Anomaly Detail. Anomaly Detail Overview. The following describes how to review an anomaly's detailed information.
|
|
|
- Sheila Little
- 5 years ago
- Views:
Transcription
1 The following describes how to review an anomaly's detailed information. Overview, page 1 Summary Information, page 2 Anomaly Whitelist Rules, page 3 Packet Buffer Capture, page 5 Anomaly Facts Pane, page 6 Conversations, page 8 Anomalous Features Graph, page 14 Anomaly Graph, page 15 Mitigation from an Anomaly, page 16 Overview The anomaly detail view contains in-depth information about an anomaly, and context to help you understand it. The information includes information about the anomaly, and visual graphs with details about the anomalous behavior. You can take several actions from the anomaly detail view, including: downloading packet data viewing the details for the previous or next anomaly in the inbox assigning relevance feedback for the anomaly configuring a mitigation based on this anomaly 1
2 Summary Information Summary Information The summary information displays much of the same information as the anomaly inbox. This allows you to review pertinent anomaly information at a glance. The summary information also displays the first time a user accessed the in-depth anomaly information. In the summary information pane, you can add a comment to the anomaly, assign relevance feedback, as well as navigate to the previous or next anomaly's details. Related Topics Assigning Relevance Feedback for an Anomaly Reviewing and Adding Comments Summary Information Fields Field Id Agent Date, time Severity Seen The reason the system considered this traffic anomalous, the anomalous traffic directionality, and the target host. The anomaly's ID number. The agent that reported the anomaly. The date and time the anomaly started. The system's rating for the possibility of negative impact upon your network. The date and time a user first viewed this anomaly's details. Viewing Other s You have the following options: To view the next anomaly's details, click the next icon ( ). To view the previous anomaly's details, click the previous icon ( ). 2
3 Anomaly Whitelist Rules Anomaly Whitelist Rules Anomaly whitelist rules act as an inbox filter, hiding anomalies that match the rule. You can whitelist based on anomalies involving hosts you know to be safe. This reduces the false positives that the system displays. When you configure a whitelist rule, the system populates the rule with multiple characteristics, including: the detected cluster, target host IP address, and application group the flow direction whether or not the conversation involves an external host detected anomalous features agents that detected the anomaly This narrowly-defined rule matches very specific traffic. You can remove characteristics to expand the scope of the rule. Note If you remove too many characteristics and create a broad whitelist rule, the system may suppress relevant anomalies in addition to irrelevant anomalies. For example, if you remove the specified cluster, the rule defaults to matching any cluster. If you then remove IP address and application group, the rule suppresses all anomalies. If you create a broad whitelist rule, you may also create overlap with other whitelist rules. Plan your whitelist rules carefully, to prevent rule overlap and only suppress anomalies you want to suppress. A whitelist rule does not suppress any matching anomalies reported prior to rule creation, nor does it suppress the anomaly you used to create the rule. It does suppress every matching anomaly detected in the future, and remains in effect until you remove the rule. You can view all configured whitelist rules from the whitelist rule table in the anomaly inbox. Whitelist Rule Fields Table 1: Whitelist Rule Fields Column Cluster IP address App. group Bidirectional conversation the cluster containing the target host the target host IP address the application group over which the target host and other host transferred traffic whether the anomalous conversation is unidirectional or bidirectional 3
4 Whitelist Rule Validation Column With external host Features Agents whether the anomalous conversation involves a host external to the branch the detected anomalous features the agents that detected the anomaly Whitelist Rule Validation When you create a whitelist rule, the system validates it using the following criteria: You must define at least one Cluster, IP address, or App. group. You do not have to define With external host, Bidirectional conversation, Features, or Agents. When the system evaluates the whitelist rule, it matches traffic that matches all defined criteria. However, if you define multiple Features, multiple Agents, or multiple Features and Agents, the rule only has to match one of the defined features or one agent associated with an anomaly to filter the anomaly from the inbox. Whitelists, Relevance Feedback, and Mitigations Whitelist rules do not directly affect relevance feedback or mitigations. While relevance feedback trains the system to report more relevant anomalies, and mitigations take action on traffic directly, whitelist rules only suppress anomalies from appearing in the anomaly inbox. If you create a whitelist rule, the system does not interpret that as relevance feedback. You can assign relevant feedback ( ) or irrelevant feedback ( ) to an anomaly, then subsequently configure a whitelist rule based on that anomaly. However, you can create a situation where you train the system to report a certain type of anomaly, then whitelist that type of anomaly. The system continues to report this type of anomaly, but the whitelist rule suppresses it from the anomaly inbox. This can severely impact system functionality. While whitelist rules suppress anomalies from the controller anomaly inbox, agents apply mitigations to traffic. Mitigations always take effect before whitelist rules. If you create a whitelist rule and a mitigation, and both contain criteria that match the same traffic, the whitelist rule never triggers because the agent always applies the mitigation first. For more information on using whitelist rules and relevance feedback, see Relevance Feedback and Whitelist Rule Use. 4
5 Creating a Whitelist Rule Creating a Whitelist Rule Step 1 Select Inbox. Step 2 Select an anomaly to view the anomaly's details. Step 3 Click Whitelist. Step 4 If you want to remove criteria from the whitelist rule, click the delete icon ( ). Step 5 Click Submit Query to create the whitelist rule. Packet Buffer Capture When an agent detects an anomaly, it creates packet capture data (PCAP) files relevant to the anomaly. The packet buffer capture feature allows you to download these PCAP files from the controller web UI for further inspection. Upon anomaly detection, an agent creates PCAP files of the packets each source or destination IP address involved in an anomalous flow transmitted during the anomaly time frame. Each PCAP covers up to 1 minute's worth of traffic, and is up to 10 MB in size, uncompressed. Note If the disk has less than 15 MB of free space, the agent may create PCAPs smaller than 10 MB in size. Based on the anomaly length of time, the agent may create multiple PCAP files to capture relevant information, for up to the first five minutes of the anomaly. The agent then compresses all PCAP files related to an anomaly into an archive. On a regular basis, the agent prunes the oldest stored PCAP archive files if agent disk storage runs low. Users logged into the controller web UI can download an anomaly's PCAP files. The controller web UI retrieves the PCAP archive file from the agent and directs the agent to delete the archive file for storage considerations. The controller web UI then provides an HTTP URL from which the user can download the PCAP archive file. Note Disable browser pop-up blockers if you want to download PCAP files. 5
6 Downloading PCAPs Downloading PCAPs Step 1 Step 2 Step 3 Step 4 Select Inbox. Click an anomaly's description. Click Get PCAP files. Wait for the controller to retrieve the PCAP from the agent. Click Download to download the PCAP file. Anomaly Facts Pane The Facts pane in the anomaly detail view provides the same information as the expanded description in the Inbox. These facts provide additional context around the anomaly, including information about the anomaly traffic, and hosts and clusters involved. Related Topics Anomaly Facts Displayed, on page 6 Anomaly Facts Displayed For the target host, and the other host communicating with the target host, the anomaly facts include the: host IP address, or hostname if available geolocation information, if available host's cluster, and number of additional hosts in the cluster number of anomalies the host was previously involved with For the target host, the anomaly facts include the number of communications with other hosts in other clusters. For the anomalous communication between the hosts, the anomaly facts include the: directionality of the communication applications used most common frequency of this traffic type that the system detects Application Groups Application Group auth Applications used for user authentication and authorization Examples Active Directory, LDAP, RADIUS 6
7 Application Groups Application Group cloud collab darknet database dns file-xfer game icmp infra media network ntp office other other-ip-proto p2p Applications that store information and files in a cloud service Applications that enable collaborative interaction between users Applications that provide access to a darknet Applications that provide access to and interaction with databases Applications related to the Domain Name System (DNS) File transfer applications Game and gaming-related applications Internet Control Message Protocol (ICMP)-related applications Applications used to test and configure network infrastructure Media streaming applications Protocols and applications used for routing internet traffic Network Time Protocol (NTP)-related applications Applications used for office work, such as Applications that do not belong to other defined application groups Internet Protocol-related applications that do not belong to other defined application groups Peer-to-peer file sharing applications Examples Hotmail, Dropbox, Google Docs ICQ, Skype, Gtalk Tor SQL Server, MySQL, Sybase DNS FTP, NFS, Gopher Call of Duty, Maple Story, Steam ICMP Ping, DHCP, Endpoint Mapper Netflix, Hulu, Pandora BPG, OSPF, IGRP NTP SMTP, IMAP, NMAP remotefs, IIOP, VPP Sprite Remote Procedure Call, Message Posting Protocol, Storage Management Services Protocol Gnutella, BitTorrent, edonkey 7
8 Conversations Application Group print proxy remote shell social syslog tunneling unknown unknown-tcp unknown-udp windows www Printing-related applications Proxy server applications Applications used to access hosts remotely Applications used to access operating systems, including CLIs Social networking applications Syslog-related applications Applications used to create a tunnel and transmit traffic across it Unknown applications Unknown TCP applications Unknown UDP applications Microsoft Windows-related applications Websites on the World Wide Web Examples Network Printing Protocol, Internet Printing Protocol, Printer Socket Secure (SOCKS) Citrix, X Window System, pcanywhere Telnet, SSH, Secure Telnet Facebook, LinkedIn, Twitter syslog Hamachi, ISAKMP, SCTP Unknown unknown-tcp unknown-udp Windows Update, Common Internet File System (CIFS), NetBIOS Rotten Tomatoes, Reuters, Stack Overflow Conversations The Conversations pane contains all traffic related to this anomaly, including: anomalous flows involving the target host non-anomalous flows involving the target host within the same time frame, provided for context Conversations may be unidirectional or bidirectional, based on the traffic. The system groups conversations at the edge-level, by source, destination, and application group. The system also displays aggregate network statistics for each conversation. Traffic from source to destination is labeled with a right arrow ( ), and from destination to source is labeled with a left arrow ( ). If one of the anomalous features involves a DNS request having a domain that is too long, you can view all DNS requests associated with the anomalous conversation. 8
9 Conversation Fields You can expand each edge-level group to view individual conversations and flows. For each conversation or flow in the pane, you can view detailed connection information. You can also view a graphical timeline, showing when and how hosts transferred packets. Conversation Fields Table 2: Edge-level Conversation Fields Field App. group Source Destination (Show Details) Bytes (sum) Packets (sum) Bitrate (avg) Anomalous Features The application group that contains the application used in the conversation. The source host IP address or hostname, and if available, the source cluster and geolocation information. The destination host IP address or hostname, and if available, the source cluster and geolocation information. Click this to show the Bytes (sum), Packets (sum), and Bitrate (avg) fields. The total number of bytes transmitted in all related conversations and flows over this application group. The total number of packets transmitted in all related conversations and flows over this application group. The average speed for all related conversations and flows in bits per second (bps), kilobits per second (Kbps), or megabits per second (Mbps). The anomalous characteristics this edge displays. Table 3: Individual Conversation and Flow Fields Field Protocol & Application Source port Destination port The protocol and application used in the conversation or flow. The source host port. The destination host port. 9
10 Conversation Fields Field Bytes Packets Bitrate The number of bytes transmitted in this conversation or flow. The number of packets transmitted in this conversation or flow. The average connection speed for this conversation or flow in bps, Kbps, or Mbps. Host Detail Panes In a conversation, you can click on a host's IP address or hostname to view more information. This information includes the cluster the host belongs to, and if available, geolocation, user identity, and threat intelligence. If the system previously detected an anomaly, and it involved this host, the pane displays a count of these anomalies, and if available, additional information on these anomalies. You can click a cluster name to view details about that cluster. Host Detail Fields Table 4: Host Detail Pane Fields Field Cluster Member since Country State City Threat intel ISE The cluster to which the selected host belongs. The date and time the system added the selected host to this cluster. If available, the country where this host is located. If available, the state where this host is located. If available, the city where this host is located. The host's reputation, based on Talos analysis. User identity information collected from the Identity Services Engine (ISE) deployment, including user name, device type, MAC address, department, and role. Cluster Detail Panes In a conversation, you can click on a cluster's name to view more information, including: 10
11 Conversation Fields the cluster display name and internal name a bar chart that shows the proportion of application traffic that hosts transfer in the cluster the total number of hosts additional information for up to 50 hosts within the cluster, including geolocation, hostname, and threat flag You can click a host name to view details about that host. You can also download a comma-separated value (CSV) file which contains up to 50 hosts in the cluster. The downloaded CSV file contains Talos threat intelligence and ISE identify information associated with the host IP addresses. Cluster Names Cluster names describe the attributes common to all hosts within the cluster. Each agent creates clusters based on these common attributes. Depending on the deployment, number of detected hosts, and shared attributes, the cluster names may be general, containing whether a host is Internal or External to the branch (directionality relative to the branch), and whether the host is newly detected. The name may also be more specific, containing branch directionality, geolocation information, application groups common among the cluster's hosts, subnet, and other information. Some clusters may also contain only hosts that fall within certain IANA-defined IP ranges, or untracked hosts. Note Branch directionality depends on the Network Element Internal or External interface direction configuration. For cluster names, the agent assigns the branch directionality, and whether the cluster contains new or known hosts. It may also include one or more common application groups, as well as either the /24 subnet, or country and region location, but not both. Cluster names follow the pattern [new]{internal external}[<application-groups>][subnet <subnet> <country>, <region>], seen in the following examples: new internal http clients - new hosts within the branch, using HTTP clients new external dns servers in Turkey - new hosts external to the branch, identified as DNS servers, geolocation information identifies the host in Turkey new internal servers and ssh servers in subnet new hosts within the branch, identified as servers and ssh servers, part of the /24 subnet external p2p clients - known hosts external to the branch, using peer-to-peer clients internal mixed hosts in subnet known hosts within the branch, using a variety of applications, part of the /24 subnet external ntp hosts in Taiwan - known hosts external to the branch, using NTP, geolocation information identifies the host in Taiwan The cluster name may relate to an IANA-defined IP range, such as linklocal or mcast (multicast). In these clusters, the IP range is the only common attribute the agent uses to assign hosts to the cluster. 11
12 Conversation Fields Cluster Name Attributes The cluster name may also be untracked, in which case the agent is not tracking hosts at the same level of granularity as with other clusters. There are three reasons the agent assigns a host to the untracked cluster: the host is detected over an interface is not configured as Internal or External, and the agent cannot determine the host's branch directionality the agent has not detected traffic transmitted from the host the agent has observed too many hosts within too small a period of time and cannot track all hosts at the same level of detail As the agent assigns more hosts to a cluster based on shared attributes, it may subdivide the cluster. For example, if a cluster named external dns servers, based on branch directionality and application group, grows too large, the system may subdivide by country: external dns servers in United States, external dns servers in France, and external dns servers in China. Table 5: Cluster Name Attributes Attribute Name new internal external subnet <subnet> <country> <region> <application-groups> hosts are recently detected, and the agent cannot yet identify the applications most often used by the hosts hosts are internal to the branch hosts are external to the branch hosts belong to the /24 subnet listed in <subnet> hosts are located in <country>, based on the geolocation database hosts are located in <region> within <country>, based on the geolocation database hosts send and receive traffic most often over applications within these application groups, or mixed if the hosts send and receive traffic over a variety of applications and application groups, without a majority of traffic sent over a specific application Note A cluster name may contain more than one application group. 12
13 Conversation Fields Attribute Name <IANA-special-range> hosts have an IP address within a special range, as defined by IANA: reserved - IP addresses reserved for benchmarking, loopback, limited broadcast, IETF protocol assignments, and documentation linklocal - link local IP addresses mcast - multicast IP addresses external - IP addresses reserved for shared address spaces, 6to4 relay anycast, AS112, and automatic multicast tunneling See iana-ipv4-special-registry/ iana-ipv4-special-registry.xhtml and multicast-addresses.xhtml for more information. untracked hosts are not tracked by the agent, because: the host is detected over an interface is not configured as Internal or External, and the agent cannot determine the host's branch directionality the agent has not detected traffic transmitted from the host the agent has observed too many hosts within too small a period of time and cannot track all hosts Cluster Detail Fields Table 6: Cluster Detail Pane Fields Field Country Host Threat Flag The geolocation flag icon representing the country in which the host is located. The host IP address, or hostname if available. Whether threat intelligence from Talos identified this host as malicious. 13
14 Filtering Conversations Downloading Hosts in a CSV File Step 1 Step 2 From an agent dashboard or an anomaly's details, click a cluster name. Click Download as CSV. Filtering Conversations Step 1 Step 2 Step 3 Select Inbox, then click an anomaly's. If it is collapsed, click the expand arrow ( ) to expand the Filters pane. Check the filter check boxes corresponding to the criteria you want to filter on. Anomalous Features Graph The Anomalous Features graph combines a radar chart with a heat map to show how anomalous traffic compares to baseline traffic. The graph combines all anomalous features detected for all related anomalous conversations For each anomalous feature type, the graph plots an axis at one of three levels: cluster-level - all conversations from a source cluster of an application group edge-level - all conversations of an edge and application group graph-level - all conversations of an application group Along each axis, the heat map shows the frequency for that traffic type. The darker the color, the more frequent that quantity of traffic. The system plots the anomalous traffic as a dot along the axis. The farther the system plots the dot from the baseline traffic, the less common the traffic is. You can hover over the anomalous traffic dot to view more information about it, or you can view the descriptions of each anomalous feature. If the timeline displays the anomaly's duration in multiple sections, you can navigate through the timeline to update the anomalous features graph. You can then see the anomaly's progression over time. 14
15 Anomalous Feature Types Anomalous Feature Types Table 7: Anomalous Feature Types Anomalous Feature DNS request subpart length Number of bytes Number of bytes per packet Number of flows Number of packets Number of packets per flow Total flow duration Unexpected created edge Unusual time of day In the DNS lookup for an anomalous conversation, one of the domains within the domain name is longer than what the agent learned about domain names. The number of bytes in an anomalous conversation is smaller or larger than what the agent learned about conversations. The number of bytes per packet in an anomalous conversation is smaller or larger than what the agent learned about conversations. The number of flows in an anomalous conversation is smaller or larger than what the agent learned about conversations. The number of packets in an anomalous conversation is smaller or larger than what the agent learned about conversations. The number of packets per flow in an anomalous conversation is smaller or larger than what the agent learned about conversations. The flow duration is longer or shorter than what the agent learned about flows. The anomalous edge involves an application not previously detected between the clusters by the agent. The anomalous edge saw traffic at a time of day either rarely seen or not seen at all, according to what the agent has learned about the edge. Anomaly Graph The anomaly graph displays the anomalous and related traffic in a graphical format. Source clusters are displayed to the left, and destination clusters to the right. Application groups are listed in the middle. A line connecting a source and destination cluster represents an edge; anomalous edges are highlighted. If you hover 15
16 Mitigation from an Anomaly your pointer over a cluster, the graph updates to display only those edges where the cluster is a source or destination. Mitigation from an Anomaly You can configure mitigations from an anomaly. If you do this, the system prepopulates two mitigation policies. One mitigation policy applies to traffic to the target host detected in the anomaly. The other policy applies to traffic from the target host. You can apply these policies with the prepopulated values, or you can modify them before applying. Configuring a Mitigation from an Anomaly Step 1 Step 2 Step 3 Step 4 Select Inbox. Click an anomaly's description. Click Mitigate this anomaly in the Mitigate pane. The system prepopulates two mitigation policies with information matching the anomaly. If you only want to apply a mitigation policy in one direction: uncheck the Mitigate forward check box to only mitigate traffic incoming to the target host. uncheck the Mitigate backward check box to only mitigate traffic outgoing from the target host. Step 5 Step 6 If you want to change the anomaly duration, update the Duration. Click Create mitigation policies. 16
The following describes an example Learning Network License deployment and example use cases.
 The following describes an example Learning Network License deployment and example use cases. Example Deployment, page 2 Example Learning Network License Deployment, page 3 Example Deployment Use Cases,
The following describes an example Learning Network License deployment and example use cases. Example Deployment, page 2 Example Learning Network License Deployment, page 3 Example Deployment Use Cases,
Compare Security Analytics Solutions
 Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
Network-Based Application Recognition
 Network-Based Application Recognition Last updated: September 2008 Common questions and answers regarding Cisco Network-Based Application Recognition (NBAR) follow. Q. What is NBAR? A. NBAR, an important
Network-Based Application Recognition Last updated: September 2008 Common questions and answers regarding Cisco Network-Based Application Recognition (NBAR) follow. Q. What is NBAR? A. NBAR, an important
Addresses, Protocols, and Ports Reference
 APPENDIXA Addresses, Protocols, and Ports Reference This appendix provides a quick reference for the following topics: IP Addresses and Subnet Masks Protocols and Applications TCP and UDP Ports ICMP Types
APPENDIXA Addresses, Protocols, and Ports Reference This appendix provides a quick reference for the following topics: IP Addresses and Subnet Masks Protocols and Applications TCP and UDP Ports ICMP Types
Access Control. Access Control Overview. Access Control Rules and the Default Action
 The following topics explain access control rules. These rules control which traffic is allowed to pass through the device, and apply advanced services to the traffic, such as intrusion inspection. Overview,
The following topics explain access control rules. These rules control which traffic is allowed to pass through the device, and apply advanced services to the traffic, such as intrusion inspection. Overview,
Addresses, Protocols, and Ports
 APPENDIXB This appendix provides a quick reference for IP addresses, protocols, and applications. This appendix includes the following sections: IPv4 Addresses and Subnet Masks, page B-1 IPv6 Addresses,
APPENDIXB This appendix provides a quick reference for IP addresses, protocols, and applications. This appendix includes the following sections: IPv4 Addresses and Subnet Masks, page B-1 IPv6 Addresses,
Realms and Identity Policies
 The following topics describe realms and identity policies: Introduction:, page 1 Creating a Realm, page 5 Creating an Identity Policy, page 11 Creating an Identity Rule, page 15 Managing Realms, page
The following topics describe realms and identity policies: Introduction:, page 1 Creating a Realm, page 5 Creating an Identity Policy, page 11 Creating an Identity Rule, page 15 Managing Realms, page
Access Control. Access Control Overview. Access Control Rules and the Default Action
 The following topics explain access control rules. These rules control which traffic is allowed to pass through the device, and apply advanced services to the traffic, such as intrusion inspection. Overview,
The following topics explain access control rules. These rules control which traffic is allowed to pass through the device, and apply advanced services to the traffic, such as intrusion inspection. Overview,
Logging. About Logging. This chapter describes how to log system messages and use them for troubleshooting.
 This chapter describes how to log system messages and use them for troubleshooting. About, page 1 Guidelines for, page 7 Configure, page 8 Monitoring the Logs, page 26 History for, page 29 About System
This chapter describes how to log system messages and use them for troubleshooting. About, page 1 Guidelines for, page 7 Configure, page 8 Monitoring the Logs, page 26 History for, page 29 About System
TCP, UDP Ports, and ICMP Message Types1
 Appendix A APPENDIX A TCP, UDP Ports, and ICMP Message Types1 I list useful TCP, UDP ports, and ICMP message types in this appendix. A comprehensive list of registered TCP and UDP services may be found
Appendix A APPENDIX A TCP, UDP Ports, and ICMP Message Types1 I list useful TCP, UDP ports, and ICMP message types in this appendix. A comprehensive list of registered TCP and UDP services may be found
Addresses, Protocols, and Ports
 This chapter provides a quick reference for IP addresses, protocols, and applications. IPv4 Addresses and Subnet Masks, page 1 IPv6 Addresses, page 5 Protocols and Applications, page 11 and Ports, page
This chapter provides a quick reference for IP addresses, protocols, and applications. IPv4 Addresses and Subnet Masks, page 1 IPv6 Addresses, page 5 Protocols and Applications, page 11 and Ports, page
Network Address Translation (NAT)
 The following topics explain and how to configure it. Why Use NAT?, page 1 NAT Basics, page 2 Guidelines for NAT, page 8 Configure NAT, page 12 Translating IPv6 Networks, page 40 Monitoring NAT, page 51
The following topics explain and how to configure it. Why Use NAT?, page 1 NAT Basics, page 2 Guidelines for NAT, page 8 Configure NAT, page 12 Translating IPv6 Networks, page 40 Monitoring NAT, page 51
Modular Policy Framework. Class Maps SECTION 4. Advanced Configuration
 [ 59 ] Section 4: We have now covered the basic configuration and delved into AAA services on the ASA. In this section, we cover some of the more advanced features of the ASA that break it away from a
[ 59 ] Section 4: We have now covered the basic configuration and delved into AAA services on the ASA. In this section, we cover some of the more advanced features of the ASA that break it away from a
Rule Management: Common Characteristics
 The following topics describe how to manage common characteristics of rules in various policies on the Firepower Management Center: Introduction to Rules, page 1 Rule Condition Types, page 2 Searching
The following topics describe how to manage common characteristics of rules in various policies on the Firepower Management Center: Introduction to Rules, page 1 Rule Condition Types, page 2 Searching
Systrome Next Gen Firewalls
 N E T K S Systrome Next Gen Firewalls Systrome s Next Generation Firewalls provides comprehensive security protection from layer 2 to layer 7 for the mobile Internet era. The new next generation security
N E T K S Systrome Next Gen Firewalls Systrome s Next Generation Firewalls provides comprehensive security protection from layer 2 to layer 7 for the mobile Internet era. The new next generation security
HP High-End Firewalls
 HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2650 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2650 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
Stonesoft Management Center. Release Notes Revision A
 Stonesoft Management Center Release Notes 5.10.5 Revision A Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
Stonesoft Management Center Release Notes 5.10.5 Revision A Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
Monitoring the Device
 The system includes dashboards and an Event Viewer that you can use to monitor the device and traffic that is passing through the device. Enable Logging to Obtain Traffic Statistics, page 1 Monitoring
The system includes dashboards and an Event Viewer that you can use to monitor the device and traffic that is passing through the device. Enable Logging to Obtain Traffic Statistics, page 1 Monitoring
CMX Dashboard Visitor Connect
 CHAPTER 11 Cisco CMX Visitor Connect is a guest access solution based on Mobility Services Engine (MSE), Cisco Wireless LAN Controller (WLC) and Lightweight Access points (AP). The CMX Visitor Connect
CHAPTER 11 Cisco CMX Visitor Connect is a guest access solution based on Mobility Services Engine (MSE), Cisco Wireless LAN Controller (WLC) and Lightweight Access points (AP). The CMX Visitor Connect
Security, Internet Access, and Communication Ports
 Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Security Requirements Security Requirements, on
Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Security Requirements Security Requirements, on
History Page. Barracuda NextGen Firewall F
 The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
plixer Scrutinizer Competitor Worksheet Visualization of Network Health Unauthorized application deployments Detect DNS communication tunnels
 Scrutinizer Competitor Worksheet Scrutinizer Malware Incident Response Scrutinizer is a massively scalable, distributed flow collection system that provides a single interface for all traffic related to
Scrutinizer Competitor Worksheet Scrutinizer Malware Incident Response Scrutinizer is a massively scalable, distributed flow collection system that provides a single interface for all traffic related to
Device Management Basics
 The following topics describe how to manage devices in the Firepower System: The Device Management Page, on page 1 Remote Management Configuration, on page 2 Adding Devices to the Firepower Management
The following topics describe how to manage devices in the Firepower System: The Device Management Page, on page 1 Remote Management Configuration, on page 2 Adding Devices to the Firepower Management
Read the following information carefully, before you begin an upgrade.
 Read the following information carefully, before you begin an upgrade. Review Supported Upgrade Paths, page 1 Review Time Taken for Upgrade, page 1 Review Available Cisco APIC-EM Ports, page 2 Securing
Read the following information carefully, before you begin an upgrade. Review Supported Upgrade Paths, page 1 Review Time Taken for Upgrade, page 1 Review Available Cisco APIC-EM Ports, page 2 Securing
CounterACT 7.0. Quick Installation Guide for a Single Virtual CounterACT Appliance
 CounterACT 7.0 Quick Installation Guide for a Single Virtual CounterACT Appliance Table of Contents Welcome to CounterACT Version 7.0... 3 Overview... 4 1. Create a Deployment Plan... 5 Decide Where to
CounterACT 7.0 Quick Installation Guide for a Single Virtual CounterACT Appliance Table of Contents Welcome to CounterACT Version 7.0... 3 Overview... 4 1. Create a Deployment Plan... 5 Decide Where to
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e. Chapter 8 Networking Essentials
 A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e Chapter 8 Networking Essentials Objectives Learn about the protocols and standards Windows uses for networking Learn how to connect
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e Chapter 8 Networking Essentials Objectives Learn about the protocols and standards Windows uses for networking Learn how to connect
CCNA R&S: Introduction to Networks. Chapter 10: The Application Layer
 CCNA R&S: Introduction to Networks Chapter 10: The Application Layer Frank Schneemann 10.0.1.1 Introduction 10.0.1.2 Activity - Application Investigation 10.1.1.1 OSI and TCP/IP Models Revisited The application
CCNA R&S: Introduction to Networks Chapter 10: The Application Layer Frank Schneemann 10.0.1.1 Introduction 10.0.1.2 Activity - Application Investigation 10.1.1.1 OSI and TCP/IP Models Revisited The application
BIG-IP Access Policy Manager : Secure Web Gateway. Version 12.1
 BIG-IP Access Policy Manager : Secure Web Gateway Version 12.1 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...11 About Secure Web Gateway for web access...11 About the benefits
BIG-IP Access Policy Manager : Secure Web Gateway Version 12.1 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...11 About Secure Web Gateway for web access...11 About the benefits
Connection and Security Intelligence Events
 and Security Intelligence Events The following topics describe how to use connection and security events tables. Event Basics, page 1 Using and Security Intelligence Event Tables, page 22 Viewing the Summary
and Security Intelligence Events The following topics describe how to use connection and security events tables. Event Basics, page 1 Using and Security Intelligence Event Tables, page 22 Viewing the Summary
Application Detection
 The following topics describe Firepower System application detection : Overview:, on page 1 Custom Application Detectors, on page 6 Viewing or Downloading Detector Details, on page 14 Sorting the Detector
The following topics describe Firepower System application detection : Overview:, on page 1 Custom Application Detectors, on page 6 Viewing or Downloading Detector Details, on page 14 Sorting the Detector
Identity Firewall. About the Identity Firewall
 This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
Device Management Basics
 The following topics describe how to manage devices in the Firepower System: The Device Management Page, on page 1 Remote Management Configuration, on page 2 Add Devices to the Firepower Management Center,
The following topics describe how to manage devices in the Firepower System: The Device Management Page, on page 1 Remote Management Configuration, on page 2 Add Devices to the Firepower Management Center,
PrepAwayExam. High-efficient Exam Materials are the best high pass-rate Exam Dumps
 PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 642-618 Title : Deploying Cisco ASA Firewall Solutions (FIREWALL v2.0) Vendors : Cisco
PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 642-618 Title : Deploying Cisco ASA Firewall Solutions (FIREWALL v2.0) Vendors : Cisco
Fireware-Essentials. Number: Fireware Essentials Passing Score: 800 Time Limit: 120 min File Version: 7.
 Fireware-Essentials Number: Fireware Essentials Passing Score: 800 Time Limit: 120 min File Version: 7.0 http://www.gratisexam.com/ Fireware Essentials Fireware Essentials Exam Exam A QUESTION 1 Which
Fireware-Essentials Number: Fireware Essentials Passing Score: 800 Time Limit: 120 min File Version: 7.0 http://www.gratisexam.com/ Fireware Essentials Fireware Essentials Exam Exam A QUESTION 1 Which
Pass4sure q. Cisco Securing Cisco Networks with Sourcefire IPS
 Pass4sure.500-285.42q Number: 500-285 Passing Score: 800 Time Limit: 120 min File Version: 6.1 Cisco 500-285 Securing Cisco Networks with Sourcefire IPS I'm quite happy to announce that I passed 500-285
Pass4sure.500-285.42q Number: 500-285 Passing Score: 800 Time Limit: 120 min File Version: 6.1 Cisco 500-285 Securing Cisco Networks with Sourcefire IPS I'm quite happy to announce that I passed 500-285
Activating Intrusion Prevention Service
 Activating Intrusion Prevention Service Intrusion Prevention Service Overview Configuring Intrusion Prevention Service Intrusion Prevention Service Overview Intrusion Prevention Service (IPS) delivers
Activating Intrusion Prevention Service Intrusion Prevention Service Overview Configuring Intrusion Prevention Service Intrusion Prevention Service Overview Intrusion Prevention Service (IPS) delivers
Security, Internet Access, and Communication Ports
 Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Security Requirements Security Requirements, on
Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Security Requirements Security Requirements, on
Network Address Translation (NAT)
 The following topics explain and how to configure it. Why Use NAT?, page 1 NAT Basics, page 2 Guidelines for NAT, page 7 Dynamic NAT, page 12 Dynamic PAT, page 21 Static NAT, page 40 Identity NAT, page
The following topics explain and how to configure it. Why Use NAT?, page 1 NAT Basics, page 2 Guidelines for NAT, page 7 Dynamic NAT, page 12 Dynamic PAT, page 21 Static NAT, page 40 Identity NAT, page
Detecting Specific Threats
 The following topics explain how to use preprocessors in a network analysis policy to detect specific threats: Introduction to Specific Threat Detection, page 1 Back Orifice Detection, page 1 Portscan
The following topics explain how to use preprocessors in a network analysis policy to detect specific threats: Introduction to Specific Threat Detection, page 1 Back Orifice Detection, page 1 Portscan
Security, Internet Access, and Communication Ports
 Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: About Security, Internet Access, and Communication
Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: About Security, Internet Access, and Communication
User Identity Sources
 The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, page 1 The User
The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, page 1 The User
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
User Identity Sources
 The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, on page 1 The
The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, on page 1 The
What s New in Fireware v12.3 WatchGuard Training
 What s New in Fireware v12.3 2 What s New in Fireware v12.3 Updates to Networking functionality: SD-WAN actions SD-WAN reporting enhancements NetFlow support Link monitor enhancements Centralized FireCluster
What s New in Fireware v12.3 2 What s New in Fireware v12.3 Updates to Networking functionality: SD-WAN actions SD-WAN reporting enhancements NetFlow support Link monitor enhancements Centralized FireCluster
4. The transport layer
 4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
HP Load Balancing Module
 HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
Device Management Basics
 The following topics describe how to manage devices in the Firepower System: The Device Management Page, page 1 Remote Management Configuration, page 2 Adding Devices to the Firepower Management Center,
The following topics describe how to manage devices in the Firepower System: The Device Management Page, page 1 Remote Management Configuration, page 2 Adding Devices to the Firepower Management Center,
Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin,
 Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin, ydlin@cs.nctu.edu.tw Chapter 1: Introduction 1. How does Internet scale to billions of hosts? (Describe what structure
Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin, ydlin@cs.nctu.edu.tw Chapter 1: Introduction 1. How does Internet scale to billions of hosts? (Describe what structure
Barracuda Firewall Release Notes 6.6.X
 Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Request for Proposal (RFP) for Supply and Implementation of Firewall for Internet Access (RFP Ref )
 Appendix 1 1st Tier Firewall The Solution shall be rack-mountable into standard 19-inch (482.6-mm) EIA rack. The firewall shall minimally support the following technologies and features: (a) Stateful inspection;
Appendix 1 1st Tier Firewall The Solution shall be rack-mountable into standard 19-inch (482.6-mm) EIA rack. The firewall shall minimally support the following technologies and features: (a) Stateful inspection;
ForeScout CounterACT. (AWS) Plugin. Configuration Guide. Version 1.3
 ForeScout CounterACT Hybrid Cloud Module: Amazon Web Services (AWS) Plugin Version 1.3 Table of Contents Amazon Web Services Plugin Overview... 4 Use Cases... 5 Providing Consolidated Visibility... 5 Dynamic
ForeScout CounterACT Hybrid Cloud Module: Amazon Web Services (AWS) Plugin Version 1.3 Table of Contents Amazon Web Services Plugin Overview... 4 Use Cases... 5 Providing Consolidated Visibility... 5 Dynamic
Validate Pre-Deployment and Live Networks and Applications
 IxChariot 8 Validate Pre-Deployment and Live Networks and Applications Key Features New HTML5-based web interface zero client installation; browser-based IxChariot 8 is a new version of the industry's
IxChariot 8 Validate Pre-Deployment and Live Networks and Applications Key Features New HTML5-based web interface zero client installation; browser-based IxChariot 8 is a new version of the industry's
Working with Contracts
 Contracts, page 1 Filters, page 9 Taboo Contracts, page 12 Inter-Tenant Contracts, page 15 Contracts Contracts provide a way for the Cisco Application Centric Infrastructure (ACI) administrator to control
Contracts, page 1 Filters, page 9 Taboo Contracts, page 12 Inter-Tenant Contracts, page 15 Contracts Contracts provide a way for the Cisco Application Centric Infrastructure (ACI) administrator to control
Configuring Caching Services
 CHAPTER 8 This chapter describes how to configure conventional caching services (HTTP, FTP [FTP-over-HTTP caching and native FTP caching], HTTPS, and DNS caching) for centrally managed Content Engines.
CHAPTER 8 This chapter describes how to configure conventional caching services (HTTP, FTP [FTP-over-HTTP caching and native FTP caching], HTTPS, and DNS caching) for centrally managed Content Engines.
Introduction. Learning Network License Introduction
 The following provides an introduction to installing the Cisco Stealthwatch Learning Network License (Learning Network License) platform, installing a controller on an ESXi host, and deploying an agent
The following provides an introduction to installing the Cisco Stealthwatch Learning Network License (Learning Network License) platform, installing a controller on an ESXi host, and deploying an agent
Chapter 10: Application Layer CCENT Routing and Switching Introduction to Networks v6.0
 Chapter 10: Application Layer CCENT Routing and Switching Introduction to Networks v6.0 CCNET v6 10 Chapter 10 - Sections & Objectives 10.1 Application Layer Protocols Explain the operation of the application
Chapter 10: Application Layer CCENT Routing and Switching Introduction to Networks v6.0 CCNET v6 10 Chapter 10 - Sections & Objectives 10.1 Application Layer Protocols Explain the operation of the application
Network Performance Analysis System. User Guide
 Network Performance Analysis System User Guide Copyrig ht Copyright 2018 Colasoft. All rights reserved. Information in this document is subject to change without notice. No part of this document may be
Network Performance Analysis System User Guide Copyrig ht Copyright 2018 Colasoft. All rights reserved. Information in this document is subject to change without notice. No part of this document may be
Spirent Avalanche. Applications and Security Testing Solutions. Application. Features & Benefits. Data Sheet. Network Performance Testing
 Data Sheet Spirent Avalanche Spirent s Avalanche Layer 4-7 testing solution provides capacity, security and performance testing for network infrastructures, cloud and virtual environments, Web application
Data Sheet Spirent Avalanche Spirent s Avalanche Layer 4-7 testing solution provides capacity, security and performance testing for network infrastructures, cloud and virtual environments, Web application
WatchGuard System Manager Fireware Configuration Guide. WatchGuard Fireware Pro v8.1
 WatchGuard System Manager Fireware Configuration Guide WatchGuard Fireware Pro v8.1 Notice to Users Information in this guide is subject to change without notice. Companies, names, and data used in examples
WatchGuard System Manager Fireware Configuration Guide WatchGuard Fireware Pro v8.1 Notice to Users Information in this guide is subject to change without notice. Companies, names, and data used in examples
Using Trend Reports. Understanding Reporting Options CHAPTER
 CHAPTER 10 To learn about supported services and platforms, see Supported Services and Platforms for Monitoring and Reports, page 1-5. The following topics describe the reporting features available in
CHAPTER 10 To learn about supported services and platforms, see Supported Services and Platforms for Monitoring and Reports, page 1-5. The following topics describe the reporting features available in
TCP /IP Fundamentals Mr. Cantu
 TCP /IP Fundamentals Mr. Cantu OSI Model and TCP/IP Model Comparison TCP / IP Protocols (Application Layer) The TCP/IP subprotocols listed in this layer are services that support a number of network functions:
TCP /IP Fundamentals Mr. Cantu OSI Model and TCP/IP Model Comparison TCP / IP Protocols (Application Layer) The TCP/IP subprotocols listed in this layer are services that support a number of network functions:
Security, Internet Access, and Communication Ports
 Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Overview: Security, Internet Access, and Communication
Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Overview: Security, Internet Access, and Communication
Configuring and Managing the IP Camera
 CHAPTER 3 The Cisco Video Surveillance IP Camera provides configuration windows that you use to configure and manage the IP camera. This chapter explains how to access the configuration windows, describes
CHAPTER 3 The Cisco Video Surveillance IP Camera provides configuration windows that you use to configure and manage the IP camera. This chapter explains how to access the configuration windows, describes
Applied Networks & Security
 Applied Networks & Security Applications http://condor.depaul.edu/~jkristof/it263/ John Kristoff jtk@depaul.edu IT 263 Winter 2006/2007 John Kristoff - DePaul University 1 HTTP/HTTPS The language of the
Applied Networks & Security Applications http://condor.depaul.edu/~jkristof/it263/ John Kristoff jtk@depaul.edu IT 263 Winter 2006/2007 John Kristoff - DePaul University 1 HTTP/HTTPS The language of the
Configuring and Managing the IP Camera
 CHAPTER 3 The Cisco Video Surveillance IP Camera provides configuration windows that you use to configure and manage the IP camera. This chapter explains how to access the configuration windows, describes
CHAPTER 3 The Cisco Video Surveillance IP Camera provides configuration windows that you use to configure and manage the IP camera. This chapter explains how to access the configuration windows, describes
McAfee Endpoint Security Firewall Product Guide. (McAfee epolicy Orchestrator)
 McAfee Endpoint Security 10.6.0 - Firewall Product Guide (McAfee epolicy Orchestrator) COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection,
McAfee Endpoint Security 10.6.0 - Firewall Product Guide (McAfee epolicy Orchestrator) COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection,
McAfee Network Security Platform 9.1
 9.1.7.15-9.1.5.9 Manager-NS-series Release Notes McAfee Network Security Platform 9.1 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known issues
9.1.7.15-9.1.5.9 Manager-NS-series Release Notes McAfee Network Security Platform 9.1 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known issues
Configuring the Management Access List
 The following topics explain how to configure the various system settings that are grouped together on the page. The settings cover overall system function. Configuring the Management Access List, page
The following topics explain how to configure the various system settings that are grouped together on the page. The settings cover overall system function. Configuring the Management Access List, page
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
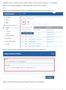 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
COMS3200/7201 Computer Networks 1 (Version 1.0)
 COMS3200/7201 Computer Networks 1 (Version 1.0) Assignment 3 Due 8pm Monday 29 th May 2017. V1 draft (hopefully final) Note that the assignment has three parts Part A, B & C, each worth 50 marks. Total
COMS3200/7201 Computer Networks 1 (Version 1.0) Assignment 3 Due 8pm Monday 29 th May 2017. V1 draft (hopefully final) Note that the assignment has three parts Part A, B & C, each worth 50 marks. Total
Static Application Mapping Using Performance Routing
 Static Application Mapping Using Performance Routing The OER - Application Aware Routing with Static Application Mapping feature introduces the ability to configure standard applications using just one
Static Application Mapping Using Performance Routing The OER - Application Aware Routing with Static Application Mapping feature introduces the ability to configure standard applications using just one
Paloalto Networks PCNSA EXAM
 Page No 1 m/ Paloalto Networks PCNSA EXAM Palo Alto Networks Certified Network Security Administrator Product: Full File For More Information: /PCNSA-dumps 2 Product Questions: 50 Version: 8.0 Question:
Page No 1 m/ Paloalto Networks PCNSA EXAM Palo Alto Networks Certified Network Security Administrator Product: Full File For More Information: /PCNSA-dumps 2 Product Questions: 50 Version: 8.0 Question:
CCNA Exploration Network Fundamentals. Chapter 03 Application Functionality and Protocols
 CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
Exam Topics Cross Reference
 Appendix R Exam Topics Cross Reference This appendix lists the exam topics associated with the ICND1 100-105 exam and the CCNA 200-125 exam. Cisco lists the exam topics on its website. Even though changes
Appendix R Exam Topics Cross Reference This appendix lists the exam topics associated with the ICND1 100-105 exam and the CCNA 200-125 exam. Cisco lists the exam topics on its website. Even though changes
Avaya Port Matrix: Avaya Diagnostic Server 3.0
 Avaya Matrix: Avaya Diagnostic Server 3.0 Issue 2.0 February 208 ALL INFORMATION IS BELIEVED TO BE CORRECT AT THE TIME OF PUBLICATION AND IS PROVIDED "AS IS". AVAYA INC. DISCLAIMS ALL WARRANTIES, EITHER
Avaya Matrix: Avaya Diagnostic Server 3.0 Issue 2.0 February 208 ALL INFORMATION IS BELIEVED TO BE CORRECT AT THE TIME OF PUBLICATION AND IS PROVIDED "AS IS". AVAYA INC. DISCLAIMS ALL WARRANTIES, EITHER
vcloud Air - Virtual Private Cloud OnDemand Networking Guide
 vcloud Air - Virtual Private Cloud OnDemand Networking Guide vcloud Air This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
vcloud Air - Virtual Private Cloud OnDemand Networking Guide vcloud Air This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
TCP/IP Networking. Training Details. About Training. About Training. What You'll Learn. Training Time : 9 Hours. Capacity : 12
 TCP/IP Networking Training Details Training Time : 9 Hours Capacity : 12 Prerequisites : There are no prerequisites for this course. About Training About Training TCP/IP is the globally accepted group
TCP/IP Networking Training Details Training Time : 9 Hours Capacity : 12 Prerequisites : There are no prerequisites for this course. About Training About Training TCP/IP is the globally accepted group
The following topics describe how to configure correlation policies and rules.
 The following topics describe how to configure correlation policies and rules. Introduction to and Rules, page 1 Configuring, page 2 Configuring Correlation Rules, page 5 Configuring Correlation Response
The following topics describe how to configure correlation policies and rules. Introduction to and Rules, page 1 Configuring, page 2 Configuring Correlation Rules, page 5 Configuring Correlation Response
Port Mirroring in CounterACT. CounterACT Technical Note
 Table of Contents About Port Mirroring and the Packet Engine... 3 Information Based on Specific Protocols... 4 ARP... 4 DHCP... 5 HTTP... 6 NetBIOS... 7 TCP/UDP... 7 Endpoint Lifecycle... 8 Active Endpoint
Table of Contents About Port Mirroring and the Packet Engine... 3 Information Based on Specific Protocols... 4 ARP... 4 DHCP... 5 HTTP... 6 NetBIOS... 7 TCP/UDP... 7 Endpoint Lifecycle... 8 Active Endpoint
Chapter 2 - Part 1. The TCP/IP Protocol: The Language of the Internet
 Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
Download the latest version of the DNS2Go Client from:
 Using DNS2Go with your Linksys Cable / DSL Router Many users with Cable and xdsl broadband connections are using hardware routers such as the Linksys Cable/DSL Routers to connect their local area network
Using DNS2Go with your Linksys Cable / DSL Router Many users with Cable and xdsl broadband connections are using hardware routers such as the Linksys Cable/DSL Routers to connect their local area network
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Different Layers Lecture 21
 Different Layers Lecture 21 10/17/2003 Jian Ren 1 The Transport Layer 10/17/2003 Jian Ren 2 Transport Services and Protocols Provide logical communication between app processes running on different hosts
Different Layers Lecture 21 10/17/2003 Jian Ren 1 The Transport Layer 10/17/2003 Jian Ren 2 Transport Services and Protocols Provide logical communication between app processes running on different hosts
Avaya Proprietary Use pursuant to the terms of your signed agreement or Avaya policy.
 Matrix Equinox 3.0 Issue 1.0 December 15, 2016 Proprietary Use pursuant to the terms of your signed agreement or policy. December 2016 Matrix: Equinox 3.0 1 ALL INFORMATION IS BELIEVED TO BE CORRECT AT
Matrix Equinox 3.0 Issue 1.0 December 15, 2016 Proprietary Use pursuant to the terms of your signed agreement or policy. December 2016 Matrix: Equinox 3.0 1 ALL INFORMATION IS BELIEVED TO BE CORRECT AT
CSCI 466 Midterm Networks Fall 2013
 CSCI 466 Midterm Networks Fall 2013 Name: This exam consists of 6 problems on the following 7 pages. You may use your single-sided hand-written 8 ½ x 11 note sheet and a calculator during the exam. No
CSCI 466 Midterm Networks Fall 2013 Name: This exam consists of 6 problems on the following 7 pages. You may use your single-sided hand-written 8 ½ x 11 note sheet and a calculator during the exam. No
App-ID. PALO ALTO NETWORKS: App-ID Technology Brief
 App-ID Application Protocol Detection / Decryption Application Protocol Decoding Application Signature Heuristics App-ID is a patent-pending traffic classification technology that identifies more than
App-ID Application Protocol Detection / Decryption Application Protocol Decoding Application Signature Heuristics App-ID is a patent-pending traffic classification technology that identifies more than
Connect the Appliance to a Cisco Cloud Web Security Proxy
 Connect the Appliance to a Cisco Cloud Web Security Proxy This chapter contains the following sections: How to Configure and Use Features in Cloud Connector Mode, on page 1 Deployment in Cloud Connector
Connect the Appliance to a Cisco Cloud Web Security Proxy This chapter contains the following sections: How to Configure and Use Features in Cloud Connector Mode, on page 1 Deployment in Cloud Connector
Accessing Data from the Web Interface
 5 CHAPTER This chapter provides information about accessing Prime Performance Manager data from Prime Performance Manager web interface. This chapter contains: Supported Browsers, page 5-1 Accessing Prime
5 CHAPTER This chapter provides information about accessing Prime Performance Manager data from Prime Performance Manager web interface. This chapter contains: Supported Browsers, page 5-1 Accessing Prime
Routing Overview. Information About Routing CHAPTER
 21 CHAPTER This chapter describes underlying concepts of how routing behaves within the ASA, and the routing protocols that are supported. This chapter includes the following sections: Information About
21 CHAPTER This chapter describes underlying concepts of how routing behaves within the ASA, and the routing protocols that are supported. This chapter includes the following sections: Information About
How to Configure a Remote Management Tunnel for an F-Series Firewall
 How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
Networks, WWW, HTTP. Web Technologies I. Zsolt Tóth. University of Miskolc. Zsolt Tóth (University of Miskolc) Networks, WWW, HTTP / 35
 Networks, WWW, HTTP Web Technologies I. Zsolt Tóth University of Miskolc 2018 Zsolt Tóth (University of Miskolc) Networks, WWW, HTTP 2018 1 / 35 Table of Contents Networks Internet 1 Networks Internet
Networks, WWW, HTTP Web Technologies I. Zsolt Tóth University of Miskolc 2018 Zsolt Tóth (University of Miskolc) Networks, WWW, HTTP 2018 1 / 35 Table of Contents Networks Internet 1 Networks Internet
Defining IPsec Networks and Customers
 CHAPTER 4 Defining the IPsec Network Elements In this product, a VPN network is a unique group of targets; a target can be a member of only one network. Thus, a VPN network allows a provider to partition
CHAPTER 4 Defining the IPsec Network Elements In this product, a VPN network is a unique group of targets; a target can be a member of only one network. Thus, a VPN network allows a provider to partition
Advanced Application Reporting USER GUIDE
 Advanced Application Reporting USER GUIDE CONTENTS 1.0 Preface: About This Document 5 2.0 Conventions 5 3.0 Chapter 1: Introducing Advanced Application Reporting 6 4.0 Features and Benefits 7 5.0 Product
Advanced Application Reporting USER GUIDE CONTENTS 1.0 Preface: About This Document 5 2.0 Conventions 5 3.0 Chapter 1: Introducing Advanced Application Reporting 6 4.0 Features and Benefits 7 5.0 Product
Configuring Traffic Policies
 CHAPTER 11 Date: 4/23/09 Cisco Application Networking Manager helps you configure class maps and policy maps to provide a global level of classification for filtering traffic received by or passing through
CHAPTER 11 Date: 4/23/09 Cisco Application Networking Manager helps you configure class maps and policy maps to provide a global level of classification for filtering traffic received by or passing through
The following topics describe how to manage various policies on the Firepower Management Center:
 The following topics describe how to manage various policies on the Firepower Management Center: Policy Deployment, page 1 Policy Comparison, page 11 Policy Reports, page 12 Out-of-Date Policies, page
The following topics describe how to manage various policies on the Firepower Management Center: Policy Deployment, page 1 Policy Comparison, page 11 Policy Reports, page 12 Out-of-Date Policies, page
Corrigendum 3. Tender Number: 10/ dated
 (A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
(A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
Introduction to Networking
 Introduction to Networking Chapters 1 and 2 Outline Computer Network Fundamentals Defining a Network Networks Defined by Geography Networks Defined by Topology Networks Defined by Resource Location OSI
Introduction to Networking Chapters 1 and 2 Outline Computer Network Fundamentals Defining a Network Networks Defined by Geography Networks Defined by Topology Networks Defined by Resource Location OSI
BIG-IQ Centralized Management: ADC. Version 5.0
 BIG-IQ Centralized Management: ADC Version 5.0 Table of Contents Table of Contents BIG-IQ Application Delivery Controller: Overview...5 What is Application Delivery Controller?...5 Managing Device Resources...7
BIG-IQ Centralized Management: ADC Version 5.0 Table of Contents Table of Contents BIG-IQ Application Delivery Controller: Overview...5 What is Application Delivery Controller?...5 Managing Device Resources...7
CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols
 CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Objectives Functions of the three upper OSI model layers, network services
CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Objectives Functions of the three upper OSI model layers, network services
Test Accredited Configuration Engineer (ACE) Exam PAN OS 6.0 Version
 Test Accredited Configuration Engineer (ACE) Exam PAN OS 6.0 Version ACE Exam Question 1 of 50. Which of the following statements is NOT True regarding a Decryption Mirror interface? Supports SSL outbound
Test Accredited Configuration Engineer (ACE) Exam PAN OS 6.0 Version ACE Exam Question 1 of 50. Which of the following statements is NOT True regarding a Decryption Mirror interface? Supports SSL outbound
