our ideas of graph search technique reported
|
|
|
- Gloria Walsh
- 5 years ago
- Views:
Transcription
1 DETECTING TERMINATION OF DISTRIBUTED COMPUTATIONS BY EXTERNAL AGENTS ABSTMCT This paper presents an algorithm for detecting termination of distributed computations by an auxiliary controlling agent. The algorithm assigns a weight to each active process and to each message in transit. The controlling agent has a weight, too. The algorithm maintains an invariant that the sum of all the weights related to a computation is equal to one. The controlling agent concludes the termination when its weight equals one. A space-efficient scheme is proposed to encode the weights such that an active process can send a very lar e number of messages without running out o f the weight. 1. Introduction. The termination detection problem for distributed computations has attracted considerable interest [1-6,8-9,111 over the past years since the works of Dijkstra and Scholten [a], and Francez [4]. In our discussion, a distributed computation consists of a set of processes, which communicate with one another via message passing. Each process may be either active or idle. An active process may become idle at any time. Only active processes may send messages to others; and, an idle process can only be reactivated by receiving a message. The computation is This work is supported in part by ATC, ERSO, Industrial Technology Institute of the Republic of China under the Contract SF-C-010-1, and the National Science Council of the Republic of China under the Contract NS C EO Shing-Tsaan Huang Institute of Computer Science National Tsing-Hua University HsinChu, Taiwan (30043)) R.O.C. said to be terminated iff all the processes are idle and there is no message in transit. This paper presents an algorithm for the termination detection problem under the following assumptions. A controlling agent monitors the computation. A logical communication channel exists between each process pair and between the controlling agent and each of the processes. Messages from a sender to a receiver are correctly received by the receiver in an order not necessary the same as the sending order. Message delay is arbitrary but finite. The presented algorithm can be easily extended to work on distributed systems with dynamic nature [8,10] in the sense that the processes may be created, destroyed, or migrated from one processing element to another. The algorithm is modified from the algorithm by Rokusawa, Ichiyoshi, Chikayama, and Nakashima [lo] by applying our ideas of graph search technique reported in [7]. Adopting the weighted throw counting scheme used in their algorithm, our algorith~n assigns a weight to each active process and to each message in transit. The controlling agent maintains a weight, too. For each weight W, we let 0 < W < 1. The a1 orithm maintains an invariant that the sum o! all the weights related to the computation is equal to one. The controlling agent concludes termination if its weight equals one. A space-efficient scheme is proposed to encode the weights such that an active process can send a large number of messages without running out of the weight, and hence avoid requiring additional weight from the controlling agent. CH2706-0/89/0000/0079$ IEEE 19
2 We have organized the rest of the paper as follows. The algorithm and its correctness are discussed in Section 2. Then, the encoding'scheme is presented in Section 3. Historic remarks of the works in [7,10] are provided in Section 4. Finally, a summary is given in Section The algorithm and its correctness. Besides the messages for the computation, which we call basic messages, there are messages from the processes to the controlling agent for the purpose of termination detection which are called control messages. The controlling agent and each of the processes maintain a variable W for its weight. Basic messages are denoted as and control messages are denoted as 3;q, where DW is a parameter of the weight. At the beginning, all the processes are idle with their weights having value zero, and the weight of the controlling agent equals one. The computation starts when the controlling agent sends a basic message to one of the processes. The algorithm consists of the following rules. In the rules, we assume that a weight is infinitely divisible. The implementation of such weights is discussed in the next section. R1: The controlling agent or an active process may send a basic message to one of the processes, say p, at any time by doing: Derive W1 and W2 such that ( W1 + W2 = W), ( W1 > 0), and (W2 > 0); Let W:= W1; Send a i(dw:= W2) to p. R2: Upon receiving a B(DW), a process p does: Let W:= W+DW; R3: R4: (If p is idle, p is reactivated.) An active process may become idle at any time by doing: Send a C(DW:= W) to the controlling agent; Let W:= 0; (The process becomes idle.) Upon receiving a c(dw), the controlling agent does: Let W:= W+ OW; If W = 1, the computation is terminated. The correctness reasoning of the algorithm is as follows. Let us define the following sets first. A the set of all the Ws on active processes. B: the set of all the Ws on basic messages in transit. C. the set of all the Ws on control messages in transit. Also, let us denote the Won the controlling agent as Wc. The following P1 and P2 are invariants. W= 1. pl: Wc + %E (A U BU c) P2:V WE(AUBUC), W>O. Hence, wc = 1 LbY P1) WE(AUBUc) [ZGy = 4) W=O The computation is terminated. That is, the algorithm never detects a false termination. Further, AUB)=(b [by P1) 80
3 Wc + EWE c W= 1 (Message delay is finite.) Eventually, Wc = 1. That is, the algorithm detects every true termination in finite time. We have presented an algorithm for the termination detection on distributed computations. With the assumption that a weight is infinitely divisible, the algorithm can be easily extended to work on distributed systems with dynamic nature. In a dynamic system, an active process may spawn another active process or migrate from one processing element to another. We can let an active process create another active process by splitting its weight into two parts, keeping one part as its new weight, and assigning the other part as the weight of the spawned process. Migration of the processes won't cause any problem provided that only active processes are allowed to migrate. However, the maximum number of co-existing active processes is bounded in an actual implementation. We shall readdress this further after the implementation of the weights is discussed. 3. The implementation of the weights. In this section, we present a space-efficient scheme to encode the weights. Except Wc, the weight on the controlling agent, all the other weight Wis encoded in a small number of bits, yet it behaves as if it were infinitely divisible. We may represent the Was a binar number in an unbounded array of bits wit the binary point before the first bit. That is, the array (100...) has a binary value or a decimal value 0.5. By doing this, W1 and W2 in rule R1 are always available. For example, let W= ( ), we can have W1 = ( ) and W2 = ( ). The computation may start when the controlling agent lets its Wc := (100...) and sends a basic message B(DW := (loo...)) to one of the 3: processes. The termination is detected when Wc has a carry from the addition in rule R4. In this way, at the beginnin one bit is sufficient to encode the weig fi t. As the computation proceeds, we may need more bits to encode the weights, and the number of bits needed might not be affordable for the processes to maintain or the messages to carry. In the following, we present a spaceefficient scheme to handle this problem. In the scheme, the controlling agent preserves an array of a sufficiently large number of bits to encode Wc. The array is evenly divided into window slots. Each other weight W on an active process or on any message in transit is represented by (...)i, where (...) is a window of bits and the subscript i is its corresponding slot number. For each W= (...)i, it is assumed that all the bits in windows other than slot i have value 0. This is similar to a floating-point encoding scheme, in which the number of leading zeros is stored rather than the zero's themselves. When an active process has weight W = (0... Ol)* and wants to send a basic message, it can slide the window to the right one slot position, or let i := i + 1, and then split its weight into two non-zero parts, keeping one part as its new weight and sending the other as the weight of the message. For example, a process can split (O...O1)o into (l...ll)l and (O...O1)l, then keep (l...ll)l as its new weight and assign (O...O1)l as the weight of the message. An active process may have two weights according to rule R2, one from itself and the other from a received basic message. If the sum of the two weights can not be fitted into a single window slot, we let the process keep the window with smaller slot number and send the other to the controlling agent. For example, when an active process having weight = (...)3 receives another weight = (...)l, we let it keep the weight and send (...)3 to the controlling agent. 81
4 The above scheme makes possible for each process to maintain only a few bits, and each message to carry the same number of bits. For example, let H be the array size of Wc and h be the window size. If h = 16, and H = 1024h, we need 26 bits to represent the W, among them 10 bits are for the slot number because 21 = 1024, and 16 bits are for the window itself. Only the weight Wc of the controlling agent then needs bit computer words. When an active process has its slot number reaching the upper limit, it can split its weight into two parts, keep one part as its new wei ht and send the other as a request for supply o B weight to the controlling agent. The weight on a request message can be of the form ( )$ Upon receiving such a request with weight (O...O1)i, the controlling agent then sends a supply of weight ( ) with j 1 < i, to the requester, or postpones the sending of the supply until it is able to do so. When an active process receives a supply, the situation is similar to what described in the paragraph before the last paragraph, and similar actions can be followed by the process. When an idle process receives a supply, it simply rebounds the weight to the controlling agent. By enlarging H, the requests for supply of weight can be eliminated. In a dynamic system, the fact that Wc is bounded by H also has its effects on the maximum number of active processes that can co-exist at any time. With H = 2, for example, the maximum number of co-existing active processes is 4 because in such a case, the minimum possible weight for each active process is binary value 0.01 and the sum of their weights is equal to one. We have presented a space-e ficient scheme to encode the weights. This scheme maintains a very large resource pool in the controlling agent which is shared by all the processes with each having only a small amount of memory space. This ideas should be interesting to the community of researchers studying resource sharing problems. 4. IIistoric Remarks. The presented algorithm applies the ideas of the graph searching technique reported in [7] on the weighted throw counting scheme discussed in [lo]. In searching a graph with logical edges, the searching can start from a root with a weight of one. The root sends a token T(DW := 1/ I NSI) to each of its neighbors. We use NS to denote the set of the neighbors of a node. Upon receiving a token T(DW) for the first time, a node sends a token T(DW := DW/(INSI-l)) to each of its neighbors except the one from which the token is received. For a revisited token T(DW), a node sends a T(DW) to the root. A sink node, a node with only one neighbor, sends a to the root upon receiving a token qzj. The root detects the termination of the searching when the sum of the weights on all the returned tokens equals one. This search technique assumes that a weight is infinitely divisible. Although different formulation and terminology are used, the termination detection dealt with in the algorithm reported in [lo] is similar to the one.discussed in this paper. However, in [lo], the weights are integer numbers; since no special encoding scheme is used, each activated process almost always needs to request for supply of weight. As discussed in (101, let us have the following weight assignment strategy: Assign a fixed weight 21 to a basic message if the weight of the sender is more than twice of that; otherwise assign half of its weight. Then, an active process which is reactivated by receiving a basic message with a weight of 2 10 can only send 10 basic messages. In our proposed scheme, however, by sliding the window to the right, the effect is receiving a supply of a very large weight from the controlling agent. For instance, let H = 1024h, and h = 16. Then, by sliding the window one slot position, a process can send an additional 2 16 basic messages. The computation can go into a depth of 1024 levels without any request messages, and hence, the processes are free 82
5 from experiencing any delays waiting for supply messages. The memory cost for each process and message is 26 bits only. The major disadvantage of the scheme is that in rule R2 the sum of the two weights may not be able to be fitted into a single window of bits, hence an extra control message is needed. However, the advantage of the freedom of the processes from waiting for supply messages should be regarded as more important. Further, in some applications, sending basic messages to an active process can be avoided. For example, in the discussed graph searching computation, a process (node) goes active upon receiving the token, and goes idle immediately after sending out the tokens to its neighbors; therefore, no token is sent to an active process. 5. summary. We have presented a termination detection algorithm for distributed computations and. proposed a space-efficient encoding scheme to implement the ideas that logically a weight can be infinitely divisible. The algorithm is modified from the one proposed by Rokusawa, et al. [lo], and borrows the ideas from our other article [7]. Using our encoding scheme, each process and message need a small number of bits to encode the weight, and the processes can almost be free from the delays waiting for supply of weights from the controlling agent. Since a termination detection algorithm should do the best to avoid bothering the computation, having an active process waiting for control messages is not desirable. And, the detecting delay, the period from the computation terminates until the controlling agent detects the termination, should be kept as less as possible. Further, the number of control messages sent should be as small as possible. The presented algorithm is almost optimal in these aspects. With a large enough H, the processes won't receive any control messages. It takes only one message delay, from the latest idled process to the controlling agent, to detect the termination. And, for every basic message, at most one control message is required for the case that the sum of the weights in rule R2 can not be fitted into a single window of bits. Finally, only one control message is needed for each idleness of the processes. ACKNOWLEDGMENT The author would like to thank the anonymous referees for their helpful comments and suggestions. References Dijkstra, E. W., Feijen, W. H. J., and van Gasteren, A. J. M. Derivation of a Termination Detection Algorithm for Distributed Computations. In form. Processing Lett., Vol. 16, pp , June Dijkstra, E. W. and Scholten, C. S. Termination Detection for Distributed Computations. In form. Processing Lett., Vol. 11, pp. 14, Aug Eriksen, 0. A Termination Detection Protocol and Its Formal Verification. J. Parallel and D.istributed Computing 5, pp , Francez, N. Distributed Termination. ACM Trans. Program. Lung. Syst., Vol. 2, pp , Jan Francez, N. and Rodeh, M. Achieving Distributed Termination without Freezing. IEEE Trans. Sojtware Engrg., Vol. 8, pp , Mar Huang, S-T. A Fully Distributed Termination Detection Scheme. Inform. Processing Lett. Vol. 29, pp , Sept A distributed deadlock detection algorithm for CSP style programs. TR-H7601, Inst. of Computer Science, Tsing-Hua University, Feb. 1987, submitted for publication, under revision. Lai, T-H. Termination Detection for Dynamically Distributed Systems with Non-fi r s t-in-fi rs t-ou t Communication. J. Parallel and Distributed Computing 3, pp , Ftana, S. P. A Distributed Solution to the Distributed Termination Problem. 83
6 Inform. Processing Lett., Vol. 17, pp. 4346, July [lo] Rokusawa, K., Ichiyoshi, N., Chikayama, T. and Nakashima, H. An efficient termination detection and abortion algorithm for distributed processing systems. Proc Int'l Conj Parallel Processing, pp , [ll] Topor, R. W. Termination Detection for Distributed Computations. Inform. Processing Lett., Vol. 18, pp , Jan
Abstract DETECTING TERMINATION OF DISTRIBUTED COMPUTATIONS USING MARKERS
 DETECTING TERMINATION OF DISTRIBUTED COMPUTATIONS USING MARKERS Jayadev Misra Department of Computer Sciences, University of Texas, Austin, 78712 Abstract A problem of considerable importance in designing
DETECTING TERMINATION OF DISTRIBUTED COMPUTATIONS USING MARKERS Jayadev Misra Department of Computer Sciences, University of Texas, Austin, 78712 Abstract A problem of considerable importance in designing
Formal Specification and Analysis of Termination Detection by Weight-throwing Protocol
 Formal Specification and Analysis of Termination Detection by Weight-throwing Protocol Imran Riaz Hasrat, Muhammad Atif Department of Computer Science and Information Technology The University of Lahore
Formal Specification and Analysis of Termination Detection by Weight-throwing Protocol Imran Riaz Hasrat, Muhammad Atif Department of Computer Science and Information Technology The University of Lahore
AN EFFICIENT DEADLOCK DETECTION AND RESOLUTION ALGORITHM FOR GENERALIZED DEADLOCKS. Wei Lu, Chengkai Yu, Weiwei Xing, Xiaoping Che and Yong Yang
 International Journal of Innovative Computing, Information and Control ICIC International c 2017 ISSN 1349-4198 Volume 13, Number 2, April 2017 pp. 703 710 AN EFFICIENT DEADLOCK DETECTION AND RESOLUTION
International Journal of Innovative Computing, Information and Control ICIC International c 2017 ISSN 1349-4198 Volume 13, Number 2, April 2017 pp. 703 710 AN EFFICIENT DEADLOCK DETECTION AND RESOLUTION
RECENTLY, researches on gigabit wireless personal area
 146 IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS II: EXPRESS BRIEFS, VOL. 55, NO. 2, FEBRUARY 2008 An Indexed-Scaling Pipelined FFT Processor for OFDM-Based WPAN Applications Yuan Chen, Student Member, IEEE,
146 IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS II: EXPRESS BRIEFS, VOL. 55, NO. 2, FEBRUARY 2008 An Indexed-Scaling Pipelined FFT Processor for OFDM-Based WPAN Applications Yuan Chen, Student Member, IEEE,
Splitter Placement in All-Optical WDM Networks
 plitter Placement in All-Optical WDM Networks Hwa-Chun Lin Department of Computer cience National Tsing Hua University Hsinchu 3003, TAIWAN heng-wei Wang Institute of Communications Engineering National
plitter Placement in All-Optical WDM Networks Hwa-Chun Lin Department of Computer cience National Tsing Hua University Hsinchu 3003, TAIWAN heng-wei Wang Institute of Communications Engineering National
Inst: Chris Davison
 ICS 153 Introduction to Computer Networks Inst: Chris Davison cbdaviso@uci.edu ICS 153 Data Link Layer Contents Simplex and Duplex Communication Frame Creation Flow Control Error Control Performance of
ICS 153 Introduction to Computer Networks Inst: Chris Davison cbdaviso@uci.edu ICS 153 Data Link Layer Contents Simplex and Duplex Communication Frame Creation Flow Control Error Control Performance of
Speed-up of Parallel Processing of Divisible Loads on k-dimensional Meshes and Tori
 The Computer Journal, 46(6, c British Computer Society 2003; all rights reserved Speed-up of Parallel Processing of Divisible Loads on k-dimensional Meshes Tori KEQIN LI Department of Computer Science,
The Computer Journal, 46(6, c British Computer Society 2003; all rights reserved Speed-up of Parallel Processing of Divisible Loads on k-dimensional Meshes Tori KEQIN LI Department of Computer Science,
Node 1. m1 5 m7. token
 An Optimal Termination Detection Algorithm for Rings Murat Demirbas Anish Arora Department of Computer and Information Science The Ohio State University Columbus, Ohio 432 USA Abstract This paper presents
An Optimal Termination Detection Algorithm for Rings Murat Demirbas Anish Arora Department of Computer and Information Science The Ohio State University Columbus, Ohio 432 USA Abstract This paper presents
The alternator. Mohamed G. Gouda F. Furman Haddix
 Distrib. Comput. (2007) 20:21 28 DOI 10.1007/s00446-007-0033-1 The alternator Mohamed G. Gouda F. Furman Haddix Received: 28 August 1999 / Accepted: 5 July 2000 / Published online: 12 June 2007 Springer-Verlag
Distrib. Comput. (2007) 20:21 28 DOI 10.1007/s00446-007-0033-1 The alternator Mohamed G. Gouda F. Furman Haddix Received: 28 August 1999 / Accepted: 5 July 2000 / Published online: 12 June 2007 Springer-Verlag
Distributed Snapshots: Determining Global States of Distributed Systems
 Distributed Snapshots: Determining Global States of Distributed Systems K. MANI CHANDY University of Texas at Austin and LESLIE LAMPORT Stanford Research Institute This paper presents an algorithm by which
Distributed Snapshots: Determining Global States of Distributed Systems K. MANI CHANDY University of Texas at Austin and LESLIE LAMPORT Stanford Research Institute This paper presents an algorithm by which
Conflict-Free Sorting Algorithms under Single-Channel and Multi-Channel Broadcast Communication Models***
 Conflict-Free Sorting Algorithms under Single-Channel and Multi-Channel Broadcast Communication Models*** Chang-Biau Yang*, R. C. T. Lee** and Wen-Tsuen Chen** * Department of Applied Mathematics, National
Conflict-Free Sorting Algorithms under Single-Channel and Multi-Channel Broadcast Communication Models*** Chang-Biau Yang*, R. C. T. Lee** and Wen-Tsuen Chen** * Department of Applied Mathematics, National
Verification of Bakery algorithm variants for two processes
 Verification of Bakery algorithm variants for two processes David Dedi 1, Robert Meolic 2 1 Nova Vizija d.o.o., Vreerjeva ulica 8, SI-3310 Žalec 2 Faculty of Electrical Engineering and Computer Science,
Verification of Bakery algorithm variants for two processes David Dedi 1, Robert Meolic 2 1 Nova Vizija d.o.o., Vreerjeva ulica 8, SI-3310 Žalec 2 Faculty of Electrical Engineering and Computer Science,
ARELAY network consists of a pair of source and destination
 158 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 55, NO 1, JANUARY 2009 Parity Forwarding for Multiple-Relay Networks Peyman Razaghi, Student Member, IEEE, Wei Yu, Senior Member, IEEE Abstract This paper
158 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 55, NO 1, JANUARY 2009 Parity Forwarding for Multiple-Relay Networks Peyman Razaghi, Student Member, IEEE, Wei Yu, Senior Member, IEEE Abstract This paper
An Anonymous Self-Stabilizing Algorithm For 1-Maximal Matching in Trees
 An Anonymous Self-Stabilizing Algorithm For 1-Maximal Matching in Trees Wayne Goddard, Stephen T. Hedetniemi Department of Computer Science, Clemson University {goddard,hedet}@cs.clemson.edu Zhengnan Shi
An Anonymous Self-Stabilizing Algorithm For 1-Maximal Matching in Trees Wayne Goddard, Stephen T. Hedetniemi Department of Computer Science, Clemson University {goddard,hedet}@cs.clemson.edu Zhengnan Shi
K 4,4 e Has No Finite Planar Cover
 K 4,4 e Has No Finite Planar Cover Petr Hliněný Dept. of Applied Mathematics, Charles University, Malostr. nám. 25, 118 00 Praha 1, Czech republic (E-mail: hlineny@kam.ms.mff.cuni.cz) February 9, 2005
K 4,4 e Has No Finite Planar Cover Petr Hliněný Dept. of Applied Mathematics, Charles University, Malostr. nám. 25, 118 00 Praha 1, Czech republic (E-mail: hlineny@kam.ms.mff.cuni.cz) February 9, 2005
Bindel, Fall 2016 Matrix Computations (CS 6210) Notes for
 1 Logistics Notes for 2016-09-07 1. We are still at 50. If you are still waiting and are not interested in knowing if a slot frees up, let me know. 2. There is a correction to HW 1, problem 4; the condition
1 Logistics Notes for 2016-09-07 1. We are still at 50. If you are still waiting and are not interested in knowing if a slot frees up, let me know. 2. There is a correction to HW 1, problem 4; the condition
Embedding Large Complete Binary Trees in Hypercubes with Load Balancing
 JOURNAL OF PARALLEL AND DISTRIBUTED COMPUTING 35, 104 109 (1996) ARTICLE NO. 0073 Embedding Large Complete Binary Trees in Hypercubes with Load Balancing KEMAL EFE Center for Advanced Computer Studies,
JOURNAL OF PARALLEL AND DISTRIBUTED COMPUTING 35, 104 109 (1996) ARTICLE NO. 0073 Embedding Large Complete Binary Trees in Hypercubes with Load Balancing KEMAL EFE Center for Advanced Computer Studies,
Fault-Tolerant Wormhole Routing Algorithms in Meshes in the Presence of Concave Faults
 Fault-Tolerant Wormhole Routing Algorithms in Meshes in the Presence of Concave Faults Seungjin Park Jong-Hoon Youn Bella Bose Dept. of Computer Science Dept. of Computer Science Dept. of Computer Science
Fault-Tolerant Wormhole Routing Algorithms in Meshes in the Presence of Concave Faults Seungjin Park Jong-Hoon Youn Bella Bose Dept. of Computer Science Dept. of Computer Science Dept. of Computer Science
Multipliers: etc. c loo IO Digits: 2 3 ; 7 ones plus 7x l= 7 3 tens plus 3x lo= 30 2 one hundreds 2 x 100 = 200 Total 237
 BINARY NUMBER SYSTEM 4 An understanding of the binary number system is necessary before proceeding with a further examination of LGP-21 programming concepts. Each digit of a decimal number has a multiplier
BINARY NUMBER SYSTEM 4 An understanding of the binary number system is necessary before proceeding with a further examination of LGP-21 programming concepts. Each digit of a decimal number has a multiplier
Cardinality of Sets MAT231. Fall Transition to Higher Mathematics. MAT231 (Transition to Higher Math) Cardinality of Sets Fall / 15
 Cardinality of Sets MAT Transition to Higher Mathematics Fall 0 MAT (Transition to Higher Math) Cardinality of Sets Fall 0 / Outline Sets with Equal Cardinality Countable and Uncountable Sets MAT (Transition
Cardinality of Sets MAT Transition to Higher Mathematics Fall 0 MAT (Transition to Higher Math) Cardinality of Sets Fall 0 / Outline Sets with Equal Cardinality Countable and Uncountable Sets MAT (Transition
Multiway Blockwise In-place Merging
 Multiway Blockwise In-place Merging Viliam Geffert and Jozef Gajdoš Institute of Computer Science, P.J.Šafárik University, Faculty of Science Jesenná 5, 041 54 Košice, Slovak Republic viliam.geffert@upjs.sk,
Multiway Blockwise In-place Merging Viliam Geffert and Jozef Gajdoš Institute of Computer Science, P.J.Šafárik University, Faculty of Science Jesenná 5, 041 54 Košice, Slovak Republic viliam.geffert@upjs.sk,
An Efficient Silent Self-Stabilizing Algorithm for 1-Maximal Matching in Anonymous Network
 An Efficient Silent Self-Stabilizing Algorithm for 1-Maximal Matching in Anonymous Network Yuma Asada and Michiko Inoue Nara Institute of Science and Technology, 8916-5 Takayama, Ikoma, NARA 630-0192 JAPAN,
An Efficient Silent Self-Stabilizing Algorithm for 1-Maximal Matching in Anonymous Network Yuma Asada and Michiko Inoue Nara Institute of Science and Technology, 8916-5 Takayama, Ikoma, NARA 630-0192 JAPAN,
Expectation and Maximization Algorithm for Estimating Parameters of a Simple Partial Erasure Model
 608 IEEE TRANSACTIONS ON MAGNETICS, VOL. 39, NO. 1, JANUARY 2003 Expectation and Maximization Algorithm for Estimating Parameters of a Simple Partial Erasure Model Tsai-Sheng Kao and Mu-Huo Cheng Abstract
608 IEEE TRANSACTIONS ON MAGNETICS, VOL. 39, NO. 1, JANUARY 2003 Expectation and Maximization Algorithm for Estimating Parameters of a Simple Partial Erasure Model Tsai-Sheng Kao and Mu-Huo Cheng Abstract
Fault-Tolerant Routing Algorithm in Meshes with Solid Faults
 Fault-Tolerant Routing Algorithm in Meshes with Solid Faults Jong-Hoon Youn Bella Bose Seungjin Park Dept. of Computer Science Dept. of Computer Science Dept. of Computer Science Oregon State University
Fault-Tolerant Routing Algorithm in Meshes with Solid Faults Jong-Hoon Youn Bella Bose Seungjin Park Dept. of Computer Science Dept. of Computer Science Dept. of Computer Science Oregon State University
in this web service Cambridge University Press
 978-0-51-85748- - Switching and Finite Automata Theory, Third Edition Part 1 Preliminaries 978-0-51-85748- - Switching and Finite Automata Theory, Third Edition CHAPTER 1 Number systems and codes This
978-0-51-85748- - Switching and Finite Automata Theory, Third Edition Part 1 Preliminaries 978-0-51-85748- - Switching and Finite Automata Theory, Third Edition CHAPTER 1 Number systems and codes This
Deduction and Logic Implementation of the Fractal Scan Algorithm
 Deduction and Logic Implementation of the Fractal Scan Algorithm Zhangjin Chen, Feng Ran, Zheming Jin Microelectronic R&D center, Shanghai University Shanghai, China and Meihua Xu School of Mechatronical
Deduction and Logic Implementation of the Fractal Scan Algorithm Zhangjin Chen, Feng Ran, Zheming Jin Microelectronic R&D center, Shanghai University Shanghai, China and Meihua Xu School of Mechatronical
Hashing Techniques. Material based on slides by George Bebis
 Hashing Techniques Material based on slides by George Bebis https://www.cse.unr.edu/~bebis/cs477/lect/hashing.ppt The Search Problem Find items with keys matching a given search key Given an array A, containing
Hashing Techniques Material based on slides by George Bebis https://www.cse.unr.edu/~bebis/cs477/lect/hashing.ppt The Search Problem Find items with keys matching a given search key Given an array A, containing
NTHU Rain Removal Project
 People NTHU Rain Removal Project Networked Video Lab, National Tsing Hua University, Hsinchu, Taiwan Li-Wei Kang, Institute of Information Science, Academia Sinica, Taipei, Taiwan Chia-Wen Lin *, Department
People NTHU Rain Removal Project Networked Video Lab, National Tsing Hua University, Hsinchu, Taiwan Li-Wei Kang, Institute of Information Science, Academia Sinica, Taipei, Taiwan Chia-Wen Lin *, Department
On the interconnection of message passing systems
 Information Processing Letters 105 (2008) 249 254 www.elsevier.com/locate/ipl On the interconnection of message passing systems A. Álvarez a,s.arévalo b, V. Cholvi c,, A. Fernández b,e.jiménez a a Polytechnic
Information Processing Letters 105 (2008) 249 254 www.elsevier.com/locate/ipl On the interconnection of message passing systems A. Álvarez a,s.arévalo b, V. Cholvi c,, A. Fernández b,e.jiménez a a Polytechnic
Multiplying and Dividing by Powers of 10
 Multiplying and Dividing by Powers of 10 1.) Complete stations A-F around the room. Copy each problem and answer it below. Problem A B C D E F Answer = = = = = = 2.) Where is the decimal point in a whole
Multiplying and Dividing by Powers of 10 1.) Complete stations A-F around the room. Copy each problem and answer it below. Problem A B C D E F Answer = = = = = = 2.) Where is the decimal point in a whole
I. Introduction. India; 2 Assistant Professor, Department of Electronics & Communication Engineering, SRIT, Jabalpur (M.P.
 A Decimal / Binary Multi-operand Adder using a Fast Binary to Decimal Converter-A Review Ruchi Bhatt, Divyanshu Rao, Ravi Mohan 1 M. Tech Scholar, Department of Electronics & Communication Engineering,
A Decimal / Binary Multi-operand Adder using a Fast Binary to Decimal Converter-A Review Ruchi Bhatt, Divyanshu Rao, Ravi Mohan 1 M. Tech Scholar, Department of Electronics & Communication Engineering,
A Fitness Function to Find Feasible Sequences of Method Calls for Evolutionary Testing of Object-Oriented Programs
 A Fitness Function to Find Feasible Sequences of Method Calls for Evolutionary Testing of Object-Oriented Programs Myoung Yee Kim and Yoonsik Cheon TR #7-57 November 7; revised January Keywords: fitness
A Fitness Function to Find Feasible Sequences of Method Calls for Evolutionary Testing of Object-Oriented Programs Myoung Yee Kim and Yoonsik Cheon TR #7-57 November 7; revised January Keywords: fitness
Discrete Optimization. Lecture Notes 2
 Discrete Optimization. Lecture Notes 2 Disjunctive Constraints Defining variables and formulating linear constraints can be straightforward or more sophisticated, depending on the problem structure. The
Discrete Optimization. Lecture Notes 2 Disjunctive Constraints Defining variables and formulating linear constraints can be straightforward or more sophisticated, depending on the problem structure. The
CHAPTER 2. Graphs. 1. Introduction to Graphs and Graph Isomorphism
 CHAPTER 2 Graphs 1. Introduction to Graphs and Graph Isomorphism 1.1. The Graph Menagerie. Definition 1.1.1. A simple graph G = (V, E) consists of a set V of vertices and a set E of edges, represented
CHAPTER 2 Graphs 1. Introduction to Graphs and Graph Isomorphism 1.1. The Graph Menagerie. Definition 1.1.1. A simple graph G = (V, E) consists of a set V of vertices and a set E of edges, represented
Treewidth and graph minors
 Treewidth and graph minors Lectures 9 and 10, December 29, 2011, January 5, 2012 We shall touch upon the theory of Graph Minors by Robertson and Seymour. This theory gives a very general condition under
Treewidth and graph minors Lectures 9 and 10, December 29, 2011, January 5, 2012 We shall touch upon the theory of Graph Minors by Robertson and Seymour. This theory gives a very general condition under
Twiddle Factor Transformation for Pipelined FFT Processing
 Twiddle Factor Transformation for Pipelined FFT Processing In-Cheol Park, WonHee Son, and Ji-Hoon Kim School of EECS, Korea Advanced Institute of Science and Technology, Daejeon, Korea icpark@ee.kaist.ac.kr,
Twiddle Factor Transformation for Pipelined FFT Processing In-Cheol Park, WonHee Son, and Ji-Hoon Kim School of EECS, Korea Advanced Institute of Science and Technology, Daejeon, Korea icpark@ee.kaist.ac.kr,
Computing with Infinitely Many Processes under assumptions on concurrency and participation -M.Merritt&G.Taubenfeld. Dean Christakos & Deva Seetharam
 Computing with Infinitely Many Processes under assumptions on concurrency and participation -M.Merritt&G.Taubenfeld Dean Christakos & Deva Seetharam November 25, 2003 Abstract This paper explores four
Computing with Infinitely Many Processes under assumptions on concurrency and participation -M.Merritt&G.Taubenfeld Dean Christakos & Deva Seetharam November 25, 2003 Abstract This paper explores four
A Connection between Network Coding and. Convolutional Codes
 A Connection between Network Coding and 1 Convolutional Codes Christina Fragouli, Emina Soljanin christina.fragouli@epfl.ch, emina@lucent.com Abstract The min-cut, max-flow theorem states that a source
A Connection between Network Coding and 1 Convolutional Codes Christina Fragouli, Emina Soljanin christina.fragouli@epfl.ch, emina@lucent.com Abstract The min-cut, max-flow theorem states that a source
Propagated Timestamps: A Scheme for The Stabilization of Maximum Flow Routing Protocols
 Propagated Timestamps: A Scheme for The Stabilization of Maximum Flow Routing Protocols Jorge A. Cobb Mohamed Waris Department of Computer Science University of Houston Houston, TX 77204-3475 Abstract
Propagated Timestamps: A Scheme for The Stabilization of Maximum Flow Routing Protocols Jorge A. Cobb Mohamed Waris Department of Computer Science University of Houston Houston, TX 77204-3475 Abstract
DIVIDE AND CONQUER ALGORITHMS ANALYSIS WITH RECURRENCE EQUATIONS
 CHAPTER 11 SORTING ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY M. AMATO AND
CHAPTER 11 SORTING ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY M. AMATO AND
T consists of finding an efficient implementation of access,
 968 IEEE TRANSACTIONS ON COMPUTERS, VOL. 38, NO. 7, JULY 1989 Multidimensional Balanced Binary Trees VIJAY K. VAISHNAVI A bstract-a new balanced multidimensional tree structure called a k-dimensional balanced
968 IEEE TRANSACTIONS ON COMPUTERS, VOL. 38, NO. 7, JULY 1989 Multidimensional Balanced Binary Trees VIJAY K. VAISHNAVI A bstract-a new balanced multidimensional tree structure called a k-dimensional balanced
Chordal deletion is fixed-parameter tractable
 Chordal deletion is fixed-parameter tractable Dániel Marx Institut für Informatik, Humboldt-Universität zu Berlin, Unter den Linden 6, 10099 Berlin, Germany. dmarx@informatik.hu-berlin.de Abstract. It
Chordal deletion is fixed-parameter tractable Dániel Marx Institut für Informatik, Humboldt-Universität zu Berlin, Unter den Linden 6, 10099 Berlin, Germany. dmarx@informatik.hu-berlin.de Abstract. It
More about The Competition
 Data Structure I More about The Competition TLE? 10 8 integer operations, or 10 7 floating point operations, in a for loop, run in around one second for a typical desktop PC. Therefore, if n = 20, then
Data Structure I More about The Competition TLE? 10 8 integer operations, or 10 7 floating point operations, in a for loop, run in around one second for a typical desktop PC. Therefore, if n = 20, then
Optimum Alphabetic Binary Trees T. C. Hu and J. D. Morgenthaler Department of Computer Science and Engineering, School of Engineering, University of C
 Optimum Alphabetic Binary Trees T. C. Hu and J. D. Morgenthaler Department of Computer Science and Engineering, School of Engineering, University of California, San Diego CA 92093{0114, USA Abstract. We
Optimum Alphabetic Binary Trees T. C. Hu and J. D. Morgenthaler Department of Computer Science and Engineering, School of Engineering, University of California, San Diego CA 92093{0114, USA Abstract. We
On combining chase-2 and sum-product algorithms for LDPC codes
 University of Wollongong Research Online Faculty of Engineering and Information Sciences - Papers: Part A Faculty of Engineering and Information Sciences 2012 On combining chase-2 and sum-product algorithms
University of Wollongong Research Online Faculty of Engineering and Information Sciences - Papers: Part A Faculty of Engineering and Information Sciences 2012 On combining chase-2 and sum-product algorithms
Clustering Using Graph Connectivity
 Clustering Using Graph Connectivity Patrick Williams June 3, 010 1 Introduction It is often desirable to group elements of a set into disjoint subsets, based on the similarity between the elements in the
Clustering Using Graph Connectivity Patrick Williams June 3, 010 1 Introduction It is often desirable to group elements of a set into disjoint subsets, based on the similarity between the elements in the
Double Patterning-Aware Detailed Routing with Mask Usage Balancing
 Double Patterning-Aware Detailed Routing with Mask Usage Balancing Seong-I Lei Department of Computer Science National Tsing Hua University HsinChu, Taiwan Email: d9762804@oz.nthu.edu.tw Chris Chu Department
Double Patterning-Aware Detailed Routing with Mask Usage Balancing Seong-I Lei Department of Computer Science National Tsing Hua University HsinChu, Taiwan Email: d9762804@oz.nthu.edu.tw Chris Chu Department
Chapter 2. Data Representation in Computer Systems
 Chapter 2 Data Representation in Computer Systems Chapter 2 Objectives Understand the fundamentals of numerical data representation and manipulation in digital computers. Master the skill of converting
Chapter 2 Data Representation in Computer Systems Chapter 2 Objectives Understand the fundamentals of numerical data representation and manipulation in digital computers. Master the skill of converting
Binary Search. Roland Backhouse February 5th, 2001
 1 Binary Search Roland Backhouse February 5th, 2001 Outline 2 An implementation in Java of the card-searching algorithm is presented. Issues concerning the correctness of the implementation are raised
1 Binary Search Roland Backhouse February 5th, 2001 Outline 2 An implementation in Java of the card-searching algorithm is presented. Issues concerning the correctness of the implementation are raised
Min-Cost Multicast Networks in Euclidean Space
 Min-Cost Multicast Networks in Euclidean Space Xunrui Yin, Yan Wang, Xin Wang, Xiangyang Xue School of Computer Science Fudan University {09110240030,11110240029,xinw,xyxue}@fudan.edu.cn Zongpeng Li Dept.
Min-Cost Multicast Networks in Euclidean Space Xunrui Yin, Yan Wang, Xin Wang, Xiangyang Xue School of Computer Science Fudan University {09110240030,11110240029,xinw,xyxue}@fudan.edu.cn Zongpeng Li Dept.
ARITHMETIC operations based on residue number systems
 IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS II: EXPRESS BRIEFS, VOL. 53, NO. 2, FEBRUARY 2006 133 Improved Memoryless RNS Forward Converter Based on the Periodicity of Residues A. B. Premkumar, Senior Member,
IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS II: EXPRESS BRIEFS, VOL. 53, NO. 2, FEBRUARY 2006 133 Improved Memoryless RNS Forward Converter Based on the Periodicity of Residues A. B. Premkumar, Senior Member,
Byzantine Consensus in Directed Graphs
 Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
Concurrent Small Shared. A New Solution to Lamport's Programming Problem Using Variables
 A New Solution to Lamport's Programming Problem Using Variables GARY L. PETERSON The University of Rochester Concurrent Small Shared A new solution to the concurrent programming control (mutual exclusion)
A New Solution to Lamport's Programming Problem Using Variables GARY L. PETERSON The University of Rochester Concurrent Small Shared A new solution to the concurrent programming control (mutual exclusion)
Lecture 15 Binary Search Trees
 Lecture 15 Binary Search Trees 15-122: Principles of Imperative Computation (Fall 2017) Frank Pfenning, André Platzer, Rob Simmons, Iliano Cervesato In this lecture, we will continue considering ways to
Lecture 15 Binary Search Trees 15-122: Principles of Imperative Computation (Fall 2017) Frank Pfenning, André Platzer, Rob Simmons, Iliano Cervesato In this lecture, we will continue considering ways to
LOW-DENSITY PARITY-CHECK (LDPC) codes [1] can
![LOW-DENSITY PARITY-CHECK (LDPC) codes [1] can LOW-DENSITY PARITY-CHECK (LDPC) codes [1] can](/thumbs/96/128999908.jpg) 208 IEEE TRANSACTIONS ON MAGNETICS, VOL 42, NO 2, FEBRUARY 2006 Structured LDPC Codes for High-Density Recording: Large Girth and Low Error Floor J Lu and J M F Moura Department of Electrical and Computer
208 IEEE TRANSACTIONS ON MAGNETICS, VOL 42, NO 2, FEBRUARY 2006 Structured LDPC Codes for High-Density Recording: Large Girth and Low Error Floor J Lu and J M F Moura Department of Electrical and Computer
ALGORITHMS EXAMINATION Department of Computer Science New York University December 17, 2007
 ALGORITHMS EXAMINATION Department of Computer Science New York University December 17, 2007 This examination is a three hour exam. All questions carry the same weight. Answer all of the following six questions.
ALGORITHMS EXAMINATION Department of Computer Science New York University December 17, 2007 This examination is a three hour exam. All questions carry the same weight. Answer all of the following six questions.
On the Finiteness of the Recursive Chromatic Number
 On the Finiteness of the Recursive Chromatic Number William I Gasarch Andrew C.Y. Lee Abstract A recursive graph is a graph whose vertex and edges sets are recursive. A highly recursive graph is a recursive
On the Finiteness of the Recursive Chromatic Number William I Gasarch Andrew C.Y. Lee Abstract A recursive graph is a graph whose vertex and edges sets are recursive. A highly recursive graph is a recursive
Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science Algorithms For Inference Fall 2014
 Suggested Reading: Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.438 Algorithms For Inference Fall 2014 Probabilistic Modelling and Reasoning: The Junction
Suggested Reading: Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.438 Algorithms For Inference Fall 2014 Probabilistic Modelling and Reasoning: The Junction
CS521 \ Notes for the Final Exam
 CS521 \ Notes for final exam 1 Ariel Stolerman Asymptotic Notations: CS521 \ Notes for the Final Exam Notation Definition Limit Big-O ( ) Small-o ( ) Big- ( ) Small- ( ) Big- ( ) Notes: ( ) ( ) ( ) ( )
CS521 \ Notes for final exam 1 Ariel Stolerman Asymptotic Notations: CS521 \ Notes for the Final Exam Notation Definition Limit Big-O ( ) Small-o ( ) Big- ( ) Small- ( ) Big- ( ) Notes: ( ) ( ) ( ) ( )
Search Algorithms for Discrete Optimization Problems
 Search Algorithms for Discrete Optimization Problems Ananth Grama, Anshul Gupta, George Karypis, and Vipin Kumar To accompany the text ``Introduction to Parallel Computing'', Addison Wesley, 2003. 1 Topic
Search Algorithms for Discrete Optimization Problems Ananth Grama, Anshul Gupta, George Karypis, and Vipin Kumar To accompany the text ``Introduction to Parallel Computing'', Addison Wesley, 2003. 1 Topic
A Synchronization Algorithm for Distributed Systems
 A Synchronization Algorithm for Distributed Systems Tai-Kuo Woo Department of Computer Science Jacksonville University Jacksonville, FL 32211 Kenneth Block Department of Computer and Information Science
A Synchronization Algorithm for Distributed Systems Tai-Kuo Woo Department of Computer Science Jacksonville University Jacksonville, FL 32211 Kenneth Block Department of Computer and Information Science
THE orthogonal frequency-division multiplex (OFDM)
 26 IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS II: EXPRESS BRIEFS, VOL. 57, NO. 1, JANUARY 2010 A Generalized Mixed-Radix Algorithm for Memory-Based FFT Processors Chen-Fong Hsiao, Yuan Chen, Member, IEEE,
26 IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS II: EXPRESS BRIEFS, VOL. 57, NO. 1, JANUARY 2010 A Generalized Mixed-Radix Algorithm for Memory-Based FFT Processors Chen-Fong Hsiao, Yuan Chen, Member, IEEE,
Coverability Graph and Fairness
 Coverability Graph and Fairness prof.dr.ir. Wil van der Aalst www.vdaalst.com Recall reachability analysis or1 x r1 rg1 g1 go1 o1 r2 rg2 g2 go2 o2 or2 Petri net standard properties Boundedness Terminating
Coverability Graph and Fairness prof.dr.ir. Wil van der Aalst www.vdaalst.com Recall reachability analysis or1 x r1 rg1 g1 go1 o1 r2 rg2 g2 go2 o2 or2 Petri net standard properties Boundedness Terminating
AsmL Specification and Verification of Lamport s Bakery Algorithm
 Journal of Computing and Information Technology - CIT 13, 2005, 4, 313-319 313 AsmL Specification and Verification of Lamport s Bakery Algorithm Matko Botinčan Department of Mathematics, University of
Journal of Computing and Information Technology - CIT 13, 2005, 4, 313-319 313 AsmL Specification and Verification of Lamport s Bakery Algorithm Matko Botinčan Department of Mathematics, University of
Verification on Port Connections
 Verification on Port Connections Geeng-Wei Lee*, Chun-Yao Wang, Juinn-Dar Huang*, and Jing-Yang Jou* * Department of Electronics Engineering National Chiao Tung University, Hsinchu, Taiwan, R.O.C. {gwlee,
Verification on Port Connections Geeng-Wei Lee*, Chun-Yao Wang, Juinn-Dar Huang*, and Jing-Yang Jou* * Department of Electronics Engineering National Chiao Tung University, Hsinchu, Taiwan, R.O.C. {gwlee,
Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute. Week 02 Module 06 Lecture - 14 Merge Sort: Analysis
 Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute Week 02 Module 06 Lecture - 14 Merge Sort: Analysis So, we have seen how to use a divide and conquer strategy, we
Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute Week 02 Module 06 Lecture - 14 Merge Sort: Analysis So, we have seen how to use a divide and conquer strategy, we
Studying Graph Connectivity
 Studying Graph Connectivity Freeman Yufei Huang July 1, 2002 Submitted for CISC-871 Instructor: Dr. Robin Dawes Studying Graph Connectivity Freeman Yufei Huang Submitted July 1, 2002 for CISC-871 In some
Studying Graph Connectivity Freeman Yufei Huang July 1, 2002 Submitted for CISC-871 Instructor: Dr. Robin Dawes Studying Graph Connectivity Freeman Yufei Huang Submitted July 1, 2002 for CISC-871 In some
COP Programming Assignment #7
 1 of 5 03/13/07 12:36 COP 3330 - Programming Assignment #7 Due: Mon, Nov 21 (revised) Objective: Upon completion of this program, you should gain experience with operator overloading, as well as further
1 of 5 03/13/07 12:36 COP 3330 - Programming Assignment #7 Due: Mon, Nov 21 (revised) Objective: Upon completion of this program, you should gain experience with operator overloading, as well as further
State-Based Synchronization Protocol in Sensor Networks
 State-Based Synchronization Protocol in Sensor Networks Shang-Chih Hsu Wei Yen 1 1 Department of Computer Science and Engineering, Tatung University, Taipei, Taiwan, ROC shanzihsu@yahoo.com.tw, wyen@ttu.edu.tw
State-Based Synchronization Protocol in Sensor Networks Shang-Chih Hsu Wei Yen 1 1 Department of Computer Science and Engineering, Tatung University, Taipei, Taiwan, ROC shanzihsu@yahoo.com.tw, wyen@ttu.edu.tw
Sorting and Selection
 Sorting and Selection Introduction Divide and Conquer Merge-Sort Quick-Sort Radix-Sort Bucket-Sort 10-1 Introduction Assuming we have a sequence S storing a list of keyelement entries. The key of the element
Sorting and Selection Introduction Divide and Conquer Merge-Sort Quick-Sort Radix-Sort Bucket-Sort 10-1 Introduction Assuming we have a sequence S storing a list of keyelement entries. The key of the element
Deadlocks in Distributed Systems: Request Models and Definitions
 Deadlocks in Distributed Systems: Request Models and Definitions Jerzy Brzezinski Jean-Michel Helary, Michel Raynal Institute of Computing Science IRISA Poznan University of Technology Campus de Beaulieu
Deadlocks in Distributed Systems: Request Models and Definitions Jerzy Brzezinski Jean-Michel Helary, Michel Raynal Institute of Computing Science IRISA Poznan University of Technology Campus de Beaulieu
6. Hoare Logic and Weakest Preconditions
 6. Hoare Logic and Weakest Preconditions Program Verification ETH Zurich, Spring Semester 07 Alexander J. Summers 30 Program Correctness There are many notions of correctness properties for a given program
6. Hoare Logic and Weakest Preconditions Program Verification ETH Zurich, Spring Semester 07 Alexander J. Summers 30 Program Correctness There are many notions of correctness properties for a given program
Asynchronous Models. Chapter Asynchronous Processes States, Inputs, and Outputs
 Chapter 3 Asynchronous Models 3.1 Asynchronous Processes Like a synchronous reactive component, an asynchronous process interacts with other processes via inputs and outputs, and maintains an internal
Chapter 3 Asynchronous Models 3.1 Asynchronous Processes Like a synchronous reactive component, an asynchronous process interacts with other processes via inputs and outputs, and maintains an internal
T Reactive Systems: Kripke Structures and Automata
 Tik-79.186 Reactive Systems 1 T-79.186 Reactive Systems: Kripke Structures and Automata Spring 2005, Lecture 3 January 31, 2005 Tik-79.186 Reactive Systems 2 Properties of systems invariants: the system
Tik-79.186 Reactive Systems 1 T-79.186 Reactive Systems: Kripke Structures and Automata Spring 2005, Lecture 3 January 31, 2005 Tik-79.186 Reactive Systems 2 Properties of systems invariants: the system
Matching and Factor-Critical Property in 3-Dominating-Critical Graphs
 Matching and Factor-Critical Property in 3-Dominating-Critical Graphs Tao Wang a,, Qinglin Yu a,b a Center for Combinatorics, LPMC Nankai University, Tianjin, China b Department of Mathematics and Statistics
Matching and Factor-Critical Property in 3-Dominating-Critical Graphs Tao Wang a,, Qinglin Yu a,b a Center for Combinatorics, LPMC Nankai University, Tianjin, China b Department of Mathematics and Statistics
Increasing Parallelism of Loops with the Loop Distribution Technique
 Increasing Parallelism of Loops with the Loop Distribution Technique Ku-Nien Chang and Chang-Biau Yang Department of pplied Mathematics National Sun Yat-sen University Kaohsiung, Taiwan 804, ROC cbyang@math.nsysu.edu.tw
Increasing Parallelism of Loops with the Loop Distribution Technique Ku-Nien Chang and Chang-Biau Yang Department of pplied Mathematics National Sun Yat-sen University Kaohsiung, Taiwan 804, ROC cbyang@math.nsysu.edu.tw
Introduction to Programming, Aug-Dec 2006
 Introduction to Programming, Aug-Dec 2006 Lecture 3, Friday 11 Aug 2006 Lists... We can implicitly decompose a list into its head and tail by providing a pattern with two variables to denote the two components
Introduction to Programming, Aug-Dec 2006 Lecture 3, Friday 11 Aug 2006 Lists... We can implicitly decompose a list into its head and tail by providing a pattern with two variables to denote the two components
The Markov Reformulation Theorem
 The Markov Reformulation Theorem Michael Kassoff and Michael Genesereth Logic Group, Department of Computer Science Stanford University {mkassoff, genesereth}@cs.stanford.edu Abstract In this paper, we
The Markov Reformulation Theorem Michael Kassoff and Michael Genesereth Logic Group, Department of Computer Science Stanford University {mkassoff, genesereth}@cs.stanford.edu Abstract In this paper, we
Research Issues and Challenges for Multiple Digital Signatures
 INTERNATION JOURNAL OF NETWORK SECURITY, VOL.1, NO.1,PP. 1-6, 2005 1 Research Issues and Challenges for Multiple Digital Signatures Min-Shiang Hwang, and Cheng-Chi Lee, Abstract In this paper, we survey
INTERNATION JOURNAL OF NETWORK SECURITY, VOL.1, NO.1,PP. 1-6, 2005 1 Research Issues and Challenges for Multiple Digital Signatures Min-Shiang Hwang, and Cheng-Chi Lee, Abstract In this paper, we survey
Arbee L.P. Chen ( 陳良弼 )
 Arbee L.P. Chen ( 陳良弼 ) Asia University Taichung, Taiwan EDUCATION Phone: (04)23323456x1011 Email: arbee@asia.edu.tw - Ph.D. in Computer Engineering, Department of Electrical Engineering, University of
Arbee L.P. Chen ( 陳良弼 ) Asia University Taichung, Taiwan EDUCATION Phone: (04)23323456x1011 Email: arbee@asia.edu.tw - Ph.D. in Computer Engineering, Department of Electrical Engineering, University of
Course Modelling of Concurrent Systems Summer Semester 2016 University of Duisburg-Essen
 Course Modelling of Concurrent Systems Summer Semester 2016 University of Duisburg-Essen Harsh Beohar LF 265, harsh.beohar@uni-due.de Harsh Beohar Course Modelling of Concurrent Systems 1 Course handler
Course Modelling of Concurrent Systems Summer Semester 2016 University of Duisburg-Essen Harsh Beohar LF 265, harsh.beohar@uni-due.de Harsh Beohar Course Modelling of Concurrent Systems 1 Course handler
Bisection Debugging. 1 Introduction. Thomas Gross. Carnegie Mellon University. Preliminary version
 Bisection Debugging Thomas Gross School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Institut für Computer Systeme ETH Zürich CH 8092 Zürich Preliminary version Abstract This paper
Bisection Debugging Thomas Gross School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Institut für Computer Systeme ETH Zürich CH 8092 Zürich Preliminary version Abstract This paper
1 Static-to-Dynamic Transformations
 You re older than you ve ever been and now you re even older And now you re even older And now you re even older You re older than you ve ever been and now you re even older And now you re older still
You re older than you ve ever been and now you re even older And now you re even older And now you re even older You re older than you ve ever been and now you re even older And now you re older still
On the Hardness of Counting the Solutions of SPARQL Queries
 On the Hardness of Counting the Solutions of SPARQL Queries Reinhard Pichler and Sebastian Skritek Vienna University of Technology, Faculty of Informatics {pichler,skritek}@dbai.tuwien.ac.at 1 Introduction
On the Hardness of Counting the Solutions of SPARQL Queries Reinhard Pichler and Sebastian Skritek Vienna University of Technology, Faculty of Informatics {pichler,skritek}@dbai.tuwien.ac.at 1 Introduction
A Quota Transfer Protocol for Upstream Transmissions in Wireless Mesh Networks
 A Quota Transfer Protocol for Upstream Transmissions in Wireless Mesh Networks Yen-Bin Lee and Wen-Shyang Hwang Department of Electrical Engineering, National Kaohsiung University of Applied Sciences,
A Quota Transfer Protocol for Upstream Transmissions in Wireless Mesh Networks Yen-Bin Lee and Wen-Shyang Hwang Department of Electrical Engineering, National Kaohsiung University of Applied Sciences,
CSMA/CD protocol for time-constrained. communication on bus networks and
 ~~ CSMA/CD protocol for time-constrained communication on bus networks R.-H. Jan Y.-J. Yeh Indexing terms: Bus networks, CSMAICD, Time-constrained communications Abstract: A multiple access protocol for
~~ CSMA/CD protocol for time-constrained communication on bus networks R.-H. Jan Y.-J. Yeh Indexing terms: Bus networks, CSMAICD, Time-constrained communications Abstract: A multiple access protocol for
New Mexico Tech Hyd 510
 Numerics Motivation Modeling process (JLW) To construct a model we assemble and synthesize data and other information to formulate a conceptual model of the situation. The model is conditioned on the science
Numerics Motivation Modeling process (JLW) To construct a model we assemble and synthesize data and other information to formulate a conceptual model of the situation. The model is conditioned on the science
Chapter 4: Sorting. Spring 2014 Sorting Fun 1
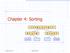 Chapter 4: Sorting 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 Spring 2014 Sorting Fun 1 What We ll Do! Quick Sort! Lower bound on runtimes for comparison based sort! Radix and Bucket sort Spring 2014
Chapter 4: Sorting 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 Spring 2014 Sorting Fun 1 What We ll Do! Quick Sort! Lower bound on runtimes for comparison based sort! Radix and Bucket sort Spring 2014
A Formula Diamond Encoding Data Hiding Scheme
 Journal of Information Hiding and Multimedia Signal Processing c 2015 ISSN 2073-4212 Ubiquitous International Volume 6, Number 6, November 2015 A Formula Diamond Encoding Data Hiding Scheme Wen-Chung Kuo
Journal of Information Hiding and Multimedia Signal Processing c 2015 ISSN 2073-4212 Ubiquitous International Volume 6, Number 6, November 2015 A Formula Diamond Encoding Data Hiding Scheme Wen-Chung Kuo
A FORWARDING CACHE VLAN PROTOCOL (FCVP) IN WIRELESS NETWORKS
 A FORWARDING CACHE VLAN PROTOCOL (FCVP) IN WIRELESS NETWORKS Tzu-Chiang Chiang,, Ching-Hung Yeh, Yueh-Min Huang and Fenglien Lee Department of Engineering Science, National Cheng-Kung University, Taiwan,
A FORWARDING CACHE VLAN PROTOCOL (FCVP) IN WIRELESS NETWORKS Tzu-Chiang Chiang,, Ching-Hung Yeh, Yueh-Min Huang and Fenglien Lee Department of Engineering Science, National Cheng-Kung University, Taiwan,
CS 31: Introduction to Computer Systems. 03: Binary Arithmetic January 29
 CS 31: Introduction to Computer Systems 03: Binary Arithmetic January 29 WiCS! Swarthmore Women in Computer Science Slide 2 Today Binary Arithmetic Unsigned addition Subtraction Representation Signed magnitude
CS 31: Introduction to Computer Systems 03: Binary Arithmetic January 29 WiCS! Swarthmore Women in Computer Science Slide 2 Today Binary Arithmetic Unsigned addition Subtraction Representation Signed magnitude
Investigating F# as a development tool for distributed multi-agent systems
 PROCEEDINGS OF THE WORKSHOP ON APPLICATIONS OF SOFTWARE AGENTS ISBN 978-86-7031-188-6, pp. 32-36, 2011 Investigating F# as a development tool for distributed multi-agent systems Extended abstract Alex
PROCEEDINGS OF THE WORKSHOP ON APPLICATIONS OF SOFTWARE AGENTS ISBN 978-86-7031-188-6, pp. 32-36, 2011 Investigating F# as a development tool for distributed multi-agent systems Extended abstract Alex
Announcements! P1 part 1 due next Tuesday P1 part 2 due next Friday
 Announcements! P1 part 1 due next Tuesday P1 part 2 due next Friday 1 Finite-state machines CS 536 Last time! A compiler is a recognizer of language S (Source) a translator from S to T (Target) a program
Announcements! P1 part 1 due next Tuesday P1 part 2 due next Friday 1 Finite-state machines CS 536 Last time! A compiler is a recognizer of language S (Source) a translator from S to T (Target) a program
Blind Signature Scheme Based on Elliptic Curve Cryptography
 Blind Signature Scheme Based on Elliptic Curve Cryptography Chwei-Shyong Tsai Min-Shiang Hwang Pei-Chen Sung Department of Management Information System, National Chung Hsing University 250 Kuo Kuang Road.,
Blind Signature Scheme Based on Elliptic Curve Cryptography Chwei-Shyong Tsai Min-Shiang Hwang Pei-Chen Sung Department of Management Information System, National Chung Hsing University 250 Kuo Kuang Road.,
1 Dijkstra s Algorithm
 Lecture 11 Dijkstra s Algorithm Scribes: Himanshu Bhandoh (2015), Virginia Williams, and Date: November 1, 2017 Anthony Kim (2016), G. Valiant (2017), M. Wootters (2017) (Adapted from Virginia Williams
Lecture 11 Dijkstra s Algorithm Scribes: Himanshu Bhandoh (2015), Virginia Williams, and Date: November 1, 2017 Anthony Kim (2016), G. Valiant (2017), M. Wootters (2017) (Adapted from Virginia Williams
Carry Select Adder with High Speed and Power Efficiency
 International OPEN ACCESS Journal ISSN: 2249-6645 Of Modern Engineering Research (IJMER) Carry Select Adder with High Speed and Power Efficiency V P C Reddy, Chenchela V K Reddy 2, V Ravindra Reddy 3 (ECE
International OPEN ACCESS Journal ISSN: 2249-6645 Of Modern Engineering Research (IJMER) Carry Select Adder with High Speed and Power Efficiency V P C Reddy, Chenchela V K Reddy 2, V Ravindra Reddy 3 (ECE
Imelda C. Go, South Carolina Department of Education, Columbia, SC
 PO 082 Rounding in SAS : Preventing Numeric Representation Problems Imelda C. Go, South Carolina Department of Education, Columbia, SC ABSTRACT As SAS programmers, we come from a variety of backgrounds.
PO 082 Rounding in SAS : Preventing Numeric Representation Problems Imelda C. Go, South Carolina Department of Education, Columbia, SC ABSTRACT As SAS programmers, we come from a variety of backgrounds.
Course Modelling of Concurrent Systems Summer Semester 2016 University of Duisburg-Essen
 Course Modelling of Concurrent Systems Summer Semester 2016 University of Duisburg-Essen Harsh Beohar LF 265, harsh.beohar@uni-due.de Harsh Beohar Course Modelling of Concurrent Systems 1 Course handler
Course Modelling of Concurrent Systems Summer Semester 2016 University of Duisburg-Essen Harsh Beohar LF 265, harsh.beohar@uni-due.de Harsh Beohar Course Modelling of Concurrent Systems 1 Course handler
Algorithms for Euclidean TSP
 This week, paper [2] by Arora. See the slides for figures. See also http://www.cs.princeton.edu/~arora/pubs/arorageo.ps Algorithms for Introduction This lecture is about the polynomial time approximation
This week, paper [2] by Arora. See the slides for figures. See also http://www.cs.princeton.edu/~arora/pubs/arorageo.ps Algorithms for Introduction This lecture is about the polynomial time approximation
We have used both of the last two claims in previous algorithms and therefore their proof is omitted.
 Homework 3 Question 1 The algorithm will be based on the following logic: If an edge ( ) is deleted from the spanning tree, let and be the trees that were created, rooted at and respectively Adding any
Homework 3 Question 1 The algorithm will be based on the following logic: If an edge ( ) is deleted from the spanning tree, let and be the trees that were created, rooted at and respectively Adding any
