Mobile Telephony Threats in Asia
|
|
|
- Antony Carpenter
- 5 years ago
- Views:
Transcription
1 Mobile Telephony Threats in Asia Black Hat Asia 2017, Singapore Dr. Marco Balduzzi Dr. Payas Gupta Lion Gu Sr. Threat Researcher Data Scientist Sr. Threat Researcher Trend Micro Pindrop Trend Micro Joint work with Prof. Debin Gao (SMU) and Prof. Mustaque Ahamad (GaTech)
2 th Marco s 9 BH Anniversary :-) 2
3 Click to play recording [removed] 3
4 Wangiri Fraud, Japan 4
5 Fake Officials Fraud, China 5
6 This is your Telco calling, UAE 6
7 Police Scam, Singapore 7
8 BringBackOurCash, Nigeria 8
9 Why is Happening? Lack of users awareness Users publicly disclose their mobile numbers Expose themselves and the organization they work for! 9
10 Current Defeat Strategies Telcos Crowd sourced FTC, fraud complaints 800notes open datasets Proprietary 10 10
11 Missing Caller's Details 11
12 No Actual Timestamps 12
13 Perception v/s Reality 13
14 Not all Fraudulent Calls are Reported Compared both FTC and 800notes against each other for a certain set of numbers 14
15 Delay in Reporting Fraudulent Calls 15
16 Any Solution?
17 17
18 Using SIP Trunks Call IP Tel. ext Switch Call Manager/ PBX IP Tel. ext SIP Trunk Telephone Exchange Rules Destination no. Destination IP Incoming call Incoming call Incoming call Incoming call Call Manager table Tel. Range to IP Tel. ext Honeypot 18
19 Using GSM/VoIP Gateways 19
20 Mobile Telephony Honeypot 20
21 Mobile Telephony Honeypot 21
22 Example of Call Recording
23 Example of SMS Recording 确认了哈 位置还留起的 之前在等qq消息 我刚才电话问 了 给我转款吧 建 行四川分行第五支行 户名 王玲 (I have confirmed. Reservation is still valid. I am waiting QQ message, and I contact you by phone call. Please transfer money to me. China Construction Bank Sichuan Provincial Branch Fifth Sub-branch, account number: , account name: Wang Ling) 23 23
24 24
25 How to make honeypot numbers appealing to fraudsters?
26 Seeding Social network Mobile malware Abuse list 26
27 Simulating Social-Network Leaks 27
28 Mobile Malware Leak Honeypot numbers in contact list ~400 samples of 60 families Track 140 C&C leakages Taint Droid Network traffic 28
29 Active Engagement with Fraudsters reported (abuse) numbers Engaged with SMS and one-ring call I am fine with our discussion. How do we want to proceed? 29
30 General Results 30
31 Effect of Seeding 31
32 Social Networks Very effective Picked up by Xinhua Quanmei [*] Daily news in the form of spam -> 221 messages [*] 32
33 Malicious Apps 79 ADs from Self-promoting app [*] (mal1) (mal2) are spoofed [*] 33
34 Fraudsters Strategies 34
35 Blended Malicious Traffic 35
36 Concealed Caller Numbers 51% fraudsters: Use of SMS gateways and VoIP services to hide identity Use of foreign sim-cards (mainly Thailand) Use of split-paid services to reduce cost on international calls 36
37 Social Engineering Human = weakest point in chain Multi-hop attack, similar to BEC Lateral movements 37 37
38 Multi-step Attack Repeated over time Combination of Calls and SMS Pretend to know the victim Confirm IM Ask for IM contact Confirm paypal Send payment instructions (paypal) 38
39 The Big Boss Example 39
40 Google Business Listing List your business online on Google Click here for recording [removed]. 40
41 Can you hear me? Subscribe you to services when you say YES Click here for recording. [removed] 41
42 Tax Collection Agency Find you and call you Intimidation Pay using tax vouchers 42
43 Technical Support Scam 43
44 Use of intimidation Postal service Fee requested for a package in customs hold Telephony provider Contract suspended because bill not paid 44
45 How campaigns operate? Use of multiple calling numbers to avoid easy detection Common sources Multiple campaigns ran by the same gang 45
46 Authentication Bypass [Tencent] Verification code Use it to change the password of the QQ number 64******5. Leaking the verification code has a risk. The QQ Security Center. Reuse of previously-terminated numbers Circumvent 2-factor auth! 46
47 Defensive Strategies 1) 2) 3) 4) 47 Adopt reputation-based solutions Protect your number Don t get social engineered Look after your 2 auth 47
48 Thanks! 48 48
Understanding Cyber Attacks That Leverage the Telephony Channel
 SESSION ID: CCT-R04 Understanding Cyber Attacks That Leverage the Telephony Channel Payas Gupta Research Scientist CRISSP-AD, New York University Abu Dhabi payasgupta@nyu.edu In collaboration with Mustaque
SESSION ID: CCT-R04 Understanding Cyber Attacks That Leverage the Telephony Channel Payas Gupta Research Scientist CRISSP-AD, New York University Abu Dhabi payasgupta@nyu.edu In collaboration with Mustaque
Fraude dans la Telephonie
 Fraude dans la Telephonie Aurélien Francillon Merve Sahin With Monaco Telecom Also with cooperations: NYU Abu Dhabi Georgia Tech Telecom Paris Tech (Marc Relieu) Telephony Fraud A long-standing problem
Fraude dans la Telephonie Aurélien Francillon Merve Sahin With Monaco Telecom Also with cooperations: NYU Abu Dhabi Georgia Tech Telecom Paris Tech (Marc Relieu) Telephony Fraud A long-standing problem
We will divide the many telecom fraud schemes into three broad categories, based on who the fraudsters are targeting. These categories are:
 Introduction to Telecom Fraud This guide will help you learn about the different types of telecom fraud and industry best practices for detection and prevention. Three Major Categories of Telecom Fraud
Introduction to Telecom Fraud This guide will help you learn about the different types of telecom fraud and industry best practices for detection and prevention. Three Major Categories of Telecom Fraud
Newcomer Finances Toolkit. Fraud. Worksheets
 Newcomer Finances Toolkit Fraud Worksheets Ottawa Community Loan Fund Fonds d emprunt Communautaire d Ottawa 22 O Meara St., Causeway Work Centre, Ottawa, ON K1Y 4N6 Tel: 613-594-3535 Fax: 613-594-8118
Newcomer Finances Toolkit Fraud Worksheets Ottawa Community Loan Fund Fonds d emprunt Communautaire d Ottawa 22 O Meara St., Causeway Work Centre, Ottawa, ON K1Y 4N6 Tel: 613-594-3535 Fax: 613-594-8118
Who We Are! Natalie Timpone
 Who We Are! Natalie Timpone Manager of Security Business Management Office Enterprise Security Awareness Manager Carmelo Walsh Security, Risk, and Compliance Security Awareness Subject Matter Expert Who
Who We Are! Natalie Timpone Manager of Security Business Management Office Enterprise Security Awareness Manager Carmelo Walsh Security, Risk, and Compliance Security Awareness Subject Matter Expert Who
Telephony Fraud and Abuse. Merve Sahin
 Telephony Fraud and Abuse Merve Sahin sahin@eurecom.fr Background 2 Telephony Networks Quick history 1870s: Plain Old Telephone System (POTS) Enabled by transmission of voice over copper lines Used in-band
Telephony Fraud and Abuse Merve Sahin sahin@eurecom.fr Background 2 Telephony Networks Quick history 1870s: Plain Old Telephone System (POTS) Enabled by transmission of voice over copper lines Used in-band
Webomania Solutions Pvt. Ltd. 2017
 The other name for link manipulation is Phishing or you can say link manipulation is type of phishing attack done generally to mislead the user to a replica website or a looka-like of some well-known site.
The other name for link manipulation is Phishing or you can say link manipulation is type of phishing attack done generally to mislead the user to a replica website or a looka-like of some well-known site.
ELECTRONIC BANKING & ONLINE AUTHENTICATION
 ELECTRONIC BANKING & ONLINE AUTHENTICATION How Internet fraudsters are trying to trick you What you can do to stop them How multi-factor authentication and other new techniques can help HELPING YOU STAY
ELECTRONIC BANKING & ONLINE AUTHENTICATION How Internet fraudsters are trying to trick you What you can do to stop them How multi-factor authentication and other new techniques can help HELPING YOU STAY
Nuno Pestana, WeDo Technologies
 Nuno Pestana, WeDo Technologies SUBSCRIPTION FRAUD SUBSCRIPTION FRAUD In Raid FMS REAL-TIME Subscription Fraud SUBSCRIPTION FRAUD SUBSCRIPTION FRAUD In Raid FMS REAL-TIME Subscription Fraud FRAUD THE IMPACT
Nuno Pestana, WeDo Technologies SUBSCRIPTION FRAUD SUBSCRIPTION FRAUD In Raid FMS REAL-TIME Subscription Fraud SUBSCRIPTION FRAUD SUBSCRIPTION FRAUD In Raid FMS REAL-TIME Subscription Fraud FRAUD THE IMPACT
Security & Phishing
 Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
Quick recap on ing Security Recap on where to find things on Belvidere website & a look at the Belvidere Facebook page
 Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Frauds & Scams. Why is the Internet so attractive to scam artists? 2006 Internet Fraud Trends. Fake Checks. Nigerian Scam
 Frauds & Scams Why is the Internet so attractive to scam artists? Anonymity Low cost Rapid growth Easy to adapt Be Cyber Savvy with C-SAFE 118 2006 Internet Fraud Trends Average Loss Online Auctions 34%
Frauds & Scams Why is the Internet so attractive to scam artists? Anonymity Low cost Rapid growth Easy to adapt Be Cyber Savvy with C-SAFE 118 2006 Internet Fraud Trends Average Loss Online Auctions 34%
The Spoofing/Authentication Threat
 The Spoofing/Authentication Threat An Analysis of the Spoofing/Authentication Threat in Voice Network Security A Whitepaper From SecureLogix Corporation Introduction Spoofing refers to the act of intentionally
The Spoofing/Authentication Threat An Analysis of the Spoofing/Authentication Threat in Voice Network Security A Whitepaper From SecureLogix Corporation Introduction Spoofing refers to the act of intentionally
Bank of america report phishing
 Search Search pages & people Search Search Search pages & people Search Bank of america report phishing email We recently discovered a new phishing scam from a Bank of America spam email some reports that
Search Search pages & people Search Search Search pages & people Search Bank of america report phishing email We recently discovered a new phishing scam from a Bank of America spam email some reports that
FRAUDULENT TRAVEL SCAMS
 FINANCIAL INTELLIGENCE CENTRE (FIC) REPUBLIC OF NAMIBIA P.O.BOX 2882, Windhoek Tel: + 264 61 2835100, Fax +264 61 2835259 Web address: www.fic.na E-mail address: helpdesk@fic.na FRAUDULENT TRAVEL SCAMS
FINANCIAL INTELLIGENCE CENTRE (FIC) REPUBLIC OF NAMIBIA P.O.BOX 2882, Windhoek Tel: + 264 61 2835100, Fax +264 61 2835259 Web address: www.fic.na E-mail address: helpdesk@fic.na FRAUDULENT TRAVEL SCAMS
LET S TALK MONEY. Fahad Pervaiz. Sam Castle, Galen Weld, Franziska Roesner, Richard Anderson
 LET S TALK MONEY Fahad Pervaiz Sam Castle, Galen Weld, Franziska Roesner, Richard Anderson Unbanked Population Branchless Banking Bank/Financial Institute Bank of America, Standard Chartered Bank Telecommunication
LET S TALK MONEY Fahad Pervaiz Sam Castle, Galen Weld, Franziska Roesner, Richard Anderson Unbanked Population Branchless Banking Bank/Financial Institute Bank of America, Standard Chartered Bank Telecommunication
CYBER SECURITY RESOURCE GUIDE. Cyber Fraud Overview. Best Practices and Resources. Quick Reference Guide for Employees. Cyber Security Checklist
 CORPORATE & INSTITUTIONAL BANKING CYBER SECURITY RESOURCE GUIDE Cyber Fraud Overview Best Practices and Resources Quick Reference Guide for Employees Cyber Security Checklist 2 5 7 9 AWARENESS OF CYBER
CORPORATE & INSTITUTIONAL BANKING CYBER SECURITY RESOURCE GUIDE Cyber Fraud Overview Best Practices and Resources Quick Reference Guide for Employees Cyber Security Checklist 2 5 7 9 AWARENESS OF CYBER
CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s
 CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s ATM Fraud - Watch out for the following scams. Scam 1 - you find you are having difficulty with your card. Someone will come
CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s ATM Fraud - Watch out for the following scams. Scam 1 - you find you are having difficulty with your card. Someone will come
SIP and VoIP What is SIP? What s a Control Channel? History of Signaling Channels
 Network Security - ISA 656 Voice Over IP (VoIP) Security Simple SIP ing Alice s Bob Session Initiation Protocol Control channel for Voice over IP (Other control channel protocols exist, notably H.323 and
Network Security - ISA 656 Voice Over IP (VoIP) Security Simple SIP ing Alice s Bob Session Initiation Protocol Control channel for Voice over IP (Other control channel protocols exist, notably H.323 and
Personal Cybersecurity
 Personal Cybersecurity The Basic Principles Jeremiah School, CEO How big is the issue? 9 8 7 6 5 4 3 2 1 Estimated global damages in 2018 0 2016 2018 2020 2022 2024 2026 2028 2030 Internet Users Billions
Personal Cybersecurity The Basic Principles Jeremiah School, CEO How big is the issue? 9 8 7 6 5 4 3 2 1 Estimated global damages in 2018 0 2016 2018 2020 2022 2024 2026 2028 2030 Internet Users Billions
E N H A N C E D F R A U D D E T E C T I O N U S I N G S I G N A L I N G. W U G M a l a y s i a
 E N H A N C E D F R A U D D E T E C T I O N U S I N G S I G N A L I N G W U G M a l a y s i a 2 0 1 7 CONTACTS NUNO PESTANA FRAUD PROFESSIONAL SERVICES MANAGER +351 939 651 481 nuno.pestana@wedotechnol
E N H A N C E D F R A U D D E T E C T I O N U S I N G S I G N A L I N G W U G M a l a y s i a 2 0 1 7 CONTACTS NUNO PESTANA FRAUD PROFESSIONAL SERVICES MANAGER +351 939 651 481 nuno.pestana@wedotechnol
Ingate SIParator /Firewall SIP Security for the Enterprise
 Ingate SIParator /Firewall SIP Security for the Enterprise Ingate Systems Ingate Systems AB (publ) Tel: +46 8 600 77 50 BACKGROUND... 1 1 NETWORK SECURITY... 2 2 WHY IS VOIP SECURITY IMPORTANT?... 3 3
Ingate SIParator /Firewall SIP Security for the Enterprise Ingate Systems Ingate Systems AB (publ) Tel: +46 8 600 77 50 BACKGROUND... 1 1 NETWORK SECURITY... 2 2 WHY IS VOIP SECURITY IMPORTANT?... 3 3
National Travel Associates
 National Travel Associates Fraud Prevention Module 2012 National Travel Associates Fraud In The Travel Industry With the popularity of online booking engines in the 90 s there was a huge insurgence of
National Travel Associates Fraud Prevention Module 2012 National Travel Associates Fraud In The Travel Industry With the popularity of online booking engines in the 90 s there was a huge insurgence of
It pays to stop and think
 It pays to stop and think Protect yourself from financial fraud Together we thrive 2 In the first six months of 2018, over 34,000 people were scammed out of 145.4m At HSBC, we work hard to keep our customers
It pays to stop and think Protect yourself from financial fraud Together we thrive 2 In the first six months of 2018, over 34,000 people were scammed out of 145.4m At HSBC, we work hard to keep our customers
2014 CliftonLarsonAllen LLP Cyber Crime and Payment Fraud Trends Key Threats to All Businesses CliftonLarsonAllen LLP. CLAconnect.
 Cyber Crime and Payment Fraud Trends Key Threats to All Businesses CLAconnect.com What do the following have in common? Catholic church parish Hospice Collection agency Main Street newspaper stand Electrical
Cyber Crime and Payment Fraud Trends Key Threats to All Businesses CLAconnect.com What do the following have in common? Catholic church parish Hospice Collection agency Main Street newspaper stand Electrical
YOU CAN'T AFFORD FAKE ACCOUNTS. NOW, NEITHER CAN THE FRAUDSTERS. Fraud Report
 YOU CAN'T AFFORD FAKE ACCOUNTS. NOW, NEITHER CAN THE FRAUDSTERS. Fraud Report Fake Accounts and the Black Market There s a thriving black market for fake accounts on the internet. Fake accounts are accounts
YOU CAN'T AFFORD FAKE ACCOUNTS. NOW, NEITHER CAN THE FRAUDSTERS. Fraud Report Fake Accounts and the Black Market There s a thriving black market for fake accounts on the internet. Fake accounts are accounts
EBOOK. Stopping Fraud. How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats.
 EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
Mavenir Spam and Fraud Control
 SOLUTION BRIEF Assuring Operator Revenue and A2P Grey Route Monetization Operators are realizing the scale and potential of A2P (Application to Person) messaging revenues, and how advances in messaging
SOLUTION BRIEF Assuring Operator Revenue and A2P Grey Route Monetization Operators are realizing the scale and potential of A2P (Application to Person) messaging revenues, and how advances in messaging
Safety and Security. April 2015
 Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
Reducing Telecoms Fraud Losses
 Reducing Telecoms Fraud Losses A Telsis White Paper Intelligence for Your Network Introduction According to the Communication Fraud Control Association (CFCA), fraud costs the telecoms industry 1.69% of
Reducing Telecoms Fraud Losses A Telsis White Paper Intelligence for Your Network Introduction According to the Communication Fraud Control Association (CFCA), fraud costs the telecoms industry 1.69% of
Consumerization. Copyright 2014 Trend Micro Inc. IT Work Load
 Complete User Protection Consumerization IT Work Load 2 Then... File/Folder & Removable Media Email & Messaging Web Access Employees IT Admin 3 Now! File/Folder & Removable Media Email & Messaging Web
Complete User Protection Consumerization IT Work Load 2 Then... File/Folder & Removable Media Email & Messaging Web Access Employees IT Admin 3 Now! File/Folder & Removable Media Email & Messaging Web
The Credential Phishing Handbook. Why It Still Works and 4 Steps to Prevent It
 The Credential Phishing Handbook Why It Still Works and 4 Steps to Prevent It Introduction Phishing is more than 20 years old, but still represents more than 90% of targeted attacks. The reason is simple:
The Credential Phishing Handbook Why It Still Works and 4 Steps to Prevent It Introduction Phishing is more than 20 years old, but still represents more than 90% of targeted attacks. The reason is simple:
Common Scams and Fraud. Charlottesville/Albemarle County TRIAD Group
 Common Scams and Fraud Charlottesville/Albemarle County TRIAD Group What We ll Cover 3 parts of a scam or fraud Common scams What can you do? Common Scams Three Parts of Any Scam or Fraud 1. Victim has
Common Scams and Fraud Charlottesville/Albemarle County TRIAD Group What We ll Cover 3 parts of a scam or fraud Common scams What can you do? Common Scams Three Parts of Any Scam or Fraud 1. Victim has
FAQs about Mobile Banking. Mobile Banking is a channel to access Cyberbanking service through BEA App or a web browser of your mobile device.
 FAQs about Mobile Banking Introduction Q1: What is Mobile Banking? Mobile Banking is a channel to access Cyberbanking service through BEA App or a web browser of your mobile device. Q2: What services are
FAQs about Mobile Banking Introduction Q1: What is Mobile Banking? Mobile Banking is a channel to access Cyberbanking service through BEA App or a web browser of your mobile device. Q2: What services are
NOT PROTECTIVELY MARKED PHISHING. July 2016
 - PHISHING July 2016 1 Introduction: The purpose of this document is to provide an analysis of the most prevalent trends and characteristics of phishing campaigns in the UK in July 2016. The analysis is
- PHISHING July 2016 1 Introduction: The purpose of this document is to provide an analysis of the most prevalent trends and characteristics of phishing campaigns in the UK in July 2016. The analysis is
Unified Communications Manager Express Toll Fraud Prevention
 Unified Communications Manager Express Toll Fraud Prevention Document ID: 107626 Contents Introduction Prerequisites Requirements Components Used Conventions Overview Internal vs. External Threats Toll
Unified Communications Manager Express Toll Fraud Prevention Document ID: 107626 Contents Introduction Prerequisites Requirements Components Used Conventions Overview Internal vs. External Threats Toll
How to Catch a Thief. Trends & Technologies in the Fight Against Fraud. Rohan Langley SAS
 How to Catch a Thief Trends & Technologies in the Fight Against Fraud Rohan Langley SAS Global Drivers & Challenges: The Changing Fraud Landscape Fixing Fraud: A Fraud Solution A Real World Example: Online
How to Catch a Thief Trends & Technologies in the Fight Against Fraud Rohan Langley SAS Global Drivers & Challenges: The Changing Fraud Landscape Fixing Fraud: A Fraud Solution A Real World Example: Online
BUILDING AN EFFECTIVE PROGRAM TO PROTECT AGAINST FRAUD
 BUILDING AN EFFECTIVE PROGRAM TO PROTECT AGAINST EMAIL FRAUD Navindra Ramnauth CISSP Principal Sales Engineer 1 2017 Proofpoint, Inc. Proofpoint at a Glance LEADING CUSTOMERS DEEP SECURITY DNA UNIQUE VISIBILITY
BUILDING AN EFFECTIVE PROGRAM TO PROTECT AGAINST EMAIL FRAUD Navindra Ramnauth CISSP Principal Sales Engineer 1 2017 Proofpoint, Inc. Proofpoint at a Glance LEADING CUSTOMERS DEEP SECURITY DNA UNIQUE VISIBILITY
CLICK TO EDIT MASTER TITLE STYLE Fraud Overview and Mitigation Strategies
 Fraud Overview and Mitigation Strategies SUNTRUST TEAM: DOUG HICKMAN SENIOR VICE PRESIDENT FOUNDATIONS AND ENDOWMENTS SPECIALTY PRACTICE JAMES BERNAL ASSISTANT VICE PRESIDENT FOUNDATIONS AND ENDOWMENTS
Fraud Overview and Mitigation Strategies SUNTRUST TEAM: DOUG HICKMAN SENIOR VICE PRESIDENT FOUNDATIONS AND ENDOWMENTS SPECIALTY PRACTICE JAMES BERNAL ASSISTANT VICE PRESIDENT FOUNDATIONS AND ENDOWMENTS
South Central Power Stop Scams
 Don t get tricked. People around the country have been receiving emails and phone calls from scammers. South Central Power wants to help you keep your money and prevent scams. Review the helpful tips below.
Don t get tricked. People around the country have been receiving emails and phone calls from scammers. South Central Power wants to help you keep your money and prevent scams. Review the helpful tips below.
IMPORTANT SECURITY INFORMATION PHISHING
 IMPORTANT SECURITY INFORMATION PHISHING Protect Yourself and Your Accounts Important Security Information At Century Savings Bank, security and privacy of your financial information is a top priority.
IMPORTANT SECURITY INFORMATION PHISHING Protect Yourself and Your Accounts Important Security Information At Century Savings Bank, security and privacy of your financial information is a top priority.
Protecting Your Devices. Dr. Leon D. Chapman
 Protecting Your Devices Dr. Leon D. Chapman 1 Device Security Threats to Devices Scams Passwords Secure your Device Security Apps / Solutions 2 Mobile device security threats ( http://www.csoonline.com/article/2157785/data-protection/five-new-threatsto-your-mobile-device-security.html
Protecting Your Devices Dr. Leon D. Chapman 1 Device Security Threats to Devices Scams Passwords Secure your Device Security Apps / Solutions 2 Mobile device security threats ( http://www.csoonline.com/article/2157785/data-protection/five-new-threatsto-your-mobile-device-security.html
Recognizing Fraud Staying Safe 2018 Information/Cyber Security Training
 Recognizing Fraud Staying Safe 2018 Information/Cyber Security Training Copyright Sage Data Security 2017-2018 All Rights Reserved Presented by: John H Rogers, CISSP Director of Advisory Services john.rogers@sagedatasecurity.com
Recognizing Fraud Staying Safe 2018 Information/Cyber Security Training Copyright Sage Data Security 2017-2018 All Rights Reserved Presented by: John H Rogers, CISSP Director of Advisory Services john.rogers@sagedatasecurity.com
Country Large Bundle Minutes Small Bundle Minutes Total Monthly Minutes United Kingdom 1, ,140
 1. What is ACN Globe Call? ACN Globe Call is a new tariff plan for the ACN Digital Phone Service (DPS) proposition. Customers now have a choice of selecting either ACN Globe Call or ACN Smart, depending
1. What is ACN Globe Call? ACN Globe Call is a new tariff plan for the ACN Digital Phone Service (DPS) proposition. Customers now have a choice of selecting either ACN Globe Call or ACN Smart, depending
What kind of information do you collect, when and how?
 Associated Telecom Solutions Privacy Policy Action- Tec Services Ltd T/A Associated Telecom Solutions collects business data in order to provide our services to our business customers. During the relationship
Associated Telecom Solutions Privacy Policy Action- Tec Services Ltd T/A Associated Telecom Solutions collects business data in order to provide our services to our business customers. During the relationship
EBOOK. Stopping Fraud. How Proofpoint Helps Protect Your Organisation from Impostors, Phishers and Other Non-Malware Threats.
 EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organisation from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organisation from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
Target Breach Overview
 Target Breach Overview Q: Media reports are stating that Target experienced a data breach. Can you provide more specifics? A: Yes, Target has confirmed that it experienced unauthorized access to its systems
Target Breach Overview Q: Media reports are stating that Target experienced a data breach. Can you provide more specifics? A: Yes, Target has confirmed that it experienced unauthorized access to its systems
Smile IT Ltd Privacy Policy. Hello, we re Smile IT Ltd. We offer computer and network support to businesses and home computer users.
 Smile IT Ltd Privacy Policy Hello, we re Smile IT Ltd. We offer computer and network support to businesses and home computer users. At Smile IT we value our clients and we re committed to protecting your
Smile IT Ltd Privacy Policy Hello, we re Smile IT Ltd. We offer computer and network support to businesses and home computer users. At Smile IT we value our clients and we re committed to protecting your
Guide to credit card security
 Contents Click on a title below to jump straight to that section. What is credit card fraud? Types of credit card fraud Current scams Keeping your card and card details safe Banking and shopping securely
Contents Click on a title below to jump straight to that section. What is credit card fraud? Types of credit card fraud Current scams Keeping your card and card details safe Banking and shopping securely
spam goes mobile Comverse User Forum 29th June 2005, Marbella (Spain)
 spam goes mobile Comverse User Forum 29th June 2005, Marbella (Spain) Lara Srivastava Project Director- ITU New Initiatives Programme Strategy and Policy Unit, ITU Note: The views expressed in this presentation
spam goes mobile Comverse User Forum 29th June 2005, Marbella (Spain) Lara Srivastava Project Director- ITU New Initiatives Programme Strategy and Policy Unit, ITU Note: The views expressed in this presentation
FAQ. Usually appear to be sent from official address
 FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
Telecom MISP. Building a Telecom Information Sharing Platform. Alexandre De Oliveira
 Telecom MISP Building a Telecom Information Sharing Platform Alexandre De Oliveira MISP history Actively developed and maintained by CIRCL Computer Incident Response Center Luxembourg Open Source Software
Telecom MISP Building a Telecom Information Sharing Platform Alexandre De Oliveira MISP history Actively developed and maintained by CIRCL Computer Incident Response Center Luxembourg Open Source Software
Best Practices Guide to Electronic Banking
 Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Ages Donʼt Fall for Fake: Activity 1 Don t bite that phishing hook! Goals for children. Letʼs talk
 Ages 11-14 Donʼt Fall for : Activity 1 Don t bite that phishing hook! Children play a game where they study various emails and texts and try to decide which messages are legit and which are phishing scams.
Ages 11-14 Donʼt Fall for : Activity 1 Don t bite that phishing hook! Children play a game where they study various emails and texts and try to decide which messages are legit and which are phishing scams.
AGILE CLOUD PBX OPERATION MANUAL
 AGILE CLOUD PBX OPERATION MANUAL 1 Table of Contents Display set (user information) This manual will explain the "Agile cloud PBX". Prior to use, take a look at our service manual, Please use it and do
AGILE CLOUD PBX OPERATION MANUAL 1 Table of Contents Display set (user information) This manual will explain the "Agile cloud PBX". Prior to use, take a look at our service manual, Please use it and do
Voice over IP. What You Don t Know Can Hurt You. by Darren Bilby
 Voice over IP What You Don t Know Can Hurt You by Darren Bilby What is VoIP? Voice over Internet Protocol A method for taking analog audio signals, like the kind you hear when you talk on the phone, and
Voice over IP What You Don t Know Can Hurt You by Darren Bilby What is VoIP? Voice over Internet Protocol A method for taking analog audio signals, like the kind you hear when you talk on the phone, and
Phishing Discussion. Pete Scheidt Lead Information Security Analyst California ISO
 Phishing Discussion Pete Scheidt Lead Information Security Analyst California ISO 2 Phish What is Phishing Types of Phish 3 Phish What is Phishing Attackers (Phishers) would email (cast their nets) far
Phishing Discussion Pete Scheidt Lead Information Security Analyst California ISO 2 Phish What is Phishing Types of Phish 3 Phish What is Phishing Attackers (Phishers) would email (cast their nets) far
The Bank of East Asia, Limited, Macau Branch BEA Macau iphone Application FAQs for Mobile Banking Service (for iphone, ipod touch, and ipad users)
 The Bank of East Asia, Limited, Macau Branch BEA Macau iphone Application FAQs for Mobile Banking Service (for iphone, ipod touch, and ipad users) Introduction Q1: What services are available via Mobile
The Bank of East Asia, Limited, Macau Branch BEA Macau iphone Application FAQs for Mobile Banking Service (for iphone, ipod touch, and ipad users) Introduction Q1: What services are available via Mobile
The strategies for preventing telecom fraud in EACO countries
 The strategies for preventing telecom fraud in EACO countries 25 th May 2011 Protais KANYANKORE RWANDA UTILITIES REGULATORY AGENCY Table of contents 1. Overview on Grey traffic Affected areas Who is involved
The strategies for preventing telecom fraud in EACO countries 25 th May 2011 Protais KANYANKORE RWANDA UTILITIES REGULATORY AGENCY Table of contents 1. Overview on Grey traffic Affected areas Who is involved
WE SEE YOUR VOICE. SecureLogix We See Your Voice
 ETM SYSTEM WE SEE YOUR VOICE We know some important things about your enterprise things that you may not know yourself. We know that you are significantly overpaying for your corporate voice network and
ETM SYSTEM WE SEE YOUR VOICE We know some important things about your enterprise things that you may not know yourself. We know that you are significantly overpaying for your corporate voice network and
Preventing fraud in public sector entities
 Preventing fraud in public sector entities Fraud is a serious problem that can affect anyone, from individuals to large companies and associations. For public sector entities, fraud both external and internal
Preventing fraud in public sector entities Fraud is a serious problem that can affect anyone, from individuals to large companies and associations. For public sector entities, fraud both external and internal
REDUCING THE RISK OF CARD NOT PRESENT FRAUD
 www.globalpaymentsinc.co.uk REDUCING THE RISK OF CARD NOT PRESENT FRAUD 02 03 REDUCING THE RISK OF CARD NOT PRESENT FRAUD INTRODUCTION Many businesses accept Card Not Present (CNP) transactions on a daily
www.globalpaymentsinc.co.uk REDUCING THE RISK OF CARD NOT PRESENT FRAUD 02 03 REDUCING THE RISK OF CARD NOT PRESENT FRAUD INTRODUCTION Many businesses accept Card Not Present (CNP) transactions on a daily
Terms and Conditions of Mobile Phone Service (Post-Paid) Between Operator and Subscriber
 Terms and Conditions of Mobile Phone Service (Post-Paid) Between Operator and Subscriber Section 1 General 1.1 This Terms and Conditions of Mobile Phone Service shall be effective between Advanced Wireless
Terms and Conditions of Mobile Phone Service (Post-Paid) Between Operator and Subscriber Section 1 General 1.1 This Terms and Conditions of Mobile Phone Service shall be effective between Advanced Wireless
CHATCHAT App User Guide
 CHATCHAT App User Guide Download and Install CHATCHAT App Scan the QR code or search CHATCHAT in the Apple App Store or Google Play Store for the App. Proprietary of Shinetown Telecom 2 Setting Up iphone
CHATCHAT App User Guide Download and Install CHATCHAT App Scan the QR code or search CHATCHAT in the Apple App Store or Google Play Store for the App. Proprietary of Shinetown Telecom 2 Setting Up iphone
A Layered Approach to Fraud Mitigation. Nick White Product Manager, FIS Payments Integrated Financial Services
 A Layered Approach to Fraud Mitigation Nick White Product Manager, FIS Payments Integrated Financial Services Session Agenda Growing Fraud Concerns Old Habits Die Hard Maneuvering through the Barriers
A Layered Approach to Fraud Mitigation Nick White Product Manager, FIS Payments Integrated Financial Services Session Agenda Growing Fraud Concerns Old Habits Die Hard Maneuvering through the Barriers
FREQUENTLY ASKED QUESTIONS
 FREQUENTLY ASKED QUESTIONS In order to better assist you with the transition to our new home banking service, we wanted to provide you with a list of anticipated questions and things that may need your
FREQUENTLY ASKED QUESTIONS In order to better assist you with the transition to our new home banking service, we wanted to provide you with a list of anticipated questions and things that may need your
Security Protection
 Email Security Protection Loay Alayadhi Abstract: Email is the most important business communication tool. Security has been an issue in mail from ancient times. Therefore, email security protection has
Email Security Protection Loay Alayadhi Abstract: Email is the most important business communication tool. Security has been an issue in mail from ancient times. Therefore, email security protection has
Cyber Security Updates and Trends Affecting the Real Estate Industry
 Cyber Security Updates and Trends Affecting the Real Estate Industry What, Why, and How? Agenda Cyber Security Today Changes to Security Standards and Trends Protecting Yourself and Your Organization Takeways
Cyber Security Updates and Trends Affecting the Real Estate Industry What, Why, and How? Agenda Cyber Security Today Changes to Security Standards and Trends Protecting Yourself and Your Organization Takeways
Service Provider View of Cyber Security. July 2017
 Service Provider View of Cyber Security July 2017 Quick Stats Caribbean and LatAm: 3 rd largest population of Internet Users You Are Here Visualization from the Opte Project of the various routes through
Service Provider View of Cyber Security July 2017 Quick Stats Caribbean and LatAm: 3 rd largest population of Internet Users You Are Here Visualization from the Opte Project of the various routes through
What is NPP, Osko and PayID?
 What is NPP, Osko and PayID? The New Payment Platform (NPP) is a new way of making payments that is: Fast You can send funds to anyone in real-time. Easy You can send funds to a PayID (such as an email
What is NPP, Osko and PayID? The New Payment Platform (NPP) is a new way of making payments that is: Fast You can send funds to anyone in real-time. Easy You can send funds to a PayID (such as an email
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco
 What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
Privacy Information - Privacy and Cookies Policy In Full
 Privacy Information - Privacy and Cookies Policy In Full Contents 1. Introduction & General Terms 2. Who are we? 3. What information will Gaucho collect about me? 4. How will Gaucho use the information
Privacy Information - Privacy and Cookies Policy In Full Contents 1. Introduction & General Terms 2. Who are we? 3. What information will Gaucho collect about me? 4. How will Gaucho use the information
Proofpoint, Inc.
 1 2018 Proofpoint, Inc. Juan Carlos Cabrera Country Manager Caribbean & Central America AMENAZAS EN EL 2018 SABES QUIEN ESTA UTILIZANDO TU DOMINIO? 2 2017 Proofpoint, Inc. Juan Carlos Cabrera Country Manager
1 2018 Proofpoint, Inc. Juan Carlos Cabrera Country Manager Caribbean & Central America AMENAZAS EN EL 2018 SABES QUIEN ESTA UTILIZANDO TU DOMINIO? 2 2017 Proofpoint, Inc. Juan Carlos Cabrera Country Manager
Retail/Consumer Client Internet Banking Awareness and Education Program
 Retail/Consumer Client Internet Banking Table of Contents Securing Your Environment... 3 Unsolicited Client Contact... 3 Protecting Your Identity... 3 1) E-mail Risk... 3 2) Internet Risks... 4 3) Telephone
Retail/Consumer Client Internet Banking Table of Contents Securing Your Environment... 3 Unsolicited Client Contact... 3 Protecting Your Identity... 3 1) E-mail Risk... 3 2) Internet Risks... 4 3) Telephone
RSA Web Threat Detection
 RSA Web Threat Detection Online Threat Detection in Real Time Alaa Abdulnabi. CISSP, CIRM RSA Pre-Sales Manager, TEAM Region 1 Web Threat Landscape In the Wild Begin Session Login Transaction Logout Web
RSA Web Threat Detection Online Threat Detection in Real Time Alaa Abdulnabi. CISSP, CIRM RSA Pre-Sales Manager, TEAM Region 1 Web Threat Landscape In the Wild Begin Session Login Transaction Logout Web
Fraud Update: Why Fraudsters Love Wires and How to Stop Them. Luis Rojas, Director, Product Management WesPay 2014
 Fraud Update: Why Fraudsters Love Wires and How to Stop Them Luis Rojas, Director, Product Management WesPay 2014 Competitive Pressures Drive Fraud and Operational Risk Availability Of Information Creates
Fraud Update: Why Fraudsters Love Wires and How to Stop Them Luis Rojas, Director, Product Management WesPay 2014 Competitive Pressures Drive Fraud and Operational Risk Availability Of Information Creates
Top 5 Tips To Take A Stand Against Telephone Scams
 Scammers often use the telephone as a method to gain personal details and con people out of their life savings. Avoid being one of them, protect yourself. Top 5 Tips To Take A Stand Against Telephone Scams
Scammers often use the telephone as a method to gain personal details and con people out of their life savings. Avoid being one of them, protect yourself. Top 5 Tips To Take A Stand Against Telephone Scams
Accelerating growth and digital adoption with seamless identity trust
 Accelerating growth and digital adoption with seamless identity trust IBM Trusteer helps organizations seamlessly establish identity trust across the omnichannel customer journey Let s get started 3 Introduction
Accelerating growth and digital adoption with seamless identity trust IBM Trusteer helps organizations seamlessly establish identity trust across the omnichannel customer journey Let s get started 3 Introduction
Syntel2 by Syntel Solutions Features
 Syntel2 by Syntel Solutions Features Interested in learning how our proven software platform can revitalize your business communications? With Syntel2 by Syntel Solutions, we give you the tools and features
Syntel2 by Syntel Solutions Features Interested in learning how our proven software platform can revitalize your business communications? With Syntel2 by Syntel Solutions, we give you the tools and features
Wire Fraud Scams: How to Protect
 1 Wire Fraud Scams: How to Protect Your Buyer Clients Connection Jessica Edgerton, NAR Associate Counsel GOV GODWIN EMEFELE URGENT NOTICE, Is my pleasure to inform you that your
1 Wire Fraud Scams: How to Protect Your Buyer Clients Connection Jessica Edgerton, NAR Associate Counsel GOV GODWIN EMEFELE URGENT NOTICE, Is my pleasure to inform you that your
To learn more about Stickley on Security visit You can contact Jim Stickley at
 Thanks for attending this session on March 15th. To learn more about Stickley on Security visit www.stickleyonsecurity.com You can contact Jim Stickley at jim@stickleyonsecurity.com Have a great day! Fraud
Thanks for attending this session on March 15th. To learn more about Stickley on Security visit www.stickleyonsecurity.com You can contact Jim Stickley at jim@stickleyonsecurity.com Have a great day! Fraud
Network Access Control and VoIP. Ben Hostetler Senior Information Security Advisor
 Network Access Control and VoIP Ben Hostetler Senior Information Security Advisor Objectives/Discussion Points Network Access Control Terms & Definitions Certificate Based 802.1X MAC Authentication Bypass
Network Access Control and VoIP Ben Hostetler Senior Information Security Advisor Objectives/Discussion Points Network Access Control Terms & Definitions Certificate Based 802.1X MAC Authentication Bypass
9/11/ FALL CONFERENCE & TRAINING SEMINAR 2014 FALL CONFERENCE & TRAINING SEMINAR
 1 2 1 Agenda: Types of Fraud Things you can do internally Things that companies can do Services Provided by the Bank 3 Because that is where the money is. 4 2 Checks Credit Cards ACH (Debits / Credits)
1 2 1 Agenda: Types of Fraud Things you can do internally Things that companies can do Services Provided by the Bank 3 Because that is where the money is. 4 2 Checks Credit Cards ACH (Debits / Credits)
Why you MUST protect your customer data
 Why you MUST protect your customer data If you think you re exempt from compliance with customer data security and privacy laws because you re a small business, think again. Businesses of all sizes are
Why you MUST protect your customer data If you think you re exempt from compliance with customer data security and privacy laws because you re a small business, think again. Businesses of all sizes are
Cyber Security Guide. For Politicians and Political Parties
 Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Evolution of Spear Phishing. White Paper
 Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
Consumers Use of Mobile Financial Services 2015
 Consumers Use of Mobile Financial Services 2015 Arturo Gonzalez and Ellen A. Merry Division of Consumer and Community Affairs Federal Reserve Board The analysis and conclusions set forth in this presentation
Consumers Use of Mobile Financial Services 2015 Arturo Gonzalez and Ellen A. Merry Division of Consumer and Community Affairs Federal Reserve Board The analysis and conclusions set forth in this presentation
PSTN Security. Sougat Ghosh Security Services Leader Asia, Nortel Delhi / September 29, 2008 BUSINESS MADE SIMPLE
 PSTN Security Sougat Ghosh Security Services Leader Asia, Nortel Delhi / September 29, 2008 BUSINESS MADE SIMPLE 1 Disclaimer The slides and presentation templates are property of Nortel and must not be
PSTN Security Sougat Ghosh Security Services Leader Asia, Nortel Delhi / September 29, 2008 BUSINESS MADE SIMPLE 1 Disclaimer The slides and presentation templates are property of Nortel and must not be
Mobile Malware Detection Comparison
 Mobile Malware Detection Comparison REVISION HISTORY Rev. Date Comment 1.0 03/21/2011 1.Initial Release Lionic Corp. 1F-C6, No. 1, Lising 1st Road, Science- Based Industrial Park, Hsinchu City 300, Taiwan,
Mobile Malware Detection Comparison REVISION HISTORY Rev. Date Comment 1.0 03/21/2011 1.Initial Release Lionic Corp. 1F-C6, No. 1, Lising 1st Road, Science- Based Industrial Park, Hsinchu City 300, Taiwan,
Simple and Powerful Security for PCI DSS
 Simple and Powerful Security for PCI DSS The regulations AccessEnforcer helps check off your list. Most merchants think they are too small to be targeted by hackers. In fact, their small size makes them
Simple and Powerful Security for PCI DSS The regulations AccessEnforcer helps check off your list. Most merchants think they are too small to be targeted by hackers. In fact, their small size makes them
Protecting Your Business From Hackers
 Protecting Your Business From Hackers Technology Has Changed Real Estate Today, consumers have access to vast troves of information that enable them to make decisions faster than ever before Real estate
Protecting Your Business From Hackers Technology Has Changed Real Estate Today, consumers have access to vast troves of information that enable them to make decisions faster than ever before Real estate
Identity Theft and Account Takeover Prevention
 Identity Theft and Account Takeover Prevention Sgt. Rick Radinsky,CFE 520-837-7814 Det. Jeff Van Norman 520-837-7827 Introduction Tucson Police Financial Crimes Unit Responsible for investigation of fraud
Identity Theft and Account Takeover Prevention Sgt. Rick Radinsky,CFE 520-837-7814 Det. Jeff Van Norman 520-837-7827 Introduction Tucson Police Financial Crimes Unit Responsible for investigation of fraud
Conjure Network LLC Privacy Policy
 Conjure Network LLC Privacy Policy Effective September 28, 2018 Conjure Network LLC ( Conjure, us, we, or our ) operates http://www.conjure.network (the Site or Website ). This Privacy Policy (the Policy
Conjure Network LLC Privacy Policy Effective September 28, 2018 Conjure Network LLC ( Conjure, us, we, or our ) operates http://www.conjure.network (the Site or Website ). This Privacy Policy (the Policy
Identifying Fraudulently Promoted Online Videos
 Identifying Fraudulently Promoted Online Videos Vlad Bulakh, Christopher W. Dunn, Minaxi Gupta April 7, 2014 April 7, 2014 Vlad Bulakh 2 Motivation Online video sharing websites are visited by millions
Identifying Fraudulently Promoted Online Videos Vlad Bulakh, Christopher W. Dunn, Minaxi Gupta April 7, 2014 April 7, 2014 Vlad Bulakh 2 Motivation Online video sharing websites are visited by millions
PCI Compliance. What is it? Who uses it? Why is it important?
 PCI Compliance What is it? Who uses it? Why is it important? Definitions: PCI- Payment Card Industry DSS-Data Security Standard Merchants Anyone who takes a credit card payment 3 rd party processors companies
PCI Compliance What is it? Who uses it? Why is it important? Definitions: PCI- Payment Card Industry DSS-Data Security Standard Merchants Anyone who takes a credit card payment 3 rd party processors companies
Wire Fraud Begins to Hammer the Construction Industry
 Wire Fraud Begins to Hammer the Construction Industry Cybercriminals are adding new housing construction to their fraud landscape and likely on a wide scale. Created and published by: Thomas W. Cronkright
Wire Fraud Begins to Hammer the Construction Industry Cybercriminals are adding new housing construction to their fraud landscape and likely on a wide scale. Created and published by: Thomas W. Cronkright
Cyber Security Guide for NHSmail
 Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
Cyber Hygiene Guide. Politicians and Political Parties
 Cyber Hygiene Guide Politicians and Political Parties Canadian Election Integrity Initiative Design by ccm.design Cover Image by Songquan Deng Helping to Safeguard the Integrity of the Electoral Process
Cyber Hygiene Guide Politicians and Political Parties Canadian Election Integrity Initiative Design by ccm.design Cover Image by Songquan Deng Helping to Safeguard the Integrity of the Electoral Process
Top 10 Global Threat Rank by Source
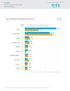 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Union Springs Telephone Company, Inc. Network TRANSPARENCY statement
 Union Springs Telephone Company, Inc. Network TRANSPARENCY statement Union Springs Telephone Company, Inc. ( Company ) provides this Network Transparency Statement in accordance with the FCC s Restore
Union Springs Telephone Company, Inc. Network TRANSPARENCY statement Union Springs Telephone Company, Inc. ( Company ) provides this Network Transparency Statement in accordance with the FCC s Restore
