LAB2 - More about ns-3
|
|
|
- Maximillian Marsh
- 6 years ago
- Views:
Transcription
1 LAB2 - More about ns-3 CS169: Mobile Wireless Networks - Winter 2017 Kittipat Apicharttrisorn (Patrick) Department of Computer Science and Engineering University of California, Riverside January 23-24, 2017 Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
2 Table of Contents 1 Logging Modules 2 Command Line Arguments 3 Tracing Systems Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
3 NS-3 Logging Go to working directory $ cd /extra/csusername/cs169lab/ns-allinone-3.25/ns-3.25 $ cp examples/tutorial/first.cc scratch/myfirst.cc $./waf $./waf --run scratch/myfirst Observe the logs... What cause them? LogComponentEnable( UdpEchoClientApplication, LOG LEVEL INFO); Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
4 Log Verbosity Levels More verbose LOG_ERROR LOG_WARN LOG_DEBUG LOG_INFO LOG_FUNCTION LOG_LEVEL_INFO LOG_LOGIC LOG_ALL Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
5 Log more, see more $ export NS LOG=UdpEchoClientApplication=level all $ export NS LOG=UdpEchoClientApplication=level all prefix func $ export NS LOG=UdpEchoClientApplication= level all prefix func : UdpEchoServerApplication=level all prefix func $ export NS LOG=UdpEchoClientApplication= level all prefix func prefix time: UdpEchoServerApplication= level all prefix func prefix time Log-all-application Masking export NS LOG=*=level all prefix func prefix time Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
6 Adding your own logs $ vim scratch/myfirst.cc NS LOG COMPONENT DEFINE ( FirstScriptExample ); NS LOG INFO( Creating Topology ); NodeContainer nodes; nodes.create (2); $./waf Clear NS LOG variables $ export NS LOG= Running... $./waf --run scratch/myfirst Do you see the log? Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
7 Seeing your own logs $ export NS LOG=FirstScriptExample=info $./waf --run scratch/myfirst $ export NS LOG=FirstScriptExample=level info $./waf --run scratch/myfirst Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
8 Command Line Arguments When we wanted to alter attribute values,... PointToPointHelper pointtopoint; pointtopoint.setdeviceattribute ( DataRate, StringValue ( 5Mbps )); pointtopoint.setchannelattribute ( Delay, StringValue ( 2ms )); Now, we want to pass these as command line arguments, then go to myfirst.cc and declare the command line parser CommandLine cmd; cmd.parse (argc, argv); Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
9 Looking for help... $./waf --run "scratch/myfirst --PrintHelp" Print attributes $./waf --run "scratch/myfirst --PrintAttributes=ns3::PointToPointNetDevice" Remove these two lines from the script pointtopoint.setdeviceattribute ( DataRate, StringValue ( 5Mbps )); pointtopoint.setchannelattribute ( Delay, StringValue ( 2ms )); Set attributes $./waf --run "scratch/myfirst --ns3::pointtopointnetdevice::datarate=5mbps" Do not forget Double quotes when passing arguments Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
10 Exercise I Hints! Insert more LOG INFO for FirstScriptExample Ex. Creating Topology, Assigning IP Addresses, Creating echoserver What is the default channel delay value? Set channel delay to 4 ms using CLA Set max packets to 4 using CLA Set data rate, channel delay, and max packets at the same run using CLA $./waf --run "scratch/myfirst --PrintGroup=PointToPoint" $./waf --run "scratch/myfirst --ns3::udpechoclient::maxpackets=4" Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
11 Using your own values Just before cmd.parse (argc, argv); add uint32 t npackets = 1; cmd.addvalue( npackets, Number of packets to echo, npackets); Type echoclient.setattribute ( MaxPackets, UintegerValue (npackets)); $./waf --run "scratch/myfirst --npackets=4" Good to know Using your own values, you do not have to know ns3 Group and Argument names (ex. ns3::udpechoclient::maxpackets) but knowing some of them allows you to get the default values used by ns3. Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
12 Tracing Systems How can you look at IP headers by using LOG? Tracing Systems are extended logging systems that provide users with more customizations. Trace source trace sink ASCII Tracing: Add the following two lines before Simulator::Run AsciiTraceHelper ascii; pointtopoint.enableasciiall (ascii.createfilestream ( myfirst.tr )); Run the script again Open myfirst.tr Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
13 ASCII Trace I Figure: ASCII Trace Event Locator Figure: ASCII Trace Event I Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
14 ASCII Trace II Figure: ASCII Trace Event Locator Figure: ASCII Trace Event II Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
15 Pcap Tracing Exercise Add this line of code before Simulator::Run pointtopoint.enablepcapall ( myfirst ); myfirst will be the prefix of the real file names: myfirst-0-0.pcap and myfirst-1-0.pcap Find a computer with Wireshark installed ( and remote access to your lab machine (tango or delta) and secure copy (scp) myfirst-0-0.pcap and myfirst-1-0.pcap from tango or delta to your Wireshark-installed computer. Finally, open pcap files using Wireshark and look around the TCP/IP headers and packet sizes (total packet length vs. data length) Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
16 Table of Contents 1 Logging Modules 2 Command Line Arguments 3 Tracing Systems Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
17 Questions? Kittipat Apicharttrisorn (Patrick) (Department of Computer LAB2Science - Moreand about Engineering ns-3 University of California, January 23-24, Riverside) / 17
LAB1 - Introduction to ns-3
 LAB1 - Introduction to ns-3 CS169: Mobile Wireless Networks - Winter 2017 Kittipat Apicharttrisorn (Patrick) Department of Computer Science and Engineering University of California, Riverside January 9,
LAB1 - Introduction to ns-3 CS169: Mobile Wireless Networks - Winter 2017 Kittipat Apicharttrisorn (Patrick) Department of Computer Science and Engineering University of California, Riverside January 9,
Point To Point Topology Default Application
 Point To Point Topology Default Application STVN 2016 Jointly organized by Poornima University, Jaipur & IIIT Kota Rahul Hada hada.rahul@gmail.com Scenario 1 Create a simple client server node and send
Point To Point Topology Default Application STVN 2016 Jointly organized by Poornima University, Jaipur & IIIT Kota Rahul Hada hada.rahul@gmail.com Scenario 1 Create a simple client server node and send
CCE 3301 Communication Systems Introduction to NS-3
 CCE 3301 Communication Systems Introduction to NS-3 Dr Ing. C.J. Debono Outline Introduction NS-3 module stack A simple example Lower level Scheduler Random variables Memory management Packets Nodes Callbacks
CCE 3301 Communication Systems Introduction to NS-3 Dr Ing. C.J. Debono Outline Introduction NS-3 module stack A simple example Lower level Scheduler Random variables Memory management Packets Nodes Callbacks
LAB6: Guildance to Final Projects
 LAB6: Guildance to Final Projects CS169: Mobile Wireless Networks - Winter 2017 Kittipat Apicharttrisorn (Patrick) Department of Computer Science and Engineering University of California, Riverside Febuary
LAB6: Guildance to Final Projects CS169: Mobile Wireless Networks - Winter 2017 Kittipat Apicharttrisorn (Patrick) Department of Computer Science and Engineering University of California, Riverside Febuary
Session 1. NS-3 의기초. 김선도 Multimedia & Wireless Networking Laboratory, SNU
 Session 1. NS-3 의기초 김선도 Multimedia & Wireless Networking Laboratory, SNU sdkim@mwnl.snu.ac.kr Contents Linux basic commands Introduction to NS-3 Starting NS-3 Simulation procedure Tweaking Tracing system
Session 1. NS-3 의기초 김선도 Multimedia & Wireless Networking Laboratory, SNU sdkim@mwnl.snu.ac.kr Contents Linux basic commands Introduction to NS-3 Starting NS-3 Simulation procedure Tweaking Tracing system
Introduction to NS-3
 Introduction to NS-3 Konstantinos Katsaros k.katsaros @ surrey.ac.uk Centre for Communications System Research University of Surrey System Level Simulations - Technical Club Outline 1 Introduction 2 NS-3
Introduction to NS-3 Konstantinos Katsaros k.katsaros @ surrey.ac.uk Centre for Communications System Research University of Surrey System Level Simulations - Technical Club Outline 1 Introduction 2 NS-3
Networks Simulation Corso di Tecnologie di Infrastrutture di Reti
 Networks Simulation Corso di Tecnologie di Infrastrutture di Reti Carlo Augusto Grazia Department of Engineering Enzo Ferrari University of Modena and Reggio Emilia Modena, 1 April 2015 C.A.Grazia (Unimore)
Networks Simulation Corso di Tecnologie di Infrastrutture di Reti Carlo Augusto Grazia Department of Engineering Enzo Ferrari University of Modena and Reggio Emilia Modena, 1 April 2015 C.A.Grazia (Unimore)
Session 4. DCE 를활용한실제 시스템과 NS-3 연동. 이규진 Multimedia & Wireless Networking Laboratory, SNU
 Session 4. DCE 를활용한실제 시스템과 NS-3 연동 이규진 Multimedia & Wireless Networking Laboratory, SNU gjlee@mwnl.snu.ac.kr 1 Overview 2 NS-3 DCE DCE (Direct Code Execution) A framework provides facilities to execute
Session 4. DCE 를활용한실제 시스템과 NS-3 연동 이규진 Multimedia & Wireless Networking Laboratory, SNU gjlee@mwnl.snu.ac.kr 1 Overview 2 NS-3 DCE DCE (Direct Code Execution) A framework provides facilities to execute
Networks Simulation Corso di Tecnologie di Infrastrutture di Reti
 Networks Simulation Corso di Tecnologie di Infrastrutture di Reti Carlo Augusto Grazia Department of Engineering Enzo Ferrari University of Modena and Reggio Emilia Modena, 16th March 2016 C.A.Grazia (Unimore)
Networks Simulation Corso di Tecnologie di Infrastrutture di Reti Carlo Augusto Grazia Department of Engineering Enzo Ferrari University of Modena and Reggio Emilia Modena, 16th March 2016 C.A.Grazia (Unimore)
ITTC Communication Networks The University of Kansas EECS 780 Introduction to Network Simulation with ns-3
 Communication Networks The University of Kansas EECS 780 Introduction to Network Simulation with ns-3 Anh Nguyen, Mohammed J.F. Alenazi, Egemen K. Çetinkaya, and James P.G. Sterbenz Department of Electrical
Communication Networks The University of Kansas EECS 780 Introduction to Network Simulation with ns-3 Anh Nguyen, Mohammed J.F. Alenazi, Egemen K. Çetinkaya, and James P.G. Sterbenz Department of Electrical
ITTC Mobile Wireless Networking The University of Kansas EECS 882 Introduction to Network Simulation with ns-3
 Mobile Wireless Networking The University of Kansas EECS 882 Introduction to Network Simulation with ns-3 Anh Nguyễn, Egemen K. Çetinkaya, James P.G. Sterbenz Department of Electrical Engineering & Computer
Mobile Wireless Networking The University of Kansas EECS 882 Introduction to Network Simulation with ns-3 Anh Nguyễn, Egemen K. Çetinkaya, James P.G. Sterbenz Department of Electrical Engineering & Computer
ns-3 Direct Code Execution (DCE) ns-3 Annual Meeting June 2018 ns-3 training, June
 ns-3 Direct Code Execution (DCE) ns-3 Annual Meeting June 2018 1 Outline DCE Introduction Download and Installation of DCE with Bake DCE examples with custom application: iperf ping Q&A 2 Credits DCE originated
ns-3 Direct Code Execution (DCE) ns-3 Annual Meeting June 2018 1 Outline DCE Introduction Download and Installation of DCE with Bake DCE examples with custom application: iperf ping Q&A 2 Credits DCE originated
Yes, we can ns-3-simu!
 Intro Yes, we can ns-3-simu! Hajime Tazaki tazaki@sfcwideadjp StarBED / Nebula Developers Workshop 2010 Summer Hajime Tazaki (Keio University) ns-3 or die SNDW, 27th July, 2010 1 / 45 Intro Objective of
Intro Yes, we can ns-3-simu! Hajime Tazaki tazaki@sfcwideadjp StarBED / Nebula Developers Workshop 2010 Summer Hajime Tazaki (Keio University) ns-3 or die SNDW, 27th July, 2010 1 / 45 Intro Objective of
The TCP Incast problem: the opposite of Buffer Bloat: what happens when ethernet switches don't have enough buffer?
 The TCP Incast problem: the opposite of Buffer Bloat: what happens when ethernet switches don't have enough buffer? Lincoln Dale Arista Networks Inc. ltd@aristanetworks.com About Arista How large scale
The TCP Incast problem: the opposite of Buffer Bloat: what happens when ethernet switches don't have enough buffer? Lincoln Dale Arista Networks Inc. ltd@aristanetworks.com About Arista How large scale
NS-3: Network Simulator 3
 NS-3: Network Simulator 3 Gustavo J. A. M. Carneiro INESC Porto / Faculdade de Engenharia / Universidade do Porto UTM Lab Meeting 2010-04-20 1 Outline NS-3 general overview NS-3 internal APIs overview
NS-3: Network Simulator 3 Gustavo J. A. M. Carneiro INESC Porto / Faculdade de Engenharia / Universidade do Porto UTM Lab Meeting 2010-04-20 1 Outline NS-3 general overview NS-3 internal APIs overview
Introduction to NS-3 COMPUTER NETWORKING MOHAMED KASSEM
 Introduction to NS-3 COMPUTER NETWORKING MOHAMED KASSEM What is NS-3? Discrete event network simulator Open Source Collection of C++ libraries, not a program Support under Linux, FreeBSD and Cygwin Installing
Introduction to NS-3 COMPUTER NETWORKING MOHAMED KASSEM What is NS-3? Discrete event network simulator Open Source Collection of C++ libraries, not a program Support under Linux, FreeBSD and Cygwin Installing
*************************************************************************************
 ************************************************************************************* Title:-Implement a fire detection system using relevant wireless sensor network install in remote area[a2] Name:- Pawar
************************************************************************************* Title:-Implement a fire detection system using relevant wireless sensor network install in remote area[a2] Name:- Pawar
Session 4. LTE in ns-3. 김선도 Multimedia & Wireless Networking Laboratory, SNU
 Session 4. LTE in ns-3 김선도 Multimedia & Wireless Networking Laboratory, SNU sdkim@mwnl.snu.ac.kr 1 LTE Overview LTE in ns-3 Simulation Examples Contents Packet Transmission Example In class Assignment
Session 4. LTE in ns-3 김선도 Multimedia & Wireless Networking Laboratory, SNU sdkim@mwnl.snu.ac.kr 1 LTE Overview LTE in ns-3 Simulation Examples Contents Packet Transmission Example In class Assignment
Session 6. LTE 응용및실습. Junseok Kim Multimedia & Wireless Networking Laboratory, SNU
 Session 6. LTE 응용및실습 Junseok Kim Multimedia & Wireless Networking Laboratory, SNU jskim14@mwnl.snu.ac.kr 1 Contents Application in Scratch File Uplink Transmission with UDP In Class Assignment Simulation
Session 6. LTE 응용및실습 Junseok Kim Multimedia & Wireless Networking Laboratory, SNU jskim14@mwnl.snu.ac.kr 1 Contents Application in Scratch File Uplink Transmission with UDP In Class Assignment Simulation
COMP1917: 09 Arrays and Strings
 COMP1917: 09 Arrays and Strings Sim Mautner s.mautner@unsw.edu.au August 15, 2016 Sim Mautner (UNSW) COMP1917: 09 Arrays and Strings August 15, 2016 1 / 14 Arrays int sum(int n1, int n2); int sum(int n1,
COMP1917: 09 Arrays and Strings Sim Mautner s.mautner@unsw.edu.au August 15, 2016 Sim Mautner (UNSW) COMP1917: 09 Arrays and Strings August 15, 2016 1 / 14 Arrays int sum(int n1, int n2); int sum(int n1,
To see how ARP (Address Resolution Protocol) works. ARP is an essential glue protocol that is used to join Ethernet and IP.
 Lab Exercise ARP Objective To see how ARP (Address Resolution Protocol) works. ARP is an essential glue protocol that is used to join Ethernet and IP. Requirements Wireshark: This lab uses the Wireshark
Lab Exercise ARP Objective To see how ARP (Address Resolution Protocol) works. ARP is an essential glue protocol that is used to join Ethernet and IP. Requirements Wireshark: This lab uses the Wireshark
COMPUTER NETWORKS. CPSC 441, Winter 2016 Prof. Mea Wang Department of Computer Science University of Calgary
 COMPUTER NETWORKS CPSC 441, Winter 2016 Prof. Mea Wang Department of Computer Science University of Calgary Introduction: Wireshark and tshark Running tshark Running Wireshark Exercise: Analyze HTTP traffic
COMPUTER NETWORKS CPSC 441, Winter 2016 Prof. Mea Wang Department of Computer Science University of Calgary Introduction: Wireshark and tshark Running tshark Running Wireshark Exercise: Analyze HTTP traffic
Integrating ns-3 Model Construction, Description, Preprocessing, Execution, and Visualization
 Integrating ns-3 Model Construction, Description, Preprocessing, Execution, and Visualization Workshop on ns-3 WNS3 2013 Cannes, France March 5, 2013 This work was performed under the auspices of the U.S.
Integrating ns-3 Model Construction, Description, Preprocessing, Execution, and Visualization Workshop on ns-3 WNS3 2013 Cannes, France March 5, 2013 This work was performed under the auspices of the U.S.
ns-3 Training Session 8: Monday 3:30pm ns-3 Annual Meeting May 2014
 ns-3 Training Session 8: Monday 3:30pm ns-3 Annual Meeting 1 NS-3 Annual Meeting Outline Emulation modes Tap Bridge FdNetDevice Direct Code Execution (DCE) Applications Linux Kernel DCE Cradle NS-3 Annual
ns-3 Training Session 8: Monday 3:30pm ns-3 Annual Meeting 1 NS-3 Annual Meeting Outline Emulation modes Tap Bridge FdNetDevice Direct Code Execution (DCE) Applications Linux Kernel DCE Cradle NS-3 Annual
Introduction to Wireshark
 Introduction to Wireshark CS3C03/SE4C03 Jason Jaskolka Department of Computing and Software Faculty of Engineering McMaster University Hamilton, Ontario, Canada jaskolj@mcmaster.ca Winter 2013 Jason Jaskolka
Introduction to Wireshark CS3C03/SE4C03 Jason Jaskolka Department of Computing and Software Faculty of Engineering McMaster University Hamilton, Ontario, Canada jaskolj@mcmaster.ca Winter 2013 Jason Jaskolka
Wireshark Lab: Getting Started
 Wireshark Lab: Getting Started This following content is edited from the wireshark lab exercise provided by J.F. Kurose, and K.W. Ross, "Computer Networking: A Top down approach" 5th ed. Pearson, 2010.
Wireshark Lab: Getting Started This following content is edited from the wireshark lab exercise provided by J.F. Kurose, and K.W. Ross, "Computer Networking: A Top down approach" 5th ed. Pearson, 2010.
Lab Assignment 3 for ECE374
 Lab Assignment 3 for ECE374 Posted: 02/25/18 Due: 03/08/18 In this lab, we ll take a quick look at the UDP and TCP transport protocol. Whenever possible you should hand in a Wireshark screenshot that you
Lab Assignment 3 for ECE374 Posted: 02/25/18 Due: 03/08/18 In this lab, we ll take a quick look at the UDP and TCP transport protocol. Whenever possible you should hand in a Wireshark screenshot that you
Installation of Ubuntu, ns3 and compiling first script for Network Animator (nam)
 REPORT Installation of Ubuntu, ns3 and compiling first script for Network Animator (nam) Jawad Ali Subject: ISPN and ComNets 08PWELE3546 Contents Vmware.exe and Ubuntu.iso downloading and installation...
REPORT Installation of Ubuntu, ns3 and compiling first script for Network Animator (nam) Jawad Ali Subject: ISPN and ComNets 08PWELE3546 Contents Vmware.exe and Ubuntu.iso downloading and installation...
NITK, Surathkal. Overview of ns-3. Mohit P. Tahiliani
 NITK, Surathkal Overview of ns-3 Mohit P. Tahiliani Assistant Professor, Department of Computer Science & Engineering, National Institute of Technology Karnataka, Surathkal Some of our work is listed @
NITK, Surathkal Overview of ns-3 Mohit P. Tahiliani Assistant Professor, Department of Computer Science & Engineering, National Institute of Technology Karnataka, Surathkal Some of our work is listed @
Avi Networks Technical Reference (17.2)
 Page 1 of 5 Packet Capture view online Most troubleshooting of connection or traffic data may be done quickly via virtual service logs. However, some troubleshooting may require full visibility into the
Page 1 of 5 Packet Capture view online Most troubleshooting of connection or traffic data may be done quickly via virtual service logs. However, some troubleshooting may require full visibility into the
CSE 390a Lecture 5. Intro to shell scripting
 CSE 390a Lecture 5 Intro to shell scripting slides created by Marty Stepp, modified by Jessica Miller & Ruth Anderson http://www.cs.washington.edu/390a/ 1 2 Lecture summary basic script syntax and running
CSE 390a Lecture 5 Intro to shell scripting slides created by Marty Stepp, modified by Jessica Miller & Ruth Anderson http://www.cs.washington.edu/390a/ 1 2 Lecture summary basic script syntax and running
Peer-to-Peer Traffic over LTE: Simulated Performance during Cell Crossover
 Peer-to-Peer Traffic over LTE: Simulated Performance during Cell Crossover ENSC 833: Network Protocols and Performance Spring 2016 Project Report Presented by :Shweta Mazumder, Brett Wiens, Katherine Manson
Peer-to-Peer Traffic over LTE: Simulated Performance during Cell Crossover ENSC 833: Network Protocols and Performance Spring 2016 Project Report Presented by :Shweta Mazumder, Brett Wiens, Katherine Manson
Wireshark Lab: Getting Started v6.0
 Wireshark Lab: Getting Started v6.0 Supplement to Computer Networking: A Top-Down Approach, 6 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand.
Wireshark Lab: Getting Started v6.0 Supplement to Computer Networking: A Top-Down Approach, 6 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand.
Programming Project II
 Programming Project II CS 322 Compiler Construction Winter Quarter 2006 Due: Saturday, January 28, at 11:59pm START EARLY! Description In this phase, you will produce a parser for our version of Pascal.
Programming Project II CS 322 Compiler Construction Winter Quarter 2006 Due: Saturday, January 28, at 11:59pm START EARLY! Description In this phase, you will produce a parser for our version of Pascal.
CSE 391 Lecture 5. Intro to shell scripting
 CSE 391 Lecture 5 Intro to shell scripting slides created by Marty Stepp, modified by Jessica Miller & Ruth Anderson http://www.cs.washington.edu/391/ 1 2 Lecture summary basic script syntax and running
CSE 391 Lecture 5 Intro to shell scripting slides created by Marty Stepp, modified by Jessica Miller & Ruth Anderson http://www.cs.washington.edu/391/ 1 2 Lecture summary basic script syntax and running
Ns-Modbus: Integration of Modbus with ns-3 network simulator
 Final Project Presentation Summer 2013 Ns-Modbus: Integration of Modbus with ns-3 network simulator Mohammad Reza Sahraei mrs16@sfu.ca May 8, 2013 1 Road map Introduction Background knowledge Ns-Modbus
Final Project Presentation Summer 2013 Ns-Modbus: Integration of Modbus with ns-3 network simulator Mohammad Reza Sahraei mrs16@sfu.ca May 8, 2013 1 Road map Introduction Background knowledge Ns-Modbus
Objectives: (1) To learn to capture and analyze packets using wireshark. (2) To learn how protocols and layering are represented in packets.
 Team Project 1 Due: Beijing 00:01, Friday Nov 7 Language: English Turn-in (via email) a.pdf file. Objectives: (1) To learn to capture and analyze packets using wireshark. (2) To learn how protocols and
Team Project 1 Due: Beijing 00:01, Friday Nov 7 Language: English Turn-in (via email) a.pdf file. Objectives: (1) To learn to capture and analyze packets using wireshark. (2) To learn how protocols and
Distributed Simulation with NS-3. Ken Renard US Army Research Lab
 Distributed Simulation with NS-3 Ken Renard US Army Research Lab Outline Introduction and Motivation for Distributed NS-3 Parallel Discrete Event Simulation MPI Concepts Distributed NS-3 Scheduler Limitations
Distributed Simulation with NS-3 Ken Renard US Army Research Lab Outline Introduction and Motivation for Distributed NS-3 Parallel Discrete Event Simulation MPI Concepts Distributed NS-3 Scheduler Limitations
Lab: 2. Wireshark Getting Started
 Lab: 2 Wireshark Getting Started One s understanding of network protocols can often be greatly deepened by seeing protocols in action and by playing around with protocols observing the sequence of messages
Lab: 2 Wireshark Getting Started One s understanding of network protocols can often be greatly deepened by seeing protocols in action and by playing around with protocols observing the sequence of messages
Lab: Supplying Inputs to Programs
 Steven Zeil May 25, 2013 Contents 1 Running the Program 2 2 Supplying Standard Input 4 3 Command Line Parameters 4 1 In this lab, we will look at some of the different ways that basic I/O information can
Steven Zeil May 25, 2013 Contents 1 Running the Program 2 2 Supplying Standard Input 4 3 Command Line Parameters 4 1 In this lab, we will look at some of the different ways that basic I/O information can
ns-3 Tutorial ns-3 project feedback: 1 April 2009
 ns-3 Tutorial ns-3 project feedback: ns-developers@isi.edu 1 April 2009 This is an ns-3 tutorial. Primary documentation for the ns-3 project is available in four forms: ns-3 Doxygen/Manual: Documentation
ns-3 Tutorial ns-3 project feedback: ns-developers@isi.edu 1 April 2009 This is an ns-3 tutorial. Primary documentation for the ns-3 project is available in four forms: ns-3 Doxygen/Manual: Documentation
Problem Set 6 Due: Start of Class, October 26
 CS242 Computer Networks Handout # 12 Randy Shull October 19, 2017 Wellesley College Problem Set 6 Due: Start of Class, October 26 Reading: Kurose & Ross, Sections 3.4, 3.5 Wireshark Lab [11] This exercise
CS242 Computer Networks Handout # 12 Randy Shull October 19, 2017 Wellesley College Problem Set 6 Due: Start of Class, October 26 Reading: Kurose & Ross, Sections 3.4, 3.5 Wireshark Lab [11] This exercise
Lab I: Using tcpdump and Wireshark
 Objectives To get the student familiar with basic network protocol analyzer, tools and equipment used in later labs, including tcpdump and Wireshark. Lab Readings Go to http://www.tcpdump.org/tcpdump_man.html
Objectives To get the student familiar with basic network protocol analyzer, tools and equipment used in later labs, including tcpdump and Wireshark. Lab Readings Go to http://www.tcpdump.org/tcpdump_man.html
Session 2. Wireless LAN in ns-3. 윤강진 Multimedia & Wireless Networking Laboratory, SNU
 Session 2. Wireless LAN in ns-3 윤강진 Multimedia & Wireless Networking Laboratory, SNU kjyoon@mwnl.snu.ac.kr 1 Contents IEEE 802.11 Wireless LAN WLAN Basic Operation in ns-3 Exercise 2 IEEE 802.11 Wireless
Session 2. Wireless LAN in ns-3 윤강진 Multimedia & Wireless Networking Laboratory, SNU kjyoon@mwnl.snu.ac.kr 1 Contents IEEE 802.11 Wireless LAN WLAN Basic Operation in ns-3 Exercise 2 IEEE 802.11 Wireless
CS 246 Winter Tutorial 1
 CS 246 Winter 2015 - Tutorial 1 January 11, 2016 1 Summary General Administration Stuff CS Undergraduate Environment Useful Software Basic Commands.profile Text Editors 2 General Administration Stuff Course
CS 246 Winter 2015 - Tutorial 1 January 11, 2016 1 Summary General Administration Stuff CS Undergraduate Environment Useful Software Basic Commands.profile Text Editors 2 General Administration Stuff Course
ECE 4110 Internetwork Programming Lab 2: TCP Traffic Generator. Lab Goals. Prelab
 ECE 4110 Internetwork Programming Lab 2: TCP Traffic Generator Group Number: Member Names: Date Issued: Tuesday January 22, 2013 Date Due: Wednesday, January 30, 2013 Last Edited: 1/21/2013 Lab Goals Finish
ECE 4110 Internetwork Programming Lab 2: TCP Traffic Generator Group Number: Member Names: Date Issued: Tuesday January 22, 2013 Date Due: Wednesday, January 30, 2013 Last Edited: 1/21/2013 Lab Goals Finish
Martin Brunner, Jonas Pfoh Sept. 6, Sept. 24, 2010
 Martin Brunner, Jonas Pfoh martin.brunner@sit.fraunhofer.de;pfoh@sec.in.tum.de IT Security Lab Technische Universität München Munich, Germany Sept. 6, 2010 - Sept. 24, 2010 Outline 1 2 3 4 5 6 Welcome
Martin Brunner, Jonas Pfoh martin.brunner@sit.fraunhofer.de;pfoh@sec.in.tum.de IT Security Lab Technische Universität München Munich, Germany Sept. 6, 2010 - Sept. 24, 2010 Outline 1 2 3 4 5 6 Welcome
4. What is the sequence number of the SYNACK segment sent by spinlab.wpi.edu to the client computer in reply to the SYN? Also Seq=0 (relative
 1. What is the IP address and TCP port number used by your client computer (source) to transfer the file to spinlab.wpi.edu? My computer is at 10.211.55.3. The source port is 49247. See screenshot below.
1. What is the IP address and TCP port number used by your client computer (source) to transfer the file to spinlab.wpi.edu? My computer is at 10.211.55.3. The source port is 49247. See screenshot below.
Rule 1-3: Use white space to break a function into paragraphs. Rule 1-5: Avoid very long statements. Use multiple shorter statements instead.
 Chapter 9: Rules Chapter 1:Style and Program Organization Rule 1-1: Organize programs for readability, just as you would expect an author to organize a book. Rule 1-2: Divide each module up into a public
Chapter 9: Rules Chapter 1:Style and Program Organization Rule 1-1: Organize programs for readability, just as you would expect an author to organize a book. Rule 1-2: Divide each module up into a public
Wireshark Lab: Getting Started
 Wireshark Lab: Getting Started Version: 2.0 2007 J.F. Kurose, K.W. Ross. All Rights Reserved Computer Networking: A Topdown Approach, 4 th edition. Tell me and I forget. Show me and I remember. Involve
Wireshark Lab: Getting Started Version: 2.0 2007 J.F. Kurose, K.W. Ross. All Rights Reserved Computer Networking: A Topdown Approach, 4 th edition. Tell me and I forget. Show me and I remember. Involve
ITTC Communication Networks Laboratory The University of Kansas EECS 563 Introduction to Protocol Analysis with Wireshark
 Communication Networks Laboratory The University of Kansas EECS 563 Introduction to Protocol Analysis with Wireshark Trúc Anh N. Nguyễn, Egemen K. Çetinkaya, Mohammed Alenazi, and James P.G. Sterbenz Department
Communication Networks Laboratory The University of Kansas EECS 563 Introduction to Protocol Analysis with Wireshark Trúc Anh N. Nguyễn, Egemen K. Çetinkaya, Mohammed Alenazi, and James P.G. Sterbenz Department
Python Basics. Lecture and Lab 5 Day Course. Python Basics
 Python Basics Lecture and Lab 5 Day Course Course Overview Python, is an interpreted, object-oriented, high-level language that can get work done in a hurry. A tool that can improve all professionals ability
Python Basics Lecture and Lab 5 Day Course Course Overview Python, is an interpreted, object-oriented, high-level language that can get work done in a hurry. A tool that can improve all professionals ability
Exercise 6a: Using free and/or open source tools to build workflows to manipulate. LAStools
 Exercise 6a: Using free and/or open source tools to build workflows to manipulate and process LiDAR data: LAStools Christopher Crosby Last Revised: December 1st, 2009 Exercises in this series: 1. LAStools
Exercise 6a: Using free and/or open source tools to build workflows to manipulate and process LiDAR data: LAStools Christopher Crosby Last Revised: December 1st, 2009 Exercises in this series: 1. LAStools
ns-3 Training Session 2: Monday 10:30am ns-3 Annual Meeting May 2014
 Training Session 2: Monday 10:30am Annual Meeting May 2014 1 Discrete-event simulation basics Simulation time moves in discrete jumps from event to event C++ functions schedule events to occur at specific
Training Session 2: Monday 10:30am Annual Meeting May 2014 1 Discrete-event simulation basics Simulation time moves in discrete jumps from event to event C++ functions schedule events to occur at specific
Introduction to Linux Part 2b: basic scripting. Brett Milash and Wim Cardoen CHPC User Services 18 January, 2018
 Introduction to Linux Part 2b: basic scripting Brett Milash and Wim Cardoen CHPC User Services 18 January, 2018 Overview Scripting in Linux What is a script? Why scripting? Scripting languages + syntax
Introduction to Linux Part 2b: basic scripting Brett Milash and Wim Cardoen CHPC User Services 18 January, 2018 Overview Scripting in Linux What is a script? Why scripting? Scripting languages + syntax
Wireshark Lab: Getting Started v7.0
 Wireshark Lab: Getting Started v7.0 Adapted by HMC from the supplement to Computer Networking: A Top-Down Approach, 7 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve
Wireshark Lab: Getting Started v7.0 Adapted by HMC from the supplement to Computer Networking: A Top-Down Approach, 7 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve
Working with Shell Scripting. Daniel Balagué
 Working with Shell Scripting Daniel Balagué Editing Text Files We offer many text editors in the HPC cluster. Command-Line Interface (CLI) editors: vi / vim nano (very intuitive and easy to use if you
Working with Shell Scripting Daniel Balagué Editing Text Files We offer many text editors in the HPC cluster. Command-Line Interface (CLI) editors: vi / vim nano (very intuitive and easy to use if you
Warm-up sheet: Programming in C
 Warm-up sheet: Programming in C Programming for Embedded Systems Uppsala University January 20, 2015 Introduction Here are some basic exercises in the programming language C. Hopefully you already have
Warm-up sheet: Programming in C Programming for Embedded Systems Uppsala University January 20, 2015 Introduction Here are some basic exercises in the programming language C. Hopefully you already have
Laboratory 1 Semester 1 11/12
 CS2106 National University of Singapore School of Computing Laboratory 1 Semester 1 11/12 MATRICULATION NUMBER: In this lab exercise, you will get familiarize with some basic UNIX commands, editing and
CS2106 National University of Singapore School of Computing Laboratory 1 Semester 1 11/12 MATRICULATION NUMBER: In this lab exercise, you will get familiarize with some basic UNIX commands, editing and
Basic Cisco Router Configuration: Multiple Routers
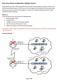 Basic Cisco Router Configuration: Multiple Routers Routers rarely exist alone. Most organizations have several to several dozens of routers. In this Lab, we will study two different ways in which routers
Basic Cisco Router Configuration: Multiple Routers Routers rarely exist alone. Most organizations have several to several dozens of routers. In this Lab, we will study two different ways in which routers
OpenMP Example. $ ssh # You might have to type yes if this is the first time you log on
 OpenMP Example Day 1, afternoon session 1: We examine a serial and parallel implementation of a code solving an N-body problem with a star, a planet and many small particles near the planet s radius. The
OpenMP Example Day 1, afternoon session 1: We examine a serial and parallel implementation of a code solving an N-body problem with a star, a planet and many small particles near the planet s radius. The
Lab Using Wireshark to Examine Ethernet Frames
 Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Lab Exercise Protocol Layers
 Lab Exercise Protocol Layers Objective To learn how protocols and layering are represented in packets. They are key concepts for structuring networks that are covered in 1.3 and 1.4 of your text. Review
Lab Exercise Protocol Layers Objective To learn how protocols and layering are represented in packets. They are key concepts for structuring networks that are covered in 1.3 and 1.4 of your text. Review
ns-2 Tutorial Exercise (1)
 ns-2 Tutorial Exercise (1) Multimedia Networking Group, The Department of Computer Science, UVA Jianping Wang Adopted from Nicolas s slides Jianping Wang, 2002 cs757 On to the Tutorial Work in group of
ns-2 Tutorial Exercise (1) Multimedia Networking Group, The Department of Computer Science, UVA Jianping Wang Adopted from Nicolas s slides Jianping Wang, 2002 cs757 On to the Tutorial Work in group of
COMP s1 Lecture 1
 COMP1511 18s1 Lecture 1 1 Numbers In, Numbers Out Andrew Bennett more printf variables scanf 2 Before we begin introduce yourself to the person sitting next to you why did
COMP1511 18s1 Lecture 1 1 Numbers In, Numbers Out Andrew Bennett more printf variables scanf 2 Before we begin introduce yourself to the person sitting next to you why did
ITTC Communication Networks Laboratory The University of Kansas EECS 780 Introduction to Protocol Analysis with Wireshark
 Communication Networks Laboratory The University of Kansas EECS 780 Introduction to Protocol Analysis with Wireshark Trúc Anh N. Nguyễn, Egemen K. Çetinkaya, Mohammed Alenazi, and James P.G. Sterbenz Department
Communication Networks Laboratory The University of Kansas EECS 780 Introduction to Protocol Analysis with Wireshark Trúc Anh N. Nguyễn, Egemen K. Çetinkaya, Mohammed Alenazi, and James P.G. Sterbenz Department
NS-2: A Free Open Source Network Simulator
 : A Free Open Source Network Simulator srinath@it.iitb.ac.in Open Source Software Research Center Workshop on FOSS tools for Engineering June 27, 2005 Simulation Introduction Definition A simulation imitates
: A Free Open Source Network Simulator srinath@it.iitb.ac.in Open Source Software Research Center Workshop on FOSS tools for Engineering June 27, 2005 Simulation Introduction Definition A simulation imitates
CHAPTER 6 IMPLEMENTATION OF TRACE ANALYZER FOR NS3
 135 CHAPTER 6 IMPLEMENTATION OF TRACE ANALYZER FOR NS3 This chapter presents a framework for NS3 Trace Analyzer which is implemented in java. NS3 trace analyzer reads the.tr file and automatically calculates
135 CHAPTER 6 IMPLEMENTATION OF TRACE ANALYZER FOR NS3 This chapter presents a framework for NS3 Trace Analyzer which is implemented in java. NS3 trace analyzer reads the.tr file and automatically calculates
C++ Lab 03 - C++ Functions
 C++ Lab 03 - C++ Functions 2.680 Unmanned Marine Vehicle Autonomy, Sensing and Communications Spring 2018 Michael Benjamin, mikerb@mit.edu Department of Mechanical Engineering Computer Science and Artificial
C++ Lab 03 - C++ Functions 2.680 Unmanned Marine Vehicle Autonomy, Sensing and Communications Spring 2018 Michael Benjamin, mikerb@mit.edu Department of Mechanical Engineering Computer Science and Artificial
Wireshark Lab: Getting Started v7.0
 Wireshark Lab: Getting Started v7.0 Supplement to Computer Networking: A Top-Down Approach, 7th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand.
Wireshark Lab: Getting Started v7.0 Supplement to Computer Networking: A Top-Down Approach, 7th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand.
9. Wireshark I: Protocol Stack and Ethernet
 Distributed Systems 205/2016 Lab Simon Razniewski/Florian Klement 9. Wireshark I: Protocol Stack and Ethernet Objective To learn how protocols and layering are represented in packets, and to explore the
Distributed Systems 205/2016 Lab Simon Razniewski/Florian Klement 9. Wireshark I: Protocol Stack and Ethernet Objective To learn how protocols and layering are represented in packets, and to explore the
Lab - TCP Traffic Generator
 ECE4110 Fall Semester, 2010 Lab - TCP Traffic Generator Assigned: Sep 10, 2010 Due: Sep 20, 2010 Group Number: Member Names: Lab Goals 1. Finish a TCP sockets programs to transmit and receive TCP data.
ECE4110 Fall Semester, 2010 Lab - TCP Traffic Generator Assigned: Sep 10, 2010 Due: Sep 20, 2010 Group Number: Member Names: Lab Goals 1. Finish a TCP sockets programs to transmit and receive TCP data.
Lab Using Wireshark to Examine Ethernet Frames
 Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ BRNO UNIVERSITY OF TECHNOLOGY. MODEL OF HTTP ADAPTIVE VIDEO STREAMING Model adaptivního streamování videa přes HTTP
 VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA ELEKTROTECHNIKY A KOMUNIKAČNÍCH TECHNOLOGIÍ ÚSTAV RADIOELEKTRONIKY FACULTY OF ELECTRICAL ENGINEERING AND COMMUNICATION DEPARTMENT OF
VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA ELEKTROTECHNIKY A KOMUNIKAČNÍCH TECHNOLOGIÍ ÚSTAV RADIOELEKTRONIKY FACULTY OF ELECTRICAL ENGINEERING AND COMMUNICATION DEPARTMENT OF
Shell script/program. Basic shell scripting. Script execution. Resources. Simple example script. Quoting
 Shell script/program Basic shell scripting CS 2204 Class meeting 5 Created by Doug Bowman, 2001 Modified by Mir Farooq Ali, 2002 A series of shell commands placed in an ASCII text file Commands include
Shell script/program Basic shell scripting CS 2204 Class meeting 5 Created by Doug Bowman, 2001 Modified by Mir Farooq Ali, 2002 A series of shell commands placed in an ASCII text file Commands include
New York University Computer Science Department Courant Institute of Mathematical Sciences
 New York University Computer Science Department Courant Institute of Mathematical Sciences Course Title: Data Communication & Networks Course Number: g22.2662-001 Instructor: Jean-Claude Franchitti Session:
New York University Computer Science Department Courant Institute of Mathematical Sciences Course Title: Data Communication & Networks Course Number: g22.2662-001 Instructor: Jean-Claude Franchitti Session:
Getting Wireshark. Detailed installing steps can be found on the Internet, so this tutorial won t cover this part.
 Wireshark Tutorial Getting Wireshark Wireshark for Windows and Mac OS X can be easily downloaded from its official website. If you are Linux users, you ll probably find Wireshark in its package repositories.
Wireshark Tutorial Getting Wireshark Wireshark for Windows and Mac OS X can be easily downloaded from its official website. If you are Linux users, you ll probably find Wireshark in its package repositories.
Advanced Network Troubleshooting Using Wireshark (Hands-on)
 Advanced Network Troubleshooting Using Wireshark (Hands-on) Description This course is a continuation of the "Basic Network Troubleshooting Using Wireshark" course, and comes to provide the participants
Advanced Network Troubleshooting Using Wireshark (Hands-on) Description This course is a continuation of the "Basic Network Troubleshooting Using Wireshark" course, and comes to provide the participants
University of Maryland Baltimore County Department of Information Systems Spring 2015
 University of Maryland Baltimore County Department of Information Systems Spring 2015 IS 450/650: Data Communications and Networks Homework Assignment 1 Wireshark Lab (Handed Out: February 3, 2015 (Tuesday),
University of Maryland Baltimore County Department of Information Systems Spring 2015 IS 450/650: Data Communications and Networks Homework Assignment 1 Wireshark Lab (Handed Out: February 3, 2015 (Tuesday),
Lab 9.8.1: Address Resolution Protocol (ARP)
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1-ISP R2-Central S0/0/0 10.10.10.6 255.255.255.252 N/A Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0 10.10.10.5
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1-ISP R2-Central S0/0/0 10.10.10.6 255.255.255.252 N/A Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0 10.10.10.5
New Zealand Cyber Security Challenge 2018 Round Zero write-up
 New Zealand Cyber Security Challenge 2018 Round Zero write-up Challenge 1 This is a simple challenge that can be solved using your browser s developer tools (right-click, inspect element). You will notice
New Zealand Cyber Security Challenge 2018 Round Zero write-up Challenge 1 This is a simple challenge that can be solved using your browser s developer tools (right-click, inspect element). You will notice
FILE MAINTENANCE COMMANDS
 Birla Institute of Technology & Science, Pilani Computer Programming (CS F111) Lab-2 ----------------------------------------------------------------------------------------------------------------------
Birla Institute of Technology & Science, Pilani Computer Programming (CS F111) Lab-2 ----------------------------------------------------------------------------------------------------------------------
LAB THREE STATIC ROUTING
 LAB THREE STATIC ROUTING In this lab you will work with four different network topologies. The topology for Parts 1-4 is shown in Figure 3.1. These parts address router configuration on Linux PCs and a
LAB THREE STATIC ROUTING In this lab you will work with four different network topologies. The topology for Parts 1-4 is shown in Figure 3.1. These parts address router configuration on Linux PCs and a
Exercise 1: Basic Tools
 Exercise 1: Basic Tools This exercise is created so everybody can learn the basic tools we will use during this course. It is really more like a tutorial than an exercise and, you are not required to submit
Exercise 1: Basic Tools This exercise is created so everybody can learn the basic tools we will use during this course. It is really more like a tutorial than an exercise and, you are not required to submit
Access Switch VLAN Y Y.1 /24
 Topology: Fa 0/1 VNC Server Fa 0/0 Port B Access Router Trunk VLAN X Access Switch VLAN Y Backbone Router 141.85.Y.1 /24 28.0.0.42 OSPF X.0.0.0/8 Port A 27.45.67.89 Work Station DHCP Server The Goal: Connect
Topology: Fa 0/1 VNC Server Fa 0/0 Port B Access Router Trunk VLAN X Access Switch VLAN Y Backbone Router 141.85.Y.1 /24 28.0.0.42 OSPF X.0.0.0/8 Port A 27.45.67.89 Work Station DHCP Server The Goal: Connect
Ethereal Lab: Getting Started
 Ethereal Lab: Getting Started Version: July 2005 2005 J.F. Kurose, K.W. Ross. All Rights Reserved Computer Networking: A Topdown Approach Featuring the Internet, 3 rd edition. Tell me and I forget. Show
Ethereal Lab: Getting Started Version: July 2005 2005 J.F. Kurose, K.W. Ross. All Rights Reserved Computer Networking: A Topdown Approach Featuring the Internet, 3 rd edition. Tell me and I forget. Show
CS 361 Computer Systems Fall 2017 Homework Assignment 1 Linking - From Source Code to Executable Binary
 CS 361 Computer Systems Fall 2017 Homework Assignment 1 Linking - From Source Code to Executable Binary Due: Thursday 14 Sept. Electronic copy due at 9:00 A.M., optional paper copy may be delivered to
CS 361 Computer Systems Fall 2017 Homework Assignment 1 Linking - From Source Code to Executable Binary Due: Thursday 14 Sept. Electronic copy due at 9:00 A.M., optional paper copy may be delivered to
4/7/2018 ARP SPOOFING. Group 1. Duan Chao Luo Yi
 4/7/2018 ARP SPOOFING Group 1 Duan Chao 301230103 Luo Yi 301220263 Abstract For the first few decades of network existence, computer networks were used by university researchers for sending e-mail and
4/7/2018 ARP SPOOFING Group 1 Duan Chao 301230103 Luo Yi 301220263 Abstract For the first few decades of network existence, computer networks were used by university researchers for sending e-mail and
Introduction to Supercomputing
 Introduction to Supercomputing TMA4280 Introduction to UNIX environment and tools 0.1 Getting started with the environment and the bash shell interpreter Desktop computers are usually operated from a graphical
Introduction to Supercomputing TMA4280 Introduction to UNIX environment and tools 0.1 Getting started with the environment and the bash shell interpreter Desktop computers are usually operated from a graphical
DA1150 DECT Examiner Installation & Usage Guide Version 1.1
 DA1150 DECT Examiner Installation & Usage Guide Version 1.1 according ETSI Standards DECT GAP, CAT-iq 2.0/2.1/3.0, DECT ULE EU, US, Brazil, and LATAM DECT 1 pa g e I n s t a l l a t i o n & U s a g e G
DA1150 DECT Examiner Installation & Usage Guide Version 1.1 according ETSI Standards DECT GAP, CAT-iq 2.0/2.1/3.0, DECT ULE EU, US, Brazil, and LATAM DECT 1 pa g e I n s t a l l a t i o n & U s a g e G
ns-3 Training Emulation
 ns-3 Training Emulation 1 Outline Main emulation devices Tap Bridge FdNetDevice NetmapNetDevice (coming soon) ns-3 training, June 2018 2 Emulation support Support moving between simulation and testbeds
ns-3 Training Emulation 1 Outline Main emulation devices Tap Bridge FdNetDevice NetmapNetDevice (coming soon) ns-3 training, June 2018 2 Emulation support Support moving between simulation and testbeds
CS197U: A Hands on Introduction to Unix
 CS197U: A Hands on Introduction to Unix Lecture 11: WWW and Wrap up Tian Guo University of Massachusetts Amherst CICS 1 Reminders Assignment 4 was graded and scores on Moodle Assignment 5 was due and you
CS197U: A Hands on Introduction to Unix Lecture 11: WWW and Wrap up Tian Guo University of Massachusetts Amherst CICS 1 Reminders Assignment 4 was graded and scores on Moodle Assignment 5 was due and you
Quick Installation Guide
 Wireless / Fast Ethernet Print Server Series Quick Installation Guide Version 1.1 January. 2006 Insert the CD shipped along with the print server into your CD- ROM drive. The Autorun.exe program should
Wireless / Fast Ethernet Print Server Series Quick Installation Guide Version 1.1 January. 2006 Insert the CD shipped along with the print server into your CD- ROM drive. The Autorun.exe program should
ns-3 Tutorial ns-3 project feedback: 20 August 2010
 ns-3 Tutorial ns-3 project feedback: ns-developers@isi.edu 20 August 2010 This is an ns-3 tutorial. Primary documentation for the ns-3 project is available in four forms: ns-3 Doxygen/Manual: Documentation
ns-3 Tutorial ns-3 project feedback: ns-developers@isi.edu 20 August 2010 This is an ns-3 tutorial. Primary documentation for the ns-3 project is available in four forms: ns-3 Doxygen/Manual: Documentation
Wireshark Lab: DNS. 1. Run nslookup to obtain the IP address of a Web server in Asia. What is the IP address of that server?
 Rick Shingu Nick Ishihara 11/30/14 Wireshark Lab: DNS 1. nslookup 1. Run nslookup to obtain the IP address of a Web server in Asia. What is the IP address of that server? Ran the command nslookup www.asdu.ait.ac.th.
Rick Shingu Nick Ishihara 11/30/14 Wireshark Lab: DNS 1. nslookup 1. Run nslookup to obtain the IP address of a Web server in Asia. What is the IP address of that server? Ran the command nslookup www.asdu.ait.ac.th.
IP Network Troubleshooting Part 3. Wayne M. Pecena, CPBE, CBNE Texas A&M University Educational Broadcast Services - KAMU
 IP Network Troubleshooting Part 3 Wayne M. Pecena, CPBE, CBNE Texas A&M University Educational Broadcast Services - KAMU February 2016 Today s Outline: Focused Upon Protocol Analysis with Wireshark Review
IP Network Troubleshooting Part 3 Wayne M. Pecena, CPBE, CBNE Texas A&M University Educational Broadcast Services - KAMU February 2016 Today s Outline: Focused Upon Protocol Analysis with Wireshark Review
CSci 4061 Introduction to Operating Systems. Programs in C/Unix
 CSci 4061 Introduction to Operating Systems Programs in C/Unix Today Basic C programming Follow on to recitation Structure of a C program A C program consists of a collection of C functions, structs, arrays,
CSci 4061 Introduction to Operating Systems Programs in C/Unix Today Basic C programming Follow on to recitation Structure of a C program A C program consists of a collection of C functions, structs, arrays,
CSE 560M Computer Systems Architecture I
 CSE 560M Computer Systems Architecture I Assignment 1, due Friday, Oct. 19, 2018 This goal of this lab assignment is to help familiarize you with simulating a system using gem5 by simulating two programs
CSE 560M Computer Systems Architecture I Assignment 1, due Friday, Oct. 19, 2018 This goal of this lab assignment is to help familiarize you with simulating a system using gem5 by simulating two programs
CMPT 300. Operating Systems. Brief Intro to UNIX and C
 CMPT 300 Operating Systems Brief Intro to UNIX and C Outline Welcome Review Questions UNIX basics and Vi editor Using SSH to remote access Lab2(4214) Compiling a C Program Makefile Basic C/C++ programming
CMPT 300 Operating Systems Brief Intro to UNIX and C Outline Welcome Review Questions UNIX basics and Vi editor Using SSH to remote access Lab2(4214) Compiling a C Program Makefile Basic C/C++ programming
Unix/Linux Basics. Cpt S 223, Fall 2007 Copyright: Washington State University
 Unix/Linux Basics 1 Some basics to remember Everything is case sensitive Eg., you can have two different files of the same name but different case in the same folder Console-driven (same as terminal )
Unix/Linux Basics 1 Some basics to remember Everything is case sensitive Eg., you can have two different files of the same name but different case in the same folder Console-driven (same as terminal )
