Cello How-To Guide. Security Management
|
|
|
- Amanda Bond
- 5 years ago
- Views:
Transcription
1 Cello How-To Guide Security Management
2 Contents 1 Security Management Introduction to Privilege Feature Privilege Configure feature privilege through Fluent API Role Privilege User Privileges Page Level Security Default Entity Configuration Action Level Security Service Level Security Contact Information
3 1 Security Management CelloSaaS allows the developers to build security management in their application more easily. The following objects can be secured using CelloSaaS o Pages/Actions o Service CelloSaaS achieves the security using privileges. Developer need to demand the right privilege in the code for Pages / Actions [presentation tier], Service [Service calls], Data and Fields. Privileges are available to the system via the license package modules and features. The Privileges for user is derived from the User s Tenant License Package and his Roles Privilege. Privileges are mapped to roles. Any application user will get access to the applications features provided he / she possesses the right privilege based on the user s tenant license. 1.1 Introduction to Privilege Privilege is used for fine grained level of access control management. Privilege will be associated with features referred to as feature privilege. Privilege will be mapped with Entity to restrict the access of an entity actions like add, edit, view, delete and etc. Privilege Id and name should be unique. Entity action privileges should follow the naming conversion Action_EntityId. 1.2 Feature Privilege Privileges are identified and configured during the development time and not at runtime. Example: While building a Feature called Leave Application Form and Leave List Page, some of the privileges such as Add Leave, View Leave details, Delete Leave, Edit Leave etc can be identified and configured in the system. Note: In case if a new privilege has to be added in the system, it can only be configured in the code or in the database. 1.3 Configure feature privilege through Fluent API Through XML Configuration In Xml configuration add necessary privileges under the Feature xml tag like below. <ModuleConfiguration> <Modules> 3
4 <Module Code="ProjectModule" Name="Project Module" Description="This module contains feature and usgae of the project"> <Features> <Feature Code="ProjectFeature" Name="Project Feature"> <Privileges> <Privilege Name="Search Project" Description="user can search their Project list">search_project</privilege> <Privilege Name="View Project" Description="user can View their Project list">view_project</privilege> <Privilege Name="Add Project" Description="user can add their Project.">Add_Project</Privilege> <Privilege Name="Edit Project" Description="user can Edit their Project.">Edit_Project</Privilege> <Privilege Name="Delete Project" Description="user can delete their Project.">Delete_Project</Privilege> <Privilege Name="Approve Project" Description="user can Approve the Project.">Approval_Project</Privilege> </Privileges> </Feature> </Features> </Module> </Modules> </ModuleConfiguration> Through Fluent API In module configuration object add privileges against the feature using WithPrivilege() method. public void Configure(ModuleConfig moduleconfiguration) moduleconfiguration.add("employee", "Employee").WithFeatures(f => f.add("manageemployee").withname("manage Employee").WithPrivileges((p => p.add("viewemployee").withname("view Employee").WithDescription("User can View Employee details.").add("addemployee").withname("add Employee").WithDescription("User can Add Employee details.").add("editemployee").withname("edit Employee").WithDescription("User can Edit Employee details.").add("deleteemployee").withname("delete Employee").WithDescription("User can Delete Employee details.")))); 1.4 Role Privilege Each role will be mapped with one or many privileges. Role and privilege combination must be unique for each tenant. Select Access Control -> Manage Roles. This page will list the available roles for logged-in user tenant. For more details refer Role Management in click here. Click Manage Privilege icon to map privilege for the particular role. 4
5 Role privilege page will display all feature privileges based on the tenant license package. This page contains two sections named Available Privileges and Assigned Privileges. 5
6 Assigned Privilege section contains the privileges of selected role. Available privilege section contains the privileges that can be assigned. Adding privilege [s] to a role Select privilege [s] from Available privilege section and click Add button to add to a role. Revoking privilege [s] from a role Select privilege [s] from Assigned privileges section and click Remove button to delete a privilege from a role. Modules & Feature filtering for Privileges Module lists the available modules from tenant license package. Feature lists the available features from tenant license package. You can filter the privileges based on Modules and Features. 1.5 User Privileges To get the logged in user privileges from his identity use CelloSaaS.Library.UserIdentity.Privileges. This contains the privileges for the user that has logged in to the system. 1.6 Page Level Security Controllers must inherit from CelloSaaS.View.CelloController to perform action method level security restrictions. Page level access is obtained by the configuration in EntityPermission.Config file. All URL s mapped to the required access rule which is then checked automatically whenever that page or action is called CelloSaaS menu provider is integrated with entity permission rule so turn off the menus to the page access rule is not met. Access rule is combination of Privileges, Roles, Identity and Tenant Settings. Example: P:Add_Employee AND R:GR$Tenant_Admin. If the logged-in user has Add Employee privilege and Tenant Admin role then user can access the particular page. CelloSaaS provide the default entity permission configuration for CelloSaaS admin pages. 6
7 1.7 Default Entity Configuration Entity permission will have two category named UI and BL. Page level configurations are to be added in the UI section under the Entity tag. Set the URL or action in name attribute. Specify the access rule in AuthorizationRule attribute. Use the following Authorization Rule formats. Format Example Role R:RoleId R:GR$Tenant_Admin Privilege P:PrivilegeId P:View_Employee Identity I:Identity Tenant Settings S:TenantSettingsId S:ShareUsers 7
8 Access rule can be constructed as a complex expression containing AND, OR and NOT. You can also combine permission, role and tenant settings. Example: AuthorizationRule="S:ShareUsers AND R:GR$Tenant_Admin AND P:View_User" 1.8 Action Level Security You can check the necessary privileges before start executing the method in Services. You can do either using CheckPrivilge method or PrivilegeContext. Use CheckPrivilege method to check required privilege for a service method. Namespace : CelloSaaS.Services.AccessControlManagement Service: AccessControlService Method : CheckPrivilege(string privilege) /// <summary> /// This method is used to Check if the user's role has access to the privilege bool CheckPrivilege(string privilege) Sample: public EmployeeDetails GetEmployeeDetailsByEmployeeID(string employeeid) IAccessControlService accesscontrolservice = (IAccessControlService) ServiceLocator.GetServiceImplementation( typeof(iaccesscontrolservice)); // Check whether the user has permission to add user details or not. if (!accesscontrolservice.checkprivilege( ManageEmployeeEmployeeDetailsConstants.ViewEmployeeDetails)) throw new UnauthorizedAccessException("Permission to access Get EmployeeDetails By EmployeeID is denied."); // Write logic to get employee details by employee id. If logged-in user doesn t have privilege to access the particular method then throw UnauthorizedAccessException. You can use PrivilegeContext to check the privilege in another way. To access the service, demand the privilege by using CelloSaaS.Library.Context which is provided by CelloSaaS. 8
9 Context has the following ethods: /// This method is used to create PrivilegeContext instance and that will be add in HttpContext.Current.Items with Privilege as key void SetPrivilegeContext(string privilegename); Usually privilege will be demanded from the controller before calling Proxy methods by using SetPrivilegeContext method. Example: CelloSaaS.Library.Context.SetPrivilegeContext( Edit_EmployeeDetails ); In services, current privilege will be taken from HttpContext by using GetCurrentPrivilegeContext method. /// This method is used to get the PrivilegeContext instance which is currently present. CelloSaaS.Library.PrivilegeContext GetCurrentPrivilegeContext(); Example public EmployeeDetails GetEmployeeDetailsByEmployeeID(string employeeid) string currentprivilege = string.empty; PrivilegeContext privilegecontext =Context.GetCurrentPrivilegeContext(); if (privilegecontext!= null) currentprivilege = privilegecontext.privilegename; if (!string.isnullorempty(currentprivilege) &&!UserIdentity.HasPrivilege(currentPrivilege)) throw new UnauthorizedAccessException("Permission to access Get EmployeeDetails By EmployeeID is denied."); // Write logic to get employee details by employee id. 1.9 Service Level Security Service level security is possible via Entity Permission config file. Need to add the Service Contract name under the Entity Category BL. Add the Contract name under entity node. Add the necessary method names with the authorization rule under Entity Sub Element. Example 9
10 <EntityPermission> <EntityCategory> <add name="bl"> <Entity> <add name="cellosaas.servicecontracts.usermanagement.iuserdetailsservice"> <EntitySubElement> <add name="searchuserdetails" AuthorizationRule="P:View_User"></add> </EntitySubElement> </add> </Entity> </add> </EntityCategory> </EntityPermission> 10
11 2 Contact Information Any problem using this guide (or) using Cello Framework. Please feel free to contact us, we will be happy to assist you in getting started with Cello. Phone: +1(609) Skype: techcello 11
Cello How-To Guide. Package Management
 Cello How-To Guide Package Management Contents 1 Package Management... 4 1.1 How to implement packages in cello... 4 1.2 Cello Package Structure... 4 1.3 How to Configure a Module... 5 1.4 How to Configure
Cello How-To Guide Package Management Contents 1 Package Management... 4 1.1 How to implement packages in cello... 4 1.2 Cello Package Structure... 4 1.3 How to Configure a Module... 5 1.4 How to Configure
Cello How To-Do guide. Notification Management
 Cello How To-Do guide Notification Management Contents 1. Notification Management... 3 1.1. CelloSaaS Notification Architecture... 3 1.2. Privileges required for Notification System... 4 1.3. Default Notification
Cello How To-Do guide Notification Management Contents 1. Notification Management... 3 1.1. CelloSaaS Notification Architecture... 3 1.2. Privileges required for Notification System... 4 1.3. Default Notification
Cello How-To Guide. Page Profiler
 Cello How-To Guide Page Profiler Contents 1 Page Profiler... 3 1.1 SQL Queries... 3 1.2 Security... 4 1.3 Performance... 5 1.4 User Identity... 7 1.5 Tenant License... 7 1.6 Environment... 8 1.7 Response...
Cello How-To Guide Page Profiler Contents 1 Page Profiler... 3 1.1 SQL Queries... 3 1.2 Security... 4 1.3 Performance... 5 1.4 User Identity... 7 1.5 Tenant License... 7 1.6 Environment... 8 1.7 Response...
Cello How-To Guide. Membership Management
 Cello How-To Guide Membership Management Contents 1 Membership Management... 3 1.1 Roles and Access provisions in CelloSaaS... 3 1.2 Add/Edit Role... 4 1.3 Delete Role... 4 1.4 Mapping Privilege to Roles...
Cello How-To Guide Membership Management Contents 1 Membership Management... 3 1.1 Roles and Access provisions in CelloSaaS... 3 1.2 Add/Edit Role... 4 1.3 Delete Role... 4 1.4 Mapping Privilege to Roles...
Cello How-To Guide. Configuring and Consuming CelloSaaS WCF Services
 Cello How-To Guide Configuring and Consuming CelloSaaS WCF Services Contents 1 Introduction... 3 2 Windows Communication Foundation (WCF) service... 4 2.1 Hosting CelloSaaS WCF service... 4 2.2 How to
Cello How-To Guide Configuring and Consuming CelloSaaS WCF Services Contents 1 Introduction... 3 2 Windows Communication Foundation (WCF) service... 4 2.1 Hosting CelloSaaS WCF service... 4 2.2 How to
Real Application Security Administration
 Oracle Database Real Application Security Administration Console (RASADM) User s Guide 12c Release 2 (12.2) E85615-01 June 2017 Real Application Security Administration Oracle Database Real Application
Oracle Database Real Application Security Administration Console (RASADM) User s Guide 12c Release 2 (12.2) E85615-01 June 2017 Real Application Security Administration Oracle Database Real Application
Oracle Database. Installation and Configuration of Real Application Security Administration (RASADM) Prerequisites
 Oracle Database Real Application Security Administration 12c Release 1 (12.1) E61899-04 May 2015 Oracle Database Real Application Security Administration (RASADM) lets you create Real Application Security
Oracle Database Real Application Security Administration 12c Release 1 (12.1) E61899-04 May 2015 Oracle Database Real Application Security Administration (RASADM) lets you create Real Application Security
Dynamics CRM Integration for Gmail. User Manual. Akvelon, Inc. 2017, All rights reserved
 User Manual Akvelon, Inc. 2017, All rights reserved Contents Overview... 3 Installation of Dynamics CRM Integration for Gmail 2.0... 3 Buying app subscription... 4 Remove the extension from Chrome... 5
User Manual Akvelon, Inc. 2017, All rights reserved Contents Overview... 3 Installation of Dynamics CRM Integration for Gmail 2.0... 3 Buying app subscription... 4 Remove the extension from Chrome... 5
OfficeClip Reference Manual
 OfficeClip Reference Manual OfficeClip Reference Manual Table of Contents 1. General Information... 1 1.1. About this Reference Manual... 1 1.2. Conventions used in this Manual... 1 1.3. About OfficeClip...
OfficeClip Reference Manual OfficeClip Reference Manual Table of Contents 1. General Information... 1 1.1. About this Reference Manual... 1 1.2. Conventions used in this Manual... 1 1.3. About OfficeClip...
It is necessary to follow all of the sections below in the presented order. Skipping steps may prevent subsequent sections from working correctly.
 The following example demonstrates how to create a basic custom module, including all steps required to create Installation packages for the module. You can use the packages to distribute the module to
The following example demonstrates how to create a basic custom module, including all steps required to create Installation packages for the module. You can use the packages to distribute the module to
TOP Server Version 6 Security Settings
 TOP Server 1 (10) TOP Server Version 6 TOP Server 2 (10) Contents Security Built In... 3 User Manager Configuration... 3 New User Accounts... 5 New User Group and Properties... 5 Configuration Security...
TOP Server 1 (10) TOP Server Version 6 TOP Server 2 (10) Contents Security Built In... 3 User Manager Configuration... 3 New User Accounts... 5 New User Group and Properties... 5 Configuration Security...
Grouper new UI. Other screens not captured here. General information. These topics are discussed in the "Grouper UI" training series.
 Grouper new UI Wiki Home Download Grouper Grouper Guides Community Contributions Developer Resources Grouper Website These topics are discussed in the "Grouper UI" training series. Grouper 2.2 and above
Grouper new UI Wiki Home Download Grouper Grouper Guides Community Contributions Developer Resources Grouper Website These topics are discussed in the "Grouper UI" training series. Grouper 2.2 and above
Application Servers G Session 11 - Sub-Topic 2 Using Enterprise JavaBeans. Dr. Jean-Claude Franchitti
 Application Servers G22.3033-011 Session 11 - Sub-Topic 2 Using Enterprise JavaBeans Dr. Jean-Claude Franchitti New York University Computer Science Department Courant Institute of Mathematical Sciences
Application Servers G22.3033-011 Session 11 - Sub-Topic 2 Using Enterprise JavaBeans Dr. Jean-Claude Franchitti New York University Computer Science Department Courant Institute of Mathematical Sciences
ExtraHop 7.3 ExtraHop Trace REST API Guide
 ExtraHop 7.3 ExtraHop Trace REST API Guide 2018 ExtraHop Networks, Inc. All rights reserved. This manual in whole or in part, may not be reproduced, translated, or reduced to any machinereadable form without
ExtraHop 7.3 ExtraHop Trace REST API Guide 2018 ExtraHop Networks, Inc. All rights reserved. This manual in whole or in part, may not be reproduced, translated, or reduced to any machinereadable form without
Using the vrealize Orchestrator Operations Client. vrealize Orchestrator 7.5
 Using the vrealize Orchestrator Operations Client vrealize Orchestrator 7.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Using the vrealize Orchestrator Operations Client vrealize Orchestrator 7.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
DOCUMENT MANAGEMENT. Sample 001 for Azure Market Place
 1 BPMS 2 Intranet 3 Document Management 4 Content Management 5 Online Commerce 6 Business Rules Tutorial DOCUMENT MANAGEMENT Sample 001 for Azure Market Place (March 29, 2016) This publication belongs
1 BPMS 2 Intranet 3 Document Management 4 Content Management 5 Online Commerce 6 Business Rules Tutorial DOCUMENT MANAGEMENT Sample 001 for Azure Market Place (March 29, 2016) This publication belongs
10/17/2011. Object Oriented Software Development. Types of interface. Interfaces example
 Object Oriented Software Development 5. Interfaces,,polymorphism p and inheritance Types of interface The word interface has more than one meaning in programming User interface The way in which the user
Object Oriented Software Development 5. Interfaces,,polymorphism p and inheritance Types of interface The word interface has more than one meaning in programming User interface The way in which the user
Quick Start: Permission requests and approvals
 Quick Start: Permission requests and approvals and approvals Microsoft Volume Licensing Field Center This guide shows field users the process for requesting access to the Volume Licensing Field Center
Quick Start: Permission requests and approvals and approvals Microsoft Volume Licensing Field Center This guide shows field users the process for requesting access to the Volume Licensing Field Center
Ohio Business Gateway Using the Gateway as a Service Provider: Requesting Service Area and Transaction Permissions
 Ohio Business Gateway Using the Gateway as a Service Provider: Requesting Service Area and Transaction Permissions Contents Contents... 1 Introduction... 2 User Roles and Permissions... 2 Requesting Service
Ohio Business Gateway Using the Gateway as a Service Provider: Requesting Service Area and Transaction Permissions Contents Contents... 1 Introduction... 2 User Roles and Permissions... 2 Requesting Service
Create and Manage Partner Portals
 Create and Manage Partner Portals Salesforce, Summer 18 @salesforcedocs Last updated: June 20, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of
Create and Manage Partner Portals Salesforce, Summer 18 @salesforcedocs Last updated: June 20, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of
USER MANUAL SATORI TEAM
 KANBAN USER MANUAL SATORI TEAM Table of Contents KanBan... 4 1. Introduction... 4 2. Roles and privileges... 6 3. Process flow... 6 4. Descriptions... 7 a) Creating the Board... 7 b) Creating the section...
KANBAN USER MANUAL SATORI TEAM Table of Contents KanBan... 4 1. Introduction... 4 2. Roles and privileges... 6 3. Process flow... 6 4. Descriptions... 7 a) Creating the Board... 7 b) Creating the section...
10265: Developing Data Access Solutions with Microsoft Visual Studio 2010 Duration: 5 Days Method: Instructor-Led
 10265: Developing Data Access Solutions with Microsoft Visual Studio 2010 Duration: 5 Days Method: Instructor-Led Course Description In this course, experienced developers who know the basics of data access
10265: Developing Data Access Solutions with Microsoft Visual Studio 2010 Duration: 5 Days Method: Instructor-Led Course Description In this course, experienced developers who know the basics of data access
Oracle Policy Automation The modern enterprise advice platform
 Oracle Policy Automation The modern enterprise advice platform Release features and benefits (November 2017) v1.01 Program agenda 1 2 3 Overview of Oracle Policy Automation New features in release For
Oracle Policy Automation The modern enterprise advice platform Release features and benefits (November 2017) v1.01 Program agenda 1 2 3 Overview of Oracle Policy Automation New features in release For
KwikTag v4.6.4 Release Notes
 KwikTag v4.6.4 Release Notes KwikTag v4.6.4 for Web Client - Release Notes a. Internet Explorer 7.0 b. Internet Explorer 8.0 c. Firefox 3.5+ Server Requirements a. KwikTag v4.6.4 New Features: Feature:
KwikTag v4.6.4 Release Notes KwikTag v4.6.4 for Web Client - Release Notes a. Internet Explorer 7.0 b. Internet Explorer 8.0 c. Firefox 3.5+ Server Requirements a. KwikTag v4.6.4 New Features: Feature:
Dan Williams Networking Services, Red Hat
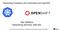 Networking Containers with Kubernetes and OpenShift Dan Williams Networking Services, Red Hat Kubernetes Components Web UI Pod apiserver etcd Container 1 Container 2 scheduler controller Command-line interface
Networking Containers with Kubernetes and OpenShift Dan Williams Networking Services, Red Hat Kubernetes Components Web UI Pod apiserver etcd Container 1 Container 2 scheduler controller Command-line interface
Managing Delegation. Table of Contents. Delegating a Proxy... 2 Receiving and Processing a Delegation Invitation... 16
 Managing Delegation Table of Contents Delegating a Proxy... 2 Receiving and Processing a Delegation Invitation... 16 Managing Delegation HR Direct Manager's Self Service provides a process to reassign
Managing Delegation Table of Contents Delegating a Proxy... 2 Receiving and Processing a Delegation Invitation... 16 Managing Delegation HR Direct Manager's Self Service provides a process to reassign
Configurations. Charles Macleod Wolfgang Kaiser
 Configurations Charles Macleod Wolfgang Kaiser Configurations Extensibility pattern introduced at 1.4 - All of the functionality of an Add-in plus: - Change the application title and icon - Change the
Configurations Charles Macleod Wolfgang Kaiser Configurations Extensibility pattern introduced at 1.4 - All of the functionality of an Add-in plus: - Change the application title and icon - Change the
Table of Contents Brainshark. All rights reserved.
 Table of Contents Administrator Reference Guide... 2 Introduction... 2 Topics... 2 Folders... 3 Manage Folders... 3 Edit Folder... 3 Edit Folder Properties... 3 Assign Folder Permissions (Viewer, Author,
Table of Contents Administrator Reference Guide... 2 Introduction... 2 Topics... 2 Folders... 3 Manage Folders... 3 Edit Folder... 3 Edit Folder Properties... 3 Assign Folder Permissions (Viewer, Author,
ArcGIS Pro SDK for.net Customize Pro to Streamline Workflows. Wolfgang Kaiser
 ArcGIS Pro SDK for.net Customize Pro to Streamline Workflows Wolfgang Kaiser Managed Configuration or Configurations Customize Pro to Streamline Workflows has been implemented with the Managed Configuration
ArcGIS Pro SDK for.net Customize Pro to Streamline Workflows Wolfgang Kaiser Managed Configuration or Configurations Customize Pro to Streamline Workflows has been implemented with the Managed Configuration
Edge Integration Guide Workday Transcript Outbound Integration
 Edge Integration Guide Workday Transcript Outbound Integration 1 TABLE OF CONTENTS Welcome To 3 Enablement 3 Prerequisite Setup in Workday 4 Setup Instructions in Cornerstone 8 Workflow 13 Field Mapping
Edge Integration Guide Workday Transcript Outbound Integration 1 TABLE OF CONTENTS Welcome To 3 Enablement 3 Prerequisite Setup in Workday 4 Setup Instructions in Cornerstone 8 Workflow 13 Field Mapping
Secret Server Web Services API Guide
 Table of Contents Overview... 1 Accessing Web Services... 1 Concepts... 1 Token... 1 s... 2 Windows Authentication... 2 Common... 2 Sample Code... 3 Web Service Methods... 3 AddDependency... 3 AddNewSecret...
Table of Contents Overview... 1 Accessing Web Services... 1 Concepts... 1 Token... 1 s... 2 Windows Authentication... 2 Common... 2 Sample Code... 3 Web Service Methods... 3 AddDependency... 3 AddNewSecret...
How to integrate dox42 with SharePoint Lists and Libraries
 How to integrate dox42 with SharePoint Lists and Libraries Johannes Linder Documentation Summary In this Document you will be given an overview how to integrate dox42 into your Microsoft SharePoint lists
How to integrate dox42 with SharePoint Lists and Libraries Johannes Linder Documentation Summary In this Document you will be given an overview how to integrate dox42 into your Microsoft SharePoint lists
CSE 565 Computer Security Fall 2018
 CSE 565 Computer Security Fall 2018 Lecture 12: Database Security Department of Computer Science and Engineering University at Buffalo 1 Review of Access Control Types We previously studied four types
CSE 565 Computer Security Fall 2018 Lecture 12: Database Security Department of Computer Science and Engineering University at Buffalo 1 Review of Access Control Types We previously studied four types
Contents. Managing Places...3. Contents 2
 Managing Places Contents 2 Contents Managing Places...3 Creating a Site Structure...3 Managing Spaces...4 Designing Space Hierarchies... 5 Changing the Name of the Root Space...5 Space Creation Options...
Managing Places Contents 2 Contents Managing Places...3 Creating a Site Structure...3 Managing Spaces...4 Designing Space Hierarchies... 5 Changing the Name of the Root Space...5 Space Creation Options...
Introduction. Overview of HCM. HCM Dashboard CHAPTER
 CHAPTER 1 This chapter describes the Hosted Collaboration Mediation (HCM) software. It includes: Overview of HCM, page 1-1 Terminology Used in HCM, page 1-2 HCM Dashboard Architecture, page 1-3 Starting
CHAPTER 1 This chapter describes the Hosted Collaboration Mediation (HCM) software. It includes: Overview of HCM, page 1-1 Terminology Used in HCM, page 1-2 HCM Dashboard Architecture, page 1-3 Starting
Secret Server SOAP Web Services API Guide
 Secret Server SOAP Web Services API Guide Table of Contents Overview... 1 Accessing Web Services... 1 Concepts... 1 Token... 1 s... 2 Windows Authentication... 2 Common... 2 Sample Code... 3 Web Service
Secret Server SOAP Web Services API Guide Table of Contents Overview... 1 Accessing Web Services... 1 Concepts... 1 Token... 1 s... 2 Windows Authentication... 2 Common... 2 Sample Code... 3 Web Service
VMware AirWatch Google Sync Integration Guide Securing Your Infrastructure
 VMware AirWatch Google Sync Integration Guide Securing Your Email Infrastructure AirWatch v9.2 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
VMware AirWatch Google Sync Integration Guide Securing Your Email Infrastructure AirWatch v9.2 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
Written by John Bell for CS 342, Spring 2018
 Advanced OO Concepts Written by John Bell for CS 342, Spring 2018 Based on chapter 3 of The Object-Oriented Thought Process by Matt Weisfeld, with additional material from other sources. Constructors Constructors
Advanced OO Concepts Written by John Bell for CS 342, Spring 2018 Based on chapter 3 of The Object-Oriented Thought Process by Matt Weisfeld, with additional material from other sources. Constructors Constructors
Policy Based Device Access Security Position Paper to Device Access Policy Working Group
 1 (8) Policy Based Device Access Security Position Paper to Device Access Policy Working Group 2 (8) 1. INTRODUCTION Nokia has implemented a policy-based device access security model for its Web runtime
1 (8) Policy Based Device Access Security Position Paper to Device Access Policy Working Group 2 (8) 1. INTRODUCTION Nokia has implemented a policy-based device access security model for its Web runtime
Defect Details. Defect Id: Error when disabling slide show in Site admin: Invalid numeric input for Slide show interval (ms)
 214 Error when disabling slide show in Site admin: Invalid numeric input for Slide show interval (ms) 6/4/2009 Medium Impact 6/4/2009 2.3.3442 1 hrs Medium The following error occurs when attempting to
214 Error when disabling slide show in Site admin: Invalid numeric input for Slide show interval (ms) 6/4/2009 Medium Impact 6/4/2009 2.3.3442 1 hrs Medium The following error occurs when attempting to
12/05/2017. Geneva ServiceNow Custom Application Development
 12/05/2017 Contents...3 Applications...3 Creating applications... 3 Parts of an application...22 Contextual development environment... 48 Application management... 56 Studio... 64 Service Creator...87
12/05/2017 Contents...3 Applications...3 Creating applications... 3 Parts of an application...22 Contextual development environment... 48 Application management... 56 Studio... 64 Service Creator...87
Defense Health Agency Protected Health Information Management Tool (PHIMT)
 Defense Health Agency Protected Health Information Management Tool (PHIMT) Training Reference: Regular User Guide Version 3.0 March 2011 Any data herein that may be construed as personal information is
Defense Health Agency Protected Health Information Management Tool (PHIMT) Training Reference: Regular User Guide Version 3.0 March 2011 Any data herein that may be construed as personal information is
Scope. General. Permissions and Roles. Roles and Permission Groups based security KB4006 1
 Roles and Permission Groups based security KB4006 1 Scope This document describes the OpenLM Roles and Permission Groups feature, and serves as a reference guide to system administrators who seek intricate
Roles and Permission Groups based security KB4006 1 Scope This document describes the OpenLM Roles and Permission Groups feature, and serves as a reference guide to system administrators who seek intricate
AWS Service Catalog. User Guide
 AWS Service Catalog User Guide AWS Service Catalog: User Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in
AWS Service Catalog User Guide AWS Service Catalog: User Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in
Perceptive Interact for Salesforce Enterprise
 Perceptive Interact for Salesforce Enterprise Installation and Setup Guide Version: 3.x.x Written by: Product Knowledge, R&D Date: April 2018 Copyright 2015-2018 Hyland Software, Inc. and its affiliates.
Perceptive Interact for Salesforce Enterprise Installation and Setup Guide Version: 3.x.x Written by: Product Knowledge, R&D Date: April 2018 Copyright 2015-2018 Hyland Software, Inc. and its affiliates.
About Working with Reports using Actuate iportal
 About Working with Reports using Actuate iportal Working with Reports using Actuate iportal includes the following chapters: About Working with Reports using Actuate iportal. This chapter provides an overview
About Working with Reports using Actuate iportal Working with Reports using Actuate iportal includes the following chapters: About Working with Reports using Actuate iportal. This chapter provides an overview
COURSE DETAILS: CORE AND ADVANCE JAVA Core Java
 COURSE DETAILS: CORE AND ADVANCE JAVA Core Java 1. Object Oriented Concept Object Oriented Programming & its Concepts Classes and Objects Aggregation and Composition Static and Dynamic Binding Abstract
COURSE DETAILS: CORE AND ADVANCE JAVA Core Java 1. Object Oriented Concept Object Oriented Programming & its Concepts Classes and Objects Aggregation and Composition Static and Dynamic Binding Abstract
VMware AirWatch Google Sync Integration Guide Securing Your Infrastructure
 VMware AirWatch Google Sync Integration Guide Securing Your Email Infrastructure Workspace ONE UEM v9.5 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard
VMware AirWatch Google Sync Integration Guide Securing Your Email Infrastructure Workspace ONE UEM v9.5 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard
EF6 - Version: 1. Entity Framework 6
 EF6 - Version: 1 Entity Framework 6 Entity Framework 6 EF6 - Version: 1 4 days Course Description: Entity Framework is the new ORM and data access technology introduced by Microsoft. Entity framework provides
EF6 - Version: 1 Entity Framework 6 Entity Framework 6 EF6 - Version: 1 4 days Course Description: Entity Framework is the new ORM and data access technology introduced by Microsoft. Entity framework provides
Customizing the vsphere Client VMware vsphere Web Services SDK 4.1
 Technical Note VMware vsphere Web Services SDK 4.1 The ExtensionManager service interface supports centralized management of plug ins (sometimes called extensions) for vcenter Server systems. Plug ins
Technical Note VMware vsphere Web Services SDK 4.1 The ExtensionManager service interface supports centralized management of plug ins (sometimes called extensions) for vcenter Server systems. Plug ins
SharePoint Online for Site Administrators
 SharePoint Online for Site Administrators Contents SharePoint Online for Site Administrators... 1 Access Your Office 365 SharePoint Website... 2 Make a New Subsite... 4 Permissions... 5 Edit the members
SharePoint Online for Site Administrators Contents SharePoint Online for Site Administrators... 1 Access Your Office 365 SharePoint Website... 2 Make a New Subsite... 4 Permissions... 5 Edit the members
DESIGN PATTERN - INTERVIEW QUESTIONS
 DESIGN PATTERN - INTERVIEW QUESTIONS http://www.tutorialspoint.com/design_pattern/design_pattern_interview_questions.htm Copyright tutorialspoint.com Dear readers, these Design Pattern Interview Questions
DESIGN PATTERN - INTERVIEW QUESTIONS http://www.tutorialspoint.com/design_pattern/design_pattern_interview_questions.htm Copyright tutorialspoint.com Dear readers, these Design Pattern Interview Questions
CIAM: Need for Identity Governance & Assurance. Yash Prakash VP of Products
 CIAM: Need for Identity Governance & Assurance Yash Prakash VP of Products Key Tenets of CIAM Solution Empower consumers, CSRs & administrators Scale to millions of entities, cloud based service Security
CIAM: Need for Identity Governance & Assurance Yash Prakash VP of Products Key Tenets of CIAM Solution Empower consumers, CSRs & administrators Scale to millions of entities, cloud based service Security
Setup Skype for Business & Salesforce (beta) Integration guide
 Setup Skype for Business & Salesforce (beta) Integration guide Overview: Skype for Business Online & Salesforce (Beta) integration enable new functionality for Salesforce users. This admin guide covers,
Setup Skype for Business & Salesforce (beta) Integration guide Overview: Skype for Business Online & Salesforce (Beta) integration enable new functionality for Salesforce users. This admin guide covers,
Perceptive Interact for Salesforce Enterprise
 Perceptive Interact for Salesforce Enterprise Installation and Setup Guide Version: 3.x.x Written by: Documentation Team, R&D Date: January 2019 Copyright 2015-2019 Hyland Software, Inc. and its affiliates.
Perceptive Interact for Salesforce Enterprise Installation and Setup Guide Version: 3.x.x Written by: Documentation Team, R&D Date: January 2019 Copyright 2015-2019 Hyland Software, Inc. and its affiliates.
Developing Mobile Apps with Xamarin and Azure
 Developing Mobile Apps with Xamarin and Azure Xamarin, a recent addition to Microsoft s list of products, allows developers to build apps using a single code base with close-to-native appearance and performance.
Developing Mobile Apps with Xamarin and Azure Xamarin, a recent addition to Microsoft s list of products, allows developers to build apps using a single code base with close-to-native appearance and performance.
Oracle Taleo Cloud for Midsize (Taleo Business Edition) Release 17B2. What s New
 Oracle Taleo Cloud for Midsize (Taleo Business Edition) Release 17B2 What s New TABLE OF CONTENTS REVISION HISTORY... 3 OVERVIEW... 4 RELEASE FEATURE SUMMARY... 4 TALENT CENTER ENHANCEMENTS... 5 My Offer
Oracle Taleo Cloud for Midsize (Taleo Business Edition) Release 17B2 What s New TABLE OF CONTENTS REVISION HISTORY... 3 OVERVIEW... 4 RELEASE FEATURE SUMMARY... 4 TALENT CENTER ENHANCEMENTS... 5 My Offer
Workspace Desktop Edition Deployment Guide. Installing The Workspace SIP Endpoint
 Workspace Desktop Edition Deployment Guide Installing The Workspace SIP Endpoint 11/20/2017 Installing The Workspace SIP Endpoint [Modified: 8.5.109.16, 8.5.114.08] The Workspace SIP Endpoint is an optional
Workspace Desktop Edition Deployment Guide Installing The Workspace SIP Endpoint 11/20/2017 Installing The Workspace SIP Endpoint [Modified: 8.5.109.16, 8.5.114.08] The Workspace SIP Endpoint is an optional
Project Manager User Manual
 Project Manager User Manual Overview Welcome to your new Project Manager application. The Project Managaer is implemented as a web site that interfaces to an SQL database where all of the project and time
Project Manager User Manual Overview Welcome to your new Project Manager application. The Project Managaer is implemented as a web site that interfaces to an SQL database where all of the project and time
Secure Role-Based Access Control on Encrypted Data in Cloud Storage using ARM
 Secure Role-Based Access Control on Encrypted Data in Cloud Storage using ARM Rohini Vidhate, V. D. Shinde Abstract With the rapid developments occurring in cloud computing and services, there has been
Secure Role-Based Access Control on Encrypted Data in Cloud Storage using ARM Rohini Vidhate, V. D. Shinde Abstract With the rapid developments occurring in cloud computing and services, there has been
EPAF 101. Basic Concepts
 EPAF 101 Basic Concepts Wayne State University November, 2007 Table of Contents Welcome to EPAF... 1 Advantages of EPAF... 1 Phase 1, Five Categories of EPAFs... 1 EPAF Roles...2 Key Terminology...3 Originator
EPAF 101 Basic Concepts Wayne State University November, 2007 Table of Contents Welcome to EPAF... 1 Advantages of EPAF... 1 Phase 1, Five Categories of EPAFs... 1 EPAF Roles...2 Key Terminology...3 Originator
1.Basic Configurations
 QUICK START GUIDE ServiceDesk Plus On-Demand is an online help desk software built on the ITIL framework with integrated asset management. It is available in 15 different languages and in three editions
QUICK START GUIDE ServiceDesk Plus On-Demand is an online help desk software built on the ITIL framework with integrated asset management. It is available in 15 different languages and in three editions
Portlet Standard JSR 168 / JSR 286
 Portlet Standard JSR 168 / JSR 286 Version 1.0 Martin Weiss Martin Weiss Informatik AG Agenda JSR 168 2 JSR 168 What Is Missing? 22 JSR 286 25 Portlet Events 28 Public Render Parameters 32 Events vs. Public
Portlet Standard JSR 168 / JSR 286 Version 1.0 Martin Weiss Martin Weiss Informatik AG Agenda JSR 168 2 JSR 168 What Is Missing? 22 JSR 286 25 Portlet Events 28 Public Render Parameters 32 Events vs. Public
maxecurity Product Suite
 maxecurity Product Suite Domain Administrator s Manual Firmware v2.2 ii Table of Contents BASICS... 1 Understanding how maxecurity products work in your company... 1 Getting started as a Domain Administrator...
maxecurity Product Suite Domain Administrator s Manual Firmware v2.2 ii Table of Contents BASICS... 1 Understanding how maxecurity products work in your company... 1 Getting started as a Domain Administrator...
Helping Administrators Prepare for Analytics 10
 Helping Administrators Prepare for Analytics 10 There are a few important configuration updates that Webtrends administrators can take in On Demand prior to the Analytics 10 release in order to prepare
Helping Administrators Prepare for Analytics 10 There are a few important configuration updates that Webtrends administrators can take in On Demand prior to the Analytics 10 release in order to prepare
Semantic and Annotation Remapping in FX Composer
 Semantic and Annotation Remapping in FX Composer April 2008 Table of Contents Semantic and Annotation Remapping... 4 Syntax... 4 List of Operators... 6 MatrixMultiply... 6 MatrixAdd...7 MatrixSubstract...
Semantic and Annotation Remapping in FX Composer April 2008 Table of Contents Semantic and Annotation Remapping... 4 Syntax... 4 List of Operators... 6 MatrixMultiply... 6 MatrixAdd...7 MatrixSubstract...
ArcGIS Pro SDK for.net Beginning Pro Customization. Charles Macleod
 ArcGIS Pro SDK for.net Beginning Pro Customization Charles Macleod Session Overview Extensibility patterns - Add-ins - Configurations Primary API Patterns - QueuedTask and Asynchronous Programming - async
ArcGIS Pro SDK for.net Beginning Pro Customization Charles Macleod Session Overview Extensibility patterns - Add-ins - Configurations Primary API Patterns - QueuedTask and Asynchronous Programming - async
The Definitive Guide to Office 365 External Sharing. An ebook by Sharegate
 The Definitive Guide to Office 365 External Sharing An ebook by Sharegate The Definitive Guide to External Sharing In any organization, whether large or small, sharing content with external users is an
The Definitive Guide to Office 365 External Sharing An ebook by Sharegate The Definitive Guide to External Sharing In any organization, whether large or small, sharing content with external users is an
Configuring RBAC Using Admin UI
 CHAPTER 13 This chapter describes the Security feature of Prime Cable Provisioning. Use this feature to configure and manage various levels of security. For conceptual information about the RBAC feature,
CHAPTER 13 This chapter describes the Security feature of Prime Cable Provisioning. Use this feature to configure and manage various levels of security. For conceptual information about the RBAC feature,
Null Service and Loopback Service Drivers Implementation Guide NetIQ Identity Manager. February 2018
 Null Service and Loopback Service Drivers Implementation Guide NetIQ Identity Manager February 2018 Legal Notice For information about NetIQ legal notices, disclaimers, warranties, export and other use
Null Service and Loopback Service Drivers Implementation Guide NetIQ Identity Manager February 2018 Legal Notice For information about NetIQ legal notices, disclaimers, warranties, export and other use
Policy Manager in Compliance 360 Version 2018
 Policy Manager in Compliance 360 Version 2018 Policy Manager Overview 3 Create a Policy 4 Relate a Policy to Other Policies, Departments, and Incidents 8 Edit a Policy 10 Edit a Policy by Using the Edit
Policy Manager in Compliance 360 Version 2018 Policy Manager Overview 3 Create a Policy 4 Relate a Policy to Other Policies, Departments, and Incidents 8 Edit a Policy 10 Edit a Policy by Using the Edit
Mobile Speech Recognizer
 Mobile Speech Recognizer by Piotr Zmudzinski ptr.zmudzinski@gmail.com!1 About Wouldn't your prefer to let your users speak instead of making them type? This plugin uses OS components for speech recognition
Mobile Speech Recognizer by Piotr Zmudzinski ptr.zmudzinski@gmail.com!1 About Wouldn't your prefer to let your users speak instead of making them type? This plugin uses OS components for speech recognition
Administration Guide
 Administration Guide This guide will cover how to customize and lock down the SCOM 2012 Maintenance Mode Scheduler for your end users. Table of Contents Customize Look and Feel... 2 Enable Auditing of
Administration Guide This guide will cover how to customize and lock down the SCOM 2012 Maintenance Mode Scheduler for your end users. Table of Contents Customize Look and Feel... 2 Enable Auditing of
Manage Administrators and Admin Access Policies
 Manage Administrators and Admin Access Policies Role-Based Access Control, page 1 Cisco ISE Administrators, page 1 Cisco ISE Administrator Groups, page 3 Administrative Access to Cisco ISE, page 11 Role-Based
Manage Administrators and Admin Access Policies Role-Based Access Control, page 1 Cisco ISE Administrators, page 1 Cisco ISE Administrator Groups, page 3 Administrative Access to Cisco ISE, page 11 Role-Based
MarkLogic Server. Security Guide. MarkLogic 9 May, Copyright 2017 MarkLogic Corporation. All rights reserved.
 Security Guide 1 MarkLogic 9 May, 2017 Last Revised: 9.0-3, September, 2017 Copyright 2017 MarkLogic Corporation. All rights reserved. Table of Contents Table of Contents Security Guide 1.0 Introduction
Security Guide 1 MarkLogic 9 May, 2017 Last Revised: 9.0-3, September, 2017 Copyright 2017 MarkLogic Corporation. All rights reserved. Table of Contents Table of Contents Security Guide 1.0 Introduction
USER MANUAL (VERSION )
 NEO SECURITY VIEWER USER MANUAL (VERSION 1.0.2.0) Contents I. What does Neo Security Viewer do?... 2 II. How to obtain the solution... 2 III. How to install the solution... 2 IV. How to open the application...
NEO SECURITY VIEWER USER MANUAL (VERSION 1.0.2.0) Contents I. What does Neo Security Viewer do?... 2 II. How to obtain the solution... 2 III. How to install the solution... 2 IV. How to open the application...
Google Sync Integration Guide. VMware Workspace ONE UEM 1902
 Google Sync Integration Guide VMware Workspace ONE UEM 1902 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation,
Google Sync Integration Guide VMware Workspace ONE UEM 1902 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation,
Zephyr Cloud for HipChat
 June 25 Zephyr Cloud for HipChat Z e p h y r, 7 7 0 7 G a t e w a y B l v d S t e 1 0 0, N e w a r k, C A 9 4 5 6 0, U S A 1 - Overview How this guide will help Zephyr Cloud for HipChat guide will guide
June 25 Zephyr Cloud for HipChat Z e p h y r, 7 7 0 7 G a t e w a y B l v d S t e 1 0 0, N e w a r k, C A 9 4 5 6 0, U S A 1 - Overview How this guide will help Zephyr Cloud for HipChat guide will guide
ControlPoint. Managing ControlPoint Users, Permissions, and Menus. February 05,
 Managing Users, Permissions, and Menus February 05, 2018 www.metalogix.com info@metalogix.com 202.609.9100 Copyright International GmbH., 2008-2018 All rights reserved. No part or section of the contents
Managing Users, Permissions, and Menus February 05, 2018 www.metalogix.com info@metalogix.com 202.609.9100 Copyright International GmbH., 2008-2018 All rights reserved. No part or section of the contents
Let your customers login to your store after pre-approval
 Customer Approve & Disapprove Let your customers login to your store after pre-approval Extension Specification Document Version: 2.0.0 Magento 2 Extension URL: https://www.extensionhut.com/customer-approve-disapprove-for-magento-2.html
Customer Approve & Disapprove Let your customers login to your store after pre-approval Extension Specification Document Version: 2.0.0 Magento 2 Extension URL: https://www.extensionhut.com/customer-approve-disapprove-for-magento-2.html
Foundations and Concepts. 20 September 2018 vrealize Automation 7.5
 Foundations and Concepts 20 September 2018 vrealize Automation 7.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about
Foundations and Concepts 20 September 2018 vrealize Automation 7.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about
Magento Extension User Guide REVIEW NEWSLETTER for Magento 2
 Magento Extension User Guide REVIEW NEWSLETTER for Magento 2 Table of contents 1. Key Features 2. Configuration 3. Email Template 4. Leaving a Review 5. Create Reviews 6. Approving a Review 7. Troubleshoots
Magento Extension User Guide REVIEW NEWSLETTER for Magento 2 Table of contents 1. Key Features 2. Configuration 3. Email Template 4. Leaving a Review 5. Create Reviews 6. Approving a Review 7. Troubleshoots
Enterprise Recruitment Marketing Platform. User Permissions and Settings Image Maps
 Enterprise Recruitment Marketing Platform User Permissions and Settings Image Maps Date: November 2017 Enterprise Table of Contents Core Navigation Maps... 3 Job Marketing Maps... 9 Event Campaign Maps...19
Enterprise Recruitment Marketing Platform User Permissions and Settings Image Maps Date: November 2017 Enterprise Table of Contents Core Navigation Maps... 3 Job Marketing Maps... 9 Event Campaign Maps...19
Application Security Introduction. Tara Gu IBM Product Security Incident Response Team
 Application Security Introduction Tara Gu IBM Product Security Incident Response Team About Me - Tara Gu - tara.weiqing@gmail.com - Duke B.S.E Biomedical Engineering - Duke M.Eng Computer Engineering -
Application Security Introduction Tara Gu IBM Product Security Incident Response Team About Me - Tara Gu - tara.weiqing@gmail.com - Duke B.S.E Biomedical Engineering - Duke M.Eng Computer Engineering -
Globalization TECHNICAL NOTE. Purpose. Product version: Document version: 1.1. Document creation date:
 Globalization Product version: 4.60 Document version: 1.1 Document creation date: 04-05-2006 Purpose EPiServer has supported the creation of multilingual Web sites, with the multi-language functionality,
Globalization Product version: 4.60 Document version: 1.1 Document creation date: 04-05-2006 Purpose EPiServer has supported the creation of multilingual Web sites, with the multi-language functionality,
Teamcenter 11.1 Systems Engineering and Requirements Management
 SIEMENS Teamcenter 11.1 Systems Engineering and Requirements Management Systems Architect/ Requirements Management Project Administrator's Manual REQ00002 U REQ00002 U Project Administrator's Manual 3
SIEMENS Teamcenter 11.1 Systems Engineering and Requirements Management Systems Architect/ Requirements Management Project Administrator's Manual REQ00002 U REQ00002 U Project Administrator's Manual 3
API Gateway Version December PassPort Interoperability Guide
 API Gateway Version 7.5.3 20 December 2018 PassPort Interoperability Guide Copyright 2018 Axway All rights reserved. This documentation describes the following Axway software: Axway API Gateway 7.5.3 No
API Gateway Version 7.5.3 20 December 2018 PassPort Interoperability Guide Copyright 2018 Axway All rights reserved. This documentation describes the following Axway software: Axway API Gateway 7.5.3 No
Repstor custodian. Configuration Guide
 Repstor custodian Configuration Guide Document Version 1.5 For custodian version 1.36 March 2016 Contents 1. INTRODUCTION TO REPSTOR CUSTODIAN 3 2. INSTALLATION 3 3. REPSTOR CUSTODIAN OVERVIEW 4 4. KEY
Repstor custodian Configuration Guide Document Version 1.5 For custodian version 1.36 March 2016 Contents 1. INTRODUCTION TO REPSTOR CUSTODIAN 3 2. INSTALLATION 3 3. REPSTOR CUSTODIAN OVERVIEW 4 4. KEY
12/05/2017. Customer Service Management
 12/05/2017 Contents...3 Get started with... 3 Activate Customer Service... 5 Set up associated entities... 6 Set up communication channels... 16 Track and analyze Customer Service case data... 40 Create
12/05/2017 Contents...3 Get started with... 3 Activate Customer Service... 5 Set up associated entities... 6 Set up communication channels... 16 Track and analyze Customer Service case data... 40 Create
LightUp Studio. Evaluation Guide CONTENTS. Introduction Creating Integrated App Launcher Tiles and Help Desk Links to the Training Portal...
 LightUp Studio Evaluation Guide CONTENTS Introduction... 2 Creating Integrated App Launcher Tiles and Help Desk Links to the Training Portal... 3 Controlling the Visibility of Libraries in the Training
LightUp Studio Evaluation Guide CONTENTS Introduction... 2 Creating Integrated App Launcher Tiles and Help Desk Links to the Training Portal... 3 Controlling the Visibility of Libraries in the Training
The aim of this guide is to explain in detail the user operationating point of view of "EA Connector for Jira ".
 User Guide Contents Contents Introduction Get Started "EA Connector for Jira " Configuration Establishing a connection with JIRA: Elements mapping between Enterprise Architect y JIRA: Changing Language
User Guide Contents Contents Introduction Get Started "EA Connector for Jira " Configuration Establishing a connection with JIRA: Elements mapping between Enterprise Architect y JIRA: Changing Language
CA IdentityMinder. Glossary
 CA IdentityMinder Glossary 12.6.3 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation ) is for your informational
CA IdentityMinder Glossary 12.6.3 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation ) is for your informational
How can you integrate Agiloft with Single Sign-On providers? What is Two-Factor Authentication and how is it used with Agiloft?
 Unit 20: Security Questions Covered What forms of security are offered by Agiloft? How can you integrate Agiloft with Single Sign-On providers? What is Two-Factor Authentication and how is it used with
Unit 20: Security Questions Covered What forms of security are offered by Agiloft? How can you integrate Agiloft with Single Sign-On providers? What is Two-Factor Authentication and how is it used with
Administering Jive Mobile Apps for ios and Android
 Administering Jive Mobile Apps for ios and Android TOC 2 Contents Administering Jive Mobile Apps...3 Configuring Jive for Android and ios...3 Custom App Wrapping for ios...3 Authentication with Mobile
Administering Jive Mobile Apps for ios and Android TOC 2 Contents Administering Jive Mobile Apps...3 Configuring Jive for Android and ios...3 Custom App Wrapping for ios...3 Authentication with Mobile
Global Search v 6.1 for Microsoft Dynamics CRM Online (2013 & 2015 versions)
 Global Search v 6.1 for Microsoft Dynamics CRM Online (2013 & 2015 versions) User Manual Akvelon, Inc. 2015, All rights reserved. 1 Overview... 3 What s New in Global Search Versions for CRM Online...
Global Search v 6.1 for Microsoft Dynamics CRM Online (2013 & 2015 versions) User Manual Akvelon, Inc. 2015, All rights reserved. 1 Overview... 3 What s New in Global Search Versions for CRM Online...
Security Administrator (SA) Training
 Security Administrator (SA) Training Training Topics Introduction of the Security Administrator Adding and Maintaining Users Assigning Roles and Contact Types Unlocking Accounts and Changing Passwords
Security Administrator (SA) Training Training Topics Introduction of the Security Administrator Adding and Maintaining Users Assigning Roles and Contact Types Unlocking Accounts and Changing Passwords
Defense Health Agency Protected Health Information Management Tool (PHIMT)
 Defense Health Agency Protected Health Information Management Tool (PHIMT) Training Reference: Privacy Specialist User Guide Version 3.0 March 2011 Any data herein that may be construed as personal information
Defense Health Agency Protected Health Information Management Tool (PHIMT) Training Reference: Privacy Specialist User Guide Version 3.0 March 2011 Any data herein that may be construed as personal information
Using AD360 as a reverse proxy server
 Using AD360 as a reverse proxy server www.manageengine.com/active-directory-360/ Table of Contents Document summary 1 What is a reverse proxy? 1 Configuring AD360 as a reverse proxy 2 Enabling a context-based
Using AD360 as a reverse proxy server www.manageengine.com/active-directory-360/ Table of Contents Document summary 1 What is a reverse proxy? 1 Configuring AD360 as a reverse proxy 2 Enabling a context-based
User Permissions Overview
 User Permissions Overview INTRODUCTION The Florence ebinder Suite User Roles and Permissions module allows you to customize and fine-tune the privileges that members of your study team have for your research
User Permissions Overview INTRODUCTION The Florence ebinder Suite User Roles and Permissions module allows you to customize and fine-tune the privileges that members of your study team have for your research
Lync is now Skype for Business see what's new
 Lync is now Skype for Business see what's new If you already use Skype to stay in touch with friends and family in your life away from work, you'll appreciate the power and simplicity of Skype for Business
Lync is now Skype for Business see what's new If you already use Skype to stay in touch with friends and family in your life away from work, you'll appreciate the power and simplicity of Skype for Business
