XPath evaluation in linear time with polynomial combined complexity
|
|
|
- Everett Campbell
- 5 years ago
- Views:
Transcription
1 XPath evaluation in linear time with polynomial combined complexity Paweł Parys (Common work with Mikołaj Bojańczyk)
2 XPath is a query language: XPath queries select nodes in a XML document tree. We consider fragments called FOXPath and AggXPath Input: XPath query Q, XML document D Output: document tree nodes, which satisfy the query Contribution: We solve the above problem 1) in time O( D. Q 3 ) for Q from FOXPath 2) in time O( D. c Q ) for Q from AggXPath easy corollary
3 Example document: <html> <title>nice document</title> <h1>section</h1> <a href= >University</a> <a href= >Search</a> <table><tr><td> <a href= > A link in a table</a> </td></tr></table> </html>
4 Example document: <html> <title>nice document</title> <h1>section</h1> <a href= >University</a> <a href= >Search</a> <table><tr><td> <a href= > A link in a table</a> </td></tr></table> </html> Example query navigation only (CoreXPath): self:: a and not (ancestor:: table )
5 Example document: <html> <title>nice document</title> <h1>section</h1> <a href= >University</a> <a href= >Search</a> <table><tr><td> <a href= > A link in a table</a> </td></tr></table> </html> Example query comparing data (FOXPath): self:: a and ((self/@href=following:: a /@href) or (self/@href=preceding:: a /@href))
6 Example document: <html> <title>nice document</title> <h1>section</h1> <a href= >University</a> <a href= >Search</a> <table><tr><td> <a href= > A link in a table</a> </td></tr></table> </html> Example query counting (AggXPath): count(preceding)+1=count(root/descendant:: a )
7 Example document: <html> <title>nice document</title> <h1>section</h1> <a href= >University</a> <a href= >Search</a> <table><tr><td> <a href= > A link in a table</a> </td></tr></table> </html> Example query positional arithmetic (full XPath 1.0): descendant[position()=4 and self:: a ]
8 Results summary CoreXPath (no data) O( D. Q ) Gottlob, Koch, Pichler 2002 O( D Q ) real world XPath engines FOXPath (comparing data) O( D 2. Q ) previous works (GKP) O( D. c Q ), O( D. log D. Q 3 ) Bojańczyk, P O( D. Q 3 ) P AggXPath (counting) O( D 2. Q ) previous works (GKP) O( D. c Q ) P Full XPath (node positions) O( D 4. Q 2 ) Gottlob, Koch, Pichler 2003
9 Two types of expressions: Definition of XPath path expression returns a set of node pairs: axes: child, parent, next sibling, previous sibling, descendant, ancestor, following sibling, preceding sibling [q] selects a pair (u,u) if u is selected by the node test q composition, union node test returns a set of nodes: name test p selects a node u if (u,v) is selected by p for some node v p=p' selects a node u if there are (u,v) and (u,v'), selected by p and p' respectively, such that v and v' have the same data value similarly p p', p<p', p=constant, etc. or, and, not most important, most difficult
10 Definition of XPath u p p' v v' p=p' selects a node u if there are (u,v) and (u,v'), selected by p and p' respectively, such that v and v' have the same data value similarly p p', p<p', p=constant, etc. most important, most difficult
11 name test or, and, not Algorithm structure For each node test expression we calculate its value (set of nodes). We do it by induction on the size of the expression: easy p=p' etc. (selects node u if for some v,v' with the same data value, pair (u,v) is selected by p and pair (u,v') is selected by p'): evaluate all subexpressions q 1...q n (node tests) store the results: in the name of every node remember which q i are satisfied in that node we may assume, that the only atomic path expressions in p and p' are axes and name tests (+ composition, union)
12 Algorithm idea Goal: find all nodes satisfying p=p' when the only atomic path expressions in p and p' are axes and name tests. A path expression p may be compiled to a nondeterministic automaton A, which reads a description of a path: a word over alphabet (node names) (one step axes) p selects a pair (u,v) iff a description of some path between u and v (not necesarly the shortest path) is accepted by A
13 Naive approach quadratic algorithm For each node u (independently) calculate all possible values reachable by p: p 159 and by p': 88 p' v p 345 u p 789 u p' 345 and check if these two sets have nonempty intersection. For each u it can be done in linear time. Thus the whole algorithm is quadratic.
14 Second naive approach quadratic algorithm For each data value (independently) mark the nodes u which can reach this data value by p and p' 345 p p' p p p' p' p For each data class it can be done in linear time. Thus the whole algorithm is quadratic. We will improve this approach!
15 Algorithm idea Goal: find all nodes satisfying p=p' when the only atomic path expressions in p and p' are axes and name tests. A path expression p may be compiled to a nondeterministic automaton A, which reads a description of a path: a word over alphabet (node names) (one step axes) p selects a pair (u,v) iff a description of some path between u and v (not necesarly the shortest path) is accepted by A But p is not an arbitrary regular expression, there is no Kleene star in XPath!!!! So the automaton has only trival cycles (reading axes): child b a child a b child a parent
16 Algorithm idea special case assume we have only a word with data (instead of a tree) automaton A for p goes only to the left and A' for p' only to the right every data value appears in exactly two places (denoted by a pair of brackets) q q' F F [ ] a b a a a a b b a a b a a b a a b b b a b d v A u A' v' We have to mark all such u. We will replace this set of bracket pairs by another one from which it is easier to calculate the selected u. pair with equal data values node names
17 q F Algorithm idea special case, continued ' [ ] a b a a a a b b a a b a a b a a b b b a b a v A u A' v' The automaton A in some of last Q positions has to visit a state q with a loop reading left. q F original pair (with equal data values) We may replace this pair of brackets by at most Q 2 new pairs: from state q in w we may reach q F in v, distance between w and v is at most Q state q has a loop reading left. q q q F F ' [ [ ] a b a a a a b b a a b a a b a a b b b a b a v w A u A' v' Q (possibly we should also mark nodes u close to v, if starting from u we may reach q F in v and q' F in w) new pair
18 a state with a loop reading left Algorithm idea special case, step 2 q q' [ ] a b a a a a b b a a b a a b a a b b b a b a v A u A' v' Starting from the end of the word we move brackets to the left: we move right bracket at v' one node to the left (changing the state) moreover, if q'=q 0 and starting at v', A reaches q at position v, then v' should be marked as u a state with a loop reading left q q'' q' [ ] ] a b a a a a b b a a b a a b a a b b b a b a v A u A' w' v' This creates Q new pairs, which have to be processed again and again, but...
19 Observation the same state with a loop reading left q q' q [ ] [ ] a b a a a a b b a a b a a b a a b b b a b a A u A' v' The closer pair may be removed, it generates the same nodes u. So for every node v' there may be at most Q 2 pairs of brackets, one for every pair of states.
20 Final lemma What is missing to solve the special case: For given u,v,q 0,q (where q has a loop reading left) check if A may reach q in v starting from q 0 in u. Equivalent question: For given u,q 0,q (where q has a loop reading left) where is the rightmost v such that A (going left) may reach q in v starting from q 0 in u. We call that first(u,q 0,q). This information may be calculated in one left to right pass: It is possible that first(u,q 0,q)=u Otherwise it is the rightmost of first(u',q',q) for q' which may be reached in u' from q 0 in u (where u' is the node one step to the left)
21 Algorithm idea more general case assume we have only a word with data (instead of a tree) automaton A for p goes only to the left and A' for p' only to the right a data value can appear in any number of places (v 1,v 2,v 3 ) q F Q' q' 2 Q 2 F [ ][ ] a b a a a a b b a a b a a b a a b b b a b d v v 1 2 v 3 Create a bracket pair for consecutive nodes with the same data. Q 2 = {q F } {q : from q in v 2, A can reach q F in v 1 } Q 2 ' =... Continue like previously. The total number of brackets is linear. After precomputation it can be read in constant time (previous slide)
22 Algorithm idea more general case assume we have only a word with data (instead of a tree) automata A and A' can make loops Precalculate the loops: loops(v) = {(p,q) : from p in v, A can reach q in v} = (loops (v) loops (v))* l e f t r i g h t Add the loops(v) set to the label of v. Construct a new automaton, which goes only left and instead of making a loop in v, it reads loops(v).
23 Algorithm idea the general case (trees) Class of a data value = nodes with these data value, and their least common ancestors
XML databases. Jan Chomicki. University at Buffalo. Jan Chomicki (University at Buffalo) XML databases 1 / 9
 XML databases Jan Chomicki University at Buffalo Jan Chomicki (University at Buffalo) XML databases 1 / 9 Outline 1 XML data model 2 XPath 3 XQuery Jan Chomicki (University at Buffalo) XML databases 2
XML databases Jan Chomicki University at Buffalo Jan Chomicki (University at Buffalo) XML databases 1 / 9 Outline 1 XML data model 2 XPath 3 XQuery Jan Chomicki (University at Buffalo) XML databases 2
XPath with transitive closure
 XPath with transitive closure Logic and Databases Feb 2006 1 XPath with transitive closure Logic and Databases Feb 2006 2 Navigating XML trees XPath with transitive closure Newton Institute: Logic and
XPath with transitive closure Logic and Databases Feb 2006 1 XPath with transitive closure Logic and Databases Feb 2006 2 Navigating XML trees XPath with transitive closure Newton Institute: Logic and
XML and Databases. Lecture 9 Properties of XPath. Sebastian Maneth NICTA and UNSW
 XML and Databases Lecture 9 Properties of XPath Sebastian Maneth NICTA and UNSW CSE@UNSW -- Semester 1, 2009 Outline 1. XPath Equivalence 2. No Looking Back: How to Remove Backward Axes 3. Containment
XML and Databases Lecture 9 Properties of XPath Sebastian Maneth NICTA and UNSW CSE@UNSW -- Semester 1, 2009 Outline 1. XPath Equivalence 2. No Looking Back: How to Remove Backward Axes 3. Containment
(Refer Slide Time: 0:19)
 Theory of Computation. Professor somenath Biswas. Department of Computer Science & Engineering. Indian Institute of Technology, Kanpur. Lecture-15. Decision Problems for Regular Languages. (Refer Slide
Theory of Computation. Professor somenath Biswas. Department of Computer Science & Engineering. Indian Institute of Technology, Kanpur. Lecture-15. Decision Problems for Regular Languages. (Refer Slide
Semantic Characterizations of XPath
 Semantic Characterizations of XPath Maarten Marx Informatics Institute, University of Amsterdam, The Netherlands CWI, April, 2004 1 Overview Navigational XPath is a language to specify sets and paths in
Semantic Characterizations of XPath Maarten Marx Informatics Institute, University of Amsterdam, The Netherlands CWI, April, 2004 1 Overview Navigational XPath is a language to specify sets and paths in
One of the main selling points of a database engine is the ability to make declarative queries---like SQL---that specify what should be done while
 1 One of the main selling points of a database engine is the ability to make declarative queries---like SQL---that specify what should be done while leaving the engine to choose the best way of fulfilling
1 One of the main selling points of a database engine is the ability to make declarative queries---like SQL---that specify what should be done while leaving the engine to choose the best way of fulfilling
XPath. Lecture 36. Robb T. Koether. Wed, Apr 16, Hampden-Sydney College. Robb T. Koether (Hampden-Sydney College) XPath Wed, Apr 16, / 28
 XPath Lecture 36 Robb T. Koether Hampden-Sydney College Wed, Apr 16, 2014 Robb T. Koether (Hampden-Sydney College) XPath Wed, Apr 16, 2014 1 / 28 1 XPath 2 Executing XPath Expressions 3 XPath Expressions
XPath Lecture 36 Robb T. Koether Hampden-Sydney College Wed, Apr 16, 2014 Robb T. Koether (Hampden-Sydney College) XPath Wed, Apr 16, 2014 1 / 28 1 XPath 2 Executing XPath Expressions 3 XPath Expressions
Regular Expressions for Data Words
 Regular Expressions for Data Words Leonid Libkin and Domagoj Vrgoč School of Informatics, University of Edinburgh Abstract. In data words, each position carries not only a letter form a finite alphabet,
Regular Expressions for Data Words Leonid Libkin and Domagoj Vrgoč School of Informatics, University of Edinburgh Abstract. In data words, each position carries not only a letter form a finite alphabet,
XPath Lecture 34. Robb T. Koether. Hampden-Sydney College. Wed, Apr 11, 2012
 XPath Lecture 34 Robb T. Koether Hampden-Sydney College Wed, Apr 11, 2012 Robb T. Koether (Hampden-Sydney College) XPathLecture 34 Wed, Apr 11, 2012 1 / 20 1 XPath Functions 2 Predicates 3 Axes Robb T.
XPath Lecture 34 Robb T. Koether Hampden-Sydney College Wed, Apr 11, 2012 Robb T. Koether (Hampden-Sydney College) XPathLecture 34 Wed, Apr 11, 2012 1 / 20 1 XPath Functions 2 Predicates 3 Axes Robb T.
ECS 120 Lesson 7 Regular Expressions, Pt. 1
 ECS 120 Lesson 7 Regular Expressions, Pt. 1 Oliver Kreylos Friday, April 13th, 2001 1 Outline Thus far, we have been discussing one way to specify a (regular) language: Giving a machine that reads a word
ECS 120 Lesson 7 Regular Expressions, Pt. 1 Oliver Kreylos Friday, April 13th, 2001 1 Outline Thus far, we have been discussing one way to specify a (regular) language: Giving a machine that reads a word
Databases and Information Systems 1. Prof. Dr. Stefan Böttcher
 9. XPath queries on XML data streams Prof. Dr. Stefan Böttcher goals of XML stream processing substitution of reverse-axes an automata-based approach to XPath query processing Processing XPath queries
9. XPath queries on XML data streams Prof. Dr. Stefan Böttcher goals of XML stream processing substitution of reverse-axes an automata-based approach to XPath query processing Processing XPath queries
YFilter: an XML Stream Filtering Engine. Weiwei SUN University of Konstanz
 YFilter: an XML Stream Filtering Engine Weiwei SUN University of Konstanz 1 Introduction Data exchange between applications: use XML Messages processed by an XML Message Broker Examples Publish/subscribe
YFilter: an XML Stream Filtering Engine Weiwei SUN University of Konstanz 1 Introduction Data exchange between applications: use XML Messages processed by an XML Message Broker Examples Publish/subscribe
Chapter 3. Graphs. Slides by Kevin Wayne. Copyright 2005 Pearson-Addison Wesley. All rights reserved.
 Chapter 3 Graphs Slides by Kevin Wayne. Copyright 2005 Pearson-Addison Wesley. All rights reserved. 1 3.1 Basic Definitions and Applications Undirected Graphs Undirected graph. G = (V, E) V = nodes. E
Chapter 3 Graphs Slides by Kevin Wayne. Copyright 2005 Pearson-Addison Wesley. All rights reserved. 1 3.1 Basic Definitions and Applications Undirected Graphs Undirected graph. G = (V, E) V = nodes. E
Λέων-Χαράλαμπος Σταματάρης
 Λέων-Χαράλαμπος Σταματάρης INTRODUCTION Two classical problems of information dissemination in computer networks: The broadcasting problem: Distributing a particular message from a distinguished source
Λέων-Χαράλαμπος Σταματάρης INTRODUCTION Two classical problems of information dissemination in computer networks: The broadcasting problem: Distributing a particular message from a distinguished source
Evaluating XPath Queries
 Chapter 8 Evaluating XPath Queries Peter Wood (BBK) XML Data Management 201 / 353 Introduction When XML documents are small and can fit in memory, evaluating XPath expressions can be done efficiently But
Chapter 8 Evaluating XPath Queries Peter Wood (BBK) XML Data Management 201 / 353 Introduction When XML documents are small and can fit in memory, evaluating XPath expressions can be done efficiently But
Chapter 3. Graphs CLRS Slides by Kevin Wayne. Copyright 2005 Pearson-Addison Wesley. All rights reserved.
 Chapter 3 Graphs CLRS 12-13 Slides by Kevin Wayne. Copyright 2005 Pearson-Addison Wesley. All rights reserved. 25 3.4 Testing Bipartiteness Bipartite Graphs Def. An undirected graph G = (V, E) is bipartite
Chapter 3 Graphs CLRS 12-13 Slides by Kevin Wayne. Copyright 2005 Pearson-Addison Wesley. All rights reserved. 25 3.4 Testing Bipartiteness Bipartite Graphs Def. An undirected graph G = (V, E) is bipartite
XML: Extensible Markup Language
 XML: Extensible Markup Language CSC 375, Fall 2015 XML is a classic political compromise: it balances the needs of man and machine by being equally unreadable to both. Matthew Might Slides slightly modified
XML: Extensible Markup Language CSC 375, Fall 2015 XML is a classic political compromise: it balances the needs of man and machine by being equally unreadable to both. Matthew Might Slides slightly modified
3.1 Basic Definitions and Applications. Chapter 3. Graphs. Undirected Graphs. Some Graph Applications
 Chapter 3 31 Basic Definitions and Applications Graphs Slides by Kevin Wayne Copyright 2005 Pearson-Addison Wesley All rights reserved 1 Undirected Graphs Some Graph Applications Undirected graph G = (V,
Chapter 3 31 Basic Definitions and Applications Graphs Slides by Kevin Wayne Copyright 2005 Pearson-Addison Wesley All rights reserved 1 Undirected Graphs Some Graph Applications Undirected graph G = (V,
Reasoning on Words and Trees with Data
 Ph.D. Thesis Summary Reasoning on Words and Trees with Data Author: Diego Figueira Supervisors: Luc Segoufin, Stéphane Demri Abstract A data word (resp. a data tree) is a finite word (resp. tree) whose
Ph.D. Thesis Summary Reasoning on Words and Trees with Data Author: Diego Figueira Supervisors: Luc Segoufin, Stéphane Demri Abstract A data word (resp. a data tree) is a finite word (resp. tree) whose
COMP9319 Web Data Compression & Search. Cloud and data optimization XPath containment Distributed path expression processing
 COMP9319 Web Data Compression & Search Cloud and data optimization XPath containment Distributed path expression processing DATA OPTIMIZATION ON CLOUD Cloud Virtualization Cloud layers Cloud computing
COMP9319 Web Data Compression & Search Cloud and data optimization XPath containment Distributed path expression processing DATA OPTIMIZATION ON CLOUD Cloud Virtualization Cloud layers Cloud computing
3.1 Basic Definitions and Applications
 Chapter 3 Graphs Slides by Kevin Wayne. Copyright 2005 Pearson-Addison Wesley. All rights reserved. 1 3.1 Basic Definitions and Applications Undirected Graphs Undirected graph. G = (V, E) V = nodes. E
Chapter 3 Graphs Slides by Kevin Wayne. Copyright 2005 Pearson-Addison Wesley. All rights reserved. 1 3.1 Basic Definitions and Applications Undirected Graphs Undirected graph. G = (V, E) V = nodes. E
Bounded depth data trees
 Bounded depth data trees Henrik Björklund 1 Miko laj Bojańczyk 2 1 University of Dortmund 2 Warsaw University Abstract. A data tree is a tree where each node has a label from a finite set, and a data value
Bounded depth data trees Henrik Björklund 1 Miko laj Bojańczyk 2 1 University of Dortmund 2 Warsaw University Abstract. A data tree is a tree where each node has a label from a finite set, and a data value
Databases and Information Systems 1 - XPath queries on XML data streams -
 Databases and Information Systems 1 - XPath queries on XML data streams - Dr. Rita Hartel Fakultät EIM, Institut für Informatik Universität Paderborn WS 211 / 212 XPath - looking forward (1) - why? News
Databases and Information Systems 1 - XPath queries on XML data streams - Dr. Rita Hartel Fakultät EIM, Institut für Informatik Universität Paderborn WS 211 / 212 XPath - looking forward (1) - why? News
Graph Algorithms Using Depth First Search
 Graph Algorithms Using Depth First Search Analysis of Algorithms Week 8, Lecture 1 Prepared by John Reif, Ph.D. Distinguished Professor of Computer Science Duke University Graph Algorithms Using Depth
Graph Algorithms Using Depth First Search Analysis of Algorithms Week 8, Lecture 1 Prepared by John Reif, Ph.D. Distinguished Professor of Computer Science Duke University Graph Algorithms Using Depth
Regular Path Queries on Graphs with Data
 Regular Path Queries on Graphs with Data Leonid Libkin Domagoj Vrgoč ABSTRACT Graph data models received much attention lately due to applications in social networks, semantic web, biological databases
Regular Path Queries on Graphs with Data Leonid Libkin Domagoj Vrgoč ABSTRACT Graph data models received much attention lately due to applications in social networks, semantic web, biological databases
Algorithm Design and Analysis
 Algorithm Design and Analysis LECTURE 4 Graphs Definitions Traversals Adam Smith 9/8/10 Exercise How can you simulate an array with two unbounded stacks and a small amount of memory? (Hint: think of a
Algorithm Design and Analysis LECTURE 4 Graphs Definitions Traversals Adam Smith 9/8/10 Exercise How can you simulate an array with two unbounded stacks and a small amount of memory? (Hint: think of a
Regular Languages and Regular Expressions
 Regular Languages and Regular Expressions According to our definition, a language is regular if there exists a finite state automaton that accepts it. Therefore every regular language can be described
Regular Languages and Regular Expressions According to our definition, a language is regular if there exists a finite state automaton that accepts it. Therefore every regular language can be described
Semi-structured Data. 8 - XPath
 Semi-structured Data 8 - XPath Andreas Pieris and Wolfgang Fischl, Summer Term 2016 Outline XPath Terminology XPath at First Glance Location Paths (Axis, Node Test, Predicate) Abbreviated Syntax What is
Semi-structured Data 8 - XPath Andreas Pieris and Wolfgang Fischl, Summer Term 2016 Outline XPath Terminology XPath at First Glance Location Paths (Axis, Node Test, Predicate) Abbreviated Syntax What is
TDDD43. Theme 1.2: XML query languages. Fang Wei- Kleiner h?p:// TDDD43
 Theme 1.2: XML query languages Fang Wei- Kleiner h?p://www.ida.liu.se/~ Query languages for XML Xpath o Path expressions with conditions o Building block of other standards (XQuery, XSLT, XLink, XPointer,
Theme 1.2: XML query languages Fang Wei- Kleiner h?p://www.ida.liu.se/~ Query languages for XML Xpath o Path expressions with conditions o Building block of other standards (XQuery, XSLT, XLink, XPointer,
XML Storage and Indexing
 XML Storage and Indexing Web Data Management and Distribution Serge Abiteboul Ioana Manolescu Philippe Rigaux Marie-Christine Rousset Pierre Senellart Web Data Management and Distribution http://webdam.inria.fr/textbook
XML Storage and Indexing Web Data Management and Distribution Serge Abiteboul Ioana Manolescu Philippe Rigaux Marie-Christine Rousset Pierre Senellart Web Data Management and Distribution http://webdam.inria.fr/textbook
Last lecture CMSC330. This lecture. Finite Automata: States. Finite Automata. Implementing Regular Expressions. Languages. Regular expressions
 Last lecture CMSC330 Finite Automata Languages Sets of strings Operations on languages Regular expressions Constants Operators Precedence 1 2 Finite automata States Transitions Examples Types This lecture
Last lecture CMSC330 Finite Automata Languages Sets of strings Operations on languages Regular expressions Constants Operators Precedence 1 2 Finite automata States Transitions Examples Types This lecture
Finite automata. We have looked at using Lex to build a scanner on the basis of regular expressions.
 Finite automata We have looked at using Lex to build a scanner on the basis of regular expressions. Now we begin to consider the results from automata theory that make Lex possible. Recall: An alphabet
Finite automata We have looked at using Lex to build a scanner on the basis of regular expressions. Now we begin to consider the results from automata theory that make Lex possible. Recall: An alphabet
Copyright 2000, Kevin Wayne 1
 Linear Time: O(n) CS 580: Algorithm Design and Analysis 2.4 A Survey of Common Running Times Merge. Combine two sorted lists A = a 1,a 2,,a n with B = b 1,b 2,,b n into sorted whole. Jeremiah Blocki Purdue
Linear Time: O(n) CS 580: Algorithm Design and Analysis 2.4 A Survey of Common Running Times Merge. Combine two sorted lists A = a 1,a 2,,a n with B = b 1,b 2,,b n into sorted whole. Jeremiah Blocki Purdue
1. Draw the state graphs for the finite automata which accept sets of strings composed of zeros and ones which:
 P R O B L E M S Finite Autom ata. Draw the state graphs for the finite automata which accept sets of strings composed of zeros and ones which: a) Are a multiple of three in length. b) End with the string
P R O B L E M S Finite Autom ata. Draw the state graphs for the finite automata which accept sets of strings composed of zeros and ones which: a) Are a multiple of three in length. b) End with the string
Informatics 1: Data & Analysis
 T O Y H Informatics 1: Data & Analysis Lecture 11: Navigating XML using XPath Ian Stark School of Informatics The University of Edinburgh Tuesday 26 February 2013 Semester 2 Week 6 E H U N I V E R S I
T O Y H Informatics 1: Data & Analysis Lecture 11: Navigating XML using XPath Ian Stark School of Informatics The University of Edinburgh Tuesday 26 February 2013 Semester 2 Week 6 E H U N I V E R S I
Chapter Seven: Regular Expressions. Formal Language, chapter 7, slide 1
 Chapter Seven: Regular Expressions Formal Language, chapter 7, slide The first time a young student sees the mathematical constant π, it looks like just one more school artifact: one more arbitrary symbol
Chapter Seven: Regular Expressions Formal Language, chapter 7, slide The first time a young student sees the mathematical constant π, it looks like just one more school artifact: one more arbitrary symbol
Graphs That Are Randomly Traceable from a Vertex
 Graphs That Are Randomly Traceable from a Vertex Daniel C. Isaksen 27 July 1993 Abstract A graph G is randomly traceable from one of its vertices v if every path in G starting at v can be extended to a
Graphs That Are Randomly Traceable from a Vertex Daniel C. Isaksen 27 July 1993 Abstract A graph G is randomly traceable from one of its vertices v if every path in G starting at v can be extended to a
H2 Spring B. We can abstract out the interactions and policy points from DoDAF operational views
 1. (4 points) Of the following statements, identify all that hold about architecture. A. DoDAF specifies a number of views to capture different aspects of a system being modeled Solution: A is true: B.
1. (4 points) Of the following statements, identify all that hold about architecture. A. DoDAF specifies a number of views to capture different aspects of a system being modeled Solution: A is true: B.
Informatics 1: Data & Analysis
 Informatics 1: Data & Analysis Lecture 11: Navigating XML using XPath Ian Stark School of Informatics The University of Edinburgh Tuesday 23 February 2016 Semester 2 Week 6 http://blog.inf.ed.ac.uk/da16
Informatics 1: Data & Analysis Lecture 11: Navigating XML using XPath Ian Stark School of Informatics The University of Edinburgh Tuesday 23 February 2016 Semester 2 Week 6 http://blog.inf.ed.ac.uk/da16
Efficient Algorithms for the Tree Homeomorphism Problem
 Efficient Algorithms for the Tree Homeomorphism Problem Michaela Götz 1, Christoph Koch 1, and Wim Martens 2 1 Saarland University Saarbrücken, Germany {goetz,koch}@infosys.uni-sb.de 2 University of Dortmund
Efficient Algorithms for the Tree Homeomorphism Problem Michaela Götz 1, Christoph Koch 1, and Wim Martens 2 1 Saarland University Saarbrücken, Germany {goetz,koch}@infosys.uni-sb.de 2 University of Dortmund
Monadic Datalog Containment on Trees
 Monadic Datalog Containment on Trees André Frochaux 1, Martin Grohe 2, and Nicole Schweikardt 1 1 Goethe-Universität Frankfurt am Main, {afrochaux,schweika}@informatik.uni-frankfurt.de 2 RWTH Aachen University,
Monadic Datalog Containment on Trees André Frochaux 1, Martin Grohe 2, and Nicole Schweikardt 1 1 Goethe-Universität Frankfurt am Main, {afrochaux,schweika}@informatik.uni-frankfurt.de 2 RWTH Aachen University,
XPath. Mario Alviano A.Y. 2017/2018. University of Calabria, Italy 1 / 21
 1 / 21 XPath Mario Alviano University of Calabria, Italy A.Y. 2017/2018 Outline 2 / 21 1 Introduction 2 XPath expressions Path expressions Value expressions Node set expressions 3 Examples 4 Exercises
1 / 21 XPath Mario Alviano University of Calabria, Italy A.Y. 2017/2018 Outline 2 / 21 1 Introduction 2 XPath expressions Path expressions Value expressions Node set expressions 3 Examples 4 Exercises
Schema-Based Independence Analysis for XML Updates
 Schema-Based Independence Analysis for XML Updates Michael Benedikt University of Oxford michael.benedikt@comlab.ox.ac.uk James Cheney University of Edinburgh jcheney@inf.ed.ac.uk ABSTRACT Query-update
Schema-Based Independence Analysis for XML Updates Michael Benedikt University of Oxford michael.benedikt@comlab.ox.ac.uk James Cheney University of Edinburgh jcheney@inf.ed.ac.uk ABSTRACT Query-update
XML Data Management. 5. Extracting Data from XML: XPath
 XML Data Management 5. Extracting Data from XML: XPath Werner Nutt based on slides by Sara Cohen, Jerusalem 1 Extracting Data from XML Data stored in an XML document must be extracted to use it with various
XML Data Management 5. Extracting Data from XML: XPath Werner Nutt based on slides by Sara Cohen, Jerusalem 1 Extracting Data from XML Data stored in an XML document must be extracted to use it with various
Complementing deterministic tree-walking automata
 Complementing deterministic tree-walking automata Anca Muscholl LIAFA & CNRS, Université Paris 7, France Luc Segoufin INRIA & Université Paris 11, France September 12, 2005 Mathias Samuelides LIAFA and
Complementing deterministic tree-walking automata Anca Muscholl LIAFA & CNRS, Université Paris 7, France Luc Segoufin INRIA & Université Paris 11, France September 12, 2005 Mathias Samuelides LIAFA and
Regular Expression Constrained Sequence Alignment
 Regular Expression Constrained Sequence Alignment By Abdullah N. Arslan Department of Computer science University of Vermont Presented by Tomer Heber & Raz Nissim otivation When comparing two proteins,
Regular Expression Constrained Sequence Alignment By Abdullah N. Arslan Department of Computer science University of Vermont Presented by Tomer Heber & Raz Nissim otivation When comparing two proteins,
Recoloring k-degenerate graphs
 Recoloring k-degenerate graphs Jozef Jirásek jirasekjozef@gmailcom Pavel Klavík pavel@klavikcz May 2, 2008 bstract This article presents several methods of transforming a given correct coloring of a k-degenerate
Recoloring k-degenerate graphs Jozef Jirásek jirasekjozef@gmailcom Pavel Klavík pavel@klavikcz May 2, 2008 bstract This article presents several methods of transforming a given correct coloring of a k-degenerate
XML Data Management. 6. XPath 1.0 Principles. Werner Nutt
 XML Data Management 6. XPath 1.0 Principles Werner Nutt 1 XPath Expressions and the XPath Document Model XPath expressions are evaluated over documents XPath operates on an abstract document structure
XML Data Management 6. XPath 1.0 Principles Werner Nutt 1 XPath Expressions and the XPath Document Model XPath expressions are evaluated over documents XPath operates on an abstract document structure
CT32 COMPUTER NETWORKS DEC 2015
 Q.2 a. Using the principle of mathematical induction, prove that (10 (2n-1) +1) is divisible by 11 for all n N (8) Let P(n): (10 (2n-1) +1) is divisible by 11 For n = 1, the given expression becomes (10
Q.2 a. Using the principle of mathematical induction, prove that (10 (2n-1) +1) is divisible by 11 for all n N (8) Let P(n): (10 (2n-1) +1) is divisible by 11 For n = 1, the given expression becomes (10
Undirected Graphs. V = { 1, 2, 3, 4, 5, 6, 7, 8 } E = { 1-2, 1-3, 2-3, 2-4, 2-5, 3-5, 3-7, 3-8, 4-5, 5-6 } n = 8 m = 11
 Chapter 3 - Graphs Undirected Graphs Undirected graph. G = (V, E) V = nodes. E = edges between pairs of nodes. Captures pairwise relationship between objects. Graph size parameters: n = V, m = E. V = {
Chapter 3 - Graphs Undirected Graphs Undirected graph. G = (V, E) V = nodes. E = edges between pairs of nodes. Captures pairwise relationship between objects. Graph size parameters: n = V, m = E. V = {
September 3, 2001 XML Processing
 XPointer and XLink Michael B. Spring Department of Information Science and Telecommunications University of Pittsburgh spring@imap.pitt.edu http://www.sis.pitt.edu/~spring Context XML adds new capabilities
XPointer and XLink Michael B. Spring Department of Information Science and Telecommunications University of Pittsburgh spring@imap.pitt.edu http://www.sis.pitt.edu/~spring Context XML adds new capabilities
CHAPTER 3 LITERATURE REVIEW
 20 CHAPTER 3 LITERATURE REVIEW This chapter presents query processing with XML documents, indexing techniques and current algorithms for generating labels. Here, each labeling algorithm and its limitations
20 CHAPTER 3 LITERATURE REVIEW This chapter presents query processing with XML documents, indexing techniques and current algorithms for generating labels. Here, each labeling algorithm and its limitations
Course: The XPath Language
 1 / 27 Course: The XPath Language Pierre Genevès CNRS University of Grenoble, 2012 2013 2 / 27 Why XPath? Search, selection and extraction of information from XML documents are essential for any kind of
1 / 27 Course: The XPath Language Pierre Genevès CNRS University of Grenoble, 2012 2013 2 / 27 Why XPath? Search, selection and extraction of information from XML documents are essential for any kind of
Implementation of Lexical Analysis. Lecture 4
 Implementation of Lexical Analysis Lecture 4 1 Tips on Building Large Systems KISS (Keep It Simple, Stupid!) Don t optimize prematurely Design systems that can be tested It is easier to modify a working
Implementation of Lexical Analysis Lecture 4 1 Tips on Building Large Systems KISS (Keep It Simple, Stupid!) Don t optimize prematurely Design systems that can be tested It is easier to modify a working
Outline. Depth-first Binary Tree Traversal. Gerênciade Dados daweb -DCC922 - XML Query Processing. Motivation 24/03/2014
 Outline Gerênciade Dados daweb -DCC922 - XML Query Processing ( Apresentação basedaem material do livro-texto [Abiteboul et al., 2012]) 2014 Motivation Deep-first Tree Traversal Naïve Page-based Storage
Outline Gerênciade Dados daweb -DCC922 - XML Query Processing ( Apresentação basedaem material do livro-texto [Abiteboul et al., 2012]) 2014 Motivation Deep-first Tree Traversal Naïve Page-based Storage
CSE 417: Algorithms and Computational Complexity. 3.1 Basic Definitions and Applications. Goals. Chapter 3. Winter 2012 Graphs and Graph Algorithms
 Chapter 3 CSE 417: Algorithms and Computational Complexity Graphs Reading: 3.1-3.6 Winter 2012 Graphs and Graph Algorithms Slides by Kevin Wayne. Copyright 2005 Pearson-Addison Wesley. All rights reserved.
Chapter 3 CSE 417: Algorithms and Computational Complexity Graphs Reading: 3.1-3.6 Winter 2012 Graphs and Graph Algorithms Slides by Kevin Wayne. Copyright 2005 Pearson-Addison Wesley. All rights reserved.
Formal Methods for XML: Algorithms & Complexity
 Formal Methods for XML: Algorithms & Complexity S. Margherita di Pula September 2004 Thomas Schwentick Schwentick XML: Algorithms & Complexity Introduction 1 Disclaimer About this talk It will be Theory
Formal Methods for XML: Algorithms & Complexity S. Margherita di Pula September 2004 Thomas Schwentick Schwentick XML: Algorithms & Complexity Introduction 1 Disclaimer About this talk It will be Theory
Foundations of Computer Science Spring Mathematical Preliminaries
 Foundations of Computer Science Spring 2017 Equivalence Relation, Recursive Definition, and Mathematical Induction Mathematical Preliminaries Mohammad Ashiqur Rahman Department of Computer Science College
Foundations of Computer Science Spring 2017 Equivalence Relation, Recursive Definition, and Mathematical Induction Mathematical Preliminaries Mohammad Ashiqur Rahman Department of Computer Science College
Context Free Languages
 Context Free Languages COMP2600 Formal Methods for Software Engineering Katya Lebedeva Australian National University Semester 2, 2016 Slides by Katya Lebedeva and Ranald Clouston. COMP 2600 Context Free
Context Free Languages COMP2600 Formal Methods for Software Engineering Katya Lebedeva Australian National University Semester 2, 2016 Slides by Katya Lebedeva and Ranald Clouston. COMP 2600 Context Free
XML Research for Formal Language Theorists
 XML Research for Formal Language Theorists Wim Martens TU Dortmund Wim Martens (TU Dortmund) XML for Formal Language Theorists May 14, 2008 1 / 65 Goal of this talk XML Research vs Formal Languages Wim
XML Research for Formal Language Theorists Wim Martens TU Dortmund Wim Martens (TU Dortmund) XML for Formal Language Theorists May 14, 2008 1 / 65 Goal of this talk XML Research vs Formal Languages Wim
1 Introduction. Philippe Michiels. Jan Hidders University of Antwerp. University of Antwerp. Roel Vercammen. University of Antwerp
 OPTIMIZING SORTING AND DUPLICATE ELIMINATION IN XQUERY PATH EXPRESSIONS Jan Hidders University of Antwerp jan.hidders@ua.ac.be Roel Vercammen University of Antwerp roel.vercammen@ua.ac.be Abstract Philippe
OPTIMIZING SORTING AND DUPLICATE ELIMINATION IN XQUERY PATH EXPRESSIONS Jan Hidders University of Antwerp jan.hidders@ua.ac.be Roel Vercammen University of Antwerp roel.vercammen@ua.ac.be Abstract Philippe
Context-Free Languages & Grammars (CFLs & CFGs) Reading: Chapter 5
 Context-Free Languages & Grammars (CFLs & CFGs) Reading: Chapter 5 1 Not all languages are regular So what happens to the languages which are not regular? Can we still come up with a language recognizer?
Context-Free Languages & Grammars (CFLs & CFGs) Reading: Chapter 5 1 Not all languages are regular So what happens to the languages which are not regular? Can we still come up with a language recognizer?
Distributed Query Evaluation with Performance Guarantees
 Distributed Query Evaluation with Performance Guarantees Gao Cong Microsoft Research Asia gaocong@microsoft.com Wenfei Fan University of Edinburgh & Bell Laboratories wenfei@inf.ed.ac.uk Anastasios Kementsietsidis
Distributed Query Evaluation with Performance Guarantees Gao Cong Microsoft Research Asia gaocong@microsoft.com Wenfei Fan University of Edinburgh & Bell Laboratories wenfei@inf.ed.ac.uk Anastasios Kementsietsidis
Introduction to Computers and Programming. Concept Question
 Introduction to Computers and Programming Prof. I. K. Lundqvist Lecture 7 April 2 2004 Concept Question G1(V1,E1) A graph G(V, where E) is V1 a finite = {}, nonempty E1 = {} set of G2(V2,E2) vertices and
Introduction to Computers and Programming Prof. I. K. Lundqvist Lecture 7 April 2 2004 Concept Question G1(V1,E1) A graph G(V, where E) is V1 a finite = {}, nonempty E1 = {} set of G2(V2,E2) vertices and
XPath Processing in a Nutshell
 XPath Processing in a Nutshell Georg Gottlob, Christoph Koch, and Reinhard Pichler Database and Artificial Intelligence Group Technische Universität Wien, A-1040 Vienna, Austria {gottlob, koch}@dbai.tuwien.ac.at,
XPath Processing in a Nutshell Georg Gottlob, Christoph Koch, and Reinhard Pichler Database and Artificial Intelligence Group Technische Universität Wien, A-1040 Vienna, Austria {gottlob, koch}@dbai.tuwien.ac.at,
XML & Databases. Tutorial. 3. XPath Queries. Universität Konstanz. Database & Information Systems Group Prof. Marc H. Scholl
 XML & Databases Tutorial Christian Grün, Database & Information Systems Group University of, Winter 2007/08 XPath Introduction navigational access to XML documents sub-language in XQuery, XSLT, or XPointer
XML & Databases Tutorial Christian Grün, Database & Information Systems Group University of, Winter 2007/08 XPath Introduction navigational access to XML documents sub-language in XQuery, XSLT, or XPointer
Depth-First Search Depth-first search (DFS) is another way to traverse the graph.
 Depth-First Search Depth-first search (DFS) is another way to traverse the graph. Motivating example: In a video game, you are searching for a path from a point in a maze to the exit. The maze can be modeled
Depth-First Search Depth-first search (DFS) is another way to traverse the graph. Motivating example: In a video game, you are searching for a path from a point in a maze to the exit. The maze can be modeled
Reachability in K 3,3 -free and K 5 -free Graphs is in Unambiguous Logspace
 CHICAGO JOURNAL OF THEORETICAL COMPUTER SCIENCE 2014, Article 2, pages 1 29 http://cjtcs.cs.uchicago.edu/ Reachability in K 3,3 -free and K 5 -free Graphs is in Unambiguous Logspace Thomas Thierauf Fabian
CHICAGO JOURNAL OF THEORETICAL COMPUTER SCIENCE 2014, Article 2, pages 1 29 http://cjtcs.cs.uchicago.edu/ Reachability in K 3,3 -free and K 5 -free Graphs is in Unambiguous Logspace Thomas Thierauf Fabian
Certain and Possible XPath Answers
 Certain and Possible XPath Answers Sara Cohen School of Computer Science and Engineering Hebrew University of Jerusalem Jerusalem, Israel sara@cs.huji.ac.il Yaacov Y. Weiss School of Computer Science and
Certain and Possible XPath Answers Sara Cohen School of Computer Science and Engineering Hebrew University of Jerusalem Jerusalem, Israel sara@cs.huji.ac.il Yaacov Y. Weiss School of Computer Science and
DFS & STRONGLY CONNECTED COMPONENTS
 DFS & STRONGLY CONNECTED COMPONENTS CS 4407 Search Tree Breadth-First Search (BFS) Depth-First Search (DFS) Depth-First Search (DFS) u d[u]: when u is discovered f[u]: when searching adj of u is finished
DFS & STRONGLY CONNECTED COMPONENTS CS 4407 Search Tree Breadth-First Search (BFS) Depth-First Search (DFS) Depth-First Search (DFS) u d[u]: when u is discovered f[u]: when searching adj of u is finished
Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) January 11, 2018 Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1 In this lecture
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) January 11, 2018 Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1 In this lecture
FOUNDATIONS OF DATABASES AND QUERY LANGUAGES
 FOUNDATIONS OF DATABASES AND QUERY LANGUAGES Lecture 14: Database Theory in Practice Markus Krötzsch TU Dresden, 20 July 2015 Overview 1. Introduction Relational data model 2. First-order queries 3. Complexity
FOUNDATIONS OF DATABASES AND QUERY LANGUAGES Lecture 14: Database Theory in Practice Markus Krötzsch TU Dresden, 20 July 2015 Overview 1. Introduction Relational data model 2. First-order queries 3. Complexity
Complexity Theory. Compiled By : Hari Prasad Pokhrel Page 1 of 20. ioenotes.edu.np
 Chapter 1: Introduction Introduction Purpose of the Theory of Computation: Develop formal mathematical models of computation that reflect real-world computers. Nowadays, the Theory of Computation can be
Chapter 1: Introduction Introduction Purpose of the Theory of Computation: Develop formal mathematical models of computation that reflect real-world computers. Nowadays, the Theory of Computation can be
Course: The XPath Language
 1 / 30 Course: The XPath Language Pierre Genevès CNRS University of Grenoble Alpes, 2017 2018 2 / 30 Why XPath? Search, selection and extraction of information from XML documents are essential for any
1 / 30 Course: The XPath Language Pierre Genevès CNRS University of Grenoble Alpes, 2017 2018 2 / 30 Why XPath? Search, selection and extraction of information from XML documents are essential for any
XML and Databases. Lecture 10 XPath Evaluation using RDBMS. Sebastian Maneth NICTA and UNSW
 XML and Databases Lecture 10 XPath Evaluation using RDBMS Sebastian Maneth NICTA and UNSW CSE@UNSW -- Semester 1, 2009 Outline 1. Recall pre / post encoding 2. XPath with //, ancestor, @, and text() 3.
XML and Databases Lecture 10 XPath Evaluation using RDBMS Sebastian Maneth NICTA and UNSW CSE@UNSW -- Semester 1, 2009 Outline 1. Recall pre / post encoding 2. XPath with //, ancestor, @, and text() 3.
Example using multiple predicates
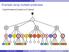 XPath Example using multiple predicates //performance[conductor][date] L C C C C p c s p p s o t d p p c p p Peter Wood (BBK) XML Data Management 162 / 366 XPath Further examples with predicates //performance[composer='frederic
XPath Example using multiple predicates //performance[conductor][date] L C C C C p c s p p s o t d p p c p p Peter Wood (BBK) XML Data Management 162 / 366 XPath Further examples with predicates //performance[composer='frederic
Reasoning about XML Update Constraints
 Reasoning about XML Update Constraints Bogdan Cautis INRIA Futurs & U. Paris Sud bogdan.cautis@inria.fr Serge Abiteboul INRIA Futurs & U. Paris Sud serge.abiteboul@inria.fr Tova Milo Tel Aviv U. milo@cs.tau.ac.il
Reasoning about XML Update Constraints Bogdan Cautis INRIA Futurs & U. Paris Sud bogdan.cautis@inria.fr Serge Abiteboul INRIA Futurs & U. Paris Sud serge.abiteboul@inria.fr Tova Milo Tel Aviv U. milo@cs.tau.ac.il
Ecient XPath Axis Evaluation for DOM Data Structures
 Ecient XPath Axis Evaluation for DOM Data Structures Jan Hidders Philippe Michiels University of Antwerp Dept. of Math. and Comp. Science Middelheimlaan 1, BE-2020 Antwerp, Belgium, fjan.hidders,philippe.michielsg@ua.ac.be
Ecient XPath Axis Evaluation for DOM Data Structures Jan Hidders Philippe Michiels University of Antwerp Dept. of Math. and Comp. Science Middelheimlaan 1, BE-2020 Antwerp, Belgium, fjan.hidders,philippe.michielsg@ua.ac.be
Graph Algorithms. Andreas Klappenecker. [based on slides by Prof. Welch]
![Graph Algorithms. Andreas Klappenecker. [based on slides by Prof. Welch] Graph Algorithms. Andreas Klappenecker. [based on slides by Prof. Welch]](/thumbs/81/84350835.jpg) Graph Algorithms Andreas Klappenecker [based on slides by Prof. Welch] 1 Directed Graphs Let V be a finite set and E a binary relation on V, that is, E VxV. Then the pair G=(V,E) is called a directed graph.
Graph Algorithms Andreas Klappenecker [based on slides by Prof. Welch] 1 Directed Graphs Let V be a finite set and E a binary relation on V, that is, E VxV. Then the pair G=(V,E) is called a directed graph.
Quiz 1: Solutions J/18.400J: Automata, Computability and Complexity. Nati Srebro, Susan Hohenberger
 6.45J/8.4J: utomata, Computability and Complexity Quiz : Solutions Prof. Nancy Lynch Nati Srebro, Susan Hohenberger Please write your name in the upper corner of each page. (2 Points) Q- Problem : True
6.45J/8.4J: utomata, Computability and Complexity Quiz : Solutions Prof. Nancy Lynch Nati Srebro, Susan Hohenberger Please write your name in the upper corner of each page. (2 Points) Q- Problem : True
Streaming XPath Processing with Forward and Backward Axes
 Streaming XPath Processing with Forward and Backward Axes Charles Barton, Philippe Charles Deepak Goyal, Mukund Raghavachari IBM T.J. Watson Research Center Marcus Fontoura, Vanja Josifovski IBM Almaden
Streaming XPath Processing with Forward and Backward Axes Charles Barton, Philippe Charles Deepak Goyal, Mukund Raghavachari IBM T.J. Watson Research Center Marcus Fontoura, Vanja Josifovski IBM Almaden
Trees, Automata and XML
 A Mini Course on Trees, Automata and XML Paris June 2004 Thomas Schwentick PODS 2004 Thomas Schwentick Trees, Automata & XML 1 Intro Three Questions Question 1 Why XML? Answer Have a look into the 20 XML
A Mini Course on Trees, Automata and XML Paris June 2004 Thomas Schwentick PODS 2004 Thomas Schwentick Trees, Automata & XML 1 Intro Three Questions Question 1 Why XML? Answer Have a look into the 20 XML
Streaming XPath Processing with Forward and Backward Axes
 Streaming XPath Processing with Forward and Backward Axes Charles Barton, Philippe Charles Deepak Goyal, Mukund Raghavachari IBM T.J. Watson Research Center Marcus Fontoura, Vanja Josifovski IBM Almaden
Streaming XPath Processing with Forward and Backward Axes Charles Barton, Philippe Charles Deepak Goyal, Mukund Raghavachari IBM T.J. Watson Research Center Marcus Fontoura, Vanja Josifovski IBM Almaden
Seleniet XPATH Locator QuickRef
 Seleniet XPATH Locator QuickRef Author(s) Thomas Eitzenberger Version 0.2 Status Ready for review Page 1 of 11 Content Selecting Nodes...3 Predicates...3 Selecting Unknown Nodes...4 Selecting Several Paths...5
Seleniet XPATH Locator QuickRef Author(s) Thomas Eitzenberger Version 0.2 Status Ready for review Page 1 of 11 Content Selecting Nodes...3 Predicates...3 Selecting Unknown Nodes...4 Selecting Several Paths...5
Formal Languages and Compilers Lecture IV: Regular Languages and Finite. Finite Automata
 Formal Languages and Compilers Lecture IV: Regular Languages and Finite Automata Free University of Bozen-Bolzano Faculty of Computer Science POS Building, Room: 2.03 artale@inf.unibz.it http://www.inf.unibz.it/
Formal Languages and Compilers Lecture IV: Regular Languages and Finite Automata Free University of Bozen-Bolzano Faculty of Computer Science POS Building, Room: 2.03 artale@inf.unibz.it http://www.inf.unibz.it/
MIT Specifying Languages with Regular Expressions and Context-Free Grammars
 MIT 6.035 Specifying Languages with Regular essions and Context-Free Grammars Martin Rinard Laboratory for Computer Science Massachusetts Institute of Technology Language Definition Problem How to precisely
MIT 6.035 Specifying Languages with Regular essions and Context-Free Grammars Martin Rinard Laboratory for Computer Science Massachusetts Institute of Technology Language Definition Problem How to precisely
MIT Specifying Languages with Regular Expressions and Context-Free Grammars. Martin Rinard Massachusetts Institute of Technology
 MIT 6.035 Specifying Languages with Regular essions and Context-Free Grammars Martin Rinard Massachusetts Institute of Technology Language Definition Problem How to precisely define language Layered structure
MIT 6.035 Specifying Languages with Regular essions and Context-Free Grammars Martin Rinard Massachusetts Institute of Technology Language Definition Problem How to precisely define language Layered structure
Chapter Seven: Regular Expressions
 Chapter Seven: Regular Expressions Regular Expressions We have seen that DFAs and NFAs have equal definitional power. It turns out that regular expressions also have exactly that same definitional power:
Chapter Seven: Regular Expressions Regular Expressions We have seen that DFAs and NFAs have equal definitional power. It turns out that regular expressions also have exactly that same definitional power:
Section 5.5. Left subtree The left subtree of a vertex V on a binary tree is the graph formed by the left child L of V, the descendents
 Section 5.5 Binary Tree A binary tree is a rooted tree in which each vertex has at most two children and each child is designated as being a left child or a right child. Thus, in a binary tree, each vertex
Section 5.5 Binary Tree A binary tree is a rooted tree in which each vertex has at most two children and each child is designated as being a left child or a right child. Thus, in a binary tree, each vertex
CSE 105 THEORY OF COMPUTATION
 CSE 105 THEORY OF COMPUTATION Spring 2017 http://cseweb.ucsd.edu/classes/sp17/cse105-ab/ Today's learning goals Sipser Ch 1.2, 1.3 Design NFA recognizing a given language Convert an NFA (with or without
CSE 105 THEORY OF COMPUTATION Spring 2017 http://cseweb.ucsd.edu/classes/sp17/cse105-ab/ Today's learning goals Sipser Ch 1.2, 1.3 Design NFA recognizing a given language Convert an NFA (with or without
Querying XML with Update Syntax
 Querying XML with Update Syntax Wenfei Fan University of Edinburgh & Bell Laboratories wenfei@inf.ed.ac.uk Gao Cong Microsoft Research Asia gaocong@microsoft.com Philip Bohannon Yahoo Research plb@yahoo-inc.com
Querying XML with Update Syntax Wenfei Fan University of Edinburgh & Bell Laboratories wenfei@inf.ed.ac.uk Gao Cong Microsoft Research Asia gaocong@microsoft.com Philip Bohannon Yahoo Research plb@yahoo-inc.com
Chapter 10: Trees. A tree is a connected simple undirected graph with no simple circuits.
 Chapter 10: Trees A tree is a connected simple undirected graph with no simple circuits. Properties: o There is a unique simple path between any 2 of its vertices. o No loops. o No multiple edges. Example
Chapter 10: Trees A tree is a connected simple undirected graph with no simple circuits. Properties: o There is a unique simple path between any 2 of its vertices. o No loops. o No multiple edges. Example
Languages and Compilers
 Principles of Software Engineering and Operational Systems Languages and Compilers SDAGE: Level I 2012-13 3. Formal Languages, Grammars and Automata Dr Valery Adzhiev vadzhiev@bournemouth.ac.uk Office:
Principles of Software Engineering and Operational Systems Languages and Compilers SDAGE: Level I 2012-13 3. Formal Languages, Grammars and Automata Dr Valery Adzhiev vadzhiev@bournemouth.ac.uk Office:
Validity-Sensitive Querying of XML Databases
 Validity-Sensitive Querying of XML Databases Slawomir Staworko Jan homicki Department of omputer Science University at Buffalo DataX, March 26, 2006 Motivation Querying Invalid XML Integration of XML documents
Validity-Sensitive Querying of XML Databases Slawomir Staworko Jan homicki Department of omputer Science University at Buffalo DataX, March 26, 2006 Motivation Querying Invalid XML Integration of XML documents
Outline of this part (I) Part IV. Querying XML Documents. Querying XML Documents. Outline of this part (II)
 Outline of this part (I) Part IV Querying XML Documents Marc H. Scholl (DBIS, Uni KN) XML and Databases Winter 2007/08 164 8 XPath Navigational access to XML documents Overview Context Location steps Navigation
Outline of this part (I) Part IV Querying XML Documents Marc H. Scholl (DBIS, Uni KN) XML and Databases Winter 2007/08 164 8 XPath Navigational access to XML documents Overview Context Location steps Navigation
Ling/CSE 472: Introduction to Computational Linguistics. 4/6/15: Morphology & FST 2
 Ling/CSE 472: Introduction to Computational Linguistics 4/6/15: Morphology & FST 2 Overview Review: FSAs & FSTs XFST xfst demo Examples of FSTs for spelling change rules Reading questions Review: FSAs
Ling/CSE 472: Introduction to Computational Linguistics 4/6/15: Morphology & FST 2 Overview Review: FSAs & FSTs XFST xfst demo Examples of FSTs for spelling change rules Reading questions Review: FSAs
Graph Theory S 1 I 2 I 1 S 2 I 1 I 2
 Graph Theory S I I S S I I S Graphs Definition A graph G is a pair consisting of a vertex set V (G), and an edge set E(G) ( ) V (G). x and y are the endpoints of edge e = {x, y}. They are called adjacent
Graph Theory S I I S S I I S Graphs Definition A graph G is a pair consisting of a vertex set V (G), and an edge set E(G) ( ) V (G). x and y are the endpoints of edge e = {x, y}. They are called adjacent
Graph Algorithms. Chapter 22. CPTR 430 Algorithms Graph Algorithms 1
 Graph Algorithms Chapter 22 CPTR 430 Algorithms Graph Algorithms Why Study Graph Algorithms? Mathematical graphs seem to be relatively specialized and abstract Why spend so much time and effort on algorithms
Graph Algorithms Chapter 22 CPTR 430 Algorithms Graph Algorithms Why Study Graph Algorithms? Mathematical graphs seem to be relatively specialized and abstract Why spend so much time and effort on algorithms
Recognizing Interval Bigraphs by Forbidden Patterns
 Recognizing Interval Bigraphs by Forbidden Patterns Arash Rafiey Simon Fraser University, Vancouver, Canada, and Indiana State University, IN, USA arashr@sfu.ca, arash.rafiey@indstate.edu Abstract Let
Recognizing Interval Bigraphs by Forbidden Patterns Arash Rafiey Simon Fraser University, Vancouver, Canada, and Indiana State University, IN, USA arashr@sfu.ca, arash.rafiey@indstate.edu Abstract Let
Containment of Data Graph Queries
 Containment of Data Graph Queries Egor V. Kostylev University of Oxford and University of Edinburgh egor.kostylev@cs.ox.ac.uk Juan L. Reutter PUC Chile jreutter@ing.puc.cl Domagoj Vrgoč University of Edinburgh
Containment of Data Graph Queries Egor V. Kostylev University of Oxford and University of Edinburgh egor.kostylev@cs.ox.ac.uk Juan L. Reutter PUC Chile jreutter@ing.puc.cl Domagoj Vrgoč University of Edinburgh
