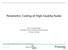
Fig. 1: The perceptual audio coding procedure and three main embedding domains.
|
|
|
- Whitney Hancock
- 5 years ago
- Views:
Transcription
1 1 Spec-ResNet: A General Audio Steganalysis Scheme based on a Deep Residual Network for Spectrograms Yanzhen Ren, Member, IEEE, Dengkai Liu, Qiaochu Xiong, Jianming Fu, and Lina Wang arxiv: v2 [cs.mm] 26 Feb 219 Abstract The widespread application of audio and video communication technologies has resulted in compressed audio data flowing across the Internet and has made it an important carrier for covert communication. Many steganographic schemes have emerged for mainstream audio data compression, including AAC and MP3, with many steganalysis schemes being subsequently developed. However, these steganalysis schemes are only effective in the given embedding domain. In this paper, a general steganalysis scheme, Spec-ResNet (Deep Residual Network of Spectrogram), is proposed to detect steganography schemes in different embedding domains for AAC and MP3. The basic idea is that the steganographic modification of different embedding domains all introduce changes in the decoded audio signal. In this paper, a spectrogram, which is a visual representation of the spectrum of the frequencies of an audio signal, is adopted as the input of the feature network to extract the universal features introduced by steganography schemes. Our deep-neural-networkbased method, Spec-ResNet, can effectively represent steganalysis features, and the features extracted from different spectrogram windows are combined to fully capture the steganalysis features. The experimental results show that the proposed scheme achieves good detection accuracy and generality. The proposed scheme achieves higher detection accuracy for three different AAC steganographic schemes and MP3Stego compared to state-ofthe-art steganalysis schemes based on traditional hand-crafted or CNN-based features. To the best of our knowledge, this audio steganalysis scheme based on spectrograms and a deep residual network is the first to be published. The method proposed in this paper can be extended to the audio steganalysis of other codecs or audio forensics. Index Terms Audio steganalysis, Spectrogram, Deep residual network, Feature representation. I. INTRODUCTION STEGANOGRAPHY is the technique of concealing secret information in digital carriers, such as text, images, audio, and video, to facilitate covert communication. In many cases, these steganography schemes are used by malicious software or malicious organizations. Therefore, steganalysis technology, which is the countermeasure technique against steganography for detecting whether there is secret information in data that appear normal, has been extensively studied. This work is supported by the Natural Science Foundation of China (NSFC) under grant nos , U , and U and the China Scholarship Council. Yanzhen Ren, Dengkai Liu, Qiaochu Xiong, Jianming Fu and Lina Wang are with Key Laboratory of Aerospace Information Security and Trusted Computing, Ministry of Education, School of Cyber Science and Engineering, Wuhan University, Wuhan 4372, China. ( renyz@whu.edu.cn; dengkailiu@whu.edu.cn; emmaxiong@whu.edu.cn; jmfu@whu.edu.cn; lnawang@163.com; ) With the widespread application of various audio and video communication technologies, compressed audio is stored and spread across the Internet. Today, the most widely used audio compression standards are AAC (Advanced Audio Coding) and MP3 (MPEG-1 Audio Layer III). AAC plays a dominant role in various Internet communication applications and can achieve better sound quality than MP3 at similar bit rates; therefore, AAC is gradually replacing MP3. AAC is specified as part of both the MPEG-2 and MPEG-4 standards [1]; therefore, it is used almost everywhere for mainstream audio applications. Today, AAC is the default audio coding format for many mainstream HDTV standards, hardware, mobile phones, and Internet communication applications [2] such as DVB (Digital Video Broadcasting), itunes, the ipod, the iphone, the Sony PlayStation, YouTube, Twitter, Facebook, Youku, Tudou, Baidu Music, QQ Music, and Himalayan. The ubiquitous storage and communication of audio compression data provides a huge covert communication carrier channel. Many steganography schemes based on AAC and MP3 have been proposed [3] [15]. There are three main embedding domains concerning the compression parameters of AAC: Modified Discrete Cosine Transform coefficients (MDCT) [3], the scale factor [4], [5], and Huffman coding [6] [8]. The basic principle behind these steganography schemes is in modifying the compression parameters to hide the secret information. Wang [3] proposed to embed secret information by modifying the small value of quantized MDCT coefficients to achieve high imperceptibility. In [6], the least significant bit (LSB) of the escape sequences in AAC Huffman coding is modified with matrix encoding [16] to embed secret information. In [7], the sign bit of the corresponding MDCT coefficient is modified to implement steganography, therein utilizing the fact that the sign bits of the MDCT coefficients in the signed codebook will be coded separately. In [8], Zhu proposed to embed secret information by modifying the sections of the Huffman coding of AAC. In [9], Luo proposed an adaptive audio steganography scheme in the time domain based on AAC and Syndrome-Trellis coding (STC). Except for [9], the above steganography schemes all modify the compression parameters of AAC. Although the embedding domains are different in each scheme, the MDCT coefficients of each AAC frame are ultimately modified at different levels. For MP3, many steganographic schemes have emerged [1] [12]. Certain MP3 steganographic tools were published early on, including MP3Stego [13], UnderMP3Cover [14], and MP3Stegz [15]. Among them, MP3Stego [13], which embeds
2 2 the secret information by modifying the scale factor in the encoding procedure, is the most well-tested state-of-the-art MP3 steganography scheme. With the development of steganography schemes for AAC and MP3, many steganalysis schemes have followed [17] [25]. To detect steganography schemes in the AAC Huffman coding domain, Ren [17] proposed to extract the Markov transition probability of the neighbouring scale factor band s (SFB s) codebook as the steganalysis feature to model the correlation of the neighbouring SFB s codebook. Calibration technology is used to improve the detection accuracy. To detect the steganography schemes in the AAC MDCT coefficient domain, Ren [19] proposed to extract the Markov transition probabilities and joint probability densities of first-order and second-order differential residuals of the inter-frame and intra-frame MDCT coefficients as steganalysis features. The performance of the schemes [17], [19] is high for certain embedding domains but decreases for other embedding domains. To detect MP3Stego [13], which is one of the most well-tested MP3 steganography schemes, many steganalysis schemes have been developed. Yan [18] proposed to extract the difference between the quantization steps of MP3 neighbouring frames as the steganalysis features. Yan [2] proposed to extract the statistical inconsistencies in the statistical distribution of the number of bits in the audio bit pool before and after recompression as the steganalysis scheme. Yu [21] used a recompression calibration technique and proposed a steganalysis scheme based on the statistical distribution features of Big value. Wang [25] used Markov features to capture the correlations between quantized MDCT coefficients, which are destroyed by the MP3stego embedding procedure. However, the steganalysis features of all the above schemes are extracted from a certain embedding domain; therefore, they achieve good performances for steganographic schemes in an identical embedding domain. With the successful application of Deep Neural Network (DNN) technology in various fields, DNNs have also been used in many steganalysis schemes [26] [38]. Among them, two audio steganalysis schemes are based on DNNs. In [32], a convolutional neural network (CNN) is designed to detect audio steganography schemes in the time domain. This work shows the effects of CNNs in improving the performance of audio steganalysis schemes. However, such schemes are effective at detecting the audio steganography scheme in the time domain but are ineffective on audio steganography schemes for AAC and MP3. In [36], to detect MP3 steganography schemes in the Huffman coding domain, a steganalysis scheme based on CNNs was proposed. This scheme includes three main characteristics: the quantified MDCT matrix is used as the input of the CNN, a high-pass filter is used to enhance the difference introduced by the steganography, and many network optimization strategies are adopted. The experimental results show that the CNN-based scheme performs better than the hand-crafted steganalysis features. However, the same problem is found: the performance of the scheme is reduced to detect other steganography schemes in different embedding domains. According to current research results in the field of steganalysis research, it can be concluded that DNN technology can significantly improve the detection accuracy of steganalysis [32], [35] [37]. However, the key point is how to express the steganalysis data in a more rich and accurate manner and to design a more effective and suitable DNN for steganalysis work. This paper attempts to address these points to improve the generality of steganalysis schemes for AAC and MP3. Although there are many embedding schemes for the audio compression parameters in AAC and MP3, such as the MDCT coefficients [3], the scale factor [4], [5], and Huffman coding [6] [8], all these schemes change the MDCT values in different ways and ultimately change the time-frequency correlations of the audio signal. Therefore, if the steganalysis features are extracted from the time-frequency characteristics of the audio signal, the steganalysis scheme will be more generative and can be used to detect steganographic schemes that cause changes in the time-frequency characteristics. Almost all steganographic schemes for AAC and MP3 audio compression [3] [15] belong to this category. Based on this idea, a steganalysis scheme called Spec-ResNet (Deep Neural Network of Spectrogram) is proposed in this paper. There are three main contributions provided by the proposed scheme. To extract the universal features introduced by the steganography schemes based on perceptual audio coding, the spectrogram, which is a visual representation of the spectrum of frequencies of an audio signal, is adopted as the input of the feature network. Because almost all steganographic schemes in the AAC and MP3 compressed domains produce changes in the spectrum energy relationships between time and different frequency bands, the spectrogram can exactly reflect these relationships. To more effectively extract the classification features of steganography schemes, a deep residual network is used as the basic framework of the proposed scheme: Spec-ResNet. Because deep residual networks use deeper neural networks and do not suffer from the problem of gradient disappearance, they are suitable for extracting steganalysis features based on weak signals. To capture the steganalysis features more completely, the features extracted from multiple spectrograms of different window sizes are combined because the timefrequency relationships in the spectrogram are different under different window sizes. A simple SVM classifier is used to verify the performance improvement of the feature combination. This paper is organized as follows. The related background knowledge is introduced in Section II. In Section III, the proposed steganalysis scheme, Spec-ResNet, is described in detail. The experiments results follow in Section IV. Finally, the conclusion is drawn, and future work is discussed in Section V. II. PRELIMINARY A. The principle of audio codecs Both AAC and MP3 are under the framework of perceptual audio coding; therefore, their encoding principles, including the MDCT transform, psychoacoustic model, quantization and
3 3 audio signal Psychoacoustic model Scale factor Quantization coding Analysis filter bank MDCT coefficient Huffman coding Entropy coding Coding stream Fig. 1: The perceptual audio coding procedure and three main embedding domains. entropy coding, are similar. The advantages of AAC over MP3 include its higher sampling rates and number of channels supported, more efficient coding, and additional modules included to increase compression efficiency. The framework for the perceptual audio coding and the three main embedding domains are shown in Fig.1. During the process of perceptual audio coding, the psychoacoustic model is used to first remove the part of the audio signal that human hearing cannot perceive to reduce the data rate. Then, the input pulse signal is subjected to frame division or block division, and an analysis filter bank is used to perform time-frequency conversion. Each frequency domain sub-band is calculated according to a psychoacoustic model to obtain the corresponding masking threshold and maximum permissible distortion. Three types of cyclic quantization and entropy coding are performed on the transformed MDCT coefficient, and finally, the audio code stream of the entropy coding is output. B. The steganographic schemes of AAC and MP3 Due to lossy quantization in AAC and MP3 coding, a slight modification of the quantized integer MDCT coefficients will not obviously decrease the audio quality. Therefore, the embedding of a secret message can be implemented by fine tuning the value of the compression parameter. There are three main embedding domains: the MDCT coefficients, the scale factor and the Huffman coding parameters, as shown in Fig.1. The basic idea behind these steganography schemes is in modifying the compression parameters slightly to hide the secret information. Many AAC and MP3 steganography schemes have been developed; four such schemes from different embedding domains will be introduced in this section. 1) LSB-EE: In [6], the least significant bit (LSB) of the escape sequences in AAC Huffman coding are modified with matrix encoding to embed secret information. In the AAC codec, the escape sequence is a special codebook used to encode MDCT coefficients with values of greater than 16. The modification of the LSB of the escape sequence produces minimal negative effects on audio quality. In AAC compressed data, MDCT coefficients with values of greater than 16 account for 5%-6% of all coefficients, and they are mainly of low frequencies; therefore, changes in this scheme to the AAC audio signal are almost always in the low-frequency part of the signal. 2) MIN: In [3], Wang proposed a method for implementing steganography in the small-value region of the MDCT coefficients because the energy of the audio is mainly concentrated in the low- and middle-frequency portions, the MDCT coefficients of which are quantized with a smaller quantization step size, and a large quantization step size is used for the highfrequency portion to reduce the distortion as much as possible. For the high-frequency portion, the quantization range is larger, thereby requiring fewer coding bits. The amplitude of the quantized coefficient is basically {-1,, 1}, which is called the small-value region of the MDCT coefficient. In the AAC quantized MDCT coefficient encoding stage, the coefficients of the small value region are generally encoded by codebook 1 and codebook 2, and the 4 quantized MDCT coefficients are grouped into one index value: index. The calculation is given in (1). 3 index = 3 i q [i] + 4, q [i] { 1,, 1} (1) i= The codeword is searched among the codebooks according to index. To further reduce the distortion in AAC audio, the steganographic algorithm uses the method of modifying the last MDCT coefficient, q[3], and calculating a new index to replace the original index. In AAC compressed data, the small MDCT coefficients are mainly in the low- and mid-frequency portions; therefore, the changes induced by this scheme to the AAC audio signal are generally in the low- and mid-frequency portions of the signal. 3) SIGN: In [7], Zhu proposed to embed a message in the Huffman encoding process of the AAC coding stream. The MDCT coefficients are encoded by a plurality of codebooks. According to the number of bits after encoding, the encoder selects an optimal codebook to encode 2 or 4 MDCT coefficients as a Huffman code. If the codebooks selected have sign bits, the sign bits of the non-zero MDCT coefficients are attached to the codeword. The coding stream structure corresponding to the codebook with sign bits is shown in Table I and Table II. In codebooks 1 and 2 or codebooks 5 and 6, Huffman code represents 4 or 2 MDCT coefficients, while sign w, sign x, sign y, sign z are the sign bits of MDCT coefficients w, x, y, z, respectively. sign = represents that the MDCT coefficient is negative, and sign = 1 represents that the MDCT coefficient is positive. TABLE I: AAC coding stream structure of codebooks 1 & 2. Huffman code sign w sign x sign y sign z TABLE II: AAC coding stream structure of codebooks 5 & 6. Huffman code sign x sign y Given an appropriate threshold T, SIGN modifies the sign bit of the MDCT coefficients ranging from T to T accordingly to implement audio steganography. This subtle modification will not change any parameters in the AAC
4 4 Amplitude Frequency(kHz) Waveform Time(s) Spectrogram Time(s) Fig. 2: Waveform and spectrogram of an audio segment. encoding procedure except for the sign bit of a specific MDCT coefficient; therefore, it produces minimal distortion in the audio quality. 4) MP3Stego: In [13], MP3Stego was developed as a public tool to hide information in MP3 files during the MP3 compression process. There are two nested loops used to quantify the MDCT coefficients in the MP3 encoder: an inner loop and an outer loop. The outer loop is used to verify the distortion of the audio signal to guarantee satisfactory audio quality. The inner loop is used to select a suitable scalar factor to qualify the MDCT coefficients with the available number of bits. The hiding operation used by MP3Stego is performed in the inner loop. The part2-3-length variable, which records the number of main-data bits, is controlled by selecting the scalar factor to make the LSB of the part2-3-length variable equal to the secret bit. All four steganographic schemes modify the compression parameters to hide information. Although the embedding domain is different, the final result of these schemes is changes in the MDCT coefficients of the encoded audio signals in different frequency ranges. Because the above four schemes cover almost the entire frequency range of audio signals, they are chosen as the target steganography schemes to verify the generalizability of the proposed steganalysis scheme. C. Spectrogram A spectrogram is a basic visual representation of the spectrum of frequencies of audio signals. A spectogram can show the energy amplitude information of different frequency bands over time, and it contains abundant time-frequency information about the audio signal. Therefore, spectrograms are a good research object for general audio steganalysis when attempting to capture more relative features introduced by different audio steganography schemes. Fig. 2 is the spectrogram of an audio segment together with its waveform. In the spectrogram, the horizontal axis represents the time domain of the audio signal, and the vertical axis represents the frequency domain; the third dimension, which is represented by the intensity of the colour of each point in the image, indicates the amplitude of the frequency at that time. To plot the spectrogram of the audio signal, the signal is divided into many frames under a given window size. The formant of the spectrogram can effectively express the acoustic parameters, and the spectrogram s local characteristics can accurately represent additive noise; therefore, it is an effective candidate for capturing the traces left by embedding operations. III. THE ARCHITECTURE OF SPEC-RESNET Based on the above analysis, a universal audio steganalysis scheme, Spec-ResNet, is proposed in this paper. The spectrogram of an audio signal is adopted as the steganalysis object, a deep residual network is used to extract the steganalysis features, and several spectrograms under different window sizes are combined to extract more rich features. The main architecture of the Spec-ResNet scheme, which consists of three main components, i.e., the Spectrogram Preprocess Module (SPM), the Deep Residual Steganalysis Network (S-ResNet) and the Classification Module (CM), is shown in Fig. 3. SPM generates the spectrogram for the given window size of the input audio signal and uses filters to preprocess the spectrogram. S-ResNet is the steganalysis feature network framework based on the deep residual network architecture and is used to extract the steganalysis features of the filtered spectrogram. The CM is a traditional classification process, which fuses the features from multiple spectrograms under different window sizes. The details of each module are described below. A. Spectrogram Preprocess Module In this module, the trained or test audio signals are represented as a spectrogram under a given window size. Audio signals are highly correlated in both the time and frequency domains; therefore, the spectrogram is a highly effective representation for analysing the correlation changes in the time and frequency domain introduced by the steganography operation. The spectrogram of the audio signal contains three type of signals: the audio content signal, the noise of the real audio signal and the noise introduced by embedding operations. As in the image steganalysis tasks, the noise introduced by steganography is weak; therefore, the audio signal noise should be amplified to improve the signal-to-noise ratio (SNR) of the steganography noise. In [39], Fridrich et al. proposed an image steganalysis scheme based on the spatial domain rich model feature (SRM), in which multiple filters are introduced to capture the noise distribution characteristics from the tested image in different directions and dimensions. Inspired by this work, the correlations between intra-frame and inter-frame information in the spectrograms of 1 cover audio samples are analysed by linear regression, and multiple filters are designed to preprocess the spectrogram. The audio signals have a duration of 2 s at 32 khz, are AAC files, and are decoded as WAV files. The spectrogram is an n m spectrogram, where n is half the window size due to the symmetry in the Fourier transform and m is the total number of frames in one piece of audio with 5% overlap (e.g., if the window size N = 124, the dimension of the spectrogram
5 5 Filters with fixed parameters Deep residual network(s-resnet) Spectrogram Original audio signal... Classification module(cm) Filters with fixed parameters Deep residual network(s-resnet) Spectrogram Fig. 3: Architecture of the proposed steganalysis scheme: Spec-ResNet Fig. 4: The results of the linear regression. The depth of the colour or the absolute value of logistic coefficients represent the strength of the correlation. Fig. 5: The filters based on the intra-frame and inter-frame correlations. +1. is ). The multiple linear regression model is shown in (2). y is the dependent variable, x t, t = 1, 2,..., s is the independent variable, and β is the bias. For the 3 3 filter, s is 8, and the correlation between the matrix centre point and the 8 neighbouring signal points is presented in Fig. 4. y = β + β 1 x β t x t β s x s (2) In Fig.4, the correlations between the neighbouring points in the horizontal and vertical directions are relatively strong, especially in the vertical direction. In the spectrogram, the vertical direction correlation is the relevance of the neighbouring frequency band in the same frame, and the horizontal direction describes the relation between successive frames in the same frequency band. Based on the above analysis, a set of filters from different directions are chosen as the first convolutional layer of the deep residual network to extract the energy difference introduced by the steganographic noise between the cover and stego samples. In this work, 4 fixed-parameter filters are chosen to preprocess the spectrogram. The size of the filters is 3 3, and blanks are filled with zeroes, as shown in Fig. 5. As future work, the filter parameters can be trained by the network to improve the performance of the proposed scheme. B. Deep Residual Steganalysis Network The spectrogram of the audio signal is filtered using the four filters. Then, it is processed by the initial convolutional layer with 1 output channels to extract the potential correlations in the feature matrix. S-ResNet consists of 3 layers, and there is a shortcut for each pair of convolutional layers. A global average pooling layer is subsequently applied. The S-ResNet
6 6 Audio Spectrogram Preprocess Module 3 3 Init conv, 1 BN ReLu, stride=2 in both directions 3 3 average pooling, stride=2 in both directions 3 3 average pooling 3 3 Conv, 1 BN ReLu 3 3 Conv, 1 + Global average pooling Classification Module Fig. 6: The structure of the S-ResNet deep residual steganalysis network.. architecture is shown in Fig. 6, and details about S-ResNet are as follows. 1) Convolutional layers: The convolutional layers in this paper are a 3 3 kernel, regardless of whether the parameters of the filters are fixed. The filters introduced in SPM are applied to weaken the influence of the audio content in the spectrogram. The remaining convolutional layers, which include the initial convolutional layer after SPM, are used to capture the potential correlations inherent in the feature matrix. Based on the number of channels, the convolutional layers in the residual network can be classified into three types: Conv- A,, and, as shown in Fig. 7. There are 1, 2, and 4 channels in,, and, respectively, and the stride is 1 in both the horizontal and vertical directions unless otherwise stated. Moreover, there are 5 residual units in each group, which means 1 convolutional layers. 2) Residual unit: Generally, for Convolutional Neural Networks (CNNs), more convolutional layers means that the features extracted from different dimensions are richer and will provide higher classification accuracy. However, once the CNN reaches a certain depth, increasing the number of neural network layers may lead to a degradation of the performance due to the vanishing gradient problem. At this time, the training and test accuracies will decrease; therefore, it would be difficult to train an effective neural network, and BN ReLU Conv, 3 3 channels, stride=1 both in horizonal and vertical direction if not specified explicitly. Fig. 7: The structure of the convolutional layer. has 1 channels, has 2 channels, and has 4 channels. the learning ability of the deep neural network will be limited. Compared with classical CNNs, the residual network [4] is capable of integrating more convolutional layers without suffering a decrease in network performance. The model learning can be simplified to approximate a mapping function learning, as described in Fig.8. H (x) = x is the hypothesis model of the cascaded convolutional layers. The objective of the CNN is in attempting to find a mapping function H (x) directly. However, a residual network is different due to the identity function x; a residual network attempts to find a residual function F (x) = H (x) x instead. In this.
7 7 x x labels. With a given threshold ranging from to 1 (default of.5), the tested samples are judged as cover or stego. Weight layer Weight layer ReLU Weight layer ReLU F(x) ReLU Weight layer x S-ResNet 4-dimension feature Fully connected layer Softmax Classification result Fig. 9: The classification module for Spec-ResNet of the spectrogram under the given window size.. H(x) F(x)+x ReLU (a) Convolutional unit (b) Residual unit. Fig. 8: The structure of the convolutional unit and the residual unit. way, the residual network is transformed to approximate an ideal hypothesis by learning the residual F (x) =, which is easier than approximating H (x) directly. Obviously, the convolutional output is more sensitive to changes in the input than previously with the identity function x introduced. In Fig.6, the arc across each pair of convolutional layers represents the shortcut. The real arc indicates that x has the same size as F (x), and the two tensors can be added together directly. A dashed arc between and or Conv- B and indicates that they have different sizes, and x requires downsampling before the add operation. 3) Batch normalization layer: Batch normalization was proposed in [41] to accelerate deep network training. The distributions of the inputs before each hidden layer vary in each training iteration. Batch normalization performs normalization for each training iteration instead of setting lower learning rates at first or restricting parameter initialization, which requires more time to train the model. Batch normalization is applied before each new convolutional layer in Fig.6. 4) Activation function: In addition to batch normalization, an activation function is applied after each batch normalization in S-ResNet. Nonlinear links between convolutional layers provide better expression ability than do linear model; therefore, the Rectified Linear Unit (ReLU) is adopted as the activation function in this paper. 5) Pooling layers: To reduce the computational complexity, a max pooling layer or average pooling layer is used in the deep network to reduce the feature dimensions. A 3 3 average pooling layer is applied to S-ResNet between and and between and with stride = 2 in both the horizontal and vertical directions. There are no pooling layers in the shortcut across,, or to keep the dimensions of x and F (x) consistent. A global average pooling is applied immediately before the classification module (CM) to obtain a 4-dimensional classification feature. C. Classification module In other CNN-based [32], [36] and RNN-based [42] steganalysis schemes, the classification module in the network is always a fully connected layer with a 2-way softmax layer, as shown in Fig.9, for obtaining the probabilities of 2 class Under the short-time Fourier transform, different spectrograms with different scales will be generated when different window sizes are used. When the window size N is small, a broad-band spectrogram will be generated, the time bandwidth is narrow, and the corresponding frequency bandwidth is broad. A narrow-band spectrogram will produce the opposite characteristics. A broad-band spectrogram can well reflect the time-varying characteristics of the spectrum; however, the frequency resolution is low and does not accurately reflect the texture characteristics of the sound. The frequency resolution of the narrow-band spectrogram is too small to properly identify the position of the formant. In the spectrogram feature map, the audio signal characteristics are different under different window sizes; therefore, it is very important to select a suitable window size for steganalysis. In this paper, a spectrogram with different window sizes is considered. For a given audio sample, its spectrogram has different dimensions with different N; however, the classification feature s dimension after global average pooling is constant. In our experiment, three spectrograms with different window sizes are chosen to increase the diversity of features. A total of three 4-dimensional features are cascaded to a 12-dimensional feature as the final steganalysis feature. Fig. 1 presents the classification module used in this paper, and the window sizes N are 124, 512, and 256. LibSVM [43] is introduced to train the ultimate classification model based on the 12-dimensional feature originating from the audio samples. In detection stage, the 12-dimensional feature extracted from the test audio samples is used to judge whether a piece of audio is cover or stego audio. IV. EXPERIMENTS To evaluate the performance of the proposed Spec-ResNet scheme, three experiments have been performed. The purpose of the first experiment is to evaluate the detection accuracy of the proposed scheme for the three AAC steganography schemes with different embedding domains. Spectrograms with three different window sizes are used to evaluate the influence on the detection performance. The second experiment is implemented to compare Spec-ResNet with work on other steganalysis schemes. The third experiment is performed to detect MP3Stego, which uses the MP3 codec and whereby the embedding domain is the scalar factor. A. Experimental setup 1) Dataset: To the best of the authors knowledge, there are no public audio datasets for AAC or MP3 steganalysis; therefore, we constructed an in-house audio dataset. A total of 186
8 8 Spectrogram with N=124 (512*128) Spectrogram with N=512 (256*256) Spectrogram with N=256 (128*512) Trained model-1 Trained model-2 Trained model-3 4-dimension feature 4-dimension feature 4-dimension feature Fig. 1: The classification module for Spec-ResNet with multiple spectrograms under different window sizes. recordings of music, including different musical styles, such as jazz, rock, country, pop; different languages (mainly Chinese and English); and different singer genders, were downloaded from the Internet. The music samples were cut into clips to construct the AAC audio dataset and the MP3 audio dataset. All the audio datasets in the experiments described below. The project is based on Tensorflow CUDA CuDNN Python In addition, all parameters are trained with the Adam optimizer: the mini-batch size is 32, which means that 16 pairs of cover and stego audio samples are used; the learning rate decay is.9; and the weight decay is a) AAC audio dataset: The 1, 16-kHz, 16-bit, 2-s long audio samples are used to construct 4 different audio sample sets, including one cover sample set (CDB AAC) and three stego sample sets (SDB AAC LSB, SDB AAC MIN, SDB AAC SIGN). The main construction of the four datasets is as follows. CDB AAC: The audio samples in WAV format are encoded using the open-source audio encoder FAAC [44] at 32 kbps and then decoded to WAV using FAAD2. The decoded audio samples are 32 khz with 2 channels, and the total number of cover samples in CDB AAC is 1,. SDB AAC LSB: The 1, audio samples (.m4a format) are generated by the LSB EE steganographic scheme [6], and the secret message is embedded with relative embedding rates (EBRs) of 1%, 2%, 3%, 5%, and 1%. EBR is the ratio of the embedded message length to the maximum embedded message length. The total number of stego samples (.wav format) in SDB AAC LSB is 1, 5 = 5, after the compressed audio bitstream is decoded using FAAD2. SDB AAC MIN: The 1, audio samples (.m4a format) are generated by the MIN steganographic scheme [3], and the secret message is embedded with EBRs of 1%, 2%, 3%, 5%, and 1%. The total number of stego samples (.wav format) in SDB AAC MIN is 1, 5 = 5, after the compressed audio samples are decoded using FAAD2.. SDB AAC SIGN: The 1, audio samples (.m4a format) are generated by the SIGN steganographic scheme [7], and the secret information is embedded with EBRs of 1%, 2%, 3%, 5%, and 1%. The total number of stego samples (.wav format) in SDB AAC SIGN is 1, 5 = 5, after the compressed audio samples are decoded with FAAD2. b) MP3 audio datasets: A total of 9, 16-bit, 44.1 khz, 5-s-long audio sample segments are used to construct 2 different audio datasets, including a cover sample set(cdb MP3) and a stego sample set(sdb MP3). The main contents of the two datasets are as follows. CDB MP3: The audio samples in the WAV file format are encoded at 128 kbps and decoded using a publicly available MP3 codec. The decoded audio samples (.wav format) are 44.1 khz samples, and the total number of cover samples in CDB MP3 is 9,. SDB MP3: The audio samples in the WAV file are encoded using MP3Stego [13]. Because the maximum embedding capacity of MP3Stego is approximately 2 bits per frame and because a 5 s audio sample into which a 3-byte message is embedded has 191 frames, the EBR is nearly 6%. In addition, the total number of stego samples in SDB MP3 is 9,. 2) Metrics: To evaluate the detection accuracy of the proposed scheme and to compare schemes, the TPR (True Positive Rate), TNR (True Negative Rate) and ACC (Classification Accuracy) are adopted as metrics. TPR indicates the proportion of stego samples that are detected as stego, TNR means the proportion of cover samples that are detected as cover, and ACC is the detection accuracy for all cover and stego samples. B. Experiments and Results 1) Experiment I: This experiment is performed to evaluate the detection accuracy of the proposed scheme. Three AAC steganography schemes with different embedding domains are detected. Spectrograms with three different window sizes N win = 256, 512, or 1, 24 are extracted from 6, audio samples in CDB AAC, SDB AAC LSB, SDB AAC MIN, and SDB AAC SIGN. In the training procedure, the spectrograms extracted from 3, audio samples in CDB AAC are used as the cover input signal, and the spectrograms of 3, audio samples with.3 EBR in SDB AAC LSB, SDB AAC MIN and SDB AAC SIGN are selected as the stego input signal. For a given window size, the training set contains 6, feature matrices, as described above (for N = 256, the dimensions of the spectrogram feature matrix are ; for N = 512, the dimensions of the spectrogram feature matrix are ; and for N = 124, the dimensions of the spectrogram feature matrix are ). However, the architecture of the test dataset is different. For the cover samples, the spectrogram of the remaining 3, audio samples in CDB AAC is selected, and spectrogram of the corresponding 3, audio samples generated by the different schemes and with different EBR (2 samples in each algorithm for a given EBR) is selected as the stego samples. Three models are trained based on the spectrogram with three different window sizes. The results of experiment I are shown in Table III. N = 256, 512, or 124 represents the spectrogram window size.
9 9 EA is the embedding scheme, and ACC is the average detection accuracy of the trained model toward cover or stego samples generated by a given steganographic algorithm with different EBR. AVERAGE represents the average detection accuracy for the cover or stego samples under a given EBR for multiple schemes. The results show that the performances of the classification model trained by a spectrogram with different window sizes are different. The average accuracy for cover samples under different models is always greater than 83.89%. When N = 512, the accuracy for the cover samples can is up to 93.47%, and the average detection accuracy for the stego samples with 1% EBR is greater than 82.6%. When N = 124, the accuracy reaches 89.5%. This shows that the proposed Spec-ResNet scheme can be used to detect multiple steganographic schemes in different embedding domains and achieve good performance. 2) Experiment II: This experiment is performed to compare the detection accuracy of the proposed scheme with other steganalysis schemes. Although the feature matrix of a spectrogram with different window sizes has a different shape, the length of the feature following the global average pooling layer is constant, i.e., 4. For a spectrogram of a given window size, a classification model is trained based on this window size and will be saved thereafter. Then, three 4-dimensional features originating from three trained classification models are merged into a 12-dimensional feature. SVM is used to train the ultimate classification model, therein considering spectrogram features with different scales. In particular, the architecture of the training and test sets is the same as that in Experiment I. The measure the performance of Spec-ResNet, it is compared with Ren s scheme [19], Luo s scheme [32], and Zhao s scheme [36]. In Ren s scheme [19], a classical rich model feature is introduced to fully analyse the Markov transition probabilities and joint probability densities of the first-order differentials and second-order differential residuals of interframe and intra-frame quantified MDCT coefficients. In Luo s scheme [32], the classifier is trained with seven convolutional neural networks based on the original audio signal in the time domain. In [36], a steganalysis scheme based on a CNN of the quantified MDCT matrix is proposed to detect the MP3 steganography schemes in the Huffman coding domain. In this experiment, the scheme in [36] is realized in the AAC codec, and the CNN is replaced with S-ResNet; this will improve the performance of the scheme in [36]. Audio samples with a duration of 2 s are adopted for performance testing in this experiment, and 8, audio samples, including 4, cover samples and 4, stego samples, are used for training. The remaining 12, audio samples are used for testing. The results of experiment II are shown in Table IV. Method represents the steganalysis scheme, and EA, AVERAGE and ACC are as in Table III. Table IV shows that the detection performance of the Spec-ResNet steganalysis scheme is better than that of the three trained models in Table III, which shows that the feature combination of spectrograms with different window sizes can improve the performance of Spec-ResNet. Compared with other steganalysis schemes, the average detection accuracy of Spec-ResNet is higher than that of the compared schemes, including traditional hand-crafted schemes [19] and CNN-based schemes [32], [36]. In [19], the length of the audio samples is 2 seconds; however, Spec-ResNet still outperformed that scheme when applied to 2 s audio samples. Fig. 11 is a graphical representation of Table IV. 3) Experiment III: To evaluate the detection performance of Spec-ResNet for MP3s, MP3Stego is chosen as the detection object. The training procedure is the same as in Experiment I. The audio duration is 5 s, and the three different window sizes are N = 512, 124, or 248 (for N = 512, 124, or 248, the dimensions of the feature matrix are , , and , respectively). The samples in the MP3 audio data set are 44.1 khz samples. The training set consists of the spectrograms of 15 audio samples in CDB MP3 and of the 15 audio samples in SDB MP3, and the test set is the same as the training set in the architecture. There is no intersection between the training set and the test set. The performance of Spec-ResNet is compared with other steganalysis schemes. Wang s method [25] proposed a Markov feature to capture the correlations between the quantized MDCT coefficients (referred to as QMDCTs), which are destroyed by MP3stego s embedding behaviour. Luo s scheme [32] is compared for detecting MP3stego with an audio duration of 5 s, in which 8 audio samples are chosen to train the CNN model and 2 audio samples are used to test the trained model. The detection performance of the proposed Spec-ResNet scheme for MP3Stego was compared with the other schemes proposed in [25], [32]. The results are presented in Table V. Mixture represents the mixture classification model, which is trained on three spectrograms with different window sizes, and S len is the sample length. Spec-ResNet outperforms the trained model based on a spectrogram with only one window size. The detection accuracy (ACC) of the proposed scheme, which is in bold, is higher than the compared steganalysis schemes based on traditional hand-crafted features [25] or deep neural networks [32]. This means that the proposed Spec- ResNet steganalysis scheme can also be applied to other audio coding standards, such as MP3, and can achieve high detection accuracy. V. CONCLUSION In this paper, a general steganalysis scheme, Spec-ResNet, based on spectrograms and deep residual networks is proposed. Spec-ResNet can be used to detect the steganographic schemes of the different embedding domains of AAC and MP3. Three conclusions can be drawn from this work: 1). A spectrogram represents the spectral relationships of time series of audio signals and can be effectively used as an analysis signal for audio steganalysis schemes to obtain more universal features. The spectrogram can be extended to other audio analysis areas, such as audio forensics, to improve the classification performance. 2) Deep residual networks, which solve the problem of gradient disappearance, are suitable for extracting steganalysis features based on weak signal changes. 3) The fusion of training features from different scales improves the classification accuracy. The experimental results show that the proposed scheme achieves good detection accuracy and generalizability. The
10 1 TABLE III: The performance of the Spec-ResNet steganalysis scheme using spectrograms with different window sizes Window Size EA TNR TPR Cover 1% 2% 3% 5% 1% ACC N =124 MIN [3] SIGN [7] AVERAGE N =512 MIN [3] SIGN [7] AVERAGE N =256 MIN [3] SIGN [7] AVERAGE TABLE IV: The performance of various steganalysis schemes, Spec-ResNet, Ren [19], Zhao [36], and Luo [32], in detecting existing AAC steganography schemes. Steganalysis Scheme EA TNR TPR Cover 1% 2% 3% 5% 1% ACC Spec-ResNet:Mixture Ren [19] Zhao [36] Luo [32] MIN [3] SIGN [7] AVERAGE MIN [3] SIGN [7] AVERAGE MIN [3] SIGN [7] AVERAGE MIN [3] SIGN [7] AVERAGE
11 11 1 LSB-EE 1 MIN 1 SIGN detection accuracy proposed, 2s.2 Ren et.al, 2s.1 Zhao et.al, 2s Luo et.al, 2s relative embedding rate(%) (a) detection accuracy proposed, 2s.2 Ren et.al, 2s.1 Zhao et.al, 2s Luo et.al, 2s relative embedding rate(%) (b) detection accuracy proposed, 2s.2 Ren et.al, 2s.1 Zhao et.al, 2s Luo et.al, 2s relative embedding rate(%) Fig. 11: The detection accuracy of the Spec-ResNet, Ren [19], Zhao [36], and Luo [32] steganalysis schemes for detecting existing AAC steganography schemes: (a), (b) MIN [3], and (c) SIGN [7]. (c) TABLE V: The performance of the steganalysis schemes to detect MP3Stego [13]. Steganalysis Scheme S len EBR TNR TPR ACC Spec-ResNet:N =512 5 s 6% Spec-ResNet:N =124 5 s 6% Spec-ResNet:N =248 5 s 6% Spec-ResNet:Mixture 5 s 6% Luo [32] 5 s 6% Wang [25] 1s 1%.925 scheme achieves a better detection accuracy for the three main AAC embedding domains, MDCT, scale factor and Huffman coding, and MP3Stego compared to other steganalysis schemes. To the best of our knowledge, this paper is the first time an audio steganalysis scheme based on spectrograms and deep residual networks has been proposed. The method in this paper can be applied to other types of audio classification works. ACKNOWLEDGEMENT The authors would like to thank Dr. Weiqi Luo for sharing the source code to their audio steganalysis scheme in [32]. REFERENCES [1] I , Iec information technology-coding of audio-visual objectspart 3: audio, 24. [2] (218) Advanced Audio Coding. [Online]. Available: wikipedia.org/wiki/advanced Audio Coding [3] Y.-J. Wang, L. Guo, and C.-P. Wang, Steganography method for advanced audio coding, Journal of Chinese Computer Systems, vol. 32, no. 7, pp , 211. [4] S. Xu, P. Zhang, P. Wang, and H. Yang, Performance analysis of data hiding in mpeg-4 aac audio, Tsinghua Science and Technology, vol. 14, no. 1, pp , 29. [5] Y. Wei, L. Guo, and Y. Wang, Controlling bitrate steganography on aac audio, in Image and Signal Processing (CISP), 21 3rd International Congress on, vol. 9. IEEE, 21, pp [6] Y. Wang, L. Guo, Y. Wei, and C. Wang, A steganography method for aac audio based on escape sequences, in 21 International Conference on Multimedia Information Networking and Security. IEEE, 21, pp [7] J. Zhu, R. Wang, and D. Yan, The sign bits of huffman codeword-based steganography for aac audio, in Multimedia Technology (ICMT), 21 International Conference on. IEEE, 21, pp [8] J. Zhu, R.-D. Wang, J. Li, and D.-Q. Yan, A huffman coding sectionbased steganography for aac audio, Information Technology Journal, vol. 1, no. 1, pp , 211. [9] W. Luo, Z. Yue, and H. Li, Adaptive audio steganography based on advanced audio coding and syndrome-trellis coding, 217. [1] M. Bazyar and R. Sudirman, A recent review of mp3 based steganography methods, International Journal of Security and Its Applications, vol. 8, no. 6, pp , 214. [11] K. Yang, X. Yi, X. Zhao, and L. Zhou, Adaptive mp3 steganography using equal length entropy codes substitution, in International Workshop on Digital Watermarking. Springer, 217, pp [12] R. Zhang, J. Liu, and F. Zhu, A steganography algorithm based on mp3 linbits bit of huffman codeword, in International Conference on Intelligent Information Hiding and Multimedia Signal Processing. Springer, 217, pp [13] F. Petitcolas, mp3stego, cl. cam. ac. uk/ fapp2/steganography/mp3stego/index. html, [14] (215) Undermp3cover. [Online]. Available: projects/ump3c/ [15] (213) Mp3stegz. [Online]. Available: mp3stegz/ [16] J. Fridrich and D. Soukal, Matrix embedding for large payloads, IEEE Transactions on Information Forensics & Security, vol. 1, no. 3, pp , 26. [17] Y. Ren, Q. Xiong, and L. Wang, Steganalysis of aac using calibrated markov model of adjacent codebook, in Acoustics, Speech and Signal Processing (ICASSP), 216 IEEE International Conference on. IEEE, 216, pp [18] D. Yan, R. Wang, X. Yu, and J. Zhu, Steganalysis for mp3stego using differential statistics of quantization step, Digital Signal Processing, vol. 23, no. 4, pp , 213. [19] Y. Ren, Q. Xiong, and L. Wang, A steganalysis scheme for aac audio based on mdct difference between intra and inter frame, in International Workshop on Digital Watermarking. Springer, 217, pp [2] D. Yan and R. Wang, Detection of mp3stego exploiting recompression calibration-based feature, Multimedia tools and applications, vol. 72, no. 1, pp , 214. [21] X. Yu, R. Wang, and D. Yan, Detecting mp3stego using calibrated side information features, Journal of Software, vol. 8, no. 1, 213. [22] M. Qiao, A. H. Sung, and Q. Liu, Mp3 audio steganalysis, Information sciences, vol. 231, pp , 213. [23] R. Kuriakose and P. Premalatha, A novel method for mp3 steganalysis, in Intelligent Computing, Communication and Devices. Springer, 215, pp [24] C. Jin, R. Wang, D. Yan, P. Ma, and K. Yang, A novel detection scheme for mp3stego with low payload, in IEEE China Summit & International Conference on Signal and Information Processing, 214, pp
STEGANOGRAPHY is the technique that conceals secret. Spec-ResNet: A General Audio Steganalysis scheme based on Deep Residual Network of Spectrogram
 1 Spec-ResNet: A General Audio Steganalysis scheme based on Deep Residual Network of Spectrogram Yanzhen Ren, Member, IEEE, Dengkai Liu, Qiaochu Xiong, Jianming Fu, and Lina Wang arxiv:191.6838v1 [cs.mm]
1 Spec-ResNet: A General Audio Steganalysis scheme based on Deep Residual Network of Spectrogram Yanzhen Ren, Member, IEEE, Dengkai Liu, Qiaochu Xiong, Jianming Fu, and Lina Wang arxiv:191.6838v1 [cs.mm]
Audio-coding standards
 Audio-coding standards The goal is to provide CD-quality audio over telecommunications networks. Almost all CD audio coders are based on the so-called psychoacoustic model of the human auditory system.
Audio-coding standards The goal is to provide CD-quality audio over telecommunications networks. Almost all CD audio coders are based on the so-called psychoacoustic model of the human auditory system.
5: Music Compression. Music Coding. Mark Handley
 5: Music Compression Mark Handley Music Coding LPC-based codecs model the sound source to achieve good compression. Works well for voice. Terrible for music. What if you can t model the source? Model the
5: Music Compression Mark Handley Music Coding LPC-based codecs model the sound source to achieve good compression. Works well for voice. Terrible for music. What if you can t model the source? Model the
CHAPTER 5 AUDIO WATERMARKING SCHEME INHERENTLY ROBUST TO MP3 COMPRESSION
 CHAPTER 5 AUDIO WATERMARKING SCHEME INHERENTLY ROBUST TO MP3 COMPRESSION In chapter 4, SVD based watermarking schemes are proposed which met the requirement of imperceptibility, having high payload and
CHAPTER 5 AUDIO WATERMARKING SCHEME INHERENTLY ROBUST TO MP3 COMPRESSION In chapter 4, SVD based watermarking schemes are proposed which met the requirement of imperceptibility, having high payload and
Audio-coding standards
 Audio-coding standards The goal is to provide CD-quality audio over telecommunications networks. Almost all CD audio coders are based on the so-called psychoacoustic model of the human auditory system.
Audio-coding standards The goal is to provide CD-quality audio over telecommunications networks. Almost all CD audio coders are based on the so-called psychoacoustic model of the human auditory system.
Multimedia Communications. Audio coding
 Multimedia Communications Audio coding Introduction Lossy compression schemes can be based on source model (e.g., speech compression) or user model (audio coding) Unlike speech, audio signals can be generated
Multimedia Communications Audio coding Introduction Lossy compression schemes can be based on source model (e.g., speech compression) or user model (audio coding) Unlike speech, audio signals can be generated
Perceptual Coding. Lossless vs. lossy compression Perceptual models Selecting info to eliminate Quantization and entropy encoding
 Perceptual Coding Lossless vs. lossy compression Perceptual models Selecting info to eliminate Quantization and entropy encoding Part II wrap up 6.082 Fall 2006 Perceptual Coding, Slide 1 Lossless vs.
Perceptual Coding Lossless vs. lossy compression Perceptual models Selecting info to eliminate Quantization and entropy encoding Part II wrap up 6.082 Fall 2006 Perceptual Coding, Slide 1 Lossless vs.
Compressed Audio Demystified by Hendrik Gideonse and Connor Smith. All Rights Reserved.
 Compressed Audio Demystified Why Music Producers Need to Care About Compressed Audio Files Download Sales Up CD Sales Down High-Definition hasn t caught on yet Consumers don t seem to care about high fidelity
Compressed Audio Demystified Why Music Producers Need to Care About Compressed Audio Files Download Sales Up CD Sales Down High-Definition hasn t caught on yet Consumers don t seem to care about high fidelity
ELL 788 Computational Perception & Cognition July November 2015
 ELL 788 Computational Perception & Cognition July November 2015 Module 11 Audio Engineering: Perceptual coding Coding and decoding Signal (analog) Encoder Code (Digital) Code (Digital) Decoder Signal (analog)
ELL 788 Computational Perception & Cognition July November 2015 Module 11 Audio Engineering: Perceptual coding Coding and decoding Signal (analog) Encoder Code (Digital) Code (Digital) Decoder Signal (analog)
Principles of Audio Coding
 Principles of Audio Coding Topics today Introduction VOCODERS Psychoacoustics Equal-Loudness Curve Frequency Masking Temporal Masking (CSIT 410) 2 Introduction Speech compression algorithm focuses on exploiting
Principles of Audio Coding Topics today Introduction VOCODERS Psychoacoustics Equal-Loudness Curve Frequency Masking Temporal Masking (CSIT 410) 2 Introduction Speech compression algorithm focuses on exploiting
A Detailed look of Audio Steganography Techniques using LSB and Genetic Algorithm Approach
 www.ijcsi.org 402 A Detailed look of Audio Steganography Techniques using LSB and Genetic Algorithm Approach Gunjan Nehru 1, Puja Dhar 2 1 Department of Information Technology, IEC-Group of Institutions
www.ijcsi.org 402 A Detailed look of Audio Steganography Techniques using LSB and Genetic Algorithm Approach Gunjan Nehru 1, Puja Dhar 2 1 Department of Information Technology, IEC-Group of Institutions
The Steganography In Inactive Frames Of Voip
 The Steganography In Inactive Frames Of Voip This paper describes a novel high-capacity steganography algorithm for embedding data in the inactive frames of low bit rate audio streams encoded by G.723.1
The Steganography In Inactive Frames Of Voip This paper describes a novel high-capacity steganography algorithm for embedding data in the inactive frames of low bit rate audio streams encoded by G.723.1
Appendix 4. Audio coding algorithms
 Appendix 4. Audio coding algorithms 1 Introduction The main application of audio compression systems is to obtain compact digital representations of high-quality (CD-quality) wideband audio signals. Typically
Appendix 4. Audio coding algorithms 1 Introduction The main application of audio compression systems is to obtain compact digital representations of high-quality (CD-quality) wideband audio signals. Typically
FUSION MODEL BASED ON CONVOLUTIONAL NEURAL NETWORKS WITH TWO FEATURES FOR ACOUSTIC SCENE CLASSIFICATION
 Please contact the conference organizers at dcasechallenge@gmail.com if you require an accessible file, as the files provided by ConfTool Pro to reviewers are filtered to remove author information, and
Please contact the conference organizers at dcasechallenge@gmail.com if you require an accessible file, as the files provided by ConfTool Pro to reviewers are filtered to remove author information, and
Robust Steganography Using Texture Synthesis
 Robust Steganography Using Texture Synthesis Zhenxing Qian 1, Hang Zhou 2, Weiming Zhang 2, Xinpeng Zhang 1 1. School of Communication and Information Engineering, Shanghai University, Shanghai, 200444,
Robust Steganography Using Texture Synthesis Zhenxing Qian 1, Hang Zhou 2, Weiming Zhang 2, Xinpeng Zhang 1 1. School of Communication and Information Engineering, Shanghai University, Shanghai, 200444,
Research Article A Novel Steganalytic Algorithm based on III Level DWT with Energy as Feature
 Research Journal of Applied Sciences, Engineering and Technology 7(19): 4100-4105, 2014 DOI:10.19026/rjaset.7.773 ISSN: 2040-7459; e-issn: 2040-7467 2014 Maxwell Scientific Publication Corp. Submitted:
Research Journal of Applied Sciences, Engineering and Technology 7(19): 4100-4105, 2014 DOI:10.19026/rjaset.7.773 ISSN: 2040-7459; e-issn: 2040-7467 2014 Maxwell Scientific Publication Corp. Submitted:
MPEG-4 General Audio Coding
 MPEG-4 General Audio Coding Jürgen Herre Fraunhofer Institute for Integrated Circuits (IIS) Dr. Jürgen Herre, hrr@iis.fhg.de 1 General Audio Coding Solid state players, Internet audio, terrestrial and
MPEG-4 General Audio Coding Jürgen Herre Fraunhofer Institute for Integrated Circuits (IIS) Dr. Jürgen Herre, hrr@iis.fhg.de 1 General Audio Coding Solid state players, Internet audio, terrestrial and
Lecture 16 Perceptual Audio Coding
 EECS 225D Audio Signal Processing in Humans and Machines Lecture 16 Perceptual Audio Coding 2012-3-14 Professor Nelson Morgan today s lecture by John Lazzaro www.icsi.berkeley.edu/eecs225d/spr12/ Hero
EECS 225D Audio Signal Processing in Humans and Machines Lecture 16 Perceptual Audio Coding 2012-3-14 Professor Nelson Morgan today s lecture by John Lazzaro www.icsi.berkeley.edu/eecs225d/spr12/ Hero
Novel Lossy Compression Algorithms with Stacked Autoencoders
 Novel Lossy Compression Algorithms with Stacked Autoencoders Anand Atreya and Daniel O Shea {aatreya, djoshea}@stanford.edu 11 December 2009 1. Introduction 1.1. Lossy compression Lossy compression is
Novel Lossy Compression Algorithms with Stacked Autoencoders Anand Atreya and Daniel O Shea {aatreya, djoshea}@stanford.edu 11 December 2009 1. Introduction 1.1. Lossy compression Lossy compression is
A Study on Different JPEG Steganograhic Schemes
 A Study on Different JPEG Steganograhic Schemes Alphy Ros Mathew, Sreekumar K Department of Computer Science, College of Engineering,Ponjar, Cochin University of Science And Technology Kottayam,Kerala,India
A Study on Different JPEG Steganograhic Schemes Alphy Ros Mathew, Sreekumar K Department of Computer Science, College of Engineering,Ponjar, Cochin University of Science And Technology Kottayam,Kerala,India
New Results in Low Bit Rate Speech Coding and Bandwidth Extension
 Audio Engineering Society Convention Paper Presented at the 121st Convention 2006 October 5 8 San Francisco, CA, USA This convention paper has been reproduced from the author's advance manuscript, without
Audio Engineering Society Convention Paper Presented at the 121st Convention 2006 October 5 8 San Francisco, CA, USA This convention paper has been reproduced from the author's advance manuscript, without
AUDIOVISUAL COMMUNICATION
 AUDIOVISUAL COMMUNICATION Laboratory Session: Audio Processing and Coding The objective of this lab session is to get the students familiar with audio processing and coding, notably psychoacoustic analysis
AUDIOVISUAL COMMUNICATION Laboratory Session: Audio Processing and Coding The objective of this lab session is to get the students familiar with audio processing and coding, notably psychoacoustic analysis
Chapter 14 MPEG Audio Compression
 Chapter 14 MPEG Audio Compression 14.1 Psychoacoustics 14.2 MPEG Audio 14.3 Other Commercial Audio Codecs 14.4 The Future: MPEG-7 and MPEG-21 14.5 Further Exploration 1 Li & Drew c Prentice Hall 2003 14.1
Chapter 14 MPEG Audio Compression 14.1 Psychoacoustics 14.2 MPEG Audio 14.3 Other Commercial Audio Codecs 14.4 The Future: MPEG-7 and MPEG-21 14.5 Further Exploration 1 Li & Drew c Prentice Hall 2003 14.1
Scalable Coding of Image Collections with Embedded Descriptors
 Scalable Coding of Image Collections with Embedded Descriptors N. Adami, A. Boschetti, R. Leonardi, P. Migliorati Department of Electronic for Automation, University of Brescia Via Branze, 38, Brescia,
Scalable Coding of Image Collections with Embedded Descriptors N. Adami, A. Boschetti, R. Leonardi, P. Migliorati Department of Electronic for Automation, University of Brescia Via Branze, 38, Brescia,
Increasing Robustness of LSB Audio Steganography Using a Novel Embedding Method
 ShriRam College of Engineering & Management 1 Increasing Robustness of LSB Audio Steganography Using a Novel Embedding Method Rinki Baghel Pragya Sharma Abstract In this paper, we present a novel high
ShriRam College of Engineering & Management 1 Increasing Robustness of LSB Audio Steganography Using a Novel Embedding Method Rinki Baghel Pragya Sharma Abstract In this paper, we present a novel high
A NEW DCT-BASED WATERMARKING METHOD FOR COPYRIGHT PROTECTION OF DIGITAL AUDIO
 International journal of computer science & information Technology (IJCSIT) Vol., No.5, October A NEW DCT-BASED WATERMARKING METHOD FOR COPYRIGHT PROTECTION OF DIGITAL AUDIO Pranab Kumar Dhar *, Mohammad
International journal of computer science & information Technology (IJCSIT) Vol., No.5, October A NEW DCT-BASED WATERMARKING METHOD FOR COPYRIGHT PROTECTION OF DIGITAL AUDIO Pranab Kumar Dhar *, Mohammad
Module 9 AUDIO CODING. Version 2 ECE IIT, Kharagpur
 Module 9 AUDIO CODING Lesson 29 Transform and Filter banks Instructional Objectives At the end of this lesson, the students should be able to: 1. Define the three layers of MPEG-1 audio coding. 2. Define
Module 9 AUDIO CODING Lesson 29 Transform and Filter banks Instructional Objectives At the end of this lesson, the students should be able to: 1. Define the three layers of MPEG-1 audio coding. 2. Define
Data Hiding in Video
 Data Hiding in Video J. J. Chae and B. S. Manjunath Department of Electrical and Computer Engineering University of California, Santa Barbara, CA 9316-956 Email: chaejj, manj@iplab.ece.ucsb.edu Abstract
Data Hiding in Video J. J. Chae and B. S. Manjunath Department of Electrical and Computer Engineering University of California, Santa Barbara, CA 9316-956 Email: chaejj, manj@iplab.ece.ucsb.edu Abstract
DRA AUDIO CODING STANDARD
 Applied Mechanics and Materials Online: 2013-06-27 ISSN: 1662-7482, Vol. 330, pp 981-984 doi:10.4028/www.scientific.net/amm.330.981 2013 Trans Tech Publications, Switzerland DRA AUDIO CODING STANDARD Wenhua
Applied Mechanics and Materials Online: 2013-06-27 ISSN: 1662-7482, Vol. 330, pp 981-984 doi:10.4028/www.scientific.net/amm.330.981 2013 Trans Tech Publications, Switzerland DRA AUDIO CODING STANDARD Wenhua
SPREAD SPECTRUM AUDIO WATERMARKING SCHEME BASED ON PSYCHOACOUSTIC MODEL
 SPREAD SPECTRUM WATERMARKING SCHEME BASED ON PSYCHOACOUSTIC MODEL 1 Yüksel Tokur 2 Ergun Erçelebi e-mail: tokur@gantep.edu.tr e-mail: ercelebi@gantep.edu.tr 1 Gaziantep University, MYO, 27310, Gaziantep,
SPREAD SPECTRUM WATERMARKING SCHEME BASED ON PSYCHOACOUSTIC MODEL 1 Yüksel Tokur 2 Ergun Erçelebi e-mail: tokur@gantep.edu.tr e-mail: ercelebi@gantep.edu.tr 1 Gaziantep University, MYO, 27310, Gaziantep,
The Analysis and Detection of Double JPEG2000 Compression Based on Statistical Characterization of DWT Coefficients
 Available online at www.sciencedirect.com Energy Procedia 17 (2012 ) 623 629 2012 International Conference on Future Electrical Power and Energy Systems The Analysis and Detection of Double JPEG2000 Compression
Available online at www.sciencedirect.com Energy Procedia 17 (2012 ) 623 629 2012 International Conference on Future Electrical Power and Energy Systems The Analysis and Detection of Double JPEG2000 Compression
Perceptual coding. A psychoacoustic model is used to identify those signals that are influenced by both these effects.
 Perceptual coding Both LPC and CELP are used primarily for telephony applications and hence the compression of a speech signal. Perceptual encoders, however, have been designed for the compression of general
Perceptual coding Both LPC and CELP are used primarily for telephony applications and hence the compression of a speech signal. Perceptual encoders, however, have been designed for the compression of general
METRIC LEARNING BASED DATA AUGMENTATION FOR ENVIRONMENTAL SOUND CLASSIFICATION
 METRIC LEARNING BASED DATA AUGMENTATION FOR ENVIRONMENTAL SOUND CLASSIFICATION Rui Lu 1, Zhiyao Duan 2, Changshui Zhang 1 1 Department of Automation, Tsinghua University 2 Department of Electrical and
METRIC LEARNING BASED DATA AUGMENTATION FOR ENVIRONMENTAL SOUND CLASSIFICATION Rui Lu 1, Zhiyao Duan 2, Changshui Zhang 1 1 Department of Automation, Tsinghua University 2 Department of Electrical and
Mpeg 1 layer 3 (mp3) general overview
 Mpeg 1 layer 3 (mp3) general overview 1 Digital Audio! CD Audio:! 16 bit encoding! 2 Channels (Stereo)! 44.1 khz sampling rate 2 * 44.1 khz * 16 bits = 1.41 Mb/s + Overhead (synchronization, error correction,
Mpeg 1 layer 3 (mp3) general overview 1 Digital Audio! CD Audio:! 16 bit encoding! 2 Channels (Stereo)! 44.1 khz sampling rate 2 * 44.1 khz * 16 bits = 1.41 Mb/s + Overhead (synchronization, error correction,
2.4 Audio Compression
 2.4 Audio Compression 2.4.1 Pulse Code Modulation Audio signals are analog waves. The acoustic perception is determined by the frequency (pitch) and the amplitude (loudness). For storage, processing and
2.4 Audio Compression 2.4.1 Pulse Code Modulation Audio signals are analog waves. The acoustic perception is determined by the frequency (pitch) and the amplitude (loudness). For storage, processing and
An Improved DCT Based Color Image Watermarking Scheme Xiangguang Xiong1, a
 International Symposium on Mechanical Engineering and Material Science (ISMEMS 2016) An Improved DCT Based Color Image Watermarking Scheme Xiangguang Xiong1, a 1 School of Big Data and Computer Science,
International Symposium on Mechanical Engineering and Material Science (ISMEMS 2016) An Improved DCT Based Color Image Watermarking Scheme Xiangguang Xiong1, a 1 School of Big Data and Computer Science,
Concealing Information in Images using Progressive Recovery
 Concealing Information in Images using Progressive Recovery Pooja R 1, Neha S Prasad 2, Nithya S Jois 3, Sahithya KS 4, Bhagyashri R H 5 1,2,3,4 UG Student, Department Of Computer Science and Engineering,
Concealing Information in Images using Progressive Recovery Pooja R 1, Neha S Prasad 2, Nithya S Jois 3, Sahithya KS 4, Bhagyashri R H 5 1,2,3,4 UG Student, Department Of Computer Science and Engineering,
Parametric Coding of High-Quality Audio
 Parametric Coding of High-Quality Audio Prof. Dr. Gerald Schuller Fraunhofer IDMT & Ilmenau Technical University Ilmenau, Germany 1 Waveform vs Parametric Waveform Filter-bank approach Mainly exploits
Parametric Coding of High-Quality Audio Prof. Dr. Gerald Schuller Fraunhofer IDMT & Ilmenau Technical University Ilmenau, Germany 1 Waveform vs Parametric Waveform Filter-bank approach Mainly exploits
Both LPC and CELP are used primarily for telephony applications and hence the compression of a speech signal.
 Perceptual coding Both LPC and CELP are used primarily for telephony applications and hence the compression of a speech signal. Perceptual encoders, however, have been designed for the compression of general
Perceptual coding Both LPC and CELP are used primarily for telephony applications and hence the compression of a speech signal. Perceptual encoders, however, have been designed for the compression of general
Data Hiding on Text Using Big-5 Code
 Data Hiding on Text Using Big-5 Code Jun-Chou Chuang 1 and Yu-Chen Hu 2 1 Department of Computer Science and Communication Engineering Providence University 200 Chung-Chi Rd., Shalu, Taichung 43301, Republic
Data Hiding on Text Using Big-5 Code Jun-Chou Chuang 1 and Yu-Chen Hu 2 1 Department of Computer Science and Communication Engineering Providence University 200 Chung-Chi Rd., Shalu, Taichung 43301, Republic
Channel Locality Block: A Variant of Squeeze-and-Excitation
 Channel Locality Block: A Variant of Squeeze-and-Excitation 1 st Huayu Li Northern Arizona University Flagstaff, United State Northern Arizona University hl459@nau.edu arxiv:1901.01493v1 [cs.lg] 6 Jan
Channel Locality Block: A Variant of Squeeze-and-Excitation 1 st Huayu Li Northern Arizona University Flagstaff, United State Northern Arizona University hl459@nau.edu arxiv:1901.01493v1 [cs.lg] 6 Jan
AUDIOVISUAL COMMUNICATION
 AUDIOVISUAL COMMUNICATION Laboratory Session: Audio Processing and Coding The objective of this lab session is to get the students familiar with audio processing and coding, notably psychoacoustic analysis
AUDIOVISUAL COMMUNICATION Laboratory Session: Audio Processing and Coding The objective of this lab session is to get the students familiar with audio processing and coding, notably psychoacoustic analysis
EE482: Digital Signal Processing Applications
 Professor Brendan Morris, SEB 3216, brendan.morris@unlv.edu EE482: Digital Signal Processing Applications Spring 2014 TTh 14:30-15:45 CBC C222 Lecture 13 Audio Signal Processing 14/04/01 http://www.ee.unlv.edu/~b1morris/ee482/
Professor Brendan Morris, SEB 3216, brendan.morris@unlv.edu EE482: Digital Signal Processing Applications Spring 2014 TTh 14:30-15:45 CBC C222 Lecture 13 Audio Signal Processing 14/04/01 http://www.ee.unlv.edu/~b1morris/ee482/
Proceedings of Meetings on Acoustics
 Proceedings of Meetings on Acoustics Volume 19, 213 http://acousticalsociety.org/ ICA 213 Montreal Montreal, Canada 2-7 June 213 Engineering Acoustics Session 2pEAb: Controlling Sound Quality 2pEAb1. Subjective
Proceedings of Meetings on Acoustics Volume 19, 213 http://acousticalsociety.org/ ICA 213 Montreal Montreal, Canada 2-7 June 213 Engineering Acoustics Session 2pEAb: Controlling Sound Quality 2pEAb1. Subjective
Random Image Embedded in Videos using LSB Insertion Algorithm
 Random Image Embedded in Videos using LSB Insertion Algorithm K.Parvathi Divya 1, K.Mahesh 2 Research Scholar 1, * Associate Professor 2 Department of Computer Science and Engg, Alagappa university, Karaikudi.
Random Image Embedded in Videos using LSB Insertion Algorithm K.Parvathi Divya 1, K.Mahesh 2 Research Scholar 1, * Associate Professor 2 Department of Computer Science and Engg, Alagappa university, Karaikudi.
Adaptive Pixel Pair Matching Technique for Data Embedding
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Audio Compression. Audio Compression. Absolute Threshold. CD quality audio:
 Audio Compression Audio Compression CD quality audio: Sampling rate = 44 KHz, Quantization = 16 bits/sample Bit-rate = ~700 Kb/s (1.41 Mb/s if 2 channel stereo) Telephone-quality speech Sampling rate =
Audio Compression Audio Compression CD quality audio: Sampling rate = 44 KHz, Quantization = 16 bits/sample Bit-rate = ~700 Kb/s (1.41 Mb/s if 2 channel stereo) Telephone-quality speech Sampling rate =
A New Approach to Compressed Image Steganography Using Wavelet Transform
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 17, Issue 5, Ver. III (Sep. Oct. 2015), PP 53-59 www.iosrjournals.org A New Approach to Compressed Image Steganography
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 17, Issue 5, Ver. III (Sep. Oct. 2015), PP 53-59 www.iosrjournals.org A New Approach to Compressed Image Steganography
QUANTIZER DESIGN FOR EXPLOITING COMMON INFORMATION IN LAYERED CODING. Mehdi Salehifar, Tejaswi Nanjundaswamy, and Kenneth Rose
 QUANTIZER DESIGN FOR EXPLOITING COMMON INFORMATION IN LAYERED CODING Mehdi Salehifar, Tejaswi Nanjundaswamy, and Kenneth Rose Department of Electrical and Computer Engineering University of California,
QUANTIZER DESIGN FOR EXPLOITING COMMON INFORMATION IN LAYERED CODING Mehdi Salehifar, Tejaswi Nanjundaswamy, and Kenneth Rose Department of Electrical and Computer Engineering University of California,
CHAPTER 4 REVERSIBLE IMAGE WATERMARKING USING BIT PLANE CODING AND LIFTING WAVELET TRANSFORM
 74 CHAPTER 4 REVERSIBLE IMAGE WATERMARKING USING BIT PLANE CODING AND LIFTING WAVELET TRANSFORM Many data embedding methods use procedures that in which the original image is distorted by quite a small
74 CHAPTER 4 REVERSIBLE IMAGE WATERMARKING USING BIT PLANE CODING AND LIFTING WAVELET TRANSFORM Many data embedding methods use procedures that in which the original image is distorted by quite a small
MPEG-4 aacplus - Audio coding for today s digital media world
 MPEG-4 aacplus - Audio coding for today s digital media world Whitepaper by: Gerald Moser, Coding Technologies November 2005-1 - 1. Introduction Delivering high quality digital broadcast content to consumers
MPEG-4 aacplus - Audio coding for today s digital media world Whitepaper by: Gerald Moser, Coding Technologies November 2005-1 - 1. Introduction Delivering high quality digital broadcast content to consumers
Inception and Residual Networks. Hantao Zhang. Deep Learning with Python.
 Inception and Residual Networks Hantao Zhang Deep Learning with Python https://en.wikipedia.org/wiki/residual_neural_network Deep Neural Network Progress from Large Scale Visual Recognition Challenge (ILSVRC)
Inception and Residual Networks Hantao Zhang Deep Learning with Python https://en.wikipedia.org/wiki/residual_neural_network Deep Neural Network Progress from Large Scale Visual Recognition Challenge (ILSVRC)
A Blind Steganalysis on JPEG Gray Level Image Based on Statistical Features and its Performance Analysis
 International Journal of Engineering Research and Development e-issn: 2278-067X, p-issn: 2278-800X, www.ijerd.com Volume 11, Issue 09 (September 2015), PP.27-31 A Blind Steganalysis on JPEG Gray Level
International Journal of Engineering Research and Development e-issn: 2278-067X, p-issn: 2278-800X, www.ijerd.com Volume 11, Issue 09 (September 2015), PP.27-31 A Blind Steganalysis on JPEG Gray Level
Image and Video Watermarking
 Telecommunications Seminar WS 1998 Data Hiding, Digital Watermarking and Secure Communications Image and Video Watermarking Herbert Buchner University of Erlangen-Nuremberg 16.12.1998 Outline 1. Introduction:
Telecommunications Seminar WS 1998 Data Hiding, Digital Watermarking and Secure Communications Image and Video Watermarking Herbert Buchner University of Erlangen-Nuremberg 16.12.1998 Outline 1. Introduction:
Implementation of Random Byte Hiding algorithm in Video Steganography
 Implementation of Random Byte Hiding algorithm in Video Steganography S.Aswath 1, K.Akshara 2, P.Pavithra 2, D.S.Abinaya 2 Asssisant Professor 1, Student 2 (IV Year) Department of Electronics and Communication
Implementation of Random Byte Hiding algorithm in Video Steganography S.Aswath 1, K.Akshara 2, P.Pavithra 2, D.S.Abinaya 2 Asssisant Professor 1, Student 2 (IV Year) Department of Electronics and Communication
VoIP Forgery Detection
 VoIP Forgery Detection Satish Tummala, Yanxin Liu and Qingzhong Liu Department of Computer Science Sam Houston State University Huntsville, TX, USA Emails: sct137@shsu.edu; yanxin@shsu.edu; liu@shsu.edu
VoIP Forgery Detection Satish Tummala, Yanxin Liu and Qingzhong Liu Department of Computer Science Sam Houston State University Huntsville, TX, USA Emails: sct137@shsu.edu; yanxin@shsu.edu; liu@shsu.edu
An Information Hiding Algorithm for HEVC Based on Angle Differences of Intra Prediction Mode
 An Information Hiding Algorithm for HEVC Based on Angle Differences of Intra Prediction Mode Jia-Ji Wang1, Rang-Ding Wang1*, Da-Wen Xu1, Wei Li1 CKC Software Lab, Ningbo University, Ningbo, Zhejiang 3152,
An Information Hiding Algorithm for HEVC Based on Angle Differences of Intra Prediction Mode Jia-Ji Wang1, Rang-Ding Wang1*, Da-Wen Xu1, Wei Li1 CKC Software Lab, Ningbo University, Ningbo, Zhejiang 3152,
Hello Edge: Keyword Spotting on Microcontrollers
 Hello Edge: Keyword Spotting on Microcontrollers Yundong Zhang, Naveen Suda, Liangzhen Lai and Vikas Chandra ARM Research, Stanford University arxiv.org, 2017 Presented by Mohammad Mofrad University of
Hello Edge: Keyword Spotting on Microcontrollers Yundong Zhang, Naveen Suda, Liangzhen Lai and Vikas Chandra ARM Research, Stanford University arxiv.org, 2017 Presented by Mohammad Mofrad University of
Adaptive Spatial Steganography Based on the Correlation of Wavelet Coefficients for Digital Images in Spatial Domain Ningbo Li, Pan Feng, Liu Jia
 216 International Conference on Information Engineering and Communications Technology (IECT 216) ISBN: 978-1-69-37- Adaptive Spatial Steganography Based on the Correlation of Wavelet Coefficients for Digital
216 International Conference on Information Engineering and Communications Technology (IECT 216) ISBN: 978-1-69-37- Adaptive Spatial Steganography Based on the Correlation of Wavelet Coefficients for Digital
The MPEG-4 General Audio Coder
 The MPEG-4 General Audio Coder Bernhard Grill Fraunhofer Institute for Integrated Circuits (IIS) grl 6/98 page 1 Outline MPEG-2 Advanced Audio Coding (AAC) MPEG-4 Extensions: Perceptual Noise Substitution
The MPEG-4 General Audio Coder Bernhard Grill Fraunhofer Institute for Integrated Circuits (IIS) grl 6/98 page 1 Outline MPEG-2 Advanced Audio Coding (AAC) MPEG-4 Extensions: Perceptual Noise Substitution
DAB. Digital Audio Broadcasting
 DAB Digital Audio Broadcasting DAB history DAB has been under development since 1981 at the Institut für Rundfunktechnik (IRT). In 1985 the first DAB demonstrations were held at the WARC-ORB in Geneva
DAB Digital Audio Broadcasting DAB history DAB has been under development since 1981 at the Institut für Rundfunktechnik (IRT). In 1985 the first DAB demonstrations were held at the WARC-ORB in Geneva
VARIABLE RATE STEGANOGRAPHY IN DIGITAL IMAGES USING TWO, THREE AND FOUR NEIGHBOR PIXELS
 VARIABLE RATE STEGANOGRAPHY IN DIGITAL IMAGES USING TWO, THREE AND FOUR NEIGHBOR PIXELS Anita Pradhan Department of CSE, Sri Sivani College of Engineering, Srikakulam, Andhra Pradesh, India anita.pradhan15@gmail.com
VARIABLE RATE STEGANOGRAPHY IN DIGITAL IMAGES USING TWO, THREE AND FOUR NEIGHBOR PIXELS Anita Pradhan Department of CSE, Sri Sivani College of Engineering, Srikakulam, Andhra Pradesh, India anita.pradhan15@gmail.com
19 th INTERNATIONAL CONGRESS ON ACOUSTICS MADRID, 2-7 SEPTEMBER 2007
 19 th INTERNATIONAL CONGRESS ON ACOUSTICS MADRID, 2-7 SEPTEMBER 2007 SUBJECTIVE AND OBJECTIVE QUALITY EVALUATION FOR AUDIO WATERMARKING BASED ON SINUSOIDAL AMPLITUDE MODULATION PACS: 43.10.Pr, 43.60.Ek
19 th INTERNATIONAL CONGRESS ON ACOUSTICS MADRID, 2-7 SEPTEMBER 2007 SUBJECTIVE AND OBJECTIVE QUALITY EVALUATION FOR AUDIO WATERMARKING BASED ON SINUSOIDAL AMPLITUDE MODULATION PACS: 43.10.Pr, 43.60.Ek
Alpha-trimmed Image Estimation for JPEG Steganography Detection
 Proceedings of the 2009 IEEE International Conference on Systems, Man, and Cybernetics San Antonio, TX, USA - October 2009 Alpha-trimmed Image Estimation for JPEG Steganography Detection Mei-Ching Chen,
Proceedings of the 2009 IEEE International Conference on Systems, Man, and Cybernetics San Antonio, TX, USA - October 2009 Alpha-trimmed Image Estimation for JPEG Steganography Detection Mei-Ching Chen,
Scalable Perceptual and Lossless Audio Coding based on MPEG-4 AAC
 Scalable Perceptual and Lossless Audio Coding based on MPEG-4 AAC Ralf Geiger 1, Gerald Schuller 1, Jürgen Herre 2, Ralph Sperschneider 2, Thomas Sporer 1 1 Fraunhofer IIS AEMT, Ilmenau, Germany 2 Fraunhofer
Scalable Perceptual and Lossless Audio Coding based on MPEG-4 AAC Ralf Geiger 1, Gerald Schuller 1, Jürgen Herre 2, Ralph Sperschneider 2, Thomas Sporer 1 1 Fraunhofer IIS AEMT, Ilmenau, Germany 2 Fraunhofer
A Flexible Scheme of Self Recovery for Digital Image Protection
 www.ijcsi.org 460 A Flexible Scheme of Self Recoery for Digital Image Protection Zhenxing Qian, Lili Zhao 2 School of Communication and Information Engineering, Shanghai Uniersity, Shanghai 200072, China
www.ijcsi.org 460 A Flexible Scheme of Self Recoery for Digital Image Protection Zhenxing Qian, Lili Zhao 2 School of Communication and Information Engineering, Shanghai Uniersity, Shanghai 200072, China
Digital Image Steganography Techniques: Case Study. Karnataka, India.
 ISSN: 2320 8791 (Impact Factor: 1.479) Digital Image Steganography Techniques: Case Study Santosh Kumar.S 1, Archana.M 2 1 Department of Electronicsand Communication Engineering, Sri Venkateshwara College
ISSN: 2320 8791 (Impact Factor: 1.479) Digital Image Steganography Techniques: Case Study Santosh Kumar.S 1, Archana.M 2 1 Department of Electronicsand Communication Engineering, Sri Venkateshwara College
Quantitative and Binary Steganalysis in JPEG: A Comparative Study
 Quantitative and Binary Steganalysis in JPEG: A Comparative Study Ahmad ZAKARIA LIRMM, Univ Montpellier, CNRS ahmad.zakaria@lirmm.fr Marc CHAUMONT LIRMM, Univ Nîmes, CNRS marc.chaumont@lirmm.fr Gérard
Quantitative and Binary Steganalysis in JPEG: A Comparative Study Ahmad ZAKARIA LIRMM, Univ Montpellier, CNRS ahmad.zakaria@lirmm.fr Marc CHAUMONT LIRMM, Univ Nîmes, CNRS marc.chaumont@lirmm.fr Gérard
Information Cloaking Technique with Tree Based Similarity
 Information Cloaking Technique with Tree Based Similarity C.Bharathipriya [1], K.Lakshminarayanan [2] 1 Final Year, Computer Science and Engineering, Mailam Engineering College, 2 Assistant Professor,
Information Cloaking Technique with Tree Based Similarity C.Bharathipriya [1], K.Lakshminarayanan [2] 1 Final Year, Computer Science and Engineering, Mailam Engineering College, 2 Assistant Professor,
ijdsp Interactive Illustrations of Speech/Audio Processing Concepts
 ijdsp Interactive Illustrations of Speech/Audio Processing Concepts NSF Phase 3 Workshop, UCy Presentation of an Independent Study By Girish Kalyanasundaram, MS by Thesis in EE Advisor: Dr. Andreas Spanias,
ijdsp Interactive Illustrations of Speech/Audio Processing Concepts NSF Phase 3 Workshop, UCy Presentation of an Independent Study By Girish Kalyanasundaram, MS by Thesis in EE Advisor: Dr. Andreas Spanias,
Figure 1. Generic Encoder. Window. Spectral Analysis. Psychoacoustic Model. Quantize. Pack Data into Frames. Additional Coding.
 Introduction to Digital Audio Compression B. Cavagnolo and J. Bier Berkeley Design Technology, Inc. 2107 Dwight Way, Second Floor Berkeley, CA 94704 (510) 665-1600 info@bdti.com http://www.bdti.com INTRODUCTION
Introduction to Digital Audio Compression B. Cavagnolo and J. Bier Berkeley Design Technology, Inc. 2107 Dwight Way, Second Floor Berkeley, CA 94704 (510) 665-1600 info@bdti.com http://www.bdti.com INTRODUCTION
A Steganography method for JPEG2000 Baseline System
 A Steganography method for JPEG2000 Baseline System P.Ramakrishna Rao M.Tech.,[CSE], Teaching Associate, Department of Computer Science, Dr.B.R.Ambedkar University, Etcherla Srikaulam, 532 410. Abstract
A Steganography method for JPEG2000 Baseline System P.Ramakrishna Rao M.Tech.,[CSE], Teaching Associate, Department of Computer Science, Dr.B.R.Ambedkar University, Etcherla Srikaulam, 532 410. Abstract
STEGANALYSIS OF STEGOSTORAGE SYSTEM
 t m Mathematical Publications DOI: 10.1515/tmmp-2015-0049 Tatra Mt. Math. Publ. 64 (2015), 205 215 STEGANALYSIS OF STEGOSTORAGE SYSTEM Michala Gulášová Matúš Jókay ABSTRACT. The aim of this contribution
t m Mathematical Publications DOI: 10.1515/tmmp-2015-0049 Tatra Mt. Math. Publ. 64 (2015), 205 215 STEGANALYSIS OF STEGOSTORAGE SYSTEM Michala Gulášová Matúš Jókay ABSTRACT. The aim of this contribution
Dynamic Routing Between Capsules
 Report Explainable Machine Learning Dynamic Routing Between Capsules Author: Michael Dorkenwald Supervisor: Dr. Ullrich Köthe 28. Juni 2018 Inhaltsverzeichnis 1 Introduction 2 2 Motivation 2 3 CapusleNet
Report Explainable Machine Learning Dynamic Routing Between Capsules Author: Michael Dorkenwald Supervisor: Dr. Ullrich Köthe 28. Juni 2018 Inhaltsverzeichnis 1 Introduction 2 2 Motivation 2 3 CapusleNet
Know your data - many types of networks
 Architectures Know your data - many types of networks Fixed length representation Variable length representation Online video sequences, or samples of different sizes Images Specific architectures for
Architectures Know your data - many types of networks Fixed length representation Variable length representation Online video sequences, or samples of different sizes Images Specific architectures for
Audio Compression for Acoustic Sensing
 Institut für Technische Informatik und Kommunikationsnetze Audio Compression for Acoustic Sensing Semester Thesis Martin Lendi lendim@student.ethz.ch Computer Engineering and Networks Laboratory Department
Institut für Technische Informatik und Kommunikationsnetze Audio Compression for Acoustic Sensing Semester Thesis Martin Lendi lendim@student.ethz.ch Computer Engineering and Networks Laboratory Department
Identifying Compression History of Wave Audio and Its Applications
 Identifying Compression History of Wave Audio and Its Applications DA LUO, WEIQI LUO, RUI YANG, Sun Yat-sen University JIWU HUANG, Shenzhen University Audio signal is sometimes stored and/or processed
Identifying Compression History of Wave Audio and Its Applications DA LUO, WEIQI LUO, RUI YANG, Sun Yat-sen University JIWU HUANG, Shenzhen University Audio signal is sometimes stored and/or processed
Deep Face Recognition. Nathan Sun
 Deep Face Recognition Nathan Sun Why Facial Recognition? Picture ID or video tracking Higher Security for Facial Recognition Software Immensely useful to police in tracking suspects Your face will be an
Deep Face Recognition Nathan Sun Why Facial Recognition? Picture ID or video tracking Higher Security for Facial Recognition Software Immensely useful to police in tracking suspects Your face will be an
International Journal of Emerging Technology and Advanced Engineering Website: (ISSN , Volume 2, Issue 4, April 2012)
 A Technical Analysis Towards Digital Video Compression Rutika Joshi 1, Rajesh Rai 2, Rajesh Nema 3 1 Student, Electronics and Communication Department, NIIST College, Bhopal, 2,3 Prof., Electronics and
A Technical Analysis Towards Digital Video Compression Rutika Joshi 1, Rajesh Rai 2, Rajesh Nema 3 1 Student, Electronics and Communication Department, NIIST College, Bhopal, 2,3 Prof., Electronics and
Deep Learning with Tensorflow AlexNet
 Machine Learning and Computer Vision Group Deep Learning with Tensorflow http://cvml.ist.ac.at/courses/dlwt_w17/ AlexNet Krizhevsky, Alex, Ilya Sutskever, and Geoffrey E. Hinton, "Imagenet classification
Machine Learning and Computer Vision Group Deep Learning with Tensorflow http://cvml.ist.ac.at/courses/dlwt_w17/ AlexNet Krizhevsky, Alex, Ilya Sutskever, and Geoffrey E. Hinton, "Imagenet classification
A Revisit to LSB Substitution Based Data Hiding for Embedding More Information
 A Revisit to LSB Substitution Based Data Hiding for Embedding More Information Yanjun Liu 1,, Chin-Chen Chang 1, and Tzu-Yi Chien 2 1 Department of Information Engineering and Computer Science, Feng Chia
A Revisit to LSB Substitution Based Data Hiding for Embedding More Information Yanjun Liu 1,, Chin-Chen Chang 1, and Tzu-Yi Chien 2 1 Department of Information Engineering and Computer Science, Feng Chia
CHAPTER 3. Digital Carriers of Steganography
 CHAPTER 3 Digital Carriers of Steganography 3.1 Introduction It has been observed that all digital file formats can be used as digital carrier for steganography, but the formats those are with a high degree
CHAPTER 3 Digital Carriers of Steganography 3.1 Introduction It has been observed that all digital file formats can be used as digital carrier for steganography, but the formats those are with a high degree
A NOVEL SCANNING SCHEME FOR DIRECTIONAL SPATIAL PREDICTION OF AVS INTRA CODING
 A NOVEL SCANNING SCHEME FOR DIRECTIONAL SPATIAL PREDICTION OF AVS INTRA CODING Md. Salah Uddin Yusuf 1, Mohiuddin Ahmad 2 Assistant Professor, Dept. of EEE, Khulna University of Engineering & Technology
A NOVEL SCANNING SCHEME FOR DIRECTIONAL SPATIAL PREDICTION OF AVS INTRA CODING Md. Salah Uddin Yusuf 1, Mohiuddin Ahmad 2 Assistant Professor, Dept. of EEE, Khulna University of Engineering & Technology
Secret Communication through Audio for Defense Application
 Secret Communication through Audio for Defense Application A.Nageshwar Rao Maduguri Sudhir R.Venkatesh Abstract: A steganographic method of embedding textual information in an audio file is presented in
Secret Communication through Audio for Defense Application A.Nageshwar Rao Maduguri Sudhir R.Venkatesh Abstract: A steganographic method of embedding textual information in an audio file is presented in
arxiv: v1 [cs.mm] 2 Mar 2017
![arxiv: v1 [cs.mm] 2 Mar 2017 arxiv: v1 [cs.mm] 2 Mar 2017](/thumbs/75/71797007.jpg) This is a preprint of the paper: arxiv:1703.00817v1 [cs.mm] 2 Mar 2017 Daniel Lerch-Hostalot, David Megías, LSB matching steganalysis based on patterns of pixel differences and random embedding, Computers
This is a preprint of the paper: arxiv:1703.00817v1 [cs.mm] 2 Mar 2017 Daniel Lerch-Hostalot, David Megías, LSB matching steganalysis based on patterns of pixel differences and random embedding, Computers
Introducing Audio Signal Processing & Audio Coding. Dr Michael Mason Senior Manager, CE Technology Dolby Australia Pty Ltd
 Introducing Audio Signal Processing & Audio Coding Dr Michael Mason Senior Manager, CE Technology Dolby Australia Pty Ltd Overview Audio Signal Processing Applications @ Dolby Audio Signal Processing Basics
Introducing Audio Signal Processing & Audio Coding Dr Michael Mason Senior Manager, CE Technology Dolby Australia Pty Ltd Overview Audio Signal Processing Applications @ Dolby Audio Signal Processing Basics
Text Hiding In Multimedia By Huffman Encoding Algorithm Using Steganography
 Text Hiding In Multimedia By Huffman Encoding Algorithm Using Steganography Madhavi V.Kale 1, Prof. Swati A.Patil 2 PG Student, Dept. Of CSE., G.H.Raisoni Institute Of Engineering And Management,Jalgaon
Text Hiding In Multimedia By Huffman Encoding Algorithm Using Steganography Madhavi V.Kale 1, Prof. Swati A.Patil 2 PG Student, Dept. Of CSE., G.H.Raisoni Institute Of Engineering And Management,Jalgaon
Video Compression An Introduction
 Video Compression An Introduction The increasing demand to incorporate video data into telecommunications services, the corporate environment, the entertainment industry, and even at home has made digital
Video Compression An Introduction The increasing demand to incorporate video data into telecommunications services, the corporate environment, the entertainment industry, and even at home has made digital
KINGS COLLEGE OF ENGINEERING DEPARTMENT OF INFORMATION TECHNOLOGY ACADEMIC YEAR / ODD SEMESTER QUESTION BANK
 KINGS COLLEGE OF ENGINEERING DEPARTMENT OF INFORMATION TECHNOLOGY ACADEMIC YEAR 2011-2012 / ODD SEMESTER QUESTION BANK SUB.CODE / NAME YEAR / SEM : IT1301 INFORMATION CODING TECHNIQUES : III / V UNIT -
KINGS COLLEGE OF ENGINEERING DEPARTMENT OF INFORMATION TECHNOLOGY ACADEMIC YEAR 2011-2012 / ODD SEMESTER QUESTION BANK SUB.CODE / NAME YEAR / SEM : IT1301 INFORMATION CODING TECHNIQUES : III / V UNIT -
Professor Laurence S. Dooley. School of Computing and Communications Milton Keynes, UK
 Professor Laurence S. Dooley School of Computing and Communications Milton Keynes, UK How many bits required? 2.4Mbytes 84Kbytes 9.8Kbytes 50Kbytes Data Information Data and information are NOT the same!
Professor Laurence S. Dooley School of Computing and Communications Milton Keynes, UK How many bits required? 2.4Mbytes 84Kbytes 9.8Kbytes 50Kbytes Data Information Data and information are NOT the same!
Adaptive Quantization for Video Compression in Frequency Domain
 Adaptive Quantization for Video Compression in Frequency Domain *Aree A. Mohammed and **Alan A. Abdulla * Computer Science Department ** Mathematic Department University of Sulaimani P.O.Box: 334 Sulaimani
Adaptive Quantization for Video Compression in Frequency Domain *Aree A. Mohammed and **Alan A. Abdulla * Computer Science Department ** Mathematic Department University of Sulaimani P.O.Box: 334 Sulaimani
Reversible Image Data Hiding with Local Adaptive Contrast Enhancement
 Reversible Image Data Hiding with Local Adaptive Contrast Enhancement Ruiqi Jiang, Weiming Zhang, Jiajia Xu, Nenghai Yu and Xiaocheng Hu Abstract Recently, a novel reversible data hiding scheme is proposed
Reversible Image Data Hiding with Local Adaptive Contrast Enhancement Ruiqi Jiang, Weiming Zhang, Jiajia Xu, Nenghai Yu and Xiaocheng Hu Abstract Recently, a novel reversible data hiding scheme is proposed
AN EFFICIENT VIDEO WATERMARKING USING COLOR HISTOGRAM ANALYSIS AND BITPLANE IMAGE ARRAYS
 AN EFFICIENT VIDEO WATERMARKING USING COLOR HISTOGRAM ANALYSIS AND BITPLANE IMAGE ARRAYS G Prakash 1,TVS Gowtham Prasad 2, T.Ravi Kumar Naidu 3 1MTech(DECS) student, Department of ECE, sree vidyanikethan
AN EFFICIENT VIDEO WATERMARKING USING COLOR HISTOGRAM ANALYSIS AND BITPLANE IMAGE ARRAYS G Prakash 1,TVS Gowtham Prasad 2, T.Ravi Kumar Naidu 3 1MTech(DECS) student, Department of ECE, sree vidyanikethan
COMP 551 Applied Machine Learning Lecture 16: Deep Learning
 COMP 551 Applied Machine Learning Lecture 16: Deep Learning Instructor: Ryan Lowe (ryan.lowe@cs.mcgill.ca) Slides mostly by: Class web page: www.cs.mcgill.ca/~hvanho2/comp551 Unless otherwise noted, all
COMP 551 Applied Machine Learning Lecture 16: Deep Learning Instructor: Ryan Lowe (ryan.lowe@cs.mcgill.ca) Slides mostly by: Class web page: www.cs.mcgill.ca/~hvanho2/comp551 Unless otherwise noted, all
Hybrid Stegnography using ImagesVaried PVD+ LSB Detection Program
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 4 Issue 5 May 2015, Page No. 12086-12090 Hybrid Stegnography using ImagesVaried PVD+ LSB Detection Program Shruti
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 4 Issue 5 May 2015, Page No. 12086-12090 Hybrid Stegnography using ImagesVaried PVD+ LSB Detection Program Shruti
H.264/AVC Video Watermarking Algorithm Against Recoding
 Sensors & Transducers 2014 by IFSA Publishing, S. L. http://www.sensorsportal.com H.264/AVC Video Watermarking Algorithm Against Recoding Rangding Wang, Qian Li, Lujian Hu, Dawen Xu College of Information
Sensors & Transducers 2014 by IFSA Publishing, S. L. http://www.sensorsportal.com H.264/AVC Video Watermarking Algorithm Against Recoding Rangding Wang, Qian Li, Lujian Hu, Dawen Xu College of Information
Partial Video Encryption Using Random Permutation Based on Modification on Dct Based Transformation
 International Refereed Journal of Engineering and Science (IRJES) ISSN (Online) 2319-183X, (Print) 2319-1821 Volume 2, Issue 6 (June 2013), PP. 54-58 Partial Video Encryption Using Random Permutation Based
International Refereed Journal of Engineering and Science (IRJES) ISSN (Online) 2319-183X, (Print) 2319-1821 Volume 2, Issue 6 (June 2013), PP. 54-58 Partial Video Encryption Using Random Permutation Based
Video Inter-frame Forgery Identification Based on Optical Flow Consistency
 Sensors & Transducers 24 by IFSA Publishing, S. L. http://www.sensorsportal.com Video Inter-frame Forgery Identification Based on Optical Flow Consistency Qi Wang, Zhaohong Li, Zhenzhen Zhang, Qinglong
Sensors & Transducers 24 by IFSA Publishing, S. L. http://www.sensorsportal.com Video Inter-frame Forgery Identification Based on Optical Flow Consistency Qi Wang, Zhaohong Li, Zhenzhen Zhang, Qinglong
The Improved Embedded Zerotree Wavelet Coding (EZW) Algorithm
 01 International Conference on Image, Vision and Computing (ICIVC 01) IPCSI vol. 50 (01) (01) IACSI Press, Singapore DOI: 10.7763/IPCSI.01.V50.56 he Improved Embedded Zerotree Wavelet Coding () Algorithm
01 International Conference on Image, Vision and Computing (ICIVC 01) IPCSI vol. 50 (01) (01) IACSI Press, Singapore DOI: 10.7763/IPCSI.01.V50.56 he Improved Embedded Zerotree Wavelet Coding () Algorithm
Deep Learning and Its Applications
 Convolutional Neural Network and Its Application in Image Recognition Oct 28, 2016 Outline 1 A Motivating Example 2 The Convolutional Neural Network (CNN) Model 3 Training the CNN Model 4 Issues and Recent
Convolutional Neural Network and Its Application in Image Recognition Oct 28, 2016 Outline 1 A Motivating Example 2 The Convolutional Neural Network (CNN) Model 3 Training the CNN Model 4 Issues and Recent
