPMC) 4th PhD School on Traffic Monitoring and Analysis (TMA) April 15th, 2014 London, UK OneLab FUTURE INTERNET
Achieving scale: Large scale active measurements from PlanetLab Marc-Olivier Buob, Jordan Augé (UPMC) 4th PhD School on Traffic Monitoring and Analysis (TMA) April 15th, 2014 London, UK OneLab FUTURE INTERNET
Lecture 4: Intradomain Routing. CS 598: Advanced Internetworking Matthew Caesar February 1, 2011
 Lecture 4: Intradomain Routing CS 598: Advanced Internetworking Matthew Caesar February 1, 011 1 Robert. How can routers find paths? Robert s local DNS server 10.1.8.7 A 10.1.0.0/16 10.1.0.1 Routing Table
Lecture 4: Intradomain Routing CS 598: Advanced Internetworking Matthew Caesar February 1, 011 1 Robert. How can routers find paths? Robert s local DNS server 10.1.8.7 A 10.1.0.0/16 10.1.0.1 Routing Table
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
CS 43: Computer Networks Internet Routing. Kevin Webb Swarthmore College November 14, 2013
 CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 14, 2013 1 Reading Quiz Hierarchical routing Our routing study thus far - idealization all routers identical network flat
CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 14, 2013 1 Reading Quiz Hierarchical routing Our routing study thus far - idealization all routers identical network flat
IP - The Internet Protocol. Based on the slides of Dr. Jorg Liebeherr, University of Virginia
 IP - The Internet Protocol Based on the slides of Dr. Jorg Liebeherr, University of Virginia Orientation IP (Internet Protocol) is a Network Layer Protocol. IP: The waist of the hourglass IP is the waist
IP - The Internet Protocol Based on the slides of Dr. Jorg Liebeherr, University of Virginia Orientation IP (Internet Protocol) is a Network Layer Protocol. IP: The waist of the hourglass IP is the waist
StrobeLight: Lightweight Availability Mapping and Anomaly Detection. James Mickens, John Douceur, Bill Bolosky Brian Noble
 StrobeLight: Lightweight Availability Mapping and Anomaly Detection James Mickens, John Douceur, Bill Bolosky Brian Noble At any given moment, how can we tell which enterprise machines are online and
StrobeLight: Lightweight Availability Mapping and Anomaly Detection James Mickens, John Douceur, Bill Bolosky Brian Noble At any given moment, how can we tell which enterprise machines are online and
On the State of the Inter-domain and Intra-domain Routing Security
 On the State of the Inter-domain and Intra-domain Routing Security Mingwei Zhang April 19, 2016 Mingwei Zhang Internet Routing Security 1 / 54 Section Internet Routing Security Background Internet Routing
On the State of the Inter-domain and Intra-domain Routing Security Mingwei Zhang April 19, 2016 Mingwei Zhang Internet Routing Security 1 / 54 Section Internet Routing Security Background Internet Routing
Routing Basics ISP/IXP Workshops
 Routing Basics ISP/IXP Workshops 1 Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 2 IPv4 Internet uses IPv4 addresses are 32 bits long range from 1.0.0.0 to
Routing Basics ISP/IXP Workshops 1 Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 2 IPv4 Internet uses IPv4 addresses are 32 bits long range from 1.0.0.0 to
CS 457 Networking and the Internet. The Global Internet (Then) The Global Internet (And Now) 10/4/16. Fall 2016
 CS 457 Networking and the Internet Fall 2016 The Global Internet (Then) The tree structure of the Internet in 1990 The Global Internet (And Now) A simple multi-provider Internet 1 The Global Internet Some
CS 457 Networking and the Internet Fall 2016 The Global Internet (Then) The tree structure of the Internet in 1990 The Global Internet (And Now) A simple multi-provider Internet 1 The Global Internet Some
A Measurement Study on the Impact of Routing Events on End-to-End Internet Path Performance
 A Measurement Study on the Impact of Routing Events on End-to-End Internet Path Performance Feng Wang University of Mass., Amherst fewang@ecs.umass.edu Zhuoqing Morley Mao University of Michigan zmao@eecs.umich.edu
A Measurement Study on the Impact of Routing Events on End-to-End Internet Path Performance Feng Wang University of Mass., Amherst fewang@ecs.umass.edu Zhuoqing Morley Mao University of Michigan zmao@eecs.umich.edu
Routing Concepts. IPv4 Routing Forwarding Some definitions Policy options Routing Protocols
 Routing Basics 1 Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 2 IPv4 Internet uses IPv4 Addresses are 32 bits long Range from 1.0.0.0 to 223.255.255.255 0.0.0.0
Routing Basics 1 Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 2 IPv4 Internet uses IPv4 Addresses are 32 bits long Range from 1.0.0.0 to 223.255.255.255 0.0.0.0
Measuring and Characterizing IPv6 Router Availability
 Measuring and Characterizing IPv6 Router Availability Robert Beverly, Matthew Luckie, Lorenza Mosley, kc claffy Naval Postgraduate School UCSD/CAIDA March 20, 2015 PAM 2015-16th Passive and Active Measurement
Measuring and Characterizing IPv6 Router Availability Robert Beverly, Matthew Luckie, Lorenza Mosley, kc claffy Naval Postgraduate School UCSD/CAIDA March 20, 2015 PAM 2015-16th Passive and Active Measurement
Routing Basics. Routing Concepts. IPv4. IPv4 address format. A day in a life of a router. What does a router do? IPv4 Routing
 Routing Concepts IPv4 Routing Routing Basics ISP/IXP Workshops Forwarding Some definitions Policy options Routing Protocols 1 2 IPv4 IPv4 address format Internet uses IPv4 addresses are 32 bits long range
Routing Concepts IPv4 Routing Routing Basics ISP/IXP Workshops Forwarding Some definitions Policy options Routing Protocols 1 2 IPv4 IPv4 address format Internet uses IPv4 addresses are 32 bits long range
Chapter 7 Lab 7-1, Configuring BGP with Default Routing
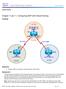 Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
Routing Basics ISP/IXP Workshops
 Routing Basics ISP/IXP Workshops 1 Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 2 IPv4 Internet uses IPv4 addresses are 32 bits long range from 1.0.0.0 to
Routing Basics ISP/IXP Workshops 1 Routing Concepts IPv4 Routing Forwarding Some definitions Policy options Routing Protocols 2 IPv4 Internet uses IPv4 addresses are 32 bits long range from 1.0.0.0 to
(ICMP), RFC
 Internet et Control o Message Protocol (ICMP), RFC 792 http://icourse.cuc.edu.cn/networkprogramming/ linwei@cuc.edu.cn Nov. 2009 Overview The IP (Internet Protocol) relies on several other protocols to
Internet et Control o Message Protocol (ICMP), RFC 792 http://icourse.cuc.edu.cn/networkprogramming/ linwei@cuc.edu.cn Nov. 2009 Overview The IP (Internet Protocol) relies on several other protocols to
CS 268: Computer Networking. Next Lecture: Interdomain Routing
 CS 268: Computer Networking L-3 BGP Next Lecture: Interdomain Routing BGP Assigned Reading MIT BGP Class Notes [Gao00] On Inferring Autonomous System Relationships in the Internet 2 Outline Need for hierarchical
CS 268: Computer Networking L-3 BGP Next Lecture: Interdomain Routing BGP Assigned Reading MIT BGP Class Notes [Gao00] On Inferring Autonomous System Relationships in the Internet 2 Outline Need for hierarchical
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
ROUTING INTRODUCTION TO IP, IP ROUTING PROTOCOLS AND PROXY ARP
 IP ROUTING INTRODUCTION TO IP, IP ROUTING PROTOCOLS AND PROXY ARP Peter R. Egli 1/37 Contents 1. IP Routing 2. Routing Protocols 3. Fragmentation in the IP Layer 4. Proxy ARP 5. Routing and IP forwarding
IP ROUTING INTRODUCTION TO IP, IP ROUTING PROTOCOLS AND PROXY ARP Peter R. Egli 1/37 Contents 1. IP Routing 2. Routing Protocols 3. Fragmentation in the IP Layer 4. Proxy ARP 5. Routing and IP forwarding
IP Addressing & Interdomain Routing. Next Topic
 IP Addressing & Interdomain Routing Next Topic IP Addressing Hierarchy (prefixes, class A, B, C, subnets) Interdomain routing Application Presentation Session Transport Network Data Link Physical Scalability
IP Addressing & Interdomain Routing Next Topic IP Addressing Hierarchy (prefixes, class A, B, C, subnets) Interdomain routing Application Presentation Session Transport Network Data Link Physical Scalability
Dongsoo S. Kim Electrical and Computer Engineering Indiana U. Purdue U. Indianapolis
 Session 8. TCP/IP Dongsoo S. Kim (dskim@iupui.edu) Electrical and Computer Engineering Indiana U. Purdue U. Indianapolis IP Packet 0 4 8 16 19 31 Version IHL Type of Service Total Length Identification
Session 8. TCP/IP Dongsoo S. Kim (dskim@iupui.edu) Electrical and Computer Engineering Indiana U. Purdue U. Indianapolis IP Packet 0 4 8 16 19 31 Version IHL Type of Service Total Length Identification
Chapter 4: outline. 4.5 routing algorithms link state distance vector hierarchical routing. 4.6 routing in the Internet RIP OSPF BGP
 Chapter 4: outline 4.1 introduction 4.2 virtual circuit and datagram networks 4.3 what s inside a router 4.4 IP: Internet Protocol datagram format IPv4 addressing ICMP 4.5 routing algorithms link state
Chapter 4: outline 4.1 introduction 4.2 virtual circuit and datagram networks 4.3 what s inside a router 4.4 IP: Internet Protocol datagram format IPv4 addressing ICMP 4.5 routing algorithms link state
Back to basics J. Addressing is the key! Application (HTTP, DNS, FTP) Application (HTTP, DNS, FTP) Transport. Transport (TCP/UDP) Internet (IPv4/IPv6)
 Routing Basics Back to basics J Application Presentation Application (HTTP, DNS, FTP) Data Application (HTTP, DNS, FTP) Session Transport Transport (TCP/UDP) E2E connectivity (app-to-app) Port numbers
Routing Basics Back to basics J Application Presentation Application (HTTP, DNS, FTP) Data Application (HTTP, DNS, FTP) Session Transport Transport (TCP/UDP) E2E connectivity (app-to-app) Port numbers
Routing and router security in an operator environment
 DD2495 p4 2011 Routing and router security in an operator environment Olof Hagsand KTH CSC 1 Router lab objectives A network operator (eg ISP) needs to secure itself, its customers and its neighbors from
DD2495 p4 2011 Routing and router security in an operator environment Olof Hagsand KTH CSC 1 Router lab objectives A network operator (eg ISP) needs to secure itself, its customers and its neighbors from
inside: THE MAGAZINE OF USENIX & SAGE April 2002 Volume 27 Number 2 SECURITY A Remote Active OS Fingerprinting Tool Using ICMP BY OFIR ARKIN
 THE MAGAZINE OF USENIX & SAGE April 2002 Volume 27 Number 2 inside: SECURITY A Remote Active OS Fingerprinting Tool Using ICMP BY OFIR ARKIN & The Advanced Computing Systems Association & The System Administrators
THE MAGAZINE OF USENIX & SAGE April 2002 Volume 27 Number 2 inside: SECURITY A Remote Active OS Fingerprinting Tool Using ICMP BY OFIR ARKIN & The Advanced Computing Systems Association & The System Administrators
PrepAwayExam. High-efficient Exam Materials are the best high pass-rate Exam Dumps
 PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 642-541 Title : VPN and Security Cisco SAFE Implementation Exam (CSI) Vendors : Cisco
PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 642-541 Title : VPN and Security Cisco SAFE Implementation Exam (CSI) Vendors : Cisco
Overview. Problem: Find lowest cost path between two nodes Factors static: topology dynamic: load
 Dynamic Routing Overview Forwarding vs Routing forwarding: to select an output port based on destination address and routing table routing: process by which routing table is built Network as a Graph C
Dynamic Routing Overview Forwarding vs Routing forwarding: to select an output port based on destination address and routing table routing: process by which routing table is built Network as a Graph C
Inter-AS routing. Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley
 Inter-AS routing Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley Some materials copyright 1996-2012 J.F Kurose and K.W. Ross, All Rights Reserved Chapter 4:
Inter-AS routing Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley Some materials copyright 1996-2012 J.F Kurose and K.W. Ross, All Rights Reserved Chapter 4:
The Interconnection Structure of. The Internet. EECC694 - Shaaban
 The Internet Evolved from the ARPANET (the Advanced Research Projects Agency Network), a project funded by The U.S. Department of Defense (DOD) in 1969. ARPANET's purpose was to provide the U.S. Defense
The Internet Evolved from the ARPANET (the Advanced Research Projects Agency Network), a project funded by The U.S. Department of Defense (DOD) in 1969. ARPANET's purpose was to provide the U.S. Defense
Auxiliary protocols. tasks that IP does not handle: Routing table management (RIP, OSPF, etc.). Congestion and error reporting (ICMP).
 Auxiliary protocols IP is helped by a number of protocols that perform specific tasks that IP does not handle: Routing table management (RIP, OSPF, etc.). Congestion and error reporting (ICMP). Multicasting
Auxiliary protocols IP is helped by a number of protocols that perform specific tasks that IP does not handle: Routing table management (RIP, OSPF, etc.). Congestion and error reporting (ICMP). Multicasting
Routing Basics. ISP Workshops. Last updated 10 th December 2015
 Routing Basics ISP Workshops Last updated 10 th December 2015 1 Routing Concepts p IPv4 & IPv6 p Routing p Forwarding p Some definitions p Policy options p Routing Protocols 2 IPv4 p Internet still uses
Routing Basics ISP Workshops Last updated 10 th December 2015 1 Routing Concepts p IPv4 & IPv6 p Routing p Forwarding p Some definitions p Policy options p Routing Protocols 2 IPv4 p Internet still uses
The Network Layer. Internet solutions. Nixu Oy PL 21. (Mäkelänkatu 91) Helsinki, Finland. tel fax.
 The Network Layer Nixu Oy PL 21 (Mäkelänkatu 91) 00601 Helsinki, Finland tel. +358 9 478 1011 fax. +358 9 478 1030 info@nixu.fi http://www.nixu.fi OVERVIEW The Internet Protocol IP addresses, address resolution
The Network Layer Nixu Oy PL 21 (Mäkelänkatu 91) 00601 Helsinki, Finland tel. +358 9 478 1011 fax. +358 9 478 1030 info@nixu.fi http://www.nixu.fi OVERVIEW The Internet Protocol IP addresses, address resolution
Chapter 2 - Part 1. The TCP/IP Protocol: The Language of the Internet
 Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
Internetwork Expert s CCNA Security Bootcamp. Common Security Threats
 Internetwork Expert s CCNA Security Bootcamp Common Security Threats http:// Today s s Network Security Challenge The goal of the network is to provide high availability and easy access to data to meet
Internetwork Expert s CCNA Security Bootcamp Common Security Threats http:// Today s s Network Security Challenge The goal of the network is to provide high availability and easy access to data to meet
COMP211 Chapter 5 Network Layer: The Control Plane
 COMP211 Chapter 5 Network Layer: The Control Plane All material copyright 1996-2016 J.F Kurose and K.W. Ross, All Rights Reserved Computer Networking: A Top Down Approach 7 th edition Jim Kurose, Keith
COMP211 Chapter 5 Network Layer: The Control Plane All material copyright 1996-2016 J.F Kurose and K.W. Ross, All Rights Reserved Computer Networking: A Top Down Approach 7 th edition Jim Kurose, Keith
Chapter 12 Network Protocols
 Chapter 12 Network Protocols 1 Outline Protocol: Set of defined rules to allow communication between entities Open Systems Interconnection (OSI) Transmission Control Protocol/Internetworking Protocol (TCP/IP)
Chapter 12 Network Protocols 1 Outline Protocol: Set of defined rules to allow communication between entities Open Systems Interconnection (OSI) Transmission Control Protocol/Internetworking Protocol (TCP/IP)
Routing. Advanced Computer Networks: Routing 1
 Routing Advanced Computer Networks: Routing 1 Gateway To internet or wide area network Metropolitan Area Network (MAN) s s Organization Servers Backbone R S R R Departmental Server s R S R s S R s s s
Routing Advanced Computer Networks: Routing 1 Gateway To internet or wide area network Metropolitan Area Network (MAN) s s Organization Servers Backbone R S R R Departmental Server s R S R s S R s s s
Computer Security. 11. Network Security. Paul Krzyzanowski. Rutgers University. Spring 2018
 Computer Security 11. Network Security Paul Krzyzanowski Rutgers University Spring 2018 April 15, 2018 CS 419 2018 Paul Krzyzanowski 1 The Internet Packet switching: store-and-forward routing across multiple
Computer Security 11. Network Security Paul Krzyzanowski Rutgers University Spring 2018 April 15, 2018 CS 419 2018 Paul Krzyzanowski 1 The Internet Packet switching: store-and-forward routing across multiple
AS-CRED: Reputation Service for Trustworthy Inter-domain Routing
 AS-CRED: Reputation Service for Trustworthy Inter-domain Routing Krishna Venkatasubramanian Computer and Information Science University of Pennsylvania ONR MURI N00014-07-1-0907 Review Meeting June 10,
AS-CRED: Reputation Service for Trustworthy Inter-domain Routing Krishna Venkatasubramanian Computer and Information Science University of Pennsylvania ONR MURI N00014-07-1-0907 Review Meeting June 10,
Border Gateway Protocol - BGP
 BGP Fundamentals Border Gateway Protocol - BGP Runs over TCP (port 179) TCP connection required before BGP session Need to be reachable! Path vector routing protocol Best path selection based on path attributes
BGP Fundamentals Border Gateway Protocol - BGP Runs over TCP (port 179) TCP connection required before BGP session Need to be reachable! Path vector routing protocol Best path selection based on path attributes
CMSC 417. Computer Networks Prof. Ashok K Agrawala Ashok Agrawala October 9, 2018 (a) October 18 October 9,
 CMSC 417 Computer Networks Prof. Ashok K Agrawala 2018 Ashok Agrawala October 9, 2018 (a) October 18 October 9, 2018 1 host Message, Segment, Packet, and Frame host HTTP HTTP message HTTP TCP TCP segment
CMSC 417 Computer Networks Prof. Ashok K Agrawala 2018 Ashok Agrawala October 9, 2018 (a) October 18 October 9, 2018 1 host Message, Segment, Packet, and Frame host HTTP HTTP message HTTP TCP TCP segment
CS 356: Computer Network Architectures. Lecture 10: IP Fragmentation, ARP, and ICMP. Xiaowei Yang
 CS 356: Computer Network Architectures Lecture 10: IP Fragmentation, ARP, and ICMP Xiaowei Yang xwy@cs.duke.edu Overview Homework 2-dimension parity IP fragmentation ARP ICMP Fragmentation and Reassembly
CS 356: Computer Network Architectures Lecture 10: IP Fragmentation, ARP, and ICMP Xiaowei Yang xwy@cs.duke.edu Overview Homework 2-dimension parity IP fragmentation ARP ICMP Fragmentation and Reassembly
Configuration and Management of Networks 2012
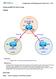 Configuring BGP with default routing Topology Objectives Background Instructions Configure BGP to exchange routing information with two ISPs. The International Travel Agency (ITA) relies extensively on
Configuring BGP with default routing Topology Objectives Background Instructions Configure BGP to exchange routing information with two ISPs. The International Travel Agency (ITA) relies extensively on
CSCD 433/533 Network Programming Fall Lecture 14 Global Address Space Autonomous Systems, BGP Protocol Routing
 CSCD 433/533 Network Programming Fall 2012 Lecture 14 Global Address Space Autonomous Systems, BGP Protocol Routing 1 Topics Interdomain Routing BGP Interdomain Routing Benefits vs. Link State Routing
CSCD 433/533 Network Programming Fall 2012 Lecture 14 Global Address Space Autonomous Systems, BGP Protocol Routing 1 Topics Interdomain Routing BGP Interdomain Routing Benefits vs. Link State Routing
Network Layer (1) Networked Systems 3 Lecture 8
 Network Layer (1) Networked Systems 3 Lecture 8 Role of the Network Layer Application Application The network layer is the first end-to-end layer in the OSI reference model Presentation Session Transport
Network Layer (1) Networked Systems 3 Lecture 8 Role of the Network Layer Application Application The network layer is the first end-to-end layer in the OSI reference model Presentation Session Transport
Configuring BGP. Cisco s BGP Implementation
 Configuring BGP This chapter describes how to configure Border Gateway Protocol (BGP). For a complete description of the BGP commands in this chapter, refer to the BGP s chapter of the Network Protocols
Configuring BGP This chapter describes how to configure Border Gateway Protocol (BGP). For a complete description of the BGP commands in this chapter, refer to the BGP s chapter of the Network Protocols
Introduction to Computer Networks
 Introduction to Computer Networks Tian Song ( 嵩天 ), Ph.D., Assoc. Prof. songtian@bit.edu.cn Introduction to Computer Networks ICMP, ARP, DHCP, OSPF, BGP Tian Song ( 嵩天 ), Ph.D., Assoc. Prof. songtian@bit.edu.cn
Introduction to Computer Networks Tian Song ( 嵩天 ), Ph.D., Assoc. Prof. songtian@bit.edu.cn Introduction to Computer Networks ICMP, ARP, DHCP, OSPF, BGP Tian Song ( 嵩天 ), Ph.D., Assoc. Prof. songtian@bit.edu.cn
COMP/ELEC 429 Introduction to Computer Networks
 COMP/ELEC 429 Introduction to Computer Networks Lecture 11: Inter-domain routing Slides used with permissions from Edward W. Knightly, T. S. Eugene Ng, Ion Stoica, Hui Zhang T. S. Eugene Ng eugeneng at
COMP/ELEC 429 Introduction to Computer Networks Lecture 11: Inter-domain routing Slides used with permissions from Edward W. Knightly, T. S. Eugene Ng, Ion Stoica, Hui Zhang T. S. Eugene Ng eugeneng at
CS4700/CS5700 Fundamentals of Computer Networks
 CS4700/CS5700 Fundamentals of Computer Networks Lecture 12: Inter-domain routing Slides used with permissions from Edward W. Knightly, T. S. Eugene Ng, Ion Stoica, Hui Zhang Alan Mislove amislove at ccs.neu.edu
CS4700/CS5700 Fundamentals of Computer Networks Lecture 12: Inter-domain routing Slides used with permissions from Edward W. Knightly, T. S. Eugene Ng, Ion Stoica, Hui Zhang Alan Mislove amislove at ccs.neu.edu
Network Protocols. Routing. TDC375 Autumn 03/04 John Kristoff - DePaul University 1
 Network Protocols Routing TDC375 Autumn 03/04 John Kristoff - DePaul University 1 IPv4 unicast routing All Internet hosts perform basic routing for local net destinations, forward to local host for non-local
Network Protocols Routing TDC375 Autumn 03/04 John Kristoff - DePaul University 1 IPv4 unicast routing All Internet hosts perform basic routing for local net destinations, forward to local host for non-local
15-441: Computer Networks Spring 2017 Homework 3
 15-441: Computer Networks Spring 2017 Homework 3 Assigned: Feb 15, 2018 Due: Mar 19, 2018 Lead TA: M.Ahmed Shah 1. Chapter 3: Exercise 41, page 294 2. Chapter 3: Exercise 43, page
15-441: Computer Networks Spring 2017 Homework 3 Assigned: Feb 15, 2018 Due: Mar 19, 2018 Lead TA: M.Ahmed Shah 1. Chapter 3: Exercise 41, page 294 2. Chapter 3: Exercise 43, page
ECE 428 Internet Protocols (Network Layer: Layer 3)
 ECE 428 Internet Protocols (Network Layer: Layer 3) 1 Done so far MAC protocols (with PHYsical layer) Transport bits from one node to another. Key element: Determine WHEN to transmit DLC protocol (running
ECE 428 Internet Protocols (Network Layer: Layer 3) 1 Done so far MAC protocols (with PHYsical layer) Transport bits from one node to another. Key element: Determine WHEN to transmit DLC protocol (running
Internet Control Message Protocol (ICMP), RFC 792. Prof. Lin Weiguo Copyleft 2009~2017, School of Computing, CUC
 Internet Control Message Protocol (ICMP), RFC 79 Prof Lin Weiguo Copyleft 009~07, School of Computing, CUC Oct 07 Overview } The IP (Internet Protocol) relies on several other protocols to perform necessary
Internet Control Message Protocol (ICMP), RFC 79 Prof Lin Weiguo Copyleft 009~07, School of Computing, CUC Oct 07 Overview } The IP (Internet Protocol) relies on several other protocols to perform necessary
Single Network: applications, client and server hosts, switches, access links, trunk links, frames, path. Review of TCP/IP Internetworking
 1 Review of TCP/IP working Single Network: applications, client and server hosts, switches, access links, trunk links, frames, path Frame Path Chapter 3 Client Host Trunk Link Server Host Panko, Corporate
1 Review of TCP/IP working Single Network: applications, client and server hosts, switches, access links, trunk links, frames, path Frame Path Chapter 3 Client Host Trunk Link Server Host Panko, Corporate
CS Paul Krzyzanowski
 The Internet Packet switching: store-and-forward routing across multiple physical networks... across multiple organizations Computer Security 11. Network Security ISP Paul Krzyzanowski Rutgers University
The Internet Packet switching: store-and-forward routing across multiple physical networks... across multiple organizations Computer Security 11. Network Security ISP Paul Krzyzanowski Rutgers University
Introduction to Information Science and Technology 2017 Networking II. Sören Schwertfeger 师泽仁
 II Sören Schwertfeger 师泽仁 Outline Review Network Layer Routing Transport Layer Applications HTTP Demos Internet: Huge network of networks Billions of hosts (computers) Internet Structure Network Edge:
II Sören Schwertfeger 师泽仁 Outline Review Network Layer Routing Transport Layer Applications HTTP Demos Internet: Huge network of networks Billions of hosts (computers) Internet Structure Network Edge:
Communication Networks ( ) / Fall 2013 The Blavatnik School of Computer Science, Tel-Aviv University. Allon Wagner
 Communication Networks (0368-3030) / Fall 2013 The Blavatnik School of Computer Science, Tel-Aviv University Allon Wagner Kurose & Ross, Chapter 4 (5 th ed.) Many slides adapted from: J. Kurose & K. Ross
Communication Networks (0368-3030) / Fall 2013 The Blavatnik School of Computer Science, Tel-Aviv University Allon Wagner Kurose & Ross, Chapter 4 (5 th ed.) Many slides adapted from: J. Kurose & K. Ross
internet technologies and standards
 Institute of Telecommunications Warsaw University of Technology 2017 internet technologies and standards Piotr Gajowniczek Andrzej Bąk Michał Jarociński Network Layer The majority of slides presented in
Institute of Telecommunications Warsaw University of Technology 2017 internet technologies and standards Piotr Gajowniczek Andrzej Bąk Michał Jarociński Network Layer The majority of slides presented in
Announcements. CS 5565 Network Architecture and Protocols. Project 2B. Project 2B. Project 2B: Under the hood. Routing Algorithms
 Announcements CS 5565 Network Architecture and Protocols Lecture 20 Godmar Back Project 2B due in 2 parts: Apr 29 and May 6 Extra Credit Opportunities: Expand simulator (and your implementation) to introduce
Announcements CS 5565 Network Architecture and Protocols Lecture 20 Godmar Back Project 2B due in 2 parts: Apr 29 and May 6 Extra Credit Opportunities: Expand simulator (and your implementation) to introduce
Examination 2D1392 Protocols and Principles of the Internet 2G1305 Internetworking 2G1507 Kommunikationssystem, fk SOLUTIONS
 Examination 2D1392 Protocols and Principles of the Internet 2G1305 Internetworking 2G1507 Kommunikationssystem, fk Date: January 17 th 2006 at 14:00 18:00 SOLUTIONS 1. General (5p) a) Draw the layered
Examination 2D1392 Protocols and Principles of the Internet 2G1305 Internetworking 2G1507 Kommunikationssystem, fk Date: January 17 th 2006 at 14:00 18:00 SOLUTIONS 1. General (5p) a) Draw the layered
Routing Security We can do better!
 Routing Security We can do better! And how MANRS can help Andrei Robachevsky robachevsky@isoc.org 1 No Day Without an Incident 120 6 month of suspicious activity 90 60 Hijack Leak 30 0 1/5/17 1/16/17 1/27/17
Routing Security We can do better! And how MANRS can help Andrei Robachevsky robachevsky@isoc.org 1 No Day Without an Incident 120 6 month of suspicious activity 90 60 Hijack Leak 30 0 1/5/17 1/16/17 1/27/17
User Datagram Protocol
 Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
Chapter 4: network layer. Network service model. Two key network-layer functions. Network layer. Input port functions. Router architecture overview
 Chapter 4: chapter goals: understand principles behind services service models forwarding versus routing how a router works generalized forwarding instantiation, implementation in the Internet 4- Network
Chapter 4: chapter goals: understand principles behind services service models forwarding versus routing how a router works generalized forwarding instantiation, implementation in the Internet 4- Network
CCNA Exploration Network Fundamentals. Chapter 06 Addressing the Network IPv4
 CCNA Exploration Network Fundamentals Chapter 06 Addressing the Network IPv4 Updated: 20/05/2008 1 6.0.1 Introduction Addressing is a key function of Network layer protocols that enables data communication
CCNA Exploration Network Fundamentals Chapter 06 Addressing the Network IPv4 Updated: 20/05/2008 1 6.0.1 Introduction Addressing is a key function of Network layer protocols that enables data communication
Module 6 Implementing BGP
 Module 6 Implementing BGP Lesson 1 Explaining BGP Concepts and Terminology BGP Border Gateway Protocol Using BGP to Connect to the Internet If only one ISP, do not need BGP. If multiple ISPs, use BGP,
Module 6 Implementing BGP Lesson 1 Explaining BGP Concepts and Terminology BGP Border Gateway Protocol Using BGP to Connect to the Internet If only one ISP, do not need BGP. If multiple ISPs, use BGP,
Connecting to a Service Provider Using External BGP
 Connecting to a Service Provider Using External BGP First Published: May 2, 2005 Last Updated: August 21, 2007 This module describes configuration tasks that will enable your Border Gateway Protocol (BGP)
Connecting to a Service Provider Using External BGP First Published: May 2, 2005 Last Updated: August 21, 2007 This module describes configuration tasks that will enable your Border Gateway Protocol (BGP)
Introduction to BGP ISP/IXP Workshops
 Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol Routing Protocol used to exchange routing information between networks exterior gateway protocol RFC1771 work in progress to update draft-ietf-idr-bgp4-18.txt
Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol Routing Protocol used to exchange routing information between networks exterior gateway protocol RFC1771 work in progress to update draft-ietf-idr-bgp4-18.txt
Configuration and Management of Networks
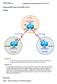 Configuring BGP using the AS_PATH attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter
Configuring BGP using the AS_PATH attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter
Lecture 5 The Network Layer part II. Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it
 Lecture 5 The Network Layer part II Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it IP datagram format IP protocol version number header length (bytes) type of data max number remaining
Lecture 5 The Network Layer part II Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it IP datagram format IP protocol version number header length (bytes) type of data max number remaining
Link State Routing & Inter-Domain Routing
 Link State Routing & Inter-Domain Routing CS640, 2015-02-26 Announcements Assignment #2 is due Tuesday Overview Link state routing Internet structure Border Gateway Protocol (BGP) Path vector routing Inter
Link State Routing & Inter-Domain Routing CS640, 2015-02-26 Announcements Assignment #2 is due Tuesday Overview Link state routing Internet structure Border Gateway Protocol (BGP) Path vector routing Inter
Shim6: Network Operator Concerns. Jason Schiller Senior Internet Network Engineer IP Core Infrastructure Engineering UUNET / MCI
 Shim6: Network Operator Concerns Jason Schiller Senior Internet Network Engineer IP Core Infrastructure Engineering UUNET / MCI Not Currently Supporting IPv6? Many parties are going forward with IPv6 Japan
Shim6: Network Operator Concerns Jason Schiller Senior Internet Network Engineer IP Core Infrastructure Engineering UUNET / MCI Not Currently Supporting IPv6? Many parties are going forward with IPv6 Japan
Introduction to BGP. ISP/IXP Workshops
 Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol A Routing Protocol used to exchange routing information between different networks Exterior gateway protocol Described in RFC4271 RFC4276
Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol A Routing Protocol used to exchange routing information between different networks Exterior gateway protocol Described in RFC4271 RFC4276
Internet Routing Basics
 Internet Routing Basics Back to basics J Application Presentation Application (HTTP, DNS, FTP) Data Application (HTTP, DNS, FTP) Session Transport Transport (TCP/UDP) E2E connectivity (app-to-app) Port
Internet Routing Basics Back to basics J Application Presentation Application (HTTP, DNS, FTP) Data Application (HTTP, DNS, FTP) Session Transport Transport (TCP/UDP) E2E connectivity (app-to-app) Port
Overview 4.2: Routing
 Overview 4.2: Routing Forwarding vs Routing forwarding: to select an output port based on destination address and routing table routing: process by which routing table is built Network as a Graph A 6 1
Overview 4.2: Routing Forwarding vs Routing forwarding: to select an output port based on destination address and routing table routing: process by which routing table is built Network as a Graph A 6 1
Network Protocols. Routing. TDC375 Winter 2002 John Kristoff - DePaul University 1
 Network Protocols Routing TDC375 Winter 2002 John Kristoff - DePaul University 1 IP routing Performed by routers Table (information base) driven Forwarding decision on a hop-by-hop basis Route determined
Network Protocols Routing TDC375 Winter 2002 John Kristoff - DePaul University 1 IP routing Performed by routers Table (information base) driven Forwarding decision on a hop-by-hop basis Route determined
CNT Computer and Network Security: BGP Security
 CNT 5410 - Computer and Network Security: BGP Security Professor Kevin Butler Fall 2015 Internet inter-as routing: BGP BGP (Border Gateway Protocol): the de facto standard BGP provides each AS a means
CNT 5410 - Computer and Network Security: BGP Security Professor Kevin Butler Fall 2015 Internet inter-as routing: BGP BGP (Border Gateway Protocol): the de facto standard BGP provides each AS a means
CS 640: Introduction to Computer Networks. Intra-domain routing. Inter-domain Routing: Hierarchy. Aditya Akella
 CS 640: Introduction to Computer Networks Aditya Akella Lecture 11 - Inter-Domain Routing - BGP (Border Gateway Protocol) Intra-domain routing The Story So Far Routing protocols generate the forwarding
CS 640: Introduction to Computer Networks Aditya Akella Lecture 11 - Inter-Domain Routing - BGP (Border Gateway Protocol) Intra-domain routing The Story So Far Routing protocols generate the forwarding
ECE 158A: Lecture 7. Fall 2015
 ECE 158A: Lecture 7 Fall 2015 Outline We have discussed IP shortest path routing Now we have a closer look at the IP addressing mechanism We are still at the networking layer, we will examine: IP Headers
ECE 158A: Lecture 7 Fall 2015 Outline We have discussed IP shortest path routing Now we have a closer look at the IP addressing mechanism We are still at the networking layer, we will examine: IP Headers
Internet Routing Protocols Lecture 01 & 02
 Internet Routing Protocols Lecture 01 & 02 Advanced Systems Topics Lent Term, 2010 Timothy G. Griffin Computer Lab Cambridge UK Internet Routing Outline Lecture 1 : Inter-domain routing architecture, the
Internet Routing Protocols Lecture 01 & 02 Advanced Systems Topics Lent Term, 2010 Timothy G. Griffin Computer Lab Cambridge UK Internet Routing Outline Lecture 1 : Inter-domain routing architecture, the
