Forensic Examination On Windows And Android Devices To Acquire Skype Artefacts
|
|
|
- Marlene Dawson
- 6 years ago
- Views:
Transcription
1 Forensic Examination On Windows And Android Devices To Acquire Skype Artefacts Anjana.R M.Tech in Computer Science with Specialization in Cyber Forensics and Information Security ER&DCIIT, Trivandrum, Kerala, India Abstract -- Skype is one of the most popular VoIP application that specializes in providing video chat and voice calls from computers, tablets, and mobile devices via the Internet to other devices or telephones/smartphones. The method by which Skype transmits data over the internet and between clients has been frequently examined, to discover any potential data leaks. An area that has not received much attention is that of the local data stored on systems by Skype. This paper describes a forensic examination on Windows and Android devices and the acquisition of Skype related artecfacts. The study aims to recover information from user account, calls, messages, contacts, group chats, file transfers, voice mail, SMS etc. 1. INTRODUCTION Skype is a telecommunications application software product that specializes in providing video chat and voice calls from computers, tablets, and mobile devices via the Internet to other devices or telephones/smartphones. Users can also send instant messages, exchange files and images, send video messages, and create conference calls. Questions regarding the security of data sent and received between Skype clients are not uncommon, with a number of investigations being carried out to see what sort of data can be intercepted whilst it is being sent over a network. Although this is quite a popular area of investigation, much less research has been done into data stored locally on systems running the Skype client. Owing to the secrecy surrounding the network protocols used by Skype, and due to the encryption methods used both whilst transmitting data over a network and storing it on local systems, it is very difficult to intercept and utilise Skype data whilst it is being transmitted, or to even read some data stored locally on Skype-enabled computer systems. There are multiple reasons why this investigation is being conducted, the first of which is purely down to curiosity as to what sort of information Skype records, stores and uses. If we then consider the information that Skype is privy to such as the information required to create an account, which includes our address, forename, surname and date of birth it can be quite concerning to think that this personal information could be stored in an insecure manner. Although this is likely to be stored on Skype s secure servers, it is also possible that some of this data may be used by the Skype local client, which may mean that the data is stored locally on the user s computer, in a directory created by Skype. Although this may not seem like an issue to the majority of people, it is likely to be much easier for an unscrupulous individual to gain access to someone s personal computer and take this information from there, rather than accessing Skype s servers, especially if the locally stored information is stored in plaintext and not encrypted or hidden in any way. The results of this investigation may be used for three key reasons. Firstly, the information found will be used to assist in the development of a software tool that will automatically gather any useful artefacts left behind by Skype on local systems. This could then be used to aid in the investigation of hard drives that may have been seized by authorities, from someone accused of committing some form of illegal activity. 2. RELATED WORKS Mohammed I. Al-Saleh in his paper Skype Forensics in Android Devices [1], investigates the artefacts of Skype calls and chats in the Android devices. This paper inspects both the RAM and NAND flash memories in different scenarios and time durations. Even though Skype provides secure communications over the Internet, this paper shows that Skype call and chat evidences can be truly found in the devices. It aim at showing that Skype artefacts in the Android 105
2 systems can be utilized in digital forensics. It shows the searching of the dumps of both of the RAM and NAND flash memories for the artefacts of Skype calls and chats. Igor Mikhaylov in the article, Extracting Evidence from Destroyed Skype Logs and Cleared SQLite Databases, describes common approaches used for the recovery of cleared Skype histories and deleted chat logs, and discusses methods and techniques for recovering evidence from cleared and damaged SQLite databases. This article represents methods and techniques used by forensic specialists to handle evidence contained in cleared Skype histories and deleted SQLite databases, particularly those located on formatted or repartitioned hard drives or discovered in the computer s volatile memory. Dodge addresses the topic of locally stored Skype data in his paper Skype Fingerprint but, although the findings are detailed, this investigation was carried out before Microsoft acquired Skype in 2011[7]. Microsoft s acquisition of Skype brought along a myriad of changes to the Skype client, including the method by which Skype stores data locally on computer systems. Much like this paper, Dodge s paper focuses on; an analysis of the information that can be gleaned from a Skype installation and use on a client system. (Dodge, 2008). All in all, Dodge s paper does a good job of detailing the discoveries he made and the processes by which he made these discoveries. Despite the fact that some of the results in this paper are relatively irrelevant in the current version of Skype (such as files that no longer exist), the locations in which a lot of his results appeared are still the same today, so these locations may still be a useful source of information. The only issue to be raised, is the method by which Dodge manufactures the Skype clients he examines. 3. EXAMINATION ON WINDOWS DEVICES With Windows being the most popular operating system in use today, the primary operating system examined within this investigation will be a recent version of Windows. Also, Microsoft owning Skype added to the appeal of using Windows as the primary operating system for this investigation. The first step of the examination on Windows was to search through the most common areas in which Windows stores application data. Firstly, the Program Files and Program Files (x86) folders were examined in an attempt to locate the Skype install files. Once located, within C:\Program Files (x86)\skype, these files were examined for any potentially useful data[7]. Although a large number of programs store the majority of their application data within their Program Files folders, in the case of Skype, the files contained within this directory were used purely for the execution of the Skype application. The only files within this location were desktop.iniǁ, which points to the icon file that should be used by the desktop shortcut, and a simple text file entitled third-party_attributions which provides copyright information for certain elements within Skype. The files contained within the subdirectories were the executable file for the Skype update program and the Skype application itself, along with an archive entitled login, which contains data such as emoticon images and different languages that can be used by the application. As the data stored within Program Files did not prove useful, the next location to be examined was the AppData folder, stored within Windows user directories. In this particular case, the full folder path was C:\Users\Daniel\AppData. Once in the AppData folder, the subdirectories of Local, LocalLow and Roaming were to be examined for any Skype data. There was a Skype directory found within Local and Roaming. The directory within Local simply contains a subdirectory entitled Apps. Within this directory, is another, entitled login, along with an.md5 file, also entitled login. The login directory seems to contain the data extracted from the login archive found previously. The.md5 file simply contains the md5 hash value (or the fingerprint) for the original archive. The Skype data stored within the Roaming directory is by far the most important. Within this directory there are a number of subdirectories, along with three individual files. The majority of the subdirectories, along with the individual files, do not seem to hold much in the way of useful information. The one useful directory here is the one that uses a Skype username as the title. Within the Skype user directory, there are a myriad of subdirectories and individual files. The first directory of interest was the chatsync folder. Within this folder, there appears a varying number of folders, each with a two character long name, that seems to be a mix of letters and numbers. Although some of these directories contain no data, the ones that do contain information are extremely useful. By opening the.dat files found within these folders in Notepad++ we can see encoded data. But while properly analysing these files we can see plaintext in places between the encoded data. This plaintext data seems to consist of the conversation history between
3 any users that were part of a Skype call or instant messaging session at that particular time. Browsing through the remaining directories within the Skype user folder does not present any useful data as the majority of the directories were either empty, or the files that were found tended to be encoded. The config.xml file also contains a list of all video input devices connected to the system, along with any audio input/output devices connected. This list not only shows that there are devices present, but also gives the make and model of each device, provided that that information is available to the system itself. The devices listed here do not always have to be physical. The final file found that contains useful information is by far the most useful. The main.db file, found within the Skype user folder, is a SQLite database file and thus must be opened within a SQLite database editor to be viewed[3]. In this investigation, the tool used was SQLite Browser. Within this database file, an extensive amount of data is stored. Although a number of sections of the database do not hold much useful data, others hold plenty. The first section containing detailed information is the Videos table. Within this table, there is a record of each time a video stream was initiated. Not only does this file identify when a video stream was initiated, it also identifies a device ID for the device used, and if the video session was a video conversation or a screen sharing session. In the cases where it was a screen sharing session, the dimensions of the screen shared is also recorded, although this is only the case when the user being examined has broadcast their screen, rather than viewing another user s screen. The next useful table is that of the CallMembers table. Within this table, a record is kept of each of the calls the user has been a part of, along with the username and display name of the users with whom the call was initiated. Skype also keeps a record of the duration of the call, but the timeframe used is not specified. The logical assumption for the timeframe would be that of seconds, but this cannot be guaranteed. Finally, the CallMembers table also keeps a record of the IP address of the other participants of the recorded conversations. The Conversations table contains similar information to that already seen in previous tables, but it also has the added record of the username and display name of anyone that the current user has been in conversations with, even if they are not on one another s contact lists. The VideoMessages table is only populated if a video message is recorded and sent to someone using the built in Skype function. If a video has been sent from the account being examined, there is no record of the user to whom it was sent, just a confirmation that it was sent from the user account in question. If a video has been received, the username for the user that sent the video is displayed. Within this table, there are two sections that are most important, the first of which is vod_path. Within this column, a URL is stored that, when copied into a web browser, displays an online version of the video sent or received. Although this is useful, testing showed that this link is only valid for around 24 hours, after which it is no longer available. The other useful column is local_path which, as the name suggests, provides the local path for any video messages sent from the computer being examined. The Contacts table presents a list of all the contacts within the current user s address book. The table presents both the display name and Skype username for each user. The majority of the rest of the information displayed here is dependent on the information that each user has entered into their Skype account details. If it has been entered, the data recorded in here includes each user s birth date, gender, spoken language, country, province, city, home telephone number, mobile telephone number and a link to any associated websites. Although the majority of this information is viewable on the user in question s profile, it is only viewable by people that have been approved by the user. If an unscrupulous individual were able to gain access to all of the above information, the potential consequences could be disastrous for the target individual. The Calls table displays a history of calls that the current user has been involved in. The list keeps a record of the identity of the user hosting the call, as well as other users involved with that particular call. Another potentially useful table is the Transfers table. As the name suggests, this table keeps a record of every file transfer made between users, including a record of who the sending/receiving party was, the local file path for where the document was sent from or saved to, and the name of the file that was sent or received. Finally, the Messages table contains a record of the majority of messages sent and received via the Skype instant messaging function, along with the users who were involved with each message. Although the messages are stored individually rather than in conversations, the majority of them are easy to read and to follow on from. 4. EXAMINATION OF ANDROID DEVICES The first Android device to be examined was the Samsung Galaxy S3, with full root permissions. The first stage of this examination was to simply use a file explorer application freely available on the Google Play Store. In this case, the application used was ES File Explorer. Upon opening the application navigating to
4 the root directory, or /, shows the directory structure used by Android. By simply browsing through the first few directories, a number of files are encountered that are key for the functioning of Android, empty folders and configuration files. Upon entering the data directory, a number of directories are located with the word app in the title, hinting that these folders may contain application data. This suspicion is confirmed by entering the very first Bridge application, the adb pull command was utilised to make an exact copy of the Skype application package file. The full command used was; adb pull /data/app/com.skype.raider-1.apk[4]. Once the file had been copied, the aim was to examine the files contained within the package to identify something that defined where the Skype data would be stored. By utilising the program 7zip s extract archive feature, access was gained to a number of different files from within the original.apk file[8]. A lot of these files were image files of emoticons and other images that users can send whilst using Skype. The file that was most intriguing was the AndroidManifest.xml file stored in the root area of the file, as the name of the file gave the impression that this would be where a large number of the core settings would be declared, for use by the Android operating system. Upon opening this file in Notepad++, a relatively large amount of text is displayed, but the majority of it appears to be either encrypted or corrupt making the majority of the data available relatively useless as the majority of it is unreadable. Utilising APKTool, the com.skype.raider-1.apk file was fully decompiled. Although this seemed to produce less files than when they were extracted using 7zip, the missing files did not seem to have much relevance, as they appear to be files generated at compilation of the.apk file. Once decompiled, the AndroidManifest.xml file was once again opened in Notepad++. This time round, all of the data was in plaintext and organised correctly. By searching through the multitude of folders for the Skype package (com.skype.raider, as defined by the title of the.apk file located earlier), data stored and utilised by the Skype application can be found. At first glance, the directory structure for the Skype application files on Android looks different to that of the directory structure found during the Windows examination. This impression is given by the first set of directories presented when accessing the com.skype.raider directory. The directories displayed are app_webview, cache, files, lib and shared_prefs. Although the majority of these folders store encoded data, the files directory brings up a set of files and directories similar to that folder, simply entitled app. Within this folder, are the.apk files (installation files) for all user-installed applications on the device, including the installation package for Skype, entitled com.skype.raider-1.apk (the full application package name). At this point, the device was connected to a Windows computer system so that the Skype installation package could be extracted for investigation. Using the Android Debug found on a Windows system running Skype. Although not all the directories found on the Windows version of Skype can be found on the Android version, the one that contained the most useful artefacts was still present. 5. CONCLUSION Owing to the secrecy surrounding the network protocols used by Skype, and due to the encryption methods used both whilst transmitting data over a network and storing it on local systems, it is very difficult to intercept and utilise Skype data whilst it is being transmitted, or to even read some data stored locally on Skype-enabled computer systems. The main aim of this paper is to demonstrate the examination of Windows and Android Devices for Skype related artefacts. The system is examined to recover information from user account, calls, messages, contacts, group chats, file transfers, voice mail, SMS etc. 6. REFERENCES 1. Mohammed I. Al-Saleh, Skype Forensics in Android Devices, Anderson, B. (2013). Android News for Costa Rica, Understanding the Android File Hierarchy Creutzburg, R. Kröger, K. Meißner, T. (2013). Client-side Skype Forensics An Overview. 4. Android. (Unknown A). Android Developers, Android Debug Bridge.- html 5. Anon. (2010). Skype IT Administrators Guide, Skype for Windows version 4.2. [Online]. Available at: uides/skype-itadministratorsguide.pdf 6. Matthew Simon and Jill Slay, What are you looking for: Identification of Remnant Communication Artefacts in Physical Memory, Dodge, R C. (2008). Skype Fingerprint, 1
5 (1) pp. 1-6 IEEE Xplore [Online]. Available at: sp? 8. Tumbleson, C. (Unknown). Android-APKTool, Project Home. Available at: 109
FORENSIC ANALYSIS OF WECHAT
 FORENSIC ANALYSIS OF WECHAT ON ANDROID SMARTPHONES Songyang Wu, Yong Zhang, Xupeng Wang, Xiong Xiong*, Lin Du Presented: Negamiye Arlene 2017 Nov 6th Content Introduction Related Works WeChat Forensics
FORENSIC ANALYSIS OF WECHAT ON ANDROID SMARTPHONES Songyang Wu, Yong Zhang, Xupeng Wang, Xiong Xiong*, Lin Du Presented: Negamiye Arlene 2017 Nov 6th Content Introduction Related Works WeChat Forensics
11/1/2018 Application Forensics
 11/1/2018 Application Forensics Eric Swisher Vashaad Fincher Tracey MacLeavy Application Forensics Computer Forensics is the practice of collecting, analyzing and reporting on digital data in a way that
11/1/2018 Application Forensics Eric Swisher Vashaad Fincher Tracey MacLeavy Application Forensics Computer Forensics is the practice of collecting, analyzing and reporting on digital data in a way that
Android Forensics: Simplifying Cell Phone Examinations
 Android Forensics: Simplifying Cell Phone Examinations Jeff Lessard, Gary Kessler 2010 Presented By: Manaf Bin Yahya Outlines Introduction Mobile Forensics Physical analysis Logical analysis CelleBrite
Android Forensics: Simplifying Cell Phone Examinations Jeff Lessard, Gary Kessler 2010 Presented By: Manaf Bin Yahya Outlines Introduction Mobile Forensics Physical analysis Logical analysis CelleBrite
Unified Meeting 5 User Guide for Windows
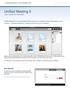 Unified Meeting 5 User Guide for Windows Unified Meeting 5 is a web based tool that puts you in complete control of all aspects of your meeting including scheduling, managing and securing your meetings.
Unified Meeting 5 User Guide for Windows Unified Meeting 5 is a web based tool that puts you in complete control of all aspects of your meeting including scheduling, managing and securing your meetings.
Evolutionary Genetics
 Evolutionary Genetics LV 25600-01 Lecture with exercises 6KP Extension 1 Unleash Linux Ubuntu on Windows Jean-Claude Walser jean-claude.walser@env.ethz.ch HS2018 2 The following slides to install, run,
Evolutionary Genetics LV 25600-01 Lecture with exercises 6KP Extension 1 Unleash Linux Ubuntu on Windows Jean-Claude Walser jean-claude.walser@env.ethz.ch HS2018 2 The following slides to install, run,
Unified Meeting 5. connecting customers, colleagues and suppliers. Real-time communication. we are
 Unified Meeting 5 Daisy Audio and Web Conferencing User Guide Real-time communication connecting customers, colleagues and suppliers What is Unified Meeting 5 Enhance your communication and make meetings
Unified Meeting 5 Daisy Audio and Web Conferencing User Guide Real-time communication connecting customers, colleagues and suppliers What is Unified Meeting 5 Enhance your communication and make meetings
Installing and configuring an Android device emulator. EntwicklerCamp 2012
 Installing and configuring an Android device emulator EntwicklerCamp 2012 Page 1 of 29 Table of Contents Lab objectives...3 Time estimate...3 Prerequisites...3 Getting started...3 Setting up the device
Installing and configuring an Android device emulator EntwicklerCamp 2012 Page 1 of 29 Table of Contents Lab objectives...3 Time estimate...3 Prerequisites...3 Getting started...3 Setting up the device
Learn about the latest offerings in Adobe Connect. This article summarizes the new features and enhancements.
 Adobe Connect 9.7 Release Notes Learn about the latest offerings in Adobe Connect. This article summarizes the new features and enhancements. Adobe Connect is a web conferencing solution for web meetings,
Adobe Connect 9.7 Release Notes Learn about the latest offerings in Adobe Connect. This article summarizes the new features and enhancements. Adobe Connect is a web conferencing solution for web meetings,
Remote Support. User Guide 7.23
 Remote Support User Guide 7.23 Copyright 1997 2011 Cisco and/or its affiliates. All rights reserved. WEBEX, CISCO, Cisco WebEx, the CISCO logo, and the Cisco WebEx logo are trademarks or registered trademarks
Remote Support User Guide 7.23 Copyright 1997 2011 Cisco and/or its affiliates. All rights reserved. WEBEX, CISCO, Cisco WebEx, the CISCO logo, and the Cisco WebEx logo are trademarks or registered trademarks
Unified Meeting 5 User Guide for MAC
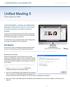 Unified Meeting 5 User Guide for MAC Unified Meeting 5, a meeting and collaboration application enhances the way you communicate by making meetings convenient and easy to manage. It improves your meeting
Unified Meeting 5 User Guide for MAC Unified Meeting 5, a meeting and collaboration application enhances the way you communicate by making meetings convenient and easy to manage. It improves your meeting
Blackboard 5 Level One Student Manual
 Blackboard 5 Level One Student Manual Blackboard, Inc. 1899 L Street NW 5 th Floor Washington DC 20036 Copyright 2000 by Blackboard Inc. All rights reserved. No part of the contents of this manual may
Blackboard 5 Level One Student Manual Blackboard, Inc. 1899 L Street NW 5 th Floor Washington DC 20036 Copyright 2000 by Blackboard Inc. All rights reserved. No part of the contents of this manual may
Getting Started with Cisco Pulse
 CHAPTER 2 These topics describe what you need know when initially logging into Cisco Pulse. Client and Browser Requirements, page 2-1 Logging Into Cisco Pulse, page 2-2 Getting Familiar with Your Home
CHAPTER 2 These topics describe what you need know when initially logging into Cisco Pulse. Client and Browser Requirements, page 2-1 Logging Into Cisco Pulse, page 2-2 Getting Familiar with Your Home
An aid to Forensic by preserving Skype evidences to present it in front of court of law
 An aid to Forensic by preserving Skype evidences to present it in front of court of law Vijay Chauhan 1, Dinesh S. Katre 2 1 PG Student, Network Security, Gtu Pg School, Ahmedabad, Gujarat, India 2 Associate
An aid to Forensic by preserving Skype evidences to present it in front of court of law Vijay Chauhan 1, Dinesh S. Katre 2 1 PG Student, Network Security, Gtu Pg School, Ahmedabad, Gujarat, India 2 Associate
Android Forensics: Investigation, Analysis And Mobile Security For Google Android PDF
 Android Forensics: Investigation, Analysis And Mobile Security For Google Android PDF Android Forensics: Investigation, Analysis, and Mobile Security for Google Android examines the Android mobile platform
Android Forensics: Investigation, Analysis And Mobile Security For Google Android PDF Android Forensics: Investigation, Analysis, and Mobile Security for Google Android examines the Android mobile platform
Blackboard 5. Instructor Manual Level One Release 5.5
 Bringing Education Online Blackboard 5 Instructor Manual Level One Release 5.5 Copyright 2001 by Blackboard Inc. All rights reserved. No part of the contents of this manual may be reproduced or transmitted
Bringing Education Online Blackboard 5 Instructor Manual Level One Release 5.5 Copyright 2001 by Blackboard Inc. All rights reserved. No part of the contents of this manual may be reproduced or transmitted
CNIT 121: Computer Forensics. 14 Investigating Applications
 CNIT 121: Computer Forensics 14 Investigating Applications Applications Not part of the operating system User applications Internet browsers, email clients, office suites, chat programs, and more Service
CNIT 121: Computer Forensics 14 Investigating Applications Applications Not part of the operating system User applications Internet browsers, email clients, office suites, chat programs, and more Service
IT Training Services. SharePoint 2013 Getting Started. Version: 2015/2016 V1
 IT Training Services SharePoint 2013 Getting Started Version: 2015/2016 V1 Table of Contents ACCESSING SHAREPOINT SITE 1 IT Intranet SharePoint Site... 1 Create a SubSite... 1 DOCUMENT LIBRARIES 2 Create
IT Training Services SharePoint 2013 Getting Started Version: 2015/2016 V1 Table of Contents ACCESSING SHAREPOINT SITE 1 IT Intranet SharePoint Site... 1 Create a SubSite... 1 DOCUMENT LIBRARIES 2 Create
and the Forensic Science CC Spring 2007 Prof. Nehru
 and the Introduction The Internet, (Information superhighway), has opened a medium for people to communicate and to access millions of pieces of information from computers located anywhere on the globe.
and the Introduction The Internet, (Information superhighway), has opened a medium for people to communicate and to access millions of pieces of information from computers located anywhere on the globe.
An overview of Moodle blocks
 An overview of Moodle blocks Academic Advisers When you click on the link in the Academic Advisers block it will display information about the students enrolled on your current Moodle course. You can change
An overview of Moodle blocks Academic Advisers When you click on the link in the Academic Advisers block it will display information about the students enrolled on your current Moodle course. You can change
Vodafone One Net app Quick Start Guide For Android phone
 Vodafone One Net app Quick Start Guide For Android phone Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Logging out 2 Changing display
Vodafone One Net app Quick Start Guide For Android phone Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Logging out 2 Changing display
Vodafone One Net app Quick Start Guide For PC
 Vodafone One Net app Quick Start Guide For PC Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Starting the One Net app when you turn
Vodafone One Net app Quick Start Guide For PC Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Starting the One Net app when you turn
Using the Mobile App for Defense Connect Online
 Using the Mobile App for Defense Connect Online Conduct and Attend Meetings Virtually Anywhere AUTHOR Aaron W Wolf DCO Evangelist Carahsoft Technology Corp. 703.889.9781 aaron.w.wolf@carahsoft.com Defense
Using the Mobile App for Defense Connect Online Conduct and Attend Meetings Virtually Anywhere AUTHOR Aaron W Wolf DCO Evangelist Carahsoft Technology Corp. 703.889.9781 aaron.w.wolf@carahsoft.com Defense
Xton Access Manager GETTING STARTED GUIDE
 Xton Access Manager GETTING STARTED GUIDE XTON TECHNOLOGIES, LLC PHILADELPHIA Copyright 2017. Xton Technologies LLC. Contents Introduction... 2 Technical Support... 2 What is Xton Access Manager?... 3
Xton Access Manager GETTING STARTED GUIDE XTON TECHNOLOGIES, LLC PHILADELPHIA Copyright 2017. Xton Technologies LLC. Contents Introduction... 2 Technical Support... 2 What is Xton Access Manager?... 3
User documentation. BEEM v1.0 January 2010
 User documentation BEEM v1.0 January 2010 1 Table of contents Table of contents... 2 About this paper... 3 Using this manual... 3 Navigation keys... 4 Conventions... 5 Support... 5 Installation/Uninstallation...
User documentation BEEM v1.0 January 2010 1 Table of contents Table of contents... 2 About this paper... 3 Using this manual... 3 Navigation keys... 4 Conventions... 5 Support... 5 Installation/Uninstallation...
Belkasoft Evidence Center 2018 ESSENTIALS TRAINING PROGRAM
 Belkasoft Evidence Center 2018 ESSENTIALS TRAINING PROGRAM INTRODUCTION Belkasoft Essentials is intended for investigators of any level of expertise who want to acquire hands-on skills in computer, mobile
Belkasoft Evidence Center 2018 ESSENTIALS TRAINING PROGRAM INTRODUCTION Belkasoft Essentials is intended for investigators of any level of expertise who want to acquire hands-on skills in computer, mobile
Obtaining the LDAP Search string (Distinguished Name)?
 How to Configure LDAP Sync with the Altium Vault Old Content - see latest equivalent Modified by Jason Howie on 31-May-2017 An LDAP Sync allows the administrator of an Altium Vault to leverage the network
How to Configure LDAP Sync with the Altium Vault Old Content - see latest equivalent Modified by Jason Howie on 31-May-2017 An LDAP Sync allows the administrator of an Altium Vault to leverage the network
Exactly User Guide. Contact information. GitHub repository. Download pages for application. Version
 Exactly User Guide Version 0.1 2016 01 11 Contact information AVPreserve http://www.avpreserve.com/ GitHub repository https://github.com/avpreserve/uk exactly Download pages for application Windows https://www.avpreserve.com/wp
Exactly User Guide Version 0.1 2016 01 11 Contact information AVPreserve http://www.avpreserve.com/ GitHub repository https://github.com/avpreserve/uk exactly Download pages for application Windows https://www.avpreserve.com/wp
Vodafone One Net app Quick Start Guide For Android tablet
 Vodafone One Net app Quick Start Guide For Android tablet Power to you Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Logging out
Vodafone One Net app Quick Start Guide For Android tablet Power to you Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Logging out
Vodafone One Net app Quick Start Guide For Android tablet
 Vodafone One Net app Quick Start Guide For Android tablet Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Logging out 2 Changing display
Vodafone One Net app Quick Start Guide For Android tablet Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Logging out 2 Changing display
Vodafone One Net app Quick Start Guide For PC
 Vodafone One Net app Quick Start Guide For PC Power to you Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Starting the One Net app
Vodafone One Net app Quick Start Guide For PC Power to you Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Starting the One Net app
Table of Contents. Page 1
 Table of Contents Logging In... 2 Adding Your Google API Key... 2 Project List... 4 Save Project (For Re-Import)... 4 New Project... 6 NAME & KEYWORD TAB... 6 GOOGLE GEO TAB... 6 Search Results... 7 Import
Table of Contents Logging In... 2 Adding Your Google API Key... 2 Project List... 4 Save Project (For Re-Import)... 4 New Project... 6 NAME & KEYWORD TAB... 6 GOOGLE GEO TAB... 6 Search Results... 7 Import
WebEx New user Orientation. Meeting Organizer Guide
 WebEx New user Orientation Meeting Organizer Guide OBJECTIVE: AGENDA: I. II. III. IV. Utilize the tools provided at Kent State University to host and attend online meetings via the WebEx application and
WebEx New user Orientation Meeting Organizer Guide OBJECTIVE: AGENDA: I. II. III. IV. Utilize the tools provided at Kent State University to host and attend online meetings via the WebEx application and
Cisco WebEx Web Conferencing Productivity Tools for Instant Messengers
 Cisco WebEx Web Conferencing Productivity Tools for Instant Messengers Installing and Setting Up WebEx Productivity Tools For more information: In the U.S.: 800.374.2441 www.intercall.com info@intercall.com
Cisco WebEx Web Conferencing Productivity Tools for Instant Messengers Installing and Setting Up WebEx Productivity Tools For more information: In the U.S.: 800.374.2441 www.intercall.com info@intercall.com
KEEPOD QUICK USER GUIDE
 Keepod Quick User Guide - Page 0 KEEPOD QUICK USER GUIDE March 2015 Keepod Quick User Guide - Page 1 You now are officially a Keepoder and can now make use of all the benefits related to Keepod and personal
Keepod Quick User Guide - Page 0 KEEPOD QUICK USER GUIDE March 2015 Keepod Quick User Guide - Page 1 You now are officially a Keepoder and can now make use of all the benefits related to Keepod and personal
What is Skype for Business?
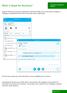 What is Skype for? Skype for is the secure collaboration tool that enables you to send instant messages to colleagues using NHSmail both inside and outside of your organisation The tool also provides you
What is Skype for? Skype for is the secure collaboration tool that enables you to send instant messages to colleagues using NHSmail both inside and outside of your organisation The tool also provides you
A Forensic Log File Extraction Tool for ICQ Instant Messaging Clients
 Edith Cowan University Research Online ECU Publications Pre. 2011 2006 A Forensic Log File Extraction Tool for ICQ Instant Messaging Clients Kim Morfitt Edith Cowan University Craig Valli Edith Cowan University
Edith Cowan University Research Online ECU Publications Pre. 2011 2006 A Forensic Log File Extraction Tool for ICQ Instant Messaging Clients Kim Morfitt Edith Cowan University Craig Valli Edith Cowan University
CALL MANAGER User Guide for Mac
 CALL MANAGER User Guide for Mac Call Manager, InterCall s free online meeting tool for our Reservationless-Plus audio service, is an application for your desktop available for download or to run in your
CALL MANAGER User Guide for Mac Call Manager, InterCall s free online meeting tool for our Reservationless-Plus audio service, is an application for your desktop available for download or to run in your
UNIFIED MEETING 5 DOWNLOAD AND SETUP
 UNIFIED MEETING 5 M A C U S E R G U I D E Unified Meeting 5, our meeting and collaboration application enhances the way you communicate by making meetings convenient and easy to manage. It improves your
UNIFIED MEETING 5 M A C U S E R G U I D E Unified Meeting 5, our meeting and collaboration application enhances the way you communicate by making meetings convenient and easy to manage. It improves your
Chapter 1. Configuring VPGO
 Chapter 1. Configuring VPGO The VPGO module is configured in the VISUAL PLANNING client. You can define as many VPGO templates as you need based on the three existing template types: Diary template Events
Chapter 1. Configuring VPGO The VPGO module is configured in the VISUAL PLANNING client. You can define as many VPGO templates as you need based on the three existing template types: Diary template Events
Analysis of a Vault App Michael Robinson 15 November 2015
 Michael Robinson 15 November 2015 Vault Apps On November 6, 2015 an article appeared in The New York Times regarding a sexting ring, which occurred at Cañon City High School in Colorado. The superintendent
Michael Robinson 15 November 2015 Vault Apps On November 6, 2015 an article appeared in The New York Times regarding a sexting ring, which occurred at Cañon City High School in Colorado. The superintendent
Building an ASP.NET Website
 In this book we are going to build a content-based ASP.NET website. This website will consist of a number of modules, which will all fit together to produce the finished product. We will build each module
In this book we are going to build a content-based ASP.NET website. This website will consist of a number of modules, which will all fit together to produce the finished product. We will build each module
V-CUBE Meeting User Manual
 V-CUBE Meeting User Manual 2. Preparing for Meetings V-cube, Inc. 2013 V-cube, Inc. All Rights Reserved. Revision history Revision date Details 2013/09/10 - Added a folder feature to the storage functionality
V-CUBE Meeting User Manual 2. Preparing for Meetings V-cube, Inc. 2013 V-cube, Inc. All Rights Reserved. Revision history Revision date Details 2013/09/10 - Added a folder feature to the storage functionality
BOLT eportfolio Student Guide
 BOLT eportfolio Student Guide Contents BOLT EPORTFOLIO STUDENT GUIDE... I BOLT EPORTFOLIO BASICS... 3 BOLT eportfolio user interface overview... 3 Dashboard... 3 My Items Page... 4 Explore Page... 5 Sharing
BOLT eportfolio Student Guide Contents BOLT EPORTFOLIO STUDENT GUIDE... I BOLT EPORTFOLIO BASICS... 3 BOLT eportfolio user interface overview... 3 Dashboard... 3 My Items Page... 4 Explore Page... 5 Sharing
InterCall Web Meeting
 InterCall Web Meeting Quick Reference Guide For more information: www.intercallapac.com Australia 1800 468 225 +61 2 8295 9000 InterCall Web Meeting offers a full-featured web conferencing service that
InterCall Web Meeting Quick Reference Guide For more information: www.intercallapac.com Australia 1800 468 225 +61 2 8295 9000 InterCall Web Meeting offers a full-featured web conferencing service that
Cisco WebEx Meeting Center Scheduling Guide
 Cisco WebEx Meeting Center Scheduling Guide Scheduling Tasks Australia 1800 468 225 +61 2 8295 9000 China 10800 650 0155 +852 3073 0418 Hong Kong 800 901 603 +852 3073 0418 India 000 800 650 1158 +61 2
Cisco WebEx Meeting Center Scheduling Guide Scheduling Tasks Australia 1800 468 225 +61 2 8295 9000 China 10800 650 0155 +852 3073 0418 Hong Kong 800 901 603 +852 3073 0418 India 000 800 650 1158 +61 2
SASKTEL INTEGRATED BUSINESS COMMUNICATIONS (IBC)
 SASKTEL INTEGRATED BUSINESS COMMUNICATIONS (IBC) DESKTOP CLIENT USER GUIDE Version 4 January 2018 TABLE OF CONTENTS About the SaskTel IBC Desktop Client...3 Requirements...3 How to download and install
SASKTEL INTEGRATED BUSINESS COMMUNICATIONS (IBC) DESKTOP CLIENT USER GUIDE Version 4 January 2018 TABLE OF CONTENTS About the SaskTel IBC Desktop Client...3 Requirements...3 How to download and install
Amazon WorkMail. User Guide Version 1.0
 Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
Searching for a contact in the Directory
 Searching for a contact in the Directory You may want to search for someone in the Directory to view their contact details or to add them to your personal contacts To search for a contact in the Directory:
Searching for a contact in the Directory You may want to search for someone in the Directory to view their contact details or to add them to your personal contacts To search for a contact in the Directory:
Vodafone One Net app Quick Start Guide For iphone
 Vodafone One Net app Quick Start Guide For iphone Power to you Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Logging out 2 Changing
Vodafone One Net app Quick Start Guide For iphone Power to you Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Logging out 2 Changing
GUJARAT TECHNOLOGICAL UNIVERSITY
 1. Learning Objectives: To be able to understand the process of developing software for the mobile To be able to create mobile applications on the Android Platform To be able to create mobile applications
1. Learning Objectives: To be able to understand the process of developing software for the mobile To be able to create mobile applications on the Android Platform To be able to create mobile applications
FREEWAY SIGNAGE series 9. user manual
 FREEWAY SIGNAGE series 9 user manual FREEWAY SIGNAGE series 9 Page 2 Table of Contents Overview...3 What is Digital Signage?...3 So what is FREEWAY SIGNAGE Series 9?...4 What can I display through my channel?...4
FREEWAY SIGNAGE series 9 user manual FREEWAY SIGNAGE series 9 Page 2 Table of Contents Overview...3 What is Digital Signage?...3 So what is FREEWAY SIGNAGE Series 9?...4 What can I display through my channel?...4
Introducing IBM Lotus Sametime 7.5 software.
 Real-time collaboration solutions March 2006 Introducing IBM Lotus Sametime 7.5 software. Adam Gartenberg Offering Manager, Real-time and Team Collaboration Page 2 Contents 2 Introduction 3 Enhanced instant
Real-time collaboration solutions March 2006 Introducing IBM Lotus Sametime 7.5 software. Adam Gartenberg Offering Manager, Real-time and Team Collaboration Page 2 Contents 2 Introduction 3 Enhanced instant
AccessData Forensic Toolkit Release Notes
 AccessData Forensic Toolkit 6.2.1 Release Notes Document Date: 4/24/2017 2017 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues
AccessData Forensic Toolkit 6.2.1 Release Notes Document Date: 4/24/2017 2017 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues
SchoolBooking LDAP Integration Guide
 SchoolBooking LDAP Integration Guide Before you start This guide has been written to help you configure SchoolBooking to connect to your LDAP server. Please treat this document as a reference guide, your
SchoolBooking LDAP Integration Guide Before you start This guide has been written to help you configure SchoolBooking to connect to your LDAP server. Please treat this document as a reference guide, your
Wimba Pronto. Version 2.1. User Guide
 Wimba Pronto Version 2.1 User Guide Wimba Pronto 2.1 User Guide Welcome to Wimba Pronto 1 What's New in Wimba Pronto? 2 Getting Started 3 Wimba Pronto System Requirements 3 Creating a New Wimba Pronto
Wimba Pronto Version 2.1 User Guide Wimba Pronto 2.1 User Guide Welcome to Wimba Pronto 1 What's New in Wimba Pronto? 2 Getting Started 3 Wimba Pronto System Requirements 3 Creating a New Wimba Pronto
Network Applications and Protocols
 Network Applications and Protocols VoIP (Voice over Internet Protocol) Voice over IP (VoIP) is a methodology and group of technologies for the delivery of voice communications and multimedia sessions over
Network Applications and Protocols VoIP (Voice over Internet Protocol) Voice over IP (VoIP) is a methodology and group of technologies for the delivery of voice communications and multimedia sessions over
eportfolio Support Guide
 eportfolio Support Guide D2L Services West Chester University of Pennsylvania www.wcupa.edu/d2l 610-436-3350, option 2 Anderson Hall, room 20 d2l@wcupa.edu v10.3 September 2014 1 CONTENTS EPortfolio Basics
eportfolio Support Guide D2L Services West Chester University of Pennsylvania www.wcupa.edu/d2l 610-436-3350, option 2 Anderson Hall, room 20 d2l@wcupa.edu v10.3 September 2014 1 CONTENTS EPortfolio Basics
Searching for Yahoo Chat fragments in Unallocated Space Detective Eric Oldenburg, Phoenix Police Department
 Searching for Yahoo Chat fragments in Unallocated Space Detective Eric Oldenburg, Phoenix Police Department Purpose and Goal To demonstrate a methodology used for locating Yahoo Instant Messenger chat
Searching for Yahoo Chat fragments in Unallocated Space Detective Eric Oldenburg, Phoenix Police Department Purpose and Goal To demonstrate a methodology used for locating Yahoo Instant Messenger chat
IBM Connections Cloud Meetings and Chat Features Guide. Imran Khan Adam Goodison IBM Collaboration Solutions, IBM Software Group, Mulhuddart, Ireland
 IBM Connections Cloud Meetings and Chat Features Guide Imran Khan Adam Goodison IBM Collaboration Solutions, IBM Software Group, Mulhuddart, Ireland Contents Introduction... 3 Meetings... 3 Starting a
IBM Connections Cloud Meetings and Chat Features Guide Imran Khan Adam Goodison IBM Collaboration Solutions, IBM Software Group, Mulhuddart, Ireland Contents Introduction... 3 Meetings... 3 Starting a
Android Forensics. Presented By: Mohamed Khaled. Thanks to: Ibrahim Mosaad Mohamed Shawky
 Android Forensics Presented By: Mohamed Khaled Thanks to: Ibrahim Mosaad Mohamed Shawky Agenda Mobile Forensic Process Different Mobile Forensic Scenario Acquisition Guide Challenges of Android Forensics
Android Forensics Presented By: Mohamed Khaled Thanks to: Ibrahim Mosaad Mohamed Shawky Agenda Mobile Forensic Process Different Mobile Forensic Scenario Acquisition Guide Challenges of Android Forensics
FirstClass and the NLC Intranet. Version 12
 FirstClass and the NLC Intranet Version 12 Date Modified 15/06/2016 Use of the FirstClass E-mail system Introduction Please read the following in conjunction with the Internet and E-mail Policies issued
FirstClass and the NLC Intranet Version 12 Date Modified 15/06/2016 Use of the FirstClass E-mail system Introduction Please read the following in conjunction with the Internet and E-mail Policies issued
SFB Mobile App For Android
 SFB Mobile App For Android UIT is not responsible for charges incurred when using the SFB mobile app on your smart phone. Contents SFB on a Mobile Device... 3 Install SFB... 3 Sign in to SFB... 3 Set Your
SFB Mobile App For Android UIT is not responsible for charges incurred when using the SFB mobile app on your smart phone. Contents SFB on a Mobile Device... 3 Install SFB... 3 Sign in to SFB... 3 Set Your
Going to Another Board from the Welcome Board. Conference Overview
 WebBoard for Users Going to Another Board from the Welcome Board Many WebBoard sites have more than one board, each with its own set of conferences and messages. When you click on Boards on the WebBoard
WebBoard for Users Going to Another Board from the Welcome Board Many WebBoard sites have more than one board, each with its own set of conferences and messages. When you click on Boards on the WebBoard
The collaboration app that keeps you connected to everyone and everything
 Data Sheet UC-One The collaboration app that keeps you connected to everyone and everything UC-One is a communications and collaboration Software as a Service (SaaS) for calling, messaging, and meeting
Data Sheet UC-One The collaboration app that keeps you connected to everyone and everything UC-One is a communications and collaboration Software as a Service (SaaS) for calling, messaging, and meeting
Vodacom One Net app Quick Start Guide For Mac
 Vodacom One Net app Quick Start Guide For Mac Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Logging out 2 Changing display language
Vodacom One Net app Quick Start Guide For Mac Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Logging out 2 Changing display language
Skype For Business(Windows) Getting Started
 Skype For Business(Windows) Getting Started This guide is for the Windows version of Skype for Business. What is Skype for Business? Skype for Business is a communication tool which allows you to interact
Skype For Business(Windows) Getting Started This guide is for the Windows version of Skype for Business. What is Skype for Business? Skype for Business is a communication tool which allows you to interact
Administrator s Guide
 Administrator s Guide (January 2017) Welcome! You have been invited to manage the subscriber community who will be using this videoconferencing service within your organization. This guide will provide
Administrator s Guide (January 2017) Welcome! You have been invited to manage the subscriber community who will be using this videoconferencing service within your organization. This guide will provide
Wimba Pronto. Version 3.1. User Guide
 Wimba Pronto Version 3.1 User Guide Wimba Pronto 3.1 User Guide Welcome to Wimba Pronto 1 Top Wimba Pronto Features 1 What's New in Wimba Pronto? 3 Getting Started 4 Wimba Pronto System Requirements 4
Wimba Pronto Version 3.1 User Guide Wimba Pronto 3.1 User Guide Welcome to Wimba Pronto 1 Top Wimba Pronto Features 1 What's New in Wimba Pronto? 3 Getting Started 4 Wimba Pronto System Requirements 4
AUDIO WITH DATA. User Guide
 User Guide WELCOME TO AUDIO WITH DATA Audio With Data is your perfect everyday business conferencing tool. The award-winning technology integrates fully-automated voice conferencing with easy-to-use web
User Guide WELCOME TO AUDIO WITH DATA Audio With Data is your perfect everyday business conferencing tool. The award-winning technology integrates fully-automated voice conferencing with easy-to-use web
Using Adobe Acrobat College. How to Host a Meeting - User s Guide
 Note: For the purpose of consistency between the Hunter College written and web documentation and the Adobe Connect pro Software terminology, we will use meeting to represent a virtual class session, host
Note: For the purpose of consistency between the Hunter College written and web documentation and the Adobe Connect pro Software terminology, we will use meeting to represent a virtual class session, host
USER MANUAL. MageMob App Builder TABLE OF CONTENTS. Version: 2.0.0
 USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of MageMob App Builder... 1 Installation & Activation... 2 Installation Steps... 2 Extension Activation... 3 How it Works?... 4 Back End Configuration:...
USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of MageMob App Builder... 1 Installation & Activation... 2 Installation Steps... 2 Extension Activation... 3 How it Works?... 4 Back End Configuration:...
Responsive Web Design Discover, Consider, Decide
 Responsive Web Design Discover, Consider, Decide Responsive Web Design. Discover, Consider, Decide Q. What is Responsive Design? A. Responsive design is a general mindset where you are designing a website,
Responsive Web Design Discover, Consider, Decide Responsive Web Design. Discover, Consider, Decide Q. What is Responsive Design? A. Responsive design is a general mindset where you are designing a website,
Online Demo Guide. Barracuda PST Enterprise. Introduction (Start of Demo) Logging into the PST Enterprise
 Online Demo Guide Barracuda PST Enterprise This script provides an overview of the main features of PST Enterprise, covering: 1. Logging in to PST Enterprise 2. Client Configuration 3. Global Configuration
Online Demo Guide Barracuda PST Enterprise This script provides an overview of the main features of PST Enterprise, covering: 1. Logging in to PST Enterprise 2. Client Configuration 3. Global Configuration
ALTIRIS Console 6.5 Overview
 ALTIRIS Console 6.5 Overview Document Version: 1.0 The information contained in the Altiris Knowledgebase is subject to the Terms of Use as outlined at http://www.altiris.com/legal/termsofuse.asp. History
ALTIRIS Console 6.5 Overview Document Version: 1.0 The information contained in the Altiris Knowledgebase is subject to the Terms of Use as outlined at http://www.altiris.com/legal/termsofuse.asp. History
ACCESSDATA FTK RELEASE NOTES
 ACCESSDATA FTK 3.3.0 RELEASE NOTES INTRODUCTION This document provides important information relative to the use of FTK 3.3.0. IMPORTANT INFORMATION If the machine running Imager or FTK has an active internet
ACCESSDATA FTK 3.3.0 RELEASE NOTES INTRODUCTION This document provides important information relative to the use of FTK 3.3.0. IMPORTANT INFORMATION If the machine running Imager or FTK has an active internet
Windows 10. By Graham
 Windows 10 By Graham This is a presentation to show you the basic structure of Windows 10. There have been many versions of Windows since the mid- 80 s when Microsoft decided to copy a version of frontend
Windows 10 By Graham This is a presentation to show you the basic structure of Windows 10. There have been many versions of Windows since the mid- 80 s when Microsoft decided to copy a version of frontend
AccessData AD Lab Release Notes
 AccessData AD Lab 6.2.1 Release Notes Document Date: 4/24/2017 2017 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues for this
AccessData AD Lab 6.2.1 Release Notes Document Date: 4/24/2017 2017 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues for this
How to Use Skype & Pamela Software to Record Your Podcast
 How to Use Skype & Pamela Software to Record Your Podcast Network 3000 Publishing 2014 1 Table of Contents Introduction...3 What is Skype?...3 The Popularity of Skype...4 What is Pamela?...4 Time to Get
How to Use Skype & Pamela Software to Record Your Podcast Network 3000 Publishing 2014 1 Table of Contents Introduction...3 What is Skype?...3 The Popularity of Skype...4 What is Pamela?...4 Time to Get
OpenEarth OpenEarthTools = Open source management of Data, Models and Tools for marine & coastal science & technology
 OpenEarth OpenEarthTools = Open source management of Data, Models and Tools for marine & coastal science & technology.. and what about What is OpenEarth: philosophy 1. philosophy 2. community 3. repository
OpenEarth OpenEarthTools = Open source management of Data, Models and Tools for marine & coastal science & technology.. and what about What is OpenEarth: philosophy 1. philosophy 2. community 3. repository
bla bla Groupware Compact Guide
 bla bla Groupware Compact Guide Groupware Groupware: Compact Guide Publication date Friday, 01. June 2018 Version 7.10.0 Copyright 2016-2018 This document is the intellectual property of OX Software GmbH
bla bla Groupware Compact Guide Groupware Groupware: Compact Guide Publication date Friday, 01. June 2018 Version 7.10.0 Copyright 2016-2018 This document is the intellectual property of OX Software GmbH
TomTom GPS Device Forensics
 TomTom GPS Device Forensics Written by Ben LeMere & Andy Sayers For more information visit GPSForensics.org blemere@gpsforensics.org asayers@gpsforensics.org Introduction: The sales of portable navigation
TomTom GPS Device Forensics Written by Ben LeMere & Andy Sayers For more information visit GPSForensics.org blemere@gpsforensics.org asayers@gpsforensics.org Introduction: The sales of portable navigation
Matt Danner Flashback Data
 Preservation Strategies and Data Collection from a Forensic Expert's Point of View Best practices on executing preservation and administering collection protocols with emphasis on forensically sound methods
Preservation Strategies and Data Collection from a Forensic Expert's Point of View Best practices on executing preservation and administering collection protocols with emphasis on forensically sound methods
Virtual Communications Express User Guide Mobile for iphone
 User Guide Mobile for iphone Feature Overview By adding Virtual Communications Express Mobile to an ios platform, you can leverage a convenient and intuitive interface for mobile calling services. Calls
User Guide Mobile for iphone Feature Overview By adding Virtual Communications Express Mobile to an ios platform, you can leverage a convenient and intuitive interface for mobile calling services. Calls
Contents. Emma User Guide
 Emma User Guide Emma User Guide i Contents Getting Started with Emma... 2 Prerequisites... 2 Installation... 4 Installing Emma... 4 Uninstalling Emma... 4 Start and registration... 4 Starting Emma... 4
Emma User Guide Emma User Guide i Contents Getting Started with Emma... 2 Prerequisites... 2 Installation... 4 Installing Emma... 4 Uninstalling Emma... 4 Start and registration... 4 Starting Emma... 4
For more information about the Cisco Jabber suite of products, see https://www.cisco.com/go/jabber.
 About Cisco Jabber, page 1 Purpose of this Guide, page 1 Feature Configuration Overview, page 1 About Cisco Jabber Cisco Jabber is a suite of Unified Communications applications that allow seamless interaction
About Cisco Jabber, page 1 Purpose of this Guide, page 1 Feature Configuration Overview, page 1 About Cisco Jabber Cisco Jabber is a suite of Unified Communications applications that allow seamless interaction
SRV Canada VRS TM USER'S MANUAL for Mobile applications
 SRV Canada VRS TM USER'S MANUAL for Mobile applications Version 1.0 SRV Canada VRS User s Manual for Mobile devices Page 1 of 35 TABLE OF CONTENTS TABLE OF CONTENTS... 2 1 Welcome and About This Manual...
SRV Canada VRS TM USER'S MANUAL for Mobile applications Version 1.0 SRV Canada VRS User s Manual for Mobile devices Page 1 of 35 TABLE OF CONTENTS TABLE OF CONTENTS... 2 1 Welcome and About This Manual...
Internet Basics. Basic Terms and Concepts. Connecting to the Internet
 Internet Basics In this Learning Unit, we are going to explore the fascinating and ever-changing world of the Internet. The Internet is the largest computer network in the world, connecting more than a
Internet Basics In this Learning Unit, we are going to explore the fascinating and ever-changing world of the Internet. The Internet is the largest computer network in the world, connecting more than a
After Conversation - A Forensic ICQ Logfile Extraction Tool
 Edith Cowan University Research Online ECU Publications Pre. 2011 2005 After Conversation - A Forensic ICQ Logfile Extraction Tool Kim Morfitt Edith Cowan University Craig Valli Edith Cowan University
Edith Cowan University Research Online ECU Publications Pre. 2011 2005 After Conversation - A Forensic ICQ Logfile Extraction Tool Kim Morfitt Edith Cowan University Craig Valli Edith Cowan University
User Guide. Version 8.0
 User Guide Version 8.0 Contents 1 Getting Started... iii 1.1... About... iii 2 Logging In... 4 2.1... Choosing Security Questions... 4 3 The File Manager... 5 3.1... Uploading a file... 6 3.2... Downloading
User Guide Version 8.0 Contents 1 Getting Started... iii 1.1... About... iii 2 Logging In... 4 2.1... Choosing Security Questions... 4 3 The File Manager... 5 3.1... Uploading a file... 6 3.2... Downloading
COLLEGE OF ENGINEERING, NASHIK-4
 Pune Vidyarthi Griha s COLLEGE OF ENGINEERING, NASHIK-4 DEPARTMENT OF COMPUTER ENGINEERING 1) What is Android? Important Android Questions It is an open-sourced operating system that is used primarily
Pune Vidyarthi Griha s COLLEGE OF ENGINEERING, NASHIK-4 DEPARTMENT OF COMPUTER ENGINEERING 1) What is Android? Important Android Questions It is an open-sourced operating system that is used primarily
Wimba Pronto. Version 2.0. User Guide
 Wimba Pronto Version 2.0 User Guide Wimba Pronto 2.0 User Guide Welcome to Wimba Pronto 1 What's New in Wimba Pronto 2.0 2 Getting Started 3 Wimba Pronto System Requirements 3 Creating a New Wimba Pronto
Wimba Pronto Version 2.0 User Guide Wimba Pronto 2.0 User Guide Welcome to Wimba Pronto 1 What's New in Wimba Pronto 2.0 2 Getting Started 3 Wimba Pronto System Requirements 3 Creating a New Wimba Pronto
Web Mechanisms. Draft: 2/23/13 6:54 PM 2013 Christopher Vickery
 Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
GETTING STARTED Contents
 2.5 Enterprise GETTING STARTED Contents Quick Start Guide... 2 Supporting Data... 3 Prompts... 3 Techniques... 4 Pragmatic Observations... 5 Locations... 6 School Levels... 6 Quick Notes... 6 Session Groups...
2.5 Enterprise GETTING STARTED Contents Quick Start Guide... 2 Supporting Data... 3 Prompts... 3 Techniques... 4 Pragmatic Observations... 5 Locations... 6 School Levels... 6 Quick Notes... 6 Session Groups...
Installing and Configuring hopto Work. System Requirements Be sure you have these system requirements to install and use hopto Work.
 Installing and Configuring hopto Work To configure and install hopto Work on your Microsoft Windows server, you ll need to have Administrator status. Note: The recommended setup is that Active Directory
Installing and Configuring hopto Work To configure and install hopto Work on your Microsoft Windows server, you ll need to have Administrator status. Note: The recommended setup is that Active Directory
Forensics on the Windows Platform, Part Two by Jamie Morris last updated February 11, 2003
 SecurityFocus HOME Infocus: Forensics on the Windows Platform, Part Two 2003-02-17 12:56:05-0900 SFOnline Forensics on the Windows Platform, Part Two by Jamie Morris last updated February 11, 2003 Introduction
SecurityFocus HOME Infocus: Forensics on the Windows Platform, Part Two 2003-02-17 12:56:05-0900 SFOnline Forensics on the Windows Platform, Part Two by Jamie Morris last updated February 11, 2003 Introduction
WebEx Meeting Center User Guide
 WebEx Meeting Center User Guide For Hosts, Presenters, and Participants 8.17 Copyright 1997 2010 Cisco and/or its affiliates. All rights reserved. WEBEX, CISCO, Cisco WebEx, the CISCO logo, and the Cisco
WebEx Meeting Center User Guide For Hosts, Presenters, and Participants 8.17 Copyright 1997 2010 Cisco and/or its affiliates. All rights reserved. WEBEX, CISCO, Cisco WebEx, the CISCO logo, and the Cisco
Password Memory 7 User s Guide
 C O D E : A E R O T E C H N O L O G I E S Password Memory 7 User s Guide 2007-2018 by code:aero technologies Phone: +1 (321) 285.7447 E-mail: info@codeaero.com Table of Contents How secure is Password
C O D E : A E R O T E C H N O L O G I E S Password Memory 7 User s Guide 2007-2018 by code:aero technologies Phone: +1 (321) 285.7447 E-mail: info@codeaero.com Table of Contents How secure is Password
Contact Information. Contact Center Operating Hours. Other Contact Information. Contact Monday through Thursday Friday
 Contact Information Contact Center Operating Hours Contact Monday through Thursday Friday Phone: 1.801.796.0944 8 AM 5 PM Eastern Time 8 AM 3 PM Eastern Time Online chat: http://support.paraben.com 10
Contact Information Contact Center Operating Hours Contact Monday through Thursday Friday Phone: 1.801.796.0944 8 AM 5 PM Eastern Time 8 AM 3 PM Eastern Time Online chat: http://support.paraben.com 10
and Security Testing Shawn Valle gmail. com May 2013
 and Security Testing Shawn Valle shawnvalle @ gmail. com May 2013 Introductions 16 years in IT and security (CISSP, MCP, LCP) Co-established FFRDC s Mobile Security Practice in 2010, leading engineering
and Security Testing Shawn Valle shawnvalle @ gmail. com May 2013 Introductions 16 years in IT and security (CISSP, MCP, LCP) Co-established FFRDC s Mobile Security Practice in 2010, leading engineering
Blogging at
 Blogging at http://familylaw.law.miami.edu A. How to Do It Many of you are doubtless already more sophisticated bloggers than I but, especially for those of you who are newbies, I lay out below some of
Blogging at http://familylaw.law.miami.edu A. How to Do It Many of you are doubtless already more sophisticated bloggers than I but, especially for those of you who are newbies, I lay out below some of
