Federal PKI Directory Profile 1/25/2001
|
|
|
- Franklin Fitzgerald
- 5 years ago
- Views:
Transcription
1 Federal PKI Directory Profile 1/25/ Introduction This profile defines the requirements for the initial operational Federal Public Key Infrastructure (FPKI) directory system. The FPKI builds upon the Federal Bridge Certification Authority (FBCA) prototype that was successfully demonstrated during the Electronic Messaging Association (EMA) Challenge in April This prototype supported S/MIME messaging among several disparate PKI domains using several different CA products, X.500 directory products, and S/MIME clients. This demonstration illustrated interoperability on several levels between CAs, between directories, and between clients. Each client created, and then processed a certificate trust path between the domain of the recipient and the domain of the sender in order to validate the signer's digital signature on the . Trust paths up to seven certificates were constructed and validated. Directories were chained using the X.500 Directory System Protocol (DSP), while the Lightweight Directory Access Protocol (LDAP) was employed by the client to access its local directory [1]. The FPKI will use a Federal Bridge CA that cross-certifies with agency Principal CAs to provide trust paths between the agencies. An FBCA directory server will be chained to agency border directories to make certificates available for PKI users. The Border CA concept is described in [2]. In the following sections, this profile will address the minimum required schema, the naming conventions, the directory protocols to support, alternatives to consider, and issues to bear in mind in order to adapt to this evolving technology. Familiarity with the PKI technology, concepts and general terms of the directory service is assumed. The draft is based on several sections of the following documents: The Evolving Federal Public Key Infrastructure [1], Governmentwide Directory Support 2 Technical Series, the Updated US Gold Schema document [3], The Bridge CA Demonstration Repository Requirements Draft 4/8/1999 [4], and NSA Bridge Certification Authority Demonstration Phase II - Directory Requirements and Architecture, 7/3/2000 [5]. 2. Schema Requirements This section addresses the minimum schema requirements for agency directories to interoperate with the FPKI directory. The schema is limited to just the objects needed to support the PKI. At a minimum, the directories are required to store and disseminate the following PKI related attributes: Certification Authority Certificates Certificate Revocation Lists Authority Revocation Lists Cross Certificates End-entity certificates RFC822MailUser In the Internet X.509v3 Public Key Infrastructure LDAPv2 Schema [6], these attributes are: cacertificate Working DRAFT - 01/25/01 1
2 certificaterevocationlist authorityrevocationlist crosscertificatepair usercertificate rfc822mailbox This schema is used in some commercial CA products. Some agencies may wish to make other information available externally to support their PKI applications. However, this profile does not address or impose requirements on application-specific data in agency directories. The cacertificate and crosscertificatepair attributes require special attention when accessing the directory to build the certificate path. Neither the PKIX specification nor the X.509 standards explicitly provide an algorithm to construct a certificate path. The PKIX LDAP-V2-schema provides guidance on what can be stored in the specific attributes. The draft states the following about the cacertificate attribute and the crosscertificatepair attribute: The cacertificate attribute of a CA's directory entry shall be used to store self-issued certificates (if any) and certificates issued to this CA by CAs in the same realm as this CA. The forward elements of the crosscertificatepair attribute of a CA's directory entry shall be used to store all, except self-issued certificates issued to this CA. Optionally, the reverse elements of the crosscertificatepair attribute of a CA's directory entry may contain a subset of certificates issued by this CA to other CAs. When both the forward and the reverse elements are present in a single attribute value, issuer name in one certificate shall match the subject name in the other and vice versa, and the subject public key in one certificate shall be capable of verifying the digital signature on the other certificate and vice versa. When a reverse element is present, the forward element value and the reverse element value need not be stored in the same attribute value; in other words, they can be stored in either a single attribute value or two attribute values. In the case of V3 certificates, none of the above CA certificates shall include a basicconstraints extension with the ca value set to FALSE. A path development algorithm must consider that the CA s certificate must be stored in the crosscertificatepair attribute, but the algorithm may consult the cacertificate attribute first, for performance reasons. The following sections define the attributes and object classes that are required for end entities and CAs. 2.1 End Entities Attributes End entity (EE) directory entries shall contain, as a minimum, the following attributes: 1. usercertificate as defined in 1997 X.509v3 [7] (OID: ), Working DRAFT - 01/25/01 2
3 2. attributecertificate as defined in 1997 X.509v3 (OID: ), 3. commonname as defined in 1997 X.521 [8] (OID: ), 4. surname as defined in 1997 X.521 (OID: ). NOTE: The EE relative distinguished name (RDN) shall consist of the commonname attribute type and value. For example: cn=john Smith Object Classes EE entries shall be made up of the following object classes: 1. person as defined in 1997 X.521 (OID: ). 2. pkiuser as defined in RFC 2587: LDAPv2 Schema (OID: ) for non-entrust EEs -- OR -- entrustuser as defined in Entrust Directory Schema Requirements version 1.0, dated August, 1998 (OID: ) for Entrust EEs. 3. securepkiuser as defined in ACP 133 Edition B [9] (OID: ). This auxiliary object class includes attributecertificate and supportedalgorithms as optional attribute types. Optionally, EEs may include the following object classes: 1. organizationalperson as defined in 1997 X.521 (OID: ), 2. inetorgperson as defined in IETF RFC 2798 [10] (OID: ). 2.2 Certification Authorities Attributes CA (including PCAs and PAAs) entries in the directory shall contain at a minimum the following attributes: 1. commonname OR organizationalunitname as defined in 1997 X.509v3 (OIDs: and respectively). 2. cacertificate as defined in 1997 X.509v3 (OID: ). As per the LDAPv2 Schema (RFC 2587), the cacertificate attribute shall be populated as follows: The cacertificate attribute of a CA's directory entry shall be used to store self-issued certificates (if any) and certificates issued to this CA by CAs in the same realm as this CA. 3. certificaterevocationlist as defined in 1997 X.509v3 (OID: ) 4. crosscertificatepair as defined in 1997 X.509v3 (OID: ). As per the LDAPv2 Schema (RFC 2587), the crosscertificatepair shall be populated as follows: The forward elements of the crosscertificatepair attribute of a CA's directory entry shall be used to store all, except self-issued certificates issued to this CA. Optionally, the reverse elements of the crosscertificatepair attribute of a CA's directory entry may contain a subset of certificates issued by this CA to other CAs. When both the forward Working DRAFT - 01/25/01 3
4 and the reverse elements are present in a single attribute value, issuer name in one certificate shall match the subject name in the other and vice versa, and the subject public key in one certificate shall be capable of verifying the digital signature on the other certificate and vice versa. When a reverse element is present, the forward element value and the reverse element value need not be stored in the same attribute value; in other words, they can be stored in either a single attribute value or two attribute values. CAs entries in the directory may optionally contain the authorityrevocationlist attribute as defined in 1997 X.509v3 (OID: ). NOTE: The CA relative distinguished name (RDN) shall consist of either the commonname attribute type and value or the organizationalunitname attribute type and value. For example: cn=nsa CA -- OR -- ou=eca1 Object Classes CA entries shall be made up of the following object classes: pkica as defined in RFC 2587: LDAPv2 Schema (OID: ) for non-entrust CAs -- OR -- entrustca as defined in Entrust Directory Schema Requirements version 1.0, dated August, 1998 (OID: ) for Entrust CAs. The base object class of CAs shall be one (or more) of the following: 1. person as defined in 1997 X.521 (OID: ) 2. organizationalperson as defined in 1997 X.521 (OID: ) 3. inetorgperson as defined in IETF RFC 2798 (OID: ) 4. organizationalunit as defined in 1997 X.521 (OID: ) 3. Namespace Control and DIT Structure PKI objects are defined in the X.509 specification, and use the X.500 information model. This model is used by both X.500 and LDAP-based directory services operated by government agencies that will rely upon the Federal Bridge CA. A PKI object (such as a public key certificate or certificate revocation list) is located using that object s Distinguished Name (DN), which specifies the location of the object within the federal directory information tree. This tree is a logical hierarchical structure composed of all the various agency directory services. A namespace is the section, or subtree, of the directory controlled by a specific agency. 3.1 Agency Directory Service Requirements Agencies are not required to conform to any specific directory protocol internally. But, in order to interoperate with the FBCA, an agency s directory service must conform to the following requirements: The agency s PKI information must conform to the X.500 information model and X.509. The agency s PKI information must conform to one of the namespace strategies stated in Sections 3.2, 3.3, and 3.4, below. Working DRAFT - 01/25/01 4
5 The agency s directory service must support 1993 X.500 chained operations, 1993 X.500 referrals, or LDAP v3 referrals. The agency must register their directory service as in Section with the FBCA in order to establish interoperability. The agency may choose to employ a Border Directory Server Agent (DSA) to provide for protocol conversions, enforce security, and restrict access to internal directory services Registration The FBCA will provide connectivity between, and references to, registered U.S. Government agency directory systems (see Section 3.4). In order to establish this connectivity, each agency participating in the FBCA must register their directory service or Border DSA registration contact info goes here name, phone #, office, etc. The following information must be provided:! Name and address of agency! Name, address and contact information for agency s directory administrator! Distinguished Name, Network Address, and Host Name of directory service! Naming Context (namespace) kept on this directory server (see Sections 3.2, 3.3, and 3.4)! Protocols (X.500 and/or LDAP) at least one is required! If X.500, state whether chained operations and/or referrals are allowed to this document contains a worksheet to aid you in collecting this information prior to registration. 3.2 X.500 Directory Services If the agency chooses to use X.500-based directory services, its directories must conform to the name space as defined for the Federal Government [3] (Figure 3-1). This namespace contains the U.S. Government level of the global X.500 Directory Information Tree (DIT) and all governmental agencies and departments. In X.500 terms, this namespace includes directory servers with the naming context of: c=us; o=u.s. Government The U.S. Government is registered as an organization (o) object class in the Global DIT. Agencies and departments are registered as organizationalunit (ou) object classes immediately beneath the o=u.s. Government entry in the Global DIT. Agency and department names in the Federal Government namespace must conform to agency and department names as stated in the Federal Government Manual. This publication cites first level agencies and departments (organizationalunits) in each branch of the Federal Government. For instance, Department of Transportation would be: Working DRAFT - 01/25/01 5
6 c=us; o=u.s. Government; ou=department of Transportation The agency or department is free to define and manage the namespace for lower levels within (underneath) the agency or department level of the directory. Figure 3-1 Federal Government Top Level DIT Abbreviations are allowed, but must be negotiated with the FBCA Registrar (above) to ensure uniqueness within the U.S. Government namespace. Potential conflicts on abbreviations can occur, and will be solved as follows. If the agency or department has a current domain registration within the Internet Domain Naming System (DNS) underneath.gov, they may use this as an abbreviation within the Federal Government directory. For example, the Department of Transportation is registered as dot.gov, and thus can use: c=us; o=u.s. Government; ou=dot Department of the Treasury, however, is registered as treas.gov, and thus could use: c=us; o=u.s. Government; ou=treas Any number of organizationalunitnames may be registered to aid in directory searches. For example, the Department of Transportation directory entry could have the following names (if authorized by the FBCA Registrar): Working DRAFT - 01/25/01 6
7 c=us; o=u.s. Government; ou=department of Transportation (specified RDN) c=us; o=u.s. Government; ou=transportation c=us; o=u.s. Government; ou=dot The actual directory entries would be found underneath the name specified in the Federal Government Manual. All other DNs would actually be aliases pointing to this official DN DNs versus RDNs In the above example, a specific directory entry could be located by three different DNs. The first DN identified the actual directory entry, and the other two were aliased to the first. Each entry contains a unique value known as the Relative Distinguished Name, or RDN. These values are chained together to form the DN for any specific object in the Global DIT. In the above examples, the DN for Department of Transportation tells us that the Directory Information Tree contains:! A country object with a RDN of c=us! An organization object with a RDN of o=u.s. Government, which is subordinate to the c=us object.! An organizationalunit object with a RDN of ou=department of Transportation, which is subordinate to the o=u.s. Government object. X.500 and LDAP allow for multi-value attributes. For instance, the Department of Transportation object could contain commonname attributes for all three names Department of Transportation, Transportation, and DOT. This feature allows users to find the object by specifying part of the name, rather than traversing the DIT Advantages and Disadvantages of X.500 The X.500 naming scheme is well understood. It has been supported in current PKI products, which have been successfully demonstrated in the PKI BCA and the EMA challenge demonstrations. However, the drawback of this naming scheme is that it is little used by anyone other than for PKI. Generally speaking, users do not necessarily understand or care about the finer distinctions of the Federal structure, therefore, distinguished names with organizational structure embedded in them are difficult for users to comprehend or remember. In addition, the more structure that is embedded in names, the more certificates that would need to be revoked when structures change. And the more structure that is built into the names, the more the name space needs to be administered. Many agencies have adopted a very flat namespace, where all the organization s users are listed directly underneath the agency object or within a single subtree, regardless of location or organizational structure. Another recurring debate, which occurs with X.500-based systems, lies in the directory tree structure within the agency. There are three basic approaches:! Put all the directory entries into a single, flat namespace (usually requires a single DSA serving the entire agency). Working DRAFT - 01/25/01 7
8 ! Divide the tree to mirror organizational structure (may create problems if the directory servers are located in multiple geographic locations).! Divide the tree to mirror geographical or network infrastructure (presents issues related to interactive searching and use). The Federal Bridge CA has no preference and issues no guidance as to the tree structure of internal agency directory services. This area is clearly outside the scope of this document. 3.3 Internet Domain Name Based Naming With the global acceptance of Internet and technologies such as the Domain Name System (DNS) and RFC822-based , many portions of the government have ignored older technologies such as X.500 and have implemented Internet-based infrastructures. These infrastructures are used primarily for and web-based delivery of services and information. The Internet DNS provides a hierarchical naming and locating system based on domain name components. For instance, the Internal Revenue Service is registered as irs.treas.gov. The U.S. Federal government owns the gov top-level domain, and is responsible for assigning and administering domain component names underneath that domain. Department of the Treasury (Treasury) has registered the domain component of treas, underneath gov. Therefore, any user at the Department of the Treasury would have an address something like any.user@treas.gov, and the main Treasury web page would be found at The Internal Revenue Service has been assigned the domain component of irs by Treasury, such that a user within IRS would have an address of any.user@irs.treas.gov and the main IRS web page would be found at This DNS-style of naming was originally developed to support hierarchical management and searching of computer system names (e.g. hostnames ). Each computer attached to the Internet has an Internet Protocol (IP) address, which consists of four numbers between 0 and 255, separated by periods. These addresses look something like Clearly, this is hard for users to comprehend, much less remember. Who wants to address an message to john.smith@ ? (Actually, this address will work on many Internet-connected systems). DNS maps this numeric IP address into a human-readable system name, called a Fully Qualified Domain Name, or FQDN. This allows a user to send to john.smith@company.com instead of trying to remember the IP address. The computer looks up company.com, finds the numeric address, and makes the connection. In this sense, IP addresses are like telephone numbers, and DNS is like a giant, worldwide electronic phone book. X.500 is a completely separate directory system from DNS. However, a proposed Internet Standard as described in RFC 2247 [11] and RFC 2377 [12] provides a method of representing Domain Name System domain components using the X.500 information model. This allows both X.500 and LDAPbased directory services to store information in a structure familiar to Internet-literate users. RFC 2247 defines an attribute, DomainComponent (dc), which can be used to store a domain component such as gov. It also defines two objects, domain and dcobject. The dcobject object can be added to existing objects so that they can contain a dc attribute. The domain object allows the addition of new entries that contain a dc attribute. Working DRAFT - 01/25/01 8
9 Using domain objects, it is possible to accurately represent the DNS tree within an X.500 or LDAP directory service (Figure 3-2). The user specified by the address would be represented by the X.500 DN: dc=gov; dc=treas; dc=irs; pn=john.smith LDAP allows a relaxed form of DN in reverse order separated by commas, which looks like: pn=john.smith, dc=irs, dc=treas, dc=gov The information in the directory is the same either way. Searching based on this DNS-style naming can be very intuitive to users who are familiar with Internet addresses. The Federal Bridge CA will allow agencies to choose to implement naming in this fashion, instead of (or in addition to) the X.500-style Federal Government naming set forth in Section 3.1. Additionally, the dcobject object can be used to add the dc attribute to other X.500 objects. Therefore it can allow for construction of DNs which look very much like X.500, but which are actually composed of DomainComponent attributes. This sort of DN would look like: dc=us; dc=u.s. Government; dc=treas; dc=irs; pn=john.smith pn=john.smith, dc=irs, dc=treas, dc=u.s. Government, dc=us (or) The Federal Bridge CA will not support this style naming. Its similarity to pure X.500 naming would cause significant confusion. Since it doesn t map to the Internet-style addresses, it is not intuitive to use and therefore provides no benefit. As DNS evolves in the future, country-based naming may come into use. If so, this decision will be revisited at that time Drawbacks of DNS-Style Naming RFC 2247, the document that proposes this style of addressing, is a proposed Internet Standard. It therefore is fairly stable and not subject to major changes. However, it may not be widely implemented in applications and commercial software products yet. The gov domain is owned by the U.S. Government. Registration of government agencies and operation of the government-level DNS is outsourced to a vendor. As far as is known, there is no official guidance relating to the creation of DNS-style domain information for government agencies. This leads to several confusing situations: Internet domain name components are typically short and cryptic. Many times, all users appear directly underneath the organization with no clue as to organizational structure or geographic location. Also, many agencies have registered domain names that don t reflect the actual Federal departmental structure. This may be because of grandfathering (an agency got the name before any policy was established), or because the public is neither interested in, nor knowledgeable about the government s departmental structure, and would simply be confused by domain names that reflect actual structure. Examples include: faa.gov rather than faa.dot.gov nist.gov rather than nist.doc.gov cg.mil rather than cg.dot.gov Working DRAFT - 01/25/01 9
10 Figure 3-2 Domain Component Naming DIT dc=gov dc=nist dc=doc dc=gsa dc=treas dc=fpa pn=nist CA pn=doc CA pn=fbca dc=irs dc=cio dc=occ pn=richard.guida Working DRAFT - 01/25/01 10
11 It may be fairly clear that the FAA should be a part of the Transportation Department, but does the public generally know that NIST is a part of the Commerce Department, or that the Coast Guard, a uniformed service, is actually under the Transportation rather than the Defense Department? Another potential problem can be confusion between the government and the private sector because of the Top Level Domain Names. The U.S. Government only has authority over domain names ending with.gov. Sites such as and most notoriously (don t go there) play off of this confusion for purposes of social satire, political commentary, and worse. And lastly, there is no automatic synchronization between X.500 and the DNS. When a domain component is registered in the DNS, it will require a second action to have it manually entered into the X.500 directory. This presents the potential for the X.500 or LDAP-based directory to get out of synchronization with the current state of the DNS. Within government, the changes are infrequent enough that this may be a manageable problem. 3.4 Combined Domain Component Names with X.500 Names Recently the Higher Education community, in a part of the Higher Ed, Internet II effort [13], has taken a slightly different approach to the use of domain component names, and asked the FPKI directory profile support this option. This community advocates combining domain component names with traditional X.500 names in the subjectname field of a certificate to enforce name uniqueness. This requires no new registration or management, and it may faciliate directory service discovery via DNS SRV records [14]. No rule in X.500 prohibits this, recent changes to the FBCA CP will also allow for this flexibility. New infrastructures are being designed in the Internet2/EDUCAUSE arenas to meet the needs of academia and a myriad of applications [13]. Allowing this flexibility will facilitate interoperability between institutions of higher education and the federal government, and foster the use of the FBCA model outside the US government. The directory working group has discussed this proposal extensively and tentatively agreed to support this option as a reasonable basis for interoperable naming. The FBCA would stand up a directory server with 2 (or 3) roots for [o=us Government, c= US], [dc=gov], and, possibly, [dc=mil]. Agencies would be encouraged to include the combined name form in entity certificates and could choose whether to use [o=us Government, C= US] (Figure 3.3) or [dc=gov] (Figure 3.4) as the most significant part of their name. It would also be acceptable to use only one name form or the other (Figure 3.1 and Figure 3.2). Using this scheme, some equivalent examples would be: 1. cn=john Smith, dc=irs, dc=treas, dc=gov, ou=department of Treasury, o=u.s. Government, c=us 2. cn=john Smith, dc=irs, ou=internal Revenue Service, dc=treas, dc=gov, ou=department of Treasury, o=u.s. Government, c=us 3. cn=john Smith, ou=internal Revenue Service, dc=irs, dc=treas, dc=gov, ou=department of Treasury, o=u.s. Government, c=us Or, starting with the.gov domain name: 1. cn=john Smith, ou=internal Revenue Service, o=u.s. Government, dc=irs, dc=treas, dc=gov Working DRAFT - 01/25/01 11
12 Figure 3.3. Combined DCN with X.500 names -1 c=us ou=u.s. Government ou=fpa ou= ou=department of Treasury ou= ou= cn=fbca cn=john Smith dc=cio cn=john Doe ou=internal Revenue Service uid= Mary Jones Working DRAFT - 01/25/01 12
13 Figure 3-4 Combined DCN with X.500 Names - 2 dc=gov dc=fpa dc= dc=treas dc= dc=doc cn=fbca cn=john Smith dc=cio ou=internal Revenue Service o=u.s. Government c=us locality=washingtondc Working DRAFT - 01/25/01 13
14 2. cn=john Smith, ou=internal Revenue Service, o=u.s. Government, c=us, dc=irs dc=treas, dc=gov Several issues have been raised regarding this combined naming scheme. One is, do X.500 DSA products object to seeing the c= attribute subordinate to the dc=. Are there other features of this naming scheme that break some directory products? What are the rules, if any, for formulating the combined names? For example all the names above start (on the right) with either the c=us or dc=gov attribute and end (on the left) with the common name. This makes sense intuitively, but does it make any difference to the processing of the name? These issues are yet to be explored. 3.5 The U.S. Government Directory Server In order to promote interoperability between various agency and department directory services, the Federal Bridge CA program will operate a Directory Server that supports both the Federal Bridge CA, and the U.S. Government level of the X.500 DIT. In support of the U.S. Government level, the FBCA program will provide the following services:! Registration of directory services for agencies that wish to (a) participate in the Bridge CA program, and/or (b) interoperate with other government directory services.! The DSA will provide knowledge references to all registered directory services, and also to international government and the private sector, as required in order to promote Electronic Government initiatives.! Coordination with E-gov and international interoperability initiatives. The DSA will support the traditional X.500 DIT for the U.S. Government (Figure 3.1), the defacto Internet DNS directory structure (Figure 3.2), as well as the hybrid DITs as illustrated in Figure 3-3 and Figure 3.4. It will be able to bridge among these namespaces, promoting interoperability among agencies that have implemented traditional X.500 naming, those that rely upon the DNS structure, and those supported both. 4. Directory Protocols Two broad categories of directory servers are currently in use: X.500 DSAs, and LDAP servers. Both use the same X.500 directory information model and the LDAP v2 or v3 client directory access protocol. An X.500 DSA also supports Directory Service Protocol (DSP) chaining of directory servers. An LDAP server typically supports the LDAPv3 [15] client interface and LDAPv3 referrals. If chaining between servers is offered, it is usually a proprietary implementation. Most agencies will choose to operate with the Federal PKI through a border directory server located outside the agency firewall rather than through an internal agency directory server. However this profile does not preclude chaining internal directory servers to the FBCA directory server. The FBCA will maintain an X.500 DSA, holding the roots for c=us, o=u.s. Government, dc=gov, and possibly, dc=mil. This FBCA DSA will be available for chaining to agency X.500 DSAs. Working DRAFT - 01/25/01 14
15 For agencies that use X.500 DSAs for their directory service, or their border directory, it is not necessary to specify the precise client to directory server access protocol. Typically, it will be some version of LDAP, but the older X.500 Directory Access Protocol (DAP) is also acceptable. All that is required is that agency clients are compatible with agency servers. Agency servers will obtain needed external certificates and CRLs for their clients via DSP chaining, and this is transparent to the clients. Each agency border directory will be chained to the FBCA directory, via DSP chaining. Agencies that choose to use LDAP servers internally may make external agency certificates available to clients in several ways: The agency may stand up an X.500 DSA as a border directory and chain it to the FBCA DSA; Alternatively, if agency clients support LDAP v3 with referrals, then the LDAP servers may refer clients to the FBCA DSA for external certificates (or may make direct referrals to the border directories of other agencies). Agencies that choose to use LDAP servers internally may make internal agency certificates and CRLs available externally by: Standing up an X.500 DSA chained to the FBCA DSA and posting externally available certificates and CRLs to it. This may be achieved by purchasing directory services from a 3 rd party supplier. This is the preferred or recommended method of interoperating with other agencies through the FBCA DSA; Alternatively, if no X.500 border DSA is set up, users may include a certificate list beginning with the certificate issued by the FBCA to their agency PCA and ending with the user s signature certificate in the header of signed S/MIME messages. This does not directly support encryption, but it allows an external relying party (who interoperates through the FBCA) to validate S/MIME signatures. As the Federal PKI develops, the FBCA directory may incorporate an meta-directory capability, to transparently resolve the queries of X.500 DSAs for information contained in LDAP servers. This capability, however, will not be a part of the initial FBCA directory. In principle, the choice to use X.500 style or Domain component names is independent of the choice to use X.500 DSAs or LDAP servers. In practice, it appears likely that those who choose to use domain component names will probably choose to use LDAP servers. It is possible to chain through the FBCA DSA from an agency that uses Domain Component names to one that uses X.500 style names. The FBCA directory shall hold the root for both c=us, o=u.s. Government and dc=gov, and support chaining of both name types. 4.1 Authentication Requirements Directories are required to support simple authentication for LDAP and DSP communications Client Authentication FPKI directory clients that read the FPKI directory (read, list, search directory operations) require no authentication (i.e. anonymous bind to the directory is acceptable). This profile does not Working DRAFT - 01/25/01 15
16 address directory access control requirements to update FPKI directory servers. Agencies must ensure that only authorized parties can update FPKI directories Server Authentication FPKI directories are required to support simple authentication for server to server chaining (X.518 DSP) communications. has argued for no authentication for DSP for the following reason, which will not appear in the final draft of the profile. The WG needs to decide on this issue.) If we are going to use simple password based authentication for DSP, then we have to define a schema for registering DSA entries, and most importantly where in the DIT these entries are named. Nearly all product vendors will want the DSA entry name in the part of the DIT their DSA manages - it makes life easy for them. Regrettably this approach breaks large-scale distributed operations. If DSA A wants to connect to DSA B, it will pass a user name and password to DSA B. DSA B needs to check this somewhere locally to verify the identity of DSA A. Where does it get this password from? The natural place is in the DSAs entry in the DIT. Alas, this is stored in DSA A, so you cannot get at it (unless all DSAs implement the complex call-back bind-compare operation chaining model). So, what often happens, is that password is configured by an administrator locally. This works for a while, but it does not scale to a distributed directory of hundreds of servers. So, to use DSP password, you have to define a mechanism for managing and distributing these passwords. The only viable I have come across way is to use the DIT itself, and ensure the part of the DIT storing the DSA entries is highly replicated. However this is generally an unpopular approach. (There was once an Internet-Draft proposing such a schema, but it never made it very far). Interestingly this problem does not exist for strong authentication. Let us also bear in mind that simple passwords offer no real security. Consequently, I propose that for DSP no authentication is used, until such time Strong Authentication is viable. DISCLAIMER The FBCA directory service is being provided to promote full interoperability between government agencies, in support of the Bridge CA. Every attempt will be made to ensure that information contained in the directory service is correct (as provided by the individual agencies), and that this information is protected from unauthorized access and modification. However, each agency or department must consider the possible consequences of unintended disclosure of information provided due to error or attack. It is the responsibility of each agency or department to establish their own policy and security posture with regard to directory-based information, and to implement whatever protocols and protection that they deem sufficient to protect critical systems, including their internal directory services. References Working DRAFT - 01/25/01 16
17 [1] The Evolving Federal Public Key Infrastructure, Federal Public Key Infrastructure Steering Committee, Federal Chief Information Officers Council, gits-sec.treas.gov. [2] Burr, W., "Public Key Infrastructure (PKI) Technical Specifications: Part A-Technical Concept of Operations", September 1998 [3] Governmentwide Directory Support 2 Technical Series, the Updated US Gold Schema document, 7/14/1997, by Booz Allen & Hamilton. [4] The Bridge CA Demonstration Repository Requirements Draft 4/8/1999 by Chromatix, Inc. [5] NSA Bridge Certification Authority Demonstration Phase II - Directory Requirements and architecture, 7/3/2000, by Entigrity Solutions. [6] Boeyen, S., Howes, T., and P. Richard, "Internet X.509 Public Key Infrastructure LDAPv2 Schema", RFC2587, June [7] ITU-T Recommendation X.509 (1997) ISO/IEC : 1997, Information technology - Open Systems Interconnection - The Directory: Authentication framework, June [8] ITU-T Recommendation X.521 (1997) ISO/IEC : 1997, Information technology - Open Systems Interconnection - The Directory: Selected object classes. [9] Common Directory Services and Procedures, ACP (Allied Communication Publication) 133 Edition B, March [10] M. Smith, "Definition of the inetorgperson LDAP Object Class", RFC 2798, April [11] Kille, S., Wahl, M., Grimstad, A., Huber, R., and S. Sataluri, "Using Domains in LDAP Distinguished Names", RFC 2247, January [12] Grimstad, A., Sataluri, S., and M. Wahl, "Naming Plan for Internet Directory-Enabled Applications", RFC 2377, September [13] The Middleware Architecture Committee for Education (MACE) [14] Armijo, M., Leach, P., Esibov, L., and R. Morgan, Discovering LDAP Services with DNS, Internet Draft <draft-ietf-ldapext-locate-o4.txt>, August [15] Wahl, M., Howes, T., and S. Kille, "Lightweight Directory Access Protocol (v3)", RFC 2251, December Working DRAFT - 01/25/01 17
Prototype PKD Interface Specification
 Prototype PKD Interface Specification 2nd Edition 2 March 2005 Ministry of Economy, Trade and Industry New Media Development Association History: 2 March, 2005 by H.Shimada P10: Modification of 6 Tree
Prototype PKD Interface Specification 2nd Edition 2 March 2005 Ministry of Economy, Trade and Industry New Media Development Association History: 2 March, 2005 by H.Shimada P10: Modification of 6 Tree
Security Digital Certificate Manager
 System i Security Digital Certificate Manager Version 6 Release 1 System i Security Digital Certificate Manager Version 6 Release 1 Note Before using this information and the product it supports, be sure
System i Security Digital Certificate Manager Version 6 Release 1 System i Security Digital Certificate Manager Version 6 Release 1 Note Before using this information and the product it supports, be sure
IBM. Security Digital Certificate Manager. IBM i 7.1
 IBM IBM i Security Digital Certificate Manager 7.1 IBM IBM i Security Digital Certificate Manager 7.1 Note Before using this information and the product it supports, be sure to read the information in
IBM IBM i Security Digital Certificate Manager 7.1 IBM IBM i Security Digital Certificate Manager 7.1 Note Before using this information and the product it supports, be sure to read the information in
Public Key Infrastructure
 Public Key Infrastructure Ed Crowley Summer 11 1 Topics Public Key Infrastructure Defined PKI Overview PKI Architecture Trust Models Components X.509 Certificates X.500 LDAP 2 Public Key Infrastructure
Public Key Infrastructure Ed Crowley Summer 11 1 Topics Public Key Infrastructure Defined PKI Overview PKI Architecture Trust Models Components X.509 Certificates X.500 LDAP 2 Public Key Infrastructure
Directory Interoperability: Requirements, Standards and Conformance (or, PICS )
 Directory Interoperability: Requirements, Standards and Conformance (or, PICS ) Sandi Miklos, Technical Director Security Management Infrastructure National Security Agency samiklo@missi.ncsc.mil 14 January
Directory Interoperability: Requirements, Standards and Conformance (or, PICS ) Sandi Miklos, Technical Director Security Management Infrastructure National Security Agency samiklo@missi.ncsc.mil 14 January
Technical Trust Policy
 Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Version 3 X.509 Certificates
 Entrust Technologies White Paper Author: Ian Curry Date: July 1996 Version: 1.0 Entrust Technologies, 1997. All rights reserved. 1 1. Introduction This document provides a description of the version 3
Entrust Technologies White Paper Author: Ian Curry Date: July 1996 Version: 1.0 Entrust Technologies, 1997. All rights reserved. 1 1. Introduction This document provides a description of the version 3
Expires October 2005 Updates RFC 3280 April 2005
 PKIX Working Group S. Santesson (Microsoft) INTERNET-DRAFT R. Housley (Vigil Security) Expires October 2005 Updates RFC 3280 April 2005 Internet X.509 Public Key Infrastructure Authority Information Access
PKIX Working Group S. Santesson (Microsoft) INTERNET-DRAFT R. Housley (Vigil Security) Expires October 2005 Updates RFC 3280 April 2005 Internet X.509 Public Key Infrastructure Authority Information Access
November 1998 Expires May Storing Certificates in the Domain Name System (DNS)
 November 1998 Expires May 1999 Storing Certificates in the Domain Name System (DNS) ------- ------------ -- --- ------ ---- ------ ----- Donald E. Eastlake 3rd, Olafur Gudmundsson Status of This Document
November 1998 Expires May 1999 Storing Certificates in the Domain Name System (DNS) ------- ------------ -- --- ------ ---- ------ ----- Donald E. Eastlake 3rd, Olafur Gudmundsson Status of This Document
ISO/IEC INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD ISO/IEC 9594-8 Sixth edition 2008-12-15 Information technology Open Systems Interconnection The Directory: Publickey and attribute certificate frameworks Technologies de l'information
INTERNATIONAL STANDARD ISO/IEC 9594-8 Sixth edition 2008-12-15 Information technology Open Systems Interconnection The Directory: Publickey and attribute certificate frameworks Technologies de l'information
IBM i Version 7.2. Security Digital Certificate Manager IBM
 IBM i Version 7.2 Security Digital Certificate Manager IBM IBM i Version 7.2 Security Digital Certificate Manager IBM Note Before using this information and the product it supports, read the information
IBM i Version 7.2 Security Digital Certificate Manager IBM IBM i Version 7.2 Security Digital Certificate Manager IBM Note Before using this information and the product it supports, read the information
MODIFYING LDAP TO SUPPORT PKI
 MODIFYING LDAP TO SUPPORT PKI D.W.Chadwick, E. Ball, M.V. Sahalayev University of Salford Abstract: Key words: One of the impediments to a successful roll out of public key infrastructures (PKIs), is that
MODIFYING LDAP TO SUPPORT PKI D.W.Chadwick, E. Ball, M.V. Sahalayev University of Salford Abstract: Key words: One of the impediments to a successful roll out of public key infrastructures (PKIs), is that
Whitepapers. LDAP and X.500. First Published in Messaging Magazine, September What is Common to X.500 and LDAP
 Page 1 of 6 Whitepapers Isode's email and directory server products are used around the world by ISPs, Multinational Corporations, Governments, and Universities. LDAP and X.500 First Published in Messaging
Page 1 of 6 Whitepapers Isode's email and directory server products are used around the world by ISPs, Multinational Corporations, Governments, and Universities. LDAP and X.500 First Published in Messaging
Request for Comments: TIS Labs March Storing Certificates in the Domain Name System (DNS)
 Network Working Group Request for Comments: 2538 Category: Standards Track D. Eastlake IBM O. Gudmundsson TIS Labs March 1999 Status of this Memo Storing Certificates in the Domain Name System (DNS) This
Network Working Group Request for Comments: 2538 Category: Standards Track D. Eastlake IBM O. Gudmundsson TIS Labs March 1999 Status of this Memo Storing Certificates in the Domain Name System (DNS) This
Certification Practice Statement of the Federal Reserve Banks Services Public Key Infrastructure
 Certification Practice Statement of the Federal Reserve Banks Services Public Key Infrastructure 1.0 INTRODUCTION 1.1 Overview The Federal Reserve Banks operate a public key infrastructure (PKI) that manages
Certification Practice Statement of the Federal Reserve Banks Services Public Key Infrastructure 1.0 INTRODUCTION 1.1 Overview The Federal Reserve Banks operate a public key infrastructure (PKI) that manages
Deficiencies in LDAP when used to support Public Key Infrastructures
 Deficiencies in LDAP when used to support Public Key Infrastructures Author: David Chadwick, University of Salford, Salford M5 4WT, England. Email: d.w.chadwick@salford.ac.uk Introduction The lightweight
Deficiencies in LDAP when used to support Public Key Infrastructures Author: David Chadwick, University of Salford, Salford M5 4WT, England. Email: d.w.chadwick@salford.ac.uk Introduction The lightweight
TECHNICAL SPECIFICATION
 TECHNICAL SPECIFICATION IEC/TS 62351-8 Edition 1.0 2011-09 colour inside Power systems management and associated information exchange Data and communications security Part 8: Role-based access control
TECHNICAL SPECIFICATION IEC/TS 62351-8 Edition 1.0 2011-09 colour inside Power systems management and associated information exchange Data and communications security Part 8: Role-based access control
ISO/IEC INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD ISO/IEC 9594-8 Fifth edition 2005-12-15 Information technology Open Systems Interconnection The Directory: Publickey and attribute certificate frameworks Technologies de l'information
INTERNATIONAL STANDARD ISO/IEC 9594-8 Fifth edition 2005-12-15 Information technology Open Systems Interconnection The Directory: Publickey and attribute certificate frameworks Technologies de l'information
Cisco TelePresence Authenticating Cisco VCS Accounts Using LDAP
 Cisco TelePresence Authenticating Cisco VCS Accounts Using LDAP Deployment Guide Cisco VCS X8.2 D14465.07 June 2014 Contents Introduction 3 Process summary 3 LDAP accessible authentication server configuration
Cisco TelePresence Authenticating Cisco VCS Accounts Using LDAP Deployment Guide Cisco VCS X8.2 D14465.07 June 2014 Contents Introduction 3 Process summary 3 LDAP accessible authentication server configuration
TeliaSonera Gateway Certificate Policy and Certification Practice Statement
 TeliaSonera Gateway Certificate Policy and Certification Practice Statement v. 1.2 TeliaSonera Gateway Certificate Policy and Certification Practice Statement TeliaSonera Gateway CA v1 OID 1.3.6.1.4.1.271.2.3.1.1.16
TeliaSonera Gateway Certificate Policy and Certification Practice Statement v. 1.2 TeliaSonera Gateway Certificate Policy and Certification Practice Statement TeliaSonera Gateway CA v1 OID 1.3.6.1.4.1.271.2.3.1.1.16
LDAP Directory Services
 ATTENTION LDAP Directory Services THE MATERIAL PROVIDED IN THIS DOCUMENT IS FOR INFORMATION PURPOSES ONLY. IT IS NOT INTENDED TO BE ADVICE. YOU SHOULD NOT ACT OR ABSTAIN FROM ACTING BASED UPON SUCH INFORMATION
ATTENTION LDAP Directory Services THE MATERIAL PROVIDED IN THIS DOCUMENT IS FOR INFORMATION PURPOSES ONLY. IT IS NOT INTENDED TO BE ADVICE. YOU SHOULD NOT ACT OR ABSTAIN FROM ACTING BASED UPON SUCH INFORMATION
Internet Engineering Task Force (IETF) Request for Comments: 5917 Category: Informational June 2010 ISSN:
 Internet Engineering Task Force (IETF) S. Turner Request for Comments: 5917 IECA Category: Informational June 2010 ISSN: 2070-1721 Abstract Clearance Sponsor Attribute This document defines the clearance
Internet Engineering Task Force (IETF) S. Turner Request for Comments: 5917 IECA Category: Informational June 2010 ISSN: 2070-1721 Abstract Clearance Sponsor Attribute This document defines the clearance
ISO/IEC INTERNATIONAL STANDARD. Information technology Open Systems Interconnection The Directory: Procedures for distributed operation
 INTERNATIONAL STANDARD ISO/IEC 9594-4 Sixth edition 2008-12-15 Information technology Open Systems Interconnection The Directory: Procedures for distributed operation Technologies de l'information Interconnexion
INTERNATIONAL STANDARD ISO/IEC 9594-4 Sixth edition 2008-12-15 Information technology Open Systems Interconnection The Directory: Procedures for distributed operation Technologies de l'information Interconnexion
T A B L E O F C O N T E N T S
 T A B L E O F C O N T E N T S PREFACE... v 1.0 INTRODUCTION... 1-1 1.1 Purpose... 1-1 1.2 Background... 1-1 1.3 Scope... 1-3 1.4 Organization of this Document... 1-3 1.5 Government Electronic Directory
T A B L E O F C O N T E N T S PREFACE... v 1.0 INTRODUCTION... 1-1 1.1 Purpose... 1-1 1.2 Background... 1-1 1.3 Scope... 1-3 1.4 Organization of this Document... 1-3 1.5 Government Electronic Directory
Internet Engineering Task Force (IETF) Request for Comments: 6490 Category: Standards Track. G. Michaelson APNIC. S. Kent BBN February 2012
 Internet Engineering Task Force (IETF) Request for Comments: 6490 Category: Standards Track ISSN: 2070-1721 G. Huston S. Weiler SPARTA, Inc. G. Michaelson S. Kent BBN February 2012 Abstract Resource Public
Internet Engineering Task Force (IETF) Request for Comments: 6490 Category: Standards Track ISSN: 2070-1721 G. Huston S. Weiler SPARTA, Inc. G. Michaelson S. Kent BBN February 2012 Abstract Resource Public
Transglobal Secure Collaboration Program Secure v.1 Technical Specification. Prepared by: TSCP Secure v.
 Transglobal Secure Collaboration Program Secure E-mail v.1 Technical Specification Prepared by: TSCP Secure E-mail v.1 Project Team Version: 3.0.2 Date: 07/16/2012 TSCP Secure E-Mail v.1 Technical Specification
Transglobal Secure Collaboration Program Secure E-mail v.1 Technical Specification Prepared by: TSCP Secure E-mail v.1 Project Team Version: 3.0.2 Date: 07/16/2012 TSCP Secure E-Mail v.1 Technical Specification
X.509 Certificate Policy. For The Federal Bridge Certification Authority (FBCA)
 X.509 Certificate Policy For The Federal Bridge Certification Authority (FBCA) September 10, 2002 Signature Page Chair, Federal Public Key Infrastructure Policy Authority DATE Table of Contents 1. INTRODUCTION...
X.509 Certificate Policy For The Federal Bridge Certification Authority (FBCA) September 10, 2002 Signature Page Chair, Federal Public Key Infrastructure Policy Authority DATE Table of Contents 1. INTRODUCTION...
National Identity Exchange Federation. Trustmark Signing Certificate Policy. Version 1.0. Published October 3, 2014 Revised March 30, 2016
 National Identity Exchange Federation Trustmark Signing Certificate Policy Version 1.0 Published October 3, 2014 Revised March 30, 2016 Copyright 2016, Georgia Tech Research Institute Table of Contents
National Identity Exchange Federation Trustmark Signing Certificate Policy Version 1.0 Published October 3, 2014 Revised March 30, 2016 Copyright 2016, Georgia Tech Research Institute Table of Contents
The LDAP Protocol. Agenda. Background and Motivation Understanding LDAP
 The LDAP Protocol Agenda Background and Motivation Understanding LDAP Information Structure Naming Functions/Operations Security Protocol Model Mapping onto Transport Services Protocol Element Encoding
The LDAP Protocol Agenda Background and Motivation Understanding LDAP Information Structure Naming Functions/Operations Security Protocol Model Mapping onto Transport Services Protocol Element Encoding
Request For Comments: 1816 August 1995 Obsoletes: 1811 Category: Informational
 Network Working Group Federal Networking Council Request For Comments: 1816 August 1995 Obsoletes: 1811 Category: Informational Status of this Memo U.S. Government Internet Domain Names This memo provides
Network Working Group Federal Networking Council Request For Comments: 1816 August 1995 Obsoletes: 1811 Category: Informational Status of this Memo U.S. Government Internet Domain Names This memo provides
Expires in six months 24 October 2004 Obsoletes: RFC , , 3377, 3771
 INTERNET-DRAFT Editor: Kurt D. Zeilenga Intended Category: Standard Track OpenLDAP Foundation Expires in six months 24 October 2004 Obsoletes: RFC 2251-2256, 2829-2830, 3377, 3771 Lightweight Directory
INTERNET-DRAFT Editor: Kurt D. Zeilenga Intended Category: Standard Track OpenLDAP Foundation Expires in six months 24 October 2004 Obsoletes: RFC 2251-2256, 2829-2830, 3377, 3771 Lightweight Directory
ING Corporate PKI G3 Internal Certificate Policy
 ING Corporate PKI G3 Internal Certificate Policy Version 1.0 March 2018 ING Corporate PKI Service Centre Final Version 1.0 Document information Commissioned by Additional copies of this document ING Corporate
ING Corporate PKI G3 Internal Certificate Policy Version 1.0 March 2018 ING Corporate PKI Service Centre Final Version 1.0 Document information Commissioned by Additional copies of this document ING Corporate
Authenticating Cisco VCS accounts using LDAP
 Authenticating Cisco VCS accounts using LDAP Cisco TelePresence Deployment Guide Cisco VCS X6 D14526.04 February 2011 Contents Contents Document revision history... 3 Introduction... 4 Usage... 4 Cisco
Authenticating Cisco VCS accounts using LDAP Cisco TelePresence Deployment Guide Cisco VCS X6 D14526.04 February 2011 Contents Contents Document revision history... 3 Introduction... 4 Usage... 4 Cisco
Cisco Expressway Authenticating Accounts Using LDAP
 Cisco Expressway Authenticating Accounts Using LDAP Deployment Guide Cisco Expressway X8.5 December 2014 Contents Introduction 3 Process summary 3 LDAP accessible authentication server configuration 4
Cisco Expressway Authenticating Accounts Using LDAP Deployment Guide Cisco Expressway X8.5 December 2014 Contents Introduction 3 Process summary 3 LDAP accessible authentication server configuration 4
Expires: 20 May December 2000 Obsoletes: 1779, 2253
 INTERNET-DRAFT Editor: Kurt D. Zeilenga Intended Category: Standard Track OpenLDAP Foundation Expires: 20 May 2001 20 December 2000 Obsoletes: 1779, 2253 Lightweight Directory Access Protocol (v3): UTF-8
INTERNET-DRAFT Editor: Kurt D. Zeilenga Intended Category: Standard Track OpenLDAP Foundation Expires: 20 May 2001 20 December 2000 Obsoletes: 1779, 2253 Lightweight Directory Access Protocol (v3): UTF-8
PKI-An Operational Perspective. NANOG 38 ARIN XVIII October 10, 2006
 PKI-An Operational Perspective NANOG 38 ARIN XVIII October 10, 2006 Briefing Contents PKI Usage Benefits Constituency Acceptance Specific Discussion of Requirements Certificate Policy Certificate Policy
PKI-An Operational Perspective NANOG 38 ARIN XVIII October 10, 2006 Briefing Contents PKI Usage Benefits Constituency Acceptance Specific Discussion of Requirements Certificate Policy Certificate Policy
ISO/IEC INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD ISO/IEC 9594-8 Fourth edition 2001-08-01 Information technology Open Systems Interconnection The Directory: Public-key and attribute certificate frameworks Technologies de l'information
INTERNATIONAL STANDARD ISO/IEC 9594-8 Fourth edition 2001-08-01 Information technology Open Systems Interconnection The Directory: Public-key and attribute certificate frameworks Technologies de l'information
The LDAP Protocol. Amrish Kaushik. Graduate Student USC Computer Science (CN)
 The LDAP Protocol Amrish Kaushik Graduate Student USC Computer Science (CN) Agenda Background and Motivation Understanding LDAP Information Structure Naming Functions/Operations Security Protocol Model
The LDAP Protocol Amrish Kaushik Graduate Student USC Computer Science (CN) Agenda Background and Motivation Understanding LDAP Information Structure Naming Functions/Operations Security Protocol Model
Network Security Essentials
 Network Security Essentials Fifth Edition by William Stallings Chapter 4 Key Distribution and User Authentication No Singhalese, whether man or woman, would venture out of the house without a bunch of
Network Security Essentials Fifth Edition by William Stallings Chapter 4 Key Distribution and User Authentication No Singhalese, whether man or woman, would venture out of the house without a bunch of
HSPD-12 : The Role of Federal PKI
 HSPD-12 : The Role of Federal PKI Judith Spencer Chair, Federal Identity Credentialing Office of Governmentwide Policy General Services Administration judith.spencer@gsa.gov How We Got Here 2005 FIPS-201
HSPD-12 : The Role of Federal PKI Judith Spencer Chair, Federal Identity Credentialing Office of Governmentwide Policy General Services Administration judith.spencer@gsa.gov How We Got Here 2005 FIPS-201
ISO/IEC Information technology Open Systems Interconnection The Directory: Protocol specifications
 This is a preview - click here to buy the full publication INTERNATIONAL STANDARD ISO/IEC 9594-5 Fifth edition 2005-12-15 Information technology Open Systems Interconnection The Directory: Protocol specifications
This is a preview - click here to buy the full publication INTERNATIONAL STANDARD ISO/IEC 9594-5 Fifth edition 2005-12-15 Information technology Open Systems Interconnection The Directory: Protocol specifications
draft-ietf-smime-cert-06.txt December 14, 1998 Expires in six months S/MIME Version 3 Certificate Handling Status of this memo
 Internet Draft draft-ietf-smime-cert-06.txt December 14, 1998 Expires in six months Editor: Blake Ramsdell, Worldtalk Status of this memo S/MIME Version 3 Certificate Handling This document is an Internet-Draft.
Internet Draft draft-ietf-smime-cert-06.txt December 14, 1998 Expires in six months Editor: Blake Ramsdell, Worldtalk Status of this memo S/MIME Version 3 Certificate Handling This document is an Internet-Draft.
FINEID - S5 Directory Specification
 FINEID SPECIFICATION 27.3.2007 FINEID - S5 Directory Specification v 2.2 Population Register Centre (VRK Certification Authority Services P.O. Box 70 FIN-00581 Helsinki Finland http://www.fineid.fi FINEID
FINEID SPECIFICATION 27.3.2007 FINEID - S5 Directory Specification v 2.2 Population Register Centre (VRK Certification Authority Services P.O. Box 70 FIN-00581 Helsinki Finland http://www.fineid.fi FINEID
ISO/IEC INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD ISO/IEC 15945 First edition 2002-02-01 Information technology Security techniques Specification of TTP services to support the application of digital signatures Technologies de l'information
INTERNATIONAL STANDARD ISO/IEC 15945 First edition 2002-02-01 Information technology Security techniques Specification of TTP services to support the application of digital signatures Technologies de l'information
ISO/IEC Information technology Open Systems Interconnection The Directory: Overview of concepts, models and services
 This is a preview - click here to buy the full publication INTERNATIONAL STANDARD ISO/IEC 9594-1 Fifth edition 2005-12-15 Information technology Open Systems Interconnection The Directory: Overview of
This is a preview - click here to buy the full publication INTERNATIONAL STANDARD ISO/IEC 9594-1 Fifth edition 2005-12-15 Information technology Open Systems Interconnection The Directory: Overview of
DirectTrust Governmental Trust Anchor Bundle Standard Operating Procedure
 DirectTrust Governmental Trust Anchor Bundle Standard Operating Procedure Change Control Date Version Description of changes 15-December- 2016 1-December- 2016 17-March- 2016 4-February- 2016 3-February-
DirectTrust Governmental Trust Anchor Bundle Standard Operating Procedure Change Control Date Version Description of changes 15-December- 2016 1-December- 2016 17-March- 2016 4-February- 2016 3-February-
Category: Standards Track June Requesting Attributes by Object Class in the Lightweight Directory Access Protocol (LDAP) Status of This Memo
 Network Working Group K. Zeilenga Request for Comments: 4529 OpenLDAP Foundation Category: Standards Track June 2006 Requesting Attributes by Object Class in the Lightweight Directory Access Protocol (LDAP)
Network Working Group K. Zeilenga Request for Comments: 4529 OpenLDAP Foundation Category: Standards Track June 2006 Requesting Attributes by Object Class in the Lightweight Directory Access Protocol (LDAP)
Some Lessons Learned from Designing the Resource PKI
 Some Lessons Learned from Designing the Resource PKI Geoff Huston Chief Scientist, APNIC May 2007 Address and Routing Security The basic security questions that need to be answered are: Is this a valid
Some Lessons Learned from Designing the Resource PKI Geoff Huston Chief Scientist, APNIC May 2007 Address and Routing Security The basic security questions that need to be answered are: Is this a valid
Machine Readable Travel Documents
 Machine Readable Travel Documents GUIDANCE DOCUMENT PKI for Machine Readable Travel Documents Version -1.0 Date - 22 June, 2011 Pg. 1 of 24 Table of Contents 1 Introduction... 5 2 Structure of the document...
Machine Readable Travel Documents GUIDANCE DOCUMENT PKI for Machine Readable Travel Documents Version -1.0 Date - 22 June, 2011 Pg. 1 of 24 Table of Contents 1 Introduction... 5 2 Structure of the document...
Federal PKI. Trust Store Management Guide
 Federal PKI Trust Store Management Guide V1.0 September 21, 2015 FINAL Disclaimer The Federal PKI Management Authority (FPKIMA) has designed and created the Trust Store Management Guide as an education
Federal PKI Trust Store Management Guide V1.0 September 21, 2015 FINAL Disclaimer The Federal PKI Management Authority (FPKIMA) has designed and created the Trust Store Management Guide as an education
September 1997 Expires March Storing Certificates in the Domain Name System
 September 1997 Expires March 1998 Storing Certificates in the Domain Name System ------- ------------ -- --- ------ ---- ------ Donald E. Eastlake 3rd Olafur Gudmundsson Status of This Document This draft,
September 1997 Expires March 1998 Storing Certificates in the Domain Name System ------- ------------ -- --- ------ ---- ------ Donald E. Eastlake 3rd Olafur Gudmundsson Status of This Document This draft,
TELIA MOBILE ID CERTIFICATE
 Telia Mobile ID Certificate CPS v2.3 1 (56) TELIA MOBILE ID CERTIFICATE CERTIFICATION PRACTICE STATEMENT (Translation from official Finnish version) Version 2.3 Valid from June 30, 2017 Telia Mobile ID
Telia Mobile ID Certificate CPS v2.3 1 (56) TELIA MOBILE ID CERTIFICATE CERTIFICATION PRACTICE STATEMENT (Translation from official Finnish version) Version 2.3 Valid from June 30, 2017 Telia Mobile ID
Expires: 11 October April 2002
 Internet-Draft AAAarch RG Intended Category: Informational David Chadwick University of Salford Expires: 11 October 2002 11 April 2002 The PERMIS X.509 Based Privilege Management Infrastructure
Internet-Draft AAAarch RG Intended Category: Informational David Chadwick University of Salford Expires: 11 October 2002 11 April 2002 The PERMIS X.509 Based Privilege Management Infrastructure
Interagency Advisory Board Meeting Agenda, December 7, 2009
 Interagency Advisory Board Meeting Agenda, December 7, 2009 1. Opening Remarks 2. FICAM Segment Architecture & PIV Issuance (Carol Bales, OMB) 3. ABA Working Group on Identity (Tom Smedinghoff) 4. F/ERO
Interagency Advisory Board Meeting Agenda, December 7, 2009 1. Opening Remarks 2. FICAM Segment Architecture & PIV Issuance (Carol Bales, OMB) 3. ABA Working Group on Identity (Tom Smedinghoff) 4. F/ERO
Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7.
![Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7. Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7.](/thumbs/84/91191448.jpg) Lecture 13 Public Key Distribution (certification) 1 PK-based Needham-Schroeder TTP 1. A, B 4. B, A 2. {PKb, B}SKT B}SKs 5. {PK a, A} SKT SKs A 3. [N a, A] PKb 6. [N a, N b ] PKa B 7. [N b ] PKb Here,
Lecture 13 Public Key Distribution (certification) 1 PK-based Needham-Schroeder TTP 1. A, B 4. B, A 2. {PKb, B}SKT B}SKs 5. {PK a, A} SKT SKs A 3. [N a, A] PKb 6. [N a, N b ] PKa B 7. [N b ] PKb Here,
Internet Engineering Task Force (IETF) Request for Comments: 6818 Updates: 5280 January 2013 Category: Standards Track ISSN:
 Internet Engineering Task Force (IETF) P. Yee Request for Comments: 6818 AKAYLA Updates: 5280 January 2013 Category: Standards Track ISSN: 2070-1721 Abstract Updates to the Internet X.509 Public Key Infrastructure
Internet Engineering Task Force (IETF) P. Yee Request for Comments: 6818 AKAYLA Updates: 5280 January 2013 Category: Standards Track ISSN: 2070-1721 Abstract Updates to the Internet X.509 Public Key Infrastructure
Network Working Group. Category: Experimental December Domain Administrative Data in Lightweight Directory Access Protocol (LDAP)
 Network Working Group A. Newton Request for Comments: 3663 VeriSign, Inc. Category: Experimental December 2003 Status of this Memo Domain Administrative Data in Lightweight Directory Access Protocol (LDAP)
Network Working Group A. Newton Request for Comments: 3663 VeriSign, Inc. Category: Experimental December 2003 Status of this Memo Domain Administrative Data in Lightweight Directory Access Protocol (LDAP)
The X.500 Directory Standard: A Key Component of Identity Management
 The X.500 Directory Standard: Key Component of Identity Management ERIK NDERSEN Erik ndersen is an independent consultant with the company ndersen s L-Service New things generally fascinate people. This
The X.500 Directory Standard: Key Component of Identity Management ERIK NDERSEN Erik ndersen is an independent consultant with the company ndersen s L-Service New things generally fascinate people. This
Cisco VCS Authenticating Devices
 Cisco VCS Authenticating Devices Deployment Guide First Published: May 2011 Last Updated: November 2015 Cisco VCS X8.7 Cisco Systems, Inc. www.cisco.com 2 About Device Authentication Device authentication
Cisco VCS Authenticating Devices Deployment Guide First Published: May 2011 Last Updated: November 2015 Cisco VCS X8.7 Cisco Systems, Inc. www.cisco.com 2 About Device Authentication Device authentication
US Federal PKI Bridge. Ram Banerjee VP Vertical Markets
 US Federal PKI Bridge Ram Banerjee VP Vertical Markets e-gov and PKI Drivers Government Paperwork Elimination and ESIGN Acts Public Expectations Long-term Cost Savings The Need for Privacy and Security
US Federal PKI Bridge Ram Banerjee VP Vertical Markets e-gov and PKI Drivers Government Paperwork Elimination and ESIGN Acts Public Expectations Long-term Cost Savings The Need for Privacy and Security
ISO/IEC INTERNATIONAL STANDARD. Information technology Software asset management Part 2: Software identification tag
 INTERNATIONAL STANDARD ISO/IEC 19770-2 First edition 2009-11-15 Information technology Software asset management Part 2: Software identification tag Technologies de l'information Gestion de biens de logiciel
INTERNATIONAL STANDARD ISO/IEC 19770-2 First edition 2009-11-15 Information technology Software asset management Part 2: Software identification tag Technologies de l'information Gestion de biens de logiciel
SONERA MOBILE ID CERTIFICATE
 Sonera Mobile ID Certificate CPS v2.1 1 (56) SONERA MOBILE ID CERTIFICATE CERTIFICATION PRACTICE STATEMENT (Translation from official Finnish version) Version 2.1 Valid from, domicile: Helsinki, Teollisuuskatu
Sonera Mobile ID Certificate CPS v2.1 1 (56) SONERA MOBILE ID CERTIFICATE CERTIFICATION PRACTICE STATEMENT (Translation from official Finnish version) Version 2.1 Valid from, domicile: Helsinki, Teollisuuskatu
Public Key Infrastructures. Using PKC to solve network security problems
 Public Key Infrastructures Using PKC to solve network security problems Distributing public keys P keys allow parties to share secrets over unprotected channels Extremely useful in an open network: Parties
Public Key Infrastructures Using PKC to solve network security problems Distributing public keys P keys allow parties to share secrets over unprotected channels Extremely useful in an open network: Parties
What is a Digital Certificate? Basic Problem. Digital Certificates, Certification Authorities, and Public Key Infrastructure. Sections
 Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Digital Certificates, Certification Authorities, and Public Key Infrastructure. Sections
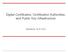 Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Cisco TelePresence Device Authentication on Cisco VCS
 Cisco TelePresence Device Authentication on Cisco VCS Deployment Guide Cisco VCS X8.5 December 2014 Contents About device authentication 4 Authentication policy 6 Configuring VCS authentication policy
Cisco TelePresence Device Authentication on Cisco VCS Deployment Guide Cisco VCS X8.5 December 2014 Contents About device authentication 4 Authentication policy 6 Configuring VCS authentication policy
Network Working Group. S.E. Hardcastle-Kille ISODE Consortium January 1993
 Network Working Group Requests for Comments 1384 P. Barker University College London S.E. Hardcastle-Kille ISODE Consortium January 1993 Status of this Memo Naming Guidelines for Directory Pilots This
Network Working Group Requests for Comments 1384 P. Barker University College London S.E. Hardcastle-Kille ISODE Consortium January 1993 Status of this Memo Naming Guidelines for Directory Pilots This
Canada Education Savings Program
 Version Number: 5.0 Version Date: August 6, 2007 Version History Version Release Date Description R 1.0 September 30, 1998 Initial version for HRSDC internal reviews. D 2.0 March 15, 1999 Ongoing updates.
Version Number: 5.0 Version Date: August 6, 2007 Version History Version Release Date Description R 1.0 September 30, 1998 Initial version for HRSDC internal reviews. D 2.0 March 15, 1999 Ongoing updates.
DRAFT REVISIONS BR DOMAIN VALIDATION
 DRAFT REVISIONS BR 3.2.2.4 DOMAIN VALIDATION (Feb. 15, 2016) Summary of changes The primary purpose of this change is to replace Domain Validation item 7 "Using any other method of confirmation which has
DRAFT REVISIONS BR 3.2.2.4 DOMAIN VALIDATION (Feb. 15, 2016) Summary of changes The primary purpose of this change is to replace Domain Validation item 7 "Using any other method of confirmation which has
PKI Services. Text PKI Definition. PKI Definition #1. Public Key Infrastructure. What Does A PKI Do? Public Key Infrastructures
 Public Key Infrastructures Public Key Infrastructure Definition and Description Functions Components Certificates 1 2 PKI Services Security Between Strangers Encryption Integrity Non-repudiation Key establishment
Public Key Infrastructures Public Key Infrastructure Definition and Description Functions Components Certificates 1 2 PKI Services Security Between Strangers Encryption Integrity Non-repudiation Key establishment
Directory Service. X.500 Directory Service. X.500 Directory Service and Lightweight Directory Access Protocol (LDAP)
 X.500 Directory Service and Lightweight Directory Access Protocol (LDAP) What if we know the names of some object/resource, but want to find out more about them What is the telephone no. of X? What department
X.500 Directory Service and Lightweight Directory Access Protocol (LDAP) What if we know the names of some object/resource, but want to find out more about them What is the telephone no. of X? What department
D. Crocker, Ed. Updates: RFC4871 June 10, 2009 (if approved) Intended status: Standards Track Expires: December 12, 2009
 DKIM D. Crocker, Ed. Internet-Draft Brandenburg InternetWorking Updates: RFC4871 June 10, 2009 (if approved) Intended status: Standards Track Expires: December 12, 2009 RFC 4871 DomainKeys Identified Mail
DKIM D. Crocker, Ed. Internet-Draft Brandenburg InternetWorking Updates: RFC4871 June 10, 2009 (if approved) Intended status: Standards Track Expires: December 12, 2009 RFC 4871 DomainKeys Identified Mail
ISO/IEC INTERNATIONAL STANDARD. Information technology Open Systems Interconnection The Directory Part 5: Protocol specifications
 INTERNATIONAL STANDARD ISO/IEC 9594-5 Seventh edition 2014-03-01 Information technology Open Systems Interconnection The Directory Part 5: Protocol specifications Technologies de l'information Interconnexion
INTERNATIONAL STANDARD ISO/IEC 9594-5 Seventh edition 2014-03-01 Information technology Open Systems Interconnection The Directory Part 5: Protocol specifications Technologies de l'information Interconnexion
IHE Change Proposal. Tracking information: Change Proposal Status: Date of last update: Sep 13, 2018 Charles Parisot, Vassil Peytchev, John Moehrke
 IHE Change Proposal Tracking information: IHE Domain IT Infrastructure Change Proposal ID: CP-ITI-1145 Change Proposal Status: Final Text Date of last update: Sep 13, 2018 Person assigned: Charles Parisot,
IHE Change Proposal Tracking information: IHE Domain IT Infrastructure Change Proposal ID: CP-ITI-1145 Change Proposal Status: Final Text Date of last update: Sep 13, 2018 Person assigned: Charles Parisot,
Validation Policy r tra is g e R ANF AC MALTA, LTD
 Maltese Registrar of Companies Number C75870 and VAT number MT ANF AC MALTA, LTD B2 Industry Street, Qormi, QRM 3000 Malta Telephone: (+356) 2299 3100 Fax:(+356) 2299 3101 Web: www.anfacmalta.com Security
Maltese Registrar of Companies Number C75870 and VAT number MT ANF AC MALTA, LTD B2 Industry Street, Qormi, QRM 3000 Malta Telephone: (+356) 2299 3100 Fax:(+356) 2299 3101 Web: www.anfacmalta.com Security
Part 5: Protocol specifications
 INTERNATIONAL STANDARD ISO/IEC 9594-5 Eighth edition 2017-05 Information technology Open Systems Interconnection The Directory Part 5: Protocol specifications Technologies de l information Interconnexion
INTERNATIONAL STANDARD ISO/IEC 9594-5 Eighth edition 2017-05 Information technology Open Systems Interconnection The Directory Part 5: Protocol specifications Technologies de l information Interconnexion
Request for Comments: 4142 Category: Standards Track Nine by Nine November 2005
 Network Working Group Request for Comments: 4142 Category: Standards Track D. Crocker Brandenburg G. Klyne Nine by Nine November 2005 Status of This Memo Full-mode Fax Profile for Internet Mail (FFPIM)
Network Working Group Request for Comments: 4142 Category: Standards Track D. Crocker Brandenburg G. Klyne Nine by Nine November 2005 Status of This Memo Full-mode Fax Profile for Internet Mail (FFPIM)
Government of Ontario IT Standard (GO ITS) GO-ITS Number 56.3 Information Modeling Standard
 Government of Ontario IT Standard (GO ITS) GO-ITS Number 56.3 Information Modeling Standard Version # : 1.6 Status: Approved Prepared under the delegated authority of the Management Board of Cabinet Queen's
Government of Ontario IT Standard (GO ITS) GO-ITS Number 56.3 Information Modeling Standard Version # : 1.6 Status: Approved Prepared under the delegated authority of the Management Board of Cabinet Queen's
Public Key Establishment
 Public Key Establishment Bart Preneel Katholieke Universiteit Leuven February 2007 Thanks to Paul van Oorschot How to establish public keys? point-to-point on a trusted channel mail business card, phone
Public Key Establishment Bart Preneel Katholieke Universiteit Leuven February 2007 Thanks to Paul van Oorschot How to establish public keys? point-to-point on a trusted channel mail business card, phone
SERIES X: DATA NETWORKS, OPEN SYSTEM COMMUNICATIONS AND SECURITY Directory
 International Telecommunication Union ITU-T X.500 TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU (11/2008) SERIES X: DATA NETWORKS, OPEN SYSTEM COMMUNICATIONS AND SECURITY Directory Information technology
International Telecommunication Union ITU-T X.500 TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU (11/2008) SERIES X: DATA NETWORKS, OPEN SYSTEM COMMUNICATIONS AND SECURITY Directory Information technology
PKI and FICAM Overview and Outlook
 PKI and FICAM Overview and Outlook Stepping Stones 2001 FPKIPA Established Federal Bridge CA established 2003 E-Authentication Program Established M-04-04 E-Authentication Guidance for Federal Agencies
PKI and FICAM Overview and Outlook Stepping Stones 2001 FPKIPA Established Federal Bridge CA established 2003 E-Authentication Program Established M-04-04 E-Authentication Guidance for Federal Agencies
Configuring a Virtual-Domain Server with LDAP
 This document provides a recipe for configuring a Mirapoint server to perform LDAP authentication, message routing, and email access proxying. Configuration requires two activities: LDAP Database User
This document provides a recipe for configuring a Mirapoint server to perform LDAP authentication, message routing, and email access proxying. Configuration requires two activities: LDAP Database User
Certificates, Certification Authorities and Public-Key Infrastructures
 (Digital) Certificates Certificates, Certification Authorities and Public-Key Infrastructures We need to be sure that the public key used to encrypt a message indeed belongs to the destination of the message
(Digital) Certificates Certificates, Certification Authorities and Public-Key Infrastructures We need to be sure that the public key used to encrypt a message indeed belongs to the destination of the message
Security Protocols and Infrastructures. Winter Term 2015/2016
 Security Protocols and Infrastructures Winter Term 2015/2016 Nicolas Buchmann (Harald Baier) Chapter 5: Standards for Security Infrastructures Contents Introduction and naming scheme X.509 and its core
Security Protocols and Infrastructures Winter Term 2015/2016 Nicolas Buchmann (Harald Baier) Chapter 5: Standards for Security Infrastructures Contents Introduction and naming scheme X.509 and its core
INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD This is a preview - click here to buy the full publication ISO/IEC 9594-8 Eighth edition 2017-05 Information technology Open Systems Interconnection The Directory Part 8: frameworks
INTERNATIONAL STANDARD This is a preview - click here to buy the full publication ISO/IEC 9594-8 Eighth edition 2017-05 Information technology Open Systems Interconnection The Directory Part 8: frameworks
ING Public Key Infrastructure Technical Certificate Policy
 ING Public Key Infrastructure Technical Certificate Policy Version 5.4 - November 2015 Commissioned by ING PKI Policy Approval Authority (PAA) Additional copies Document version General Of this document
ING Public Key Infrastructure Technical Certificate Policy Version 5.4 - November 2015 Commissioned by ING PKI Policy Approval Authority (PAA) Additional copies Document version General Of this document
Server-based Certificate Validation Protocol
 Server-based Certificate Validation Protocol Digital Certificate and PKI a public-key certificate is a digital certificate that binds a system entity's identity to a public key value, and possibly to additional
Server-based Certificate Validation Protocol Digital Certificate and PKI a public-key certificate is a digital certificate that binds a system entity's identity to a public key value, and possibly to additional
CERTIFICATE POLICY CIGNA PKI Certificates
 CERTIFICATE POLICY CIGNA PKI Certificates Version: 1.1 Effective Date: August 7, 2001 a Copyright 2001 CIGNA 1. Introduction...3 1.1 Important Note for Relying Parties... 3 1.2 Policy Identification...
CERTIFICATE POLICY CIGNA PKI Certificates Version: 1.1 Effective Date: August 7, 2001 a Copyright 2001 CIGNA 1. Introduction...3 1.1 Important Note for Relying Parties... 3 1.2 Policy Identification...
Internet Engineering Task Force (IETF) Request for Comments: 6403 Category: Informational ISSN: M. Peck November 2011
 Internet Engineering Task Force (IETF) Request for Comments: 6403 Category: Informational ISSN: 2070-1721 L. Zieglar NSA S. Turner IECA M. Peck November 2011 Suite B Profile of Certificate Management over
Internet Engineering Task Force (IETF) Request for Comments: 6403 Category: Informational ISSN: 2070-1721 L. Zieglar NSA S. Turner IECA M. Peck November 2011 Suite B Profile of Certificate Management over
DECISION OF THE EUROPEAN CENTRAL BANK
 L 74/30 Official Journal of the European Union 16.3.2013 DECISIONS DECISION OF THE EUROPEAN CENTRAL BANK of 11 January 2013 laying down the framework for a public key infrastructure for the European System
L 74/30 Official Journal of the European Union 16.3.2013 DECISIONS DECISION OF THE EUROPEAN CENTRAL BANK of 11 January 2013 laying down the framework for a public key infrastructure for the European System
Security Protocols and Infrastructures
 Security Protocols and Infrastructures Dr. Michael Schneider michael.schneider@h-da.de Chapter 5: Standards for Security Infrastructures November 13, 2017 h_da WS2017/18 Dr. Michael Schneider 1 1 Introduction
Security Protocols and Infrastructures Dr. Michael Schneider michael.schneider@h-da.de Chapter 5: Standards for Security Infrastructures November 13, 2017 h_da WS2017/18 Dr. Michael Schneider 1 1 Introduction
Report: EDUCAUSE NIH PKI Interoperability Pilot Project
 Report: EDUCAUSE NIH PKI Interoperability Pilot Project Peter Alterman, Russel Weiser, Michael Gettes, Kenneth Stillson, Deborah Blanchard, James Fisher, Robert Brentrup, Eric Norman Background Under mandate
Report: EDUCAUSE NIH PKI Interoperability Pilot Project Peter Alterman, Russel Weiser, Michael Gettes, Kenneth Stillson, Deborah Blanchard, James Fisher, Robert Brentrup, Eric Norman Background Under mandate
FPKIPA CPWG Antecedent, In-Person Task Group
 FBCA Supplementary Antecedent, In-Person Definition This supplement provides clarification on the trust relationship between the Trusted Agent and the applicant, which is based on an in-person antecedent
FBCA Supplementary Antecedent, In-Person Definition This supplement provides clarification on the trust relationship between the Trusted Agent and the applicant, which is based on an in-person antecedent
A PKI For IDR Public Key Infrastructure and Number Resource Certification
 A PKI For IDR Public Key Infrastructure and Number Resource Certification AUSCERT 2006 Geoff Huston Research Scientist APNIC If You wanted to be Bad on the Internet And you wanted to: Hijack a site Inspect
A PKI For IDR Public Key Infrastructure and Number Resource Certification AUSCERT 2006 Geoff Huston Research Scientist APNIC If You wanted to be Bad on the Internet And you wanted to: Hijack a site Inspect
Draft ETSI EN V ( )
 Draft EN 319 412-2 V2.0.15 (2015-06) EUROPEAN STANDARD Electronic Signatures and Infrastructures (ESI); Certificate Profiles; Part 2: Certificate profile for certificates issued to natural persons 2 Draft
Draft EN 319 412-2 V2.0.15 (2015-06) EUROPEAN STANDARD Electronic Signatures and Infrastructures (ESI); Certificate Profiles; Part 2: Certificate profile for certificates issued to natural persons 2 Draft
Lecture 15 Public Key Distribution (certification)
 0 < i < 2 n = N X i,y i random secret keys index i = random (secret) value Merkle s Puzzles (1974) Puzzle P i = {index i,x i,s} Y i S fixed string, e.g., " Alice to Bob" { P 0 < i < 2 i n } Pick random
0 < i < 2 n = N X i,y i random secret keys index i = random (secret) value Merkle s Puzzles (1974) Puzzle P i = {index i,x i,s} Y i S fixed string, e.g., " Alice to Bob" { P 0 < i < 2 i n } Pick random
Introduction to Network Security Missouri S&T University CPE 5420 Key Management and Distribution
 Introduction to Network Security Missouri S&T University CPE 5420 Key Management and Distribution Egemen K. Çetinkaya Egemen K. Çetinkaya Department of Electrical & Computer Engineering Missouri University
Introduction to Network Security Missouri S&T University CPE 5420 Key Management and Distribution Egemen K. Çetinkaya Egemen K. Çetinkaya Department of Electrical & Computer Engineering Missouri University
Send and Receive Exchange Use Case Test Methods
 Send and Receive Exchange Use Case Test Methods Release 1 Version 1.0 October 1, 2017 Send and Receive Exchange Test Methods Release 1 Version 1.0 Technology Sponsor [Name] [Email] [Telephone] Signature
Send and Receive Exchange Use Case Test Methods Release 1 Version 1.0 October 1, 2017 Send and Receive Exchange Test Methods Release 1 Version 1.0 Technology Sponsor [Name] [Email] [Telephone] Signature
RFC 4871 DomainKeys Identified Mail (DKIM) Signatures -- Update draft-ietf-dkim-rfc4871-errata-03-01dc
 Network Working Group D. Crocker, Editor Internet Draft Brandenburg InternetWorking April 2, 2009 Updates: RFC4871 (if approved) Intended status: Standards Track
Network Working Group D. Crocker, Editor Internet Draft Brandenburg InternetWorking April 2, 2009 Updates: RFC4871 (if approved) Intended status: Standards Track
Higher Education PKI Initiatives
 Higher Education PKI Initiatives (Scott Rea) Securing the ecampus - Hanover NH July 28, 2009 Overview What are the drivers for PKI in Higher Education? Stronger authentication to resources and services
Higher Education PKI Initiatives (Scott Rea) Securing the ecampus - Hanover NH July 28, 2009 Overview What are the drivers for PKI in Higher Education? Stronger authentication to resources and services
