Unified Access Control
|
|
|
- Helena Pearson
- 6 years ago
- Views:
Transcription
1 Unified Access Control UAC Interoperability with the ScreenOS Enforcer Release Published: Part Number:, Revision 1
2 Juniper Networks, Inc North Mathilda Avenue Sunnyvale, California USA This product includes the Envoy SNMP Engine, developed by Epilogue Technology, an Integrated Systems Company. Copyright , Epilogue Technology Corporation. All rights reserved. This program and its documentation were developed at private expense, and no part of them is in the public domain. This product includes memory allocation software developed by Mark Moraes, copyright 1988, 1989, 1993, University of Toronto. This product includes FreeBSD software developed by the University of California, Berkeley, and its contributors. All of the documentation and software included in the 4.4BSD and 4.4BSD-Lite Releases is copyrighted by the Regents of the University of California. Copyright 1979, 1980, 1983, 1986, 1988, 1989, 1991, 1992, 1993, The Regents of the University of California. All rights reserved. GateD software copyright 1995, the Regents of the University. All rights reserved. Gate Daemon was originated and developed through release 3.0 by Cornell University and its collaborators. Gated is based on Kirton s EGP, UC Berkeley s routing daemon (routed), and DCN s HELLO routing protocol. Development of Gated has been supported in part by the National Science Foundation. Portions of the GateD software copyright 1988, Regents of the University of California. All rights reserved. Portions of the GateD software copyright 1991, D. L. S. Associates. This product includes software developed by Maker Communications, Inc., copyright 1996, 1997, Maker Communications, Inc. Juniper Networks, Junos, Steel-Belted Radius, NetScreen, and ScreenOS are registered trademarks of Juniper Networks, Inc. in the United States and other countries. The Juniper Networks Logo, the Junos logo, and JunosE are trademarks of Juniper Networks, Inc. All other trademarks, service marks, registered trademarks, or registered service marks are the property of their respective owners. Juniper Networks assumes no responsibility for any inaccuracies in this document. Juniper Networks reserves the right to change, modify, transfer, or otherwise revise this publication without notice. Products made or sold by Juniper Networks or components thereof might be covered by one or more of the following patents that are owned by or licensed to Juniper Networks: U.S. Patent Nos. 5,473,599, 5,905,725, 5,909,440, 6,192,051, 6,333,650, 6,359,479, 6,406,312, 6,429,706, 6,459,579, 6,493,347, 6,538,518, 6,538,899, 6,552,918, 6,567,902, 6,578,186, and 6,590,785. Unified Access Control UAC Interoperability with the ScreenOS and Junos Enforcer Revision History July 2009 New Unified Access Control Solution Guide for Using the ScreenOS Enforcer and the ScreenOS Enforcer with the IC Series Appliance The information in this document is current as of the date listed in the revision history. ii
3 END USER LICENSE AGREEMENT READ THIS END USER LICENSE AGREEMENT ( AGREEMENT ) BEFORE DOWNLOADING, INSTALLING, OR USING THE SOFTWARE. BY DOWNLOADING, INSTALLING, OR USING THE SOFTWARE OR OTHERWISE EXPRESSING YOUR AGREEMENT TO THE TERMS CONTAINED HEREIN, YOU (AS CUSTOMER OR IF YOU ARE NOT THE CUSTOMER, AS A REPRESENTATIVE/AGENT AUTHORIZED TO BIND THE CUSTOMER) CONSENT TO BE BOUND BY THIS AGREEMENT. IF YOU DO NOT OR CANNOT AGREE TO THE TERMS CONTAINED HEREIN, THEN (A) DO NOT DOWNLOAD, INSTALL, OR USE THE SOFTWARE, AND (B) YOU MAY CONTACT JUNIPER NETWORKS REGARDING LICENSE TERMS. 1. The Parties. The parties to this Agreement are (i) Juniper Networks, Inc. (if the Customer s principal office is located in the Americas) or Juniper Networks (Cayman) Limited (if the Customer s principal office is located outside the Americas) (such applicable entity being referred to herein as Juniper ), and (ii) the person or organization that originally purchased from Juniper or an authorized Juniper reseller the applicable license(s) for use of the Software ( Customer ) (collectively, the Parties ). 2. The Software. In this Agreement, Software means the program modules and features of the Juniper or Juniper-supplied software, for which Customer has paid the applicable license or support fees to Juniper or an authorized Juniper reseller, or which was embedded by Juniper in equipment which Customer purchased from Juniper or an authorized Juniper reseller. Software also includes updates, upgrades and new releases of such software. Embedded Software means Software which Juniper has embedded in or loaded onto the Juniper equipment and any updates, upgrades, additions or replacements which are subsequently embedded in or loaded onto the equipment. 3. License Grant. Subject to payment of the applicable fees and the limitations and restrictions set forth herein, Juniper grants to Customer a non-exclusive and non-transferable license, without right to sublicense, to use the Software, in executable form only, subject to the following use restrictions: a. Customer shall use Embedded Software solely as embedded in, and for execution on, Juniper equipment originally purchased by Customer from Juniper or an authorized Juniper reseller. b. Customer shall use the Software on a single hardware chassis having a single processing unit, or as many chassis or processing units for which Customer has paid the applicable license fees; provided, however, with respect to the Steel-Belted Radius or Odyssey Access Client software only, Customer shall use such Software on a single computer containing a single physical random access memory space and containing any number of processors. Use of the Steel-Belted Radius or IMS AAA software on multiple computers or virtual machines (e.g., Solaris zones) requires multiple licenses, regardless of whether such computers or virtualizations are physically contained on a single chassis. c. Product purchase documents, paper or electronic user documentation, and/or the particular licenses purchased by Customer may specify limits to Customer s use of the Software. Such limits may restrict use to a maximum number of seats, registered endpoints, concurrent users, sessions, calls, connections, subscribers, clusters, nodes, realms, devices, links, ports or transactions, or require the purchase of separate licenses to use particular features, functionalities, services, applications, operations, or capabilities, or provide throughput, performance, configuration, bandwidth, interface, processing, temporal, or geographical limits. In addition, such limits may restrict the use of the Software to managing certain kinds of networks or require the Software to be used only in conjunction with other specific Software. Customer s use of the Software shall be subject to all such limitations and purchase of all applicable licenses. d. For any trial copy of the Software, Customer s right to use the Software expires 30 days after download, installation or use of the Software. Customer may operate the Software after the 30-day trial period only if Customer pays for a license to do so. Customer may not extend or create an additional trial period by re-installing the Software after the 30-day trial period. e. The Global Enterprise Edition of the Steel-Belted Radius software may be used by Customer only to manage access to Customer s enterprise network. Specifically, service provider customers are expressly prohibited from using the Global Enterprise Edition of the Steel-Belted Radius software to support any commercial network access services. The foregoing license is not transferable or assignable by Customer. No license is granted herein to any user who did not originally purchase the applicable license(s) for the Software from Juniper or an authorized Juniper reseller. 4. Use Prohibitions. Notwithstanding the foregoing, the license provided herein does not permit the Customer to, and Customer agrees not to and shall not: (a) modify, unbundle, reverse engineer, or create derivative works based on the Software; (b) make unauthorized copies of the Software (except as necessary for backup purposes); (c) rent, sell, transfer, or grant any rights in and to any copy of the Software, in any form, to any third party; (d) remove any proprietary notices, labels, or marks on or in any copy of the Software or any product in which the Software is embedded; (e) distribute any copy of the Software to any third party, including as may be embedded in Juniper equipment sold in the secondhand market; (f) use any locked or key-restricted feature, function, service, application, operation, or capability without first purchasing the applicable license(s) and obtaining a valid key from Juniper, even if such feature, function, service, application, operation, or capability is enabled without a key; (g) distribute any key for the Software provided by Juniper to any third party; (h) use the iii
4 Software in any manner that extends or is broader than the uses purchased by Customer from Juniper or an authorized Juniper reseller; (i) use Embedded Software on non-juniper equipment; (j) use Embedded Software (or make it available for use) on Juniper equipment that the Customer did not originally purchase from Juniper or an authorized Juniper reseller; (k) disclose the results of testing or benchmarking of the Software to any third party without the prior written consent of Juniper; or (l) use the Software in any manner other than as expressly provided herein. 5. Audit. Customer shall maintain accurate records as necessary to verify compliance with this Agreement. Upon request by Juniper, Customer shall furnish such records to Juniper and certify its compliance with this Agreement. 6. Confidentiality. The Parties agree that aspects of the Software and associated documentation are the confidential property of Juniper. As such, Customer shall exercise all reasonable commercial efforts to maintain the Software and associated documentation in confidence, which at a minimum includes restricting access to the Software to Customer employees and contractors having a need to use the Software for Customer s internal business purposes. 7. Ownership. Juniper and Juniper s licensors, respectively, retain ownership of all right, title, and interest (including copyright) in and to the Software, associated documentation, and all copies of the Software. Nothing in this Agreement constitutes a transfer or conveyance of any right, title, or interest in the Software or associated documentation, or a sale of the Software, associated documentation, or copies of the Software. 8. Warranty, Limitation of Liability, Disclaimer of Warranty. The warranty applicable to the Software shall be as set forth in the warranty statement that accompanies the Software (the Warranty Statement ). Nothing in this Agreement shall give rise to any obligation to support the Software. Support services may be purchased separately. Any such support shall be governed by a separate, written support services agreement. TO THE MAXIMUM EXTENT PERMITTED BY LAW, JUNIPER SHALL NOT BE LIABLE FOR ANY LOST PROFITS, LOSS OF DATA, OR COSTS OR PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES, OR FOR ANY SPECIAL, INDIRECT, OR CONSEQUENTIAL DAMAGES ARISING OUT OF THIS AGREEMENT, THE SOFTWARE, OR ANY JUNIPER OR JUNIPER-SUPPLIED SOFTWARE. IN NO EVENT SHALL JUNIPER BE LIABLE FOR DAMAGES ARISING FROM UNAUTHORIZED OR IMPROPER USE OF ANY JUNIPER OR JUNIPER-SUPPLIED SOFTWARE. EXCEPT AS EXPRESSLY PROVIDED IN THE WARRANTY STATEMENT TO THE EXTENT PERMITTED BY LAW, JUNIPER DISCLAIMS ANY AND ALL WARRANTIES IN AND TO THE SOFTWARE (WHETHER EXPRESS, IMPLIED, STATUTORY, OR OTHERWISE), INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. IN NO EVENT DOES JUNIPER WARRANT THAT THE SOFTWARE, OR ANY EQUIPMENT OR NETWORK RUNNING THE SOFTWARE, WILL OPERATE WITHOUT ERROR OR INTERRUPTION, OR WILL BE FREE OF VULNERABILITY TO INTRUSION OR ATTACK. In no event shall Juniper s or its suppliers or licensors liability to Customer, whether in contract, tort (including negligence), breach of warranty, or otherwise, exceed the price paid by Customer for the Software that gave rise to the claim, or if the Software is embedded in another Juniper product, the price paid by Customer for such other product. Customer acknowledges and agrees that Juniper has set its prices and entered into this Agreement in reliance upon the disclaimers of warranty and the limitations of liability set forth herein, that the same reflect an allocation of risk between the Parties (including the risk that a contract remedy may fail of its essential purpose and cause consequential loss), and that the same form an essential basis of the bargain between the Parties. 9. Termination. Any breach of this Agreement or failure by Customer to pay any applicable fees due shall result in automatic termination of the license granted herein. Upon such termination, Customer shall destroy or return to Juniper all copies of the Software and related documentation in Customer s possession or control. 10. Taxes. All license fees payable under this agreement are exclusive of tax. Customer shall be responsible for paying Taxes arising from the purchase of the license, or importation or use of the Software. If applicable, valid exemption documentation for each taxing jurisdiction shall be provided to Juniper prior to invoicing, and Customer shall promptly notify Juniper if their exemption is revoked or modified. All payments made by Customer shall be net of any applicable withholding tax. Customer will provide reasonable assistance to Juniper in connection with such withholding taxes by promptly: providing Juniper with valid tax receipts and other required documentation showing Customer s payment of any withholding taxes; completing appropriate applications that would reduce the amount of withholding tax to be paid; and notifying and assisting Juniper in any audit or tax proceeding related to transactions hereunder. Customer shall comply with all applicable tax laws and regulations, and Customer will promptly pay or reimburse Juniper for all costs and damages related to any liability incurred by Juniper as a result of Customer s non-compliance or delay with its responsibilities herein. Customer s obligations under this Section shall survive termination or expiration of this Agreement. 11. Export. Customer agrees to comply with all applicable export laws and restrictions and regulations of any United States and any applicable foreign agency or authority, and not to export or re-export the Software or any direct product thereof in violation of any such restrictions, laws or regulations, or without all necessary approvals. Customer shall be liable for any such violations. The version of the Software supplied to Customer may contain encryption or other capabilities restricting Customer s ability to export the Software without an export license. iv
5 12. Commercial Computer Software. The Software is commercial computer software and is provided with restricted rights. Use, duplication, or disclosure by the United States government is subject to restrictions set forth in this Agreement and as provided in DFARS through , FAR , FAR (b)(2), FAR , or FAR (ALT III) as applicable. 13. Interface Information. To the extent required by applicable law, and at Customer's written request, Juniper shall provide Customer with the interface information needed to achieve interoperability between the Software and another independently created program, on payment of applicable fee, if any. Customer shall observe strict obligations of confidentiality with respect to such information and shall use such information in compliance with any applicable terms and conditions upon which Juniper makes such information available. 14. Third Party Software. Any licensor of Juniper whose software is embedded in the Software and any supplier of Juniper whose products or technology are embedded in (or services are accessed by) the Software shall be a third party beneficiary with respect to this Agreement, and such licensor or vendor shall have the right to enforce this Agreement in its own name as if it were Juniper. In addition, certain third party software may be provided with the Software and is subject to the accompanying license(s), if any, of its respective owner(s). To the extent portions of the Software are distributed under and subject to open source licenses obligating Juniper to make the source code for such portions publicly available (such as the GNU General Public License ( GPL ) or the GNU Library General Public License ( LGPL )), Juniper will make such source code portions (including Juniper modifications, as appropriate) available upon request for a period of up to three years from the date of distribution. Such request can be made in writing to Juniper Networks, Inc., 1194 N. Mathilda Ave., Sunnyvale, CA 94089, ATTN: General Counsel. You may obtain a copy of the GPL at and a copy of the LGPL at Miscellaneous. This Agreement shall be governed by the laws of the State of California without reference to its conflicts of laws principles. The provisions of the U.N. Convention for the International Sale of Goods shall not apply to this Agreement. For any disputes arising under this Agreement, the Parties hereby consent to the personal and exclusive jurisdiction of, and venue in, the state and federal courts within Santa Clara County, California. This Agreement constitutes the entire and sole agreement between Juniper and the Customer with respect to the Software, and supersedes all prior and contemporaneous agreements relating to the Software, whether oral or written (including any inconsistent terms contained in a purchase order), except that the terms of a separate written agreement executed by an authorized Juniper representative and Customer shall govern to the extent such terms are inconsistent or conflict with terms contained herein. No modification to this Agreement nor any waiver of any rights hereunder shall be effective unless expressly assented to in writing by the party to be charged. If any portion of this Agreement is held invalid, the Parties agree that such invalidity shall not affect the validity of the remainder of this Agreement. This Agreement and associated documentation has been written in the English language, and the Parties agree that the English version will govern. (For Canada: Les parties aux présentés confirment leur volonté que cette convention de même que tous les documents y compris tout avis qui s'y rattaché, soient redigés en langue anglaise. (Translation: The parties confirm that this Agreement and all related documentation is and will be in the English language)). v
6 vi
7 Abbreviated Table of Contents Part 1 Chapter 1 Front Part xv Concepts and Configuration Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control Chapter 2 Using IPsec Chapter 3 Policies and Procedures for Interoperability Between the UAC Enforcer and the IC Series Part 2 Index Index vii
8 Using the Infranet Controller with the ScreenOS Enforcer viii
9 Table of Contents Front Part xv Related Documentation xv Document Conventions xvi Requesting Technical Support xvi Self-Help Online Tools and Resources xvii Opening a Case with JTAC xvii Part 1 Chapter 1 Concepts and Configuration Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control The IC Series and the UAC Enforcer How the IC Series and the UAC Enforcer Work Together Juniper Networks ScreenOS Enforcer Features by Release Configuration Overview Communication Between the IC Series and the Infranet Enforcer Certificates on the IC Series and the Infranet Enforcer Task Summary: Setting up Certificates for the IC Series and Infranet Enforcer Setting up Certificates for the IC Series and Infranet Enforcer Using OpenSSL to create a CA and Sign the Server Certificate Creating a CA and Signing the Server Certificate Using OpenSSL Importing the Certificate to the Infranet Enforcer Configuring Certificate Authority Server Settings Binding an Interface to a Security Zone on a ScreenOS Enforcer Binding the Physical Interface Configuring the ScreenOS Enforcer Connecting with the ScreenOS Enforcer Configuring the ScreenOS Connection Setting up an Infranet Enforcer in Route Mode Creating a Route Mode Instance with the ScreenOS Enforcer WebUI CLI Setting up an Infranet Enforcer in Transparent Mode Creating a Transparent Mode Instance with the ScreenOS Enforcer CLI Viewing the Configuration of an IC Series Device on the ScreenOS Enforcer WebUI CLI Captive Portal on the Infranet Enforcer Before Configuring Captive Portal Creating a Redirect Policy on the Infranet Enforcer ix
10 Using the Infranet Controller with the ScreenOS Enforcer Overriding the Default Redirection Destination for Captive Portal Configuring a New Redirection Destination for Captive Portal Using VSYS on the ScreenOS Enforcer Chapter 2 Using IPsec IPsec and the UAC Infranet Enforcer How this Section is Organized IPsec Policies Using IPsec with the Infranet Enforcer IPsec Enforcement on the Infranet Enforcer Refreshing IPsec Policies on the IC Series Before Configuring IPsec Configuring Basic IPsec Policies for the ScreenOS Enforcer on the IC Series IPsec Routing Policices Before you Begin Configuring an IPsec Routing Policy IP Address Pool Policies for IPsec in a NAT Environment IP Address Pool Policies Configuring an IP Address Pool Policy Source Interface Policies for the ScreenOS Enforcer Configuring Source Interface Policies Upgrading IPsec Enforcement Policies from Version 1.x of the Infranet Controller Setting up IPsec Enforcement on the ScreenOS Enforcer Configuring the IPsec Encryption Settings on the ScreenOS Enforcer Bidirectional VPN Policies on the ScreenOS Enforcer Creating a Bidirectional VPN Policy Junos Enforcer IPsec Configuration Task Summary: Configuring IPsec on the Junos Enforcer Chapter 3 Policies and Procedures for Interoperability Between the UAC Enforcer and the IC Series Infranet Enforcer Policies About Resource Access Policies Notifying the User of Denied Traffic in a Resource Access Policy Configuring Resource Access Policies Setting up Source IP Enforcement on the Infranet Enforcer Infranet-Auth Policies for Source IP on the ScreenOS Enforcer Security Policies for Source IP on the Junos Enforcer Auth Tables on the Infranet Enforcer Dynamic Auth Table Allocation Configuring Dynamic Auth Table Allocation Configuring Auth Table Mapping Policies for Source IP Enforcement Configuring Auth Table Mapping Policies Part 2 Index Index x
11 List of Figures Part 1 Chapter 1 Concepts and Configuration Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control Figure 1: Binding a Physical Interface to a Security Zone Figure 2: Captive Portal Figure 3: Multiple VSYS with Shared and Unshared Zones Chapter 2 Using IPsec Figure 4: Using an IP Address Pool in a NAT Environment Chapter 3 Policies and Procedures for Interoperability Between the UAC Enforcer and the IC Series Figure 5: Policy Interaction Figure 6: Using Auth Table Mapping Policies xi
12 Using the Infranet Controller with the ScreenOS Enforcer xii
13 List of Tables Front Part xv Table 1: IC Series Publications xv Table 2: Notice Icons xvi Part 1 Chapter 1 Concepts and Configuration Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control Table 3: ScreenOS Options Chapter 2 Using IPsec Table 4: Syntax for IP Address Pools xiii
14 Using the Infranet Controller with the ScreenOS Enforcer xiv
15 Front Part Related Documentation Related Documentation on page xv Document Conventions on page xvi Requesting Technical Support on page xvi Table 1 on page xv describes documentation for the IC Series Appliance. All documentation is available at Table 1: IC Series Publications Book Description UAC Interoperability with the ScreenOS and Junos Enforcer Details using the IC Series Applicance with the UAC Enforcer. Layer 2 and the IC Series RADIUS Server This guide provides an overview of RADIUS and the IC Series Appliance RADIUS server. Implementation details for 802.1X, MAC address authentication, and several other practical use cases are provided. UAC Guide to IF-MAP Federation Provides a comprehensive overview of IF-MAP and details using IF-MAP Federation with the UAC solution. Unified Access Control Administration Guide Includes comprehensive information about configuring the Unified Access Control solution and the Infranet Controller 4500 and 6500 appliances. Client Side Changes Guide Lists changes that the Infranet Controller clients and Odyssey Access Client make to client computers, including installed files and registry changes. Custom Sign-in Pages Solution Guide Includes guidelines for personalizing the look-and-feel of sign-in pages. Deployment Scenarios Guide Describes several example network scenarios for deploying the Unified Access Control solution. Installation Guide Describes how to install the Infranet Controller 4500 and 6500 appliances on your network and begin configuration. xv
16 Using the Infranet Controller with the ScreenOS Enforcer Table 1: IC Series Publications (continued) Book Description Quick Start Guide Includes an example of configuring the Unified Access Control solution for a front-end server deployment scenario. Troubleshooting Guide Tips for troubleshooting the UAC Solution. Document Conventions Table 2: Notice Icons Table 2 on page xvi defines notice icons used in this guide. Icon Meaning Description Informational note Indicates important features or instructions. Caution Indicates a situation that might result in loss of data or hardware damage. Warning Alerts you to the risk of personal injury or death. Laser warning Alerts you to the risk of personal injury from a laser. Requesting Technical Support Technical product support is available through the Juniper Networks Technical Assistance Center (JTAC). If you are a customer with an active J-Care or JNASC support contract, or are covered under warranty, and need post-sales technical support, you can access our tools and resources online or open a case with JTAC. JTAC policies For a complete understanding of our JTAC procedures and policies, review the JTAC User Guide located at Product warranties For product warranty information, visit JTAC hours of operation The JTAC centers have resources available 24 hours a day, 7 days a week, 365 days a year. xvi
17 Front Part Self-Help Online Tools and Resources For quick and easy problem resolution, Juniper Networks has designed an online self-service portal called the Customer Support Center (CSC) that provides you with the following features: Find CSC offerings: Search for known bugs: Find product documentation: Find solutions and answer questions using our Knowledge Base: Download the latest versions of software and review release notes: Search technical bulletins for relevant hardware and software notifications: Join and participate in the Juniper Networks Community Forum: Open a case online in the CSC Case Management tool: To verify service entitlement by product serial number, use our Serial Number Entitlement (SNE) Tool: Opening a Case with JTAC You can open a case with JTAC on the Web or by telephone. Use the Case Management tool in the CSC at Call JTAC ( toll-free in the USA, Canada, and Mexico). For international or direct-dial options in countries without toll-free numbers, see xvii
18 Using the Infranet Controller with the ScreenOS Enforcer xviii
19 PART 1 Concepts and Configuration Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control on page 3 Using IPsec on page 33 Policies and Procedures for Interoperability Between the UAC Enforcer and the IC Series on page 59 1
20 Using the Infranet Controller with the ScreenOS Enforcer 2
21 CHAPTER 1 Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control The IC Series and the UAC Enforcer on page 4 How the IC Series and the UAC Enforcer Work Together on page 4 Certificates on the IC Series and the Infranet Enforcer on page 7 Task Summary: Setting up Certificates for the IC Series and Infranet Enforcer on page 7 Setting up Certificates for the IC Series and Infranet Enforcer on page 8 Using OpenSSL to create a CA and Sign the Server Certificate on page 9 Creating a CA and Signing the Server Certificate Using OpenSSL on page 9 Importing the Certificate to the Infranet Enforcer on page 12 Configuring Certificate Authority Server Settings on page 12 Binding an Interface to a Security Zone on a ScreenOS Enforcer on page 13 Binding the Physical Interface on page 15 Configuring the ScreenOS Enforcer on page 15 Configuring the ScreenOS Connection on page 16 Setting up an Infranet Enforcer in Route Mode on page 17 Creating a Route Mode Instance with the ScreenOS Enforcer on page 18 Setting up an Infranet Enforcer in Transparent Mode on page 21 Creating a Transparent Mode Instance with the ScreenOS Enforcer on page 22 Viewing the Configuration of an IC Series Device on the ScreenOS Enforcer on page 23 Captive Portal on the Infranet Enforcer on page 24 Before Configuring Captive Portal on page 25 Creating a Redirect Policy on the Infranet Enforcer on page 26 Overriding the Default Redirection Destination for Captive Portal on page 28 Configuring a New Redirection Destination for Captive Portal on page 29 Using VSYS on the ScreenOS Enforcer on page 31 3
22 Using the Infranet Controller with the ScreenOS Enforcer The IC Series and the UAC Enforcer NOTE: A UAC Enforcer is an Infranet Enforcer, which can be either a ScreenOS firewall device, or a J Series or SRX Series Services Gateway. The Infranet Controller is the policy decision point that determines which users and endpoints can access protected resources. You can use Juniper Networks firewalls to serve as the enforcement point to provide the ultimate protection to ensure that your network assets are secured. You can use a ScreenOS Enforcer or a Junos Enforcer with the UAC solution. A Junos Enforcer is a J Series Services Router or an SRX Series Services Gateway configured as a Layer 3 enforcement point. This document contains configuration details for the ScreenOS Enforcer. See the Unified Access Control Supported Platforms document for version compatibility. How the IC Series and the UAC Enforcer Work Together The Infranet Controller authenticates users, ensures that endpoints meet security policies, and serves resource access policy information to Juniper Networks security devices. After you configure the Infranet Controller and the Infranet Enforcer to successfully communicate, you set up trust and untrust zones to define network boundaries. You configure source IP policies or encrypted IPsec tunnels for endpoints to route traffic between zones. Finally, you use resource access policies to permit or deny traffic to protected resources. Juniper Networks ScreenOS Enforcer Features by Release You can use Juniper Networks ScreenOS version 5.4 or greater with UAC. Depending on the release version of ScreenOS that you are using, not all of the features outlined in this guide are supported. Table 3 on page 4indicates what release version of ScreenOS is required for specific features. Table 3: ScreenOS Options Feature ScreenOS Release Required Captive portal 5.4 Configurable auth table entries 6.0 Seamless cluster failover 6.0R2 Dynamic auth table allocation roles per auth table entry 6.1 4
23 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control Table 3: ScreenOS Options (continued) Feature ScreenOS Release Required Messages to authenticated but unauthorized users 6.2 Support for ISG-IDP 6.2 Support for VSYS 6.2 Non-standard port for captive portal 6.3 Configuration Overview The following basic tasks must be accomplished to use the Infranet Controller with an Infranet Enforcer: Configure the Infranet Controller and the ScreenOS Enforcer to communicate over a secure connection. Configure user authentication and authorization by setting up user roles, authentication and authorization servers, and authentication realms on the Infranet Controller. Configure resource access policies on the Infranet Controller to specify which endpoints are allowed or denied access to protected resources. Configure traffic enforcement between each source and destination zone with ScreenOS Enforcer Infranet auth policies using one of the following methods: Source IP enforcement IPsec enforcement Communication Between the IC Series and the Infranet Enforcer This section describes the communication between the Infranet Controller and the Infranet Enforcer. At startup, the ScreenOS Enforcer contacts the Infranet Controller over an SSL connection using the NetScreen Address Change Notification (NACN) protocol. After the ScreenOS Enforcer successfully establishes a connection with the Infranet Controller, the Infranet Controller opens an SSH connection with the ScreenOS Enforcer. The Infranet Controller uses this SSH connection to push policy and user authentication information to the ScreenOS Enforcer. With ScreenOS release 6.0 or earlier, when the Infranet Controller authenticates a user and verifies that the user s endpoint is compliant with endpoint security policies, the Infranet Controller pushes user-specific configuration information to the ScreenOS Enforcer. This user-specific configuration information includes an auth table entry for each authenticated user. An auth table entry consists of the user s name, a set of roles, and the IP address of the wired adapter, wireless adapter, or virtual adapter in the user s computer. With ScreenOS release 6.1 or later, and with the Junos Enforcer you 5
24 Using the Infranet Controller with the ScreenOS Enforcer can configure the Infranet Controller to dynamically create auth table entries on the Infranet Enforcer after a specific resource is requested. To use source IP enforcement, you create infranet-auth source IP policies on ScreenOS Enforcers that allow traffic from the endpoint to protected resources. To use IPsec enforcement, you set up a VPN tunnel for a dialup user with Internet Key Exchange (IKE) with an Enforcer policy. The VPN tunnel and the infranet-auth IPsec policy enable the user's endpoint (Odyssey Access Client or Junos Pulse) to use an IPsec tunnel to the Infranet Enforcer and access protected resources. The Infranet Enforcer sends the necessary setup information to the client. When the Infranet Enforcer detects traffic from an endpoint that matches an Infranet Enforcer policy, it uses the endpoint s auth table entry to determine the role(s) associated with that user. The Infranet Enforcer then matches the destination IP address of the protected resource (from the Infranet Enforcer policy) with a resource access policy. The Infranet Enforcer searches to find a matching role and applies the policy action. As necessary, the Infranet Controller sends commands to the Infranet Enforcer to remove policies or auth table entries and deny access to protected resources. This can occur, for example, when the user s computer becomes non-compliant with endpoint security policies or loses its connection with the Infranet Controller, when you change the configuration of a user s role, or when you disable all user accounts on the Infranet Controller in response to a security problem such as a virus on the network. The FIPS IC6500 or a non-fips Infranet Controller can be used with a ScreenOS Enforcer that is in FIPS mode. If FIPS is enabled on the Infranet Enforcer, the admin console displays that FIPS is enabled on the Infranet Enforcer > Connection page. You can configure an Infranet Enforcer to work with more than one Infranet Controller in a high availability configuration known as an Infranet Controller cluster. The Infranet Enforcer communicates with only one Infranet Controller at a time; the other Infranet Controllers are used for fail-over. If the Infranet Enforcer cannot connect to the first Infranet Controller you added to a cluster, it attempts to connect to the next one in the configuration list until a connection occurs. If the currently-connected Infranet Controller fails, the Infranet Enforcer attempts to connect to the first Infranet Controller again. The Infranet Controllers configured on an Infranet Enforcer should all be members of the same Infranet Controller cluster. You can use the Infranet Enforcer as a policy enforcement point for any number of Infranet Controllers or Instant Virtual Extranet (IVE) Secure Access devices in a federated network. Related Topics Certificates on the IC Series and the Infranet Enforcer on page 7 Binding an Interface to a Security Zone on page 13 Configuring the ScreenOS Enforcer on page 15 6
25 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control Certificates on the IC Series and the Infranet Enforcer The Infranet Controller and the Infranet Enforcer communicate over a secure channel using digital security certificates as the mechanism for establishing trust. A digital certificate is a form of identification. The certificate provides information about the identity of the presenter and other data that helps determine whether or not the presenter should be trusted. Public Key Infrastructure (PKI) refers to the hierarchical structure of trust required for the successful implementation of public key cryptography. When the Infranet Enforcer first connects with the Infranet Controller, the devices exchange security information to verify secure communication. In ScreenOS implementations, the Infranet Controller presents its device certificate and the ScreenOS Enforcer is required to verify the certificate before further communication is initiated. In Junos implementations, the Junos Enforcer presents its password to the Infranet Controller and the Infranet Controller optionally verifies the password before further communication is initiated. Once verified, the Infranet Controller presents its device certificate to the Junos Enforcer. Server certificate verification is not required for the Junos Enforcer to connect; however, as an extra security measure you can verify the certificate if you wish to implement an additional layer of trust. If you are using the FIPS IC6500, only the Certificate Signing Request (CSR) method for creating device certificates can be used. You cannot import a CA created certificate (pfx) with a private key file on FIPS IC6500. Digital certificates are issued by a Certificate Authority (CA). PKI was designed so the CA is always a trusted entity, so there is a guarantee that the information contained in a certificate issued or signed by a CA is valid. To ensure that the trust relationship in your network between the Infranet Controller and the Infranet Enforcer is secure, you create a certificate hierarchy for this trust relationship, and then upload the appropriate certificates into the devices. Related Topics Task Summary: Setting up Certificates for the IC Series and Infranet Enforcer on page 7 Setting up Certificates for the IC Series and Infranet Enforcer on page 8 Using OpenSSL to create a CA and Sign the Server Certificate on page 9 Configuring Certificate Authority Server Settings on page 12 Task Summary: Setting up Certificates for the IC Series and Infranet Enforcer To allow the ScreenOS Enforcer (certificate use is optional with the Junos Enforcer) to communicate with the Infranet Controller, you must do all of the following steps: 7
26 Using the Infranet Controller with the ScreenOS Enforcer If you do not have one already, obtain the CA (Certificate Authority) certificate that signed the Infranet Controller server certificate to load on the Infranet Enforcer. Create a certificate signing request (CSR) for an Infranet Controller server certificate, and use the CA certificate to sign the server certificate. Import the CA certificate into the Infranet Enforcer. Specify the CA certificate to be used to verify the Infranet Controller. If the server certificate or the CA certificate is missing or expired, the Infranet Enforcer cannot communicate with the ScreenOS Enforcer. The Infranet Enforcer does not accept the temporary self-signed certificate that the Infranet Controller created during initialization. Related Topics Using OpenSSL to create a CA and Sign the Server Certificate on page 9 Setting up Certificates for the IC Series and Infranet Enforcer To set up Certificates for the Infranet Controller and Infranet Enforcer: 1. If you do not have a certificate authority, install and use OpenSSL to generate a CA certificate. 2. Create a certificate signing request (CSR) for a server certificate, and then sign the CSR by using your CA or by using OpenSSL. 3. Import the signed server certificate created from the CSR into the Infranet Controller by clicking System > Configuration > Certificates > Device Certificates from the left navigation bar of the Infranet Controller admin console. Under Certificate Signing Requests, click the Pending CSR link that corresponds to the signed certificate. The Pending Certificate Signing Request dialog box appears. Under Step 2: Import signed certificate, browse to the certificate file you received from the CA. For example: <c:\openssl\certs\ic.crt> Click Import. 4. By default, the signed server certificate is automatically associated with the internal port on the Infranet Controller. If you want to associate the certificate with the external or virtual port, do the following steps: Click System > Configuration > Certificates > Device Certificates from the left navigation bar. Click the link that corresponds to a certificate that you want to use. The Certificate Details dialog box appears. Under Present certificate on these ports, specify the port(s) that the Infranet Controller should associate with the certificate you can choose internal or external 8
27 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control ports and primary or virtual ports, but you cannot choose a port that is already associated with another certificate. Click Save Changes. 5. Import the certificate of the CA that signed the Infranet Controller s server certificate into the Infranet Enforcer. NOTE: You can prevent your Web browser s security warning from appearing each time you sign into the Infranet Controller by importing the certificate of the CA that signed the Infranet Controller s server certificate into your browser s list of trusted root certification authorities. NOTE: If later you import a different server certificate and CA certificate, you may need to initiate a new connection to use them. To initiate a new connection, click Maintenance > System > Platform > Restart Services in the Infranet Controller admin console. The Infranet Enforcer connects to the Infranet Controller and validates the new certificate. Related Topics Creating a CA and Signing the Server Certificate Using OpenSSL on page 9 Importing the Certificate to the Infranet Enforcer on page 12 Configuring Certificate Authority Server Settings on page 12 Using OpenSSL to create a CA and Sign the Server Certificate If you do not have a certificate authority, use the instructions in this section to use OpenSSL on Windows to create a CA certificate and sign the CSR for the server certificate. You can also use OpenSSL to create a trusted root CA certificate for Odyssey Access Client certificate validation of the Infranet Controller. Use the instructions in this section to create a CA certificate and sign the CSR for the Infranet Controller s server certificate. Related Topics Creating a CA and Signing the Server Certificate Using OpenSSL on page 9 Importing the Certificate to the Infranet Enforcer on page 12 Creating a CA and Signing the Server Certificate Using OpenSSL To set up OpenSSL: 1. Download and install OpenSSL from 2. At the Windows command prompt, type the following commands: C: cd \openssl C: md certs 9
28 Using the Infranet Controller with the ScreenOS Enforcer C: cd certs C: md democa C: md democa\newcerts C: edit democa\index.txt 3. Press ALT+F, S keys to save the file. 4. Press the ALT+F, X keys to exit the editor. 5. At the Windows command prompt, type the following command: C: edit democa\serial 6. Type 01 in the document window. 7. Press ALT+F, S keys to save the file. 8. Press the ALT+F, X keys to exit the editor. 9. At the Windows command prompt, type the following command: C: set path=c:\openssl\bin;%path% 10. To create a CA key, type the following command at the Windows command prompt in the c:\openssl\certs directory: C: openssl genrsa -out ca.key 1024 Loading 'screen' into random state - done Generating RSA private key, 1024 bit long modulus e is (0x10001 To create and sign a certificate signing request (CSR) from the CLI: 1. Type the following command at the Windows command prompt in the c:\openssl\certs directory: C: openssl req -new -x509 -days 365 -key ca.key -out democa/cacert.pem 2. Enter the appropriate distinguished name (DN) information for the CA certificate. You can leave some fields blank by entering a period. For example: Country Name: US State or Province Name: CA Locality Name: Sunnyvale Organization Name: XYZ Org. Unit Name: IT 10
29 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control Common Name: ic.xyz.com Address: To create and sign a certificate signing request (CSR) from the WebUI: 1. Click the System > Configuration > Certificates > Device Certificates on the left navigation bar. 2. Click New CSR. The new Certificate Signing Request page appears. 3. Enter the required information. For example: Country Name: US State or Province Name: CA Locality Name: Sunnyvale Organization Name: XYZ Org. Unit Name: IT Common Name: ic.xyz.com Address: user@xyz.com The organization name in the CSR must match the CA certificate's organization name. If the organization names do not match, you cannot sign the CSR. 4. Enter random characters in the Random Data box. 5. Click Create CSR. The Pending Certificate Signing Request page appears. 6. Select and copy all of the text in the text box in Step 1 into a text editor, and save the text file in the certs directory as: c:\openssl\certs\ic.csr 7. To sign the certificate, type the following command at the Windows command prompt in the c:\openssl\certs directory: openssl ca -in ic.csr -out ic.crt -keyfile ca.key 8. Enter Y to sign the certificate. 9. Enter Y to commit the certificate. You are now ready to import the server certificate into the Infranet Controller and the CA certificate into the Infranet Enforcer. Related Topics Importing the Certificate to the Infranet Enforcer on page 12 11
30 Using the Infranet Controller with the ScreenOS Enforcer Importing the Certificate to the Infranet Enforcer To import a CA certificate on the ScreenOS Enforcer: 1. On the Infranet Enforcer WebUI, click Objects > Certificates from the left navigation bar. 2. Select CA from the Show list. 3. Click Browse, to find and select the CA certificate (such as c:\openssl\certs\democa\cacert.pem), and then click Load. 4. Select CA from the Show list to display the CA certificate. Related Topics Setting up Certificates for the IC Series and Infranet Enforcer on page 8 Configuring Certificate Authority Server Settings The CA server you use can be owned and operated by an independent CA or by your own organization, in which case you become your own CA. If you use an independent CA, you must contact them for the addresses of their CA and CRL servers (for obtaining certificates and certificate revocation lists), and for the information they require when submitting certificate requests. When you are your own CA, you determine this information yourself. On the ScreenOS Enforcer, you can use the WebUI to configure CA server settings. Select Objects > Certificates and navigate to the proper certificate. You can configure the following options: X509 Certificate Path Validation Level: Within X509 is a specification for a certificate that binds an entity's distinguished name to its public key through the use of a digital signature. Select Full to validate the certificate path all the way back to the root, or select Partial to validate it only part of the way. The CRL distribution point extension (.cdp) in an X509 certificate can be either an HTTP URL or an LDAP URL. Certificate Revocation Check Settings: CRL (Certificate Revocation List): Enables the Juniper Networks security device to use only CRL to check the certificate status. OCSP (Online Certificate Status Protocol): Enables the Juniper Networks security device to use only OCSP to check the certificate status. None: Disables CRL certificate checking. If you are not using CRL certificate checking, be sure to disable it in the CA Server Settings dialog box. Best Effort: Enables the Juniper Networks security device to use CRL to check the certificate status, but if there is no information that indicates that the certificate is revoked, accept the certificate. 12
31 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control CRL Settings: URL Address: Specifies the internal Web-based URL of the LDAP server managing your CRL. LDAP Server: Specifies the IP address or domain name of the LDAP Root CA server that manages the CRL. Refresh Frequency: Applies only to the CRL only. From the drop-down list, select whether you want to update the CRL daily, weekly, monthly, or according to the default setting (which updates the CRL shortly after the next scheduled update). OCSP Settings: URL Address: Specifies the internal Web-based URL of the OCSP server. Advanced Settings: Specifies a CA with which the Juniper Networks security device verifies the OCSP response. SCEP (Simple Certificate Enrollment Protocol) Settings: RA CGI (registration authority certificate generation information): Specifies the RA URL where the Juniper Networks security device will request a CA certificate. CA CGI (certificate authority certificate generation information): Specifies the CA URL. CA IDENT: Specifies the name of the certificate authority for purposes of certificate ownership, if necessary. Challenge: Specifies the challenge word(s) sent to you by the CA that will prove your identity to the CA. Advanced Settings: Configures Advanced SCEP settings such as polling interval and certificate authentication. Related Topics Certificates on the IC Series and the Infranet Enforcer on page 7 Binding an Interface to a Security Zone on a ScreenOS Enforcer Security zones represent virtual sections of the network, segmented into logical areas. Security zones can be assigned to an interface, or on large devices to a virtual system. From the perspective of security policies, traffic enters into one security zone and goes out on another security zone. On the ScreenOS Enforcer, there are several predefined zones, for example trust and untrust. You might need to bind the physical interfaces on the Juniper Networks security device to security zones or change a binding to accommodate your deployment. Figure 1 on page 14 shows a typical setup for a ScreenOS Enforcer Integrated Security Gateway 2000 (ISG 2000). 13
32 Using the Infranet Controller with the ScreenOS Enforcer NOTE: Slot numbering varies by platform, and interface numbering varies by module type. Refer to the User Guide that accompanied the device for slot and interface numbering information or visit to obtain a copy of the User Guide specific to your platform. Endpoints must reside in a security zone different from your protected resources. The trust and untrust security zones in Figure 4, are default zones for Route mode configurations on a ScreenOS Enforcer. For Transparent mode (on ScreenOS Enforcers), you should use the v1-trust and v1-untrust security zones (not shown). The Infranet Controller (not shown) can reside in any security zone. If you place the Infranet Controller in a security zone that is different from the security zone that contains endpoints, you must set a policy allowing traffic from the endpoints to the Infranet Controller. To view the zones available on the ScreenOS Enforcer, enter the get zone command in the ScreenOS CLI. To configure custom zones, refer to the Concepts & Examples ScreenOS Reference Guide: Volume 2, Fundamentals. Figure 1: Binding a Physical Interface to a Security Zone In Figure 1 on page 14the endpoints reside in the Untrust zone, and the protected resources reside in the Trust zone. Port numbering is dependent on chassis configuration. Related Topics Binding the Physical Interface on page 15 14
33 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control Binding the Physical Interface On the ScreenOS Enforcer you can bind an interface to a security zone from either the WebUI or the CLI. ScreenOS WebUI Select Network > Interfaces > Edit: Select a Zone from the pull-down menu then click OK. ScreenOS CLI <set interface ethernet4/1 zone trust > <set interface ethernet3/8 zone untrust > <save> Related Topics Configuring the ScreenOS Enforcer on page 15 Configuring the ScreenOS Enforcer This following sections contain instructions for configuring the Infranet Enforcer. For cabling, rack mounting, and basic configuration instructions for platforms, such as the ISG 1000 or ISG 2000, refer to the User s Guide that shipped with the system or visit the Juniper Networks Web site at to download the User s Guide appropriate for the platform you are using. You can use Route mode or Transparent mode to configure a Juniper Networks ScreenOS Enforcer. By default, the ScreenOS Enforcer operates in Route mode. The Junos Enforcer operates only in Route mode. For more information about how to set up routing, see the Routing volume of the Concepts & Examples ScreenOS Reference Guide, which you can download from For more information about Route or Transparent mode, see the Fundamentals volume of the Concepts & Examples ScreenOS Reference Guide. Juniper Networks recommends configuring the Infranet Enforcer to use SSHv2. To perform ScreenOS configuration tasks the administrator must have root access. Connecting with the ScreenOS Enforcer The ScreenOS Enforcer connects with the Infranet Controller over an SSH connection that uses the NetScreen Address Change Notification (NACN) protocol. To configure a connection between the two appliances, you must specify the following items on the Infranet Controller in an Infranet Enforcer connection policy: An NACN password 15
34 Using the Infranet Controller with the ScreenOS Enforcer An administrator name and password for signing into the Infranet Enforcer using SSH The Serial number(s) of the Infranet Enforcer(s) The Infranet Controller uses the NACN password and serial number for a connection from the ScreenOS Enforcer. When the ScreenOS Enforcer first turns on, it sends an NACN message containing the NACN password and serial number to the Infranet Controller. The Infranet Controller uses the serial number to determine which ScreenOS Enforcer is attempting to connect, and the Infranet Controller uses the NACN password to authenticate the ScreenOS Enforcer. The Infranet Controller then begins communicating with the ScreenOS Enforcer using SSH. Related Topics Configuring the ScreenOS Connection on page 16 Setting up an Infranet Enforcer in Route Mode on page 17 Setting up an Infranet Enforcer in Transparent Mode on page 21 Configuring the ScreenOS Connection Topic Details Using a ScreenOS Enforcer with 802.1X To use the ScreenOS Enforcer as an 802.1X enforcement point in front of protected resources, you must first create the location group, which is added to the Location Group list. You can select the location group you have created from the list. Initiating the connection To initiate a connection immediately after you finish configuring the Infranet Enforcer, restart the Infranet Controller services by clicking Maintenance > System > Platform > Restart Services from the Infranet Controller admin console. To configure the Infranet Controller to connect to the Infranet Enforcer: 1. From the left navigation bar in the Infranet Controller admin console, select UAC > Infranet Enforcer > Connection. 2. Click New Enforcer. By default, the new ScreenOS Enforcer page appears. 3. Enter an NACN password for this Infranet Enforcer in the NACN password box. You must enter this same NACN password when configuring the Infranet Enforcer. 4. Enter the administrator name and password for signing into the Infranet Enforcer in the appropriate boxes. 5. Enter the serial number(s) of the Infranet Enforcer. You can view the serial number on the Home page of the Infranet Enforcer WebUI, or by entering the following Juniper Networks ScreenOS CLI command: get system. 6. Select No 802.1X from the Location Group list if you are not using an Infranet Enforcer as an 802.1X RADIUS client of the Infranet Controller. This is the typical setting. 7. Click Save Changes. 16
35 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control When you finish configuring the Infranet Enforcer, the Infranet Enforcer attempts to connect to the Infranet Controller. If the connection is successful, a green dot appears next to the Infranet Enforcer icon under Enforcer Status in System > Status > Overview in the Infranet Controller admin console. The Infranet Enforcer IP address also appears in UAC > Infranet Enforcer > Connection. Related Topics Certificates on the IC Series and the Infranet Enforcer on page 7 Binding an Interface to a Security Zone on page 13 Configuring the ScreenOS Enforcer on page 15 Setting up an Infranet Enforcer in Route Mode It is possible to have the Infranet Controller reside on either side of the Infranet Enforcer. If the Infranet Controller resides on the trust interface side, and users come in through the untrust interface, the administrator must configure a policy (untrust to trust) on the Infranet Enforcer that allows traffic to pass between the Infranet Controller and Odyssey Access Client or Junos Pulse. Infranet Enforcer traffic from the untrust interface to the trust interface is denied by default. This example explains the setup with the Infranet Controller on the untrust interface side (same side as end users). To configure an Infranet Enforcer in Route mode: 1. Set up the trust interface. The trust interface connects to the protected resource(s).the untrust interface connects to the Infranet Controller. Set the following interface (that is, ethernet1/1) settings: Set routing. Enable management of the following services: SSL SSH IP (optionsl) 2. Ensure that the DHCP server is disabled or enabled as desired for the deployment. 17
36 Using the Infranet Controller with the ScreenOS Enforcer 3. Import the certificate of the CA (Certificate Authority) that signed the Infranet Controller s server certificate into the Infranet Enforcer. a. If you set up an NSRP cluster before importing the CA certificate into the Infranet Enforcer, the CA certificate is automatically synchronized to all Infranet Enforcers in the cluster. However, if you set up the NSRP cluster after importing the CA certificate, you must manually synchronize the certificate to the other Infranet Enforcers in the cluster by using the following CLI command: exec nsrp sync pki You cannot load the self-signed Infranet Controller SSL certificate into the Juniper Networks security device. For more information about certificates and certificate options, see the Concepts & Examples ScreenOS Reference Guide: Volume 5, VPNs. The certificate of the CA that signed the Infranet Controller s certificate must be imported on the Infranet Enforcer because the Infranet Enforcer must be able to trust the Infranet Controller during an SSL session. When you, as a user, sign into a server by means of SSL, the server displays a dialog box where you can manually choose to accept the certificate that is associated with that server. For the Infranet Enforcer to skip that manual step and automatically accept the Infranet Controller s certificate, the Infranet Enforcer must have the certificate of the CA that signed the Infranet Controller s certificate. 4. Create an instance of the Infranet Controller on the Juniper Networks security device. 5. Enable SSH. 6. Verify routing from the Infranet Controller to the untrust interface. 7. Ensure that both the Infranet Enforcer and the Infranet Controller have the correct time. If possible, use a Network Time Protocol (NTP) Server to set the date and time of both appliances. Related Topics Creating a Route Mode Instance with the ScreenOS Enforcer on page 18 Creating a Route Mode Instance with the ScreenOS Enforcer Before you begin this procedure, you must possess the certificate of the CA that signed the Infranet Controller s server certificate or generate a self-signed CA if you do not already have an authentic CA from a trusted source. After you achieve connectivity to the Juniper Networks security device and set interface management options, you can create an Infranet Controller instance. You need to name the instance and set these items: IP address or host name of the Infranet Controller Password that will be used when the Infranet Enforcer uses NACN to contact the Infranet Controller Source interface CA index number (ca-idx) 18
37 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control You can set these items in the WebUI or through the CLI. Because the Juniper Networks security device can store more than one Infranet Controller instance, you need to include the name of the Infranet Controller with each command. In the following example, you first set interface management options and disable the DCHP server option. Then you enable SSHv2 and configure an Infranet Controller instance named controller1. Next, you set the host IP address, which is the IP address of the Infranet Controller, to The NACN password is 8!JsP37cK9a*_HiEwe. The NACN password must match the NACN password that you entered for the Infranet Controller. The source-interface is the interface that the Infranet Enforcer uses to communicate with the Infranet Controller, and the CA index number is 001. For this example, the source interface is ethernet 1/1. You can retrieve a descriptive list of CA index numbers by entering the following in the ScreenOS CLI: get ssl ca-list You must use the WebUI to import the CA. For more information about certificates, see the Concepts & Examples ScreenOS Reference Guide: Volume 5, VPNs. If you need to change SSH versions, you will need to use the CLI to delete SSH settings with the following command: delete ssh device all When using the WebUI, you do not need to fill in the Full Subject Name of IC Cert field. But, if you do fill it in, be sure to enter the entire certificate subject. For example: CN=ic1.juniper.net,CN= ,CN= ,OU=Software,O=Juniper,S=CA, C=US After creating the Infranet Controller instance, you need to set the Infranet Controller with the serial number of the Infranet Enforcer. To view the serial number of the system, look at the Device Information pane on the home page of the WebUI or enter the following command in the CLI: get system WebUI To use the WebUI: 1. Select Network > Interfaces > Edit >Services from the left navigation bar to set management options. 2. Select Network > DHCP > Edit to disable the DHCP server for both interfaces (Trust and Untrust). 3. Select and load the Certificate Authority if you have not already done so. a. Select Objects > Certificates. b. Click Browse to find and select the certificate and click Load. c. Select CA from the show list. 19
38 Using the Infranet Controller with the ScreenOS Enforcer d. Click on Server Settings and make sure Check Method is set correctly for the certificate you are using. e. Click OK. 4. Create the Infranet Controller instance. a. Select Configuration > Infranet Auth > Controllers (List) > New. b. Type controller1 in the Infranet Controller instance box. c. Type IP/domain name: in the IP/Domain Name box. d. For the NACN Parameters select ethernet1/1 from the Source Interface list. e. Type 8!JsP37cK9a*_HiEwe in the Password box. f. Select the CA from the Selected CA list. 5. Enable SSH version 2. a. Select Configuration > Admin > Management > Enable SSH (v2). Related Topics Configuring the ScreenOS Connection on page 16 CLI To use the CLI: 1. Enter the following commands: set interface ethernet1/1 manage ssl set interface ethernet1/1 manage ssh set interface ethernet1/1 manage ip set interface ethernet2/1manage ping set interface ethernet2/1 dhcp server disable set interface ethernet1/1 dhcp server disable delete ssh device all set ssh version v2 set ssh enable set infranet controller name controller1 host-name set infranet controller name controller1 password 8!JsP37cK9a*_HiEwe set infranet controller name controller1 src-interface ethernet1/1 set infranet controller name controller1 ca-idx 001 save Related Topics Viewing the Configuration of an IC Series Device on the ScreenOS Enforcer on page 23 20
39 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control Setting up an Infranet Enforcer in Transparent Mode In Transparent mode, the Juniper Networks security device is usually installed between a core router and an access distribution device. Services are enabled at the zone level and VLAN1 is used for management. Transparent mode permits you to implement the following functionality: The device can act as a Layer-2 forwarding device, such as a bridge. You can control traffic flow between Layer-2 security zones through policies. To configure a ScreenOS Enforcer in Transparent mode: 1. Set up Transparent mode using the predefined security zones, v1-trust and v1- untrust. a. Assign interfaces to v1-trust and v1-untrust as appropriate. b. Configure the IP address for a source interface to establish connectivity with the Infranet Controller. You can use V1-trust, V1-untrust or V1-dmz. c. Configure the broadcast mechanism to flooding (default) or ARP/traceroute. ARP/trace-route is more secure than broadcast. d. Enable management of the following services for VLAN1: SSL SSH Web (optional) 2. Set up the Juniper Networks security device zones. The protected resources can be in either zone (v1-trust or v1-untrust), as long as the protected resources are in a zone different from the endpoints. The Infranet Controller can also reside in either zone. If the Infranet Controller resides in a zone different from the endpoints, configure a policy that allows traffic to the endpoints through the ScreenOS Enforcer. 3. Import the certificate of the CA that signed the Infranet Controller s server certificate into the ScreenOS Enforcer. Do not import the Infranet Controller SSL certificate into the Juniper Networks security device. For more information about certificates and certificate options, see the Concepts & Examples ScreenOS Reference Guide: Volume 5, VPNs. The certificate of the CA that signed the Infranet Controller s certificate must be imported on the ScreenOS Enforcer because the Infranet Enforcer must be able to trust the Infranet Controller during an SSL session. When you, as a user, sign into a server by means of SSL, the server displays a dialog box where you can manually choose to accept the certificate that is associated with that server. For the ScreenOS Enforcer to skip that manual step and automatically accept the Infranet Controller s 21
40 Using the Infranet Controller with the ScreenOS Enforcer certificate, the ScreenOS Enforcer must have the certificate of the CA that signed the Infranet Controller s certificate. 4. Create an instance of the Infranet Controller on the ScreenOS Enforcer. 5. Enable SSH. 6. Verify routing from the Infranet Controller to the V1-untrust zone. If you want to use IPsec enforcement with a ScreenOS Enforcer in Transparent mode, you may need to configure a source interface policy on the Infranet Controller. 7. Ensure that both the Infranet Enforcer and the Infranet Controller have the correct time. If possible, use a Network Time Protocol (NTP) Server to set the date and time of both appliances. Related Topics Creating a Transparent Mode Instance with the ScreenOS Enforcer on page 22 Viewing the Configuration of an IC Series Device on the ScreenOS Enforcer on page 23 Creating a Transparent Mode Instance with the ScreenOS Enforcer To create an Infranet Controller instance in transparent mode use the CLI to perform the following actions: Assign all interfaces to Layer 2 zones. Assign an IP address to vlan1 and set the route command. Set interface management options. Configure an Infranet Controller instance named controller1. Set the host IP address, which is the IP address of the Infranet Controller, to Enter the NACN password. The NACN password is 8!JsP37cK9a*_HiEwe. The NACN password must match the NACN password that you entered for the Infranet Controller. The source-interface, vlan1, is the interface that the Infranet Enforcer uses to communicate with the Infranet Controller; and the CA index number is 001.You can retrieve a descriptive list of CA index numbers by entering the following: get ssl ca-list You must use the WebUI to import the CA. 22
41 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control CLI To use the CLI: 1. Enter the following commands: NOTE: For the firewall to operate in Transparent (Layer 2) mode, all interfaces must be in a Layer 2 zone, such as v1-trust or in the null zone. Interfaces cannot remain in a Layer 3 zone. set interface eth1 zone v1-trust set interface eth2 zone v1-untrust set interface vlan1 ip x set interface vlan1 route set interface vlan1 ip manageable unset interface vlan1 manage ping unset interface vlan1 manage telnet unset interface vlan1 manage snmp unset interface vlan1 manage web set infranet controller name controller1 host-name set infranet controller name controller1 password 8!JsP37cK9a*_HiEwe set infranet controller name controller1 src-interface vlan1 set infranet controller name controller1 ca-idx 0001 Related Topics Configuring the ScreenOS Enforcer on page 15Configuring the ScreenOS Connection on page 16 Setting up an Infranet Enforcer in Transparent Mode on page 21 Viewing the Configuration of an IC Series Device on the ScreenOS Enforcer You can view the configuration of an Infranet Controller instance through the WebUI and the CLI. You can view the following information: Name of the Infranet Controller instance IP address or domain name of the Infranet Controller Port number (should always be 11122) Timeout (60 seconds by default) Source interface The WebUI also allows you to view the NACN password 23
42 Using the Infranet Controller with the ScreenOS Enforcer WebUI Select the following on the WebUI: 1. Select Configuration > Infranet Auth > Controllers from the left navigation bar. 2. Select Configuration > Infranet Auth > General Settings from the left navigation bar. CLI Use the following command: 1. get infranet controller name controller1 Related Topics Setting up an Infranet Enforcer in Route Mode on page 17 Setting up an Infranet Enforcer in Transparent Mode on page 21 Related Topics Configuring the ScreenOS Enforcer on page 15 Captive Portal on the Infranet Enforcer When you deploy the Infranet Controller and Infranet Enforcer, users may not know that they must first sign into the Infranet Controller for authentication and endpoint security checking before they are allowed to access a protected resource behind the Infranet Enforcer. To help users sign into the Infranet Controller, you can configure a redirect infranet auth policy in the ScreenOS Enforcer, or a security policy on the Junos Enforcer to automatically redirect HTTP traffic destined for protected resources to the Infranet Controller. When the sign-in page for the Infranet Controller appears, the user signs in and Host Checker for Odyssey Access Client or Junos Pulse or agentless Host Checker examines the endpoint for compliance to security policies, and if the endpoint passes the security check, access is granted to the protected resource. This Infranet Enforcer feature is called a captive portal. You can configure a captive portal for endpoint clients that use either source IP enforcement or IPsec enforcement, or a combination of both enforcement methods. Figure 2 on page 25 illustrates the sequence of events when a user attempts to access protected resources with captive portal configured. 24
43 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control Figure 2: Captive Portal Captive portal enables an endpoint to be redirected to a to a different URL when the user attempts to access a protected resource behind an Infranet Enforcer, provided the appropriate access policies are configured on the security device. By default, users are not redirected if captive portal is not configured for a policy. Related Topics Before Configuring Captive Portal on page 25 Creating a Redirect Policy on the Infranet Enforcer on page 26 Overriding the Default Redirection Destination for Captive Portal on page 28 Configuring a New Redirection Destination for Captive Portal on page 29 Before Configuring Captive Portal Topic Details ScreenOS Version The captive portal feature requires ScreenOS release 5.4 or later running on the ScreenOS Enforcer. Junos Version To use captive portal with the Junos Enforcer, version 10.2 is required. External Web Server You can configure the ScreenOS Enforcer to redirect HTTP traffic to an external Web server instead of the Infranet Controller. For example, you can redirect HTTP traffic to a Web page that explains to users the requirement to sign into the Infranet Controller before they can access the protected resource. For example, you could explain your security policy and include a link to the Infranet Controller on that Web page to help users sign in. 25
44 Using the Infranet Controller with the ScreenOS Enforcer HTTP vs. HTTPS The captive portal feature redirects HTTP traffic only. If the user attempts to access a protected resource using HTTPS or another protocol such as SMTP, the Infranet Enforcer does not redirect the user s traffic. When using HTTPS or another application, the user must manually sign into the Infranet Controller first before attempting to access protected resources. HTTP Proxy If there is an HTTP proxy between the endpoint and the Infranet Enforcer, the Infranet Enforcer might not redirect the HTTP traffic. Default Port In standard configurations, ScreenOS uses default HTTP ports as the redirection destination port for traffic. In addition to default http ports, non-standard HTTP port 3128 is defined for HTTP-EXT traffic to accommodate the SQUID proxy. With the Junos Enforcer, only port 80 is supported. Creating a Redirect Policy on the Infranet Enforcer To configure the captive portal feature you must create special policies on the Infranet Enforcer. On the Junos Enforcer, you configure a security policy using the CLI. On the ScreenOS Enforcer, you can configure an infranet-auth policy through either the WebUI or the CLI. When you configure a policy for captive portal, you can choose to redirect all traffic, or only unauthenticated traffic. unauthenticated Select this option if your deployment uses source IP only, or a combination of source IP and IPsec. The Junos Enforcer redirects clear-text traffic from unauthenticated users to the currently connected Infranet Controller, or to an IP address or domain name that you specify in a redirect URL. After a user signs in to the Infranet Controller and the user s endpoint system meets the requirements of the Infranet Controller s security policies, the Junos Enforcer allows the user s clear-text traffic to pass through in source IP deployments. For IPsec deployments, the Odyssey Access Client or Junos Pulse creates a VPN tunnel between the user and the Junos Enforcer. The Junos Enforcer then applies the VPN policy allowing the encrypted traffic to pass through. all With the ScreenOS Enforcer, select this option if your deployment uses IPsec only. The ScreenOS Enforcer redirects all clear-text traffic to the currently connected Infranet Controller, or to an IP address or domain name that you specify in a redirect URL. After a user signs in to the Infranet Controller, Odyssey Access Client or Junos Pulse creates a VPN tunnel between the user and the Junos Enforcer. The Junos Enforcer then applies the VPN policy allowing the user s encrypted traffic to pass through. This option does not allow clear text traffic to pass through the Junos Enforcer, which protects your network from IP spoofing. Junos CLI You enable captive portal by associating an instance of a captive portal with a security zone using the following: 26
45 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control set security policies from-zone zone-name to-zone zone-name policy policy-name You create the captive portal using the following: permit application-services uac-policy captive-portal captive-portal-name On the Junos Enforcer you can redirect all traffic, or only unauthenticated traffic using the following: edit services unified-access-control captive-portal policy redirect-traffic (all unauthenticated) ScreenOS WebUI To create a redirect infranet-auth policy on the ScreenOS Enforcer: 1. Click Policies from the left navigation bar. 2. Select a source zone from the From list. 3. Select a destination zone from the To list. 4. Click New. The advanced Policy Settings page appears. 5. Enter the policy configuration information such as source and destination addresses. (See the ScreenOS Enforcer WebUI online Help for more details about the policy configuration options.) 6. Click Advanced. 7. Select Authentication and then select Infranet-Auth. 8. Specify a redirection option for the infranet-auth policy: Redirect unauthenticated traffic Redirect all traffic 9. Optionally, type a Redirect URL to specify where matching traffic should be redirected. 10. Click OK. 11. Click OK. You can permit more versatile redirect support on a per-policy basis. If your ScreenOS Enforcer connects to different Infranet Controllers (though only one at a time can communicate), you can configure the URL for each redirect policy. If a policy-based URL is defined and redirect is enabled in the policy, unauthenticated HTTP traffic that matches the policy will be redirected to that URL even if a global redirect URL is configured. If policy-based URL redirect is not defined and redirect is enabled, unauthenticated traffic that matches the policy will be redirected to the global redirect. ScreenOS CLI To configure a redirect infranet-auth policy for deployments that use source IP only, or a combination of source IP and IPsec enter: set policy from source-zone to dest-zone src_addr dst_addr any permit infranet-auth redirect-unauthenticated To configure a redirect infranet-auth policy for deployments that use IPsec only enter: 27
46 Using the Infranet Controller with the ScreenOS Enforcer set policy from source-zone to dest-zone src_addr dst_addr any permit infranet-auth redirect-all Overriding the Default Redirection Destination for Captive Portal By default, after you configure a redirect infranet-auth policy (for ScreenOS), the Infranet Enforcer redirects HTTP traffic to the currently connected Infranet Controller using HTTPS. To perform the redirection, the Infranet Enforcer uses the IP address or domain name that you specified when you configured the Infranet Controller instance on the Infranet Enforcer. The format of the URL that the ScreenOS Enforcer uses for default redirection is: Infranet Controller IP or domain name>/?target=%dest-url% If you configured your ScreenOS Enforcer to work with multiple Infranet Controllers in a cluster, and the current Infranet Controller becomes disconnected, the ScreenOS Enforcer automatically redirects HTTP traffic to the next active Infranet Controller in its configuration list. The ScreenOS Enforcer redirects traffic to only one Infranet Controller at a time. The Infranet Controller domain name that you specify when configuring the Infranet Controller instance in the ScreenOS Enforcer must match the Infranet Controller domain name in the Web browser certificate that is used when users sign in. Otherwise, the browser displays a certificate warning to users when they sign in. You do not need to override the default redirection destination except in these situations: You are using a VIP for a cluster of Infranet Controller appliances and the ScreenOS Enforcer is configured to connect to the Infranet Controller s physical IP addresses. You want to redirect traffic to a Web server instead of the Infranet Controller. If, because of split DNS or IP routing restrictions at your site, the ScreenOS Enforcer uses a different address for the Infranet Controller than endpoints, you must specify the domain name or IP address that endpoints must use to access the Infranet Controller. By default, the ScreenOS Enforcer also encodes and forwards to the Infranet Controller the protected resource URL that the user entered. The Infranet Controller uses the protected resource URL to help users navigate to the protected resource. The manner in which the Infranet Controller uses the protected resource URL depends on whether or not the user s endpoint is running Odyssey Access Client or Junos Pulse: If the user s endpoint is not running Odyssey Access Client or Junos Pulse (that is, it is in an agentless or Java agent configuration), the Infranet Controller automatically opens a new browser window and uses HTTP to access the protected resource after the user signs in. If the endpoint is using Odyssey Access Client or Junos Pulse, the Infranet Controller inserts a hypertext link in the Web page that automatically opens after the user signs in. The user must then click that hypertext link to access the protected resource by means of HTTP in the same browser window. 28
47 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control Configuring a New Redirection Destination for Captive Portal To override the default redirection destination you must configure policies on the Infranet Enforcer. On the Junos Enforcer, you configure a redirect url policy using the CLI. On the ScreenOS Enforcer, you can configure an infranet-auth policy through either the WebUI or the CLI. Junos CLI You specify the redirect url in a Junos Enforcer security policy using the following hierarchy: user@host# set services unified-access-control captive-portal policy redirect-url url You can configure the following options in the redirect URL string: %dest-url% Specifies the protected resource which the user is trying to access. %enforcer-id% Specifies the ID assigned to the Junos Enforcer by the Infranet Controller. %policy-id% Specifies the encrypted policy ID for the security policy that redirected the traffic. %dest-ip% Specifies the IP address or hostname of the protected resource which the user is trying to access. %ic-ip% IP address or hostname of the Infranet Controller to which the Junos Enforcer is currently connected to. If you do not specify the redirect URL, the Junos Enforcer uses the default configuration. NOTE: To set a redirect URL for the Junos Enforcer, you must use escape characters instead of dot (.). For example: For configuration instructions and examples, see the Junos Software Security Configuration Guide. ScreenOS WebUI 1. Select Configuration > Infranet Auth > Controllers > Edit from the left navigation bar. 2. In the Redirect URL box specify the IP address or domain name of the Infranet Controller or external Web server using HTTP or HTTPS in the following format: or domain name>/<url path>/?target=%dest-url% For example, to redirect to an Infranet Controller and forward the protected resource URL, enter: To redirect to a Web server and forward the protected resource URL enter: 29
48 Using the Infranet Controller with the ScreenOS Enforcer The ScreenOS Enforcer replaces the %dest-url% parameter with the protected resource URL, and then forwards the protected resource URL in encrypted form to the Infranet Controller. NOTE: In the Redirect URL string, you can omit the?target=%dest-url% string. For example: If you do not include the?target=%dest-url% string, the user must manually open a new browser window and enter the protected resource URL again after signing in. ScreenOS CLI 1. To specify the redirect URL, enter: set infranet controller name controller1 url " 2. To specify the redirect URL without the?target=%dest-url% string, enter: set infranet controller name controller1 url Non-standard Ports With ScreenOS 6.3, HTTP traffic on any port is supported with captive portal. To use this feature, you must define a new service on ScreenOS, and use the service in an infranet auth policy. You define the service with the destination port/ports on which HTTP is running. Select this service in the infranet auth policy, and associate it with application HTTP. For unauthenticated HTTP traffic on the port specified in the service, ScreenOS redirects the traffic to the URL that is mentioned in the Inranet Controller configuration or that is mentioned in the Redirect URL field of the infranet-auth policy. To configure an alternative port for redirct: WebUI 1. Create a new service in ScreenOS. 2. Create an infranet auth policy and select DSTA-HTTP (or the name you are using when you create the service) as the service in the infranet auth policy. 3. Set the application as HTTP for the policy. CLI set service DSTA-HTTP protocol tcp dst-port set policy id 1 from trust to untrust any any DSTA-HTTP permit infranet-auth redirect-unauthenticated 30
49 Chapter 1: Configuring the ScreenOS Enforcer to Interoperate with Unified Access Control set policy id 1 application HTTP For unauthenticated HTTP traffic on the specified port, ScreenOS redirects the traffic to the URL that is specified in the Infranet Controller configuration, or that is mentioned in the Redirect URL field of the infranet auth polcy. If non-standard ports are not used in the infranet auth policy, behavior will be the same as in ScreenOS 6.2. Related Topics Captive Portal on the Infranet Enforcer on page 24 Before Configuring Captive Portal on page 25 Using VSYS on the ScreenOS Enforcer You can logically partition a single ScreenOS Enforcer into multiple virtual systems (VSYS) to provide multi-tenant services. Each VSYS is a unique security domain and can have its own administrator. VSYS is supported on ISG-1000, ISG-2000, and NS series ScreenOS Enforcers. VSYS support on the Infranet Controller allows you to provision different auth table entries and resource access policies on discrete virtual systems on the same firewall. You can also choose a virtual system for ScreenOS infranet-auth policies and VPN objects. When you add a VSYS to a ScreenOS Enforcer with the appropriate CLI commands, the virtual system appears as an Infranet Enforcer on the Infranet Controller. See Concepts and Examples ScreenOS Reference Guide Volume 10: Virtual Systems. From the perspective of the Infranet Controller, the virtual system appears as a stand-alone firewall device. You configure policies on the virtual system just as if you were configuring policies for a separate firewall. For resource access policies and auth table policies, you type the name of a vsys in the provided field. For Enforcer policies, you select the VSYS from a pull-down menu. This is because resource access policies and auth table policies can be distributed to multiple ScreenOS Enforcers, while Enforcer policies apply to only one ScreenOS Enforcer. Virtual systems do not inherit resource access policies or auth table policies from the root-vsys (the ScreenOS Enforcer on which the vsys is created). If you have a resource access policy or auth table policy configured for an existing ScreenOS Enforcer, and subsequently create one or more VSYS, you need to add new policies for the vsys if you want to allow users to access resources behind the VSYS. If you enable command tracing in the event log, the command exec-bulkcli appears in the log for vsys events. You can configure multiple VSYS with no shared zones, or you can configure different VSYS to share a common zone. For example, you could configure all endpoints to be on the untrust zone connecting to multiple VSYS on different zones. IPsec is not supported with a shared zone configuration. See Figure 3 on page 32 VSYS support on the Infranet Controller requires ScreenOS 6.2 or greater. 31
50 Using the Infranet Controller with the ScreenOS Enforcer Figure 3: Multiple VSYS with Shared and Unshared Zones When a ScreenOS Enforcer with version 6.2 or greater and the appropriate VSYS licensing connects to the Infranet Controller, the Infranet Controller automatically issues a command to the firewall to enable UAC support for VSYS in ScreenOS Enforcers. Individual configuration details of ScreenOS policies with VSYS is explained in the applicable policy sections. Related Topics Configuring the ScreenOS Enforcer on page 15 32
51 CHAPTER 2 Using IPsec IPsec and the UAC Infranet Enforcer IPsec and the UAC Infranet Enforcer on page 33 How this Section is Organized on page 34 IPsec Policies on page 35 Using IPsec with the Infranet Enforcer on page 35 IPsec Enforcement on the Infranet Enforcer on page 36 Before Configuring IPsec on page 37 Configuring Basic IPsec Policies for the ScreenOS Enforcer on the IC Series on page 39 IPsec Routing Policices on page 40 Before you Begin on page 41 Configuring an IPsec Routing Policy on page 41 IP Address Pool Policies for IPsec in a NAT Environment on page 43 IP Address Pool Policies on page 45 Configuring an IP Address Pool Policy on page 46 Source Interface Policies for the ScreenOS Enforcer on page 47 Configuring Source Interface Policies on page 48 Upgrading IPsec Enforcement Policies from Version 1.x of the Infranet Controller on page 49 Setting up IPsec Enforcement on the ScreenOS Enforcer on page 49 Configuring the IPsec Encryption Settings on the ScreenOS Enforcer on page 50 Bidirectional VPN Policies on the ScreenOS Enforcer on page 51 Creating a Bidirectional VPN Policy on page 51 Junos Enforcer IPsec Configuration on page 52 IP Security (IPsec) is a suite of related protocols for cryptographically securing communications at the IP Packet Layer. IPsec also provides methods for the manual and automatic negotiation of security associations (SAs) and key distribution. 33
52 Using the Infranet Controller with the ScreenOS Enforcer An IPsec tunnel consists of a pair of unidirectional SAs one at each end of the tunnel that specify the security parameter index (SPI), destination IP address, and security protocol. In a dial-up VPN, there is no tunnel gateway on the VPN dial-up client end of the tunnel; the tunnel extends directly to the client itself. Odyssey Access Client and Junos Pulse support IPsec using IKEv1 with XAuth. For the client to establish an IPsec tunnel, it must retrieve configuration information from the Infranet Enforcer. This information is forwarded to The Infranet Controller by the respective device. When a user with Odyssey Access Client or Junos Pulse signs in to the Infranet Controller, these configuration details are passed on to the client to establish an IPsec tunnel with the Infranet Enforcer. IPsec is supported on both the ScreenOS Enforcer and the Junos Enforcer (beginning in version 10.0). You configure IPsec routing policies and IP address pool policies on the Infranet Controller. For the ScreenOS Enforcer, you can configure basic IPsec policies on the Infranet Controller and then push the policies to the device. You configure security policies on the Junos Enforcer. IPsec policies allow you to specify the parameters for SAs between endpoints and the Infranet Enforcer. This chapter contains information about both the Junos Enforcer and the ScreenOS Enforcer. Related Topics How the IC Series and UAC Enforcer Work Together on page 4 IPsec Policies on page 35 IPsec Enforcement on the Infranet Enforcer on page 36 How this Section is Organized To set up IPsec for endpoints with Odyssey Access Client or Junos Pulse, you configure policies on the Infranet Controller, and on the security device. The Infranet Controller pushes the required IPsec configuration parameters to the client when the client first attempts to connect to a protected resource behind and Infranet Controller for which IPsec has been configured. All of the configuration details that are performed on the Infranet Controller are presented first in this chapter. Items that you configure on the ScreenOS Enforcer and the Junos Enforcer are detailed in respective sections. Related Topics Using IPsec with the Infranet Enforcer on page 35 Setting up IPsec Enforcement on the ScreenOS Enforcer on page 49 Junos Enforcer IPsec Configuration on page 52 34
53 Chapter 2: Using IPsec IPsec Policies This section details the policies that you configure in association with using IPsec on the Infranet Enforcer. IPsec Routing Policy This type of policy specifies which Infranet Enforcer an endpoint must use to access a resource. This policy also specifies whether that resource requires an IPsec tunnel for endpoints to access it. Note that an IPsec tunnel does not automatically give the endpoint access. You configure IPsec routing policies on the Infranet Controller. ScreenOS Infranet Auth IPsec Policy An IPsec policy contains the source and destination. The Infranet Controller uses the source and destination to set up a user, user group, IKE gateway, and VPN for each source interface in the source zone of the policy. You can set up a basic ScreenOS IPsec policy on the Infranet Controller and push the policy to the ScreenOS Enforcer, or you can set up the policy using ScreenOS WebUI or the command line. IP Address Pools Policy This type of policy specifies a pool of virtual IP addresses that you want the Infranet Controller to automatically assign to endpoints in NAT environments that use IPsec tunnels to the Infranet Enforcer. You configure IP address pools policies on the Infranet Controller. ScreenOS Source Interface Policy This type of policy specifies the source interface on the ScreenOS Enforcer that receives traffic from endpoints if the ScreenOS Enforcer is in Transparent mode. You create this type of policy only if you want endpoints to use IPsec to communicate with a ScreenOS Enforcer that is in Transparent mode, and you are using virtual routers. You configure source interface policies on the Infranet Controller. Junos Enforcer Security Policy On the Junos Enforcer, security policies are used to define the source and destination address, the application, and the phase 2 policy. You configure security policies on the Junos Enforcer. You cannot configure security policies on the Infranet Controller. Related Topics Using IPsec with the Infranet Enforcer on page 35 Setting up IPsec Enforcement on the ScreenOS Enforcer on page 49 Configuring the IPsec Encryption Settings on the ScreenOS Enforcer on page 50 IPsec Enforcement on the Infranet Enforcer on page 36 Before Configuring IPsec on page 37 Using IPsec with the Infranet Enforcer On supported endpoints that use Odyssey Access Client or Junos Pulse, you can use IPsec enforcement to encrypt the traffic between an endpoint and the ScreenOS Enforcer, adding an additional layer of protection for network assets. 35
54 Using the Infranet Controller with the ScreenOS Enforcer IPsec is not supported on agentless or Java agent endpoints. or on endpoints that connect with non-uac software. Instead, you must use source IP enforcement for these clients. To use IPsec enforcement, you set up a VPN tunnel with IKE (Internet Key Exchange) on the Infranet Enforcer. You can configure IPsec enforcement by creating IPsec routing policies on the Infranet Controller. For IPsec on the ScreenOS Enforcer, you can create basic IPsec policies. For IPsec with the Junos Enforcer, you must create security policies on the device. Alternately, you can manually set up the VPN tunnel using ScreenOS CLI commands or WebUI. Juniper Networks recommends that you use the Infranet Controller to set up basic VPN policies on the Infranet Enforcer. If necessary, you can modify the VPN tunnel setup afterwards on the Infranet Enforcer by using ScreenOS CLI commands or WebUI. If you modify the VPN tunnel setup on the Infranet Enforcer by using the ScreenOS CLI commands or WebUI, you must refresh the policies on the Infranet Controller. When you use the Infranet Controller to configure IPsec on the ScreenOS Enforcer, the Infranet Controller sets up a user, user group, IKE gateway, and VPN for each source interface in the source zone of the policy in addition to the policy itself. The Infranet Controller uses the source interface number and the ID of the destination zone to uniquely name each of these objects. For IPsec with the Junos Enforcer you use the CLI to create security policies. With the Junos Enforcer, the Infranet Controller uses the destination zone to match the IPsec Routing policies configured on the Infranet Controller. Related Topics Setting up IPsec Enforcement on the ScreenOS Enforcer on page 49 Junos Enforcer IPsec Configuration on page 52 IPsec Enforcement on the Infranet Enforcer This section details the tasks required to configure IPsec on the Infranet Controller. Depending on the version of ScreenOS you are using, the steps for configuring IPsec differs. If you are using a ScreenOS version prior to 6.1, you configure ScreenOS IPsec policies and an IPsec routing policy for each resource that you wish to protect. With ScreenOS version 6.1 or later the Infranet Controller can dynamically provision IPsec routing policies for you, eliminating the need to configure a separate policy for each resource. The Infranet Controller initially queries all connected Infranet Enforcers for version information. If ScreenOS version 6.1 or greater is detected, the Infranet Controller initiates a command to enable dynamic provisioning. When an authenticated endpoint without an auth table entry attempts to access a resource through the Infranet Enforcer, the Infranet Enforcer sends a message to the Infranet Controller including the source and destination IP, the source interface the 36
55 Chapter 2: Using IPsec dropped packet was received on, and the ID of the Enforcer policy associated with the resource. Refreshing IPsec Policies on the IC Series This information allows the Infranet Controller to negotiate an IPsec tunnel between the endpoint and the Infranet Enforcer and provision a dynamic IPsec routing policy. Odyssey Access Client or Junos Pulse must be running on the endpoint to use IPsec. IPsec is not supported on agentless endpoints, or on endpoints with the Java agent. On all other platforms, such as Linux and Solaris, or Windows and Macintosh machines that connect using a non-uac client, you must use source IP enforcement by setting up a source-based policy on the Infranet Enforcer. For more information. IPsec is optional. Instead of IPsec, you can use source IP enforcement for endpoints. Source IP enforcement allows the endpoint to communicate with unencrypted traffic. If you upgraded your Infranet Controller from a version 1.x to 2.0 or later, be aware that the Infranet Controller does not automatically upgrade any previously configured IPsec enforcement policies. You must manually reconfigure all IPsec enforcement policies. Each time the Infranet Enforcer and Infranet Controller establish a new connection with each other, the Infranet Controller queries the Infranet Enforcer for policy information, which it uses for provisioning IPsec to endpoints. If you modify the IPsec policies on the Infranet Enforcer while the Infranet Enforcer is connected to the Infranet Controller, you must refresh the policies on the Infranet Controller because the Infranet Controller does not automatically detect changes to Infranet Enforcer policies that occur while the Infranet Enforcer is connected. If you don t refresh the policies, the Infranet Controller continues to use the older policies until the next time the Infranet Controller disconnects and reconnects to the Infranet Enforcer. Related Topics Configuring Basic IPsec Policies for the ScreenOS Enforcer on the IC Series on page 39 Setting up IPsec Enforcement on the ScreenOS Enforcer on page 49 Junos Enforcer IPsec Configuration on page 52 Before Configuring IPsec Topic Details Connection The Infranet Enforcer and the Infranet Controller must be connected before you use the Infranet Controller to set up IPsec enforcement on the Infranet Enforcer. 37
56 Using the Infranet Controller with the ScreenOS Enforcer IPsec access server on ScreenOS Enforcer You cannot establish an IPsec tunnel if IAS (IPsec access server) is enabled on the ScreenOS Enforcer. To determine if IAS is enabled, enter the following command on the ScreenOS Enforcer Command Line Interface: get ipsec access_session status To turn off IAS, use the following command: unset ipsec access-session enable. See the Concepts & Examples ScreenOS Reference Guide, which you can download from for details of this functionality. Multiple interfaces If you configure IPsec enforcement for an Infranet Enforcer that has multiple interfaces in the source zone, the Infranet Controller configures a unique IKE gateway, VPN, and tunnel policy for each interface. To distinguish between the tunnel policies, the Infranet Controller displays the name of the vpn for each tunnel policy in the VPN column on the UAC > Infranet Enforcer > Enforcer Policies page after you click Save Changes. Dynamic IPsec routing policies If you are using ScreenOS version 6.1 or higher you can configure the Infranet Enforcer to dynamically provision IPsec routing policies. To implement this feature, you create a ScreenOS source IP policy with a source and destination zone that matches the ScreenOS IPsec policy. Then, you configure captive portal for the source IP policy. Dynamic IPsec routing policies are not supported on the Junos Enforcer. Default encryption settings on the ScreenOS Enforcer When you use the Infranet Controller to configure IPsec on the Infranet Enforcer, the Infranet Controller creates an IPsec policy that uses these default IPsec encryption settings: NoPFS, ESP, 3DES, and SHA1 You can, however, change the phase 2 proposal on the Infranet Enforcer by using the CLI or Web UI. Bi-directional VPN policy If you need to connect from a computer inside the protected network back to the endpoint, you can create a bidirectional VPN policy on the Infranet Enforcer. CLI commands To include the CLI commands that the Infranet Controller sends to the Infranet Enforcer in the Infranet Controller event logs, select the Enforcer Command Trace option on the System > Log/Monitoring > Events > Settings page. Junos Enforcer zone limitation On the Junos Enforcer, only one IPsec vpn tunnel per from-zone to to-zone is supported. Troubleshooting To troubleshoot your IPsec configuration, you can view the Event logs on the Infranet Controller. You can also view IPsec information on the endpoint by choosing Tools > Diagnostics > IPsec Diagnostics in Odyssey Access Client. Related Topics Configuring Basic IPsec Policies for the ScreenOS Enforcer on the IC Series on page 39 IPsec Routing Policices on page 40 38
57 Chapter 2: Using IPsec Setting up IPsec Enforcement on the ScreenOS Enforcer on page 49 Junos Enforcer IPsec Configuration on page 52 Configuring Basic IPsec Policies for the ScreenOS Enforcer on the IC Series NOTE: The ScreenOS Enforcer supports static and dynamic IPsec. If you are configuring IPsec with the ScreenOS Enforcer, you can create basic IPsec policies on the Infranet Controller and then push the policies to the ScreenOS Enforcer, where you can modify the policies. To configure IPsec enforcement on the ScreenOS Enforcer: 1. On the UAC > Infranet Enforcer > Connection page, select New Enforcer if you have not already configured a connection to the Infranet Enforcer on which you want to configure IPsec enforcement. 2. Select UAC > Infranet Enforcer > Connection and click the name in the Enforcer column of the Infranet Enforcer on which you want to configure IPsec enforcement. 3. On the UAC> Infranet Enforcer > Enforcer Policies page: a. Choose the source zone for the policy from the Source Zone drop-down list. The source zone is the zone where the endpoint is located. b. Choose the destination zone for the policy from the Destination Zone drop-down list. The destination zone is where the protected resources are located. c. Choose IPsec from the Type drop-down list. d. Click Add. e. Click Save Changes to save the IPsec policy. As required, the Infranet Controller sets up a VPN tunnel with IKE on the Infranet Enforcer that consists of a user, user-group, IKE gateway, and VPN for each source interface in the source zone of the policy. The Infranet Controller uses the source interface number and the ID of the destination zone to uniquely name each of these objects. 4. To configure the Infranet Controller to provision dynamic IPsec routing policies, create a new source IP policy on the Infranet Enforcer with the same source and destination zone as the ScreenOS IPsec policy and the captive portal feature configured to Redirect all traffic. 5. On the UAC > Infranet Enforcer > Resource Access page, configure Infranet Enforcer resource access policies to specify which users are allowed or denied access to a set of protected resources 39
58 Using the Infranet Controller with the ScreenOS Enforcer 6. On the UAC > Infranet Enforcer > IPsec Routing page, configure IPsec routing policies to specify which Infranet Enforcer device the endpoints must use to access each set of resources when using IPsec. 7. If you are using IPsec in a NAT environment, configure IP address pool policies on the UAC > Infranet Enforcer > IP Address Pools page. 8. If you want endpoints to use IPsec to communicate with an Infranet Enforcer that is in Transparent mode, in some cases you may need a source interface policy. 9. If you need to refresh IPsec policies, navigate to the UAC > Infranet Enforcer > Policies page and click the Refresh Policies button. Related Topics Setting up IPsec Enforcement on the ScreenOS Enforcer on page 49 IPsec Routing Policices on page 40 Setting up IPsec Enforcement on the ScreenOS Enforcer on page 49 Junos Enforcer IPsec Configuration on page 52 IPsec Routing Policices An IPsec routing policy specifies which Infranet Enforcer device endpoints must use to access resources when using IPsec. The IPsec routing policy also specifies that endpoints must use an IPsec tunnel to the Infranet Enforcer to access resources. To use IPsec with ScreenOS versions earlier than 6.1, you must configure separate IPsec routing policies for different resources that you wish to protect. IPsec routing policies are specific to the resources that you add. If you are using Screen OS 6.1 or later, you can configure one dynamic IPsec routing policy for each destination zone on each Infranet Enforcer. In IPsec routing policies with ScreenOS versions earlier than 6.1, you can specify a range of exceptions for traffic to certain resources that you do not want to use IPsec. The exceptions can fall within the ranges of resources that the Infranet Enforcer protects. In this case, if you create an exception for traffic that flows through the Infranet Enforcer, you must also create another policy on the Infranet Enforcer that allows the exception traffic to flow through. For example, you might create an IPsec routing policy that uses IPsec for /0 (the entire network). In the same policy, you could specify the resources that are exceptions and do not use IPsec, such as (the Infranet Controller), (the Infranet Enforcer), and /21 (a wireless network). With ScreenOS 6.1 or greater, there is no need for policy exceptions. Dynamic IPsec routing ensures that IPsec tunnels are created only for destinations that are governed by the ScreenOS IPsec policy. Related Topics Before you Begin on page 41 40
59 Chapter 2: Using IPsec Configuring an IPsec Routing Policy on page 41 Before you Begin Topic Details IP address exceptions Do not use IPsec for the Infranet Controller, the Infranet Enforcer, and networks where your endpoints are located. For example, if you create an IPsec routing policy that uses IPsec on an entire network range (such as /0) for your protected resources, be sure to specify exceptions in the same policy for the IP addresses assigned to Infranet Controller, Infranet Enforcer, and the endpoints. UDP encapsulation and virtual adapters For maximum inter-operability with other third-party IPsec clients, select both Always use UDP encapsulation and Always use a virtual adapter. When both options are selected, NAT is simulated even if a NAT device is not present. Juniper Networks recommends that you select both options or neither option. For example, if an endpoint contains two network interfaces, such as a wired and a wireless interface, and a NAT device is not present between the endpoint and the Infranet Enforcer. If the endpoint doesn't access a protected resource by using the interface that is connected to the network where the Infranet Enforcer is installed, then the user will not be able to access the protected resource through either interface without a virtual adapter. Because the Infranet Controller does not automatically install a virtual adapter unless a NAT device is detected, enable the Always use a virtual adapter option to simulate NAT and force the use of a virtual adapter for this use case. Related Topics Configuring an IPsec Routing Policy on page 41 IP Address Pool Policies for IPsec in a NAT Environment on page 43 Configuring an IPsec Routing Policy To configure an IPsec routing policy: 1. In the Infranet Controller admin console, select UAC > Infranet Enforcer > IPsec Routing. 2. Click New Policy. 3. On the New Policy page: a. For Name, enter a name to label this IPsec routing policy. b. For Description, enter an optional description. 4. If you are ScreenOS version 6.1 or later, and you want to configure the Infranet Controller to dynamically provision IPsec routing policies, select the Dynamic check box. The Resources and Exceptions text boxes and the Infranet Enforcer check boxes disappear. 5. Go to step 10 to continue configuring this policy for ScreenOS 6.1 or greater. 6. For Resources, enter the IP address and netmask of each resource that requires endpoints to use IPsec, one per line, in the following format: <ip address>[/netmask] 41
60 Using the Infranet Controller with the ScreenOS Enforcer You cannot specify a host name in an IPsec routing policy. You must specify an IP address. 7. For Exceptions, use the following format, one per line, to specify the IP address and netmask of each resource that has traffic which you do not want to flow through the Infranet Enforcer: <ip address>[/netmask] Each exception must be a subset of what you specify for Resources. 8. For Destination Zone, enter the zone that is configured on the Infranet Enforcer where the protected resources specified in this IPsec routing policy are located. For example: trust 9. Select these options to configure IPsec interoperability and tunnel persistence: Always use UDP encapsulation This option allows the client and the Infranet Enforcer to create an IPsec tunnel inside a third-party IPsec tunnel by using UDP encapsulation even if a NAT device is not present. For example, for inter-operability with third-party IPsec clients running on the endpoint The Infranet Controller uses port 4500 for UDP encapsulation in compliance with RFC Always use a virtual adapter This option forces the use of a virtual adapter on the endpoint. If you select this option, you must also set up IP address pools even if a NAT device is not present. For more information, Persistent Tunnel Mode This option allows you to determine whether or not a tunnel is established when a user first connects to the Infranet Controller. If the check box is selected, an IPsec tunnel is established, and users can access protected resources behind the Infranet Enforcer. If the check box is not selected, the tunnel is not automatically set up: a tunnel will not be initiated until there is a request for traffic. 10. From the Enforcer drop-down list, choose the Infranet Enforcer to which endpoints connect to access the resources specified in this IPsec routing policy. 11. In the Roles section, specify: Policy applies to ALL roles Choose this option to apply this IPsec routing policy to all users. Policy applies to SELECTED roles Choose this option to apply this IPsec routing policy only to users who are mapped to roles in the Selected roles list. Be sure to add roles to this list from the Available roles list. Policy applies to all roles OTHER THAN those selected below Choose this option to apply this IPsec routing policy to all users except for those who map to the roles in the Selected roles list. Be sure to add roles to this list from the Available roles list. 12. Click Save Changes. Related Topics IPsec Routing Policices on page 40 42
61 Chapter 2: Using IPsec Setting up IPsec Enforcement on the ScreenOS Enforcer on page 49 Junos Enforcer IPsec Configuration on page 52 IP Address Pool Policies for IPsec in a NAT Environment The Infranet Controller supports using IPsec tunnels through Network Address Translation (NAT) devices to enable users to have secure access to protected resources. In a NAT environment, a virtual IP address must be used for the IPsec tunnel s inner address. You can configure a pool of virtual IP addresses that you want the Infranet Controller to automatically assign to endpoints by creating IP address pool policies. An IP address pool is a contiguous range of IP addresses which you configure by specifying the starting address and the number of addresses in the pool. You can associate an IP address pool with one or more Infranet Enforcers. IP address pool policies are required if one of the following applies to your situation: You are using IPsec in a NAT environment. You selected the Always use a virtual adapter option in an IPsec routing policy to enable inter-operability with other third-party IPsec clients running simultaneously on the endpoint, such as Juniper Networks Network Connect or Microsoft IPsec. If you want to use Network Address Translation (NAT) devices in the Unified Access Control solution, the endpoints must be located on one side of the NAT devices, and the Infranet Controller and Infranet Enforcer must both be located on the other side of the devices. Also note the following if you are using NAT: NAT is not supported between the Infranet Controller and Infranet Enforcer. If there is a NAT device between the endpoint and the Infranet Controller, but not between the endpoint and the Infranet Enforcer, source IP enforcement does not work. This is also true if there is a NAT device between the endpoint and the Infranet Enforcer, but not between the endpoint and the Infranet Controller. If NAT is not detected, the client uses the endpoint s physical IP address when creating the IPsec tunnel to the Infranet Enforcer. The Infranet Controller does not allocate an IP address from the pool. Figure 4 on page 44 illustrates an example of a NAT environment where endpoints 1 and 2 have the same physical IP address: By using an IP address pool policy, you can configure the Infranet Controller to assign a unique, routable, virtual IP address to each endpoint. 43
62 Using the Infranet Controller with the ScreenOS Enforcer Figure 4: Using an IP Address Pool in a NAT Environment The following sequence of events occur when the Infranet Controller and a Juniper Networks client (Odyssey Access Client or Junos Pulse) use an IPsec tunnel through a NAT device: When the client connects to the Infranet Controller and authenticates the user, the client returns the endpoint s source IP address that will be used to access the Infranet Enforcer to the Infranet Controller. The Infranet Controller saves the source IP address internally. When the user attempts to access a protected resource, an IKE exchange occurs to set up an IPsec tunnel between the endpoint and the Infranet Enforcer. During the IKE exchange, the Infranet Enforcer detects the source IP address of the endpoint and sends that IP address to the Infranet Controller. The Infranet Controller compares its saved source IP address for the endpoint with the endpoint s IP address sent from the Infranet Enforcer. If the addresses do not match, the Infranet Controller determines there is a NAT device between the endpoint and the Infranet Enforcer. The Infranet Controller automatically provisions an IP address from an IP address pool policy that you configured (for example, ). The Infranet Controller assigns the IP address to the endpoint based on the IP address pool policy that applies to the user s role. The Infranet Controller then sends the IP address to the Infranet Enforcer. The Infranet Enforcer sends that IP address from the IP address pool (for example, ) to the client on the endpoint during the Xauth authentication exchange. 44
63 Chapter 2: Using IPsec The client on the endpoint configures a virtual network adapter using the IP address sent from the Infranet Enforcer. The endpoint initiates an IPsec connection to the Infranet Enforcer, and the Infranet Enforcer sets up dynamic routes for each IP address. The user can now use the endpoint to access protected resources. The Infranet Controller allocates one IP address for the duration of each client session, which lasts as long as the client is connected to the Infranet Controller. After a session ends, the Infranet Controller may reuse the allocated address for a different endpoint. When the Infranet Controller needs to provide an inner IP address for a new IPsec tunnel, it attempts to reuse an existing inner IP address assigned to the endpoint before allocating a new one. The Infranet Controller checks all of the inner IPs allocated from IP address pools for the endpoint. For each IP address, the Infranet Controller determines whether the policy from which that address was allocated applies to the user and the Infranet Enforcer for the new IPsec tunnel. If a compliant IP address is found, it is used and no new IP address is allocated. If no compliant IP address is found, a new IP address is allocated. Related Topics IP Address Pool Policies on page 45 Configuring an IP Address Pool Policy on page 46 IP Address Pool Policies Topic Details Multiple Infranet Enforcers If you are using multiple Infranet Enforcers across a LAN, make sure that the IP address pool contains addresses that are valid for each Infranet Enforcer. Multiple unclustered Infranet Controllers If you are using multiple unclustered Infranet Controllers across a LAN, make sure that the IP address pool contains addresses that are unique for each Infranet Controller. The endpoint is assigned an virtual IP address for each unclustered Infranet Controller to which Odyssey Access Client connects. IP address conflicts Make sure that the IP pool addresses do not conflict with addresses of hosts that the endpoint might access. Deleting IP addresses in an IP pool If you change or delete the IP addresses in an IP address pool, you must delete all user sessions in order to stop using those addresses. To delete all user sessions, click Delete All Sessions on the System > Status > Active Users page of the Infranet Controller admin console. Number of available IP addresses Be sure to specify a sufficient number of addresses in the IP address pool for all of the endpoints in your deployment. When all of the addresses in the pool have been assigned to endpoints, additional endpoints are unable to obtain a virtual IP address and are blocked from accessing protected resources. The Infranet Controller logs a message in the Event log when an IP address cannot be assigned to an endpoint. 45
64 Using the Infranet Controller with the ScreenOS Enforcer Related Topics IP Address Pool Policies for IPsec in a NAT Environment on page 43 Configuring an IP Address Pool Policy on page 46 Configuring an IP Address Pool Policy To configure an IP address pool policy: 1. In the Infranet Controller admin console, choose UAC > Infranet Enforcer > IP Address Pools. 2. Click New Policy. 3. On the New Policy page: a. For Name, enter a name to label this IP address pool policy. b. For Description, enter an optional description. 4. For IP address pool, specify IP addresses or a range of IP addresses for the Infranet Controller to assign to endpoints. The IP address range can be specified as shown in Table 15 where the last component of the IP address is a range delimited by a hyphen (-). No special characters are allowed. Table 4: Syntax for IP Address Pools IP Address Range Description a.b.c.d Specifies a single IP address a.b.c.d-e.f.g.h Specifies all IP addresses from the first address to the last address, inclusive a.b.c.d-f.g.h An abbreviated form that specifies the range a.b.c.d through a.f.g.h a.b.c.d-g.h An abbreviated form that specifies the range a.b.c.d through a.b.g.h a.b.c.d-h An abbreviated form that specifies the range a.b.c.d through a.b.c.h a.b.c.d/mask Specifies all addresses in a network For example, to allocate all addresses in the range through , specify Or, to allocate all addresses in a class C network, specify / Under Infranet Enforcer, select the Infranet Enforcer(s) to which you want to apply this IP address pool policy and click Add. To apply the policy to all Infranet Enforcers, do not add any Infranet Enforcers and leave the default setting (all) listed in the Selected Enforcers list. 6. In the Roles section, specify: Policy applies to ALL roles Choose this option to apply this IP address pool policy to all users. 46
65 Chapter 2: Using IPsec Policy applies to SELECTED roles Choose this option to apply this IP address pool policy only to users who are mapped to roles in the Selected roles list. Be sure to add roles to this list from the Available roles list. Policy applies to all roles OTHER THAN those selected below Choose this option to apply this IP address pool policy to all users except for those who map to the roles in the Selected roles list. Be sure to add roles to this list from the Available roles list. 7. Click Save Changes. If the IP addresses you specify in the IP address pool policies (that is, the virtual IP addresses) are not routable from the network where your protected resources are located, make sure you enable Source Network Address Translation (NAT-src) on the infranet-auth tunnel policies that configure IPsec on the Infranet Enforcer(s). To enable NAT-src using the Infranet Enforcer WebUI: 1. Click Policies. 2. Click Edit on the infranet-auth tunnel policy. 3. Click Advanced. 4. Select Source Translation and click OK. For information on enabling NAT-src on the infranet-auth tunnel policy, see the Concepts & Examples ScreenOS Reference Guide: Volume 8, Address Translation or the ScreenOS CLI Reference Guide, which you can download from Related Topics IP Address Pool Policies for IPsec in a NAT Environment on page 43 IP Address Pool Policies on page 45 Source Interface Policies for the ScreenOS Enforcer If you want endpoints to use IPsec to communicate with a ScreenOS Enforcer that is in Transparent mode, in some cases you may need to configure a source interface policy on the Infranet Controller. A source interface policy specifies the source interface on the ScreenOS Enforcer that receives traffic from endpoints. The use cases for configuring source interface policies are limited. You will need to use a source interface policy only if you have multiple virtual routers, AND you have an IPsec routing policy with destination zone DEST, and one of the following is true: There are multiple IPsec policies on the enforcer with a destination zone DEST and different source zones. There is an IPsec policy on the ScreenOS Enforcer with a destination zone DEST whose source zone has multiple interfaces. 47
66 Using the Infranet Controller with the ScreenOS Enforcer For more information on how to set up a virtual router in the ScreenOS Enforcer, see the Routing volume of the Concepts & Examples ScreenOS Reference Guide, which you can download from Related Topics Setting up an Infranet Enforcer in Transparent Mode on page 21 Configuring Source Interface Policies on page 48 Configuring Source Interface Policies To configure a source interface policy: 1. In the Infranet Controller admin console, choose UAC > Enforcer > IPsec Routing. 2. Select the check box for Always show source interface policies. The Save Changes button begins to blink. 3. Click Save Changes. The Source Interface tab appears at the top of the page. 4. Select the Source Interface tab. 5. Click New Policy. 6. On the New Policy page: a. For Name, enter a name to label this source interface policy. b. For Description, enter an optional description. 7. From the Enforcer drop-down list, choose the Infranet Enforcer to which endpoints connect. 8. For Source Interface, specify the interface on the ScreenOS Enforcer to which traffic from endpoints connects. This is the default interface for the zone you want to build a gateway for, not the interface name. To view the zone table on the ScreenOS Enforcer, enter the following command: get zone 9. In the Roles section, specify: Policy applies to ALL roles Choose this option to apply this source interface policy to all users. Policy applies to SELECTED roles Choose this option to apply this source interface policy only to users who are mapped to roles in the Selected roles list. Be sure to add roles to this list from the Available roles list. Policy applies to all roles OTHER THAN those selected below Choose this option to apply this source interface policy to all users except for those who map to the roles in the Selected roles list. Be sure to add roles to this list from the Available roles list. 10. Click Save Changes. Related Topics Source Interface Policies for the ScreenOS Enforcer on page 47 48
67 Chapter 2: Using IPsec Setting up an Infranet Enforcer in Transparent Mode on page 21 Upgrading IPsec Enforcement Policies from Version 1.x of the Infranet Controller If you upgraded your Infranet Controller from a version 1.x to 2.0 or later, be aware that the Infranet Controller does not automatically upgrade any previously configured IPsec enforcement policies. You must manually reconfigure all IPsec enforcement policies by using the following instructions. To manually reconfigure IPsec enforcement policies from version 1.x of the Infranet Controller: 1. In the Infranet Controller admin console, choose UAC > Enforcer > IPsec Routing. Note the Infranet Enforcer and destination zone specified in each previously configured IPsec routing policy. 2. While the Infranet Enforcer is connected to the Infranet Controller, navigate to the UAC > Enforcer > Connection page. 3. Click the name in the Enforcer column of the Infranet Enforcer on which you want to configure IPsec enforcement. 4. Click the Enforcer Policies tab. 5. On the Enforcer Policies page, create a new IPsec enforcement policy for each IPsec routing policy and specify the: Source zone (the zone on which end-points are connected) Destination zone (as specified in each IPsec routing policy) 6. If necessary, use the ScreenOS Web UI or CLI to customize the new IPsec enforcement policy. 7. Configure IP address pool policies if you are using IPsec in a NAT environment, or if the endpoints are simultaneously running other third-party IPsec clients such as Juniper Network Connect or Microsoft IPsec. Related Topics Using IPsec with the Infranet Enforcer on page 35 Setting up IPsec Enforcement on the ScreenOS Enforcer In this example, if you use the Infranet Controller to set up IPsec enforcement from Untrust to Trust, and Untrust has one source interface ethernet2. If ethernet2 has an interface number of 5, and Trust has a zone id of 2, then the Infranet Controller runs the following CLI commands on the ScreenOS Enforcer: set user $infra-u-5-2 ike-id u-fqdn u5-2.juniper.net share-limit set user $infra-u-5-2 type ike set user-group $infra-g-5-2 user $infra-u
68 Using the Infranet Controller with the ScreenOS Enforcer set ike gateway $infra-gw-5-2 dialup $infra-g-5-2 Aggr outgoing-interface ethernet2 seedpreshare ARANDOMSTRING proposal pre-g2-3des-sha set ike gateway $infra-gw-5-2 xauth server $infranet query-config set ike gateway $infra-gw-5-2 xauth server auth-method chap set vpn $infra-vpn-5-2 gateway $infra-gw-5-2 no-replay tunnel idletime 0 sec-level compatible set policy from Untrust to Trust "Dial-Up VPN" any any tunnel vpn $infra-vpn-5-2 infranet-auth To use dynamic IPsec with ScreenOS, you configure two policies. On the ScreenOS Enforcer you must have two policies between the zones of interest: a source IP infranet-auth policy with the "redirect-all" option, and a tunnel infranet-auth policy for IPsec. Configuring the IPsec Encryption Settings on the ScreenOS Enforcer When you use the Infranet Controller to configure IPsec on the Infranet Enforcer, the Infranet Controller creates an IPsec policy that uses these default IPsec encryption settings for the phase 2 proposal: NoPFS, ESP, 3DES, and SHA1. You can, however, change the phase 2 proposal by using the Infranet Enforcer CLI or Web UI. For example, you can change the phase 2 proposal using the following CLI command: set vpn $infra-vpn-2-11 gateway $infra-gw-2-11 proposal nopfs-esp-aes128-sha The possible values for the phase 2 proposal are: nopfs-esp-des-md5 nopfs-esp-des-sha1 nopfs-esp-3des-md5 nopfs-esp-3des-sha1 nopfs-esp-aes128-md5 nopfs-esp-aes128-sha1 nopfs-esp-aes256-sha1 nopfs-esp-null-sha1 g2-esp-des-md5 g2-esp-des-sha1 g2-esp-3des-md5 g2-esp-3des-sha1 g2-esp-aes128-md5 g2-esp-aes128-sha1 g2-esp-aes192-sha1 g2-esp-aes256-sha1 In the WebUI select the following: VPN > AutoKey IKE > edit > advanced > select user defined custom. 50
69 Chapter 2: Using IPsec It does not matter what preshared seed you use for the IKE gateway because the Infranet Controller will override it when it connects to the Infranet Enforcer. Use the following settings for the VPN tunnel setup or else the IPsec enforcement will not work correctly between the Infranet Controller and the Infranet Enforcer: xauth authentication dialup VPN CHAP auth method For more information on setting up a VPN tunnel for a dialup user with IKE, see the Concepts & Examples ScreenOS Reference Guide: Volume 5, Virtual Private Networks or the ScreenOS CLI Reference Guide. Related Topics Setting up IPsec Enforcement on the ScreenOS Enforcer on page 49 Bidirectional VPN Policies on the ScreenOS Enforcer If users need to connect from a computer inside the protected network back to the endpoint that is connected by means of a dialup VPN policy, you can create a bidirectional VPN policy on the Infranet Enforcer. You create a bidirectional VPN policy on an existing IPsec (dialup VPN) policy that you created previously to allow traffic from the endpoint to the protected network. Here are two example use cases for bidirectional VPN policies: A user s endpoint at the office is connected by means of a dialup VPN policy, and the user wants to remotely connect to his office computer from another computer outside the office. To diagnose a problem, a Helpdesk employee needs to use a remote desktop system such as Virtual Network Computing (VNC) or Microsoft Remote Desktop on another computer to connect to a user s computer, and the user s computer is connected by means of a dialup VPN policy. Related Topics Creating a Bidirectional VPN Policy on page 51 Creating a Bidirectional VPN Policy To create a bidirectional VPN policy using the CLI: set pol from <protected-resource-zone> to <endpoint-zone> any Dial-up VPN any tunnel vpn <vpn-from-policy-going-the-other-way> pair policy <id-of-policy-going-the-other-way> For example, suppose you have an infranet-auth dialup VPN policy from untrust to trust on your Infranet Enforcer. The ID of the policy is 36, and the vpn is $infra-vpn The following command sets up the corresponding bidirectional VPN policy to allow traffic from trust to untrust: 51
70 Using the Infranet Controller with the ScreenOS Enforcer set pol from trust to untrust any "Dial-up VPN" any tunnel vpn $infra-vpn-1-2 pair-policy 36 To create a bidirectional VPN policy using the WebUI: 1. Using the Infranet Controller, create the IPsec (dialup VPN) policy on the UAC > Infranet Enforcer > Enforcer Policies page. 2. Using the Infranet Enforcer Web UI, edit the dialup VPN policy that you created in the previous step: Policies > Edit <existing dialup vpn policy> 3. Select Modify matching bidirectional VPN policy and click OK. 4. Edit the new bidirectional VPN policy that you just created in the previous step: Policies > Edit <new dialup vpn policy> a. Deselect Modify matching bidirectional VPN policy. b. Click Advanced. c. Deselect Authentication on the Advanced Policy Settings page. d. Click OK. Related Topics Bidirectional VPN Policies on the ScreenOS Enforcer on page 51 Junos Enforcer IPsec Configuration You use the CLI to configure IPsec on the Junos Enforcer. Unlike the ScreenOS Enforcer, you cannot create policies on the Infranet Controller and push the policies to the Junos Enforcer. The source interface is specified in the IKE gateway configuration on the Junos Enforcer. In security policies you specify a VPN, and you specify the IKE gateway in the VPN. See Security Configuration Guide for J Series Services and SRX Series Services Gateways. NOTE: IPsec on the Junos enforcer can handle up to 5,000 concurrent IKE gateways. Dynamic IPsec is not supported with the Junos Enforcer. To configure IPsec on the Junos Enforcer, you must perform three primary tasks: Configure the Infranet Controller as a RADIUS server for the Junos Enforcer client to enable XAUTH. (you must use the internal interface on the Infranet Controller, the external interface does not support XAUTH). Configure IKE and IPsec parameters to specify security restrictions for SAs. 52
71 Chapter 2: Using IPsec Configure Security policies to route traffic between the security gateway and the interface for endpoints. The Infranet Controller polls the Junos Enforcer to retrieve the following configuration details: The IKE gateway interface The destination zone Identity The pre-shared seed The RADIUS shared secret The Infranet Controller pushes these details to the client to allow establishment of a dial-up VPN tunnel. Task Summary: Configuring IPsec on the Junos Enforcer This example details a sample configuration for setting up IPsec on the Junos Enforcer. To use IPsec with the ScreenOS Enforcer, you can configure basic IPsec security policies on the Infranet Controller and then you push the policies to the firewall. On the Junos Enforcer, this functionality does not exist. For the Junos Enforcer, you use the CLI to configure settings to create SAs on the Junos Enforcer that are negotiated with the UAC client. Before beginning, ensure that security zones and interfaces have been set up, and IPsec routing policies and optional IP address pool policies have been configured on the Infranet Controller. J Series Juniper Networks devices support up to four proposals for Phase 2 negotiations, allowing you to define the range of tunnel parameter restrictions that endpoints will accept. For a complete explanation of IPsec on the Junos Enforcer see the Security Configuration Guide for J-series Services Routers and SRX-series Services Gateways. To configure IPsec on the Junos Enforcer: 1. Configure the Infranet Controller as a RADIUS server for the Junos Enforcer client. In this example, you create an instance of the Infranet Controller hostname dev1086 as the RADIUS server. The IP address is You need to provide a shared secret, which is used to permit the Infranet Controller to accept RADIUS packets from the device. user@host# set access profile dev1086 authentication-order radius user@host# set access profile dev1086 radius-server secret some-shared-secret 53
72 Using the Infranet Controller with the ScreenOS Enforcer If you are configuring Infranet Controllers in an active/active cluster, you must configure all IP addresses for individual Infranet Controllers. The shared secret should be the same, as in the following example: set access profile dev1086 authentication-order radius set access profile dev1086 radius-server secret some-shared-secret set access profile dev1086 radius-server secret some-shared-secret If you are configuring and active/passive cluster, configure the Infranet Controllers VIP as the RADIUS server IP address. 2. Configure IKE and IPsec security parameters. NOTE: IPsec with the Junos Enforcer is supported only with aggressive mode and Encapsulation Security Payload (ESP). In aggressive mode, phase 1 security proposals are negotiated with two exchanges and a total of three messages: First message The initiator proposes the SA, initiates a Diffie-Hellman exchange, and sends a pseudo-random number and the IKE identity. Second message The recipient accepts the SA; authenticates the initiator; and sends a pseudo-random number, the IKE identity, and, if using certificates, the recipient's certificate. Third message The initiator authenticates the recipient, confirms the exchange, and, if using certificates, sends the initiator's certificate. Because the participants' identities are exchanged in the clear (in the first two messages), Aggressive mode does not provide identity protection. ESP protects the inner IP packet, while the outer header remains unprotected. You define the security proposals, including all of the IKE parameters that determine the strength of the IPsec tunnels. These options define the SAs for this IPsec tunnel. 54
73 Chapter 2: Using IPsec In this section, you set up a phase 1 IKE proposal named prop1, using Diffie-Hellman Group 2, authentication algorithm SHA1, and encryption algorithm 3DES-CBC. user@host# set security ike proposal prop1 authentication-method pre-shared-keys The client supports only the pre-shared key authentication method. user@host# set security ike proposal prop1 dh-group group2 The client supports group1, group2, and group5. user@host# set security ike proposal prop1 authentication-algorithm sha1 The client supports md5 and sha1. user@host# set security ike proposal prop1 encryption-algorithm 3des-cbc The client supports des-cbc, 3des-dbc, aes-128-cbc, aes-192-cbc, and aes-256-cbc In this section, you set up an IKE policy named pol1 with aggressive mode, the pre-shared key and the proposal configured above. user@host# set security ike policy pol1 mode aggressive The client supports only aggressive mode. user@host# set security ike policy pol1 proposals prop1 user@host# set security ike policy pol1 pre-shared-key ascii-text some-preshared-key Only ascii-text is supported. Do not use a hexadecimal pre-shared key. In this section, you configure an IKE gateway named gateway1 with 5000 connection-limits, host.company.com identity, group IKE ID, IKE policy pol1 configured above, and XAUTH dev1086 as configured above. user@host# user@host# set security ike gateway gateway1 ike-policy pol1 user@host# user@host# set security ike gateway gateway1 dynamic hostname host.company.com user@host# set security ike gateway gateway1 dynamic ike-user-type group-ike-id user@host# set security ike gateway gateway1 dynamic connections-limit (maximum 5,000) user@host# set security ike gateway gateway1 external-interface ge-0/0/2.0 user@host# set security ike gateway gateway1 xauth access-profile dev1086 The Infranet Controller and the client support only group-ike-id. 55
74 Using the Infranet Controller with the ScreenOS Enforcer In this section, you configure an IPsec phase 2 proposal named prop1 with ESP protocol, HMAC-SHA1-96 authentication algorithm, and 3DES-CBC encryption algorithm. user@host# set security ipsec proposal prop1 protocol esp The client supports only esp. user@host# set security ipsec proposal prop1 authentication-algorithm hmac-sha1-96 The client supports hmac-md5-96, and hmac-sha1-96. user@host# set security ipsec proposal prop1 encryption-algorithm 3des-cbc The client supports des-cbc, 3des-cbc, aes-128-cbc, aes-192-cbc, aes-256-cbc, and no encryption-algorithm. In this section, you configure an IPsec phase 2 policy name pol1 with proposal prop1 as configured above. user@host# set security ipsec policy pol1 proposals prop1 In this section, you configure an IPsec VPN named vpn1 with IKE gateway gateway1 as configured in the above example, and IPsec policy pol1 as configured above. user@host# set security ipsec vpn vpn1 ike gateway gateway1 user@host# set security ipsec vpn vpn1 ike ipsec-policy pol1 user@host# set security ipsec vpn vpn1 establish-tunnels immediately user@host#set security ike gateway gateway1 external-interface ge-0/0/0.0 user@host#set security ike gateway gateway1 xauth access-profile name The client requires the tunnel to be established immediately. 3. Create security policy. 56
75 Chapter 2: Using IPsec In this section enable the VPN vpn1 configured above, and add enforcement in UAC a security policy named pol1 from the zone named untrust to the zone named trust. user@host# set security policies from-zone untrust to-zone trust policy pol1 match source-address any NOTE: You should always specify any with the following command. user@host# set security policies from-zone untrust to-zone trust policy pol1 match destination-address any user@host# set security policies from-zone untrust to-zone trust policy pol1 match application any user@host# set security policies from-zone untrust to-zone trust policy pol1 then permit tunnel ipsec-vpn vpn1 user@host# set security policies from-zone untrust to-zone trust policy pol1 then permit application-services uac-policy Related Topics IPsec Policies on page 35 Before Configuring IPsec on page 37 IPsec Routing Policices on page 40 57
76 Using the Infranet Controller with the ScreenOS Enforcer 58
77 CHAPTER 3 Policies and Procedures for Interoperability Between the UAC Enforcer and the IC Series Infranet Enforcer Policies Infranet Enforcer Policies on page 59 About Resource Access Policies on page 60 Configuring Resource Access Policies on page 62 Setting up Source IP Enforcement on the Infranet Enforcer on page 63 Auth Tables on the Infranet Enforcer on page 64 Dynamic Auth Table Allocation on page 65 Configuring Dynamic Auth Table Allocation on page 66 Configuring Auth Table Mapping Policies for Source IP Enforcement on page 66 Configuring Auth Table Mapping Policies on page 68 After you set up user roles, authentication servers, realms and sign-in policies, you deploy the Infranet Enforcer in front of servers and resources that you want to protect. You control access through a number of different security policies that you configure on the Infranet Controller. All policy options are supported on the ScreenOS Enforcer. Resource Access Policy A resource access policy specifies which users are allowed or denied access to a set of protected resources. You specify which users you want to allow or deny by choosing roles for each resource access policy. Source IP Policy A source IP policy is an infranet-auth policy the on ScreenOS Enforcer or a security policy on the Junos Enforcer that contains a source and destination that permits the Infranet Enforcer to route clear-text traffic between source and destination zones. You can set up a source IP policy on the Infranet Controller and push the policy to the Infranet Enforcer, or you can set up the policy using ScreenOS WebUI or the command line. Auth Table Mapping Policy This type of policy specifies which Infranet Enforcer device(s) an endpoint must use to access resources when the endpoint is using source 59
78 Using the Infranet Controller with the ScreenOS Enforcer IP enforcement. If you are using a ScreenOS Enforcer with version 6.1 or greater or the Junos Enforcer, it is not necessary to configure auth table mapping policies. You can use dynamic auth table provisioning. NOTE: You can use a user name with spaces, a user name with quotes, a user name with UTF-8 characters, or a user name with a \. Each of these conventions are accepted by the firewall with a valid corresponding auth table entry. Figure 5 on page 60 demonstrates how policies on the Infranet Enforcer and the Infranet Controller interact when a user has an auth table entry on the Infranet Enforcer. Figure 5: Policy Interaction The Infranet Enforcer detects a flow to a specific resource and compares the source IP of the packet with IP addresses in the auth tables. The IP address is associated with a set of roles in the auth table. The destination IP of the packet is matched with the destination IP of a resource access policy, which has a set of roles assigned. The Infranet Enforcer parses the roles in the resource access policy to determine whether or not the role can access the resource. Related Topics How the IC Series and UAC Enforcer Work Together on page 4 About Resource Access Policies on page 60 Setting up Source IP Enforcement on the Infranet Enforcer on page 63 Configuring Auth Table Mapping Policies for Source IP Enforcement on page 66 About Resource Access Policies A resource access policy specifies which users are allowed or denied access to a set of protected resources. You identify resources within your protected network, then you specify which users you want to allow or deny by choosing the roles for each resource access policy. Auth table 60
79 Chapter 3: Policies and Procedures for Interoperability Between the UAC Enforcer and the IC Series entries on the Infranet Enforcer match user requests for access with resource access policies. The Infranet Enforcer evaluates traffic and enforces access control based on the policies that you specify. When traffic from a role with a security policy enabled is compared to a policy and there is a matching entry, the Infranet Enforcer applies the appropriate policy action. For example, a resource access policy can specify that a user must have an Antivirus role to access a particular network, and the Antivirus role requires the user s computer to run a particular antivirus program. With the ScreenOS Infranet Enforcer you can create an additional layer of security by applying security policy actions to endpoints. Antispam, logging, IDP, web filtering, antivirus, and deep inspection policies can be applied to any role. The Infranet Controller pushes the policies to the Infranet Enforcer when the Infranet Enforcer first connects to the Infranet Controller, and any time you make a change to a resource access policy. When any change is made on the resource access policies page, all resource access policies on the Infranet Enforcer are refreshed, and endpoints that are accessing resources through resource access policies will be temporarily interrupted. With ScreenOS 6.2 or greater, the Infranet Controller supports Virtual systems (VSYS). VSYS do not inherit resource access policies from the root-vsys. If you have a resource access policy configured for an existing ScreenOS Enforcer, and subsequently create one or more VSYS, you need to add new policies for the VSYS if you want to allow users to access resources within the VSYS. Notifying the User of Denied Traffic in a Resource Access Policy If you are using ScreenOS version 6.2 or greater on the ScreenOS Enforcer or the Junos Enforcer, you can configure customized messages for authenticated users who attempt to access a resource to which you have denied access. When you specify the deny action in a resource access policy for a role or roles, a text field appears. You can use the following variables to display information for the user: <USER> the login name of the user <SOURCEIP> the source IP of the packet <DESTIP> the destination IP of the packet <PROTOCOL> the protocol of the packet <DESTPORT> the destination port of the packet You can use these variables along with your own text to compose the deny message that you send to users. 61
80 Using the Infranet Controller with the ScreenOS Enforcer When the message is sent to the user, the applicable information about the session or the resource is substituted. The information is displayed on the user s endpoint in a balloon in the tray icon. Related Topics Configuring Resource Access Policies on page 62 Infranet Enforcer Policies on page 59 Configuring Resource Access Policies To configure Infranet Enforcer resource access policies: 1. In the Infranet Controller admin console, choose UAC > Enforcer > Resource Access Policy. 2. Click New Policy. 3. On the New Policy page: a. For Name, enter a name to label this Infranet Enforcer resource access policy. b. For Description, enter an optional description. 4. For Resources, specify the protocol, IP address, network mask, and port of each resource (or range of addresses) for which this Infranet Enforcer resource access policy applies, one per line. Do not insert any spaces in your entries, or the policy may not be applied correctly. You cannot specify a host name in a resource access policy. You can only specify an IP address. You can use TCP, UDP, or ICMP. 5. Under Infranet Enforcer, specify the Infranet Enforcer to which this policy applies by using the Add button. 6. Specify one of the following in the Roles section: Policy applies to ALL roles Choose this option to apply this Infranet Enforcer resource access policy to all users. Policy applies to SELECTED roles Choose this option to apply this Infranet Enforcer resource access policy only to users who are mapped to roles in the Selected roles list. Be sure to add roles to this list from the Available roles list. Policy applies to all roles OTHER THAN those selected below Choose this option to apply this Infranet Enforcer resource access policy to all users except those who map to the roles in the Selected roles list. Be sure to add roles to this list from the Available roles list. 7. In the Action section, specify whether you want to use this Infranet Enforcer resource access policy to allow or deny access to the specified resources. If you choose deny, a text box appears that allows you to customize a deny message for users. 62
81 Chapter 3: Policies and Procedures for Interoperability Between the UAC Enforcer and the IC Series If you want to record deny actions in the User Access Log, select the check box for Infranet Enforcer Deny Messages on the Log/monitoring > User Access > Settings page. The log records the user, source IP, destination IP, protocol, and destination port. 8. For ScreenOS Enforcers, in the ScreenOS Options section, use the option buttons to determine the policy options that you want to apply to selected roles. Use the Add and Remove buttons to specify antispam, logging, IDP, web filtering, antivirus, and deep inspection. By default, all policy options are enabled on the Infranet Controller. To enforce the policies, you must create corresponding policies on the ScreenOS Enforcer. If the Infranet Controller is upgraded from a previous version, all ScreenOS options are enabled for all of the resource access policies that were available prior to the upgrade. 9. If you have created a VSYS on a ScreenOS Enforcer, enter the name of the VSYS in the VSYS text box, if applicable. The main UAC > Infranet Enforcer > Resource Access Policy page displays the Enforcers and/or VSYS that are associated with each policy. 10. Click Save Changes. Related Topics About Resource Access Policies on page 60 Setting up Source IP Enforcement on the Infranet Enforcer Source IP enforcement permits end users to access protected resources that are protected by the Infranet Enforcer. IPsec provides an encrypted tunnel for bidirectional traffic, source IP enforcement allows unencrypted (clear text) traffic between endpoints and the Infranet Enforcer. You can use source IP enforcement on the Infranet Enforcer to protect resources alone, or with IPsec on the ScreenOS Enforcer. To use source IP enforcement, you configure infranet-auth Enforcer policies for the ScreenOS Enforcer and for VSYS on the ScreenOS Enforcer, and you configure security policies on the Junos Enforcer. Infranet-auth policies and security policies control which zones use Infranet Enforcer resource access policies to allow or deny traffic. By default, traffic is denied through the Infranet Enforcer. With infranet-auth policies and security policies you control the traffic that is permitted to pass. When you first set up the Infranet Enforcer and the Infranet Controller you bound zones to interfaces. Infranet-auth policies and security policies control the traffic flow between zones. For example, you can configure an infranet-auth policy on the ScreenOS Enforcer to enforce traffic from the Untrust zone to the Trust zone. Then, you configure resource access policies and specify resources that are within the Trust zone. The roles that you assign to the resource access policy are permitted to access the specified resources. 63
82 Using the Infranet Controller with the ScreenOS Enforcer Infranet-Auth Policies for Source IP on the ScreenOS Enforcer You can configure basic infranet-auth Enforcer policies that specify a source zone and a destination zone on the Infranet Controller, and then push the policies to the ScreenOS Enforcer to add additional policy details, or you can use the ScreenOS Enforcer to configure the policies with the CLI or WebUI. Juniper Networks recommends that you use the Infranet Controller to set up the policies for source IP enforcement on the Infranet Enforcer. Before setting a policy, you must create address book entries for the destination and source addresses unless you use address book entries that already exist, such as Any. In the following example, you set an infranet-auth policy and add it to the top of the list of policies using Any. The policy allows all traffic of any type from any host to another host. The following policy allows traffic according to the Infranet Enforcer resource access policies that you configure on the Infranet Controller. set policy top from untrust to trust any any permit infranet-auth In the following example, you create two address book entries and a policy between them for anyone in the /16 range to be able to reach the /16 range. set address Trust Range set address Untrust Range set policy from trust to untrust Range Range any permit infranet-auth Security Policies for Source IP on the Junos Enforcer On the Junos Enforcer, security policies enforce rules for the transit traffic. From the perspective of security policies, traffic enters one security zone and exits another. This combination of a from-zone and a to-zone is called a context on the Junos Enforcer. A security zone is a logical group of interfaces with identical security requirements. Each security zone contains an address book. Before you can set up policies between two zones, you must define the addresses for each of the zone s address books. A zone s address book must contain entries for the addressable networks and end hosts belonging to the zone. Each security policy that you create must contain at a minimum match criteria and an action. You can specify additional policy options as required. You can create security polices on the Junos Enforcer from the J-Web interface, or from the CLI. For details about setting up security polices on the Junos Enforcer, see the Junos Software Security Configuration Guide. For CLI instructions see Junos Software CLI Reference. Auth Tables on the Infranet Enforcer The Infranet Enforcer holds authentication tables, or auth tables for valid sessions on the Infranet Controller. Auth tables consist of a unique identification number, the source IP address of the endpoint that initiated the session, the username and a list of roles that the user has been assigned. 64
83 Chapter 3: Policies and Procedures for Interoperability Between the UAC Enforcer and the IC Series You can allow the Infranet Enforcer to automatically generate auth tables whenever users authenticate, or you can configure dynamic auth table allocation. With dynamic auth table allocation, auth tables are provisioned only as a response to a valid request from an authenticated user for a resource behind the Infranet Enforcer. Dynamic auth table allocation is available on all Junos enforcers, and on ScreenOS Enforcers with version 6.1 or greater. Dynamic auth table allocation is required to use IF-MAP Federation. Related Topics Dynamic Auth Table Allocation on page 65 Configuring Dynamic Auth Table Allocation on page 66 Configuring Auth Table Mapping Policies for Source IP Enforcement on page 66 Configuring Auth Table Mapping Policies on page 68 Dynamic Auth Table Allocation Prior to ScreenOS release 6.1, you manually created auth table mapping policies to use Source IP enforcement. Each authenticated user had an auth table entry on the Infranet Enforcer, whether they were accessing resources or not. With the Junos Enforcer and ScreenOS 6.1 or greater on the ScreenOS Enforcer you can dynamically create auth table entries when a user attempts to access a protected resource, eliminating the need to manually create Auth Table Mapping Policies. Dynamic auth table allocation reduces auth table entries to only those that are needed, enabling you to deploy smaller firewalls with a larger user population. After the user has disconnected, the Infranet Enforcer automatically expires the auth table entry. Dynamic auth table allocation does not work with http traffic if the ScreenOS Enforcer s captive portal feature is configured to redirect user traffic to an external web server other than the Infranet Controller. If you permit dynamic auth table allocation on the Infranet Controller, and the DNS server for your network is behind the Infranet Enforcer, endpoints may occasionally experience DNS time-out issues before resources are provisioned. In most deployments, Juniper Networks recommends that you use dynamic auth table allocation. The benefits of dynamic auth table allocation are based on many factors within your network deployment: the number of Infranet Enforcers, the anticipated number of sessions, and the persistence of user sessions. One scenario in which static auth tables are more practical are in deployments that force every endpoint to go through a single Infranet Enforcer for all access. In this case, static auth tables can reduce overall traffic between Infranet Controllers and Infranet Enforcers. In deployments that use static auth table mapping policies (for example, if you are using a ScreenOS version prior to 6.1), Juniper Networks recommends no more than
84 Using the Infranet Controller with the ScreenOS Enforcer connected Infranet Enforcers. For deployment scenarios with greater than 100 Infranet Enforcers, Juniper recommends a deployment strategy using Dynamic Auth Table Allocation. Juniper Networks testing has shown that with 5,000 active sessions, performance is impacted significantly when dynamic auth table allocation is not configured and 100 connected firewalls are deployed. Performance metrics will vary for each UAC release. Please refer to Juniper Networks or your strategic partner for current performance information. Dynamic auth table allocation is required to use IF-MAP Federation. Related Topics Configuring Dynamic Auth Table Allocation on page 66 Configuring Dynamic Auth Table Allocation To permit dynamic auth table allocation: 1. From the UAC > Enforcer > Auth Table Mapping page on the admin console, delete the Default Policy, or specify an Enforcer for which you do not want to configure this feature. 2. Click Save Changes. 3. Configure a source IP policy for all traffic, whether source IP or IPsec. Related Topics Dynamic Auth Table Allocation on page 65 Configuring Auth Table Mapping Policies for Source IP Enforcement NOTE: If you are using the Junos Enforcer or ScreenOS version 6.1 or greater on the ScreenOS Enforcer, and have permitted dynamic auth table allocation, you do not need to configure auth table mapping policies. You can use dynamic auth table allocation. The Infranet Controller configuration includes one default auth table mapping policy. When the default auth table mapping policy is enabled, the Infranet Controller pushes one auth table entry for each authenticated user to all Infranet Enforcer devices connected to the Infranet Controller. An auth table entry consists of the user s name, a set of roles, and the IP address of the wired adapter, wireless adapter, or virtual adapter in the user s computer. If your deployment includes a mixture of low and high capacity Infranet Enforcer devices, the lower capacity Infranet Enforcer devices may reach the limit of concurrent auth table entries and prevent additional users from accessing protected resources behind the lower capacity Infranet Enforcer devices. Figure 6 on page 67illustrates an example of a deployment that includes a higher capacity ScreenOS Enforcer ISG 2000 and a lower capacity SSG 5 in two branch offices. If the default auth table mapping policy is enabled and the number of users that attempt to 66
85 Chapter 3: Policies and Procedures for Interoperability Between the UAC Enforcer and the IC Series access protected resources behind the ISG 2000 in Branch Office 1 exceeds the limit of concurrent auth table entries on the SSG 5, then additional users are unable to access protected resources behind the SSG 5 in Branch Office 2. You can prevent overloading the lower capacity Infranet Enforcer devices in mixed deployments by deleting the default auth table mapping policy and creating new policies. An auth table mapping policy specifies which Infranet Enforcer device(s) each user role is allowed to use when the endpoint is using source IP enforcement. These policies prevent the Infranet Controller from creating unnecessary auth table entries on all connected Infranet Enforcer devices. In the example in Figure 8, auth table entries for users assigned the Branch1-Role are mapped to the ISG 2000 in Branch Office 1 only, which avoids overloading the SSG 5in Branch Office 2. Likewise, the auth table entries for users assigned the HQ-Role are mapped to the ISG 2000 in HQ Office only, and auth table entries for users assigned the Branch2- Role are mapped to the SSG 5 in Branch Office 2 only. Figure 6: Using Auth Table Mapping Policies You can also use auth table mapping policies to restrict users from accessing resources behind an Infranet Enforcer based on the user s assigned role. If your deployment does not use source IP enforcement, or if you have configured dynamic provisioning of auth tables, you do not need to create auth table mapping policies. For IPsec enforcement with the ScreenOS Enforcer, the Infranet Controller pushes auth table entries only to the Infranet Enforcer devices you specify in IPsec routing policies. If you 67
vgw Series Installation and Administration Guide Release 5.0 r2 Published: Revision 2 Copyright 2012, Juniper Networks, Inc.
 vgw Series Installation and Administration Guide Release 5.0 r2 Published: 2012-02-03 Revision 2 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net
vgw Series Installation and Administration Guide Release 5.0 r2 Published: 2012-02-03 Revision 2 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net
Migration Guide. Release 9.2. JUNOS Software with Enhanced Services. for J-series Services Routers. Juniper Networks, Inc.
 JUNOS Software with Enhanced Services Migration Guide for J-series Services Routers Release 9.2 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Part
JUNOS Software with Enhanced Services Migration Guide for J-series Services Routers Release 9.2 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Part
Pulse Policy Secure. UAC Interoperability with the ScreenOS Enforcer. Product Release 5.1. Document Revision 1.0 Published:
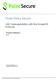 Pulse Policy Secure UAC Interoperability with the ScreenOS Enforcer Product Release 5.1 Document Revision 1.0 Published: 2015-02-10 2015 by Pulse Secure, LLC. All rights reserved Pulse Secure, LLC 2700
Pulse Policy Secure UAC Interoperability with the ScreenOS Enforcer Product Release 5.1 Document Revision 1.0 Published: 2015-02-10 2015 by Pulse Secure, LLC. All rights reserved Pulse Secure, LLC 2700
Junos OS. WLAN Configuration and Administration Guide for SRX210, SRX240, and SRX650 Services Gateways. Release Published:
 Junos OS WLAN Configuration and Administration Guide for SRX210, SRX240, and SRX650 Services Gateways Release 11.2 Published: 2011-05-11 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California
Junos OS WLAN Configuration and Administration Guide for SRX210, SRX240, and SRX650 Services Gateways Release 11.2 Published: 2011-05-11 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California
Junos Pulse Access Control Service
 Junos Pulse Access Control Service RADIUS Server Management Guide Release 4.4 Published: 2013-02-15 Part Number: Juniper Networks, Inc. 1194 rth Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000
Junos Pulse Access Control Service RADIUS Server Management Guide Release 4.4 Published: 2013-02-15 Part Number: Juniper Networks, Inc. 1194 rth Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000
Web Device Manager Guide
 Juniper Networks EX2500 Ethernet Switch Web Device Manager Guide Release 3.0 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Part Number: 530-029704-01,
Juniper Networks EX2500 Ethernet Switch Web Device Manager Guide Release 3.0 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Part Number: 530-029704-01,
Junos Pulse Secure Access Service
 Junos Pulse Secure Access Service IF-MAP Feature Guide Release 8.0 Published: 2013-11-15 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All
Junos Pulse Secure Access Service IF-MAP Feature Guide Release 8.0 Published: 2013-11-15 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All
End User License Agreement
 End User License Agreement Kyocera International, Inc. ( Kyocera ) End User License Agreement. CAREFULLY READ THE FOLLOWING TERMS AND CONDITIONS ( AGREEMENT ) BEFORE USING OR OTHERWISE ACCESSING THE SOFTWARE
End User License Agreement Kyocera International, Inc. ( Kyocera ) End User License Agreement. CAREFULLY READ THE FOLLOWING TERMS AND CONDITIONS ( AGREEMENT ) BEFORE USING OR OTHERWISE ACCESSING THE SOFTWARE
Juniper Secure Analytics
 Juniper Secure Analytics Managing Juniper SRX PCAP Data Release 2014.1 Modified: 2016-03-16 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights
Juniper Secure Analytics Managing Juniper SRX PCAP Data Release 2014.1 Modified: 2016-03-16 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights
1. License Grant; Related Provisions.
 IMPORTANT: READ THIS AGREEMENT CAREFULLY. THIS IS A LEGAL AGREEMENT BETWEEN AVG TECHNOLOGIES CY, Ltd. ( AVG TECHNOLOGIES ) AND YOU (ACTING AS AN INDIVIDUAL OR, IF APPLICABLE, ON BEHALF OF THE INDIVIDUAL
IMPORTANT: READ THIS AGREEMENT CAREFULLY. THIS IS A LEGAL AGREEMENT BETWEEN AVG TECHNOLOGIES CY, Ltd. ( AVG TECHNOLOGIES ) AND YOU (ACTING AS AN INDIVIDUAL OR, IF APPLICABLE, ON BEHALF OF THE INDIVIDUAL
Network Configuration Example
 Network Configuration Example Configuring a Two-Tiered Virtualized Data Center for Large Enterprise Networks Release 11.2 Published: 2011-04-21 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale,
Network Configuration Example Configuring a Two-Tiered Virtualized Data Center for Large Enterprise Networks Release 11.2 Published: 2011-04-21 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale,
Subscriber Traffic Redirection
 Subscriber Traffic Redirection Published: 2014-06-06 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights reserved. Juniper Networks,
Subscriber Traffic Redirection Published: 2014-06-06 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights reserved. Juniper Networks,
RingMaster Software. Configuration Guide. Release 9.1. March 2014 (Release Date) Copyright 2014, Juniper Networks, Inc. 1
 RingMaster Software Configuration Guide Release 9.1 March 2014 (Release Date) Copyright 2014, Juniper Networks, Inc. 1 Juniper Network, Inc. 1194 N. Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000
RingMaster Software Configuration Guide Release 9.1 March 2014 (Release Date) Copyright 2014, Juniper Networks, Inc. 1 Juniper Network, Inc. 1194 N. Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000
Technical Configuration Example
 Technical Configuration Example Feature Automation Script cpu-usage-60.slax View a chart of the CPU usage for the last 60 minutes Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA
Technical Configuration Example Feature Automation Script cpu-usage-60.slax View a chart of the CPU usage for the last 60 minutes Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA
Junos Pulse Secure Access Service
 Junos Pulse Secure Access Service Intrusion Detection and Prevention Sensors Release 8.0 Published: 2013-11-15 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000
Junos Pulse Secure Access Service Intrusion Detection and Prevention Sensors Release 8.0 Published: 2013-11-15 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000
Terms of Use. Changes. General Use.
 Terms of Use THESE TERMS AND CONDITIONS (THE TERMS ) ARE A LEGAL CONTRACT BETWEEN YOU AND SPIN TRANSFER TECHNOLOGIES ( SPIN TRANSFER TECHNOLOGIES, STT, WE OR US ). THE TERMS EXPLAIN HOW YOU ARE PERMITTED
Terms of Use THESE TERMS AND CONDITIONS (THE TERMS ) ARE A LEGAL CONTRACT BETWEEN YOU AND SPIN TRANSFER TECHNOLOGIES ( SPIN TRANSFER TECHNOLOGIES, STT, WE OR US ). THE TERMS EXPLAIN HOW YOU ARE PERMITTED
Mobile Banking and Mobile Deposit Terms & Conditions
 Mobile Banking and Mobile Deposit Terms & Conditions PLEASE CAREFULLY REVIEW THESE TERMS AND CONDITIONS BEFORE PROCEEDING: This Mobile Banking and Mobile Deposit Addendum ( Addendum ) to the Old National
Mobile Banking and Mobile Deposit Terms & Conditions PLEASE CAREFULLY REVIEW THESE TERMS AND CONDITIONS BEFORE PROCEEDING: This Mobile Banking and Mobile Deposit Addendum ( Addendum ) to the Old National
Junos Pulse Secure Access Service
 Junos Pulse Secure Access Service License Management Guide Release 7.4 Published: 2014-03-03 Part Number:, Revision 1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000
Junos Pulse Secure Access Service License Management Guide Release 7.4 Published: 2014-03-03 Part Number:, Revision 1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000
Entrust SSL Web Server Certificate Subscription Agreement
 Entrust SSL Web Server Certificate Subscription Agreement ATTENTION - READ CAREFULLY: THIS SUBSCRIPTION AGREEMENT (THIS "AGREEMENT") IS A LEGAL CONTRACT BETWEEN THE PERSON, ENTITY, OR ORGANIZATION NAMED
Entrust SSL Web Server Certificate Subscription Agreement ATTENTION - READ CAREFULLY: THIS SUBSCRIPTION AGREEMENT (THIS "AGREEMENT") IS A LEGAL CONTRACT BETWEEN THE PERSON, ENTITY, OR ORGANIZATION NAMED
Pulse Policy Secure. Getting Started Guide. Product Release 5.1. Document Revision 1.0 Published:
 Pulse Policy Secure Getting Started Guide Product Release 5.1 Document Revision 1.0 Published: 2014-12-15 2014 by Pulse Secure, LLC. All rights reserved Pulse Secure, LLC 2700 Zanker Road, Suite 200 San
Pulse Policy Secure Getting Started Guide Product Release 5.1 Document Revision 1.0 Published: 2014-12-15 2014 by Pulse Secure, LLC. All rights reserved Pulse Secure, LLC 2700 Zanker Road, Suite 200 San
Implementing Interprovider Layer-3 VPN Option 3
 Network Configuration Example Implementing Interprovider Layer-3 VPN Option 3 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net Published: 2009-12-17
Network Configuration Example Implementing Interprovider Layer-3 VPN Option 3 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net Published: 2009-12-17
NSM Plug-In Users Guide
 Security Threat Response Manager Release 2013.2 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2013-07-19 Copyright Notice Copyright 2013
Security Threat Response Manager Release 2013.2 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2013-07-19 Copyright Notice Copyright 2013
Oracle Technology Network Developer License Terms for Java Card Classic Edition and Java Card Connected Edition Software Development Kits
 Oracle Technology Network Developer License Terms for Java Card Classic Edition and Java Card Connected Edition Software Development Kits Export Controls Export laws and regulations of the United States
Oracle Technology Network Developer License Terms for Java Card Classic Edition and Java Card Connected Edition Software Development Kits Export Controls Export laws and regulations of the United States
Junos Space. Reports. Release Published: Copyright 2014, Juniper Networks, Inc.
 Junos Space Reports Release 14.1 Published: 2014-11-18 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights reserved. Juniper Networks,
Junos Space Reports Release 14.1 Published: 2014-11-18 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights reserved. Juniper Networks,
Installing the Shrew Soft VPN Client
 Windows Install Installing the Shrew Soft VPN Client ShrewVPNWindows201211-01 Global Technology Associates 3505 Lake Lynda Drive Suite 109 Orlando, FL 32817 Tel: +1.407.380.0220 Fax. +1.407.380.6080 Email:
Windows Install Installing the Shrew Soft VPN Client ShrewVPNWindows201211-01 Global Technology Associates 3505 Lake Lynda Drive Suite 109 Orlando, FL 32817 Tel: +1.407.380.0220 Fax. +1.407.380.6080 Email:
Funding University Inc. Terms of Service
 Funding University Inc. Terms of Service None of the information contained in Funding University's website constitutes a recommendation, solicitation or offer by Funding University or its affiliates to
Funding University Inc. Terms of Service None of the information contained in Funding University's website constitutes a recommendation, solicitation or offer by Funding University or its affiliates to
NSM Plug-In Users Guide
 Juniper Secure Analytics Release 2014.3 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2014-10-15 Copyright Notice Copyright 2014 Juniper
Juniper Secure Analytics Release 2014.3 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2014-10-15 Copyright Notice Copyright 2014 Juniper
If you do not wish to agree to these terms, please click DO NOT ACCEPT and obtain a refund of the purchase price as follows:
 IMPORTANT: READ THIS AGREEMENT CAREFULLY. THIS IS A LEGAL AGREEMENT BETWEEN AVG TECHNOLOGIES CZ, s.r.o. ( AVG TECHNOLOGIES ) AND YOU (ACTING AS AN INDIVIDUAL OR, IF APPLICABLE, ON BEHALF OF THE INDIVIDUAL
IMPORTANT: READ THIS AGREEMENT CAREFULLY. THIS IS A LEGAL AGREEMENT BETWEEN AVG TECHNOLOGIES CZ, s.r.o. ( AVG TECHNOLOGIES ) AND YOU (ACTING AS AN INDIVIDUAL OR, IF APPLICABLE, ON BEHALF OF THE INDIVIDUAL
Installing Enterprise Switch Manager
 Installing Enterprise Switch Manager NN47300-300 Document status: Standard Document version: 0401 Document date: 26 March 2008 All Rights Reserved The information in this document is subject to change
Installing Enterprise Switch Manager NN47300-300 Document status: Standard Document version: 0401 Document date: 26 March 2008 All Rights Reserved The information in this document is subject to change
Junos OS. Unified Access Control Solution Guide for SRX Series Services Gateways. Release Junos Pulse Access Control Service 4.2/Junos OS 12.
 Junos OS Unified Access Control Solution Guide for SRX Series Services Gateways Release Junos Pulse Access Control Service 4.2/Junos OS 12.1 Published: 2012-04-03 Juniper Networks, Inc. 1194 North Mathilda
Junos OS Unified Access Control Solution Guide for SRX Series Services Gateways Release Junos Pulse Access Control Service 4.2/Junos OS 12.1 Published: 2012-04-03 Juniper Networks, Inc. 1194 North Mathilda
Oracle Technology Network Developer License Terms for Java Card Classic Edition and Java Card Connected Edition Specifications
 Oracle Technology Network Developer License Terms for Java Card Classic Edition and Java Card Connected Edition Specifications Export Controls Export laws and regulations of the United States and any other
Oracle Technology Network Developer License Terms for Java Card Classic Edition and Java Card Connected Edition Specifications Export Controls Export laws and regulations of the United States and any other
Installing Enterprise Switch Manager
 Installing Enterprise Switch Manager ATTENTION Clicking on a PDF hyperlink takes you to the appropriate page If necessary, scroll up or down the page to see the beginning of the referenced section NN47300-300
Installing Enterprise Switch Manager ATTENTION Clicking on a PDF hyperlink takes you to the appropriate page If necessary, scroll up or down the page to see the beginning of the referenced section NN47300-300
Administration Guide. Release 5.6 February Odyssey Access Client for Windows. Enterprise Edition FIPS Edition. Juniper Networks, Inc.
 Odyssey Access Client for Windows Administration Guide Enterprise Edition FIPS Edition Release 5.6 February 2013 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net
Odyssey Access Client for Windows Administration Guide Enterprise Edition FIPS Edition Release 5.6 February 2013 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net
Oracle Binary Code License Agreement for Java Secure Sockets Extension for Connected Device Configuration 1.0.2
 Oracle Binary Code License Agreement for Java Secure Sockets Extension 1.0.3 for Connected Device Configuration 1.0.2 ORACLE AMERICA, INC. ("ORACLE"), FOR AND ON BEHALF OF ITSELF AND ITS SUBSIDIARIES AND
Oracle Binary Code License Agreement for Java Secure Sockets Extension 1.0.3 for Connected Device Configuration 1.0.2 ORACLE AMERICA, INC. ("ORACLE"), FOR AND ON BEHALF OF ITSELF AND ITS SUBSIDIARIES AND
Complete Hardware Guide for EX 3200 and EX 4200 Switches
 Complete Hardware Guide for EX 3200 and EX 4200 Switches Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net Part Number:, Revision R1 This product
Complete Hardware Guide for EX 3200 and EX 4200 Switches Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net Part Number:, Revision R1 This product
Daniel MeterLink Software v1.40
 Quick Start Manual P/N 3-9000-763, Rev K June 2017 Daniel MeterLink Software v1.40 for Daniel Gas and Liquid Ultrasonic Flow Meters Software License Agreement PLEASE READ THIS SOFTWARE LICENSE AGREEMENT
Quick Start Manual P/N 3-9000-763, Rev K June 2017 Daniel MeterLink Software v1.40 for Daniel Gas and Liquid Ultrasonic Flow Meters Software License Agreement PLEASE READ THIS SOFTWARE LICENSE AGREEMENT
Network-MIDI Driver Installation Guide
 Network-MIDI Driver Installation Guide ATTENTION SOFTWARE LICENSE AGREEMENT PLEASE READ THIS SOFTWARE LICENSE AGREEMENT ( AGREEMENT ) CAREFULLY BEFORE USING THIS SOFTWARE. YOU ARE ONLY PERMITTED TO USE
Network-MIDI Driver Installation Guide ATTENTION SOFTWARE LICENSE AGREEMENT PLEASE READ THIS SOFTWARE LICENSE AGREEMENT ( AGREEMENT ) CAREFULLY BEFORE USING THIS SOFTWARE. YOU ARE ONLY PERMITTED TO USE
HPE Education Services ESE (East and South Europe) Terms and Conditions
 HPE Education Services ESE (East and South Europe) Terms and Conditions These terms and conditions govern the purchase of education services from Hewlett Packard Enterprise Company ( HPE ). 1. Definitions
HPE Education Services ESE (East and South Europe) Terms and Conditions These terms and conditions govern the purchase of education services from Hewlett Packard Enterprise Company ( HPE ). 1. Definitions
LOGO LICENSE AGREEMENT(S) CERTIPORT AND IC³
 LOGO LICENSE AGREEMENT(S) CERTIPORT AND IC³ EXHIBIT B-2 LICENSEE: Address: Attention: Phone: Fax: Email: Account #: CERTIPORT LOGO LICENSE AGREEMENT Authorized Testing Centers This Logo License Agreement
LOGO LICENSE AGREEMENT(S) CERTIPORT AND IC³ EXHIBIT B-2 LICENSEE: Address: Attention: Phone: Fax: Email: Account #: CERTIPORT LOGO LICENSE AGREEMENT Authorized Testing Centers This Logo License Agreement
DME-N Network Driver Installation Guide for M7CL
 DME-N Network Driver Installation Guide for M7CL ATTENTION SOFTWARE LICENSE AGREEMENT PLEASE READ THIS SOFTWARE LICENSE AGREEMENT ( AGREEMENT ) CAREFULLY BEFORE USING THIS SOFTWARE. YOU ARE ONLY PERMITTED
DME-N Network Driver Installation Guide for M7CL ATTENTION SOFTWARE LICENSE AGREEMENT PLEASE READ THIS SOFTWARE LICENSE AGREEMENT ( AGREEMENT ) CAREFULLY BEFORE USING THIS SOFTWARE. YOU ARE ONLY PERMITTED
Administration Guide. Version 4.1r3. Intrusion Detection and Prevention. Juniper Networks, Inc.
 Intrusion Detection and Prevention Administration Guide Version 4.1r3 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net Copyright 2009, Juniper
Intrusion Detection and Prevention Administration Guide Version 4.1r3 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net Copyright 2009, Juniper
Webfont License End User License Agreement (EULA)
 Hurme Design Webfont End User License Agreement 2018 Page 1 5 Webfont License End User License Agreement (EULA) Hurme Design 2018 This License Agreement ( Agreement or License ) is a legal contract between
Hurme Design Webfont End User License Agreement 2018 Page 1 5 Webfont License End User License Agreement (EULA) Hurme Design 2018 This License Agreement ( Agreement or License ) is a legal contract between
SUPPORT SERVICES FOR DGX PRODUCTS TERMS AND CONDITIONS Release Date: August 17, 2017
 SUPPORT SERVICES FOR DGX PRODUCTS TERMS AND CONDITIONS Release Date: August 17, 2017 WHAT SUPPORT SERVICES ARE INCLUDED NVIDIA Corporation or a designated subsidiary of NVIDIA Corporation with distribution
SUPPORT SERVICES FOR DGX PRODUCTS TERMS AND CONDITIONS Release Date: August 17, 2017 WHAT SUPPORT SERVICES ARE INCLUDED NVIDIA Corporation or a designated subsidiary of NVIDIA Corporation with distribution
Junosphere. Connector Guide. Release 2.4. Published: Revision 4. Copyright 2012, Juniper Networks, Inc.
 Junosphere Connector Guide Release 2.4 Published: 2012-07-24 Revision 4 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net This product includes
Junosphere Connector Guide Release 2.4 Published: 2012-07-24 Revision 4 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net This product includes
FLUENDO GENERIC EULA
 FLUENDO GENERIC EULA FLUENDO S.A. Avenida Diagonal 579, 8th floor 08014 Barcelona Spain 1 END USER LICENSE AGREEMENT (EULA) FLUENDO LICENSE AGREEMENT BY FLUENDO, S.A. ( FLUENDO ) IMPORTANT - READ CAREFULLY
FLUENDO GENERIC EULA FLUENDO S.A. Avenida Diagonal 579, 8th floor 08014 Barcelona Spain 1 END USER LICENSE AGREEMENT (EULA) FLUENDO LICENSE AGREEMENT BY FLUENDO, S.A. ( FLUENDO ) IMPORTANT - READ CAREFULLY
Beta Testing Licence Agreement
 Beta Testing Licence Agreement This Beta Testing Licence Agreement is a legal agreement (hereinafter Agreement ) between BullGuard UK Limited ( BullGuard ) and you, either an individual or a single entity,
Beta Testing Licence Agreement This Beta Testing Licence Agreement is a legal agreement (hereinafter Agreement ) between BullGuard UK Limited ( BullGuard ) and you, either an individual or a single entity,
Site Impact Policies for Website Use
 Site Impact Policies for Website Use Thank you for visiting the Site Impact website (the Website ). We have set up some ground rules to ensure protection of our rights and yours. Site Impact reserves the
Site Impact Policies for Website Use Thank you for visiting the Site Impact website (the Website ). We have set up some ground rules to ensure protection of our rights and yours. Site Impact reserves the
HIGHSOFT SOLUTIONS AS STANDARD LICENSE TERMS AND CONDITIONS 2.2
 HIGHSOFT SOLUTIONS AS STANDARD LICENSE TERMS AND CONDITIONS 2.2 1. Definitions: Agreement shall mean the standard terms and conditions in this document; Confidential Information shall mean any and all
HIGHSOFT SOLUTIONS AS STANDARD LICENSE TERMS AND CONDITIONS 2.2 1. Definitions: Agreement shall mean the standard terms and conditions in this document; Confidential Information shall mean any and all
PLAINSCAPITAL BANK SAMSUNG PAY TERMS AND CONDITIONS - PERSONAL
 PLAINSCAPITAL BANK SAMSUNG PAY TERMS AND CONDITIONS - PERSONAL Last Modified: 3/12/2018 These terms and conditions ( Terms and Conditions ) are a legal agreement between you and PlainsCapital Bank that
PLAINSCAPITAL BANK SAMSUNG PAY TERMS AND CONDITIONS - PERSONAL Last Modified: 3/12/2018 These terms and conditions ( Terms and Conditions ) are a legal agreement between you and PlainsCapital Bank that
OCTOSHAPE SDK AND CLIENT LICENSE AGREEMENT (SCLA)
 OCTOSHAPE SDK AND CLIENT LICENSE AGREEMENT (SCLA) This is a License Agreement (the "Agreement") for certain code (the Software ) owned by Akamai Technologies, Inc. ( Akamai ) that is useful in connection
OCTOSHAPE SDK AND CLIENT LICENSE AGREEMENT (SCLA) This is a License Agreement (the "Agreement") for certain code (the Software ) owned by Akamai Technologies, Inc. ( Akamai ) that is useful in connection
Bar Code Discovery. Administrator's Guide
 Bar Code Discovery Administrator's Guide November 2012 www.lexmark.com Contents 2 Contents Overview...3 Configuring the application...4 Configuring the application...4 Configuring Bar Code Discovery...4
Bar Code Discovery Administrator's Guide November 2012 www.lexmark.com Contents 2 Contents Overview...3 Configuring the application...4 Configuring the application...4 Configuring Bar Code Discovery...4
STRM Administration Guide
 Security Threat Response Manager Release 20.2 Juniper Networks, Inc. 94 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 204-09-2 Copyright Notice Copyright 20 Juniper
Security Threat Response Manager Release 20.2 Juniper Networks, Inc. 94 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 204-09-2 Copyright Notice Copyright 20 Juniper
Junos Pulse Access Control Service
 Junos Pulse Access Control Service UAC Solution Guide for SRX Series Services Gateways Release 4.4 Published: 2013-02-15 Revision 1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California
Junos Pulse Access Control Service UAC Solution Guide for SRX Series Services Gateways Release 4.4 Published: 2013-02-15 Revision 1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California
CALSTRS ONLINE AGREEMENT TERMS AND CONDITIONS
 CALSTRS ONLINE AGREEMENT TERMS AND CONDITIONS INTRODUCTION: Before the California State Teachers Retirement System (hereinafter "CalSTRS," "We," or "Us") will provide services found at mycalstrs.com (the
CALSTRS ONLINE AGREEMENT TERMS AND CONDITIONS INTRODUCTION: Before the California State Teachers Retirement System (hereinafter "CalSTRS," "We," or "Us") will provide services found at mycalstrs.com (the
Terms Of Use AGREEMENT BETWEEN USER AND DRAKE MODIFICATION OF THESE TERMS OF USE LINKS TO THIRD PARTY WEB SITES USE OF COOKIES
 Terms Of Use AGREEMENT BETWEEN USER AND DRAKE This website and other related websites and mobile applications (collectively referred to as "Sites") comprise various web pages and services operated by Drake
Terms Of Use AGREEMENT BETWEEN USER AND DRAKE This website and other related websites and mobile applications (collectively referred to as "Sites") comprise various web pages and services operated by Drake
PORSCHE DESIGN SMARTPHONE FROM BLACKBERRY REPAIR SERVICE TERMS AND CONDITIONS
 PORSCHE DESIGN SMARTPHONE FROM BLACKBERRY REPAIR SERVICE TERMS AND CONDITIONS THESE PORSCHE DESIGN SMARTPHONE FROM BLACKBERRY REPAIR SERVICE TERMS AND CONDITIONS (THIS AGREEMENT ) FORM A LEGAL AGREEMENT
PORSCHE DESIGN SMARTPHONE FROM BLACKBERRY REPAIR SERVICE TERMS AND CONDITIONS THESE PORSCHE DESIGN SMARTPHONE FROM BLACKBERRY REPAIR SERVICE TERMS AND CONDITIONS (THIS AGREEMENT ) FORM A LEGAL AGREEMENT
The Travel Tree Terms and Conditions
 The Travel Tree Terms and Conditions Please read the following Terms & Conditions carefully before using this site. Use of this site indicates acceptance of these Terms and Conditions. The following terms
The Travel Tree Terms and Conditions Please read the following Terms & Conditions carefully before using this site. Use of this site indicates acceptance of these Terms and Conditions. The following terms
Juniper Secure Analytics Virtual Appliance Installation Guide
 Juniper Secure Analytics Virtual Appliance Installation Guide Release 7.3.0 Modified: 2017-09- Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 9089 USA 08-75-2000 www.juniper.net Copyright
Juniper Secure Analytics Virtual Appliance Installation Guide Release 7.3.0 Modified: 2017-09- Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 9089 USA 08-75-2000 www.juniper.net Copyright
Apple Inc. itunes 10 and QuickTime 7 Bundling Agreement (University CD Distribution) Licensee (Institution Name): Individual to Contact:
 Apple Inc. itunes 10 and QuickTime 7 Bundling Agreement (University CD Distribution) Please complete, sign and mail this agreement to: APPLE INC. Software Licensing Department 12545 Riata Vista Circle
Apple Inc. itunes 10 and QuickTime 7 Bundling Agreement (University CD Distribution) Please complete, sign and mail this agreement to: APPLE INC. Software Licensing Department 12545 Riata Vista Circle
End User License Agreement
 End User License Agreement This End User License Agreement ( EULA ) is a legal agreement between the end-user Customer of Gigamon hardware and software products ( Customer ) and Gigamon Inc. ( Gigamon
End User License Agreement This End User License Agreement ( EULA ) is a legal agreement between the end-user Customer of Gigamon hardware and software products ( Customer ) and Gigamon Inc. ( Gigamon
Updated December 12, Chapter 10 Service Description IBM Cloud for Government
 Updated December 12, 2018 Chapter 10 Service Description IBM Cloud for Government IBM Cloud for Government This Service Description describes IBM s Cloud for Government available to Clients under the Federal
Updated December 12, 2018 Chapter 10 Service Description IBM Cloud for Government IBM Cloud for Government This Service Description describes IBM s Cloud for Government available to Clients under the Federal
CBA850 3G/4G/LTE Wireless WAN Bridge Application Guide
 CBA850 3G/4G/LTE Wireless WAN Bridge Application Guide Modified: 2016-06-06 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights reserved.
CBA850 3G/4G/LTE Wireless WAN Bridge Application Guide Modified: 2016-06-06 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights reserved.
ABSOFT Corporation Software License Agreement. Specifically for IMSL FORTRAN 5.0 BUNDLED WITH FORTRAN COMPILERS FROM ABSOFT FOR WINDOWS OR OS X
 ABSOFT Corporation Software License Agreement Specifically for IMSL FORTRAN 5.0 BUNDLED WITH FORTRAN COMPILERS FROM ABSOFT FOR WINDOWS OR OS X (March 2008) IMPORTANT - READ THIS ENTIRE LICENSE AGREEMENT
ABSOFT Corporation Software License Agreement Specifically for IMSL FORTRAN 5.0 BUNDLED WITH FORTRAN COMPILERS FROM ABSOFT FOR WINDOWS OR OS X (March 2008) IMPORTANT - READ THIS ENTIRE LICENSE AGREEMENT
AhnLab Software License Agreement
 AhnLab Software License Agreement IMPORTANT - READ CAREFULLY BEFORE USING THE SOFTWARE. This AhnLab Software License Agreement (this "Agreement") is a legal agreement by and between you and AhnLab, Inc.
AhnLab Software License Agreement IMPORTANT - READ CAREFULLY BEFORE USING THE SOFTWARE. This AhnLab Software License Agreement (this "Agreement") is a legal agreement by and between you and AhnLab, Inc.
CA File Master Plus. Release Notes. Version
 CA File Master Plus Release Notes Version 9.0.00 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation ) is for
CA File Master Plus Release Notes Version 9.0.00 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation ) is for
Entrust WAP Server Certificate Relying Party Agreement
 Entrust WAP Server Certificate Relying Party Agreement The WAP/WTLS specification v1.1 does not provide a means for certificate revocation checking. The following Relying Party Agreement" provides further
Entrust WAP Server Certificate Relying Party Agreement The WAP/WTLS specification v1.1 does not provide a means for certificate revocation checking. The following Relying Party Agreement" provides further
BCDC 2E, 2012 (On-line Bidding Document for Stipulated Price Bidding)
 BCDC 2E, 2012 (On-line Bidding Document for Stipulated Price Bidding) CLAUSE 13 ON-LINE BIDDING 13.1 ON-LINE BIDDING.1 Definitions: Owner means the party and/or their agent designated to receive on-line
BCDC 2E, 2012 (On-line Bidding Document for Stipulated Price Bidding) CLAUSE 13 ON-LINE BIDDING 13.1 ON-LINE BIDDING.1 Definitions: Owner means the party and/or their agent designated to receive on-line
Mobile Banking Enrollment Terms & Conditions
 END USER TERMS Mobile Banking Enrollment Terms & Conditions This service is provided to you by Bremer Bank and powered by a Third Party (the Licensor ) mobile technology solution. Section A of these End
END USER TERMS Mobile Banking Enrollment Terms & Conditions This service is provided to you by Bremer Bank and powered by a Third Party (the Licensor ) mobile technology solution. Section A of these End
Oracle Binary Code License Agreement for the Java SE Platform Products and JavaFX
 Oracle Binary Code License Agreement for the Java SE Platform Products and JavaFX ORACLE AMERICA, INC. ("ORACLE"), FOR AND ON BEHALF OF ITSELF AND ITS SUBSIDIARIES AND AFFILIATES UNDER COMMON CONTROL,
Oracle Binary Code License Agreement for the Java SE Platform Products and JavaFX ORACLE AMERICA, INC. ("ORACLE"), FOR AND ON BEHALF OF ITSELF AND ITS SUBSIDIARIES AND AFFILIATES UNDER COMMON CONTROL,
STRM Series to JSA Series
 STRM Series to JSA Series Migration Guide Published: 2014-06-04 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights reserved. Juniper
STRM Series to JSA Series Migration Guide Published: 2014-06-04 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights reserved. Juniper
You may use the Service to either access, establish or change the following:
 Online Access Agreement June 18, 2015 (Revision date) I. Introduction This Online Access Agreement (this "Agreement") contains the terms that govern your use of the Participants' Private Area of the www.afmsagaftrafund.org
Online Access Agreement June 18, 2015 (Revision date) I. Introduction This Online Access Agreement (this "Agreement") contains the terms that govern your use of the Participants' Private Area of the www.afmsagaftrafund.org
Installation and Configuration Guide
 Installation and Configuration Guide BlackBerry Blend Version 1.2 Published: 2015-07-06 SWD-20150706173035792 Contents About BlackBerry Blend... 4 BlackBerry Blend architecture... 4 Security... 5 IT policy
Installation and Configuration Guide BlackBerry Blend Version 1.2 Published: 2015-07-06 SWD-20150706173035792 Contents About BlackBerry Blend... 4 BlackBerry Blend architecture... 4 Security... 5 IT policy
PRIVATE MOBILE CONNECTION (formerly COMMERCIAL CONNECTIVITY SERVICE (CCS)) CUSTOM APN ATTACHMENT
 PRIVATE MOBILE CONNECTION (formerly COMMERCIAL CONNECTIVITY SERVICE (CCS)) CUSTOM APN ATTACHMENT Last Revised: 12/20/17 1. Private Mobile Connection - Custom APN. Pursuant to the terms and conditions of
PRIVATE MOBILE CONNECTION (formerly COMMERCIAL CONNECTIVITY SERVICE (CCS)) CUSTOM APN ATTACHMENT Last Revised: 12/20/17 1. Private Mobile Connection - Custom APN. Pursuant to the terms and conditions of
PRODUCT GUIDE. N u c l e u s D a t a R e c o v e r y. C o m P r i v a t e L i m i t e d
 PRODUCT GUIDE Table of Contents 1. About Kernel for PST Compress and Compact...4 1.1 Using this Manual...4 1.2 Introduction to Kernel for Compress and Compact...4 1.3 Key Features...5 1.4 System Requirements...5
PRODUCT GUIDE Table of Contents 1. About Kernel for PST Compress and Compact...4 1.1 Using this Manual...4 1.2 Introduction to Kernel for Compress and Compact...4 1.3 Key Features...5 1.4 System Requirements...5
TERMS OF SERVICE AGREEMENT
 TERMS OF SERVICE AGREEMENT LAST REVISION: [Date-Month-Year] PLEASE READ THIS TERMS OF SERVICE AGREEMENT CAREFULLY. BY USING THIS WEBSITE OR ORDERING PRODUCTS FROM THIS WEBSITE YOU AGREE TO BE BOUND BY
TERMS OF SERVICE AGREEMENT LAST REVISION: [Date-Month-Year] PLEASE READ THIS TERMS OF SERVICE AGREEMENT CAREFULLY. BY USING THIS WEBSITE OR ORDERING PRODUCTS FROM THIS WEBSITE YOU AGREE TO BE BOUND BY
Online Localization Service
 DEVELOPER EXPRESS INC DEVEXPRESS Copyright (C) 2011-2017 Developer Express Inc. IMPORTANT- READ CAREFULLY: This DEVELOPER EXPRESS INC ("DEVEXPRESS") End-User License Agreement ("EULA") is a legal agreement
DEVELOPER EXPRESS INC DEVEXPRESS Copyright (C) 2011-2017 Developer Express Inc. IMPORTANT- READ CAREFULLY: This DEVELOPER EXPRESS INC ("DEVEXPRESS") End-User License Agreement ("EULA") is a legal agreement
CERTIFIED MAIL LABELS TERMS OF USE and PRIVACY POLICY Agreement
 CERTIFIED MAIL LABELS TERMS OF USE and PRIVACY POLICY Agreement Welcome to Certified Mail Envelopes and Certified Mail Labels web sites (the Site ) a website, trademark and business name owned and operated
CERTIFIED MAIL LABELS TERMS OF USE and PRIVACY POLICY Agreement Welcome to Certified Mail Envelopes and Certified Mail Labels web sites (the Site ) a website, trademark and business name owned and operated
XO SITE SECURITY SERVICES
 XO SITE SECURITY SERVICES 1.0 Product and Services 1.1 Product Description. XO Site Security (the "Service") is a managed security service which uses Premises-based, multi-threat sensing Customer Premises
XO SITE SECURITY SERVICES 1.0 Product and Services 1.1 Product Description. XO Site Security (the "Service") is a managed security service which uses Premises-based, multi-threat sensing Customer Premises
1.4 Oracle Linux/Oracle VM Term(s) is defined as the duration for which You have acquired the applicable Oracle Linux/Oracle VM Service Offering(s).
 ORACLE LINUX AND ORACLE VM SERVICES AGREEMENT GENERAL TERMS This Oracle Linux and Oracle VM Services Agreement is between Oracle America, Inc. ( Oracle ) and the individual or entity identified below in
ORACLE LINUX AND ORACLE VM SERVICES AGREEMENT GENERAL TERMS This Oracle Linux and Oracle VM Services Agreement is between Oracle America, Inc. ( Oracle ) and the individual or entity identified below in
Apple Inc. Certification Authority Certification Practice Statement
 Apple Inc. Certification Authority Certification Practice Statement Apple Application Integration Sub-CA Apple Application Integration 2 Sub-CA Apple Application Integration - G3 Sub-CA Version 6.2 Effective
Apple Inc. Certification Authority Certification Practice Statement Apple Application Integration Sub-CA Apple Application Integration 2 Sub-CA Apple Application Integration - G3 Sub-CA Version 6.2 Effective
WEBSITE DESIGN CONTRACT RECITALS AGREEMENT
 WEBSITE DESIGN CONTRACT We are delighted that you have selected Wards Enterprise Web Design, Inc. for your website design needs! We look forward to working with you on this exciting project. In order to
WEBSITE DESIGN CONTRACT We are delighted that you have selected Wards Enterprise Web Design, Inc. for your website design needs! We look forward to working with you on this exciting project. In order to
Weebly API Terms of Use
 Weebly API Terms of Use Thank you for using Weebly s application programming interfaces (the "Weebly APIs"). By accessing and using the Weebly APIs, including using the Weebly APIs through a third-party
Weebly API Terms of Use Thank you for using Weebly s application programming interfaces (the "Weebly APIs"). By accessing and using the Weebly APIs, including using the Weebly APIs through a third-party
MX480 3D Universal Edge Router
 MX480 3D Universal Edge Router Hardware Guide Published: 2013-08-29 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net This product includes
MX480 3D Universal Edge Router Hardware Guide Published: 2013-08-29 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net This product includes
Junos OS Multiple Instances for Label Distribution Protocol Feature Guide Release 11.4 Published: Copyright 2011, Juniper Networks, Inc.
 Junos OS Multiple Instances for Label Distribution Protocol Feature Guide Release 11.4 Published: 2011-11-08 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000
Junos OS Multiple Instances for Label Distribution Protocol Feature Guide Release 11.4 Published: 2011-11-08 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000
SonicWall Secure Mobile Access SMA 500v Virtual Appliance 8.6. Getting Started Guide
 SonicWall Secure Mobile Access SMA 500v Virtual Appliance 8.6 Getting Started Guide Copyright 2017 SonicWall Inc. All rights reserved. SonicWall is a trademark or registered trademark of SonicWall Inc.
SonicWall Secure Mobile Access SMA 500v Virtual Appliance 8.6 Getting Started Guide Copyright 2017 SonicWall Inc. All rights reserved. SonicWall is a trademark or registered trademark of SonicWall Inc.
JunosE Software for E Series Broadband Services Routers
 JunosE Software for E Series Broadband Services Routers RADIUS Dynamic-Request Server Release 14.3.x Published: 2013-07-15 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089
JunosE Software for E Series Broadband Services Routers RADIUS Dynamic-Request Server Release 14.3.x Published: 2013-07-15 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089
Apple Inc. Certification Authority Certification Practice Statement
 Apple Inc. Certification Authority Certification Practice Statement Apple Application Integration Sub-CA Apple Application Integration 2 Sub-CA Apple Application Integration - G3 Sub-CA Version 6.3 Effective
Apple Inc. Certification Authority Certification Practice Statement Apple Application Integration Sub-CA Apple Application Integration 2 Sub-CA Apple Application Integration - G3 Sub-CA Version 6.3 Effective
Z.com Hosting Service Order
 1 Z.com Hosting Service Order This Z.com Hosting Service Order (hereinafter referred to as the Order ) is an integral part of the Master Service Agreement (hereinafter referred to as the Agreement or MSA
1 Z.com Hosting Service Order This Z.com Hosting Service Order (hereinafter referred to as the Order ) is an integral part of the Master Service Agreement (hereinafter referred to as the Agreement or MSA
Upgrading STRM to
 Security Threat Response Manager Release 2013.2 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2015-04-27 Copyright Notice Copyright 2015
Security Threat Response Manager Release 2013.2 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2015-04-27 Copyright Notice Copyright 2015
VSC-PCTS2003 TEST SUITE TIME-LIMITED LICENSE AGREEMENT
 VSC-PCTS2003 TEST SUITE TIME-LIMITED LICENSE AGREEMENT Notes These notes are intended to help prospective licensees complete the attached Test Suite Time-Limited License Agreement. If you wish to execute
VSC-PCTS2003 TEST SUITE TIME-LIMITED LICENSE AGREEMENT Notes These notes are intended to help prospective licensees complete the attached Test Suite Time-Limited License Agreement. If you wish to execute
TOOLS for n Version2 Update Guide
 TOOLS for n Version2 Update Guide SOFTWARE LICENSE AGREEMENT PLEASE READ THIS SOFTWARE LICENSE AGREEMENT ( AGREEMENT ) CAREFULLY BEFORE USING THIS SOFTWARE. YOU ARE ONLY PERMITTED TO USE THIS SOFTWARE
TOOLS for n Version2 Update Guide SOFTWARE LICENSE AGREEMENT PLEASE READ THIS SOFTWARE LICENSE AGREEMENT ( AGREEMENT ) CAREFULLY BEFORE USING THIS SOFTWARE. YOU ARE ONLY PERMITTED TO USE THIS SOFTWARE
INCLUDING MEDICAL ADVICE DISCLAIMER
 Jordan s Guardian Angels Terms and Conditions of Use INCLUDING MEDICAL ADVICE DISCLAIMER Your use of this website and its content constitutes your agreement to be bound by these terms and conditions of
Jordan s Guardian Angels Terms and Conditions of Use INCLUDING MEDICAL ADVICE DISCLAIMER Your use of this website and its content constitutes your agreement to be bound by these terms and conditions of
SafeNet Authentication Client
 SafeNet Authentication Client Integration Guide All information herein is either public information or is the property of and owned solely by Gemalto and/or its subsidiaries who shall have and keep the
SafeNet Authentication Client Integration Guide All information herein is either public information or is the property of and owned solely by Gemalto and/or its subsidiaries who shall have and keep the
AGREEMENT FOR RECEIPT AND USE OF MARKET DATA: ADDITIONAL PROVISIONS
 EXHIBIT C AGREEMENT FOR RECEIPT AND USE OF MARKET DATA: ADDITIONAL PROVISIONS 21. NYSE DATA PRODUCTS (a) SCOPE This Exhibit C applies insofar as Customer receives, uses and redistributes NYSE Data Products
EXHIBIT C AGREEMENT FOR RECEIPT AND USE OF MARKET DATA: ADDITIONAL PROVISIONS 21. NYSE DATA PRODUCTS (a) SCOPE This Exhibit C applies insofar as Customer receives, uses and redistributes NYSE Data Products
Troubleshooting Guide
 Juniper Secure Analytics Release 2014.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2014-13-03 Copyright Notice Copyright 2014 Juniper
Juniper Secure Analytics Release 2014.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2014-13-03 Copyright Notice Copyright 2014 Juniper
TERMS OF USE. 1.3 This Site is intended for personal use only. Any commercial use without the prior written consent of Eretz Hemdah is prohibited.
 TERMS OF USE 1. General 1.1 The Eretz Hemdah organization and the Eretz Hemdah higher education institute for Jewish studies in Jerusalem and/or any of its representatives ( Eretz Hemdah or the Operator
TERMS OF USE 1. General 1.1 The Eretz Hemdah organization and the Eretz Hemdah higher education institute for Jewish studies in Jerusalem and/or any of its representatives ( Eretz Hemdah or the Operator
Subscriber Management in a Wireless Roaming Environment
 Subscriber Management in a Wireless Roaming Environment Published: 2014-06-06 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights reserved.
Subscriber Management in a Wireless Roaming Environment Published: 2014-06-06 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights reserved.
Release Notes. BlackBerry Enterprise Identity
 Release Notes BlackBerry Enterprise Identity Published: 2018-03-13 SWD-20180606100327990 Contents New in this release...4 Fixed issues...5 Known issues... 6 Legal notice...8 New in this release New in
Release Notes BlackBerry Enterprise Identity Published: 2018-03-13 SWD-20180606100327990 Contents New in this release...4 Fixed issues...5 Known issues... 6 Legal notice...8 New in this release New in
NOOTRY TERMS OF SERVICE
 NOOTRY TERMS OF SERVICE Nootry LLC ( Nootry ), a Delaware limited liabilities company, provides access to and use of the services, including our website, APIs, email notifications, and application (the
NOOTRY TERMS OF SERVICE Nootry LLC ( Nootry ), a Delaware limited liabilities company, provides access to and use of the services, including our website, APIs, email notifications, and application (the
HPE CUSTOMER TERMS - PORTFOLIO
 HPE Agreement Number(s) where required:. HPE entity: Customer: Effective Date (if applicable):. Term Length (if applicable):... HPE CUSTOMER TERMS - PORTFOLIO 1. Parties. These terms represent the agreement
HPE Agreement Number(s) where required:. HPE entity: Customer: Effective Date (if applicable):. Term Length (if applicable):... HPE CUSTOMER TERMS - PORTFOLIO 1. Parties. These terms represent the agreement
