k 1234 k-nodes k 12 k 234 k 4 k 1 k 2 k 3 u 3 u 4 u 1 u 2 u-nodes
|
|
|
- Avice Lizbeth Payne
- 6 years ago
- Views:
Transcription
1 Secure Group Communications Using Key Graphs æ Chung Kei Wong Mohamed Gouda Simon S. Lam Department of Computer Sciences University of Texas at Austin Austin, TX Abstract Many emerging applications èe.g., teleconference, real-time information services, pay per view, distributed interactive simulation, and collaborative workè are based upon a group communications model, i.e., they require packet delivery from one or more authorized senders to a very large number of authorized receivers. As a result, securing group communications èi.e., providing conædentiality, integrity, and authenticity of messages delivered between group membersè will become a critical networking issue. In this paper, we present a novel solution to the scalability problem of groupèmulticast key management. We formalize the notion of a secure group as a triple èu; K; Rè where U denotes a set of users, K a set of keys held by the users, and R a user-key relation. We then introduce key graphs to specify secure groups. For a special class of key graphs, we present three strategies for securely distributing rekey messages after a joinèleave, and specify protocols for joining and leaving a secure group. The rekeying strategies and joinèleave protocols are implemented in a prototype group key server we have built. We present measurement results from experiments and discuss performance comparisons. We show that our group key management service, using any of the three rekeying strategies, is scalable to large groups with frequent joins and leaves. In particular, the average measured processing time per joinèleave increases linearly with the logarithm of group size. Introduction Most network applications are based upon the client-server paradigm and make use of unicast èor point-to-pointè packet delivery. Many emerging applications èe.g., teleconference, real-time information services, pay per view, distributed interactive simulation, and collaborative workè, on the other hand, are based upon a group communications model. That is, they require packet delivery from one or more authorized senderèsè to a large number of authorized receivers. In the Internet, multicast has been used successfully to provide an æ Research sponsored in part by Texas Advanced Research Program grant no and by NSA INFOSEC University Research Program grant no. MDA C-606. Experiments were performed on equipment procured with National Science Foundation grant no. CDA eæcient, best-eæort delivery service to large groups ë6ë. We envision that deployment of network applications requiring group communications will accelerate in coming years. While the technical issues of securing unicast communications for client-server computing are fairly well understood, the technical issues of securing group communications are not. Yet group communications have amuch greater exposure to security breaches than unicast communications. In particular, copies of a group communication packet traverse many more links than those of a unicast packet, thereby creating more opportunity for traæc interception. We believe that securing group communications èi.e., providing conædentiality, integrity, and authenticity of messages delivered between group membersè will become a critical issue of networking in the near future. Conceptually, since every point-to-multipoint communication can be represented as a set of point-to-point communications, the current technology base for securing unicast communications can be extended in a straightforward manner to secure group communications ë9, 0ë. However, such an extension is not scalable to large groups. For a more concrete illustration of this point, we outline a typical procedure for securing unicast communications between a client and and a server. Initially, the client and server mutually authenticate each other using an authentication protocol or service; subsequently, a symmetric key is created and shared by them to be used for pairwise conædential communications ë4, 7, 9, ë. This procedure can be extended to a group as follows: Let there be a trusted group server which isgiven membership information to exercise group access control. When a client wants to join the group, the client and group server mutually authenticate using an authentication protocol. Having been authenticated and accepted into the group, each member shares with the group server a key, to be called the member's individual key. For group communications, the group server distributes to each member a group key to be shared by all members of the group. For a group of n members, distributing the group key securely to all members requires n messages encrypted with individual keys èa computation cost proportional to group size nè. Each such message may besent separately via unicast. Alternatively, the n messages may be sent as a combined message to all group members via multicast. Either way, there is a communication cost proportional to group In this paper, key means a key from a symmetric cryptosystem, such as DES, unless explicitly stated otherwise. It is easy to see that sharing a group key enables conædential group communications. In addition to conædentiality, authenticity and integrity can be provided in group communications using standard techniques such as digital signature and message digest. We will not elaborate upon these techniques since the focus of this paper is key management.
2 size n èmeasured in terms of the number of messages or the size of the combined messageè. Observe that for a point-to-point session, the costs of session establishment and key distribution are incurred just once, at the beginning of the session. A group session, on the other hand, may persist for a relatively long time with members joining and leaving the session. Consequently, the group key should be changed frequently. To achieve a high level of security, the group key should be changed after every join and leave so that a former group member has no access to current communications and a new member has no access to previous communications. Consider a group server that creates a new group key after every join and leave. After a join, the new group key can be sent via unicast to the new member èencrypted with its individual keyè and via multicast to existing group members èencrypted with the previous group keyè. Thus, changing the group key securely after a join is not too muchwork. After a leave, however, the previous group key can no longer be used and the new group key must be encrypted for each remaining group member using its individual key. Thus we see that changing the group key securely after a leave incurs computation and communication costs proportional to n, the same as initial group key distribution. That is, large groups whose members join and leave frequently pose a scalability problem. The topic of secure group communications has been investigated ë,, 8, 5ë. Also the problem of how to distribute a secret to a group of users has been addressed in the cryptography literature ë3, 5, 7, 8ë. However, with the exception of ë5ë, no one has addressed the need for frequent key changes and the associated scalability problem for a very large group. The approach proposed in Iolus ë5ë to improve scalability is to decompose a large group of clients into many subgroups and employ a hierarchy of group security agents.. Our approach We present in this paper a diæerent hierarchical approach to improve scalability. Instead of a hierarchy of group security agents, we employ a hierarchy ofkeys. A detailed comparison of our approach and the Iolus approach ë5ë is given in Section 6. We begin by formalizing the notion of a secure group as a triple èu; K; Rè where U denotes a set of users, K a set of keys, and R ç U æ K a user-key relation which speciæes keys held by each user in U. In particular, each user is given a subset of keys which includes the user's individual key and a group key. We next illustrate how scalability of group key management can be improved by organizing the keys in K into a hierarchy and giving users additional keys. Let there be a trusted group server responsible for group access control and key management. In particular, the server securely distributes keys to group members and maintains the user-key relation. 3 To illustrate our approach, consider the following simple example of a secure group with nine members partitioned into three subgroups, fu ;u ;u 3g, fu 4;u 5;u 6g, and fu 7;u 8;u 9g. Each member is given three keys, its individual key, a key for the entire group, and a key for its subgroup. Suppose that u leaves the group, the remaining eight members form a new secure group and require a new group key; also, u and u 3 form a new subgroup and require a new subgroup key. To send the new subgroup 3 In practice, such a server may be distributed or replicated to enhance reliability and performance. key securely to u èu 3è, the server encrypts it with the individual key of u èu 3è. Subsequently, the server can send the new group key securely to members of each subgroup by encrypting it with the subgroup key. Thus by giving each user three keys instead of two, the server performs æve encryptions instead of eight. As a more general example, suppose the number n of users is a power of d, and the keys in K are organized as the nodes of a full and balanced d-ary tree. When a user leaves the secure group, to distribute new keys, the server needs to perform approximately d log d ènè encryptions èrather than n, encryptionsè. 4 For a large group, say 00,000, the savings can be very substantial.. Contributions of this paper With a hierarchy of keys, there are many diæerent ways to construct rekey messages and securely distribute them to users. We investigate three rekeying strategies, useroriented, and. We design and specify joinèleave protocols based upon these rekeying strategies. For and rekeying, which use multiple rekey messages per joinèleave, we present a technique for signing multiple messages with a single digital signature operation. Compared to using one digital signature per rekey message, the technique provides a tenfold reduction in the average server processing time of a joinèleave. The rekeying strategies and protocols are implemented in a prototype group key server we have built. We performed experiments on two lightly loaded SGI Origin 00 machines, with the server running on one and up to 8,9 clients on the other. From measurement results, we show that our group key management service, using any of the rekeying strategies with a key tree, is scalable; in particular, the average server processing time per joinèleave increases linearly with the logarithm of group size. We found that the optimal key tree degree is around four. Group-oriented rekeying provides the best performance of the three strategies on the server side, but is worst of the three on the client side. User-oriented rekeying has the best performance on the client side, but worst on the server side. The balance of this paper is organized as follows. In Section, we introduce key graphs as a method for specifying secure groups. In Section 3, we present protocols for users to join and leave a secure group as well as the three rekeying strategies. In Section 4, we present a technique for signing multiple rekey messages using a single digital signature operation. Experiments and performance results are presented in Section 5. A comparison of our approach and the Iolus approach is given in Section 6. Our conclusions are in Section 7. Secure Groups A secure group is a triple èu; K; Rè where æ U is a ænite and nonempty set of users, æ K is a ænite and nonempty set of keys, and æ R is a binary relation between U and K, that is, R ç U æ K, called the user-key relation of the secure group. User u has key k if and only if èu; kè isinr. 4 A similar observation was independently made in ë0ë at about the same time as when this paper was ærst published as a technical report ëë.
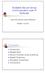
3 Each secure group has a trusted group server responsible for generating and securely distributing keys in K to users in the group. 5 Speciæcally, the group server knows the user set U and the key set K, and maintains the user-key relation R. Every user in U hasakey in K, called its individual key, which is shared only with the group server, and is used for pairwise conædential communication with the group server. There is a group key in K, shared by the group server and all users in U. The group key can be used by each user to send messages to the entire group conædentially.. Key graphs Akey graph is a directed acyclic graph G with two types of nodes, u-nodes representing users and k-nodes representing keys. Each u-node has one or more outgoing edges but no incoming edge. Each k-node has one or more incoming edges. If a k-node has incoming edges only and no outgoing edge, then this k-node is called a root. èa key graph can have multiple roots.è Given a key graph G, it speciæes a secure group èu; K; Rè as follows: i. There is a one-to-one correspondence between U and the set of u-nodes in G. ii. There is a one-to-one correspondence between K and the set of k-nodes in G. iii. èu; kè isinr if and only if G has a directed path from the u-node that corresponds to u to the k- node that corresponds to k. k k u u k 34 k k 34 k 3 k 4 u 3 u 4 Figure : A key graph. k-nodes u-nodes As an example, the key graph in Figure speciæes the following secure group: U = fu ;u ;u 3;u 4g K = fk ;k ;k 3;k 4;k ;k 34;k 34g R = f èu ;k è, èu ;k è, èu ;k 34è, èu ;k è, èu ;k è, èu ;k 34è, èu ;k 34è, èu 3;k 3è, èu 3;k 34è, èu 3;k 34è, èu 4;k 4è, èu 4;k 34è, èu 4;k 34è g Associated with each secure group èu; K; Rè are two functions, keyset èè and userset èè, deæned as follows: keysetèuè =f k j èu; kè R g usersetèkè =f u j èu; kè R g Intuitively, keysetèuè is the set of keys that are held by user 5 Note that individual keys may have been generated and securely distributed by an authentication service and do not have to be generated by the group server. u in U, and userset èkè isthe set of users that hold key k in K. For examples, referring to the key graph in Figure, we have keysetèu 4è=fk 4;k 34;k 34g and usersetèk 34è = fu ;u 3;u 4g. We generalize the deænition of function keyset èè to any subset U 0 of U, and function userset èè to any subset K 0 of K, in a straighforward manner, i.e., keysetèu 0 è is the set of keys each of which is held by at least one user in U 0, and usersetèk 0 è is the set of users each of which holds at least one key in K 0. When a user u leaves a secure group èu; K; Rè, every key that has been held by u and shared by other users in U should be changed. Let k be such a key. To replace k, the server randomly generates a new key k new and sends it to every user in usersetèkè except u. To dososecurely, the server needs to ænd a subset K 0 of keys such that userset èk 0 è = usersetèkè,fug, and use keys in K 0 to encrypt k new. To minimize the work of rekeying, the server would like to ænd a minimal size set K 0. This suggests the following key-covering problem: Given a secure group èu; K; Rè, and a subset S of U, ænd a minimum size subset K 0 of K such that usersetèk 0 è=s. Unfortunately, the key-covering problem in general is NP-hard ëë.. Special classes of key graphs We next consider key graphs with special structures for which the key covering problem can be easily solved. Star: This is the special class of a secure group èu; K; Rè where each user in U has two keys: its individual key and a group key that is shared by every user in U. 6 Tree: This is the special class of a secure group èu; K; Rè whose key graph G is a single-root tree. A tree key graph èor key treeè is speciæed bytwo parameters. æ The height h of the tree is the length èin number of edgesè of the longest directed path in the tree. æ The degree d of the tree is the maximum number of incoming edges of a node in the tree. Note that since the leaf node of each path is a u-node, each user in U has at most h keys. Also the key at the root of the tree is shared by every user in U, and serves as the group key. Lastly, it is easy to see that star is a special case of tree. Complete: This is the special class of a secure group èu; K; Rè, where for every nonempty subset S of U, there is a key k in K such that usersetèkè = S. Let n be the number of users in U. There are n, keys in K, one for each of the n, nonempty subsets of U. Moreover, each user u in U has n, keys, one for each of the n, subsets of U that contains u. Since U is a subset of U, there is a key shared by every user in U which serves as the group key. The total number of keys held by the server and the number of keys held by a user are presented in Table where n is the size of U. In particular, in the case of a complete key graph, each user needs to hold n, keys which is practical only for small n. Note that the number of keys in a key tree is dh, ç d n when the tree is full and balanced èi.e. d, d, n = d h, è. 6 This is the base case where no additional keys are used to improve scalability of group key management.
4 Class of key graph Star Tree Complete d Total number of keys n+ n d, n, Number of keys per user h n, Table : Number of keys held by the server and by each user. 3 Rekeying Strategies and Protocols A user u who wants to join èleaveè a secure group sends a join èleaveè request to the group server, denoted by s. For a join request from user u, we assume that group access control is performed by server s using an access control list provided by the initiator of the secure group. 7 A join request initiates an authentication exchange between u and s, possibly with the help of an authentication server. If user u is not authorized to join the group, server s sends a join-denied reply to u. If the join request is granted, we assume that the session key distributed as a result of the authentication exchange ë7, ë will be used as the individual key k u of u. To simplify protocol speciæcations below, we use the following notation s, u : authenticate u and distribute k u to represent the authentication exchange between server s and user u, and secure distribution of key k u to be shared by u and s. After each join or leave, a new secure group is formed. Server s has to update the group's key graph by replacing the keys of some existing k-nodes, deleting some k-nodes èin the case of a leaveè, and adding some k-nodes èin the case of a joinè. It then securely sends rekey messages containing new groupèsubgroup keys to users of the new secure group. èa reliable message delivery system, for both unicast and multicast, is assumed.è In protocol speciæcations below, we also use the following notation to denote x! y : z æ if y is a single user, the sending of message z from x to y; æ if y is a set of users, the sending of message z from x to every user in y èvia multicast or unicastè. In the following subsections, we ærst present protocols for joining and leaving a secure group speciæed by a star key graph. These protocols correspond to conventional rekeying procedures informally described in the Introduction ë9, 0ë. We then consider secure groups speciæed by tree key graphs. With a hierarchy of group and subgroup keys, rekeying after a joinèleave can be carried out in a variety of ways. We present three rekeying strategies,,, and, as well as protocols for joining and leaving a secure group. 3. Joining a star key graph After granting a join request from user u, server s updates the key graph by creating a new u-node for u and a new k-node for k u, and attaching them to the root node. Server 7 The authorization function may be oæoaded to an authorization server. In this case, the authorization server provides an authorized user with a ticket to join the secure group ë6, 3ë. The user submits the ticket together with its join request to server s. s also generates a new group key k U 0 for the root node, encrypts it with the individual key k u of user u, and sends the encrypted new group key to u. To notify other users of the new group key, server s encrypts the new group key k U 0 with the old group key k U, and then multicasts the encrypted new group key to every user in the group. èsee Figure.è èè u! s : join request èè s, u : authenticate u and distribute k u è3è s : randomly generate a new group key k U 0 è4è s! u : fk U 0g ku è5è s! U : fk U 0g ku k k u u Figure : Join protocol for a star key graph. k 3 0 k 3 u 3 u 4 u 4 joins leaves k k k 34 k 3 k 4 u u u 3 u 4 Figure 3: Star key graphs before and after a join èleaveè. For example, as shown in Figure 3, suppose user u 4 wants to join the left secure group in the ægure, and it is allowed to join. After server s changes the group key from k 3 to a new key k 34, server s needs to send out the following two rekey messages. s!fu ;u ;u 3g : fk 34g k3 s! u 4 : fk 34g k4 For clarity of presentation, we have assumed that rekey messages contain new keys only and secure distribution means that the new keys are encrypted just for conædentiality. In our prototype implementation, rekey messages have additional æelds, such as, subgroup labels for new keys, server digital signature, message integrity check, timestamp, etc. èsee ëë for rekey message format.è 3. Leaving a star key graph èè u! s : f leave-request g ku èè s! u : f leave-granted g ku è3è s : randomly generate a new group key k U 0 è4è for each user v in U except user u do s! v : fk U 0g kv Figure 4: Leave protocol for a star key graph. After granting a leave request from user u, server s updates the key graph by deleting the u-node for user u and the k-node for its individual key k u from the key graph. Server s generates a new group key k U 0 for the new secure group without u, encrypts it with the individual key of each remaining user, and unicasts the encrypted new group key to the user. èsee Figure 4.è
5 k-9 k-node x 0 k 3 k 456 k k k k3 k 4 k 5 k 6 k 7 k 8 k 9 u u u 3 u 4 k-8 u 9 leaves u 9 joins u 5 u 6 k-node x 0 k-node x u k 3 k 456 k 78 k k k3 k 4 k 5 k 6 k 7 k 8 u u u 3 u 4 u 5 u 6 k-node x Figure 5: Key trees before and after a join èleaveè. 3.3 Joining a tree key graph After granting a join request from u, server s creates a new u-node for user u and a new k-node for its individual key k u. Server s ænds an existing k-node ècalled the joining point for this join requestè in the key tree and attaches k-node k u to the joining point as its child. To prevent the joining user from accessing past communications, all keys along the path from the joining point to the root node need to be changed. After generating new keys for these nodes, server s needs to securely distribute them to the existing users as well as the joining user. For example, as shown in Figure 5, suppose u 9 is granted to join the upper key graph in the ægure. The joining point is k-node k 78 in the key graph, and the key of this k-node is changed to k 789 in the new key graph below. Moreover, the group key at the root is changed from k,8 to k,9. Users u ;:::;u 6 only need the new group key k,9, while users u 7;u 8, and u 9 need the new group key k,9 as well as the new key k 789 to be shared by them. To securely distribute the new keys to the users, the server constructs and sends rekey messages to the users. A rekey message contains one or more encrypted new keyèsè, and a user needs to decrypt it with appropriate keys in order to get the new keys. We next present three diæerent approaches to construct and send rekey messages. User-oriented rekeying. Consider each user and the subset of new keys it needs. The idea of rekeying is that for each user, the server constructs a rekey message that contains precisely the new keys needed by the user, and encrypts them using a key held by the user. For example, as shown in Figure 5, for user u 9 to join the upper secure group in the ægure, server s needs to send u 7 u 8 u 8 u 9 the following three rekey messages. s!fu ;:::;u 6g : fk,9g k,8 s!fu 7;u 8g : fk,9;k 789g k78 s! u 9 : fk,9;k 789g k9 Note that users u ;:::;u 6 need to get the new group key k,9. There is no single key that is shared only by u ;:::;u 6. However, key k,8 can be used to encrypt the new key k,9 for u ;:::;u 6 without security breach since users u 7 and u 8 will also get this new group key from another rekey message. User-oriented rekey messages can be constructed as follows. For each k-node x whose key has been changed, say from k to k 0, the server constructs a rekey message by encrypting the new keys of k-node x and all its ancestors èupto the rootè by the old key k. This rekey message is then sent to the subset of users that need precisely these new keys. Either unicast or subgroup multicast may be used. 8 Moreover, one rekey message is sent to the joining user which contains all of the new keys encrypted by the individual key of the joining user. This approach needs h rekey messages. Counting the number of keys encrypted, the encryption cost for the server is given by ++:::+ h, +h, = hèh+è,. Key-oriented rekeying. In this approach, each new key is encrypted individually èexcept keys for the joining userè. For each k-node x whose key has been changed, say from k to k 0, the server constructs two rekey messages. First, the server encrypts the new key k 0 with the old key k, and sends it to userset èkè which is the set of users that share k. All of the original users that need the new key k 0 can get it from this rekey message. The other rekey message contains the new key k 0 encrypted by the individual key of the joining user, and is sent to the joining user. As described, a user may have to get multiple rekey messages in order to get all the new keys it needs. For example, as shown in Figure 5, for user u 9 to join the upper secure group in the ægure, server s needs to send the following four rekey messages. Note that users u 7;u 8; and u 9 need to get two rekey messages each. s!fu ;:::;u 8g : fk,9g k,8 s! u 9 : fk,9g k9 s!fu 7;u 8g : fk 789g k78 s! u 9 : fk 789g k9 Compared to rekeying, the above approach reduces the encryption cost of the server from hèh+è, to èh,è, but it requires èh,è rekey messages instead of h. To reduce the number of rekey messages, all of the rekey messages for a particular user can be combined and sent as one message. Thus, server s can send the following three rekey messages instead of the four rekey messages shown above. s!fu ;:::;u 6g : fk,9g k,8 s!fu 7;u 8g : fk,9g k,8 ; fk 789g k78 s! u 9 : fk,9;k 789g k9 The join protocol based upon this rekeying strategy is presented in Figure 6. Steps è4è and è5è in Figure 6 specify how the combined rekey messages are constructed and distributed by server s. Using combined rekey messages, the number of rekey messages for rekeying is h èsame as user- 8 A rekey message can be sent via multicast to a subgroup if a multicast address has been established for the subgroup in addition to the multicast address for the entire group. Alternatively, the method in ë3ë may be used in lieu of allocating a large number of multicast addresses for subgroups. See Section 7 for more discussion.
6 oriented rekeyingè while the encryption cost is èh, è. From this analysis, rekeying is clearly better for the server than rekeying. èthis conclusion is conærmed by measurement results presented in Section 5.è èè u! s : join request èè s, u : authenticate u and distribute k u è3è s : ænd a joining point and attach k u, let x j denote the joining point, x 0 the root, and x i, the parent ofx i for i =;:::;j, let K j+ denote k u, and K 0;:::;K j the old keys of x 0;:::;x j, randomly generate new keys K 0 0;:::;K 0 j è4è for i = 0 upto j do let M = fk 0 0g K0 ;:::;fk 0 ig Ki s! èuserset èk iè, usersetèk i+èè : M è5è s! u : fk 0 0;:::;K 0 jg ku Figure 6: Join protocol for a tree key graph è rekeyingè. Group-oriented rekeying. In rekeying, each new key is encrypted individually èexcept keys for the joining userè. The server constructs multiple rekey messages, each tailored to the needs of a subgroup. Speciæcally, the users of a subgroup receive a rekey message containing precisely the new keys each needs. An alternative approach, called, is for the server to construct a single rekey message containing all new keys. This rekey message is then multicasted to the entire group. Clearly such a rekey message is relatively large and contains information not needed by individual users. However, scalability is not a concern because the message size is Oèlog d ènèè for group size n and d. The approach has several advantages over and rekeying. First, there is no need for subgroup multicast. Second, with fewer rekey messages, the server's per rekey message overheads are reduced. Third, the total number of bytes transmitted by the server per joinèleave request is less than those of and rekeying which duplicate information in rekey messages. èsee Section 5 and Section 7 for a more thorough discussion on performance comparisons.è For example, as shown in Figure 5, for user u 9 to join the upper secure group in the ægure, server s needs to send the following two rekey messages; one is multicasted to the group, and the other is unicasted to the joining user. s!fu ;:::;u 8g : fk,9g k,8 ; fk 789g k78 s! u 9 : fk,9;k 789g k9 The join protocol based upon rekeying is presented in Figure 7. This approach reduces the number of rekey messages to one multicast message and one unicast message, while maintaining the encryption cost at èh, è èsame as rekeyingè. èè - è3è èsame as Figure 6è è4è s! usersetèk 0è:fK0g 0 K0 ;:::;fkjg 0 Kj è5è s! u : fk0;:::;k 0 jg 0 ku Figure 7: Join protocol for a tree key graph è rekeyingè. 3.4 Leaving a tree key graph After granting a leave request from user u, server s updates the key graph by deleting the u-node for user u and the k- node for its individual key from the key graph. The parent of the k-node for its individual key is called the leaving point. To prevent the leaving user from accessing future communications, all keys along the path from the leaving point to the root node need to be changed. After generating new keys for these k-nodes, server s needs to securely distribute them to the remaining users. For example, as shown in Figure 5, suppose u 9 is granted to leave the lower key graph in the ægure. The leaving point is the k-node for k 789 in the key graph, and the key of this k-node is changed to k 78 in the new key graph above. Moreover, the group key is also changed from k,9 to k,8. Users u ;:::;u 6 only need to know the new group key k,8. Users u 7 and u 8 need to know the new group key k,8 and the new key k 78 shared by them. To securely distribute the new keys to users after a leave, we revisit the three rekeying strategies. User-oriented rekeying In this approach, each user gets a rekey message in which all the new keys it needs are encrypted using a key it holds. For example, as shown in Figure 5, for user u 9 to leave the lower secure group in the ægure, server s needs to send the following four rekey messages. s!fu ;u ;u 3g : fk,8g k3 s!fu 4;u 5;u 6g : fk,8g k456 s! u 7 : fk,8;k 78g k7 s! u 8 : fk,8;k 78g k8 User-oriented rekey messages for a leave can be constructed as follows. For each k-node x whose key has been changed, say from k to k 0, and for each unchanged child y of x, the server constructs a rekey message by encrypting the new keys of k-node x and all its ancestors èupto the rootè by the key K of k-node y. This rekey message is then multicasted to userset èkè. This approach requires èd, èèh, è rekey messages. The encryption cost for the server is given by èd, èè + + :::+ h, è = èd,èhèh,è. Key-oriented rekeying In this approach, each new key is encrypted individually. For example, as shown in Figure 5, for user u 9 to leave the lower secure group in the ægure, server s needs to send the following four rekey messages. s!fu ;u ;u 3g : fk,8g k3 s!fu 4;u 5;u 6g : fk,8g k456 s! u 7 : fk,8g k78 ; fk 78g k7 s! u 8 : fk,8g k78 ; fk 78g k8 The leave protocol based upon rekeying is presented in Figure 8. Step è4è in Figure 8 speciæes how the rekey messages are constructed and distributed to users. Note that by storing encrypted new keys for use in different rekey messages, the encryption cost of this approach is dèh, è, which is much less than that of rekeying. The number of rekey messages is èd, èèh, è, same as rekeying. Group-oriented rekeying. A single rekey message is constructed containing all new keys. For example, as shown in Figure 5, for user u 9 to leave the lower secure group in the ægure, server s needs to send the following rekey message:
7 èè u! s : f leave-request g ku èè s! u : f leave-granted g ku è3è s : ænd the leaving point èthe parent ofk uè, remove k u from the tree, let x j+ denote the deleted k-node for k u, x j the leaving point, x 0 the root, and x i, the parent ofx i for i =;:::;j, randomly generate keys K 0 0;:::;K 0 j as the new keys of x 0;:::;x j è4è for i = 0 upto j do for each child y of x i do let K denote the key at k-node y if y 6= x i+ then do let M = fk 0 ig K; fk 0 i,g K 0 i ;:::;fk0 0g K 0 s! userset èkè : M Figure 8: Leave protocol for a tree key graph è rekeyingè. let L 0 denote fk,8g k3 ; fk,8g k456 ; fk,8g k78 let L denote fk 78g k7 ; fk 78g k8 s!fu ;:::;u 8g : L 0;L Note that for a leave, this single rekey message is about d times bigger than the rekey message for a join, where d is the average degree of a k-node. The leave protocol based upon rekeying is presented in Figure 9. This approach uses only one rekey message which is multicasted to the entire group, and the encryption cost is dèh, è, same as rekeying. èè - è3è èsame as Figure 8è è4è for i = 0 upto j do let fz ;:::;z rg be the set of the children of x i let J ;:::;J r denote the keys at z ;:::;z r let L i denote fk 0 ig J ;:::;fk 0 ig Jr s! userset èk 0 0è:L 0;:::;L j Figure 9: Leave protocol for a tree key graph è rekeyingè. 3.5 Cost of encryptions and decryptions An approximate measure of the computational costs of the server and users is the number of key encryptions and decryptions required by a joinèleave operation. Let n be the number of users in a secure group. For each joinèleave operation, the user that requests the operation is called the requesting user, and the other users in the group are nonrequesting users. For a joinèleave operation, we tabulate the cost of a requesting user in Table èaè, the cost of a nonrequesting user in Table èbè, and the cost of the server in Table ècè. These costs are from the protocols described above for star and tree key graphs, and from ëë for complete key graphs. èkey-oriented or rekeying is assumed for tree key graphs.è For a key tree, recall that d and h denote the degree and height of the tree respectively. In this case, for a nonrequesting user u, the average cost of u for a join or a leave d d, is less than which is independent of the size of the tree èderivation in ëëè. Assuming that the number of join operations is the same as the number of leave operations, the average costs per operation are tabulated in Table 3 for the server and a user in the group. èaè the requesting user Star Tree Complete join h, n leave èbè a non-requesting user Star Tree Complete d join n, d, d leave 0 d, ècè the server Star Tree Complete join èh,è n+ leave n, dèh,è 0 Table : Cost of a joinèleave operation. cost Star Tree Complete cost of the server n= èd + èèh, è= n cost of a user d=èd, è n Table 3: Average cost per operation. From Table 3, it is obvious that complete key graphs should not be used. On the other hand, scalable group key management can be achieved by using tree key graphs. Note that for a full and balanced d-ary tree, the average server cost is èd + èèh, è= =èd + èèlog d ènèè=. However, each user has to do slightly more work èfrom to d è. For d =4, d, a user needs to do :33 decryptions on the average instead of one. èit can be shown that the server cost is minimized for d = 4, i.e., the optimal degree of key trees is four.è 4 Technique for Signing Rekey Messages In our joinèleave protocols, each rekey message contains one or more new keys. Each new key, destined for a set of users, is encrypted by a key known only to these users and the server. It is possible for a user to masquerade as the server and send out rekey messages to other users. Thus if users cannot be trusted, then each rekey message should be digitally signed by the server. We note that a digital signature operation is around two orders of magnitude slower than a key encryption using DES. For this reason, it is highly desirable to reduce the number of digital signature operations required per joinèleave. If each rekey message is signed individually, then rekeying, using just one rekey message per joinèleave, would be far superior to èè rekeying, which uses many rekey messages per joinèleave. Consider m rekey messages, M ;:::;M m, with message digests, d i = hèm iè for i =;:::;m, where hèè is a secure message digest function such as MD5. The standard way to provide authenticity is for the server to sign each message digest èwith its private keyè and send the signed message digest together with the message. This would require m digital signature operations for m messages. We next describe a technique, implemented in our prototype key server, for signing a set of messages using just a single digital signature operation. The technique is based upon a scheme proposed by Merkle ë4ë. Suppose there are four messages with message digests d ;d ;d 3, and d 4. Construct message D containing d and d, and compute message digest d = hèd è. Similarly, construct message D 34 containing d 3 and d 4, and compute message digest d 34 = hèd 34è. Then construct message
8 key tree one signature per rekey msg one signature for all rekey msgs degree 4 msg size èbyteè proc time èmsecè msg size èbyteè proc time èmsecè join leave join leave ave join leave join leave ave user key group Table 4: Average rekey message size and server processing time èn=89, DES, MD5, RSAè group size èaè with encryption only group size èbè with encryption and signature Figure 0: Server processing time per request vs group size è 4è. D,4 containing d and d 34, and compute message digest d,4 = hèd,4è. The server signs message digest d,4 with its private key. The server then sends the signed message digest, signèd,4è, together with D,4, D 34, and M 4 to a user that needs M 4. The user veriæes, by ærst decrypting signèd,4è, that d,4 = hèd,4è. Subsequently, the user veriæes that d 34 in D,4 is equal to hèd 34è, and also d 4 in D 34 is equal to hèm 4è, which assures that M 4 was indeed sentby the server. The above example can be easily extended to m messages in general. The beneæts of this technique for signing rekey messages are demonstrated in Table 4 for both and useroriented rekeying. ènote that it is not needed by grouporiented rekeying which uses one rekey message per joinè leave.è The average rekey message size per joinèleave is shown, as well as the server's processing time per joinèleave èave denotes the average of average join and leave processing timesè. The experiments were performed for an initial group size of 89, with DES-CBC encryption, MD5 message digest, and RSA digital signature è5-bit modulusè. Additional details of our experimental setup can be found in Section 5. With the technique for signing rekey messages, the processing time reduction for and rekeying is about a factor of ten èfor example, 4.5 msec versus 40. msec in the case of rekeyingè. There is however a small increase èaround bytesè in the average rekey message size. 5 Experiments and Performance Comparisons We have designed and constructed a prototype group key server, as well as a client layer, which implement joinèleave protocols for all three rekeying strategies in Section 3 and the technique for signing rekey messages in Section 4. We performed a large number of experiments to evaluate the performance of the rekeying strategies and the technique for signing rekey messages. The experiments were carried out on two lightly loaded SGI Origin 00 machines running IRIX 6.4. The machines were connected by a 00 Mbps Ethernet. The group key server process runs on one SGI machine. The server is initialized from a speciæcation æle which determines the inital group size, the rekeying strategy, the, the encryption algorithm, the message digest algorithm, the digital signature algorithm, etc. A client-simulator runs on the other SGI simulating a large number of clients. Actual rekey messages, as well as join, join-ack, leave, leave-ack messages, are sent between individual clients and the server using UDP over the 00 Mbps Ethernet. Cryptographic routines from the publicly available CrytoLib library are used ëë. For each experiment with an initial group size n, the client-simulator ærst sent n join requests, and the server built a key tree. Then the client-simulator sent 000 joinè leave requests. The sequence of 000 joinèleave requests was generated randomly according to a given ratio èthe ratio was : in all our experiments to be presentedè. Each experiment was performed with three diæerent sequences of 000 joinèleave requests. For fair comparisons èbetween diæerent rekeying strategies, key trees of diæerent degrees, etc.è, the same three sequences were used for a given group size. The server employs a heuristic that attempts to build and maintain a key tree that is full and balanced. However, since the sequence of joinèleave requests is randomly generated, it is unlikely that the tree is truly full and balanced at any time. To evaluate the performance of diæerent rekeying strategies as well as the technique for signing rekey messages, we measured rekey message sizes èin bytesè and processing time èin msecè used by the server per joinèleave request. Specifically, the processing time per joinèleave request consists of the following components. First, the server parses a request, traverses the key graph to determine which keys are to be updated, generates new keys, and updates the key graph.
9 key tree rekey msg size èbyteè no. of rekey msgs degree 4 per join per leave per join per leave ave min max ave min max ave min max ave min max user key group key tree rekey msg size èbyteè no. of rekey msgs degree 8 per join per leave per join per leave ave min max ave min max ave min max ave min max user key group key tree rekey msg size èbyteè no. of rekey msgs degree 6 per join per leave per join per leave ave min max ave min max ave min max ave min max user key group Table 5: Number and size of rekey messages, with encryption and signature, sent by the server èinitial group size 89è Second, the server performs encryption of new keys and constructs rekey messages. Third, if message digest is speciæed, the server computes message digests of the rekey messages. Fourth, if digital signature is speciæed, the server computes message digests and a digital signature as described in Section 4. Lastly, the server sends out rekey messages as UDP packets using socket system calls. 9 The server processing time per request èaveraged over joins and leavesè versus group size èfrom 3 to 89è is shown in Figure 0. Note that the horizontal axis is in log scale. The left ægure is for rekey messages with DES-CBC encryption only èno message digest and no digital signatureè. The right ægure is for rekey messages with DES-CBC encryption, MD5 message digest, and RSA-5 digital signature. The was four in all experiments. We conclude from the experimental results that our group key management service is scalable to very large groups since the processing time per request increases èapproximatelyè linearly with the logarithm of group size for all three rekeying strategies. Other experiments support the same conclusion for key tree degrees of 8 and 6. The average server processing time versus is shown in Figure. These experimental results illustrate three observations. First, the optimal degree for key trees is around four. Second, with respect to server processing time, rekeying has the best performance, with rekeying in second place. Third, signing rekey messages increases the server processing time by an order of magnitude èit would be another order of magnitude more for and rekeying without a special technique for signing multiple messagesè. The left hand side of the ægure is for rekey messages with DES-CBC encryption only èno message digest and no digital signatureè. The right hand side of the ægure is for rekey messages with DES-CBC encryption, MD5 message digest, and RSA-5 digital signature. The initial group size was 89 in these experiments. 9 The processing time is measured using the UNIX system call getrusageèè which returns processing time èincluding time of system callsè used by a process. In the results presented herein, the processing time for a join request does not include any time used to authenticate the requesting user èi.e., step èè in the join protocols of Figure 6 and Figure 7è. We feel that any authentication overhead should be accounted for separately. key tree rekey msg size èbyteè no. of rekey degree 4 per join per leave msgs per ave ave joinèleave user key group key tree rekey msg size èbyteè no. of rekey degree 8 per join per leave msgs per ave ave joinèleave user key group key tree rekey msg size èbyteè no. of rekey degree 6 per join per leave msgs per ave ave joinèleave user key group Table 6: Number and size of rekey messages, with encryption and signature, received by a client èinitial group size 89è Table 5 presents the size and number of rekey messages sent by the server. Note that rekeying uses a single large rekey message per request èsent via group multicastè, while and rekeying use multiple smaller rekey messages per request èsent via subgroup multicast or unicastè. 0 Note that the total number of bytes per joinèleave transmitted by the server is much higher in and rekeying than in rekeying. Table 6 presents the size and number of rekey messages received by a client. Only the average message sizes are shown, because the minimum and maximum sizes are the same as those in Table 5. Note that each client gets exactly one rekey message for all three rekeying strategies. For keyoriented and rekeying, the average message size is smaller than the corresponding average message size in Table 5. The is because the average message size here 0 The experiments reported herein were performed with each rekey message sent just once by the server via subgroup multicast.
10 èaè per join with encryption only èdè per join with encryption and signature èbè per leave with encryption only èeè per leave with encryption and signature ècè per request with encryption only èfè per request with encryption and signature Figure : Server processing time vs èinitial group size 89è. was calculated over all clients, and many more clients received small rekey messages than clients that received large rekey messages. The results in this table show that grouporiented rekeying, which has the best performance on the server side, requires more work on the client side to process a larger message than and rekeying. The average rekey message size on the client side is the smallest in rekeying. From the contents of rekey messages, we counted and computed the average number of key changes by a client per joinèleave request, which is shown in Figure. The top ægure shows the average number of key changes versus the, and the bottom ægure shows the average number of key changes versus the initial group size of each experiment. Note that the average numberof key changes by a client is relatively small, and is very close to the analytical result, d=èd, è shown in Table 3 in Section 3.
11 number of key changes number of key changes n = 04 n = 048 n = 4086 n = 89 analysis tree degree is 4 tree degree is 8 tree degree is group size Figure : Number of key changes by a client per request. 6 Related Work The scalability problem of group key management for a large group with frequent joins and leaves was previously addressed by Mittra with his Iolus system ë5ë. Both Iolus and our approach solve the scalability problem by making use of a hierarchy. The similarity, however, ends here. The system architectures are very diæerent in the two approaches. We next compare them by considering a tree hierarchy with a single root èi.e., a single secure groupè. Iolus's tree hierarchy consists of clients at the leaves with multiple levels of group security agents èagents, in shortè above. For each tree node, the tree node èan agentè and its children èclients or lower-level agentsè form a subgroup and share a subgroup key. There is no globally shared group key. Thus a join and leave in a subgroup does not aæect other subgroups; only the local subgroup key needs to be changed. Our tree hierarchy consists of keys, with individual keys at leaves, the group key at the root, and subgroup keys elsewhere. There is a single key server for all the clients. There are no agents, but each client is given multiple keys èits individual key, the group key, and some subgroup keysè. In comparing the two approaches, there are several issues to consider: performance, trust, and reliability. Performance. Roughly speaking, since both approaches make use of a hierarchy, both attempt to change a Oènè problem into a Oèlogènèè problem where n denotes group size. They diæer however in where and when work is performed to achieve secure rekeying when a client joinsèleaves the secure group. Secure rekeying after a leave requires more work than after a join because, unlike a join, the previous group key cannot used and n rekey messages are required èthis is referred to in ë5ë as a does not equal n type problemè. This is precisely the problem solved by using a hierarchy in both approaches. The main diæerence between Iolus and our approachisin how the aæects n type problem ë5ë is addressed. In our approach, every time a client joinsèleaves the secure group a rekeying operation is required which aæects the entire group. Note that this is not a scalability concern in our approach because the server cost is Oèlogènèè and the client cost is Oèè. In Iolus, there is no globally shared group key with the apparent advantage that whenever a client joinsèleaves a subgroup only the subgroup needs to be rekeyed. However, for a client to send a message conædentially to the entire group, the client needs to generate a message key for encrypting the message and the message key has to be securely distributed to the entire group via agents. Each agent decrypts using one subgroup key to retrieve the message key and reencrypts it with another subgroup key for forwarding ë5ë. That is, most of the work in handling the aæects n type problem is performed in Iolus when a client sends a message conædentially to the entire group èrather than when a client joinsèleaves the groupè. In our approach, most of the work in handling the aæects n type problem is performed when a client joinsèleaves the secure group èrather than when a client sends messages conædentially to the entire groupè. Trust. Our architecture requires a single trusted entity, namely, the key server. The key server may be replicated for reliabilityèperformance enhancement, in which case, several trusted entities are needed. Each trusted entity should be protected using strong security measures èe.g. physical security, kernel security, etc.è. In Iolus, however, there are many agents and all of the agents are trusted entities. Thus the level of trust required of the system components is much greater in Iolus than in our approach. Reliability. In Iolus, agents are needed to securely forward message keys. When an agent fails, a backup is needed. It would appear that replicating a single key server èin our approachè to improve reliability is easier than backing up a large number of agents. 7 Conclusions We present three rekeying strategies,, keyoriented and and specify joinèleave protocols based upon these strategies. For and useroriented rekeying, which use multiple rekey messages per joinèleave, we present a technique for signing multiple messages with a single digital signature operation. Compared to using one digital signature per rekey message, the technique provides a tenfold reduction in the average server processing time of a joinèleave. The rekeying strategies and protocols are implemented in a prototype group key server we have built. From measurement results of a large number of experiments, we conclude that our group key management service using any of the three rekeying strategies is scalable to large groups with frequent joins and leaves. In particular, the average server processing time per joinèleave increases linearly with the Craig Partridge observed that agents can be implemented in existing ærewalls and derive their reliability and trustworthiness from those of ærewalls.
Iolus: A Framework for Scalable Secure Multicasting
 Iolus: A Framework for Scalable Secure Multicasting Vladica Stanisic Multicast Efficient means of distributing data to a group of participants Supports one to many and many to many service Needs to transmit
Iolus: A Framework for Scalable Secure Multicasting Vladica Stanisic Multicast Efficient means of distributing data to a group of participants Supports one to many and many to many service Needs to transmit
P0 P1 P2 P3 P4 P5 P6 P7 P
 A Scalable Framework for Secure Multicast Sreedhar Mukkamalla Randy H. Katz fmsreedha,randyg@cs.berkeley.edu CS Division, EECS Department, U.C.Berkeley Abstract The lack of security mechanisms for IP multicast
A Scalable Framework for Secure Multicast Sreedhar Mukkamalla Randy H. Katz fmsreedha,randyg@cs.berkeley.edu CS Division, EECS Department, U.C.Berkeley Abstract The lack of security mechanisms for IP multicast
19.2 View Serializability. Recall our discussion in Section?? of how our true goal in the design of a
 1 19.2 View Serializability Recall our discussion in Section?? of how our true goal in the design of a scheduler is to allow only schedules that are serializable. We also saw how differences in what operations
1 19.2 View Serializability Recall our discussion in Section?? of how our true goal in the design of a scheduler is to allow only schedules that are serializable. We also saw how differences in what operations
Mykil: A Highly Scalable Key Distribution Protocol for Large Group Multicast
 Mykil: A Highly Scalable Key Distribution Protocol for Large Group Multicast Jyh-How Huang and Shivakant Mishra Department of Computer Science University of Colorado, Campus Box 0430 Boulder, CO 80309-0430,
Mykil: A Highly Scalable Key Distribution Protocol for Large Group Multicast Jyh-How Huang and Shivakant Mishra Department of Computer Science University of Colorado, Campus Box 0430 Boulder, CO 80309-0430,
D1 D2 D3 D4 D5 D6 D7 D8
 Digital Signatures for Flows and Multicasts Chung Kei Wong Simon S. Lam Department of Computer Sciences The University of Texas at Austin Austin, TX 78712-1188 fckwong,lamg@cs.utexas.edu TR-98-15 May 31,
Digital Signatures for Flows and Multicasts Chung Kei Wong Simon S. Lam Department of Computer Sciences The University of Texas at Austin Austin, TX 78712-1188 fckwong,lamg@cs.utexas.edu TR-98-15 May 31,
CSC/ECE 774 Advanced Network Security
 Computer Science CSC/ECE 774 Advanced Network Security Topic 4.3 Group Key Distribution Acknowledgment: Slides on LKH were originally provided by Dr. Wensheng Zhang at Iowa State. Dr. Peng Ning CSC 774
Computer Science CSC/ECE 774 Advanced Network Security Topic 4.3 Group Key Distribution Acknowledgment: Slides on LKH were originally provided by Dr. Wensheng Zhang at Iowa State. Dr. Peng Ning CSC 774
Efficient Group Rekeying Using Application-Layer Multicast
 Efficient Group Rekeying Using Application-Layer Multicast X. Brian Zhang, Simon S. Lam, and Huaiyu Liu Department of Computer Sciences, The University of Texas at Austin, Austin, TX 7872 {zxc, lam, huaiyu}@cs.utexas.edu
Efficient Group Rekeying Using Application-Layer Multicast X. Brian Zhang, Simon S. Lam, and Huaiyu Liu Department of Computer Sciences, The University of Texas at Austin, Austin, TX 7872 {zxc, lam, huaiyu}@cs.utexas.edu
Scalable Secure Group Communication over IP Multicast. Authors:Suman Banerjee, Bobby Bhattacharjee. Speaker: Kun Sun
 Scalable Secure Group Communication over IP Multicast Authors:Suman Banerjee, Bobby Bhattacharjee Speaker: Kun Sun Contents Introduction Related Work Secure multicast using clustering Spatial Clustering
Scalable Secure Group Communication over IP Multicast Authors:Suman Banerjee, Bobby Bhattacharjee Speaker: Kun Sun Contents Introduction Related Work Secure multicast using clustering Spatial Clustering
The Encoding Complexity of Network Coding
 The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
Name: 2 Useful Formulas Pn i=1 i = nèn+1è 2 Pn i=1 xi = xn+1,1 x,1 P Pn 1 =lnn + Oè1è 1 i=1 i i=0 = ixi x è1,xè 2 e x =1+x + x2 + x 3 2! 3! + ::: lim
 1 Exam 2 Computer Engineering 251 Santa Clara University Thursday, 23 April 1998 NAME èprintedè NAME èsignedè Login Day of Lab Session Please show all your work and circle your answers. Your grade will
1 Exam 2 Computer Engineering 251 Santa Clara University Thursday, 23 April 1998 NAME èprintedè NAME èsignedè Login Day of Lab Session Please show all your work and circle your answers. Your grade will
An Information-Theoretic Approach for Design and Analysis of Rooted-Tree-Based Multicast Key Management Schemes
 2824 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 47, NO. 7, NOVEMBER 2001 An Information-Theoretic Approach for Design and Analysis of Rooted-Tree-Based Multicast Key Management Schemes Radha Poovendran,
2824 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 47, NO. 7, NOVEMBER 2001 An Information-Theoretic Approach for Design and Analysis of Rooted-Tree-Based Multicast Key Management Schemes Radha Poovendran,
Boundary layer quadrilateral. Boundary layer
 CHAPTER 5 BOUNDARY LAYER MESHING - GROWTH CURVES 5.1 Boundary Layer Meshing Notations Cj i p i j;k Mi;j;k 0 fp i jg c i j;k Mi;j;k 1 fc i jg j th growth curve originating from Mi 0 k th node of the j th
CHAPTER 5 BOUNDARY LAYER MESHING - GROWTH CURVES 5.1 Boundary Layer Meshing Notations Cj i p i j;k Mi;j;k 0 fp i jg c i j;k Mi;j;k 1 fc i jg j th growth curve originating from Mi 0 k th node of the j th
53 M 0 j èm 2 i è ;1 M 0 j èm 2 i è ;1 èm 2 i è ;0 èm 2 i è ;0 (a) (b) M 0 i M 0 i (c) (d) Figure 6.1: Invalid boundary layer elements due to invisibi
 CHAPTER 6 BOUNDARY LAYER MESHING - ENSURING ELEMENT VALIDITY Growth curves are created with maximum consideration for topological validity and topological compatibility with the model. However, only preliminary
CHAPTER 6 BOUNDARY LAYER MESHING - ENSURING ELEMENT VALIDITY Growth curves are created with maximum consideration for topological validity and topological compatibility with the model. However, only preliminary
On The Complexity of Virtual Topology Design for Multicasting in WDM Trees with Tap-and-Continue and Multicast-Capable Switches
 On The Complexity of Virtual Topology Design for Multicasting in WDM Trees with Tap-and-Continue and Multicast-Capable Switches E. Miller R. Libeskind-Hadas D. Barnard W. Chang K. Dresner W. M. Turner
On The Complexity of Virtual Topology Design for Multicasting in WDM Trees with Tap-and-Continue and Multicast-Capable Switches E. Miller R. Libeskind-Hadas D. Barnard W. Chang K. Dresner W. M. Turner
AN OPTIMAL AND COST EFFECTIVE KEY MANAGEMENT SCHEME FOR SECURE MULTICAST COMMUNICATION
 AN OPTIMAL AND COST EFFECTIVE KEY MANAGEMENT SCHEME FOR SECURE MULTICAST COMMUNICATION SRIDHAR J K 1, SENTHIL KUMAR R 2, ARUN KUMAR S 3 1,2 Student, School Of Computing, SASTRA University, Thanjavur, India.
AN OPTIMAL AND COST EFFECTIVE KEY MANAGEMENT SCHEME FOR SECURE MULTICAST COMMUNICATION SRIDHAR J K 1, SENTHIL KUMAR R 2, ARUN KUMAR S 3 1,2 Student, School Of Computing, SASTRA University, Thanjavur, India.
Efficient Secured Model For Communication In Dynamic Multicast Groups
 IOSR Journal of Engineering (IOSRJEN) ISSN (e): 2250-3021, ISSN (p): 2278-8719 Vol. 05, Issue 06 (June. 2015), V1 PP 55-59 www.iosrjen.org Efficient Secured Model For Communication In Dynamic Multicast
IOSR Journal of Engineering (IOSRJEN) ISSN (e): 2250-3021, ISSN (p): 2278-8719 Vol. 05, Issue 06 (June. 2015), V1 PP 55-59 www.iosrjen.org Efficient Secured Model For Communication In Dynamic Multicast
Issues. Separation of. Distributed system security. Security services. Security policies. Security mechanism
 Module 9 - Security Issues Separation of Security policies Precise definition of which entities in the system can take what actions Security mechanism Means of enforcing that policy Distributed system
Module 9 - Security Issues Separation of Security policies Precise definition of which entities in the system can take what actions Security mechanism Means of enforcing that policy Distributed system
Cluster Based Group Key Management in Mobile Ad hoc Networks
 42 IJCSNS International Journal of Computer Science and Network Security, VOL.9 No.4, April 2009 Cluster Based Group Key Management in Mobile Ad hoc Networks Renuka A. and K.C.Shet, Dept. of Computer Science
42 IJCSNS International Journal of Computer Science and Network Security, VOL.9 No.4, April 2009 Cluster Based Group Key Management in Mobile Ad hoc Networks Renuka A. and K.C.Shet, Dept. of Computer Science
This chapter continues our overview of public-key cryptography systems (PKCSs), and begins with a description of one of the earliest and simplest
 1 2 3 This chapter continues our overview of public-key cryptography systems (PKCSs), and begins with a description of one of the earliest and simplest PKCS, Diffie- Hellman key exchange. This first published
1 2 3 This chapter continues our overview of public-key cryptography systems (PKCSs), and begins with a description of one of the earliest and simplest PKCS, Diffie- Hellman key exchange. This first published
Overview. SSL Cryptography Overview CHAPTER 1
 CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
Configuring Port-Based and Client-Based Access Control (802.1X)
 9 Configuring Port-Based and Client-Based Access Control (802.1X) Contents Overview..................................................... 9-3 Why Use Port-Based or Client-Based Access Control?............
9 Configuring Port-Based and Client-Based Access Control (802.1X) Contents Overview..................................................... 9-3 Why Use Port-Based or Client-Based Access Control?............
Ticket granting. Voting S. Ticket counting
 Anonymous Secure E-oting over a Network Yi Mu and ijay aradharajan School of Computing & IT, University of Western Sydney, Nepean, PO Box 10, Kingswood, NSW 2747, Australia Email: fyimu,vijayg@st.nepean.uws.edu.au
Anonymous Secure E-oting over a Network Yi Mu and ijay aradharajan School of Computing & IT, University of Western Sydney, Nepean, PO Box 10, Kingswood, NSW 2747, Australia Email: fyimu,vijayg@st.nepean.uws.edu.au
Decentralized Key Management for Large Dynamic Multicast Groups using Distributed Balanced Trees
 Decentralized Key Management for Large Dynamic Multicast Groups using Distributed Balanced Trees Thesis by Junaid Haroon MSCS018 Supervised by Mr Shafiq ur Rahman Flow of Presentation Background Proposed
Decentralized Key Management for Large Dynamic Multicast Groups using Distributed Balanced Trees Thesis by Junaid Haroon MSCS018 Supervised by Mr Shafiq ur Rahman Flow of Presentation Background Proposed
Efficient Group Key Management Schemes for Multicast Dynamic Communication Systems. Muhammad Yasir Malik
 Efficient Group Key Management Schemes for Multicast Dynamic Communication Systems Muhammad Yasir Malik 2012 Abstract Key management in multicast dynamic groups, where users can leave or join at their
Efficient Group Key Management Schemes for Multicast Dynamic Communication Systems Muhammad Yasir Malik 2012 Abstract Key management in multicast dynamic groups, where users can leave or join at their
2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006
 2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006 The Encoding Complexity of Network Coding Michael Langberg, Member, IEEE, Alexander Sprintson, Member, IEEE, and Jehoshua Bruck,
2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006 The Encoding Complexity of Network Coding Michael Langberg, Member, IEEE, Alexander Sprintson, Member, IEEE, and Jehoshua Bruck,
Secret Instantiation in Ad-Hoc Networks
 Secret Instantiation in Ad-Hoc Networs Sandeep S. Kularni Mohamed G. Gouda Anish Arora Department of Computer Department of Computer Sciences Department of Computer Science and Engineering The University
Secret Instantiation in Ad-Hoc Networs Sandeep S. Kularni Mohamed G. Gouda Anish Arora Department of Computer Department of Computer Sciences Department of Computer Science and Engineering The University
Networking Acronym Smorgasbord: , DVMRP, CBT, WFQ
 Networking Acronym Smorgasbord: 802.11, DVMRP, CBT, WFQ EE122 Fall 2011 Scott Shenker http://inst.eecs.berkeley.edu/~ee122/ Materials with thanks to Jennifer Rexford, Ion Stoica, Vern Paxson and other
Networking Acronym Smorgasbord: 802.11, DVMRP, CBT, WFQ EE122 Fall 2011 Scott Shenker http://inst.eecs.berkeley.edu/~ee122/ Materials with thanks to Jennifer Rexford, Ion Stoica, Vern Paxson and other
process variable x,y,a,b,c: integer begin x := b; -- d2 -- while (x < c) loop end loop; end process; d: a := b + c
 ControlData-æow Analysis for VHDL Semantic Extraction æ Yee-Wing Hsieh Steven P. Levitan Department of Electrical Engineering University of Pittsburgh Abstract Model abstraction reduces the number of states
ControlData-æow Analysis for VHDL Semantic Extraction æ Yee-Wing Hsieh Steven P. Levitan Department of Electrical Engineering University of Pittsburgh Abstract Model abstraction reduces the number of states
Group Key Agreement Protocols for Dynamic Peer Groups
 Nirav Jasapara jasapara@isi.edu Group Key Agreement Protocols for Dynamic Peer Groups ABSTRACT With the increased use of distributed services and applications, secure group communication over unsecured
Nirav Jasapara jasapara@isi.edu Group Key Agreement Protocols for Dynamic Peer Groups ABSTRACT With the increased use of distributed services and applications, secure group communication over unsecured
The ray tracing software package implements an object-oriented approach to
 Chapter 1 RayTracing 1.1 Using the ray tracer package The ray tracing software package implements an object-oriented approach to rendering and ray tracing. The object oriented design includes base classes
Chapter 1 RayTracing 1.1 Using the ray tracer package The ray tracing software package implements an object-oriented approach to rendering and ray tracing. The object oriented design includes base classes
Security: Focus of Control. Authentication
 Security: Focus of Control Three approaches for protection against security threats a) Protection against invalid operations b) Protection against unauthorized invocations c) Protection against unauthorized
Security: Focus of Control Three approaches for protection against security threats a) Protection against invalid operations b) Protection against unauthorized invocations c) Protection against unauthorized
(In)security of ecient tree-based group key agreement using bilinear map
 Loughborough University Institutional Repository (In)security of ecient tree-based group key agreement using bilinear map This item was submitted to Loughborough University's Institutional Repository by
Loughborough University Institutional Repository (In)security of ecient tree-based group key agreement using bilinear map This item was submitted to Loughborough University's Institutional Repository by
Security: Focus of Control
 Security: Focus of Control Three approaches for protection against security threats a) Protection against invalid operations b) Protection against unauthorized invocations c) Protection against unauthorized
Security: Focus of Control Three approaches for protection against security threats a) Protection against invalid operations b) Protection against unauthorized invocations c) Protection against unauthorized
Red-Black-Trees and Heaps in Timestamp-Adjusting Sweepline Based Algorithms
 Department of Informatics, University of Zürich Vertiefungsarbeit Red-Black-Trees and Heaps in Timestamp-Adjusting Sweepline Based Algorithms Mirko Richter Matrikelnummer: 12-917-175 Email: mirko.richter@uzh.ch
Department of Informatics, University of Zürich Vertiefungsarbeit Red-Black-Trees and Heaps in Timestamp-Adjusting Sweepline Based Algorithms Mirko Richter Matrikelnummer: 12-917-175 Email: mirko.richter@uzh.ch
Master s Thesis. A Construction Method of an Overlay Network for Scalable P2P Video Conferencing Systems
 Master s Thesis Title A Construction Method of an Overlay Network for Scalable P2P Video Conferencing Systems Supervisor Professor Masayuki Murata Author Hideto Horiuchi February 14th, 2007 Department
Master s Thesis Title A Construction Method of an Overlay Network for Scalable P2P Video Conferencing Systems Supervisor Professor Masayuki Murata Author Hideto Horiuchi February 14th, 2007 Department
Inænitely Long Walks on 2-colored Graphs Which Don't Cover the. Graph. Pete Gemmell æ. December 14, Abstract
 Inænitely Long Walks on 2-colored Graphs Which Don't Cover the Graph Pete Gemmell æ December 14, 1992 Abstract Suppose we have a undirected graph G =èv; Eè where V is the set of vertices and E is the set
Inænitely Long Walks on 2-colored Graphs Which Don't Cover the Graph Pete Gemmell æ December 14, 1992 Abstract Suppose we have a undirected graph G =èv; Eè where V is the set of vertices and E is the set
BWM CRM, PRM CRM, WB, PRM BRM, WB CWM, CWH, PWM. Exclusive (read/write) CWM PWM
 University of California, Berkeley College of Engineering Computer Science Division EECS Spring 1998 D.A. Patterson Quiz 2 April 22, 1998 CS252 Graduate Computer Architecture You are allowed to use a calculator
University of California, Berkeley College of Engineering Computer Science Division EECS Spring 1998 D.A. Patterson Quiz 2 April 22, 1998 CS252 Graduate Computer Architecture You are allowed to use a calculator
Heuristics for Improving Cryptographic Key Assignment in a Hierarchy
 Heuristics for Improving Cryptographic Key Assignment in a Hierarchy Anne V.D.M. Kayem, Patrick Martin, and Selim G. Akl School of Computing, Queen s University Kingston, Ontario, CANADA, K7L 3N6 kayem@cs.queensu.ca,
Heuristics for Improving Cryptographic Key Assignment in a Hierarchy Anne V.D.M. Kayem, Patrick Martin, and Selim G. Akl School of Computing, Queen s University Kingston, Ontario, CANADA, K7L 3N6 kayem@cs.queensu.ca,
REDUCTION CUT INVERTED SUM
 Irreducible Plane Curves Jason E. Durham æ Oregon State University Corvallis, Oregon durhamj@ucs.orst.edu August 4, 1999 Abstract Progress in the classiæcation of plane curves in the last æve years has
Irreducible Plane Curves Jason E. Durham æ Oregon State University Corvallis, Oregon durhamj@ucs.orst.edu August 4, 1999 Abstract Progress in the classiæcation of plane curves in the last æve years has
An Optimal Symmetric Secret Distribution of Star Networks 1
 An Optimal Symmetric Secret Distribution of Star Networks 1 Bruhadeshwar Bezawada Department of Computer Science International Institute of Information Technology Hyderabad, India 500032 Sandeep S. Kulkarni
An Optimal Symmetric Secret Distribution of Star Networks 1 Bruhadeshwar Bezawada Department of Computer Science International Institute of Information Technology Hyderabad, India 500032 Sandeep S. Kulkarni
Cryptography and Network Security. Prof. D. Mukhopadhyay. Department of Computer Science and Engineering. Indian Institute of Technology, Kharagpur
 Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Module No. # 01 Lecture No. # 38 A Tutorial on Network Protocols
Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Module No. # 01 Lecture No. # 38 A Tutorial on Network Protocols
æ When a query is presented to the system, it is useful to ænd an eæcient method of ænding the answer,
 CMPT-354-98.2 Lecture Notes July 26, 1998 Chapter 12 Query Processing 12.1 Query Interpretation 1. Why dowe need to optimize? æ A high-level relational query is generally non-procedural in nature. æ It
CMPT-354-98.2 Lecture Notes July 26, 1998 Chapter 12 Query Processing 12.1 Query Interpretation 1. Why dowe need to optimize? æ A high-level relational query is generally non-procedural in nature. æ It
Slow Path. Output Buffers 1 N N. Fast Path Switch Fabric. Slow Path. Output Buffers. Fast Path
 High-Speed Policy-based Packet Forwarding Using Eæcient Multi-dimensional Range Matching T.V. Lakshman and D. Stiliadis Bell Laboratories Crawfords Corner Rd. Holmdel, NJ 7733 flakshman, stiliadi g@bell-labs.com
High-Speed Policy-based Packet Forwarding Using Eæcient Multi-dimensional Range Matching T.V. Lakshman and D. Stiliadis Bell Laboratories Crawfords Corner Rd. Holmdel, NJ 7733 flakshman, stiliadi g@bell-labs.com
One motivation for developing axiomatic systems is to determine precisely which properties
 1 Axiomatic Systems 1.1 Features of Axiomatic Systems One motivation for developing axiomatic systems is to determine precisely which properties of certain objects can be deduced from which other properties.
1 Axiomatic Systems 1.1 Features of Axiomatic Systems One motivation for developing axiomatic systems is to determine precisely which properties of certain objects can be deduced from which other properties.
TECHNICAL RESEARCH REPORT
 TECHNICAL RESEARCH REPORT A Scalable Extension of Group Key Management Protocol by R. Poovendran, S. Ahmed, S. Corson, J. Baras CSHCN T.R. 98-5 (ISR T.R. 98-14) The Center for Satellite and Hybrid Communication
TECHNICAL RESEARCH REPORT A Scalable Extension of Group Key Management Protocol by R. Poovendran, S. Ahmed, S. Corson, J. Baras CSHCN T.R. 98-5 (ISR T.R. 98-14) The Center for Satellite and Hybrid Communication
Verteilte Systeme (Distributed Systems)
 Verteilte Systeme (Distributed Systems) Lorenz Froihofer l.froihofer@infosys.tuwien.ac.at http://www.infosys.tuwien.ac.at/teaching/courses/ VerteilteSysteme/ Security Threats, mechanisms, design issues
Verteilte Systeme (Distributed Systems) Lorenz Froihofer l.froihofer@infosys.tuwien.ac.at http://www.infosys.tuwien.ac.at/teaching/courses/ VerteilteSysteme/ Security Threats, mechanisms, design issues
Analysis of Binary Adjustment Algorithms in Fair Heterogeneous Networks
 Analysis of Binary Adjustment Algorithms in Fair Heterogeneous Networks Sergey Gorinsky Harrick Vin Technical Report TR2000-32 Department of Computer Sciences, University of Texas at Austin Taylor Hall
Analysis of Binary Adjustment Algorithms in Fair Heterogeneous Networks Sergey Gorinsky Harrick Vin Technical Report TR2000-32 Department of Computer Sciences, University of Texas at Austin Taylor Hall
Packet Classification Using Dynamically Generated Decision Trees
 1 Packet Classification Using Dynamically Generated Decision Trees Yu-Chieh Cheng, Pi-Chung Wang Abstract Binary Search on Levels (BSOL) is a decision-tree algorithm for packet classification with superior
1 Packet Classification Using Dynamically Generated Decision Trees Yu-Chieh Cheng, Pi-Chung Wang Abstract Binary Search on Levels (BSOL) is a decision-tree algorithm for packet classification with superior
PART I. Answer each of the following. è1è Let! u = h2;,1;,2i and! v = h3; 1;,1i. Calculate: èaè! u, 2! v èbè the dot product of! u and! v ècè! u æ! v
 MATH 241: FINAL EXAM Name Instructions and Point Values: Put your name in the space provided above. Check that your test contains 14 diæerent pages including one blank page. Work each problem below and
MATH 241: FINAL EXAM Name Instructions and Point Values: Put your name in the space provided above. Check that your test contains 14 diæerent pages including one blank page. Work each problem below and
FDLKH: Fully Decentralized Key Management Scheme on Logical Key Hierarchy
 FDLKH: Fully Decentralized Key Management Scheme on Logical Key Hierarchy Daisuke Inoue and Masahiro Kuroda National Institute of Information and Communications Technology, 3-4, Hikarino-oka, Yokosuka,
FDLKH: Fully Decentralized Key Management Scheme on Logical Key Hierarchy Daisuke Inoue and Masahiro Kuroda National Institute of Information and Communications Technology, 3-4, Hikarino-oka, Yokosuka,
Math 241: Calculus III Final Exam è300 points totalè Show All Work Name This test consists of 2 parts. There are 10 problems in Part I, each worth 18
 Math 241: Calculus III Final Exam è300 points totalè Show All Work Name This test consists of 2 parts. There are 10 problems in Part I, each worth 18 points; and there are 5 problems in Part II, each worth
Math 241: Calculus III Final Exam è300 points totalè Show All Work Name This test consists of 2 parts. There are 10 problems in Part I, each worth 18 points; and there are 5 problems in Part II, each worth
No, the bogus packet will fail the integrity check (which uses a shared MAC key).!
 1. High level questions a. Suppose Alice and Bob are communicating over an SSL session. Suppose an attacker, who does not have any of the shared keys, inserts a bogus TCP segment into a packet stream with
1. High level questions a. Suppose Alice and Bob are communicating over an SSL session. Suppose an attacker, who does not have any of the shared keys, inserts a bogus TCP segment into a packet stream with
task type nodes is entry initialize èwith mailbox: access to mailboxes; with state: in statesè; entry ænalize èstate: out statesè; end nodes; task bod
 Redistribution in Distributed Ada April 16, 1999 Abstract In this paper we will provide a model using Ada and the Distributed Annex for relocating concurrent objects in a distributed dataæow application.
Redistribution in Distributed Ada April 16, 1999 Abstract In this paper we will provide a model using Ada and the Distributed Annex for relocating concurrent objects in a distributed dataæow application.
Lectures 4+5: The (In)Security of Encrypted Search
 Lectures 4+5: The (In)Security of Encrypted Search Contents 1 Overview 1 2 Data Structures 2 3 Syntax 3 4 Security 4 4.1 Formalizing Leaky Primitives.......................... 5 1 Overview In the first
Lectures 4+5: The (In)Security of Encrypted Search Contents 1 Overview 1 2 Data Structures 2 3 Syntax 3 4 Security 4 4.1 Formalizing Leaky Primitives.......................... 5 1 Overview In the first
Network Security CHAPTER 31. Solutions to Review Questions and Exercises. Review Questions
 CHAPTER 3 Network Security Solutions to Review Questions and Exercises Review Questions. A nonce is a large random number that is used only once to help distinguish a fresh authentication request from
CHAPTER 3 Network Security Solutions to Review Questions and Exercises Review Questions. A nonce is a large random number that is used only once to help distinguish a fresh authentication request from
CIS 6930/4930 Computer and Network Security. Topic 7. Trusted Intermediaries
 CIS 6930/4930 Computer and Network Security Topic 7. Trusted Intermediaries 1 Trusted Intermediaries Problem: authentication for large networks Solution #1 Key Distribution Center (KDC) Representative
CIS 6930/4930 Computer and Network Security Topic 7. Trusted Intermediaries 1 Trusted Intermediaries Problem: authentication for large networks Solution #1 Key Distribution Center (KDC) Representative
Multicast EECS 122: Lecture 16
 Multicast EECS 1: Lecture 16 Department of Electrical Engineering and Computer Sciences University of California Berkeley Broadcasting to Groups Many applications are not one-one Broadcast Group collaboration
Multicast EECS 1: Lecture 16 Department of Electrical Engineering and Computer Sciences University of California Berkeley Broadcasting to Groups Many applications are not one-one Broadcast Group collaboration
CS007 Fall Out : November 25, 1997; 2:30 pm. You have recently come to appreciate the aesthetic beauty of lava lamps, and want to purchase one.
 Experiment 1: Lab è8 Out : November 25, 1997; 2:30 pm Due : Dec 4, 1997, 12:30 pm You have recently come to appreciate the aesthetic beauty of lava lamps, and want to purchase one. You've found a great
Experiment 1: Lab è8 Out : November 25, 1997; 2:30 pm Due : Dec 4, 1997, 12:30 pm You have recently come to appreciate the aesthetic beauty of lava lamps, and want to purchase one. You've found a great
FUTURE communication networks are expected to support
 1146 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL 13, NO 5, OCTOBER 2005 A Scalable Approach to the Partition of QoS Requirements in Unicast and Multicast Ariel Orda, Senior Member, IEEE, and Alexander Sprintson,
1146 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL 13, NO 5, OCTOBER 2005 A Scalable Approach to the Partition of QoS Requirements in Unicast and Multicast Ariel Orda, Senior Member, IEEE, and Alexander Sprintson,
BWM CRM, PRM CRM, WB, PRM BRM, WB CWM, CWH, PWM. Exclusive (read/write) CWM PWM
 University of California, Berkeley College of Engineering Computer Science Division EECS Spring 998 D.A. Patterson Quiz 2 Solutions CS252 Graduate Computer Architecture Question : Bigger, Better, Faster?
University of California, Berkeley College of Engineering Computer Science Division EECS Spring 998 D.A. Patterson Quiz 2 Solutions CS252 Graduate Computer Architecture Question : Bigger, Better, Faster?
I Metric I Explanation Robustness
 Towards Solving Multicast Key Management Problem Fan Du, Lionel M. Ni and Abdol-Hossein Esfahanian Department of Computer Science and Engineering Michigan State University East Lansing, M 48824 Abstract-
Towards Solving Multicast Key Management Problem Fan Du, Lionel M. Ni and Abdol-Hossein Esfahanian Department of Computer Science and Engineering Michigan State University East Lansing, M 48824 Abstract-
Introduction. Trusted Intermediaries. CSC/ECE 574 Computer and Network Security. Outline. CSC/ECE 574 Computer and Network Security.
 Trusted Intermediaries CSC/ECE 574 Computer and Network Security Topic 7. Trusted Intermediaries Problem: authentication for large networks Solution #1 Key Distribution Center () Representative solution:
Trusted Intermediaries CSC/ECE 574 Computer and Network Security Topic 7. Trusted Intermediaries Problem: authentication for large networks Solution #1 Key Distribution Center () Representative solution:
Cryptography CS 555. Topic 16: Key Management and The Need for Public Key Cryptography. CS555 Spring 2012/Topic 16 1
 Cryptography CS 555 Topic 16: Key Management and The Need for Public Key Cryptography CS555 Spring 2012/Topic 16 1 Outline and Readings Outline Private key management between two parties Key management
Cryptography CS 555 Topic 16: Key Management and The Need for Public Key Cryptography CS555 Spring 2012/Topic 16 1 Outline and Readings Outline Private key management between two parties Key management
An Algorithm for Multicast with Multiple QoS Constraints
 An Algorithm for Multicast with Multiple QoS Constraints and Dynamic Membership Aiguo Fei and Mario Gerla Network Research Lab, Department of Computer Science University of California, Los Angeles, CA
An Algorithm for Multicast with Multiple QoS Constraints and Dynamic Membership Aiguo Fei and Mario Gerla Network Research Lab, Department of Computer Science University of California, Los Angeles, CA
Core Security Services and Bootstrapping in the Cherubim Security System
 Core Security Services and Bootstrapping in the Cherubim Security System Charles Willis cfwillis@uiuc.edu Technical Report 2 July 1998 University of Illinois at Urbana-Champaign Department of Computer
Core Security Services and Bootstrapping in the Cherubim Security System Charles Willis cfwillis@uiuc.edu Technical Report 2 July 1998 University of Illinois at Urbana-Champaign Department of Computer
A CPLD-based RC-4 Cracking System. short ètypically 32 or 40 bitsè sequence of bits. As long as. thus can not decrypt the message.
 A CPLD-based RC-4 Cracking System Paul D. Kundarewich and Steven J.E. Wilton Dept. of Electrical and Computer Engineering University of British Columbia Vancouver, BC, Canada kundarew@ieee.org, stevew@ece.ubc.ca
A CPLD-based RC-4 Cracking System Paul D. Kundarewich and Steven J.E. Wilton Dept. of Electrical and Computer Engineering University of British Columbia Vancouver, BC, Canada kundarew@ieee.org, stevew@ece.ubc.ca
Bayeux: An Architecture for Scalable and Fault Tolerant Wide area Data Dissemination
 Bayeux: An Architecture for Scalable and Fault Tolerant Wide area Data Dissemination By Shelley Zhuang,Ben Zhao,Anthony Joseph, Randy Katz,John Kubiatowicz Introduction Multimedia Streaming typically involves
Bayeux: An Architecture for Scalable and Fault Tolerant Wide area Data Dissemination By Shelley Zhuang,Ben Zhao,Anthony Joseph, Randy Katz,John Kubiatowicz Introduction Multimedia Streaming typically involves
CSC 774 Network Security
 CSC 774 Network Security Mid-Term Exam #2 4:10pm 5:00pm, March 26, 2004 Student Name: Score: You are allowed to use your textbook and notes; however, you are not allowed to exchange anything before you
CSC 774 Network Security Mid-Term Exam #2 4:10pm 5:00pm, March 26, 2004 Student Name: Score: You are allowed to use your textbook and notes; however, you are not allowed to exchange anything before you
Encryption Algorithms Authentication Protocols Message Integrity Protocols Key Distribution Firewalls
 Security Outline Encryption Algorithms Authentication Protocols Message Integrity Protocols Key Distribution Firewalls Overview Cryptography functions Secret key (e.g., DES) Public key (e.g., RSA) Message
Security Outline Encryption Algorithms Authentication Protocols Message Integrity Protocols Key Distribution Firewalls Overview Cryptography functions Secret key (e.g., DES) Public key (e.g., RSA) Message
Abstract. over which the system is scattered. The administrative dimension consists of the number
 Scale in Distributed Systems B. Cliæord Neuman Information Sciences Institute University of Southern California Abstract In recent years, scale has become a factor of increasing importance in the design
Scale in Distributed Systems B. Cliæord Neuman Information Sciences Institute University of Southern California Abstract In recent years, scale has become a factor of increasing importance in the design
TECHNICAL RESEARCH REPORT
 TECHNICAL RESEARCH REPORT A Simulation Study of Enhanced TCP/IP Gateways for Broadband Internet over Satellite by Manish Karir, Mingyan Liu, Bradley Barrett, John S. Baras CSHCN T.R. 99-34 (ISR T.R. 99-66)
TECHNICAL RESEARCH REPORT A Simulation Study of Enhanced TCP/IP Gateways for Broadband Internet over Satellite by Manish Karir, Mingyan Liu, Bradley Barrett, John S. Baras CSHCN T.R. 99-34 (ISR T.R. 99-66)
CSCE 813 Internet Security Secure Services I
 CSCE 813 Internet Security Secure E-Mail Services I Professor Lisa Luo Fall 2017 Previous Class Why do we need cloud computing? Three models of cloud service Software as a service (SaaS) Platform as a
CSCE 813 Internet Security Secure E-Mail Services I Professor Lisa Luo Fall 2017 Previous Class Why do we need cloud computing? Three models of cloud service Software as a service (SaaS) Platform as a
(2½ hours) Total Marks: 75
 (2½ hours) Total Marks: 75 N. B.: (1) All questions are compulsory. (2) Makesuitable assumptions wherever necessary and state the assumptions made. (3) Answers to the same question must be written together.
(2½ hours) Total Marks: 75 N. B.: (1) All questions are compulsory. (2) Makesuitable assumptions wherever necessary and state the assumptions made. (3) Answers to the same question must be written together.
Review for Chapter 4 R1,R2,R3,R7,R10,R11,R16,R17,R19,R22,R24, R26,R30 P1,P2,P4,P7,P10,P11,P12,P14,P15,P16,P17,P22,P24,P29,P30
 Review for Chapter 4 R1,R2,R3,R7,R10,R11,R16,R17,R19,R22,R24, R26,R30 P1,P2,P4,P7,P10,P11,P12,P14,P15,P16,P17,P22,P24,P29,P30 R1. Let s review some of the terminology used in this textbook. Recall that
Review for Chapter 4 R1,R2,R3,R7,R10,R11,R16,R17,R19,R22,R24, R26,R30 P1,P2,P4,P7,P10,P11,P12,P14,P15,P16,P17,P22,P24,P29,P30 R1. Let s review some of the terminology used in this textbook. Recall that
University of Texas at Austin. Austin, TX Nathaniel Dean. Combinatorics and Optimization Research. Bell Communications Research
 Implementation of Parallel Graph Algorithms on a Massively Parallel SIMD Computer with Virtual Processing Tsan-sheng Hsu æy & Vijaya Ramachandran æ Department of Computer Sciences University of Texas at
Implementation of Parallel Graph Algorithms on a Massively Parallel SIMD Computer with Virtual Processing Tsan-sheng Hsu æy & Vijaya Ramachandran æ Department of Computer Sciences University of Texas at
3. G. G. Lemieux and S. D. Brown, ëa detailed router for allocating wire segments
 . Xilinx, Inc., The Programmable Logic Data Book, 99.. G. G. Lemieux and S. D. Brown, ëa detailed router for allocating wire segments in æeld-programmable gate arrays," in Proceedings of the ACM Physical
. Xilinx, Inc., The Programmable Logic Data Book, 99.. G. G. Lemieux and S. D. Brown, ëa detailed router for allocating wire segments in æeld-programmable gate arrays," in Proceedings of the ACM Physical
Security. Communication security. System Security
 Security Communication security security of data channel typical assumption: adversary has access to the physical link over which data is transmitted cryptographic separation is necessary System Security
Security Communication security security of data channel typical assumption: adversary has access to the physical link over which data is transmitted cryptographic separation is necessary System Security
Figure 4.1: The evolution of a rooted tree.
 106 CHAPTER 4. INDUCTION, RECURSION AND RECURRENCES 4.6 Rooted Trees 4.6.1 The idea of a rooted tree We talked about how a tree diagram helps us visualize merge sort or other divide and conquer algorithms.
106 CHAPTER 4. INDUCTION, RECURSION AND RECURRENCES 4.6 Rooted Trees 4.6.1 The idea of a rooted tree We talked about how a tree diagram helps us visualize merge sort or other divide and conquer algorithms.
Secure Group Key Management Scheme for Multicast Networks
 International Journal of Network Security, Vol.11, No.1, PP.33 38, July 21 33 Secure Group Key Management Scheme for Multicast Networks R. Srinivasan, V. Vaidehi, R. Rajaraman, S. Kanagaraj, R. Chidambaram
International Journal of Network Security, Vol.11, No.1, PP.33 38, July 21 33 Secure Group Key Management Scheme for Multicast Networks R. Srinivasan, V. Vaidehi, R. Rajaraman, S. Kanagaraj, R. Chidambaram
VPN Overview. VPN Types
 VPN Types A virtual private network (VPN) connection establishes a secure tunnel between endpoints over a public network such as the Internet. This chapter applies to Site-to-site VPNs on Firepower Threat
VPN Types A virtual private network (VPN) connection establishes a secure tunnel between endpoints over a public network such as the Internet. This chapter applies to Site-to-site VPNs on Firepower Threat
Encryption. INST 346, Section 0201 April 3, 2018
 Encryption INST 346, Section 0201 April 3, 2018 Goals for Today Symmetric Key Encryption Public Key Encryption Certificate Authorities Secure Sockets Layer Simple encryption scheme substitution cipher:
Encryption INST 346, Section 0201 April 3, 2018 Goals for Today Symmetric Key Encryption Public Key Encryption Certificate Authorities Secure Sockets Layer Simple encryption scheme substitution cipher:
Cryptography and Network Security Chapter 14
 Cryptography and Network Security Chapter 14 Fifth Edition by William Stallings Lecture slides by Lawrie Brown Chapter 14 Key Management and Distribution No Singhalese, whether man or woman, would venture
Cryptography and Network Security Chapter 14 Fifth Edition by William Stallings Lecture slides by Lawrie Brown Chapter 14 Key Management and Distribution No Singhalese, whether man or woman, would venture
The most important development from the work on public-key cryptography is the digital signature. Message authentication protects two parties who
 1 The most important development from the work on public-key cryptography is the digital signature. Message authentication protects two parties who exchange messages from any third party. However, it does
1 The most important development from the work on public-key cryptography is the digital signature. Message authentication protects two parties who exchange messages from any third party. However, it does
On the Space-Time Trade-off in Solving Constraint Satisfaction Problems*
 Appeared in Proc of the 14th Int l Joint Conf on Artificial Intelligence, 558-56, 1995 On the Space-Time Trade-off in Solving Constraint Satisfaction Problems* Roberto J Bayardo Jr and Daniel P Miranker
Appeared in Proc of the 14th Int l Joint Conf on Artificial Intelligence, 558-56, 1995 On the Space-Time Trade-off in Solving Constraint Satisfaction Problems* Roberto J Bayardo Jr and Daniel P Miranker
Trees. Q: Why study trees? A: Many advance ADTs are implemented using tree-based data structures.
 Trees Q: Why study trees? : Many advance DTs are implemented using tree-based data structures. Recursive Definition of (Rooted) Tree: Let T be a set with n 0 elements. (i) If n = 0, T is an empty tree,
Trees Q: Why study trees? : Many advance DTs are implemented using tree-based data structures. Recursive Definition of (Rooted) Tree: Let T be a set with n 0 elements. (i) If n = 0, T is an empty tree,
Trusted Intermediaries
 AIT 682: Network and Systems Security Topic 7. Trusted Intermediaries Instructor: Dr. Kun Sun Trusted Intermediaries Problem: authentication for large networks Solution #1 Key Distribution Center (KDC)
AIT 682: Network and Systems Security Topic 7. Trusted Intermediaries Instructor: Dr. Kun Sun Trusted Intermediaries Problem: authentication for large networks Solution #1 Key Distribution Center (KDC)
AIT 682: Network and Systems Security
 AIT 682: Network and Systems Security Topic 7. Trusted Intermediaries Instructor: Dr. Kun Sun Trusted Intermediaries Problem: authentication for large networks Solution #1 Key Distribution Center (KDC)
AIT 682: Network and Systems Security Topic 7. Trusted Intermediaries Instructor: Dr. Kun Sun Trusted Intermediaries Problem: authentication for large networks Solution #1 Key Distribution Center (KDC)
CSC/ECE 774 Advanced Network Security
 Computer Science CSC/ECE 774 Advanced Network Security Topic 2. Network Security Primitives CSC/ECE 774 Dr. Peng Ning 1 Outline Absolute basics Encryption/Decryption; Digital signatures; D-H key exchange;
Computer Science CSC/ECE 774 Advanced Network Security Topic 2. Network Security Primitives CSC/ECE 774 Dr. Peng Ning 1 Outline Absolute basics Encryption/Decryption; Digital signatures; D-H key exchange;
IBM i Version 7.2. Security Digital Certificate Manager IBM
 IBM i Version 7.2 Security Digital Certificate Manager IBM IBM i Version 7.2 Security Digital Certificate Manager IBM Note Before using this information and the product it supports, read the information
IBM i Version 7.2 Security Digital Certificate Manager IBM IBM i Version 7.2 Security Digital Certificate Manager IBM Note Before using this information and the product it supports, read the information
Lutz Prechelt Fakultíat fíur Informatik. Universitíat Karlsruhe, Postfach Dí7500 Karlsruhe, Germany.
 Comparison of MasPar MP-1 and MP- Communication Operations Lutz Prechelt èprechelt@ira.uka.deè Institut fíur Programmstrukturen und Datenorganisation Fakultíat fíur Informatik Universitíat Karlsruhe, Postfach
Comparison of MasPar MP-1 and MP- Communication Operations Lutz Prechelt èprechelt@ira.uka.deè Institut fíur Programmstrukturen und Datenorganisation Fakultíat fíur Informatik Universitíat Karlsruhe, Postfach
Binary Decision Diagrams
 Logic and roof Hilary 2016 James Worrell Binary Decision Diagrams A propositional formula is determined up to logical equivalence by its truth table. If the formula has n variables then its truth table
Logic and roof Hilary 2016 James Worrell Binary Decision Diagrams A propositional formula is determined up to logical equivalence by its truth table. If the formula has n variables then its truth table
Cryptography Today. Ali El Kaafarani. Mathematical Institute Oxford University. 1 of 44
 Cryptography Today Ali El Kaafarani Mathematical Institute Oxford University 1 of 44 About the Course Regular classes with worksheets so you can work with some concrete examples (every Friday at 1pm).
Cryptography Today Ali El Kaafarani Mathematical Institute Oxford University 1 of 44 About the Course Regular classes with worksheets so you can work with some concrete examples (every Friday at 1pm).
CIS265/ Trees Red-Black Trees. Some of the following material is from:
 CIS265/506 2-3-4 Trees Red-Black Trees Some of the following material is from: Data Structures for Java William H. Ford William R. Topp ISBN 0-13-047724-9 Chapter 27 Balanced Search Trees Bret Ford 2005,
CIS265/506 2-3-4 Trees Red-Black Trees Some of the following material is from: Data Structures for Java William H. Ford William R. Topp ISBN 0-13-047724-9 Chapter 27 Balanced Search Trees Bret Ford 2005,
Binary search trees. We can define a node in a search tree using a Python class definition as follows: class SearchTree:
 Binary search trees An important use of binary trees is to store values that we may want to look up later. For instance, a binary search tree could be used to store a dictionary of words. A binary search
Binary search trees An important use of binary trees is to store values that we may want to look up later. For instance, a binary search tree could be used to store a dictionary of words. A binary search
Outline. Data Encryption Standard. Symmetric-Key Algorithms. Lecture 4
 EEC 693/793 Special Topics in Electrical Engineering Secure and Dependable Computing Lecture 4 Department of Electrical and Computer Engineering Cleveland State University wenbing@ieee.org Outline Review
EEC 693/793 Special Topics in Electrical Engineering Secure and Dependable Computing Lecture 4 Department of Electrical and Computer Engineering Cleveland State University wenbing@ieee.org Outline Review
Maintaining Mutual Consistency for Cached Web Objects
 Maintaining Mutual Consistency for Cached Web Objects Bhuvan Urgaonkar, Anoop George Ninan, Mohammad Salimullah Raunak Prashant Shenoy and Krithi Ramamritham Department of Computer Science, University
Maintaining Mutual Consistency for Cached Web Objects Bhuvan Urgaonkar, Anoop George Ninan, Mohammad Salimullah Raunak Prashant Shenoy and Krithi Ramamritham Department of Computer Science, University
A,B,C,D 1 E,F,G H,I,J 3 B 5 6 K,L 4 M,N,O
 HYCORE: A Hybrid Static-Dynamic Technique to Reduce Communication in Parallel Systems via Scheduling and Re-routing æ David R. Surma Edwin H.-M. Sha Peter M. Kogge Department of Computer Science and Engineering
HYCORE: A Hybrid Static-Dynamic Technique to Reduce Communication in Parallel Systems via Scheduling and Re-routing æ David R. Surma Edwin H.-M. Sha Peter M. Kogge Department of Computer Science and Engineering
Organizing Spatial Data
 Organizing Spatial Data Spatial data records include a sense of location as an attribute. Typically location is represented by coordinate data (in 2D or 3D). 1 If we are to search spatial data using the
Organizing Spatial Data Spatial data records include a sense of location as an attribute. Typically location is represented by coordinate data (in 2D or 3D). 1 If we are to search spatial data using the
Junos Security. Chapter 8: IPsec VPNs Juniper Networks, Inc. All rights reserved. Worldwide Education Services
 Junos Security Chapter 8: IPsec VPNs 2012 Juniper Networks, Inc. All rights reserved. www.juniper.net Worldwide Education Services Chapter Objectives After successfully completing this chapter, you will
Junos Security Chapter 8: IPsec VPNs 2012 Juniper Networks, Inc. All rights reserved. www.juniper.net Worldwide Education Services Chapter Objectives After successfully completing this chapter, you will
George Mason University. Fairfax, VA æa paper submitted for possible presentation at the IEEE Computer Security Foundations
 On the Expressive Power of the Unary Transformation Model æy Ravi S. Sandhu and Srinivas Ganta z Center for Secure Information Systems & Department of Information and Software Systems Engineering George
On the Expressive Power of the Unary Transformation Model æy Ravi S. Sandhu and Srinivas Ganta z Center for Secure Information Systems & Department of Information and Software Systems Engineering George
