How to Configure User Authentication and Access Control
|
|
|
- Bernard Marsh
- 5 years ago
- Views:
Transcription
1 How to Configure User Authentication and Access Control For user authentication with the HTTP Proxy, the external authentication scheme that you can use depends on the proxy mode. With a transparent or reverse proxy, you can only use the Barracuda DC Agent. With the forward proxy, you can use either MS-CHAP or Kerberos. To configure access control, you have the following options: Access Control Policy An access control policy is composed of ACL entries that define the connections to be restricted or allowed. An ACL entry can define IP addresses, domains, users, groups, browsers, MIME types, URLs, protocols, ports, connections, and times. Access control policies are processed one by one, according to their priority numbers. You can specify the priority of a policy when you create it. Access Control File List In addition to ACL entries and policies, you can also configure ACL file lists. ACL file lists are processed before ACL entries and policies. Legacy ACL Settings With this option, you can configure ACL files using the squid.conf syntax. From the command line, you can check the syntax of the squid.conf file. In this article: Configure User Authentication To configure user authentication, follow the instructions for the HTTP Proxy mode that you are using: Transparent and Reverse Proxy Authentication With a transparent or reverse proxy, you can only configure user authentication with the Barracuda DC Agent. For instructions on how to set up the Barracuda DC Agent with the Barracuda NG Firewall, see How to Configure MSAD DC Client Authentication. For general information about the Barracuda DC Agent, see Barracuda DC Agent for User Authentication. Forward Proxy Authentication With the forward proxy, you can use either MS-CHAP or Kerberos for user authentication. If you want your users to authenticate themselves on a Windows domain controller or a RADIUS server, activate and configure Kerberos. To configure user authentication for the forward proxy: 1. Verify that you have properly configured the external authentication scheme for the forward proxy: MS-CHAP For instructions, see How to Configure MS-CHAP Authentication. Kerberos For instructions, see How to Configure Kerberos Authentication. Open the HTTP Proxy Settings page (Config > Full Config > Virtual Servers > your virtual server > Assigned Services > HTTP-Proxy). 3. Click Lock. 4. From the Configuration menu in the left navigation pane, select User Authentication. 5. Next to Authentication Settings, click Set. To use MS-CHAPv2, edit the settings in the MS-CHAPv2 Settings section. To use Kerberos, edit the settings in the Kerberos Settings section. 6. Click OK. 1 / 10
2 7. Click Send Changes and Activate. Configure Access Control To configure access control, you have the following options: Access Control Policy First create the ACL entries that are required by the policy. Then create the access control policy by adding the ACL entries and selecting an action to handle them. To configure an an access control policy: Open the HTTP-Proxy Settings page (Config > Full Config > Virtual Servers > your virtual server > Assigned Services > HTTP-Proxy). From the Configuration menu in the left navigation pane, click Access Control. Click Lock. From the Default Access Control Policy list, select Allow. In the ACL Entries table, add all of the entries that are required for the access control policy. For each entry: 1. In the Enter Name window, enter a name for the entry, specify the entry type, and then click OK. In the ACL Entries window, configure the entry settings and then click OK. If you choose to later delete an ACL entry, you must also delete it from any ACL policies that it has been added to. When you delete an ACL entry, it is not automatically deleted from ACL policies. Actions with broken links to its parent will cause the proxy to fail. 6. In the Access Control Policies table, add the policy. 1. Enter a name for the policy and click OK. In the Access Control Policies configuration window, specify the priority, required ACL entries, and action for the policy. Then click OK For more details on the settings that you can configure for the ACL entries or access control policies, see Access Control Settings. Click Send Changes and Activate. For examples and explanations to help you understand access control policies, see Access Control Policy Example. Access Control File List To configure an ACL file list: Open the HTTP-Proxy Settings page (Config > Full Config > Virtual Servers > your virtual server > Assigned Services > HTTP-Proxy). From the Configuration menu in the left navigation pane, click Access Control. From the Configuration Mode menu in the left navigation pane, click Switch to Advanced View. Click Lock. From the Default Access Control Policy list, select Allow. In the ACL FileList table, add the ACL file list. 1. Enter a name for the list and then click OK. The name must be numerical. It determines the priority of the ACL file list. To assign higher priority to the ACL file list, enter a lower number. 2 / 10
3 In the ACL FileList window, configure the file list. Specify the following settings: Filename The name of the ACL file. By default, the file is saved to the /var/phion/preserve/proxy/<servername>_<servicename>/root/ directory. You can save the file to a different location, but this is not recommended. First verify that the destination directory has been properly created. When you specify the file name, add the absolute path to the destination directory. Do not use file names such as squid.conf and ftpsquid.conf; otherwise, you may lose configuration information. To avoid such situations, it is recommended that you use the default location and.acl as the file name extension. For example, aclfile.acl. ACL Entries The entries that are written to the file. ACL entries are processed line by line. If a line must exceed 1012 characters, use the forward slash (/) to section lines. ACL entries must match the squid.conf syntax. They are not checked against squid.conf for compatibility. Do NOT use Inverted CIDR Notation. Access control policies will only apply if all ACL entries are met. For example, if you add three ACL entries to one policy, the policy only applies if all three ACL entries match Click OK. Click Send Changes and Activate. Legacy ACL Settings To configure legacy ACL settings: Open the HTTP-Proxy Settings page (Config > Full Config > Virtual Servers > your virtual server > Assigned Services > HTTP-Proxy). From the Configuration menu in the left navigation pane, click Access Control. From the Configuration Mode menu in the left navigation pane, click Switch to Advanced View. Click Lock. From the Default Access Control Policy list, select Allow. From the Access Configuration list, select legacy. Next to Legacy, click Set. 8. In the Access Control Entries field, enter your ACL entries. These entries must use the squid.conf syntax. You can enter complete ACLs, as well as entries from the ACL file list. Because your ACL entries are not checked against squid.conf for compatibility, make sure that you use the exact syntax. Do NOT use inverted CIDR notation. 9. Click OK. 10. Click Send Changes and Activate. 3 / 10
4 The squid.conf file can be located at /var/phion/preserve/proxy/<servername_servicename>/root/. Check the squid.conf Syntax To check the syntax of the squid.conf file from the command line, enter: squid -X -N -f /phion0/preserve/proxy/<servername_servicename>/root/squid.conf If there are any errors in your configuration, the number of the row that contains the error is printed. On the Barracuda NG Firewall, Perl-compatible regular expressions (PCRE) can be used (for example in the HTTP Proxy server ACL configuration section). You can use PCRE when you want to substitute hard coded character strings against expressions that match in multiple cases. For an overview of meta characters in regular expressions, see Regular Expressions. Access Control Policy Example These sections provide steps to configure two example access control policies and an explanation of how the the policies are processed: Creating the Example Access Control Policies This example procedure configures two access control policies that limit FTP and HTTP access for a client at to the following days and times: Access Control Policy Access Times FTP Access Mondays, 08:00-12:00 and 14:00-17:00 HTTP Access Mondays to Fridays, 08:00-17:00 First create all of the required ACL entries. Then add these entries to the policies Open the HTTP-Proxy Settings page (Config > Full Config > Virtual Servers > your virtual server > Assigned Services > HTTP-Proxy). From the Configuration menu in the left navigation pane, click Access Control. Click Lock. From the Default Access Control Policy list, select Allow. In the ACL Entries table, create these ACL entries: ACL Entry Name clientpc ACL Entry Type Source IP IP Configuration: Singlemode Set IPs: portftp TCP-Port Specify Destination Port Address: 21 porthttp TCP-Port Specify Destination Port Address: 80 protocolftp Protocol Define Transfer Protocol: FTP protocolhttp Protocol Define Transfer Protocol: HTTP Settings 4 / 10
5 Access is enabled during Mondays from 08:00 to 12:00 and 14:00 to 17:00: timeftp Time Restrictions Access is enabled during Mondays to Fridays from 08:00 to 17:00: timeweb Time Restrictions After all of the required ACL entries are created, they are displayed in the ACL Entries table as follows: In the squid.conf file, the days of the week are stated as follows: M Monday T Tuesday W Wednesday H Thursday F Friday A Saturday S Sunday For the example timeftp and timehttp settings, the following ACL entries are generated in squid.conf for all of the times when access is enabled: timeftp timehttp 5 / 10
6 acl mytime time M 08:00-12:00 acl mytime time M 14:00-17:00 There are two entries for Monday because access is enabled from 8:00 to 12:00, restricted from 12:00 to 14:00, and then re-enabled from 14:00 to 17:00. acl mytime time M 08:00-17:00 acl mytime time T 08:00-17:00 acl mytime time W 08:00-17:00 acl mytime time H 08:00-17:00 acl mytime time F 08:00-17:00 6. In the Access Control Policies table, create these access control policies: Access Control Policy Name webaccess ftpaccess Settings ACL Priority: 1 Action: Allow ACL Entries for this Action: clientpc porthttp protocolhttp timeweb ACL Priority: 2 Action: Allow ACL Entries for this Action: clientpc portftp protocolftp timeftp After the access control policies are created, they are displayed in the Access Control Policies as follows: In squid.conf, the following lines are generated for the example webaccess and ftpaccess policies: http_access allow clientpc porthttp protocolhttp timeweb http_access allow clientpc portftp protocolftp timeftp Processing of the Example Policies When the HTTP proxy URL filter is configured with the example webaccess and ftpaccess policies, it grants access to connections that match the ACL entries that are included in the policies. To determine if access should be granted, the HTTP proxy URL filter first processes the webaccess policy (which has higher priority) for a match. If the connection does not match the webaccess policy, then the ftpaccess policy is processed. The policies are processed as follows: 6 / 10
7 1. If clientpc AND porthttp AND protocolhttp AND timeweb are TRUE, grant access and stop processing rules. Otherwise, proceed to the next rule. If clientpc AND portftp AND protocolftp AND timeftp are TRUE, grant access. Example Scenarios It is Monday at 9:00. If a user at tries to access the Internet on port 80, the first rule is processed. The connection is allowed by the http_access rule because clientpc AND porthttp AND protocolhttp AND timeweb are TRUE. No other rules are processed. It is Monday at 18:00. If a user at tries to access an FTP server on port 21, the the first rule is processed and determined to be FALSE because the connection does not match any criteria except for clientpc. Subsequently the second rule is processed, but it is determined that the connection does not match timeftp. The connection attempt is then rejected because it does not match both rules. Access Control Settings These sections provide more detailed descriptions of the settings that you configure for ACL entries and access control policies: ACL Entries Settings This table provides descriptions of the setting that you can configure for each ACL entry type: ACL Type Time Restrictions Source IP Destination IP Source IPv6 Destination IPv6 Source Domain Destination Domain Description Defines times and days. For this ACL entry type, you can configure the following settings: Time Zone Select one of the following options to specify which time zone to use: Use Local Box Time Zone Uses the local time zone of the system. explicit Uses the time zone that is selected from the following Time Zone list. Time Settings Click Always and then select the required days and times in the Time Interval window. If specific days and times have already been selected for the time restriction, Always is changed to Restricted. By default, the configuration is always active. Use Extended Time List Enables the days and times that are listed in the Extended Time List table instead of those that are configured in the Time Settings section. (This setting is only available if Advanced View is selected from the Configuration Mode menu on the left.) Extended Time List In this table, add an entry for each day of the week. For each day, specify the times to include. If time restriction applies, the label of the button changes to Restricted!. Defines the source or destination IP address of a connection. For these ACL entry types, you can configure the following settings: IP Configuration From this list, select one of the following options to specify if you are adding specific IP addresses or a range of IP addresses: Singlemode Select to add specific IP addresses. Rangemode Select to add a range of IP addresses. NG Admin Settings applies if activated. IP Ranges From To In these fields, enter the first and last IP addresses in the IP range. Single IPs In this section, add specific IP addresses to the Set IPs table. Defines client domains. Add the domains to the Domains table. Include a dot before the domain names. Example:.barracuda.com. Processing delays may be caused when using domain names. Squid needs to reverse DNS lookups (from client IP address to client domain name) before it can interpret the ACL. 7 / 10
8 User Authentication Groups URL Path URL Maximum Connections Protocol Requestmethod TCP Port Browser Mime Types URL Filter Categories Defines users who must authenticate themselves in an external authentication program. For this ACL entry type, you can configure the following settings: Required for All Users Specifies if all users or only select users using the proxy must authenticate themselves. From this list, you can select: yes All users must be authenticated. no Only certain users must be authenticated. Add these users to the following Users table. Users If only certain users must be authentication, add their usernames to this table. Defines groups. For this ACL entry type, you can configure the following settings: Interpret as RegEx If the groups list contains regular expressions and matching should be possible for RegEx meta symbols, select Yes. When this setting is enabled, the Partial Search and Case Insensitive settings are disabled. If there is only one meta symbol * or it is the first one in a RegEx, enter it by a leading. (dot). Partial Search To enable partial pattern matching, select Yes. Case insensitive If group matching is case insensitive, select Yes. Groups In this table, add meta directory group patterns. Group names are the distinguished names of meta directories. Example for LDAP: CN=myname, OU=myOU, DC=com Defines URL path regular expressions (urlpath_regex) that match the URL but not the protocol or hostname. In the URL Path Extensions table, add regular expressions, words, or word patterns. All entries are treated as case-insensitive. The urlpath_regex looks for the specified value in the URL path following the hostname. For example, with the word "example" will only be looked for within the path "/example/domain/index.htm". Defines URL extensions (url_regex) considering protocol and hostname (ACL Type = urlextension). In the URL Path Extensions table, add regular expressions, words, or word patterns. All entries are treated as case-insensitive. The url_regex looks for the specified value in the URL path including the protocol and hostname. Defines the maximum number of connections from a single client IP address. In the Define Maximum Connections field, enter this limit. The value of the ACL is TRUE if the limit is exceeded. Defines a list of protocols. In the Define Transfer Protocol table, add transfer protocols such as HTTP. Defines a list of request methods. In the Define Request Method table, add request methods such as GET, POST, or UPDATE. Defines a destination's port address. In the Specify Destination Port Address field, enter the destination server s port number. Defines regular expression patterns or words, matching the user-agent header transmitted during the request. In the Define Browser Access table, add the regular expressions or words. For example, if you add Firefox, it will be searched for in the user-agent header of an incoming request. Defines a list of MIME types. In the Mime Types table, add mime type expressions. For more information, see Defines an ACL consisting of URL filter categories. For this ACL entry type, you can configure the following settings: URL Filter Categories In this table, add the URL filter categories. Num Categorize Helpers The number of helpers for URL Filter categorization. 8 / 10
9 External Defines an ACL by using external helper programs. For this ACL entry type, you can configure the following settings: External Group Uses an existing external helper or a new one. External ACL Format Defines the ACL input format, for example: the external ACL input type. External ACL Binary Import dialogue for external ACL binaries/scripts. External ACL Binary Parameter Parameter that will be passed to the external ACL helper program/script. External Group Reference Select an already defined external group ACL. External ACL Parameter Parameter for the defined external ACL. Access Control Policies Settings This table provides descriptions of the settings that you can configure for access control policies: ACL Priority Action Setting ACL Entries for this Action Overall Maximum File Size ACL Policy Description Description Enter a number to specify the priority for this policy. To assign higher priority to a policy, enter a lower number. Access control policies with higher priority are processed first. Specifies how to handle the ACL entries that are added to this policy. You can select Allow, Deny or, Limit-Size. In this table, add the ACL entries to which the selected action will be applied. Access control policies will only apply if all ACL entries are met. For example, if you add three ACL entries to one policy, the policy only applies if all three ACL entries match. When you delete an ACL entry, you must also delete it from any access control policies that it has been added to. If the selected action for this policy is Limit-Size, enter the maximum size of files that can be downloaded. To disable this setting, enter 0. This setting may be configured more granular as ACL. Brief description of the policy action and the ACL entries that it affects. 9 / 10
10 Figures 10 / 10
How to Configure User Authentication and Access Control
 How to Configure User Authentication and Access Control For user authentication with the HTTP Proxy, the external authentication scheme that you can use depends on the proxy mode. With a transparent or
How to Configure User Authentication and Access Control For user authentication with the HTTP Proxy, the external authentication scheme that you can use depends on the proxy mode. With a transparent or
Example - Reverse Proxy for Exchange Services
 The reverse proxy redirects incoming requests from Microsoft Exchange Server services to clients without providing the origin details. This example configuration shows how to configure a reverse proxy
The reverse proxy redirects incoming requests from Microsoft Exchange Server services to clients without providing the origin details. This example configuration shows how to configure a reverse proxy
How to Configure Neighbor Proxies
 For the HTTP proxy service, you can configure the proxy server to treat adjacent proxies as parents or siblings. For the neighbor proxies, you can configure authentication and caching. Configure a Neighbor
For the HTTP proxy service, you can configure the proxy server to treat adjacent proxies as parents or siblings. For the neighbor proxies, you can configure authentication and caching. Configure a Neighbor
Connect the Appliance to a Cisco Cloud Web Security Proxy
 Connect the Appliance to a Cisco Cloud Web Security Proxy This chapter contains the following sections: How to Configure and Use Features in Cloud Connector Mode, on page 1 Deployment in Cloud Connector
Connect the Appliance to a Cisco Cloud Web Security Proxy This chapter contains the following sections: How to Configure and Use Features in Cloud Connector Mode, on page 1 Deployment in Cloud Connector
BIG-IP Access Policy Manager : Secure Web Gateway. Version 13.0
 BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
Best Practice - Protect Against TCP SYN Flooding Attacks with TCP Accept Policies
 Best Practice - Protect Against TCP SYN Flooding Attacks with TCP Accept Policies In order to establish a TCP connection, the TCP three-way handshake must be completed. You can use different accept policies
Best Practice - Protect Against TCP SYN Flooding Attacks with TCP Accept Policies In order to establish a TCP connection, the TCP three-way handshake must be completed. You can use different accept policies
IPv4 ACLs, identified by ACL numbers, fall into four categories, as shown in Table 1. Table 1 IPv4 ACL categories
 Table of Contents ACL Configuration 1 ACL Overview 1 IPv4 ACL Classification 1 IPv4 ACL Rule Order 1 Rule Numbering Step with IPv4 ACLs 3 Effective Time Period of an IPv4 ACL 3 IP Fragments Filtering with
Table of Contents ACL Configuration 1 ACL Overview 1 IPv4 ACL Classification 1 IPv4 ACL Rule Order 1 Rule Numbering Step with IPv4 ACLs 3 Effective Time Period of an IPv4 ACL 3 IP Fragments Filtering with
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
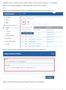 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Configuring Request Authentication and Authorization
 CHAPTER 15 Configuring Request Authentication and Authorization Request authentication and authorization is a means to manage employee use of the Internet and restrict access to online content. This chapter
CHAPTER 15 Configuring Request Authentication and Authorization Request authentication and authorization is a means to manage employee use of the Internet and restrict access to online content. This chapter
Syslog and the Barracuda Web Security Gateway
 What is the Barracuda Syslog? The Barracuda Web Security Gateway generates syslog messages as a means of logging both changes to the web interface configuration and what happens to each traffic request
What is the Barracuda Syslog? The Barracuda Web Security Gateway generates syslog messages as a means of logging both changes to the web interface configuration and what happens to each traffic request
Objects for Access Control
 Objects are reusable components for use in your configuration. You can define and use them in Cisco ASA configurations in the place of inline IP addresses, services, names, and so on. Objects make it easy
Objects are reusable components for use in your configuration. You can define and use them in Cisco ASA configurations in the place of inline IP addresses, services, names, and so on. Objects make it easy
How to Configure a Remote Management Tunnel for Barracuda NG Firewalls
 How to Configure a Remote Management Tunnel for Barracuda NG Firewalls If the managed NG Firewall can not directly reach the NG Control Center it must connect via a remote management tunnel. The remote
How to Configure a Remote Management Tunnel for Barracuda NG Firewalls If the managed NG Firewall can not directly reach the NG Control Center it must connect via a remote management tunnel. The remote
DM-NVX-E30(C) DigitalMedia 4K60 4:4:4 HDR Network AV Encoder Web interface Guide. Crestron Electronics, Inc.
 DM-NVX-E30(C) DigitalMedia 4K60 4:4:4 HDR Network AV Encoder Web interface Guide Crestron Electronics, Inc. The product warranty can be found at www.crestron.com/warranty. The specific patents that cover
DM-NVX-E30(C) DigitalMedia 4K60 4:4:4 HDR Network AV Encoder Web interface Guide Crestron Electronics, Inc. The product warranty can be found at www.crestron.com/warranty. The specific patents that cover
DM-NVX-D30(C) DigitalMedia 4K60 4:4:4 HDR Network AV Decoder Web interface Guide. Crestron Electronics, Inc.
 DM-NVX-D30(C) DigitalMedia 4K60 4:4:4 HDR Network AV Decoder Web interface Guide Crestron Electronics, Inc. The product warranty can be found at www.crestron.com/warranty. The specific patents that cover
DM-NVX-D30(C) DigitalMedia 4K60 4:4:4 HDR Network AV Decoder Web interface Guide Crestron Electronics, Inc. The product warranty can be found at www.crestron.com/warranty. The specific patents that cover
Security Provider Integration Kerberos Authentication
 Security Provider Integration Kerberos Authentication 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
Security Provider Integration Kerberos Authentication 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
ForeScout CounterACT. Configuration Guide. Version 4.3
 ForeScout CounterACT Authentication Module: RADIUS Plugin Version 4.3 Table of Contents Overview... 4 Understanding the 802.1X Protocol... 4 About the CounterACT RADIUS Plugin... 6 IPv6 Support... 7 About
ForeScout CounterACT Authentication Module: RADIUS Plugin Version 4.3 Table of Contents Overview... 4 Understanding the 802.1X Protocol... 4 About the CounterACT RADIUS Plugin... 6 IPv6 Support... 7 About
Configuring Content Authentication and Authorization on Standalone Content Engines
 CHAPTER 10 Configuring Content Authentication and Authorization on Standalone Content Engines This chapter describes how to configure content authentication and authorization on standalone Content Engines
CHAPTER 10 Configuring Content Authentication and Authorization on Standalone Content Engines This chapter describes how to configure content authentication and authorization on standalone Content Engines
Identity Firewall. About the Identity Firewall
 This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
Configuring Traffic Policies
 CHAPTER 11 Date: 4/23/09 Cisco Application Networking Manager helps you configure class maps and policy maps to provide a global level of classification for filtering traffic received by or passing through
CHAPTER 11 Date: 4/23/09 Cisco Application Networking Manager helps you configure class maps and policy maps to provide a global level of classification for filtering traffic received by or passing through
Security Provider Integration: Kerberos Server
 Security Provider Integration: Kerberos Server 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are the
Security Provider Integration: Kerberos Server 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are the
Barracuda Networks NG Firewall 7.0.0
 RSA SECURID ACCESS Standard Agent Implementation Guide Barracuda Networks.0 fal, RSA Partner Engineering Last Modified: 10/13/16 Solution Summary The Barracuda NG Firewall
RSA SECURID ACCESS Standard Agent Implementation Guide Barracuda Networks.0 fal, RSA Partner Engineering Last Modified: 10/13/16 Solution Summary The Barracuda NG Firewall
Managing External Identity Sources
 CHAPTER 5 The Cisco Identity Services Engine (Cisco ISE) integrates with external identity sources to validate credentials in user authentication functions, and to retrieve group information and other
CHAPTER 5 The Cisco Identity Services Engine (Cisco ISE) integrates with external identity sources to validate credentials in user authentication functions, and to retrieve group information and other
Comodo One Software Version 3.8
 rat Comodo One Software Version 3.8 Dome Cloud Firewall Quick Start Guide Guide Version 1.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Dome Cloud Firewall Quick Start This
rat Comodo One Software Version 3.8 Dome Cloud Firewall Quick Start Guide Guide Version 1.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Dome Cloud Firewall Quick Start This
Managing Authentication and Identity Services
 You can create access policies based on user identity rather than IP addresses. To enable identity-based services, you configure policies and options to obtain user identity, and then use identity objects
You can create access policies based on user identity rather than IP addresses. To enable identity-based services, you configure policies and options to obtain user identity, and then use identity objects
How to Integrate RSA SecurID with the Barracuda Web Application Firewall
 How to Integrate RSA SecurID with the Barracuda Web Application Firewall The Barracuda Web Application Firewall can be configured as a RADIUS client to the RSA SecurID Server System, comprised of the RSA
How to Integrate RSA SecurID with the Barracuda Web Application Firewall The Barracuda Web Application Firewall can be configured as a RADIUS client to the RSA SecurID Server System, comprised of the RSA
Configuring User Defined Patterns
 The allows you to create customized data patterns which can be detected and handled according to the configured security settings. The uses regular expressions (regex) to define data type patterns. Custom
The allows you to create customized data patterns which can be detected and handled according to the configured security settings. The uses regular expressions (regex) to define data type patterns. Custom
ZENworks 2017 Update 1 HTTP Proxy Reference. July 2017
 ZENworks 2017 Update 1 HTTP Proxy Reference July 2017 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent
ZENworks 2017 Update 1 HTTP Proxy Reference July 2017 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent
History Page. Barracuda NextGen Firewall F
 The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER
 DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER Table of Contents Table of Contents Introducing the F5 and Oracle Access Manager configuration Prerequisites and configuration notes... 1 Configuration
DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER Table of Contents Table of Contents Introducing the F5 and Oracle Access Manager configuration Prerequisites and configuration notes... 1 Configuration
Configuring Caching Services
 CHAPTER 8 This chapter describes how to configure conventional caching services (HTTP, FTP [FTP-over-HTTP caching and native FTP caching], HTTPS, and DNS caching) for centrally managed Content Engines.
CHAPTER 8 This chapter describes how to configure conventional caching services (HTTP, FTP [FTP-over-HTTP caching and native FTP caching], HTTPS, and DNS caching) for centrally managed Content Engines.
Configuring the Rules Template on Standalone Content Engines
 CHAPTER 13 Configuring the Rules Template on Standalone Content Engines This chapter describes how to configure the Rules Template on standalone Content Engines. The Rules Template specifies the rules
CHAPTER 13 Configuring the Rules Template on Standalone Content Engines This chapter describes how to configure the Rules Template on standalone Content Engines. The Rules Template specifies the rules
Load Balancing Overview
 The "Load Balancing" feature is available only in the Barracuda Web Application Firewall 460 and above. A load balancer is a networking device that distributes traffic across multiple back-end servers
The "Load Balancing" feature is available only in the Barracuda Web Application Firewall 460 and above. A load balancer is a networking device that distributes traffic across multiple back-end servers
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
Internet Architecture. Web Programming - 2 (Ref: Chapter 2) IP Software. IP Addressing. TCP/IP Basics. Client Server Basics. URL and MIME Types HTTP
 Web Programming - 2 (Ref: Chapter 2) TCP/IP Basics Internet Architecture Client Server Basics URL and MIME Types HTTP Routers interconnect the network TCP/IP software provides illusion of a single network
Web Programming - 2 (Ref: Chapter 2) TCP/IP Basics Internet Architecture Client Server Basics URL and MIME Types HTTP Routers interconnect the network TCP/IP software provides illusion of a single network
Forescout. Configuration Guide. Version 4.4
 Forescout Version 4.4 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 4.4 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
LDAP Servers for AAA
 This chapter describes how to configure LDAP servers used in AAA. About LDAP and the ASA, page 1 Guidelines for, page 5 Configure, page 5 Test LDAP Server Authentication and Authorization, page 9 Monitoring,
This chapter describes how to configure LDAP servers used in AAA. About LDAP and the ASA, page 1 Guidelines for, page 5 Configure, page 5 Test LDAP Server Authentication and Authorization, page 9 Monitoring,
User Identity Sources
 The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, on page 1 The
The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, on page 1 The
Security Provider Integration Kerberos Server
 Security Provider Integration Kerberos Server 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property
Security Provider Integration Kerberos Server 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property
DEPLOYMENT GUIDE Version 1.1. Deploying the BIG-IP Access Policy Manager with IBM, Oracle, and Microsoft
 DEPLOYMENT GUIDE Version 1.1 Deploying the BIG-IP Access Policy Manager with IBM, Oracle, and Microsoft Table of Contents Table of Contents Introducing the BIG-IP APM deployment guide Revision history...1-1
DEPLOYMENT GUIDE Version 1.1 Deploying the BIG-IP Access Policy Manager with IBM, Oracle, and Microsoft Table of Contents Table of Contents Introducing the BIG-IP APM deployment guide Revision history...1-1
How to Configure a Remote Management Tunnel for an F-Series Firewall
 How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
Scheduling WebEx Meetings with Microsoft Outlook
 Scheduling WebEx Meetings with Microsoft Outlook About WebEx Integration to Outlook, page 1 Scheduling a WebEx Meeting from Microsoft Outlook, page 2 Starting a Scheduled Meeting from Microsoft Outlook,
Scheduling WebEx Meetings with Microsoft Outlook About WebEx Integration to Outlook, page 1 Scheduling a WebEx Meeting from Microsoft Outlook, page 2 Starting a Scheduled Meeting from Microsoft Outlook,
Infoblox Authenticated DHCP
 Infoblox Authenticated DHCP Unified Visitor Management amigopod Technical Note Revision 1.1 5 July 2010 United States of America +1 (888) 590-0882 Europe, Middle East & Asia +34 91 766 57 22 Australia
Infoblox Authenticated DHCP Unified Visitor Management amigopod Technical Note Revision 1.1 5 July 2010 United States of America +1 (888) 590-0882 Europe, Middle East & Asia +34 91 766 57 22 Australia
Webthority can provide single sign-on to web applications using one of the following authentication methods:
 Webthority HOW TO Configure Web Single Sign-On Webthority can provide single sign-on to web applications using one of the following authentication methods: HTTP authentication (for example Kerberos, NTLM,
Webthority HOW TO Configure Web Single Sign-On Webthority can provide single sign-on to web applications using one of the following authentication methods: HTTP authentication (for example Kerberos, NTLM,
WatchGuard Firebox and MUVPN. Quick Start Guide. Copyright CRYPTOCard Corporation All Rights Reserved
 WatchGuard Firebox and MUVPN Quick Start Guide Copyright 2004 2005 CRYPTOCard Corporation All Rights Reserved 2005.04.15 http://www.cryptocard.com Table of Contents 1. PURPOSE...1 1.1 Prerequisites...
WatchGuard Firebox and MUVPN Quick Start Guide Copyright 2004 2005 CRYPTOCard Corporation All Rights Reserved 2005.04.15 http://www.cryptocard.com Table of Contents 1. PURPOSE...1 1.1 Prerequisites...
Router and ACL ACL Filter traffic ACL: The Three Ps One ACL per protocol One ACL per direction One ACL per interface
 CCNA4 Chapter 5 * Router and ACL By default, a router does not have any ACLs configured and therefore does not filter traffic. Traffic that enters the router is routed according to the routing table. *
CCNA4 Chapter 5 * Router and ACL By default, a router does not have any ACLs configured and therefore does not filter traffic. Traffic that enters the router is routed according to the routing table. *
Wireless LAN Controller Web Authentication Configuration Example
 Wireless LAN Controller Web Authentication Configuration Example Document ID: 69340 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Web Authentication Process
Wireless LAN Controller Web Authentication Configuration Example Document ID: 69340 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Web Authentication Process
Deploying and Provisioning the Barracuda CloudGen WAF in the Classic Microsoft Azure Management Portal
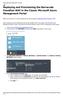 Deploying and Provisioning the Barracuda CloudGen WAF in the Classic Microsoft Azure Management Portal Before you proceed, it is recommended that you go through the Deployment Best Practices article. Before
Deploying and Provisioning the Barracuda CloudGen WAF in the Classic Microsoft Azure Management Portal Before you proceed, it is recommended that you go through the Deployment Best Practices article. Before
GSS Administration and Troubleshooting
 CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
Table of Contents. Cisco Configuring IP Access Lists
 Table of Contents Configuring IP Access Lists...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2 ACL Concepts...2 Masks...2 ACL Summarization...3 Process ACLs...4
Table of Contents Configuring IP Access Lists...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2 ACL Concepts...2 Masks...2 ACL Summarization...3 Process ACLs...4
ALTEVA ARCHIVE USER GUIDE
 ALTEVA ARCHIVE USER GUIDE Welcome This guide provides information about Alteva s SmartRecord IP End-User Interface features, functions, and reports presented as tools to be used to solve your business
ALTEVA ARCHIVE USER GUIDE Welcome This guide provides information about Alteva s SmartRecord IP End-User Interface features, functions, and reports presented as tools to be used to solve your business
Ciphermail Webmail Messenger Administration Guide
 CIPHERMAIL EMAIL ENCRYPTION Ciphermail Webmail Messenger Administration Guide October 27, 2017, Rev: 8630 Copyright 2013-2017, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Admin login
CIPHERMAIL EMAIL ENCRYPTION Ciphermail Webmail Messenger Administration Guide October 27, 2017, Rev: 8630 Copyright 2013-2017, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Admin login
SysMaster GW 7000 Digital Gateway. User Manual. version 1.0
 SysMaster GW 7000 Digital Gateway User Manual version 1.0 Copyright 2003 by All rights reserved. No part of this manual may be reproduced or transmitted in any form without written permission from. The
SysMaster GW 7000 Digital Gateway User Manual version 1.0 Copyright 2003 by All rights reserved. No part of this manual may be reproduced or transmitted in any form without written permission from. The
SuperLumin Nemesis. Getting Started Guide. February 2011
 SuperLumin Nemesis Getting Started Guide February 2011 SuperLumin Nemesis Legal Notices Information contained in this document is believed to be accurate and reliable. However, SuperLumin assumes no responsibility
SuperLumin Nemesis Getting Started Guide February 2011 SuperLumin Nemesis Legal Notices Information contained in this document is believed to be accurate and reliable. However, SuperLumin assumes no responsibility
Using Kerberos Authentication in a Reverse Proxy Environment
 Using Kerberos Authentication in a Reverse Proxy Environment Legal Notice Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat
Using Kerberos Authentication in a Reverse Proxy Environment Legal Notice Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat
WebsitePanel User Guide
 WebsitePanel User Guide User role in WebsitePanel is the last security level in roles hierarchy. Users are created by reseller and they are consumers of hosting services. Users are able to create and manage
WebsitePanel User Guide User role in WebsitePanel is the last security level in roles hierarchy. Users are created by reseller and they are consumers of hosting services. Users are able to create and manage
Amazon Virtual Private Cloud. Getting Started Guide
 Amazon Virtual Private Cloud Getting Started Guide Amazon Virtual Private Cloud: Getting Started Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks
Amazon Virtual Private Cloud Getting Started Guide Amazon Virtual Private Cloud: Getting Started Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks
Content Rules. Feature Description
 Feature Description UPDATED: 11 January 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo are registered trademarks
Feature Description UPDATED: 11 January 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo are registered trademarks
Configuring Administrative Operations
 Configuring Administrative Operations This section includes the following topics: Administrative Operation Conventions, page 1 Configuring Backup Operations, page 1 Restoring a Backup Configuration, page
Configuring Administrative Operations This section includes the following topics: Administrative Operation Conventions, page 1 Configuring Backup Operations, page 1 Restoring a Backup Configuration, page
Chapter 6 Global CONFIG Commands
 Chapter 6 Global CONFIG Commands aaa accounting Configures RADIUS or TACACS+ accounting for recording information about user activity and system events. When you configure accounting on an HP device, information
Chapter 6 Global CONFIG Commands aaa accounting Configures RADIUS or TACACS+ accounting for recording information about user activity and system events. When you configure accounting on an HP device, information
Barracuda Firewall Release Notes 6.6.X
 Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Copyright and Trademarks
 Copyright and Trademarks Specops Password Reset is a trademark owned by Specops Software. All other trademarks used and mentioned in this document belong to their respective owners. 2 Contents Key Components
Copyright and Trademarks Specops Password Reset is a trademark owned by Specops Software. All other trademarks used and mentioned in this document belong to their respective owners. 2 Contents Key Components
Identity Policies. Identity Policy Overview. Establishing User Identity through Active Authentication
 You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
MediCal QAWeb Relay installation instructions
 MediCal QAWeb Relay installation instructions Table of contents Minimum system requirements...2 Gathering important information...2 Configuring network devices...4 Installing MediCal QAWeb Relay...8 Reinstalling/updating
MediCal QAWeb Relay installation instructions Table of contents Minimum system requirements...2 Gathering important information...2 Configuring network devices...4 Installing MediCal QAWeb Relay...8 Reinstalling/updating
BIG-IP Access Policy Manager : Implementations. Version 12.1
 BIG-IP Access Policy Manager : Implementations Version 12.1 Table of Contents Table of Contents Web Access Management...11 Overview: Configuring APM for web access management...11 About ways to time out
BIG-IP Access Policy Manager : Implementations Version 12.1 Table of Contents Table of Contents Web Access Management...11 Overview: Configuring APM for web access management...11 About ways to time out
Configuring Web-Based Authentication
 This chapter describes how to configure web-based authentication on the switch. It contains these sections: Finding Feature Information, page 1 Web-Based Authentication Overview, page 1 How to Configure
This chapter describes how to configure web-based authentication on the switch. It contains these sections: Finding Feature Information, page 1 Web-Based Authentication Overview, page 1 How to Configure
How to Configure ATP in the HTTP Proxy
 Configure when and which types of files are uploaded to the Barracuda ATP Cloud for traffic passing through the HTTP proxy service. Users will receive downloaded files immediately. When files with a risk
Configure when and which types of files are uploaded to the Barracuda ATP Cloud for traffic passing through the HTTP proxy service. Users will receive downloaded files immediately. When files with a risk
3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings 4. Select the check box for SPoE as default.
 Week 1 Lab Lab 1: Connect to the Barracuda network. 1. Download the Barracuda NG Firewall Admin 5.4 2. Launch NG Admin 3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings
Week 1 Lab Lab 1: Connect to the Barracuda network. 1. Download the Barracuda NG Firewall Admin 5.4 2. Launch NG Admin 3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings
Office 365 Standalone Security
 The standalone Email Security option is available for purchase only through the Barracuda Self-Service Gateway or Barracuda MSP. Once you complete the Essentials for Office 365 Wizard, the Essentials page
The standalone Email Security option is available for purchase only through the Barracuda Self-Service Gateway or Barracuda MSP. Once you complete the Essentials for Office 365 Wizard, the Essentials page
User Identity Sources
 The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, page 1 The User
The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, page 1 The User
How to Integrate an External Authentication Server
 How to Integrate an External Authentication Server Required Product Model and Version This article applies to the Barracuda Load Balancer ADC 540 and above, version 5.1 and above, and to all Barracuda
How to Integrate an External Authentication Server Required Product Model and Version This article applies to the Barracuda Load Balancer ADC 540 and above, version 5.1 and above, and to all Barracuda
Okta Integration Guide for Web Access Management with F5 BIG-IP
 Okta Integration Guide for Web Access Management with F5 BIG-IP Contents Introduction... 3 Publishing SAMPLE Web Application VIA F5 BIG-IP... 5 Configuring Okta as SAML 2.0 Identity Provider for F5 BIG-IP...
Okta Integration Guide for Web Access Management with F5 BIG-IP Contents Introduction... 3 Publishing SAMPLE Web Application VIA F5 BIG-IP... 5 Configuring Okta as SAML 2.0 Identity Provider for F5 BIG-IP...
Create and Apply Clientless SSL VPN Policies for Accessing. Connection Profile Attributes for Clientless SSL VPN
 Create and Apply Clientless SSL VPN Policies for Accessing Resources, page 1 Connection Profile Attributes for Clientless SSL VPN, page 1 Group Policy and User Attributes for Clientless SSL VPN, page 3
Create and Apply Clientless SSL VPN Policies for Accessing Resources, page 1 Connection Profile Attributes for Clientless SSL VPN, page 1 Group Policy and User Attributes for Clientless SSL VPN, page 3
Microsoft Microsoft TS: MS Internet Security & Acceleration Server 2006, Configuring. Practice Test. Version:
 Microsoft 70-351 Microsoft 70-351 TS: MS Internet Security & Acceleration Server 2006, Configuring Practice Test Version: 2.2 QUESTION NO: 1 Your network consists of a single Active Directory domain named
Microsoft 70-351 Microsoft 70-351 TS: MS Internet Security & Acceleration Server 2006, Configuring Practice Test Version: 2.2 QUESTION NO: 1 Your network consists of a single Active Directory domain named
Using Centralized Security Reporting
 This chapter contains the following sections: Centralized Email Reporting Overview, on page 1 Setting Up Centralized Email Reporting, on page 2 Working with Email Report Data, on page 4 Understanding the
This chapter contains the following sections: Centralized Email Reporting Overview, on page 1 Setting Up Centralized Email Reporting, on page 2 Working with Email Report Data, on page 4 Understanding the
C L O U D V O I C E B U S I N E S S P O R T A L
 C L O U D V O I C E B U S I N E S S P O R T A L A P P L I C A T I O N U S E R G U I DE T O O L B A R V E R S I O N 2. 0 Page 1 of 29 Toolbar Application User guide Contents Overview... 4 Hardware & Software
C L O U D V O I C E B U S I N E S S P O R T A L A P P L I C A T I O N U S E R G U I DE T O O L B A R V E R S I O N 2. 0 Page 1 of 29 Toolbar Application User guide Contents Overview... 4 Hardware & Software
How to Configure Guest Access with the Ticketing System
 How to Configure Guest Access with the Ticketing System Set up a login or ticketing system to temporarily grant access to guest users. Ticketing admins assign guest tickets to the users. The user credentials
How to Configure Guest Access with the Ticketing System Set up a login or ticketing system to temporarily grant access to guest users. Ticketing admins assign guest tickets to the users. The user credentials
Configuring the CSS for Device Management
 CHAPTER 2 Configuring the CSS for Device Management Before you can use the WebNS Device Management user interface software, you need to perform the tasks described in the following sections: WebNS Device
CHAPTER 2 Configuring the CSS for Device Management Before you can use the WebNS Device Management user interface software, you need to perform the tasks described in the following sections: WebNS Device
Cisco Secure ACS 3.0+ Quick Start Guide. Copyright , CRYPTOCard Corporation, All Rights Reserved
 Cisco Secure ACS 3.0+ Quick Start Guide Copyright 2004-2005, CRYPTOCard Corporation, All Rights Reserved. 2005.05.06 http://www.cryptocard.com Table of Contents OVERVIEW... 1 CONFIGURING THE EXTERNAL
Cisco Secure ACS 3.0+ Quick Start Guide Copyright 2004-2005, CRYPTOCard Corporation, All Rights Reserved. 2005.05.06 http://www.cryptocard.com Table of Contents OVERVIEW... 1 CONFIGURING THE EXTERNAL
CounterACT 802.1X Plugin
 CounterACT 802.1X Plugin Version 4.2.0 Table of Contents Overview... 4 Understanding the 802.1X Protocol... 4 About the CounterACT 802.1X Plugin... 6 About This Document... 7 802.1X Plugin Components...
CounterACT 802.1X Plugin Version 4.2.0 Table of Contents Overview... 4 Understanding the 802.1X Protocol... 4 About the CounterACT 802.1X Plugin... 6 About This Document... 7 802.1X Plugin Components...
How to Configure the RSA Authentication Manager
 How to Configure the RSA Authentication Manager The Barracuda Load Balancer ADC can be configured as a RADIUS client to the RSA SecurID Server System, comprised of the RSA Authentication Manager and the
How to Configure the RSA Authentication Manager The Barracuda Load Balancer ADC can be configured as a RADIUS client to the RSA SecurID Server System, comprised of the RSA Authentication Manager and the
Skandocs Installation and Connectivity Guide What you need to know to successfully utilise the Internet connectivity in Skandocs
 Skandocs Installation and Connectivity Guide What you need to know to successfully utilise the Internet connectivity in Skandocs Intended Audience This document is aimed at IT technical support professionals
Skandocs Installation and Connectivity Guide What you need to know to successfully utilise the Internet connectivity in Skandocs Intended Audience This document is aimed at IT technical support professionals
Apptix Online Backup by Mozy User Guide
 Apptix Online Backup by Mozy User Guide 1.10.1.2 Contents Chapter 1: Overview...5 Chapter 2: Installing Apptix Online Backup by Mozy...7 Downloading the Apptix Online Backup by Mozy Client...7 Installing
Apptix Online Backup by Mozy User Guide 1.10.1.2 Contents Chapter 1: Overview...5 Chapter 2: Installing Apptix Online Backup by Mozy...7 Downloading the Apptix Online Backup by Mozy Client...7 Installing
Sophos Mobile as a Service
 startup guide Product Version: 8 Contents About this guide... 1 What are the key steps?... 2 Change your password... 3 Change your login name... 4 Activate Mobile Advanced licenses...5 Check your licenses...6
startup guide Product Version: 8 Contents About this guide... 1 What are the key steps?... 2 Change your password... 3 Change your login name... 4 Activate Mobile Advanced licenses...5 Check your licenses...6
User and System Administration
 CHAPTER 2 This chapter provides information about performing user and system administration tasks and generating diagnostic information for obtaining technical assistance. The top-level Admin window displays
CHAPTER 2 This chapter provides information about performing user and system administration tasks and generating diagnostic information for obtaining technical assistance. The top-level Admin window displays
BlueCoat BCCPP. Blue Coat Certified Proxy Professional.
 BlueCoat BCCPP Blue Coat Certified Proxy Professional https://killexams.com/pass4sure/exam-detail/bccpp Question: 201 Which method of controlling downloads of certain file types works fastest on ProxySG?
BlueCoat BCCPP Blue Coat Certified Proxy Professional https://killexams.com/pass4sure/exam-detail/bccpp Question: 201 Which method of controlling downloads of certain file types works fastest on ProxySG?
VII. Corente Services SSL Client
 VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
Advanced Clientless SSL VPN Configuration
 Microsoft Kerberos Constrained Delegation Solution, page 1 Configure Application Profile Customization Framework, page 7 Encoding, page 11 Use Email over Clientless SSL VPN, page 13 Microsoft Kerberos
Microsoft Kerberos Constrained Delegation Solution, page 1 Configure Application Profile Customization Framework, page 7 Encoding, page 11 Use Email over Clientless SSL VPN, page 13 Microsoft Kerberos
Creating a File and Folder Backup
 Applicable Products These instructions apply to the following products: Barracuda Intronis Backup - MSP How to Create a Files and Folders Backup Before creating a files and folders backup set, make sure
Applicable Products These instructions apply to the following products: Barracuda Intronis Backup - MSP How to Create a Files and Folders Backup Before creating a files and folders backup set, make sure
Smart Machine Smart Decision. R700_User Guide_V1.05 1
 R700_User Guide_V1.05 R700_User Guide_V1.05 1 Document Title R700_User Guide Version 1.05 Date Status Document Control ID Released R700_User Guide_V1.05 General Notes SIMCom offers this information as
R700_User Guide_V1.05 R700_User Guide_V1.05 1 Document Title R700_User Guide Version 1.05 Date Status Document Control ID Released R700_User Guide_V1.05 General Notes SIMCom offers this information as
Checkpoint VPN-1 NG/FP3
 Checkpoint VPN-1 NG/FP3 Quick Start Guide Copyright 2002-2005 CRYPTOCard Corporation All Rights Reserved 2005.04.15 http://www.cryptocard.com Table of Contents SECTION 1... 1 OVERVIEW... 1 PREPARATION
Checkpoint VPN-1 NG/FP3 Quick Start Guide Copyright 2002-2005 CRYPTOCard Corporation All Rights Reserved 2005.04.15 http://www.cryptocard.com Table of Contents SECTION 1... 1 OVERVIEW... 1 PREPARATION
IP Access List Overview
 Access control lists (ACLs) perform packet filtering to control which packets move through the network and where. Such control provides security by helping to limit network traffic, restrict the access
Access control lists (ACLs) perform packet filtering to control which packets move through the network and where. Such control provides security by helping to limit network traffic, restrict the access
Cisco Cloud Web Security
 Cisco Cloud Web Security WSA ment Guide Internal Use Only 1 October 2014 Cisco CWS WSA/WSAv ment Guide Contents Introduction... 1 Cloud ment... 1 Additional Redirect Methods... 1... 2 Verify connection
Cisco Cloud Web Security WSA ment Guide Internal Use Only 1 October 2014 Cisco CWS WSA/WSAv ment Guide Contents Introduction... 1 Cloud ment... 1 Additional Redirect Methods... 1... 2 Verify connection
Sophos Mobile SaaS startup guide. Product version: 7.1
 Sophos Mobile SaaS startup guide Product version: 7.1 Contents 1 About this guide...4 2 What are the key steps?...5 3 Change your password...6 4 Change your login name...7 5 Activate SMC Advanced licenses...8
Sophos Mobile SaaS startup guide Product version: 7.1 Contents 1 About this guide...4 2 What are the key steps?...5 3 Change your password...6 4 Change your login name...7 5 Activate SMC Advanced licenses...8
KYOCERA Net Admin User Guide
 KYOCERA Net Admin User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
KYOCERA Net Admin User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
Configuring Network Proximity
 CHAPTER 9 This chapter describes how to configure a Global Site Selector to perform network proximity to determine the best (most proximate) resource for handling global load-balancing requests. This chapter
CHAPTER 9 This chapter describes how to configure a Global Site Selector to perform network proximity to determine the best (most proximate) resource for handling global load-balancing requests. This chapter
vcloud Director User's Guide
 vcloud Director 8.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of
vcloud Director 8.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of
Connector for Microsoft SharePoint 2013, 2016 and Online Setup and Reference Guide
 Connector for Microsoft SharePoint 2013, 2016 and Online Setup and Reference Guide Published: 2018-Oct-09 Contents 1 Microsoft SharePoint 2013, 2016 and Online Connector 4 1.1 Products 4 1.2 Supported
Connector for Microsoft SharePoint 2013, 2016 and Online Setup and Reference Guide Published: 2018-Oct-09 Contents 1 Microsoft SharePoint 2013, 2016 and Online Connector 4 1.1 Products 4 1.2 Supported
CounterACT User Directory Plugin
 Version 6.1.2 and Above Table of Contents About the User Directory Plugin... 3 Endpoint User Details... 3 Verify Endpoint Authentication... 3 User Directory Inventory... 4 HTTP Login Action... 5 HTTP Sign
Version 6.1.2 and Above Table of Contents About the User Directory Plugin... 3 Endpoint User Details... 3 Verify Endpoint Authentication... 3 User Directory Inventory... 4 HTTP Login Action... 5 HTTP Sign
Activating Intrusion Prevention Service
 Activating Intrusion Prevention Service Intrusion Prevention Service Overview Configuring Intrusion Prevention Service Intrusion Prevention Service Overview Intrusion Prevention Service (IPS) delivers
Activating Intrusion Prevention Service Intrusion Prevention Service Overview Configuring Intrusion Prevention Service Intrusion Prevention Service Overview Intrusion Prevention Service (IPS) delivers
ACL Compliance Director Tutorial
 Abstract Copyright 2008 Cyber Operations, Inc. This is a tutorial on ACL Compliance Director intended to guide new users through the core features of the system. Table of Contents Introduction... 1 Login
Abstract Copyright 2008 Cyber Operations, Inc. This is a tutorial on ACL Compliance Director intended to guide new users through the core features of the system. Table of Contents Introduction... 1 Login
