Identity Proofing Standards and Beyond
|
|
|
- Eleanor Bryant
- 5 years ago
- Views:
Transcription
1 Solutions for Health Care Providers Identity Proofing Standards and Beyond Kimberly Little Sutherland LexisNexis Risk Solutions Sr. Director, Identity Management Solution Strategy
2 Agenda Identity Proofing Primer Identity Proofing Standards Identity Proofing Challenges More on Identity Resolution Other Considerations Summary
3 Identity Proofing Primer 3
4 Identity Management Basics Identity Management is a process designed to correctly identify the right individual for the right purpose. Identity Management risks can occur due to: Misidentification Impersonation or theft Fabrication or use of a synthetic identity, and Collusion Identity Proofing Standards and Beyond 4
5 Identity Proofing Defined No consistent definition for identity proofing Goes by multiple names Basic definition: The process by which an organization collects and verifies information about a person for the purpose of account opening or issuing credentials to that person. Other terms: Identity Verification, Verification and Authentication Identity Proofing Standards and Beyond 5
6 Identity Proofing The top reasons for incorporating identity proofing processes: Regulatory compliance Enhancing fraud prevention Improving business efficiencies Identity Proofing decisions impact nearly every user interaction, beginning at registration. These choices will not only impact a company s technology decisions, but also user experience processes, and even privacy policies. Identity Proofing Standards and Beyond 6
7 Identity Proofing Standards 7
8 Identity Proofing Standards and Regulations There is a patchwork landscape at the federal, state, and local level and for commercial industries for identity proofing and identity authentication. Government Federal: NIST (eauthentication) Commercial Banking: Section 326 of the USA PATRIOT Act (Customer Identification Program) The Nevada Gaming Commission and State Gaming Control Board: Regulation 5A (110 - Registration of Authorized Player) Identity Proofing Standards and Beyond 8
9 NIST Identity Proofing Standards and Beyond 9
10 NIST NIST requirements include measures to ensure that: A person with the Applicant s claimed attributes exists, and those attributes are sufficient to uniquely identify a single person; The Applicant whose token is registered is in fact the person who is entitled to the identity; It is difficult for the Claimant to later repudiate the registration and dispute an authentication using the Subscriber s token. Identity Proofing Standards and Beyond 10
11 RISK In-Person Identity Proofing Levels of Assurance HIGH MED- HIGH Level of Assurance 3 Level of Assurance 4 MED- LOW Level of Assurance 2 LOW Level of Assurance 1 ASSURANCE LOW MED-LOW MED-HIGH HIGH Identity Proofing Standards and Beyond 11
12 RISK Remote Identity Proofing Levels of Assurance HIGH MED- HIGH Level of Assurance 3 Level of Assurance 4 MED- LOW Level of Assurance 2 LOW Level of Assurance 1 ASSURANCE LOW MED-LOW MED-HIGH HIGH Identity Proofing Standards and Beyond 12
13 The Basic Components of Identity Proofing RESOLVE VERIFY AUTHENTICATE Resolve the identity Capture and disambiguate the data to identify one unique identity. Who you are? Bob Jones Verify the identity Establish that the identity exists. Does Bob Jones exist? Authenticate the identity Determine whether an individual or business owns the identity. Are you Bob Jones? Identity Proofing Standards and Beyond 13
14 Identity Proofing at LOA2 Verify Government ID Inspect photo-id, compare picture to applicant, and record the ID number, name, address and date of birth Inspection and Recording In Person Verify Personal Identity Confirm accuracy of application data to identify a unique individual Full name Address Date of birth (full or partial) Social Security Number* Remote Verify Government ID Number Verify Contact Information and Ability to Receive Communication Confirmation of , phone number or address Verify Account Number Verify Financial Account Verify Utility Account Verify Phone Number and Message Confirmation Knowledge Based Authentication (optional) Identity Proofing Standards and Beyond 14
15 Identity Proofing Challenges 15
16 Identity Proofing Challenges Garbage in, garbage out Data hygiene and reducing duplicate records is critical to having effective identity proofing processes. One way only Organizations should plan for alternate online workflows and contact channels, and try to limit manual reviews (more costly, not real-time). Citizens of the world Organizations should ensure their KYC processes can be used for US citizens with established identities, those with limited societal footprints, and even individuals temporarily residing in or visiting the US. Identity Proofing Standards and Beyond 16
17 Identity Proofing Challenges In-Person vs. Remote Organizations must identify the risks for both in-person and remote proofing and establish some form of equivalence in both processes. Also account for hybrid processes. Virtual Reality Organizations should avoid overreliance on self-asserted data in virtual/remote processes. Identify methods to strengthen and enhance the data collection process. Universal Translator Without a common lexicon, equivalence of identity attributes, and consistent identity resolution processes, organizations need to seek clarity in their identity proofing processes. Identity Proofing Standards and Beyond 17
18 More on Identity Resolution 18
19 Identity Proofing Standards and Beyond 19
20 IDPV Identity Attribute Framework Below is a summary of our framework for selecting identity attributes: 1) EFFECTIVENESS: How EFFECTIVE is the attribute at distinguishing an identity? 2) SENSITIVITY: Is the person SENSITIVE about the data attribute? Are they offended that we would ask such a question? 3) ACCESSIBILITY: Can the enroller verify the attribute? Does the enroller have ACCESS to resources that know? 4) PERMANENCE: Is this attribute stable over time? 5) NECESSITY: Is the attribute NECESSARY, something that I am required to collect in my business processes? Identity Proofing Standards and Beyond 20
21 Identity Resolution Project: Demographic Details The total core identities in the LexisNexis analysis: 268,182,500 Identities determined to be below the age of 18 have been excluded from the analysis Deceased identities will not be excluded from the analysis This is not intended to be a representation of the US population US Population comparison The total US resident population, 18 years and older*: 234,564,071 (population estimate from the 2010 US Census, US Census Bureau) The US annual deaths are estimated at 2.4M (based on Centers for Disease Control and Prevention s National Vital Statistics System mortality demographics: Work tables GMWK23F) Identity Proofing Standards and Beyond 21
22 Identity Resolution Project: Project Details A total of 112 distributions were performed: Location-oriented - 29 Time-oriented - 12 Identifier-oriented 12 Advanced combinations 60 * Name was used in all distributions Identity Proofing Standards and Beyond 22
23 Identity Resolution Project: Distribution Details Birth date-oriented identifying data (12): 1. Distribution of Name crossed by DOB 2. Name should include the following variants: a. First Name, Middle Initial and Last Name b. First Name and Last Name c. First Initial and Last Name d. First Name 3. DOB should include the following variants: a. Full Date of Birth b. Year of Birth c. Month and Day Identity Proofing Standards and Beyond 23
24 Identity Resolution Project: Example of a Distribution count of Identities count of DOB + fname + lname % DOB + fname + lname of total core ADL cnt = 1 228,542, cnt = 2 3,294, cnt = 3 356, cnt = 4 93, cnt = 5 36, cnt = 6 18, cnt = 7 11, cnt = 8 6, cnt = 9 5, cnt = 10 3, cnt > 10 14, total DOB- oriented cnt 237,346, total core ADL 268,154,531 Identity Proofing Standards and Beyond 24
25 A Further Illustration of Identity Resolution 34,135 The number of females born in 1970 with the name Kimberly Identity Proofing Standards and Beyond 25
26 First Name, Last Name Combinations are Not So Unique The number of females named Kimberly Little in the US: Identity Proofing Standards and Beyond 26
27 First Name, Last Name with Location Provides More Focus 104 people named Kimberly Little in GA 3 people named Kimberly Little in Alpharetta, GA - All three have different years of birth (1962, 1963 and 1970) - One of us has a different zip code Identity Proofing Standards and Beyond 27
28 Identity Resolution Project: Attribute Guidelines Core Attributes must uniquely resolve at least 95% of identities: First Name, Last Name + SSN 9 (96.52%) First Name, Last Name + Full DOB (96.29%) First Name, Last Name + SSN4 +. Identity Proofing Standards and Beyond 28
29 Identity Resolution Project: Attributes Analyzed Name: a. First Name, Middle Initial and Last Name b. First Name and Last Name c. First Initial and Last Name d. First Name Location: a. Full Address b. Street Address c. City and State d. County and State e. House Number f. Secondary Number (Suite or Apt No.) g. Street Name h. Postal Code Time: a. Full Date of Birth b. Year of Birth (YYYY) c. Month and Day of Birth (MMDD) Identifier: a. Full Social Security Number (SSN9) b. First 5 digits of the Social Security Number (SSN5) c. Last 4 digits of the Social Security Number (SSN4) Identity Proofing Standards and Beyond 29
30 Identity Proofing Standards and Beyond 30
31 Identity Proofing Standards and Beyond 31
32 Identity Proofing Standards and Beyond 32
33 IDPV Identity Attribute Framework Revisited Below is a summary of our framework for selecting identity attributes: 1) EFFECTIVENESS: How EFFECTIVE is the attribute at distinguishing an identity? 2) SENSITIVITY: Is the person SENSITIVE about the data attribute? Are they offended that we would ask such a question? 3) ACCESSIBILITY: Can the enroller verify the attribute? Does the enroller have ACCESS to resources that know? 4) PERMANENCE: Is this attribute stable over time? 5) NECESSITY: Is the attribute NECESSARY, something that I am required to collect in my business processes? Identity Proofing Standards and Beyond 33
34 Identity Resolution Project - Sensitivity Javelin Identity Proofing Standards and Beyond 34
35 Consumer Willingness to Share PII: With Government Agencies When Filing a Tax Return Identity Proofing Standards and Beyond 35
36 Consumer Willingness to Share PII: When Opening a New Financial Account Identity Proofing Standards and Beyond 36
37 Consumer Willingness to Share PII: With Government Agencies When Registering To Receive Program Details or Benefits Identity Proofing Standards and Beyond 37
38 Consumer Willingness to Share PII: For Returning a Purchase For A Refund Identity Proofing Standards and Beyond 38
39 IDPV Identity Attribute Framework Revisited Below is a summary of our framework for selecting identity attributes: 1) EFFECTIVENESS: How EFFECTIVE is the attribute at distinguishing an identity? 2) SENSITIVITY: Is the person SENSITIVE about the data attribute? Are they offended that we would ask such a question? 3) ACCESSIBILITY: Can the enroller verify the attribute? Does the enroller have ACCESS to resources that know? 4) PERMANENCE: Is this attribute stable over time? 5) NECESSITY: Is the attribute NECESSARY, something that I am required to collect in my business processes? Identity Proofing Standards and Beyond 39
40 Other Considerations 40
41 Future Research: Establishing Equivalence of Identity Attributes HIGH TRUST Biometrics Expert/electronic ID document authentication Verified bank account MODERATE TRUST Dynamic knowledge based authentication Electronic copy of passport Electronic copy of drivers license Mobile number LOW TRUST Social login address Source: MiiCard (adapted) Identity Proofing Standards and Beyond 41
42 Summary 42
43 Summary 1. Despite the fact that identity proofing is a foundational activity for user registration/new account opening activities and credential issuance, there are limited standards to guide organizations in this process. 2. Resolution to one unique individual should be clearly understood in the proofing process. Extra attention should be given to identity resolution when multiple databases and/or vendors are used in the proofing process. 3. Identity proofing should align with: The assessed risk based on the type of user activities to be permitted and whether the process will performed be in-person, remote or a hybrid. The interaction channel being leveraged (via face-to-face, kiosk, website, a mobile browser or mobile app). 4. Future research is needed for identity proofing in terms of identity resolution, establishing equivalence of identity attributes, new methods for identity proofing and strengthening the proofing process. Identity Proofing Standards and Beyond 43
44 Questions? Identity Proofing Standards and Beyond 44
45 Thank You Kimberly Little Sutherland, Sr. Director, Identity Management Solution Strategy LexisNexis Risk Solutions Identity Proofing Standards and Beyond 45
NASS Remote Notarization Task Force
 NASS Remote Notarization Task Force Knowledge-Based Verification David Temoshok Applied Cybersecurity IT Laboratory National Institute of Standards and Technology (NIST) 2/23/2017 1 Today s Discussion
NASS Remote Notarization Task Force Knowledge-Based Verification David Temoshok Applied Cybersecurity IT Laboratory National Institute of Standards and Technology (NIST) 2/23/2017 1 Today s Discussion
Universal Representation of a Consumer's Identity Is it Possible? Presenter: Rob Harris, VP of Product Strategy, FIS
 Universal Representation of a Consumer's Identity Is it Possible? Presenter: Rob Harris, VP of Product Strategy, FIS Topics Consumer identity why it is important How big a problem is identity fraud? What
Universal Representation of a Consumer's Identity Is it Possible? Presenter: Rob Harris, VP of Product Strategy, FIS Topics Consumer identity why it is important How big a problem is identity fraud? What
Measuring Authentication: NIST and Vectors of Trust
 SESSION ID: IDY-F01 Measuring Authentication: NIST 800-63 and Vectors of Trust auth Sarah Squire Senior Identity Solution Architect Engage Identity @SarahKSquire Eyewitness News 3 A Play in Five Acts
SESSION ID: IDY-F01 Measuring Authentication: NIST 800-63 and Vectors of Trust auth Sarah Squire Senior Identity Solution Architect Engage Identity @SarahKSquire Eyewitness News 3 A Play in Five Acts
A Layered Approach to Fraud Mitigation. Nick White Product Manager, FIS Payments Integrated Financial Services
 A Layered Approach to Fraud Mitigation Nick White Product Manager, FIS Payments Integrated Financial Services Session Agenda Growing Fraud Concerns Old Habits Die Hard Maneuvering through the Barriers
A Layered Approach to Fraud Mitigation Nick White Product Manager, FIS Payments Integrated Financial Services Session Agenda Growing Fraud Concerns Old Habits Die Hard Maneuvering through the Barriers
Online Batch Services
 Online Batch Services LexisNexis has enhanced its batch services to allow more user-friendly functionality for uploading batches and mapping layouts. Users sign in to the main product to access the online
Online Batch Services LexisNexis has enhanced its batch services to allow more user-friendly functionality for uploading batches and mapping layouts. Users sign in to the main product to access the online
Qatar e-authentication Framework
 Policy Proposal The Supreme Council of Information & Communication Technology ictqatar PD Reference: CS 1212 PUBLICATION DATE Document Reference Table of Contents Table of Contents... 2 Definitions...
Policy Proposal The Supreme Council of Information & Communication Technology ictqatar PD Reference: CS 1212 PUBLICATION DATE Document Reference Table of Contents Table of Contents... 2 Definitions...
Assuring Identity. The Identity Assurance Framework CTST Conference, New Orleans, May-09
 Assuring Identity The Identity Assurance Framework CTST Conference, New Orleans, May-09 Brett McDowell, Executive Director, Liberty Alliance email@brettmcdowell +1-413-652-1248 1 150+ Liberty Alliance
Assuring Identity The Identity Assurance Framework CTST Conference, New Orleans, May-09 Brett McDowell, Executive Director, Liberty Alliance email@brettmcdowell +1-413-652-1248 1 150+ Liberty Alliance
Securing Americans Identities: The Future of the Social Security Number
 Cha : Testimony, SASC 04 /25 /2017 1 Statement Before the House Ways and Means Subcommittee on Social Security Securing Americans Identities: The Future of the Social Security Number A Testimony by: James
Cha : Testimony, SASC 04 /25 /2017 1 Statement Before the House Ways and Means Subcommittee on Social Security Securing Americans Identities: The Future of the Social Security Number A Testimony by: James
Oracle Banking Digital Experience
 Oracle Banking Digital Experience Checking Account Originations User Manual Release 18.2.0.0.0 Part No. E97823-01 June 2018 Checkings Account Originations User Manual June 2018 Oracle Financial Services
Oracle Banking Digital Experience Checking Account Originations User Manual Release 18.2.0.0.0 Part No. E97823-01 June 2018 Checkings Account Originations User Manual June 2018 Oracle Financial Services
Stakeholder and community feedback. Trusted Digital Identity Framework
 Stakeholder and community feedback Trusted Digital Identity Framework Digital Transformation Agency This work is copyright. Apart from any use as permitted under the Copyright Act 1968 and the rights explicitly
Stakeholder and community feedback Trusted Digital Identity Framework Digital Transformation Agency This work is copyright. Apart from any use as permitted under the Copyright Act 1968 and the rights explicitly
Conjure Network LLC Privacy Policy
 Conjure Network LLC Privacy Policy Effective September 28, 2018 Conjure Network LLC ( Conjure, us, we, or our ) operates http://www.conjure.network (the Site or Website ). This Privacy Policy (the Policy
Conjure Network LLC Privacy Policy Effective September 28, 2018 Conjure Network LLC ( Conjure, us, we, or our ) operates http://www.conjure.network (the Site or Website ). This Privacy Policy (the Policy
SWAMID Person-Proofed Multi-Factor Profile
 Document SWAMID Person-Proofed Multi-Factor Profile Identifier http://www.swamid.se/policy/assurance/al2mfa Version V1.0 Last modified 2018-09-12 Pages 10 Status FINAL License Creative Commons BY-SA 3.0
Document SWAMID Person-Proofed Multi-Factor Profile Identifier http://www.swamid.se/policy/assurance/al2mfa Version V1.0 Last modified 2018-09-12 Pages 10 Status FINAL License Creative Commons BY-SA 3.0
Trust Services for Electronic Transactions
 Trust Services for Electronic Transactions ROUMEN TRIFONOV Faculty of Computer Systems and Control Technical University of Sofia 8 st. Kliment Ohridski bul., 1000 Sofia BULGARIA r_trifonov@tu-sofia.bg
Trust Services for Electronic Transactions ROUMEN TRIFONOV Faculty of Computer Systems and Control Technical University of Sofia 8 st. Kliment Ohridski bul., 1000 Sofia BULGARIA r_trifonov@tu-sofia.bg
UNIWEB REGISTRATION. International Office
 1 UNIWEB REGISTRATION International Office TABLE OF CONTENTS 2 HOW TO REGISTER ON UNIWEB... 3 1. HOME PAGE... 3 2. PERSONAL DATA PROTECTION... 4 3. TAX IDENTIFICATION NUMBER... 4 4. PERSONAL DETAILS...
1 UNIWEB REGISTRATION International Office TABLE OF CONTENTS 2 HOW TO REGISTER ON UNIWEB... 3 1. HOME PAGE... 3 2. PERSONAL DATA PROTECTION... 4 3. TAX IDENTIFICATION NUMBER... 4 4. PERSONAL DETAILS...
Oracle Banking Digital Experience
 Oracle Banking Digital Experience US Originations Certificate of Deposit User Manual Release 18.2.0.0.0 Part No. E97823-01 June 2018 US Originations Certificate of Deposit User Manual June 2018 Oracle
Oracle Banking Digital Experience US Originations Certificate of Deposit User Manual Release 18.2.0.0.0 Part No. E97823-01 June 2018 US Originations Certificate of Deposit User Manual June 2018 Oracle
in a National Service Delivery Model 3 rd Annual Privacy, Access and Security Congress October 4, 2012
 Identity Management and Federation of Identity in a National Service Delivery Model 3 rd Annual Privacy, Access and Security Congress October 4, 2012 HRSDC - National Service Delivery HRSDC and its service
Identity Management and Federation of Identity in a National Service Delivery Model 3 rd Annual Privacy, Access and Security Congress October 4, 2012 HRSDC - National Service Delivery HRSDC and its service
Oracle Banking Digital Experience
 Oracle Banking Digital Experience Checking Account Originations User Manual Release 17.2.0.0.0 Part No. E88573-01 July 2017 Checkings Account Originations User Manual July 2017 Oracle Financial Services
Oracle Banking Digital Experience Checking Account Originations User Manual Release 17.2.0.0.0 Part No. E88573-01 July 2017 Checkings Account Originations User Manual July 2017 Oracle Financial Services
Oracle Banking Digital Experience
 Oracle Banking Digital Experience US Originations Checking Account User Manual Release 18.2.0.0.0 Part No. E97823-01 June 2018 US Originations Checking Account User Manual June 2018 Oracle Financial Services
Oracle Banking Digital Experience US Originations Checking Account User Manual Release 18.2.0.0.0 Part No. E97823-01 June 2018 US Originations Checking Account User Manual June 2018 Oracle Financial Services
Digital Solutions. January, 2016
 Digital Solutions January, 2016 This document provides an outline of a presentation and is incomplete without the accompanying oral commentary and discussion. Conclusions and/ or potential strategies contained
Digital Solutions January, 2016 This document provides an outline of a presentation and is incomplete without the accompanying oral commentary and discussion. Conclusions and/ or potential strategies contained
FinFit will request and collect information in order to determine whether you qualify for FinFit Loans*.
 FinFit Web Privacy Policy General: This Privacy Policy ( Policy ) describes the ways FinFit, LLC ( FinFit, we, us) collects, stores, uses and protects information we receive from you or that you may provide
FinFit Web Privacy Policy General: This Privacy Policy ( Policy ) describes the ways FinFit, LLC ( FinFit, we, us) collects, stores, uses and protects information we receive from you or that you may provide
Singapore s National Digital Identity (NDI):
 Singapore s National Digital Identity (NDI): Leaving no one behind Kwok Quek Sin Director, National Digital Identity Programme Government Technology Agency PART 1 INTRODUCTION TO NDI Better Living For
Singapore s National Digital Identity (NDI): Leaving no one behind Kwok Quek Sin Director, National Digital Identity Programme Government Technology Agency PART 1 INTRODUCTION TO NDI Better Living For
Oracle Banking Digital Experience
 Oracle Banking Digital Experience US Originations Savings Account User Manual Release 18.1.0.0.0 Part No. E92727-01 January 2018 Preface US Originations Savings Account User Manual January 2018 Oracle
Oracle Banking Digital Experience US Originations Savings Account User Manual Release 18.1.0.0.0 Part No. E92727-01 January 2018 Preface US Originations Savings Account User Manual January 2018 Oracle
Oracle Banking Digital Experience
 Oracle Banking Digital Experience US Originations Certificate of Deposit User Manual Release 18.1.0.0.0 Part No. E92727-01 January 2018 Preface US Originations Certificate of Deposit User Manual January
Oracle Banking Digital Experience US Originations Certificate of Deposit User Manual Release 18.1.0.0.0 Part No. E92727-01 January 2018 Preface US Originations Certificate of Deposit User Manual January
Privacy Statement. Your privacy and trust are important to us and this Privacy Statement ( Statement ) provides important information
 Privacy Statement Introduction Your privacy and trust are important to us and this Privacy Statement ( Statement ) provides important information about how IT Support (UK) Ltd handle personal information.
Privacy Statement Introduction Your privacy and trust are important to us and this Privacy Statement ( Statement ) provides important information about how IT Support (UK) Ltd handle personal information.
Q2 How many attorneys practice at the firm, organization, agency or department, or other entity you listed above?
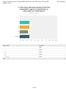 Q How many attorneys practice at the firm, organization, agency or department, or other entity you listed above? Answered: 7 Skipped: - 5-9 or more % % % % % 5% 6% 7% 8% 9% % - 5-9 or more.% 5.9% 7 5.9%
Q How many attorneys practice at the firm, organization, agency or department, or other entity you listed above? Answered: 7 Skipped: - 5-9 or more % % % % % 5% 6% 7% 8% 9% % - 5-9 or more.% 5.9% 7 5.9%
FAQ: Privacy, Security, and Data Protection at Libraries
 FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
Oracle Banking Digital Experience
 Oracle Banking Digital Experience FCUBS Originations Saving Account User Manual Release 18.3.0.0.0 Part No. F12056-01 December 2018 Preface FCUBS Originations Saving Account User Manual December 2018 Oracle
Oracle Banking Digital Experience FCUBS Originations Saving Account User Manual Release 18.3.0.0.0 Part No. F12056-01 December 2018 Preface FCUBS Originations Saving Account User Manual December 2018 Oracle
Oracle Banking Digital Experience
 Oracle Banking Digital Experience US Originations Checking Account User Manual Release 17.2.0.0.0 Part No. E88573-01 July 2017 US Originations Checking Account User Manual July 2017 Oracle Financial Services
Oracle Banking Digital Experience US Originations Checking Account User Manual Release 17.2.0.0.0 Part No. E88573-01 July 2017 US Originations Checking Account User Manual July 2017 Oracle Financial Services
Digital Identity Guidelines aka NIST SP March 1, 2017 Ken Klingenstein, Internet2
 Digital Identity Guidelines aka NIST SP 800-63 March 1, 2017 Ken Klingenstein, Internet2 Topics 800-63 History and Current Revision process Caveats and Comments LOA Evolution Sections: 800-63A (Enrollment
Digital Identity Guidelines aka NIST SP 800-63 March 1, 2017 Ken Klingenstein, Internet2 Topics 800-63 History and Current Revision process Caveats and Comments LOA Evolution Sections: 800-63A (Enrollment
Identity Theft Victim s Complaint and Affidavit
 Average time to complete: 10 minutes Identity Theft Victim s Complaint and Affidavit A voluntary form for filing a report with law enforcement, and disputes with credit reporting agencies and creditors
Average time to complete: 10 minutes Identity Theft Victim s Complaint and Affidavit A voluntary form for filing a report with law enforcement, and disputes with credit reporting agencies and creditors
National IAS Academy Current Affairs: Contact: PRELIMS. Impeachment of a SC judge. Ice sheets found in Mars
 Topic: Polity PRELIMS Impeachment of a SC judge More about Impeachment of a SC judge: Recently four Supreme Court judges went public with charges against Chief Justice of India. According to constitution
Topic: Polity PRELIMS Impeachment of a SC judge More about Impeachment of a SC judge: Recently four Supreme Court judges went public with charges against Chief Justice of India. According to constitution
EXPERIENCE SIMPLER, STRONGER AUTHENTICATION
 1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 783 data breaches >1 billion records stolen since 2012 $3.5 million average cost per breach 4 We have a PASSWORD
1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 783 data breaches >1 billion records stolen since 2012 $3.5 million average cost per breach 4 We have a PASSWORD
Hot Topics in Privacy
 Hot Topics in Privacy Gretchen S. Herault Monster Worldwide SCCE Conference April 12, 2013 Agenda Privacy Landscape current state of regulatory coverage > Global > Industry Sector > Technology Hot Topics
Hot Topics in Privacy Gretchen S. Herault Monster Worldwide SCCE Conference April 12, 2013 Agenda Privacy Landscape current state of regulatory coverage > Global > Industry Sector > Technology Hot Topics
Hot Topics in Privacy
 Hot Topics in Privacy Gretchen S. Herault Monster Worldwide SCCE Conference April 12, 2013 Agenda Privacy Landscape current state of regulatory coverage > Global > Industry Sector > Technology Hot Topics
Hot Topics in Privacy Gretchen S. Herault Monster Worldwide SCCE Conference April 12, 2013 Agenda Privacy Landscape current state of regulatory coverage > Global > Industry Sector > Technology Hot Topics
Will Federated Cross Credentialing Solutions Accelerate Adoption of Smart Card Based Identity Solutions?
 Will Federated Cross Credentialing Solutions Accelerate Adoption of Smart Card Based Identity Solutions? Jack Radzikowski,, Northrop Grumman & FiXs Smart Card Alliance Annual Meeting La Jolla, California
Will Federated Cross Credentialing Solutions Accelerate Adoption of Smart Card Based Identity Solutions? Jack Radzikowski,, Northrop Grumman & FiXs Smart Card Alliance Annual Meeting La Jolla, California
Remote Deposit Capture Member User Guide. RDC Brought to you by Sprig
 Remote Deposit Capture Member User Guide RDC Brought to you by Sprig This document will provide you the basic understanding of how to access the Sprig app, add accounts to your virtual wallet and utilize
Remote Deposit Capture Member User Guide RDC Brought to you by Sprig This document will provide you the basic understanding of how to access the Sprig app, add accounts to your virtual wallet and utilize
NLAD User Guide for Release 3.8.0
 NLAD User Guide for Release 3.8.0 11-28-2017 Document Version 1 NLAD User Guide for Release 3.8.0 Contents 1. Introduction...1 1.1. NLAD Capabilities...1 1.2. Supported Web Browsers...1 2. Login...2 2.1.
NLAD User Guide for Release 3.8.0 11-28-2017 Document Version 1 NLAD User Guide for Release 3.8.0 Contents 1. Introduction...1 1.1. NLAD Capabilities...1 1.2. Supported Web Browsers...1 2. Login...2 2.1.
The HITRUST CSF. A Revolutionary Way to Protect Electronic Health Information
 The HITRUST CSF A Revolutionary Way to Protect Electronic Health Information June 2015 The HITRUST CSF 2 Organizations in the healthcare industry are under immense pressure to improve quality, reduce complexity,
The HITRUST CSF A Revolutionary Way to Protect Electronic Health Information June 2015 The HITRUST CSF 2 Organizations in the healthcare industry are under immense pressure to improve quality, reduce complexity,
Dissecting NIST Digital Identity Guidelines
 Dissecting NIST 800-63 Digital Identity Guidelines KEY CONSIDERATIONS FOR SELECTING THE RIGHT MULTIFACTOR AUTHENTICATION Embracing Compliance More and more business is being conducted digitally whether
Dissecting NIST 800-63 Digital Identity Guidelines KEY CONSIDERATIONS FOR SELECTING THE RIGHT MULTIFACTOR AUTHENTICATION Embracing Compliance More and more business is being conducted digitally whether
Kickstart. Overview. Oct 2017
 Kickstart Overview Oct 2017 Passwords are broken 75% of users leave themselves open to fraud & identity theft through insecure passwords 68% 40% of users say forgetting passwords is a significant problem
Kickstart Overview Oct 2017 Passwords are broken 75% of users leave themselves open to fraud & identity theft through insecure passwords 68% 40% of users say forgetting passwords is a significant problem
The most extensive identity protection plan available
 The most extensive identity protection plan available AGENDA Identity theft About InfoArmor PrivacyArmor coverage Portal walkthrough Q&A Sharing data is now a fact of daily life. Our work requires personal
The most extensive identity protection plan available AGENDA Identity theft About InfoArmor PrivacyArmor coverage Portal walkthrough Q&A Sharing data is now a fact of daily life. Our work requires personal
HITPC Stage 3 Request for Comments Smart Card Alliance Comments January, 14, 2013
 HITPC Stage 3 Request for Comments Smart Card Alliance Comments January, 14, 2013 The Smart Card Alliance hereby submits the following comments regarding the Health Information Technology Policy Committee
HITPC Stage 3 Request for Comments Smart Card Alliance Comments January, 14, 2013 The Smart Card Alliance hereby submits the following comments regarding the Health Information Technology Policy Committee
Aspects of Identity. InfoSec April BCS Security Community of Expertise
 Aspects of Identity InfoSec April 2011 BCS Security Community of Expertise SCoE Representatives Dr. Louise Bennett FBCS CITP Chair of the BCS Security Community of Expertise Ian Fish FBCS BCS Information
Aspects of Identity InfoSec April 2011 BCS Security Community of Expertise SCoE Representatives Dr. Louise Bennett FBCS CITP Chair of the BCS Security Community of Expertise Ian Fish FBCS BCS Information
eidas Regulation eid and assurance levels Outcome of eias study
 eidas Regulation eid and assurance levels Outcome of eias study Dr. Marijke De Soete Security4Biz (Belgium) ETSI eidas Workshop 24 June 2015 Sophia Antipolis eidas Regulation Regulation on electronic identification
eidas Regulation eid and assurance levels Outcome of eias study Dr. Marijke De Soete Security4Biz (Belgium) ETSI eidas Workshop 24 June 2015 Sophia Antipolis eidas Regulation Regulation on electronic identification
How. Biometrics. Expand the Reach of Mobile Banking ENTER
 How Biometrics Expand the Reach of Mobile Banking ENTER Table of Contents 01 The Mobile Banking Opportunity 02 What s Suppressing Mobile Adoption? 03 Onboarding Challenges: Proving One s Identity 04 Authentication
How Biometrics Expand the Reach of Mobile Banking ENTER Table of Contents 01 The Mobile Banking Opportunity 02 What s Suppressing Mobile Adoption? 03 Onboarding Challenges: Proving One s Identity 04 Authentication
ONE ID Identity and Access Management System
 ONE ID Identity and Access Management System Local Registration Authority User Guide Document Identifier: 2274 Version: 1.8 Page 1 Copyright Notice Copyright 2011, ehealth Ontario All rights reserved No
ONE ID Identity and Access Management System Local Registration Authority User Guide Document Identifier: 2274 Version: 1.8 Page 1 Copyright Notice Copyright 2011, ehealth Ontario All rights reserved No
Hardware One-Time Password User Guide November 2017
 Hardware One-Time Password User Guide November 2017 1 Table of Contents Table of Contents... 2 Purpose... 3 About One-Time Password Credentials... 3 How to Determine if You Need a Credential... 3 Acquisition
Hardware One-Time Password User Guide November 2017 1 Table of Contents Table of Contents... 2 Purpose... 3 About One-Time Password Credentials... 3 How to Determine if You Need a Credential... 3 Acquisition
Mobile verification. If your Mobile Number is correct, click Get Code.
 KYC Process To complete your KYC (Know Your Customer) verification, please login to your Back Office. Navigate to Support KYC- Status and the following submenus (as stated on top of every section) to perform
KYC Process To complete your KYC (Know Your Customer) verification, please login to your Back Office. Navigate to Support KYC- Status and the following submenus (as stated on top of every section) to perform
TRUSTIS FPS. Enrolment Requirements: Acceptable Evidence in Support of an Application for a Digital Certificate
 TRUSTIS FPS Enrolment Requirements: Acceptable Evidence in Support of an Application for a Digital Certificate Important Notice: The information here is guidance on the minimum requirements of Enrolment
TRUSTIS FPS Enrolment Requirements: Acceptable Evidence in Support of an Application for a Digital Certificate Important Notice: The information here is guidance on the minimum requirements of Enrolment
NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY
 NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY Standardization of Entity Authentication Assurance 5th ETSI Security Workshop 20-2222 January 2010 ETSI, Sophia Antipolis, France Erika McCallister, Esq.,
NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY Standardization of Entity Authentication Assurance 5th ETSI Security Workshop 20-2222 January 2010 ETSI, Sophia Antipolis, France Erika McCallister, Esq.,
Mobile: Purely a Powerful Platform; Or Panacea?
 EBT: The Next Generation 2017 Mobile: Purely a Powerful Platform; Or Panacea? Evan O Regan, Director of Product Management Authentication & Fraud Solutions Entrust Datacard POWERFUL PLATFORM OR PANACEA
EBT: The Next Generation 2017 Mobile: Purely a Powerful Platform; Or Panacea? Evan O Regan, Director of Product Management Authentication & Fraud Solutions Entrust Datacard POWERFUL PLATFORM OR PANACEA
Red Flags Program. Purpose
 Red Flags Program Purpose The purpose of this Red Flags Rules Program is to document the protocol adopted by the University of Memphis in compliance with the Red Flags Rules. Many offices at the University
Red Flags Program Purpose The purpose of this Red Flags Rules Program is to document the protocol adopted by the University of Memphis in compliance with the Red Flags Rules. Many offices at the University
Lecture 41 Blockchain in Government III (Digital Identity)
 Blockchains Architecture, Design and Use Cases Prof. Sandip Chakraborty Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 41 Blockchain in Government III
Blockchains Architecture, Design and Use Cases Prof. Sandip Chakraborty Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 41 Blockchain in Government III
Oracle Banking Digital Experience
 Oracle Banking Digital Experience FCUBS Originations Auto Loan User Manual Release 18.1.0.0.0 Part No. E92727-01 January 2018 FCUBS Originations Auto Loan User Manual January 2018 Oracle Financial Services
Oracle Banking Digital Experience FCUBS Originations Auto Loan User Manual Release 18.1.0.0.0 Part No. E92727-01 January 2018 FCUBS Originations Auto Loan User Manual January 2018 Oracle Financial Services
Identity Theft Policies and Procedures
 Identity Theft Policies and Procedures Davis & Wehrle, LLC 1104 S. Mays, Suite 105 Round Rock, TX 78664-6700 United States (512) 346-1131 Davis & Wehrle Identity Theft Policies & Procedures September 2017
Identity Theft Policies and Procedures Davis & Wehrle, LLC 1104 S. Mays, Suite 105 Round Rock, TX 78664-6700 United States (512) 346-1131 Davis & Wehrle Identity Theft Policies & Procedures September 2017
DigitalPersona Altus. Solution Guide
 DigitalPersona Altus Solution Guide Contents DigitalPersona... 1 DigitalPersona Altus Solution... 4 MODULAR SOLUTION CREATE-CONFIRM-CONTROL... 4 EXPERT SERVICES ASSESS-DESIGN-DEPLOY-SUPPORT... 5 DigitalPersona
DigitalPersona Altus Solution Guide Contents DigitalPersona... 1 DigitalPersona Altus Solution... 4 MODULAR SOLUTION CREATE-CONFIRM-CONTROL... 4 EXPERT SERVICES ASSESS-DESIGN-DEPLOY-SUPPORT... 5 DigitalPersona
HIPAA and HIPAA Compliance with PHI/PII in Research
 HIPAA and HIPAA Compliance with PHI/PII in Research HIPAA Compliance Federal Regulations-Enforced by Office of Civil Rights State Regulations-Texas Administrative Codes Institutional Policies-UTHSA HOPs/IRB
HIPAA and HIPAA Compliance with PHI/PII in Research HIPAA Compliance Federal Regulations-Enforced by Office of Civil Rights State Regulations-Texas Administrative Codes Institutional Policies-UTHSA HOPs/IRB
User Authentication Best Practices for E-Signatures Wednesday February 25, 2015
 User Authentication Best Practices for E-Signatures Wednesday February 25, 2015 Agenda E-Signature Overview Legality, Authentication & Best Practices Role of authentication in e-signing Options and applications
User Authentication Best Practices for E-Signatures Wednesday February 25, 2015 Agenda E-Signature Overview Legality, Authentication & Best Practices Role of authentication in e-signing Options and applications
ISO/IEC INTERNATIONAL STANDARD. Information technology Security techniques Entity authentication assurance framework
 INTERNATIONAL STANDARD ISO/IEC 29115 First edition 2013-04-01 Information technology Security techniques Entity authentication assurance framework Technologies de l'information Techniques de sécurité Cadre
INTERNATIONAL STANDARD ISO/IEC 29115 First edition 2013-04-01 Information technology Security techniques Entity authentication assurance framework Technologies de l'information Techniques de sécurité Cadre
Hardware One-Time Password User Guide August 2018
 Hardware One-Time Password User Guide August 2018 Copyright 2017 Exostar LLC. All rights reserved 1 Version Impacts Date Owner Hardware One-Time Password User Guide Image updates August 2018 M. Williams
Hardware One-Time Password User Guide August 2018 Copyright 2017 Exostar LLC. All rights reserved 1 Version Impacts Date Owner Hardware One-Time Password User Guide Image updates August 2018 M. Williams
Pennsylvania Certification by Endorsement
 Pennsylvania Certification by Endorsement Thank you for your interest in obtaining Pennsylvania EMS Certification by Endorsement. This is the process whereby a person certified by a state other than Pennsylvania
Pennsylvania Certification by Endorsement Thank you for your interest in obtaining Pennsylvania EMS Certification by Endorsement. This is the process whereby a person certified by a state other than Pennsylvania
Interagency Advisory Board HSPD-12 Insights: Past, Present and Future. Carol Bales Office of Management and Budget December 2, 2008
 Interagency Advisory Board HSPD-12 Insights: Past, Present and Future Carol Bales Office of Management and Budget December 2, 2008 Importance of Identity, Credential and Access Management within the Federal
Interagency Advisory Board HSPD-12 Insights: Past, Present and Future Carol Bales Office of Management and Budget December 2, 2008 Importance of Identity, Credential and Access Management within the Federal
Emsi Privacy Shield Policy
 Emsi Privacy Shield Policy Scope The Emsi Privacy Shield Policy ( Policy ) applies to the collection and processing of Personal Data that Emsi obtains from Data Subjects located in the European Union (
Emsi Privacy Shield Policy Scope The Emsi Privacy Shield Policy ( Policy ) applies to the collection and processing of Personal Data that Emsi obtains from Data Subjects located in the European Union (
Implementing Electronic Signature Solutions 11/10/2015
 Implementing Electronic Signature Solutions 11/10/2015 Agenda Methodology, Framework & Approach: High-Level Overarching Parameters Regarding Electronic Service Delivery Business Analysis & Risk Assessment
Implementing Electronic Signature Solutions 11/10/2015 Agenda Methodology, Framework & Approach: High-Level Overarching Parameters Regarding Electronic Service Delivery Business Analysis & Risk Assessment
Frequently Asked Questions (FAQ)
 Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
TATA CONSULTANCY SERVICES LIMITED CERTIFYING AUTHORITY REQUEST FORM FOR CLASS-2 CERTIFICATE FOR FOREIGN DIRECTORS.
 TATA CONSULTANCY SERVICES LIMITED CERTIFYING AUTHORITY REQUEST FORM FOR CLASS-2 CERTIFICATE FOR FOREIGN DIRECTORS. USER TYPE INDIVIDUAL Instructions: 1. Please fill the form in BLOCK LETTERS 2. Items marked
TATA CONSULTANCY SERVICES LIMITED CERTIFYING AUTHORITY REQUEST FORM FOR CLASS-2 CERTIFICATE FOR FOREIGN DIRECTORS. USER TYPE INDIVIDUAL Instructions: 1. Please fill the form in BLOCK LETTERS 2. Items marked
When this policy mentions WanderJaunt, we, us, or our, it refers to the WanderJaunt, Inc.
 WanderJaunt Privacy Policy Last Updated: June 20, 2018 Thank you for using WanderJaunt! This Privacy Policy describes how we collect, use, process, and disclose your information, including personal information,
WanderJaunt Privacy Policy Last Updated: June 20, 2018 Thank you for using WanderJaunt! This Privacy Policy describes how we collect, use, process, and disclose your information, including personal information,
Online Batch Services
 Online Batch Services LexisNexis has enhanced its batch services to allow more user-friendly functionality for uploading batches and mapping layouts. Users log into the main product to access the online
Online Batch Services LexisNexis has enhanced its batch services to allow more user-friendly functionality for uploading batches and mapping layouts. Users log into the main product to access the online
Trust. Trustworthiness Trusted. Trust: Who? What? When? Why? How?
 Trust Trustworthiness Trusted Trust: Who? What? When? Why? How? 1 Certification / Assessment is a spectrum GAFAT Websites Apps Self Asserted Basic Check Self Certified Independent Verification Independently
Trust Trustworthiness Trusted Trust: Who? What? When? Why? How? 1 Certification / Assessment is a spectrum GAFAT Websites Apps Self Asserted Basic Check Self Certified Independent Verification Independently
Trusted Identities. Foundational to Cloud Services LILA KEE CHIEF PRODUCT OFFICER GLOBALSIGN
 Trusted Identities Foundational to Cloud Services LILA KEE CHIEF PRODUCT OFFICER GLOBALSIGN WHAT YOU WILL LEARN TODAY Strong identity verification as a security measure and business enabler Authentication
Trusted Identities Foundational to Cloud Services LILA KEE CHIEF PRODUCT OFFICER GLOBALSIGN WHAT YOU WILL LEARN TODAY Strong identity verification as a security measure and business enabler Authentication
ID Theft Information Form - Instructions
 ID Theft Information Form - Instructions Identity Theft may occur when someone uses your personally identifiable information such as your name or social security number (SSN) to obtain services from Charter
ID Theft Information Form - Instructions Identity Theft may occur when someone uses your personally identifiable information such as your name or social security number (SSN) to obtain services from Charter
Interagency Advisory Board Meeting Agenda, August 25, 2009
 Interagency Advisory Board Meeting Agenda, August 25, 2009 1. Opening Remarks 2. Policy, process, regulations, technology, and infrastructure to employ HSPD-12 in USDA (Owen Unangst, USDA) 3. Policy and
Interagency Advisory Board Meeting Agenda, August 25, 2009 1. Opening Remarks 2. Policy, process, regulations, technology, and infrastructure to employ HSPD-12 in USDA (Owen Unangst, USDA) 3. Policy and
SWAMID Identity Assurance Level 2 Profile
 Document SWAMID Identity Assurance Level 2 Profile Identifier http://www.swamid.se/policy/assurance/al2 Version V1.0 Last modified 2015-12-02 Pages 11 Status FINAL License Creative Commons BY-SA 3.0 SWAMID
Document SWAMID Identity Assurance Level 2 Profile Identifier http://www.swamid.se/policy/assurance/al2 Version V1.0 Last modified 2015-12-02 Pages 11 Status FINAL License Creative Commons BY-SA 3.0 SWAMID
In this policy, whenever you see the words we, us, our, it refers to Ashby Concert Band Registered Charity Number
 ASHBY CONCERT BAND PRIVACY POLICY The privacy and security of your personal information is extremely important to us. This privacy policy explains how and why we use your personal data. We will keep this
ASHBY CONCERT BAND PRIVACY POLICY The privacy and security of your personal information is extremely important to us. This privacy policy explains how and why we use your personal data. We will keep this
Colorado Sex Offender Management Board (SOMB) INTENT TO APPLY. as a POLYGRAPH EXAMINER. for the Adult and Juvenile Provider List
 Colorado Sex Offender Management Board (SOMB) INTENT TO APPLY as a POLYGRAPH EXAMINER for the Adult and Juvenile Provider List Colorado Department of Public Safety Division of Criminal Justice Office of
Colorado Sex Offender Management Board (SOMB) INTENT TO APPLY as a POLYGRAPH EXAMINER for the Adult and Juvenile Provider List Colorado Department of Public Safety Division of Criminal Justice Office of
8/28/2014. Patron Records. About. Patron Records. Patron Records. Patron Records. Patron Records. Overview of Creating and Maintaining.
 About These instructions should serve as a basic overview of creating and updating patron accounts. Overview of Creating and Maintaining Please refer to the PINES Circulation Policies and Procedures Manual
About These instructions should serve as a basic overview of creating and updating patron accounts. Overview of Creating and Maintaining Please refer to the PINES Circulation Policies and Procedures Manual
NEW! Financial Aid is now available for non-credit workforce training programs at DCC!
 NEW! Financial Aid is now available for non-credit workforce training programs at DCC! Awarding Policy and Distribution Plan for FANTIC (Financial Aid for Noncredit Training leading to an Industry Credential)
NEW! Financial Aid is now available for non-credit workforce training programs at DCC! Awarding Policy and Distribution Plan for FANTIC (Financial Aid for Noncredit Training leading to an Industry Credential)
GROUPON.COM - PRIVACY POLICY
 PRIVACY STATEMENT Last Updated: September 13, 2012 This Privacy Statement ( Privacy Statement ) explains how Groupon, Inc. ( Groupon, us, our, and we ) uses your information and applies to all who use
PRIVACY STATEMENT Last Updated: September 13, 2012 This Privacy Statement ( Privacy Statement ) explains how Groupon, Inc. ( Groupon, us, our, and we ) uses your information and applies to all who use
FPKIPA CPWG Antecedent, In-Person Task Group
 FBCA Supplementary Antecedent, In-Person Definition This supplement provides clarification on the trust relationship between the Trusted Agent and the applicant, which is based on an in-person antecedent
FBCA Supplementary Antecedent, In-Person Definition This supplement provides clarification on the trust relationship between the Trusted Agent and the applicant, which is based on an in-person antecedent
BEYOND AUTHENTICATION IDENTITY AND ACCESS MANAGEMENT FOR THE MODERN ENTERPRISE
 BEYOND AUTHENTICATION IDENTITY AND ACCESS MANAGEMENT FOR THE MODERN ENTERPRISE OUR ORGANISATION AND SPECIALIST SKILLS Focused on delivery, integration and managed services around Identity and Access Management.
BEYOND AUTHENTICATION IDENTITY AND ACCESS MANAGEMENT FOR THE MODERN ENTERPRISE OUR ORGANISATION AND SPECIALIST SKILLS Focused on delivery, integration and managed services around Identity and Access Management.
ITU-T SG 17 Q10/17. Trust Elevation Frameworks
 ITU-T SG 17 Q10/17 Trust Elevation Frameworks Abbie Barbir, Ph.D. ITU-T SG 17 Q10 Rapporteur Martin Euchner SG 17 Advisor ITU Workshop on "Future Trust and Knowledge Infrastructure July 1 2016 Contents
ITU-T SG 17 Q10/17 Trust Elevation Frameworks Abbie Barbir, Ph.D. ITU-T SG 17 Q10 Rapporteur Martin Euchner SG 17 Advisor ITU Workshop on "Future Trust and Knowledge Infrastructure July 1 2016 Contents
Oracle Banking Digital Experience
 Oracle Banking Digital Experience US Originations Checking Account User Manual Release 17.1.0.0.0 Part No. E83887-01 March 2017 US Originations Checking Account User Manual March 2017 Oracle Financial
Oracle Banking Digital Experience US Originations Checking Account User Manual Release 17.1.0.0.0 Part No. E83887-01 March 2017 US Originations Checking Account User Manual March 2017 Oracle Financial
Introduction of the Identity Assurance Framework. Defining the framework and its goals
 Introduction of the Identity Assurance Framework Defining the framework and its goals 1 IAEG Charter Formed in August of 07 to develop a global standard framework and necessary support programs for validating
Introduction of the Identity Assurance Framework Defining the framework and its goals 1 IAEG Charter Formed in August of 07 to develop a global standard framework and necessary support programs for validating
ORC ECA Subscriber Instructions for Individual Identity and Encryption Certificates
 ORC ECA Subscriber Instructions for Individual Identity and Encryption Certificates Getting Prepared Print these instructions for easy reference. (Note: this is a good test to see that you are able to
ORC ECA Subscriber Instructions for Individual Identity and Encryption Certificates Getting Prepared Print these instructions for easy reference. (Note: this is a good test to see that you are able to
Better Privacy Through Identity Management:
 Better Privacy Through Identity Management: Report of the Identity Theft Prevention and Identity Management Standards Panel (IDSP) Presented By: Jim McCabe Director, Consumer Relations and IDSP American
Better Privacy Through Identity Management: Report of the Identity Theft Prevention and Identity Management Standards Panel (IDSP) Presented By: Jim McCabe Director, Consumer Relations and IDSP American
nanopay Privacy Notice and Policy
 Last Updated: November 28, 2018 1. Executive Summary nanopay Privacy Notice and Policy This privacy notice and privacy policy ( Notice or Notice and Privacy Policy ) sets forth the manner in which the
Last Updated: November 28, 2018 1. Executive Summary nanopay Privacy Notice and Policy This privacy notice and privacy policy ( Notice or Notice and Privacy Policy ) sets forth the manner in which the
Electronic Authentication Steps for Accessing EvaluationWeb
 Electronic Authentication Steps for Accessing EvaluationWeb Before EvaluationWeb access is granted, all persons requesting access must be e-authenticated (identity proofed) via the CDC s Secure Access
Electronic Authentication Steps for Accessing EvaluationWeb Before EvaluationWeb access is granted, all persons requesting access must be e-authenticated (identity proofed) via the CDC s Secure Access
Fraud Mobility: Exploitation Patterns and Insights
 WHITEPAPER Fraud Mobility: Exploitation Patterns and Insights September 2015 2 Table of Contents Introduction 3 Study Methodology 4 Once a SSN has been Compromised, it Remains at Risk 4 Victims Remain
WHITEPAPER Fraud Mobility: Exploitation Patterns and Insights September 2015 2 Table of Contents Introduction 3 Study Methodology 4 Once a SSN has been Compromised, it Remains at Risk 4 Victims Remain
Authentication Work stream FIGI Security Infrastructure and Trust Working Group. Abbie Barbir, Chair
 Authentication Work stream FIGI Security Infrastructure and Trust Working Group Abbie Barbir, Chair Security, Infrastructure, Trust Working Group To enhance confidence in using Digital Financial Services
Authentication Work stream FIGI Security Infrastructure and Trust Working Group Abbie Barbir, Chair Security, Infrastructure, Trust Working Group To enhance confidence in using Digital Financial Services
Please provide us with your current information below. Your personal information is required in order for us to properly process your dispute.
 Consumer Dispute In accordance with FCRA guidelines, your dispute investigation will be completed within thirty days. A Trusted Employees representative will contact you if we require further information
Consumer Dispute In accordance with FCRA guidelines, your dispute investigation will be completed within thirty days. A Trusted Employees representative will contact you if we require further information
Red Flags/Identity Theft Prevention Policy: Purpose
 Red Flags/Identity Theft Prevention Policy: 200.3 Purpose Employees and students depend on Morehouse College ( Morehouse ) to properly protect their personal non-public information, which is gathered and
Red Flags/Identity Theft Prevention Policy: 200.3 Purpose Employees and students depend on Morehouse College ( Morehouse ) to properly protect their personal non-public information, which is gathered and
CENTRAL INTAKE. AES Central Intake User Guide. AES University Manual. Adaptive Enterprise Solutions
 CENTRAL INTAKE AES Central Intake User Guide AES University Manual Adaptive Enterprise Solutions 8401 Colesville Road Suite 450 Silver Spring, MD 20910 800.237.9785 Toll Free 301.589.3434 Voice 301.589.9254
CENTRAL INTAKE AES Central Intake User Guide AES University Manual Adaptive Enterprise Solutions 8401 Colesville Road Suite 450 Silver Spring, MD 20910 800.237.9785 Toll Free 301.589.3434 Voice 301.589.9254
PREVENTION WEB CIVIL CITATION PROGRAM REGISTRATION WIZARD. A JJIS User Guide
 PREVENTION WEB CIVIL CITATION PROGRAM REGISTRATION WIZARD A JJIS User Guide Table of Contents Overview... 2 Logging in to Prevention Web... 2 Program Registration Wizard Youth Search... 3 Program Registration
PREVENTION WEB CIVIL CITATION PROGRAM REGISTRATION WIZARD A JJIS User Guide Table of Contents Overview... 2 Logging in to Prevention Web... 2 Program Registration Wizard Youth Search... 3 Program Registration
JOB AID: SINGLE STREAMLINED APPLICATION
 Your destination for affordable, quality health care, including Medi-Cal October 7, 2015 The Covered California Single Streamlined Application (SSA) supports all online applications, whether processed
Your destination for affordable, quality health care, including Medi-Cal October 7, 2015 The Covered California Single Streamlined Application (SSA) supports all online applications, whether processed
5LINX ID GUARD Product Overview. Credit/Presenter Goes Here
 5LINX ID GUARD Product Overview Credit/Presenter Goes Here Statistics According to the FTC approximately 11 million people were victims of identity theft in 2009. It s estimated that $221 billion a year
5LINX ID GUARD Product Overview Credit/Presenter Goes Here Statistics According to the FTC approximately 11 million people were victims of identity theft in 2009. It s estimated that $221 billion a year
Data Quality Blueprint for Pentaho: Better Data Leads to Better Results. Charles Gaddy Director Global Sales & Alliances, Melissa Data
 Data Quality Blueprint for Pentaho: Better Data Leads to Better Results Charles Gaddy Director Global Sales & Alliances, Melissa Data Agenda What is Data Quality, and What Role Does it Play? 6 Concepts
Data Quality Blueprint for Pentaho: Better Data Leads to Better Results Charles Gaddy Director Global Sales & Alliances, Melissa Data Agenda What is Data Quality, and What Role Does it Play? 6 Concepts
Emergency Compliance DG Special Case DAMA INDIANA
 1 Emergency Compliance DG Special Case DAMA INDIANA Agenda 2 Overview of full-blown data governance (DG) program Emergency compliance with a specific regulation We'll use GDPR as an example What is GDPR
1 Emergency Compliance DG Special Case DAMA INDIANA Agenda 2 Overview of full-blown data governance (DG) program Emergency compliance with a specific regulation We'll use GDPR as an example What is GDPR
Breaches and Remediation
 Breaches and Remediation Ramona Oliver US Department of Labor Personally Identifiable Information Personally Identifiable Information (PII): Any information about an individual maintained by an agency,
Breaches and Remediation Ramona Oliver US Department of Labor Personally Identifiable Information Personally Identifiable Information (PII): Any information about an individual maintained by an agency,
Securing Federal Government Facilities A Primer on the Why, What and How of PIV Systems and PACS
 Securing Federal Government Facilities A Primer on the Why, What and How of PIV Systems and PACS Introduction The expectations and requirements on government contracts for safety and security projects
Securing Federal Government Facilities A Primer on the Why, What and How of PIV Systems and PACS Introduction The expectations and requirements on government contracts for safety and security projects
e-sign and TimeStamping
 e-sign and TimeStamping Dr. Balaji Rajendran Centre for Development of Advanced Computing (C-DAC) Bangalore Under the Aegis of Controller of Certifying Authorities (CCA) Government of India 1 Recent Developments:
e-sign and TimeStamping Dr. Balaji Rajendran Centre for Development of Advanced Computing (C-DAC) Bangalore Under the Aegis of Controller of Certifying Authorities (CCA) Government of India 1 Recent Developments:
