Once the VM is started, the VirtualBox OS Manager window can be closed. But our Ubuntu VM is still running.
|
|
|
- Kristina Holt
- 6 years ago
- Views:
Transcription
1 How to use iptables on Ubuntu Revised: 16-August-2016 by David Walling This "How To" document describes using the iptables program to define firewall rules for our Ubuntu server. We will also explore using the iptables-persistent package for Ubuntu. Also, we will demonstrate running our VM "headless" and accessing Ubuntu for our configuration work using SSH instead of the native console. First we will restart our Ubuntu server VM using the "headless start" VirtualBox feature and connect to Ubuntu over SSH using PuTTY. The "Headless Start" option will start our VM without a GUI. During startup, we can see what the VM would display in the "Preview" pane. Once the VM is started, the VirtualBox OS Manager window can be closed. But our Ubuntu VM is still running.
2 Now, connect using PuTTY to Ubuntu using SSH-2 and public-key authentication. Since we have some work to do in this session, we can change our SSH console settings to make our screen dimensions a little bigger and maybe change the color options. Here, I am setting columns to 136, rows to 56 and scrollback lines to 2000.
3 On the "Colours" dialog, we set the "Default Background" to RGB values 255, 255, 255 and the "Default Foreground" values to 0, 0, 0. Working with iptables requires supervisor privileges. So, we will "su" to the osboxes logon. To display the current iptables configuration, use the command "iptables -L". As you can see, by default, Ubuntu sets the three default iptables "chains" to a wide-open ACCEPT policy. Nothing is restricted.
4 Before we define firewall rules with iptables, we want to make sure we can persist the changes. There are several methods to do this. Analyzing all of them is beyond the scope of this "How To". The method we will use here is to leverage the iptables-persistent package. Use apt to install this. Once installed, iptables-persistent will save IPv4 and IPv6 rules in separate files in the /etc/iptables folder. During installation of this package, you will be prompted whether to save the current IPv4 rules into the /etc/iptables/rules.v4 file. We answer "<Yes>" to this question.
5 With iptables-persistent installed, the current firewall rules can still be displayed using the command "iptables -L". In addition, displaying the file /etc/iptables/rules.v4 will display the last saved configuration, which will take effect when the system is restarted. The format of the /etc/iptables/rules.v4 file is different than the ouput of the "iptables -L" command. But, provided that the active firewall state matches the rules.v4 file, both outputs indicate the same state. Just remember that updating rules.v4 doesn't make new rules active. We will see below how to activate new rules with "iptables-save" and update the rules.v4 file in a single command. Now, we're going to create a local rules.v4 file to issue a series of iptables commands to define our firewall rules. This file will be only a working copy. We are going to create this file as the "root" user. On this installation of Ubuntu, the osboxes user was not able write to /etc/iptables. Change the root user password. Use appropriate password policies. Then switch to the root user.
6 Now we can edit the local rules.v4 file The first commands we will include will set the INPUT policy to ACCEPT and clear, or "flush", the current set of rules. We want to set the INPUT policy to ACCEPT at first so that, in case we make an error in our configuration, we can still connect to our server to make edits. Once we are satisfied that our rules are working, we will set the INPUT policy to DROP so that any incoming connection not covered by our rules is not allowed. We update the permissions on our rules.v4 file so that the osboxes user can read, write and execute it. Other "users" group members can read it.
7 Now when we run the rules.v4 as a script, we will define firewall rules, save them and list them. Note that the iptables-save command will output rules for each table. The "iptables -L" command lists one consolidated output. Next we will add rules to protect against common attacks. We will stop SYN-flood attacks, packet fragments, Christmas-tree packets, null packets and we will prevent ICMP echo requests generated by the "ping" command.
8 Next, we want to explicitly allow incoming SSH connections on our non-standard port 8642, but only from addresses on our host interface. We have already allowed established and related packets, so incoming and outgoing data flow on SSH connections will be allowed. We will also allow NTP (network time protocol) packets on port 123 using the UDP protocol. After allowing this traffic, we will change the INPUT and FORWARD chain policies to DROP, but leave the OUTPUT chain policy as ACCEPT. Here is our completed rules.v4 file:
9 Here is the output of the iptables-save command. Here is the output of the "iptables -L" command.
10 Now, with our rules saved locally and made active using the iptables-save command. We can overwrite the copy of rules.v4 in /etc/iptables. Use this command for this purpose: iptables-save >> /etc/iptables/rules.v4 Now we can restart Ubuntu and verify that our firewall rules are in place on startup. Issue the "reboot" command from our root user prompt. This will close our SSH connection immediately and restart the Ubuntu VM in headless mode. Open a new SSH session using PuTTY. Logon as our SSH user. use the "su" command to logon as osboxes and issue the "sudo iptables -L" command to display active firewall rules. That concludes this "How To". We have installed the iptables-persistent package and defined our initial firewall configuration.
Start the Ubuntu Linux VM in VirtualBox. In the VM X Window session, logon as the default user osboxes.
 How to use apt-get to update Ubuntu Revised: 15-August-2016 In our last two "How To" documents, we stepped through installing Oracle VirtualBox and Ubuntu 16.04 as a guest OS. This document how to apply
How to use apt-get to update Ubuntu Revised: 15-August-2016 In our last two "How To" documents, we stepped through installing Oracle VirtualBox and Ubuntu 16.04 as a guest OS. This document how to apply
iptables and ip6tables An introduction to LINUX firewall
 7 19-22 November, 2017 Dhaka, Bangladesh iptables and ip6tables An introduction to LINUX firewall Imtiaz Rahman SBAC Bank Ltd AGENDA iptables and ip6tables Structure Policy (DROP/ACCEPT) Syntax Hands on
7 19-22 November, 2017 Dhaka, Bangladesh iptables and ip6tables An introduction to LINUX firewall Imtiaz Rahman SBAC Bank Ltd AGENDA iptables and ip6tables Structure Policy (DROP/ACCEPT) Syntax Hands on
Stateless Firewall Implementation
 Stateless Firewall Implementation Network Security Lab, 2016 Group 16 B.Gamaliel K.Noellar O.Vincent H.Tewelde Outline : I. Enviroment Setup II. Today s Task III. Conclusion 2 Lab Objectives : After this
Stateless Firewall Implementation Network Security Lab, 2016 Group 16 B.Gamaliel K.Noellar O.Vincent H.Tewelde Outline : I. Enviroment Setup II. Today s Task III. Conclusion 2 Lab Objectives : After this
Open a browser and download the Apache Tomcat 7 and Oracle JDBC 6 JAR from these locations. The Oracle site may require that you register as a user.
 Installing Tomcat 7 on CentOS 7 David J. Walling, March 8 th, 2017 Email: david@davidjwalling.com This how to describes a process to download and install Apache Tomcat 7 on a CentOS 7 virtual machine using
Installing Tomcat 7 on CentOS 7 David J. Walling, March 8 th, 2017 Email: david@davidjwalling.com This how to describes a process to download and install Apache Tomcat 7 on a CentOS 7 virtual machine using
Click on the VM IMAGES drop-down menu and select VirtualBox Images
 How to install Ubuntu Linux in VirtualBox Revised: 12-August-2016, David Walling In our previous How To, we stepped through how to download and install Oracle VirtualBox on a Windows 10 host. This How
How to install Ubuntu Linux in VirtualBox Revised: 12-August-2016, David Walling In our previous How To, we stepped through how to download and install Oracle VirtualBox on a Windows 10 host. This How
BPPM Patrol Agent Installation Steps on Linux and Automation Integration
 BPPM Patrol Agent Installation Steps on Linux and Automation Integration Author: Karlis Peterson, Software Consultant, BMC Software Version: 1.0 Date: May 12, 2013 DISCLAIMER NOTICE This is Field Developed
BPPM Patrol Agent Installation Steps on Linux and Automation Integration Author: Karlis Peterson, Software Consultant, BMC Software Version: 1.0 Date: May 12, 2013 DISCLAIMER NOTICE This is Field Developed
Communication protocols and services
 This chapter describes various protocols and that may be enabled on Modberry. SSH Connection SSH service is started up on boot and already preinstalled and configured. You may access your device through
This chapter describes various protocols and that may be enabled on Modberry. SSH Connection SSH service is started up on boot and already preinstalled and configured. You may access your device through
Firewalls. IT443 Network Security Administration Slides courtesy of Bo Sheng
 Firewalls IT443 Network Security Administration Slides courtesy of Bo Sheng 1 Internet Security Mechanisms Prevent: Firewall, IPsec, SSL Detect: Intrusion Detection Survive/ Response: Recovery, Forensics
Firewalls IT443 Network Security Administration Slides courtesy of Bo Sheng 1 Internet Security Mechanisms Prevent: Firewall, IPsec, SSL Detect: Intrusion Detection Survive/ Response: Recovery, Forensics
This material is based on work supported by the National Science Foundation under Grant No
 Source: http://en.wikipedia.org/wiki/file:firewall.png This material is based on work supported by the National Science Foundation under Grant No. 0802551 Any opinions, findings, and conclusions or recommendations
Source: http://en.wikipedia.org/wiki/file:firewall.png This material is based on work supported by the National Science Foundation under Grant No. 0802551 Any opinions, findings, and conclusions or recommendations
Bitnami Apache Solr for Huawei Enterprise Cloud
 Bitnami Apache Solr for Huawei Enterprise Cloud Description Apache Solr is an open source enterprise search platform from the Apache Lucene project. It includes powerful full-text search, highlighting,
Bitnami Apache Solr for Huawei Enterprise Cloud Description Apache Solr is an open source enterprise search platform from the Apache Lucene project. It includes powerful full-text search, highlighting,
Web Server ( ): FTP, SSH, HTTP, HTTPS, SMTP, POP3, IMAP, POP3S, IMAPS, MySQL (for some local services[qmail/vpopmail])
![Web Server ( ): FTP, SSH, HTTP, HTTPS, SMTP, POP3, IMAP, POP3S, IMAPS, MySQL (for some local services[qmail/vpopmail]) Web Server ( ): FTP, SSH, HTTP, HTTPS, SMTP, POP3, IMAP, POP3S, IMAPS, MySQL (for some local services[qmail/vpopmail])](/thumbs/72/66962801.jpg) The following firewall scripts will help you secure your web and db servers placed on the internet. The scenario is such that the MySQL db server is desired to receive db connections / traffic only from
The following firewall scripts will help you secure your web and db servers placed on the internet. The scenario is such that the MySQL db server is desired to receive db connections / traffic only from
Bitnami JRuby for Huawei Enterprise Cloud
 Bitnami JRuby for Huawei Enterprise Cloud Description JRuby is a 100% Java implementation of the Ruby programming language. It is Ruby for the JVM. JRuby provides a complete set of core built-in classes
Bitnami JRuby for Huawei Enterprise Cloud Description JRuby is a 100% Java implementation of the Ruby programming language. It is Ruby for the JVM. JRuby provides a complete set of core built-in classes
Bitnami MEAN for Huawei Enterprise Cloud
 Bitnami MEAN for Huawei Enterprise Cloud Description Bitnami MEAN Stack provides a complete development environment for mongodb and Node.js that can be deployed in one click. It includes the latest stable
Bitnami MEAN for Huawei Enterprise Cloud Description Bitnami MEAN Stack provides a complete development environment for mongodb and Node.js that can be deployed in one click. It includes the latest stable
Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning
 Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning Last revised 10-4-17 KonBoot Get into any account without the password Works on Windows and Linux No longer free Link Ch 5r From the
Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning Last revised 10-4-17 KonBoot Get into any account without the password Works on Windows and Linux No longer free Link Ch 5r From the
Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning
 Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning Last revised 1-11-17 KonBoot Get into any account without the password Works on Windows and Linux No longer free Link Ch 5r From the
Hands-On Ethical Hacking and Network Defense Chapter 5 Port Scanning Last revised 1-11-17 KonBoot Get into any account without the password Works on Windows and Linux No longer free Link Ch 5r From the
Parallel Programming
 Parallel Programming Installing Ubuntu Virtual Machine within VirtualBox Author B. Wilkinson - Modification date Januray 3, 2016 These instructions assume you have already installed VirtualBox (See separate
Parallel Programming Installing Ubuntu Virtual Machine within VirtualBox Author B. Wilkinson - Modification date Januray 3, 2016 These instructions assume you have already installed VirtualBox (See separate
Eaton NetWatch NetWatch installation and configuration guide VMware ESXi 3 Virtual architecture
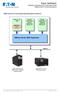 Eaton NetWatch NetWatch installation and configuration guide VMware ESXi 3 Virtual architecture VMware ESXi server host and guest operating systems architecture Vima 1.0 or vma Netwatch client Virtual/
Eaton NetWatch NetWatch installation and configuration guide VMware ESXi 3 Virtual architecture VMware ESXi server host and guest operating systems architecture Vima 1.0 or vma Netwatch client Virtual/
Lockdown & support access guide
 Lockdown & support access guide How to lock down your cloud, and enable the OnApp support team to help you with troubleshooting and ticket resolution. Document version 1.4 Document release date 21 st February
Lockdown & support access guide How to lock down your cloud, and enable the OnApp support team to help you with troubleshooting and ticket resolution. Document version 1.4 Document release date 21 st February
NIDS: Snort. Group 8. Niccolò Bisagno, Francesco Fiorenza, Giulio Carlo Gialanella, Riccardo Isoli
 NIDS: Snort Group 8 Niccolò Bisagno, Francesco Fiorenza, Giulio Carlo Gialanella, Riccardo Isoli 1 Summary NIDS Snort Syn Flood Attack Exploit Kit Detection: Bleeding Life Packet Level Evasion Snort as
NIDS: Snort Group 8 Niccolò Bisagno, Francesco Fiorenza, Giulio Carlo Gialanella, Riccardo Isoli 1 Summary NIDS Snort Syn Flood Attack Exploit Kit Detection: Bleeding Life Packet Level Evasion Snort as
Configure HOSTNAME by adding the hostname to the file /etc/sysconfig/network. Do the same to all the all nodes.
 Network setup As the root user execute the command "ifconfig" on each host. Take a note of ipaddress's of all machines I have a home LAN so my addresses are class C which might be in the format 192.168.192.x.
Network setup As the root user execute the command "ifconfig" on each host. Take a note of ipaddress's of all machines I have a home LAN so my addresses are class C which might be in the format 192.168.192.x.
Virtual Recovery Assistant user s guide
 Virtual Recovery Assistant user s guide Part number: T2558-96323 Second edition: March 2009 Copyright 2009 Hewlett-Packard Development Company, L.P. Hewlett-Packard Company makes no warranty of any kind
Virtual Recovery Assistant user s guide Part number: T2558-96323 Second edition: March 2009 Copyright 2009 Hewlett-Packard Development Company, L.P. Hewlett-Packard Company makes no warranty of any kind
Monitoring Windows Systems with WMI
 Monitoring Windows Systems with WMI ScienceLogic version 8.8.1 Table of Contents Introduction 4 Monitoring Windows Devices in the ScienceLogic Platform 5 What is SNMP? 5 What is WMI? 5 PowerPacks 5 Configuring
Monitoring Windows Systems with WMI ScienceLogic version 8.8.1 Table of Contents Introduction 4 Monitoring Windows Devices in the ScienceLogic Platform 5 What is SNMP? 5 What is WMI? 5 PowerPacks 5 Configuring
Bitnami Ruby for Huawei Enterprise Cloud
 Bitnami Ruby for Huawei Enterprise Cloud Description Bitnami Ruby Stack provides a complete development environment for Ruby on Rails that can be deployed in one click. It includes most popular components
Bitnami Ruby for Huawei Enterprise Cloud Description Bitnami Ruby Stack provides a complete development environment for Ruby on Rails that can be deployed in one click. It includes most popular components
User Agent Preparing the Windows Environment and Installing the User Agent. How-To
 User Agent 1.1.5 Preparing the Windows Environment and Installing the User Agent How-To CONTENTS Introduction to the User Agent... 2 Selecting the User Account to Run the User Agent... 3 Setting Access
User Agent 1.1.5 Preparing the Windows Environment and Installing the User Agent How-To CONTENTS Introduction to the User Agent... 2 Selecting the User Account to Run the User Agent... 3 Setting Access
Configure HOSTNAME by adding the hostname to the file /etc/sysconfig/network. Do the same to all the other 3(4) nodes.
 Network setup As the root user execute the command "ifconfig" on each host. Take a note of ipaddress's of all machines I have a home LAN so my addresses are class C which might be in the format 192.168.192.x.
Network setup As the root user execute the command "ifconfig" on each host. Take a note of ipaddress's of all machines I have a home LAN so my addresses are class C which might be in the format 192.168.192.x.
Setting up a Chaincoin Masternode
 Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Bitnami MySQL for Huawei Enterprise Cloud
 Bitnami MySQL for Huawei Enterprise Cloud Description MySQL is a fast, reliable, scalable, and easy to use open-source relational database system. MySQL Server is intended for mission-critical, heavy-load
Bitnami MySQL for Huawei Enterprise Cloud Description MySQL is a fast, reliable, scalable, and easy to use open-source relational database system. MySQL Server is intended for mission-critical, heavy-load
How to Configure a Remote Management Tunnel for an F-Series Firewall
 How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
Parallels Plesk Control Panel. Plesk 8.4 for Linux/Unix Firewall Module Administrator's Guide. Revision 1.0
 Parallels Plesk Control Panel Plesk 8.4 for Linux/Unix Firewall Module Administrator's Guide Revision 1.0 Copyright Notice ISBN: N/A Parallels 660 SW 39th Street Suite 205 Renton, Washington 98057 USA
Parallels Plesk Control Panel Plesk 8.4 for Linux/Unix Firewall Module Administrator's Guide Revision 1.0 Copyright Notice ISBN: N/A Parallels 660 SW 39th Street Suite 205 Renton, Washington 98057 USA
Introduction TELE 301. Routers. Firewalls. Gateways. Sample Large Network
 Introduction TELE 301 Lecture 21: s David Eyers (dme@cs.otago.ac.nz) Telecommunications Programme University of Otago Discernment of Routers, s, Gateways Placement of such devices Elementary firewalls
Introduction TELE 301 Lecture 21: s David Eyers (dme@cs.otago.ac.nz) Telecommunications Programme University of Otago Discernment of Routers, s, Gateways Placement of such devices Elementary firewalls
How to Secure SSH with Google Two-Factor Authentication
 How to Secure SSH with Google Two-Factor Authentication WELL, SINCE IT IS QUITE COMPLEX TO SET UP, WE VE DECIDED TO DEDICATE A WHOLE BLOG TO THAT PARTICULAR STEP! A few weeks ago we took a look at how
How to Secure SSH with Google Two-Factor Authentication WELL, SINCE IT IS QUITE COMPLEX TO SET UP, WE VE DECIDED TO DEDICATE A WHOLE BLOG TO THAT PARTICULAR STEP! A few weeks ago we took a look at how
PVS Deployment in the Cloud. Last Updated: June 17, 2016
 PVS Deployment in the Cloud Last Updated: June 17, 2016 Contents Amazon Web Services Introduction 3 Software Requirements 4 Set up a NAT Gateway 5 Install PVS on the NAT Gateway 11 Example Deployment 12
PVS Deployment in the Cloud Last Updated: June 17, 2016 Contents Amazon Web Services Introduction 3 Software Requirements 4 Set up a NAT Gateway 5 Install PVS on the NAT Gateway 11 Example Deployment 12
Expedition. Hardening Guide Version Palo Alto Networks, Inc.
 Expedition Hardening Guide Version 1.0 1 Palo Alto Networks, Inc. www.paloaltonetworks.com 2018 Palo Alto Networks, Inc. Palo Alto Networks is a registered trademark of Palo Alto Networks. You can find
Expedition Hardening Guide Version 1.0 1 Palo Alto Networks, Inc. www.paloaltonetworks.com 2018 Palo Alto Networks, Inc. Palo Alto Networks is a registered trademark of Palo Alto Networks. You can find
Lab - Configure the Firewall in Windows 8
 Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected over the network Windows 8 installed
Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected over the network Windows 8 installed
OPENSTACK CLOUD RUNNING IN A VIRTUAL MACHINE. In Preferences, add 3 Host-only Ethernet Adapters with the following IP Addresses:
 OPENSTACK CLOUD RUNNING IN A VIRTUAL MACHINE VirtualBox Install VirtualBox In Preferences, add 3 Host-only Ethernet Adapters with the following IP Addresses: 192.168.1.2/24 192.168.2.2/24 192.168.3.2/24
OPENSTACK CLOUD RUNNING IN A VIRTUAL MACHINE VirtualBox Install VirtualBox In Preferences, add 3 Host-only Ethernet Adapters with the following IP Addresses: 192.168.1.2/24 192.168.2.2/24 192.168.3.2/24
SQL Server vnext on Linux Ubuntu - Part 1
 SQL Server vnext on Linux Ubuntu - Part 1 Built on SQL Server 2016, SQL Server vnext represents a major step towards making SQL Server a cross operating systems and bringing the power of SQL Server to
SQL Server vnext on Linux Ubuntu - Part 1 Built on SQL Server 2016, SQL Server vnext represents a major step towards making SQL Server a cross operating systems and bringing the power of SQL Server to
UNIT 9 Introduction to Linux and Ubuntu
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT 9 Introduction to Linux and Ubuntu Learning Objectives Participants will understand the basics of Linux, including the nature,
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT 9 Introduction to Linux and Ubuntu Learning Objectives Participants will understand the basics of Linux, including the nature,
Who s Attacking Your Database? Monitoring Authentication and Logon Failures in SQL Server
 Who s Attacking Your Database? Monitoring Authentication and Logon Failures in SQL Server Sponsored by 2016 Monterey Technology Group Inc. Made possible by Thanks to www.logbinder.com 1 Preview of Key
Who s Attacking Your Database? Monitoring Authentication and Logon Failures in SQL Server Sponsored by 2016 Monterey Technology Group Inc. Made possible by Thanks to www.logbinder.com 1 Preview of Key
Bitnami MariaDB for Huawei Enterprise Cloud
 Bitnami MariaDB for Huawei Enterprise Cloud First steps with the Bitnami MariaDB Stack Welcome to your new Bitnami application running on Huawei Enterprise Cloud! Here are a few questions (and answers!)
Bitnami MariaDB for Huawei Enterprise Cloud First steps with the Bitnami MariaDB Stack Welcome to your new Bitnami application running on Huawei Enterprise Cloud! Here are a few questions (and answers!)
Setting up PuTTY. Version Updated for 2015 Fall (with corrections)
 Setting up PuTTY CTEC1330 Data and Telecommunications CTEC1767 Data Communications & Networking I CTEC1863 Operating Systems CTEC1906 Internet Computing Version 1.9.2 Updated for 2015 Fall (with corrections)
Setting up PuTTY CTEC1330 Data and Telecommunications CTEC1767 Data Communications & Networking I CTEC1863 Operating Systems CTEC1906 Internet Computing Version 1.9.2 Updated for 2015 Fall (with corrections)
Setting up PuTTY. Software* Downoad PuTTY. Download PuTTY Download the putty.zip file. It contains several programs for SSH, SFTP, and SCP.
 Software* Setting up PuTTY Microsoft Windows 7 PuTTY 0.65 PuTTYgen 0.65 WinSCP 5.7.5 CTEC1330 Data and Telecommunications CTEC1767 Data Communications & Networking I CTEC1863 Operating Systems CTEC1906
Software* Setting up PuTTY Microsoft Windows 7 PuTTY 0.65 PuTTYgen 0.65 WinSCP 5.7.5 CTEC1330 Data and Telecommunications CTEC1767 Data Communications & Networking I CTEC1863 Operating Systems CTEC1906
Installing and Upgrading Cisco Network Registrar Virtual Appliance
 CHAPTER 3 Installing and Upgrading Cisco Network Registrar Virtual Appliance The Cisco Network Registrar virtual appliance includes all the functionality available in a version of Cisco Network Registrar
CHAPTER 3 Installing and Upgrading Cisco Network Registrar Virtual Appliance The Cisco Network Registrar virtual appliance includes all the functionality available in a version of Cisco Network Registrar
Configuring Cross Platform Monitoring Using System Centre Operation Manager 2007 R2
 Configuring Cross Platform Monitoring Using System Centre Operation Manager 2007 R2 One of the more desirable features introduced in System Center Operations Manager 2007 R2 is the ability to monitor non-windows
Configuring Cross Platform Monitoring Using System Centre Operation Manager 2007 R2 One of the more desirable features introduced in System Center Operations Manager 2007 R2 is the ability to monitor non-windows
Preparing Your Google Cloud VM for W4705
 Preparing Your Google Cloud VM for W4705 August 27, 2017 1. Get a cloud.cs.columbia.edu account 1. Sign up for a cloud Columbia CS account using this link. Note that is is an entirely new account and is
Preparing Your Google Cloud VM for W4705 August 27, 2017 1. Get a cloud.cs.columbia.edu account 1. Sign up for a cloud Columbia CS account using this link. Note that is is an entirely new account and is
Config Server Firewall. Đặng Thanh Bình
 Config Server Firewall Đặng Thanh Bình Contents Introduction Features Installation Basic CSF commands Advanced Configuration 2 INTRODUCTION Intro Config Server Firewall (CSF) is a free and advanced firewall
Config Server Firewall Đặng Thanh Bình Contents Introduction Features Installation Basic CSF commands Advanced Configuration 2 INTRODUCTION Intro Config Server Firewall (CSF) is a free and advanced firewall
Overview of the Cisco NCS Command-Line Interface
 CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
Configuring a Palo Alto Firewall in AWS
 Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
OpenStack Havana All-in-One lab on VMware Workstation
 OpenStack Havana All-in-One lab on VMware Workstation With all of the popularity of OpenStack in general, and specifically with my other posts on deploying the Rackspace Private Cloud lab on VMware Workstation,
OpenStack Havana All-in-One lab on VMware Workstation With all of the popularity of OpenStack in general, and specifically with my other posts on deploying the Rackspace Private Cloud lab on VMware Workstation,
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Dr. Tom Hicks. Computer Science Department Trinity University
 Dr. Tom Hicks Computer Science Department Trinity University 1 1 Remote Desktop Into CS-X That Contains Your Switch? Open Putty To Your Switch 2 What is the Command To Go Into Privilege Mode DO IT! enable
Dr. Tom Hicks Computer Science Department Trinity University 1 1 Remote Desktop Into CS-X That Contains Your Switch? Open Putty To Your Switch 2 What is the Command To Go Into Privilege Mode DO IT! enable
Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development
 Weekly Tasks Week 5 Rich Macfarlane 2013 Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development Aim: The aim of these labs are to further investigate the Snort, network IDS, and methods
Weekly Tasks Week 5 Rich Macfarlane 2013 Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development Aim: The aim of these labs are to further investigate the Snort, network IDS, and methods
CSC 474/574 Information Systems Security
 CSC 474/574 Information Systems Security Topic 7.4 Firewalls CSC 474/574 Dr. Peng Ning 1 Outline What are firewalls? Types Filtering Packet filtering Session filtering Proxy Circuit Level Application Level
CSC 474/574 Information Systems Security Topic 7.4 Firewalls CSC 474/574 Dr. Peng Ning 1 Outline What are firewalls? Types Filtering Packet filtering Session filtering Proxy Circuit Level Application Level
:13 1/10 Traffic counting on the CCGX
 2017-08-18 15:13 1/10 Traffic counting on the CCGX Traffic counting on the CCGX There are situation in which it is interesting to know the traffic usage of the color control. This can be done on the CCGX
2017-08-18 15:13 1/10 Traffic counting on the CCGX Traffic counting on the CCGX There are situation in which it is interesting to know the traffic usage of the color control. This can be done on the CCGX
Remote Process Explorer
 Remote Process Explorer Frequently Asked Questions LizardSystems Table of Contents Introduction 3 What is Remote Process Explorer? 3 Before Installing 3 How can I download Remote Process Explorer? 3 Will
Remote Process Explorer Frequently Asked Questions LizardSystems Table of Contents Introduction 3 What is Remote Process Explorer? 3 Before Installing 3 How can I download Remote Process Explorer? 3 Will
Instituto Superior Técnico, Universidade de Lisboa Network and Computer Security. Lab guide: Traffic analysis and TCP/IP Vulnerabilities
 Instituto Superior Técnico, Universidade de Lisboa Network and Computer Security Lab guide: Traffic analysis and TCP/IP Vulnerabilities Revised on 2016-10-18 Alpha version: This is an early version and
Instituto Superior Técnico, Universidade de Lisboa Network and Computer Security Lab guide: Traffic analysis and TCP/IP Vulnerabilities Revised on 2016-10-18 Alpha version: This is an early version and
Adding a Boot Disk Entry to an HP Integrity rx2660
 Effective: 12/18/18 Revision: A Adding a Boot Disk Entry to an HP Integrity rx2660 Necessary Items Terminal Emulator application (e.g., PuTTY). Hard drive to be mounted. Overview In order to boot an rx2660
Effective: 12/18/18 Revision: A Adding a Boot Disk Entry to an HP Integrity rx2660 Necessary Items Terminal Emulator application (e.g., PuTTY). Hard drive to be mounted. Overview In order to boot an rx2660
ADSelfService Plus Client Software Installation via Group Policy Objects (GPOs)
 ADSelfService Plus Client Software Installation via Group Policy Objects (GPOs) Contents Document Summary:... 3 ADSelfService Plus Client Software:... 3 ADSelfService Plus Client Software Installation
ADSelfService Plus Client Software Installation via Group Policy Objects (GPOs) Contents Document Summary:... 3 ADSelfService Plus Client Software:... 3 ADSelfService Plus Client Software Installation
Basic Linux Desktop Security. Konrad Rosenbaum this presentation is protected by the GNU General Public License version 2 or any newer
 Basic Linux Desktop Security Konrad Rosenbaum this presentation is protected by the GNU General Public License version 2 or any newer Think Security: 5Q 1)What is the problem? 2)What is the proposed solution?
Basic Linux Desktop Security Konrad Rosenbaum this presentation is protected by the GNU General Public License version 2 or any newer Think Security: 5Q 1)What is the problem? 2)What is the proposed solution?
Jaringan Komputer (CCNA-1)
 Jaringan Komputer (CCNA-1) #2 Configuring a Network Operating System Susmini I. Lestariningati, M.T Introduction (1) Home networks typically interconnect a wide variety of end devices including PCs, laptops,
Jaringan Komputer (CCNA-1) #2 Configuring a Network Operating System Susmini I. Lestariningati, M.T Introduction (1) Home networks typically interconnect a wide variety of end devices including PCs, laptops,
Contrail Sandbox Tutorial Script
 Contrail Sandbox Tutorial Script Tutorial Flow Login to lab setup Add security rules Add IP address manager Add two networks Add network policy Add two VMs (can t ping) Add network policy to networks (VMs
Contrail Sandbox Tutorial Script Tutorial Flow Login to lab setup Add security rules Add IP address manager Add two networks Add network policy Add two VMs (can t ping) Add network policy to networks (VMs
EASYLAMP UBUNTU V1.0 DOCUMENT OWNER: OUDHUIS, JONATHAN INGRAM MICRO CLOUD EUROPE
 EASYLAMP UBUNTU V1.0 DOCUMENT OWNER: OUDHUIS, JONATHAN INGRAM MICRO CLOUD EUROPE CONTENTS 1 Introduction... 2 2 Creating and configuring a virtual machine... 3 3 Installing Apache... 8 4 Installing MySQL...
EASYLAMP UBUNTU V1.0 DOCUMENT OWNER: OUDHUIS, JONATHAN INGRAM MICRO CLOUD EUROPE CONTENTS 1 Introduction... 2 2 Creating and configuring a virtual machine... 3 3 Installing Apache... 8 4 Installing MySQL...
Eaton Intelligent Power Manager as a Virtual Appliance Deployment s Guide
 Eaton Intelligent Power Manager as a Virtual Appliance Deployment s Guide Table of Contents 1 Introduction... 3 2 Free Version Limitation... 3 3 Virtualization Platform Supported... 3 4 Requirements...
Eaton Intelligent Power Manager as a Virtual Appliance Deployment s Guide Table of Contents 1 Introduction... 3 2 Free Version Limitation... 3 3 Virtualization Platform Supported... 3 4 Requirements...
ACL Compliance Director Tutorial
 Abstract Copyright 2008 Cyber Operations, Inc. This is a tutorial on ACL Compliance Director intended to guide new users through the core features of the system. Table of Contents Introduction... 1 Login
Abstract Copyright 2008 Cyber Operations, Inc. This is a tutorial on ACL Compliance Director intended to guide new users through the core features of the system. Table of Contents Introduction... 1 Login
This tutorial will guide you how to setup and run your own minecraft server on a Linux CentOS 6 in no time.
 This tutorial will guide you how to setup and run your own minecraft server on a Linux CentOS 6 in no time. Running your own server lets you play together with your friends and family with your own set
This tutorial will guide you how to setup and run your own minecraft server on a Linux CentOS 6 in no time. Running your own server lets you play together with your friends and family with your own set
Pexip Infinity and Amazon Web Services Deployment Guide
 Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Remote GUI access to a Linux computer using Tightvnc
 Remote GUI access to a Linux computer using Tightvnc The command line is a great way to manage a remote Linux computer if you don't mind typing in commands, but sometimes you need to be able to view a
Remote GUI access to a Linux computer using Tightvnc The command line is a great way to manage a remote Linux computer if you don't mind typing in commands, but sometimes you need to be able to view a
08 March 2017 NETOP HOST FOR ANDROID USER S GUIDE
 08 March 2017 NETOP HOST FOR ANDROID USER S GUIDE Contents 1 Introduction... 2 1.1 Document Scope... 2 1.2 Technical Specifications... 2 2 Using the Netop Host... 3 2.1 Netop Host Display... 3 2.2 Netop
08 March 2017 NETOP HOST FOR ANDROID USER S GUIDE Contents 1 Introduction... 2 1.1 Document Scope... 2 1.2 Technical Specifications... 2 2 Using the Netop Host... 3 2.1 Netop Host Display... 3 2.2 Netop
Introduction p. 1 The Need for Security p. 2 Public Network Threats p. 2 Private Network Threats p. 4 The Role of Routers p. 5 Other Security Devices
 Preface p. xv Acknowledgments p. xvii Introduction p. 1 The Need for Security p. 2 Public Network Threats p. 2 Private Network Threats p. 4 The Role of Routers p. 5 Other Security Devices p. 6 Firewall
Preface p. xv Acknowledgments p. xvii Introduction p. 1 The Need for Security p. 2 Public Network Threats p. 2 Private Network Threats p. 4 The Role of Routers p. 5 Other Security Devices p. 6 Firewall
Lab Authentication, Authorization, and Accounting
 Objectives Given a scenario, select the appropriate authentication, authorization, or access control Install and configure security controls when performing account management, based on best practices
Objectives Given a scenario, select the appropriate authentication, authorization, or access control Install and configure security controls when performing account management, based on best practices
Purpose. Target Audience. Install SNMP On The Remote Linux Machine. Nagios XI. Monitoring Linux Using SNMP
 Purpose This document describes how to monitor Linux machines with using SNMP. SNMP is an agentless method of monitoring network devices and servers, and is often preferable to installing dedicated agents
Purpose This document describes how to monitor Linux machines with using SNMP. SNMP is an agentless method of monitoring network devices and servers, and is often preferable to installing dedicated agents
Grandstream Networks, Inc. UCM6100 Security Manual
 Grandstream Networks, Inc. UCM6100 Security Manual Index Table of Contents OVERVIEW... 3 WEB UI ACCESS... 4 UCM6100 HTTP SERVER ACCESS... 4 PROTOCOL TYPE... 4 USER LOGIN... 4 LOGIN TIMEOUT... 5 TWO-LEVEL
Grandstream Networks, Inc. UCM6100 Security Manual Index Table of Contents OVERVIEW... 3 WEB UI ACCESS... 4 UCM6100 HTTP SERVER ACCESS... 4 PROTOCOL TYPE... 4 USER LOGIN... 4 LOGIN TIMEOUT... 5 TWO-LEVEL
Installing Cisco VTS on a VMware Environment, page 6 Installing the Virtual Topology Forwarder, page 9 Verifying VTS Installation, page 14
 The following sections provide details about installing VTS on a Linux-OpenStack environment or a VMware-based environment. Ensure that you review the Prerequisites chapter, before you begin installing
The following sections provide details about installing VTS on a Linux-OpenStack environment or a VMware-based environment. Ensure that you review the Prerequisites chapter, before you begin installing
ADVANCED COMPUTER NETWORKS Assignment 9: Introduction to OpenFlow
 Spring Term 2014 ADVANCED COMPUTER NETWORKS Assignment 9: Introduction to OpenFlow Assigned on: 8 May 2014 Due by: 21 May 2014, 23:59 1 Introduction The goal of this assignment is to give an introduction
Spring Term 2014 ADVANCED COMPUTER NETWORKS Assignment 9: Introduction to OpenFlow Assigned on: 8 May 2014 Due by: 21 May 2014, 23:59 1 Introduction The goal of this assignment is to give an introduction
Cyber Common Technical Core (CCTC) Advance Sheet Windows Operating Systems
 Cyber Common Technical Core (CCTC) Advance Sheet Windows Operating Systems Section 1: Command Line Tools Skill 1: Employ commands using command line interface 1.1 Use command line commands to gain situational
Cyber Common Technical Core (CCTC) Advance Sheet Windows Operating Systems Section 1: Command Line Tools Skill 1: Employ commands using command line interface 1.1 Use command line commands to gain situational
VMware vsphere Replication Security Guide
 VMware Security Guide 6.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
VMware Security Guide 6.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
Setting up PuTTY. CTEC1767 Data Communications & Networking CTEC1863 Operating Systems CTEC1906 Internet Computing
 Setting up PuTTY CTEC1767 Data Communications & Networking CTEC1863 Operating Systems CTEC1906 Internet Computing Version 2.0 Updated for 2017 Winter Software* Microsoft Windows 7 (64-bit) PuTTY 0.67 PuTTYgen
Setting up PuTTY CTEC1767 Data Communications & Networking CTEC1863 Operating Systems CTEC1906 Internet Computing Version 2.0 Updated for 2017 Winter Software* Microsoft Windows 7 (64-bit) PuTTY 0.67 PuTTYgen
Configuring Control Plane Policing
 This chapter contains the following sections: Information About CoPP Information About CoPP, on page 1 Control Plane Protection, on page 2 CoPP Policy Templates, on page 4 CoPP Class Maps, on page 8 Packets
This chapter contains the following sections: Information About CoPP Information About CoPP, on page 1 Control Plane Protection, on page 2 CoPP Policy Templates, on page 4 CoPP Class Maps, on page 8 Packets
F5 BIG-IQ Centralized Management: Local Traffic & Network. Version 5.2
 F5 BIG-IQ Centralized Management: Local Traffic & Network Version 5.2 Table of Contents Table of Contents BIG-IQ Local Traffic & Network: Overview... 5 What is Local Traffic & Network?... 5 Understanding
F5 BIG-IQ Centralized Management: Local Traffic & Network Version 5.2 Table of Contents Table of Contents BIG-IQ Local Traffic & Network: Overview... 5 What is Local Traffic & Network?... 5 Understanding
Flexible Engine. Startup Guide
 Flexible Engine Startup Guide This guide presents the deployment of a web server accessible from the internet and its database, on the Flexible Engine platform 2017 Orange Business Services version July
Flexible Engine Startup Guide This guide presents the deployment of a web server accessible from the internet and its database, on the Flexible Engine platform 2017 Orange Business Services version July
NAT Router Performance Evaluation
 University of Aizu, Graduation Thesis. Mar, 22 17173 1 NAT Performance Evaluation HAYASHI yu-ichi 17173 Supervised by Atsushi Kara Abstract This thesis describes a quantitative analysis of NAT routers
University of Aizu, Graduation Thesis. Mar, 22 17173 1 NAT Performance Evaluation HAYASHI yu-ichi 17173 Supervised by Atsushi Kara Abstract This thesis describes a quantitative analysis of NAT routers
Linux Security & Firewall
 Linux Security & Firewall Linux is not secure No computer system can ever be "completely secure". make it increasingly difficult for someone to compromise your system. The more secure your system, the
Linux Security & Firewall Linux is not secure No computer system can ever be "completely secure". make it increasingly difficult for someone to compromise your system. The more secure your system, the
G-router GSM/GPRS to RS-232 and Ethernet Gateway Release Notes
 G-router GSM/GPRS to RS-232 and Ethernet Gateway Release Notes Author RFI Support Team Revision A0 Version RN_G-router_1.2.2 Date 23-05-2011 Covering Product code G-router, RE.40.QGSM Contents 1 Introduction...
G-router GSM/GPRS to RS-232 and Ethernet Gateway Release Notes Author RFI Support Team Revision A0 Version RN_G-router_1.2.2 Date 23-05-2011 Covering Product code G-router, RE.40.QGSM Contents 1 Introduction...
Introduction to lab assignments with GNS3
 Politecnico di Torino TSR/CNTS, PRL, PAR Introduction to lab assignments with GNS3 User guide and helpful tips Roberto Bonafiglia, Fulvio Risso October 27, 2017 Contents 1 Requirements 4 2 Access to GNS3
Politecnico di Torino TSR/CNTS, PRL, PAR Introduction to lab assignments with GNS3 User guide and helpful tips Roberto Bonafiglia, Fulvio Risso October 27, 2017 Contents 1 Requirements 4 2 Access to GNS3
Lab Router Configuration Using Setup Instructor Version 2500
 Lab 2.2.1 Router Configuration Using Setup Instructor Version 2500 Objective Use the System Configuration dialog (setup). Establish some basic router configurations. Background/Preparation A new router
Lab 2.2.1 Router Configuration Using Setup Instructor Version 2500 Objective Use the System Configuration dialog (setup). Establish some basic router configurations. Background/Preparation A new router
Windows Service Manually Command Line Start Remote Machine
 Windows Service Manually Command Line Start Remote Machine Instructions on manually installing or removing the DameWare Mini Remote Control EXE) or DameWare NT Utilities Client Agent Service (DNTUS26.
Windows Service Manually Command Line Start Remote Machine Instructions on manually installing or removing the DameWare Mini Remote Control EXE) or DameWare NT Utilities Client Agent Service (DNTUS26.
Gns3 You Must Use 'manual Mode' To Connect A Link
 Gns3 You Must Use 'manual Mode' To Connect A Link It puts the IOS into a sleep state when it is not in active use and wakes it up only when Well the reason for adding the modules is they offer the ability
Gns3 You Must Use 'manual Mode' To Connect A Link It puts the IOS into a sleep state when it is not in active use and wakes it up only when Well the reason for adding the modules is they offer the ability
How to Configure a Remote Management Tunnel for Barracuda NG Firewalls
 How to Configure a Remote Management Tunnel for Barracuda NG Firewalls If the managed NG Firewall can not directly reach the NG Control Center it must connect via a remote management tunnel. The remote
How to Configure a Remote Management Tunnel for Barracuda NG Firewalls If the managed NG Firewall can not directly reach the NG Control Center it must connect via a remote management tunnel. The remote
This release of the product includes these new features that have been added since NGFW 5.5.
 Release Notes Revision B McAfee Next Generation Firewall 5.7.4 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Release Notes Revision B McAfee Next Generation Firewall 5.7.4 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
PlateSpin Transformation Manager Appliance Guide. June 2018
 PlateSpin Transformation Manager Appliance Guide June 2018 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights,
PlateSpin Transformation Manager Appliance Guide June 2018 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights,
Lenovo ThinkAgile XClarity Integrator for Nutanix Installation and User's Guide
 Lenovo ThinkAgile XClarity Integrator for Nutanix Installation and User's Guide Version 1.0 Note Before using this information and the product it supports, read the information in Appendix A Notices on
Lenovo ThinkAgile XClarity Integrator for Nutanix Installation and User's Guide Version 1.0 Note Before using this information and the product it supports, read the information in Appendix A Notices on
Configuring High Availability for VMware vcenter in RMS All-In-One Setup
 Configuring High Availability for VMware vcenter in RMS All-In-One Setup This chapter describes the process of configuring high availability for the VMware vcenter in an RMS All-In-One setup. It provides
Configuring High Availability for VMware vcenter in RMS All-In-One Setup This chapter describes the process of configuring high availability for the VMware vcenter in an RMS All-In-One setup. It provides
Network Security. Thierry Sans
 Network Security Thierry Sans HTTP SMTP DNS BGP The Protocol Stack Application TCP UDP Transport IPv4 IPv6 ICMP Network ARP Link Ethernet WiFi The attacker is capable of confidentiality integrity availability
Network Security Thierry Sans HTTP SMTP DNS BGP The Protocol Stack Application TCP UDP Transport IPv4 IPv6 ICMP Network ARP Link Ethernet WiFi The attacker is capable of confidentiality integrity availability
Sides Colour Coding. Applies to both Xp and Windows 7. Applies to Xp only. Applies to Vista and Windows 7 only
 GUIDE TO INSTALLING IQCARE This is a visual guide, it does not explicitly explain each and every detail. It also assumes you have a basic degree of technical knowledge Xp Vista Windows 7 Wamathaga Kamau
GUIDE TO INSTALLING IQCARE This is a visual guide, it does not explicitly explain each and every detail. It also assumes you have a basic degree of technical knowledge Xp Vista Windows 7 Wamathaga Kamau
Quick Start Guide to Compute Canada Cloud Service
 Quick Start Guide to Compute Canada Cloud Service Launching your first instance (VM) Login to the East or West cloud Dashboard SSH key pair Importing an existing key pair Creating a new key pair Launching
Quick Start Guide to Compute Canada Cloud Service Launching your first instance (VM) Login to the East or West cloud Dashboard SSH key pair Importing an existing key pair Creating a new key pair Launching
Enabling Remote Access to the ACE
 CHAPTER 3 Note The information in this chapter applies to both the ACE module and the ACE appliance unless otherwise noted. All features described in this chapter are supported with IPv6 unless otherwise
CHAPTER 3 Note The information in this chapter applies to both the ACE module and the ACE appliance unless otherwise noted. All features described in this chapter are supported with IPv6 unless otherwise
Sirindhorn International Institute of Technology Thammasat University
 Name.............................. ID............... Section...... Seat No...... Sirindhorn International Institute of Technology Thammasat University Course Title: IT Security Instructor: Steven Gordon
Name.............................. ID............... Section...... Seat No...... Sirindhorn International Institute of Technology Thammasat University Course Title: IT Security Instructor: Steven Gordon
Laboration 2 Troubleshooting Switching and First-Hop Redundancy
 Laboration 2 Troubleshooting Switching and First-Hop Redundancy Topology All contents are Copyright 1992 2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1
Laboration 2 Troubleshooting Switching and First-Hop Redundancy Topology All contents are Copyright 1992 2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1
Lab Configure Basic AP security through GUI
 Lab 8.3.1.1 Configure Basic AP security through GUI Estimated Time: 30 minutes Number of Team Members: Students will work in teams of two. Objective In this lab, the student will learn the following objectives:
Lab 8.3.1.1 Configure Basic AP security through GUI Estimated Time: 30 minutes Number of Team Members: Students will work in teams of two. Objective In this lab, the student will learn the following objectives:
Pexip Infinity and Amazon Web Services Deployment Guide
 Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
MassTransit 6.0 Installation Guide for Enterprise and Professional Servers on Macintosh
 MassTransit 6.0 Installation Guide for Enterprise and Professional Servers on Macintosh March 11, 2009 Group Logic, Inc. 1100 North Glebe Road, Suite 800 Arlington, VA 22201 Phone: 703-528-1555 Fax: 703-528-3296
MassTransit 6.0 Installation Guide for Enterprise and Professional Servers on Macintosh March 11, 2009 Group Logic, Inc. 1100 North Glebe Road, Suite 800 Arlington, VA 22201 Phone: 703-528-1555 Fax: 703-528-3296
