Docusnap X - Windows Firewall Exceptions. Configuring Windows Firewall Exceptions for Docusnap
|
|
|
- Jacob Walsh
- 5 years ago
- Views:
Transcription
1 Docusnap X - Windows Firewall Exceptions Configuring Windows Firewall Exceptions for Docusnap
2 TITLE Docusnap X - Windows Firewall Exceptions AUTHOR Docusnap Consulting DATE 12/18/2018 VERSION 1.2 valid from September 26, 2018 This document contains proprietary information and may not be reproduced in any form or parts whatsoever, nor may be used by or its contents divulged to third parties without written permission of itelio GmbH. All rights reserved. Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 2 of 18
3 CONTENTS INTRODUCTION 4 BASICS REQUIRED FIREWALL EXCEPTIONS 5 WINDOWS FIREWALL CONFIGURATION ACTIVE DIRECTORY MANAGEMENT CONSOLE (GPMC) STARTING GPMC CREATING A GROUP POLICY OBJECT EDITING A GROUP POLICY OBJECT ENABLING EXCEPTIONS FOR FILE AND PRINTER SHARES ENABLING A REMOTE ADMINISTRATION EXCEPTION 12 WINDOWS 10 - WINDOWS FIREWALL CONFIGURATION (LOCAL) DEFINING EXCEPTIONS 14 Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 3 of 18
4 Introductio For the inventory of Windows systems, Docusnap uses the standard Windows Management Instrumentation (WMI) interface. If the Windows Firewall is enabled on a Windows system, it may be impossible for Docusnap to scan the system. This document explains the necessary adjustments of firewall settings for Windows systems. The chapter named WINDOWS FIREWALL CONFIGURATION ACTIVE DIRECTORY describes how the required Windows Firewall exceptions can be configured by defining corporate group policies using the Active Directory. This is the method recommended by itelio. The chapter named WINDOWS 10 - WINDOWS FIREWALL CONFIGURATION (LOCAL) describes an example of how to configure local group policies for Windows 10. Adjusting the local group policies only makes sense in the context of workgroups or for testing purposes. Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 4 of 18
5 Basics To make sure that Windows systems with the firewall enabled can be scanned successfully by Docusnap, you need to check or configure two firewall exceptions. These settings can be set up and administered using group policies. To enable you to quickly check your environment, we will also describe how to manually configure your Windows firewall. 2.1 Required firewall exceptions The following is a brief description of the exceptions to be configured. File and Printer Sharing Allows you to share files and printers. For this purpose, the Windows Firewall opens UDP ports 137 and 138 as well as TCP ports 139 and 445. Once you enable these policy settings, the Windows Firewall opens these ports so that the Windows system can receive print jobs and access requests for shared files. Note: This setting lets inbound ICMP echo requests (messages sent by the Ping utility) pass through the Windows Firewall, even if the Windows Firewall: Allow ICMP Exceptions policy setting normally blocked them. Allow Remote Administration Exception Essentially corresponds to the Windows Management Instrumentation (WMI) Windows Firewall exception and enables remote administration of the Windows system using management programs such as Microsoft Management Console (MMC) and Windows Management Instrumentation (WMI). For this purpose, the Windows Firewall opens TCP ports 135 and 445. Services normally use these ports for RPC (Remote Procedure Call) and DCOM (Distributed Component Object Model) communication. Security notice We recommend that you distribute the setting by means of a group policy. This way, you can globally set allowed IP addresses or subnets for these exceptions. Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 5 of 18
6 Windows Firewall configuration Active Directory 3.1 Management console (GPMC) To configure the firewall for multiple computers, it is advisable to define the required settings by means of a group policy. The following example shows how to define a domain-wide setting using the Microsoft Group Policy Management Console (GPMC) tool. GPO settings can be made at the local (L), site (S), domain (D), and organizational unit (OU) levels. Subsequent settings always overwrite the previously defined values. The hierarchy is L, S, D, OU. If the Microsoft Group Policy Management Console has not been installed on your system, you can download it for free from Microsoft. The following example shows how to change the firewall settings for all systems in the domain. It is strongly recommended to previously test this measure in a test environment or to implement the settings only in a dedicated test OU (organizational unit) in the Active Directory. The remote server management tools including the GPMC can be downloaded from the Microsoft website for the Windows client operating systems. Windows server operating systems (2008 and higher) already include the GPMC, but it might be necessary to install it subsequently via the Server Manager. Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 6 of 18
7 3.2 Starting GPMC Open the Windows Run dialog (Windows key+r) and type gpmc.msc. Fig. 1 - Group Policy Management Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 7 of 18
8 3.3 Creating a Group Policy Object Right-click the desired domain or OU and select the Create a GPO in this domain, and Link it here option. Enter a descriptive name for the GPO. Fig. 2 - Create a GPO in this domain, and Link it here... option Fig. 3 - New GPO dialog 3.4 Editing a Group Policy Object Right-click the previously created group policy object to select it and select Edit. Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 8 of 18
9 Fig. 4 - Editing a group policy object Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 9 of 18
10 The Group Policy Management Editor window opens: Fig. 5 - Group Policy Management Editor window The group policies to be configured are located in the following path: Computer Configuration Policies Administrative Templates Network Network Connections Windows Firewall o Domain Profile Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 10 of 18
11 3.5 Enabling exceptions for file and printer shares In this example, enabling the firewall exception is restricted to the local subnet. Fig. 6 - Enabling an exception for file and printer shares and restricting its scope Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 11 of 18
12 3.6 Enabling a remote administration exception For this example, enabling the firewall exception is restricted to the local subnet. Fig. 7 - Enabling a remote administration exception and restricting its scope Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 12 of 18
13 Windows 10 - Windows Firewall configuration (local) The firewall configuration can be opened directly by entering the firewall.cpl command. Search Enter firewall.cpl Fig. 8 - Windows 10 - Search Enter firewall.cpl Alternatively, you can enter the command from a console window: Fig. 9 - Windows 10 - command prompt for firewall.cpl Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 13 of 18
14 4.1 Defining exceptions Click Allow an app or feature through Windows Firewall. Fig Windows 10 Windows-Firewall - Allow an app or feature through Windows Firewall option Fig Windows 10 Windows-Firewall: Allowed apps window Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 14 of 18
15 Click Change settings to edit the apps and features listed here. This is only possible if you have adequate rights. Windows 10 manages three different types of networks: Domain, Private, and Public. You need to define the firewall exceptions separately for each type. Define the following exceptions for the network types in use by setting the corresponding checkmarks in the Allowed apps and features list. File and Printer Sharing Windows Management Instrumentation (WMI) Click the OK button to apply the new settings. The firewall settings thus defined allow Docusnap to scan the computer. Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 15 of 18
16 LIST OF FIGURES FIG. 1 - GROUP POLICY MANAGEMENT... 7 FIG. 2 - CREATE A GPO IN THIS DOMAIN, AND LINK IT HERE... OPTION... 8 FIG. 3 - NEW GPO DIALOG... 8 FIG. 4 - EDITING A GROUP POLICY OBJECT... 9 FIG. 5 - GROUP POLICY MANAGEMENT EDITOR WINDOW...10 FIG. 6 - ENABLING AN EXCEPTION FOR FILE AND PRINTER SHARES AND RESTRICTING ITS SCOPE FIG. 7 - ENABLING A REMOTE ADMINISTRATION EXCEPTION AND RESTRICTING ITS SCOPE...12 FIG. 8 - WINDOWS 10 - SEARCH ENTER FIREWALL.CPL...13 FIG. 9 - WINDOWS 10 - COMMAND PROMPT FOR FIREWALL.CPL...13 FIG WINDOWS 10 WINDOWS-FIREWALL - ALLOW AN APP OR FEATURE THROUGH WINDOWS FIREWALL OPTION FIG WINDOWS 10 WINDOWS-FIREWALL: ALLOWED APPS WINDOW Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 16 of 18
17 VERSION HISTORY Date Description 01/03/2017 HowTo Creation 10/24/2018 Screenshots updated and modified content to Windows 10 Docusnap X - Windows Firewall Exceptions 2018 Docusnap All rights reserved Page 17 of 18
18 itelio GmbH -
Docusnap X - WMI Access Problems. Analysis and Troubleshooting
 Docusnap X - WMI Access Problems Analysis and Troubleshooting TITLE Docusnap X - WMI Access Problems AUTHOR Docusnap Consulting DATE 12/18/2018 VERSION 1.2 valid from September 26, 2018 This document contains
Docusnap X - WMI Access Problems Analysis and Troubleshooting TITLE Docusnap X - WMI Access Problems AUTHOR Docusnap Consulting DATE 12/18/2018 VERSION 1.2 valid from September 26, 2018 This document contains
Inventorying Microsoft Azure. Inventorying Microsoft Azure Information with Docusnap X
 Inventorying Microsoft Azure Inventorying Microsoft Azure Information with Docusnap X TITLE Inventorying Microsoft Azure AUTHOR Docusnap Consulting DATE 2/7/2018 VERSION 1.0 valid from January 25, 2018
Inventorying Microsoft Azure Inventorying Microsoft Azure Information with Docusnap X TITLE Inventorying Microsoft Azure AUTHOR Docusnap Consulting DATE 2/7/2018 VERSION 1.0 valid from January 25, 2018
Docusnap X - Docusnap Script Linux. Script-based Inventory for Linux
 Docusnap X - Docusnap Script Linux Script-based Inventory for Linux TITLE Docusnap X - Docusnap Script Linux AUTHOR Docusnap Consulting DATE 12/18/2018 VERSION 1.1 valid from 26.09.2018 This document contains
Docusnap X - Docusnap Script Linux Script-based Inventory for Linux TITLE Docusnap X - Docusnap Script Linux AUTHOR Docusnap Consulting DATE 12/18/2018 VERSION 1.1 valid from 26.09.2018 This document contains
Docusnap X Installing and Configuring. Installing and Configuring Docusnap X
 Docusnap X Installing and Configuring Installing and Configuring Docusnap X TITLE Docusnap X Installing and Configuring AUTHOR Docusnap Consulting DATE 12/18/2018 VERSION 1.4 valid as of September 26,
Docusnap X Installing and Configuring Installing and Configuring Docusnap X TITLE Docusnap X Installing and Configuring AUTHOR Docusnap Consulting DATE 12/18/2018 VERSION 1.4 valid as of September 26,
Docusnap X User Management. Managing User Access to Docusnap
 Docusnap X User Management Managing User Access to Docusnap TITLE Docusnap X User Management AUTHOR Docusnap Consulting DATE 12/18/2018 VERSION 1.1 valid from September 26, 2018 This document contains
Docusnap X User Management Managing User Access to Docusnap TITLE Docusnap X User Management AUTHOR Docusnap Consulting DATE 12/18/2018 VERSION 1.1 valid from September 26, 2018 This document contains
Docusnap X Docusnap Web Version 2.0. Installing and Customizing Docusnap Web
 Docusnap X Docusnap Web Version 2.0 Installing and Customizing Docusnap Web TITLE Docusnap X Docusnap Web Version 2.0 AUTHOR Docusnap Consulting DATE June 12, 2018 HOW-TO VERSION 2.0 valid as of June 12,
Docusnap X Docusnap Web Version 2.0 Installing and Customizing Docusnap Web TITLE Docusnap X Docusnap Web Version 2.0 AUTHOR Docusnap Consulting DATE June 12, 2018 HOW-TO VERSION 2.0 valid as of June 12,
Other Assets. Creation and Add-on of other Assets
 Other Assets Creation and Add-on of other Assets TITLE Other Assets AUTHOR Docusnap Consulting DATE 7/12/2017 This document contains proprietary information and may not be reproduced in any form or parts
Other Assets Creation and Add-on of other Assets TITLE Other Assets AUTHOR Docusnap Consulting DATE 7/12/2017 This document contains proprietary information and may not be reproduced in any form or parts
Installation Guide. . All right reserved. For more information about Specops Deploy and other Specops products, visit
 . All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
. All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
In this lab you will explore the Windows Vista Firewall and configure some advanced settings.
 16.3.2 Optional Lab: Configure Windows Vista Firewall Print and complete this lab. In this lab you will explore the Windows Vista Firewall and configure some advanced settings. Recommended Equipment Two
16.3.2 Optional Lab: Configure Windows Vista Firewall Print and complete this lab. In this lab you will explore the Windows Vista Firewall and configure some advanced settings. Recommended Equipment Two
Lab - Configure the Firewall in Windows 7 and Vista
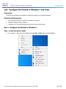 Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected on a network Windows installed
Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected on a network Windows installed
Lab - Configure the Firewall in Windows 8
 Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected over the network Windows 8 installed
Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected over the network Windows 8 installed
Monitoring Windows Systems with WMI
 Monitoring Windows Systems with WMI ScienceLogic version 8.8.1 Table of Contents Introduction 4 Monitoring Windows Devices in the ScienceLogic Platform 5 What is SNMP? 5 What is WMI? 5 PowerPacks 5 Configuring
Monitoring Windows Systems with WMI ScienceLogic version 8.8.1 Table of Contents Introduction 4 Monitoring Windows Devices in the ScienceLogic Platform 5 What is SNMP? 5 What is WMI? 5 PowerPacks 5 Configuring
Docusnap X. Installing and Configuring Docusnap X
 Docusnap X Installing and Configuring Docusnap X TITLE Docusnap X AUTHOR Docusnap Consulting DATE 7/12/2017 VERSION 1.2 valid as of September 27, 2016 The reproduction and distribution of this document
Docusnap X Installing and Configuring Docusnap X TITLE Docusnap X AUTHOR Docusnap Consulting DATE 7/12/2017 VERSION 1.2 valid as of September 27, 2016 The reproduction and distribution of this document
Windows 7 Professional 64 bit Configuration for MassLynx Security
 Windows 7 Professional 64 bit Configuration for MassLynx Security 1. Purpose This document outlines the procedure to configure Microsoft Windows 7 Professional 64 bit operating system in order for installations
Windows 7 Professional 64 bit Configuration for MassLynx Security 1. Purpose This document outlines the procedure to configure Microsoft Windows 7 Professional 64 bit operating system in order for installations
App Orchestration 2.0
 App Orchestration 2.0 Getting Started with Citrix App Orchestration 2.0 Prepared by: Jenny Berger Commissioning Editor: Erin Smith Version: 1.0 Last Updated: April 4, 2014 Page 1 Contents Welcome to App
App Orchestration 2.0 Getting Started with Citrix App Orchestration 2.0 Prepared by: Jenny Berger Commissioning Editor: Erin Smith Version: 1.0 Last Updated: April 4, 2014 Page 1 Contents Welcome to App
User Agent Preparing the Windows Environment and Installing the User Agent. How-To
 User Agent 1.1.5 Preparing the Windows Environment and Installing the User Agent How-To CONTENTS Introduction to the User Agent... 2 Selecting the User Account to Run the User Agent... 3 Setting Access
User Agent 1.1.5 Preparing the Windows Environment and Installing the User Agent How-To CONTENTS Introduction to the User Agent... 2 Selecting the User Account to Run the User Agent... 3 Setting Access
Installation Guide. . All right reserved. For more information about Specops Password Policy and other Specops products, visit
 . All right reserved. For more information about Specops Password Policy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Password Policy is a trademark owned by Specops
. All right reserved. For more information about Specops Password Policy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Password Policy is a trademark owned by Specops
1. HY 헤드라인 M(20pt) All about Data Connectivity Solutions
 All about Data Connectivity Solutions How to Setup OPC DCOM BridgeWare +82-31-346-1981 info@opchub.com DCOM Setup Procedure You need to configure DCOM on both server and client machines. Configure your
All about Data Connectivity Solutions How to Setup OPC DCOM BridgeWare +82-31-346-1981 info@opchub.com DCOM Setup Procedure You need to configure DCOM on both server and client machines. Configure your
RAP as a Service Active Directory Security: Prerequisites
 RAP as a Service Active Directory Security: Prerequisites This document explains the required steps to configure the RAP as a Service for Active Directory Security. There are two scenarios available to
RAP as a Service Active Directory Security: Prerequisites This document explains the required steps to configure the RAP as a Service for Active Directory Security. There are two scenarios available to
You need to make sure that branch office administrators are able to create and manage their own GPOs respectively.
 Enforce settings, Block inheritance Deny apply group policy Child group also called shadow group Set security permissions on the group -------------------------------- You need to make sure that branch
Enforce settings, Block inheritance Deny apply group policy Child group also called shadow group Set security permissions on the group -------------------------------- You need to make sure that branch
Managing Windows Environments with Group Policy
 Managing Windows Environments with Group Policy 50255D; 5 Days, Instructor-led Course Description In this course, you will learn how to reduce costs and increase efficiencies in your network. You will
Managing Windows Environments with Group Policy 50255D; 5 Days, Instructor-led Course Description In this course, you will learn how to reduce costs and increase efficiencies in your network. You will
Group Policy change monitoring, reporting, and alerting
 Group Policy change monitoring, reporting, and alerting Group Policy change monitoring, reporting, and alerting Every organization relies on Group Policy to control and manage users and computers in their
Group Policy change monitoring, reporting, and alerting Group Policy change monitoring, reporting, and alerting Every organization relies on Group Policy to control and manage users and computers in their
How to Configure IPSec Tunneling in Windows 2000
 Home Self Support Assisted Support Custom Support Worldwide Support How to Configure IPSec Tunneling in Windows 2000 The information in this article applies to: Article ID: Q252735 Last Reviewed: February
Home Self Support Assisted Support Custom Support Worldwide Support How to Configure IPSec Tunneling in Windows 2000 The information in this article applies to: Article ID: Q252735 Last Reviewed: February
Managing Group Policy application and infrastructure
 CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
Patch Manager INSTALLATION GUIDE. Version Last Updated: September 25, 2017
 INSTALLATION GUIDE Patch Manager Version 2.1.5 Last Updated: September 25, 2017 Retrieve the latest version from: https://support.solarwinds.com/success_center/patch_manager/patch_manager_documentation
INSTALLATION GUIDE Patch Manager Version 2.1.5 Last Updated: September 25, 2017 Retrieve the latest version from: https://support.solarwinds.com/success_center/patch_manager/patch_manager_documentation
Installation Guide. . All right reserved. For more information about Specops Deploy and other Specops products, visit
 . All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
. All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
KB How to Configure IPSec Tunneling in Windows 2000
 Page 1 of 5 Knowledge Base How to Configure IPSec Tunneling in Windows 2000 PSS ID Number: 252735 Article Last Modified on 3/17/2004 The information in this article applies to: Microsoft Windows 2000 Server
Page 1 of 5 Knowledge Base How to Configure IPSec Tunneling in Windows 2000 PSS ID Number: 252735 Article Last Modified on 3/17/2004 The information in this article applies to: Microsoft Windows 2000 Server
Remote Process Explorer
 Remote Process Explorer Frequently Asked Questions LizardSystems Table of Contents Introduction 3 What is Remote Process Explorer? 3 Before Installing 3 How can I download Remote Process Explorer? 3 Will
Remote Process Explorer Frequently Asked Questions LizardSystems Table of Contents Introduction 3 What is Remote Process Explorer? 3 Before Installing 3 How can I download Remote Process Explorer? 3 Will
20411D D Enayat Meer
 Lab A Module 8: Implementing Direct Access by Using the Getting Started Wizard Scenario: Recommended lab time is 240 Minutes {a complete class session is dedicated for this lab} Many users at A. Datum
Lab A Module 8: Implementing Direct Access by Using the Getting Started Wizard Scenario: Recommended lab time is 240 Minutes {a complete class session is dedicated for this lab} Many users at A. Datum
Windows XP Service Pack 2 Windows Firewall Group Policy Setup for Executive Software Products
 Windows XP Service Pack 2 Windows Firewall Group Policy Setup for Executive Software Products 1.0 Overview By default, Windows XP Service Pack 2 (SP2) enables Windows Firewall, previously known as Internet
Windows XP Service Pack 2 Windows Firewall Group Policy Setup for Executive Software Products 1.0 Overview By default, Windows XP Service Pack 2 (SP2) enables Windows Firewall, previously known as Internet
Virtual Recovery Assistant user s guide
 Virtual Recovery Assistant user s guide Part number: T2558-96323 Second edition: March 2009 Copyright 2009 Hewlett-Packard Development Company, L.P. Hewlett-Packard Company makes no warranty of any kind
Virtual Recovery Assistant user s guide Part number: T2558-96323 Second edition: March 2009 Copyright 2009 Hewlett-Packard Development Company, L.P. Hewlett-Packard Company makes no warranty of any kind
Sharing Data between Applications Connecting 2 PC s running ic/icontrol
 Sharing Data between Applications Connecting 2 PC s running ic/icontrol To connect two PC s running ic or icontrol products, you must have an Ethernet connection between them. The common situations are:
Sharing Data between Applications Connecting 2 PC s running ic/icontrol To connect two PC s running ic or icontrol products, you must have an Ethernet connection between them. The common situations are:
Below is the list of Windows Server Group Policy Interview Questions Asked in Windows System Administrator / L1/l2/l3 Support Engineer Interviews.
 Below is the list of Windows Server Group Policy Interview Questions Asked in Windows System Administrator / L1/l2/l3 Support Engineer Interviews. What is group policy in active directory? What are Group
Below is the list of Windows Server Group Policy Interview Questions Asked in Windows System Administrator / L1/l2/l3 Support Engineer Interviews. What is group policy in active directory? What are Group
MCSA Guide to Administering Microsoft Windows Server 2012/R2, Exam Chapter 10 Managing Group Policies
 MCSA Guide to Administering Microsoft Windows Server 2012/R2, Exam 70-411 Chapter 10 Managing Group Policies Objectives Configure group policy scope, precedence, and inheritance Configure group policy
MCSA Guide to Administering Microsoft Windows Server 2012/R2, Exam 70-411 Chapter 10 Managing Group Policies Objectives Configure group policy scope, precedence, and inheritance Configure group policy
Installation Guide. . All right reserved. For more information about Specops Deploy and other Specops products, visit
 . All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
. All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
Freshservice Discovery Probe User Guide
 Freshservice Discovery Probe User Guide 1. What is Freshservice Discovery Probe? 1.1 What details does Probe fetch? 1.2 How does Probe fetch the information? 2. What are the minimum system requirements
Freshservice Discovery Probe User Guide 1. What is Freshservice Discovery Probe? 1.1 What details does Probe fetch? 1.2 How does Probe fetch the information? 2. What are the minimum system requirements
Veritas System Recovery 16 Monitor Readme
 Veritas System Recovery 16 Monitor Readme About this readme Features No Longer Supported in Veritas System Recovery 16 Monitor About Veritas System Recovery 16 Monitor System requirements Prerequisites
Veritas System Recovery 16 Monitor Readme About this readme Features No Longer Supported in Veritas System Recovery 16 Monitor About Veritas System Recovery 16 Monitor System requirements Prerequisites
Windows Management Instrumentation Troubleshooting for Orion APM
 Windows Management Instrumentation Troubleshooting for Orion APM Why do my APM WMI Monitors Show Status Unknown?... 1 WMI Troubleshooting Flowchart for Orion APM 2 Testing Local WMI Services... 3 Test
Windows Management Instrumentation Troubleshooting for Orion APM Why do my APM WMI Monitors Show Status Unknown?... 1 WMI Troubleshooting Flowchart for Orion APM 2 Testing Local WMI Services... 3 Test
Click Studios. Passwordstate. Password Discovery, Reset and Validation. Requirements
 Passwordstate Password Discovery, Reset and Validation Requirements This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise
Passwordstate Password Discovery, Reset and Validation Requirements This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise
Cybowall Configuration Guide
 1. Cybowall Configuration Guide Last Modified 27 May 2018 Contents Introduction... 5 Initial Configuration Steps... 6 Network Scanning... 7 Before You Begin... 7 Determining the Network Environment...
1. Cybowall Configuration Guide Last Modified 27 May 2018 Contents Introduction... 5 Initial Configuration Steps... 6 Network Scanning... 7 Before You Begin... 7 Determining the Network Environment...
Purpose. Target Audience. Windows Machine Requirements. Windows Server Core (No Desktop) Nagios XI. Monitoring Windows Using WMI
 Purpose This document describes how to monitor Windows machines with Nagios XI using Windows Management Instrumentation (WMI). WMI allows for agentless monitoring of Windows machines which without having
Purpose This document describes how to monitor Windows machines with Nagios XI using Windows Management Instrumentation (WMI). WMI allows for agentless monitoring of Windows machines which without having
SolarWinds. Patch Manager. Evaluation Guide. Version 2.1.2
 This PDF is no longer being maintained. Search the SolarWinds Success Center for more information. SolarWinds Patch Manager Version 2.1.2 Evaluation Guide Last Updated: Friday, June 3, 2016 1 About SolarWinds
This PDF is no longer being maintained. Search the SolarWinds Success Center for more information. SolarWinds Patch Manager Version 2.1.2 Evaluation Guide Last Updated: Friday, June 3, 2016 1 About SolarWinds
Grant Minimum Permission to an Active Directory User Account Used by the Sourcefire User Agent
 Grant Minimum Permission to an Active Directory User Account Used by the Sourcefire User Agent Document ID: 118637 Contributed by Nazmul Rajib and Douglas Loss, Cisco TAC Engineers. Jun 05, 2015 Contents
Grant Minimum Permission to an Active Directory User Account Used by the Sourcefire User Agent Document ID: 118637 Contributed by Nazmul Rajib and Douglas Loss, Cisco TAC Engineers. Jun 05, 2015 Contents
Active Directory Auditing Guide
 Active Directory Auditing Guide www.adauditplus.com Table of Contents Document summary 1. Configuring Active Directory domains and domain controllers in ADAudit Plus 1.1 Automatic configuration 1.2 Manual
Active Directory Auditing Guide www.adauditplus.com Table of Contents Document summary 1. Configuring Active Directory domains and domain controllers in ADAudit Plus 1.1 Automatic configuration 1.2 Manual
No part of this document may be used for any purpose other than for the purposes specifically indicated herein nor may it be reproduced or
 UniOPC 3/07 No part of this document may be used for any purpose other than for the purposes specifically indicated herein nor may it be reproduced or transmitted in any form or by any means, electronic
UniOPC 3/07 No part of this document may be used for any purpose other than for the purposes specifically indicated herein nor may it be reproduced or transmitted in any form or by any means, electronic
Managing Group Policy application and infrastructure
 CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
MonitorPack Guard deployment
 MonitorPack Guard deployment Table of contents 1 - Download the latest version... 2 2 - Check the presence of Framework 3.5... 2 3 - Install MonitorPack Guard... 4 4 - Data Execution Prevention... 5 5
MonitorPack Guard deployment Table of contents 1 - Download the latest version... 2 2 - Check the presence of Framework 3.5... 2 3 - Install MonitorPack Guard... 4 4 - Data Execution Prevention... 5 5
White Paper. Deployment of ActiveX Controls via Microsoft Windows Active Directory. Fabasoft Folio 2016 Update Rollup 6
 White Paper Fabasoft Folio 2016 Update Rollup 6 Copyright Fabasoft R&D GmbH, Linz, Austria, 2017. All rights reserved. All hardware and software names used are registered trade names and/or registered
White Paper Fabasoft Folio 2016 Update Rollup 6 Copyright Fabasoft R&D GmbH, Linz, Austria, 2017. All rights reserved. All hardware and software names used are registered trade names and/or registered
EXAMGOOD QUESTION & ANSWER. Accurate study guides High passing rate! Exam Good provides update free of charge in one year!
 EXAMGOOD QUESTION & ANSWER Exam Good provides update free of charge in one year! Accurate study guides High passing rate! http://www.examgood.com Exam : 70-298 Title : Designing Security for a MS Windows
EXAMGOOD QUESTION & ANSWER Exam Good provides update free of charge in one year! Accurate study guides High passing rate! http://www.examgood.com Exam : 70-298 Title : Designing Security for a MS Windows
PROXY Pro Deployment Tool v10.0. User Guide October 2017
 PROXY Pro Deployment Tool v10.0 User Guide October 2017 Table of contents 1. System Requirements...3 2. Target Computer Requirements...4 3. Deployment Tool Operation...5 3.1 Loading a Host Install File...6
PROXY Pro Deployment Tool v10.0 User Guide October 2017 Table of contents 1. System Requirements...3 2. Target Computer Requirements...4 3. Deployment Tool Operation...5 3.1 Loading a Host Install File...6
SEVENMENTOR TRAINING PVT.LTD
 Installing and Configuring Windows Server 2012 Module 1: Deploying and Managing Windows Server 2012 This module introduces students to the editions of Windows Server 2012 and the new Windows Server 2012
Installing and Configuring Windows Server 2012 Module 1: Deploying and Managing Windows Server 2012 This module introduces students to the editions of Windows Server 2012 and the new Windows Server 2012
Océ Scan Router. Océ Scan Router Administrators Guide. Scan Distribution System
 Scan Router Océ Scan Router Administrators Guide Océ Scan Router Administrators Guide Scan Distribution System Océ Scan Router is a tool desig ned to help distribute scan files from any scan capable device
Scan Router Océ Scan Router Administrators Guide Océ Scan Router Administrators Guide Scan Distribution System Océ Scan Router is a tool desig ned to help distribute scan files from any scan capable device
Microsoft User Experience Virtualization Deployment Guide
 Microsoft User Experience Virtualization Deployment Guide Microsoft User Experience Virtualization (UE-V) is an enterprise-scalable user state virtualization solution that can provide users a consistent
Microsoft User Experience Virtualization Deployment Guide Microsoft User Experience Virtualization (UE-V) is an enterprise-scalable user state virtualization solution that can provide users a consistent
Introduction to Firewalls using IPTables
 Introduction to Firewalls using IPTables The goal of this lab is to implement a firewall solution using IPTables, and to write and to customize new rules to achieve security. You will need to turn in your
Introduction to Firewalls using IPTables The goal of this lab is to implement a firewall solution using IPTables, and to write and to customize new rules to achieve security. You will need to turn in your
6 Months Training Module in MS SQL SERVER 2012
 6 Months Training Module in MS SQL SERVER 2012 Module 1 Installing and Configuring Windows Server 2012 Installing and Managing Windows Server 2012 Windows Server 2012 Overview Installing Windows Server
6 Months Training Module in MS SQL SERVER 2012 Module 1 Installing and Configuring Windows Server 2012 Installing and Managing Windows Server 2012 Windows Server 2012 Overview Installing Windows Server
AVG Business Edition Remote Administration
 AVG Business Edition Remote Administration User Manual Document revision AVG.02 (1/7/2018) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective
AVG Business Edition Remote Administration User Manual Document revision AVG.02 (1/7/2018) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective
Windows Server 2003 Network Administration Goals
 Objectives Differentiate between the different editions of Windows Server 2003 Explain Windows Server 2003 network models and server roles Identify concepts relating to Windows Server 2003 network management
Objectives Differentiate between the different editions of Windows Server 2003 Explain Windows Server 2003 network models and server roles Identify concepts relating to Windows Server 2003 network management
Microsoft Exactexams Questions & Answers
 Microsoft Exactexams 70-410 Questions & Answers Number: 70-410 Passing Score: 800 Time Limit: 120 min File Version: 32.7 http://www.gratisexam.com/ Microsoft 70-410 Questions & Answers Exam Name: Installing
Microsoft Exactexams 70-410 Questions & Answers Number: 70-410 Passing Score: 800 Time Limit: 120 min File Version: 32.7 http://www.gratisexam.com/ Microsoft 70-410 Questions & Answers Exam Name: Installing
Parallels Mac Management for Microsoft SCCM
 Parallels Mac Management for Microsoft SCCM Administrator's Guide v4.5 Copyright 1999-2016 Parallels IP Holdings GmbH and its affiliates. All rights reserved. Parallels IP Holdings GmbH Vordergasse 59
Parallels Mac Management for Microsoft SCCM Administrator's Guide v4.5 Copyright 1999-2016 Parallels IP Holdings GmbH and its affiliates. All rights reserved. Parallels IP Holdings GmbH Vordergasse 59
Dell GPOADmin 5.7. About Dell GPOADmin 5.7. New features. Release Notes. December 2013
 Dell GPOADmin 5.7 December 2013 These release notes provide information about the Dell GPOADmin release. About Dell GPOADmin 5.7 New features Resolved issues s System requirements Product licensing Getting
Dell GPOADmin 5.7 December 2013 These release notes provide information about the Dell GPOADmin release. About Dell GPOADmin 5.7 New features Resolved issues s System requirements Product licensing Getting
Welcome to PDQ Inventory
 Getting Started Contents Welcome to PDQ Inventory........ 1 Licensing.................... 2 PDQ Inventory Licensing Mode Comparison.................. 2 PDQ Inventory Product Feature Comparison..................
Getting Started Contents Welcome to PDQ Inventory........ 1 Licensing.................... 2 PDQ Inventory Licensing Mode Comparison.................. 2 PDQ Inventory Product Feature Comparison..................
Sharpdesk V3.3. Push Installation Guide for system administrator Version
 Sharpdesk V3.3 Push Installation Guide for system administrator Version 3.3.04 Copyright 2000-2010 by SHARP CORPORATION. All rights reserved. Reproduction, adaptation or translation without prior written
Sharpdesk V3.3 Push Installation Guide for system administrator Version 3.3.04 Copyright 2000-2010 by SHARP CORPORATION. All rights reserved. Reproduction, adaptation or translation without prior written
Manual. DriveLock Setup. Quick Start Guide
 Manual DriveLock Setup Quick Start Guide DriveLock SE 2017 Contents 1 INTRODUCTION... 2 2 REQUIREMENTS... 2 3 INSTALLATION / UPDATE... 3 3.1 DRIVELOCK ENTERPRISE SERVICE AND MANAGEMENT COMPONENTS... 3
Manual DriveLock Setup Quick Start Guide DriveLock SE 2017 Contents 1 INTRODUCTION... 2 2 REQUIREMENTS... 2 3 INSTALLATION / UPDATE... 3 3.1 DRIVELOCK ENTERPRISE SERVICE AND MANAGEMENT COMPONENTS... 3
StoneFax provides the Print To Fax feature to any user who is in the same Windows Domain of the StoneFax server.
 Print To Fax StoneFax provides the Print To Fax feature to any user who is in the same Windows Domain of the StoneFax server. Note: StoneFax and the client PC using this feature must be in the same Windows
Print To Fax StoneFax provides the Print To Fax feature to any user who is in the same Windows Domain of the StoneFax server. Note: StoneFax and the client PC using this feature must be in the same Windows
VMware vrealize Operations for Published Applications Installation and Administration
 VMware vrealize Operations for Published Applications Installation and Administration vrealize Operations for Published Applications 6.4 This document supports the version of each product listed and supports
VMware vrealize Operations for Published Applications Installation and Administration vrealize Operations for Published Applications 6.4 This document supports the version of each product listed and supports
Exam Identity with Windows Server 2016
 MCSA / MCSE for Windows Server 2016 Exam 70-742 Identity with Windows Server 2016 Version 15.35 (198 Questions) (70-742) Identify with Windows Server 2016 QUESTION 1 You have a server named Server1 that
MCSA / MCSE for Windows Server 2016 Exam 70-742 Identity with Windows Server 2016 Version 15.35 (198 Questions) (70-742) Identify with Windows Server 2016 QUESTION 1 You have a server named Server1 that
Setting up Certificate Authentication for SonicWall SRA / SMA 100 Series
 Setting up Certificate Authentication for SonicWall SRA / SMA 100 Series SonicWall SRA and SMA devices now have the option to authenticate using Client User Certificates. This is a guide on how to implement
Setting up Certificate Authentication for SonicWall SRA / SMA 100 Series SonicWall SRA and SMA devices now have the option to authenticate using Client User Certificates. This is a guide on how to implement
Getting started with System Center Essentials 2007
 At a glance: Installing and upgrading Configuring Essentials 2007 Troubleshooting steps Getting started with System Center Essentials 2007 David Mills System Center Essentials 2007 is a new IT management
At a glance: Installing and upgrading Configuring Essentials 2007 Troubleshooting steps Getting started with System Center Essentials 2007 David Mills System Center Essentials 2007 is a new IT management
GT-SCCM Onboard/Environment Overview
 GT-SCCM Onboard/Environment Overview Page 1 Server Information: Name: GT-SCCM.ad.gatech.edu IP: 130.207.162.14 Site Code for SCCM: GTS SCCM Version: 1802 Firewall Information: If you are planning on using
GT-SCCM Onboard/Environment Overview Page 1 Server Information: Name: GT-SCCM.ad.gatech.edu IP: 130.207.162.14 Site Code for SCCM: GTS SCCM Version: 1802 Firewall Information: If you are planning on using
Secure Web Appliance. SSL Intercept
 Secure Web Appliance SSL Intercept Table of Contents 1. Introduction... 1 1.1. About CYAN Secure Web Appliance... 1 1.2. About SSL Intercept... 1 1.3. About this Manual... 1 1.3.1. Document Conventions...
Secure Web Appliance SSL Intercept Table of Contents 1. Introduction... 1 1.1. About CYAN Secure Web Appliance... 1 1.2. About SSL Intercept... 1 1.3. About this Manual... 1 1.3.1. Document Conventions...
Module 9. Configuring IPsec. Contents:
 Configuring IPsec 9-1 Module 9 Configuring IPsec Contents: Lesson 1: Overview of IPsec 9-3 Lesson 2: Configuring Connection Security Rules 9-11 Lesson 3: Configuring IPsec NAP Enforcement 9-21 Lab: Configuring
Configuring IPsec 9-1 Module 9 Configuring IPsec Contents: Lesson 1: Overview of IPsec 9-3 Lesson 2: Configuring Connection Security Rules 9-11 Lesson 3: Configuring IPsec NAP Enforcement 9-21 Lab: Configuring
Click Studios. Passwordstate. Password Discovery, Reset and Validation. Requirements
 Passwordstate Password Discovery, Reset and Validation Requirements This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise
Passwordstate Password Discovery, Reset and Validation Requirements This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise
Using CSC SSM with Trend Micro Damage Cleanup Services
 APPENDIXD Using CSC SSM with Trend Micro Damage Cleanup Services Trend Micro InterScan for CSC SSM works with Trend Micro Damage Cleanup Services (DCS) as part of an enterprise protection strategy. The
APPENDIXD Using CSC SSM with Trend Micro Damage Cleanup Services Trend Micro InterScan for CSC SSM works with Trend Micro Damage Cleanup Services (DCS) as part of an enterprise protection strategy. The
SQL Server 2016 installation/setup instructions
 SQL Server 2016 installation/setup instructions Abbreviated notes for installing SQL 2016 servers. Installation Install SQL Server 2016 and then configure it as per below. Some steps like the SQL Server
SQL Server 2016 installation/setup instructions Abbreviated notes for installing SQL 2016 servers. Installation Install SQL Server 2016 and then configure it as per below. Some steps like the SQL Server
VMware vrealize Operations for Published Applications Installation and Administration
 VMware vrealize Operations for Published Applications Installation and Administration vrealize Operations for Published Applications 6.2 This document supports the version of each product listed and supports
VMware vrealize Operations for Published Applications Installation and Administration vrealize Operations for Published Applications 6.2 This document supports the version of each product listed and supports
Personal vdisk Implementation Guide. Worldwide Technical Readiness
 Worldwide Technical Readiness Table of Contents Table of Contents... 2 Overview... 3 Implementation Guide... 4 Pre-requisites... 5 Preparing PVS vdisk to be used with Personal vdisk... 6 Creating a Desktop
Worldwide Technical Readiness Table of Contents Table of Contents... 2 Overview... 3 Implementation Guide... 4 Pre-requisites... 5 Preparing PVS vdisk to be used with Personal vdisk... 6 Creating a Desktop
Turn On Windows Firewall Manually Windows 7 Remote Management
 Turn On Windows Firewall Manually Windows 7 Remote Management When the Firewall is disabled on any Windows 7 workstation machine, no error is logged and the Remote Management works fine. I did some digging,
Turn On Windows Firewall Manually Windows 7 Remote Management When the Firewall is disabled on any Windows 7 workstation machine, no error is logged and the Remote Management works fine. I did some digging,
LepideAuditor. Installation and Configuration Guide
 Installation and Configuration Guide Table of Contents 1. Introduction... 6 2. Requirements and Prerequisites... 6 2.1 System Requirements... 6 2.2 Supported Servers for Auditing... 7 2.3 Prerequisites
Installation and Configuration Guide Table of Contents 1. Introduction... 6 2. Requirements and Prerequisites... 6 2.1 System Requirements... 6 2.2 Supported Servers for Auditing... 7 2.3 Prerequisites
PRAGATHI TECHNOLOGIES BTM Marathahalli Ph:
 PRAGATHI TECHNOLOGIES BTM Marathahalli Ph: 97420-95494 Course 20413C: Designing and Implementing a Server Infrastructure Course Outline Module 1: Planning Server Upgrade and Migration This module explains
PRAGATHI TECHNOLOGIES BTM Marathahalli Ph: 97420-95494 Course 20413C: Designing and Implementing a Server Infrastructure Course Outline Module 1: Planning Server Upgrade and Migration This module explains
Pcounter for Windows
 Pcounter for Windows Pcounter Client and Printer Distribution Guide Copyright 2014 A.N.D. Technologies 4104 24 th Street #627 San Francisco, CA 94114 USA E-Mail: support@pcounter.com Web: http://www.pcounter.com
Pcounter for Windows Pcounter Client and Printer Distribution Guide Copyright 2014 A.N.D. Technologies 4104 24 th Street #627 San Francisco, CA 94114 USA E-Mail: support@pcounter.com Web: http://www.pcounter.com
How to guide: Setup RMSSA for Security Manager
 How to guide: Setup RMSSA for Security Manager The intention of this guide is to give instructions on how to adjust the settings and configurations of RMS Security Patch Manager in order to use the RayManageSoft
How to guide: Setup RMSSA for Security Manager The intention of this guide is to give instructions on how to adjust the settings and configurations of RMS Security Patch Manager in order to use the RayManageSoft
RALS Remote Connect (RRC) Version 2.2 Installation and Configuration Instructions
 RALS Remote Connect (RRC) Installation and Configuration Instructions Contents Page Overview.. 2 RRC v2.2 Installation Procedure... 3 Configuring the RRC 2.2 Software.. 6 Procedure for Uninstalling RRC
RALS Remote Connect (RRC) Installation and Configuration Instructions Contents Page Overview.. 2 RRC v2.2 Installation Procedure... 3 Configuring the RRC 2.2 Software.. 6 Procedure for Uninstalling RRC
Self-Service Password Reset
 Citrix Product Documentation docs.citrix.com September 21, 2018 Contents Self-Service Password Reset 1.1.x 3 What s new 3 What s new in version 1.1.20................................... 3 What s new in
Citrix Product Documentation docs.citrix.com September 21, 2018 Contents Self-Service Password Reset 1.1.x 3 What s new 3 What s new in version 1.1.20................................... 3 What s new in
Barracuda Outlook Add-In Deployment Guide version 7 and Above
 Barracuda Outlook Add-In Deployment Guide version 7 and Above This article applies to the Barracuda Email Security Gateway running version 7 and above. For information about the features of the Barracuda
Barracuda Outlook Add-In Deployment Guide version 7 and Above This article applies to the Barracuda Email Security Gateway running version 7 and above. For information about the features of the Barracuda
SOLUS3 for Schools. Applicable to onwards
 SOLUS3 for Schools Applicable to 3.10.88 onwards Revision History Version Change Description Date 3.10.88-1.0 Initial release. 24/03/2016 Capita Business Services Ltd 2016. All rights reserved. No part
SOLUS3 for Schools Applicable to 3.10.88 onwards Revision History Version Change Description Date 3.10.88-1.0 Initial release. 24/03/2016 Capita Business Services Ltd 2016. All rights reserved. No part
Quest GPOADmin 5.6. User Guide
 Quest GPOADmin 5.6 User Guide 2012 Quest Software, Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished under
Quest GPOADmin 5.6 User Guide 2012 Quest Software, Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished under
ms-help://ms.technet.2004apr.1033/win2ksrv/tnoffline/prodtechnol/win2ksrv/howto/grpolwt.htm
 Page 1 of 17 Windows 2000 Server Step-by-Step Guide to Understanding the Group Policy Feature Set Operating System Abstract Group Policy is the central component of the Change and Configuration Management
Page 1 of 17 Windows 2000 Server Step-by-Step Guide to Understanding the Group Policy Feature Set Operating System Abstract Group Policy is the central component of the Change and Configuration Management
Step-by-step installation guide for monitoring untrusted servers using Operations Manager
 Step-by-step installation guide for monitoring untrusted servers using Operations Manager Most of the time through Operations Manager, you may require to monitor servers and clients that are located outside
Step-by-step installation guide for monitoring untrusted servers using Operations Manager Most of the time through Operations Manager, you may require to monitor servers and clients that are located outside
Installing and Configuring Windows Server 2012
 Microsoft 70-410 Installing and Configuring Windows Server 2012 Version: Demo 23.0 QUESTION NO: 1 Microsoft 70-410 Exam named ABC.com. All servers in the ABC.com domain, including domain controllers, have
Microsoft 70-410 Installing and Configuring Windows Server 2012 Version: Demo 23.0 QUESTION NO: 1 Microsoft 70-410 Exam named ABC.com. All servers in the ABC.com domain, including domain controllers, have
Designing and Implementing a Server Infrastructure
 Designing and Implementing a Server Infrastructure Duration: 5 Days Course Code: 20413 About this course Get hands-on instruction and practice planning, designing and deploying a physical and logical Windows
Designing and Implementing a Server Infrastructure Duration: 5 Days Course Code: 20413 About this course Get hands-on instruction and practice planning, designing and deploying a physical and logical Windows
Defining Notifications Reminders
 Defining Notifications E-mail Reminders www.docusnap.com TITLE Defining Notifications AUTHOR Docusnap Consulting DATE 07/07/2015 The reproduction and distribution of this document as a whole or in part
Defining Notifications E-mail Reminders www.docusnap.com TITLE Defining Notifications AUTHOR Docusnap Consulting DATE 07/07/2015 The reproduction and distribution of this document as a whole or in part
Password Reset Utility. Configuration
 Password Reset Utility Configuration 1 Table of Contents 1. Uninstalling Legacy Password Reset... 2 2. Password Reset Utility: How to deploy and configure via Group Policy... 2 3. Configuring Group Policy
Password Reset Utility Configuration 1 Table of Contents 1. Uninstalling Legacy Password Reset... 2 2. Password Reset Utility: How to deploy and configure via Group Policy... 2 3. Configuring Group Policy
Parallels Mac Management for Microsoft SCCM
 Parallels Mac Management for Microsoft SCCM Administrator's Guide v6.1 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright 1999-2017
Parallels Mac Management for Microsoft SCCM Administrator's Guide v6.1 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright 1999-2017
Contents. Managing Places...3. Contents 2
 Managing Places Contents 2 Contents Managing Places...3 Creating a Site Structure...3 Managing Spaces...4 Designing Space Hierarchies... 5 Changing the Name of the Root Space...5 Space Creation Options...
Managing Places Contents 2 Contents Managing Places...3 Creating a Site Structure...3 Managing Spaces...4 Designing Space Hierarchies... 5 Changing the Name of the Root Space...5 Space Creation Options...
One Identity Active Roles 7.2. Web Interface Administrator Guide
 One Identity Active Roles 7.2 Web Interface Administrator Guide Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described
One Identity Active Roles 7.2 Web Interface Administrator Guide Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described
Security Removable Media Manager
 Security Removable Media Manager Version 9.9.0.0 (January 2018) Protect your valuable data 2011 Squadra Technologies, LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by
Security Removable Media Manager Version 9.9.0.0 (January 2018) Protect your valuable data 2011 Squadra Technologies, LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by
Authentication Services ActiveRoles Integration Pack 2.1.x. Administration Guide
 Authentication Services ActiveRoles Integration Pack 2.1.x Administration Guide Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright.
Authentication Services ActiveRoles Integration Pack 2.1.x Administration Guide Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright.
INUVIKA TECHNICAL GUIDE
 Version 1.6 December 13, 2018 Passing on or copying of this document, use and communication of its content not permitted without Inuvika written approval PREFACE This document describes how to integrate
Version 1.6 December 13, 2018 Passing on or copying of this document, use and communication of its content not permitted without Inuvika written approval PREFACE This document describes how to integrate
Healthcare Desktop Office GPO Templates for GPMC v1
 Healthcare Desktop Office GPO Templates for GPMC v1 Release Notes Prepared by Microsoft First published 27 September 2007 Copyright This document and/or software ( this Content ) has been created in partnership
Healthcare Desktop Office GPO Templates for GPMC v1 Release Notes Prepared by Microsoft First published 27 September 2007 Copyright This document and/or software ( this Content ) has been created in partnership
Find MAC Address. Getting Started. LizardSystems
 Find MAC Address Getting Started LizardSystems Table of Contents Introduction 3 Installing Find MAC Address 3 Starting the application 4 Main Window 6 Main Menu 6 File menu 6 Edit menu 7 Tools menu 8 Administrative
Find MAC Address Getting Started LizardSystems Table of Contents Introduction 3 Installing Find MAC Address 3 Starting the application 4 Main Window 6 Main Menu 6 File menu 6 Edit menu 7 Tools menu 8 Administrative
