2.9 Modularization. Department of CSE,Coimbatore
|
|
|
- Rafe Allison
- 5 years ago
- Views:
Transcription
1 2.9 Modularization
2 Objectives To understand how algorithms are modularized. To learn how smaller units can be made flexible through the use of formal parameters. To understand the characteristics of well-defined modules.
3 Eg. Recipe book for Pizza Let us consider a short recipe book for Pizza. It might start with a contents page, that list all the recipes inside. It then may have a series of recipes, each having a name, followed by a set of instructions, to make that recipe. Suppose you wish to make Fiorentina Pizza, you would check where to find it in the contents, and then follow its instructions. In doing so you might, part way through be referred to another recipe, for example, to make the pizza dough.
4 Making of Pizza 1. Pizza Dough 1. Mix yeast and water, add flour and stir. 2. Knead for 10 minutes. 3. Leave to rise for 30 minutes. 4. Roll out the dough. 5. Place in a large round pizza tin. 2. Fiorentina Pizza 1.Make the pizza dough following the recipe Pizza Dough, leaving to rise. 2. Spread with tomato puree, and cheese and spinach. 3. Crack an egg into the middle. 4. Bake in oven for 25 minutes.
5 Making of Pizza contd Tomato and Chilli Pizza 1.Make the pizza dough following the recipe Pizza Dough, leaving to rise. 2.Fry the chilli pepper for 3 minutes, add onions and garlic and fry for further 5 minutes. 3.Add tomatoes and spread over the base. 4. Bake in oven for 25 minutes.
6 Perhaps we came across a pizza dough recipe that was easier to make. We can change the instructions in just one place in the book and all the pizza recipes that use it now refer to the new version. If the dough instructions had been written out in every single recipe then we would need to make the changes in all those sets of instructions.
7 contd--- Splitting up recipes (or algorithms for that matter) in this way can also make them easier to understand. Each separate set of instructions in a recipe book is a recipe in its own right. It is in fact an algorithm that does something distinct and worthwhile in its own right.
8 Advantages of such an approach This way of structuring a recipe book or algorithm has several advantages. It means that the same instructions do not need to be written out over and over again. This saves space, but also reduces the chances of the different versions being different. It also makes it easy to substitute one recipe or algorithm to do a particular thing in a different way for another.
9 Modularization Algorithms can be modularized by breaking them into independent subprocesses. A module is a named subprocess. It is an individual algorithm that should do something coherent in its own right. You do not just take a random set of instructions from an algorithm and turn them into a separate module. Modularization is a vital element of programming that allows us to define new computable actions by assigning a name to some computable process. Modules are vital when writing large algorithms that consist of many individual parts.
10 Syntactic pattern Module NAME() is ACTIONS endmodule Figure: The syntactic pattern - naming a subprocess as a module Here, NAME is the place holder for the name of the module (the subprocess). For eg. Module average(), is understood to mean execute the process named average.
11 Eg. Grill a steak The grillsteak module, shows how the steak grilling algorithm can be written as a module. The name grillsteak is associated with the process of grilling a steak. We can execute the subprocess by writing grillsteak(). 1. Module grillsteak() is 2. steaktemp while steaktemp < 135 do a. steaktemp steaktemp endwhile 5. endmodule Figure: The grillsteak module
12 Eg. Making a dinner Consider, for example, a grill chef who is making dinner for a small private party. We might describe the entire process of making dinner as the execution of a series of modules that involve: baking a cake, fixing a salad, making lemonade, and grilling a steak. Each of these modules can be understood as an individual, algorithemmerdefined computable action, and these actions can be invoked by simply referring to them by name.
13 A make dinner module 1. module makedinner() is 2. bakecake() 3. fixsalad() 4. makelemonade() 5. grillsteak() 6. endmodule Figure: Making a dinner a sequence of subprocesses Since these modules have been elevated to the status of a computable action, we can also incorporate them into our flowchart notation. Bake a cake Fix a salad Make lemonade Grill a steak Figure: Make dinner flowchart
14 Hosting a private party Hosting a private party involves more than just making dinner. The host must, for example, send out invitations, gather up the responses, purchase food, clean the house, and choose background music. We can describe the process of hosting a private party as a module that is composed of these other submodules. Write a module for hosting a private dinner party.
15 Well designed modules Well-designed modules should meet several criteria. These criteria generally ensure that: the module can be used in a wide variety of larger processes. the module is self-contained. any errors caused by a module have a limited effect on any system that makes use of the module. the module can be used in a wide variety of contexts.
16 Criteria Understandability: Every module is self-contained, which implies that it can be fully understood without any knowledge of actions that take place outside of the module itself. Encapsulation: Every module affects only the data that it contains. Any errors that arise from a module are also contained within the module. Composition: Every module can be incorporated into a larger module without special treatment.
17 Summarizing modularity Modularity is an extremely powerful technique for designing complex algorithms. Modules allow us to isolate smaller parts of a large process such that those smaller parts are much easier to understand and manage. These smaller parts are self-contained, they can be easily inserted into other complex algorithms without needing to customize them or rewrite them. Also, although we must understand precisely what a sub module does, we do not need to fully understand the details of how a sub module actually works.
18 Module flexibility Modules should typically be flexible enough to be used in a variety of conditions. Modules are made flexible by allowing users to feed input values into the algorithm. The module can then respond differently depending on the input values provided by the user. The number of inputs that a module accepts must be defined when a module is written. The modules behavior then depends upon the initial value that is provided by the user.
19 Parameters of a module The number of inputs that a module accepts must be defined when a module is written. These are known as formal parameters. A formal parameter is a variable where the initial value is bound to the values provided as input to the module. The initial values provided by the module user are known as arguments or actual parameter.
20 Formal parameters Module NAME(V1,V2,.,Vn)is ACTIONS endmodule Figure: The syntactic pattern - formal parameters The figure gives an expanded syntactic pattern for defining a module. The formal parameters are listed within the parentheses associated with the name. A formal parameter is simply a variable name and a module may have as many formal parameters as convenient for the module's function. Of course, a module may have no formal parameters, as illustrated by all of the modules we have previously described.
21 One more look at the starting temperature of grill a steak algorithm.. To grill a steak, the steak has to have a starting temperature. It is the variable steaktemp in the algorithm. While writing the process for grilling a steak, It may initially seem that we have to know the value of the steaktemp variable. All we have to know is that there is instruction to set a starting temperature! Of course, if we are ever asked to grill an actual steak, we then need to obtain the starting steak temperature to actually carry out the process.
22 A flexible module for grill a steak Remember that a module simply defines what actions should be taken to grill a steak. We can make our grillsteak module flexible by making the starting temperature an input that is controlled from the outside of the module. 1. Module grillsteak(steaktemp) is 2. while steaktemp < 135 do a. steaktemp steaktemp endwhile 4. endmodule Figure: A flexible grillsteak module
23 Parameters of the flexible grill a steak module The rewritten grillsteak module now has one formal parameter. This implies that if we ever need to use this module to grill a steak that we must supply one actual parameter. The actual parameter becomes the starting steak temperature for the steak grilling subprocess. If, for example, we want to grill a steak from a starting temperature of 94 degrees because we are grilling on a scorching hot summer day from our back porch in Phoenix, Arizona, we would write grillsteak(94). Can you think of circumstances that might not hold in the flexible grillsteak module? Can you to include the identified circumstances?
24 Can you think of any circumstances that might not hold? There are two further circumstances that might not hold. We might sometimes want to grill a rare steak and hence stop grilling when the steak reaches 130 degrees. We might also want to grill a well-done steak and not stop grilling until the steak reaches perhaps 155 degrees. Also, perhaps it is the case that we have a very thick steak on a slowcooking grill such that the steak's temperature only increases by 2 degrees for every three minutes the steak is on the grill. These observations imply that we can optimize the flexibility of our grillsteak module. How do we achieve this?...
25 How to optimize the existing module? By adding two additional formal parameters: the target steak temperature the increase in temperature for every three minutes of grilling time. Figure: An optimally flexible grillsteak module
26 How to use the revised module? Three actual parameters for: starting temperature target steak temperature the amount by which the temperature of the steak will increase with every three minutes left on the grill. Each of the following shows how we can use this grillsteak module to achieve very different outcomes under very different circumstances. grillsteak(65, 130, 2) grillsteak(94, 155, 13) grillsteak(94, 135, 5)
27 A print module Assume that a print module allows you to write text onto a computer screen. If, for example, you wanted to write the text Computational Thinking onto the computer screen, you would express this action as print(computationalthinking). Draw a flowchart to print the values 0, 3, 6, 9, and 12 to the computer screen.you must use a loop. Write a module named countby3 that prints the values 0, 3, 6, 9, and 12 to the computer screen.
28 Who uses modular approach? Typical industry programming projects consist of thousands of lines of code or more. One single large block of programming statements would be unmanageable, incomprehensible, difficult to design, write, debug, test, etc. Modular Programming: Divide-and-Conquer approach to programming. Divide into sub-problems. Size of modules reduced to humanly comprehensible and manageable level. Analogous developments: manufacturing a spacecraft, or a car. Manufacture individual components, test separately. Assemble into larger components, integrate and test.
29 Entropy of software development A monolithic algorithm is one that is a single large block of instructions. A monolithic program is one that is a single large block of programming statements. Where generally, fixing one bug or error always seemed to create additional new bugs or errors. It is one which is increasingly interconnected, unreadable, and ultimately unreliable. That is the entropy of software development.
30 An overview of the development process Analysis and Design Implement
31 To design and implement a Robot The Robot is based on user input from keyboard. Requirements Specification: Develop a program that does the following: Display a menu of choices for robot motion. Read keyboard input. Move Robot based on keyboard input. Input can be any one of 4 arrows showing movement up, down, left, right.
32 Analysis and design Analysis Input = A value for keyboard input. Output = Direction of robot movement. Design Algorithm 1. Display a menu of choices for Robot movement. 2. Read request from the user. 3. Move the robot for the request.
33 Divide into sub problems Algorithm contains sub-problems Print menu. Read request. Move Robot. Perform top-down stepwise refinement. Define algorithms for sub-problems. Refine them - may need to be broken down into sub-sub-problems. At lowest level, assign name to each module and combine named modules into higher level sub-problem algorithm.
34 Sub problem #1: Print Menu and Read request 1. print "This program moves the Robot based on user input." 2. print "Enter to move Robot forward" 3. print "Enter to move Robot left" 4. print "Enter to move Robot right" 5. print "Enter to move Robot backward" 6. read request Sub problem #2: Move Robot 1. If request is move robot forward 2. Else if request is move robot left 3. Else if request is move robot right 4. Else if request is move robot backward.
35 Modularization characteristics Manageable: Reduce problem to smaller, simpler, humanly comprehensible sub problems. Divisible: Modules can be assigned to different teams/ programmers. Enables parallel work, reducing program development time. Facilitates programming, debugging, testing, maintenance. Portable: Individual modules can be modified to run on other platforms. Re-usable: Modules can be re-used within a program and across programs.
36 Value of this approach Applications are getting more and more complicated (growing in size and functionality). It is necessary to separate them into individual pieces (whether as components, modules, or plugins ). No one is surprised anymore that operating systems are designed in a modular way. The final product is assembled from independently developed components. Modularity is a mechanism to coordinate the work of many people around the world, manage interdependencies between their parts of the project, and assemble very complex systems in a reasonably reliable way. It enables you to achieve and manage that complexity. Not a silver bullet though
37 What has been described? Modules as ways of expressing algorithms and computational processes. How modules allow us to break large problems into smaller units. How these smaller units can be made flexible through the use of formal parameters. The importance of modular approach to software development. Credits Computing without computers, Paul Curzon; web.mit.edu/16.070/www/year2001/modular_programming.pdf The Benefits of ModularProgramming, Copyright Sun Microsystems, 2007 Google images
LN #6 & 7 (2 Hrs) Modularization 1 & 2 CTPS Department of CSE,Coimbatore
 LN #6 & 7 (2 Hrs) Modularization 1 & 2 CTPS 2018 Objectives To understand how algorithms are modularized. To learn how smaller units can be made flexible through the use of formal parameters. To understand
LN #6 & 7 (2 Hrs) Modularization 1 & 2 CTPS 2018 Objectives To understand how algorithms are modularized. To learn how smaller units can be made flexible through the use of formal parameters. To understand
The diagram below is only partially complete. Use the terms in the word list to complete the empty boxes. Make dinner
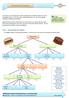 Decomposing Problems As we have seen, decomposition means breaking down a difficult problem into more manageable pieces. A common way to tackle this process is to use a tree diagram showing increasing
Decomposing Problems As we have seen, decomposition means breaking down a difficult problem into more manageable pieces. A common way to tackle this process is to use a tree diagram showing increasing
LN #3 (3 Hrs) Repetition, Computational state CTPS Department of CSE,Coimbatore
 LN #3 (3 Hrs) Repetition, Computational state CTPS 2018 Objectives To understand repetition of statements. To comprehend the form of test and termination in looping. To study the form and function of elements
LN #3 (3 Hrs) Repetition, Computational state CTPS 2018 Objectives To understand repetition of statements. To comprehend the form of test and termination in looping. To study the form and function of elements
Programming II (CS300)
 1 Programming II (CS300) Chapter 01: Procedural Programming MOUNA KACEM mouna@cs.wisc.edu Fall 2018 Procedural Programming 2 Introduction Procedural Programming: General Overview Procedural Programming:
1 Programming II (CS300) Chapter 01: Procedural Programming MOUNA KACEM mouna@cs.wisc.edu Fall 2018 Procedural Programming 2 Introduction Procedural Programming: General Overview Procedural Programming:
Introduction to Computer Programming concepts using StarLogo TNG
 Introduction to Computer Programming concepts using StarLogo TNG Overview In this class, we will use the StarLogo TNG language to introduce basic concepts used in computer programs. Learning Objectives
Introduction to Computer Programming concepts using StarLogo TNG Overview In this class, we will use the StarLogo TNG language to introduce basic concepts used in computer programs. Learning Objectives
6.001 Notes: Section 8.1
 6.001 Notes: Section 8.1 Slide 8.1.1 In this lecture we are going to introduce a new data type, specifically to deal with symbols. This may sound a bit odd, but if you step back, you may realize that everything
6.001 Notes: Section 8.1 Slide 8.1.1 In this lecture we are going to introduce a new data type, specifically to deal with symbols. This may sound a bit odd, but if you step back, you may realize that everything
Scheme of work Cambridge International AS & A Level Computing (9691)
 Scheme of work Cambridge International AS & A Level Computing (9691) Unit 2: Practical programming techniques Recommended prior knowledge Students beginning this course are not expected to have studied
Scheme of work Cambridge International AS & A Level Computing (9691) Unit 2: Practical programming techniques Recommended prior knowledge Students beginning this course are not expected to have studied
Statistics Case Study 2000 M. J. Clancy and M. C. Linn
 Statistics Case Study 2000 M. J. Clancy and M. C. Linn Problem Write and test functions to compute the following statistics for a nonempty list of numeric values: The mean, or average value, is computed
Statistics Case Study 2000 M. J. Clancy and M. C. Linn Problem Write and test functions to compute the following statistics for a nonempty list of numeric values: The mean, or average value, is computed
clicker question Comments Using comments Topic 3 static Methods and Structured Programming
 Topic 3 static Methods and Structured Programming "The cleaner and nicer the program, the faster it's going to run. And if it doesn't, it'll be easy to make it fast." -Joshua Bloch clicker question What
Topic 3 static Methods and Structured Programming "The cleaner and nicer the program, the faster it's going to run. And if it doesn't, it'll be easy to make it fast." -Joshua Bloch clicker question What
Chapter 1: Getting Started
 Getting Started Page 9 Chapter 1: Getting Started HOW MANY MICROCONTROLLERS DID YOU USE TODAY? A microcontroller is a kind of miniature computer brain that you can find in all kinds of devices. Some common,
Getting Started Page 9 Chapter 1: Getting Started HOW MANY MICROCONTROLLERS DID YOU USE TODAY? A microcontroller is a kind of miniature computer brain that you can find in all kinds of devices. Some common,
SOFTWARE ANALYSIS & DESIGN TOOLS
 SOFTWARE ANALYSIS & DESIGN TOOLS http://www.tutorialspoint.com/software_engineering/software_analysis_design_tools.htm Copyright tutorialspoint.com Software analysis and design includes all activities,
SOFTWARE ANALYSIS & DESIGN TOOLS http://www.tutorialspoint.com/software_engineering/software_analysis_design_tools.htm Copyright tutorialspoint.com Software analysis and design includes all activities,
1. Write two major differences between Object-oriented programming and procedural programming?
 1. Write two major differences between Object-oriented programming and procedural programming? A procedural program is written as a list of instructions, telling the computer, step-by-step, what to do:
1. Write two major differences between Object-oriented programming and procedural programming? A procedural program is written as a list of instructions, telling the computer, step-by-step, what to do:
Design of Embedded Systems
 Design of Embedded Systems José Costa Software for Embedded Systems Departamento de Engenharia Informática (DEI) Instituto Superior Técnico 2015-01-02 José Costa (DEI/IST) Design of Embedded Systems 1
Design of Embedded Systems José Costa Software for Embedded Systems Departamento de Engenharia Informática (DEI) Instituto Superior Técnico 2015-01-02 José Costa (DEI/IST) Design of Embedded Systems 1
Topic 3: Fractions. Topic 1 Integers. Topic 2 Decimals. Topic 3 Fractions. Topic 4 Ratios. Topic 5 Percentages. Topic 6 Algebra
 Topic : Fractions Topic Integers Topic Decimals Topic Fractions Topic Ratios Topic Percentages Duration / weeks Content Outline PART (/ week) Introduction Converting Fractions to Decimals Converting Decimals
Topic : Fractions Topic Integers Topic Decimals Topic Fractions Topic Ratios Topic Percentages Duration / weeks Content Outline PART (/ week) Introduction Converting Fractions to Decimals Converting Decimals
Abstraction. Abstraction
 9/11/2003 1 Software today is more complex than it has ever been. Software controls Space shuttle systems during launch Elevators in 100-story buildings Cross-Atlantic transportation routes of freighters
9/11/2003 1 Software today is more complex than it has ever been. Software controls Space shuttle systems during launch Elevators in 100-story buildings Cross-Atlantic transportation routes of freighters
Dr. Scheme evaluates expressions so we will start by using the interactions window and asking Dr. Scheme to evaluate some expressions.
 1.0 Expressions Dr. Scheme evaluates expressions so we will start by using the interactions window and asking Dr. Scheme to evaluate some expressions. Numbers are examples of primitive expressions, meaning
1.0 Expressions Dr. Scheme evaluates expressions so we will start by using the interactions window and asking Dr. Scheme to evaluate some expressions. Numbers are examples of primitive expressions, meaning
Understanding Recursion
 Understanding Recursion sk, rob and dbtucker (modified for CS 536 by kfisler) 2002-09-20 Writing a Recursive Function Can we write the factorial function in AFunExp? Well, we currently don t have multiplication,
Understanding Recursion sk, rob and dbtucker (modified for CS 536 by kfisler) 2002-09-20 Writing a Recursive Function Can we write the factorial function in AFunExp? Well, we currently don t have multiplication,
Lesson #17 Function Introduction
 Lesson #17 Function Introduction A.A.37 A.A.40 A.A.41 Define a relation and function Write functions in functional notation Use functional notation to evaluate functions for given values in the domain
Lesson #17 Function Introduction A.A.37 A.A.40 A.A.41 Define a relation and function Write functions in functional notation Use functional notation to evaluate functions for given values in the domain
Object-Oriented Design גרא וייס המחלקה למדעי המחשב אוניברסיטת בן-גוריון
 Object-Oriented Design גרא וייס המחלקה למדעי המחשב אוניברסיטת בן-גוריון 2 Why Start with Design? Object-oriented thinking begins with objectoriented design It is the easiest way to see the problems of
Object-Oriented Design גרא וייס המחלקה למדעי המחשב אוניברסיטת בן-גוריון 2 Why Start with Design? Object-oriented thinking begins with objectoriented design It is the easiest way to see the problems of
Chapter 3: Modules. Starting Out with Programming Logic & Design. Second Edition. by Tony Gaddis
 Chapter 3: Modules Starting Out with Programming Logic & Design Second Edition by Tony Gaddis Copyright 2010 Pearson Education, Inc. Publishing as Pearson Addison-Wesley Chapter Topics 3.1 Introduction
Chapter 3: Modules Starting Out with Programming Logic & Design Second Edition by Tony Gaddis Copyright 2010 Pearson Education, Inc. Publishing as Pearson Addison-Wesley Chapter Topics 3.1 Introduction
MAS115: R programming Lecture 2: Pseudocode Lab Class and Technical Material: Matrices, Factors, Data frames, Lists
 MAS115: R programming Lecture 2: Pseudocode Lab Class and Technical Material: Matrices, Factors, Data frames, Lists The University of Sheffield School of Mathematics and Statistics Problems Class Aims
MAS115: R programming Lecture 2: Pseudocode Lab Class and Technical Material: Matrices, Factors, Data frames, Lists The University of Sheffield School of Mathematics and Statistics Problems Class Aims
SP 713 Slide Rule Practice for our MIT Museum visit By Alva Couch and Elizabeth Cavicchi
 SP 713 Slide Rule Practice for our MIT Museum visit By Alva Couch and Elizabeth Cavicchi On your slide rule, look for the rows of short vertical marks, with numbers just above them. Notice how the spacing
SP 713 Slide Rule Practice for our MIT Museum visit By Alva Couch and Elizabeth Cavicchi On your slide rule, look for the rows of short vertical marks, with numbers just above them. Notice how the spacing
Software Design Fundamentals. CSCE Lecture 11-09/27/2016
 Software Design Fundamentals CSCE 740 - Lecture 11-09/27/2016 Today s Goals Define design Introduce the design process Overview of design criteria What results in a good design? Gregory Gay CSCE 740 -
Software Design Fundamentals CSCE 740 - Lecture 11-09/27/2016 Today s Goals Define design Introduce the design process Overview of design criteria What results in a good design? Gregory Gay CSCE 740 -
such a manner that we are able to understand, grasp and grapple with the problem at hand in a more organized fashion.
 Programming and Data Structure Dr.P.P.Chakraborty Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 32 Conclusions Hello everybody. Today, we come to the
Programming and Data Structure Dr.P.P.Chakraborty Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 32 Conclusions Hello everybody. Today, we come to the
CS61A Notes Week 6: Scheme1, Data Directed Programming You Are Scheme and don t let anyone tell you otherwise
 CS61A Notes Week 6: Scheme1, Data Directed Programming You Are Scheme and don t let anyone tell you otherwise If you re not already crazy about Scheme (and I m sure you are), then here s something to get
CS61A Notes Week 6: Scheme1, Data Directed Programming You Are Scheme and don t let anyone tell you otherwise If you re not already crazy about Scheme (and I m sure you are), then here s something to get
The Christmas motives which served as a base for the cookie cutters.
 Seasonal 3D Printing 3D Printed Cookie Cutters (Part 2) As described in yesterday s blog post, cookiecaster.com is a neat and free service to create your own cookie cutters within minutes. However, the
Seasonal 3D Printing 3D Printed Cookie Cutters (Part 2) As described in yesterday s blog post, cookiecaster.com is a neat and free service to create your own cookie cutters within minutes. However, the
Chapter 9. Software Testing
 Chapter 9. Software Testing Table of Contents Objectives... 1 Introduction to software testing... 1 The testers... 2 The developers... 2 An independent testing team... 2 The customer... 2 Principles of
Chapter 9. Software Testing Table of Contents Objectives... 1 Introduction to software testing... 1 The testers... 2 The developers... 2 An independent testing team... 2 The customer... 2 Principles of
Unit II. (i) Computer Programming Languages
 Unit II. (i) Computer Programming Languages Need of a computer programming language: A programming language is an artificial language designed to communicate instructions to a computer. Thousands of different
Unit II. (i) Computer Programming Languages Need of a computer programming language: A programming language is an artificial language designed to communicate instructions to a computer. Thousands of different
Programming Logic and Design Seventh Edition Chapter 2 Elements of High-Quality Programs
 Programming Logic and Design Chapter 2 Elements of High-Quality Programs Objectives In this chapter, you will learn about: Declaring and using variables and constants Assigning values to variables [assignment
Programming Logic and Design Chapter 2 Elements of High-Quality Programs Objectives In this chapter, you will learn about: Declaring and using variables and constants Assigning values to variables [assignment
JavaScript V. Higher Order Functions
 JavaScript V Higher Order Functions Tzu-li and Tzu-ssu were boasting about the size of their latest programs. Two-hundred thousand lines, said Tzu-li, not counting comments! Tzu-ssu responded, Pssh, mine
JavaScript V Higher Order Functions Tzu-li and Tzu-ssu were boasting about the size of their latest programs. Two-hundred thousand lines, said Tzu-li, not counting comments! Tzu-ssu responded, Pssh, mine
Chapter Twelve. Systems Design and Development
 Chapter Twelve Systems Design and Development After reading this chapter, you should be able to: Describe the process of designing, programming, and debugging a computer program Explain why there are many
Chapter Twelve Systems Design and Development After reading this chapter, you should be able to: Describe the process of designing, programming, and debugging a computer program Explain why there are many
ITC213: STRUCTURED PROGRAMMING. Bhaskar Shrestha National College of Computer Studies Tribhuvan University
 ITC213: STRUCTURED PROGRAMMING Bhaskar Shrestha National College of Computer Studies Tribhuvan University Lecture 02: Algorithms Readings: Not Covered in Textbook Problem Solving Process System Design:
ITC213: STRUCTURED PROGRAMMING Bhaskar Shrestha National College of Computer Studies Tribhuvan University Lecture 02: Algorithms Readings: Not Covered in Textbook Problem Solving Process System Design:
Rationale for TR Extension to the programming language C. Decimal Floating-Point Arithmetic
 WG14 N1161 Rationale for TR 24732 Extension to the programming language C Decimal Floating-Point Arithmetic Contents 1 Introduction... 1 1.1 Background... 1 1.2 The Arithmetic Model... 3 1.3 The Encodings...
WG14 N1161 Rationale for TR 24732 Extension to the programming language C Decimal Floating-Point Arithmetic Contents 1 Introduction... 1 1.1 Background... 1 1.2 The Arithmetic Model... 3 1.3 The Encodings...
1.8 Database and data modelling
 Introduction Organizations often maintain large amounts of data, which are generated as a result of day-to-day operations. A database is an organized form of such data. It may consist of one or more related
Introduction Organizations often maintain large amounts of data, which are generated as a result of day-to-day operations. A database is an organized form of such data. It may consist of one or more related
Part II Composition of Functions
 Part II Composition of Functions The big idea in this part of the book is deceptively simple. It s that we can take the value returned by one function and use it as an argument to another function. By
Part II Composition of Functions The big idea in this part of the book is deceptively simple. It s that we can take the value returned by one function and use it as an argument to another function. By
Big Ideas. Chapter Computational Recipes
 Chapter 1 Big Ideas This course is an introduction to programming and problem solving. We shall focus on some big ideas of computer science key themes that are seen again and again throughout the discipline.
Chapter 1 Big Ideas This course is an introduction to programming and problem solving. We shall focus on some big ideas of computer science key themes that are seen again and again throughout the discipline.
Math 1: Solutions to Written Homework 1 Due Friday, October 3, 2008
 Instructions: You are encouraged to work out solutions to these problems in groups! Discuss the problems with your classmates, the tutors and/or the instructors. After working doing so, please write up
Instructions: You are encouraged to work out solutions to these problems in groups! Discuss the problems with your classmates, the tutors and/or the instructors. After working doing so, please write up
Programming II. Modularity 2017/18
 Programming II Modularity 2017/18 Module? Lecture Outline Evolution and history of programming languages Modularity Example History of Programming Programming Paradigms How and why languages develop? How
Programming II Modularity 2017/18 Module? Lecture Outline Evolution and history of programming languages Modularity Example History of Programming Programming Paradigms How and why languages develop? How
An Interesting Way to Combine Numbers
 An Interesting Way to Combine Numbers Joshua Zucker and Tom Davis October 12, 2016 Abstract This exercise can be used for middle school students and older. The original problem seems almost impossibly
An Interesting Way to Combine Numbers Joshua Zucker and Tom Davis October 12, 2016 Abstract This exercise can be used for middle school students and older. The original problem seems almost impossibly
Introduction to Computer Programming Using FORTRAN 77
 Introduction to Computer Programming Using FORTRAN 77 Al-Dhaher, K. Garout, Y. Lafi, A. Al-Muhtaseb, H. Nazzal, A. Saeed, M. Yazdani, J. Zeidan, Y. August 1995 Second Edition Information and Computer Science
Introduction to Computer Programming Using FORTRAN 77 Al-Dhaher, K. Garout, Y. Lafi, A. Al-Muhtaseb, H. Nazzal, A. Saeed, M. Yazdani, J. Zeidan, Y. August 1995 Second Edition Information and Computer Science
Unit 4: Multiplication
 Math Fundamentals for Statistics I (Math 52) Unit 4: Multiplication By Scott Fallstrom and Brent Pickett The How and Whys Guys This work is licensed under a Creative Commons Attribution- NonCommercial-ShareAlike
Math Fundamentals for Statistics I (Math 52) Unit 4: Multiplication By Scott Fallstrom and Brent Pickett The How and Whys Guys This work is licensed under a Creative Commons Attribution- NonCommercial-ShareAlike
Higher Computing Science Software Design and Development - Programming Summary Notes
 Higher Computing Science Software Design and Development - Programming Summary Notes Design notations A design notation is the method we use to write down our program design. Pseudocode is written using
Higher Computing Science Software Design and Development - Programming Summary Notes Design notations A design notation is the method we use to write down our program design. Pseudocode is written using
Summary See complete responses
 1 of 6 12/17/2010 2:27 AM responses Summary See complete responses What is your initial impression of the site? 3 1 8% 4 8 67% 5-3 25% Task: Finding a recipe For your first task, I'd like you to find a
1 of 6 12/17/2010 2:27 AM responses Summary See complete responses What is your initial impression of the site? 3 1 8% 4 8 67% 5-3 25% Task: Finding a recipe For your first task, I'd like you to find a
Creating and Using File Folders
 Creating and Using File Folders ~ 1 ~ Creating and Using File Folders Introduction: File Folders are named storage areas which we create in our computers to keep any documents, pictures, music, videos
Creating and Using File Folders ~ 1 ~ Creating and Using File Folders Introduction: File Folders are named storage areas which we create in our computers to keep any documents, pictures, music, videos
Lecture Notes on Memory Layout
 Lecture Notes on Memory Layout 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 11 1 Introduction In order to understand how programs work, we can consider the functions,
Lecture Notes on Memory Layout 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 11 1 Introduction In order to understand how programs work, we can consider the functions,
Difference Between Dates Case Study 2002 M. J. Clancy and M. C. Linn
 Difference Between Dates Case Study 2002 M. J. Clancy and M. C. Linn Problem Write and test a Scheme program to compute how many days are spanned by two given days. The program will include a procedure
Difference Between Dates Case Study 2002 M. J. Clancy and M. C. Linn Problem Write and test a Scheme program to compute how many days are spanned by two given days. The program will include a procedure
The way I feel about music is that there is no right and wrong. Only true and false. Fiona Apple. true false false
 5 Conditionals Conditionals 59 That language is an instrument of human reason, and not merely a medium for the expression of thought, is a truth generally admitted. George Boole The way I feel about music
5 Conditionals Conditionals 59 That language is an instrument of human reason, and not merely a medium for the expression of thought, is a truth generally admitted. George Boole The way I feel about music
FLOW CHART AND PSEUDO CODE
 FLOW CHART AND PSEUDO CODE Flowchart A Flowchart is a pictorial representation of an algorithm. The First flowchart is made by John Von Newman in 1945. It is a symbolic diagram of operation sequence, dataflow,
FLOW CHART AND PSEUDO CODE Flowchart A Flowchart is a pictorial representation of an algorithm. The First flowchart is made by John Von Newman in 1945. It is a symbolic diagram of operation sequence, dataflow,
CP122 CS I. Chapter 1: Introduction
 CP122 CS I Chapter 1: Introduction Introductions Webpage and Syllabus cs.coloradocollege.edu/~mwhitehead Hacker's Tip of the Day Hacker A person interested in how things work. A critical thinker, an endless
CP122 CS I Chapter 1: Introduction Introductions Webpage and Syllabus cs.coloradocollege.edu/~mwhitehead Hacker's Tip of the Day Hacker A person interested in how things work. A critical thinker, an endless
EXAMINING THE CODE. 1. Examining the Design and Code 2. Formal Review: 3. Coding Standards and Guidelines: 4. Generic Code Review Checklist:
 EXAMINING THE CODE CONTENTS I. Static White Box Testing II. 1. Examining the Design and Code 2. Formal Review: 3. Coding Standards and Guidelines: 4. Generic Code Review Checklist: Dynamic White Box Testing
EXAMINING THE CODE CONTENTS I. Static White Box Testing II. 1. Examining the Design and Code 2. Formal Review: 3. Coding Standards and Guidelines: 4. Generic Code Review Checklist: Dynamic White Box Testing
STATISTICAL TECHNIQUES. Interpreting Basic Statistical Values
 STATISTICAL TECHNIQUES Interpreting Basic Statistical Values INTERPRETING BASIC STATISTICAL VALUES Sample representative How would one represent the average or typical piece of information from a given
STATISTICAL TECHNIQUES Interpreting Basic Statistical Values INTERPRETING BASIC STATISTICAL VALUES Sample representative How would one represent the average or typical piece of information from a given
HOW TO DIVIDE: MCC6.NS.2 Fluently divide multi-digit numbers using the standard algorithm. WORD DEFINITION IN YOUR WORDS EXAMPLE
 MCC6.NS. Fluently divide multi-digit numbers using the standard algorithm. WORD DEFINITION IN YOUR WORDS EXAMPLE Dividend A number that is divided by another number. Divisor A number by which another number
MCC6.NS. Fluently divide multi-digit numbers using the standard algorithm. WORD DEFINITION IN YOUR WORDS EXAMPLE Dividend A number that is divided by another number. Divisor A number by which another number
Interaction Design. Task Analysis & Modelling
 Interaction Design Task Analysis & Modelling This Lecture Conducting task analysis Constructing task models Understanding the shortcomings of task analysis Task Analysis for Interaction Design Find out
Interaction Design Task Analysis & Modelling This Lecture Conducting task analysis Constructing task models Understanding the shortcomings of task analysis Task Analysis for Interaction Design Find out
Binghamton University. CS-211 Fall Software Design
 Software Design 1 Typical Life Cycle of an Application Requirements Evaluate Design Support Implement 2 Design starts from Specifications No good formal method of capturing specifications Figuring out
Software Design 1 Typical Life Cycle of an Application Requirements Evaluate Design Support Implement 2 Design starts from Specifications No good formal method of capturing specifications Figuring out
Intro. Scheme Basics. scm> 5 5. scm>
 Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
Going Modular: Turning Legacy Docs into User Story-Based Content. Open Source Summit Europe 2017
 Going Modular: Turning Legacy Docs into User Story-Based Content Open Source Summit Europe 2017 Robert Krátký, rkratky@redhat.com Principal Technical Writer, Red Hat IN THIS PRESENTATION 1. Terminology,
Going Modular: Turning Legacy Docs into User Story-Based Content Open Source Summit Europe 2017 Robert Krátký, rkratky@redhat.com Principal Technical Writer, Red Hat IN THIS PRESENTATION 1. Terminology,
Checking for an existing school record and entering your school name
 Registering for tournaments using SpeechWire.com In order to register for a tournament that is using SpeechWire to run its entry registration, you will need to create a free SpeechWire registration account
Registering for tournaments using SpeechWire.com In order to register for a tournament that is using SpeechWire to run its entry registration, you will need to create a free SpeechWire registration account
INTRODUCTION TO ALGORITHMS
 INTRODUCTION TO ALGORITHMS Logic Logic is a tool to develop reasonable conclusions based on a given set of data. Logic is free of emotion and deals very specifically with information in its purest form.
INTRODUCTION TO ALGORITHMS Logic Logic is a tool to develop reasonable conclusions based on a given set of data. Logic is free of emotion and deals very specifically with information in its purest form.
World-level Classes and Methods. Chapter 6
 World-level Classes and Methods Chapter 6 Programs Grow Code seems to grow and grow Makes program more difficult to read and process in our minds Games and other software can have thousands, even millions
World-level Classes and Methods Chapter 6 Programs Grow Code seems to grow and grow Makes program more difficult to read and process in our minds Games and other software can have thousands, even millions
You might already know that tables are organized into vertical columns and horizontal rows.
 Access 2013 Introduction to Objects Introduction Databases in Access are composed of four objects: tables, queries, forms, and reports. Together, these objects allow you to enter, store, analyze, and compile
Access 2013 Introduction to Objects Introduction Databases in Access are composed of four objects: tables, queries, forms, and reports. Together, these objects allow you to enter, store, analyze, and compile
Case study on PhoneGap / Apache Cordova
 Chapter 1 Case study on PhoneGap / Apache Cordova 1.1 Introduction to PhoneGap / Apache Cordova PhoneGap is a free and open source framework that allows you to create mobile applications in a cross platform
Chapter 1 Case study on PhoneGap / Apache Cordova 1.1 Introduction to PhoneGap / Apache Cordova PhoneGap is a free and open source framework that allows you to create mobile applications in a cross platform
Menu Reference Guide
 Menu Reference Guide Overview Introduction to Toast Menus a.) Important Concepts Saving and Publishing Menu Hierarchy a.) Menus Adding New Menus Ordering of Menus Deleting Menus Renaming Existing Menus
Menu Reference Guide Overview Introduction to Toast Menus a.) Important Concepts Saving and Publishing Menu Hierarchy a.) Menus Adding New Menus Ordering of Menus Deleting Menus Renaming Existing Menus
CREATIVE ASSERTION AND CONSTRAINT METHODS FOR FORMAL DESIGN VERIFICATION
 CREATIVE ASSERTION AND CONSTRAINT METHODS FOR FORMAL DESIGN VERIFICATION Joseph Richards SGI, High Performance Systems Development Mountain View, CA richards@sgi.com Abstract The challenges involved in
CREATIVE ASSERTION AND CONSTRAINT METHODS FOR FORMAL DESIGN VERIFICATION Joseph Richards SGI, High Performance Systems Development Mountain View, CA richards@sgi.com Abstract The challenges involved in
6.001 Notes: Section 6.1
 6.001 Notes: Section 6.1 Slide 6.1.1 When we first starting talking about Scheme expressions, you may recall we said that (almost) every Scheme expression had three components, a syntax (legal ways of
6.001 Notes: Section 6.1 Slide 6.1.1 When we first starting talking about Scheme expressions, you may recall we said that (almost) every Scheme expression had three components, a syntax (legal ways of
Introduction to programming (LT2111) Lecture 1: Introduction
 Introduction to programming (LT2111) Lecture 1: Introduction Richard Johansson September 2, 2014 Introduction & Administration The main goal of the course is that you will learn how to program using the
Introduction to programming (LT2111) Lecture 1: Introduction Richard Johansson September 2, 2014 Introduction & Administration The main goal of the course is that you will learn how to program using the
Python - Week 1. Mohammad Shokoohi-Yekta
 Python - Week 1 Mohammad Shokoohi-Yekta 1 An Introduction to Computers and Problem Solving 1.1 An Introduction to Computers 1.2 Program Development Cycle 1.3 Programming Tools 1.4 Starting Python 2 Communicating
Python - Week 1 Mohammad Shokoohi-Yekta 1 An Introduction to Computers and Problem Solving 1.1 An Introduction to Computers 1.2 Program Development Cycle 1.3 Programming Tools 1.4 Starting Python 2 Communicating
potions. The troll doubles in size.
 Tutorial 3: Use Procedures and Arguments, Add Rotation and Randomization Overview In this tutorial, you will practice using procedures and arguments to create an animation. You will practice rotating an
Tutorial 3: Use Procedures and Arguments, Add Rotation and Randomization Overview In this tutorial, you will practice using procedures and arguments to create an animation. You will practice rotating an
St. Benedict s High School. Computing Science. Software Design & Development. (Part 1 Computer Programming) National 5
 Computing Science Software Design & Development (Part 1 Computer Programming) National 5 VARIABLES & DATA TYPES Variables provide temporary storage for information that will be needed while a program is
Computing Science Software Design & Development (Part 1 Computer Programming) National 5 VARIABLES & DATA TYPES Variables provide temporary storage for information that will be needed while a program is
Divisibility Rules and Their Explanations
 Divisibility Rules and Their Explanations Increase Your Number Sense These divisibility rules apply to determining the divisibility of a positive integer (1, 2, 3, ) by another positive integer or 0 (although
Divisibility Rules and Their Explanations Increase Your Number Sense These divisibility rules apply to determining the divisibility of a positive integer (1, 2, 3, ) by another positive integer or 0 (although
Chapter Two: Classes and Objects
 Chapter Two: Classes and Objects Section 1: Real Objects Versus Virtual Objects Computer games do not have to match reality. In them we can violate the rules of physics (or make up our own), pigs can fly
Chapter Two: Classes and Objects Section 1: Real Objects Versus Virtual Objects Computer games do not have to match reality. In them we can violate the rules of physics (or make up our own), pigs can fly
Students interpret the meaning of the point of intersection of two graphs and use analytic tools to find its coordinates.
 Student Outcomes Students interpret the meaning of the point of intersection of two graphs and use analytic tools to find its coordinates. Classwork Example 1 (7 minutes) Have students read the situation
Student Outcomes Students interpret the meaning of the point of intersection of two graphs and use analytic tools to find its coordinates. Classwork Example 1 (7 minutes) Have students read the situation
UNIT II Requirements Analysis and Specification & Software Design
 UNIT II Requirements Analysis and Specification & Software Design Requirements Analysis and Specification Many projects fail: because they start implementing the system: without determining whether they
UNIT II Requirements Analysis and Specification & Software Design Requirements Analysis and Specification Many projects fail: because they start implementing the system: without determining whether they
THE OBJECT-ORIENTED DESIGN PROCESS AND DESIGN AXIOMS (CH -9)
 THE OBJECT-ORIENTED DESIGN PROCESS AND DESIGN AXIOMS (CH -9) By: Mr.Prachet Bhuyan Assistant Professor, School of Computer Engineering, KIIT Topics to be Discussed 9.1 INTRODUCTION 9.2 THE O-O DESIGN PROCESS
THE OBJECT-ORIENTED DESIGN PROCESS AND DESIGN AXIOMS (CH -9) By: Mr.Prachet Bhuyan Assistant Professor, School of Computer Engineering, KIIT Topics to be Discussed 9.1 INTRODUCTION 9.2 THE O-O DESIGN PROCESS
Principles of Algorithm Design
 Principles of Algorithm Design When you are trying to design an algorithm or a data structure, it s often hard to see how to accomplish the task. The following techniques can often be useful: 1. Experiment
Principles of Algorithm Design When you are trying to design an algorithm or a data structure, it s often hard to see how to accomplish the task. The following techniques can often be useful: 1. Experiment
Working with Health IT Systems is available under a Creative Commons Attribution-NonCommercial- ShareAlike 3.0 Unported license.
 Working with Health IT Systems is available under a Creative Commons Attribution-NonCommercial- ShareAlike 3.0 Unported license. Johns Hopkins University. Welcome to the Fundamentals of Health Workflow
Working with Health IT Systems is available under a Creative Commons Attribution-NonCommercial- ShareAlike 3.0 Unported license. Johns Hopkins University. Welcome to the Fundamentals of Health Workflow
communications and software
 1 Computer systems, communications and software 1.1 Components of a computer system and modes of use A computer system is made up of hardware and flow of data and information. The storage device is both
1 Computer systems, communications and software 1.1 Components of a computer system and modes of use A computer system is made up of hardware and flow of data and information. The storage device is both
II. Linear Programming
 II. Linear Programming A Quick Example Suppose we own and manage a small manufacturing facility that produced television sets. - What would be our organization s immediate goal? - On what would our relative
II. Linear Programming A Quick Example Suppose we own and manage a small manufacturing facility that produced television sets. - What would be our organization s immediate goal? - On what would our relative
Building Java Programs
 Comments Building Java Programs Chapter 1 Lecture 1-2: Static Methods reading: 1.4-1.5 comment: A note written in source code by the programmer to describe or clarify the code. Comments are not executed
Comments Building Java Programs Chapter 1 Lecture 1-2: Static Methods reading: 1.4-1.5 comment: A note written in source code by the programmer to describe or clarify the code. Comments are not executed
Fortunately, you only need to know 10% of what's in the main page to get 90% of the benefit. This page will show you that 10%.
 NAME DESCRIPTION perlreftut - Mark's very short tutorial about references One of the most important new features in Perl 5 was the capability to manage complicated data structures like multidimensional
NAME DESCRIPTION perlreftut - Mark's very short tutorial about references One of the most important new features in Perl 5 was the capability to manage complicated data structures like multidimensional
Operating systems and security - Overview
 Operating systems and security - Overview Protection in Operating systems Protected objects Protecting memory, files User authentication, especially passwords Trusted operating systems, security kernels,
Operating systems and security - Overview Protection in Operating systems Protected objects Protecting memory, files User authentication, especially passwords Trusted operating systems, security kernels,
Operating systems and security - Overview
 Operating systems and security - Overview Protection in Operating systems Protected objects Protecting memory, files User authentication, especially passwords Trusted operating systems, security kernels,
Operating systems and security - Overview Protection in Operating systems Protected objects Protecting memory, files User authentication, especially passwords Trusted operating systems, security kernels,
Trombone players produce different pitches partly by varying the length of a tube.
 Trombone players produce different pitches partly by varying the length of a tube. 7 Variables A variable is a connection between a name and a value.* That sounds simple enough, but some complexities arise
Trombone players produce different pitches partly by varying the length of a tube. 7 Variables A variable is a connection between a name and a value.* That sounds simple enough, but some complexities arise
CP122 CS I. Hello, World!
 CP122 CS I Hello, World! Introductions Webpage and Syllabus cs.coloradocollege.edu/~mwhitehead Tech News! AlphaGo Zero defeats AlphaGo 100 games to 0. Tech News! AlphaGo Zero defeats AlphaGo 100 games
CP122 CS I Hello, World! Introductions Webpage and Syllabus cs.coloradocollege.edu/~mwhitehead Tech News! AlphaGo Zero defeats AlphaGo 100 games to 0. Tech News! AlphaGo Zero defeats AlphaGo 100 games
Key Learning for Grade 3
 Key Learning for Grade 3 The Ontario Curriculum: Mathematics (2005) Number Sense and Numeration Read, represent, compare and order whole numbers to 1000, and use concrete materials to investigate fractions
Key Learning for Grade 3 The Ontario Curriculum: Mathematics (2005) Number Sense and Numeration Read, represent, compare and order whole numbers to 1000, and use concrete materials to investigate fractions
Introduction CHAPTER1. Strongly Recommend: Guidelines that, if not followed, could result in an unusable application.
 sg-midp20.book Page 1 Wednesday, May 14, 2003 1:27 PM CHAPTER1 Introduction MOBILE Information Device Profile (MIDP) defines the Java application environment for mobile information devices (MIDs), such
sg-midp20.book Page 1 Wednesday, May 14, 2003 1:27 PM CHAPTER1 Introduction MOBILE Information Device Profile (MIDP) defines the Java application environment for mobile information devices (MIDs), such
Database Architectures
 Database Architectures CPS352: Database Systems Simon Miner Gordon College Last Revised: 11/15/12 Agenda Check-in Centralized and Client-Server Models Parallelism Distributed Databases Homework 6 Check-in
Database Architectures CPS352: Database Systems Simon Miner Gordon College Last Revised: 11/15/12 Agenda Check-in Centralized and Client-Server Models Parallelism Distributed Databases Homework 6 Check-in
PROGRAMMING LANGUAGE PARADIGMS & THE MAIN PRINCIPLES OF OBJECT-ORIENTED PROGRAMMING
 10.2478/cris-2013-0011 PROGRAMMING LANGUAGE PARADIGMS & THE MAIN PRINCIPLES OF OBJECT-ORIENTED PROGRAMMING NIKOLETTA MINAROVA 77 INTRODUCTION Since the first design concept of computers came into the world,
10.2478/cris-2013-0011 PROGRAMMING LANGUAGE PARADIGMS & THE MAIN PRINCIPLES OF OBJECT-ORIENTED PROGRAMMING NIKOLETTA MINAROVA 77 INTRODUCTION Since the first design concept of computers came into the world,
Practice 1 1: Instance or Entity
 Practice 1 1: Instance or Entity Practice 1 1: Instance or Entity Goal (See Page 47) The goal of this practice is to learn to make a distinction between an entity, an attribute, and an instance of an entity.
Practice 1 1: Instance or Entity Practice 1 1: Instance or Entity Goal (See Page 47) The goal of this practice is to learn to make a distinction between an entity, an attribute, and an instance of an entity.
DMN Section 11 Loan Origination Example. By Maarten P.D. Schadd Senior Product Consultant at Blueriq B.V.
 DMN Section 11 Loan Origination Example By Maarten P.D. Schadd Senior Product Consultant at Blueriq B.V. Contents 1 Introduction......................................... 3 2 Problem definition.....................................
DMN Section 11 Loan Origination Example By Maarten P.D. Schadd Senior Product Consultant at Blueriq B.V. Contents 1 Introduction......................................... 3 2 Problem definition.....................................
1: Introduction to Object (1)
 1: Introduction to Object (1) 김동원 2003.01.20 Overview (1) The progress of abstraction Smalltalk Class & Object Interface The hidden implementation Reusing the implementation Inheritance: Reusing the interface
1: Introduction to Object (1) 김동원 2003.01.20 Overview (1) The progress of abstraction Smalltalk Class & Object Interface The hidden implementation Reusing the implementation Inheritance: Reusing the interface
Alverton Community Primary School
 Year 1 I can tell an adult if I see anything worrying online. I can give instructions to my friend and follow their instructions to move around. I can describe what happens when I press buttons on a robot.
Year 1 I can tell an adult if I see anything worrying online. I can give instructions to my friend and follow their instructions to move around. I can describe what happens when I press buttons on a robot.
Pre-Algebra Notes Unit 8: Graphs and Functions
 Pre-Algebra Notes Unit 8: Graphs and Functions The Coordinate Plane A coordinate plane is formed b the intersection of a horizontal number line called the -ais and a vertical number line called the -ais.
Pre-Algebra Notes Unit 8: Graphs and Functions The Coordinate Plane A coordinate plane is formed b the intersection of a horizontal number line called the -ais and a vertical number line called the -ais.
Guidelines for Coding of SAS Programs Thomas J. Winn, Jr. Texas State Auditor s Office
 Guidelines for Coding of SAS Programs Thomas J. Winn, Jr. Texas State Auditor s Office Abstract This paper presents a set of proposed guidelines that could be used for writing SAS code that is clear, efficient,
Guidelines for Coding of SAS Programs Thomas J. Winn, Jr. Texas State Auditor s Office Abstract This paper presents a set of proposed guidelines that could be used for writing SAS code that is clear, efficient,
6.001 Notes: Section 4.1
 6.001 Notes: Section 4.1 Slide 4.1.1 In this lecture, we are going to take a careful look at the kinds of procedures we can build. We will first go back to look very carefully at the substitution model,
6.001 Notes: Section 4.1 Slide 4.1.1 In this lecture, we are going to take a careful look at the kinds of procedures we can build. We will first go back to look very carefully at the substitution model,
Register Transfer Level
 Register Transfer Level Something between the logic level and the architecture level A convenient way to describe synchronous sequential systems State diagrams for pros Hierarchy of Designs The design
Register Transfer Level Something between the logic level and the architecture level A convenient way to describe synchronous sequential systems State diagrams for pros Hierarchy of Designs The design
Classes, Objects, and World-level Methods. Alice
 Classes, Objects, and World-level Methods Alice Larger Programs As you become more skilled in writing programs, you will find that programs quickly increase to many, many lines of code. Games and other
Classes, Objects, and World-level Methods Alice Larger Programs As you become more skilled in writing programs, you will find that programs quickly increase to many, many lines of code. Games and other
Topic 3 static Methods and Structured Programming
 Topic 3 static Methods and Structured Programming "The cleaner and nicer the program, the faster it's going to run. And if it doesn't, it'll be easy to make it fast." -Joshua Bloch Based on slides by Marty
Topic 3 static Methods and Structured Programming "The cleaner and nicer the program, the faster it's going to run. And if it doesn't, it'll be easy to make it fast." -Joshua Bloch Based on slides by Marty
FLOWCHARTS A flowchart is a graphical representation of the steps to be followed for solving problem. It consists of a set of symbols.
 FLOWCHARTS A flowchart is a graphical representation of the steps to be followed for solving problem. It consists of a set of symbols. Each symbol represents a specific activity. A typical problem involves
FLOWCHARTS A flowchart is a graphical representation of the steps to be followed for solving problem. It consists of a set of symbols. Each symbol represents a specific activity. A typical problem involves
TASKS IN THE SYSTEMS DEVELOPMENT LIFE CYCLE
 SUMMARY AND REFERENCE ACTG 313 TASKS IN THE SYSTEMS DEVELOPMENT LIFE CYCLE PREPARATION PHASE 1. Identification of the Need for a new Information System 2. Initial Feasibility Study (always flawed because
SUMMARY AND REFERENCE ACTG 313 TASKS IN THE SYSTEMS DEVELOPMENT LIFE CYCLE PREPARATION PHASE 1. Identification of the Need for a new Information System 2. Initial Feasibility Study (always flawed because
Limits. f(x) and lim. g(x) g(x)
 Limits Limit Laws Suppose c is constant, n is a positive integer, and f() and g() both eist. Then,. [f() + g()] = f() + g() 2. [f() g()] = f() g() [ ] 3. [c f()] = c f() [ ] [ ] 4. [f() g()] = f() g()
Limits Limit Laws Suppose c is constant, n is a positive integer, and f() and g() both eist. Then,. [f() + g()] = f() + g() 2. [f() g()] = f() g() [ ] 3. [c f()] = c f() [ ] [ ] 4. [f() g()] = f() g()
