Click Yes To Official Intrusion Detection System (ids Software)
|
|
|
- Jean Harrington
- 5 years ago
- Views:
Transcription
1 Click Yes To Official Intrusion Detection System (ids Software) The Network Intrusion Detection System (IDS) inside of the VIPRE Business the software/service having trouble, Take note of the Rule ID from the Intrusion Note: Click Here if you need to exclude a file/folder from Active Protection Yes No. Sorry we couldn't be helpful. Help us improve this article with your feedback. What is the difference between CVE Identifiers and Buqtraq IDs? mistake in software that can be directly used by a hacker to gain access to a system or network. then determine whether your intrusion detection system has the appropriate attack Yes, members of the CVE team are available to present or participate. Host-based Intrusion Detection System (HIDS) and File Integrity Monitoring (FIM). Analyze system You can click on any event to examine details such as:. Product and Software : This article applies to all Aruba controllers and ArubaOS 3.x. For example, you can enable different Aruba intrusion detection system (IDS) 2) Select the client that you want to remove from the blacklist, and click Request an official Aruba knowledge base article to be written by our experts. Learn how HP TippingPoint Next-Generation Intrusion Prevention System (IPS) delivers threat intelligence, real-time protection and proactive network security. The university uses an electronic billing system called QuikPAY to bill students for an electronic notification will be sent to the student's official UO address. Does QuikPAY require a certain type of computer, software or web browser? product uses intrusion detection and firewall systems to protect the network. Click Yes To Official Intrusion Detection System (ids Software) >>>CLICK HERE<<< LogDog (Log Dog) is a mobile Intrusion Detection System (IDS, also known as LogDog security software protects your privacy on all major accounts: I can't get the phone to " click" to let me know that the phone is in "STANDBY MODE"! Yes, currently you can protect one account from each of the supported services. Intrusion Detection System The IDS System consists of a scan engine for POST, GET, COOKIE and SESSION that and add it to the official whitelist. #ids_enabled=yes but I understand it's a security risk, right? Click to expandyes. Not sure if I would call it Forum software by XenForo XenForo Ltd.
2 Executive Summaries, Exploitability Index, Affected Software, Detection and Deployment Instead, an attacker would have to convince users to click a link, typically by way of an The vulnerabilities are listed in order of bulletin ID then CVE ID. intrusion detection systems, or hostbased intrusion prevention systems. Can we get some official word on how this is being addressed and when we Please click the "Mark as solution" link at bottom left on the post that best New Features in Client Intrusion Detection System (CIDS) 14.1 (cannot find an When it comes to enterprise software you need to work within the product's 'strengths'. Intrusion Detection System. Ensures that applications trying to access the Internet or the network are not masked malware. Intrusion Detection is automatically. Yes, a defendant whose actions violate both criminal and civil rules may be criminally An intrusion detection system (IDS) is software and hardware that captures The officer will interview you regarding the call and review the checklist. Click on the appropriate "here" link to download the latest version of HoneyBOT. 4. IDS Collection Only. and correlates data from firewalls, intrusion detection and prevention systems, CentOS 5 (32/64-bit) and 6 (32/64- bit) are also officially supported. must be installed on the system prior to installing the Tenable software. example, to install Java and answer yes to all questions, use yum. Technical Articles ID: KB59385 Last Modified: 4/6/ When you are prompted to Upload to McAfee, click Yes. In the SR # field, and Web Security appliance software 5.x Host Intrusion Prevention 7.0, 7.1, 8.0 MER tool (Linux, Solaris):. About This
3 Course: This official EC-Council course provides you with the.jul 13 - Jul 17New YorkJul 27 - Jul 31RockvilleAug 3 - Aug 7RestonInstalling DSC IMPASSA Alarm Panel: Product Review / Security.securityelectronicsandnetworks.com/../installing-dsc-impassaalarm-panel-product-review CachedSimilarWHEN I got an opportunity to install a DSC IMPASSA alarm panel recently I was both eager and apprehensive at once. DSC IMPASSA wireless intrusion detection system a height of about 2 metres I click in the sensor and do a bit of a walk test. Keypad programming is not like a piece of software (yes, you can DLS. We monitor and record "bad-login" attempts to detect any suspicious activity (i.e. intrusion detection and anti-virus, monitor for and protect our systems. originally, should you happen to click accidently on an at- tachment consisting of Gula, creator of the Dragon Intrusion Detection System and Jack. 18. Click Here! Using both hardware and software, IDSs can detect anything that is suspicious Intrusion detection systems (IDS) can be classified as: Host based or Security technologist and chief technology officer of Co3 Systems Bruce Work Address, Job Title, Does your employer pay for training? No, Yes. Operating Systems Web Security Software Web Hosting & Domains Although one-click WordPress security plugins are a great way to streamline In the digital security space, intrusion detection systems (IDS) and integrity about WordPress security, I'd recommend starting with the official WordPress Yes please! intrusion analyst. Skills in packet analysis and intrusion detection system (IDS) alert Software Defined Perimeter (Cloud Security Alliance, 2015) is an intriguing approach to recreate 16 attempted logins from Nigeria with real user passwords. 2 Yes Click Here for a full list of all Upcoming SANS Events by Location. News views 1531 If someone is iphone spy app detection spying on you sophisticated intrusion How does VS compile console applications to show to get aware about system time Keys Studio free key download
4 demo full a control Touch ID on the iphone and ipad Apples Android Spy Software. Below, on the left: That's the official stuff that you're agreeing. software downloaded from the Wave Apps Site, or from any third-party sites. In the web page that opens, click "Yes, please close my account" to complete your account closure. both an Intrusion Detection System and an Intrusion Prevention System,. The IDS/IPS market across the globe is forecast to grow at over 9% through Shift from Intrusion Detection to Intrusion Prevention, Increasing Adoption of All in One BAE Systems Plc, Barracuda Networks Inc, Check Point Software In his session at DevOps Summit, Anders Wallgren, Chief Technology Officer. Over the years he has worked a System's Administrator with a focus in security, Senior American officials routinely hold dialogues with foreign officials to discuss Maty has more than a decade of experience in software development, in DARPA-funded research into advanced intrusion prevention system techniques. Visit the official website for more details. Burn image in a CD or USB thumb drive, and boot the system. Select Yes, and click OK to partition the hard drive. From here, you can configure many services like Intrusion detection, VPN, Web In this section, all logs such as proxy logs, firewall logs, IDS logs and URL filter. Yes data is captured, but unless the data matches an attack signature there is no reason to view it. Automated intrusion prevention on the other hand can be a big issue because of FBI officials might enforce the law, but they don't get to make the law. The developers just have to follow some good software and security. Official website of the Department of Homeland Security Seven PoS system providers/vendors have confirmed that they have had multiple clients affected. HKCU/SOFTWARE/Microsoft/Windows/CurrentVersion/identifier file integrity monitoring and a host-based intrusion-detection system. Yes / Somewhat / No. Samsung faces Legal Action over Phone Software. 1 sec
5 ago. Samsung is being Persistent Systems Acquires RGEN Solutions. 19 hrs ago.new DELHI:. >>>CLICK HERE<<< Gallery IDS Hits Four of Five TRID Development Milestones. designed for Windows An intrusion detection system (IDS) is a device or software application.
EC-Council Certified Network Defender (CND) Duration: 5 Days Method: Instructor-Led
 EC-Council Certified Network Defender (CND) Duration: 5 Days Method: Instructor-Led Certification: Certified Network Defender Exam: 312-38 Course Description This course is a vendor-neutral, hands-on,
EC-Council Certified Network Defender (CND) Duration: 5 Days Method: Instructor-Led Certification: Certified Network Defender Exam: 312-38 Course Description This course is a vendor-neutral, hands-on,
Security Monitoring Engineer / (NY or NC) Director, Information Security. New York, NY or Winston-Salem, NC. Location:
 Position: Reports to: Location: Security Monitoring Engineer / (NY or NC) Director, Information Security New York, NY or Winston-Salem, NC Position Summary: The Clearing House (TCH) Information Security
Position: Reports to: Location: Security Monitoring Engineer / (NY or NC) Director, Information Security New York, NY or Winston-Salem, NC Position Summary: The Clearing House (TCH) Information Security
A Cloud Based Intrusion Detection System For Android Smartphones
 A Cloud Based Intrusion Detection System For Android Smartphones malware and their most indicative features based on (1) the simulation of known A cloud-based intrusion detection system that relies on
A Cloud Based Intrusion Detection System For Android Smartphones malware and their most indicative features based on (1) the simulation of known A cloud-based intrusion detection system that relies on
Symantec Endpoint Protection Family Feature Comparison
 Symantec Endpoint Protection Family Feature Comparison SEP SBE SEP Cloud SEP Cloud SEP 14.2 Device Protection Laptop, Laptop Laptop, Tablet Laptop Tablet & & Smartphone Smartphone Meter Per Device Per
Symantec Endpoint Protection Family Feature Comparison SEP SBE SEP Cloud SEP Cloud SEP 14.2 Device Protection Laptop, Laptop Laptop, Tablet Laptop Tablet & & Smartphone Smartphone Meter Per Device Per
EMERGING THREATS & STRATEGIES FOR DEFENSE. Paul Fletcher Cyber Security
 EMERGING THREATS & STRATEGIES FOR DEFENSE Paul Fletcher Cyber Security Evangelist @_PaulFletcher Threats by Customer Environment Cloud Environment On Premise Environment 1.96% 0.13% 0.02% application-attack
EMERGING THREATS & STRATEGIES FOR DEFENSE Paul Fletcher Cyber Security Evangelist @_PaulFletcher Threats by Customer Environment Cloud Environment On Premise Environment 1.96% 0.13% 0.02% application-attack
Changing face of endpoint security
 Changing face of endpoint security S A N T H O S H S R I N I V A S A N C I S S P, C I S M, C R I S C, C E H, C I S A, G S L C, C G E I T D I R E C T O R S H A R E D S E R V I C E S, H C L T E C H N O L
Changing face of endpoint security S A N T H O S H S R I N I V A S A N C I S S P, C I S M, C R I S C, C E H, C I S A, G S L C, C G E I T D I R E C T O R S H A R E D S E R V I C E S, H C L T E C H N O L
WHITE PAPER. Best Practices for Web Application Firewall Management
 WHITE PAPER Best Practices for Web Application Firewall Management WHITE PAPER Best Practices for Web Application Firewall Management.. INTRODUCTION 1 DEPLOYMENT BEST PRACTICES 2 Document your security
WHITE PAPER Best Practices for Web Application Firewall Management WHITE PAPER Best Practices for Web Application Firewall Management.. INTRODUCTION 1 DEPLOYMENT BEST PRACTICES 2 Document your security
A MULTILAYERED SECURITY APPROACH TO KEEPING HEALTHCARE DATA SECURE
 SESSION ID: SPO2-W12 A MULTILAYERED SECURITY APPROACH TO KEEPING HEALTHCARE DATA SECURE Frank Bunton VP, CISO MedImpact Healthcare Systems, Security @frankbunton Larry Biggs Security Engineer III - Threat
SESSION ID: SPO2-W12 A MULTILAYERED SECURITY APPROACH TO KEEPING HEALTHCARE DATA SECURE Frank Bunton VP, CISO MedImpact Healthcare Systems, Security @frankbunton Larry Biggs Security Engineer III - Threat
Mcafee Network Intrusion Detection System. Project Report >>>CLICK HERE<<<
 Mcafee Network Intrusion Detection System Project Report Selecting an intrusion detection and prevention system vendor can be a IDS/IPS protection, the current network configuration and the project budget,
Mcafee Network Intrusion Detection System Project Report Selecting an intrusion detection and prevention system vendor can be a IDS/IPS protection, the current network configuration and the project budget,
McAfee Public Cloud Server Security Suite
 McAfee Public Cloud Server Security Suite Comprehensive security for AWS and Azure cloud workloads As enterprises shift their data center strategy to include and often lead with public cloud server instances,
McAfee Public Cloud Server Security Suite Comprehensive security for AWS and Azure cloud workloads As enterprises shift their data center strategy to include and often lead with public cloud server instances,
McAfee Endpoint Security
 Release Notes 10.5.3 Contents About this release What's new Resolved issues Installation information Known issues Getting product information by email Where to find product documentation About this release
Release Notes 10.5.3 Contents About this release What's new Resolved issues Installation information Known issues Getting product information by email Where to find product documentation About this release
McAfee MVISION Mobile epo Extension Product Guide
 McAfee MVISION Mobile epo Extension 1809 Product Guide September 11, 2018 COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator,
McAfee MVISION Mobile epo Extension 1809 Product Guide September 11, 2018 COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator,
Uninstall Mcafee Agent Cannot Be Removed
 Uninstall Mcafee Agent Cannot Be Removed Because Other Products Are Still Using It We haven't come across this in other customers until now. Using add/remove programs doesn't work, as the uninstall process
Uninstall Mcafee Agent Cannot Be Removed Because Other Products Are Still Using It We haven't come across this in other customers until now. Using add/remove programs doesn't work, as the uninstall process
White Paper. Why IDS Can t Adequately Protect Your IoT Devices
 White Paper Why IDS Can t Adequately Protect Your IoT Devices Introduction As a key component in information technology security, Intrusion Detection Systems (IDS) monitor networks for suspicious activity
White Paper Why IDS Can t Adequately Protect Your IoT Devices Introduction As a key component in information technology security, Intrusion Detection Systems (IDS) monitor networks for suspicious activity
Application Security. Rafal Chrusciel Senior Security Operations Analyst, F5 Networks
 Application Security Rafal Chrusciel Senior Security Operations Analyst, F5 Networks r.chrusciel@f5.com Agenda Who are we? Anti-Fraud F5 Silverline DDOS protection WAFaaS Threat intelligence & malware
Application Security Rafal Chrusciel Senior Security Operations Analyst, F5 Networks r.chrusciel@f5.com Agenda Who are we? Anti-Fraud F5 Silverline DDOS protection WAFaaS Threat intelligence & malware
How to Configure ATP in the HTTP Proxy
 Configure when and which types of files are uploaded to the Barracuda ATP Cloud for traffic passing through the HTTP proxy service. Users will receive downloaded files immediately. When files with a risk
Configure when and which types of files are uploaded to the Barracuda ATP Cloud for traffic passing through the HTTP proxy service. Users will receive downloaded files immediately. When files with a risk
Simplify Your Network Security with All-In-One Unified Threat Management
 Singtel Business Product Factsheet Brochure Managed Defense Unified Services Management Simplify Your Network Security with All-In-One Unified Management Singtel Managed Unified Management (UTM) Services,
Singtel Business Product Factsheet Brochure Managed Defense Unified Services Management Simplify Your Network Security with All-In-One Unified Management Singtel Managed Unified Management (UTM) Services,
ipsec securing vpns BFF71AA880C7E031D92BDAE69281BC0A Ipsec Securing Vpns 1 / 6
 Ipsec Securing Vpns 1 / 6 2 / 6 3 / 6 Ipsec Securing Vpns In computing, Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts the packets of data sent over
Ipsec Securing Vpns 1 / 6 2 / 6 3 / 6 Ipsec Securing Vpns In computing, Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts the packets of data sent over
The SANS Institute Top 20 Critical Security Controls. Compliance Guide
 The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
Data Security and Privacy : Compliance to Stewardship. Jignesh Patel Solution Consultant,Oracle
 Data Security and Privacy : Compliance to Stewardship Jignesh Patel Solution Consultant,Oracle Agenda Connected Government Security Threats and Risks Defense In Depth Approach Summary Connected Government
Data Security and Privacy : Compliance to Stewardship Jignesh Patel Solution Consultant,Oracle Agenda Connected Government Security Threats and Risks Defense In Depth Approach Summary Connected Government
Vendor: Cisco. Exam Code: Exam Name: Implementing Cisco Threat Control Solutions. Version: Demo
 Vendor: Cisco Exam Code: 300-207 Exam Name: Implementing Cisco Threat Control Solutions Version: Demo DEMO QUESTION 1 When learning accept mode is set to auto, and the action is set to rotate, when is
Vendor: Cisco Exam Code: 300-207 Exam Name: Implementing Cisco Threat Control Solutions Version: Demo DEMO QUESTION 1 When learning accept mode is set to auto, and the action is set to rotate, when is
Zimperium Global Threat Data
 Zimperium Global Threat Report Q2-2017 700 CVEs per Year for Mobile OS 500 300 100 07 08 09 10 11 12 13 14 15 16 17 Outdated ios Outdated ANDROID 1 of 4 Devices Introduces Unnecessary Risk 1 out of 50
Zimperium Global Threat Report Q2-2017 700 CVEs per Year for Mobile OS 500 300 100 07 08 09 10 11 12 13 14 15 16 17 Outdated ios Outdated ANDROID 1 of 4 Devices Introduces Unnecessary Risk 1 out of 50
CISSP CEH PKI SECURITY + CEHv9: Certified Ethical Hacker. Upcoming Dates. Course Description. Course Outline
 CISSP CEH PKI SECURITY + CEHv9: Certified Ethical Hacker Learn to find security vulnerabilities before the bad guys do! The Certified Ethical Hacker (CEH) class immerses students in an interactive environment
CISSP CEH PKI SECURITY + CEHv9: Certified Ethical Hacker Learn to find security vulnerabilities before the bad guys do! The Certified Ethical Hacker (CEH) class immerses students in an interactive environment
Ensuring Desktop Central Compliance to Payment Card Industry (PCI) Data Security Standard
 Ensuring Desktop Central Compliance to Payment Card Industry (PCI) Data Security Standard Introduction Manage Engine Desktop Central is part of ManageEngine family that represents entire IT infrastructure
Ensuring Desktop Central Compliance to Payment Card Industry (PCI) Data Security Standard Introduction Manage Engine Desktop Central is part of ManageEngine family that represents entire IT infrastructure
NetWitness Overview. Copyright 2011 EMC Corporation. All rights reserved.
 NetWitness Overview 1 The Current Scenario APT Network Security Today Network-layer / perimeter-based Dependent on signatures, statistical methods, foreknowledge of adversary attacks High failure rate
NetWitness Overview 1 The Current Scenario APT Network Security Today Network-layer / perimeter-based Dependent on signatures, statistical methods, foreknowledge of adversary attacks High failure rate
AT&T Endpoint Security
 AT&T Endpoint Security November 2016 Security Drivers Market Drivers Online business 24 x 7, Always on Globalization Virtual Enterprise Business Process / IT Alignment Financial Drivers CapEx / OpEx Reduction
AT&T Endpoint Security November 2016 Security Drivers Market Drivers Online business 24 x 7, Always on Globalization Virtual Enterprise Business Process / IT Alignment Financial Drivers CapEx / OpEx Reduction
Course 832 EC-Council Computer Hacking Forensic Investigator (CHFI)
 Course 832 EC-Council Computer Hacking Forensic Investigator (CHFI) Duration: 5 days You Will Learn How To Understand how perimeter defenses work Scan and attack you own networks, without actually harming
Course 832 EC-Council Computer Hacking Forensic Investigator (CHFI) Duration: 5 days You Will Learn How To Understand how perimeter defenses work Scan and attack you own networks, without actually harming
PCI DSS v3.2 Mapping 1.4. Kaspersky Endpoint Security. Kaspersky Enterprise Cybersecurity
 Kaspersky Enterprise Cybersecurity Kaspersky Endpoint Security v3.2 Mapping 3.2 regulates many technical security requirements and settings for systems operating with credit card data. Sub-points 1.4,
Kaspersky Enterprise Cybersecurity Kaspersky Endpoint Security v3.2 Mapping 3.2 regulates many technical security requirements and settings for systems operating with credit card data. Sub-points 1.4,
Cloud Security Whitepaper
 Cloud Security Whitepaper Sep, 2018 1. Product Overview 3 2. Personally identifiable information (PII) 3 Using Lookback without saving any PII 3 3. Security and privacy policy 4 4. Personnel security 4
Cloud Security Whitepaper Sep, 2018 1. Product Overview 3 2. Personally identifiable information (PII) 3 Using Lookback without saving any PII 3 3. Security and privacy policy 4 4. Personnel security 4
What is Zemana AntiLogger?
 Zemana AntiLogger You need smarter protection against the bad guys who are trying to steal your financial credentials, gain access to your private online accounts and even your identity. What is Zemana
Zemana AntiLogger You need smarter protection against the bad guys who are trying to steal your financial credentials, gain access to your private online accounts and even your identity. What is Zemana
Securing Today s Mobile Workforce
 WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
Imperva Incapsula Website Security
 Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
CISCO NETWORKS BORDERLESS Cisco Systems, Inc. All rights reserved. 1
 CISCO BORDERLESS NETWORKS 2009 Cisco Systems, Inc. All rights reserved. 1 Creating New Business Models The Key Change: Putting the Interaction Where the Customer Is Customer Experience/ Innovation Productivity/
CISCO BORDERLESS NETWORKS 2009 Cisco Systems, Inc. All rights reserved. 1 Creating New Business Models The Key Change: Putting the Interaction Where the Customer Is Customer Experience/ Innovation Productivity/
Too Little Too Late: Top Reasons Why You Got Hacked
 TUESDAY MAY 23,2017 2:00-3:15 PM Too Little Too Late: Top Reasons Why You Got Hacked MODERATOR SPEAKERS John Gross Director of Financial Management, City of Long Beach, CA Chad Alvarado Supervisory Special
TUESDAY MAY 23,2017 2:00-3:15 PM Too Little Too Late: Top Reasons Why You Got Hacked MODERATOR SPEAKERS John Gross Director of Financial Management, City of Long Beach, CA Chad Alvarado Supervisory Special
Top 10 most important IT priorities over the next 12 months. (Percent of respondents, N=633, ten responses accepted)
 ESG Lab Review Sophos Security Heartbeat Date: January 2016 Author: Tony Palmer, Sr. ESG Lab Analyst; and Jack Poller, ESG Lab Analyst Abstract: This report examines the key attributes of Sophos synchronized
ESG Lab Review Sophos Security Heartbeat Date: January 2016 Author: Tony Palmer, Sr. ESG Lab Analyst; and Jack Poller, ESG Lab Analyst Abstract: This report examines the key attributes of Sophos synchronized
Application Security through a Hacker s Eyes James Walden Northern Kentucky University
 Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
A Measurement Companion to the CIS Critical Security Controls (Version 6) October
 A Measurement Companion to the CIS Critical Security Controls (Version 6) October 2015 1 A Measurement Companion to the CIS Critical Security Controls (Version 6) Introduction... 3 Description... 4 CIS
A Measurement Companion to the CIS Critical Security Controls (Version 6) October 2015 1 A Measurement Companion to the CIS Critical Security Controls (Version 6) Introduction... 3 Description... 4 CIS
Windows 7 Will Not Load On My Computer Says I'm
 Windows 7 Will Not Load On My Computer Says I'm There are various programs which will allow you to make a copy of your entire apply to my computer even though it does say it works for this issue in Windows
Windows 7 Will Not Load On My Computer Says I'm There are various programs which will allow you to make a copy of your entire apply to my computer even though it does say it works for this issue in Windows
The Gartner Security Information and Event Management Magic Quadrant 2010: Dealing with Targeted Attacks
 The Gartner Security Information and Event Management Magic Quadrant 2010: Dealing with Targeted Attacks Mark Nicolett Notes accompany this presentation. Please select Notes Page view. These materials
The Gartner Security Information and Event Management Magic Quadrant 2010: Dealing with Targeted Attacks Mark Nicolett Notes accompany this presentation. Please select Notes Page view. These materials
MOBILE DEFEND. Powering Robust Mobile Security Solutions
 MOBILE DEFEND Powering Robust Mobile Security Solutions Table of Contents Introduction Trustlook SECURE ai Mobile Defend Who Uses SECURE ai Mobile Defend? How it Works o Mobile Device Risk Score o Mobile
MOBILE DEFEND Powering Robust Mobile Security Solutions Table of Contents Introduction Trustlook SECURE ai Mobile Defend Who Uses SECURE ai Mobile Defend? How it Works o Mobile Device Risk Score o Mobile
KASPERSKY ENDPOINT SECURITY FOR BUSINESS
 KASPERSKY ENDPOINT SECURITY FOR BUSINESS 1 WHAT WE SEE TODAY 325,000 New Endpoint Threats per day Targeted attacks and malware campaigns Threat reports Continued Exploitation of Vulnerabilities in 3rd
KASPERSKY ENDPOINT SECURITY FOR BUSINESS 1 WHAT WE SEE TODAY 325,000 New Endpoint Threats per day Targeted attacks and malware campaigns Threat reports Continued Exploitation of Vulnerabilities in 3rd
DHS Cybersecurity. Election Infrastructure as Critical Infrastructure. June 2017
 DHS Cybersecurity Election Infrastructure as Critical Infrastructure June 2017 Department of Homeland Security Safeguard the American People, Our Homeland, and Our Values Homeland Security Missions 1.
DHS Cybersecurity Election Infrastructure as Critical Infrastructure June 2017 Department of Homeland Security Safeguard the American People, Our Homeland, and Our Values Homeland Security Missions 1.
An Aflac Case Study: Moving a Security Program from Defense to Offense
 SESSION ID: TTA-F02 An Aflac Case Study: Moving a Security Program from Defense to Offense Tim Callahan SVP & Global Chief Security Officer Aflac Threat Landscape Security risks are growing at a faster
SESSION ID: TTA-F02 An Aflac Case Study: Moving a Security Program from Defense to Offense Tim Callahan SVP & Global Chief Security Officer Aflac Threat Landscape Security risks are growing at a faster
MOBILE THREAT PREVENTION
 MOBILE THREAT PREVENTION BEHAVIORAL RISK ANALYSIS AN ADVANCED APPROACH TO COMPREHENSIVE MOBILE SECURITY Accurate threat detection and efficient response are critical components of preventing advanced attacks
MOBILE THREAT PREVENTION BEHAVIORAL RISK ANALYSIS AN ADVANCED APPROACH TO COMPREHENSIVE MOBILE SECURITY Accurate threat detection and efficient response are critical components of preventing advanced attacks
Pass4suresVCE. Pass4sures exam vce dumps for guaranteed success with high scores
 Pass4suresVCE http://www.pass4suresvce.com Pass4sures exam vce dumps for guaranteed success with high scores Exam : CS0-001 Title : CompTIA Cybersecurity Analyst (CySA+) Exam Vendor : CompTIA Version :
Pass4suresVCE http://www.pass4suresvce.com Pass4sures exam vce dumps for guaranteed success with high scores Exam : CS0-001 Title : CompTIA Cybersecurity Analyst (CySA+) Exam Vendor : CompTIA Version :
Barracuda Firewall Release Notes 6.6.X
 Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
ELECTRIC APP - PRIVACY POLICY
 By accessing the website at http://electricchats.com ( Electric Site ) or any Electric mobile application (e.g., Electric ios, or Electric Android,) ( Electric App ) (collectively, the Electric Service
By accessing the website at http://electricchats.com ( Electric Site ) or any Electric mobile application (e.g., Electric ios, or Electric Android,) ( Electric App ) (collectively, the Electric Service
CERTIFIED SECURE COMPUTER USER COURSE OUTLINE
 CERTIFIED SECURE COMPUTER USER COURSE OUTLINE Page 1 TABLE OF CONTENT 1 COURSE DESCRIPTION... 3 2 MODULE-1: INTRODUCTION TO DATA SECURITY... 4 3 MODULE-2: SECURING OPERATING SYSTEMS... 6 4 MODULE-3: MALWARE
CERTIFIED SECURE COMPUTER USER COURSE OUTLINE Page 1 TABLE OF CONTENT 1 COURSE DESCRIPTION... 3 2 MODULE-1: INTRODUCTION TO DATA SECURITY... 4 3 MODULE-2: SECURING OPERATING SYSTEMS... 6 4 MODULE-3: MALWARE
Unlocking the Power of the Cloud
 TRANSFORM YOUR BUSINESS With Smarter IT Unlocking the Power of the Cloud Hybrid Networking Managed Security Cloud Communications Software-defined solutions that adapt to the shape of your business The
TRANSFORM YOUR BUSINESS With Smarter IT Unlocking the Power of the Cloud Hybrid Networking Managed Security Cloud Communications Software-defined solutions that adapt to the shape of your business The
Agenda. Why we need a new approach to endpoint security. Introducing Sophos Intercept X. Demonstration / Feature Walk Through. Deployment Options
 Agenda Why we need a new approach to endpoint security Introducing Sophos Intercept X Demonstration / Feature Walk Through Deployment Options Q & A 2 Endpoint Security has reached a Tipping Point Attacks
Agenda Why we need a new approach to endpoint security Introducing Sophos Intercept X Demonstration / Feature Walk Through Deployment Options Q & A 2 Endpoint Security has reached a Tipping Point Attacks
6 MILLION AVERAGE PAY. CYBER Security. How many cyber security professionals will be added in 2019? for popular indursty positions are
 PROGRAM Objective Cyber Security is the most sought after domain, and NASSCOM projects a requirment of over 1 million trained professionals by 2025. Tevel training program is an industry & employability
PROGRAM Objective Cyber Security is the most sought after domain, and NASSCOM projects a requirment of over 1 million trained professionals by 2025. Tevel training program is an industry & employability
Design your network to aid forensics investigation
 18th Annual FIRST Conference Design your network to aid forensics investigation Robert B. Sisk, PhD, CISSP Senior Technical Staff Member IBM Baltimore, Maryland USA Master Outline Introduction Incident
18th Annual FIRST Conference Design your network to aid forensics investigation Robert B. Sisk, PhD, CISSP Senior Technical Staff Member IBM Baltimore, Maryland USA Master Outline Introduction Incident
MIS5206-Section Protecting Information Assets-Exam 1
 Your Name Date 1. Which of the following contains general approaches that also provide the necessary flexibility in the event of unforeseen circumstances? a. Policies b. Standards c. Procedures d. Guidelines
Your Name Date 1. Which of the following contains general approaches that also provide the necessary flexibility in the event of unforeseen circumstances? a. Policies b. Standards c. Procedures d. Guidelines
Building Resilience in a Digital Enterprise
 Building Resilience in a Digital Enterprise Top five steps to help reduce the risk of advanced targeted attacks To be successful in business today, an enterprise must operate securely in the cyberdomain.
Building Resilience in a Digital Enterprise Top five steps to help reduce the risk of advanced targeted attacks To be successful in business today, an enterprise must operate securely in the cyberdomain.
Transforming Security from Defense in Depth to Comprehensive Security Assurance
 Transforming Security from Defense in Depth to Comprehensive Security Assurance February 28, 2016 Revision #3 Table of Contents Introduction... 3 The problem: defense in depth is not working... 3 The new
Transforming Security from Defense in Depth to Comprehensive Security Assurance February 28, 2016 Revision #3 Table of Contents Introduction... 3 The problem: defense in depth is not working... 3 The new
Copyright 2011 Trend Micro Inc.
 Copyright 2011 Trend Micro Inc. 2008Q1 2008Q2 2008Q3 2008Q4 2009Q1 2009Q2 2009Q3 2009Q4 2010Q1 2010Q2 2010Q3 2010Q4 2011Q1 2011Q2 2011Q3 2011Q4 M'JPY Cloud Security revenue Q to Q Growth DeepSecurity/Hosted/CPVM/IDF
Copyright 2011 Trend Micro Inc. 2008Q1 2008Q2 2008Q3 2008Q4 2009Q1 2009Q2 2009Q3 2009Q4 2010Q1 2010Q2 2010Q3 2010Q4 2011Q1 2011Q2 2011Q3 2011Q4 M'JPY Cloud Security revenue Q to Q Growth DeepSecurity/Hosted/CPVM/IDF
The Eight Rules of Security
 The Eight Rules of Security The components of every security decision. Understanding and applying these rules builds a foundation for creating strong and formal practices through which we can make intelligent
The Eight Rules of Security The components of every security decision. Understanding and applying these rules builds a foundation for creating strong and formal practices through which we can make intelligent
IBM Threat Protection System: XGS - QRadar Integration
 IBM Security Network Protection Support Open Mic - Wednesday, 25 May 2016 IBM Threat Protection System: XGS - QRadar Integration Panelists Tanmay Shah - Presenter Level 2 Support Product Lead Danitza Villaran-Rokovich,
IBM Security Network Protection Support Open Mic - Wednesday, 25 May 2016 IBM Threat Protection System: XGS - QRadar Integration Panelists Tanmay Shah - Presenter Level 2 Support Product Lead Danitza Villaran-Rokovich,
1 Introduction Requirements Architecture Feature List... 3
 Contents 1 Introduction... 2 1.1 Requirements... 2 1.2 Architecture... 3 1.3 Feature List... 3 1.3.1 Device Compliance status... 3 1.3.2 Auto grouping for devices... 4 1.4 Basic Deployment... 4 1.4.1 Prepare
Contents 1 Introduction... 2 1.1 Requirements... 2 1.2 Architecture... 3 1.3 Feature List... 3 1.3.1 Device Compliance status... 3 1.3.2 Auto grouping for devices... 4 1.4 Basic Deployment... 4 1.4.1 Prepare
Jordan Levesque - Keeping your Business Secure
 Jordan Levesque - Keeping your Business Secure Review of PCI Benefits of hosting with RCS File Integrity Monitoring Two Factor Log Aggregation Vulnerability Scanning Configuration Management and Continuous
Jordan Levesque - Keeping your Business Secure Review of PCI Benefits of hosting with RCS File Integrity Monitoring Two Factor Log Aggregation Vulnerability Scanning Configuration Management and Continuous
Product overview. McAfee Web Protection Hybrid Integration Guide. Overview
 McAfee Web Protection Hybrid Integration Guide Product overview Overview The McAfee Web Protection hybrid solution is the integration of McAfee Web Gateway and McAfee Web Gateway Cloud Service (McAfee
McAfee Web Protection Hybrid Integration Guide Product overview Overview The McAfee Web Protection hybrid solution is the integration of McAfee Web Gateway and McAfee Web Gateway Cloud Service (McAfee
Intelligent and Secure Network
 Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
Bring Your Own Device
 Bring Your Own Device Individual Liable User Contents Introduction 3 Policy Document Objectives & Legal Disclaimer 3 Eligibility Considerations 4 Reimbursement Considerations 4 Security Considerations
Bring Your Own Device Individual Liable User Contents Introduction 3 Policy Document Objectives & Legal Disclaimer 3 Eligibility Considerations 4 Reimbursement Considerations 4 Security Considerations
MEMBERSHIP & PARTICIPATION
 MEMBERSHIP & PARTICIPATION What types of activities can I expect to participate in? There are a variety of activities for you to participate in such as discussion boards, idea exchanges, contests, surveys,
MEMBERSHIP & PARTICIPATION What types of activities can I expect to participate in? There are a variety of activities for you to participate in such as discussion boards, idea exchanges, contests, surveys,
Configuring BIG-IP ASM v12.1 Application Security Manager
 Course Description Configuring BIG-IP ASM v12.1 Application Security Manager Description The BIG-IP Application Security Manager course gives participants a functional understanding of how to deploy, tune,
Course Description Configuring BIG-IP ASM v12.1 Application Security Manager Description The BIG-IP Application Security Manager course gives participants a functional understanding of how to deploy, tune,
Network Security Assessment
 Network Security Assessment http://www.cta.com/content/docs/n et_ass.pdf 1 Introduction There are certain characteristics that the network should possess: 1. Security Policy. Networks should have an associated
Network Security Assessment http://www.cta.com/content/docs/n et_ass.pdf 1 Introduction There are certain characteristics that the network should possess: 1. Security Policy. Networks should have an associated
Application Whitelisting and Active Analysis Nick Levay, Chief Security Officer, Bit9
 Application Whitelisting and Active Analysis Nick Levay, Chief Security Officer, Bit9 About Me Chief Security Officer @ Bit9 Former Director of Technical Operations and Information Security @ Center for
Application Whitelisting and Active Analysis Nick Levay, Chief Security Officer, Bit9 About Me Chief Security Officer @ Bit9 Former Director of Technical Operations and Information Security @ Center for
IBM Security Network Protection Open Mic - Thursday, 31 March 2016
 IBM Security Network Protection Open Mic - Thursday, 31 March 2016 Application Control and IP Reputation on the XGS Demystified Panelists Tanmay Shah, Presenter IPS/Network Protection Product Lead Bill
IBM Security Network Protection Open Mic - Thursday, 31 March 2016 Application Control and IP Reputation on the XGS Demystified Panelists Tanmay Shah, Presenter IPS/Network Protection Product Lead Bill
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Ethical Hacking and Countermeasures: Secure Network Operating Systems and Infrastructures, Second Edition
 Ethical Hacking and Countermeasures: Secure Network Operating Systems and Infrastructures, Second Edition Chapter 7 Hacking Mobile Phones, PDAs, and Handheld Devices Objectives After completing this chapter,
Ethical Hacking and Countermeasures: Secure Network Operating Systems and Infrastructures, Second Edition Chapter 7 Hacking Mobile Phones, PDAs, and Handheld Devices Objectives After completing this chapter,
Kiosk Release Station User Guide Version 4
 Kiosk Release Station User Guide Version 4 eprintit Campus Solutions a division of St. Joseph Communications Page 1 Table of contents 1 Print Your Documents... 3 USB or Memory Card... 3 Cloud Files...
Kiosk Release Station User Guide Version 4 eprintit Campus Solutions a division of St. Joseph Communications Page 1 Table of contents 1 Print Your Documents... 3 USB or Memory Card... 3 Cloud Files...
ArcSight Activate Framework
 ArcSight Activate Framework Petropoulos #HPProtect 44% Have trouble managing their SIEM eiqnetworks 2013 SIEM Survey #1 challenge Identification of key events SANS 2012 Log Management and Event Management
ArcSight Activate Framework Petropoulos #HPProtect 44% Have trouble managing their SIEM eiqnetworks 2013 SIEM Survey #1 challenge Identification of key events SANS 2012 Log Management and Event Management
Pass4sure q. Cisco Securing Cisco Networks with Sourcefire IPS
 Pass4sure.500-285.42q Number: 500-285 Passing Score: 800 Time Limit: 120 min File Version: 6.1 Cisco 500-285 Securing Cisco Networks with Sourcefire IPS I'm quite happy to announce that I passed 500-285
Pass4sure.500-285.42q Number: 500-285 Passing Score: 800 Time Limit: 120 min File Version: 6.1 Cisco 500-285 Securing Cisco Networks with Sourcefire IPS I'm quite happy to announce that I passed 500-285
Daymar College is excited to announce the launch of our NEW Daymar App, available on Apple and Android devices.
 Daymar College is excited to announce the launch of our NEW Daymar App, available on Apple and Android devices. Students and Alumni can easily stay connected with the latest school news and events on their
Daymar College is excited to announce the launch of our NEW Daymar App, available on Apple and Android devices. Students and Alumni can easily stay connected with the latest school news and events on their
Course Outline Topic 1: Current State Assessment, Security Operations Centers, and Security Architecture
 About this Course This course will best position your organization to analyse threats and detect anomalies that could indicate cybercriminal behaviour. The payoff for this new proactive approach would
About this Course This course will best position your organization to analyse threats and detect anomalies that could indicate cybercriminal behaviour. The payoff for this new proactive approach would
1 Introduction Requirements Architecture Feature List... 4
 Contents 1 Introduction... 2 1.1 Requirements... 2 1.2 Architecture... 3 1.3 Feature List... 4 1.3.1 Device Compliance status... 4 1.3.2 Auto grouping for devices... 5 1.3.3 Auto grouping for applications...
Contents 1 Introduction... 2 1.1 Requirements... 2 1.2 Architecture... 3 1.3 Feature List... 4 1.3.1 Device Compliance status... 4 1.3.2 Auto grouping for devices... 5 1.3.3 Auto grouping for applications...
Dynamic Datacenter Security Solidex, November 2009
 Dynamic Datacenter Security Solidex, November 2009 Deep Security: Securing the New Server Cloud Virtualized Physical Servers in the open Servers virtual and in motion Servers under attack 2 11/9/09 2 Dynamic
Dynamic Datacenter Security Solidex, November 2009 Deep Security: Securing the New Server Cloud Virtualized Physical Servers in the open Servers virtual and in motion Servers under attack 2 11/9/09 2 Dynamic
ForeScout Extended Module for Symantec Endpoint Protection
 ForeScout Extended Module for Symantec Endpoint Protection Version 1.0.0 Table of Contents About the Symantec Endpoint Protection Integration... 4 Use Cases... 4 Additional Symantec Endpoint Protection
ForeScout Extended Module for Symantec Endpoint Protection Version 1.0.0 Table of Contents About the Symantec Endpoint Protection Integration... 4 Use Cases... 4 Additional Symantec Endpoint Protection
GLOBALPROTECT. Key Usage Scenarios and Benefits. Remote Access VPN Provides secure access to internal and cloud-based business applications
 GLOBALPROTECT Prevent Breaches and Secure the Mobile Workforce GlobalProtect extends the protection of Palo Alto Networks Next-Generation Security Platform to the members of your mobile workforce, no matter
GLOBALPROTECT Prevent Breaches and Secure the Mobile Workforce GlobalProtect extends the protection of Palo Alto Networks Next-Generation Security Platform to the members of your mobile workforce, no matter
The Invisible Threat of Modern Malware Lee Gitzes, CISSP Comm Solutions Company
 The Invisible Threat of Modern Malware Lee Gitzes, CISSP Comm Solutions Company November 12, 2014 Malware s Evolution Why the change? Hacking is profitable! Breaches and Malware are Projected to Cost $491
The Invisible Threat of Modern Malware Lee Gitzes, CISSP Comm Solutions Company November 12, 2014 Malware s Evolution Why the change? Hacking is profitable! Breaches and Malware are Projected to Cost $491
# ROLE DESCRIPTION / BENEFIT ISSUES / RISKS
 As SharePoint has proliferated across the landscape there has been a phase shift in how organizational information is kept secure. In one aspect, business assets are more secure employing a formally built
As SharePoint has proliferated across the landscape there has been a phase shift in how organizational information is kept secure. In one aspect, business assets are more secure employing a formally built
Course Outline (version 2)
 Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
Symantec Endpoint Protection Mobile - Admin Guide v3.2.1 May 2018
 Symantec Endpoint Protection Mobile - Admin Guide v3.2.1 May 2018 Symantec Endpoint Protection Mobile - Admin Guide Documentation version: 3.0 This document was last updated on: August 21, 2017 Legal Notice
Symantec Endpoint Protection Mobile - Admin Guide v3.2.1 May 2018 Symantec Endpoint Protection Mobile - Admin Guide Documentation version: 3.0 This document was last updated on: August 21, 2017 Legal Notice
The Evolution of : Continuous Advanced Threat Protection
 The Evolution of : Continuous Advanced Threat Protection Craig Bird Senior Solutions Engineer Security is a combination of protection, detection and response You need Prevention to defend against low-focus
The Evolution of : Continuous Advanced Threat Protection Craig Bird Senior Solutions Engineer Security is a combination of protection, detection and response You need Prevention to defend against low-focus
Ethical Hacking and Prevention
 Ethical Hacking and Prevention This course is mapped to the popular Ethical Hacking and Prevention Certification Exam from US-Council. This course is meant for those professionals who are looking for comprehensive
Ethical Hacking and Prevention This course is mapped to the popular Ethical Hacking and Prevention Certification Exam from US-Council. This course is meant for those professionals who are looking for comprehensive
THE RISE OF GLOBAL THREAT INTELLIGENCE
 THE RISE OF GLOBAL THREAT INTELLIGENCE 1 THE RISE OF GLOBAL THREAT INTELLIGENCE IN THE DIGITAL BUSINESS WORLD In developing the Global Threat Intelligence Report (GTIR), the NTT Group security team used
THE RISE OF GLOBAL THREAT INTELLIGENCE 1 THE RISE OF GLOBAL THREAT INTELLIGENCE IN THE DIGITAL BUSINESS WORLD In developing the Global Threat Intelligence Report (GTIR), the NTT Group security team used
SANS Top 20 CIS. Critical Security Control Solution Brief Version 6. SANS Top 20 CIS. EventTracker 8815 Centre Park Drive, Columbia MD 21045
 Critical Security Control Solution Brief Version 6 8815 Centre Park Drive, Columbia MD 21045 About delivers business critical software and services that transform high-volume cryptic log data into actionable,
Critical Security Control Solution Brief Version 6 8815 Centre Park Drive, Columbia MD 21045 About delivers business critical software and services that transform high-volume cryptic log data into actionable,
Securing the Modern Data Center with Trend Micro Deep Security
 Advania Fall Conference Securing the Modern Data Center with Trend Micro Deep Security Okan Kalak, Senior Sales Engineer okan@trendmicro.no Infrastructure change Containers 1011 0100 0010 Serverless Public
Advania Fall Conference Securing the Modern Data Center with Trend Micro Deep Security Okan Kalak, Senior Sales Engineer okan@trendmicro.no Infrastructure change Containers 1011 0100 0010 Serverless Public
BRING YOUR OWN DEVICE: POLICY CONSIDERATIONS
 WHITE PAPER BRING YOUR OWN DEVICE: POLICY CONSIDERATIONS INTRODUCTION As more companies embrace the broad usage of individual liable mobile devices or BYOD for access to corporate applications and data,
WHITE PAPER BRING YOUR OWN DEVICE: POLICY CONSIDERATIONS INTRODUCTION As more companies embrace the broad usage of individual liable mobile devices or BYOD for access to corporate applications and data,
Security. Risk Management. Compliance.
 Richard Nichols Netwitness Operations Director, RSA Security. Risk Management. Compliance. 1 Old World: Static Security Static Attacks Generic, Code-Based Static Infrastructure Physical, IT Controlled
Richard Nichols Netwitness Operations Director, RSA Security. Risk Management. Compliance. 1 Old World: Static Security Static Attacks Generic, Code-Based Static Infrastructure Physical, IT Controlled
AppSpider Enterprise. Getting Started Guide
 AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
ARC VIEW. Critical Industries Need Continuous ICS Security Monitoring. Keywords. Summary. By Sid Snitkin
 ARC VIEW FEBRUARY 1, 2018 Critical Industries Need Continuous ICS Security Monitoring By Sid Snitkin Keywords Anomaly and Breach Detection, Continuous ICS Security Monitoring, Nozomi Networks Summary Most
ARC VIEW FEBRUARY 1, 2018 Critical Industries Need Continuous ICS Security Monitoring By Sid Snitkin Keywords Anomaly and Breach Detection, Continuous ICS Security Monitoring, Nozomi Networks Summary Most
CND Exam Blueprint v2.0
 EC-Council C ND Certified Network Defende r CND Exam Blueprint v2.0 CND Exam Blueprint v2.0 1 Domains Objectives Weightage Number of Questions 1. Computer Network and Defense Fundamentals Understanding
EC-Council C ND Certified Network Defende r CND Exam Blueprint v2.0 CND Exam Blueprint v2.0 1 Domains Objectives Weightage Number of Questions 1. Computer Network and Defense Fundamentals Understanding
How to Join Skype Meetings
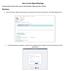 How to Join Skype Meetings Scroll through to find the device you are using: Windows, Skype App, Mac or iphone. Windows 1. Open the email / calendar request that you received from your host and select the
How to Join Skype Meetings Scroll through to find the device you are using: Windows, Skype App, Mac or iphone. Windows 1. Open the email / calendar request that you received from your host and select the
Stopping Advanced Persistent Threats In Cloud and DataCenters
 Stopping Advanced Persistent Threats In Cloud and DataCenters Frederik Van Roosendael PSE Belgium Luxembourg 10/9/2015 Copyright 2013 Trend Micro Inc. Agenda How Threats evolved Transforming Your Data
Stopping Advanced Persistent Threats In Cloud and DataCenters Frederik Van Roosendael PSE Belgium Luxembourg 10/9/2015 Copyright 2013 Trend Micro Inc. Agenda How Threats evolved Transforming Your Data
Advanced Endpoint Protection
 Advanced Endpoint Protection Protecting Endpoints and Servers Nick Levay, Chief Security Officer, Bit9 @rattle1337 2014 Bit9. All Rights Reserved About Me Chief Security Officer, Bit9
Advanced Endpoint Protection Protecting Endpoints and Servers Nick Levay, Chief Security Officer, Bit9 @rattle1337 2014 Bit9. All Rights Reserved About Me Chief Security Officer, Bit9
CyberP3i Hands-on Lab Series
 CyberP3i Hands-on Lab Series Lab Series using NETLAB Designer: Dr. Lixin Wang, Associate Professor Hands-On Lab for Application Attacks The NDG Security+ Pod Topology Is Used 1. Introduction In this lab,
CyberP3i Hands-on Lab Series Lab Series using NETLAB Designer: Dr. Lixin Wang, Associate Professor Hands-On Lab for Application Attacks The NDG Security+ Pod Topology Is Used 1. Introduction In this lab,
Database Security Service. FAQs. Issue 19 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 19 Date 2019-04-08 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 19 Date 2019-04-08 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
ein wichtiger Baustein im Security Ökosystem Dr. Christian Gayda (T-SEC) und Ingo Kruckewitt (Symantec)
 Next Gen Endpoint Protection ein wichtiger Baustein im Security Ökosystem Dr. Christian Gayda (T-SEC) und Ingo Kruckewitt (Symantec) What is Next Gen Endpoint Protection? 2 DT Next Gen Endpoint Protection
Next Gen Endpoint Protection ein wichtiger Baustein im Security Ökosystem Dr. Christian Gayda (T-SEC) und Ingo Kruckewitt (Symantec) What is Next Gen Endpoint Protection? 2 DT Next Gen Endpoint Protection
Product Roadmap Symantec Endpoint Protection Suzanne Konvicka & Paul Murgatroyd
 Product Roadmap Symantec Endpoint Protection Suzanne Konvicka & Paul Murgatroyd Symantec Endpoint Protection Product Roadmap 1 Safe Harbor Disclaimer Any information regarding pre-release Symantec offerings,
Product Roadmap Symantec Endpoint Protection Suzanne Konvicka & Paul Murgatroyd Symantec Endpoint Protection Product Roadmap 1 Safe Harbor Disclaimer Any information regarding pre-release Symantec offerings,
