Packet Tracer Simulation - TCP and UDP Communications
|
|
|
- Christina Williams
- 6 years ago
- Views:
Transcription
1 Topology Objectives Part 1: Generate Network Traffic in Simulation Mode Part 2: Examine the Functionality of the TCP and UDP Protocols Background This simulation activity is intended to provide a foundation for understanding the TCP and UDP in detail. Simulation mode provides the ability to view the functionality of the different protocols. As data moves through the network, it is broken down into smaller pieces and identified in some fashion so that the pieces can be put back together. Each of these pieces is assigned a specific name (protocol data unit [PDU]) and associated with a specific layer. Packet Tracer Simulation mode enables the user to view each of the protocols and the associated PDU. The steps outlined below lead the user through the process of requesting services using various applications available on a client PC. This activity provides an opportunity to explore the functionality of the TCP and UDP protocols, multiplexing and the function of port numbers in determining which local application requested the data or is sending the data. Part 1: Generate Network Traffic in Simulation Mode Step 1: Generate traffic to populate Address Resolution Protocol (ARP) tables. Perform the following tasks task to reduce the amount of network traffic viewed in the simulation. a. Click MultiServer and click the Desktop tab > Command Prompt. b. Enter the ping command. This will take a few seconds as every device on the network responds to MultiServer. c. Close the MultiServer window Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 6
2 Step 2: Generate web (HTTP) traffic. a. Switch to Simulation mode. b. Click HTTP Client and click the Desktop tab > Web Browser. c. In the URL field, enter and click Go. Envelopes (PDUs) will appear in the simulation window. d. Minimize, but do not close, the HTTP Client configuration window. Step 3: Generate FTP traffic. a. Click FTP Client and click the Desktop tab > Command Prompt. b. Enter the ftp command. PDUs will appear in the simulation window. c. Minimize, but do not close, the FTP Client configuration window. Step 4: Generate DNS traffic. a. Click DNS Client and click the Desktop tab > Command Prompt. b. Enter the nslookup multiserver.pt.ptu command. A PDU will appear in the simulation window. c. Minimize, but do not close, the DNS Client configuration window. Step 5: Generate traffic. a. Click Client and click the Desktop tab > E Mail tool. b. Click Compose and enter the following information: 1) To: user@multiserver.pt.ptu 2) Subject: Personalize the subject line 3) Body: Personalize the c. Click Send. d. Minimize, but do not close, the Client configuration window. Step 6: Verify that the traffic is generated and ready for simulation. Every client computer should have PDUs listed in the Simulation Panel. Part 2: Examine Functionality of the TCP and UDP Protocols Step 1: Examine multiplexing as all of the traffic crosses the network. You will now use the Capture/Forward button and the Back button in the Simulation Panel. a. Click Capture/Forward once. All of the PDUs are transferred to the switch. b. Click Capture/Forward again. Some of the PDUs disappear. What do you think happened to them? c. Click Capture/Forward six times. All clients should have received a reply. Note that only one PDU can cross a wire in each direction at any given time. What is this called? 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 2 of 6
3 d. A variety of PDUs appears in the event list in the upper right pane of the simulation window. Why are they so many different colors? e. Click Back eight times. This should reset the simulation. Note: Do not click Reset Simulation any time during this activity; if you do, you will need to repeat the steps in Part 1. Step 2: Examine HTTP traffic as the clients communicate with the server. a. Filter the traffic that is currently displayed to display only HTTP and TCP PDUs filter the traffic that is currently displayed: 1) Click Edit Filters and toggle the Show All/None check box. 2) Select HTTP and TCP. Click anywhere outside of the Edit Filters box to hide it. The Visible Events should now display only HTTP and TCP PDUs. b. Click Capture/Forward. Hold your mouse above each PDU until you find one that originates from HTTP Client. Click the PDU envelope to open it. c. Click the Inbound PDU Details tab and scroll down to the last section. What is the section labeled? d. Record the SRC PORT, DEST PORT, SEQUENCE NUM, and ACK NUM values. What is written in the field to the left of the WINDOW field? e. Close the PDU and click Capture/Forward until a PDU returns to the HTTP Client with a checkmark. g. There is a second PDU of a different color, which HTTP Client has prepared to send to MultiServer. This is the beginning of the HTTP communication. Click this second PDU envelope and select Outbound PDU Details. h. What information is now listed in the TCP section? How are the port and sequence numbers different from the previous two PDUs? i. Click Back until the simulation is reset. Step 3: Examine FTP traffic as the clients communicate with the server. a. In the Simulation Panel, change Edit Filters to display only FTP and TCP. b. Click Capture/Forward. Hold your cursor above each PDU until you find one that originates from FTP Client. Click that PDU envelope to open it. c. Click the Inbound PDU Details tab and scroll down to the last section. What is the section labeled? 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 3 of 6
4 d. Record the SRC PORT, DEST PORT, SEQUENCE NUM, and ACK NUM values. What is written in the field to the left of the WINDOW field? e. Close the PDU and click Capture/Forward until a PDU returns to the FTP Client with a checkmark. g. Click the Outbound PDU Details tab. How are the port and sequence numbers different from the previous two results? h. Close the PDU and click Capture/Forward until a second PDU returns to the FTP Client. The PDU is a different color. i. Open the PDU and select Inbound PDU Details. Scroll down past the TCP section. What is the message from the server? j. Click Back until the simulation is reset. Step 4: Examine DNS traffic as the clients communicate with the server. a. In the Simulation Panel, change Edit Filters to display only DNS and UDP. b. Click the PDU envelope to open it. c. Click the Inbound PDU Details tab and scroll down to the last section. What is the section labeled? d. Record the SRC PORT and DEST PORT values. Why is there no sequence and acknowledgement number? e. Close the PDU and click Capture/Forward until a PDU returns to the DNS Client with a checkmark. g. What is the last section of the PDU called? h. Click Back until the simulation is reset. Step 5: Examine traffic as the clients communicate with the server. a. In the Simulation Panel, change Edit Filters to display only POP3, SMTP and TCP Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 4 of 6
5 b. Click Capture/Forward. Hold your cursor above each PDU until you find one that originates from Client. Click that PDU envelope to open it. c. Click the Inbound PDU Details tab and scroll down to the last section. What transport layer protocol does traffic use? d. Record the SRC PORT, DEST PORT, SEQUENCE NUM, and ACK NUM values. What is written in the field to the left of the WINDOW field? e. Close the PDU and click Capture/Forward until a PDU returns to the Client with a checkmark. g. Click the Outbound PDU Details tab. How are the port and sequence numbers different from the previous two results? h. There is a second PDU of a different color that HTTP Client has prepared to send to MultiServer. This is the beginning of the communication. Click this second PDU envelope and select Outbound PDU Details. i. How are the port and sequence numbers different from the previous two PDUs? j. What protocol is associated with TCP port 25? What protocol is associated with TCP port 110? k. Click Back until the simulation is reset. Step 6: Examine the use of port numbers from the server. a. To see TCP active sessions, perform the following steps in quick succession: 1) Switch back to Realtime mode. 2) Click MultiServer and click the Desktop tab > Command Prompt. b. Enter the netstat command. What protocols are listed in the left column? What port numbers are being used by the server? c. What states are the sessions in? d. Repeat the netstat command several times until you see only one session still ESTABLISHED. For which service is this connection still open? 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 5 of 6
6 Why doesn t this session close like the other three? (Hint: Check the minimized clients) Suggested Scoring Rubric Activity Section Question Location Possible Points Earned Points Part 2: Examine Functionality of the TCP and UDP Protocols Step 1 15 Step 2 15 Step 3 15 Step 4 15 Step 5 15 Step 6 25 Total Score Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 6 of 6
Packet Tracer - Investigating the TCP/IP and OSI Models in Action (Instructor Version Optional Packet Tracer)
 (Instructor Version Optional Packet Tracer) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding
(Instructor Version Optional Packet Tracer) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding
Packet Tracer - Explore a Network
 Topology Objectives Part 1: Examine Internetwork Traffic at Branch Part 2: Examine Internetwork Traffic to Central Part 3: Examine Internet Traffic from Branch Background This simulation activity is intended
Topology Objectives Part 1: Examine Internetwork Traffic at Branch Part 2: Examine Internetwork Traffic to Central Part 3: Examine Internet Traffic from Branch Background This simulation activity is intended
Use of the TCP/IP Protocols and the OSI Model in Packet Tracer
 Communication Networks [Netw501] Spring 2018 Tutorial 3 Packet Tracer Activity 3 Use of the TCP/IP Protocols and the OSI Model in Packet Tracer Introduction: In Packet Tracer simulation mode, detailed
Communication Networks [Netw501] Spring 2018 Tutorial 3 Packet Tracer Activity 3 Use of the TCP/IP Protocols and the OSI Model in Packet Tracer Introduction: In Packet Tracer simulation mode, detailed
Experiment 3: Protocol Visualization with Packet Tracer
 Experiment 3: Protocol Visualization with Packet Tracer Learning Objectives: Explore Packet Tracer Real-time mode Explore the Logical Workspace Explore Packet Tracer operation Connect devices Examine a
Experiment 3: Protocol Visualization with Packet Tracer Learning Objectives: Explore Packet Tracer Real-time mode Explore the Logical Workspace Explore Packet Tracer operation Connect devices Examine a
GAME100 Lab 5. Before beginning the lab, please download and install Cisco Packet Trace
 GAME100 Lab 5 Name: Part 1: Learn to Use Packet Tracer Objectives Develop an understanding of the basic functions of Packet Tracer. Create/model a simple Ethernet network using two hosts and a switch.
GAME100 Lab 5 Name: Part 1: Learn to Use Packet Tracer Objectives Develop an understanding of the basic functions of Packet Tracer. Create/model a simple Ethernet network using two hosts and a switch.
Introduction to the Packet Tracer Interface using a Hub Topology
 Introduction to Packet Tracer What is Packet Tracer? Packet Tracer is a protocol simulator developed by Dennis Frezzo and his team at Cisco Systems. Packet Tracer (PT) is a powerful and dynamic tool that
Introduction to Packet Tracer What is Packet Tracer? Packet Tracer is a protocol simulator developed by Dennis Frezzo and his team at Cisco Systems. Packet Tracer (PT) is a powerful and dynamic tool that
Department Of Computer Science
 Department Of Computer Science Laboratory Manual Prepared By: Muhammad Nouman Farooq Lecturer and Course Coordinator Course: Computer Communication and Networks (CS-205) Page 1 of 43 Table of Contents
Department Of Computer Science Laboratory Manual Prepared By: Muhammad Nouman Farooq Lecturer and Course Coordinator Course: Computer Communication and Networks (CS-205) Page 1 of 43 Table of Contents
BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic. Topology. Objectives. Background / Scenario
 BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic Topology Objectives Part 1: (Optional) Download and Install Wireshark Part 2: Capture and Analyze Local ICMP Data in Wireshark
BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic Topology Objectives Part 1: (Optional) Download and Install Wireshark Part 2: Capture and Analyze Local ICMP Data in Wireshark
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Network II Lab 03 Part 01: Ping command in simula on mode
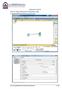 Network II Lab 03 Part 01: Ping command in simula on mode 1. Open the file saved from the previous lab. [Dr. Ahmed ElShafee, ACU Fall 2011, Network II] 1 / 18 2. add simple packet from client to server
Network II Lab 03 Part 01: Ping command in simula on mode 1. Open the file saved from the previous lab. [Dr. Ahmed ElShafee, ACU Fall 2011, Network II] 1 / 18 2. add simple packet from client to server
NET323 D: NETWORKS PROTOCOLS
 1 NET323 D: NETWORKS PROTOCOLS Networks and Communication Systems Department TA. Anfal AlHazzaa Lab # 8: DNS (Domain Name System) Lab Objectives 2 To understand how DNS works Lab Content 3 Introduction
1 NET323 D: NETWORKS PROTOCOLS Networks and Communication Systems Department TA. Anfal AlHazzaa Lab # 8: DNS (Domain Name System) Lab Objectives 2 To understand how DNS works Lab Content 3 Introduction
PT Activity 5.6.1: Packet Tracer Skills Integration Challenge Topology Diagram
 Topology Diagram All contents are Copyright 2008 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 6 Addressing Table Device Interface IP Address Subnet Mask
Topology Diagram All contents are Copyright 2008 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 6 Addressing Table Device Interface IP Address Subnet Mask
CNBK Communications and Networks Lab Book: Purpose of Hardware and Protocols Associated with Networking Computer Systems
 Lab Book: Purpose of Hardware and Protocols Associated with Networking Computer Systems Contents Purpose of Hardware and Protocols Associated with Computer Networks... 3 Lab Objectives... 3 Lab Resources...
Lab Book: Purpose of Hardware and Protocols Associated with Networking Computer Systems Contents Purpose of Hardware and Protocols Associated with Computer Networks... 3 Lab Objectives... 3 Lab Resources...
Lab - Using Wireshark to Examine TCP and UDP Captures
 Topology Part 1 (FTP) Part 1 will highlight a TCP capture of an FTP session. This topology consists of a PC with Internet access. Topology Part 2 (TFTP) Part 2 will highlight a UDP capture of a TFTP session.
Topology Part 1 (FTP) Part 1 will highlight a TCP capture of an FTP session. This topology consists of a PC with Internet access. Topology Part 2 (TFTP) Part 2 will highlight a UDP capture of a TFTP session.
Lab - Configure the Firewall in Windows 8
 Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected over the network Windows 8 installed
Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected over the network Windows 8 installed
CNPE Communications and Networks Lab Book: Data Transmission Over Digital Networks
 Lab Book: Data Transmission Over Digital Networks Contents Data Transmission Over Digital Networks... 3 Lab Objectives... 3 Lab Resources... 3 Task 1 Build the Home Network... 3 Task 2 Configure IP Addresses...
Lab Book: Data Transmission Over Digital Networks Contents Data Transmission Over Digital Networks... 3 Lab Objectives... 3 Lab Resources... 3 Task 1 Build the Home Network... 3 Task 2 Configure IP Addresses...
Appendix B Policies and Filters
 Appendix B Policies and Filters NOTE: This appendix does not describe Access Control Lists (ACLs) or IPX SAP ACLs, which are additional methods for filtering packets. See Software-Based IP Access Control
Appendix B Policies and Filters NOTE: This appendix does not describe Access Control Lists (ACLs) or IPX SAP ACLs, which are additional methods for filtering packets. See Software-Based IP Access Control
Packet Tracer: Novice Session. Packet Tracer: Novice Session 2007 Cisco Systems, Inc. All rights reserved. Cisco Public
 Packet Tracer: Novice Session Packet Tracer: Novice Session 1 How Can I Use Packet Tracer? Problem Scenario: Your students need to learn how to configure a router Ethernet interface and to verify connectivity
Packet Tracer: Novice Session Packet Tracer: Novice Session 1 How Can I Use Packet Tracer? Problem Scenario: Your students need to learn how to configure a router Ethernet interface and to verify connectivity
Internetworking with Packet Tracer
 Internetworking with Packet Tracer Objectives Develop an understanding of the basic functions of Packet Tracer. Create/model two simple Ethernet networks connected by a switch. Observe traffic behavior
Internetworking with Packet Tracer Objectives Develop an understanding of the basic functions of Packet Tracer. Create/model two simple Ethernet networks connected by a switch. Observe traffic behavior
OSI Transport Layer. objectives
 LECTURE 5 OSI Transport Layer objectives 1. Roles of the Transport Layer 1. segmentation of data 2. error detection 3. Multiplexing of upper layer application using port numbers 2. The TCP protocol Communicating
LECTURE 5 OSI Transport Layer objectives 1. Roles of the Transport Layer 1. segmentation of data 2. error detection 3. Multiplexing of upper layer application using port numbers 2. The TCP protocol Communicating
CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols
 CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Objectives Functions of the three upper OSI model layers, network services
CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Objectives Functions of the three upper OSI model layers, network services
Packet Tracer - Navigating the IOS
 Topology Objectives Part 1: Establish Basic Connections, Access the CLI, and Explore Help Part 2: Explore EXEC Modes Part 3: Set the Clock Background In this activity, you will practice skills necessary
Topology Objectives Part 1: Establish Basic Connections, Access the CLI, and Explore Help Part 2: Explore EXEC Modes Part 3: Set the Clock Background In this activity, you will practice skills necessary
Lab - Configure the Firewall in Windows 7 and Vista
 Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected on a network Windows installed
Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected on a network Windows installed
Lab Using Wireshark to Examine Ethernet Frames
 Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
CCNA Semester 1 labs. Part 2 of 2 Labs for chapters 8 11
 CCNA Semester 1 labs Part 2 of 2 Labs for chapters 8 11 8.1.4.6 Lab - Calculating IPv4 Subnets 8.1.4.8 Lab - Designing and Implementing a Subnetted IPv4 Addressing Scheme 8.2.1.5 Lab - Designing and Implementing
CCNA Semester 1 labs Part 2 of 2 Labs for chapters 8 11 8.1.4.6 Lab - Calculating IPv4 Subnets 8.1.4.8 Lab - Designing and Implementing a Subnetted IPv4 Addressing Scheme 8.2.1.5 Lab - Designing and Implementing
Packet Tracer: Novice Session 2007 Cisco Systems, Inc. All rights reserved. Cisco Public. Packet Tracer: Novice Session
 Packet Tracer: Novice Session Packet Tracer: Novice Session 1 How Can I Use Packet Tracer? Problem Scenario: Your students need to learn how to configure a router Ethernet interface and to verify connectivity
Packet Tracer: Novice Session Packet Tracer: Novice Session 1 How Can I Use Packet Tracer? Problem Scenario: Your students need to learn how to configure a router Ethernet interface and to verify connectivity
Unit 28 Website Production ASSIGNMENT 1
 Unit 28 Website Production ASSIGNMENT 1 Last week Learning outcomes History HTML skeleton Annotated diagram of a WAN Servers, routers, client PC, browser, Server OS Switch, packet Architecture ISP Web
Unit 28 Website Production ASSIGNMENT 1 Last week Learning outcomes History HTML skeleton Annotated diagram of a WAN Servers, routers, client PC, browser, Server OS Switch, packet Architecture ISP Web
Packet Tracer - Subnet Scenario 2 Topology
 Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 5 Addressing Table Device Interface IP Address Subnet Mask Default Gateway G0/0 R1 S0/0/0 G0/0 S0/0/0
Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 5 Addressing Table Device Interface IP Address Subnet Mask Default Gateway G0/0 R1 S0/0/0 G0/0 S0/0/0
Lab Using Wireshark to Examine Ethernet Frames
 Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Teacher s Reference Manual
 UNIVERSITY OF MUMBAI Teacher s Reference Manual Subject: Security in Computing Practical with effect from the academic year 2018 2019 Practical 1: Packet Tracer - Configure Cisco Routers for Syslog, NTP,
UNIVERSITY OF MUMBAI Teacher s Reference Manual Subject: Security in Computing Practical with effect from the academic year 2018 2019 Practical 1: Packet Tracer - Configure Cisco Routers for Syslog, NTP,
SC/CSE 3213 Winter Sebastian Magierowski York University CSE 3213, W13 L8: TCP/IP. Outline. Forwarding over network and data link layers
 SC/CSE 3213 Winter 2013 L8: TCP/IP Overview Sebastian Magierowski York University 1 Outline TCP/IP Reference Model A set of protocols for internetworking The basis of the modern IP Datagram Exchange Examples
SC/CSE 3213 Winter 2013 L8: TCP/IP Overview Sebastian Magierowski York University 1 Outline TCP/IP Reference Model A set of protocols for internetworking The basis of the modern IP Datagram Exchange Examples
EXAM - HP0-Y52. Applying HP FlexNetwork Fundamentals. Buy Full Product.
 HP EXAM - HP0-Y52 Applying HP FlexNetwork Fundamentals Buy Full Product http://www.examskey.com/hp0-y52.html Examskey HP HP0-Y52 exam demo product is here for you to test the quality of the product. This
HP EXAM - HP0-Y52 Applying HP FlexNetwork Fundamentals Buy Full Product http://www.examskey.com/hp0-y52.html Examskey HP HP0-Y52 exam demo product is here for you to test the quality of the product. This
1. Which OSI layers offers reliable, connection-oriented data communication services?
 CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
Packet Tracer - Using Traceroute to Discover the Network (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Scenario The company you work for has acquired a new branch location.
(Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Scenario The company you work for has acquired a new branch location.
Lab - Observing DNS Resolution
 Objectives Part 1: Observe the DNS Conversion of a URL to an IP Address Part 2: Observe DNS Lookup Using the Nslookup Command on a Web Site Part 3: Observe DNS Lookup Using the Nslookup Command on Mail
Objectives Part 1: Observe the DNS Conversion of a URL to an IP Address Part 2: Observe DNS Lookup Using the Nslookup Command on a Web Site Part 3: Observe DNS Lookup Using the Nslookup Command on Mail
Router and ACL ACL Filter traffic ACL: The Three Ps One ACL per protocol One ACL per direction One ACL per interface
 CCNA4 Chapter 5 * Router and ACL By default, a router does not have any ACLs configured and therefore does not filter traffic. Traffic that enters the router is routed according to the routing table. *
CCNA4 Chapter 5 * Router and ACL By default, a router does not have any ACLs configured and therefore does not filter traffic. Traffic that enters the router is routed according to the routing table. *
INBOUND AND OUTBOUND NAT
 INBOUND AND OUTBOUND NAT Network Address Translation Course # 2011 1 Overview! Network Address Translation (NAT)! Aliases! Static Address Mappings! Inbound Tunnels! Advanced Tunnel Option SYN Cookies Authentication
INBOUND AND OUTBOUND NAT Network Address Translation Course # 2011 1 Overview! Network Address Translation (NAT)! Aliases! Static Address Mappings! Inbound Tunnels! Advanced Tunnel Option SYN Cookies Authentication
Interconnecting Networks with TCP/IP. 2000, Cisco Systems, Inc. 8-1
 Interconnecting Networks with TCP/IP 2000, Cisco Systems, Inc. 8-1 Objectives Upon completion of this chapter you will be able to perform the following tasks: Identify the IP protocol stack, its protocol
Interconnecting Networks with TCP/IP 2000, Cisco Systems, Inc. 8-1 Objectives Upon completion of this chapter you will be able to perform the following tasks: Identify the IP protocol stack, its protocol
Packet Tracer Create a Simple Network Using Packet Tracer
 Using Packet Tracer Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway PC Ethernet0 DHCP 192.168.0.1 Wireless Router Cisco.com Server LAN 192.168.0.1 255.255.255.0 Internet
Using Packet Tracer Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway PC Ethernet0 DHCP 192.168.0.1 Wireless Router Cisco.com Server LAN 192.168.0.1 255.255.255.0 Internet
Lab Viewing Wireless and Wired NIC Information
 Objectives Part 1: Identify and Work with PC NICs Part 2: Identify and Use the System Tray Network Icons Background / Scenario This lab requires you to determine the availability and status of the network
Objectives Part 1: Identify and Work with PC NICs Part 2: Identify and Use the System Tray Network Icons Background / Scenario This lab requires you to determine the availability and status of the network
Lab Configure and Test Advanced Protocol Handling on the Cisco PIX Security Appliance
 Lab 9.4.10 Configure and Test Advanced Protocol Handling on the Cisco PIX Security Appliance Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Display the
Lab 9.4.10 Configure and Test Advanced Protocol Handling on the Cisco PIX Security Appliance Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Display the
Defining Networks with the OSI Model. Module 2
 Defining Networks with the OSI Model Module 2 Objectives Skills Concepts Objective Domain Description Objective Domain Number Understanding OSI Basics Defining the Communications Subnetwork Defining the
Defining Networks with the OSI Model Module 2 Objectives Skills Concepts Objective Domain Description Objective Domain Number Understanding OSI Basics Defining the Communications Subnetwork Defining the
Experiment 2: Wireshark as a Network Protocol Analyzer
 Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
Cisco 1: Networking Fundamentals
 Western Technical College 10150110 Cisco 1: Networking Fundamentals Course Outcome Summary Course Information Description Career Cluster Instructional Level Total Credits 3.00 Total Hours 90.00 This course
Western Technical College 10150110 Cisco 1: Networking Fundamentals Course Outcome Summary Course Information Description Career Cluster Instructional Level Total Credits 3.00 Total Hours 90.00 This course
SR-201 Network Relay Quick Start Guide
 SR-201 Network Relay Quick Start Guide Table of Content Connect to your device...2 Change configurations...3 Setup remote control via internet...4 Android software...5 Integrate to your applications...6
SR-201 Network Relay Quick Start Guide Table of Content Connect to your device...2 Change configurations...3 Setup remote control via internet...4 Android software...5 Integrate to your applications...6
PT Activity: Configuring a Zone-Based Policy Firewall (ZPF)
 PT Activity: Configuring a Zone-Based Policy Firewall (ZPF) Instructor Version Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 R2 R3 Fa0/1 192.168.1.1 255.255.255.0
PT Activity: Configuring a Zone-Based Policy Firewall (ZPF) Instructor Version Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 R2 R3 Fa0/1 192.168.1.1 255.255.255.0
TCP/IP Transport Layer Protocols, TCP and UDP
 TCP/IP Transport Layer Protocols, TCP and UDP Learning Objectives Identify TCP header fields and operation using a Wireshark FTP session capture. Identify UDP header fields and operation using a Wireshark
TCP/IP Transport Layer Protocols, TCP and UDP Learning Objectives Identify TCP header fields and operation using a Wireshark FTP session capture. Identify UDP header fields and operation using a Wireshark
Packet Tracer - Subnet Scenario 2 (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology 2015 Cisco and/or its affiliates. All rights reserved. This document
(Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology 2015 Cisco and/or its affiliates. All rights reserved. This document
Configuring Commonly Used IP ACLs
 Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
Firewall Policy. Edit Firewall Policy/ACL CHAPTER7. Configure a Firewall Before Using the Firewall Policy Feature
 CHAPTER7 The feature lets you view and modify firewall configurations access rules and CBAC inspection rules in the context of the interfaces whose traffic they filter. Using a graphical representation
CHAPTER7 The feature lets you view and modify firewall configurations access rules and CBAC inspection rules in the context of the interfaces whose traffic they filter. Using a graphical representation
CCNA 1 Chapter 10 v5.0 Exam Answers 2013
 CCNA 1 Chapter 10 v5.0 Exam Answers 2013 1 Which three layers of the OSI model provide similar network services to those provided by the application layer of the TCP/IP model? (Choose three.) physical
CCNA 1 Chapter 10 v5.0 Exam Answers 2013 1 Which three layers of the OSI model provide similar network services to those provided by the application layer of the TCP/IP model? (Choose three.) physical
CSC Network Security
 CSC 474 -- Security Topic 9. Firewalls CSC 474 Dr. Peng Ning 1 Outline Overview of Firewalls Filtering Firewalls Proxy Servers CSC 474 Dr. Peng Ning 2 Overview of Firewalls CSC 474 Dr. Peng Ning 3 1 Internet
CSC 474 -- Security Topic 9. Firewalls CSC 474 Dr. Peng Ning 1 Outline Overview of Firewalls Filtering Firewalls Proxy Servers CSC 474 Dr. Peng Ning 2 Overview of Firewalls CSC 474 Dr. Peng Ning 3 1 Internet
Unit 4: Firewalls (I)
 Unit 4: Firewalls (I) What is a firewall? Types of firewalls Packet Filtering Statefull Application and Circuit Proxy Firewall services and limitations Writing firewall rules Example 1 Example 2 What is
Unit 4: Firewalls (I) What is a firewall? Types of firewalls Packet Filtering Statefull Application and Circuit Proxy Firewall services and limitations Writing firewall rules Example 1 Example 2 What is
CCRI Networking Technology I CSCO-1850 Spring 2014
 CCRI Networking Technology I CSCO-1850 Spring 2014 Instructor John Mowry Telephone 401-825-2138 E-mail jmowry@ccri.edu Office Hours Room 2126 Class Sections 102 Monday & Wednesday 6:00PM-9:50PM, starts
CCRI Networking Technology I CSCO-1850 Spring 2014 Instructor John Mowry Telephone 401-825-2138 E-mail jmowry@ccri.edu Office Hours Room 2126 Class Sections 102 Monday & Wednesday 6:00PM-9:50PM, starts
CSCD 330 Network Programming
 CSCD 330 Network Programming Lecture 9 Transport Layer Winter 2019 Reading: Begin Chapter 3 Some Material in these slides from J.F Kurose and K.W. Ross All material copyright 1996-2007 1 Outline Overview
CSCD 330 Network Programming Lecture 9 Transport Layer Winter 2019 Reading: Begin Chapter 3 Some Material in these slides from J.F Kurose and K.W. Ross All material copyright 1996-2007 1 Outline Overview
a. the physical layer, b. and the data-link layer. a. three physical layers, b. three data-link layers, c. and only one network layer.
 CHAPTER PRACTICE SET Questions Q-. Q-. To make the communication bidirectional, each layer needs to be able to provide two opposite tasks, one in each direction. The link-layer switch is normally involved
CHAPTER PRACTICE SET Questions Q-. Q-. To make the communication bidirectional, each layer needs to be able to provide two opposite tasks, one in each direction. The link-layer switch is normally involved
ch02 True/False Indicate whether the statement is true or false.
 ch02 True/False Indicate whether the statement is true or false. 1. No matter what medium connects computers on a network copper wires, fiber-optic cables, or a wireless setup the same protocol must be
ch02 True/False Indicate whether the statement is true or false. 1. No matter what medium connects computers on a network copper wires, fiber-optic cables, or a wireless setup the same protocol must be
Guide to Networking Essentials, 6 th Edition. Chapter 5: Network Protocols
 Guide to Networking Essentials, 6 th Edition Chapter 5: Network Protocols Objectives Describe the purpose of a network protocol, the layers in the TCP/IP architecture, and the protocols in each TCP/IP
Guide to Networking Essentials, 6 th Edition Chapter 5: Network Protocols Objectives Describe the purpose of a network protocol, the layers in the TCP/IP architecture, and the protocols in each TCP/IP
CCNA Exploration Network Fundamentals. Chapter 3 Application Layer Functionality and Protocols
 CCNA Exploration Network Fundamentals Chapter 3 Application Layer Functionality and Protocols Application Layer Functionality and Protocols Applications: The Interface Between the Networks Horny/Coufal
CCNA Exploration Network Fundamentals Chapter 3 Application Layer Functionality and Protocols Application Layer Functionality and Protocols Applications: The Interface Between the Networks Horny/Coufal
Layer 4: UDP, TCP, and others. based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers
 Layer 4: UDP, TCP, and others based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers Concepts application set transport set High-level, "Application Set" protocols deal only with how handled
Layer 4: UDP, TCP, and others based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers Concepts application set transport set High-level, "Application Set" protocols deal only with how handled
CSEN 503 Introduction to Communication Networks. Mervat AbuElkheir Hana Medhat Ayman Dayf. ** Slides are attributed to J. F.
 CSEN 503 Introduction to Communication Networks Mervat AbuElkheir Hana Medhat Ayman Dayf ** Slides are attributed to J. F. Kurose Chapter 3 outline Transport-layer services Multiplexing and demultiplexing
CSEN 503 Introduction to Communication Networks Mervat AbuElkheir Hana Medhat Ayman Dayf ** Slides are attributed to J. F. Kurose Chapter 3 outline Transport-layer services Multiplexing and demultiplexing
Sirindhorn International Institute of Technology Thammasat University
 Name.............................. ID............... Section...... Seat No...... Thammasat University Final Exam: Semester, 205 Course Title: Introduction to Data Communications Instructor: Steven Gordon
Name.............................. ID............... Section...... Seat No...... Thammasat University Final Exam: Semester, 205 Course Title: Introduction to Data Communications Instructor: Steven Gordon
Firewall Simulation COMP620
 Firewall Simulation COMP620 Firewall Simulation The simulation allows participants to configure their own simulated firewalls using Cisco-like syntax. Participants can take benign or malicious actions
Firewall Simulation COMP620 Firewall Simulation The simulation allows participants to configure their own simulated firewalls using Cisco-like syntax. Participants can take benign or malicious actions
Interconnecting Networks with TCP/IP
 Chapter 8 Interconnecting s with TCP/IP 1999, Cisco Systems, Inc. 8-1 Introduction to TCP/IP Internet TCP/IP Early protocol suite Universal 1999, Cisco Systems, Inc. www.cisco.com ICND 8-2 TCP/IP Protocol
Chapter 8 Interconnecting s with TCP/IP 1999, Cisco Systems, Inc. 8-1 Introduction to TCP/IP Internet TCP/IP Early protocol suite Universal 1999, Cisco Systems, Inc. www.cisco.com ICND 8-2 TCP/IP Protocol
Inspection of Router-Generated Traffic
 Inspection of Router-Generated Traffic The Inspection of Router-Generated Traffic feature allows Context-Based Access Control (CBAC) to inspect traffic that is originated by or destined to the router on
Inspection of Router-Generated Traffic The Inspection of Router-Generated Traffic feature allows Context-Based Access Control (CBAC) to inspect traffic that is originated by or destined to the router on
Blackboard Learn: Basics
 Blackboard Learn: Basics This document includes the following topics: 1. Log in Page 2 2. Find Your Courses Page 2 3. View Course Content Page 3 4. Add a Folder Page 3 5. Add a File Page 5 6. Add a Web
Blackboard Learn: Basics This document includes the following topics: 1. Log in Page 2 2. Find Your Courses Page 2 3. View Course Content Page 3 4. Add a Folder Page 3 5. Add a File Page 5 6. Add a Web
OSI Model with Protocols. Layer Name PDU Address Protocols Device
 NetEss Name: Networking Essentials Prof. CHIN OSI Model with Protocols Layer Name PDU Address Protocols Device 7 Application Data FTP, SSH, Telnet, SMTP, DNS TFTP,HTTP, POP3, IMAP, HTTPS 6 Presentation
NetEss Name: Networking Essentials Prof. CHIN OSI Model with Protocols Layer Name PDU Address Protocols Device 7 Application Data FTP, SSH, Telnet, SMTP, DNS TFTP,HTTP, POP3, IMAP, HTTPS 6 Presentation
Network II Lab 01. Part 01: Interface Overview. Program interface
 Part 01: Interface Overview Network II Lab 01 This initial interface contains ten components. If you are unsure of what a particular interface item does, move your mouse over the item and a help balloon
Part 01: Interface Overview Network II Lab 01 This initial interface contains ten components. If you are unsure of what a particular interface item does, move your mouse over the item and a help balloon
Game100 Networking Lab 4. Part 1 (5.1.4) Using the Windows Calculator with Network Addresses
 Game100 Networking Lab 4 Name: Part 1 (5.1.4) Using the Windows Calculator with Network Addresses Objectives Switch between the two Windows Calculator modes. Use Windows Calculator to convert between decimal,
Game100 Networking Lab 4 Name: Part 1 (5.1.4) Using the Windows Calculator with Network Addresses Objectives Switch between the two Windows Calculator modes. Use Windows Calculator to convert between decimal,
Hands-On Activity. Firewall Simulation. Simulated Network. Firewall Simulation 3/19/2010. On Friday, February 26, we will be meeting in
 Hands-On Activity Firewall Simulation COMP620 On Friday, February 26, we will be meeting in the Graham 212 lab to participate in a firewall configuration simulation. This simulator was written by Dr. Williams
Hands-On Activity Firewall Simulation COMP620 On Friday, February 26, we will be meeting in the Graham 212 lab to participate in a firewall configuration simulation. This simulator was written by Dr. Williams
SonicWALL / Toshiba General Installation Guide
 SonicWALL / Toshiba General Installation Guide SonicWALL currently maintains two operating systems for its Unified Threat Management (UTM) platform, StandardOS and EnhancedOS. When a SonicWALL is implemented
SonicWALL / Toshiba General Installation Guide SonicWALL currently maintains two operating systems for its Unified Threat Management (UTM) platform, StandardOS and EnhancedOS. When a SonicWALL is implemented
Network+ Guide to Networks 6 th Edition. Chapter 9 In-Depth TCP/IP Networking
 Network+ Guide to Networks 6 th Edition Chapter 9 In-Depth TCP/IP Networking Objectives Describe methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Network+ Guide to Networks 6 th Edition Chapter 9 In-Depth TCP/IP Networking Objectives Describe methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Network+ Guide to Networks 5 th Edition. Chapter 10 In-Depth TCP/IP Networking
 Network+ Guide to Networks 5 th Edition Chapter 10 In-Depth TCP/IP Networking Objectives Understand methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Network+ Guide to Networks 5 th Edition Chapter 10 In-Depth TCP/IP Networking Objectives Understand methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
CCNA R&S: Introduction to Networks. Chapter 10: The Application Layer
 CCNA R&S: Introduction to Networks Chapter 10: The Application Layer Frank Schneemann 10.0.1.1 Introduction 10.0.1.2 Activity - Application Investigation 10.1.1.1 OSI and TCP/IP Models Revisited The application
CCNA R&S: Introduction to Networks Chapter 10: The Application Layer Frank Schneemann 10.0.1.1 Introduction 10.0.1.2 Activity - Application Investigation 10.1.1.1 OSI and TCP/IP Models Revisited The application
CCNA Exploration Network Fundamentals. Chapter 04 OSI Transport Layer
 CCNA Exploration Network Fundamentals Chapter 04 OSI Transport Layer Updated: 05/05/2008 1 4.1 Roles of the Transport Layer 2 4.1 Roles of the Transport Layer The OSI Transport layer accept data from the
CCNA Exploration Network Fundamentals Chapter 04 OSI Transport Layer Updated: 05/05/2008 1 4.1 Roles of the Transport Layer 2 4.1 Roles of the Transport Layer The OSI Transport layer accept data from the
Chapter 2 Layer Architecture of Network Protocols. School of Info. Sci. & Eng. Shandong Univ.
 Chapter 2 Architecture of Network Protocols School of Info. Sci. & Eng. Shandong Univ. Outline 2.1 Examples of ing 2.2 OSI Reference Model (Continued from last time) 2.3. TCP/IP Architecture 2.4 Berkeley
Chapter 2 Architecture of Network Protocols School of Info. Sci. & Eng. Shandong Univ. Outline 2.1 Examples of ing 2.2 OSI Reference Model (Continued from last time) 2.3. TCP/IP Architecture 2.4 Berkeley
Introduction to Networking
 Introduction to Networking Chapters 1 and 2 Outline Computer Network Fundamentals Defining a Network Networks Defined by Geography Networks Defined by Topology Networks Defined by Resource Location OSI
Introduction to Networking Chapters 1 and 2 Outline Computer Network Fundamentals Defining a Network Networks Defined by Geography Networks Defined by Topology Networks Defined by Resource Location OSI
Communicating over the Network
 Communicating over the Network Network Fundamentals Chapter 2 Version 4.0 1 Network Structure The elements of communication 3 common elements of communication Message source people/electronic devices need
Communicating over the Network Network Fundamentals Chapter 2 Version 4.0 1 Network Structure The elements of communication 3 common elements of communication Message source people/electronic devices need
Lab Configure Cisco IOS Firewall CBAC on a Cisco Router
 Lab 3.8.3 Configure Cisco IOS Firewall CBAC on a Cisco Router Objective Scenario Topology Estimated Time: 35 minutes Number of Team Members: Two teams with four students per team In this lab, students
Lab 3.8.3 Configure Cisco IOS Firewall CBAC on a Cisco Router Objective Scenario Topology Estimated Time: 35 minutes Number of Team Members: Two teams with four students per team In this lab, students
How to configure the AT-AR450S Firewall using the Graphical User Interface (GUI)
 How to configure the AT-AR450S Firewall using the Graphical User Interface (GUI) Introduction This document describes the firewall configuration facility available on the AT-AR450S HTTP-based Graphical
How to configure the AT-AR450S Firewall using the Graphical User Interface (GUI) Introduction This document describes the firewall configuration facility available on the AT-AR450S HTTP-based Graphical
Ethernet / TCP-IP - Training Suite Application level protocols
 Ethernet / TCP-IP - Training Suite 05 - Application level protocols Application layer protocols 2 World Wide Web HTTP I want HTTP this resource. Hypertext Transfer Protocol (HTTP) Used by the World Wide
Ethernet / TCP-IP - Training Suite 05 - Application level protocols Application layer protocols 2 World Wide Web HTTP I want HTTP this resource. Hypertext Transfer Protocol (HTTP) Used by the World Wide
CS 356 Lab #1: Basic LAN Setup & Packet capture/analysis using Ethereal
 CS 356 Lab #1: Basic LAN Setup & Packet capture/analysis using Ethereal Tasks: Time: 2:00 hrs (Task 1-6 should take 45 min; the rest of the time is for Ethereal) 1 - Verify that TCP/IP is installed on
CS 356 Lab #1: Basic LAN Setup & Packet capture/analysis using Ethereal Tasks: Time: 2:00 hrs (Task 1-6 should take 45 min; the rest of the time is for Ethereal) 1 - Verify that TCP/IP is installed on
Hands-On Ethical Hacking and Network Defense
 Hands-On Ethical Hacking and Network Defense Chapter 2 TCP/IP Concepts Review Last modified 1-11-17 Objectives Describe the TCP/IP protocol stack Explain the basic concepts of IP addressing Explain the
Hands-On Ethical Hacking and Network Defense Chapter 2 TCP/IP Concepts Review Last modified 1-11-17 Objectives Describe the TCP/IP protocol stack Explain the basic concepts of IP addressing Explain the
Connectionless and Connection-Oriented Protocols OSI Layer 4 Common feature: Multiplexing Using. The Transmission Control Protocol (TCP)
 Lecture (07) OSI layer 4 protocols TCP/UDP protocols By: Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU Fall2014, Computer Networks II Introduction Most data-link protocols notice errors then discard frames
Lecture (07) OSI layer 4 protocols TCP/UDP protocols By: Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU Fall2014, Computer Networks II Introduction Most data-link protocols notice errors then discard frames
B.Sc. (Hons.) Computer Science with Network Security B.Eng. (Hons) Telecommunications B.Sc. (Hons) Business Information Systems
 B.Sc. (Hons.) Computer Science with Network Security B.Eng. (Hons) Telecommunications B.Sc. (Hons) Business Information Systems Bridge BTEL/PT BCNS/14/FT BIS/14/FT BTEL/14/FT Examinations for 2014-2015
B.Sc. (Hons.) Computer Science with Network Security B.Eng. (Hons) Telecommunications B.Sc. (Hons) Business Information Systems Bridge BTEL/PT BCNS/14/FT BIS/14/FT BTEL/14/FT Examinations for 2014-2015
TCP/IP Fundamentals. Introduction. Practice Practice : Name. Date Period
 Name Date Period TCP/IP Fundamentals Introduction For the Network+ Certification exam, you should be able to identify the class of an IP address, an APIPA IP address, and a private IP address as well as
Name Date Period TCP/IP Fundamentals Introduction For the Network+ Certification exam, you should be able to identify the class of an IP address, an APIPA IP address, and a private IP address as well as
Actual4Test. Actual4test - actual test exam dumps-pass for IT exams
 Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 200-125 Title : CCNA Cisco Certified Network Associate CCNA (v3.0) Vendor : Cisco Version : DEMO Get
Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 200-125 Title : CCNA Cisco Certified Network Associate CCNA (v3.0) Vendor : Cisco Version : DEMO Get
ECE 333: Introduction to Communication Networks Fall 2001
 ECE 333: Introduction to Communication Networks Fall 2001 Lecture 26: Transport layer I 1 Transport Layer In the remaining lectures, we will discuss several issues that are commonly addressed at the transport
ECE 333: Introduction to Communication Networks Fall 2001 Lecture 26: Transport layer I 1 Transport Layer In the remaining lectures, we will discuss several issues that are commonly addressed at the transport
Lab Capturing and Analyzing Network Traffic
 Lab 1.2.2 Capturing and Analyzing Network Traffic Host Name IP Address Fa0/0 Subnet Mask IP Address S0/0/0 Subnet Mask Default Gateway RouterA 172.17.0.1 255.255.0.0 192.168.1.1 (DCE) 255.255.255.0 N/A
Lab 1.2.2 Capturing and Analyzing Network Traffic Host Name IP Address Fa0/0 Subnet Mask IP Address S0/0/0 Subnet Mask Default Gateway RouterA 172.17.0.1 255.255.0.0 192.168.1.1 (DCE) 255.255.255.0 N/A
Interconnecting Cisco Networking Devices Part1 ( ICND1) Exam.
 Cisco 640-822 Interconnecting Cisco Networking Devices Part1 ( ICND1) Exam TYPE: DEMO http://www.examskey.com/640-822.html Examskey Cisco 640-822 exam demo product is here for you to test quality of the
Cisco 640-822 Interconnecting Cisco Networking Devices Part1 ( ICND1) Exam TYPE: DEMO http://www.examskey.com/640-822.html Examskey Cisco 640-822 exam demo product is here for you to test quality of the
Lecture (11) OSI layer 4 protocols TCP/UDP protocols
 Lecture (11) OSI layer 4 protocols TCP/UDP protocols Dr. Ahmed M. ElShafee ١ Agenda Introduction Typical Features of OSI Layer 4 Connectionless and Connection Oriented Protocols OSI Layer 4 Common feature:
Lecture (11) OSI layer 4 protocols TCP/UDP protocols Dr. Ahmed M. ElShafee ١ Agenda Introduction Typical Features of OSI Layer 4 Connectionless and Connection Oriented Protocols OSI Layer 4 Common feature:
4.0.1 CHAPTER INTRODUCTION
 4.0.1 CHAPTER INTRODUCTION Data networks and the Internet support the human network by supplying seamless, reliable communication between people - both locally and around the globe. On a single device,
4.0.1 CHAPTER INTRODUCTION Data networks and the Internet support the human network by supplying seamless, reliable communication between people - both locally and around the globe. On a single device,
CCNA 1 Final Exam Answers UPDATE 2012 eg.1
 CCNA 1 Final Exam Answers UPDATE 2012 eg.1 January 12th, 2012AdminLeave a commentgo to comments Which of the following are the address ranges of the private IP addresses? (Choose three.) 10.0.0.0 to 10.255.255.255
CCNA 1 Final Exam Answers UPDATE 2012 eg.1 January 12th, 2012AdminLeave a commentgo to comments Which of the following are the address ranges of the private IP addresses? (Choose three.) 10.0.0.0 to 10.255.255.255
Network+ Guide to Networks, Seventh Edition Chapter 2, Solutions
 Network+ Guide to Networks, Seventh Edition Chapter 2, Solutions Review Questions 1. Which part of a MAC address is unique to each manufacturer? A. The network identifier B. The OUI C. The device identifier
Network+ Guide to Networks, Seventh Edition Chapter 2, Solutions Review Questions 1. Which part of a MAC address is unique to each manufacturer? A. The network identifier B. The OUI C. The device identifier
Cisco Spark API Workshop
 BRING YOUR LAPTOP! Cisco Spark API Workshop Eugene Morozov Technical Manager CEE-RCIS, N&B 21 April 2018 Fulda What is this? This session IS NOT: The upcoming Emerging Technologies Workshop Experimenting
BRING YOUR LAPTOP! Cisco Spark API Workshop Eugene Morozov Technical Manager CEE-RCIS, N&B 21 April 2018 Fulda What is this? This session IS NOT: The upcoming Emerging Technologies Workshop Experimenting
Protocol Analysis: Capturing Packets
 Protocol Analysis: Capturing Packets This project is intended to be done on the EiLab Network, but if you want to try to VPN into the EiLab Network on your own PC from your home or workplace, follow these
Protocol Analysis: Capturing Packets This project is intended to be done on the EiLab Network, but if you want to try to VPN into the EiLab Network on your own PC from your home or workplace, follow these
CCNA Exploration Network Fundamentals. Chapter 03 Application Functionality and Protocols
 CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
Lab 6: Access Lists. Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/ R1
 Lab 6: Access Lists Network Topology:- Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/0 192.168.0.1 255.255.255.0 ----- R1 Fa 0/1 192.168.10.1 255.255.255.0 ----- Se 0/0/0 10.0.0.1 255.255.255.252
Lab 6: Access Lists Network Topology:- Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/0 192.168.0.1 255.255.255.0 ----- R1 Fa 0/1 192.168.10.1 255.255.255.0 ----- Se 0/0/0 10.0.0.1 255.255.255.252
Applied Networks & Security
 Applied Networks & Security TCP/IP Networks with Critical Analysis http://condor.depaul.edu/~jkristof/it263/ John Kristoff jtk@depaul.edu IT 263 Spring 2006/2007 John Kristoff - DePaul University 1 Critical
Applied Networks & Security TCP/IP Networks with Critical Analysis http://condor.depaul.edu/~jkristof/it263/ John Kristoff jtk@depaul.edu IT 263 Spring 2006/2007 John Kristoff - DePaul University 1 Critical
