Check List: Linux Machines
|
|
|
- Joshua Melton
- 6 years ago
- Views:
Transcription
1 Check List: Linux Machines High Level Install and maintain malware protection software o Install MalWare (Defender) o Install AntiVirus (Microsoft Security Essentials) Account Management o Remove guest user o Remove old accounts o Ensure all accounts use strong passwords Delete Suspicious Files o Write down file names and locations that were deleted Delete Unauthorized Files o Write down file names and locations that were deleted Enabling the Firewall Services (Also called a daemon) Disable unnecessary services Attach Detection o Monitor your processes o Port Checks o System Logs (syslog) Network Installing and Automating Updates Setting Audit Policies PAM Files
2 Low Level Install and maintain malware protection software o Install Malware (Linux Malware Detect (LMD)) o Install Anti Virus (AVG Anti Virus) o Adding and Removing Software Linux software is bundled into packages Packages are managed by packagemanagers In Ubuntu, the package manager is called Ubuntu Software Center. It looks and functions a lot like Mac s App Store To access Ubuntu Software Center, click the shopping bag on your Ubuntu menu bar Use to manage or uninstall software you have already installed Use to view a log of all the recent software installs, removals, and updates on your system Users must enact root permissions to install, uninstall, or modify software. Account Management o Click User Accounts in the System Settings window o Write Down Accounts you delete o Account types: User and Root o Root the Linux Administrator account For Ubuntu, the root account must be enabled by giving it a password using the sudo command Sudo allows an authorized user to temporarily elevate their privileges using their own password instead of having to know the password belonging to the root account Root users are authorized to do many different tasks, but they must first authenticate their identity by entering their password o Groups To list all groups: cat /etc/group To add a group: addgroup [groupname] To add a user to a group: adduser [username] [groupname o Defaults Users and Groups Permissions and privilege tips Disable login for well known accounts (bin,sys,uucp) Disable all account(s) with no password and lock them down passwd l {user name} o Turn off guest account Like in Windows, the Ubuntu guest account is turned on by default You should disable it so people can t access the computer anonymously The guest account is controlled by LightDM, the display manager controlling the Ubuntu login screen To turn off the guest account, edit the LightDMfile: After root authenticating, type gedit/etc/lightdm/lightdm.conf Add the line allow guest=falseto the end of the Light DM file that pops up and click Save Restart your system and click your username button in the top right corner of your desktop. The guest account should be disabled. o User Accounts Locking a user account may not prevent a user access. They may still be able to gain shell access, without the need for any password. As in Windows, it is important to restrict root (Admin) privileges and password protect all accounts A. To make account management changes, you must enact root permissions by clicking Unlock and authenticate yourself by entering your password B. Switch users from Administrator to Standard User by clicking next to Account Type C. Change passwords by clicking the asterisks next to the Password option Delete Suspicious Files o Write down file names and locations that were deleted Delete Unauthorized Files o Write down file names and locations that were deleted
3 Enabling the Firewall o Enable UFW (Uncomplicated Firewall) Default Ubuntu firewall; but not activated by default Command line interface (frontend for iptables) Configure and enable Set default policies such as drop all connections (deny), then add (allow) rules for specific services Enable logging o Using Gufw You can download Gufw, a graphical firewall interface, from the Software Center and use it to make changes to the UFW in the GUI Type sudo apt get install gufw at the command line Screenshots for Gufw at You might need to install Ubuntu updates before installing Gufw After downloading Gufw from the Software Center, click the Ubuntu button in your menu bar Search Firewall Configura on Click the Unlock button on the Gufwwindow Enact root permissions by authen ca ng Turn Firewall Status On The default (and recommended rules) governing traffic are to Deny all incoming traffic and Allow all outgoing traffic The Reject option is the same as Deny, but also sends a notification to the sender that connection has been blocked The Preconfigured rule panel allows incoming and/or outgoing traffic to be controlled for certain applications or services Similar to the Windows Firewall Exceptions list Open entire ports by clicking the Simple or Advanced tabs Services (Also called a daemon) o Process that runs in the background o Can be viewed and managed in the GUI o To install, type apt get install bum in Terminal o After installing, type bum to run To enable a service, check the box next to it To start a service, right click it and select Start When a service is started, the light bulb will light up. When stopped, the light bulb will be dark. o Disable unnecessary services (daemons) If your system is configured with inetd, look at /etc/inetd.conf and prefix a line with a "#" character to make it a comment; then restart the inetd service or reboot If you are using xinetd, its configuration will be in the directory /etc/xinetd.d. Each file in the directory defines a service, and add disable = yes to any that you want to disable Disable daemons not normally used such as Telnet Anonymous FTP Remote processes (Rexec.Rlogin,Rsh) Rstatd Finger Talk, Ntalk Attach Detection o Monitor your processes Use tools such as Snort, Nessus Monitor syslog Monitor run levels (0 to 6) Runlevels define what services or processes should be running on the system o Runlevels.html Make sure all processes are operating on the appropriate runlevel
4 Check running proceses (approx. 203 processes) ps ef o Port Checks netstat tulpn o System Logs (syslog) Similar to Windows Event Viewer From the Search field in the Ubuntu menu on the left of the desktop, type System Log to view available logs Four types of logs auth.log: Tracks authentication events that prompt for user passwords (e.g., uses of PAM files and sudo) dpkg.log: Tracks software events (e.g., installations and updates) syslog: Tracks operating system events (e.g. error messages) Xorg.0.log: Tracks desktop events (e.g., service changes and graphic card errors. Can add different types of logs Configure the Syslog daemon to log messages and events Located at the /etc/syslog.conf Network o Encrypt network traffic Install ssh o Utilize access control Configure hosts.allow and hosts.deny files for tcpd and sshd Installing and Automating Updates o The open source community regularly develops improvements and patches for Ubuntu o You should install these updates regularly 1. Click the Ubuntu button in the menu bar and search for Update Manager 2. Click Settings on the Update Manager Screen 3. To set automatic updates, go to the Updates Tab and make sure Automatically check for updates is set to Daily 4. After applying the changes, install any available updates from the main Update Manager window Setting Audit Policies o Unlike Windows, auditing is not set up by default in Ubuntu o Three step process to setting up audits: 1. Install the auditing program by typing apt get install auditd 2..Enable audits by typing auditctl e 1 3. View and modify policies by typing gedit/etc/audit/auditd.conf PAM Files o Pluggable Authentication Modules (PAM) are used for logon and applications o They simplify user authentication They do not govern authorization (i.e. grant privileges to users) o 4 types of PAM files: Account control account conditions (e.g. not expired, etc.) Authentication verify user identities Password control some password policies Session define actions performed at the beginning and end of user sessions. o Editing the PAM Password File Type gedit /etc/pam.d/common password Lines in the file starting with # are comments to help the user understand the file. They do not enforce any policies. After making changes, save the file and close it. To enforce password history of : Add remember=5 to the end of the line that has pam_unix.so in it. To enforce password complexity with one of each type of character:* Add ucredit= 1 lcredit= 1 dcredit= 1 ocredit= 1 to the end of the line with pam_cracklib.so in it.** *ucredit= upper case, lcredit=lower case, dcredit= number and ocredit= symbol **cracklibmay need to be installed before enforcing password complexity
5 To enforce Password length of 8: Add minlen=8 to the end of the line that has pam_unix.so in it Account Lockout Set to a high enough number that authorized users are not locked out of their user accounts simply because they mistype a password o Usually set to 5 Add the following two lines highlighted in blue to the /etc/pam.d/system auth file o o auth required /lib/security/$isa/pam_tally.so onerr=fail no_magic_root account required /lib/security/$isa/pam_tally.so per_user deny=5 no_magic_root reset The first added line counts failed login and failed su attempts for each user. The default location for attempted accesses is recorded in /var/log/faillog The second added line specifies to lock accounts automatically after 5 failed login or su attempts (deny=5) User profile The adduser utility creates a brand new home directory named /home/username /etc/default/useradd By default, user home directories in Ubuntu are created with world read/execute permissions Password Files Located at /etc/passwd and /etc/shadow Passwords are usually not stored in the /etc/passwd file, but rather in the /etc/shadow file Passwords are encrypted in the /etc/shadow file File permissions o /etc/passwd Owned by Root Read only to users o /etc/shadow Owned by Root Users should not have access to this file To crack Linux passwords you need the shadow file and sometimes have to merge the passwd and shadow file Password Policy Minimum Password Length o Add the minlen = <x> parameter to the pam_unix configuration in the /etc/pam.d/common password file Set to 8 password required pam_cracklib.so retry=3 minlen=8 difok=3 o By default, Ubuntu requires a minimum password length of 4 characters Password Expiration o Needs a minimum and maximum password age forcing users to change their passwords when they expire PASS_MIN_DAYS Set to 7 days Minimum number of days allowed between password changes PASS_MAX_DAYS Set from 30 to 90 days Maximum number of days a password may be used PASS_WARN_AGE Set to 14 days Number of days warning given before a password expires Parameters can be set in /etc/login.defs Password History (reuse) Create an empty /etc/security/opasswd file for storing old user passwords Set permissions to opasswd to the same as the /etc/shawdow file
6 o Enable password history by adding the remember=<x> to the pam_unix configuration in the /etc/pam.d/common password file o password required pam_unix.so md5 remember=12 use_authtok o The value of the "remember" parameter is the number of old passwords to store for a user Edit Password History o Type gedit /etc/login.defs o This is a much longer file. To easily find the section to edit, type Ctrl+Fand then PASS_MAX_AGE o Modify the following variables to the same recommended settings used in Windows: Maximum Password Duration: PASS_MAX_DAYS 90 Minimum Password Duration: PASS_MIN_DAYS 10 Days Before Expiration to Warn Users to Change Their Password: PASS_WARN_AGE 7 o Save the file and close it More explanation can be found at o run.com/~hal/sysadmin/pam_cracklib.html Edit Set Account Policy Type gedit /etc/pam.d/common auth This file allows you to set an account lockout policy Add this line to the end of the file: auth required pam_tally2.so deny=5 onerr=fail unlock_time=1800 Sets the number of allowed failed login attempts (in this case 5) Sets the account lockout duration in seconds (in this case, 30 minutes) Save the file and close it
7 Additional Information Terminal o Command line is accessed through a program called Terminal o Click the Ubuntu Button on the Ubuntu menu bar Search Terminal Open Terminal o typing commands in Terminal, it is very important to pay attention to capitalization and spaces o Hitting Enter will execute your command and hitting Ctrl+D will close any commands you have running or exit the Terminal File System o The file system can be accessed by clicking the orange folder on your Ubuntu menu bar o Important folders: home: stores each user s documents, media files, etc. Users can only access their own folders, unless they have enacted root permissions etc: system configuration files. boot: contains startup files and kernel files. Should not be modified unless you are an expert user. o Network File System (NFS) Security Method of sharing access to a filesystem between Unix systems Only run NFS as needed, apply latest patches (including nfsd, mountd, statd, lockd) Careful use of /etc/exports Read only if possible No suid if possible Fully qualified hostnames Device Security Device files /dev/null, /dev/tty & /dev/console should be world writeable but NEVER executable Most other device files should be unreadable and unwriteable by regular users Editor o VI is a text editor used on most Unix operating systems o gedit geditis one of many text editor commands in Ubuntu Syntax: gedit [filepath] Unlike with other text editors, using geditwill cause a second window to pop up where you can easily change the text of a file This command will allow you to edit security policy files You need to enact root permissions before using gedit to edit files that cannot be accessed by standard users (e.g. system and security files) When using gedit for the first time, go to Edit Preferences Uncheck Create a backup copy of files to avoid saving issues Try using gedit by opening Terminal and entering gedithello2.txt You will not be prompted to authenticate because this is a public file sudo command o Allows an authorized user (one with root permissions) to temporarily elevate their privileges using their own password instead of having to know the password belonging to the built in root account o This command must be used to perform administrative tasks (e.g. adding a user account) Example: To add archimedes as a user on your system, type adduser archimedes and hit Enter You will get the error message below because you have not authenticated yourself Note: user names must be lower case o Now try adding archimedes as a user by entering the sudo command first: Type sudo adduser archimedes Hi tenter When prompted, type in your password and hit Enter Note: Your password will not be visible when you type. This is an Ubuntu security feature. Remember, the sudocommand will only work if your are using an account with root permissions When prompted, type a passwordand any other details you wish to add to the user account
8 Hit Enter o The sudosucommand is a variation of the sudocommand It tells the command line that you want to run all of the subsequent commands in your current session as root, so that you do not have to enter the sudocommand and your password each time Firestarter o Shows active connections and who they belong to o Controls inbound and outbound traffic o Displays intrusion attempts as they occur o Configure firewall to behave in a specific manner for certain types of connections o Create security policies o Screenshots can be found at security.com/screenshots.php o Download at security.com/ o Installation directions can be found at the firestarterfirewall on ubuntu linux/ Packages o A compressed program or piece of software o Package Managers All software on a linux system is divided into RPM packages, which can be installed, upgraded, or uninstalled Contain a list of software repositories You will be prompted to enter the superuser (root) password before changes are made to the system RPM Package Manager.rpm is the file format for the software package files System administrators must manually install with dependencies Instead, a front end can be used to automate this process Common Package Managers (front end) YUM automatic update and package installer o PackageKit (GUI) o Open Software Updates by clicking Applications System Tools Software Update from the Activities menu within the GNOME desktop apt get o Command line tool Aptitude o Menu driven text based tool ( Synaptic Package Manager (GUI) o
UNIT 10 Ubuntu Security
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT 10 Ubuntu Security Learning Objectives Participants will understand how to configure major components of Linux/Ubuntu Account
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT 10 Ubuntu Security Learning Objectives Participants will understand how to configure major components of Linux/Ubuntu Account
UNIT 9 Introduction to Linux and Ubuntu
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT 9 Introduction to Linux and Ubuntu Learning Objectives Participants will understand the basics of Linux, including the nature,
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT 9 Introduction to Linux and Ubuntu Learning Objectives Participants will understand the basics of Linux, including the nature,
Security Design in. Avaya Aura Presence Services. Release 5.2. Issue 1
 Security Design in Avaya Aura Presence Services Release 5.2 Issue 1 November 2009 2009 Avaya Inc. All Rights Reserved. Notice While reasonable efforts were made to ensure that the information in this document
Security Design in Avaya Aura Presence Services Release 5.2 Issue 1 November 2009 2009 Avaya Inc. All Rights Reserved. Notice While reasonable efforts were made to ensure that the information in this document
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE. Microsoft Windows Security.
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
CIT 470: Advanced Network and System Administration. Topics. Risk Management. Security
 CIT 470: Advanced Network and System Administration Security CIT 470: Advanced Network and System Administration Slide #1 Topics 1. Risk Management 2. Security Policies 3. OS Hardening 4. Authentication
CIT 470: Advanced Network and System Administration Security CIT 470: Advanced Network and System Administration Slide #1 Topics 1. Risk Management 2. Security Policies 3. OS Hardening 4. Authentication
10 Defense Mechanisms
 SE 4C03 Winter 2006 10 Defense Mechanisms Instructor: W. M. Farmer Revised: 23 March 2006 1 Defensive Services Authentication (subject, source) Access control (network, host, file) Data protection (privacy
SE 4C03 Winter 2006 10 Defense Mechanisms Instructor: W. M. Farmer Revised: 23 March 2006 1 Defensive Services Authentication (subject, source) Access control (network, host, file) Data protection (privacy
Linux Security & Firewall
 Linux Security & Firewall Linux is not secure No computer system can ever be "completely secure". make it increasingly difficult for someone to compromise your system. The more secure your system, the
Linux Security & Firewall Linux is not secure No computer system can ever be "completely secure". make it increasingly difficult for someone to compromise your system. The more secure your system, the
Linux Kung Fu. Ross Ventresca UBNetDef, Fall 2017
 Linux Kung Fu Ross Ventresca UBNetDef, Fall 2017 GOTO: https://apps.ubnetdef.org/ What is Linux? Linux generally refers to a group of Unix-like free and open source operating system distributions built
Linux Kung Fu Ross Ventresca UBNetDef, Fall 2017 GOTO: https://apps.ubnetdef.org/ What is Linux? Linux generally refers to a group of Unix-like free and open source operating system distributions built
Setting up a Chaincoin Masternode
 Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Linux Kung Fu. Stephen James UBNetDef, Spring 2017
 Linux Kung Fu Stephen James UBNetDef, Spring 2017 Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and
Linux Kung Fu Stephen James UBNetDef, Spring 2017 Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and
TELE 301 Lecture 8: Post
 Last Lecture System installation This Lecture Post installation Next Lecture Wireless networking Overview TELE 301 Lecture 8: Post 1 Post-configuration Create user accounts and environments Sort out the
Last Lecture System installation This Lecture Post installation Next Lecture Wireless networking Overview TELE 301 Lecture 8: Post 1 Post-configuration Create user accounts and environments Sort out the
SERVER HARDENING CHECKLIST
 SERVER HARDENING CHECKLIST WINDOWS 2003 SERVER CHECKLIST This checklist contains server hardening procedures for Windows 2003 Server. The procedures listed in this document are a balance of industry best
SERVER HARDENING CHECKLIST WINDOWS 2003 SERVER CHECKLIST This checklist contains server hardening procedures for Windows 2003 Server. The procedures listed in this document are a balance of industry best
Introduction. What is Linux? What is the difference between a client and a server?
 Linux Kung Fu Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and open-source operating system distributions
Linux Kung Fu Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and open-source operating system distributions
Basic Linux Security. Roman Bohuk University of Virginia
 Basic Linux Security Roman Bohuk University of Virginia What is Linux? An open source operating system Project started by Linus Torvalds kernel Kernel: core program that controls everything else (controls
Basic Linux Security Roman Bohuk University of Virginia What is Linux? An open source operating system Project started by Linus Torvalds kernel Kernel: core program that controls everything else (controls
Upgrade Tool Guide. July
 Upgrade Tool Guide July 2015 http://www.liveaction.com 4.X to 5.0 The Upgrade Guide from 4.X to 5.0 consists of three parts: Upgrading the LiveAction Server Upgrading the LiveAction Node Upgrading the
Upgrade Tool Guide July 2015 http://www.liveaction.com 4.X to 5.0 The Upgrade Guide from 4.X to 5.0 consists of three parts: Upgrading the LiveAction Server Upgrading the LiveAction Node Upgrading the
The Wonderful World of Services VINCE
 The Wonderful World of Services VINCE Agenda definitions services for Windows and Linux breaks? auditing Linux logs for Linux useful tools Goals develop a better understanding of Linux and Windows services
The Wonderful World of Services VINCE Agenda definitions services for Windows and Linux breaks? auditing Linux logs for Linux useful tools Goals develop a better understanding of Linux and Windows services
CompTIA Linux Course Overview. Prerequisites/Audience. Course Outline. Exam Code: XK0-002 Course Length: 5 Days
 CompTIA Linux+ 2009 Exam Code: XK0-002 Course Length: 5 Days Course Overview This instructor-led course will prepare students for the 2009 CompTIA Linux+ certification exam. It provides a comprehensive
CompTIA Linux+ 2009 Exam Code: XK0-002 Course Length: 5 Days Course Overview This instructor-led course will prepare students for the 2009 CompTIA Linux+ certification exam. It provides a comprehensive
NETW 110 Lab 5 Creating and Assigning Users and Groups Page 1
 NETW 110 Lab 5 Creating and Assigning Users and Groups Page 1 Objective At the conclusion of this lab, the student will be able to add and delete users, create and assign users to groups, and assign users
NETW 110 Lab 5 Creating and Assigning Users and Groups Page 1 Objective At the conclusion of this lab, the student will be able to add and delete users, create and assign users to groups, and assign users
Hands-on Keyboard: Cyber Experiments for Strategists and Policy Makers
 Hands-on Keyboard: Cyber Experiments for Strategists and Policy Makers Review of the Linux File System and Linux Commands 1. Introduction Becoming adept at using the Linux OS requires gaining familiarity
Hands-on Keyboard: Cyber Experiments for Strategists and Policy Makers Review of the Linux File System and Linux Commands 1. Introduction Becoming adept at using the Linux OS requires gaining familiarity
DirectControl and RSA SecurID
 WHITE PAPER CENTRIFY CORP. DirectControl and RSA SecurID NOV 2010 Enabling Active Directory users to authenticate to Unix/Linux using SecurID tokens ABSTRACT This document describes the steps necessary
WHITE PAPER CENTRIFY CORP. DirectControl and RSA SecurID NOV 2010 Enabling Active Directory users to authenticate to Unix/Linux using SecurID tokens ABSTRACT This document describes the steps necessary
Optional Labs. 0Handouts: 2002 ProsoftTraining All Rights Reserved. Version 3.07
 0Handouts: Optional Lab 1-1: Understanding the /etc/securetty file In this lab, you will examine a PAM component, the /etc/securetty file. 1. Boot into Linux as root. Open a Telnet client and attempt to
0Handouts: Optional Lab 1-1: Understanding the /etc/securetty file In this lab, you will examine a PAM component, the /etc/securetty file. 1. Boot into Linux as root. Open a Telnet client and attempt to
Q) Q) What is Linux and why is it so popular? Answer - Linux is an operating system that uses UNIX like Operating system...
 Q) Q) What is Linux and why is it so popular? Answer - Linux is an operating system that uses UNIX like Operating system... Q) Q) What is the difference between home directory and working directory? Answer
Q) Q) What is Linux and why is it so popular? Answer - Linux is an operating system that uses UNIX like Operating system... Q) Q) What is the difference between home directory and working directory? Answer
Redhat Basic. Need. Your. What. Operation G U I D E. Technical Hand Note template version
 Redhat Basic Operation G U I D E What Need Your www.next-asia.com Readhat Basic Operation Guide, Prepared by Nazmul Khan Page 1 of 43 Redhat Basic Operation Guide RedHat Installation Guide... 2 Installation...
Redhat Basic Operation G U I D E What Need Your www.next-asia.com Readhat Basic Operation Guide, Prepared by Nazmul Khan Page 1 of 43 Redhat Basic Operation Guide RedHat Installation Guide... 2 Installation...
Project #3: Implementing NIS
 Project #3: Implementing NIS NIS Daemons Limitations of NIS How We Will Use NIS NIS Domain Name NIS Software Setting Up NIS on it20 /etc/nsswitch.conf Creating New Accounts on Ubuntu /etc/passwd /etc/shadow
Project #3: Implementing NIS NIS Daemons Limitations of NIS How We Will Use NIS NIS Domain Name NIS Software Setting Up NIS on it20 /etc/nsswitch.conf Creating New Accounts on Ubuntu /etc/passwd /etc/shadow
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Prerequisites: Students must be proficient in general computing skills but not necessarily experienced with Linux or Unix. Supported Distributions:
 This GL124 course is designed to follow an identical set of topics as the Red Hat RH124 course with the added benefit of very comprehensive lab exercises and detailed lecture material. The Red Hat Enterprise
This GL124 course is designed to follow an identical set of topics as the Red Hat RH124 course with the added benefit of very comprehensive lab exercises and detailed lecture material. The Red Hat Enterprise
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Operating System Security. 0Handouts: Quizzes ProsoftTraining All Rights Reserved. Version 3.07
 0Handouts: Lesson 1 Quiz 1. What is the working definition of authentication? a. The ability for a person or system to prove identity. b. Protection of data on a system or host from unauthorized access.
0Handouts: Lesson 1 Quiz 1. What is the working definition of authentication? a. The ability for a person or system to prove identity. b. Protection of data on a system or host from unauthorized access.
0Activity Answers. Table A1-1: Operating system elements and security mechanisms. The Security Accounts Manager (SAM)
 Activity Answers-1 0Activity Answers Activity 1-1: Reviewing elements and mechanisms found in operating systems In this activity, you will compare Windows 2000 and Linux to discover how each implements
Activity Answers-1 0Activity Answers Activity 1-1: Reviewing elements and mechanisms found in operating systems In this activity, you will compare Windows 2000 and Linux to discover how each implements
Linux Systems Security. Access Control and Authentication NETS1028 Fall 2016
 Linux Systems Security Access Control and Authentication NETS1028 Fall 2016 Access Control Authenticating users is the act of trying to verify that a user is who they claim to be We generally rely on the
Linux Systems Security Access Control and Authentication NETS1028 Fall 2016 Access Control Authenticating users is the act of trying to verify that a user is who they claim to be We generally rely on the
Adaptec Storage Examiner. Installation and User Guide
 Adaptec Storage Examiner MAN-00006-UG Revision 03 17 th November 2003 Adaptec, Inc., Clonshaugh Industrial Estate, Clonshaugh, Dublin 17. IRELAND www.adaptec.com This document may be subject to change
Adaptec Storage Examiner MAN-00006-UG Revision 03 17 th November 2003 Adaptec, Inc., Clonshaugh Industrial Estate, Clonshaugh, Dublin 17. IRELAND www.adaptec.com This document may be subject to change
Unit 2: Manage Files Graphically with Nautilus Objective: Manage files graphically and access remote systems with Nautilus
 Linux system administrator-i Unit 1: Get Started with the GNOME Graphical Desktop Objective: Get started with GNOME and edit text files with gedit Unit 2: Manage Files Graphically with Nautilus Objective:
Linux system administrator-i Unit 1: Get Started with the GNOME Graphical Desktop Objective: Get started with GNOME and edit text files with gedit Unit 2: Manage Files Graphically with Nautilus Objective:
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
1Z Oracle Linux 5 and 6 System Administration Exam Summary Syllabus Questions
 1Z0-100 Oracle Linux 5 and 6 System Administration Exam Summary Syllabus Questions Table of Contents Introduction to 1Z0-100 Exam on Oracle Linux 5 and 6 System Administration2 Oracle 1Z0-100 Certification
1Z0-100 Oracle Linux 5 and 6 System Administration Exam Summary Syllabus Questions Table of Contents Introduction to 1Z0-100 Exam on Oracle Linux 5 and 6 System Administration2 Oracle 1Z0-100 Certification
UNIX/Linux Auditing. Baccam Consulting, LLC Training Events
 UNIX/Linux Auditing Baccam Consulting, LLC tanya@securityaudits.org Training Events www.securityaudits.org/events.html ***CISSP Course being offered April 25-April 29, 2016 Copyright 2005-2016, Baccam
UNIX/Linux Auditing Baccam Consulting, LLC tanya@securityaudits.org Training Events www.securityaudits.org/events.html ***CISSP Course being offered April 25-April 29, 2016 Copyright 2005-2016, Baccam
Lab Authentication, Authorization, and Accounting
 Objectives Given a scenario, select the appropriate authentication, authorization, or access control Install and configure security controls when performing account management, based on best practices
Objectives Given a scenario, select the appropriate authentication, authorization, or access control Install and configure security controls when performing account management, based on best practices
CTEC1863/2018F Bonus Lab Page 1 of 5
 CTEC1863/2018F Bonus Lab Page 1 of 5 Bonus Lab: OpenSUSE Linux Rescue In this lab, we will install an OpenSUSE virtual machine. However, both the non-root user and the root passwords are unknown. To fix
CTEC1863/2018F Bonus Lab Page 1 of 5 Bonus Lab: OpenSUSE Linux Rescue In this lab, we will install an OpenSUSE virtual machine. However, both the non-root user and the root passwords are unknown. To fix
Introduction to UNIX/LINUX Security. Hu Weiwei
 Introduction to UNIX/LINUX Security Hu Weiwei Operation System Security The Security Problems in Operation Systems become more and more important The Security techniques improved rapidly The number of
Introduction to UNIX/LINUX Security Hu Weiwei Operation System Security The Security Problems in Operation Systems become more and more important The Security techniques improved rapidly The number of
Using RDP with Azure Linux Virtual Machines
 Using RDP with Azure Linux Virtual Machines 1. Create a Linux Virtual Machine with Azure portal Create SSH key pair 1. Install Ubuntu Bash shell by downloading and running bash.exe file as administrator.
Using RDP with Azure Linux Virtual Machines 1. Create a Linux Virtual Machine with Azure portal Create SSH key pair 1. Install Ubuntu Bash shell by downloading and running bash.exe file as administrator.
Ftp Command Line Manual Windows Example Port 22
 Ftp Command Line Manual Windows Example Port 22 Session, Logging, Console/scripting mode, Operations, Configuration enables passive ( =on ) or active ( =off ) transfer mode (FTP protocol only). winscp.exe
Ftp Command Line Manual Windows Example Port 22 Session, Logging, Console/scripting mode, Operations, Configuration enables passive ( =on ) or active ( =off ) transfer mode (FTP protocol only). winscp.exe
About Backup and Restore, on page 1 Supported Backup and Restore Procedures, on page 3
 About, on page 1 Supported Procedures, on page 3 Back Up Automation Data Using the GUI, on page 4 Restore Automation Data Using the GUI, on page 6 Schedule a Backup of Automation Data Using the GUI, on
About, on page 1 Supported Procedures, on page 3 Back Up Automation Data Using the GUI, on page 4 Restore Automation Data Using the GUI, on page 6 Schedule a Backup of Automation Data Using the GUI, on
Working with Ubuntu Linux. Track 2 Workshop June 2010 Pago Pago, American Samoa
 Working with Ubuntu Linux Track 2 Workshop June 2010 Pago Pago, American Samoa Assumptions You are comfortable with the following: Core Linux concepts - Shells - Permissions - Graphical user interface
Working with Ubuntu Linux Track 2 Workshop June 2010 Pago Pago, American Samoa Assumptions You are comfortable with the following: Core Linux concepts - Shells - Permissions - Graphical user interface
OS Security. Authentication. Radboud University Nijmegen, The Netherlands. Winter 2014/2015
 OS Security Authentication Radboud University Nijmegen, The Netherlands Winter 2014/2015 What does an OS do? Definition An operating system (OS) is a computer program that manages access of processes (programs)
OS Security Authentication Radboud University Nijmegen, The Netherlands Winter 2014/2015 What does an OS do? Definition An operating system (OS) is a computer program that manages access of processes (programs)
3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings 4. Select the check box for SPoE as default.
 Week 1 Lab Lab 1: Connect to the Barracuda network. 1. Download the Barracuda NG Firewall Admin 5.4 2. Launch NG Admin 3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings
Week 1 Lab Lab 1: Connect to the Barracuda network. 1. Download the Barracuda NG Firewall Admin 5.4 2. Launch NG Admin 3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings
Why secure the OS? Operating System Security. Privilege levels in 80X86 processors. The basis of protection: Seperation. Privilege levels - A problem
 Why secure the OS? Operating System Security Works directly on the hardware but can be adapted during runtime Data and process are directly visible Application security can be circumvented from lower layers
Why secure the OS? Operating System Security Works directly on the hardware but can be adapted during runtime Data and process are directly visible Application security can be circumvented from lower layers
RedHat Certified Engineer
 RedHat Certified Engineer Red Hat Certified Engineer (RHCE) is a performance-based test that measures actual competency on live systems. Called the "crown jewel of Linux certifications," RHCE proves an
RedHat Certified Engineer Red Hat Certified Engineer (RHCE) is a performance-based test that measures actual competency on live systems. Called the "crown jewel of Linux certifications," RHCE proves an
MassTransit Server Installation Guide for Windows
 MassTransit 6.1.1 Server Installation Guide for Windows November 24, 2009 Group Logic, Inc. 1100 North Glebe Road, Suite 800 Arlington, VA 22201 Phone: 703-528-1555 Fax: 703-528-3296 E-mail: info@grouplogic.com
MassTransit 6.1.1 Server Installation Guide for Windows November 24, 2009 Group Logic, Inc. 1100 North Glebe Road, Suite 800 Arlington, VA 22201 Phone: 703-528-1555 Fax: 703-528-3296 E-mail: info@grouplogic.com
Hardened Virtual Appliance Operations Guide
 Hardened Virtual Appliance Operations Guide Securing the Appliance Base Platform to Meet High Governance Requirements VMWARE WHITEPAPER Table of Contents Introduction... 3 Purpose... 4 Root password...
Hardened Virtual Appliance Operations Guide Securing the Appliance Base Platform to Meet High Governance Requirements VMWARE WHITEPAPER Table of Contents Introduction... 3 Purpose... 4 Root password...
GSS Administration and Troubleshooting
 CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
Ubuntu Supplement to X350 & X550 User s Guide NComputing X350 & X550 vspace Software for Linux on Ubuntu 8.04
 Ubuntu Supplement to X350 & X550 User s Guide NComputing X350 & X550 vspace Software for Linux on Ubuntu 8.04 Prepared by: NComputing TID 110.118-2c Revision 1.2 Updated: December 02, 2009 Copyright NComputing
Ubuntu Supplement to X350 & X550 User s Guide NComputing X350 & X550 vspace Software for Linux on Ubuntu 8.04 Prepared by: NComputing TID 110.118-2c Revision 1.2 Updated: December 02, 2009 Copyright NComputing
LOCAL WALLET (COLD WALLET):
 This tutorial will teach you how to create a masternode with a "cold/hot" setup. The whole process is as follows. LOCAL WALLET (COLD WALLET): Visit TRAID platform s official repository on GitHub and download
This tutorial will teach you how to create a masternode with a "cold/hot" setup. The whole process is as follows. LOCAL WALLET (COLD WALLET): Visit TRAID platform s official repository on GitHub and download
LAB #7 Linux Tutorial
 Gathering information: LAB #7 Linux Tutorial Find the password file on a Linux box Scenario You have access to a Linux computer. You must find the password file on the computer. Objective Get a listing
Gathering information: LAB #7 Linux Tutorial Find the password file on a Linux box Scenario You have access to a Linux computer. You must find the password file on the computer. Objective Get a listing
Securing Linux Systems Before Deployment
 Securing Linux Systems Before Deployment Richard Williams Senior Support Services Specialist Symark Why secure Linux systems? Your Linux enterprise installation is growing Assets on Linux systems are becoming
Securing Linux Systems Before Deployment Richard Williams Senior Support Services Specialist Symark Why secure Linux systems? Your Linux enterprise installation is growing Assets on Linux systems are becoming
OS Security. Authentication. Radboud University Nijmegen, The Netherlands. Winter 2014/2015
 OS Security Authentication Radboud University Nijmegen, The Netherlands Winter 2014/2015 What does an OS do? Definition An operating system (OS) is a computer program that manages access of processes (programs)
OS Security Authentication Radboud University Nijmegen, The Netherlands Winter 2014/2015 What does an OS do? Definition An operating system (OS) is a computer program that manages access of processes (programs)
Author A.Kishore/Sachin WinSCP
 WinSCP WinSCP is a freeware windows client for the SCP (secure copy protocol), a way to transfer files across the network using the ssh (secure shell) encrypted protocol. It replaces other FTP programs
WinSCP WinSCP is a freeware windows client for the SCP (secure copy protocol), a way to transfer files across the network using the ssh (secure shell) encrypted protocol. It replaces other FTP programs
Operating system hardening
 Operating system Comp Sci 3600 Security Outline 1 2 3 4 5 6 What is OS? Hardening process that includes planning, ation, uration, update, and maintenance of the operating system and the key applications
Operating system Comp Sci 3600 Security Outline 1 2 3 4 5 6 What is OS? Hardening process that includes planning, ation, uration, update, and maintenance of the operating system and the key applications
Networks Lab Pod Diagram
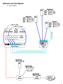 (Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
(Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
SA2 v6 Linux System Administration II Net Configuration, Software, Troubleshooting
 SA2 v6 Linux System Administration II Net Configuration, Software, Troubleshooting Synopsis: This is the second System Administration class, a follow-on class for new administrators with limited networking
SA2 v6 Linux System Administration II Net Configuration, Software, Troubleshooting Synopsis: This is the second System Administration class, a follow-on class for new administrators with limited networking
OPERATING SYSTEMS LINUX
 OPERATING SYSTEMS LINUX Božo Krstajić, PhD, University of Montenegro Podgorica bozok@cg.ac.yu Process management Linux operating systems work with processes. Basically a process consists of program code
OPERATING SYSTEMS LINUX Božo Krstajić, PhD, University of Montenegro Podgorica bozok@cg.ac.yu Process management Linux operating systems work with processes. Basically a process consists of program code
LiveNX Upgrade Guide from v5.2.0 to v5.2.1
 LIVEACTION, INC. LiveNX Upgrade Guide from v5.2.0 to v5.2.1 UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the LiveAction
LIVEACTION, INC. LiveNX Upgrade Guide from v5.2.0 to v5.2.1 UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the LiveAction
IT Essentials v6.0 Windows 10 Software Labs
 IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
Linux Administration
 Linux Administration This course will cover all aspects of Linux Certification. At the end of the course delegates will have the skills required to administer a Linux System. It is designed for professionals
Linux Administration This course will cover all aspects of Linux Certification. At the end of the course delegates will have the skills required to administer a Linux System. It is designed for professionals
FileCruiser. Administrator Portal Guide
 FileCruiser Administrator Portal Guide Contents Administrator Portal Guide Contents Login to the Administration Portal 1 Home 2 Capacity Overview 2 Menu Features 3 OU Space/Team Space/Personal Space Usage
FileCruiser Administrator Portal Guide Contents Administrator Portal Guide Contents Login to the Administration Portal 1 Home 2 Capacity Overview 2 Menu Features 3 OU Space/Team Space/Personal Space Usage
Managing GSS User Accounts Through a TACACS+ Server
 CHAPTER 4 Managing GSS User Accounts Through a TACACS+ Server This chapter describes how to configure the GSS, primary GSSM, or standby GSSM as a client of a Terminal Access Controller Access Control System
CHAPTER 4 Managing GSS User Accounts Through a TACACS+ Server This chapter describes how to configure the GSS, primary GSSM, or standby GSSM as a client of a Terminal Access Controller Access Control System
Veritas NetBackup Appliance Security Guide
 Veritas NetBackup Appliance Security Guide Release 2.7.3 NetBackup 52xx and 5330 Veritas NetBackup Appliance Security Guide Document version: 2.7.3 Legal Notice Copyright 2016 Veritas Technologies LLC.
Veritas NetBackup Appliance Security Guide Release 2.7.3 NetBackup 52xx and 5330 Veritas NetBackup Appliance Security Guide Document version: 2.7.3 Legal Notice Copyright 2016 Veritas Technologies LLC.
HANDS UP IF YOU DON T HAVE A VM OR IF YOU DON T REMEMBER YOUR PASSWORDS. Or something broke
 HANDS UP IF YOU DON T HAVE A VM OR IF YOU DON T REMEMBER YOUR PASSWORDS Or something broke Securing your VM 101 Getting Comfy in Linux -> Comfort ++ You After This Talk Quick recap from last week. Setup
HANDS UP IF YOU DON T HAVE A VM OR IF YOU DON T REMEMBER YOUR PASSWORDS Or something broke Securing your VM 101 Getting Comfy in Linux -> Comfort ++ You After This Talk Quick recap from last week. Setup
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Everything about Linux User- and Filemanagement
 Everything about Linux User- and Filemanagement Lukas Prokop 20. April 2009 Inhaltsverzeichnis 1 Who I am 2 1.1 whoami..................................... 3 1.2 passwd......................................
Everything about Linux User- and Filemanagement Lukas Prokop 20. April 2009 Inhaltsverzeichnis 1 Who I am 2 1.1 whoami..................................... 3 1.2 passwd......................................
Lab 1: Accessing the Linux Operating System Spring 2009
 CIS 90 Linux Lab Exercise Lab 1: Accessing the Linux Operating System Spring 2009 Lab 1: Accessing the Linux Operating System This lab takes a look at UNIX through an online experience on an Ubuntu Linux
CIS 90 Linux Lab Exercise Lab 1: Accessing the Linux Operating System Spring 2009 Lab 1: Accessing the Linux Operating System This lab takes a look at UNIX through an online experience on an Ubuntu Linux
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Installation Guide. Research Computing Team V2.0 RESTRICTED
 Installation Guide Research Computing Team V2.0 RESTRICTED Document History This document relates to the BEAR DataShare service which is based on the product Power Folder, version 10.3.232 ( some screenshots
Installation Guide Research Computing Team V2.0 RESTRICTED Document History This document relates to the BEAR DataShare service which is based on the product Power Folder, version 10.3.232 ( some screenshots
NetIQ Privileged Account Manager 3.5 includes new features, improves usability and resolves several previous issues.
 Privileged Account Manager 3.5 Release Notes July 2018 NetIQ Privileged Account Manager 3.5 includes new features, improves usability and resolves several previous issues. Many of these improvements were
Privileged Account Manager 3.5 Release Notes July 2018 NetIQ Privileged Account Manager 3.5 includes new features, improves usability and resolves several previous issues. Many of these improvements were
Agent and Agent Browser. Updated Friday, January 26, Autotask Corporation
 Agent and Agent Browser Updated Friday, January 26, 2018 2018 Autotask Corporation Table of Contents Table of Contents 2 The AEM Agent and Agent Browser 3 AEM Agent 5 Privacy Mode 9 Agent Browser 11 Agent
Agent and Agent Browser Updated Friday, January 26, 2018 2018 Autotask Corporation Table of Contents Table of Contents 2 The AEM Agent and Agent Browser 3 AEM Agent 5 Privacy Mode 9 Agent Browser 11 Agent
Siemens PLM Software. HEEDS MDO Setting up a Windows-to- Linux Compute Resource.
 Siemens PLM Software HEEDS MDO 2018.04 Setting up a Windows-to- Linux Compute Resource www.redcedartech.com. Contents Introduction 1 On Remote Machine B 2 Installing the SSH Server 2 Configuring the SSH
Siemens PLM Software HEEDS MDO 2018.04 Setting up a Windows-to- Linux Compute Resource www.redcedartech.com. Contents Introduction 1 On Remote Machine B 2 Installing the SSH Server 2 Configuring the SSH
Protegent Total Security Solution USER GUIDE Unistal Systems Pvt. Ltd. All rights Reserved Page 1
 Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
Once the VM is started, the VirtualBox OS Manager window can be closed. But our Ubuntu VM is still running.
 How to use iptables on Ubuntu Revised: 16-August-2016 by David Walling This "How To" document describes using the iptables program to define firewall rules for our Ubuntu server. We will also explore using
How to use iptables on Ubuntu Revised: 16-August-2016 by David Walling This "How To" document describes using the iptables program to define firewall rules for our Ubuntu server. We will also explore using
WebAdmin IceWarp WebAdmin Manual
 WebAdmin IceWarp WebAdmin Manual WWW.ICEWARP.COM 1 WebClient WebAdmin User Manual Guide Contents About IceWarp WebAdmin Manual 3 1/ Login Page 4 2/ 4 Control bar 5 User Account Menu 5 Main Windows 6 Dashboard
WebAdmin IceWarp WebAdmin Manual WWW.ICEWARP.COM 1 WebClient WebAdmin User Manual Guide Contents About IceWarp WebAdmin Manual 3 1/ Login Page 4 2/ 4 Control bar 5 User Account Menu 5 Main Windows 6 Dashboard
AsteriskNow IPTables Firewall Configuration
 AsteriskNow IPTables Firewall Configuration In a previous guide I discussed how to setup an AsteriskNow server with Polycom phone support. In this guide I will illustrate how to tighten up your server
AsteriskNow IPTables Firewall Configuration In a previous guide I discussed how to setup an AsteriskNow server with Polycom phone support. In this guide I will illustrate how to tighten up your server
The kernel is the low-level software that manages hardware, multitasks programs, etc.
 November 2011 1 Why Use Linux? Save Money Initial purchase and maintenance Resume Linux is used by MANY organizations More choices Tons of Linux operating systems November 2011 2 What is Linux? 1. Contains
November 2011 1 Why Use Linux? Save Money Initial purchase and maintenance Resume Linux is used by MANY organizations More choices Tons of Linux operating systems November 2011 2 What is Linux? 1. Contains
SCRIV NETWORK COLD WALLET MASTERNODE SETUP GUIDE DETAILED
 SCRIV NETWORK MASTERNODE SETUP GUIDE COLD WALLET DETAILED March, 2018 Table of Contents Requirements for running SCRIV cold wallet masternode on Linux VPS: 3 Setup Linux-based VPS... 3 1. Install SCRIV
SCRIV NETWORK MASTERNODE SETUP GUIDE COLD WALLET DETAILED March, 2018 Table of Contents Requirements for running SCRIV cold wallet masternode on Linux VPS: 3 Setup Linux-based VPS... 3 1. Install SCRIV
MAC HOST GUIDE. Remote Support & Management PC Mac Tablet Smartphone Embedded device. WiseMo Host module on your Mac computer
 MAC HOST GUIDE Remote Support & Management PC Mac Tablet Smartphone Embedded device WiseMo Guest module for example on your Windows PC WiseMo Host module on your Mac computer WiseMo develops software for
MAC HOST GUIDE Remote Support & Management PC Mac Tablet Smartphone Embedded device WiseMo Guest module for example on your Windows PC WiseMo Host module on your Mac computer WiseMo develops software for
SECURITY+ LAB SERIES. Lab 3: Protocols and Default Network Ports Connecting to a Remote System
 SECURITY+ LAB SERIES Lab 3: Protocols and Default Network Ports Connecting to a Remote System Document Version: 2015-09-24 otherwise noted, is licensed under the Creative Commons Attribution 3.0 Unported
SECURITY+ LAB SERIES Lab 3: Protocols and Default Network Ports Connecting to a Remote System Document Version: 2015-09-24 otherwise noted, is licensed under the Creative Commons Attribution 3.0 Unported
HP-UX Security I. Ideal candidate for this course Experienced system and network administrators responsible for securing and monitoring HP-UX systems
 Course Data Sheet HP-UX Security I Course description This course teaches you about the most common HP-UX system security vulnerabilities, and introduces a variety of tools and techniques that can be used
Course Data Sheet HP-UX Security I Course description This course teaches you about the most common HP-UX system security vulnerabilities, and introduces a variety of tools and techniques that can be used
VII. Corente Services SSL Client
 VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
Xton Access Manager GETTING STARTED GUIDE
 Xton Access Manager GETTING STARTED GUIDE XTON TECHNOLOGIES, LLC PHILADELPHIA Copyright 2017. Xton Technologies LLC. Contents Introduction... 2 Technical Support... 2 What is Xton Access Manager?... 3
Xton Access Manager GETTING STARTED GUIDE XTON TECHNOLOGIES, LLC PHILADELPHIA Copyright 2017. Xton Technologies LLC. Contents Introduction... 2 Technical Support... 2 What is Xton Access Manager?... 3
SAP GUI 7.30 for Windows Computer
 SAP GUI 7.30 for Windows Computer Student and Faculty Installation Instructions Table of Contents Caution:... 2 System Requirements:... 2 System Memory (RAM) requirements:... 2 Disk Space requirements:...
SAP GUI 7.30 for Windows Computer Student and Faculty Installation Instructions Table of Contents Caution:... 2 System Requirements:... 2 System Memory (RAM) requirements:... 2 Disk Space requirements:...
Copyright
 This video will look at configuring the default password policy in Active Directory. These setting determines setting like how long a user password will be, if the password needs to complex, and how many
This video will look at configuring the default password policy in Active Directory. These setting determines setting like how long a user password will be, if the password needs to complex, and how many
Configuring Windows Security Features
 04_0789737213_ch03.qxd 10/26/07 3:31 PM Page 77 3 CHAPTER THREE Configuring Windows Security Features This chapter covers the following objectives: Configure and troubleshoot User Account Control. Configure
04_0789737213_ch03.qxd 10/26/07 3:31 PM Page 77 3 CHAPTER THREE Configuring Windows Security Features This chapter covers the following objectives: Configure and troubleshoot User Account Control. Configure
NetSupport ServiceDesk Product Manual Version 3.10
 NetSupport ServiceDesk Product Manual Version 3.10 Manual COPYRIGHT (C) 2013 NetSupport Ltd. All rights reserved. The Information in this document is subject to change without notice. NetSupport Ltd. reserves
NetSupport ServiceDesk Product Manual Version 3.10 Manual COPYRIGHT (C) 2013 NetSupport Ltd. All rights reserved. The Information in this document is subject to change without notice. NetSupport Ltd. reserves
Table of Contents Chapter 1: Migrating NIMS to OMS... 3 Index... 17
 Migrating from NIMS to OMS 17.3.2.0 User Guide 7 Dec 2017 Table of Contents Chapter 1: Migrating NIMS to OMS... 3 Before migrating to OMS... 3 Purpose of this migration guide...3 Name changes from NIMS
Migrating from NIMS to OMS 17.3.2.0 User Guide 7 Dec 2017 Table of Contents Chapter 1: Migrating NIMS to OMS... 3 Before migrating to OMS... 3 Purpose of this migration guide...3 Name changes from NIMS
Sophos Enterprise Console
 secure network quick startup guide Product Version: 5.5 Contents About this guide... 1 Limitations on the secure network...2 What do I install?...3 What are the key steps?... 4 Download the installers...5
secure network quick startup guide Product Version: 5.5 Contents About this guide... 1 Limitations on the secure network...2 What do I install?...3 What are the key steps?... 4 Download the installers...5
Sophos Mobile SaaS startup guide. Product version: 7.1
 Sophos Mobile SaaS startup guide Product version: 7.1 Contents 1 About this guide...4 2 What are the key steps?...5 3 Change your password...6 4 Change your login name...7 5 Activate SMC Advanced licenses...8
Sophos Mobile SaaS startup guide Product version: 7.1 Contents 1 About this guide...4 2 What are the key steps?...5 3 Change your password...6 4 Change your login name...7 5 Activate SMC Advanced licenses...8
Red Hat Enterprise Linux 7 Getting Started with Cockpit
 Red Hat Enterprise Linux 7 Getting Started with Cockpit Getting Started with Cockpit Red Hat Enterprise Linux Documentation Team Red Hat Enterprise Linux 7 Getting Started with Cockpit Getting Started
Red Hat Enterprise Linux 7 Getting Started with Cockpit Getting Started with Cockpit Red Hat Enterprise Linux Documentation Team Red Hat Enterprise Linux 7 Getting Started with Cockpit Getting Started
Parallel Programming
 Parallel Programming Installing Ubuntu Virtual Machine within VirtualBox Author B. Wilkinson - Modification date Januray 3, 2016 These instructions assume you have already installed VirtualBox (See separate
Parallel Programming Installing Ubuntu Virtual Machine within VirtualBox Author B. Wilkinson - Modification date Januray 3, 2016 These instructions assume you have already installed VirtualBox (See separate
Secure Single Sign On with FingerTec OFIS
 Secure Single Sign On with FingerTec OFIS User Guide CONTENTS 3 1 INTRODUCTION Welcome to OFIS Gateway 4-11 2 INSTALLATION & SETUP Registering Your OFIS Gateway Installing & Setting Up Your OFIS Gateway
Secure Single Sign On with FingerTec OFIS User Guide CONTENTS 3 1 INTRODUCTION Welcome to OFIS Gateway 4-11 2 INSTALLATION & SETUP Registering Your OFIS Gateway Installing & Setting Up Your OFIS Gateway
Managing GSS User Accounts Through a TACACS+ Server
 4 CHAPTER Managing GSS User Accounts Through a TACACS+ Server This chapter describes how to configure the GSS, primary GSSM, or standby GSSM as a client of a Terminal Access Controller Access Control System
4 CHAPTER Managing GSS User Accounts Through a TACACS+ Server This chapter describes how to configure the GSS, primary GSSM, or standby GSSM as a client of a Terminal Access Controller Access Control System
Purpose. Target Audience. Install SNMP On The Remote Linux Machine. Nagios XI. Monitoring Linux Using SNMP
 Purpose This document describes how to monitor Linux machines with using SNMP. SNMP is an agentless method of monitoring network devices and servers, and is often preferable to installing dedicated agents
Purpose This document describes how to monitor Linux machines with using SNMP. SNMP is an agentless method of monitoring network devices and servers, and is often preferable to installing dedicated agents
Likewise Enterprise Administrators Guide
 Likewise Enterprise Administrators Guide v4 Information Services University of Oregon December 2010 Table of Contents Definitions... 4 opt/likewise... 4 AD... 4 Domain... 4 DuckID... 4 GPO... 4 UNIX Attributes...
Likewise Enterprise Administrators Guide v4 Information Services University of Oregon December 2010 Table of Contents Definitions... 4 opt/likewise... 4 AD... 4 Domain... 4 DuckID... 4 GPO... 4 UNIX Attributes...
ESET Mobile Security for Windows Mobile. Installation Manual and User Guide - Public Beta
 ESET Mobile Security for Windows Mobile Installation Manual and User Guide - Public Beta Contents...3 1. Installation of ESET Mobile Security 1.1 Minimum...3 system requirements 1.2 Installation...3 1.2.1
ESET Mobile Security for Windows Mobile Installation Manual and User Guide - Public Beta Contents...3 1. Installation of ESET Mobile Security 1.1 Minimum...3 system requirements 1.2 Installation...3 1.2.1
Perl and R Scripting for Biologists
 Perl and R Scripting for Biologists Lukas Mueller PLBR 4092 Course overview Linux basics (today) Linux advanced (Aure, next week) Why Linux? Free open source operating system based on UNIX specifications
Perl and R Scripting for Biologists Lukas Mueller PLBR 4092 Course overview Linux basics (today) Linux advanced (Aure, next week) Why Linux? Free open source operating system based on UNIX specifications
