Multiple Type Passwords to Overcome Online Guessing Attacks
|
|
|
- Horatio Hicks
- 5 years ago
- Views:
Transcription
1 Multiple Type Passwords to Overcome Online Guessing Attacks R. Manoj Kumar, M. Ragulvignesh, N. Sunil, M. Anu PG Scholar, Assistant Professor, PG Scholar, PG Scholar PPG IT, PPG IT, PPG IT, PPG IT ABSTRACT--- Today security issues square measure on the increase all told areas like banks, governmental applications, health care business, military organization, instructional establishments, etc. Government organizations square measure setting standards, passing laws and forcing organizations and agencies to fits these standards with non-compliance being met with wide-ranging consequences. There square measure many problems once it involves security issues in these various and ranging industries with one common weak link being passwords. Most systems nowadays deem static passwords to verify the user s identity. However, such passwords escort major management security issues. Users tend to use easy-toguess passwords, use identical Arcanum in multiple accounts, write the passwords or store them on their machines, etc. what is more, hackers have the choice of victimization several techniques to steal passwords like shoulder aquatics, snooping, sniffing, guessing, many correct methods for victimization passwords are planned. However they didn t meet the company s security issues. 2 issue authentication victimization devices like tokens and ATM cards are planned to unravel the arcanum drawback and have shown to be tough to hack. Two issue authentications may be a mechanism that implements two issues thus thought of stronger and safer than the historically enforced one factor authentication system. Retreating cash from associate ATM machine utilizes two issue authentications. Index Terms--- Password guessing, snooping attack, Authentication, MD5 algorithm. I. INTRODUCTION Over the past few decades of text Arcanum has been adopted because the primary mean of user authentication for websites. Individuals choose their username and text passwords once registering accounts on an internet site. So as to log into the web site with success, users should recall the chosen passwords. Generally, passwordbased user authentication will resist brute force and lexicon attacks if users choose sturdy passwords to produce spare entropy. However, password-based user authentication encompasses a major drawback that humans aren't specialists in memorizing text strings. Thus, most users would select easy-to-remember passwords (i.e., weak passwords) albeit they understand the passwords could be unsafe. Another crucial drawback is that users tend to utilize arcanum s across varied websites indicated that a user reuses a password across completely different websites on the average. arcanum utilize causes users to lose sensitive info hold on in several websites if a hacker compromises one amongst their passwords. The higher than issues square measure caused by the negative influence of 2714
2 human factors. Therefore, it's necessary to require human factors into thought once planning a user authentication protocol. Project proposing a user authentication protocol named o Pass that leverages a user s telephone and short message service (SMS) to stop arcanum stealing and arcanum utilize attacks. Here, it\'s tough to thwart arcanum utilize attacks from any theme wherever the users got to keep in mind that the most reason behind stealing arcanum attacks is once users kind passwords to untrusted public computers. Therefore, the most idea of o Pass is free users from having to recollect or kind any passwords into standard computers for authentication. Not like generic user authentication, o Pass involves a brand new element, the telephone that is employed to get one-time passwords and a brand new channel, SMS that is employed to transmit authentication messages. Anti-malware:- Malware (e.g., key logger) that gathers sensitive info from users, particularly their passwords square measure amazingly common. In o Pass, users square measure able to log into net services while not getting into passwords on their computers. Thus, malware cannot acquire a user s arcanum from untrusted computers. Phishing Protection: Adversaries usually launch phishing attacks to steal users passwords by cheating users once they hook up with solid websites. As mentioned higher, o Pass permits users to with success log into websites while not revealing passwords to computers. Users United Nations agency adopt o Pass square measure bound to face up to phishing attacks. Secure Registration and Recovery: In o Pass, SMS is associate out-of-band communication interface. O Pass cooperates with the telecommunication service supplier (TSP) so as to get the proper phone numbers of internet sites and users severally. SMS aids o Pass in establishing a secure channel for message exchange within the registration and recovery phases. Recovery section is meant to subsume cases wherever a user loses his telephone. With the help of recent SIM cards, o Pass still works on new cell phones. arcanum utilize hindrance and Weak arcanum Avoidance: O-Pass achieves onetime arcanum approach. The telephone mechanically derives completely different passwords for every login. That s to mention, the arcanum is completely different throughout every login. Underneath this approach, users don't have to keep in mind any arcanum for login. They solely keep a protracted term arcanum for accessing their cell phones, and leave the remainder of the work to O- Pass. Telephone Protection: associate resister will steal users cell phones and check out to withstand user authentication. However, the cell phones square measure protected by a long arcanum. The resister cannot impersonate a legal user to login while not being detected. I. PROBLEM STATEMENT The Most systems nowadays deem static passwords to verify the user s identity in on-line dealings; however it's not enforced in mastercard user in on-line transition. By victimization static passwords there's no full authentication and anybody will hack that even. Later there exist some third party organizations wherever they need introduced Tokens. Token may be a hardware device that is provided outwardly to each account holder. By this we have some issues like; price of buying is additional, issuance of token is overhead and therefore the system needs multiple tokens and even these is also lost or purloined. 2715
3 II. User will pay through the mastercard bills by providing the cardboard identification number. She/he doesn't offer any extra info for on-line card payment. PROPOSED SCHEME FOR PASSWORD SECURITY factors victimization mobile phones. The planned technique guarantees that authenticating to services, like on-line banking or ATM machines, is finished in an exceedingly very secure manner. The state-of-art is generating a secret key for every individual user. And that we are victimization OTP (One Time Password) Generation algorithmic program and MD5 to get a secret key. This secret is sent to the account holder s mobile directly victimization the GSM electronic equipment. To get the dynamic arcanum victimization the non-public info of the cardboard holder and therefore the current date, day, time and is send to the client and therefore the secret is valid for the short period of 3 minutes. Implementation of project is predicated on the GPRS techniques. With facilitate of the GPRS technique we will offer quicker authentication. A image of o Pass is additionally enforced to live its performance. The common time spent on registration and login is severally. per the result, SMS delay ought to be scale back the entire execution time. The delay may be shorter by victimization advanced devices. Consequently, all of them united o Pass is safer than the first login system. Certainly, a number of the participants like o Pass to the first system. Then the requirement for one thing safer alongside being user friendly is needed. This is often wherever Image based mostly Authentication (IBA) comes into play. Associate IBA encapsulated in Kerberos Protocol, Version 5, and provides purchasers a totally distinctive and secured authentication tools. This technique of implementing involves two authentication Fig 1: Image Authentication System The planned system involves employing a movable as a computer code token for only once arcanum generation. The deals with another necessary half within the security of IBA - the choice of pictures in a picture set and generation of image set itself. Image set may be a assortment of n pictures organized into r rows and c columns. The protection of the systems is often compromised if we tend to choose correct pictures for the image set. A user is often to recollect his image arcanum simply. Another necessary side regarding image set is however these pictures square measure organized once conferred to a user A random show of pictures at intervals a picture set i.e. at intervals a picture set, pictures square measure organized willynilly and their position is not any wherever associated with previous image set that was generated. By doing this, the system protects itself from several security attacks (to be mentioned later) particularly from associate snooper trying from behind. 2716
4 III. ARCHITECTURE OF PROPOSED SYSTEM The customers use a private arcanum to substantiate his identity and defend his/her card once the cardboard is employed on the web, providing bigger support and security. Dynamic pass code authentication is one answer that uses the supplementary security of credit cards to supply higher protection against on-line fraud. registration SMS with AES-CBC. The TSP and therefore the server can establish associate SSL tunnel to guard the communication. SERVER Server Application Reques t/reply Internet Request /reply Client Client System GSM Client Mobile Fig 2: System Architecture Design IV. REGISTRATION PHASE The aim of this section is to permit a user and a server to barter a shared secret to manifest succeeding logins for this user. The user begins by gap the o Pass program put in on her telephone she enters IDU (account id she prefers) and IDs (usually the web site universal resource locator or domain name) to the program. The mobile program sends account id and universal resource locator to the telecommunication service supplier (TSP) through a 3G association to create a call for participation of registration. Once the TSP received the account id and therefore the universal resource locator, it will trace the user s sign supported user s SIM card. The TSP conjointly plays the role of third-party to distribute a shared key between the user and therefore the server. The shared secret is wont to cipher the Fig 3: DFD-Registration Phase Then the TSP forwards account id and assigns server. Server can generate the corresponding info for this account and reply a response, together with server s identity ID, a random seed, and server s sign. The TSP then forwards id, and a shared key to the user s telephone. Once reception of the response is finished, the user continues to setup a long arcanum together with her telephone. V. LOGIN PHASE The login section begins once the user sends a call for participation to the server through associate untrusted browser 2717
5 (on a kiosk). The user uses her telephone to supply a one-time arcanum, e.g. associated deliver necessary info encrypted with to server via an SMS message. Supported pre shared secret certification, server will verify and manifest user. The detail flows of the login section. The protocol starts once user needs to log into her favorite net server (already registered). However, begins the login procedure by accessing the specified web site via a browser on associate world organization trustworthy booth. The browser sends a call for participation to with account IDs. Next, server provides the ID and a contemporary time being to the browser. Meanwhile, this message is forwarded to the telephone through GSM electronic equipment. Once reception of the message, the telephone inquiries connected info from its info via IDs, which incorporates server s sign and different parameters. Successive step is promoting a dialog for her long arcanum. Secret shared certification will regenerate by inputting the proper on the telephone. legitimate; otherwise, the server can reject this login request. Upon productive verification, the server sends back a hit message through the web, if the user is with success log into the server. VI. RECOVERY PHASE Recovery section is selected for a few specific conditions; as an example, a user might lose her telephone. The protocol is ready to recover opass setting on her new telephone forward she still uses identical sign (apply a brand new SIM card with recent phone number). Once user installs the opass program on her new telephone, she will launch the program to send a recovery request together with her account ID and requested server ID to predefined TSP through a 3G association. As mentioned before this ID name or universal resource locator link of server. Kind of like registration, TSP will trace her sign supported her SIM card associated forward her account ID and therefore the server through an SSL tunnel. Once server receives the request, probes the account info in its info to substantiate if account is registered. If account ID exists, the knowledge wont to reason the key certification are fetched and be sent back to the user. Fig 4: DFD- Login Phase The one-time arcanum for current login is recomputed if the received equals the antecedently generated, the user is This recovery section includes all necessary components for generating successive one-time passwords to the user. Once the mobile program receives the message, like registration, it forces the user to enter her long arcanum to breed the proper one-time arcanum. throughout the last step, the user s telephone encrypts the key certification and server time being to a cipher text. 2718
6 Fig 5: DFD- Recovery Phase The recovery SMS message is delivered back to the server for checking. Similarly, the server computers and decrypts this message to make sure that user is already recovered. At now, her new telephone is recovered and prepared to perform more logins. For successive login, one-time Arcanum is used for user authentication. VII. MD5 ALGORITHM MD5 is associate algorithmic program that's wont to verify knowledge integrity through the creation of a 128-bit message digest from knowledge input (which is also a message of any length) that\'s claimed to be as distinctive thereto specific knowledge as a fingerprint is to the particular individual. MD5 is that the third message digest algorithmic program created by Rivest. All 3 (the others square measure MD2 and MD4) have similar structures, however MD2 was optimized for 8-bit machines, as compared with the 2 later formulas, that square measure optimized for 32-bit machines. The MD5 algorithmic program is associate extension of MD4 that the literary criticism found to be quick, however presumably conditionally secure. As compared, MD5 isn't quite as quick because the MD4 algorithmic program, however offers rather more assurance of knowledge security The MD5 Message-Digest algorithmic program may be a wide used scientific discipline hash operate that produces a 128-bit (16-byte) hash worth. per RFC 1321, MD5 has been used in a very large choice of security applications, and is additionally normally wont to check knowledge integrity. However, it's been shown that MD5 isn't collision resistant; in and of itself, MD5 isn't appropriate for applications like SSL certificates or digital signatures that deem this property. An MD5 hash is often expressed as a 32-digit positional representation system variety. MD5 was designed by West Chadic Rivest in 1991 to interchange associate earlier hash functionmd4, a flaw was found with the planning of MD5. whereas it absolutely was not a clearly fatal weakness, cryptographers began recommending the employment of different algorithms, such as SHA-1 (which has since been found conjointly to be vulnerable), additional serious flaws were discovered, creating more use of the algorithmic program for security functions questionable; specifically, a gaggle of researchers represented the way to produce a try of files that share identical MD5 substantiation. More advances were created in breaking MD5 may be a cluster of researchers used this system to pretend SSL certificate validity. 2719
7 MD5 (Message-Digest algorithmic program 5) may be a wide used scientific discipline hash operate with a 128-bit hash worth per RFC 1321, MD5 is one in a very series of message digest algorithms designed by academic Ronald Rivest of university (Rivest, 1994). Nowadays MD5 has been used in a very large choice of security applications, and is additionally normally wont to check the integrity of files. Fig 6: MD5 Operation MD5 is dead fine answer for security thinking, jointly Java developer, we tend to typically got to take over or cryptography to md5 secret writing, the md5 secret writing is extremely sophisticated and to not simple implement. Ideally, the quality edition of Java has extremely come with MD5 support in-built. According to Java specification category support applications the practicality of a message digest algorithmic program, like MD5 or SHA. it\'s outlined within the java security package. first off you wish some string manipulation to show the plain text into computer memory unit array. This is often going simple simply use technique get bytes() of sophistication string. The digest is then updated from the computer memory units from the byte array and a hash computation is conducted upon them. VIII. CONCLUSION A user authentication protocol named opass that leverages cell phones and SMS to thwart arcanum stealing and arcanum utilize attacks. We tend to assume that every web site possesses a singular sign. We tend to conjointly assume that a telecommunication service supplier participates within the registration and recovery phases. The planning principle of opass is to eliminate the negative influence of human factors the maximum amount as attainable. Through opass, every user solely has to keep in mind a long arcanum that has been wont to defend her cell. Compared with previous schemes, opass is that the initial user authentication protocol to stop arcanum stealing (i.e., phishing, keylogger, and malware) and arcanum utilize attacks at the same time. The explanation is that opass adopts the one-time arcanum approach to make sure independence between every login. They will recover our opass system with reissued SIM cards and long passwords. A image of opass is additionally enforced to live its performance. The common time spent on registration and login is severally. As per the result, SMS delay occupies quite the entire execution time. The delay may be shorter by victimization advanced devices. Besides, the performance of login of o Pass is healthier than graphical arcanum schemes, as an example, Pass faces. The login time of Pass faces is from that is longer than o Pass. Therefore, we tend to believe o Pass is appropriate and reliable for users. To investigate o Pass s usability, we tend to invited twenty four participants to conduct the user study. Most participants might simply operate all procedures of the o Pass system. The login success rate is high, aside from a couple of writing errors. Consequently, all of them united o Pass is safer than the first login system. Certainly, a number of the participants like o Pass to the first system. 2720
8 IX. REFERENCES [1] S. Chiasson, A. Forget, E. Stobert, P. C. van Oorschot, and R. Biddle, Multiple password interference in text passwords and click-based graphical passwords, in CCS 09: Proc. 16th ACM Conf. ComputerCommunications Security, New York, 2009, pp , ACM. [2] S. Chiasson, R. Biddle, and P. C. van Oorschot, A second look at the usability of click-based graphical passwords, in SOUPS 07: Proc. 3 rd Symp. Usable Privacy Security, New York, 2007, pp. 1 12, ACM. [3] R. Dhamija, J. D. Tygar, andm. Hearst, Why phishing works, in CHI 06: Proc. SIGCHI Conf. Human Factors Computing Systems, NewYork, 2006, pp , ACM. [4] K. M. Everitt, T. Bragin, J. Fogarty, and T. Kohno, A comprehensive study of frequency, interference, and training of multiple graphical passwords, in CHI 09: Proc. 27th Int. Conf. Human Factors ComputingSystems, New York, 2009, pp , ACM. [5] D. Florencio and C. Herley, A large-scale study of web password habits, in WWW 07: Proc. 16th Int. Conf. World Wide Web., NewYork, 2007, pp , ACM. [6] S. Garriss, R. Cáceres, S. Berger, R. Sailer, L. van Doorn, and X. Zhang, Trustworthy and personalized computing on public kiosks, in Proc. 6th Int. Conf. Mobile Systems, Applications Services, 2008, pp , ACM. [7] H. Gilbert and H. Handschuh, Security analysis of SHA-256 and sisters, in Selected Areas Cryptography, 2003, pp , Springer. [8] J.A. Halderman, B. Waters, and E. W. Felten, Aconvenient method securely managing passwords, in WWW 05: Proc. 14th Int. Conf.World Wide Web, New York, 2005, pp , ACM. [9] T. Holz, M. Engelberth, and F. Freiling, Learning more about the underground economy:acase-study of keyloggers and dropzones, Proc.Computer Security ESORICS 2009, pp. 1 18, [10] C.Karlof,U. Shankar, J. D.Tygar, andd.wagner, Dynamic pharming attacks and locked same-origin policies for web browsers, in CCS 07:Proc. 14th ACMConf. Computer Communications Security, NewYork, 2007, pp , ACM. [11] L. Lamport, Password authentication with insecure communication, Commun. ACM, vol- 24, pp , Nov [12] B. Parno, C. Kuo, and A. Perrig, Phoolproof phishing prevention, Financial Cryptography Data Security, pp. 1 19, [13] B. Pinkas and T. Sander, Securing passwords against dictionary attacks, in CCS 02: Proc. 9th ACM Conf. Computer Communications Security, New York, 2002, pp , ACM.[14].N. Provos, D. Mcnamee, P. Mavrommatis, K. Wang, and N. Modadugu, The ghost in the browser: Analysis of webbasedmalware, in Proc. 1st Conf. Workshop Hot Topics in Understanding Botnets, Berkeley, CA, [15] J. Thorpe and P. C. van Oorschot, Graphical dictionaries and thememorable space of graphical passwords, in SSYM 04: Proc. 13th Conf.USENIX Security Symp., Berkeley, CA, 2004, pp , USENIX Association. [16] P. van Oorschot, A. Salehi-Abari, and J. Thorpe, Purely automated attacks on passpoints-style graphical passwords, IEEE Trans. InformationForensics Security, vol. 5, no. 3, pp , Sep [17] S. Wiedenbeck, J. Waters, L. Sobrado, and J.- C. Birget, Design and evaluation of a shoulder-surfing resistant graphical password scheme, in AVI 06: Proc. Working Conf. Advanced Visual Interfaces, New York, 2006, pp , ACM. [18] K.-P. Yee and K. Sitaker, Passpet: Convenient password management and phishing protection, in SOUPS 06: Proc. 2nd Symp. Usable PrivacySecurity, New York, 2006, pp , ACM. 2721
User Authentication Protocol
 opass: A User Authentication Protocol Sao Vikram B., Gore Vishwanath P., Sankhe Bhakti A., Rananaware Rahul C., ABSTRACT Password security is significant for user authentication on small networking system
opass: A User Authentication Protocol Sao Vikram B., Gore Vishwanath P., Sankhe Bhakti A., Rananaware Rahul C., ABSTRACT Password security is significant for user authentication on small networking system
SECURED PASSWORD MANAGEMENT TECHNIQUE USING ONE-TIME PASSWORD PROTOCOL IN SMARTPHONE
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 3, March 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 3, March 2014,
Improved Password Authentication System against Password attacks for web Applications
 Improved Password Authentication System against Password attacks for web Applications Vaishnavi Yalamanchili, Department of Computer Science & Engineering, Gudlavalleru Engineering College, Gudlavalleru,
Improved Password Authentication System against Password attacks for web Applications Vaishnavi Yalamanchili, Department of Computer Science & Engineering, Gudlavalleru Engineering College, Gudlavalleru,
Enhancing Performance of User Authentication Protocol with Resist to Password Reuse Attacks
 Enhancing Performance of User Authentication Protocol with Resist to Password Reuse Attacks 1, Ms. R.R.Karthiga, 2, Mr.K.Aravindhan, 1, Final year, M.E/CSE, SNS College of Engineering 2, Asst Professor/CSE,
Enhancing Performance of User Authentication Protocol with Resist to Password Reuse Attacks 1, Ms. R.R.Karthiga, 2, Mr.K.Aravindhan, 1, Final year, M.E/CSE, SNS College of Engineering 2, Asst Professor/CSE,
Defenses against Large Scale Online Password Guessing by Using Persuasive Cued Click Points
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 2, Issue. 4, April 2013,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 2, Issue. 4, April 2013,
Cued Click Point Technique for Graphical Password Authentication
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Security Enhancement Using SCTP against Password Stealing in Multi-Homed Networks P.Venkadesh, S.V.Rajalakshmi, S.V.Divya
 Security Enhancement Using SCTP against Password Stealing in Multi-Homed Networks P.Venkadesh, S.V.Rajalakshmi, S.V.Divya Abstract SCTP is a young transport layer protocol. It is designed for transferring
Security Enhancement Using SCTP against Password Stealing in Multi-Homed Networks P.Venkadesh, S.V.Rajalakshmi, S.V.Divya Abstract SCTP is a young transport layer protocol. It is designed for transferring
KNOWLEDGE BASED AUTHENTICATION MECHANISM FOR SECURED DATA TRANSFER
 KNOWLEDGE BASED AUTHENTICATION MECHANISM FOR SECURED DATA TRANSFER R.T.Narmadha1, R.T.Nivetha2, M.Roobia Fathima 2, P.Vijayalakshmi 2 1 Department of Information Technology, Info Institute of Engineering,
KNOWLEDGE BASED AUTHENTICATION MECHANISM FOR SECURED DATA TRANSFER R.T.Narmadha1, R.T.Nivetha2, M.Roobia Fathima 2, P.Vijayalakshmi 2 1 Department of Information Technology, Info Institute of Engineering,
ISSN: (Online) Volume 2, Issue 2, February 2014 International Journal of Advance Research in Computer Science and Management Studies
 ISSN: 2321-7782 (Online) Volume 2, Issue 2, February 2014 International Journal of Advance Research in Computer Science and Management Studies Research Article / Paper / Case Study Available online at:
ISSN: 2321-7782 (Online) Volume 2, Issue 2, February 2014 International Journal of Advance Research in Computer Science and Management Studies Research Article / Paper / Case Study Available online at:
International Journal of Emerging Technology in Computer Science & Electronics (IJETCSE) ISSN: Volume 14 Issue 2 APRIL 2015
 Persuasive Cued Click Point Authentication Mechanism with Sound Signature MOUNESHWAR KANAMADI 1,AMIT SAWANT 2,JAMDADE MARUTI 3,4 MEGHARANI BAMBUGADE, 5 ROKADE KOMAL 1 Department of CSE, Ashokrao Mane Group
Persuasive Cued Click Point Authentication Mechanism with Sound Signature MOUNESHWAR KANAMADI 1,AMIT SAWANT 2,JAMDADE MARUTI 3,4 MEGHARANI BAMBUGADE, 5 ROKADE KOMAL 1 Department of CSE, Ashokrao Mane Group
Usable Privacy and Security, Fall 2011 Nov. 10, 2011
 Usable Privacy and Security, Fall 2011 Nov. 10, 2011 YoungSeok Yoon (youngseok@cs.cmu.edu) Institute for Software Research School of Computer Science Carnegie Mellon University picture/photo based vs.
Usable Privacy and Security, Fall 2011 Nov. 10, 2011 YoungSeok Yoon (youngseok@cs.cmu.edu) Institute for Software Research School of Computer Science Carnegie Mellon University picture/photo based vs.
SHOULDER SURFING ATTACK PREVENTION USING COLOR PASS METHOD
 SHOULDER SURFING ATTACK PREVENTION USING COLOR PASS METHOD Bagade Om, Sonawane Anuja, Patil Akash, Patil Yogita, Maurya Jagruti Department of Computer Engineering Shram sadhana trust s college of engineering
SHOULDER SURFING ATTACK PREVENTION USING COLOR PASS METHOD Bagade Om, Sonawane Anuja, Patil Akash, Patil Yogita, Maurya Jagruti Department of Computer Engineering Shram sadhana trust s college of engineering
Using a Personal Device to Strengthen Password Authentication from an Untrusted Computer
 Financial Cryptography - Feb 13, 2007 Using a Personal Device to Strengthen Password Authentication from an Untrusted Computer Mohammad Mannan and Paul C. van Oorschot Digital Security Group Carleton University,
Financial Cryptography - Feb 13, 2007 Using a Personal Device to Strengthen Password Authentication from an Untrusted Computer Mohammad Mannan and Paul C. van Oorschot Digital Security Group Carleton University,
MODULE NO.28: Password Cracking
 SUBJECT Paper No. and Title Module No. and Title Module Tag PAPER No. 16: Digital Forensics MODULE No. 28: Password Cracking FSC_P16_M28 TABLE OF CONTENTS 1. Learning Outcomes 2. Introduction 3. Nature
SUBJECT Paper No. and Title Module No. and Title Module Tag PAPER No. 16: Digital Forensics MODULE No. 28: Password Cracking FSC_P16_M28 TABLE OF CONTENTS 1. Learning Outcomes 2. Introduction 3. Nature
MULTI-FACTOR AUTHENTICATION USING GRAPHICAL PASSWORDS THROUGH HANDHELD DEVICE
 MULTI-FACTOR AUTHENTICATION USING GRAPHICAL PASSWORDS THROUGH HANDHELD DEVICE P.Shyam Sunder 1, Ballikonda Sai Chaitanya 2, D.Vijay Kumar 3, P.Satya Shekar Varma 4 1,2,4 Department of Computer Science
MULTI-FACTOR AUTHENTICATION USING GRAPHICAL PASSWORDS THROUGH HANDHELD DEVICE P.Shyam Sunder 1, Ballikonda Sai Chaitanya 2, D.Vijay Kumar 3, P.Satya Shekar Varma 4 1,2,4 Department of Computer Science
Authentication schemes for session password using color and special characters
 Authentication schemes for session password using color and special characters Rohit Jagtap1, a, Vaibhav Ahirrao2,b Vinayak Kadam3,c Nilesh Aher4 1.Department of Computer Engineering, 2 Department of Computer
Authentication schemes for session password using color and special characters Rohit Jagtap1, a, Vaibhav Ahirrao2,b Vinayak Kadam3,c Nilesh Aher4 1.Department of Computer Engineering, 2 Department of Computer
Chapter 1 Protecting Financial Institutions from Brute-Force Attacks
 Chapter 1 Protecting Financial Institutions from Brute-Force Attacks Cormac Herley and Dinei Florêncio Abstract We examine the problem of protecting online banking accounts from password brute-forcing
Chapter 1 Protecting Financial Institutions from Brute-Force Attacks Cormac Herley and Dinei Florêncio Abstract We examine the problem of protecting online banking accounts from password brute-forcing
Graphical Password to Increase the Capacity of Alphanumeric Password
 Graphical Password to Increase the Capacity of Alphanumeric Password Gaddam Ramu Computer Science & Engineering. S.R.Engineering College, Warangal, Telangana, India. Goje Roopa(Asst.Prof) Computer Science
Graphical Password to Increase the Capacity of Alphanumeric Password Gaddam Ramu Computer Science & Engineering. S.R.Engineering College, Warangal, Telangana, India. Goje Roopa(Asst.Prof) Computer Science
Divide and Conquer Approach for Solving Security and Usability Conflict in User Authentication
 Divide and Conquer Approach for Solving Security and Usability Conflict in User Authentication Shah Zaman Nizamani Waqas Ali Sahito Shafique Awan Department of IT Department of IT Department of Computer
Divide and Conquer Approach for Solving Security and Usability Conflict in User Authentication Shah Zaman Nizamani Waqas Ali Sahito Shafique Awan Department of IT Department of IT Department of Computer
DESIGN, IMPLEMENTATION AND EVALUATION OF A KNOWLEDGE BASED AUTHENTICATION SCHEME UPON COMPELLING PLAIT CLICKS
 http:// DESIGN, IMPLEMENTATION AND EVALUATION OF A KNOWLEDGE BASED AUTHENTICATION SCHEME UPON COMPELLING PLAIT CLICKS Chalichima Harshitha 1, Devika Rani 2 1 Pursuing M.tech (CSE), 2 Assistant professor
http:// DESIGN, IMPLEMENTATION AND EVALUATION OF A KNOWLEDGE BASED AUTHENTICATION SCHEME UPON COMPELLING PLAIT CLICKS Chalichima Harshitha 1, Devika Rani 2 1 Pursuing M.tech (CSE), 2 Assistant professor
NETWORK SECURITY - OVERCOME PASSWORD HACKING THROUGH GRAPHICAL PASSWORD AUTHENTICATION
 NETWORK SECURITY - OVERCOME PASSWORD HACKING THROUGH GRAPHICAL PASSWORD AUTHENTICATION P.Kiruthika R.Tamilarasi Department of Computer Applications, Dr.Mahalingam College Of Engineering and Technology,
NETWORK SECURITY - OVERCOME PASSWORD HACKING THROUGH GRAPHICAL PASSWORD AUTHENTICATION P.Kiruthika R.Tamilarasi Department of Computer Applications, Dr.Mahalingam College Of Engineering and Technology,
An efficient and practical solution to secure password-authenticated scheme using smart card
 An efficient and practical solution to secure password-authenticated scheme using smart card R. Deepa 1, R. Prabhu M.Tech 2, PG Research scholor 1, Head of the Department 2 Dept.of Information Technology,
An efficient and practical solution to secure password-authenticated scheme using smart card R. Deepa 1, R. Prabhu M.Tech 2, PG Research scholor 1, Head of the Department 2 Dept.of Information Technology,
Captcha as Textual Passwords with Click Points to Protect Information
 Captcha as Textual Passwords with Click Points to Protect Information Sandeep Kumar Vengala Computer Science & Engineering. S.R.Engineering College, Warangal, Telangana, India. Goje Roopa(Asst.Prof) Computer
Captcha as Textual Passwords with Click Points to Protect Information Sandeep Kumar Vengala Computer Science & Engineering. S.R.Engineering College, Warangal, Telangana, India. Goje Roopa(Asst.Prof) Computer
3LAS (Three Level Authentication Scheme)
 3LAS (Three Level Authentication Scheme) Kunal Mulwani 1, Saurabh Naik 2, Navinkumar Gurnani 3, Dr. Nupur Giri 4, Prof. Sharmila Sengupta 5 1, 2,3,4,5 Vivekanand Education Society's Institute of Technology,
3LAS (Three Level Authentication Scheme) Kunal Mulwani 1, Saurabh Naik 2, Navinkumar Gurnani 3, Dr. Nupur Giri 4, Prof. Sharmila Sengupta 5 1, 2,3,4,5 Vivekanand Education Society's Institute of Technology,
Authentication Methods
 CERT-EU Security Whitepaper 16-003 Authentication Methods D.Antoniou, K.Socha ver. 1.0 20/12/2016 TLP: WHITE 1 Authentication Lately, protecting data has become increasingly difficult task. Cyber-attacks
CERT-EU Security Whitepaper 16-003 Authentication Methods D.Antoniou, K.Socha ver. 1.0 20/12/2016 TLP: WHITE 1 Authentication Lately, protecting data has become increasingly difficult task. Cyber-attacks
Graphical User Authentication Using Random Codes
 Graphical User Authentication Using Random Codes Mr.D.S.Gawande 1, Manisha P. Thote 2, Madhavi M. Jangam 3, Payal P. Khonde 4, Payal R. Katre 5, Rohini V. Tiwade 6 1Assistant Professor, Computer Science
Graphical User Authentication Using Random Codes Mr.D.S.Gawande 1, Manisha P. Thote 2, Madhavi M. Jangam 3, Payal P. Khonde 4, Payal R. Katre 5, Rohini V. Tiwade 6 1Assistant Professor, Computer Science
Lecture 3 - Passwords and Authentication
 CSE497b Introduction to Computer and Network Security - Spring 2007 - Professor Jaeger Lecture 3 - Passwords and Authentication CSE497b - Spring 2007 Introduction Computer and Network Security Professor
CSE497b Introduction to Computer and Network Security - Spring 2007 - Professor Jaeger Lecture 3 - Passwords and Authentication CSE497b - Spring 2007 Introduction Computer and Network Security Professor
A New Conditional Key based Authentication for Secure Shopping
 A New Conditional Key based Authentication for Secure Shopping Dr. A.V. Senthil Kumar 1, J. Thiyagarajan 2 Head and Associate Professor, Department of Computer Applications, Hindusthan College of arts
A New Conditional Key based Authentication for Secure Shopping Dr. A.V. Senthil Kumar 1, J. Thiyagarajan 2 Head and Associate Professor, Department of Computer Applications, Hindusthan College of arts
Security Awareness. Chapter 2 Personal Security
 Security Awareness Chapter 2 Personal Security Objectives After completing this chapter, you should be able to do the following: Define what makes a weak password Describe the attacks against passwords
Security Awareness Chapter 2 Personal Security Objectives After completing this chapter, you should be able to do the following: Define what makes a weak password Describe the attacks against passwords
Introduction to Security and User Authentication
 Introduction to Security and User Authentication Brad Karp UCL Computer Science CS GZ03 / M030 14 th November 2016 Topics We ll Cover User login authentication (local and remote) Cryptographic primitives,
Introduction to Security and User Authentication Brad Karp UCL Computer Science CS GZ03 / M030 14 th November 2016 Topics We ll Cover User login authentication (local and remote) Cryptographic primitives,
KNOWLEDGE BASED AUTHENTICATION SYSTEM DESIGN BASED ON PERSUASIVE CUED CLICK POINTS
 http:// KNOWLEDGE BASED AUTHENTICATION SYSTEM DESIGN BASED ON PERSUASIVE CUED CLICK POINTS G Anil Kumar 1, K Devika Rani 2 1 Pursuing M.tech (CSE), 2 Assistant professor (CSE), Nalanda Institute of Engineering
http:// KNOWLEDGE BASED AUTHENTICATION SYSTEM DESIGN BASED ON PERSUASIVE CUED CLICK POINTS G Anil Kumar 1, K Devika Rani 2 1 Pursuing M.tech (CSE), 2 Assistant professor (CSE), Nalanda Institute of Engineering
key distribution requirements for public key algorithms asymmetric (or public) key algorithms
 topics: cis3.2 electronic commerce 24 april 2006 lecture # 22 internet security (part 2) finish from last time: symmetric (single key) and asymmetric (public key) methods different cryptographic systems
topics: cis3.2 electronic commerce 24 april 2006 lecture # 22 internet security (part 2) finish from last time: symmetric (single key) and asymmetric (public key) methods different cryptographic systems
Authentication Using Grid-Based Authentication Scheme and Graphical Password
 Authentication Using Grid-Based Authentication Scheme and Graphical Password Vijayshri D. Vaidya 1 Department of Computer engineering SND COE & RC Yeola, India Imaran R. Shaikh 2 Department of Computer
Authentication Using Grid-Based Authentication Scheme and Graphical Password Vijayshri D. Vaidya 1 Department of Computer engineering SND COE & RC Yeola, India Imaran R. Shaikh 2 Department of Computer
Network Working Group Request for Comments: 1984 Category: Informational August 1996
 Network Working Group IAB Request for Comments: 1984 IESG Category: Informational August 1996 IAB and IESG Statement on Cryptographic Technology and the Internet Status of This Memo This memo provides
Network Working Group IAB Request for Comments: 1984 IESG Category: Informational August 1996 IAB and IESG Statement on Cryptographic Technology and the Internet Status of This Memo This memo provides
A simple approach of Peer-to-Peer E-Cash system
 A simple approach of Peer-to-Peer E-Cash system Mr. Dharamvir, Mr. Rabinarayan Panda Asst. Professor, Dept. of MCA, The Oxford College of Engineering Bangalore, India. Abstract-With the popularization
A simple approach of Peer-to-Peer E-Cash system Mr. Dharamvir, Mr. Rabinarayan Panda Asst. Professor, Dept. of MCA, The Oxford College of Engineering Bangalore, India. Abstract-With the popularization
The Design of an Anonymous and a Fair Novel E-cash System
 International Journal of Information & Computation Technology. ISSN 0974-2239 Volume 2, Number 2 (2012), pp. 103-109 International Research Publications House http://www. ripublication.com The Design of
International Journal of Information & Computation Technology. ISSN 0974-2239 Volume 2, Number 2 (2012), pp. 103-109 International Research Publications House http://www. ripublication.com The Design of
International Journal of Advance Engineering and Research Development. Retrieval Of information Using QR code
 Scientific Journal of Impact Factor (SJIF): 4.14 International Journal of Advance Engineering and Research Development Volume 3, Issue 12, December -2016 Retrieval Of information Using QR code e-issn (O):
Scientific Journal of Impact Factor (SJIF): 4.14 International Journal of Advance Engineering and Research Development Volume 3, Issue 12, December -2016 Retrieval Of information Using QR code e-issn (O):
Controlling Website Account Information. A recent survey done by Privacy Rights Clearinghouse shows that in the past five years
 Colson 1 Alex Colson Dr. Lunsford Information Security Management 10 July 2007 Controlling Website Account Information A recent survey done by Privacy Rights Clearinghouse shows that in the past five years
Colson 1 Alex Colson Dr. Lunsford Information Security Management 10 July 2007 Controlling Website Account Information A recent survey done by Privacy Rights Clearinghouse shows that in the past five years
Authentication Technology for a Smart eid Infrastructure.
 Authentication Technology for a Smart eid Infrastructure. www.aducid.com One app to access all public and private sector online services. One registration allows users to access all their online accounts
Authentication Technology for a Smart eid Infrastructure. www.aducid.com One app to access all public and private sector online services. One registration allows users to access all their online accounts
International Journal of Advanced Research in Computer Science and Software Engineering
 Volume 3, Issue 8, August 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com An Enhanced Authentication
Volume 3, Issue 8, August 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com An Enhanced Authentication
MULTIPLE GRID BASED GRAPHICAL TEXT PASSWORD AUTHENTICATION
 MULTIPLE GRID BASED GRAPHICAL TEXT PASSWORD AUTHENTICATION Vinothini T 1, Rajesh I 2, Kirupa Rani D 3 1 PG Scholar, Dept of CSE, Knowledge Institute of Technology, Salem, Tamil Nadu, India 2 Associate
MULTIPLE GRID BASED GRAPHICAL TEXT PASSWORD AUTHENTICATION Vinothini T 1, Rajesh I 2, Kirupa Rani D 3 1 PG Scholar, Dept of CSE, Knowledge Institute of Technology, Salem, Tamil Nadu, India 2 Associate
Lecture 3 - Passwords and Authentication
 Lecture 3 - Passwords and Authentication CMPSC 443 - Spring 2012 Introduction Computer and Network Security Professor Jaeger www.cse.psu.edu/~tjaeger/cse443-s12 What is authentication? Reliably verifying
Lecture 3 - Passwords and Authentication CMPSC 443 - Spring 2012 Introduction Computer and Network Security Professor Jaeger www.cse.psu.edu/~tjaeger/cse443-s12 What is authentication? Reliably verifying
CS 361S - Network Security and Privacy Spring Homework #1
 CS 361S - Network Security and Privacy Spring 2017 Homework #1 Due: 11am CST (in class), February 13, 2017 YOUR NAME: Collaboration policy No collaboration is permitted on this assignment. Any cheating
CS 361S - Network Security and Privacy Spring 2017 Homework #1 Due: 11am CST (in class), February 13, 2017 YOUR NAME: Collaboration policy No collaboration is permitted on this assignment. Any cheating
Thematic Graphical User Authentication: Graphical User Authentication Using Themed Images on Mobile Devices
 Int'l Conf. Security and Management SAM'17 273 Thematic Graphical User Authentication: Graphical User Authentication Using Themed Images on Mobile Devices Joshua Sherfield 1, Cheryl V. Hinds 2 1 Lawrence
Int'l Conf. Security and Management SAM'17 273 Thematic Graphical User Authentication: Graphical User Authentication Using Themed Images on Mobile Devices Joshua Sherfield 1, Cheryl V. Hinds 2 1 Lawrence
Public-key Cryptography: Theory and Practice
 Public-key Cryptography Theory and Practice Department of Computer Science and Engineering Indian Institute of Technology Kharagpur Chapter 1: Overview What is Cryptography? Cryptography is the study of
Public-key Cryptography Theory and Practice Department of Computer Science and Engineering Indian Institute of Technology Kharagpur Chapter 1: Overview What is Cryptography? Cryptography is the study of
Securing Web Accounts Using Graphical Password Authentication through MD5 Algorithm
 Securing Web Accounts Using Graphical Password Authentication through MD5 Algorithm Siddheshwar A. Suratkar Rahul A. Udgirkar Pratik D. Kale Amit A. Shelke Mohsin H. Shaikh Prof. D. C. Dhanwani Prof. CSE,
Securing Web Accounts Using Graphical Password Authentication through MD5 Algorithm Siddheshwar A. Suratkar Rahul A. Udgirkar Pratik D. Kale Amit A. Shelke Mohsin H. Shaikh Prof. D. C. Dhanwani Prof. CSE,
Biometrics problem or solution?
 Biometrics problem or solution? Summary Biometrics are a security approach that offers great promise, but also presents users and implementers with a number of practical problems. Whilst some of these
Biometrics problem or solution? Summary Biometrics are a security approach that offers great promise, but also presents users and implementers with a number of practical problems. Whilst some of these
A SECURE PASSWORD-BASED REMOTE USER AUTHENTICATION SCHEME WITHOUT SMART CARDS
 ISSN 1392 124X INFORMATION TECHNOLOGY AND CONTROL, 2012, Vol.41, No.1 A SECURE PASSWORD-BASED REMOTE USER AUTHENTICATION SCHEME WITHOUT SMART CARDS Bae-Ling Chen 1, Wen-Chung Kuo 2*, Lih-Chyau Wuu 3 1
ISSN 1392 124X INFORMATION TECHNOLOGY AND CONTROL, 2012, Vol.41, No.1 A SECURE PASSWORD-BASED REMOTE USER AUTHENTICATION SCHEME WITHOUT SMART CARDS Bae-Ling Chen 1, Wen-Chung Kuo 2*, Lih-Chyau Wuu 3 1
Network Security Issues and Cryptography
 Network Security Issues and Cryptography PriyaTrivedi 1, Sanya Harneja 2 1 Information Technology, Maharishi Dayanand University Farrukhnagar, Gurgaon, Haryana, India 2 Information Technology, Maharishi
Network Security Issues and Cryptography PriyaTrivedi 1, Sanya Harneja 2 1 Information Technology, Maharishi Dayanand University Farrukhnagar, Gurgaon, Haryana, India 2 Information Technology, Maharishi
Online Banking Security
 Online Banking Security Fabian Alenius Uwe Bauknecht May 17, 2009 Contents 1 Introduction 2 2 Secure Communication 2 2.1 Password authentication..................... 2 2.2 One-time Passwords.......................
Online Banking Security Fabian Alenius Uwe Bauknecht May 17, 2009 Contents 1 Introduction 2 2 Secure Communication 2 2.1 Password authentication..................... 2 2.2 One-time Passwords.......................
Computer Security & Privacy
 Computer Security & Privacy Melissa Winstanley (mwinst@cs.washington.edu) (based on slides by Daniel Halperin) How exploration sessions work You get 1/3 point of extra credit for each session Attendance
Computer Security & Privacy Melissa Winstanley (mwinst@cs.washington.edu) (based on slides by Daniel Halperin) How exploration sessions work You get 1/3 point of extra credit for each session Attendance
A Smart Card Based Authentication Protocol for Strong Passwords
 A Smart Card Based Authentication Protocol for Strong Passwords Chin-Chen Chang 1,2 and Hao-Chuan Tsai 2 1 Department of Computer Science and Information Engineering, Feng Chia University, Taichung, Taiwan,
A Smart Card Based Authentication Protocol for Strong Passwords Chin-Chen Chang 1,2 and Hao-Chuan Tsai 2 1 Department of Computer Science and Information Engineering, Feng Chia University, Taichung, Taiwan,
Smart-card-loss-attack and Improvement of Hsiang et al. s Authentication Scheme
 Smart-card-loss-attack and Improvement of Hsiang et al. s Authentication Scheme Y.. Lee Department of Security Technology and Management WuFeng niversity, hiayi, 653, Taiwan yclee@wfu.edu.tw ABSTRAT Due
Smart-card-loss-attack and Improvement of Hsiang et al. s Authentication Scheme Y.. Lee Department of Security Technology and Management WuFeng niversity, hiayi, 653, Taiwan yclee@wfu.edu.tw ABSTRAT Due
(2½ hours) Total Marks: 75
 (2½ hours) Total Marks: 75 N. B.: (1) All questions are compulsory. (2) Makesuitable assumptions wherever necessary and state the assumptions made. (3) Answers to the same question must be written together.
(2½ hours) Total Marks: 75 N. B.: (1) All questions are compulsory. (2) Makesuitable assumptions wherever necessary and state the assumptions made. (3) Answers to the same question must be written together.
Password Guessing Resistant Protocol
 RESEARCH ARTICLE OPEN ACCESS Password Guessing Resistant Protocol Arya Kumar #1, A. K. Gupta *2 # Student, M.E. Computer, JSCOE, Pune, University of Pune * Associate Professor, JSCOE, Pune, University
RESEARCH ARTICLE OPEN ACCESS Password Guessing Resistant Protocol Arya Kumar #1, A. K. Gupta *2 # Student, M.E. Computer, JSCOE, Pune, University of Pune * Associate Professor, JSCOE, Pune, University
Encryption I. An Introduction
 Encryption I An Introduction Reading List ADO and SQL Server Security A Simple Guide to Cryptography Protecting Private Data with the Cryptography Namespaces Using MD5 to Encrypt Passwords in a Database
Encryption I An Introduction Reading List ADO and SQL Server Security A Simple Guide to Cryptography Protecting Private Data with the Cryptography Namespaces Using MD5 to Encrypt Passwords in a Database
Whitepaper on AuthShield Two Factor Authentication with SAP
 Whitepaper on AuthShield Two Factor Authentication with SAP By AuthShield Labs Pvt. Ltd Table of Contents Table of Contents...2 1.Overview...4 2. Threats to account passwords...5 2.1 Social Engineering
Whitepaper on AuthShield Two Factor Authentication with SAP By AuthShield Labs Pvt. Ltd Table of Contents Table of Contents...2 1.Overview...4 2. Threats to account passwords...5 2.1 Social Engineering
Vidder PrecisionAccess
 Vidder PrecisionAccess Transparent Multi-Factor Authentication June 2015 910 E HAMILTON AVENUE. SUITE 430. CAMPBELL, CA 95008 P: 408.418.0440 F: 408.706.5590 WWW.VIDDER.COM Table of Contents I. Overview...
Vidder PrecisionAccess Transparent Multi-Factor Authentication June 2015 910 E HAMILTON AVENUE. SUITE 430. CAMPBELL, CA 95008 P: 408.418.0440 F: 408.706.5590 WWW.VIDDER.COM Table of Contents I. Overview...
Information Security. message M. fingerprint f = H(M) one-way hash. 4/19/2006 Information Security 1
 Information Security message M one-way hash fingerprint f = H(M) 4/19/2006 Information Security 1 Outline and Reading Digital signatures Definition RSA signature and verification One-way hash functions
Information Security message M one-way hash fingerprint f = H(M) 4/19/2006 Information Security 1 Outline and Reading Digital signatures Definition RSA signature and verification One-way hash functions
CSE 565 Computer Security Fall 2018
 CSE 565 Computer Security Fall 2018 Lecture 9: Authentication Department of Computer Science and Engineering University at Buffalo 1 Lecture Outline Definition of entity authentication Solutions password-based
CSE 565 Computer Security Fall 2018 Lecture 9: Authentication Department of Computer Science and Engineering University at Buffalo 1 Lecture Outline Definition of entity authentication Solutions password-based
Innovative Graphical Passwords using Sequencing and Shuffling Together
 Innovative Graphical Passwords using Sequencing and Shuffling Together Rashmi Wable 1, Dr.Suhas Raut 2 N.K. Orchid College of Engineering and Technology, Solapur ABSTRACT Graphical authentication technology
Innovative Graphical Passwords using Sequencing and Shuffling Together Rashmi Wable 1, Dr.Suhas Raut 2 N.K. Orchid College of Engineering and Technology, Solapur ABSTRACT Graphical authentication technology
CS 161 Computer Security
 Popa & Weaver Fall 2016 CS 161 Computer Security 10/4 Passwords 1 Passwords are widely used for authentication, especially on the web. What practices should be used to make passwords as secure as possible?
Popa & Weaver Fall 2016 CS 161 Computer Security 10/4 Passwords 1 Passwords are widely used for authentication, especially on the web. What practices should be used to make passwords as secure as possible?
Address for Correspondence 1 Associate Professor department o f Computer Engineering BVUCOE, Pune
 Research Article THREE DIMENSIONAL VIRTUAL ENVIRONMENT FOR SECURED AND RELIABLE AUTHENTICATION 1 Gauri Rao, 2 Dr. S.H. Patil Address for Correspondence 1 Associate Professor department o f Computer Engineering
Research Article THREE DIMENSIONAL VIRTUAL ENVIRONMENT FOR SECURED AND RELIABLE AUTHENTICATION 1 Gauri Rao, 2 Dr. S.H. Patil Address for Correspondence 1 Associate Professor department o f Computer Engineering
Introduction...1. Authentication Methods...1. Classes of Attacks on Authentication Mechanisms...4. Security Analysis of Authentication Mechanisms...
 WHITE PAPER A Security Survey of Strong Authentication Technologies Contents Introduction...1 Authentication Methods...1 Classes of Attacks on Authentication Mechanisms...4 Security Analysis of Authentication
WHITE PAPER A Security Survey of Strong Authentication Technologies Contents Introduction...1 Authentication Methods...1 Classes of Attacks on Authentication Mechanisms...4 Security Analysis of Authentication
FAQ: Privacy, Security, and Data Protection at Libraries
 FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
CS 161 Computer Security
 Popa & Wagner Spring 2016 CS 161 Computer Security Midterm 2 Print your name:, (last) (first) I am aware of the Berkeley Campus Code of Student Conduct and acknowledge that academic misconduct will be
Popa & Wagner Spring 2016 CS 161 Computer Security Midterm 2 Print your name:, (last) (first) I am aware of the Berkeley Campus Code of Student Conduct and acknowledge that academic misconduct will be
Secure Data Deduplication with Dynamic Ownership Management in Cloud Storage
 Secure Data Deduplication with Dynamic Ownership Management in Cloud Storage Dr.S.Masood Ahamed 1, N.Mounika 2, N.vasavi 3, M.Vinitha Reddy 4 HOD, Department of Computer Science & Engineering,, Guru Nanak
Secure Data Deduplication with Dynamic Ownership Management in Cloud Storage Dr.S.Masood Ahamed 1, N.Mounika 2, N.vasavi 3, M.Vinitha Reddy 4 HOD, Department of Computer Science & Engineering,, Guru Nanak
Image Password Based Authentication in an Android System
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology ISSN 2320 088X IMPACT FACTOR: 5.258 IJCSMC,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology ISSN 2320 088X IMPACT FACTOR: 5.258 IJCSMC,
Lecture Notes for Chapter 3 System Security
 Lecture Notes for Chapter 3 System Security Digital Signatures: A digital signature is a scheme that is used to simulate the security properties provided by a hand-written signature. It is something which
Lecture Notes for Chapter 3 System Security Digital Signatures: A digital signature is a scheme that is used to simulate the security properties provided by a hand-written signature. It is something which
Multi-factor Authentication Using Mobile Phones
 Multi-factor Authentication Using Mobile Phones Prathamesh S. Dhanorkar 1, Atish R. Jadhav 2, Assistant Professor Shweta B. Barshe 3 1 Department of Computer Engineering, BVCOE, 2 Department of Computer
Multi-factor Authentication Using Mobile Phones Prathamesh S. Dhanorkar 1, Atish R. Jadhav 2, Assistant Professor Shweta B. Barshe 3 1 Department of Computer Engineering, BVCOE, 2 Department of Computer
Computer Security 3/20/18
 Authentication Identification: who are you? Authentication: prove it Computer Security 08. Authentication Authorization: you can do it Protocols such as Kerberos combine all three Paul Krzyzanowski Rutgers
Authentication Identification: who are you? Authentication: prove it Computer Security 08. Authentication Authorization: you can do it Protocols such as Kerberos combine all three Paul Krzyzanowski Rutgers
INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE METHODS FOR REMAINING ANONYMOUS, PRIVATE, AND SECURE WHILE COMMUNICATING, PUBLISHING, BUYING,
 INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE METHODS FOR REMAINING ANONYMOUS, PRIVATE, AND SECURE WHILE COMMUNICATING, PUBLISHING, BUYING, DOWNLOAD EBOOK : INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE
INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE METHODS FOR REMAINING ANONYMOUS, PRIVATE, AND SECURE WHILE COMMUNICATING, PUBLISHING, BUYING, DOWNLOAD EBOOK : INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE
Computer Security. 08. Authentication. Paul Krzyzanowski. Rutgers University. Spring 2018
 Computer Security 08. Authentication Paul Krzyzanowski Rutgers University Spring 2018 1 Authentication Identification: who are you? Authentication: prove it Authorization: you can do it Protocols such
Computer Security 08. Authentication Paul Krzyzanowski Rutgers University Spring 2018 1 Authentication Identification: who are you? Authentication: prove it Authorization: you can do it Protocols such
Minimizing Shoulder Surfing Attack using Text and Color Based Graphical Password Scheme
 Minimizing Shoulder Surfing Attack using Text and Color Based Graphical Password Scheme 1 Prof. S. K. Sonkar, 2 Prof. R. L. Paikrao Computer Engineering Dept. Amrutvahini College of engineering Sangamner,
Minimizing Shoulder Surfing Attack using Text and Color Based Graphical Password Scheme 1 Prof. S. K. Sonkar, 2 Prof. R. L. Paikrao Computer Engineering Dept. Amrutvahini College of engineering Sangamner,
DEFENSES AGAINST LARGE SCALE ONLINE PASSWORD GUESSING ATTACKS BY USING PERSUASIVE CLICK POINTS
 DEFENSES AGAINST LARGE SCALE ONLINE PASSWORD GUESSING ATTACKS BY USING PERSUASIVE CLICK POINTS Abdul Rasheed. Sk 1 Asst. Professor Narasaraopeta Engineering College, Narasaraopet. rasheed4321@gmail.com
DEFENSES AGAINST LARGE SCALE ONLINE PASSWORD GUESSING ATTACKS BY USING PERSUASIVE CLICK POINTS Abdul Rasheed. Sk 1 Asst. Professor Narasaraopeta Engineering College, Narasaraopet. rasheed4321@gmail.com
Graphical User Authentication System An Overview P. Baby Maruthi 1, Dr. K. Sandhya Rani 2
 Graphical User Authentication System An Overview P. Baby Maruthi 1, Dr. K. Sandhya Rani 2 1 Research Scholar: Dept of Computer Science S.P.M.V.V, Tirupati, Andhra Pradesh, India mail2maruthi03@gmail.com
Graphical User Authentication System An Overview P. Baby Maruthi 1, Dr. K. Sandhya Rani 2 1 Research Scholar: Dept of Computer Science S.P.M.V.V, Tirupati, Andhra Pradesh, India mail2maruthi03@gmail.com
Keywords security model, online banking, authentication, biometric, variable tokens
 Volume 4, Issue 11, November 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Authentication
Volume 4, Issue 11, November 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Authentication
A Novel Approaches for Keylogging-Resistant Visual Authentication Protocols
 A Novel Approaches for Keylogging-Resistant Visual Authentication Protocols Prof. Priyanka Mane 1,Prabhakar Avhad 2,Devarsh Khedkar 3 Ravikant Jadhav 4,Abhijit Gogre 5 Genba Sopanrao Moze College of Engineering,
A Novel Approaches for Keylogging-Resistant Visual Authentication Protocols Prof. Priyanka Mane 1,Prabhakar Avhad 2,Devarsh Khedkar 3 Ravikant Jadhav 4,Abhijit Gogre 5 Genba Sopanrao Moze College of Engineering,
PKI Credentialing Handbook
 PKI Credentialing Handbook Contents Introduction...3 Dissecting PKI...4 Components of PKI...6 Digital certificates... 6 Public and private keys... 7 Smart cards... 8 Certificate Authority (CA)... 10 Key
PKI Credentialing Handbook Contents Introduction...3 Dissecting PKI...4 Components of PKI...6 Digital certificates... 6 Public and private keys... 7 Smart cards... 8 Certificate Authority (CA)... 10 Key
The Money Is in the Square Cash Lets Users Funds to Friends
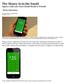 The Money Is in the Email Square Cash Lets Users Email Funds to Friends By: WALTER S. MOSSBERG October 15, 2013 Square now has a service that makes transferring money to a friend as easy as sending them
The Money Is in the Email Square Cash Lets Users Email Funds to Friends By: WALTER S. MOSSBERG October 15, 2013 Square now has a service that makes transferring money to a friend as easy as sending them
A hash function is strongly collision-free if it is computationally infeasible to find different messages M and M such that H(M) = H(M ).
 CA4005: CRYPTOGRAPHY AND SECURITY PROTOCOLS 1 5 5.1 A hash function is an efficient function mapping binary strings of arbitrary length to binary strings of fixed length (e.g. 128 bits), called the hash-value
CA4005: CRYPTOGRAPHY AND SECURITY PROTOCOLS 1 5 5.1 A hash function is an efficient function mapping binary strings of arbitrary length to binary strings of fixed length (e.g. 128 bits), called the hash-value
Give Me Letters 2, 3 and 6! Partial Password Implementations and Attacks
 Give Me Letters 2, 3 and 6! Partial Password Implementations and Attacks David Aspinall, University of Edinburgh, UK Mike Just, Glasgow Caledonian University, UK Financial Cryptography and Data Security,
Give Me Letters 2, 3 and 6! Partial Password Implementations and Attacks David Aspinall, University of Edinburgh, UK Mike Just, Glasgow Caledonian University, UK Financial Cryptography and Data Security,
Web Tap Payment Authentication and Encryption With Zero Customer Effort
 Web Tap Payment Authentication and Encryption With Zero Customer Effort Henry Ng Tap-Card-Pay Systems Corporation, Vancouver BC V5X3Y3, Canada henryng@tapcardpay.com Abstract. We propose a public-key authentication
Web Tap Payment Authentication and Encryption With Zero Customer Effort Henry Ng Tap-Card-Pay Systems Corporation, Vancouver BC V5X3Y3, Canada henryng@tapcardpay.com Abstract. We propose a public-key authentication
===============================================================================
 We have looked at how to use public key crypto (mixed with just the right amount of trust) for a website to authenticate itself to a user's browser. What about when Alice needs to authenticate herself
We have looked at how to use public key crypto (mixed with just the right amount of trust) for a website to authenticate itself to a user's browser. What about when Alice needs to authenticate herself
Protocols II. Computer Security Lecture 12. David Aspinall. 17th February School of Informatics University of Edinburgh
 Protocols II Computer Security Lecture 12 David Aspinall School of Informatics University of Edinburgh 17th February 2011 Outline Introduction Shared-key Authentication Asymmetric authentication protocols
Protocols II Computer Security Lecture 12 David Aspinall School of Informatics University of Edinburgh 17th February 2011 Outline Introduction Shared-key Authentication Asymmetric authentication protocols
Survey Paper on Efficient and Secure Dynamic Auditing Protocol for Data Storage in Cloud
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Key Management. Digital signatures: classical and public key Classic and Public Key exchange. Handwritten Signature
 Key Management Digital signatures: classical and public key Classic and Public Key exchange 1 Handwritten Signature Used everyday in a letter, on a check, sign a contract A signature on a signed paper
Key Management Digital signatures: classical and public key Classic and Public Key exchange 1 Handwritten Signature Used everyday in a letter, on a check, sign a contract A signature on a signed paper
Securing today s identity and transaction systems:! What you need to know! about two-factor authentication!
 Securing today s identity and transaction systems:! What you need to know! about two-factor authentication! 1 Today s Speakers! Alex Doll! CEO OneID Jim Fenton! Chief Security Officer OneID 2 Contents!
Securing today s identity and transaction systems:! What you need to know! about two-factor authentication! 1 Today s Speakers! Alex Doll! CEO OneID Jim Fenton! Chief Security Officer OneID 2 Contents!
Paystar Remittance Suite Tokenless Two-Factor Authentication
 Paystar Remittance Suite Tokenless Two-Factor Authentication Introduction Authentication is the process by which a computer system positively identifies a user It is commonly considered to be one of the
Paystar Remittance Suite Tokenless Two-Factor Authentication Introduction Authentication is the process by which a computer system positively identifies a user It is commonly considered to be one of the
Network Security and Cryptography. 2 September Marking Scheme
 Network Security and Cryptography 2 September 2015 Marking Scheme This marking scheme has been prepared as a guide only to markers. This is not a set of model answers, or the exclusive answers to the questions,
Network Security and Cryptography 2 September 2015 Marking Scheme This marking scheme has been prepared as a guide only to markers. This is not a set of model answers, or the exclusive answers to the questions,
Implementation of Knowledge Based Authentication System Using Persuasive Cued Click Points
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 12, Issue 2 (May. - Jun. 2013), PP 39-46 Implementation of Knowledge Based Authentication System Using Persuasive
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 12, Issue 2 (May. - Jun. 2013), PP 39-46 Implementation of Knowledge Based Authentication System Using Persuasive
Introduction. Controlling Information Systems. Threats to Computerised Information System. Why System are Vulnerable?
 Introduction Controlling Information Systems When computer systems fail to work as required, firms that depend heavily on them experience a serious loss of business function. M7011 Peter Lo 2005 1 M7011
Introduction Controlling Information Systems When computer systems fail to work as required, firms that depend heavily on them experience a serious loss of business function. M7011 Peter Lo 2005 1 M7011
Credit Card Frauds Sept.08, 2016
 Credit Card Frauds Sept.08, 2016 Definitions Credit Card A card allowing the holder to purchasing goods or services on credit Debit Card A card allowing transfer of money from a bank a/c electronically
Credit Card Frauds Sept.08, 2016 Definitions Credit Card A card allowing the holder to purchasing goods or services on credit Debit Card A card allowing transfer of money from a bank a/c electronically
System-Level Failures in Security
 System-Level Failures in Security Non linear offset component (ms) 0.0 0.5 1.0 1.5 2.0 Variable skew De noised Non linear offset Temperature 26.4 26.3 26.2 26.1 26.0 25.9 25.8 Temperature ( C) Fri 11:00
System-Level Failures in Security Non linear offset component (ms) 0.0 0.5 1.0 1.5 2.0 Variable skew De noised Non linear offset Temperature 26.4 26.3 26.2 26.1 26.0 25.9 25.8 Temperature ( C) Fri 11:00
Frequently Asked Questions (FAQ)
 Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
Comparison of ZKP based Authentication Mechanisms for securing the web server
 Comparison of ZKP based Authentication Mechanisms for securing the web server Kayathri Devi D #1, Akilan S S *2 # Department of Information technology, Kamaraj College of Engineering and technology Virudhunagar,
Comparison of ZKP based Authentication Mechanisms for securing the web server Kayathri Devi D #1, Akilan S S *2 # Department of Information technology, Kamaraj College of Engineering and technology Virudhunagar,
DEFENSES AGAINST LARGE SCALE ONLINE PASSWORD GUESSING ATTACKS BY USING PERSUASIVE CLICK POINTS
 DEFENSES AGAINST LARGE SCALE ONLINE PASSWORD GUESSING ATTACKS BY USING PERSUASIVE CLICK POINTS Chippy.T chippyrevathy@gmail.com Dhanalakshmi Srinivasan Engineering College R.Nagendran nanonagendran@gmail.com
DEFENSES AGAINST LARGE SCALE ONLINE PASSWORD GUESSING ATTACKS BY USING PERSUASIVE CLICK POINTS Chippy.T chippyrevathy@gmail.com Dhanalakshmi Srinivasan Engineering College R.Nagendran nanonagendran@gmail.com
ECEN 5022 Cryptography
 Introduction University of Colorado Spring 2008 Historically, cryptography is the science and study of secret writing (Greek: kryptos = hidden, graphein = to write). Modern cryptography also includes such
Introduction University of Colorado Spring 2008 Historically, cryptography is the science and study of secret writing (Greek: kryptos = hidden, graphein = to write). Modern cryptography also includes such
Dashlane Security Whitepaper
 Dashlane Security Whitepaper November 2017 Contents 1. General Security Principles... 2 a. Protection of User Data in Dashlane... 2 b. Local access to User Data... 2 c. Local Data Usage after deciphering...
Dashlane Security Whitepaper November 2017 Contents 1. General Security Principles... 2 a. Protection of User Data in Dashlane... 2 b. Local access to User Data... 2 c. Local Data Usage after deciphering...
Online Threats. This include human using them!
 Online Threats There are many dangers from using the web (and computer in general). One should watch out for malware, automated programs designed to cause harm to you, your data, and your system. You are
Online Threats There are many dangers from using the web (and computer in general). One should watch out for malware, automated programs designed to cause harm to you, your data, and your system. You are
