Work Book. Sharkfest Presentation Material. Copyright Advance Seven Limited. All rights reserved.
|
|
|
- Brook Price
- 5 years ago
- Views:
Transcription
1 Work Book Presentation Material Copyright Advance Seven Limited. All rights reserved. Advance Seven Limited Melville House High Street Dunmow Essex CM6 1AF United Kingdowm
2 Table of Contents 1 TMS HTTP Trace TMS Database Trace Scenario Summary Trace... 2 Database Performance Analysis TMS Database Trace Scenario Summary Trace... 6 Response Packet... 7 Request Packet Correlation Strategies... 9 Introduction... 9 TCP Port-to-port Mapping... 9 Data Content Multi-tier Characterisation... 13
3 1 TMS HTTP Trace No. Time Source Destination Src Port Dst Port Info 48 11:42: GET /TicketView.php?TicketNo= HTTP/ :42: [TCP segment of a reassembled PDU] 51 11:42: [TCP segment of a reassembled PDU] 52 11:42: [TCP segment of a reassembled PDU] 53 11:42: HTTP/ OK (text/html) 64 11:42: GET /TicketView.php?TicketNo= HTTP/ :42: [TCP segment of a reassembled PDU] 67 11:42: [TCP segment of a reassembled PDU] 68 11:42: [TCP segment of a reassembled PDU] 69 11:42: HTTP/ OK (text/html) 88 11:42: GET /TicketView.php?TicketNo= HTTP/ :42: [TCP segment of a reassembled PDU] 91 11:42: [TCP segment of a reassembled PDU] 92 11:42: [TCP segment of a reassembled PDU] 94 11:42: [TCP segment of a reassembled PDU] 95 11:42: HTTP/ OK (text/html) :42: GET /TicketView.php?TicketNo= HTTP/ :42: [TCP segment of a reassembled PDU] :42: [TCP segment of a reassembled PDU] :42: [TCP segment of a reassembled PDU] :42: HTTP/ OK (text/html) :42: GET /TicketView.php?TicketNo= HTTP/ :42: [TCP segment of a reassembled PDU] :42: [TCP segment of a reassembled PDU] :42: [TCP segment of a reassembled PDU] :42: HTTP/ OK (text/html) :42: Echo (ping) request id=0x0001, seq=19439/61259, :42: Echo (ping) reply id=0x0001, seq=19439/61259, 1
4 2 TMS Database Trace Scenario 1 Summary Trace No. Time Source Destination Src Port Dst Port Info Trace lines deleted :42: > :42: [TCP segment of a reassembled PDU] :42: > :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >X :42: > :42: [TCP segment of a reassembled PDU] :42: > :42: <R/S/S/S/S/S/S/S/S/S/S/K/Z :42: >Q :42: <T/D/C/Z :42: >X :42: > :42: [TCP segment of a reassembled PDU] :42: > :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] 2
5 214 11:42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >X :42: > :42: [TCP segment of a reassembled PDU] :42: > :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >X :42: > :42: [TCP segment of a reassembled PDU] :42: > :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >X 3
6 Database Performance Analysis No. Client Time (ms) Req Spread (ms) Rsp Spread (ms) Server Time (ms) Source Destination Client IP Client Port Src Port Dst Port Info Time :42: > :42: [TCP segment of a reassembled PDU] :42: > :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >X :42: > :42: [TCP segment of a reassembled PDU] :42: > :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: , >Q :42: [TCP segment of a reassembled PDU] :42: >X 6,
7 Server Time (ms) 7,000 Client Time for Database Trace 6,000 5,000 Client Time (ms) 4,000 3,000 2, Server Time for Database Trace 1,
8 3 TMS Database Trace Scenario 2 Summary Trace No. Time Source Destination Src Port Dst Port Info Trace lines deleted :42: > :42: [TCP segment of a reassembled PDU] :42: > :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >X :42: > :42: [TCP segment of a reassembled PDU] :42: > :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >Q :42: [TCP segment of a reassembled PDU] :42: >X 6
9 Response Packet 7
10 Request Packet 8
11 4 Correlation Strategies Introduction As we track the execution of a user transaction through a system we have to deal with multiple protocols. A B C PC WAN HTTP Web Server TDS Database Server iscsi SAN In the system above we have HTTP flowing from Internet Explorer to the web server. The web server may need to make calls to the database, and so perhaps we will have to use the Microsoft SQL protocol TDS. The database may then access its storage via iscsi. There isn t a one-to-one match between the packets flowing at each interface (A, B and C), and so we need strategies to match packets at one tier to packets at another. There are three strategies available: TCP port-to-port mapping Data content Comparison with a sample transaction TCP Port-to-port Mapping In this case we rely on the situation where a TCP connection from one client to a server has a constant relationship with a connection between another client and another server. NB: In examples showing packets, time increases down the page. Citrix XenApp Example Consider the situation where a user s desktop is delivered from a Citrix XenApp server. In this case the user PC will maintain one (or three) constant connections to the Citrix server to carry the ICA presentation protocol. Once the user completes the login, there will be TCP connections to network file servers. For the duration of the login, there is a direct and constant relationship between ICA connections and the file server connections. 9
12 Therefore if we capture the creation of these connections at login time it s relatively easy to identify these mappings. PC to the XenApp server simply filter to select ICA traffic from and to the PC and note the time of day that the PC started the connection XenApp to file server filter the appropriate trace to show TCP SYN packets to the file server (IP address and port number) and find sessions that start shortly after the ICA connection is established Once a XenApp to file server session has been identified, cross-check by using the follow TCP stream Wireshark feature to select just that stream. Add to the stream filter: smb2.cmd == 0x03 - to view all SMB 2 TreeConnect requests with share information smb2.cmd == 0x05 - to view all SMB 2 Create requests with file name information smb.cmd == 0x32 to view all SMB 1 Query Path Info packets with path information smb.cmd == 0xa2 to view all SMB 1 NT Create AndX requests with file name information Do the paths and file names seem appropriate for the user? Perhaps they actually include the userid. An identifiable marker can help. For example, ask the user to make a copy of a file and then rename the copy to something distinctive, such as marker101.docx. You can then use this marker to check the TCP session. In the above example we see that the SMB 2 connection defined by the quadruplet :47006: :445 'belongs' to the ICA session :8276: :2598 A further method is to; use the command netstat b to see all connections and the process (PID) that owns them, then use Task Manager to identify the User Name for the PID Of course this has to be done at the time, and it won t work with SMB connections since they are owned by the system. 10
13 The final way is to run Process Monitor (procmon) in conjunction with the network trace, and then review the.pml file later. Procmon shows the TCP Send and Receive details including userid. Again SMB is a problem here as the owning PID will always be 4 (system), but by looking at the file operations and paths specified it s relatively easy to work out who owns what. Redirected file operations are a problem though since they all appear to flow on one TCP connection. In this case, content matching is needed. Web Server to Application Server Example Although the connections from a browser to a web server are often short-lived, there will probably be a connection from the web server to an application server (or other service) for the duration of the browser to web server connection. The same principle as in the XenApp example applies; we determine the timestamp for the start and end of the browser to web server connection. We then look for TCP connections between the web server and the application server that start and end at around the same time. Again, we can cross-check the findings by checking the data being carried on each connection and looking for distinctions. Because these connections are typically short-lived, it s not possible to use a marker for correlation. Summary We have covered two examples to illustrate this general principle. The above technique will also work with other scenarios such as: User to Outlook on Citrix or terminal services to Exchange User to web or application server to database connections (although most now use connection pooling) User to a proxy or gateway server to web or application server 11
14 If the traces you capture are reasonably well synchronised, and you can t spot the patterns we have covered here then you ll need to consider a different approach to correlation. Data Content The principle here is very simple. If we have a multi-tiered system, application data that is delivered to the user was probably retrieved from another server such as a database. Therefore, if we know what data was delivered to the user we can search for that data at other tiers. The above trace shows HTML data being sent from a web server to the user's browser. A screenshot of the browser shows a variable description value of 'RPRsupport Development and Bug Fixing'. This can be clearly seen in the trace data. 12
15 A corresponding trace was captured for traffic to and from the system's database. A search for the description string in the database trace, within the timeframe of the web transaction, quickly identifies this data being retrieved from the database. If we have a video recording of the problem occurring we can use data submitted by the user and data rendered on the user s screen when the transaction completes. However, if we don t have a video recording it can be difficult to get information about what precisely was entered by the user. In this case we must rely on the data return to the user; this is why a screenshot is so powerful in diagnosing a problem. Applications that are presented to the user via a web browser are perhaps the simplest to study. Remember to consider that data from the browser to the first server could be via a GET query string, POST data or cookie data. When using an Office application like Word, be sure to record information such as the name and path of the file being worked on, so that it can then be found easily in the network trace (in Wireshark simply use search string ). Multi-tier Characterisation By repeating the failing or slow transaction (even if it doesn t fail or go slow) we can capture a baseline example showing the interactions at all of the tiers. This characterisation must be done during a maintenance period where the transaction is the only one executed on the system at that time. App Server Database S C S Req Type 1 Req Type A Time increasing Rsp Type 1 Req Type 2 Rsp Type 2 Rsp Type A Req Type B Rsp Type B Req Type V Rsp Type V 13
16 In the example above we conduct a controlled test that shows that when a Type 1 transaction hits the app server, we see that the code on this server generates two database transactions; Types A and B. When a Type 2 transaction is processed by the application server, a single Type V database transaction is needed. We need to be conscious of the fact that the mapping of transactions in this way may be affected by application transaction parameter values, and so it's a good idea to work with the developer (if possible) and test a range of parameter values. Gathering the baseline information in a test environment is not a good idea since it s quite likely that it will look different to a sample taken in production, even though the differences may be subtle. Ideally we need to capture the baseline using the same input data, same userid and same user PC as was used when the problem occurred. 14
Lab Assignment 3 for ECE374
 Lab Assignment 3 for ECE374 Posted: 02/25/18 Due: 03/08/18 In this lab, we ll take a quick look at the UDP and TCP transport protocol. Whenever possible you should hand in a Wireshark screenshot that you
Lab Assignment 3 for ECE374 Posted: 02/25/18 Due: 03/08/18 In this lab, we ll take a quick look at the UDP and TCP transport protocol. Whenever possible you should hand in a Wireshark screenshot that you
Experiment 2: Wireshark as a Network Protocol Analyzer
 Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
4. What is the sequence number of the SYNACK segment sent by spinlab.wpi.edu to the client computer in reply to the SYN? Also Seq=0 (relative
 1. What is the IP address and TCP port number used by your client computer (source) to transfer the file to spinlab.wpi.edu? My computer is at 10.211.55.3. The source port is 49247. See screenshot below.
1. What is the IP address and TCP port number used by your client computer (source) to transfer the file to spinlab.wpi.edu? My computer is at 10.211.55.3. The source port is 49247. See screenshot below.
Sirindhorn International Institute of Technology Thammasat University
 1 Name...ID....Section. Seat No.. Sirindhorn International Institute of Technology Thammasat University Midterm Examination: Semester 2/2007 Course Title : ITS 332 Information Technology II Lab (Networking)
1 Name...ID....Section. Seat No.. Sirindhorn International Institute of Technology Thammasat University Midterm Examination: Semester 2/2007 Course Title : ITS 332 Information Technology II Lab (Networking)
Browser behavior can be quite complex, using more HTTP features than the basic exchange, this trace will show us how much gets transferred.
 Lab Exercise HTTP Objective HTTP (HyperText Transfer Protocol) is the main protocol underlying the Web. HTTP functions as a request response protocol in the client server computing model. A web browser,
Lab Exercise HTTP Objective HTTP (HyperText Transfer Protocol) is the main protocol underlying the Web. HTTP functions as a request response protocol in the client server computing model. A web browser,
CNBK Communications and Networks Lab Book: Purpose of Hardware and Protocols Associated with Networking Computer Systems
 Lab Book: Purpose of Hardware and Protocols Associated with Networking Computer Systems Contents Purpose of Hardware and Protocols Associated with Computer Networks... 3 Lab Objectives... 3 Lab Resources...
Lab Book: Purpose of Hardware and Protocols Associated with Networking Computer Systems Contents Purpose of Hardware and Protocols Associated with Computer Networks... 3 Lab Objectives... 3 Lab Resources...
Chapter 4. TCP / UDP Transport Protocol Overview
 Network Basic v0.1 Chapter 4. TCP / UDP Transport Protocol Overview 1 Network Basic v0.1 Chapter 4 TCP / UDP Overview 1. Object 2. Transport Layer Role and Services 3. App and Operation of TCP Mechanism
Network Basic v0.1 Chapter 4. TCP / UDP Transport Protocol Overview 1 Network Basic v0.1 Chapter 4 TCP / UDP Overview 1. Object 2. Transport Layer Role and Services 3. App and Operation of TCP Mechanism
9. Wireshark I: Protocol Stack and Ethernet
 Distributed Systems 205/2016 Lab Simon Razniewski/Florian Klement 9. Wireshark I: Protocol Stack and Ethernet Objective To learn how protocols and layering are represented in packets, and to explore the
Distributed Systems 205/2016 Lab Simon Razniewski/Florian Klement 9. Wireshark I: Protocol Stack and Ethernet Objective To learn how protocols and layering are represented in packets, and to explore the
Wireshark Lab: TCP v7.0
 Wireshark Lab: TCP v7.0 Supplement to Computer Networking: A Top-Down Approach, 7th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand. Chinese proverb
Wireshark Lab: TCP v7.0 Supplement to Computer Networking: A Top-Down Approach, 7th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand. Chinese proverb
Protocol Analysis: Capturing Packets
 Protocol Analysis: Capturing Packets This project is intended to be done on the EiLab Network, but if you want to try to VPN into the EiLab Network on your own PC from your home or workplace, follow these
Protocol Analysis: Capturing Packets This project is intended to be done on the EiLab Network, but if you want to try to VPN into the EiLab Network on your own PC from your home or workplace, follow these
SC/CSE 3213 Winter Sebastian Magierowski York University CSE 3213, W13 L8: TCP/IP. Outline. Forwarding over network and data link layers
 SC/CSE 3213 Winter 2013 L8: TCP/IP Overview Sebastian Magierowski York University 1 Outline TCP/IP Reference Model A set of protocols for internetworking The basis of the modern IP Datagram Exchange Examples
SC/CSE 3213 Winter 2013 L8: TCP/IP Overview Sebastian Magierowski York University 1 Outline TCP/IP Reference Model A set of protocols for internetworking The basis of the modern IP Datagram Exchange Examples
Objectives: (1) To learn to capture and analyze packets using wireshark. (2) To learn how protocols and layering are represented in packets.
 Team Project 1 Due: Beijing 00:01, Friday Nov 7 Language: English Turn-in (via email) a.pdf file. Objectives: (1) To learn to capture and analyze packets using wireshark. (2) To learn how protocols and
Team Project 1 Due: Beijing 00:01, Friday Nov 7 Language: English Turn-in (via email) a.pdf file. Objectives: (1) To learn to capture and analyze packets using wireshark. (2) To learn how protocols and
Problem Set 6 Due: Start of Class, October 26
 CS242 Computer Networks Handout # 12 Randy Shull October 19, 2017 Wellesley College Problem Set 6 Due: Start of Class, October 26 Reading: Kurose & Ross, Sections 3.4, 3.5 Wireshark Lab [11] This exercise
CS242 Computer Networks Handout # 12 Randy Shull October 19, 2017 Wellesley College Problem Set 6 Due: Start of Class, October 26 Reading: Kurose & Ross, Sections 3.4, 3.5 Wireshark Lab [11] This exercise
BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic. Topology. Objectives. Background / Scenario
 BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic Topology Objectives Part 1: (Optional) Download and Install Wireshark Part 2: Capture and Analyze Local ICMP Data in Wireshark
BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic Topology Objectives Part 1: (Optional) Download and Install Wireshark Part 2: Capture and Analyze Local ICMP Data in Wireshark
Wireless LAN Controller Web Authentication Configuration Example
 Wireless LAN Controller Web Authentication Configuration Example Document ID: 69340 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Web Authentication Process
Wireless LAN Controller Web Authentication Configuration Example Document ID: 69340 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Web Authentication Process
Use of the TCP/IP Protocols and the OSI Model in Packet Tracer
 Communication Networks [Netw501] Spring 2018 Tutorial 3 Packet Tracer Activity 3 Use of the TCP/IP Protocols and the OSI Model in Packet Tracer Introduction: In Packet Tracer simulation mode, detailed
Communication Networks [Netw501] Spring 2018 Tutorial 3 Packet Tracer Activity 3 Use of the TCP/IP Protocols and the OSI Model in Packet Tracer Introduction: In Packet Tracer simulation mode, detailed
3. WWW and HTTP. Fig.3.1 Architecture of WWW
 3. WWW and HTTP The World Wide Web (WWW) is a repository of information linked together from points all over the world. The WWW has a unique combination of flexibility, portability, and user-friendly features
3. WWW and HTTP The World Wide Web (WWW) is a repository of information linked together from points all over the world. The WWW has a unique combination of flexibility, portability, and user-friendly features
SMB Analysis OPSEC 2016
 SMB Analysis http://blogs.technet.com/b/josebda/archive/2013/10/02/windows-server-2012-r2-which-version-of-the-smb-protocol-smb-1-0 If Malware crafts a packet to negotiate only using LanMan v1, then Unlocked
SMB Analysis http://blogs.technet.com/b/josebda/archive/2013/10/02/windows-server-2012-r2-which-version-of-the-smb-protocol-smb-1-0 If Malware crafts a packet to negotiate only using LanMan v1, then Unlocked
Lab Capturing and Analyzing Network Traffic
 Lab 1.2.2 Capturing and Analyzing Network Traffic Host Name IP Address Fa0/0 Subnet Mask IP Address S0/0/0 Subnet Mask Default Gateway RouterA 172.17.0.1 255.255.0.0 192.168.1.1 (DCE) 255.255.255.0 N/A
Lab 1.2.2 Capturing and Analyzing Network Traffic Host Name IP Address Fa0/0 Subnet Mask IP Address S0/0/0 Subnet Mask Default Gateway RouterA 172.17.0.1 255.255.0.0 192.168.1.1 (DCE) 255.255.255.0 N/A
Network setup and troubleshooting
 ACTi Knowledge Base Category: Application Note Sub-category: Application Model: All Firmware: All Software: NVR Published: 2009/12/21 Reviewed: 2010/06/10 Network setup and troubleshooting Contents Introduction
ACTi Knowledge Base Category: Application Note Sub-category: Application Model: All Firmware: All Software: NVR Published: 2009/12/21 Reviewed: 2010/06/10 Network setup and troubleshooting Contents Introduction
Exploring TCP and UDP based on Kurose and Ross (Computer Networking: A Top-Down Approach) May 15, 2018
 Exploring TCP and UDP based on Kurose and Ross (Computer Networking: A Top-Down Approach) May 15, 2018 Exploring TCP Description Capturing a bulk TCP transfer from your computer to a remote server. In
Exploring TCP and UDP based on Kurose and Ross (Computer Networking: A Top-Down Approach) May 15, 2018 Exploring TCP Description Capturing a bulk TCP transfer from your computer to a remote server. In
Update your network settings
 IT2400 - ARP Lab Objectives Use different network utilities to obtain information about your computer and network This should be done on your Windows virtual machine Update your network settings Make sure
IT2400 - ARP Lab Objectives Use different network utilities to obtain information about your computer and network This should be done on your Windows virtual machine Update your network settings Make sure
CS 355. Computer Networking. Wei Lu, Ph.D., P.Eng.
 CS 355 Computer Networking Wei Lu, Ph.D., P.Eng. Chapter 2: Application Layer Overview: Principles of network applications? Introduction to Wireshark Web and HTTP FTP Electronic Mail SMTP, POP3, IMAP DNS
CS 355 Computer Networking Wei Lu, Ph.D., P.Eng. Chapter 2: Application Layer Overview: Principles of network applications? Introduction to Wireshark Web and HTTP FTP Electronic Mail SMTP, POP3, IMAP DNS
Wireshark HTTP. Introduction. The Basic HTTP GET/response interaction
 Wireshark HTTP Introduction Having gotten our feet wet with the Wireshark packet sniffer in the introductory lab, we re now ready to use Wireshark to investigate protocols in operation. In this lab, we
Wireshark HTTP Introduction Having gotten our feet wet with the Wireshark packet sniffer in the introductory lab, we re now ready to use Wireshark to investigate protocols in operation. In this lab, we
CSE4344 Project 2 (Spring 2017) Wireshark Lab: HTTP
 Objectives CSE4344 Project 2 (Spring 2017) Wireshark Lab: HTTP To get familiar with capturing network packets using Wireshark. To explore the HTTP message formats and basic operations of HTTP protocol.
Objectives CSE4344 Project 2 (Spring 2017) Wireshark Lab: HTTP To get familiar with capturing network packets using Wireshark. To explore the HTTP message formats and basic operations of HTTP protocol.
Wireshark Lab: HTTP v6.1
 Wireshark Lab: HTTP v6.1 Supplement to Computer Networking: A Top-Down Approach, 6 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand. Chinese proverb
Wireshark Lab: HTTP v6.1 Supplement to Computer Networking: A Top-Down Approach, 6 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand. Chinese proverb
Network Control, Con t
 Network Control, Con t CS 161 - Computer Security Profs. Vern Paxson & David Wagner TAs: John Bethencourt, Erika Chin, Matthew Finifter, Cynthia Sturton, Joel Weinberger http://inst.eecs.berkeley.edu/~cs161/
Network Control, Con t CS 161 - Computer Security Profs. Vern Paxson & David Wagner TAs: John Bethencourt, Erika Chin, Matthew Finifter, Cynthia Sturton, Joel Weinberger http://inst.eecs.berkeley.edu/~cs161/
CCNA 1 Chapter 7 v5.0 Exam Answers 2013
 CCNA 1 Chapter 7 v5.0 Exam Answers 2013 1 A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the
CCNA 1 Chapter 7 v5.0 Exam Answers 2013 1 A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the
How to open ports in the DSL router firmware version 2.xx and above
 How to open ports in the DSL router firmware version 2.xx and above This example shows how to open port 3389 (which is used by Remote Desktop service) in the DSL router running firmware version 2.xx or
How to open ports in the DSL router firmware version 2.xx and above This example shows how to open port 3389 (which is used by Remote Desktop service) in the DSL router running firmware version 2.xx or
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Packet Tracer - Investigating the TCP/IP and OSI Models in Action (Instructor Version Optional Packet Tracer)
 (Instructor Version Optional Packet Tracer) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding
(Instructor Version Optional Packet Tracer) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding
Lab 4: Network Packet Capture and Analysis using Wireshark
 Lab 4: Network Packet Capture and Analysis using Wireshark 4.1 Details Aim: To provide a foundation in network packet capture and analysis. You may be faced with network traffic analysis, from traffic
Lab 4: Network Packet Capture and Analysis using Wireshark 4.1 Details Aim: To provide a foundation in network packet capture and analysis. You may be faced with network traffic analysis, from traffic
A Simplified Example of TCP/IP Communication Chuck Cusack
 A Simplified Example of TCP/IP Communication Chuck Cusack This is a simple example of how messages are sent from one machine to another (from a source to a destination) using the four-layer Internet software
A Simplified Example of TCP/IP Communication Chuck Cusack This is a simple example of how messages are sent from one machine to another (from a source to a destination) using the four-layer Internet software
Secure Access Troubleshooting Rewrite related issues (Core/Web Based Access)
 Secure Access Troubleshooting Rewrite related issues (Core/Web Based Access) Published June 2015 Why do certain web-based applications have issues through the rewrite engine compared to accessing the resource
Secure Access Troubleshooting Rewrite related issues (Core/Web Based Access) Published June 2015 Why do certain web-based applications have issues through the rewrite engine compared to accessing the resource
CS 716: Introduction to communication networks. Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay
 CS 716: Introduction to communication networks - 16 th class; 28 th Sept 2011 Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay What is IP address An identifier for a computer or device on a TCP/IP
CS 716: Introduction to communication networks - 16 th class; 28 th Sept 2011 Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay What is IP address An identifier for a computer or device on a TCP/IP
SQL Parsers with Message Analyzer. Eric Bortei-Doku
 SQL Parsers with Message Analyzer Eric Bortei-Doku Agenda Message Analyzer Overview Simplified Operation Message Analyzer Parsers Overview Desktop UI Demos Analyzing Local Ping Traffic Analyzing a Capture
SQL Parsers with Message Analyzer Eric Bortei-Doku Agenda Message Analyzer Overview Simplified Operation Message Analyzer Parsers Overview Desktop UI Demos Analyzing Local Ping Traffic Analyzing a Capture
K2289: Using advanced tcpdump filters
 K2289: Using advanced tcpdump filters Non-Diagnostic Original Publication Date: May 17, 2007 Update Date: Sep 21, 2017 Topic Introduction Filtering for packets using specific TCP flags headers Filtering
K2289: Using advanced tcpdump filters Non-Diagnostic Original Publication Date: May 17, 2007 Update Date: Sep 21, 2017 Topic Introduction Filtering for packets using specific TCP flags headers Filtering
Wireshark Lab: DNS. 1. Run nslookup to obtain the IP address of a Web server in Asia. What is the IP address of that server?
 Rick Shingu Nick Ishihara 11/30/14 Wireshark Lab: DNS 1. nslookup 1. Run nslookup to obtain the IP address of a Web server in Asia. What is the IP address of that server? Ran the command nslookup www.asdu.ait.ac.th.
Rick Shingu Nick Ishihara 11/30/14 Wireshark Lab: DNS 1. nslookup 1. Run nslookup to obtain the IP address of a Web server in Asia. What is the IP address of that server? Ran the command nslookup www.asdu.ait.ac.th.
SharkFest'17 US. Analysis Visualizations. Robert Bullen Blue Cross and Blue Shield of Minnesota
 SharkFest'17 US Analysis Visualizations Robert Bullen Blue Cross and Blue Shield of Minnesota SharkFest'17 US Carnegie Mellon University June 19-22, 2017 Agenda Included Create firewall latency charts
SharkFest'17 US Analysis Visualizations Robert Bullen Blue Cross and Blue Shield of Minnesota SharkFest'17 US Carnegie Mellon University June 19-22, 2017 Agenda Included Create firewall latency charts
Internet Layers. Physical Layer. Application. Application. Transport. Transport. Network. Network. Network. Network. Link. Link. Link.
 Internet Layers Application Application Transport Transport Network Network Network Network Link Link Link Link Ethernet Fiber Optics Physical Layer Wi-Fi ARP requests and responses IP: 192.168.1.1 MAC:
Internet Layers Application Application Transport Transport Network Network Network Network Link Link Link Link Ethernet Fiber Optics Physical Layer Wi-Fi ARP requests and responses IP: 192.168.1.1 MAC:
Syslog and the Barracuda Web Security Gateway
 What is the Barracuda Syslog? The Barracuda Web Security Gateway generates syslog messages as a means of logging both changes to the web interface configuration and what happens to each traffic request
What is the Barracuda Syslog? The Barracuda Web Security Gateway generates syslog messages as a means of logging both changes to the web interface configuration and what happens to each traffic request
UNI CS 3470 Networking Project 5: Using Wireshark to Analyze Packet Traces 12
 UNI CS 3470 Networking Project 5: Using Wireshark to Analyze Packet Traces 12 Due Wednesday, 12/7, at 11:59:59 PM. One s understanding of network protocols can often be greatly deepened by seeing protocols
UNI CS 3470 Networking Project 5: Using Wireshark to Analyze Packet Traces 12 Due Wednesday, 12/7, at 11:59:59 PM. One s understanding of network protocols can often be greatly deepened by seeing protocols
Lecture 7b: HTTP. Feb. 24, Internet and Intranet Protocols and Applications
 Internet and Intranet Protocols and Applications Lecture 7b: HTTP Feb. 24, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu WWW - HTTP/1.1 Web s application layer protocol
Internet and Intranet Protocols and Applications Lecture 7b: HTTP Feb. 24, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu WWW - HTTP/1.1 Web s application layer protocol
Protocol Analysis: Capturing Packets
 Protocol Analysis: Capturing Packets This project is intended to be done on your assigned Windows VM on the EiLab Network. This is, in part, because you must do this on a PC that you have administrative
Protocol Analysis: Capturing Packets This project is intended to be done on your assigned Windows VM on the EiLab Network. This is, in part, because you must do this on a PC that you have administrative
Networking By: Vince
 Networking 192.168.1.101 By: Vince Disclaimer I am NOT a Networking expert you might ask questions that I don t know the answer to Networking is hard to teach but I know how to do your homeworks so that
Networking 192.168.1.101 By: Vince Disclaimer I am NOT a Networking expert you might ask questions that I don t know the answer to Networking is hard to teach but I know how to do your homeworks so that
To get a feel for how to use the FIREWALL > Live page in NextGen Admin, watch the following video:
 Under the Live tab, you can view and filter real-time information for the traffic that passes through the Barracuda NextGen Firewall F-Series. You can also manage the traffic sessions. To access the Live
Under the Live tab, you can view and filter real-time information for the traffic that passes through the Barracuda NextGen Firewall F-Series. You can also manage the traffic sessions. To access the Live
Polaris Under the Hood. Prepared by: Wes Osborn
 Polaris Under the Hood Prepared by: Wes Osborn Overview Client Communication Kerberos Authentication SQL Profiler SIP Service !! WARNING!! Help -> About Where to start Click on the Application Server link
Polaris Under the Hood Prepared by: Wes Osborn Overview Client Communication Kerberos Authentication SQL Profiler SIP Service !! WARNING!! Help -> About Where to start Click on the Application Server link
Application-Centric Analysis Helps Maximize the Value of Wireshark
 Application-Centric Analysis Helps Maximize the Value of Wireshark The cost of freeware Protocol analysis has long been viewed as the last line of defense when it comes to resolving nagging network and
Application-Centric Analysis Helps Maximize the Value of Wireshark The cost of freeware Protocol analysis has long been viewed as the last line of defense when it comes to resolving nagging network and
Lab Exercise Protocol Layers
 Lab Exercise Protocol Layers Objective To learn how protocols and layering are represented in packets. They are key concepts for structuring networks that are covered in 1.3 and 1.4 of your text. Review
Lab Exercise Protocol Layers Objective To learn how protocols and layering are represented in packets. They are key concepts for structuring networks that are covered in 1.3 and 1.4 of your text. Review
Lecture 2-ter. 2. A communication example Managing a HTTP v1.0 connection. Managing a HTTP request. transport session. Step 1 - opening transport
 Lecture 2-ter. 2 A communication example Managing a HTTP v1.0 connection Managing a HTTP request User digits URL and press return (or clicks ). What happens (HTTP 1.0): 1. opens a TCP transport session
Lecture 2-ter. 2 A communication example Managing a HTTP v1.0 connection Managing a HTTP request User digits URL and press return (or clicks ). What happens (HTTP 1.0): 1. opens a TCP transport session
MYPLACE USER GUIDE User Guide for myplace.hexagon.com March 08, 2017
 MYPLACE USER GUIDE User Guide for myplace.hexagon.com March 08, 2017 General Contents General... 3 1 Requirements... 4 1.1 Citrix client... 4 1.2 Citrix NetScaler (Access Gateway) plugin... 4 1.3 SMS Passcode...
MYPLACE USER GUIDE User Guide for myplace.hexagon.com March 08, 2017 General Contents General... 3 1 Requirements... 4 1.1 Citrix client... 4 1.2 Citrix NetScaler (Access Gateway) plugin... 4 1.3 SMS Passcode...
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Lab Applying a Logical Layered Model to a Physical Network
 Lab 3.1.1 Applying a Logical Layered Model to a Physical Network Objective In this exercise, you will use various Cisco IOS commands and a protocol analyzer to map the layers in the OSI model to the encapsulated
Lab 3.1.1 Applying a Logical Layered Model to a Physical Network Objective In this exercise, you will use various Cisco IOS commands and a protocol analyzer to map the layers in the OSI model to the encapsulated
Timmy is the name of a UNCW file server which provides students with 20MB of storage space. It is secure and backed-up nightly. It is available from
 Whether you are on or off campus, using a PC, Mac or mobile device, you can access UNCW software (including Microsoft Office) through TealWare in the Teal Cloud. Please note that this is a secure, private
Whether you are on or off campus, using a PC, Mac or mobile device, you can access UNCW software (including Microsoft Office) through TealWare in the Teal Cloud. Please note that this is a secure, private
Wireshark Lab: HTTP SOLUTION
 Wireshark Lab: HTTP SOLUTION Supplement to Computer Networking: A Top-Down Approach, 7th ed., J.F. Kurose and K.W. Ross 2005-2012, J.F Kurose and K.W. Ross, All Rights Reserved The following screen shots
Wireshark Lab: HTTP SOLUTION Supplement to Computer Networking: A Top-Down Approach, 7th ed., J.F. Kurose and K.W. Ross 2005-2012, J.F Kurose and K.W. Ross, All Rights Reserved The following screen shots
Packet Tracer Simulation - TCP and UDP Communications
 Topology Objectives Part 1: Generate Network Traffic in Simulation Mode Part 2: Examine the Functionality of the TCP and UDP Protocols Background This simulation activity is intended to provide a foundation
Topology Objectives Part 1: Generate Network Traffic in Simulation Mode Part 2: Examine the Functionality of the TCP and UDP Protocols Background This simulation activity is intended to provide a foundation
Packet Capture & Wireshark. Fakrul Alam
 Packet Capture & Wireshark Fakrul Alam fakrul@bdhub.com Why we need to capture packet & how it s related to security? tcpdump Definition tcpdump is a utility used to capture and analyze packets on network
Packet Capture & Wireshark Fakrul Alam fakrul@bdhub.com Why we need to capture packet & how it s related to security? tcpdump Definition tcpdump is a utility used to capture and analyze packets on network
Agility2018-TCPdump Documentation
 Agility2018-TCPdump Documentation Release.01 David Larsen Aug 10, 2018 Switches 1 F5 tcpdump and Wireshark 3 1.1 tcpdump Switches............................................ 3 1.2 tcpdump Filters..............................................
Agility2018-TCPdump Documentation Release.01 David Larsen Aug 10, 2018 Switches 1 F5 tcpdump and Wireshark 3 1.1 tcpdump Switches............................................ 3 1.2 tcpdump Filters..............................................
Deploying Citrix Access Gateway VPX with Web Interface 5.4
 Deploying Citrix Access Gateway VPX with Web Interface 5.4 Ben Piper President Ben Piper Consulting, LLC Copyright 2012 Ben Piper. All rights reserved. Page 1 Introduction Deploying Citrix Access Gateway
Deploying Citrix Access Gateway VPX with Web Interface 5.4 Ben Piper President Ben Piper Consulting, LLC Copyright 2012 Ben Piper. All rights reserved. Page 1 Introduction Deploying Citrix Access Gateway
ZENworks for Desktops Preboot Services
 3.2 Novell ZENworks for Desktops Preboot Services DEPLOYMENT www.novell.com Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
3.2 Novell ZENworks for Desktops Preboot Services DEPLOYMENT www.novell.com Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
Lab 2. All datagrams related to favicon.ico had been ignored. Diagram 1. Diagram 2
 Lab 2 All datagrams related to favicon.ico had been ignored. Diagram 1 Diagram 2 1. Is your browser running HTTP version 1.0 or 1.1? What version of HTTP is the server running? According to the diagram
Lab 2 All datagrams related to favicon.ico had been ignored. Diagram 1 Diagram 2 1. Is your browser running HTTP version 1.0 or 1.1? What version of HTTP is the server running? According to the diagram
This tutorial shows how to use ACE to Identify the true causes of poor response time Document the problems that are found
 FTP Application Overview This tutorial shows how to use ACE to Identify the true causes of poor response time Document the problems that are found The screen images in this tutorial were captured while
FTP Application Overview This tutorial shows how to use ACE to Identify the true causes of poor response time Document the problems that are found The screen images in this tutorial were captured while
Sirindhorn International Institute of Technology Thammasat University
 Name.............................. ID............... Section...... Seat No...... Sirindhorn International Institute of Technology Thammasat University Course Title: IT Security Instructor: Steven Gordon
Name.............................. ID............... Section...... Seat No...... Sirindhorn International Institute of Technology Thammasat University Course Title: IT Security Instructor: Steven Gordon
Basic Cisco Router Configuration: Multiple Routers
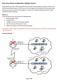 Basic Cisco Router Configuration: Multiple Routers Routers rarely exist alone. Most organizations have several to several dozens of routers. In this Lab, we will study two different ways in which routers
Basic Cisco Router Configuration: Multiple Routers Routers rarely exist alone. Most organizations have several to several dozens of routers. In this Lab, we will study two different ways in which routers
Using NAT in Overlapping Networks
 Using NAT in Overlapping Networks Document ID: 13774 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Related Information
Using NAT in Overlapping Networks Document ID: 13774 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Related Information
CNPE Communications and Networks Lab Book: Data Transmission Over Digital Networks
 Lab Book: Data Transmission Over Digital Networks Contents Data Transmission Over Digital Networks... 3 Lab Objectives... 3 Lab Resources... 3 Task 1 Build the Home Network... 3 Task 2 Configure IP Addresses...
Lab Book: Data Transmission Over Digital Networks Contents Data Transmission Over Digital Networks... 3 Lab Objectives... 3 Lab Resources... 3 Task 1 Build the Home Network... 3 Task 2 Configure IP Addresses...
Google Docs Tipsheet. ABEL Summer Institute 2009
 Google Docs Tipsheet ABEL Summer Institute 2009 Contents Logging in to Google Apps for CollaborativeSchools.net for the First Time... 2 Text Documents Creating a New Text Document in Google Docs... 5 Uploading
Google Docs Tipsheet ABEL Summer Institute 2009 Contents Logging in to Google Apps for CollaborativeSchools.net for the First Time... 2 Text Documents Creating a New Text Document in Google Docs... 5 Uploading
Overview of Web Interface to CenturyLink B2B Gateway
 Overview of Web Interface to CenturyLink B2B Gateway Access and Password Policy for the Web Interface Like all Internet sites, the CenturyLink B2B web site requires an account containing both an identity
Overview of Web Interface to CenturyLink B2B Gateway Access and Password Policy for the Web Interface Like all Internet sites, the CenturyLink B2B web site requires an account containing both an identity
Internetworking Models The OSI Reference Model
 Internetworking Models When networks first came into being, computers could typically communicate only with computers from the same manufacturer. In the late 1970s, the Open Systems Interconnection (OSI)
Internetworking Models When networks first came into being, computers could typically communicate only with computers from the same manufacturer. In the late 1970s, the Open Systems Interconnection (OSI)
Using Wireshark as an Applica1on Support Engineer Tim Poth. Senior Priority Response Analyst Bentley Systems, Inc.
 Using Wireshark as an Applica1on Support Engineer Tim Poth Senior Priority Response Analyst Bentley Systems, Inc. tim.poth@bentley.com 1 Agenda Quick intro to Bentley Systems, Inc How the Priority Response
Using Wireshark as an Applica1on Support Engineer Tim Poth Senior Priority Response Analyst Bentley Systems, Inc. tim.poth@bentley.com 1 Agenda Quick intro to Bentley Systems, Inc How the Priority Response
INBOUND AND OUTBOUND NAT
 INBOUND AND OUTBOUND NAT Network Address Translation Course # 2011 1 Overview! Network Address Translation (NAT)! Aliases! Static Address Mappings! Inbound Tunnels! Advanced Tunnel Option SYN Cookies Authentication
INBOUND AND OUTBOUND NAT Network Address Translation Course # 2011 1 Overview! Network Address Translation (NAT)! Aliases! Static Address Mappings! Inbound Tunnels! Advanced Tunnel Option SYN Cookies Authentication
SteelCentral Packet Analyser Walkthrough
 SteelCentral Packet Analyser Walkthrough The aim of this demo is to show how to perform simple analysis of packets using the SteelCentral Packet Analyser in conjunction with NetShark. We will talk through
SteelCentral Packet Analyser Walkthrough The aim of this demo is to show how to perform simple analysis of packets using the SteelCentral Packet Analyser in conjunction with NetShark. We will talk through
TCP/IP Attack Lab. 1 Lab Overview. 2 Lab Environment. 2.1 Environment Setup. SEED Labs TCP/IP Attack Lab 1
 SEED Labs TCP/IP Attack Lab 1 TCP/IP Attack Lab Copyright c 2006-2016 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation under Award
SEED Labs TCP/IP Attack Lab 1 TCP/IP Attack Lab Copyright c 2006-2016 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation under Award
Mohammad Hossein Manshaei 1393
 Mohammad Hossein Manshaei manshaei@gmail.com 1393 Voice and Video over IP Slides derived from those available on the Web site of the book Computer Networking, by Kurose and Ross, PEARSON 2 Multimedia networking:
Mohammad Hossein Manshaei manshaei@gmail.com 1393 Voice and Video over IP Slides derived from those available on the Web site of the book Computer Networking, by Kurose and Ross, PEARSON 2 Multimedia networking:
1. Which OSI layers offers reliable, connection-oriented data communication services?
 CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
TheGreenBow IPsec VPN Client. Configuration Guide CISCO RV042. Website: Contact:
 TheGreenBow IPsec VPN Client Configuration Guide CISCO RV042 Website: www.thegreenbow.com Contact: support@thegreenbow.com Table of Contents 1 Introduction... 3 1.1 Goal of this document... 3 1.2 VPN Network
TheGreenBow IPsec VPN Client Configuration Guide CISCO RV042 Website: www.thegreenbow.com Contact: support@thegreenbow.com Table of Contents 1 Introduction... 3 1.1 Goal of this document... 3 1.2 VPN Network
Wire Shark Lab1. Intro
 Jae Sook Lee FA16 CSIT 340 01 Dr. Constantine Coutras Wire Shark Lab1 Intro 1. List 3 different protocols that appear in the protocol column in the unfiltered packet-listing window in step 7 above. : 1)
Jae Sook Lee FA16 CSIT 340 01 Dr. Constantine Coutras Wire Shark Lab1 Intro 1. List 3 different protocols that appear in the protocol column in the unfiltered packet-listing window in step 7 above. : 1)
Project points. CSE422 Computer Networking Spring 2018
 Project 1 100 points Introduction One s understanding of network protocols can often be greatly deepened by seeing protocols in action and by playing around with protocols observing the sequence of messages
Project 1 100 points Introduction One s understanding of network protocols can often be greatly deepened by seeing protocols in action and by playing around with protocols observing the sequence of messages
Configuration examples for the D-Link NetDefend Firewall series DFL-260/860
 Configuration examples for the D-Link NetDefend Firewall series DFL-260/860 Scenario: How to configure User Authentication for multiple groups Last update: 2008-04-29 Overview In this document, the notation
Configuration examples for the D-Link NetDefend Firewall series DFL-260/860 Scenario: How to configure User Authentication for multiple groups Last update: 2008-04-29 Overview In this document, the notation
Network Model: Each layer has a specific function.
 OBJECTIVES: To discuss the OSI model and its layer architecture and to show the interface between the layers. To briefly discuss the functions of each layer in the OSI model. To introduce the TCP/IP protocol.
OBJECTIVES: To discuss the OSI model and its layer architecture and to show the interface between the layers. To briefly discuss the functions of each layer in the OSI model. To introduce the TCP/IP protocol.
Application Layer -1- Network Tools
 EITF25 Internet: Technology and Applications Application Layer -1- Network Tools 2013, Lecture 06 Kaan Bür, Stefan Höst Previously on EITF25 Transport Layer Addressing above IP Ports, sockets Process-to-process
EITF25 Internet: Technology and Applications Application Layer -1- Network Tools 2013, Lecture 06 Kaan Bür, Stefan Höst Previously on EITF25 Transport Layer Addressing above IP Ports, sockets Process-to-process
Packet Tracer - Explore a Network
 Topology Objectives Part 1: Examine Internetwork Traffic at Branch Part 2: Examine Internetwork Traffic to Central Part 3: Examine Internet Traffic from Branch Background This simulation activity is intended
Topology Objectives Part 1: Examine Internetwork Traffic at Branch Part 2: Examine Internetwork Traffic to Central Part 3: Examine Internet Traffic from Branch Background This simulation activity is intended
Combating Common Web App Authentication Threats
 Security PS Combating Common Web App Authentication Threats Bruce K. Marshall, CISSP, NSA-IAM Senior Security Consultant bmarshall@securityps.com Key Topics Key Presentation Topics Understanding Web App
Security PS Combating Common Web App Authentication Threats Bruce K. Marshall, CISSP, NSA-IAM Senior Security Consultant bmarshall@securityps.com Key Topics Key Presentation Topics Understanding Web App
Lecture 9a: Sessions and Cookies
 CS 655 / 441 Fall 2007 Lecture 9a: Sessions and Cookies 1 Review: Structure of a Web Application On every interchange between client and server, server must: Parse request. Look up session state and global
CS 655 / 441 Fall 2007 Lecture 9a: Sessions and Cookies 1 Review: Structure of a Web Application On every interchange between client and server, server must: Parse request. Look up session state and global
EBU response to the public consultation on the draft BEREC report 'Monitoring quality of Internet access services in the context of net neutrality'
 BoR PC02 (14) 11 EBU response to the public consultation on the draft BEREC report 'Monitoring quality of Internet access services in the context of net neutrality' 28.04.2014 The European Broadcasting
BoR PC02 (14) 11 EBU response to the public consultation on the draft BEREC report 'Monitoring quality of Internet access services in the context of net neutrality' 28.04.2014 The European Broadcasting
A Simple Network Analyzer Decoding TCP, UDP, DNS and DHCP headers
 A Simple Network Analyzer Decoding TCP, UDP, DNS and DHCP headers Objectives The main objective of this assignment is to gain a deeper understanding of network activities and network packet formats using
A Simple Network Analyzer Decoding TCP, UDP, DNS and DHCP headers Objectives The main objective of this assignment is to gain a deeper understanding of network activities and network packet formats using
Citrix NetScaler Essentials and Unified Gateway
 Course Code: CNS2221 Vendor: Citrix Course Overview Duration: 5 RRP: 2,690 Citrix NetScaler Essentials and Unified Gateway Overview Designed for students with little or no previous NetScaler, NetScaler
Course Code: CNS2221 Vendor: Citrix Course Overview Duration: 5 RRP: 2,690 Citrix NetScaler Essentials and Unified Gateway Overview Designed for students with little or no previous NetScaler, NetScaler
TechNote AltitudeCDN Multicast+ and OmniCache Support for Citrix
 TechNote AltitudeCDN Multicast+ and OmniCache Support for Citrix Version 1.0 AltitudeCDN TM Multicast+ and AltitudeCDN OmniCache TM have been certified as Citrix Ready for Citrix platforms that support
TechNote AltitudeCDN Multicast+ and OmniCache Support for Citrix Version 1.0 AltitudeCDN TM Multicast+ and AltitudeCDN OmniCache TM have been certified as Citrix Ready for Citrix platforms that support
Lab Using Wireshark to Examine Ethernet Frames
 Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
5. Write a capture filter for question 4.
 Pre-Lab 2: Single Segment IP Networks 1. Review Linux man pages for arp at www.linuxmanpages.com (in both Sections 7 and 8), the ARP RFC (RFC 826) at www.ietf.org, and Section 3.4 of the IBM Red Book.
Pre-Lab 2: Single Segment IP Networks 1. Review Linux man pages for arp at www.linuxmanpages.com (in both Sections 7 and 8), the ARP RFC (RFC 826) at www.ietf.org, and Section 3.4 of the IBM Red Book.
idatafax Troubleshooting
 idatafax Troubleshooting About idatafax idatafax is a client application that connects back to a server at the PHRI based in Hamilton, Ontario, Canada. It is not known to interfere with any software and
idatafax Troubleshooting About idatafax idatafax is a client application that connects back to a server at the PHRI based in Hamilton, Ontario, Canada. It is not known to interfere with any software and
Capturing & Analyzing Network Traffic: tcpdump/tshark and Wireshark
 Capturing & Analyzing Network Traffic: tcpdump/tshark and Wireshark EE 122: Intro to Communication Networks Vern Paxson / Jorge Ortiz / Dilip Anthony Joseph 1 Some slides added from Fei Xu's slides, Small
Capturing & Analyzing Network Traffic: tcpdump/tshark and Wireshark EE 122: Intro to Communication Networks Vern Paxson / Jorge Ortiz / Dilip Anthony Joseph 1 Some slides added from Fei Xu's slides, Small
CCNA Exploration Network Fundamentals. Chapter 03 Application Functionality and Protocols
 CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
Web, HTTP and Web Caching
 Web, HTTP and Web Caching 1 HTTP overview HTTP: hypertext transfer protocol Web s application layer protocol client/ model client: browser that requests, receives, displays Web objects : Web sends objects
Web, HTTP and Web Caching 1 HTTP overview HTTP: hypertext transfer protocol Web s application layer protocol client/ model client: browser that requests, receives, displays Web objects : Web sends objects
ITEC 350: Introduction To Computer Networking Midterm Exam #2 Key. Fall 2008
 ITEC 350: Introduction To Computer Networking Midterm Exam #2 Key Closed book and closed notes. Fall 2008 No electronic devices allowed, e.g., calculator, laptop, PDA. Show your work. No work, no credit.
ITEC 350: Introduction To Computer Networking Midterm Exam #2 Key Closed book and closed notes. Fall 2008 No electronic devices allowed, e.g., calculator, laptop, PDA. Show your work. No work, no credit.
AT&T SD-WAN Network Based service quick start guide
 AT&T SD-WAN Network Based service quick start guide After you order your AT&T SD-WAN Network Based service, you can: Create administrator accounts Log in to the SD-WAN orchestrator Configure business policy
AT&T SD-WAN Network Based service quick start guide After you order your AT&T SD-WAN Network Based service, you can: Create administrator accounts Log in to the SD-WAN orchestrator Configure business policy
Transport and Security Specification
 Transport and Security Specification 15 November 2017 Version: 6.3 Contents Overview 3 Standard network requirements 3 Source and Destination Ports 3 Configuring the Connection Wizard 4 Private Bloomberg
Transport and Security Specification 15 November 2017 Version: 6.3 Contents Overview 3 Standard network requirements 3 Source and Destination Ports 3 Configuring the Connection Wizard 4 Private Bloomberg
If you re a Facebook marketer, you re likely always looking for ways to
 Chapter 1: Custom Apps for Fan Page Timelines In This Chapter Using apps for Facebook marketing Extending the Facebook experience Discovering iframes, Application Pages, and Canvas Pages Finding out what
Chapter 1: Custom Apps for Fan Page Timelines In This Chapter Using apps for Facebook marketing Extending the Facebook experience Discovering iframes, Application Pages, and Canvas Pages Finding out what
NetScaler for Apps and Desktops CNS-222; 5 Days; Instructor-led
 NetScaler for Apps and Desktops CNS-222; 5 Days; Instructor-led Course Description Designed for students with little or no previous NetScaler, NetScaler Gateway or Unified Gateway experience, this course
NetScaler for Apps and Desktops CNS-222; 5 Days; Instructor-led Course Description Designed for students with little or no previous NetScaler, NetScaler Gateway or Unified Gateway experience, this course
Lab Assignment 4 ECE374 Spring Posted: 03/22/18 Due: 03/29/18. In this lab, we ll take a quick look at the ICMP and IP protocols.
 Lab Assignment 4 ECE374 Spring 2018 Posted: 03/22/18 Due: 03/29/18 In this lab, we ll take a quick look at the ICMP and IP protocols. Whenever possible you should hand in Wireshark screenshots that you
Lab Assignment 4 ECE374 Spring 2018 Posted: 03/22/18 Due: 03/29/18 In this lab, we ll take a quick look at the ICMP and IP protocols. Whenever possible you should hand in Wireshark screenshots that you
