Project 2-3: Intrusion Detection System
|
|
|
- Lawrence Walters
- 6 years ago
- Views:
Transcription
1 Project 2-3: Intrusion Detection System Information Security April 18, Introduction 1.1 General Summary An intrusion detection system looks for known attacks. A simple type of intrusion detection system looks for attack signatures. This assignment will require you to detect some known attacks and log them. 2 Network Integrity (50%) You will only have a single program for this assignment. It must be named ids on Linux/Unix platforms, or ids.exe on Windows platforms. You will only need to worry about monitoring TCP traffic. Modern IDS programs check for a variety of things, you will be asked to check for only three significant signatures of attack. 1.) Detect for OS remote detection. You should be able to use your code from a previous lab to accomplish this fairly easily. Consider a remote hosts that sends 5 packets with different Syn, Ack, and Fin combinations within 20 seconds to be malicious. 2.) Check for rudimentary(not stealth) style of port scans. To do this, simply monitor traffic and watch for a single IP trying to connect to sequential ports. For this assignment, consider a host trying connecting to 5 sequential ports to be malicious. 3.) Implement the ability to detect buffer overflow attacks. This can be done by sniffing data from the network traffic and looking for a group of NOP (no operation) commands. Using NOP is a common occurrence when an attacker writes a buffer overflow program. Consider a packet load containing 5 or more sequential NOP commands to be malicious. Also, instead of searching for the exact machine code of the NOP command, consider the ASCII letters NOP to be the NOP command. In order to read packets, use libpcap if you are programming in a Linux/Unix type of environment, or WinPcap if you are programming in a Microsoft Windows environment. They can natively be 1
2 used with C/C++ and have bindings to Java as well. For Linux/Unix users, the libpcap library can be downloaded from For Windows useres, the winpcap library can be downloaded form Whether you use libpcap, or winpcap, read the tutorial from each website, which will give you a very good understanding and examples of how pcap works. It is also recommended you read and understand the supplied examples that come with the source code download. For ease of programming, only worry about IPV4 and disregard IPV6. 3 Intrusion Notification (35%) When an attack signature is identified, it should log the suspicion to a file named ids.txt, including: the type of intrusion that was detected, where it was from, and what time it occurred. It should then completely block the offending IP using your code from your previously created firewall program. The following is an example of what an ids.txt file might look like : Port Scan : OS Fingerprint : Buffer Overflow The file should be in this format: MMDDYY-HH:MM.SS <IP> <Reason> 4 User Interface (10%) Your program will have menu that must look and behave like the following: 1) Start IDS 2) Stop IDS 3) View Current Traffic 4) View Block List 5) View Current Firewall Rules 6) Unblock User 7) Quit 2
3 4.1 Start IDS Start monitoring all traffic, and begin analyzing for criteria specified in below sections. If activation works, respond Started IDS!, else respond Error! Unable to start IDS!, with appropriate error message. # Start the firewall, should give positive feedback 1 Started IDS! # If there is an error 1 Error! Unable to start IDS! Can t Open Device 4.2 Stop IDS Stop monitoring traffic, and clear all lists of blocked users and firewall rules. If deactivation works, respond Stopped IDS!, else respond Error! Unable to stop IDS!, with appropriate error message. # Start the firewall, should give positive feedback 2 Stopped IDS! 3
4 # If there is an error 1 Error! Unable to stop IDS! IDS already stopped 4.3 View Current Traffic Simply start dumping all sniffed traffic to the console traffic for 10 seconds. Use the standard pcap way of presenting the data. 4.4 View Block List List all IP addresses that are currently blocked and the reason for being blocked. Below are the three possible reasons for being blocked Port Scan OS Fingerprint Buffer Overflow The output should be in this format: <User#>-<SIP> - <Reason> 4.5 View Current Firewall Rules Print rules in order they were entered. Make sure to number them, so the user can tell what rule they want to delete if needed. 4
5 / : / : / : / : / : / :0 0 1 The output should be in this format: <Rule#>-<SIP>/<SMask>:<SPort> <DIP>/<DMask>:<DPort> <Protocol> <Action> 4.6 Unblock User Have user enter number that corresponds to the IP address from the View Block List command, then unblock this user. This means you must keep track of which firewall rule belongs to which blocked user. If unblocking works, respond Unblocked User!, else respond Error! Unable to unblock user!, with appropriate error message. # Delete the second user 6 2 Unblocked user! # The user is not in the blocked list anymore Port Scan Buffer Overflow 5
6 # Now print the firewall rules, and see corresponding rule is gone / : / : / : / :0 0 1 # If you try to delete the third user, we would now get an error 6 3 Error! Unable to unblock user! There is no user Quit Stop all firewall and packet monitoring processes and exit gracefully. 5 Testing Along with your assignment, include a document test.txt that includes the resulting firewall rules, and output from ids.txt from running the following commands on your computer: # This tests for an OS fingerprinting attack hping2 localhost -SAF hping2 localhost -SA hping2 localhost -S hping2 localhost -SF hping2 localhost -AF # Tests for buffer overflow # nop.txt should be a text file containing "NOPNOPNOPNOPNOP" hping2 localhost -E nop.txt # Tests for port scan hping2 localhost -p
7 If done correctly, your test.txt file would look like the following: / : / : / : / : / : / : : OS Fingerprint : Buffer Overflow : Port Scan Please note that this example should work, even though the packets are getting blocked by the firewall, because pcap reads the packages straight from the device before the OS gets them. This isn t the most amazing example, but allows you to test your program without the need of another computer on the network. 6 Required Document (5%) In addition to your source code and your output you are required to submit a 1-3 page document that is flawlessly written. No spelling errors. No grammatical errors, etc. If the document is deemed unprofessional (e.g.; a significant number of grammatical or spelling errors it will be assigned a grade of zero.) Your document should state clearly the status of the assignment. Is it done or not? Does it meet all of the requirements. If anything is missing state clearly what is missing. Failure to give the status will result in a grade of zero for the entire assignment. Providing a that is false or significantly misleading will also result in a zero for the entire assignment. Make sure your document is well-written, succinct, and easy to ready. If you had problems with the assignment, give a detailed discussion of the problems and how you handled the problem. 7 Assignment Submission (5%) You are required to make both an electronic submission, and a paper submission. You may turn in your paper submission, before class on the due date, or in my mailbox before class time on the due date. For the paper submission, make sure to do the following: * Make sure your completeted handout is on top, with your name on it. * Next, attach all source code files printed out. * Also, submit a printed copy of the required document(see above). * Make sure they are all stapled together. Submit your electronic copy using Blackboard (attach the assignment as a compressed archive file(.zip,.tgz,.tbz2,.rar), make sure you do the following: 7
8 * The name of the compressed archive should have your name and project number(ie: Jordan Wilberding Project 2-2.zip) * Include the source code and a README file on how to run each program. * Include your status should come right at the beginning of the document. * Include your address in the Comment field when submitting the assignment through the Digital Drop Box. * If for any reason you are submitting the assignment more than once, indicate this in the Comment filed by including the word COMPLEMENT. * Include a shell script or batch file that will compile your programs when executed. Including a Makefile (see GNU Make for details) would be most appropriate but any form of script or building tool will do. * Include some form of executable that will run each individual program. If you are doing C/C++ for example, include the compiled executable, if you are using Java, or a fully interpreted language such as perl, include a shell script or batch file that will give the proper arguments and perform the execution. 8
CSC 4992 Cyber Security Practice
 CSC 4992 Cyber Security Practice Fengwei Zhang Wayne State University CSC 4992 Cyber Security Practice 1 Who Am I? Fengwei Zhang Assistant Professor of Computer Science Office: Maccabees Building, Room
CSC 4992 Cyber Security Practice Fengwei Zhang Wayne State University CSC 4992 Cyber Security Practice 1 Who Am I? Fengwei Zhang Assistant Professor of Computer Science Office: Maccabees Building, Room
CS395/495 Computer Security Project #2
 CS395/495 Computer Security Project #2 Important Dates Out: 1/19/2005 Due: 2/15/2005 11:59pm Winter 2005 Project Overview Intrusion Detection System (IDS) is a common tool to detect the malicious activity
CS395/495 Computer Security Project #2 Important Dates Out: 1/19/2005 Due: 2/15/2005 11:59pm Winter 2005 Project Overview Intrusion Detection System (IDS) is a common tool to detect the malicious activity
Actual4Test. Actual4test - actual test exam dumps-pass for IT exams
 Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : GCFW Title : GIAC Certified Firewall Analyst Vendors : GIAC Version : DEMO Get Latest & Valid GCFW Exam's
Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : GCFW Title : GIAC Certified Firewall Analyst Vendors : GIAC Version : DEMO Get Latest & Valid GCFW Exam's
ICSI 516 Fall 2018 Project 1 Due October 26th at 11:59PM via Blackboard
 ICSI 516 Fall 2018 Project 1 Due October 26th at 11:59PM via Blackboard Objectives: There are a number of objectives to this assignment. The first is to make sure you have some experience developing a
ICSI 516 Fall 2018 Project 1 Due October 26th at 11:59PM via Blackboard Objectives: There are a number of objectives to this assignment. The first is to make sure you have some experience developing a
COMP 412, Fall 2018 Lab 1: A Front End for ILOC
 COMP 412, Lab 1: A Front End for ILOC Due date: Submit to: Friday, September 7, 2018 at 11:59 PM comp412code@rice.edu Please report suspected typographical errors to the class Piazza site. We will issue
COMP 412, Lab 1: A Front End for ILOC Due date: Submit to: Friday, September 7, 2018 at 11:59 PM comp412code@rice.edu Please report suspected typographical errors to the class Piazza site. We will issue
Outline. What is TCP protocol? How the TCP Protocol Works SYN Flooding Attack TCP Reset Attack TCP Session Hijacking Attack
 Attacks on TCP Outline What is TCP protocol? How the TCP Protocol Works SYN Flooding Attack TCP Reset Attack TCP Session Hijacking Attack TCP Protocol Transmission Control Protocol (TCP) is a core protocol
Attacks on TCP Outline What is TCP protocol? How the TCP Protocol Works SYN Flooding Attack TCP Reset Attack TCP Session Hijacking Attack TCP Protocol Transmission Control Protocol (TCP) is a core protocol
CS155: Computer Security Spring Project #1
 CS155: Computer Security Spring 2018 Project #1 Due: Part 1: Thursday, April 12-11:59pm, Parts 2 and 3: Thursday, April 19-11:59pm. The goal of this assignment is to gain hands-on experience finding vulnerabilities
CS155: Computer Security Spring 2018 Project #1 Due: Part 1: Thursday, April 12-11:59pm, Parts 2 and 3: Thursday, April 19-11:59pm. The goal of this assignment is to gain hands-on experience finding vulnerabilities
Due: 9 February 2017 at 1159pm (2359, Pacific Standard Time)
 CSE 11 Winter 2017 Program Assignment #2 (100 points) START EARLY! Due: 9 February 2017 at 1159pm (2359, Pacific Standard Time) PROGRAM #2: DoubleArray11 READ THE ENTIRE ASSIGNMENT BEFORE STARTING In lecture,
CSE 11 Winter 2017 Program Assignment #2 (100 points) START EARLY! Due: 9 February 2017 at 1159pm (2359, Pacific Standard Time) PROGRAM #2: DoubleArray11 READ THE ENTIRE ASSIGNMENT BEFORE STARTING In lecture,
Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning
 Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning Last revised 10-4-17 KonBoot Get into any account without the password Works on Windows and Linux No longer free Link Ch 5r From the
Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning Last revised 10-4-17 KonBoot Get into any account without the password Works on Windows and Linux No longer free Link Ch 5r From the
Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning
 Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning Last revised 1-11-17 KonBoot Get into any account without the password Works on Windows and Linux No longer free Link Ch 5r From the
Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning Last revised 1-11-17 KonBoot Get into any account without the password Works on Windows and Linux No longer free Link Ch 5r From the
Lab 8: Introduction to Pen Testing (HPING)
 Lab 8: Introduction to Pen Testing (HPING) Aim: To provide a foundation in understanding of email with a focus on hping to provide security assessments and in understanding the trails of evidence produced.
Lab 8: Introduction to Pen Testing (HPING) Aim: To provide a foundation in understanding of email with a focus on hping to provide security assessments and in understanding the trails of evidence produced.
Nmap & Metasploit. Chun-Jen (James) Chung. Arizona State University
 Nmap & Metasploit Chun-Jen (James) Chung Nmap recap Nmap uses raw IP packets in novel ways to determine what hosts are available on the network What services (application name and version) those hosts
Nmap & Metasploit Chun-Jen (James) Chung Nmap recap Nmap uses raw IP packets in novel ways to determine what hosts are available on the network What services (application name and version) those hosts
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Fall CSEE W4119 Computer Networks Programming Assignment 1 - Simple Chat Application
 Fall 2011 - CSEE W4119 Computer Networks Programming Assignment 1 - Simple Chat Application Prof. Gil Zussman due: 10/26/2011, 11 AM, EST 1 Introduction This programming assignment is to implement a simple
Fall 2011 - CSEE W4119 Computer Networks Programming Assignment 1 - Simple Chat Application Prof. Gil Zussman due: 10/26/2011, 11 AM, EST 1 Introduction This programming assignment is to implement a simple
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
ITTC Communication Networks Laboratory The University of Kansas EECS 780 Introduction to Protocol Analysis with Wireshark
 Communication Networks Laboratory The University of Kansas EECS 780 Introduction to Protocol Analysis with Wireshark Trúc Anh N. Nguyễn, Egemen K. Çetinkaya, Mohammed Alenazi, and James P.G. Sterbenz Department
Communication Networks Laboratory The University of Kansas EECS 780 Introduction to Protocol Analysis with Wireshark Trúc Anh N. Nguyễn, Egemen K. Çetinkaya, Mohammed Alenazi, and James P.G. Sterbenz Department
Programming Standards: You must conform to good programming/documentation standards. Some specifics:
 CS3114 (Spring 2011) PROGRAMMING ASSIGNMENT #3 Due Thursday, April 7 @ 11:00 PM for 100 points Early bonus date: Wednesday, April 6 @ 11:00 PM for a 10 point bonus Initial Schedule due Thursday, March
CS3114 (Spring 2011) PROGRAMMING ASSIGNMENT #3 Due Thursday, April 7 @ 11:00 PM for 100 points Early bonus date: Wednesday, April 6 @ 11:00 PM for a 10 point bonus Initial Schedule due Thursday, March
FOCUS on Intrusion Detection: Intrusion Detection Level Analysis of Nmap and Queso Page 1 of 6
 FOCUS on Intrusion Detection: Intrusion Detection Level Analysis of Nmap and Queso Page 1 of 6 Intrusion Detection Level Analysis of Nmap and Queso by Toby Miller last updated Wednesday, August 30, 2000
FOCUS on Intrusion Detection: Intrusion Detection Level Analysis of Nmap and Queso Page 1 of 6 Intrusion Detection Level Analysis of Nmap and Queso by Toby Miller last updated Wednesday, August 30, 2000
Introduction to using Netcat
 Introduction to using Netcat Objectives To learn basic features of Netcat that using in security field. Introduction : Netcat is a wonderfully versatile tool which has been dubbed the hackers' Swiss army
Introduction to using Netcat Objectives To learn basic features of Netcat that using in security field. Introduction : Netcat is a wonderfully versatile tool which has been dubbed the hackers' Swiss army
Operating Systems. Project #2: System Calls
 Operating Systems Project #2: System Calls Project #2: System Calls Objective Background Getting Started Using BIOS Routines Printing to the Screen via the BIOS (Interrupt 0x10) Reading from the Keyboard
Operating Systems Project #2: System Calls Project #2: System Calls Objective Background Getting Started Using BIOS Routines Printing to the Screen via the BIOS (Interrupt 0x10) Reading from the Keyboard
ITEC 350: Introduction To Computer Networking Midterm Exam #2 Key. Fall 2008
 ITEC 350: Introduction To Computer Networking Midterm Exam #2 Key Closed book and closed notes. Fall 2008 No electronic devices allowed, e.g., calculator, laptop, PDA. Show your work. No work, no credit.
ITEC 350: Introduction To Computer Networking Midterm Exam #2 Key Closed book and closed notes. Fall 2008 No electronic devices allowed, e.g., calculator, laptop, PDA. Show your work. No work, no credit.
9. Security. Safeguard Engine. Safeguard Engine Settings
 9. Security Safeguard Engine Traffic Segmentation Settings Storm Control DoS Attack Prevention Settings Zone Defense Settings SSL Safeguard Engine D-Link s Safeguard Engine is a robust and innovative technology
9. Security Safeguard Engine Traffic Segmentation Settings Storm Control DoS Attack Prevention Settings Zone Defense Settings SSL Safeguard Engine D-Link s Safeguard Engine is a robust and innovative technology
Firewalls, Tunnels, and Network Intrusion Detection
 Firewalls, Tunnels, and Network Intrusion Detection 1 Intrusion Detection Systems Intrusion Actions aimed at compromising the security of the target (confidentiality, integrity, availability of computing/networking
Firewalls, Tunnels, and Network Intrusion Detection 1 Intrusion Detection Systems Intrusion Actions aimed at compromising the security of the target (confidentiality, integrity, availability of computing/networking
CS 450 Introduction to Networking Spring 2014 Homework Assignment 1 File Transfer and Data Bandwidth Analysis Tool
 CS 450 Introduction to Networking Spring 2014 Homework Assignment 1 File Transfer and Data Bandwidth Analysis Tool Due: Monday 17 February. Electronic copy due at 10:30 A.M., Optional paper copy may be
CS 450 Introduction to Networking Spring 2014 Homework Assignment 1 File Transfer and Data Bandwidth Analysis Tool Due: Monday 17 February. Electronic copy due at 10:30 A.M., Optional paper copy may be
A Distributed Intrusion Alert System
 A Distributed Intrusion Alert System Chih-Yao Lin, Hsiang-Ren Shih, and Yomin Hou Taiwan National Computer Emergency Response Team {chinyao, shr, yominhou}@twncert.org.tw Abstract In this paper, a distributed
A Distributed Intrusion Alert System Chih-Yao Lin, Hsiang-Ren Shih, and Yomin Hou Taiwan National Computer Emergency Response Team {chinyao, shr, yominhou}@twncert.org.tw Abstract In this paper, a distributed
Unicornscan Documentation Getting Started
 Getting Started Presented to End Users Important Notice: This documentation is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY
Getting Started Presented to End Users Important Notice: This documentation is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY
What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1
 What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1 PB478675 Product Overview The Cisco ACE Application Control Engine 4710 represents the next generation of application switches
What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1 PB478675 Product Overview The Cisco ACE Application Control Engine 4710 represents the next generation of application switches
Distributed Systems. 29. Firewalls. Paul Krzyzanowski. Rutgers University. Fall 2015
 Distributed Systems 29. Firewalls Paul Krzyzanowski Rutgers University Fall 2015 2013-2015 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive data & systems not accessible Integrity:
Distributed Systems 29. Firewalls Paul Krzyzanowski Rutgers University Fall 2015 2013-2015 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive data & systems not accessible Integrity:
Detecting Specific Threats
 The following topics explain how to use preprocessors in a network analysis policy to detect specific threats: Introduction to Specific Threat Detection, page 1 Back Orifice Detection, page 1 Portscan
The following topics explain how to use preprocessors in a network analysis policy to detect specific threats: Introduction to Specific Threat Detection, page 1 Back Orifice Detection, page 1 Portscan
3. When you process a largest recent earthquake query, you should print out:
 CS3114 (Fall 2013) PROGRAMMING ASSIGNMENT #1 Due Wednesday, September 18 @ 11:00 PM for 100 points Due Tuesday, September 17 @ 11:00 PM for 10 point bonus Updated: 9/11/2013 Assignment: This is the first
CS3114 (Fall 2013) PROGRAMMING ASSIGNMENT #1 Due Wednesday, September 18 @ 11:00 PM for 100 points Due Tuesday, September 17 @ 11:00 PM for 10 point bonus Updated: 9/11/2013 Assignment: This is the first
BSc Computing CSY2026 Modern Networks. Module Tutor: Signed:
 Division of Computing BSc Computing CSY2026 Modern Networks Date of Issue: 17/02/2017 Date for Submission: 28/04 2017 (23:59 by e-submission) Agreed Date for late submission: Student Name: Student ID:
Division of Computing BSc Computing CSY2026 Modern Networks Date of Issue: 17/02/2017 Date for Submission: 28/04 2017 (23:59 by e-submission) Agreed Date for late submission: Student Name: Student ID:
Buffer Overflow Defenses
 Buffer Overflow Defenses Some examples, pros, and cons of various defenses against buffer overflows. Caveats: 1. Not intended to be a complete list of products that defend against buffer overflows. 2.
Buffer Overflow Defenses Some examples, pros, and cons of various defenses against buffer overflows. Caveats: 1. Not intended to be a complete list of products that defend against buffer overflows. 2.
Lab 1: Silver Dollar Game 1 CSCI 2101B Fall 2018
 Lab 1: Silver Dollar Game 1 CSCI 2101B Fall 2018 Due: Tuesday, September 18, 11:59 pm Collaboration Policy: Level 1 (review full policy for details) Group Policy: Individual This lab will give you experience
Lab 1: Silver Dollar Game 1 CSCI 2101B Fall 2018 Due: Tuesday, September 18, 11:59 pm Collaboration Policy: Level 1 (review full policy for details) Group Policy: Individual This lab will give you experience
Fall CSEE W4119 Computer Networks Programming Assignment 1 - Simple Online Bidding System
 Fall 2012 - CSEE W4119 Computer Networks Programming Assignment 1 - Simple Online Bidding System Prof. Gil Zussman due: Wed. 10/24/2012, 23:55 EST 1 Introduction In this programming assignment, you are
Fall 2012 - CSEE W4119 Computer Networks Programming Assignment 1 - Simple Online Bidding System Prof. Gil Zussman due: Wed. 10/24/2012, 23:55 EST 1 Introduction In this programming assignment, you are
INF5290 Ethical Hacking. Lecture 3: Network reconnaissance, port scanning. Universitetet i Oslo Laszlo Erdödi
 INF5290 Ethical Hacking Lecture 3: Network reconnaissance, port scanning Universitetet i Oslo Laszlo Erdödi Lecture Overview Identifying hosts in a network Identifying services on a host What are the typical
INF5290 Ethical Hacking Lecture 3: Network reconnaissance, port scanning Universitetet i Oslo Laszlo Erdödi Lecture Overview Identifying hosts in a network Identifying services on a host What are the typical
Web-CAT Guidelines. 1. Logging into Web-CAT
 Contents: 1. Logging into Web-CAT 2. Submitting Projects via jgrasp a. Configuring Web-CAT b. Submitting Individual Files (Example: Activity 1) c. Submitting a Project to Web-CAT d. Submitting in Web-CAT
Contents: 1. Logging into Web-CAT 2. Submitting Projects via jgrasp a. Configuring Web-CAT b. Submitting Individual Files (Example: Activity 1) c. Submitting a Project to Web-CAT d. Submitting in Web-CAT
P2P Programming Assignment
 P2P Programming Assignment Overview This project is to implement a Peer-to-Peer (P2P) networking project similar to a simplified Napster. You will provide a centralized server to handle cataloging the
P2P Programming Assignment Overview This project is to implement a Peer-to-Peer (P2P) networking project similar to a simplified Napster. You will provide a centralized server to handle cataloging the
Creating a Shell or Command Interperter Program CSCI411 Lab
 Creating a Shell or Command Interperter Program CSCI411 Lab Adapted from Linux Kernel Projects by Gary Nutt and Operating Systems by Tannenbaum Exercise Goal: You will learn how to write a LINUX shell
Creating a Shell or Command Interperter Program CSCI411 Lab Adapted from Linux Kernel Projects by Gary Nutt and Operating Systems by Tannenbaum Exercise Goal: You will learn how to write a LINUX shell
CS 356 Operating System Security. Fall 2013
 CS 356 Operating System Security Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5 Database
CS 356 Operating System Security Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5 Database
Programming Assignments
 ELEC 486/586, Summer 2017 1 Programming Assignments 1 General Information 1.1 Software Requirements Detailed specifications are typically provided for the software to be developed for each assignment problem.
ELEC 486/586, Summer 2017 1 Programming Assignments 1 General Information 1.1 Software Requirements Detailed specifications are typically provided for the software to be developed for each assignment problem.
Application Inspection and Control for SMTP
 Application Inspection and Control for SMTP First Published: July 11, 2008 Last Updated: July 11, 2008 The Application Inspection for SMTP feature provides an intense provisioning mechanism that can be
Application Inspection and Control for SMTP First Published: July 11, 2008 Last Updated: July 11, 2008 The Application Inspection for SMTP feature provides an intense provisioning mechanism that can be
New York University Computer Science Department Courant Institute of Mathematical Sciences
 New York University Computer Science Department Courant Institute of Mathematical Sciences Course Title: Data Communication & Networks Course Number: g22.2662-001 Instructor: Jean-Claude Franchitti Session:
New York University Computer Science Department Courant Institute of Mathematical Sciences Course Title: Data Communication & Networks Course Number: g22.2662-001 Instructor: Jean-Claude Franchitti Session:
The Swiss Army Knife netcat
 The Swiss Army Knife netcat Lab Objectives In this lab, you will perform the following six labs: Lab 1 Use Netcat for Port Scanning Lab 2 Use Netcat for Banner Grabbing Lab 3 Use Netcat to Transfer Files
The Swiss Army Knife netcat Lab Objectives In this lab, you will perform the following six labs: Lab 1 Use Netcat for Port Scanning Lab 2 Use Netcat for Banner Grabbing Lab 3 Use Netcat to Transfer Files
Programming Assignment 3
 UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 3550 Section 002 Communication Networks Spring 2018 Programming Assignment 3 Introduction Having created a TCP client in programming assignment 2, it s
UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 3550 Section 002 Communication Networks Spring 2018 Programming Assignment 3 Introduction Having created a TCP client in programming assignment 2, it s
CSC 5991 Cyber Security Prac1ce
 CSC 5991 Cyber Security Prac1ce Fengwei Zhang Wayne State University CSC 5991 Cyber Security Prac1ce 1 Who Am I? Fengwei Zhang Assistant Professor of Computer Science Office: Maccabees Building, Room 14109.3
CSC 5991 Cyber Security Prac1ce Fengwei Zhang Wayne State University CSC 5991 Cyber Security Prac1ce 1 Who Am I? Fengwei Zhang Assistant Professor of Computer Science Office: Maccabees Building, Room 14109.3
Assignment 6: The Power of Caches
 Assignment 6: The Power of Caches Due by: April 20, 2018 before 10:00 pm Collaboration: Individuals or Registered Pairs (see Piazza). It is mandatory for every student to register on Piazza. Grading: Packaging
Assignment 6: The Power of Caches Due by: April 20, 2018 before 10:00 pm Collaboration: Individuals or Registered Pairs (see Piazza). It is mandatory for every student to register on Piazza. Grading: Packaging
User Datagram Protocol
 Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
CS 202, Fall 2017 Homework #4 Balanced Search Trees and Hashing Due Date: December 18, 2017
 CS 202, Fall 2017 Homework #4 Balanced Search Trees and Hashing Due Date: December 18, 2017 Important Notes Please do not start the assignment before reading these notes. Before 23:55, December 18, upload
CS 202, Fall 2017 Homework #4 Balanced Search Trees and Hashing Due Date: December 18, 2017 Important Notes Please do not start the assignment before reading these notes. Before 23:55, December 18, upload
Exam4Tests. Latest exam questions & answers help you to pass IT exam test easily
 Exam4Tests http://www.exam4tests.com Latest exam questions & answers help you to pass IT exam test easily Exam : CEH-001 Title : Certified Ethical Hacker (CEH) Vendor : GAQM Version : DEMO 1 / 9 Get Latest
Exam4Tests http://www.exam4tests.com Latest exam questions & answers help you to pass IT exam test easily Exam : CEH-001 Title : Certified Ethical Hacker (CEH) Vendor : GAQM Version : DEMO 1 / 9 Get Latest
Scanning. Course Learning Outcomes for Unit III. Reading Assignment. Unit Lesson UNIT III STUDY GUIDE
 UNIT III STUDY GUIDE Course Learning Outcomes for Unit III Upon completion of this unit, students should be able to: 1. Recall the terms port scanning, network scanning, and vulnerability scanning. 2.
UNIT III STUDY GUIDE Course Learning Outcomes for Unit III Upon completion of this unit, students should be able to: 1. Recall the terms port scanning, network scanning, and vulnerability scanning. 2.
REVE EPS- Product Guide (Ver )
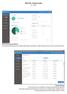 REVE EPS- Product Guide (Ver. 3.0.0.6) REVE EPS Console Dashboard: The console dashboard gives the details about status of endpoints, signature date, activity summary and license status. Network Devices:
REVE EPS- Product Guide (Ver. 3.0.0.6) REVE EPS Console Dashboard: The console dashboard gives the details about status of endpoints, signature date, activity summary and license status. Network Devices:
Means for Intrusion Detection. Intrusion Detection. INFO404 - Lecture 13. Content
 Intrusion Detection INFO404 - Lecture 13 21.04.2009 nfoukia@infoscience.otago.ac.nz Content Definition Network vs. Host IDS Misuse vs. Behavior Based IDS Means for Intrusion Detection Definitions (1) Intrusion:
Intrusion Detection INFO404 - Lecture 13 21.04.2009 nfoukia@infoscience.otago.ac.nz Content Definition Network vs. Host IDS Misuse vs. Behavior Based IDS Means for Intrusion Detection Definitions (1) Intrusion:
File Upload Instructions Customer Access To Transcript Bulletin Publishing s FTP Site
 File Upload Instructions Customer Access To Transcript Bulletin Publishing s FTP Site In order to upload files to our FTP site, you will need a Java-enabled web browser for Microsoft Windows and Mac OS
File Upload Instructions Customer Access To Transcript Bulletin Publishing s FTP Site In order to upload files to our FTP site, you will need a Java-enabled web browser for Microsoft Windows and Mac OS
2.1 A Primer on Network Sniffing Reconstructing TCP Streams Reconstructing Fragmented Packets 14
 Index 1 Executive Summary 4 1 Introduction 6 2 NIDS Concepts 8 2.1 A Primer on Network Sniffing 9 2.2 NIDS Placement 11 2.3 Logging 12 2.4 Reconstructing TCP Streams 13 2.5 Reconstructing Fragmented Packets
Index 1 Executive Summary 4 1 Introduction 6 2 NIDS Concepts 8 2.1 A Primer on Network Sniffing 9 2.2 NIDS Placement 11 2.3 Logging 12 2.4 Reconstructing TCP Streams 13 2.5 Reconstructing Fragmented Packets
ECE2049: Embedded Systems in Engineering Design Lab Exercise #3 C Term Making a Time and Temperature Display
 ECE2049: Embedded Systems in Engineering Design Lab Exercise #3 C Term 2019 Making a Time and Temperature Display In this laboratory you will use the MSP430 and several of its peripherals to implement
ECE2049: Embedded Systems in Engineering Design Lab Exercise #3 C Term 2019 Making a Time and Temperature Display In this laboratory you will use the MSP430 and several of its peripherals to implement
Wireshark Lab: Getting Started v7.0
 Wireshark Lab: Getting Started v7.0 Adapted by HMC from the supplement to Computer Networking: A Top-Down Approach, 7 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve
Wireshark Lab: Getting Started v7.0 Adapted by HMC from the supplement to Computer Networking: A Top-Down Approach, 7 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve
Port Scanning A Brief Introduction
 Port Scanning A Brief Introduction Sven Helmer April 4, 2018 Contents 1 Background 2 1.1 Ports.................................... 2 1.2 Port Scanning............................... 2 1.3 Port Scanning
Port Scanning A Brief Introduction Sven Helmer April 4, 2018 Contents 1 Background 2 1.1 Ports.................................... 2 1.2 Port Scanning............................... 2 1.3 Port Scanning
Reliable File Transfer
 Due date Wednesday, Mar 14, 11:59pm Reliable File Transfer CS 5565 Spring 2012, Project 2 This project is worth 100 points. You may form teams of up to two students for this project. You are not required
Due date Wednesday, Mar 14, 11:59pm Reliable File Transfer CS 5565 Spring 2012, Project 2 This project is worth 100 points. You may form teams of up to two students for this project. You are not required
GMU SWE 443 Software Architecture Spring Lab 2: Implicit-invocation System. Sousa Discuss Feb 23, due March 8
 GMU SWE 443 Software Architecture Spring 2012 Lab 2: Implicit-invocation System Sousa Discuss Feb 23, due March 8 This lab is to be done individually. If there is something you don t understand, or if
GMU SWE 443 Software Architecture Spring 2012 Lab 2: Implicit-invocation System Sousa Discuss Feb 23, due March 8 This lab is to be done individually. If there is something you don t understand, or if
CS3114 (Fall 2013) PROGRAMMING ASSIGNMENT #2 Due Tuesday, October 11:00 PM for 100 points Due Monday, October 11:00 PM for 10 point bonus
 CS3114 (Fall 2013) PROGRAMMING ASSIGNMENT #2 Due Tuesday, October 15 @ 11:00 PM for 100 points Due Monday, October 14 @ 11:00 PM for 10 point bonus Updated: 10/10/2013 Assignment: This project continues
CS3114 (Fall 2013) PROGRAMMING ASSIGNMENT #2 Due Tuesday, October 15 @ 11:00 PM for 100 points Due Monday, October 14 @ 11:00 PM for 10 point bonus Updated: 10/10/2013 Assignment: This project continues
CS337 Project 1 : Compression
 CS337 Project 1 : Compression TA: Yan Li (yanli@cs.utexas.edu) Due Date: Sept. 29, 2008 11:59PM 1 Part 1: Lower Bound of Lossless Compression 1.1 Description Given a text file, which contains only ASCII
CS337 Project 1 : Compression TA: Yan Li (yanli@cs.utexas.edu) Due Date: Sept. 29, 2008 11:59PM 1 Part 1: Lower Bound of Lossless Compression 1.1 Description Given a text file, which contains only ASCII
How to Configure IPS Policies
 IPS policies control the behavior of the IPS when an attack is detected. You can define multiple IPS policies and apply them to individual firewall rules as needed. In this article: Default IPS Policy
IPS policies control the behavior of the IPS when an attack is detected. You can define multiple IPS policies and apply them to individual firewall rules as needed. In this article: Default IPS Policy
Lab 3. A Multi-Message Reader
 Lab 3 A Multi-Message Email Reader Due: Wed. 2/21 at 11PM (for Mon. aft. lab), Thurs. 2/22 at 5PM (for Mon. evening), or Thurs. 2/22 at 11 (for Tues. aft.) The goal in this week s lab is to exercise your
Lab 3 A Multi-Message Email Reader Due: Wed. 2/21 at 11PM (for Mon. aft. lab), Thurs. 2/22 at 5PM (for Mon. evening), or Thurs. 2/22 at 11 (for Tues. aft.) The goal in this week s lab is to exercise your
Intrusion Detection. October 19, 2018
 Intrusion Detection October 19, 2018 Administrative submittal instructions answer the lab assignment s questions in written report form, as a text, pdf, or Word document file (no obscure formats please)
Intrusion Detection October 19, 2018 Administrative submittal instructions answer the lab assignment s questions in written report form, as a text, pdf, or Word document file (no obscure formats please)
Introduction to using Netcat
 Introduction to using Netcat Objectives To learn basic features of Netcat that using in security field. Introduction Netcat is a computer networking service for reading from and writing network connections
Introduction to using Netcat Objectives To learn basic features of Netcat that using in security field. Introduction Netcat is a computer networking service for reading from and writing network connections
CS 455 / Computer Networks Fall Using an Echo Application to Measure TCP Performance Due: THURSDAY, October 2, 2014 (1pm)
 CS 455 / 655 - Computer Networks Fall 2014 Using an Echo Application to Measure TCP Performance Due: THURSDAY, October 2, 2014 (1pm) [See posted grading criteria.] To be completed individually. In this
CS 455 / 655 - Computer Networks Fall 2014 Using an Echo Application to Measure TCP Performance Due: THURSDAY, October 2, 2014 (1pm) [See posted grading criteria.] To be completed individually. In this
Packet Analysis - Wireshark
 Packet Analysis - Wireshark Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea Why do we need to capture packet & how is it relevant to security? tcpdump tcpdump is a utility used
Packet Analysis - Wireshark Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea Why do we need to capture packet & how is it relevant to security? tcpdump tcpdump is a utility used
FACULTY GUIDE TO USING VOICETHREAD IN BLACKBOARD
 What is VoiceThread? VoiceThread is an interactive collaboration and sharing tool that enables users to add images, documents, and videos, and to which other users can add voice, text, audio file, or video
What is VoiceThread? VoiceThread is an interactive collaboration and sharing tool that enables users to add images, documents, and videos, and to which other users can add voice, text, audio file, or video
Peer to Peer Instant Messaging
 Peer to Peer Instant Messaging Assignment in Computer Networks I, Department of Information Technology, Uppsala University. Overview In this assignment you will implement an instant messaging system that
Peer to Peer Instant Messaging Assignment in Computer Networks I, Department of Information Technology, Uppsala University. Overview In this assignment you will implement an instant messaging system that
Preliminary steps before starting the experiment: 1) Click the Launch button to start the experiment. 2) Click OK to create a new session
 Preliminary steps before starting the experiment: 1) Click the Launch button to start the experiment. 2) Click OK to create a new session 3) Click the Screen Sharing option and click connect to establish
Preliminary steps before starting the experiment: 1) Click the Launch button to start the experiment. 2) Click OK to create a new session 3) Click the Screen Sharing option and click connect to establish
University of Maryland Baltimore County Department of Information Systems Spring 2015
 University of Maryland Baltimore County Department of Information Systems Spring 2015 IS 450/650: Data Communications and Networks Homework Assignment 1 Wireshark Lab (Handed Out: February 3, 2015 (Tuesday),
University of Maryland Baltimore County Department of Information Systems Spring 2015 IS 450/650: Data Communications and Networks Homework Assignment 1 Wireshark Lab (Handed Out: February 3, 2015 (Tuesday),
Project Proposal. ECE 526 Spring Modified Data Structure of Aho-Corasick. Benfano Soewito, Ed Flanigan and John Pangrazio
 Project Proposal ECE 526 Spring 2006 Modified Data Structure of Aho-Corasick Benfano Soewito, Ed Flanigan and John Pangrazio 1. Introduction The internet becomes the most important tool in this decade
Project Proposal ECE 526 Spring 2006 Modified Data Structure of Aho-Corasick Benfano Soewito, Ed Flanigan and John Pangrazio 1. Introduction The internet becomes the most important tool in this decade
Circular Linked List Assignment
 Page 1 of 6 Circular Linked List Assignment Overview A circular linked list is essentially a singly linked list in which the next pointer of the tail node is set to point to the head node of the linked
Page 1 of 6 Circular Linked List Assignment Overview A circular linked list is essentially a singly linked list in which the next pointer of the tail node is set to point to the head node of the linked
Lecture 33. Firewalls. Firewall Locations in the Network. Castle and Moat Analogy. Firewall Types. Firewall: Illustration. Security April 15, 2005
 Firewalls Lecture 33 Security April 15, 2005 Idea: separate local network from the Internet Trusted hosts and networks Intranet Firewall DMZ Router Demilitarized Zone: publicly accessible servers and networks
Firewalls Lecture 33 Security April 15, 2005 Idea: separate local network from the Internet Trusted hosts and networks Intranet Firewall DMZ Router Demilitarized Zone: publicly accessible servers and networks
Network Security. Thierry Sans
 Network Security Thierry Sans HTTP SMTP DNS BGP The Protocol Stack Application TCP UDP Transport IPv4 IPv6 ICMP Network ARP Link Ethernet WiFi The attacker is capable of confidentiality integrity availability
Network Security Thierry Sans HTTP SMTP DNS BGP The Protocol Stack Application TCP UDP Transport IPv4 IPv6 ICMP Network ARP Link Ethernet WiFi The attacker is capable of confidentiality integrity availability
CSCD433/533 Advanced Networks Winter 2017 Lecture 13. Raw vs. Cooked Sockets
 CSCD433/533 Advanced Networks Winter 2017 Lecture 13 Raw vs. Cooked Sockets Introduction Better Understand the Protocol Stack Use Raw Sockets So far, sockets in Java either TCP or UDP based In fact, Java
CSCD433/533 Advanced Networks Winter 2017 Lecture 13 Raw vs. Cooked Sockets Introduction Better Understand the Protocol Stack Use Raw Sockets So far, sockets in Java either TCP or UDP based In fact, Java
CSc 450/550: Computer Communications and Networks (Summer 2007)
 1 2 3 4 5 6 CSc 450/550: Computer Communications and Networks (Summer 2007) Lab Project 3: A Simple Network Traffic Analyzer Spec Out: July 6, 2007 Demo Due: July 25, 2007 Code Due: July 27, 2007 7 8 9
1 2 3 4 5 6 CSc 450/550: Computer Communications and Networks (Summer 2007) Lab Project 3: A Simple Network Traffic Analyzer Spec Out: July 6, 2007 Demo Due: July 25, 2007 Code Due: July 27, 2007 7 8 9
A quick theorical introduction to network scanning. 23rd November 2005
 A quick theorical introduction to network ASBL CSRRT-LU (Computer Security Research and Response Team Luxembourg) http://www.csrrt.org/ 23rd November 2005 IP protocol ACK Network is not exact science When
A quick theorical introduction to network ASBL CSRRT-LU (Computer Security Research and Response Team Luxembourg) http://www.csrrt.org/ 23rd November 2005 IP protocol ACK Network is not exact science When
UP L13: Leveraging the full protection of SEP 12.1.x
 UP L13: Leveraging the full protection of SEP 12.1.x Hands on lab Description In this hands on lab you will learn about the different protection technologies bundled in SEP 12.1.x and see how they complement
UP L13: Leveraging the full protection of SEP 12.1.x Hands on lab Description In this hands on lab you will learn about the different protection technologies bundled in SEP 12.1.x and see how they complement
New York University Computer Science Department Courant Institute of Mathematical Sciences
 New York University Computer Science Department Courant Institute of Mathematical Sciences Course Title: Data Communications & Networks Course Number: CSCI-GA.2662-001 Instructor: Jean-Claude Franchitti
New York University Computer Science Department Courant Institute of Mathematical Sciences Course Title: Data Communications & Networks Course Number: CSCI-GA.2662-001 Instructor: Jean-Claude Franchitti
9th Slide Set Computer Networks
 Prof. Dr. Christian Baun 9th Slide Set Computer Networks Frankfurt University of Applied Sciences WS1718 1/49 9th Slide Set Computer Networks Prof. Dr. Christian Baun Frankfurt University of Applied Sciences
Prof. Dr. Christian Baun 9th Slide Set Computer Networks Frankfurt University of Applied Sciences WS1718 1/49 9th Slide Set Computer Networks Prof. Dr. Christian Baun Frankfurt University of Applied Sciences
CS Fundamentals of Programming II Fall Very Basic UNIX
 CS 215 - Fundamentals of Programming II Fall 2012 - Very Basic UNIX This handout very briefly describes how to use Unix and how to use the Linux server and client machines in the CS (Project) Lab (KC-265)
CS 215 - Fundamentals of Programming II Fall 2012 - Very Basic UNIX This handout very briefly describes how to use Unix and how to use the Linux server and client machines in the CS (Project) Lab (KC-265)
Anomaly Detection in Communication Networks
 Anomaly Detection in Communication Networks Prof. D. J. Parish High Speed networks Group Department of Electronic and Electrical Engineering D.J.Parish@lboro.ac.uk Loughborough University Overview u u
Anomaly Detection in Communication Networks Prof. D. J. Parish High Speed networks Group Department of Electronic and Electrical Engineering D.J.Parish@lboro.ac.uk Loughborough University Overview u u
Some of the slides borrowed from the book Computer Security: A Hands on Approach by Wenliang Du. TCP Attacks. Chester Rebeiro IIT Madras
 Some of the slides borrowed from the book Computer Security: A Hands on Approach by Wenliang Du TCP Attacks Chester Rebeiro IIT Madras A Typical TCP Client 2 A Typical TCP Server create a IPV4 stream socket
Some of the slides borrowed from the book Computer Security: A Hands on Approach by Wenliang Du TCP Attacks Chester Rebeiro IIT Madras A Typical TCP Client 2 A Typical TCP Server create a IPV4 stream socket
Cisco IOS Firewall Intrusion Detection System Commands
 Cisco IOS Firewall Intrusion Detection System Commands This chapter describes the commands used to configure the integrated Intrusion Detection System (IDS) features in Cisco IOS Firewall. Intrusion detection
Cisco IOS Firewall Intrusion Detection System Commands This chapter describes the commands used to configure the integrated Intrusion Detection System (IDS) features in Cisco IOS Firewall. Intrusion detection
Lab 3: Simple Firewall using OpenFlow
 Lab 3: Simple Firewall using OpenFlow This lab builds on the knowledge acquired through Lab 1 where you were first introduced to the Mininet environment. It will also help you prepare for the class project.
Lab 3: Simple Firewall using OpenFlow This lab builds on the knowledge acquired through Lab 1 where you were first introduced to the Mininet environment. It will also help you prepare for the class project.
Last lecture we talked about how Intrusion Detection works. Today we will talk about the attacks. Intrusion Detection. Shell code
 4/25/2006 Lecture Notes: DOS Beili Wang Last lecture we talked about how Intrusion Detection works. Today we will talk about the attacks. Intrusion Detection Aps Monitor OS Internet Shell code Model In
4/25/2006 Lecture Notes: DOS Beili Wang Last lecture we talked about how Intrusion Detection works. Today we will talk about the attacks. Intrusion Detection Aps Monitor OS Internet Shell code Model In
Intrusion Detection Systems (IDS)
 Intrusion Detection Systems (IDS) Presented by Erland Jonsson Department of Computer Science and Engineering Contents Motivation and basics (Why and what?) IDS types and detection principles Key Data Problems
Intrusion Detection Systems (IDS) Presented by Erland Jonsson Department of Computer Science and Engineering Contents Motivation and basics (Why and what?) IDS types and detection principles Key Data Problems
ECCouncil Exam v9 Certified Ethical Hacker Exam V9 Version: 7.0 [ Total Questions: 125 ]
![ECCouncil Exam v9 Certified Ethical Hacker Exam V9 Version: 7.0 [ Total Questions: 125 ] ECCouncil Exam v9 Certified Ethical Hacker Exam V9 Version: 7.0 [ Total Questions: 125 ]](/thumbs/78/77837973.jpg) s@lm@n ECCouncil Exam 312-50v9 Certified Ethical Hacker Exam V9 Version: 7.0 [ Total Questions: 125 ] Question No : 1 An Intrusion Detection System(IDS) has alerted the network administrator to a possibly
s@lm@n ECCouncil Exam 312-50v9 Certified Ethical Hacker Exam V9 Version: 7.0 [ Total Questions: 125 ] Question No : 1 An Intrusion Detection System(IDS) has alerted the network administrator to a possibly
CSCI 201 Lab 1 Environment Setup
 CSCI 201 Lab 1 Environment Setup "The journey of a thousand miles begins with one step." - Lao Tzu Introduction This lab document will go over the steps to install and set up Eclipse, which is a Java integrated
CSCI 201 Lab 1 Environment Setup "The journey of a thousand miles begins with one step." - Lao Tzu Introduction This lab document will go over the steps to install and set up Eclipse, which is a Java integrated
DO NOT OPEN UNTIL INSTRUCTED
 CS 378 - Network Security and Privacy Spring 2017 FINAL May 3, 2017 DO NOT OPEN UNTIL INSTRUCTED YOUR NAME: Collaboration policy No collaboration is permitted on this exam. Any cheating (e.g., submitting
CS 378 - Network Security and Privacy Spring 2017 FINAL May 3, 2017 DO NOT OPEN UNTIL INSTRUCTED YOUR NAME: Collaboration policy No collaboration is permitted on this exam. Any cheating (e.g., submitting
Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development
 Weekly Tasks Week 5 Rich Macfarlane 2013 Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development Aim: The aim of these labs are to further investigate the Snort, network IDS, and methods
Weekly Tasks Week 5 Rich Macfarlane 2013 Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development Aim: The aim of these labs are to further investigate the Snort, network IDS, and methods
Instruction: Download and Install R and RStudio
 1 Instruction: Download and Install R and RStudio We will use a free statistical package R, and a free version of RStudio. Please refer to the following two steps to download both R and RStudio on your
1 Instruction: Download and Install R and RStudio We will use a free statistical package R, and a free version of RStudio. Please refer to the following two steps to download both R and RStudio on your
CS 351 Design of Large Programs Java and Socket Communication
 CS 351 Design of Large Programs Java and Socket Communication Instructor: Joel Castellanos e-mail: joel@unm.edu 4/6/2017 Transmission Control Protocol The Transmission Control Protocol (TCP) is one of
CS 351 Design of Large Programs Java and Socket Communication Instructor: Joel Castellanos e-mail: joel@unm.edu 4/6/2017 Transmission Control Protocol The Transmission Control Protocol (TCP) is one of
Network Security. Kitisak Jirawannakool Electronics Government Agency (public organisation)
 1 Network Security Kitisak Jirawannakool Electronics Government Agency (public organisation) A Brief History of the World 2 OSI Model vs TCP/IP suite 3 TFTP & SMTP 4 ICMP 5 NAT/PAT 6 ARP/RARP 7 DHCP 8
1 Network Security Kitisak Jirawannakool Electronics Government Agency (public organisation) A Brief History of the World 2 OSI Model vs TCP/IP suite 3 TFTP & SMTP 4 ICMP 5 NAT/PAT 6 ARP/RARP 7 DHCP 8
ECE2049 Embedded Computing in Engineering Design. Lab #0 Introduction to the MSP430F5529 Launchpad-based Lab Board and Code Composer Studio
 ECE2049 Embedded Computing in Engineering Design Lab #0 Introduction to the MSP430F5529 Launchpad-based Lab Board and Code Composer Studio In this lab you will be introduced to the Code Composer Studio
ECE2049 Embedded Computing in Engineering Design Lab #0 Introduction to the MSP430F5529 Launchpad-based Lab Board and Code Composer Studio In this lab you will be introduced to the Code Composer Studio
CS 118 Project Phase 2 P2P Networking
 CS 118 Project Phase 2 P2P Networking Due Monday, March 15 th at 11:59pm Boelter Hall 4428, Box D3/C4 and via Electronic Submission Overview In this phase you will extend your work from Phase 1 to create
CS 118 Project Phase 2 P2P Networking Due Monday, March 15 th at 11:59pm Boelter Hall 4428, Box D3/C4 and via Electronic Submission Overview In this phase you will extend your work from Phase 1 to create
Corrigendum 3. Tender Number: 10/ dated
 (A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
(A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
Distributed Systems Project 4 Assigned: Friday March 20 Due: Friday April 3, 11:59pm
 95-702 Distributed Systems Project 4 Assigned: Friday March 20 Due: Friday April 3, 11:59pm Project Topics: Java RMI and a distributed, Mobile to Cloud application This project has 2 tasks. Task 1 is a
95-702 Distributed Systems Project 4 Assigned: Friday March 20 Due: Friday April 3, 11:59pm Project Topics: Java RMI and a distributed, Mobile to Cloud application This project has 2 tasks. Task 1 is a
New York University Computer Science Department Courant Institute of Mathematical Sciences
 New York University Computer Science Department Courant Institute of Mathematical Sciences Course Title: Data Communications & Networks Course Number: g22.2662-001 Instructor: Jean-Claude Franchitti Session:
New York University Computer Science Department Courant Institute of Mathematical Sciences Course Title: Data Communications & Networks Course Number: g22.2662-001 Instructor: Jean-Claude Franchitti Session:
