Abstract Keywords 1. INTRODUCTION
|
|
|
- Kelly Holmes
- 5 years ago
- Views:
Transcription
1 Safe & Secure Ciphertext Policy Attribute Based Encryption To Avoid Suicidal Games nn Entering Whatsapp or Mobile Like Bluewhale Game or Momo Challenge S.Porkodi, ME Final Year Department of Computer Science and Engineering Dr.Sivanthi Aditanar College of Engineering Tiruchendur D.Kesavaraja, Assistant Professor Department of Computer Science and Engineering Dr.Sivanthi Aditanar College of Engineering Tiruchendur Abstract Now-a-days there are lots of application are been used by the people. While using an application, a user s data is to be protected. So encryption is used in many applications when the data is transferred from one place to another. More over in order to register in an application either phone number or id is used commonly and so a single user may have many accounts which cannot be identified. So some hackers use this as advantage and use some application as the medium to give threat and harm to the other users and the main problem is that we cannot find the real culprit as they use some fake information to create the account. In this paper, we propose an encryption algorithm based on user attributes, called ciphertext policy attribute based encryption. With this algorithm in use we can find the culprit who is misusing the application. Also we can add that person to the blacklist and all the accounts associated with that identity can also be blacklisted. Keywords Blacklist, Ciphertext policy attribute based encryption (cp-abe), Data transfer, Security, Whatsapp 1. INTRODUCTION Many application uses encryption for the secure transfer of data from one place to another. End to end encryption is used in whatsapp, when using this photos, videos, voice messages, documents, status updates and calls are secured from falling into wrong hands. Even though now a days, there are lot of hackers using whatsapp as medium to spread malwares via whatsapp to be installed on to the mobile device which in turn sends data from our mobile to the hacker through whatsapp. Even some malware are used to hack the mobile s front camera to get a detailed information, photos and videos of the users. These hackers are hard to find since they use several different numbers and they does not have a unique user Id to be tracked. To avoid these types of hacking, usage of ciphertext policy attribute based encryption can be used. So that when a data is been encrypted and transferred from one user to another only they both can see the actual text and others cannot hack the data from the whatsapp. The same technique can be used in mobile too, which ensures that the data from the mobile can be only seen to the person to whom the data is transferred to. As the CP- ABE encryption uses the attributes of the user to encrypt data only that particular user will have the permission to access the data by matching their attribute. Whereas others who try to hack the datas will not have the attribute of that particular user and thus they cannot get the actual data and it is hard to hack. This algorithm can also be used to deduct the person who is illegally using the applications in a wrong way and we can also blacklist them. As unique Id is an attribute the different accounts using the same identity can also be blacklisted. The main objective of the project is to encrypt user identity and to protect their data and privacy. Then to blacklist the user when the user is doubted to involve in illegal activities, regulators can reveal the identity of the user and blacklist them. This project can also be used in other applications like bitcoin system, ATM system and other systems to protect user s privacy and to track 201
2 the culprit who is trying to steal the user s bitcoins or user s cash. National and International needs BlueWhale Game The Blue whale was a game which was played across over a wide range of nations in One among those nations was India. It was a "game" reportedly consisting of a different series of tasks given by the admin to the users over a 50-day period of time, initially introducing the player to the elements of selfharm and then the final challenge is to make the player to commit suicide. Throughout 2017 the media in India reported several child suicide cases, self-harm and attempted suicide cases linked to be a result of Blue Whale and to the response, the Government of India's Ministry of Electronics and Information Technology requested several internet companies (including Google, Facebook, and Yahoo) to remove all the links which diverts the users to the game. Some commentators blamed the government of creating a moral panic. Indian internet watchdog, the Centre for Internet and Society blamed the coverage of effectively spreading and advertising a "game" for which there was only a little evidence. The Supreme Court requested the Indian Central government to ban the game. But following that the Central government responded that since Blue Whale wasn't an application, so it couldn't be banned. If our project is made possible, we can get the identities of the people who threaten like this and so the person who is responsible for all these issues can be found therefore crimes and criminals can be avoided easily. Momo Challenge The Momo Challenge is a form of digital tormenting or cyber bullying that spreads through online social media and mobile phones. After the victims are subjected to contact a Momo account through social media network such as WhatsApp, they get realistic threats in forms of image, text and they are threatened to perform a series of dangerous tasks. This may also include hacking the victim's phone. The Momo Challenge relies entirely on threats just to get the victims to perform deadly tasks. Focusing on young people, Momo relies on Whatsapp messages to convince common young people as victims to use their mobile phone to contact one of different Momo account phone numbers. Whoever has set up the account then repeatedly threatens the victim to make personal and private information public, or threaten to harm on their family members, unless a series of tasks is completed. Some victims are even threatened with supernatural harm such as magical curses. These threats and the corresponding communications are often done with the help of disturbing, scary or aggravating images. If our project is made possible, we can get the identities of the people who threaten like this and so crimes can be easily avoided. 202
3 2. RELATED WORKS In this session, we can see about the attribute based encryption and a brief overview on existing ciphertext policy attribute based encryption with access control schemes. Attribute Based Encryption Attribute Based Encryption is a type of encryption where the key values and the ciphertext depend on the attributes of the user which was first proposed by Goyal, Sahai and Waters[1]. Many applications use encryption to protect data where the data is protected but the identity of the illegal or problematic user cannot be deducted since the accounts in the application or registered mostly with mobile numbers or ids. These details are not unique identities of the users and thus the culprits cannot be found. The challenges faced in attribute based encryption are key coordination, key escrow and key revocation and thus different types of attribute based encryptions were proposed. There are two types of attribute based encryptions they are Keypolicy attribute based encryption and cipher text policy attribute based encryption. In our paper we propose a Cipher text policy attribute based encryption to encrypt with the user s real identities with which fine grained access control can be achieved. If a user is reported to involve in cyber bulling or cybercrime then the account of that user and the accounts with same identity can also be blacklisted. Since same user can have different accounts but their identity will be same so it is easy to blacklist them by avoiding threats to the common people. As well as if any action is to be taken then that can also be done as now the identity of the user can be found if needed. 3. METHODOLOGY Flow Chart Key Policy Attribute Based Encryption and Ciphertext Policy Attribute Based Encryption In 2006, sahai and waters introduced attribute based encryption. Then it was classified into two where in KP-ABE[2], the encrypted data is based on the set of attributes and access rules which supports mono access tree where in cipertext policy attribute based encryption[3] (CP-ABE) the plain text is encrypted with access policy written by the encryptors and the user s private key is based on the set of attributes. The decryption is only done when the user attributes satisfies the access control policy of the ciphertext. The ciphertext policy attribute based encryption is used in this project since the access policy of a user can be determined by the data owner. In 2011, for the flexible and scalable access zhiguo wan, jun e Liu and Robert H. Deng proposed a system [4] with access control scheme which supports disjunction normal form (DNF) and conjuctive normal form (CNF) access control policy. But this system can t provide flexible access. In 2011, an expressive, efficient and secure realization of cipher text policy attribute based encryption system [5] was proposed by Brent waters. In 2014, for more flexible access, Hua Deng and team proposed a system [6] which is based on LSSS which enriches the expression of access control policy but this system has low efficiency in decryption phase. The purpose of our system is to make it possible to find the illegal user in the system. The main idea is to encrypt the users identities using CP- HABE (Ciphertext Policy Hierarchical Attribute based Encryption). Only the authorized regulation nodes have the correct key to the decrypted identities. User Registration The necessary attributes alone with a unique attribute is gathered from the users who are then registered into the application. As a user is registered, a key pair along with the account address is distributed to the user. 203
4 Key Pair Generation The key pair of public key and master secret key (pk, msk) is generated with the attributes of the registered users. The public key is related with the user identity. This relationship is known only to the user and the server. When the identity of the user is identified to be valid then the key pair is distributed to the user. If a user is identified with fake identity then no key pair is generated. Some attributes are hashed with the key pair to produce a private key. CP-ABE Encryption When a user A sends message to another user B, the message gets encrypted with CP-ABE algorithm along with the access control policy and private key to produce an encrypted secured message as output. The encrypted message is passed through the internet to reach the receiver side from the sender side. CP-ABE Decryption When the user B receives the encrypted message, the public key which is based on the user attributes is used to decrypt the message and thus original text is obtained. The hackers who try to hack the message will not have the real attribute of that particular user and thus they cannot get the original message and it is hard to hack. This algorithm can also be used to deduct the person who is illegally using the applications in a wrong way and we can also blacklist them. As one unique Id is used as an attribute the different accounts using the same identity can also be blacklisted. 4. SAFE AND SECURE CP-ABE ENCRYPTION SYSTEM The proposed CP-ABE Scheme G and GT are two multiplicative cyclic groups of prime order p and e₂: G*G -> Gₜ be a bilinear map g is defined as generator of group G. CP-ABE Setup The attributes are S {w 1, w 2,.. w N ) where w 1, w 2,... w N Z p. The subscript N is the number of attributes in S which is divided into n trees according to the relationship. The depth of i th tree is l i and l max {l i } i [1,n] for i1 n. Then choose a random element u' i G and random vector U i (u i1, u i2,... u li ) G li. Choose two random value α, a Z p. The key pair is PK abe (Public Key) and MK abe (Master Secret Key). PK abe (g, g a, Ye 2 (g, g) α, u' 1 u' n, U 1 U n ) MK abe g α CP-ABE KeyGen The inputs of this algorithm are User s set of attributes (S u S) and Master Secret Key (MK abe ). The output of this algorithm would be the Private Key (SK u ). The key server takes the random number r Z p and computes D g α + ar. Suppose if w S u is an attribute in the i th tree with depth k and path R(w) (w i0,w i1, w ik ) for every w S u, it computes d i (u' I Π k δ1 u wiδ iδ) r SK u D (g α+ar, D' g r, {D w } wεsu ) Where, CP-ABE Encryption D w {d i, d i,..k+1., d ili } d iδ u r iδ for k+1 δ l i The input for performing encryption would be Public parameters (PK abe ), Message to be sent (m), Access structure (M,ρ), access policy (AP). Where, M is the matrix of d rows and e columns. Ρ maps the ζ th row M ζ of matrix M to a certain attribute ρ(ζ). The output will be cipher text (CT). Only users who have a set of attributes that satisfies the access structure can decrypt the message. CT (Č, C, {C ζ1, C ζ2 } ζε[1,d] ) C ζ1 g asζ (u' j Π k δ 1 u jδ w1/jδ ) -rζ C ζ2 g rζ Č my s C g -s Choose a secret value S Z p and some random elements v 2 v e. Let v (s, v 2 v e ) T be the column vector for ζ 1,2 d. s ζ M ζ. v where s ζ is the ζ th share of secret s. ρ(ζ) w' where attribute w' is in the j th tree with depth k' and path of R(w') (w' j0, w' j1, w' jk' ) then s ζ belongs to w' according to the map ρ. To encrypt message m, choose r ζ Z p for all ζ 1,2 d. CP-ABE Decryption When a user attribute set matches the access policy of the cipher text then the user is the authorized user. If the authorized user with the secret key wants to decrypt the cipher text then the user should match 204
5 their attributes to find the minimum set S u, which satisfies the access policy. The original message can be recovered by, Regular Communication Monitoring with SVM The communication between the users is regularly monitored. To do this SVM classification in the data mining is used. This is done only to protect the users from the persons who try to harm large amount of users. ( ( ) ) m 5. TECHNIQUES Prevent Unauthorized Users with Unique ID All the users should register the account with their unique user Id in order to prevent the unauthorized user access. For the unique user Id finger prints or iris scan or verified aadhar number can be used Methodology for Irrelevant Message Detection The application can maintain an ABE dictionary which consists of all malicious or irrelevant words to be muted. When a word is added to the muted list, the message consist of those words can generate an alert message for the user. Eg. If the word blue whale is added to the dictionary of muted list, a message with the word blue whale to the mobile generates alert message to the user. User s Data Access Permissions with Sessions The user s profile picture, status and last seen are to be protected as the user need privacy. So sessions can be maintained for not giving other users access to the data of the user who updates the data. 6. CONCLUSION For the secure transfer of data in the modern world encryption is used. In this paper we use ciphertext policy attribute based encryption in order to protect data privacy and also to find the people who are misleading other peoples or harassing and causing harm to other people in the name of game and challenge which sometime even lead the victim to suicide. As these criminals are not found till date, since their identities can t be recognized our society will soon be in danger. To avoid such conditions in future, ciphertext attribute based encryption can be used. In order to obtain the security certain techniques has been implemented, such as to prevent unauthorized user we use unique ID such a finger prints or face recognition which are now commonly used in most of the mobile phones to unlock the mobile screen. To deduct the irrelevant or inappropriate messages we can use mute the words or block the words in order to avoid panic among public. As when a word is been added to the block list then if those words occur in the chat of the user or from a new number there will be an alert will be raised which will can be used to create alert and awareness among common people. Regular communication monitoring is also used to find if anyone is trying to harass people. The data which are shared among other people should have privacy as like one should not have access to download the display picture or status without the knowledge of the owner of the data. In this paper, we propose the ABE encryption with access policy rights. In this system, the identity of the culprit or who cause harm to people can be found very easily with the help of their own verified attributes. Even if a person opens different accounts with the same attribute and that particular attribute is in the harm list then this new account will be in suspect list and this new account is also causing harm to the users them that account will also be blocked. If there involves any blackmails or threats 205
6 then necessary action can also be taken like arresting the criminal, etc. we can blacklist or block the user with their wallet address that is generated at the time of creating a new account. In future, this system can be used in applications like bitcoin system and ATM systems to avoid money being stolen from the account. If money or bitcoins are stolen the user who did this can be traced with the help of wallet address and punished accordingly. REFERENCES [1] V. Goyal, O. Pandey, A. Sahai and B.Waters, Fuzzy identity-based encryption, in EUROCRYPT 05, Springer, 2005, pp [2] V. Goyal, O. Pandey, A. Sahai and B.Waters, Attribute based encryption for fine-grained access control of encrypted data, ACM conference on computer and communication safty, 2006 pp [3] J.Bethencourt, A. Sahai and B.Waters, Ciphertext-policy attribute-based encryption, in Magnetism, vol. III, G. T. Rado and H. Suhl, Eds. New York: Academic, 1963, pp [4] Zhiguo Wan, Jun e Liu and Robert H.Deng, HASBE: A Hierarchical Attribute-Based Solution for Flexible and Scalable Access Control in cloud computing, in IEEE Transactions on Information Forensics and Security, vol.7,no.2, April [5] Brent Waters, Ciphertext-policy Attribute-Based Encryption: An Expressive, Efficient, and Provably Secure Realization, in International Association for Crytologic Research, PKC 2011, LNCS 6571, pp , [6] Hua Deng, Qianhong Wu, Bo Qin, Josep Domingo-Ferrer, Lei Zhang, Jianwei Liu and Wenchang Shi, Ciphertext-policy hierarchical attribute-based encryption with short ciphertexts, in International Science 275, pp ,
A compact Aggregate key Cryptosystem for Data Sharing in Cloud Storage systems.
 A compact Aggregate key Cryptosystem for Data Sharing in Cloud Storage systems. G Swetha M.Tech Student Dr.N.Chandra Sekhar Reddy Professor & HoD U V N Rajesh Assistant Professor Abstract Cryptography
A compact Aggregate key Cryptosystem for Data Sharing in Cloud Storage systems. G Swetha M.Tech Student Dr.N.Chandra Sekhar Reddy Professor & HoD U V N Rajesh Assistant Professor Abstract Cryptography
Security Weaknesses of an Anonymous Attribute Based Encryption appeared in ASIACCS 13
 Security Weaknesses of an Anonymous Attribute Based Encryption appeared in ASIACCS 13 Payal Chaudhari, Manik Lal Das, Anish Mathuria DA-IICT, Gandhinagar, India {payal chaudhari, maniklal das, anish mathuria}@daiict.ac.in
Security Weaknesses of an Anonymous Attribute Based Encryption appeared in ASIACCS 13 Payal Chaudhari, Manik Lal Das, Anish Mathuria DA-IICT, Gandhinagar, India {payal chaudhari, maniklal das, anish mathuria}@daiict.ac.in
Secure Data Storage and Data Retrieval in Cloud Storage using Cipher Policy Attribute based Encryption
 Indian Journal of Science and Technology, Vol 8(S9), 318 325, May 2015 ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 DOI: 10.17485/ijst/2015/v8iS9/65600 Secure Data Storage and Data Retrieval in Cloud
Indian Journal of Science and Technology, Vol 8(S9), 318 325, May 2015 ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 DOI: 10.17485/ijst/2015/v8iS9/65600 Secure Data Storage and Data Retrieval in Cloud
Session Based Ciphertext Policy Attribute Based Encryption Method for Access Control in Cloud Storage
 IOSR Journal of Engineering (IOSRJEN) ISSN (e): 2250-3021, ISSN (p): 2278-8719 Vol. 04, Issue 09 (September. 2014), V3 PP 21-25 www.iosrjen.org Session Based Ciphertext Policy Attribute Based Encryption
IOSR Journal of Engineering (IOSRJEN) ISSN (e): 2250-3021, ISSN (p): 2278-8719 Vol. 04, Issue 09 (September. 2014), V3 PP 21-25 www.iosrjen.org Session Based Ciphertext Policy Attribute Based Encryption
Secure Data Sharing using Attribute Based Encryption with Revocation in Cloud Computing
 ISSN No: 2454-9614 Secure Data Sharing using Attribute Based Encryption with Revocation in Cloud Computing *Corresponding Author: D. Vaduganathan E-mail:vaduganathan.kce@gmail.com D. Vaduganathan a a)
ISSN No: 2454-9614 Secure Data Sharing using Attribute Based Encryption with Revocation in Cloud Computing *Corresponding Author: D. Vaduganathan E-mail:vaduganathan.kce@gmail.com D. Vaduganathan a a)
Attribute-based encryption with encryption and decryption outsourcing
 Edith Cowan University Research Online Australian Information Security Management Conference Conferences, Symposia and Campus Events 2014 Attribute-based encryption with encryption and decryption outsourcing
Edith Cowan University Research Online Australian Information Security Management Conference Conferences, Symposia and Campus Events 2014 Attribute-based encryption with encryption and decryption outsourcing
A Procedural Based Encryption Technique for Accessing Data on Cloud
 A Procedural Based Encryption Technique for Accessing Data on Cloud Avinash N 1, Divya C 2 P.G. Student, Department of Computer Science and Engineering, SVIT, Bangalore, Karnataka, India 1 Assistant Professor,
A Procedural Based Encryption Technique for Accessing Data on Cloud Avinash N 1, Divya C 2 P.G. Student, Department of Computer Science and Engineering, SVIT, Bangalore, Karnataka, India 1 Assistant Professor,
Time-Based Proxy Re-encryption Review
 Time-Based Proxy Re-encryption Review Meghatai Maruti Bhoite 1, I Govardhan Rao 2 CSE, University College of Engineering Osmania University, Hyderabad, India Abstract :- Fundamentals approach for secure
Time-Based Proxy Re-encryption Review Meghatai Maruti Bhoite 1, I Govardhan Rao 2 CSE, University College of Engineering Osmania University, Hyderabad, India Abstract :- Fundamentals approach for secure
Insecurity of an Dynamic User Revocation and Key Refreshing for Attribute-Based Encryption Scheme
 2014 Tenth 10th International Conference on Computational Intelligence and Security Insecurity of an Dynamic User Revocation and Key Refreshing for Attribute-Based Encryption Scheme Changji Wang, Haitao
2014 Tenth 10th International Conference on Computational Intelligence and Security Insecurity of an Dynamic User Revocation and Key Refreshing for Attribute-Based Encryption Scheme Changji Wang, Haitao
Online Threats. This include human using them!
 Online Threats There are many dangers from using the web (and computer in general). One should watch out for malware, automated programs designed to cause harm to you, your data, and your system. You are
Online Threats There are many dangers from using the web (and computer in general). One should watch out for malware, automated programs designed to cause harm to you, your data, and your system. You are
PRIVACY PRESERVING RANKED MULTI KEYWORD SEARCH FOR MULTIPLE DATA OWNERS. SRM University, Kattankulathur, Chennai, IN.
 Volume 115 No. 6 2017, 585-589 ISSN: 1311-8080 (printed version); ISSN: 1314-3395 (on-line version) url: http://www.ijpam.eu ijpam.eu PRIVACY PRESERVING RANKED MULTI KEYWORD SEARCH FOR MULTIPLE DATA OWNERS
Volume 115 No. 6 2017, 585-589 ISSN: 1311-8080 (printed version); ISSN: 1314-3395 (on-line version) url: http://www.ijpam.eu ijpam.eu PRIVACY PRESERVING RANKED MULTI KEYWORD SEARCH FOR MULTIPLE DATA OWNERS
IJREAT International Journal of Research in Engineering & Advanced Technology, Volume 1, Issue 5, Oct-Nov, 2013 ISSN:
 SIMHA : Secure Biometric Multi-Host Authentication Ramya K P 1, Chithra Devi R 2 and Revathi M K 3 1 Information Technology, Dr.Sivanthi Aditanar College of Engineering, Tiruchendur, Tamil Nadu 628215,
SIMHA : Secure Biometric Multi-Host Authentication Ramya K P 1, Chithra Devi R 2 and Revathi M K 3 1 Information Technology, Dr.Sivanthi Aditanar College of Engineering, Tiruchendur, Tamil Nadu 628215,
Attribute Based Encryption with Privacy Protection in Clouds
 Attribute Based Encryption with Privacy Protection in Clouds Geetanjali. M 1, Saravanan. N 2 PG Student, Department of Information Technology, K.S.R College of Engineering, Tiruchengode, Tamilnadu, India
Attribute Based Encryption with Privacy Protection in Clouds Geetanjali. M 1, Saravanan. N 2 PG Student, Department of Information Technology, K.S.R College of Engineering, Tiruchengode, Tamilnadu, India
Fine-Grained Data Sharing Supporting Attribute Extension in Cloud Computing
 wwwijcsiorg 10 Fine-Grained Data Sharing Supporting Attribute Extension in Cloud Computing Yinghui Zhang 12 1 National Engineering Laboratory for Wireless Security Xi'an University of Posts and Telecommunications
wwwijcsiorg 10 Fine-Grained Data Sharing Supporting Attribute Extension in Cloud Computing Yinghui Zhang 12 1 National Engineering Laboratory for Wireless Security Xi'an University of Posts and Telecommunications
EFFICIENT DATA SHARING WITH ATTRIBUTE REVOCATION FOR CLOUD STORAGE
 EFFICIENT DATA SHARING WITH ATTRIBUTE REVOCATION FOR CLOUD STORAGE Chakali Sasirekha 1, K. Govardhan Reddy 2 1 M.Tech student, CSE, Kottam college of Engineering, Chinnatekuru(V),Kurnool,Andhra Pradesh,
EFFICIENT DATA SHARING WITH ATTRIBUTE REVOCATION FOR CLOUD STORAGE Chakali Sasirekha 1, K. Govardhan Reddy 2 1 M.Tech student, CSE, Kottam college of Engineering, Chinnatekuru(V),Kurnool,Andhra Pradesh,
An Efficient Verifiable Multi-Authority Secret Access control scheme in Cloud Storage M.Sreelakshmi & P.Gangadhara
 An Efficient Verifiable Multi-Authority Secret Access control scheme in Cloud Storage M.Sreelakshmi & P.Gangadhara 1 M.Tech, Dept of CSE,Shri Shirdi Sai Institute of Science and Engineering, Affiliated
An Efficient Verifiable Multi-Authority Secret Access control scheme in Cloud Storage M.Sreelakshmi & P.Gangadhara 1 M.Tech, Dept of CSE,Shri Shirdi Sai Institute of Science and Engineering, Affiliated
Framework Research on Privacy Protection of PHR Owners in Medical Cloud System Based on Aggregation Key Encryption Algorithm
 Framework Research on Privacy Protection of PHR Owners in Medical Cloud System Based on Aggregation Key Encryption Algorithm Huiqi Zhao 1,2,3, Yinglong Wang 2,3*, Minglei Shu 2,3 1 Department of Information
Framework Research on Privacy Protection of PHR Owners in Medical Cloud System Based on Aggregation Key Encryption Algorithm Huiqi Zhao 1,2,3, Yinglong Wang 2,3*, Minglei Shu 2,3 1 Department of Information
Enhancing Reliability and Scalability in Dynamic Group System Using Three Level Security Mechanisms
 Enhancing Reliability and Scalability in Dynamic Group System Using Three Level Security Mechanisms A.Sarika*1, Smt.J.Raghaveni*2 M.Tech Student, Dept of CSE, S.R.K.R Engineering college, Bhimavaram, AP,
Enhancing Reliability and Scalability in Dynamic Group System Using Three Level Security Mechanisms A.Sarika*1, Smt.J.Raghaveni*2 M.Tech Student, Dept of CSE, S.R.K.R Engineering college, Bhimavaram, AP,
Cyber Security Guide. For Politicians and Political Parties
 Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Efficient Generation of Linear Secret Sharing. Scheme Matrices from Threshold Access Trees
 Efficient Generation of Linear Secret Sharing 1 Scheme Matrices from Threshold Access Trees Zhen Liu, Zhenfu Cao, and Duncan S. Wong Abstract Linear Secret Sharing Scheme (LSSS) matrices are commonly used
Efficient Generation of Linear Secret Sharing 1 Scheme Matrices from Threshold Access Trees Zhen Liu, Zhenfu Cao, and Duncan S. Wong Abstract Linear Secret Sharing Scheme (LSSS) matrices are commonly used
Efficient Auditable Access Control Systems for Public Shared Cloud Storage
 Efficient Auditable Access Control Systems for Public Shared Cloud Storage Vidya Patil 1, Prof. Varsha R. Dange 2 Student, Department of Computer Science Dhole Patil College of Engineering, Pune, Maharashtra,
Efficient Auditable Access Control Systems for Public Shared Cloud Storage Vidya Patil 1, Prof. Varsha R. Dange 2 Student, Department of Computer Science Dhole Patil College of Engineering, Pune, Maharashtra,
Chapter 6 Network and Internet Security and Privacy
 Chapter 6 Network and Internet Security and Privacy Learning Objectives LO6.1: Explain network and Internet security concerns LO6.2: Identify online threats LO6.3: Describe cyberstalking and other personal
Chapter 6 Network and Internet Security and Privacy Learning Objectives LO6.1: Explain network and Internet security concerns LO6.2: Identify online threats LO6.3: Describe cyberstalking and other personal
Military Secured Network Data Transmission
 Military Secured Network Data Transmission Shubham Jain 1, Umesh Dusane 2, Smita Lokhande 3, Vinod Kadam 4, Asst. Prof. Neha Jamdar 5 1University of Pune, Sinhgad Institute of Technology and Science, jains7272@gmail.com
Military Secured Network Data Transmission Shubham Jain 1, Umesh Dusane 2, Smita Lokhande 3, Vinod Kadam 4, Asst. Prof. Neha Jamdar 5 1University of Pune, Sinhgad Institute of Technology and Science, jains7272@gmail.com
ENSURING PRIVACY OF E-MEDICAL HEALTH RECORDS USING TRIPLE- DES ALGORITHM
 ENSURING PRIVACY OF E-MEDICAL HEALTH RECORDS USING TRIPLE- DES ALGORITHM Ms. S. P. Vidhya Priya 1, Dharani.N.R 2, Gokilavani.M 3, Jeevitha.R 4 1,2,3,4 Department of Information Technology, Kathir College
ENSURING PRIVACY OF E-MEDICAL HEALTH RECORDS USING TRIPLE- DES ALGORITHM Ms. S. P. Vidhya Priya 1, Dharani.N.R 2, Gokilavani.M 3, Jeevitha.R 4 1,2,3,4 Department of Information Technology, Kathir College
Anti-Cyber Bullying Policy.
 Anti-Cyber Bullying Policy. Bullying, in any form, is an issue that we all take very seriously at Bredon School. We accept that victims can become depressed and suicidal, and even take their own lives.
Anti-Cyber Bullying Policy. Bullying, in any form, is an issue that we all take very seriously at Bredon School. We accept that victims can become depressed and suicidal, and even take their own lives.
Features. Product Highlights. Not just an app, but a friend for your phone. Optimization. Speed. Battery. Storage. Data Usage
 PRO Not just an app, but a friend for your phone. Product Highlights Fonetastic is an all-in-one app for Android devices. Built with multiple productivity and security features, it enhances your device
PRO Not just an app, but a friend for your phone. Product Highlights Fonetastic is an all-in-one app for Android devices. Built with multiple productivity and security features, it enhances your device
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY
 INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK A PROPOSAL FOR UNIQUE IDENTIFICATION NUMBER FOR ALL ONLINE ACCOUNT HOLDERS TO CURB
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK A PROPOSAL FOR UNIQUE IDENTIFICATION NUMBER FOR ALL ONLINE ACCOUNT HOLDERS TO CURB
Survey Paper on Efficient and Secure Dynamic Auditing Protocol for Data Storage in Cloud
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
ENCRYPTED DATA MANAGEMENT WITH DEDUPLICATION IN CLOUD COMPUTING
 ENCRYPTED DATA MANAGEMENT WITH DEDUPLICATION IN CLOUD COMPUTING S KEERTHI 1*, MADHAVA REDDY A 2* 1. II.M.Tech, Dept of CSE, AM Reddy Memorial College of Engineering & Technology, Petlurivaripalem. 2. Assoc.
ENCRYPTED DATA MANAGEMENT WITH DEDUPLICATION IN CLOUD COMPUTING S KEERTHI 1*, MADHAVA REDDY A 2* 1. II.M.Tech, Dept of CSE, AM Reddy Memorial College of Engineering & Technology, Petlurivaripalem. 2. Assoc.
International Journal of Advanced Research in Computer Science and Software Engineering
 Volume 3, Issue 3, March 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Reliable Proxy
Volume 3, Issue 3, March 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Reliable Proxy
DECENTRALIZED ATTRIBUTE-BASED ENCRYPTION AND DATA SHARING SCHEME IN CLOUD STORAGE
 DECENTRALIZED ATTRIBUTE-BASED ENCRYPTION AND DATA SHARING SCHEME IN CLOUD STORAGE ABSTRACT We propose a Multi-Authority Attribute-Based Encryption (ABE) system. In our system, any party can become an authority
DECENTRALIZED ATTRIBUTE-BASED ENCRYPTION AND DATA SHARING SCHEME IN CLOUD STORAGE ABSTRACT We propose a Multi-Authority Attribute-Based Encryption (ABE) system. In our system, any party can become an authority
Various Attribute Based Encryption Algorithms in Clouds-A Survey P. Sivakumar 1 K. Devi 2 M. Navinkumar 3
 IJSRD - International Journal for Scientific Research & Development Vol. 3, Issue 03, 2015 ISSN (online): 2321-0613 Various Attribute Based Encryption Algorithms in Clouds-A Survey P. Sivakumar 1 K. Devi
IJSRD - International Journal for Scientific Research & Development Vol. 3, Issue 03, 2015 ISSN (online): 2321-0613 Various Attribute Based Encryption Algorithms in Clouds-A Survey P. Sivakumar 1 K. Devi
HIGH LEVEL SECURITY IMPLEMENTATION IN DATA SHARING ON SOCIAL WEBSITES
 HIGH LEVEL SECURITY IMPLEMENTATION IN DATA SHARING ON SOCIAL WEBSITES P.Senthil Kumar 1 Associate professor, PSNA college of engineering and technology,dindigul,tamilnadu,india Abstract: With the recent
HIGH LEVEL SECURITY IMPLEMENTATION IN DATA SHARING ON SOCIAL WEBSITES P.Senthil Kumar 1 Associate professor, PSNA college of engineering and technology,dindigul,tamilnadu,india Abstract: With the recent
Cyber Hygiene Guide. Politicians and Political Parties
 Cyber Hygiene Guide Politicians and Political Parties Canadian Election Integrity Initiative Design by ccm.design Cover Image by Songquan Deng Helping to Safeguard the Integrity of the Electoral Process
Cyber Hygiene Guide Politicians and Political Parties Canadian Election Integrity Initiative Design by ccm.design Cover Image by Songquan Deng Helping to Safeguard the Integrity of the Electoral Process
Collusion-Resistant Group Key Management Using Attributebased
 Collusion-Resistant Group Key Management Using Attributebased Encryption Presented by: Anurodh Joshi Overview of the Paper Presents a ciphertext-policy attribute-based encryption (CP-ABE) scheme to solve
Collusion-Resistant Group Key Management Using Attributebased Encryption Presented by: Anurodh Joshi Overview of the Paper Presents a ciphertext-policy attribute-based encryption (CP-ABE) scheme to solve
Three Levels of Access Control to Personal Health Records in a Healthcare Cloud
 Three Levels of Access Control to Personal Health Records in a Healthcare Cloud Gabriel Sanchez Bautista and Ning Zhang School of Computer Science The University of Manchester Manchester M13 9PL, United
Three Levels of Access Control to Personal Health Records in a Healthcare Cloud Gabriel Sanchez Bautista and Ning Zhang School of Computer Science The University of Manchester Manchester M13 9PL, United
A Survey on Chat Log Investigation Using Text Mining
 A Survey on Chat Log Investigation Using Text Mining Khan Sameera, Pinki Vishwakarma M.E 2 nd Year, Dept. of Computer Engineering, Shah & Anchor Kutchhi Engineering College, Mumbai, India Professor, Dept.
A Survey on Chat Log Investigation Using Text Mining Khan Sameera, Pinki Vishwakarma M.E 2 nd Year, Dept. of Computer Engineering, Shah & Anchor Kutchhi Engineering College, Mumbai, India Professor, Dept.
AN ANALYSIS ON ATTRIBUTE-BASED SOLUTION FOR ADAPTABLE AND SCALABLE SECURITY ACCESS CONTROL IN CLOUD COMPUTING
 International Journal of Computing Communication and Information System(IJCCIS) Vol 6. No.3 July-September 2014 Pp. 96-105 gopalax Journals, Singapore available at : www.ijcns.com ISSN: 0976 1349 AN ANALYSIS
International Journal of Computing Communication and Information System(IJCCIS) Vol 6. No.3 July-September 2014 Pp. 96-105 gopalax Journals, Singapore available at : www.ijcns.com ISSN: 0976 1349 AN ANALYSIS
Structure-Preserving Certificateless Encryption and Its Application
 SESSION ID: CRYP-T06 Structure-Preserving Certificateless Encryption and Its Application Prof. Sherman S. M. Chow Department of Information Engineering Chinese University of Hong Kong, Hong Kong @ShermanChow
SESSION ID: CRYP-T06 Structure-Preserving Certificateless Encryption and Its Application Prof. Sherman S. M. Chow Department of Information Engineering Chinese University of Hong Kong, Hong Kong @ShermanChow
EFFICIENT REVOCATION AND SECURE ATTRIBUTE-BASED PROXY RE-ENCRYPTION SCHEME
 EFFICIENT REVOCATION AND SECURE ATTRIBUTE-BASED PROXY RE-ENCRYPTION SCHEME MAHESH S. GUNJAL 1, Dr. B. L. GUNJAL 2 1PG Student, Dept. of Computer Engineering, AVCOE, Maharashtra, India 2Associate Professor,
EFFICIENT REVOCATION AND SECURE ATTRIBUTE-BASED PROXY RE-ENCRYPTION SCHEME MAHESH S. GUNJAL 1, Dr. B. L. GUNJAL 2 1PG Student, Dept. of Computer Engineering, AVCOE, Maharashtra, India 2Associate Professor,
CYBERCRIME AS A NEW FORM OF CONTEMPORARY CRIME
 FACULTY OF LAW DEPARTEMENT: CIVIL LAW MASTER STUDY THEME: CYBERCRIME AS A NEW FORM OF CONTEMPORARY CRIME Mentor: Prof. Ass. Dr. Xhemajl Ademaj Candidate: Abdurrahim Gashi Pristinë, 2015 Key words List
FACULTY OF LAW DEPARTEMENT: CIVIL LAW MASTER STUDY THEME: CYBERCRIME AS A NEW FORM OF CONTEMPORARY CRIME Mentor: Prof. Ass. Dr. Xhemajl Ademaj Candidate: Abdurrahim Gashi Pristinë, 2015 Key words List
D Facebook A. E Twitter B. F WhatsApp C. C Skype D. A Snapchat E. SECTION 1 Matching
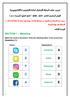 SETION 1 Matching Match the word to the picture. Write the matching letter in the correct box. Question (1) Terms Explanations D Facebook E Twitter F Whatspp Skype D Snapchat E 1 Instagram F Question (2)
SETION 1 Matching Match the word to the picture. Write the matching letter in the correct box. Question (1) Terms Explanations D Facebook E Twitter F Whatspp Skype D Snapchat E 1 Instagram F Question (2)
A Survey on Secure Sharing In Cloud Computing
 A Survey on Secure Sharing In Cloud Computing Aakanksha maliye, Sarita Patil Department of Computer Engineering, G.H.Raisoni College of Engineering & Management, Wagholi, India ABSTRACT: Cloud computing
A Survey on Secure Sharing In Cloud Computing Aakanksha maliye, Sarita Patil Department of Computer Engineering, G.H.Raisoni College of Engineering & Management, Wagholi, India ABSTRACT: Cloud computing
EADS up. stop think connect
 EADS up stop think connect You text, you play games, you share photos and video. You update your status, you post comments, you probably spend some time in a virtual world. Being online connected through
EADS up stop think connect You text, you play games, you share photos and video. You update your status, you post comments, you probably spend some time in a virtual world. Being online connected through
Question 1: What steps can organizations take to prevent incidents of cybercrime? Answer 1:
 Cybercrime Question 1: What steps can organizations take to prevent incidents of cybercrime? Answer 1: Organizations can prevent cybercrime from occurring through the proper use of personnel, resources,
Cybercrime Question 1: What steps can organizations take to prevent incidents of cybercrime? Answer 1: Organizations can prevent cybercrime from occurring through the proper use of personnel, resources,
On the Security of Group-based Proxy Re-encryption Scheme
 On the Security of Group-based Proxy Re-encryption Scheme Purushothama B R 1, B B Amberker Department of Computer Science and Engineering National Institute of Technology Warangal Warangal, Andhra Pradesh-506004,
On the Security of Group-based Proxy Re-encryption Scheme Purushothama B R 1, B B Amberker Department of Computer Science and Engineering National Institute of Technology Warangal Warangal, Andhra Pradesh-506004,
BEST PRACTICES FOR PERSONAL Security
 BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
A to Z of the Darknet
 A to Z of the Darknet Professional acknowledgements The Investigator conferences Thomas Olofson Intelliagg author of Shining a Light on the Dark Web Colin Tansley Intelect Solutions Limited A is for Anonymity
A to Z of the Darknet Professional acknowledgements The Investigator conferences Thomas Olofson Intelliagg author of Shining a Light on the Dark Web Colin Tansley Intelect Solutions Limited A is for Anonymity
Privileged Document Access In Google Cloud Environment
 Privileged Document Access In Google Cloud Environment 1 Miss. S.V. Sarode, 2 Prof. K.N.Shedge 1 PG student, 2 Assi. Professor 1 Computer Engineering Department, 1 SVIT, Chincholi, Sinner, Nashik, India
Privileged Document Access In Google Cloud Environment 1 Miss. S.V. Sarode, 2 Prof. K.N.Shedge 1 PG student, 2 Assi. Professor 1 Computer Engineering Department, 1 SVIT, Chincholi, Sinner, Nashik, India
Protecting Security and Privacy of Outsourced Data in the Cloud
 Protecting Security and Privacy of Outsourced Data in the Cloud Robert H. Deng School of Information Systems Singapore Management University ASI@CityU, HK 2-4 December 2014 1 Outline Introduction Using
Protecting Security and Privacy of Outsourced Data in the Cloud Robert H. Deng School of Information Systems Singapore Management University ASI@CityU, HK 2-4 December 2014 1 Outline Introduction Using
User Revocation And Fine Grained Access Control Of Phr In Cloud Using Hasbe
 User Revocation And Fine Grained Access Control Of Phr In Cloud Using Hasbe T.Radhika 1, S.Vasumathi Kannagi 2 P.G.Scholar, Department of CSE, Info Institute of Engineering, Coimbatore, India 1 Assistant
User Revocation And Fine Grained Access Control Of Phr In Cloud Using Hasbe T.Radhika 1, S.Vasumathi Kannagi 2 P.G.Scholar, Department of CSE, Info Institute of Engineering, Coimbatore, India 1 Assistant
Lambton Primary School
 Lambton Primary School Advice to pupils on Cyber Bullying For pupils If you re being bullied by phone or the internet Remember, bullying is never your fault. It can be stopped, and it can usually be traced.
Lambton Primary School Advice to pupils on Cyber Bullying For pupils If you re being bullied by phone or the internet Remember, bullying is never your fault. It can be stopped, and it can usually be traced.
A Less Weight Secure Data Sharing Scheme for Mobile Cloud Computing
 A Less Weight Secure Data Sharing Scheme for Mobile Cloud Computing P. Likitha Department of Computer Science and Engineering, MJR College of Engineering & Technology, Piler, A.P - 517214, India. ABSTRACT:
A Less Weight Secure Data Sharing Scheme for Mobile Cloud Computing P. Likitha Department of Computer Science and Engineering, MJR College of Engineering & Technology, Piler, A.P - 517214, India. ABSTRACT:
Secure Data Sharing in Cloud Computing: Challenges and Research Directions
 Cyber Summer School Melbourne, 12-13 Feb 2018 Secure Data Sharing in Cloud Computing: Challenges and Research Directions Willy Susilo Institute of Cybersecurity and Cryptology School of Computing and Information
Cyber Summer School Melbourne, 12-13 Feb 2018 Secure Data Sharing in Cloud Computing: Challenges and Research Directions Willy Susilo Institute of Cybersecurity and Cryptology School of Computing and Information
Network Security Issues and Cryptography
 Network Security Issues and Cryptography PriyaTrivedi 1, Sanya Harneja 2 1 Information Technology, Maharishi Dayanand University Farrukhnagar, Gurgaon, Haryana, India 2 Information Technology, Maharishi
Network Security Issues and Cryptography PriyaTrivedi 1, Sanya Harneja 2 1 Information Technology, Maharishi Dayanand University Farrukhnagar, Gurgaon, Haryana, India 2 Information Technology, Maharishi
Attribute-Based Encryption. Allison Lewko, Microsoft Research
 Attribute-Based Encryption Allison Lewko, Microsoft Research The Cast of Characters This talk will feature work by: Brent Waters Amit Sahai Vipul Goyal Omkant Pandey With special guest appearances by:
Attribute-Based Encryption Allison Lewko, Microsoft Research The Cast of Characters This talk will feature work by: Brent Waters Amit Sahai Vipul Goyal Omkant Pandey With special guest appearances by:
Forensic Analysis Approach Based on Metadata and Hash Values for Digital Objects in the Cloud
 Forensic Analysis Approach Based on Metadata and Hash Values for Digital Objects in the Cloud Ezz El-Din Hemdan 1, Manjaiah D.H 2 Research Scholar, Department of Computer Science, Mangalore University,
Forensic Analysis Approach Based on Metadata and Hash Values for Digital Objects in the Cloud Ezz El-Din Hemdan 1, Manjaiah D.H 2 Research Scholar, Department of Computer Science, Mangalore University,
On the security of a certificateless signature scheme in the standard model
 On the security of a certificateless signature scheme in the standard model Lin Cheng, Qiaoyan Wen, Zhengping Jin, Hua Zhang State Key Laboratory of Networking and Switch Technology, Beijing University
On the security of a certificateless signature scheme in the standard model Lin Cheng, Qiaoyan Wen, Zhengping Jin, Hua Zhang State Key Laboratory of Networking and Switch Technology, Beijing University
SecRBAC: Secure data in the Clouds
 SecRBAC: Secure data in the Clouds Dr.K.Rameshwaraiah *1 G. Shiva Prasad *2 *1 Professor Department of Computer Science and Engineering *2 M.Tech *123 Nalla Narasimha Reddy Educational Society s Group
SecRBAC: Secure data in the Clouds Dr.K.Rameshwaraiah *1 G. Shiva Prasad *2 *1 Professor Department of Computer Science and Engineering *2 M.Tech *123 Nalla Narasimha Reddy Educational Society s Group
Digital Safety and Digital Citizenship
 Digital Safety and Digital Citizenship A Guide for Students The laptop has been given to you as a tool for learning. Use it for that. While doing so, here are some important rules for keeping yourself
Digital Safety and Digital Citizenship A Guide for Students The laptop has been given to you as a tool for learning. Use it for that. While doing so, here are some important rules for keeping yourself
The Research and Application of the Fingerprint Key based USB-Key Pin Number Protection System Yu Lu 1, a, Zhong Liang 2, b, Chen Yue 3, c
 5th International Conference on Information Engineering for Mechanics and Materials (ICIMM 2015) The Research and Application of the Fingerprint Key based USB-Key Pin Number Protection System Yu Lu 1,
5th International Conference on Information Engineering for Mechanics and Materials (ICIMM 2015) The Research and Application of the Fingerprint Key based USB-Key Pin Number Protection System Yu Lu 1,
Door Automation Security System Using OTP
 Door Automation Security System Using OTP Snehalata Raut 1, Dimple chapke 2, Akash Sontakke 3, Nayan Pounikar 4, Prof. Neha Israni 5 1234 Final Year Students, 5 Assistant professor of Department of Information
Door Automation Security System Using OTP Snehalata Raut 1, Dimple chapke 2, Akash Sontakke 3, Nayan Pounikar 4, Prof. Neha Israni 5 1234 Final Year Students, 5 Assistant professor of Department of Information
Efficient Access Control Scheme with Multiple Attribute Authorities for Public Cloud Storage
 Efficient Access Control Scheme with Multiple Attribute Authorities for Public Cloud Storage Mr. Ramesh 1, Prof. Girish Kumar D 2, Student, M.tech(Computer Networking) 1,, Assistant Professor, Computer
Efficient Access Control Scheme with Multiple Attribute Authorities for Public Cloud Storage Mr. Ramesh 1, Prof. Girish Kumar D 2, Student, M.tech(Computer Networking) 1,, Assistant Professor, Computer
A LTERATURE SURVEY ON REVOCABLE MULTIAUTHORITY CIPHER TEXT-POLICY ATTRIBUTE-BASED ENCRYPTION (CP-ABE) SCHEME FOR CLOUD STORAGE
 A LTERATURE SURVEY ON REVOCABLE MULTIAUTHORITY CIPHER TEXT-POLICY ATTRIBUTE-BASED ENCRYPTION (CP-ABE) SCHEME FOR CLOUD STORAGE Vinoth Kumar P, Dr.P.D.R. Vijaya Kumar 1 PG Student, INFO Institute of Engineering,
A LTERATURE SURVEY ON REVOCABLE MULTIAUTHORITY CIPHER TEXT-POLICY ATTRIBUTE-BASED ENCRYPTION (CP-ABE) SCHEME FOR CLOUD STORAGE Vinoth Kumar P, Dr.P.D.R. Vijaya Kumar 1 PG Student, INFO Institute of Engineering,
The Research on PGP Private Key Ring Cracking and Its Application
 The Research on PGP Private Key Ring Cracking and Its Application Xiaoyan Deng 1 *, Qingbing Ji 2, Lijun Zhang 3 1. College of Applied Mathematics,Chengdu University of Information Technology,Chengdu,
The Research on PGP Private Key Ring Cracking and Its Application Xiaoyan Deng 1 *, Qingbing Ji 2, Lijun Zhang 3 1. College of Applied Mathematics,Chengdu University of Information Technology,Chengdu,
Ethical Hacking. Content Outline: Session 1
 Ethical Hacking Content Outline: Session 1 Ethics & Hacking Hacking history : How it all begin - Why is security needed? - What is ethical hacking? - Ethical Hacker Vs Malicious hacker - Types of Hackers
Ethical Hacking Content Outline: Session 1 Ethics & Hacking Hacking history : How it all begin - Why is security needed? - What is ethical hacking? - Ethical Hacker Vs Malicious hacker - Types of Hackers
Enhanced Novel Multilevel Secure User Authentication Scheme in Cloud.
 Enhanced Novel Multilevel Secure User Authentication Scheme in Cloud. A.Lakshmi Pavani 1, K.Devi Priya 2 1 M. Tech Student, Department of Computer Science and Engineering, Aditya Engineering College, Surampalem,
Enhanced Novel Multilevel Secure User Authentication Scheme in Cloud. A.Lakshmi Pavani 1, K.Devi Priya 2 1 M. Tech Student, Department of Computer Science and Engineering, Aditya Engineering College, Surampalem,
Fair Cryptography. Cryptography CS 507 Erkay Savas Sabanci University
 Fair Cryptography Cryptography CS 507 Erkay Savas Sabanci University erkays@sabanciuniv.edu Conflicting Interests Private Industry wants to secure communications Citizens want privacy Law enforcement wants
Fair Cryptography Cryptography CS 507 Erkay Savas Sabanci University erkays@sabanciuniv.edu Conflicting Interests Private Industry wants to secure communications Citizens want privacy Law enforcement wants
Tracing Insider Attacks in the Context of Predicate Encryption Schemes
 Tracing Insider Attacks in the Context of Predicate Encryption Schemes Jonathan Katz and Dominique Schröder University of Maryland Email: {jkatz,schroder}@cs.umd.edu Abstract In a predicate encryption
Tracing Insider Attacks in the Context of Predicate Encryption Schemes Jonathan Katz and Dominique Schröder University of Maryland Email: {jkatz,schroder}@cs.umd.edu Abstract In a predicate encryption
Computer Security. Assoc. Prof. Pannipa Phaiboonnimit. Adapted for English Section by Kittipitch Kuptavanich and Prakarn Unachak
 Computer Security Assoc. Prof. Pannipa Phaiboonnimit 1 Adapted for English Section by Kittipitch Kuptavanich and Prakarn Unachak Classification of Threats Computer Attack Intend to damage files, computers
Computer Security Assoc. Prof. Pannipa Phaiboonnimit 1 Adapted for English Section by Kittipitch Kuptavanich and Prakarn Unachak Classification of Threats Computer Attack Intend to damage files, computers
Key-Policy Attribute-Based Encryption
 Key-Policy Attribute-Based Encryption Present by Xiaokui Shu 09/08/2011 Identity-Based Encryption Basic KP-ABE Secret-Sharing Scheme Fine-grained Access Control Application Scenario Advanced Topics Related
Key-Policy Attribute-Based Encryption Present by Xiaokui Shu 09/08/2011 Identity-Based Encryption Basic KP-ABE Secret-Sharing Scheme Fine-grained Access Control Application Scenario Advanced Topics Related
Zero private information leak using multi-level security and privileged access for designated authorities on demand
 Zero private information leak using multi-level security and privileged access for designated authorities on demand Syama BabuRaj 1, Pretty Babu 2 Dept.Computer Science & Engg., Sree Buddha College of
Zero private information leak using multi-level security and privileged access for designated authorities on demand Syama BabuRaj 1, Pretty Babu 2 Dept.Computer Science & Engg., Sree Buddha College of
Secure Role-Based Access Control on Encrypted Data in Cloud Storage using ARM
 Secure Role-Based Access Control on Encrypted Data in Cloud Storage using ARM Rohini Vidhate, V. D. Shinde Abstract With the rapid developments occurring in cloud computing and services, there has been
Secure Role-Based Access Control on Encrypted Data in Cloud Storage using ARM Rohini Vidhate, V. D. Shinde Abstract With the rapid developments occurring in cloud computing and services, there has been
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Group User Revocation in Cloud for Shared Data
 Group User Revocation in Cloud for Shared Data Mahesh Salunke, Harshal Meher, Ajay Tambe, Sudir Deshmukh,Prof.Sanjay Agarwal Abstract With the excessive use of internet cloud has received much of the attention.
Group User Revocation in Cloud for Shared Data Mahesh Salunke, Harshal Meher, Ajay Tambe, Sudir Deshmukh,Prof.Sanjay Agarwal Abstract With the excessive use of internet cloud has received much of the attention.
Clock-Based Proxy Re-encryption Scheme in Unreliable Clouds
 Clock-Based Proxy Re-encryption Scheme in Unreliable Clouds Qin Liu [1][2], Guojun Wang [1], and Jie Wu [2], [1] Central South University, China [2] Temple University, USA 1 Outline 1. 1. Introduction
Clock-Based Proxy Re-encryption Scheme in Unreliable Clouds Qin Liu [1][2], Guojun Wang [1], and Jie Wu [2], [1] Central South University, China [2] Temple University, USA 1 Outline 1. 1. Introduction
Cyber Smarts Using Social Media Wisely
 Cyber Smarts Using Social Media Wisely Posted on March 24, 2016 by Shridevi Stock Photo You have access to the world s largest museum, art gallery, library and social group ever created. You also have
Cyber Smarts Using Social Media Wisely Posted on March 24, 2016 by Shridevi Stock Photo You have access to the world s largest museum, art gallery, library and social group ever created. You also have
China and International Governance of Cybercrime
 China and International Governance of Cybercrime Prof. Dr. Shenkuo WU Law Professor of CCLS, Beijing Normal University Head of Research Centre of Internet Society of China Consultant of Supreme Court of
China and International Governance of Cybercrime Prof. Dr. Shenkuo WU Law Professor of CCLS, Beijing Normal University Head of Research Centre of Internet Society of China Consultant of Supreme Court of
Electronic Commerce ~ Secure Messaging. V Rajaraman
 Electronic Commerce 3. Secure Messaging V Rajaraman In this part we will describe some of the security issues which arise in e-commerce. In particular we will describe firewalls, encryption techniques
Electronic Commerce 3. Secure Messaging V Rajaraman In this part we will describe some of the security issues which arise in e-commerce. In particular we will describe firewalls, encryption techniques
AES and DES Using Secure and Dynamic Data Storage in Cloud
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Protect Your Endpoint, Keep Your Business Safe. White Paper. Exosphere, Inc. getexosphere.com
 Protect Your Endpoint, Keep Your Business Safe. White Paper Exosphere, Inc. getexosphere.com White Paper Today s Threat Landscape Cyber attacks today are increasingly sophisticated and widespread, rendering
Protect Your Endpoint, Keep Your Business Safe. White Paper Exosphere, Inc. getexosphere.com White Paper Today s Threat Landscape Cyber attacks today are increasingly sophisticated and widespread, rendering
On the Diculty of Software Key Escrow. Abstract. At Eurocrypt'95, Desmedt suggested a scheme which allows individuals to encrypt
 On the Diculty of Software Key Escrow Lars R. Knudsen Katholieke Universiteit Leuven Dept. Elektrotechniek-ESAT Kardinaal Mercierlaan 94 B-3001 Heverlee Torben P. Pedersen y Cryptomathic Arhus Science
On the Diculty of Software Key Escrow Lars R. Knudsen Katholieke Universiteit Leuven Dept. Elektrotechniek-ESAT Kardinaal Mercierlaan 94 B-3001 Heverlee Torben P. Pedersen y Cryptomathic Arhus Science
AoT: Authentication and Access Control for the Entire IoT Device Life-Cycle
 AoT: Authentication and Access Control for the Entire IoT Device Life-Cycle Noura Alomar November 7th, 2018 1 AoT The AoT paper is one of the earliest and most cited papers on IoT defense and it considers
AoT: Authentication and Access Control for the Entire IoT Device Life-Cycle Noura Alomar November 7th, 2018 1 AoT The AoT paper is one of the earliest and most cited papers on IoT defense and it considers
II.C.4. Policy: Southeastern Technical College Computer Use
 II.C.4. Policy: Southeastern Technical College Computer Use 1.0 Overview Due to the technological revolution in the workplace, businesses such as Southeastern Technical College (STC) have turned to computer
II.C.4. Policy: Southeastern Technical College Computer Use 1.0 Overview Due to the technological revolution in the workplace, businesses such as Southeastern Technical College (STC) have turned to computer
Key Escrow free Identity-based Cryptosystem
 Key Escrow free Manik Lal Das DA-IICT, Gandhinagar, India About DA-IICT and Our Group DA-IICT is a private university, located in capital of Gujarat state in India. DA-IICT offers undergraduate and postgraduate
Key Escrow free Manik Lal Das DA-IICT, Gandhinagar, India About DA-IICT and Our Group DA-IICT is a private university, located in capital of Gujarat state in India. DA-IICT offers undergraduate and postgraduate
State of Israel Prime Minister's Office National Cyber Bureau. Unclassified
 - 1 - Background for the Government Resolutions Regarding Advancing the National Preparedness for Cyber Security and Advancing National Regulation and Governmental Leadership in Cyber Security On February
- 1 - Background for the Government Resolutions Regarding Advancing the National Preparedness for Cyber Security and Advancing National Regulation and Governmental Leadership in Cyber Security On February
ACCEPTABLE USE POLICY
 Great Lakes Energy Connections, Inc. Truestream ACCEPTABLE USE POLICY Contents OVERVIEW... 2 INTRODUCTION... 2 VIOLATION OF THIS ACCEPTABLE USE POLICY... 2 PROHIBITED USES AND ACTIVITIES... 2 CUSTOMER
Great Lakes Energy Connections, Inc. Truestream ACCEPTABLE USE POLICY Contents OVERVIEW... 2 INTRODUCTION... 2 VIOLATION OF THIS ACCEPTABLE USE POLICY... 2 PROHIBITED USES AND ACTIVITIES... 2 CUSTOMER
Technology Safety Quick Tips
 Technology Safety Quick Tips Spyware: Computer & Phone Monitoring Software It enables a person to secretly monitor someone else s entire computer activity. It can be installed remotely by sending an email,
Technology Safety Quick Tips Spyware: Computer & Phone Monitoring Software It enables a person to secretly monitor someone else s entire computer activity. It can be installed remotely by sending an email,
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that simplifies security and significantly
Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that simplifies security and significantly
Assistant Professor, Dept of CSE, Vasireddy Venkatadri Institute of Technology (VVIT), Nambur (v), Guntur, Andhra Pradesh, India
 Volume 5, Issue 10, October-2015 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Efficient User
Volume 5, Issue 10, October-2015 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Efficient User
Quick recap on ing Security Recap on where to find things on Belvidere website & a look at the Belvidere Facebook page
 Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
1. INTRODUCTION 2. PROPOSED SYSTEM. Parashar Sangle, IJECS Volume 05 Issue 12 Dec., 2016 Page No Page 19489
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN: 2319-7242 Volume 5 Issue 12 Dec. 2016, Page No. 19489-19493 Data Security System in Cloud by Using Fog Computing and Data Mining
www.ijecs.in International Journal Of Engineering And Computer Science ISSN: 2319-7242 Volume 5 Issue 12 Dec. 2016, Page No. 19489-19493 Data Security System in Cloud by Using Fog Computing and Data Mining
Implementation of IBE with Outsourced Revocation technique in Cloud Computing
 Implementation of IBE with Outsourced Revocation technique in Cloud Computing M.MOHANRAO, POCKLA PAVANI Assistant Professor, M.TECH STUDENT Dept of CSE,Megha Institute of Engineering & Technology For womens,edulabad,ghatkesar
Implementation of IBE with Outsourced Revocation technique in Cloud Computing M.MOHANRAO, POCKLA PAVANI Assistant Professor, M.TECH STUDENT Dept of CSE,Megha Institute of Engineering & Technology For womens,edulabad,ghatkesar
OVERVIEW OF SUBJECT REQUIREMENTS
 Course Bachelor of Information Technology (Network Security) Course Number HE20524 Location Meadowbank OVERVIEW OF SUBJECT REQUIREMENTS Note: This document is intended as a guide only. Enrolling students
Course Bachelor of Information Technology (Network Security) Course Number HE20524 Location Meadowbank OVERVIEW OF SUBJECT REQUIREMENTS Note: This document is intended as a guide only. Enrolling students
Improvement of Camenisch-Neven-Shelat Oblivious Transfer Scheme
 Improvement of Camenisch-Neven-Shelat Oblivious Transfer Scheme Zhengjun Cao and Hanyue Cao Department of Mathematics, Shanghai University, Shanghai, China caozhj@shu.edu.cn Abstract. In 2007, Camenisch,
Improvement of Camenisch-Neven-Shelat Oblivious Transfer Scheme Zhengjun Cao and Hanyue Cao Department of Mathematics, Shanghai University, Shanghai, China caozhj@shu.edu.cn Abstract. In 2007, Camenisch,
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY
 INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK THE STUDY OF PROGRESSION OF TECHNOLOGY AND THEIR AMPLIFICATION OF DIFFERENT TYPES
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK THE STUDY OF PROGRESSION OF TECHNOLOGY AND THEIR AMPLIFICATION OF DIFFERENT TYPES
Dark Web. Ronald Bishof, MS Cybersecurity. This Photo by Unknown Author is licensed under CC BY-SA
 Dark Web Ronald Bishof, MS Cybersecurity This Photo by Unknown Author is licensed under CC BY-SA Surface, Deep Web and Dark Web Differences of the Surface Web, Deep Web and Dark Web Surface Web - Web
Dark Web Ronald Bishof, MS Cybersecurity This Photo by Unknown Author is licensed under CC BY-SA Surface, Deep Web and Dark Web Differences of the Surface Web, Deep Web and Dark Web Surface Web - Web
E-guide Getting your CISSP Certification
 Getting your CISSP Certification Intro to the 10 CISSP domains of the Common Body of Knowledge : The Security Professional (CISSP) is an information security certification that was developed by the International
Getting your CISSP Certification Intro to the 10 CISSP domains of the Common Body of Knowledge : The Security Professional (CISSP) is an information security certification that was developed by the International
Making Decryption Accountable
 Making Decryption Accountable Mark D. Ryan University of Birmingham Abstract. Decryption is accountable if the users that create ciphertexts can gain information about the circumstances of the decryptions
Making Decryption Accountable Mark D. Ryan University of Birmingham Abstract. Decryption is accountable if the users that create ciphertexts can gain information about the circumstances of the decryptions
1-7 Attacks on Cryptosystems
 1-7 Attacks on Cryptosystems In the present era, not only business but almost all the aspects of human life are driven by information. Hence, it has become imperative to protect useful information from
1-7 Attacks on Cryptosystems In the present era, not only business but almost all the aspects of human life are driven by information. Hence, it has become imperative to protect useful information from
