Protect Session B10039 ArcSight Activate Threat Intelligence Packages
|
|
|
- Kelley Clarke
- 5 years ago
- Views:
Transcription
1 Protect Session B10039 ArcSight Activate Threat Intelligence Packages Time to stop reinventing the wheel Prepared by SEMplicity & HPE George A. Boitano gboitano@semplicityinc.com Yun Peng yunp@hpe.com
2 Overview Session: Speakers: George A. Boitano, SEMplicity Inc. Yun Peng, HPE Use the mobile app: 1. Access My schedule 2. Click on this session 3. Go to Rate & review If the session is not on your schedule, access it via the session scheduler, click on it, and go to Rate & review. Or use the hard copy surveys Thank you for providing your feedback, which helps us enhance content for future events. 2
3 Overview Activate Review The Data Fusion Model Activate LifeCycle Applicability to Threat Intelligence Activate Threat Intelligence Model Objectives Implementation The Collective Intelligence Framework Threat Intelligence Level 1: Warnings and Indicators Threat Intelligence Level 2: Situational Awareness Where to from here? 3
4 ArcSight Activate Overview 4
5 Activate Essentials: The Model 5
6 Activate Essentials: The Lifecycle 6
7 Activate Threat Intelligence Objectives Level 0: Ingest all forms of Threat Intelligence Process data from any number of sources: open source, proprietary, governmental, etc. Process data in any format: csv, XML, STIX, HTML, Flat File, web services, etc. Normalize data to 20+ standard fields in Activate Threat Intel Schema Level 1: Populate Threat Model Model is several Active Lists conforming to Activate Threat Intel Schema Also show summary information on Threat Model activity Level 2: Contextualize Events Enrich incoming and correlated events with data from Threat Model Level 3: Track State Mark assets based on threat activity Report on threat activity across assets 7
8 Prior Art for ArcSight Threat Intelligence Subscription Services: Threat Central, ThreatStream, ISS Open Source: 60+ sites offering free Threat Intelligence Government intelligence, distributed to certain clients Industry-specific intelligence shared with certain verticals Homegrown intelligence derived from internal events All using their own FlexConnectors, ESM Content, etc. This is the problem Activate is designed to solve Standardize on a common schema and ESM content; Provide common framework for sharing content and intelligence; Stop reinventing the wheel for each company, each industry, each individual threat feed. 8
9 Populating the Threat Model 9
10 Activate Threat Model Architecture Intel Sources Open Source Industry / Governmental Derived Internally Subscription Other? Protocols: http ftp flat file odbc/jdbc web services Formats: csv fixed column report STIX/TAXI XML JSON CIF yml config files Elastic Search Ubuntu TLS 14 Malicious Indicator csv files: bad IPV4s, bad IPv6s bad URLs, bad s bad userids, bad filehashes CIF Event Rules ArcSight CIF FlexConnector Malicious Indicator Lists ArcSight ESM 10
11 Collective Intelligence Framework (CIF) History Open Source Project Part of CSIRTGadgets Founded active community Implementation Runs on Ubuntu 14 LTS Uses ElasticSearch Current release (2.0, massive-octo-spice) implemented in Perl Next release (3.0, bearded-avenger) due in about 1 year, re-coded in Python For more info
12 CIF: Strengths and Weaknesses Strengths: open source handles all formats handles all protocols Standardizes on STIX-like schema easy intel source config w/yml very easy one-line install consolidates threat intel data into feeds via line command runs as a daemon with configurable poll intervals easily customized and expanded Weaknesses: open source one-line install doesn t always work due to dependency changes error handling and error messages not great documentation about average for open source requires a lot of disk storage for ElasticSearch 12
13 CIF Samples EasyButton Install Sample YML config file for a threat intel source Sample line commands to create CSVs for FlexConnector 13
14 CIF yml Activate Content ymlconfiguration files: Each file contains configuration for one or more open source sites Configurations within a yml file may inherit attributes It is is relatively easy to create new yml configuration for new or custom threat intelligence Regex parsing of feeds is implemented Support for corporate proxies CIF as delivered contains config for ~25 popular open source feeds The Activate L1 content delivers configuration for an additional 25 feeds now, all major open source feeds are covered Each source has its own configurable confidence score, used to resolve collisions with other feeds Periodic harvest of each source configurable in CIF Data from each source is normalized into CIF schema. 14
15 The CIF FlexConnector & ESM Content Reads csv output from cif --feed command as scheduled cron jobs: Multi Folder File Follower Separate csv files for malicious ipv4s, ipv6s, s, hashes, users Formats SmartMessage and sends to ESM devicevendor=cif deviceproduct=threat Intel Rules populate active lists with fields from these events, thus building the threat model Global variables extract data from these lists to detect malicious activity and enrich events Dashboards display and monitor threat model activity 15
16 Threat Model Activity Dashboard 16
17 Threat Model Malicious IP List Drilldown 17
18 Threat Intel L1 Global Variables Determine if an indicator is malicious: IPv4, IPv6 URL or Domain To be implemented: , hash, user Problem with URLs/Domains: List: mybadurl.google.com Event: steve.mybadurl.google.com Result: InActivateList performs string compare, returns False, which is incorrect Solution: Global Variables to perform malicious URL lookups Given mybadurl.google.com in malicious list and steve.mybadurl.google.com in sourcehostname, variable InMalciousUrlList returns True, which is correct Other variables extract data from these Active Lists to enrich events: Source Severity Confidence Date first observed in wild Over 16 other fields! 18
19 Using the Threat Model 19
20 This is a rolling (up to 3 year) roadmap and is subject to change without notice Threat Intelligence Packages Activate Base (required) L1-Threat Intelligence - Indicators and Warnings Suspicious active lists Rules to populate suspicious lists Variables to retrieve suspicious data L2-Threat Intelligence - Situational Awareness Rules to detect events/attacks from suspicious list Dashboards/Reports/Active channels Product packages, such as Threat Central
21 This is a rolling (up to 3 year) roadmap and is subject to change without notice Alerts to Detect Suspicious Activities Command and control Dangerous Browsing DNS Queries Phishing Reconnaissance Internal Assets Found in Reputation Data Anonymization
22 This is a rolling (up to 3 year) roadmap and is subject to change without notice Threat Intelligence Alerts
23 This is a rolling (up to 3 year) roadmap and is subject to change without notice Threat Intelligence Activity Overview
24 This is a rolling (up to 3 year) roadmap and is subject to change without notice Reputation Address Data Overview
25 This is a rolling (up to 3 year) roadmap and is subject to change without notice Report of Threat Intelligence Alerts
26 Roadmap Improve collision logic in CIF Improve error handling in CIF Beaded-Avenger release Place Public CIF server in Cloud? 26
27 Anyone Interested? Your Site! CIF SEMplicity Cloud CSV Files Syslog or SmartMessage Connector ArcSight CIF FlexConnector CIF Event Rules Malicious Indicator Lists ArcSight ESM 27
28 Thanks you for coming! Session B10039 For more information, please feel free to contact: George A. Boitano Yun Peng
Asset and network modeling in HP ArcSight ESM and Express
 Asset and network modeling in HP ArcSight ESM and Express Till Jäger, CISSP, CEH EMEA ArcSight Architect, HP ESP Agenda Overview Walkthrough of asset modeling in ArcSight ESM More inside info about the
Asset and network modeling in HP ArcSight ESM and Express Till Jäger, CISSP, CEH EMEA ArcSight Architect, HP ESP Agenda Overview Walkthrough of asset modeling in ArcSight ESM More inside info about the
ArcSight Activate Framework
 ArcSight Activate Framework Petropoulos #HPProtect 44% Have trouble managing their SIEM eiqnetworks 2013 SIEM Survey #1 challenge Identification of key events SANS 2012 Log Management and Event Management
ArcSight Activate Framework Petropoulos #HPProtect 44% Have trouble managing their SIEM eiqnetworks 2013 SIEM Survey #1 challenge Identification of key events SANS 2012 Log Management and Event Management
Enriching and Automating Fraud Response with HP ArcSight ESM
 Enriching and Automating Fraud Response with HP ArcSight ESM TB3022 Ron Stamper, Regions Financial, Cybersecurity Engineer Josh Larkins, Malcovery Security, Sr Threat Intel Analyst Table of Contents Introduction
Enriching and Automating Fraud Response with HP ArcSight ESM TB3022 Ron Stamper, Regions Financial, Cybersecurity Engineer Josh Larkins, Malcovery Security, Sr Threat Intel Analyst Table of Contents Introduction
Automated Response in Cyber Security SOC with Actionable Threat Intelligence
 Automated Response in Cyber Security SOC with Actionable Threat Intelligence while its biggest weakness is lack of visibility: SOCs still can t detect previously unknown threats, which is a consistent
Automated Response in Cyber Security SOC with Actionable Threat Intelligence while its biggest weakness is lack of visibility: SOCs still can t detect previously unknown threats, which is a consistent
HPE Security ArcSight User Behavior Analytics
 HPE Security ArcSight Analytics Software Version: 5.0 Integration and Content Guide July 21, 2016 Legal Notices Warranty The only warranties for Hewlett Packard Enterprise products and services are set
HPE Security ArcSight Analytics Software Version: 5.0 Integration and Content Guide July 21, 2016 Legal Notices Warranty The only warranties for Hewlett Packard Enterprise products and services are set
McAfee Enterprise Security Manager 11.1.x Release Notes
 McAfee Enterprise Security Manager 11.1.x Release Notes Contents Installation information What's new in the 11.1.3 update Resolved issues in update 11.1.3 Flash to HTML migration Installation information
McAfee Enterprise Security Manager 11.1.x Release Notes Contents Installation information What's new in the 11.1.3 update Resolved issues in update 11.1.3 Flash to HTML migration Installation information
ElasticIntel. Scalable Threat Intel Aggregation in AWS
 ElasticIntel Scalable Threat Intel Aggregation in AWS Presenter: Matt Jane Obligatory Who I Am slide.. Builder/Automator I put things in clouds Open Source Advocate
ElasticIntel Scalable Threat Intel Aggregation in AWS Presenter: Matt Jane Obligatory Who I Am slide.. Builder/Automator I put things in clouds Open Source Advocate
<Partner Name> RSA NETWITNESS Security Operations Implementation Guide. Swimlane 2.x. <Partner Product>
 RSA NETWITNESS Security Operations Implementation Guide Jeffrey Carlson, RSA Partner Engineering Last Modified: 05/01/2017 Solution Summary The RSA NetWitness integration
RSA NETWITNESS Security Operations Implementation Guide Jeffrey Carlson, RSA Partner Engineering Last Modified: 05/01/2017 Solution Summary The RSA NetWitness integration
<Partner Name> RSA NETWITNESS Intel Feeds Implementation Guide. Kaspersky Threat Feed Service. <Partner Product>
 RSA NETWITNESS Intel Feeds Implementation Guide Kaspersky Jeffrey Carlson, RSA Partner Engineering Last Modified: December 19 th, 2017 Solution Summary Kaspersky Lab offers
RSA NETWITNESS Intel Feeds Implementation Guide Kaspersky Jeffrey Carlson, RSA Partner Engineering Last Modified: December 19 th, 2017 Solution Summary Kaspersky Lab offers
<Partner Name> <Partner Product> RSA NETWITNESS Security Operations Implementation Guide. Gurucul Risk Analytics
 RSA NETWITNESS Security Operations Implementation Guide Jeffrey Carlson, RSA Partner Engineering Last Modified: June 27 th, 2017 (GRA) Overview Gurucul is changing the
RSA NETWITNESS Security Operations Implementation Guide Jeffrey Carlson, RSA Partner Engineering Last Modified: June 27 th, 2017 (GRA) Overview Gurucul is changing the
McAfee Enterprise Security Manager 10.3.x Release Notes
 McAfee Enterprise Security Manager 10.3.x Release Notes Contents Installation information What's new in update 10.3.4 Resolved issues in update 10.3.4 Migrating from Flash to HTML Installation information
McAfee Enterprise Security Manager 10.3.x Release Notes Contents Installation information What's new in update 10.3.4 Resolved issues in update 10.3.4 Migrating from Flash to HTML Installation information
Detect Cyber Threats with Securonix Proxy Traffic Analyzer
 Detect Cyber Threats with Securonix Proxy Traffic Analyzer Introduction Many organizations encounter an extremely high volume of proxy data on a daily basis. The volume of proxy data can range from 100
Detect Cyber Threats with Securonix Proxy Traffic Analyzer Introduction Many organizations encounter an extremely high volume of proxy data on a daily basis. The volume of proxy data can range from 100
Tanium Connect User Guide. Version 4.8.3
 Tanium Connect User Guide Version 4.8.3 September 11, 2018 The information in this document is subject to change without notice. Further, the information provided in this document is provided as is and
Tanium Connect User Guide Version 4.8.3 September 11, 2018 The information in this document is subject to change without notice. Further, the information provided in this document is provided as is and
ArcSight priority formula
 ArcSight priority formula Fred Thiele, Managing Principal, South Pacific @fgthiele #HPProtect Our journey The priority formula Let s understand the ins and outs Look at some examples Take advantage of
ArcSight priority formula Fred Thiele, Managing Principal, South Pacific @fgthiele #HPProtect Our journey The priority formula Let s understand the ins and outs Look at some examples Take advantage of
THE RSA SUITE NETWITNESS REINVENT YOUR SIEM. Presented by: Walter Abeson
 THE RSA NETWITNESS SUITE REINVENT YOUR SIEM Presented by: Walter Abeson 1 Reality Goals GOALS VERSUS REALITY OF SIEM 1.0 Single compliance & security interface Analyze & prioritize alerts across various
THE RSA NETWITNESS SUITE REINVENT YOUR SIEM Presented by: Walter Abeson 1 Reality Goals GOALS VERSUS REALITY OF SIEM 1.0 Single compliance & security interface Analyze & prioritize alerts across various
HP HP0-M54. ArcSight ESM Security Analyst. Version: 4.0
 HP HP0-M54 ArcSight ESM Security Analyst Version: 4.0 QUESTION NO: 1 Which statement is true about inline filters? A. An inline filter applies only to its current Active Channel. B. An inline filter applies
HP HP0-M54 ArcSight ESM Security Analyst Version: 4.0 QUESTION NO: 1 Which statement is true about inline filters? A. An inline filter applies only to its current Active Channel. B. An inline filter applies
ThreatConnect Learning Exercises
 ThreatConnect Learning Exercises The following exercises will teach you some of the important features within the ThreatConnect platform. You will learn various ways of adding intelligence data into ThreatConnect,
ThreatConnect Learning Exercises The following exercises will teach you some of the important features within the ThreatConnect platform. You will learn various ways of adding intelligence data into ThreatConnect,
Tuning HP ArcSight ESM prioritization
 Tuning HP ArcSight ESM prioritization Beirne Konarski, Principal Consultant #HPProtect Priority What does the priority score mean? The priority helps you determine which events are most important to act
Tuning HP ArcSight ESM prioritization Beirne Konarski, Principal Consultant #HPProtect Priority What does the priority score mean? The priority helps you determine which events are most important to act
Tracking Evil with Passive DNS
 Tracking Evil with Passive DNS Bojan Ždrnja, CISSP, GCIA, GCIH Bojan.Zdrnja@infigo.hr INFIGO IS http://www.infigo.hr Who am I? Senior information security consultant with INFIGO IS (Croatia) Mainly doing
Tracking Evil with Passive DNS Bojan Ždrnja, CISSP, GCIA, GCIH Bojan.Zdrnja@infigo.hr INFIGO IS http://www.infigo.hr Who am I? Senior information security consultant with INFIGO IS (Croatia) Mainly doing
DomainTools App for QRadar
 DomainTools App for QRadar App Startup Guide for Version 1.0.480 Updated November 1, 2017 Table of Contents DomainTools App for QRadar... 1 App Features... 2 Prerequisites... 3 Data Source Identification...
DomainTools App for QRadar App Startup Guide for Version 1.0.480 Updated November 1, 2017 Table of Contents DomainTools App for QRadar... 1 App Features... 2 Prerequisites... 3 Data Source Identification...
McAfee Enterprise Security Manager 10.3.x Release Notes
 McAfee Enterprise Security Manager 10.3.x Release Notes Contents Installation information What's new in update 10.3.3 Resolved issues in update 10.3.3 Migrating from Flash to HTML Installation information
McAfee Enterprise Security Manager 10.3.x Release Notes Contents Installation information What's new in update 10.3.3 Resolved issues in update 10.3.3 Migrating from Flash to HTML Installation information
Top 10 use cases of HP ArcSight Logger
 Top 10 use cases of HP ArcSight Logger Sridhar Karnam @Sri747 Karnam@hp.com #HPSecure Big data is driving innovation The Big Data will continue to expand Collect Big Data for analytics Store Big Data for
Top 10 use cases of HP ArcSight Logger Sridhar Karnam @Sri747 Karnam@hp.com #HPSecure Big data is driving innovation The Big Data will continue to expand Collect Big Data for analytics Store Big Data for
Compare Security Analytics Solutions
 Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
Enterprise Security Biology
 Enterprise Security Biology Dissecting the Threat Intelligence Framework John Stoner Staff Security Architect US Public Sector and then some September 2017 Forward-Looking Statements During the course
Enterprise Security Biology Dissecting the Threat Intelligence Framework John Stoner Staff Security Architect US Public Sector and then some September 2017 Forward-Looking Statements During the course
Adobe Analytics Integration Customer Attributes Solution
 Adobe Analytics Integration Customer Attributes Solution This document explains the architecture of the Clicktale / Adobe Integration based on customer attributes and provides step-by-step details on how
Adobe Analytics Integration Customer Attributes Solution This document explains the architecture of the Clicktale / Adobe Integration based on customer attributes and provides step-by-step details on how
REST access to ESM Web Services
 REST access to ESM Web Services Dmitry Udalov, Sr. Software Engineer #HPProtect Forward-looking statements This is a rolling (up to three year) Roadmap and is subject to change without notice. This document
REST access to ESM Web Services Dmitry Udalov, Sr. Software Engineer #HPProtect Forward-looking statements This is a rolling (up to three year) Roadmap and is subject to change without notice. This document
ThreatScape App for QRadar: Overview, Installation and Configuration
 ThreatScape App for QRadar: Overview, Installation and Configuration December 16, 2015 App Description... 3 System Requirements... 3 ThreatScape App for QRadar Installation and Configuration... 3 Configuration...
ThreatScape App for QRadar: Overview, Installation and Configuration December 16, 2015 App Description... 3 System Requirements... 3 ThreatScape App for QRadar Installation and Configuration... 3 Configuration...
Fighting Phishing I: Get phish or die tryin.
 Fighting Phishing I: Get phish or die tryin. Micah Nelson and Max Hyppolite bit.ly/nercomp_sap918 Please, don t forget to submit your feedback for today s session at the above URL. If you use social media
Fighting Phishing I: Get phish or die tryin. Micah Nelson and Max Hyppolite bit.ly/nercomp_sap918 Please, don t forget to submit your feedback for today s session at the above URL. If you use social media
NGFW Security Management Center
 NGFW Security Management Center Release Notes 6.2.4 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5
NGFW Security Management Center Release Notes 6.2.4 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5
Cisco Threat Intelligence Director (TID)
 The topics in this chapter describe how to configure and use TID in the Firepower System. Overview, page 1 Using TID Sources to Ingest Feed Data, page 6 Using Access Control to Publish TID Data and Generate
The topics in this chapter describe how to configure and use TID in the Firepower System. Overview, page 1 Using TID Sources to Ingest Feed Data, page 6 Using Access Control to Publish TID Data and Generate
Reduce security analysis time from hours to minutes by enriching your events Amit Khandekar, Sr. Solution Architect
 Reduce security analysis time from hours to minutes by enriching your events Amit Khandekar, Sr. Solution Architect #HPProtect Security incident analysis flow and data required Incident analysis overview
Reduce security analysis time from hours to minutes by enriching your events Amit Khandekar, Sr. Solution Architect #HPProtect Security incident analysis flow and data required Incident analysis overview
Security, Internet Access, and Communication Ports
 Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Security Requirements Security Requirements, on
Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Security Requirements Security Requirements, on
Security, Internet Access, and Communication Ports
 Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: About Security, Internet Access, and Communication
Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: About Security, Internet Access, and Communication
Post-Exploitation Hunting with ATT&CK & Elastic
 Post-Exploitation Hunting with ATT&CK & Elastic John Hubbard @SecHubb SOC Lead at GlaxoSmithKline SANS Author & Instructor SEC455: SIEM Design & Implementation SEC511: Continuous Monitoring & Security
Post-Exploitation Hunting with ATT&CK & Elastic John Hubbard @SecHubb SOC Lead at GlaxoSmithKline SANS Author & Instructor SEC455: SIEM Design & Implementation SEC511: Continuous Monitoring & Security
HPE Security ArcSight Connectors
 HPE Security ArcSight Connectors SmartConnector for Barracuda Firewall NG F- Series Syslog Configuration Guide October 17, 2017 Configuration Guide SmartConnector for Barracuda Firewall NG F-Series Syslog
HPE Security ArcSight Connectors SmartConnector for Barracuda Firewall NG F- Series Syslog Configuration Guide October 17, 2017 Configuration Guide SmartConnector for Barracuda Firewall NG F-Series Syslog
<Partner Name> RSA NETWITNESS Intel Feeds Implementation Guide. Anomali STAXX 3.0. <Partner Product>
 RSA NETWITNESS Intel Feeds Implementation Guide Anomali Jeffrey Carlson, RSA Partner Engineering Last Modified: 09/28/2017 Solution Summary Anomali STAXX is a free client
RSA NETWITNESS Intel Feeds Implementation Guide Anomali Jeffrey Carlson, RSA Partner Engineering Last Modified: 09/28/2017 Solution Summary Anomali STAXX is a free client
Eyes Everywhere: Monitoring Today's Borderless Landscape
 SESSION ID: CMI1-R09 Eyes Everywhere: Monitoring Today's Borderless Landscape Bill Shinn Principal Security Architect Amazon Web Services @packet791 What we ll cover today Event & Finding Reference Architecture
SESSION ID: CMI1-R09 Eyes Everywhere: Monitoring Today's Borderless Landscape Bill Shinn Principal Security Architect Amazon Web Services @packet791 What we ll cover today Event & Finding Reference Architecture
End-to-End Security Analytics with the Elastic Stack. Samir Bennacer
 End-to-End Security Analytics with the Elastic Stack Samir Bennacer!1 !2 Attacks are inevitable Cybersecurity Maturity Curve Phase 1 Security Event Management Phase 2 Automation Phase 3 Proactive Analytics
End-to-End Security Analytics with the Elastic Stack Samir Bennacer!1 !2 Attacks are inevitable Cybersecurity Maturity Curve Phase 1 Security Event Management Phase 2 Automation Phase 3 Proactive Analytics
CYBER ANALYTICS. Architecture Overview. Technical Brief. May 2016 novetta.com 2016, Novetta
 CYBER ANALYTICS Architecture Overview Technical Brief May 2016 novetta.com 2016, Novetta Novetta Cyber Analytics: Technical Architecture Overview 1 INTRODUCTION 2 CAPTURE AND PROCESS ALL NETWORK TRAFFIC
CYBER ANALYTICS Architecture Overview Technical Brief May 2016 novetta.com 2016, Novetta Novetta Cyber Analytics: Technical Architecture Overview 1 INTRODUCTION 2 CAPTURE AND PROCESS ALL NETWORK TRAFFIC
Stonesoft Management Center. Release Notes Revision B
 Stonesoft Management Center Release Notes 6.1.0 Revision B Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
Stonesoft Management Center Release Notes 6.1.0 Revision B Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
McAfee Network Security Platform 8.3
 8.3.7.28-8.3.3.9 Manager-Mxx30-series Release Notes McAfee Network Security Platform 8.3 Revision C Contents About this release New features Enhancements Resolved issues Installation instructions Known
8.3.7.28-8.3.3.9 Manager-Mxx30-series Release Notes McAfee Network Security Platform 8.3 Revision C Contents About this release New features Enhancements Resolved issues Installation instructions Known
HPE Security ArcSight Connectors
 HPE Security ArcSight Connectors SmartConnector for Microsoft DHCP File Configuration Guide October 17, 2017 Configuration Guide SmartConnector for Microsoft DHCP File October 17, 2017 Copyright 2006 2017
HPE Security ArcSight Connectors SmartConnector for Microsoft DHCP File Configuration Guide October 17, 2017 Configuration Guide SmartConnector for Microsoft DHCP File October 17, 2017 Copyright 2006 2017
Monitoring the Device
 The system includes dashboards and an Event Viewer that you can use to monitor the device and traffic that is passing through the device. Enable Logging to Obtain Traffic Statistics, page 1 Monitoring
The system includes dashboards and an Event Viewer that you can use to monitor the device and traffic that is passing through the device. Enable Logging to Obtain Traffic Statistics, page 1 Monitoring
Data Onboarding. Where Do I begin? Luke Netto Senior Professional Services Splunk. September 26, 2017 Washington, DC
 Data Onboarding Where Do I begin? Luke Netto Senior Professional Services Consultant @ Splunk September 26, 2017 Washington, DC Forward-Looking Statements During the course of this presentation, we may
Data Onboarding Where Do I begin? Luke Netto Senior Professional Services Consultant @ Splunk September 26, 2017 Washington, DC Forward-Looking Statements During the course of this presentation, we may
McAfee Enterprise Security Manager
 Release Notes McAfee Enterprise Security Manager 10.0.2 Contents About this release New features Resolved issues Instructions for upgrading Find product documentation About this release This document contains
Release Notes McAfee Enterprise Security Manager 10.0.2 Contents About this release New features Resolved issues Instructions for upgrading Find product documentation About this release This document contains
The Interactive Guide to Protecting Your Election Website
 The Interactive Guide to Protecting Your Election Website 1 INTRODUCTION Cloudflare is on a mission to help build a better Internet. Cloudflare is one of the world s largest networks. Today, businesses,
The Interactive Guide to Protecting Your Election Website 1 INTRODUCTION Cloudflare is on a mission to help build a better Internet. Cloudflare is one of the world s largest networks. Today, businesses,
Imperva CounterBreach
 Imperva CounterBreach DATASHEET Protect Your Data from Insider Threats The greatest threat to enterprise security is the people already on the payroll. To do their jobs, employees, contractors, consultants
Imperva CounterBreach DATASHEET Protect Your Data from Insider Threats The greatest threat to enterprise security is the people already on the payroll. To do their jobs, employees, contractors, consultants
Stonesoft Management Center. Release Notes Revision A
 Stonesoft Management Center Release Notes 5.10.2 Revision A Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
Stonesoft Management Center Release Notes 5.10.2 Revision A Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
ForeScout CounterACT. Configuration Guide. Version 2.2
 ForeScout CounterACT Core Extensions Module: IOC Scanner Plugin Version 2.2 Table of Contents About the CounterACT IOC Scanner Plugin... 4 Use Cases... 5 Broaden the Scope and Capacity of Scanning Activities...
ForeScout CounterACT Core Extensions Module: IOC Scanner Plugin Version 2.2 Table of Contents About the CounterACT IOC Scanner Plugin... 4 Use Cases... 5 Broaden the Scope and Capacity of Scanning Activities...
Insight Frequently Asked Questions version 2.0 (8/24/2011)
 Insight Frequently Asked Questions version 2.0 (8/24/2011) Insight Overview 1. What is a reputation system and how does it work? Insight, our reputation system, leverages anonymous telemetry data from
Insight Frequently Asked Questions version 2.0 (8/24/2011) Insight Overview 1. What is a reputation system and how does it work? Insight, our reputation system, leverages anonymous telemetry data from
Security, Internet Access, and Communication Ports
 Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Overview: Security, Internet Access, and Communication
Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Overview: Security, Internet Access, and Communication
NetFlow Optimizer. Overview. Version (Build ) May 2017
 NetFlow Optimizer Overview Version 2.4.9 (Build 2.4.9.0.3) May 2017 Copyright 2013-2017 NetFlow Logic Corporation. All rights reserved. Patents both issued and pending. Contents About NetFlow Optimizer...
NetFlow Optimizer Overview Version 2.4.9 (Build 2.4.9.0.3) May 2017 Copyright 2013-2017 NetFlow Logic Corporation. All rights reserved. Patents both issued and pending. Contents About NetFlow Optimizer...
Cyberattack Analysis and Information Sharing in the U.S.
 Cyberattack Analysis and Information Sharing in the U.S. Promoting the sharing and utilization of the Analyzed Information Sean Barnum February 2013 Sponsored by the US Department of Homeland Security
Cyberattack Analysis and Information Sharing in the U.S. Promoting the sharing and utilization of the Analyzed Information Sean Barnum February 2013 Sponsored by the US Department of Homeland Security
Intelligent and Secure Network
 Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
Threat Centric Network Security
 BRKSEC-2056 Threat Centric Network Security Ted Bedwell, Principal Engineer Network Threat Defence Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this
BRKSEC-2056 Threat Centric Network Security Ted Bedwell, Principal Engineer Network Threat Defence Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
McAfee Advanced Threat Defense 3.4.4
 Release Notes McAfee Advanced Threat Defense 3.4.4 Revision B Contents About this release New Features Enhancements Resolved issues Installation and upgrade notes Known issues Product documentation About
Release Notes McAfee Advanced Threat Defense 3.4.4 Revision B Contents About this release New Features Enhancements Resolved issues Installation and upgrade notes Known issues Product documentation About
Stonesoft Management Center. Release Notes Revision B
 Stonesoft Management Center Release Notes 6.1.1 Revision B Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
Stonesoft Management Center Release Notes 6.1.1 Revision B Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
Qualys Cloud Platform
 18 QUALYS SECURITY CONFERENCE 2018 Qualys Cloud Platform Looking Under the Hood: What Makes Our Cloud Platform so Scalable and Powerful Dilip Bachwani Vice President, Engineering, Qualys, Inc. Cloud Platform
18 QUALYS SECURITY CONFERENCE 2018 Qualys Cloud Platform Looking Under the Hood: What Makes Our Cloud Platform so Scalable and Powerful Dilip Bachwani Vice President, Engineering, Qualys, Inc. Cloud Platform
Sharing is Caring: Improving Detection with Sigma
 SANS Tactical Detection and Data Analytics Summit 2018 Sharing is Caring: Improving Detection with Sigma John Hubbard (@SecHubb) The Blue Team's Journey Sharing is Caring - John Hubbard @SecHubb 2 Blue
SANS Tactical Detection and Data Analytics Summit 2018 Sharing is Caring: Improving Detection with Sigma John Hubbard (@SecHubb) The Blue Team's Journey Sharing is Caring - John Hubbard @SecHubb 2 Blue
DomainTools for Splunk
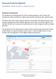 DomainTools for Splunk Installation Guide version 2.0 January 2018 Solution Overview The DomainTools Technology Add-On (TA) for Splunk populates a whois index with DomainTools Whois and Risk Score data
DomainTools for Splunk Installation Guide version 2.0 January 2018 Solution Overview The DomainTools Technology Add-On (TA) for Splunk populates a whois index with DomainTools Whois and Risk Score data
Features and Functionality
 Features and functionality introduced in previous versions may be superseded by new features and functionality in later versions. New or Changed Functionality in Version 6.2.2.x, page 1 Features Introduced
Features and functionality introduced in previous versions may be superseded by new features and functionality in later versions. New or Changed Functionality in Version 6.2.2.x, page 1 Features Introduced
SOC AUTOMATION OF THREAT INVESTIGATION
 SOC AUTOMATION OF THREAT INVESTIGATION White Paper When a Security Operations Center (SOC) is shown on TV, it has a specific portrayal. There is a large wall full of screens. World maps showing the threat
SOC AUTOMATION OF THREAT INVESTIGATION White Paper When a Security Operations Center (SOC) is shown on TV, it has a specific portrayal. There is a large wall full of screens. World maps showing the threat
IBM QRadar User Behavior Analytics (UBA) app Version 2 Release 5. User Guide IBM
 IBM QRadar User Behavior Analytics (UBA) app Version 2 Release 5 User Guide IBM Note Before you use this information and the product that it supports, read the information in Notices on page 111. Product
IBM QRadar User Behavior Analytics (UBA) app Version 2 Release 5 User Guide IBM Note Before you use this information and the product that it supports, read the information in Notices on page 111. Product
Avoiding Information Overload: Automated Data Processing with n6
 Avoiding Information Overload: Automated Data Processing with n6 Paweł Pawliński pawel.pawlinski@cert.pl 26th annual FIRST conference Boston, June 23rd 2014 Who we are part of national CERT for Poland
Avoiding Information Overload: Automated Data Processing with n6 Paweł Pawliński pawel.pawlinski@cert.pl 26th annual FIRST conference Boston, June 23rd 2014 Who we are part of national CERT for Poland
All about actors in HP ArcSight ESM Anurag Singla Sr. Manager, Software Development Sep 2012
 All about actors in HP ArcSight ESM Anurag Singla Sr. Manager, Software Development Sep 2012 Forward-looking statements This is a rolling (up to three year) Roadmap and is subject to change without notice.
All about actors in HP ArcSight ESM Anurag Singla Sr. Manager, Software Development Sep 2012 Forward-looking statements This is a rolling (up to three year) Roadmap and is subject to change without notice.
RSA ECAT DETECT, ANALYZE, RESPOND!
 RSA ECAT DETECT, ANALYZE, RESPOND! Cyber Threat Landscape Attack surface (& attackers) expanding Web app Existing strategies & controls are failing Laptop EHR Firewall Attacks sophistication on the rise
RSA ECAT DETECT, ANALYZE, RESPOND! Cyber Threat Landscape Attack surface (& attackers) expanding Web app Existing strategies & controls are failing Laptop EHR Firewall Attacks sophistication on the rise
HPE Security ArcSight Connectors
 HPE Security ArcSight Connectors SmartConnector for HPE c7000 Virtual Connect Module Syslog Configuration Guide October 17, 2017 SmartConnector for HPE c7000 Virtual Connect Module Syslog October 17, 2017
HPE Security ArcSight Connectors SmartConnector for HPE c7000 Virtual Connect Module Syslog Configuration Guide October 17, 2017 SmartConnector for HPE c7000 Virtual Connect Module Syslog October 17, 2017
TAXII 1.0 (DRAFT) Capabilities and Services. Charles Schmidt & Mark Davidson
 TAXII 1.0 (DRAFT) Capabilities and Services Charles Schmidt & Mark Davidson 2 About This Talk Look at the use scenarios we want to support and how we have designed TAXII to support them TAXII supports
TAXII 1.0 (DRAFT) Capabilities and Services Charles Schmidt & Mark Davidson 2 About This Talk Look at the use scenarios we want to support and how we have designed TAXII to support them TAXII supports
Bring Context To Your Machine Data With Hadoop, RDBMS & Splunk
 Bring Context To Your Machine Data With Hadoop, RDBMS & Splunk Raanan Dagan and Rohit Pujari September 25, 2017 Washington, DC Forward-Looking Statements During the course of this presentation, we may
Bring Context To Your Machine Data With Hadoop, RDBMS & Splunk Raanan Dagan and Rohit Pujari September 25, 2017 Washington, DC Forward-Looking Statements During the course of this presentation, we may
NGFW Security Management Center
 NGFW Security Management Center Release Notes 6.3.4 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 5 New features on page 5
NGFW Security Management Center Release Notes 6.3.4 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 5 New features on page 5
Infoblox Dossier User Guide
 Infoblox Dossier User Guide 2017 Infoblox Inc. All rights reserved. ActiveTrust Platform Dossier and TIDE - June 2017 Page 1 of 16 1. Overview of Dossier... 3 2. Prerequisites... 3 3. Access to the Dossier
Infoblox Dossier User Guide 2017 Infoblox Inc. All rights reserved. ActiveTrust Platform Dossier and TIDE - June 2017 Page 1 of 16 1. Overview of Dossier... 3 2. Prerequisites... 3 3. Access to the Dossier
Cisco Threat Intelligence Director (TID)
 The topics in this chapter describe how to configure and use TID in the Firepower System. Overview, page 1 Requirements for Threat Intelligence Director, page 4 How To Set Up, page 6 Analyze TID Incident
The topics in this chapter describe how to configure and use TID in the Firepower System. Overview, page 1 Requirements for Threat Intelligence Director, page 4 How To Set Up, page 6 Analyze TID Incident
HPE Security ArcSight Connectors
 HPE Security ArcSight Connectors SmartConnector for Microsoft System Center Configuration Manager DB Configuration Guide October 17, 2017 SmartConnector for Microsoft System Center Configuration Manager
HPE Security ArcSight Connectors SmartConnector for Microsoft System Center Configuration Manager DB Configuration Guide October 17, 2017 SmartConnector for Microsoft System Center Configuration Manager
GFI Product Comparison. GFI WebMonitor 2015 vs. McAfee Web Gateway
 GFI Product Comparison GFI WebMonitor 2015 vs. McAfee Web Gateway Features GFI WebMonitor 2015 McAfee Web Gateway General features Platforms Windows servers and workstation OS Standalone proxy Win 7, 8,
GFI Product Comparison GFI WebMonitor 2015 vs. McAfee Web Gateway Features GFI WebMonitor 2015 McAfee Web Gateway General features Platforms Windows servers and workstation OS Standalone proxy Win 7, 8,
HPE Security ArcSight Reputation Security Monitor Plus (RepSM Plus)
 HPE Security ArcSight Reputation Plus (RepSM Plus) Software Version: 1.6 RepSM Plus Solution Guide February 6, 2017 Legal Notices Warranty The only warranties for Hewlett Packard Enterprise products and
HPE Security ArcSight Reputation Plus (RepSM Plus) Software Version: 1.6 RepSM Plus Solution Guide February 6, 2017 Legal Notices Warranty The only warranties for Hewlett Packard Enterprise products and
An Aflac Case Study: Moving a Security Program from Defense to Offense
 SESSION ID: CXO-W11 An Aflac Case Study: Moving a Security Program from Defense to Offense Tim Callahan SVP & Global CISO Aflac Threat Landscape Selected losses > 30,000 records (updated 10/15/16) Security
SESSION ID: CXO-W11 An Aflac Case Study: Moving a Security Program from Defense to Offense Tim Callahan SVP & Global CISO Aflac Threat Landscape Selected losses > 30,000 records (updated 10/15/16) Security
ArcGIS for Intelligence: Discern Activities of Interest Through Advanced Analysis. Natalie Feuerstein Ben Conklin Lyle Wright
 ArcGIS for Intelligence: Discern Activities of Interest Through Advanced Analysis Natalie Feuerstein Ben Conklin Lyle Wright Challenges Demo Movement Pattern Dashboard Key Concepts New Analytic Workflow
ArcGIS for Intelligence: Discern Activities of Interest Through Advanced Analysis Natalie Feuerstein Ben Conklin Lyle Wright Challenges Demo Movement Pattern Dashboard Key Concepts New Analytic Workflow
NGFW Security Management Center
 NGFW Security Management Center Release Notes 6.4.5 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5
NGFW Security Management Center Release Notes 6.4.5 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5
Stonesoft Management Center. Release Notes Revision A
 Stonesoft Management Center Release Notes 6.1.3 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5 Enhancements
Stonesoft Management Center Release Notes 6.1.3 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5 Enhancements
Configuring the Management Access List
 The following topics explain how to configure the various system settings that are grouped together on the page. The settings cover overall system function. Configuring the Management Access List, page
The following topics explain how to configure the various system settings that are grouped together on the page. The settings cover overall system function. Configuring the Management Access List, page
SOLUTION BRIEF. RiskSense Platform. RiskSense Platform the industry s most comprehensive, intelligent platform for managing cyber risk.
 RiskSense Platform RiskSense Platform the industry s most comprehensive, intelligent platform for managing cyber risk. 27 RiskSense, Inc. Executive Summary The RiskSense Platform is a Software-as-a-Service
RiskSense Platform RiskSense Platform the industry s most comprehensive, intelligent platform for managing cyber risk. 27 RiskSense, Inc. Executive Summary The RiskSense Platform is a Software-as-a-Service
Enterprise Data Catalog for Microsoft Azure Tutorial
 Enterprise Data Catalog for Microsoft Azure Tutorial VERSION 10.2 JANUARY 2018 Page 1 of 45 Contents Tutorial Objectives... 4 Enterprise Data Catalog Overview... 5 Overview... 5 Objectives... 5 Enterprise
Enterprise Data Catalog for Microsoft Azure Tutorial VERSION 10.2 JANUARY 2018 Page 1 of 45 Contents Tutorial Objectives... 4 Enterprise Data Catalog Overview... 5 Overview... 5 Objectives... 5 Enterprise
Winning on Windows with a WiNC and a smile
 Winning on Windows with a WiNC and a smile Vianney Boncorps Nanjoo Ban Forward-looking statements This is a rolling (up to three year) Roadmap and is subject to change without notice. This document contains
Winning on Windows with a WiNC and a smile Vianney Boncorps Nanjoo Ban Forward-looking statements This is a rolling (up to three year) Roadmap and is subject to change without notice. This document contains
Forescout. eyeextend for Palo Alto Networks Wildfire. Configuration Guide. Version 2.2
 Forescout Version 2.2 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 2.2 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Azure Security Center
 Azure Security Center Security Center Playbook: Linux Detections Version 1.0 Prepared by Yuri Diogenes Senior Program Manager Microsoft C+AI Security CxE @yuridiogenes Reviewed by Ram Pliskin, Senior Program
Azure Security Center Security Center Playbook: Linux Detections Version 1.0 Prepared by Yuri Diogenes Senior Program Manager Microsoft C+AI Security CxE @yuridiogenes Reviewed by Ram Pliskin, Senior Program
Deep Security Integration with Sumo Logic
 A Trend Micro White Paper I May 2016 Install, Integrate and Analyze» This paper is aimed at information security and solution architects looking to integrate the Trend Micro Deep Security with Sumo Logic.
A Trend Micro White Paper I May 2016 Install, Integrate and Analyze» This paper is aimed at information security and solution architects looking to integrate the Trend Micro Deep Security with Sumo Logic.
Forescout. Configuration Guide. Version 3.5
 Forescout Version 3.5 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 3.5 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Update on new Microsoft Cloud Technology
 Update on new Microsoft Cloud Technology Advanced Threat Protection Thomas Collier Technical Pre-Sales OFFICE 365 PHISH PROTECTION STACK Protect during Mail Flow Protect Post Delivery Detect & Respond
Update on new Microsoft Cloud Technology Advanced Threat Protection Thomas Collier Technical Pre-Sales OFFICE 365 PHISH PROTECTION STACK Protect during Mail Flow Protect Post Delivery Detect & Respond
NGFW Security Management Center
 NGFW Security Management Center Release Notes 6.4.4 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 5 New features on page 5
NGFW Security Management Center Release Notes 6.4.4 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 5 New features on page 5
QuickSpecs. Aruba IntroSpect User and Entity Behavior Analytics. Overview. Aruba IntroSpect User and Entity Behavior Analytics Product overview
 Overview Product overview Aruba s User and Entity Behavior Analytics (UEBA) solution, Aruba IntroSpect, detects attacks by spotting small changes in behavior that are often indicative of attacks that have
Overview Product overview Aruba s User and Entity Behavior Analytics (UEBA) solution, Aruba IntroSpect, detects attacks by spotting small changes in behavior that are often indicative of attacks that have
KASPERSKY FRAUD PREVENTION FOR ENDPOINTS
 KASPERSKY FRAUD PREVENTION FOR ENDPOINTS www.kaspersky.com KASPERSKY FRAUD PREVENTION 1. Ways of Attacking Online Banking The prime motive behind cybercrime is making money and today s sophisticated criminal
KASPERSKY FRAUD PREVENTION FOR ENDPOINTS www.kaspersky.com KASPERSKY FRAUD PREVENTION 1. Ways of Attacking Online Banking The prime motive behind cybercrime is making money and today s sophisticated criminal
BlackBerry Enterprise Server for Microsoft Office 365. Version: 1.0. Administration Guide
 BlackBerry Enterprise Server for Microsoft Office 365 Version: 1.0 Administration Guide Published: 2013-01-29 SWD-20130131125552322 Contents 1 Related resources... 18 2 About BlackBerry Enterprise Server
BlackBerry Enterprise Server for Microsoft Office 365 Version: 1.0 Administration Guide Published: 2013-01-29 SWD-20130131125552322 Contents 1 Related resources... 18 2 About BlackBerry Enterprise Server
ActiveTrust Cloud Threats API
 QUICK START GUIDE ActiveTrust Cloud Threats API March 2018 2018 Infoblox Inc. All rights reserved. ActiveTrust Cloud Threats API Quick Start Guide March 2018 Page 1 of 19 Contents Overview... 3 Prerequisites...
QUICK START GUIDE ActiveTrust Cloud Threats API March 2018 2018 Infoblox Inc. All rights reserved. ActiveTrust Cloud Threats API Quick Start Guide March 2018 Page 1 of 19 Contents Overview... 3 Prerequisites...
Secure web proxy resistant to probing attacks
 Technical Disclosure Commons Defensive Publications Series December 04, 2017 Secure web proxy resistant to probing attacks Benjamin Schwartz Follow this and additional works at: http://www.tdcommons.org/dpubs_series
Technical Disclosure Commons Defensive Publications Series December 04, 2017 Secure web proxy resistant to probing attacks Benjamin Schwartz Follow this and additional works at: http://www.tdcommons.org/dpubs_series
NGFW Security Management Center
 NGFW Security Management Center Release Notes 6.3.7 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 5 New features on page 5
NGFW Security Management Center Release Notes 6.3.7 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 5 New features on page 5
NGFW Security Management Center
 NGFW Security Management Center Release Notes 6.4.1 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5
NGFW Security Management Center Release Notes 6.4.1 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5
Keeping your HP ArcSight connectors healthy
 Keeping your HP ArcSight connectors healthy Tracy Barella Chief Services Strategist HP ArcSight Connector Health Agenda What is a Health? Health steps by ArcSight component Connectors Connector Appliances
Keeping your HP ArcSight connectors healthy Tracy Barella Chief Services Strategist HP ArcSight Connector Health Agenda What is a Health? Health steps by ArcSight component Connectors Connector Appliances
NGFW Security Management Center
 NGFW Security Management Center Release Notes 6.4.0 Revision B Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5
NGFW Security Management Center Release Notes 6.4.0 Revision B Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5
McAfee Network Security Platform 8.3
 8.3.7.44-8.3.7.14 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known
8.3.7.44-8.3.7.14 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known
