CREATING AND USING THE CLIENT-PRINCIPAL
|
|
|
- Stanley Fletcher
- 6 years ago
- Views:
Transcription
1 CREATING AND USING THE CLIENT-PRINCIPAL Fellow and OpenEdge Evangelist Document Version 1.0 December 2011 December, 2011 Page 1 of 9
2 DISCLAIMER Certain portions of this document contain information about Progress Software Corporation s plans for future product development and overall business strategies. Such information is proprietary and confidential to Progress Software Corporation and may be used by you solely in accordance with the terms and conditions specified in the PSDN Online ( Terms of Use ( Progress Software Corporation reserves the right, in its sole discretion, to modify or abandon without notice any of the plans described herein pertaining to future development and/or business development strategies. Any reference to third party software and/or features is intended for illustration purposes only. Progress Software Corporation does not endorse or sponsor such third parties or software. In the previous video and paper in this series on support for multi-tenancy in OpenEdge 11, Loading Data into Tenant Tables, I loaded data into the new database for each of four tenants, and showed how you can use the SETUSERID function in ABL to connect to the database using the combination of a userid and that user s domain, which provides access to the data for a single tenant. In this paper I show what s going on behind the scenes when the SETUSERID function is run, and how you can explicitly create and use the OpenEdge authentication object, called a Client- Principal, to provide access to a multi-tenant database. To look at what s happening when you establish your user identity with SETUSERID, I ll create a simple ABL procedure (this is saved as MT6_1.p). First the procedure needs a handle variable to hold a reference to a security object. DEFINE VARIABLE hcp AS HANDLE. Following the SETUSERID function, the procedure then uses the GET-DB-CLIENT function to return the underlying security object that has given me access to the EastSports tenant s data, which is a built-in ABL object that has a handle like other built-in objects. SETUSERID("JoeEast@EastSportsUser", "Joe"). hcp = GET-DB-CLIENT("sportsmt"). Displaying the TYPE attribute for the handle reference returned confirms that GET-DB- CLIENT returns a Client-Principal. The Client-Principal is the security object that was introduced in OpenEdge 10.1 as part of our support for auditing. In OpenEdge 11 its use has been extended to support multi-tenancy, where obviously it is essential to assure that users have access only to their tenant s data. The procedure then displays some of the other attributes of the Client-Principal. One is the USER-ID that was used to connect, and also the DOMAIN-NAME. Remember that it s the combination of user id and domain name that uniquely identifies a user. The Client-Principal also holds the TENANT-NAME for the domain the user connects with. This has been retrieved from the schema tables in the database. And each tenant has a numeric TENANT-ID as well that s used internally. Regular tenants like the ones I ve been creating are assigned positive values starting with 1. The default tenant that has access to shared data and the default tenant partition has an id of zero. The LOGIN-STATE attribute tells you the state of the Client-Principal. If you re successfully connected, its value is LOGIN. You December, 2011 Page 2 of 9
3 can also LOGOUT, which prohibits further use of the Client-Principal for authentication. It can also be EXPIRED, if you ve set an expiration time for the Client-Principal, or FAILED if it was invalid for some reason. Here is the procedure: DEFINE VARIABLE hcp AS HANDLE. "Joe"). hcp = GET-DB-CLIENT("sportsmt"). MESSAGE hcp:type SKIP "User -" hcp:user-id SKIP "Domain -" hcp:domain-name SKIP "Tenant -" hcp:tenant-name SKIP "Tenant ID -" hcp:tenant-id SKIP "State -" hcp:login-state VIEW-AS ALERT-BOX. When I run, you see the values for these attributes. I m user JoeEast, my domain is EastSportsUser, that connects me to the EastSports tenant, whose Id is 1, and my state is LOGIN, which really means that I m connected. There are other attributes this example doesn t show you, and the Client-Principal is also extensible so that you can define your own attributes for specialized security situations.when the procedure ran the SETUSERID function, OpenEdge created this Client-Principal for me automatically. And note that I didn t need to know the domain s access code to get in. Openedge does this basically for backward compatibility with earlier use of _User. If you use _User and the _oeusertable authentication system, then the only thing that is checked by SETUSERID is the user id, now qualified by the domain name, and the user s password. The domain access code is simply retrieved from the database for you and plugged into the Client- Principal. So if you re using _User for your security, you re not really getting the benefit of the additional security of the domain access code. Keep that in mind. Later in this paper there s a brief introduction to an alternative way of doing things. December, 2011 Page 3 of 9
4 Back in the DB Admin Console, I want to set up an alternative to using _oeusertable and the _User schema table. On the main detail frame for the database connection is a link to edit authentication systems: This was shown briefly once before, in an earlier session, but there I didn t modify anything, because the first sample domains use the _oeusertable authentication system. Now I m going to create a new one: I just call it ApplAuth, because this represents an authentication and login system that s managed by my application. Now, one way to enhance the security of your application would be to use a type of plug-in on the server side that s called a PAM, for Pluggable Authentication Module. OpenEdge may provide support for these modules in the future, but this is not yet available in OpenEdge For now the December, 2011 Page 4 of 9
5 database does not know anything about the particulars of my new authentication system, so other than an optional description, there s nothing to be done but save it. Now I return to the sportsmt connection, and add a domain for the new authentication system: I call this one EastSportsAppl, to show that it uses the ApplAuth authentication system. It will be a second domain for the EastSports tenant, so I can configure different groups of EastSports users if I want to use different domains with different security systems. Once again I have to define an access code as a kind of password for the domain. In this case I enter the domain name plus the string Code. As with any password, setting this up carefully and protecting it from unauthorized access will be an important part of setting up security for your application. December, 2011 Page 5 of 9
6 That s all I need to do in the Admin Console. Since I m not using _User for this domain, I don t create any users in the tool. Now I want to show you a very simplified example of how your application can create Client-Principal objects of its own to connect to the database with. This is the procedure saved as MT6_2.p. First I need some variable definitions: DEFINE VARIABLE hcp AS HANDLE NO-UNDO. DEFINE VARIABLE cuserid AS CHARACTER NO-UNDO. DEFINE VARIABLE cdomainname AS CHARACTER NO-UNDO. DEFINE VARIABLE cpassword AS CHARACTER NO-UNDO. DEFINE VARIABLE lauthenticated AS LOGICAL NO-UNDO. DEFINE VARIABLE caccesscode AS CHARACTER NO-UNDO. Next I ve created a simple function that represents your application s user authentication mechanism. It doesn t check the username and password; that would be up to you to do. And it simply says that if the domain name the user specifies ends in appl, it appends Code to that and returns that as the domain access code to use: FUNCTION ApplAuth RETURNS LOGICAL (INPUT pcuserid AS CHARACTER, INPUT pcpassword AS CHARACTER, INPUT pcdomainname AS CHARACTER, OUTPUT pcaccesscode AS CHARACTER): IF SUBSTR(pcDomainName, LENGTH(pcDomainName) - 3) = "Appl" THEN DO: pcaccesscode = pcdomainname + "Code". RETURN TRUE. ELSE RETURN FALSE. Now I said this is a highly simplified example. In a later presentation I show a more realistic example of separating responsibilities between client and AppServer and protecting the integrity of the domain access code. Here the access code is available December, 2011 Page 6 of 9
7 on the client, which is not a good idea. But again, this is just to introduce you to the Client-Principal if you haven t used it before. Next the procedure uses the simplest possible user interface to get the userid, the user s password, and the domain name: UPDATE cuserid FORMAT "x(12)" cpassword FORMAT "x(12)" cdomainname FORMAT "x(20)". Once those are entered, the procedure calls the ApplAuth function, and gets a success or failure flag back, along with the access code if the login succeeded. lauthenticated = ApplAuth(INPUT cuserid, INPUT cpassword, INPUT cdomainname, OUTPUT caccesscode). If that succeeds, the code creates an instance of the Client-Principal, just like any other built-in ABL object: IF lauthenticated THEN DO: CREATE CLIENT-PRINCIPAL hcp. The essential method that must be run in that instance is Initialize(). At a minimum you pass the userid and domain to that method, with the usual at sign in between. There are other optional parameters I won t go into here. IF NOT hcp:initialize(cuserid + "@" + cdomainname) THEN MESSAGE "Initialize of Client-Principal failed" VIEW-AS ALERT-BOX. Once the Client-Principal is set up, you then have to Seal() it. To do this you pass in the domain access code. This is the essential security step. Whatever entity in your application knows the domain access code can use it to seal a Client-Principal for that domain, and after that you can use it to gain access to any database that recognizes that domain and its access code. So this is why it s essential to protect the code in a completed application. IF NOT hcp:seal(caccesscode) THEN MESSAGE "Seal failed for User " cuserid VIEW-AS ALERT-BOX. Now that the Client-Principal is sealed, I can use it to establish my user identity with the SET-DB-CLIENT function. ELSE IF NOT SET-DB-CLIENT(hCP) THEN MESSAGE "SET-DB-CLIENT failed for user " cuserid VIEW-AS ALERT-BOX. December, 2011 Page 7 of 9
8 Now I m authenticated in the sportsmt database as an EastSports user, and I can do the FOR EACH Customer again, to verify that I m connected to the right tenant s data: ELSE DO: FOR EACH Customer: DISPLAY CustNum NAME. One more thing. I mentioned that there s a LOGOUT method on the Client-Principal. This doesn t actually log me out of the database connection. What it does is disable this Client-Principal instance from further use, for instance to connect to another database. I should also clean up by deleting the object and erasing the handle s value: hcp:logout(). DELETE OBJECT hcp. hcp =?. Now I can run the whole procedure. Here s the login: Again, I didn t build any user and password checking into the function, so it doesn t matter what I enter here. Or for the password either. But I do need to enter a domain name that ends with appl: December, 2011 Page 8 of 9
9 When I continue, I ve been authenticated as a user in the EastSportsAppl domain, and here are the EastSports customers: That s the introduction to the Client-Principal, and that s all for this presentation. Next I cover a few more basic multi-tenancy topics, including how to define sequences for multi-tenant tables, and how to define groups of tenants who have some of their data in common. December, 2011 Page 9 of 9
LOADING DATA INTO TENANT TABLES
 LOADING DATA INTO TENANT TABLES Fellow and OpenEdge Evangelist Document Version 1.0 December 2011 December, 2011 Page 1 of 10 DISCLAIMER Certain portions of this document contain information about Progress
LOADING DATA INTO TENANT TABLES Fellow and OpenEdge Evangelist Document Version 1.0 December 2011 December, 2011 Page 1 of 10 DISCLAIMER Certain portions of this document contain information about Progress
USING APPSERVER SUPPORT IN OPENEDGE ARCHITECT
 USING APPSERVER SUPPORT IN OPENEDGE ARCHITECT Fellow and OpenEdge Evangelist Document Version 1.0 August 2010 September, 2010 Page 1 of 17 DISCLAIMER Certain portions of this document contain information
USING APPSERVER SUPPORT IN OPENEDGE ARCHITECT Fellow and OpenEdge Evangelist Document Version 1.0 August 2010 September, 2010 Page 1 of 17 DISCLAIMER Certain portions of this document contain information
UPDATING DATA WITH.NET CONTROLS AND A PROBINDINGSOURCE
 UPDATING DATA WITH.NET CONTROLS AND A PROBINDINGSOURCE Fellow and OpenEdge Evangelist Document Version 1.0 March 2010 April, 2010 Page 1 of 17 DISCLAIMER Certain portions of this document contain information
UPDATING DATA WITH.NET CONTROLS AND A PROBINDINGSOURCE Fellow and OpenEdge Evangelist Document Version 1.0 March 2010 April, 2010 Page 1 of 17 DISCLAIMER Certain portions of this document contain information
DEFINING AN ABL FORM AND BINDING SOURCE
 DEFINING AN ABL FORM AND BINDING SOURCE Fellow and OpenEdge Evangelist Document Version 1.0 November 2009 Using Visual Designer and GUI for.net Defining an ABL Form and Binding Source December, 2009 Page
DEFINING AN ABL FORM AND BINDING SOURCE Fellow and OpenEdge Evangelist Document Version 1.0 November 2009 Using Visual Designer and GUI for.net Defining an ABL Form and Binding Source December, 2009 Page
CALLING AN OPENEDGE WEB SERVICE
 CALLING AN OPENEDGE WEB SERVICE Fellow and OpenEdge Evangelist Document Version 1.0 August 2011 August, 2011 Page 1 of 16 DISCLAIMER Certain portions of this document contain information about Progress
CALLING AN OPENEDGE WEB SERVICE Fellow and OpenEdge Evangelist Document Version 1.0 August 2011 August, 2011 Page 1 of 16 DISCLAIMER Certain portions of this document contain information about Progress
USING THE OEBPM API. John Sadd Fellow and OpenEdge Evangelist Document Version 1.0 May May, 2012 Page 1 of 15
 USING THE OEBPM API Fellow and OpenEdge Evangelist Document Version 1.0 May 2012 May, 2012 Page 1 of 15 DISCLAIMER Certain portions of this document contain information about Progress Software Corporation
USING THE OEBPM API Fellow and OpenEdge Evangelist Document Version 1.0 May 2012 May, 2012 Page 1 of 15 DISCLAIMER Certain portions of this document contain information about Progress Software Corporation
BUILDING AND USING WEB APPLICATIONS
 BUILDING AND USING WEB APPLICATIONS Fellow and OpenEdge Evangelist Document Version 1.0 July 2010 August, 2011 Page 1 of 21 DISCLAIMER Certain portions of this document contain information about Progress
BUILDING AND USING WEB APPLICATIONS Fellow and OpenEdge Evangelist Document Version 1.0 July 2010 August, 2011 Page 1 of 21 DISCLAIMER Certain portions of this document contain information about Progress
Identity Management Basics
 Identity Management Basics Part 1 of Identity Management with Progress OpenEdge Peter Judge OpenEdge Development pjudge@progress.com What Is Identity Management? Identity management is all about trust
Identity Management Basics Part 1 of Identity Management with Progress OpenEdge Peter Judge OpenEdge Development pjudge@progress.com What Is Identity Management? Identity management is all about trust
MultiTenancy - An Overview For Techies
 MultiTenancy - An Overview For Techies Timothy D. Kuehn Senior OpenEdge Consultant timk@tdkcs.ca tim.kuehn@gmail.com Ph 519-576-8100 Cell: 519-781-0081 MultiTenancy for Developers PUG Challenge 2013 -
MultiTenancy - An Overview For Techies Timothy D. Kuehn Senior OpenEdge Consultant timk@tdkcs.ca tim.kuehn@gmail.com Ph 519-576-8100 Cell: 519-781-0081 MultiTenancy for Developers PUG Challenge 2013 -
Company System Administrator (CSA) User Guide
 BMO HARRIS ONLINE BANKING SM FOR SMALL BUSINESS Company System Administrator (CSA) User Guide Copyright 2011 BMO Harris Bank N.A. TABLE OF CONTENTS WELCOME... 1 Who should use this guide... 1 What it covers...
BMO HARRIS ONLINE BANKING SM FOR SMALL BUSINESS Company System Administrator (CSA) User Guide Copyright 2011 BMO Harris Bank N.A. TABLE OF CONTENTS WELCOME... 1 Who should use this guide... 1 What it covers...
Installing Dolphin on Your PC
 Installing Dolphin on Your PC Note: When installing Dolphin as a test platform on the PC there are a few things you can overlook. Thus, this installation guide won t help you with installing Dolphin on
Installing Dolphin on Your PC Note: When installing Dolphin as a test platform on the PC there are a few things you can overlook. Thus, this installation guide won t help you with installing Dolphin on
Quick Guide to Installing and Setting Up MySQL Workbench
 Quick Guide to Installing and Setting Up MySQL Workbench If you want to install MySQL Workbench on your own computer: Go to: http://www.mysql.com/downloads/workbench/ Windows Users: 1) You will need to
Quick Guide to Installing and Setting Up MySQL Workbench If you want to install MySQL Workbench on your own computer: Go to: http://www.mysql.com/downloads/workbench/ Windows Users: 1) You will need to
Deltek Touch CRM for Vision. User Guide
 Deltek Touch CRM for Vision User Guide September 2017 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or technical errors may exist.
Deltek Touch CRM for Vision User Guide September 2017 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or technical errors may exist.
SORTING DATA WITH A PROBINDINGSOURCE AND.NET CONTROLS
 SORTING DATA WITH A PROBINDINGSOURCE AND.NET CONTROLS Fellow and OpenEdge Evangelist Document Version 1.0 December 2009 December, 2009 Page 1 of 31 DISCLAIMER Certain portions of this document contain
SORTING DATA WITH A PROBINDINGSOURCE AND.NET CONTROLS Fellow and OpenEdge Evangelist Document Version 1.0 December 2009 December, 2009 Page 1 of 31 DISCLAIMER Certain portions of this document contain
Deltek Touch CRM for Deltek CRM. User Guide
 Deltek Touch CRM for Deltek CRM User Guide February 2017 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or technical errors may
Deltek Touch CRM for Deltek CRM User Guide February 2017 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or technical errors may
XP: Backup Your Important Files for Safety
 XP: Backup Your Important Files for Safety X 380 / 1 Protect Your Personal Files Against Accidental Loss with XP s Backup Wizard Your computer contains a great many important files, but when it comes to
XP: Backup Your Important Files for Safety X 380 / 1 Protect Your Personal Files Against Accidental Loss with XP s Backup Wizard Your computer contains a great many important files, but when it comes to
Sync to a Secondary Salesforce Organization
 Sync to a Secondary Salesforce Organization Salesforce, Summer 17 @salesforcedocs Last updated: August 9, 2017 Copyright 2000 2017 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Sync to a Secondary Salesforce Organization Salesforce, Summer 17 @salesforcedocs Last updated: August 9, 2017 Copyright 2000 2017 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
1.7 Limit of a Function
 1.7 Limit of a Function We will discuss the following in this section: 1. Limit Notation 2. Finding a it numerically 3. Right and Left Hand Limits 4. Infinite Limits Consider the following graph Notation:
1.7 Limit of a Function We will discuss the following in this section: 1. Limit Notation 2. Finding a it numerically 3. Right and Left Hand Limits 4. Infinite Limits Consider the following graph Notation:
Deltek Touch CRM for GovWin Capture Management. User Guide
 Deltek Touch CRM for GovWin Capture Management User Guide September 2017 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or technical
Deltek Touch CRM for GovWin Capture Management User Guide September 2017 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or technical
ONE of the challenges we all face when developing
 Using SQL-DMO to Handle Security in ADPs Russell Sinclair 2000 2002 Smart Access MSDE is a powerful, free version of SQL Server that you can make available to your users. In this issue, Russell Sinclair
Using SQL-DMO to Handle Security in ADPs Russell Sinclair 2000 2002 Smart Access MSDE is a powerful, free version of SQL Server that you can make available to your users. In this issue, Russell Sinclair
How to Add or Invite Colleagues
 Page 1 of 5 How to Add or Invite Colleagues This how-to document contains four sections, addressing the most common questions about Point K collaboration features: Do my colleagues have to be co-workers
Page 1 of 5 How to Add or Invite Colleagues This how-to document contains four sections, addressing the most common questions about Point K collaboration features: Do my colleagues have to be co-workers
Installing the WHI Virtual Private Network (VPN) for WHIX Users Updated 12/16/2016
 Installing the WHI Virtual Private Network (VPN) for WHIX Users Updated 12/16/2016 Note: Please read the FAQ section at the end of this document. I. Overview The way in which you connect to the WHI network
Installing the WHI Virtual Private Network (VPN) for WHIX Users Updated 12/16/2016 Note: Please read the FAQ section at the end of this document. I. Overview The way in which you connect to the WHI network
CS354 gdb Tutorial Written by Chris Feilbach
 CS354 gdb Tutorial Written by Chris Feilbach Purpose This tutorial aims to show you the basics of using gdb to debug C programs. gdb is the GNU debugger, and is provided on systems that
CS354 gdb Tutorial Written by Chris Feilbach Purpose This tutorial aims to show you the basics of using gdb to debug C programs. gdb is the GNU debugger, and is provided on systems that
Testing Documentation
 Testing Documentation Create-A-Page Group 9: John Campbell, Matthew Currier, Dan Martin 5/1/2009 This document defines the methods for testing Create-A-Page, as well as the results of those tests and the
Testing Documentation Create-A-Page Group 9: John Campbell, Matthew Currier, Dan Martin 5/1/2009 This document defines the methods for testing Create-A-Page, as well as the results of those tests and the
WordPress Tutorial for Beginners with Step by Step PDF by Stratosphere Digital
 WordPress Tutorial for Beginners with Step by Step PDF by Stratosphere Digital This WordPress tutorial for beginners (find the PDF at the bottom of this post) will quickly introduce you to every core WordPress
WordPress Tutorial for Beginners with Step by Step PDF by Stratosphere Digital This WordPress tutorial for beginners (find the PDF at the bottom of this post) will quickly introduce you to every core WordPress
How to Secure SSH with Google Two-Factor Authentication
 How to Secure SSH with Google Two-Factor Authentication WELL, SINCE IT IS QUITE COMPLEX TO SET UP, WE VE DECIDED TO DEDICATE A WHOLE BLOG TO THAT PARTICULAR STEP! A few weeks ago we took a look at how
How to Secure SSH with Google Two-Factor Authentication WELL, SINCE IT IS QUITE COMPLEX TO SET UP, WE VE DECIDED TO DEDICATE A WHOLE BLOG TO THAT PARTICULAR STEP! A few weeks ago we took a look at how
Audio is in normal text below. Timestamps are in bold to assist in finding specific topics.
 Transcript of: Overview of Data Entry Video production date: April 2, 2012 Video length: 16:05 REDCap version featured: 4.7.1 (standard branch) Author: Veida Elliott, Vanderbilt University Medical Center,
Transcript of: Overview of Data Entry Video production date: April 2, 2012 Video length: 16:05 REDCap version featured: 4.7.1 (standard branch) Author: Veida Elliott, Vanderbilt University Medical Center,
Configuring Facebook for a More Secure Social Networking Experience
 CPF 0037-14-CID361-9H-Facebook* 5 December 2014 Configuring Facebook for a More Secure Social Networking Experience Settings Settings are available under the Facebook Configuration Arrow. General Settings
CPF 0037-14-CID361-9H-Facebook* 5 December 2014 Configuring Facebook for a More Secure Social Networking Experience Settings Settings are available under the Facebook Configuration Arrow. General Settings
Deploy Enhancements from Sandboxes
 Deploy Enhancements from Sandboxes Salesforce, Spring 17 @salesforcedocs Last updated: March 10, 2017 Copyright 2000 2017 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Deploy Enhancements from Sandboxes Salesforce, Spring 17 @salesforcedocs Last updated: March 10, 2017 Copyright 2000 2017 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Binary, Hexadecimal and Octal number system
 Binary, Hexadecimal and Octal number system Binary, hexadecimal, and octal refer to different number systems. The one that we typically use is called decimal. These number systems refer to the number of
Binary, Hexadecimal and Octal number system Binary, hexadecimal, and octal refer to different number systems. The one that we typically use is called decimal. These number systems refer to the number of
Learner. Help Guide. Page 1 of 36 Training Partner (Learner Help Guide) Revised 09/16/09
 Learner Help Guide Page 1 of 36 Table of Contents ACCESS INFORMATION Accessing Training Partner on the Web..... 3 Login to Training Partner........ 4 Add/Change Email Address....... 6 Change Password.........
Learner Help Guide Page 1 of 36 Table of Contents ACCESS INFORMATION Accessing Training Partner on the Web..... 3 Login to Training Partner........ 4 Add/Change Email Address....... 6 Change Password.........
Importing source database objects from a database
 Importing source database objects from a database We are now at the point where we can finally import our source database objects, source database objects. We ll walk through the process of importing from
Importing source database objects from a database We are now at the point where we can finally import our source database objects, source database objects. We ll walk through the process of importing from
Here s how this whole external IRB thing works: A handbook for external IRB submissions
 Here s how this whole external IRB thing works: A handbook for external IRB submissions For all communication relating to external IRBs, call 414-219-7744 or email CentralIRB.Office@aurora.org. External
Here s how this whole external IRB thing works: A handbook for external IRB submissions For all communication relating to external IRBs, call 414-219-7744 or email CentralIRB.Office@aurora.org. External
Create a Login System in Visual Basic. Creating a login system. Start a new visual basic Windows Forms application project. Call it Login System
 Creating a login system Start a new visual basic Windows Forms application project Call it Login System Change the form TITLE from Form1 to Login System Add the following to the form Component Text Name
Creating a login system Start a new visual basic Windows Forms application project Call it Login System Change the form TITLE from Form1 to Login System Add the following to the form Component Text Name
Data encryption & security. An overview
 Data encryption & security An overview Agenda Make sure the data cannot be accessed without permission Physical security Network security Data security Give (some) people (some) access for some time Authentication
Data encryption & security An overview Agenda Make sure the data cannot be accessed without permission Physical security Network security Data security Give (some) people (some) access for some time Authentication
Without further ado, let s go over and have a look at what I ve come up with.
 JIRA Integration Transcript VLL Hi, my name is Jonathan Wilson and I m the service management practitioner with NHS Digital based in the United Kingdom. NHS Digital is the provider of services to the National
JIRA Integration Transcript VLL Hi, my name is Jonathan Wilson and I m the service management practitioner with NHS Digital based in the United Kingdom. NHS Digital is the provider of services to the National
AT&T Business Messaging Account Management
 Account Management Administrator User Guide July 2016 1 Copyright 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T
Account Management Administrator User Guide July 2016 1 Copyright 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T
Deltek Touch CRM for Ajera CRM. User Guide
 Deltek Touch CRM for Ajera CRM User Guide September 2017 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or technical errors may
Deltek Touch CRM for Ajera CRM User Guide September 2017 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or technical errors may
Conecta application. User Manual Conecta Release 9. June Currently Supporting
 Conecta application User Manual Conecta Release 9 June 2015 Currently Supporting 1 TABLE OF CONTENTS 1 What is Conecta?... 1 2 Platform overview... 2 2.1 Accessing the Platform... 2 2.2 Home page... 2
Conecta application User Manual Conecta Release 9 June 2015 Currently Supporting 1 TABLE OF CONTENTS 1 What is Conecta?... 1 2 Platform overview... 2 2.1 Accessing the Platform... 2 2.2 Home page... 2
Deploy Enhancements from Sandboxes
 Deploy Enhancements from Sandboxes Salesforce, Spring 18 @salesforcedocs Last updated: April 13, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Deploy Enhancements from Sandboxes Salesforce, Spring 18 @salesforcedocs Last updated: April 13, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Support Backups and Secure Transfer Server Changes - i-cam
 Support Backups and Secure Transfer Server Changes - i-cam 3.1.24 Contents What is the Secure Transfer Server?... 2 Initial Setup in i-cam 3.1.24... 2 Getting your account credentials... 2 Setting your
Support Backups and Secure Transfer Server Changes - i-cam 3.1.24 Contents What is the Secure Transfer Server?... 2 Initial Setup in i-cam 3.1.24... 2 Getting your account credentials... 2 Setting your
SECURITY AND DATA REDUNDANCY. A White Paper
 SECURITY AND DATA REDUNDANCY A White Paper Security and Data Redundancy Whitepaper 2 At MyCase, Security is Our Top Priority. Here at MyCase, we understand how important it is to keep our customer s data
SECURITY AND DATA REDUNDANCY A White Paper Security and Data Redundancy Whitepaper 2 At MyCase, Security is Our Top Priority. Here at MyCase, we understand how important it is to keep our customer s data
Office 365 for IT Pros
 Office 365 for IT Pros Fourth edition Performing a Cutover migration to Exchange Online Published by Tony Redmond, Paul Cunningham, Michael Van Horenbeeck, and Ståle Hansen. Copyright 2015-2017 by Tony
Office 365 for IT Pros Fourth edition Performing a Cutover migration to Exchange Online Published by Tony Redmond, Paul Cunningham, Michael Van Horenbeeck, and Ståle Hansen. Copyright 2015-2017 by Tony
Accuterm 7 Usage Guide
 P a g e 1 Accuterm 7 Usage Guide Most if not all computers on our campus have Accuterm 7 already installed on them. To log in, you will double click the icon on your desktop that looks like the one shown
P a g e 1 Accuterm 7 Usage Guide Most if not all computers on our campus have Accuterm 7 already installed on them. To log in, you will double click the icon on your desktop that looks like the one shown
One-Time PIN. User Guide
 One-Time PIN User Guide Table of Contents Online Banking Setting up One-Time PIN Registering your device Logging in with One-Time PIN Changing One-Time PIN Delivery Method Mobile Banking Setting up One-Time
One-Time PIN User Guide Table of Contents Online Banking Setting up One-Time PIN Registering your device Logging in with One-Time PIN Changing One-Time PIN Delivery Method Mobile Banking Setting up One-Time
OpsCenter Basics Why Aren t You Using It?
 OpsCenter Basics Why Aren t You Using It? This is a SELF-GUIDED LAB if you prefer. You are welcome to get started and leave when you are finished, or you can play with the OC instance to gain more knowledge.
OpsCenter Basics Why Aren t You Using It? This is a SELF-GUIDED LAB if you prefer. You are welcome to get started and leave when you are finished, or you can play with the OC instance to gain more knowledge.
The Connector. Version 1.2 Microsoft Project to Atlassian JIRA Connectivity. User Manual
 The Connector Version 1.2 Microsoft Project to Atlassian JIRA Connectivity User Manual Ecliptic Technologies, Inc. Copyright 2008 www.the-connector.com Page 1 of 86 Copyright and Disclaimer All rights
The Connector Version 1.2 Microsoft Project to Atlassian JIRA Connectivity User Manual Ecliptic Technologies, Inc. Copyright 2008 www.the-connector.com Page 1 of 86 Copyright and Disclaimer All rights
SharePoint Designer Advanced
 SharePoint Designer Advanced SharePoint Designer Advanced (1:00) Thank you for having me here today. As mentioned, my name is Susan Hernandez, and I work at Applied Knowledge Group (http://www.akgroup.com).
SharePoint Designer Advanced SharePoint Designer Advanced (1:00) Thank you for having me here today. As mentioned, my name is Susan Hernandez, and I work at Applied Knowledge Group (http://www.akgroup.com).
Money Management Account
 Money Management Account Overview Red represents debt accounts. Add An Account lets you add any account you want including loans, property, credit cards and investments. Click an account to edit it. Note:
Money Management Account Overview Red represents debt accounts. Add An Account lets you add any account you want including loans, property, credit cards and investments. Click an account to edit it. Note:
Introduction to Unix - Lab Exercise 0
 Introduction to Unix - Lab Exercise 0 Along with this document you should also receive a printout entitled First Year Survival Guide which is a (very) basic introduction to Unix and your life in the CSE
Introduction to Unix - Lab Exercise 0 Along with this document you should also receive a printout entitled First Year Survival Guide which is a (very) basic introduction to Unix and your life in the CSE
1 Register 2 Take Course 3 Take Test 4 Get Certificate
 Training Guide for Group Administrators Use this Admin Guide if you manage a training account for a group of learners. If you are not managing a group account, please use the Learner Guide instead. Training
Training Guide for Group Administrators Use this Admin Guide if you manage a training account for a group of learners. If you are not managing a group account, please use the Learner Guide instead. Training
Clean & Speed Up Windows with AWO
 Clean & Speed Up Windows with AWO C 400 / 1 Manage Windows with this Powerful Collection of System Tools Every version of Windows comes with at least a few programs for managing different aspects of your
Clean & Speed Up Windows with AWO C 400 / 1 Manage Windows with this Powerful Collection of System Tools Every version of Windows comes with at least a few programs for managing different aspects of your
Data Management Unit, V3.1 University of Pennsylvania Treatment Research Center, 2010 Page 2
 Welcome to the Data Entry System User s Manual. This manual will cover all of the steps necessary for you to successfully navigate and operate the Data Management Unit s Web based data entry system. We
Welcome to the Data Entry System User s Manual. This manual will cover all of the steps necessary for you to successfully navigate and operate the Data Management Unit s Web based data entry system. We
If you experience issues at any point in the process, try checking our Troublshooting guide.
 Follow along with this guide to set up your Omega2 for the first time. We ll first learn how to properly connect your Omega to a Dock and power it up. Then we ll connect to it to use the Setup Wizard to
Follow along with this guide to set up your Omega2 for the first time. We ll first learn how to properly connect your Omega to a Dock and power it up. Then we ll connect to it to use the Setup Wizard to
Pragmatic Guide to Git
 Extracted from: Pragmatic Guide to Git This PDF file contains pages extracted from Pragmatic Guide to Git, published by the Pragmatic Bookshelf. For more information or to purchase a paperback or PDF copy,
Extracted from: Pragmatic Guide to Git This PDF file contains pages extracted from Pragmatic Guide to Git, published by the Pragmatic Bookshelf. For more information or to purchase a paperback or PDF copy,
Configuring Facebook for a More Secure Social Networking Experience
 CPF 00004-16-CID361-9H-Facebook* 8 March 2017 Configuring Facebook for a More Secure Social Networking Experience Settings Settings are available under the Facebook Configuration Arrow. General Account
CPF 00004-16-CID361-9H-Facebook* 8 March 2017 Configuring Facebook for a More Secure Social Networking Experience Settings Settings are available under the Facebook Configuration Arrow. General Account
Akana API Platform: Upgrade Guide
 Akana API Platform: Upgrade Guide Version 8.0 to 8.2 Akana API Platform Upgrade Guide Version 8.0 to 8.2 November, 2016 (update v2) Copyright Copyright 2016 Akana, Inc. All rights reserved. Trademarks
Akana API Platform: Upgrade Guide Version 8.0 to 8.2 Akana API Platform Upgrade Guide Version 8.0 to 8.2 November, 2016 (update v2) Copyright Copyright 2016 Akana, Inc. All rights reserved. Trademarks
How to Login, Logout and Manage Password (QRG)
 How to Login, Logout and Manage Password (QRG) This Quick Reference Guide covers the following topics: 1. How to login in to the DCC. How to change (reset) your password 3. What to do if you have forgotten
How to Login, Logout and Manage Password (QRG) This Quick Reference Guide covers the following topics: 1. How to login in to the DCC. How to change (reset) your password 3. What to do if you have forgotten
How to set up your wireless network
 How to set up your wireless network There are several steps involved in securing your wireless network. I recommend that you take these steps in order and only change one item at a time. While this may
How to set up your wireless network There are several steps involved in securing your wireless network. I recommend that you take these steps in order and only change one item at a time. While this may
Publications Database
 Getting Started Guide Publications Database To w a r d s a S u s t a i n a b l e A s i a - P a c i f i c!1 Table of Contents Introduction 3 Conventions 3 Getting Started 4 Suggesting a Topic 11 Appendix
Getting Started Guide Publications Database To w a r d s a S u s t a i n a b l e A s i a - P a c i f i c!1 Table of Contents Introduction 3 Conventions 3 Getting Started 4 Suggesting a Topic 11 Appendix
Prompts that will appear on your PC that will allow you to print to a copier/printer with PaperCut installed:
 Introduction to using PaperCut (printing cost management system): Printing: Prompts that will appear on your PC that will allow you to print to a copier/printer with PaperCut installed: Initial identification
Introduction to using PaperCut (printing cost management system): Printing: Prompts that will appear on your PC that will allow you to print to a copier/printer with PaperCut installed: Initial identification
Designing the staging area contents
 We are going to design and build our very first ETL mapping in OWB, but where do we get started? We know we have to pull data from the acme_pos transactional database as we saw back in topic 2. The source
We are going to design and build our very first ETL mapping in OWB, but where do we get started? We know we have to pull data from the acme_pos transactional database as we saw back in topic 2. The source
CIS 231 Windows 7 Install Lab #2
 CIS 231 Windows 7 Install Lab #2 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in the
CIS 231 Windows 7 Install Lab #2 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in the
Creating a target user and module
 The Warehouse Builder contains a number of objects, which we can use in designing our data warehouse, that are either relational or dimensional. OWB currently supports designing a target schema only in
The Warehouse Builder contains a number of objects, which we can use in designing our data warehouse, that are either relational or dimensional. OWB currently supports designing a target schema only in
ACCELERATOR 8.0 CISCO JABBER INTEGRATION GUIDE
 ACCELERATOR 8.0 CISCO JABBER INTEGRATION GUIDE April 2017 Tango Networks, Inc. phone: +1 469-920-2100 2801 Network Blvd, Suite 200 fax: +1 469-920-2099 Frisco, TX 75034 USA www.tango-networks.com 2004-2017
ACCELERATOR 8.0 CISCO JABBER INTEGRATION GUIDE April 2017 Tango Networks, Inc. phone: +1 469-920-2100 2801 Network Blvd, Suite 200 fax: +1 469-920-2099 Frisco, TX 75034 USA www.tango-networks.com 2004-2017
INSTALLATION GUIDE Spring 2017
 INSTALLATION GUIDE Spring 2017 Copyright and Disclaimer This document, as well as the software described in it, is furnished under license of the Instant Technologies Software Evaluation Agreement and
INSTALLATION GUIDE Spring 2017 Copyright and Disclaimer This document, as well as the software described in it, is furnished under license of the Instant Technologies Software Evaluation Agreement and
Intro. Scheme Basics. scm> 5 5. scm>
 Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
Setting Up Identity Management
 APPENDIX D Setting Up Identity Management To prepare for the RHCSA and RHCE exams, you need to use a server that provides Lightweight Directory Access Protocol (LDAP) and Kerberos services. The configuration
APPENDIX D Setting Up Identity Management To prepare for the RHCSA and RHCE exams, you need to use a server that provides Lightweight Directory Access Protocol (LDAP) and Kerberos services. The configuration
FREQUENTLY ASKED QUESTIONS (FAQs)
 FREQUENTLY ASKED QUESTIONS (FAQs) OMREB s New Single Sign-On (SSO) Portal & Scout for SAFEAccess from Clareity 2 FAQs FREQUENTLY ASKED QUESTIONS (FAQs) Q: What is Clareity? A: Clareity Security s Single
FREQUENTLY ASKED QUESTIONS (FAQs) OMREB s New Single Sign-On (SSO) Portal & Scout for SAFEAccess from Clareity 2 FAQs FREQUENTLY ASKED QUESTIONS (FAQs) Q: What is Clareity? A: Clareity Security s Single
Final Examination CS 111, Fall 2016 UCLA. Name:
 Final Examination CS 111, Fall 2016 UCLA Name: This is an open book, open note test. You may use electronic devices to take the test, but may not access the network during the test. You have three hours
Final Examination CS 111, Fall 2016 UCLA Name: This is an open book, open note test. You may use electronic devices to take the test, but may not access the network during the test. You have three hours
Quick Start Manual for Mechanical TA
 Quick Start Manual for Mechanical TA Chris Thornton cwthornt@cs.ubc.ca August 18, 2013 Contents 1 Quick Install 1 2 Creating Courses 2 3 User Management 2 4 Assignment Management 3 4.1 Peer Review Assignment
Quick Start Manual for Mechanical TA Chris Thornton cwthornt@cs.ubc.ca August 18, 2013 Contents 1 Quick Install 1 2 Creating Courses 2 3 User Management 2 4 Assignment Management 3 4.1 Peer Review Assignment
Best Practices for Naming/Creating Report Templates
 Best Practices for Naming/Creating Report Templates This document is for any Skyward Web Student Management users, and covers best practices for naming and/or creating Skyward report templates. It covers
Best Practices for Naming/Creating Report Templates This document is for any Skyward Web Student Management users, and covers best practices for naming and/or creating Skyward report templates. It covers
Google Analytics 101
 Copyright GetABusinessMobileApp.com All rights reserved worldwide. YOUR RIGHTS: This book is restricted to your personal use only. It does not come with any other rights. LEGAL DISCLAIMER: This book is
Copyright GetABusinessMobileApp.com All rights reserved worldwide. YOUR RIGHTS: This book is restricted to your personal use only. It does not come with any other rights. LEGAL DISCLAIMER: This book is
The Dynamic Typing Interlude
 CHAPTER 6 The Dynamic Typing Interlude In the prior chapter, we began exploring Python s core object types in depth with a look at Python numbers. We ll resume our object type tour in the next chapter,
CHAPTER 6 The Dynamic Typing Interlude In the prior chapter, we began exploring Python s core object types in depth with a look at Python numbers. We ll resume our object type tour in the next chapter,
Assignment 0. Nothing here to hand in
 Assignment 0 Nothing here to hand in The questions here have solutions attached. Follow the solutions to see what to do, if you cannot otherwise guess. Though there is nothing here to hand in, it is very
Assignment 0 Nothing here to hand in The questions here have solutions attached. Follow the solutions to see what to do, if you cannot otherwise guess. Though there is nothing here to hand in, it is very
Your . A setup guide. Last updated March 7, Kingsford Avenue, Glasgow G44 3EU
 fuzzylime WE KNOW DESIGN WEB DESIGN AND CONTENT MANAGEMENT 19 Kingsford Avenue, Glasgow G44 3EU 0141 416 1040 hello@fuzzylime.co.uk www.fuzzylime.co.uk Your email A setup guide Last updated March 7, 2017
fuzzylime WE KNOW DESIGN WEB DESIGN AND CONTENT MANAGEMENT 19 Kingsford Avenue, Glasgow G44 3EU 0141 416 1040 hello@fuzzylime.co.uk www.fuzzylime.co.uk Your email A setup guide Last updated March 7, 2017
Live Agent for Support Agents
 Live Agent for Support Agents Salesforce, Winter 18 @salesforcedocs Last updated: November 30, 2017 Copyright 2000 2017 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of
Live Agent for Support Agents Salesforce, Winter 18 @salesforcedocs Last updated: November 30, 2017 Copyright 2000 2017 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of
Using Hive for Data Warehousing
 An IBM Proof of Technology Using Hive for Data Warehousing Unit 5: Hive Storage Formats An IBM Proof of Technology Catalog Number Copyright IBM Corporation, 2015 US Government Users Restricted Rights -
An IBM Proof of Technology Using Hive for Data Warehousing Unit 5: Hive Storage Formats An IBM Proof of Technology Catalog Number Copyright IBM Corporation, 2015 US Government Users Restricted Rights -
In the previous lecture we went over the process of building a search. We identified the major concepts of a topic. We used Boolean to define the
 In the previous lecture we went over the process of building a search. We identified the major concepts of a topic. We used Boolean to define the relationships between concepts. And we discussed common
In the previous lecture we went over the process of building a search. We identified the major concepts of a topic. We used Boolean to define the relationships between concepts. And we discussed common
Data Protection and Information Security. Presented by Emma Hawksworth Slater and Gordon
 Data Protection and Information Security Webinar Presented by Emma Hawksworth Slater and Gordon 1 3 ways to participate Ask questions link below this presentation Answer the polls link below this presentation
Data Protection and Information Security Webinar Presented by Emma Hawksworth Slater and Gordon 1 3 ways to participate Ask questions link below this presentation Answer the polls link below this presentation
Read this first. It ll help you get started.
 Your Sony EB1E0E laptop guide Read this first. It ll help you get started. We re better, connected Tips before getting started Some messages from McAfee might pop up while you set up your laptop. Close
Your Sony EB1E0E laptop guide Read this first. It ll help you get started. We re better, connected Tips before getting started Some messages from McAfee might pop up while you set up your laptop. Close
1Password for Mac. by Marcia Bolsinga for AshMUG 1/12/2019
 Why do we need passwords? First of all - why passwords? Passwords are one of the Primary Pain Points in our modern digital existence. Despite all the advances of our modern technology, we haven t managed
Why do we need passwords? First of all - why passwords? Passwords are one of the Primary Pain Points in our modern digital existence. Despite all the advances of our modern technology, we haven t managed
Quick Reference Guide
 Quick Reference Guide Microsoft Surface Hub Learn how to unlock the power of the group by using Microsoft Surface Hub Table of contents Start your session Make a call Add people to a call in progress Use
Quick Reference Guide Microsoft Surface Hub Learn how to unlock the power of the group by using Microsoft Surface Hub Table of contents Start your session Make a call Add people to a call in progress Use
Decision Support Software (DSS)
 Decision Support Software (DSS) 2017.1 March 11, 2017 2017 Tyler Technologies. All Rights Reserved. All rights reserved. Information within this document is the sole property of Tyler Technologies and
Decision Support Software (DSS) 2017.1 March 11, 2017 2017 Tyler Technologies. All Rights Reserved. All rights reserved. Information within this document is the sole property of Tyler Technologies and
PROJECT: NEW JERSEY WATER QUALITY DATA EXCHANGE WQX REPORTER USER S GUIDE. Prepared for New Jersey Department of Environmental Protection
 PROJECT: NEW JERSEY WATER QUALITY DATA EXCHANGE WQX REPORTER USER S GUIDE Prepared for New Jersey Department of Environmental Protection January 29, 2009 11 Princess Road, Unit A Lawrenceville, New Jersey
PROJECT: NEW JERSEY WATER QUALITY DATA EXCHANGE WQX REPORTER USER S GUIDE Prepared for New Jersey Department of Environmental Protection January 29, 2009 11 Princess Road, Unit A Lawrenceville, New Jersey
CS125 : Introduction to Computer Science. Lecture Notes #11 Procedural Composition and Abstraction. c 2005, 2004 Jason Zych
 CS125 : Introduction to Computer Science Lecture Notes #11 Procedural Composition and Abstraction c 2005, 2004 Jason Zych 1 Lecture 11 : Procedural Composition and Abstraction Solving a problem...with
CS125 : Introduction to Computer Science Lecture Notes #11 Procedural Composition and Abstraction c 2005, 2004 Jason Zych 1 Lecture 11 : Procedural Composition and Abstraction Solving a problem...with
Novell Identity Manager
 AUTHORIZED DOCUMENTATION WorkOrder Driver Implementation Guide Novell Identity Manager 4.0.1 April 15, 2011 www.novell.com Legal Notices Novell, Inc. makes no representations or warranties with respect
AUTHORIZED DOCUMENTATION WorkOrder Driver Implementation Guide Novell Identity Manager 4.0.1 April 15, 2011 www.novell.com Legal Notices Novell, Inc. makes no representations or warranties with respect
GOOGLE ANALYTICS 101 INCREASE TRAFFIC AND PROFITS WITH GOOGLE ANALYTICS
 GOOGLE ANALYTICS 101 INCREASE TRAFFIC AND PROFITS WITH GOOGLE ANALYTICS page 2 page 3 Copyright All rights reserved worldwide. YOUR RIGHTS: This book is restricted to your personal use only. It does not
GOOGLE ANALYTICS 101 INCREASE TRAFFIC AND PROFITS WITH GOOGLE ANALYTICS page 2 page 3 Copyright All rights reserved worldwide. YOUR RIGHTS: This book is restricted to your personal use only. It does not
Frequently Asked Questions
 Frequently Asked Questions ACCESS AND NAVIGATION 1. Can I change my password? 2. What are the guidelines for a new password? 3. What types of information will I get in RDC news? 4. I closed RDC Onsite
Frequently Asked Questions ACCESS AND NAVIGATION 1. Can I change my password? 2. What are the guidelines for a new password? 3. What types of information will I get in RDC news? 4. I closed RDC Onsite
Sage Installation and Administration Guide
 Sage 300 2016 Installation and Administration Guide This is a publication of Sage Software, Inc. Copyright 2015. Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product and
Sage 300 2016 Installation and Administration Guide This is a publication of Sage Software, Inc. Copyright 2015. Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product and
No More Passwords (with SSH)
 No More Passwords (with SSH) Ted Dustman March 30, 2009 Contents 1 Introduction 1 1.1 Local or Remote?................................. 1 1.2 SSH Command Set................................ 1 2 Authentication
No More Passwords (with SSH) Ted Dustman March 30, 2009 Contents 1 Introduction 1 1.1 Local or Remote?................................. 1 1.2 SSH Command Set................................ 1 2 Authentication
Lutheran High North Technology The Finder
 Lutheran High North Technology shanarussell@lutheranhighnorth.org www.lutheranhighnorth.org/technology The Finder Your Mac s filing system is called the finder. In this document, we will explore different
Lutheran High North Technology shanarussell@lutheranhighnorth.org www.lutheranhighnorth.org/technology The Finder Your Mac s filing system is called the finder. In this document, we will explore different
Coding with Identity Management & Security
 Coding with Identity Management & Security Part 2 of Identity Management with Progress OpenEdge Peter Judge OpenEdge Development pjudge@progress.com What Is Identity Management? Identity management is
Coding with Identity Management & Security Part 2 of Identity Management with Progress OpenEdge Peter Judge OpenEdge Development pjudge@progress.com What Is Identity Management? Identity management is
Installing Joomla
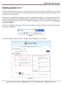 Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
The Definitive Guide to Office 365 External Sharing. An ebook by Sharegate
 The Definitive Guide to Office 365 External Sharing An ebook by Sharegate The Definitive Guide to External Sharing In any organization, whether large or small, sharing content with external users is an
The Definitive Guide to Office 365 External Sharing An ebook by Sharegate The Definitive Guide to External Sharing In any organization, whether large or small, sharing content with external users is an
How to Make a Book Interior File
 How to Make a Book Interior File These instructions are for paperbacks or ebooks that are supposed to be a duplicate of paperback copies. (Note: This is not for getting a document ready for Kindle or for
How to Make a Book Interior File These instructions are for paperbacks or ebooks that are supposed to be a duplicate of paperback copies. (Note: This is not for getting a document ready for Kindle or for
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3
 Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
WORKING IN TEAMS WITH CASECOMPLETE AND SUBVERSION. Contents
 WORKING IN TEAMS WITH CASECOMPLETE AND SUBVERSION Contents Working in Teams with CaseComplete... 3 Need an introduction to how version control works?... 3 Exclusive Checkout... 4 Multiple Checkout... 4
WORKING IN TEAMS WITH CASECOMPLETE AND SUBVERSION Contents Working in Teams with CaseComplete... 3 Need an introduction to how version control works?... 3 Exclusive Checkout... 4 Multiple Checkout... 4
Virtual Food Drive. Administrator User Guide
 Virtual Food Drive Administrator User Guide Contents 1. LOGIN... 2 2. CREATE A VIRTUAL DRIVE... 3 3. VIEW REPORTS... 7 4. VIEW/EDIT DETAILS... 8 5. COPY A DRIVE... 9 6. UPLOAD LOGO(S)... 10 7. UPLOAD ITEM(S)
Virtual Food Drive Administrator User Guide Contents 1. LOGIN... 2 2. CREATE A VIRTUAL DRIVE... 3 3. VIEW REPORTS... 7 4. VIEW/EDIT DETAILS... 8 5. COPY A DRIVE... 9 6. UPLOAD LOGO(S)... 10 7. UPLOAD ITEM(S)
Step 1: Upload a video (skip to Step 2 if you ve already uploaded a video directly from your ipod, Uploading to YouTube and Posting in Blackboard
 Uploading to YouTube and Posting in Blackboard This document will explain 1. How to upload videos from your computer to YouTube 2. How to obtain the URL (web link) or embed code for your video 3. How to
Uploading to YouTube and Posting in Blackboard This document will explain 1. How to upload videos from your computer to YouTube 2. How to obtain the URL (web link) or embed code for your video 3. How to
