Integrating Soar into the OneSAF Models Framework. Dr. Doug Reece
|
|
|
- Derick Clarke
- 5 years ago
- Views:
Transcription
1 Integrating Soar into the OneSAF Models Framework Dr. Doug Reece
2 Outline OneSAF Modeling Infrastructure (MI) overview Emphasis on entity architecture Ideas for integrating Soar Not interfacing 2
3 OneSAF Summary A composable, next generation Computer-Generated Forces (CGF) that can represent a full range of operations, systems, and control process (TTP) from entity up to brigade level, with variable level of fidelity that supports multiple Army Modeling and Simulation (M&S) domains (ACR, RDA, TEMO) applications. Software only Automated Composable Extensible Interoperable Replaces legacy entity based Simulations: BBS - ModSAF - JANUS - CCTT SAF AVCATT SAF Platform Independent Fielded to: National Guard Armories RDECs / Battle Labs Reserve Training Centers All Active Duty Brigades and Battalions 3
4 Scalability Composability OneSAF Requirements Interoperability (HLA/DIS, WARSIM, CATT, and two-way, real-world C4I) Entity-based model that can display collective unit icons Composable equipment and units (up to battalion size) Complex automated behaviors Multiple sides (a minimum of 25) Manageability FLEXIBILITY User-friendly features (scalability, composability, and manageability) Dynamic data editors 2-D and 3-D visualization Data collection, analysis, and AAR graphics and tables Compatible with various hardware (WARSIM and PCs) Full Lifecycle Scenario Generation, Simulation Execution, AAR/Analysis Constructive Interoperability Interoperability WARSIM Interoperability Virtual CATT Linkage Live C4I Interface Manageability Data Editors: unit, organization, behavior, terrain, environment, battlefield graphics, user preferences, fire support, engineering, damage and equipment repair, logistics 4
5 MI Goals Just the infrastructure Behavior content comes later this year Represent normative military behavior Represent reactions to events SME-composition of behaviors (!) Software Engineer definition of primitive behaviors Predicate functions So once the primitives are done, the SMEs will program all the behavior 5
6 Entity Overview Entity Model Module or agent Module or agent Module or agent Module or agent Blackboard Behavior Execution agent Executable composed behaviors Behavior repository Entity description language defines entity modules 6
7 Entity Model Situation Assessment, Planning, Decision Making, Scheduling World Model Behavior Execution (infrastructure) Executable behavior Behavior model repository (infrastructure) Vulnerability (damage) Sensor Communications Movement Weapon Simulation Engine (infrastructure) 7
8 Blackboard All entity modules (agents) communicate via BB Modules must register to receive data Register for a class of data Detonations, communications, clock timers Execution is event driven On new event (data), BB executes all registrants New events (data) produced by modules causes second wave of execution Runs to quiescence Events do not persist on BB 8
9 World Model Stores perceptions, inferred facts Facts are instances of fact-class objects Pre-defined set of objects and attributes Rules in behavior models can assert or retract facts Pre-defined set of predicates and functions Rules combine predicates with boolean ops Matching may be limited (or not) E.g. (x) ( IF Entity(x) Tank(x) (Range(x) < 2000)) may be implemented by walking a known entity list 9
10 Behavior Models Flow chart-like action sequence descriptions Includes sequential, parallel, looping, and branching Use predicates to branch Actions can use parameters Parameters can be computed by preceeding actions Actions can be primitive or composite Include IF-THEN rules Assert facts or Start reactive behaviors Interaction between reactive and background behaviors still undefined 10
11 Behavior Model Language Structure 11
12 Behavior Modeling Editor 12
13 Primitive Behaviors Simple actions using physical agents in entity Put command data on blackboard, which triggers physical agents, OR Calls physical agent functions directly Process data make inferences Add facts to world model 13
14 Soar Rule-based engine + Facts Rules Goal stack 14
15 Facts Arbitrary object-attribute-value triples Working memory Special facts for input and output 15
16 General matcher Rules Modified RETE for efficiency Long-term memory Knowledge of preferences for taking action in certain situations 16
17 Soar Agent Interface code puts input data into facts New data may trigger rules Change decision anywhere in goal stack Make new subgoals from that point Make inferences outside of goal stack Put new data in output facts Runs to quiescence 17
18 Approach for Soar in OneSAF Replace all behavior agents with Soar Use OneSAF physical agents Primitive actions only Replace blackboard (Soar working memory) Replace world model (Soar working memory) Use OneSAF composed behaviors But don t execute in OneSAF infrastructure 18
19 Replace Blackboard Create interface between physical agents and Soar using OneSAF BB protocol Allows same physical agents to be used Interface puts input in working memory, sets triggers from working memory 19
20 Use Composed Behaviors Soar reads composed behaviors from OneSAF run-time repository Soar builds its own representation of order/behaviors Soar must implement the same named primitives used in behaviors Named facts Predicate functions Primitive behaviors 20
21 Soar Entity Model Example Soar engine and rules Working memory Soar representation of behavior model Soar-repository interface code Behavior model repository (infrastructure) Special input fact Special output fact Soar- Blackboard Interface code Vulnerability (damage) Sensor Communications Movement Weapon Simulation Engine (infrastructure) 21
22 Conclusion Interesting thought experiment for now Ideas? Simple examples? Interfaces Soar representation of flow-chart behavior 22
A Case-Based Behavior Design Aid for OneSAF
 A Case-Based Behavior Design Aid for OneSAF Douglas Reece Jenifer McCormack Jackie Zhang Science Applications International Corporation Outline Problem expense of CGF behavior building Solution approach
A Case-Based Behavior Design Aid for OneSAF Douglas Reece Jenifer McCormack Jackie Zhang Science Applications International Corporation Outline Problem expense of CGF behavior building Solution approach
A Design Method for Composition and Reuse Oriented Weaponry Model Architecture Meng Zhang1, a, Hong Wang1, Yiping Yao1, 2
 2nd International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 2016) A Design Method for Composition and Reuse Oriented Weaponry Model Architecture Meng Zhang1, a,
2nd International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 2016) A Design Method for Composition and Reuse Oriented Weaponry Model Architecture Meng Zhang1, a,
An Open Source MSDL/C-BML Interface to VR-Forces
 An Open Source MSDL/C-BML Interface to VR-Forces Dr. Mark Pullen Mohammad Ababneh Lisa Nicklas Michael Connor Alexandre Barreto GMU C4I Center 1 Presentation Outline Overview/Introduction BML and C-BML
An Open Source MSDL/C-BML Interface to VR-Forces Dr. Mark Pullen Mohammad Ababneh Lisa Nicklas Michael Connor Alexandre Barreto GMU C4I Center 1 Presentation Outline Overview/Introduction BML and C-BML
Product Training. VR-Forces Systems Training Syllabus. Section 1: Basics and Background
 Product Training VR-Forces Systems Training Syllabus This 1 week course will provide in-depth training on the VR-Forces computer generated forces product. The first section will focus on basic concepts,
Product Training VR-Forces Systems Training Syllabus This 1 week course will provide in-depth training on the VR-Forces computer generated forces product. The first section will focus on basic concepts,
24 February Dr. Harold Hawkins Program Officer Office of Naval Research Ballston Tower One 800 North Quincy Street Arlington, VA
 24 February 2006 Dr. Harold Hawkins Program Officer Office of Naval Research Ballston Tower One 800 North Quincy Street Arlington, VA 22217-5660 Subject: Reference: Case-Based Reasoning (CBR) Final Report
24 February 2006 Dr. Harold Hawkins Program Officer Office of Naval Research Ballston Tower One 800 North Quincy Street Arlington, VA 22217-5660 Subject: Reference: Case-Based Reasoning (CBR) Final Report
ACCELERATING ROUTE PLANNING AND COLLISION DETECTION FOR COMPUTER GENERATED FORCES USING GPUS
 ACCELERATING ROUTE PLANNING AND COLLISION DETECTION FOR COMPUTER GENERATED FORCES USING GPUS David Tuft, Russell Gayle, Brian Salomon, Naga Govindaraju, Ming Lin, and Dinesh Manocha University of North
ACCELERATING ROUTE PLANNING AND COLLISION DETECTION FOR COMPUTER GENERATED FORCES USING GPUS David Tuft, Russell Gayle, Brian Salomon, Naga Govindaraju, Ming Lin, and Dinesh Manocha University of North
Outline. CS5984 Mobile Computing. Dr. Ayman Abdel-Hamid, CS5984. Wireless Sensor Networks 1/2. Wireless Sensor Networks 2/2
 CS5984 Mobile Computing Outline : a Survey Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech An Introduction to 1 2 1/2 Advances in micro-electro-mechanical systems technology, wireless communications,
CS5984 Mobile Computing Outline : a Survey Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech An Introduction to 1 2 1/2 Advances in micro-electro-mechanical systems technology, wireless communications,
Using Datalog to Describe Simulation Capabilities
 U.S. Army Research, Development and Engineering Command Executable Scenario Definition Using Datalog to Describe Simulation Capabilities US Army Research Laboratory (ARL) Human Research and Engineering
U.S. Army Research, Development and Engineering Command Executable Scenario Definition Using Datalog to Describe Simulation Capabilities US Army Research Laboratory (ARL) Human Research and Engineering
TERRA VISTA CONTENT CREATION
 CONTENT CREATION TERRA VISTA MAP. ROUTE. GENERATE Terra Vista is a terrain generation software that converts imagery, elevation, vectors, and other GIS data into optimized 3D simulation-ready virtual environments.
CONTENT CREATION TERRA VISTA MAP. ROUTE. GENERATE Terra Vista is a terrain generation software that converts imagery, elevation, vectors, and other GIS data into optimized 3D simulation-ready virtual environments.
A Framework for Vulnerability/Lethality Modeling and Simulation National Industrial Association 47 th Annual Fuze Conference April 10, 2003
 A Framework for Vulnerability/Lethality Modeling and Simulation National Industrial Association 47 th Annual Fuze Conference April 10, 2003 Mr. Eric Scarborough (850) 678-5222 scarboro@ara ara.com Mr.
A Framework for Vulnerability/Lethality Modeling and Simulation National Industrial Association 47 th Annual Fuze Conference April 10, 2003 Mr. Eric Scarborough (850) 678-5222 scarboro@ara ara.com Mr.
A multi-threaded architecture for cognitive robotics. Keith Clark Imperial College London
 A multi-threaded architecture for cognitive robotics Keith Clark Imperial College London Overview of talk Nilsson s Teleo-Reactive (TR) Procedures Simulation demo of TR controlled can collecting robot
A multi-threaded architecture for cognitive robotics Keith Clark Imperial College London Overview of talk Nilsson s Teleo-Reactive (TR) Procedures Simulation demo of TR controlled can collecting robot
TERRA VISTA CONTENT CREATION MAP. ROUTE. GENERATE
 CONTENT CREATION MAP. ROUTE. GENERATE Terra Vista is a terrain generation software that converts imagery, elevation, vectors, and other geospatial data into optimized 3D simulation-ready virtual environments.
CONTENT CREATION MAP. ROUTE. GENERATE Terra Vista is a terrain generation software that converts imagery, elevation, vectors, and other geospatial data into optimized 3D simulation-ready virtual environments.
Interoperability among Federated Simulated Multinational Operations
 United States Military Academy of West Point, New York USA. Interoperability among Federated Simulated Multinational Operations Second Lieutenant CHATELET Second Lieutenant HELLIO Jan. 5 2011 1 CONTENTS
United States Military Academy of West Point, New York USA. Interoperability among Federated Simulated Multinational Operations Second Lieutenant CHATELET Second Lieutenant HELLIO Jan. 5 2011 1 CONTENTS
Service-Oriented Architecture for Command and Control Systems with Dynamic Reconfiguration
 Service-Oriented Architecture for Command and Control Systems with Dynamic Reconfiguration Raymond A. Paul Department of Defense Washington, DC raymond.paul@osd.mil 2004-5-22 1 Outlines Motivation Dynamic
Service-Oriented Architecture for Command and Control Systems with Dynamic Reconfiguration Raymond A. Paul Department of Defense Washington, DC raymond.paul@osd.mil 2004-5-22 1 Outlines Motivation Dynamic
6/20/2018 CS5386 SOFTWARE DESIGN & ARCHITECTURE LECTURE 5: ARCHITECTURAL VIEWS C&C STYLES. Outline for Today. Architecture views C&C Views
 1 CS5386 SOFTWARE DESIGN & ARCHITECTURE LECTURE 5: ARCHITECTURAL VIEWS C&C STYLES Outline for Today 2 Architecture views C&C Views 1 Components and Connectors (C&C) Styles 3 Elements Relations Properties
1 CS5386 SOFTWARE DESIGN & ARCHITECTURE LECTURE 5: ARCHITECTURAL VIEWS C&C STYLES Outline for Today 2 Architecture views C&C Views 1 Components and Connectors (C&C) Styles 3 Elements Relations Properties
Raytheon Mission Architecture Program (RayMAP) Topic 1: C2 Concepts, Theory, and Policy Paper #40
 Raytheon Mission Architecture Program (RayMAP) Topic 1: C2 Concepts, Theory, and Policy Paper #40 Dale Anglin Erik Baumgarten John Dinh Mark Hall Bert Schneider May 13, 2008 Cleared for public release
Raytheon Mission Architecture Program (RayMAP) Topic 1: C2 Concepts, Theory, and Policy Paper #40 Dale Anglin Erik Baumgarten John Dinh Mark Hall Bert Schneider May 13, 2008 Cleared for public release
Coalition Interoperability Ontology:
 Coalition Interoperability Ontology: Sharing Situational Awareness with Allies and Agents Erik Chaum Naval Undersea Warfare Center, Division Newport, TTCP, Maritime Systems Group, TP1 US National Leader
Coalition Interoperability Ontology: Sharing Situational Awareness with Allies and Agents Erik Chaum Naval Undersea Warfare Center, Division Newport, TTCP, Maritime Systems Group, TP1 US National Leader
developing Real Time Distributed Simulations NADS Nextel Aerospace, Defence & Security
 Use of the OMG standard in Simulation. A new Way for developing Real Time Distributed Simulations NADS Nextel Aerospace, Defence & Security Jose M Lopez-Rodriguez Business Development Director http://www.nexteleng.es/microsite/ncware
Use of the OMG standard in Simulation. A new Way for developing Real Time Distributed Simulations NADS Nextel Aerospace, Defence & Security Jose M Lopez-Rodriguez Business Development Director http://www.nexteleng.es/microsite/ncware
JTRS Network Emulator (JNE): Overview and Use Cases
 JTRS Network Emulator (JNE): Overview and Use Cases Presentation at JSTeF March 14-17, 2011 Sheetal Doshi, Ph.D. Project Lead, JTRS Network Emulator Scalable Network Technologies, Los Angeles CA Email:
JTRS Network Emulator (JNE): Overview and Use Cases Presentation at JSTeF March 14-17, 2011 Sheetal Doshi, Ph.D. Project Lead, JTRS Network Emulator Scalable Network Technologies, Los Angeles CA Email:
Computing and Communications Infrastructure for Network-Centric Warfare: Exploiting COTS, Assuring Performance
 for Network-Centric Warfare: Exploiting COTS, Assuring Performance Dr. James P. Richardson Mr. Lee Graba Mr. Mukul Agrawal Honeywell International, Inc. {james.p.richardson,lee.graba,mukul.agrawal}@honeywell.com
for Network-Centric Warfare: Exploiting COTS, Assuring Performance Dr. James P. Richardson Mr. Lee Graba Mr. Mukul Agrawal Honeywell International, Inc. {james.p.richardson,lee.graba,mukul.agrawal}@honeywell.com
Next Steps in MSDL and C-BML Alignment for Convergence
 Next Steps in MSDL and C-BML Alignment for Convergence Dr. Mark Pullen Douglas Corner GMU C4I Center Dr. Robert Wittman MITRE Corp. Presentation Overview Introduction/overview MSDL and C-BML alignment
Next Steps in MSDL and C-BML Alignment for Convergence Dr. Mark Pullen Douglas Corner GMU C4I Center Dr. Robert Wittman MITRE Corp. Presentation Overview Introduction/overview MSDL and C-BML alignment
Modeling and Simulation Body of Knowledge (M&SBOK) - Index
 Modeling and Simulation Body of Knowledge (M&SBOK) - Index updated and by: Dr. Tuncer Ören - 2010-12-17 Terminology: Types of Data & Terms Related with Data (based on the first version of the Multi-lingual
Modeling and Simulation Body of Knowledge (M&SBOK) - Index updated and by: Dr. Tuncer Ören - 2010-12-17 Terminology: Types of Data & Terms Related with Data (based on the first version of the Multi-lingual
The Evolution of Computer Generated Forces (CGF) Architectures to Support Information Warfare Effects
 The Evolution of Computer Generated Forces (CGF) Architectures to Support Information Warfare Effects Presentation to NMSG-143 20-21 October 2016 Bucharest, Romania Mark G Hazen, DRDC Jon P Lloyd, Dstl
The Evolution of Computer Generated Forces (CGF) Architectures to Support Information Warfare Effects Presentation to NMSG-143 20-21 October 2016 Bucharest, Romania Mark G Hazen, DRDC Jon P Lloyd, Dstl
Presentation Outline. JOEF Prototype Development Team JOEF Focus Areas and Concept JOEF Prototype Development Process COCOM/User Visits Summary
 JOEF Prototype Development Activities Dr. Tom Stark Cubic Defense Applications 26 October 2005 Presentation Outline JOEF Prototype Development Team JOEF Focus Areas and Concept JOEF Prototype Development
JOEF Prototype Development Activities Dr. Tom Stark Cubic Defense Applications 26 October 2005 Presentation Outline JOEF Prototype Development Team JOEF Focus Areas and Concept JOEF Prototype Development
SPARQL-Based Applications for RDF-Encoded Sensor Data
 SPARQL-Based Applications for RDF-Encoded Sensor Data Mikko Rinne, Seppo Törmä, Esko Nuutila http://cse.aalto.fi/instans/ 5 th International Workshop on Semantic Sensor Networks 12.11.2012 Department of
SPARQL-Based Applications for RDF-Encoded Sensor Data Mikko Rinne, Seppo Törmä, Esko Nuutila http://cse.aalto.fi/instans/ 5 th International Workshop on Semantic Sensor Networks 12.11.2012 Department of
Get Started with Blackboard For Instructors
 Get Started with Blackboard For Instructors Log in to Blackboard... 2 View a Student Roster... 3 Upload a Syllabus... 4 Upload Files... 5 Set up a Discussion... 6 Create an Assignment... 7 Preview a Course
Get Started with Blackboard For Instructors Log in to Blackboard... 2 View a Student Roster... 3 Upload a Syllabus... 4 Upload Files... 5 Set up a Discussion... 6 Create an Assignment... 7 Preview a Course
Using Coalition Battle Management Language DS RT 11 Briefing
 Using Coalition Battle Management Language DS RT 11 Briefing Adam Brook Contents Motivation why connect C2 applications with simulations About C-BML Recent Experiences Some Approaches to Developing Systems
Using Coalition Battle Management Language DS RT 11 Briefing Adam Brook Contents Motivation why connect C2 applications with simulations About C-BML Recent Experiences Some Approaches to Developing Systems
U.S. Army Cyber Center of Excellence and Fort Gordon
 U.S. Army Cyber Center of Excellence and Fort Gordon W BUILDING A WORLD CLASS CYBER WORKFORCE TECHNET 2018 Cyberspace Capabilities in Support of Unified Land Operations- Outpacing Our Adversaries This
U.S. Army Cyber Center of Excellence and Fort Gordon W BUILDING A WORLD CLASS CYBER WORKFORCE TECHNET 2018 Cyberspace Capabilities in Support of Unified Land Operations- Outpacing Our Adversaries This
Electronic Health Records with Cleveland Clinic and Oracle Semantic Technologies
 Electronic Health Records with Cleveland Clinic and Oracle Semantic Technologies David Booth, Ph.D., Cleveland Clinic (contractor) Oracle OpenWorld 20-Sep-2010 Latest version of these slides: http://dbooth.org/2010/oow/
Electronic Health Records with Cleveland Clinic and Oracle Semantic Technologies David Booth, Ph.D., Cleveland Clinic (contractor) Oracle OpenWorld 20-Sep-2010 Latest version of these slides: http://dbooth.org/2010/oow/
EPLRS within the BCS/L November 2013
 EPLRS within the BCS/L November 2013 Copyright 2013 Raytheon Company. All rights reserved. Customer Success Is Our Mission is a registered trademark of Raytheon Company. Wade Hughes Lead CIS Engineer Integrated
EPLRS within the BCS/L November 2013 Copyright 2013 Raytheon Company. All rights reserved. Customer Success Is Our Mission is a registered trademark of Raytheon Company. Wade Hughes Lead CIS Engineer Integrated
The Research On C2 System in networked environment
 The Research On C2 System in networked environment XiaoMing Zhou, ChengHao Guo, Kejian Zhao National Key Lab of Science and Technology on C 4 ISR, 69 of Mailbox 1406, Nanjing, Jiangsu, 210007, P.R. China
The Research On C2 System in networked environment XiaoMing Zhou, ChengHao Guo, Kejian Zhao National Key Lab of Science and Technology on C 4 ISR, 69 of Mailbox 1406, Nanjing, Jiangsu, 210007, P.R. China
Integrating a Distributed Agent-Based Simulation into an HLA Federation
 Integrating a Distributed Agent-Based Simulation into an HLA Federation Gary Kratkiewicz Amelia Fedyk Daniel Cerys Distributed Systems & Logistics Department BBN Technologies 10 Moulton Street Cambridge,
Integrating a Distributed Agent-Based Simulation into an HLA Federation Gary Kratkiewicz Amelia Fedyk Daniel Cerys Distributed Systems & Logistics Department BBN Technologies 10 Moulton Street Cambridge,
BES - Battle Eye System
 Battle Eye System is a state of the art GIS based battlefield management and fire control system. Positioned on a C2 ( command and control) level, BES enhances the soldier s understanding of the surroundings
Battle Eye System is a state of the art GIS based battlefield management and fire control system. Positioned on a C2 ( command and control) level, BES enhances the soldier s understanding of the surroundings
Intelligent Systems: Reasoning and Recognition. Rule based programming - Introduction to CLIPS 6.0
 Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2010/2011 Lesson 5 16 February 2011 Rule based programming - Introduction to CLIPS 6.0 Production Systems...2
Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2010/2011 Lesson 5 16 February 2011 Rule based programming - Introduction to CLIPS 6.0 Production Systems...2
FZI Research Center for Information Technology, Germany
 FZI FORSCHUNGSZENTRUM INFORMATIK Event Processing and Stream Reasoning with ETALIS Darko Anicic FZI Research Center for Information Technology, Germany INQUEST 2012, Oxford, United Kingdom Agenda Motivation
FZI FORSCHUNGSZENTRUM INFORMATIK Event Processing and Stream Reasoning with ETALIS Darko Anicic FZI Research Center for Information Technology, Germany INQUEST 2012, Oxford, United Kingdom Agenda Motivation
SCALABLE. Network modeling software for: Development Analysis Testing Cyber Assessment DATASHEET NETWORK TECHNOLOGIES. Virtual Network Model
 SCALABLE NETWORK TECHNOLOGIES DATASHEET Network modeling software for: Development Analysis Testing Cyber Assessment EXata software (EXata) is a tool for scientists, engineers, IT technicians and communications
SCALABLE NETWORK TECHNOLOGIES DATASHEET Network modeling software for: Development Analysis Testing Cyber Assessment EXata software (EXata) is a tool for scientists, engineers, IT technicians and communications
Sebastian Rodriguez Nicolas Gaud Stéphane Galland. Seminar at ISCOD / LSTI - Institut Henri Fayol Saint Étienne February 19 th, 2014
 SARL: www.sarl.io Agent-Oriented Programming Language Sebastian Rodriguez Nicolas Gaud Stéphane Galland Seminar at ISCOD / LSTI - Institut Henri Fayol Saint Étienne February 19 th, 2014 Université de Technologie
SARL: www.sarl.io Agent-Oriented Programming Language Sebastian Rodriguez Nicolas Gaud Stéphane Galland Seminar at ISCOD / LSTI - Institut Henri Fayol Saint Étienne February 19 th, 2014 Université de Technologie
Re-hosting a Constructive Legacy Simulation With Modern Technologies
 e-hosting a Constructive Legacy Simulation With Modern echnologies Leroy A. Jackson Gerald M. Pearman Michael L. McGinnis US Army ADOC Analysis Center PO Box 8692 MONY, CALIFONIA 93943-0692 Keywords: Simulation,
e-hosting a Constructive Legacy Simulation With Modern echnologies Leroy A. Jackson Gerald M. Pearman Michael L. McGinnis US Army ADOC Analysis Center PO Box 8692 MONY, CALIFONIA 93943-0692 Keywords: Simulation,
UNCLASSIFIED. ADF Tactical Data Link Authority Ground Network Capability Assurance Services UNCLASSIFIED
 UNCLASSIFIED MilCIS 2013 TDL Stream, Session 2.5a ADF Tactical Data Link Authority Ground Network Capability Assurance Services Mr. Josh Roth Ground Networks Manager joshua.roth1@defence.gov.au 02 626
UNCLASSIFIED MilCIS 2013 TDL Stream, Session 2.5a ADF Tactical Data Link Authority Ground Network Capability Assurance Services Mr. Josh Roth Ground Networks Manager joshua.roth1@defence.gov.au 02 626
CS Computer Science I
 CS 1309-001 Computer Science I Fall 2017, Sul Ross State University Instructor: Dr. Kennard Laviers Office Location: ACR 107 Office Phone: 432-837- 8500 Email: kennard.laviers@sulross.edu Office Hours:
CS 1309-001 Computer Science I Fall 2017, Sul Ross State University Instructor: Dr. Kennard Laviers Office Location: ACR 107 Office Phone: 432-837- 8500 Email: kennard.laviers@sulross.edu Office Hours:
Architecture Styles. Instructor: Yongjie Zheng February 7, CS 5553: Software Architecture and Design
 Architecture Styles Instructor: Yongjie Zheng February 7, 2017 CS 5553: Software Architecture and Design Architecture styles: a named collection of architecture design decisions that (1) are applicable
Architecture Styles Instructor: Yongjie Zheng February 7, 2017 CS 5553: Software Architecture and Design Architecture styles: a named collection of architecture design decisions that (1) are applicable
Intelligent Systems: Reasoning and Recognition. Rule based programming - Forward chaining
 Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2015/2016 Lesson 13 1 April 2016 Rule based programming - Forward chaining Production Systems...2 Production
Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2015/2016 Lesson 13 1 April 2016 Rule based programming - Forward chaining Production Systems...2 Production
Toward a Standard Rule Language for Semantic Integration of the DoD Enterprise
 1 W3C Workshop on Rule Languages for Interoperability Toward a Standard Rule Language for Semantic Integration of the DoD Enterprise A MITRE Sponsored Research Effort Suzette Stoutenburg 28 April 2005
1 W3C Workshop on Rule Languages for Interoperability Toward a Standard Rule Language for Semantic Integration of the DoD Enterprise A MITRE Sponsored Research Effort Suzette Stoutenburg 28 April 2005
Lockheed Martin DAML Project
 Lockheed Martin DAML Project PI: Dr. Paul Kogut Yui Leung, Ted Mielczarek, Kathleen Ryan, Linda Gohari, Roger Lee Key Researchers: Dr. Jeff Heflin Lehigh University Dr. Mitch Kokar, Dr. Chris Matheus,
Lockheed Martin DAML Project PI: Dr. Paul Kogut Yui Leung, Ted Mielczarek, Kathleen Ryan, Linda Gohari, Roger Lee Key Researchers: Dr. Jeff Heflin Lehigh University Dr. Mitch Kokar, Dr. Chris Matheus,
Mounted Family of Computer Systems (MFoCS)
 Mounted Family of Computer Systems (MFoCS) MOUNTED FAMILY OF COMPUTER SYSTEMS (MFoCS) TODAY S GENERATION OF WARFIGHTER DESERVES A NEXT-GENERATION MOUNTED COMPUTER. MFoCS improves Situational Awareness
Mounted Family of Computer Systems (MFoCS) MOUNTED FAMILY OF COMPUTER SYSTEMS (MFoCS) TODAY S GENERATION OF WARFIGHTER DESERVES A NEXT-GENERATION MOUNTED COMPUTER. MFoCS improves Situational Awareness
European Component Oriented Architecture (ECOA ) Collaboration Programme: Architecture Specification Part 2: Definitions
 European Component Oriented Architecture (ECOA ) Collaboration Programme: Part 2: Definitions BAE Ref No: IAWG-ECOA-TR-012 Dassault Ref No: DGT 144487-D Issue: 4 Prepared by BAE Systems (Operations) Limited
European Component Oriented Architecture (ECOA ) Collaboration Programme: Part 2: Definitions BAE Ref No: IAWG-ECOA-TR-012 Dassault Ref No: DGT 144487-D Issue: 4 Prepared by BAE Systems (Operations) Limited
17/03/2018. Meltem Özturan
 Meltem Özturan www.mis.boun.edu.tr/ozturan/samd 2 1 Traditional Approach to Requirements Traditional Analysis Model Data flow diagrams Process description Data flow definiton Data store definition (Entity-Relationship
Meltem Özturan www.mis.boun.edu.tr/ozturan/samd 2 1 Traditional Approach to Requirements Traditional Analysis Model Data flow diagrams Process description Data flow definiton Data store definition (Entity-Relationship
Security Configuration Assessment (SCA)
 Security Configuration Assessment (SCA) Getting Started Guide Security Configuration Assessment (SCA) is a lightweight cloud service which can quickly perform the configuration assessment of the IT assets,
Security Configuration Assessment (SCA) Getting Started Guide Security Configuration Assessment (SCA) is a lightweight cloud service which can quickly perform the configuration assessment of the IT assets,
Sensors Network Simulators
 Sensors Network Simulators Sensing Networking Qing Fang 10/14/05 Computation This Talk Not on how to run various network simulators Instead What differentiates various simulators Brief structures of the
Sensors Network Simulators Sensing Networking Qing Fang 10/14/05 Computation This Talk Not on how to run various network simulators Instead What differentiates various simulators Brief structures of the
Make Networks Work. Network simulation emulation software for: Development Analysis Testing Cyber Assessment DATASHEET
 DATASHEET Make Networks Work Network simulation emulation software for: Development Analysis Testing Cyber Assessment The EXata Simulation Emulation Platform The EXata software (EXata) provides ultra high-fidelity
DATASHEET Make Networks Work Network simulation emulation software for: Development Analysis Testing Cyber Assessment The EXata Simulation Emulation Platform The EXata software (EXata) provides ultra high-fidelity
Distributed Simulation Concepts and Protocols
 CS 582 Modeling and Simulation II Distributed Simulation Concepts and Protocols Mikel D. Petty, Ph.D. University of Alabama in Huntsville Center for Modeling, Simulation, and Analysis Center for Modeling,
CS 582 Modeling and Simulation II Distributed Simulation Concepts and Protocols Mikel D. Petty, Ph.D. University of Alabama in Huntsville Center for Modeling, Simulation, and Analysis Center for Modeling,
MODEL-DRIVEN DEVELOPMENT OF COMMAND AND CONTROL CAPABILITIES FOR JOINT AND COALITION WARFARE
 9 TH International Command and Control Research & Technology Symposium MODEL-DRIVEN DEVELOPMENT OF COMMAND AND CONTROL CAPABILITIES FOR JOINT AND COALITION WARFARE Robert Jacobs Computer Systems Center
9 TH International Command and Control Research & Technology Symposium MODEL-DRIVEN DEVELOPMENT OF COMMAND AND CONTROL CAPABILITIES FOR JOINT AND COALITION WARFARE Robert Jacobs Computer Systems Center
Question Answering in the InfoSphere: Semantic Interoperability and Lexicon Development
 Question Answering in the InfoSphere: Semantic Interoperability and Lexicon Development Paul Thompson and Steven Lulich Institute for Security Technology Studies Dartmouth College 15 May 2002 Outline The
Question Answering in the InfoSphere: Semantic Interoperability and Lexicon Development Paul Thompson and Steven Lulich Institute for Security Technology Studies Dartmouth College 15 May 2002 Outline The
The Literature: Self-Synchronization and Shared Awareness
 Enabling Adaptive C2 via Semantic Communication and Smart Push: A Model-based Network Communication Approach LtCol Carl Oros, USMC Brief to AFCEA-GMU C4I Center Symposium Critical Issues in C4I Fairfax,
Enabling Adaptive C2 via Semantic Communication and Smart Push: A Model-based Network Communication Approach LtCol Carl Oros, USMC Brief to AFCEA-GMU C4I Center Symposium Critical Issues in C4I Fairfax,
Robotics. CSPP Artificial Intelligence March 10, 2004
 Robotics CSPP 56553 Artificial Intelligence March 10, 2004 Roadmap Robotics is AI-complete Integration of many AI techniques Classic AI Search in configuration space (Ultra) Modern AI Subsumption architecture
Robotics CSPP 56553 Artificial Intelligence March 10, 2004 Roadmap Robotics is AI-complete Integration of many AI techniques Classic AI Search in configuration space (Ultra) Modern AI Subsumption architecture
A PROTOCOL DATA UNIT FOR TRAINING SIMULATED COMMAND FORCES
 A PROTOCOL DATA UNIT FOR TRAINING SIMULATED COMMAND FORCES Kenneth E. Frosch, Elizabeth L. White, J. Mark Pullen C 3 I Center and Department of Computer Science George Mason University 4400 University
A PROTOCOL DATA UNIT FOR TRAINING SIMULATED COMMAND FORCES Kenneth E. Frosch, Elizabeth L. White, J. Mark Pullen C 3 I Center and Department of Computer Science George Mason University 4400 University
Managing the Emerging Semantic Risks
 The New Information Security Agenda: Managing the Emerging Semantic Risks Dr Robert Garigue Vice President for information integrity and Chief Security Executive Bell Canada Page 1 Abstract Today all modern
The New Information Security Agenda: Managing the Emerging Semantic Risks Dr Robert Garigue Vice President for information integrity and Chief Security Executive Bell Canada Page 1 Abstract Today all modern
Software Architecture
 Software Architecture Lecture 6 Event Systems Rob Pettit George Mason University SWE 443 Software Architecture Event Systems 1 previously data flow and call-return styles data flow batch sequential dataflow
Software Architecture Lecture 6 Event Systems Rob Pettit George Mason University SWE 443 Software Architecture Event Systems 1 previously data flow and call-return styles data flow batch sequential dataflow
A CGF (Computer Generated Forces) Model for Single Tank
 216 International Congress on Computation Algorithms in Engineering (ICCAE 216) ISBN: 978-1-6595-386-1 A CGF (Computer Generated Forces) Model for Single Tank Lu Chen, Renyou Zhang & Bo Dong Operational
216 International Congress on Computation Algorithms in Engineering (ICCAE 216) ISBN: 978-1-6595-386-1 A CGF (Computer Generated Forces) Model for Single Tank Lu Chen, Renyou Zhang & Bo Dong Operational
13/11/2017. Meltem Özturan misprivate.boun.edu.tr/ozturan/mis515
 Meltem Özturan misprivate.boun.edu.tr/ozturan/mis515 2 1 Traditional Approach to Requirements Data Flow Diagram (DFD) A graphical system model that shows all of the main requirements for an information
Meltem Özturan misprivate.boun.edu.tr/ozturan/mis515 2 1 Traditional Approach to Requirements Data Flow Diagram (DFD) A graphical system model that shows all of the main requirements for an information
DEVELOPING WEB APPLICATIONS WITH MICROSOFT VISUAL STUDIO Course: 10264A; Duration: 5 Days; Instructor-led
 CENTER OF KNOWLEDGE, PATH TO SUCCESS Website: DEVELOPING WEB APPLICATIONS WITH MICROSOFT VISUAL STUDIO 2010 Course: 10264A; Duration: 5 Days; Instructor-led WHAT YOU WILL LEARN In this course, students
CENTER OF KNOWLEDGE, PATH TO SUCCESS Website: DEVELOPING WEB APPLICATIONS WITH MICROSOFT VISUAL STUDIO 2010 Course: 10264A; Duration: 5 Days; Instructor-led WHAT YOU WILL LEARN In this course, students
An Architecture for Web-Services Based Interest Management in Real Time Distributed Simulation
 An Architecture for Web-Services Based Interest Management in Real Time Distributed Simulation Mark Pullen and Priscilla McAndrews George Mason University C3I Center Katherine Morse and Ryan Brunton SAIC
An Architecture for Web-Services Based Interest Management in Real Time Distributed Simulation Mark Pullen and Priscilla McAndrews George Mason University C3I Center Katherine Morse and Ryan Brunton SAIC
Integrated Planning of Tactical, Test Support, and Tactical Engagement Networks (IPT3N)
 Test & Evaluation/Science & Technology Program C4I & Software Intensive Systems Test (C4T) Test Technology Area Integrated Planning of Tactical, Test Support, and Tactical Engagement Networks (IPT3N) International
Test & Evaluation/Science & Technology Program C4I & Software Intensive Systems Test (C4T) Test Technology Area Integrated Planning of Tactical, Test Support, and Tactical Engagement Networks (IPT3N) International
Emergency Services: Process, Rules and Events
 Emergency Services: Process, Rules and Events Mauricio Salatino, Esteban Aliverti, and Demian Calcaprina Plugtree salaboy@gmail.com Abstract. The Emergency Service Application was built as a blue print
Emergency Services: Process, Rules and Events Mauricio Salatino, Esteban Aliverti, and Demian Calcaprina Plugtree salaboy@gmail.com Abstract. The Emergency Service Application was built as a blue print
Evaluation of Organizational Designs with Network-Centric Philosophy
 Evaluation of Organizational Designs with Network-Centric Philosophy Celestine A. Ntuen, Ph.D Distinguished University Professor The Army Center for Human-Centric C2 Decision Making ntuen@ncat.edu http://gandalf.ncat.edu/ihms
Evaluation of Organizational Designs with Network-Centric Philosophy Celestine A. Ntuen, Ph.D Distinguished University Professor The Army Center for Human-Centric C2 Decision Making ntuen@ncat.edu http://gandalf.ncat.edu/ihms
Core Solutions of Microsoft Lync Server 2013 (NI110) 40 Hours
 Core Solutions of Microsoft Lync Server 2013 (NI110) 40 Hours Outline This instructor-led course teaches IT professionals how to plan, design, deploy, configure, and administer a Microsoft Lync Server
Core Solutions of Microsoft Lync Server 2013 (NI110) 40 Hours Outline This instructor-led course teaches IT professionals how to plan, design, deploy, configure, and administer a Microsoft Lync Server
Mobile Wireless Sensor Network enables convergence of ubiquitous sensor services
 1 2005 Nokia V1-Filename.ppt / yyyy-mm-dd / Initials Mobile Wireless Sensor Network enables convergence of ubiquitous sensor services Dr. Jian Ma, Principal Scientist Nokia Research Center, Beijing 2 2005
1 2005 Nokia V1-Filename.ppt / yyyy-mm-dd / Initials Mobile Wireless Sensor Network enables convergence of ubiquitous sensor services Dr. Jian Ma, Principal Scientist Nokia Research Center, Beijing 2 2005
CASE STUDY: Integrating Agile Operations to support NFV/SDN Deployment & B2B services redefinition, Orange Polska case study
 CASE STUDY: Integrating Agile Operations to support NFV/SDN Deployment & B2B services redefinition, Orange Polska case study Rafal Dziedzic Sebastian Nowosielski Strategy, Orange Polska SA Coexistence
CASE STUDY: Integrating Agile Operations to support NFV/SDN Deployment & B2B services redefinition, Orange Polska case study Rafal Dziedzic Sebastian Nowosielski Strategy, Orange Polska SA Coexistence
Processing Heterogeneous RDF Event Streams with Standing SPARQL Update
 Processing Heterogeneous RDF Streams with Standing SPARQL Update Mikko Rinne, Haris Abdullah, Seppo Törmä, Esko Nuutila http://cse.aalto.fi/instans/ 11.9.2012 Department of Computer Science and Engineering
Processing Heterogeneous RDF Streams with Standing SPARQL Update Mikko Rinne, Haris Abdullah, Seppo Törmä, Esko Nuutila http://cse.aalto.fi/instans/ 11.9.2012 Department of Computer Science and Engineering
Utilizing Network Emulation to Provide Cost Effective Large Scale System of Systems Test and Evaluation
 DISTRIBUTION STATEMENT A. Approved for public release; distribution is unlimited. Utilizing Network Emulation to Provide Cost Effective Large Scale System of Systems Test and Evaluation 20 Jan 17 CERDEC
DISTRIBUTION STATEMENT A. Approved for public release; distribution is unlimited. Utilizing Network Emulation to Provide Cost Effective Large Scale System of Systems Test and Evaluation 20 Jan 17 CERDEC
CS612: IT Technology and Course Overview
 CS612: IT Technology and Course Overview Dr. Lixin Tao ltao@pace.edu http://csis.pace.edu/lixin Computer Science Department Pace University Outline What is New in Computing Application Environment? What
CS612: IT Technology and Course Overview Dr. Lixin Tao ltao@pace.edu http://csis.pace.edu/lixin Computer Science Department Pace University Outline What is New in Computing Application Environment? What
SDD Proposal to COSMOS
 IBM Tivoli Software SDD Proposal to COSMOS Jason Losh (SAS), Oasis SDD TC Tooling Lead Mark Weitzel (IBM), COSMOS Architecture Team Lead Why: Customer Problems Customer Feedback More than half of outages
IBM Tivoli Software SDD Proposal to COSMOS Jason Losh (SAS), Oasis SDD TC Tooling Lead Mark Weitzel (IBM), COSMOS Architecture Team Lead Why: Customer Problems Customer Feedback More than half of outages
DoD Strategy for Cyber Resilient Weapon Systems
 DoD Strategy for Cyber Resilient Weapon Systems Melinda K. Reed Office of the Deputy Assistant Secretary of Defense for Systems Engineering NDIA Systems Engineering Conference October 2016 10/24/2016 Page-1
DoD Strategy for Cyber Resilient Weapon Systems Melinda K. Reed Office of the Deputy Assistant Secretary of Defense for Systems Engineering NDIA Systems Engineering Conference October 2016 10/24/2016 Page-1
Course Outline - COMP150. Lectures and Labs
 Course Outline - COMP150 Lectures and Labs 1 The way of the program 1.1 The Python programming language 1.2 What is a program? 1.3 What is debugging? 1.4 Experimental debugging 1.5 Formal and natural languages
Course Outline - COMP150 Lectures and Labs 1 The way of the program 1.1 The Python programming language 1.2 What is a program? 1.3 What is debugging? 1.4 Experimental debugging 1.5 Formal and natural languages
Multi-Schema and Multi-Server Advances for C2-Simulation Interoperation in MSG-085
 Multi-Schema and Multi-Server Advances for C2-Simulation Interoperation in MSG-085 Dr. Mark Pullen Douglas Corner GMU C4I Center Dr. Robert Wittman MITRE Corp. Adam Brook QinitiQ Dr. Per Gustavsson Saab
Multi-Schema and Multi-Server Advances for C2-Simulation Interoperation in MSG-085 Dr. Mark Pullen Douglas Corner GMU C4I Center Dr. Robert Wittman MITRE Corp. Adam Brook QinitiQ Dr. Per Gustavsson Saab
Developing Windows Applications with Microsoft Visual Studio 2010
 Developing Windows Applications with Microsoft Visual Studio 2010 Course 10262A: Five days; Instructor-Led Course Description: In this course, experienced developers who know the basics of Windows Forms
Developing Windows Applications with Microsoft Visual Studio 2010 Course 10262A: Five days; Instructor-Led Course Description: In this course, experienced developers who know the basics of Windows Forms
Design and implementation of a software communication architecture for the Janus-3D visualizer
 Calhoun: The NPS Institutional Archive Theses and Dissertations Thesis Collection 1994-09 Design and implementation of a software communication architecture for the Janus-3D visualizer Upson, Christopher
Calhoun: The NPS Institutional Archive Theses and Dissertations Thesis Collection 1994-09 Design and implementation of a software communication architecture for the Janus-3D visualizer Upson, Christopher
A Time-Triggered View. Peter PUSCHNER
 Predictable Timing on MPSoC A Time-Triggered View Peter PUSCHNER 1 st Workshop on Mapping Applications to MPSoCs Schloss Rheinfels, Germany June 2008 Focus goal: build safety-critical hard real-time systems
Predictable Timing on MPSoC A Time-Triggered View Peter PUSCHNER 1 st Workshop on Mapping Applications to MPSoCs Schloss Rheinfels, Germany June 2008 Focus goal: build safety-critical hard real-time systems
CENTRAL TEXAS COLLEGE COSC 1315 INTRODUCTION TO COMPUTER PROGRAMMING. Semester Hours Credit: 3 INSTRUCTOR: OFFICE HOURS:
 CENTRAL TEXAS COLLEGE COSC 1315 INTRODUCTION TO COMPUTER PROGRAMMING Semester Hours Credit: 3 INSTRUCTOR: OFFICE HOURS: I. INTRODUCTION A. This course presents an introduction to computer programming for
CENTRAL TEXAS COLLEGE COSC 1315 INTRODUCTION TO COMPUTER PROGRAMMING Semester Hours Credit: 3 INSTRUCTOR: OFFICE HOURS: I. INTRODUCTION A. This course presents an introduction to computer programming for
OpenPlant Accelerating ISO Adoption Through Open Applications.
 OpenPlant Accelerating ISO 15926 Adoption Through Open Applications. Presented By: Dr. Manoj Dharwadkar Director of Data Interoperability, Bentley Systems POSC Caesar Members Meeting - Houston February
OpenPlant Accelerating ISO 15926 Adoption Through Open Applications. Presented By: Dr. Manoj Dharwadkar Director of Data Interoperability, Bentley Systems POSC Caesar Members Meeting - Houston February
DevOps Using VSTS and Azure
 DevOps Using VSTS and Azure ALMDO; 5 Days, Instructor-led Course Description The combination of Visual Studio Team Services (VSTS) and Microsoft Azure provides a powerful and fully featured solution to
DevOps Using VSTS and Azure ALMDO; 5 Days, Instructor-led Course Description The combination of Visual Studio Team Services (VSTS) and Microsoft Azure provides a powerful and fully featured solution to
The Early American Wars Scenario Editor
 The Early American Wars Scenario Editor Introduction The Early American Wars Scenario Editor can be used to create new scenarios and to modify existing scenarios in the Early American Wars series including
The Early American Wars Scenario Editor Introduction The Early American Wars Scenario Editor can be used to create new scenarios and to modify existing scenarios in the Early American Wars series including
Implementing the Army Net Centric Data Strategy in a Service Oriented Environment
 Implementing the Army Net Centric Strategy in a Service Oriented Environment Michelle Dirner Army Net Centric Strategy (ANCDS) Center of Excellence (CoE) Service Team Lead RDECOM CERDEC SED in support
Implementing the Army Net Centric Strategy in a Service Oriented Environment Michelle Dirner Army Net Centric Strategy (ANCDS) Center of Excellence (CoE) Service Team Lead RDECOM CERDEC SED in support
Live Training Transformation (LT2) LT2 Tatical Engagement Simulation System (TESS) Component Architecture Foundation Overview
 COMPONENT SPECIFICATION Live Training Transformation (LT2) LT2 Tatical Engagement Simulation System (TESS) Component Architecture Foundation Overview Document Number LT2 TESS CA-001 VERSION 0.1 31 December
COMPONENT SPECIFICATION Live Training Transformation (LT2) LT2 Tatical Engagement Simulation System (TESS) Component Architecture Foundation Overview Document Number LT2 TESS CA-001 VERSION 0.1 31 December
Requests Charges. Librarian. University affiliated patrons students, faculty, staff. Media Center Staff
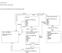 Catherine Rutan INFO 530-901 Dr. Valerie Yonker Circulation of Media Materials from University Media Center: Requests Charges Librarian Circulation Desk Attendant Inquires University ID # (Primary Key)
Catherine Rutan INFO 530-901 Dr. Valerie Yonker Circulation of Media Materials from University Media Center: Requests Charges Librarian Circulation Desk Attendant Inquires University ID # (Primary Key)
The University of Alabama in Huntsville ECE Department CPE Midterm Exam February 26, 2003
 The University of Alabama in Huntsville ECE Department CPE 526 01 Midterm Exam February 26, 2003 1. (20 points) Describe the following logic expression (A B D) + (A B C) + (B C ) with a structural VHDL
The University of Alabama in Huntsville ECE Department CPE 526 01 Midterm Exam February 26, 2003 1. (20 points) Describe the following logic expression (A B D) + (A B C) + (B C ) with a structural VHDL
SRM: Can You Get What You Want? John Webster Principal IT Advisor, Illuminata
 John Webster Principal IT Advisor, Illuminata SNIA Legal Notice The material contained in this tutorial is copyrighted by the SNIA. Member companies and individual members may use this material in presentations
John Webster Principal IT Advisor, Illuminata SNIA Legal Notice The material contained in this tutorial is copyrighted by the SNIA. Member companies and individual members may use this material in presentations
Module 4. Programmable Logic Control Systems. Version 2 EE IIT, Kharagpur 1
 Module 4 Programmable Logic Control Systems Version 2 EE IIT, Kharagpur 1 Lesson 21 Programming of PLCs: Sequential Function Charts Version 2 EE IIT, Kharagpur 2 Instructional Objectives After learning
Module 4 Programmable Logic Control Systems Version 2 EE IIT, Kharagpur 1 Lesson 21 Programming of PLCs: Sequential Function Charts Version 2 EE IIT, Kharagpur 2 Instructional Objectives After learning
Cyber, Command, Control, Communications, and Computers Assessments Division (C5AD)
 Cyber, Command, Control, Communications, and Computers Assessments Division (C5AD) 1 C5AD Presentation (Approved for Public Release: 20150219) ITEA 26 March 2019 Greg Curth J6/DDC5I/C5AD/ENG Cyber Capability
Cyber, Command, Control, Communications, and Computers Assessments Division (C5AD) 1 C5AD Presentation (Approved for Public Release: 20150219) ITEA 26 March 2019 Greg Curth J6/DDC5I/C5AD/ENG Cyber Capability
Introduction to INSTANS
 Introduction to INSTANS Mikko Rinne, Seppo Törmä, Esko Nuutila http://cse.aalto.fi/instans/ 11.10.2013 Department of Computer Science and Engineering Distributed Systems Group INSTANS *) Event Processing
Introduction to INSTANS Mikko Rinne, Seppo Törmä, Esko Nuutila http://cse.aalto.fi/instans/ 11.10.2013 Department of Computer Science and Engineering Distributed Systems Group INSTANS *) Event Processing
IoT Week Workshop on Globally Interoperable IoT Identification and Data Processing Identifiers in IoT
 IoT Week 2017 - Workshop on Globally Interoperable IoT Identification and Data Processing Identifiers in IoT Juergen Heiles, Siemens AG AIOTI WG3 IoT Identifier Task Force Co-Chair 1 Introduction In any
IoT Week 2017 - Workshop on Globally Interoperable IoT Identification and Data Processing Identifiers in IoT Juergen Heiles, Siemens AG AIOTI WG3 IoT Identifier Task Force Co-Chair 1 Introduction In any
Resilient Linked Data. Dave Reynolds, Epimorphics
 Resilient Linked Data Dave Reynolds, Epimorphics Ltd @der42 Outline What is Linked Data? Dependency problem Approaches: coalesce the graph link sets and partitioning URI architecture governance and registries
Resilient Linked Data Dave Reynolds, Epimorphics Ltd @der42 Outline What is Linked Data? Dependency problem Approaches: coalesce the graph link sets and partitioning URI architecture governance and registries
Real-Life Augmentation of the Xbox Controller
 Real-Life Augmentation of the Xbox Controller Justin Schmelzer, Christy Swartz November 4, 2011 Abstract Our project is an augmentation of the Xbox controller. We will be using various sensors on the legs,
Real-Life Augmentation of the Xbox Controller Justin Schmelzer, Christy Swartz November 4, 2011 Abstract Our project is an augmentation of the Xbox controller. We will be using various sensors on the legs,
Collage: A Declarative Programming Model for Compositional Development and Evolution of Cross-Organizational Applications
 Collage: A Declarative Programming Model for Compositional Development and Evolution of Cross-Organizational Applications Bruce Lucas, IBM T J Watson Research Center (bdlucas@us.ibm.com) Charles F Wiecha,
Collage: A Declarative Programming Model for Compositional Development and Evolution of Cross-Organizational Applications Bruce Lucas, IBM T J Watson Research Center (bdlucas@us.ibm.com) Charles F Wiecha,
Why we need Intelligent Security? Juha Launonen Sourcefire, Inc.
 Why we need Intelligent Security? Juha Launonen Sourcefire, Inc. 11-2010 About Sourcefire Mission: To be the leading provider of intelligent cybersecurity solutions for the enterprise. 2 Founded in 2001
Why we need Intelligent Security? Juha Launonen Sourcefire, Inc. 11-2010 About Sourcefire Mission: To be the leading provider of intelligent cybersecurity solutions for the enterprise. 2 Founded in 2001
OPP Site & InfoPath Requirements Document
 OPP Site & InfoPath Requirements Document Date: 2/26/2009 Contact: Rozanne Gallegos Department: Training & Documentation Location: Email: Click here to enter text. Telephone: Document Revision History:
OPP Site & InfoPath Requirements Document Date: 2/26/2009 Contact: Rozanne Gallegos Department: Training & Documentation Location: Email: Click here to enter text. Telephone: Document Revision History:
Networks on Chip. Axel Jantsch. November 24, Royal Institute of Technology, Stockholm
 Networks on Chip Axel Jantsch Royal Institute of Technology, Stockholm November 24, 2004 Network on Chip Seminar, Linköping, November 25, 2004 Networks on Chip 1 Overview NoC as Future SoC Platforms What
Networks on Chip Axel Jantsch Royal Institute of Technology, Stockholm November 24, 2004 Network on Chip Seminar, Linköping, November 25, 2004 Networks on Chip 1 Overview NoC as Future SoC Platforms What
A Verification Approach for GALS Integration of Synchronous Components
 GALS 2005 Preliminary Version A Verification Approach for GALS Integration of Synchronous Components F. Doucet, M. Menarini, I. H. Krüger and R. Gupta 1 Computer Science and Engineering University of California,
GALS 2005 Preliminary Version A Verification Approach for GALS Integration of Synchronous Components F. Doucet, M. Menarini, I. H. Krüger and R. Gupta 1 Computer Science and Engineering University of California,
UNCLASSIFIED UNCLASSIFIED
 : February 6 Exhibit R, RDT&E Budget Item Justification: PB : Research,, Test & Evaluation, / BA 5: System & Demonstration (SDD) COST ($ in Millions) FY 5 FY 6 R Program Element (Number/Name) PE 65A /
: February 6 Exhibit R, RDT&E Budget Item Justification: PB : Research,, Test & Evaluation, / BA 5: System & Demonstration (SDD) COST ($ in Millions) FY 5 FY 6 R Program Element (Number/Name) PE 65A /
Study of Smart Home System based on Zigbee Wireless Sensor System. Jie Huang 1
 2nd Workshop on Advanced Research and Technology in Industry Applications (WARTIA 2016) Study of Smart Home System based on Zigbee Wireless Sensor System Jie Huang 1 1 College of Mechanical and Electronic
2nd Workshop on Advanced Research and Technology in Industry Applications (WARTIA 2016) Study of Smart Home System based on Zigbee Wireless Sensor System Jie Huang 1 1 College of Mechanical and Electronic
